Text
The Differences Between Types of Tokens

At first glance, tokens can appear complicated. The oldest and perhaps simplest example of a digital token is Bitcoin. It’s often referred to as digital cash or digital gold — but which is it? And what gives it value? And how does it work? Going down this rabbit hole is fun, but time consuming, and ultimately not required to obtain a high-level understanding of the different types of tokens.
Tokens have many nuanced differentiators such as use case, structure, governance rights, fungibility, and others, and therefore fall into different classifications similar to how you might think of taxonomies in biology. Just like biologists classified the world into domains, kingdoms, phylums, etc., token designers are now discovering and classifying emerging tokens in the blockchain ecosystem.
By and large, tokens fall into two broad categories: fungible and non-fungible.
Fungible tokens are essentially interchangeable for one another and are most often compared to dollar bills. You don’t really care about the serial number or date of creation for the dollar bill a clerk gives you because the one printed in 1998 has the same nominal value and is accepted by the same people as the one printed yesterday.
Non-fungible tokens (NFTs) means that each one is unique. Plane tickets, for example, are unique in that each is tagged to a specific individual, time, flight, and destination. You can trade plane tickets with a random person at the airport, but it’s unlikely you’ll be able to use theirs to get to your desired destination.
So how are these fungible and non-fungible tokens used?
Fungible tokens are really great for regular transactions and standardized exchanges of value. We want one bitcoin from Alice to be equal in value and accepted by the same people as one bitcoin from Bob. All ERC-20 tokens on Ethereum, such as Augur or 0x, are also fungible, as are most other cryptocurrencies. You can use them to:
· Transact with other individuals and companies
· Stake on certain outcomes (e.g., outcomes of an Augur prediction market)
· Stake to provide a service (think taxi medallions)
· Use as collateral for crypto-backed loans
· Make loans
· … And most other things that you can also do with dollars
Non-fungible tokens, often represented by ERC-721’s on Ethereum, get quite a bit more interesting because they can essentially represent just about anything in the world. These can be broken up into two primary categories: digitally native and digital representations. They either exist on their own for their own sake or are tied to another object (whether physical or digital).
Cryptokitties is the most famous example of a digitally native non-fungible token. They were created as a blockchain-based game and reside within the Ethereum ecosystem. There weren’t physical plushies previously on which the kitties were based or a previous version of the game that didn’t use blockchain.
Land registries and home ownership “on the blockchain” is a common example of a digital representation non-fungible token. The land or the house itself is not on the blockchain, of course, but a record of it is. And if you create non-fungible tokens that represent land deeds on the blockchain so that whoever owns that token is the one that owns the land, then you’ve effectively created a blockchain-based digital representation of a real world asset.
What about consumer and security tokens?
This is yet another classification that’s important to understand, but on which token designers are still working out the kinks. Consumer tokens are not a legally-recognized distinction because nothing like it existed before and it doesn’t fit neatly into any established precedent.
For now, consumer tokens are viewed as giving access to a protocol’s or company’s products or service without implicating the securities laws.
When selling consumer tokens, projects should ensure that people are buying and using the token so that they can interact with that protocol or company– not so that they can speculate. This is really good for several reasons:
· If many speculators hold the token, its price will be artificially high, making it expensive for regular individuals to interact with the protocol or company
· Speculators increase the volatility of your token because they buy/sell it based on its future price, not its current utility
· Having real users, not speculators, in possession of these tokens creates a community of people interacting with your product, providing feedback, recommending it to their friends, and generally helping the network grow
Token Foundry takes this distinction seriously and has created the Token Foundry Standards, a framework for selling consumer tokens and launching decentralized networks in a way that directs the tokens offered in the sale to actual users of these networks.
Security tokens, on the other hand, are tradable blockchain-based assets that fall under traditional definitions of securities (i.e., debt or equity). They are subject to all the same regulations as regular non-blockchain based securities. There’s two really exciting areas in security tokens that hold a lot of promise:
1. Securitizing more things
2. Increasing liquidity, efficiency, speed of execution, and security
Securitizing is the process of “converting (an asset, especially a loan) into marketable securities, typically for the purpose of raising cash by selling them to other investors.” It can often be an expensive proposition, as there are numerous legal and financial restraints and requirements and third party costs involved in the issuance, management, tracking, securing, trade execution, settlement, etc. of these securities.
Blockchain and, more specifically, smart contracts offer the possibility of making those costs plummet while making these securities more liquid, cutting out middlemen to increase efficiency and speed of execution, and making them more secure (code is law). For example, you would be able to securitize many new assets like fine art that were previously cost-prohibitive, allowing for fractional ownership. You could also structure auditable collateralized debt obligations with programmatically defined payments to owners of various tranches that auto-execute, eliminating enormous inefficiencies in reconciliation.
The interesting bit is that fungible vs non-fungible and consumer vs security classifications actually interact. You can have:
· Fungible consumer tokens such as Augur tokens
· Non-fungible consumer tokens such as Cryptokitties
· Fungible securities such as blockchain-based equities
· Non-fungible securities such as blockchain-based land deeds
But aside from the classifications we have already discovered, the truth remains that we are more excited about ones that are still a mystery. No one could have predicted the incredible advances in the internet and how it would fundamentally change our social structures, networks, work styles, and many more things. This is the potential of tokens now — we don’t know what will come, but we know it will be incredible.
0 notes
Text
What Is The Metaverse?

The Metaverse is the sum of all shared, persistent virtual spaces. It is the totality of all the digital and virtual worlds as well as digital assets and the data on the entire internet.
Merging The Digital & The Physical
There are several projects which are creating digital twins of our physical world and building apps and programs that can be overlaid and used in our local environments. These programs will enrich the physical world around us by filling it with information and making use cases available at our fingertips.
AR applications in the metaverse will enable users to choose from several layers which can be projected onto their current surroundings. We’ve had to go to our devices to access the internet and the information on it, but the metaverse combined with AR, VR, and MR will allow applications to take information about locations and things and digitally place them into the physical world where it is relevant.
We’ll be able to interact with this information layer through augmented reality or virtual reality devices. Users will be able to experience the internet all around them using connected devices whenever and wherever they like.
Characteristics of the Metaverse
The metaverse is a concept that is still evolving but it has some common characteristics. Some recognizable characteristics of the metaverse are:
1. The worlds and digital assets in the metaverse are live and constantly available. If a user logs on it doesn’t mean the digital world in that area gets shut off, it just means the user has logged out of that world and it will be available whenever they decide to back in.
2. Interoperability will be built into many of the digital assets and information in the metaverse. This means the assets and information will be available and interchangeable across different digital worlds and environments.
3. The metaverse will be able to host experiences and content that is available to the users on it to access whenever they like.
4. It will be able to host audiences of any size. Meaning the system will have enough bandwidth to offer an audience of any size at any given time.
5. The metaverse will be accessible using multiple different physical devices and ISP providers. An example of this is a popular website like google is available to users regardless of which device and ISP provider they are using.
6. There will be a fully functioning economy on the metaverse. There will most likely be fully functioning economies on numerous applications and layers of the metaverse.
7. It will consist of a complex network of different platforms, applications, and digital worlds.
Technologies Used In The Metaverse
To function optimally the metaverse will rely on the following technologies among others:
· In order to stream high-quality stream data and content in real-time applications within the metaverse will lean on strong 5G & 6G networks
· Access Devices which support Augmented Reality, Virtual Reality & Mixed Reality viewing will be necessary to properly experience all of the applications on the metaverse
· A wide set of protocols and languages will underlie the applications and content delivery mechanisms within the metaverse
· Secure Cryptocurrencies with minimal transaction fees will enable on-platform instantly auditable peer to peer transactions
· The ownership of digital assets and virtual items in the metaverse will be easy to verify and trade using NFTs (non-fungible tokens)and the underlying secured blockchain platforms, NFTs will also change the way digital rights of assets and content are licensed and distributed
· Smart Contracts will allow users to create and execute complex transactions with service providers and other users within the virtual worlds, smart contracts will also be used by application providers within the network to manage their contracts and relationships with other vendors and users
· In order to allow millions of people to attend a particular live event in a given digital location at the same time in the metaverse some issues related to server capacity and latency might arise. Developers are likely to use a technique called Sharding to work around this problem. Sharding creates batches of users and assigns each batch a unique digital venue. The live event can then be broadcast to each batch simultaneously. In practice, this would enable millions of users to attend the event together and be part of a similar shared experience without overloading the digital architecture of the system.
Culture Within the Metaverse
Much like how many subcultures have developed in games like World of Warcraft or GTA V, communities in the applications games and platforms within the metaverse will develop numerous subcultures as well. Cultures will develop around applications, interest groups, use cases, geography, and purpose.
Economy Within the Metaverse
Virtual economies exist across several applications today. Within the metaverse larger and more connected virtual economies will exist. Activities as diverse as world-building, charity, concerts, fashion, shopping, advertising, education, politics and activism will find a place in the metaverse. A lot of the applications will offer cryptocurrencies and Peer to Peer transactions as mediums of payment between their users.
Conclusion
The metaverse is the next frontier for online interaction which will unlock a new generation of apps, platforms and use cases. It will redefine the digital space. Organizations that take the time to understand and adapt their digital strategies to properly engage with the metaverse will be at an advantage.
If you have questions and requests, leave comments below the article.
0 notes
Text
How Blockchain Web 3.0 Is Changing Industries

In this article, we’re having a look at the impact of Web 3.0 and blockchain on traditional industries. But first, for those of you who are unfamiliar with Web 3.0, here is a quick recap.
Many experts and companies describe Web 3.0 in a different way. For example, Coinmarketcap describes Web 3.0 as an internet in which data will be interconnected in a decentralized way. Forbes describes Web 3.0 as something that will bring us a fairer internet by enabling the individual to be a sovereign. True sovereignty implies owning and being able to control who profits from one’s time and information.
And so, these definitions make one thing clear, Web 3.0 is all about decentralization and its users. In Web 3.0 machines and users can interact with data; however, this can only happen if programs understand information both conceptually and contextually. This leads us to the cornerstones of Web 3.0: semantic web and artificial intelligence (AI). Web 3.0 is driven by blockchain technology, decentralized protocols and cryptocurrencies and is opening the phase of the internet revolution in which the true power lies in the hands of the users.
Web 3.0 is preparing to change how businesses operate and how internet users interact with the digital world, thanks to the most disruptive technology of our time. In this article, we will look in-depth at Web 3.0 Blockchain.
The Benefits of Web 3.0
Web 3.0 features include pro-privacy and anti-monopoly models. It will not incentivize centralized platforms that retain control over their users’ data. A shift with decentralization and privacy at the forefront will happen. Users are now in control of their data, and tech monopolies on Web 3.0 will no longer exist, thus data privacy violations will almost never happen.
Secondly, Web 3.0 is a lot more secure than its predecessor's Web 1.0 and 2.0; because of the decentralized and distributed nature. On Web 3.0 it is almost impossible for hackers to penetrate the network without the operation being traced back to them. Additionally, the data generated by users that were previously owned by tech giants will now be owned by the users. Data transmitted over the network will be completely encrypted. Users will be able to choose which information they want to share with corporations and advertising firms, and they will be able to earn money from it.
Then, there is interoperability. Web 3.0 features enable users to access data across multiple applications without being restricted to a single platform. This means you won’t have to worry about one device having access to Web 3.0 while others don’t. Finally, Web 3.0 is based on permissionless blockchain, and thus, doesn’t need a central authority. Anyone will be able to join and participate in the network by creating an address. This will eliminate the possibility of users being barred based on their gender, income, orientation, geographical location, or other sociological factors. It will also make it possible to transfer digital assets and wealth across borders in a timely and cost-effective manner.
Blockchain Web 3.0 In Different Industries
While blockchain Web 3.0 has the possibility to change many more industries, in this article we’ll expand on ten of them.
Finance and Banking
Decentralized Finance or Open Finance is already a 55 billion USD industry and digital currencies have already become a cross-border, global store of value. In fact, El Salvador recently became the first country to recognize cryptocurrency Bitcoin as their second national currency. DeFi is working hard on revolutionizing the banking and finance industry by making it more decentralized and giving authority back to its users. Furthermore, while digitizing currencies requires retooling in the banking system, Web 3.0 could make this possible. Moreover, securities and other tradable assets could also use blockchain signatures to ensure security and allow for around-the-clock trading.
Real Estate
A distributed ledger can also be used to record and manage land and resources. A global property ownership blockchain could be made up of satellite imagery, computer vision, and government records. Buying and selling real estate becomes as simple as transferring a digital certificate. Web 3.0 will make real estate transactions faster and easier in thriving economies. It can make a huge difference in the developing world for people who have lived on a piece of land for a long time but do not have any legal documentation of ownership.
Voting and Governance
Online voting has long been a dream of technophiles, dating back to the early days of the World Wide Web. The problem is that Web 1.0 and 2.0 don’t have good solutions for verifying identity, preventing duplicate voting, and protecting against attacks. Blockchain, AI, and facial recognition/biometrics assist in resolving these issues by enabling independent, verifiable online identities.
Advertising
Web 2.0 has had a significant impact on advertising, which has increasingly moved online. This means that companies have an incentive to collect and sell user data, which is bad for your privacy and attention. Furthermore, online ad fraud occurs when bad actors use bots to simulate impressions and clicks, charging advertisers for traffic that will never result in a purchase. Web 3.0 technologies will assist by keeping user data in users’ hands and allowing them to decide how to share or sell their information. By verifying impressions and clicks with the user’s identity, these new technologies will also prevent many types of ad fraud.
Computing and Data-Storage
Companies like Google Drive and Dropbox own massive amounts of user data, but they are centralized, vulnerable to attack, and expensive. A better solution could be to store data on unused space across thousands of computers on a decentralized network. Encryption and file sharding techniques enable this with redundancy and reduced vulnerability to attack. Furthermore, network node processing power is another resource for Web 3.0, and this decentralized infrastructure will become increasingly important as Web 3.0 matures.
Healthcare
From the standpoint of data security, storing data on the blockchain makes sense. It also has the added benefit of allowing your care providers to share your records if you give consent. Real-time health data will be able to write directly from your body to the blockchain as wearable devices and sensors become more popular. AI algorithms can then recommend when to see a doctor.
Social Networking and Other Entertainment Forms
Any service that requires login authentication and user data input could benefit from a distributed ledger that is encrypted. AI is already making recommendations for things to do, content to watch and read, and people to meet. To take it a step further, IoT in the real world, as well as augmented and virtual reality, have the potential to fundamentally alter how we interact online and in person.
Insurance
On a case-by-case basis, AI can learn to evaluate risk and assess claims. Then, when claims are filed, blockchain smart contracts can collect payments and automate payouts. Consider paying your car insurance on a daily or even hourly basis, with a higher premium when you’re stuck in traffic and a lower premium when your car is parked in your driveway.
Logistics
Blockchain technology has the potential to create a global ledger that makes the supply chain for products transparent. Furthermore, IoT sensors embedded in the products can update the blockchain ledger at each stage of production and shipment. Companies become more efficient when they have a clear view of the supply chain, and consumers can verify the sustainability of the products they buy.
Ecommerce
With Web 3.0 marketplaces will no longer need to rely on a central authority to bring buyers and sellers together. Instead, vendors can sell directly to consumers through open platforms.
Final Thoughts
As the blockchain space progresses, so do the implementations for Web 3.0. More and more use cases appear, and more and more people believe in a decentralized future. At Stakin, we are excited to see where Web 3.0 and blockchain will take us all.
1 note
·
View note
Text
What is DeFi?
The ecosystem behind Decentralized Finance explained simply

It’s been on everyone’s lips for quite some time now, and it reflects the idea of decentralization better than pretty much anything that came before it. We are talking about Decentralized Finance or called DeFi for short. It’s an idea on which big-name projects such as the decentralized lending platform MakerDAO are already built and celebrate great success. But there is so much more behind DeFi. It’s an entire ecosystem. Credit protocols, security coins, stablecoins, derivatives, exchanges, and much more adorn the wonderful world of DeFi. Sound interesting? Then wait and see because DeFi has so much more to offer.
In this article, we will clarify the most important question of all: what is DeFi? Then, we’ll introduce you to the vision behind it all. We will explain what DeFi is all about and which promising projects are already working on it at full speed. As always, it’s worth staying tuned because this will be not only educational but also exciting.
What is DeFi?
DeFi is essentially just a conventional financial instrument built on a blockchain. Primarily, the Ethereum blockchain is used for this purpose. DeFi applications are mostly based on open-source protocols for creating and issuing digital assets. Their advantage, among others, is that they are designed to offer notable benefits of operating on a public blockchain, such as censorship resistance and improved access to financial services. In this way, the DeFi movement addresses an important core criterion of cryptocurrencies, and that is the promise of making money and its transaction universally accessible. And that is for every person, no matter where he or she lives in the world.
The DeFi movement takes this promise even a step further. It aims to provide a global, open alternative to every financial service available today. These include the ability
· to save,
· take out loans,
· trade,
· take out insurance
and much more. All that is needed is a smartphone or computer with an internet connection.
This makes it possible to use smart contracts. Those who have already read our knowledge article about Ethereum already know that smart contracts are self-executing contracts. These make it possible to develop far more sophisticated functions than simply automating the sending and receiving of cryptocurrencies. Such decentralized applications are called dApps.
· In the context of DeFi, dApps already exist that can
· The creation of stablecoins,
· the completion of a credit transaction
· executing automated advanced investment strategies.
· What makes DeFi different from the traditional financial system?
The key question, of course, is why use these DeFi-dApps at all? After all, traditional banking or Wall Street counterparts already exist for all of these products mentioned. Unfortunately, this is only true in certain parts of the world. There is also the following difference. At their core, dApps and their associated business processes are not managed by a company, institution, or individual. Instead, the processes are automatic, and the associated rules are hardcoded in the smart contract. There, they are visible to all and transparently represented in the form of code.
Once the smart contract is implemented on the blockchain, it can execute itself with little or no human intervention. DeFi-dApps are thus visible to everyone but pseudonymous. They cannot be directly assigned to the real identity of the user. DeFi-dApps can be used from anywhere in the world where an internet connection is available. They are censorship-resistant and, thanks to the automated execution of the smart contracts and the visible code, conclude contracts and/or their use trustworthy and transparent, even without intermediaries.
Not without reason, DeFi is currently one of the fastest-growing sectors in the crypto field. More than $600 million worth of cryptocurrencies have already been invested in smart contracts in question, and thus in infrastructure. What exactly are some of the most important and popular use cases and projects in the DeFi sector, let’s take a closer look now.
1. open credit protocols — accessible to everyone
Open credit protocols have probably attracted more attention recently than any other category in the field of DeFi on Ethereum. Largely due to the meteoric rise in Dai's use and other P2P protocols like Dharma and the creation of liquidity pools like Compound Finance, decentralized lending is garnering powerful attention, and rightfully so. Open, decentralized lending offers numerous advantages over traditional lending structures. It enables
· The integration of lending/borrowing of digital assets,
· the insurance of digital assets,
· instant transaction processing and new methods of secured lending,
· broader access to people who are unable to access traditional services
· standardization and interoperability, which can reduce costs through automation.
Secured lending using open protocols such as MakerDAO and Dharma are designed to minimize the need for trust. They achieve this by making use of the functionality of Ethereum-based smart contracts. Open protocol lending is entirely confined to the public blockchain and has some intriguing long-term implications for expanding financial inclusion worldwide. MakerDAO is the most well-known decentralized lending protocol.
2. issuance platforms and investment
Issuing platforms encompass a wide range of platforms, including multiple exchanges that simultaneously serve as issuing media. A significant portion of issuance platforms are in the security token space.
Well-known security token issuance platforms such as Polymath and Harbor provide issuers with the framework, tools, and resources to launch security tokens on a blockchain. They are preparing their own standardized token contracts for securities (i.e., ST-20 and R-Tokens) that allow for automated compliance and customizable trading parameters to meet regulatory requirements. Besides, they are similarly integrated with service providers such as broker-dealers, legal entities, and others to assist issuers in their process. Dual exchange/issuance platforms include Overstock’s tZERO, for example.
Issuance platforms and investment management systems are likely to grow rapidly in importance as more participants enter the open finance world while providing growth for the DeFi ecosystem.
3. decentralized betting platforms
Decentralized betting platforms are among the more compelling components of open finance that are highly complex but offer tremendous potential. Augur launched a censorship-resistant platform based on Ethereum last year that allows people to bet on just about anything. Other projects, such as Gnosis, are aiming for something similar.
Betting platforms, or prediction markets, have long been popular financial tools for hedging risk and speculating worldwide events. Decentralized prediction markets enable the same thing, but with cryptocurrencies and without the ability to censor the markets. Everything from political and weather forecasts to hedging all kinds of risks on financial or adverse events in the real world is already offered in Augur.
4. exchanges and open marketplaces
The role of exchanges is fulfilled by decentralized exchanges (DEX). A DEX is a P2P marketplace for assets on Ethereum between two parties, where no third party acts as an intermediary in a transaction. Thus, they differ from centralized exchanges like Coinbase & Co. in this respect. Some DEX also uses some highly innovative methods of exchanging tokens such as atomic swaps and other non-depository means of exchanging one asset for another with minimal settlement time and risk.
Other types of open marketplaces focus on exchanging non-fungible tokens (NFTs), often referred to as crypto-collectibles. Platforms such as OpenSea and Rarebits facilitate the search and buy/sell of crypto assets ranging from NFTs in games such as Cryptokitties to virtual land parcels in the game Decentraland. Some marketplaces, such as District0X, are even said to allow users to create their own exchanges and vote on management procedures. Current examples of dexs that offer cryptocurrency trading include Binance DEX and Ether Delta.
5. stablecoins
Stablecoins now come in a wide variety of models. They differ in part in how they issue coins, how their reserves are checked, and the mechanism for fixing their price. Stablecoins are tokens issued by a blockchain that are intended to maintain a stable value. There usually is a peg to an external asset such as USD, gold, or others to achieve this. Roughly, the following 3 categories can be distinguished in stablecoins:
1. Crypto collateralized
2. Fiat collateralized
3. Non-collateralized
Crypto collateralized stable coins include Maker’s Dai. Fiat-backed stablecoins, however, are by far the most popular stablecoins on the market. First and foremost is Tether, although there are now numerous alternatives. The models for these stablecoins do not differ much from each other. With all of them, users have to trust the providers. Some offer regular and voluntary audits to create the necessary trust through transparency.
Unsecured stablecoins are neither centralized nor backed by crypto assets. They are built on an algorithm to maintain a stable value. To put it simply, the algorithm considers supply and demand as parameters and adjusts them accordingly, always to keep them in a balanced ratio. The basis was the pioneer in this category but failed due to regulatory concerns. As a result, the project was scrapped.
The future of DeFi — potential or all hype?
The final question, of course, is how great the potential of the whole DeFi movement is? Basically, it can be stated that there are many things in the field of cryptocurrencies that are simply overhyped. The immeasurable potential is attributed to the vision so that the actual product has no chance at all to live up to the exaggerated expectations. What follows is severe disillusionment and disinterest. However, with DeFi, it is a bit different because there are already some finished products like MakerDao, and the market has received them well.
Nevertheless, we are still in a very early phase of the whole DeFi movement. However, the potential behind it is huge. Even if only one spate of DeFi, such as Lending, were to succeed in the future, that is already more than enough. If the DeFi ecosystem can offer loans at better conditions than most national banks and other lending institutions, this could lead to global adoption.
But this is also where we are already at one of the biggest hurdles that the DeFi sector still has to overcome. For one thing, more education is needed so that the masses even know that this alternative exists. As before, only a tiny percentage is even concerned with the issues surrounding cryptocurrencies and blockchain technology. Even fewer deal with the DeFi sector in particular or have even heard of it. On the other hand, the user-friendliness of such products must be improved enormously to set the necessary course for the broad masses to use it and for global adoption to take place.
0 notes
Text
Decrypting NFTs

Every generation had their personalised currency. Millennials had Pokémon and wrestling cards, Generation X had baseball cards and mailing stamps and the baby boomers had their magic 8 balls and comic books. While we would like to believe we live in a single paper currency economy, this isn’t true. Children exchange video games for favours, adults offer old wine for reciprocity and retirees trade favours with cigars. It is not just the incarcerated who have parallel economies, we all do!
Why does the original near mint condition 1988 Spider-Man comic fetch thousands at the pawn store? And why not my reprint on glossy paper? Its ‘fungibility’ of the item which complement or moderate values. Since the barter system, we have agreed on the value of different commodities, based on their demand. Demand for consumption, hoarding or fashion-ability. Commodities which are replicated and can be exchanged for the same ‘value’ of the same item are called fungible.

A five-dollar note and 2 kgs Taj Mahal basmati rice bag is fungible. However, a five-dollar bill with Mohammad Ali’s autograph or the first basmati rice ever grown in outer space are ‘non-fungible’. The same applies to digital commodities, 1 cryptocurrency can be exchanged for another, making it fungible, but the first tweet ever is an ‘original’.
What is a token?
Non-fungible digital commodities have recently been making headlines for their commercial lucrativeness. Memes, social media posts, sports clips, gifs, images etc are sold for millions of dollars. There is an interesting difference between physical non-fungible items and digital non-fungible tokens. Non-Fungible Tokens (NFT) don’t necessarily have to be intrinsically ‘original’, however the ‘token’ is unique. When you purchase a cat meme, a token is generated against that purchase, which is recorded under your name and identification. This token is unique and non-fungible, hence making your cat meme NFT!
To put it more simply, an NFT is a digital asset, even a digital version of a real-world occurrence, with a receipt which confirms your ownership. NFTs can be recording of ‘real-world’ art-form, soundbites, memes, tweets, painting or video clippings. One can cash on digitizing existing popular culture phenomena or create your own crypto art.
How to make Crypto Art or NFTs?
Making crypto art and putting it out isn’t too complicated nor does it require intricate knowledge about block chain technology. Your fist step will be to decide which blockchain you want to support and issue your NFT. While there are many including WAX, Cosmos Trom, Binaca Smart Chain etc., Ethereum is by far the most popular and robust choice at the moment.
The catch is here, how and where you sell your NFT is dependent on your block chain. It is the block chain which records and confirms your token giving you ownership of an NTF. Each blockchains have their ecosystems which allow you access to marketplaces and digital wallets. In other words, you can’t use the British pound to buy bread in Australia, your access to different platforms and markets is restricted by the blockchain.




Ethereum, which is the most popular blockchain for NFT. The Ethereum wallet gives you access to the thriving markets of OpenSea, Rarible, Mintable and Makersplace. Once your art is ready and you are prepared to sell it as crypto art. You should explore the different market space and decide on your appeal and personal preferences. From here, it’s quite straight forward. However, just as in an arcade you can only trade in their currency. Here the currency is ether! Ether is your cryptocurrency. You will have to link your wallet which has your ethers to your profile on NFT the marketplace. And you are good to buy or sell NFTs!
Mechanics of the crypto art market
So, first of all purchase some ether from Coinbase website and store it in your Metamask wallet. Coinbase and Metamask are the most reliable and popular platforms in the crypto world. However, they are the preferred choice for those who trade in larger volumes on cryptocurrency, hence can justify the higher operating costs. New users can explore alternatives to Coinbase, Liquid, Gemini, Binance, Bitstamp, Kraken, BitMEX. It is imperative to weigh the pros and cons of each of these. While initially a preferred choice for all users due to its user-friendly interface, increasingly Metamask is found to be expensive. Fortmatic, TrustWallet and Portis are other wallets which are compatible with Opensea.
Once your crypto wallet is set up linked with your Opensea profile, you can update your information. The Opensea dashboard is very professionally designed and easy to use. You can ‘create’ your collection and upload your art, name it, add description and detail, and link to the artist’s website. To add more value you can add properties, which demonstrates the uniqueness of the crypto and other details like levels and stats. However, these are popular largely within the gaming community. An important aspect is unlockable content. Which is a message you can deliver to the buyer, it could be pleasantries or contact details or links for more value in addition to the sale.
The money spinner, gas prices!
Now comes the interesting bit of gas price. Before that you will have to choose your selling model, from highest bid, set price and bundle. Affiliate boundaries to increase opportunities of sale. Schedule sale time for a future date and time. And you post a listing. Here comes the gas fee. Gas fees are a steep ask for most amateur content creators. It is the cost you pay for your listing. It does vary depending on your urgency, if you are willing to upload the art over a few more days, your fee reduces. If you want it uploaded immediately, you will have to pay the maximum set price. This cost varies depending on the day of the week and the time of day. It is said, cheaper costs are found during weekends. Further, when you go to buy an NFT you have to pay a smaller gas fee.
Hype or Future?
NFTs could be a bubble as crypto sceptics have claimed. But similar claims had and are being made about crypto currency, the crypto market has seen some recent downturn with dogecoin, but so, did Bitcoin and it has bounced back! Increasingly more and more countries are looking at ways to monetise this technology and users are increasing. Its acceptability moved past a fad.

NFTs future may not be created, but it has opened up a whole new world of content creators and artists. For example, Niio Art has demonstrated how users can rent art without owning it for a time period. Blockchain has used a new age to authentication, and this is set to continue revolutionizing creative business models. NFTs are a manifestation of this revolution, which will keep evolving hence investing in it may not be a bad idea.
0 notes
Text
What is a blockchain oracle?

A blockchain oracle is responsible for sending external data to a blockchain. Essentially, they bring data from the real world and give it to the blockchain to utilize. Oracles fulfill this need because blockchains only have access to data that happens on their network. By expanding the amount of data blockchains have access to, it can significantly increase the number of capabilities of the applications that run on it.
Oracles are extremely beneficial for smart contracts because they are the basis for Dapps and have many potential use cases that couldn’t occur without the use of real-world data. An oracle isn’t the source of the data but it instead acts as a messenger, by relaying information from other sources and confirming the information is correct before sending it to its desired destination on the blockchain. It is important this information is correct, otherwise the oracle would be feeding incorrect information, which can be extremely problematic.
Blockchain Oracle example
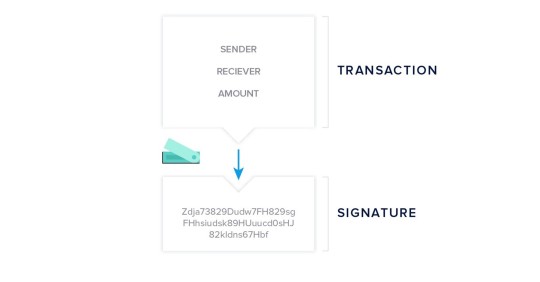
Let’s say you wanted to bet on the winner of a football match with your friend. You could create a smart contract with the odds and both you and your friend lock your desired bet into the smart contract with a payout for the winning person. But the smart contract won’t know the winner because it isn’t able to access this data. After all, it doesn’t run natively on the blockchain. Here, an oracle would query its trusted source for the information of the winning football team, verify the information is correct, then feed it back to the smart contract. Now that the smart contract has access to the result of the football match, it can payout the winner accordingly.
Let’s look at another example. A farmer depends on the weather for their crops to grow well, and to make money from those crops. Insurance companies can provide protection to farms, however, farmers can be limited with their choices of only local providers which may give them an unfair deal. The farmer could instead enter into a smart contract with an online insurance company where the criteria are based on the amount of rainfall in the region. By using an oracle, the smart contract can receive accurate rainfall data from national weather bodies, and use it to provide coverage based on the amount of rainfall in the region. Below you can see a visual representation of a smart contract, powered by Chainlink, that demonstrates this example.

The different types of oracles
Software oracles
A software oracle is an oracle that pulls data that originates from online sources. This could include information like weather, crypto prices, or even flight schedules. Since software oracles are connected to the internet, they can feed information in real-time. Because this allows them to provide information that constantly updates as necessary, they are the most common type of oracle used by blockchains.
Hardware oracles
A hardware oracle is an oracle that pulls data from a physical device in the real world. This could include devices like a photocopier or a barcode scanner. For example, a supply chain may be responsible for packing and shipping boxes of electronic parts. At the end of the packaging line, someone may scan the box to mark it’s been packaged. A smart contract can be created where the oracle feeds it information about boxes that have been scanned, which the smart contract can make decisions based on.
Inbound and outbound oracles
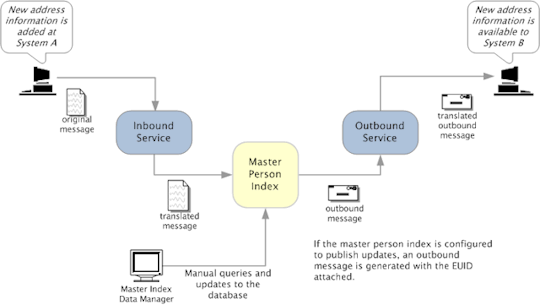
Inbound and outbound refer to which way the information is being sent. If an oracle is sending information to a smart contract, then it is inbound. If an oracle is sending information from a smart contract to an external source, then it is outbound. An inbound oracle might supply information to a smart contract about the winner of a football match. An outbound oracle might use a method to unlock a smart contract and send the payout of a bet to the winner’s address.
Centralized and decentralized oracles

bitA centralized and decentralized oracle refers to the control structure of an oracle. If an oracle is centralized, its information is coming from a single entity and can be considered a single point of failure. There is a risk in using a centralized oracle because if that single entity were to fail then the oracle would be unable to function properly. This single point of failure also poses a security risk because only one entity needs to be attacked for the oracle to be rendered useless.
A decentralized oracle has multiple entities that it uses to provide information. In this instance, the oracle has multiple points of failure and can be considered more trustworthy from an information and security standpoint. Moreover, a smart contract could also utilize multiple oracles to achieve consensus for the necessary information, similar to how blockchains need consensus to confirm transactions — this is an example of consensus-based oracles.
The oracle problem
Since oracles act as the middleman between blockchains and external information, there is an underlying problem that faces them from achieving widespread adoption. Blockchains can’t pull data from external sources so they require oracles to fulfill that. If an oracle is compromised, then this also compromises the smart contract. This is the oracle problem. For the oracle to be trustworthy for a blockchain it needs to be secure from attacks, decentralized to reduce the concentration of failure and provide correct data.
If you have questions and requests, leave comments below the article.
0 notes
Text
How to Choose a Mining Pool

The purpose of a bitcoin mining pool is for a group of miners to join together and form a pool. By combining resources from all clients in that pool, they increase the odds of discovering the solution to a given block. When a solution is found to the block, it rewards the newly issued coin to the pool owner. The pool owner then divides the coins between the miners based on their contribution.
• Pooled mining produces a constant revenue of smaller values, whereas solo mining tends to be more erratic and could take years to mine one block.
• Pooled mining can generate a 1–2% higher income (before fees, if any) due to long polling provided by the pools. Solo mining wastes time due to only supporting getwork pull.
When looking for the right mining pool to join, your goal is to find a fair pool that you can trust to provide you with optimal payouts in exchange for your time and energy resources. Though, the pool you choose, statistically, will not increase or decrease your odds. Choosing the right pool can greatly increase your overall earnings.
10 things to consider when choosing a pool
Reputation
Join a group and see what others are saying about any pool before joining it. You will get the best information from miners who have already tried the pool themselves.
Pool Fee’s
Most pool’s charge a fee everytime a block is discovered. For the highest payout over time finding a reliable pool with the lowest fees is crucial. When making your decision, start with considering pools with no fee at all.
Uptime Efficiency
Do the research before committing to a pool. Make sure they have an uptime of 99.5% or higher, check to see if the pool supports backup servers in the case an outage.
Support and Feedback
It’s important that a pool has an open line for support and feedback in case you encounter technical issues or notice any discrepancy in your payout.
Location/Latency
Choose a pool running on a server near you. If your computer takes too long to communicate with the pools server you will lose precious shares. Shares received after a block change, intended for the previous block, are considered stale and not counted.
User Interface Panel
When choosing a pool, be sure to check their statistics page and API tools to determine which provides a better user experience.
Difficulty
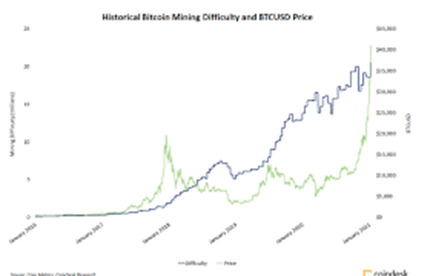
A pool with a higher difficulty means they either there are more miners in that pool or they are using high-end mining hardware. This shouldn’t be a concern when picking the right pool, as the difficulty will adjust based on the shares your hardware submits.
Payout Threshold

Always check a pools payout threshold, If the pool has a high payment threshold, low-end mining hardware may not be feasible.
Pool Hashrate
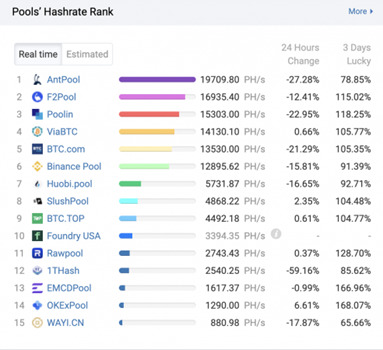
Comparing a pools hashrate to the network hashrate is a good way to measure how often the pool will discover a block. Statistically, this will average out over time and should not affect your overall payout over time.
Payout/Reward Method
Proportional — In this method, rewards are determined based on a division of rounds, the round is measured by the time separating one block discovered by the pool to the next.
CPPSRB — Capped Pay Per Share including Recent Backpay.
DGM — Double Geometric Method. A combination of PPLNS and Geometric reward models that allows operators to absorb some of the variance risks. Operators receive a piece of the reward on short rounds and replace it on longer rounds to normalize payments.
ESMPPS — Equalized Shared Maximum Pay Per Share. Like SMPPS, but equalizes payments justly among all those who have contributed.
POT- Pay On Target. A high variance PPS method, that pays based on the difficulty of work delivered to pool instead of the difficulty of work completed by pool
PPLNS - Pay Per Last N Shares. Similar to proportional, but rather than paying by the number of shares in a round, it instead pays via the last N shares, disregarding the round difficulty and length.
PPLNSG - Pay Per Last N Groups (or shifts). Comparable to PPLNS, but shares are grouped into “shifts” which are paid in whole.
PPS - Pay Per Share. Each submitted share is worth set amount BTC. Since finding a block demands shares on average, a PPS method with 0% fee would be 12.5 BTC divided by . It is risky for pool operators, therefore the fee is highest.
RSMPPS - Recent Shared Maximum Pay Per Share. Like SMPPS, but system proposes to prioritize the most recent miners first.
Score - Score based system: a proportional reward, but weighed by time submitted. Each submitted share is worth more over time since the start of the round. Rewards are calculated proportionally to scores and not to shares.
SMPPS - Shared Maximum Pay Per Share, works the same as Pay Per Share, but is capped to never pay more than the pool receives.
FPPS —Full Pay Per Share. Similar to PPS,but not only divide regular block reward but includes some of the transaction fees. It Calculates a standard transaction fee based on a previous round and distributes it by hash power contributions. It increases the miners’ earnings by sharing some of the transaction fees
It’s impossible to find a pool that meets every expectation perfectly, but as you see there are many factors to consider while choosing the right mining pool for you. Ideally, the right pool should offer low/no pool fee’s, a great support team, a server near you, flawless uptime and backup server, a great reputation, and a provides a friendly user experience.
#cloudmining#cloudminingwebsite#cloudminingwebsites#crypto#cryptocurrency#cryptocurrencies#cryptotrading#cryptonews#bitcoin#bitcoinmining#bitcoins
0 notes
Text
TYPES OF CRYPTO WALLETS

A crypto wallet is an app for generating, managing, and storing cryptographic keys - your public and private key. You can check your balance, receive, and send funds with a wallet.
Your Mnemonic Phrase
Your mnemonic phrase is a backup of your private key that is used by most wallets. It is a list of random words given to you when creating a wallet, usually 12 or 24. If you break or lose a device with a wallet - no matter if mobile, desktop or hardware wallet - your mnemonic phrase is usually your last line of defense against a loss of funds.
This implies, that any attacker that gets their hands on your recovery phrase will be able to do the same. Therefore, you must protect your mnemonic phrase as well as you would protect your funds themselves.
Important Note: You should write the phrase of words down on paper or save them in any analog format you see fit, but do not save them as a text file on your computer or a screenshot. You don’t want to make it too easy for any potential attacker to steal your money.
The Different Types of Wallets
In this article, we want to give you an overview of what types of wallets there are and help you find the right wallet for you.
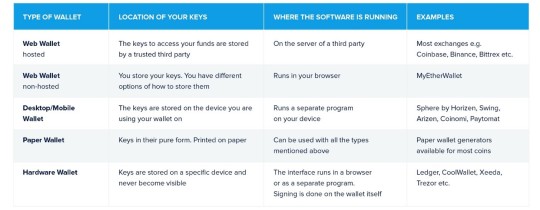
Hosted Web Wallets
We can distinguish between hosted and non-hosted web wallets. With hosted web wallets, your keys are stored online by a trusted third party. These parties are mostly exchanges such as Coinbase, Binance or Bittrex. When you create an account with these entities they will create an entry in their internal database linking your account to a set of key pairs for the different coins they have listed.
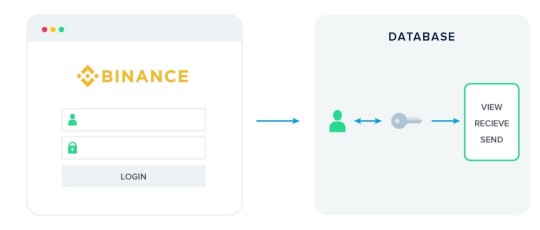
An advantage with a hosted web wallet is the option to recover your password in case you forget or misplace it. Losing your private keys (together with your mnemonic phrase) leads to a loss of funds in all other cases.
While this may sound reassuring, there are some drawbacks with hosted wallets (also called hot wallets/cloud wallets). Remember: if you don’t control your keys, you don’t control your funds. There is always a third party risk, no matter how trustworthy the party might seem. First, they are a more attractive target for hackers than individuals because their honeypot is much bigger. Second, a sudden change in regulation might not allow them to have you withdraw your funds in a worst-case scenario. It is unlikely, but definitely not impossible. Thirdly, there is always a chance of an entity going bankrupt or stealing money. With the major exchanges like the ones mentioned above this risk seems small, but it does exist. Just ask former Mt. Gox customers. For the reasons above we do advise everybody to store the keys to their funds themselves. This means storing them in a wallet where you have control over your private keys. There is a responsibility that comes with being in charge of the safety of your funds yourself, but enabling you to do this is one of the main motivations for the existence of cryptocurrencies!
You will need to keep some funds on an exchange permanently if you plan to trade often. If you want to do this right, then your level of expertise should be exceeding this article by far anyways.
Non-Hosted Web Wallets
Besides hosted web wallets there is also a range of non-hosted web wallets. The most popular non-hosted web wallet is likely MyEtherWallet, which can store Ether (ETH) and all ERC-20 tokens (tokens that are “living” on the Ethereum blockchain). Those wallets provide an interface to check your funds or create transactions in your web browser, but you have to provide the keys with each login.
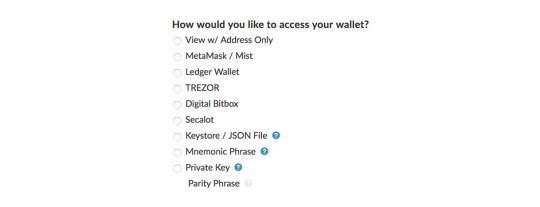
There is a range of options to access your wallet with MyEtherWallet (often abbreviated as MEW). The first option requires your address but only lets you view your funds.
MetaMask is a browser plugin that provides the option to make ETH payments within your browser and the ability to login to MEW. It also provides a function detecting phishing sites and warning you when you are about to open one. The next couple of options, Ledger Wallet, Trezor, Digital Bitbox, and Secalot are hardware wallets. We will get to those later in the article.
Accessing your wallet with a keystore /.json file is possible but not recommended. The file contains your private key and when you create your wallet you have the option to download it. If it gets into the wrong hands they will have access to your funds so saving it on your desktop is not the ideal solution. If you want to use this method, you should encrypt the .json file and store it on a separate device like a USB drive. To use it, connect the drive, decrypt the file, then select the file in your browser and voila. After that, you can disconnect your storage medium of choice again.
The last two options are more or less the same with regards to safety. You can either enter your private key directly or your mnemonic phrase (which yields your private key when hashed) which is both problematic if your machine is compromised.
In conclusion, a non-hosted web wallet is quite convenient and just as secure, as the method, you choose to provide your keys with.
Desktop and Mobile Wallets
If you start off with the question “where are your keys?” the desktop and mobile wallet will give you the same answer: on the device. Phones and tablets are more powerful than ever, the difference between a desktop and a mobile wallet is marginal. It is also arguable whether one is safer than the other.
By now you know the tasks a wallet performs: viewing, receiving and sending. If you want to use crypto for everyday transactions there is almost no way around keeping some funds in a mobile wallet. As mentioned before, when creating your wallet you will get a mnemonic phrase that you should keep safe. Usually, there is a PIN, password or Face-/Touch-ID protection to access the wallet. You should never keep more funds in a mobile wallet than you are willing to lose. It’s the same as with cash: you don’t carry around all your money in a wallet. You withdraw as much as you are comfortable handling in cash and keep the rest in your account (or under the mattress :P).
With desktop and mobile wallets, there is a choice between single- and multi-currency wallets. Those should be rather self-explanatory terms. The former allows you to store one coin, while the latter supports multiple currencies. Some of the more popular examples for desktop include Electrum and Exodus. For mobile, there are Mycelium or Paytomat to name just a few.



If you got your first coins on an exchange, I would recommend you to transfer your funds out of the exchange (hosted web wallet) onto a desktop, paper, or hardware wallet. Send a fraction first to make sure everything works as planned. If your first transaction works then you can send the rest. You are now protected from third-party risk, but have full responsibility for your funds yourself.
Paper Wallets
Grabbing our golden thread again and asking “where are the keys” give you a simple answer with a paper wallet: in your hand! A paper wallet is your public and private key pair printed on paper. Almost every cryptocurrency offers a paper wallet generator. To create a key pair you generally first have to create some entropy (a term for disorder), in other words: you want your keys to be as random as possible. This is mostly done automatically, but sometimes you will find features were you have to randomly move your mouse or hit keys on your keyboard to create randomness.
When printing your paper wallet you shouldn’t use a shared printer like the one in your office. In a best-case scenario, the printer doesn’t even have an internet connection. Printers usually keep a copy of the files they printed last, and an attacker might exploit this. You will end up with something looking like this after printing the wallet.

There is only one thing left to do: send your coins to the public key. After that, you have a perfect gift or long term storage for your coins. The main risk with a paper wallet is you actually losing or destroying the wallet by accident. If you don’t have a mnemonic phrase to recover the private key you are at risk of losing all funds on the wallet by accident. So choose wisely where to store your paper wallet. Print several copies if you feel uncomfortable having only one and store all of them in separate, safe places.
Hardware Wallets
Moving on to everybody’s darling: hardware wallets. With a hardware wallet, your keys are stored on the device in something called the “secure element”. The secure element is a place to store data (here, keys) that cannot be directly accessed by your computer or any other device even when it is connected. Although it does look like a simple USB drive, it can actually do a little more than just providing storage for your keys. To use a hardware wallet you usually have a few options of which interface to use with it. Like MyEtherWallet, a few other wallets offer hardware wallet support. Additionally, you have the native wallet apps provided by the producer. In the case of Ledger, for example, the native App is called Ledger Live.
How Does a Hardware Wallet Work?
The interface generates an address when you want to receive funds. Using this feature is pretty straightforward: if you click the receive button the process runs in the background and the address is displayed for you to share with the sender. If you want to send money the app creates the raw transaction that needs to be signed. The unsigned transaction is now sent to your hardware wallet, where it gets signed with your private key. The signature is then returned to your computer and the complete transaction including the signature broadcasted to the network.
Your private key(s) do not leave the device, so they are not visible to the computer you are using your hardware wallet with at any time. This is why a hardware wallet is considered the most secure way of storing crypto, especially large amounts.
If your device ever breaks, you have your mnemonic phrase as a backup. At the risk of being repetitive: your mnemonic phrase, under all circumstances, must stay private and in a secure location. A copy at a trusted family member or in a bank vault might be a good idea in case of a fire, flooding or a playing dog.
Summary
There are many ways to store your cryptocurrencies. Usually, there is a trade-off between convenience and security. The most important question is: where are the keys? A wallet is only a piece of software, an interface, that helps you perform the basic functions of cryptocurrencies: view your balance, create an address to receive funds, and create transactions to send funds.
With a hosted online wallet you are trusting a third party to handle your keys. You have the option to recover your password if misplaced, but there is always a significant third-party risk. If you don’t control your keys, you don’t control your funds!
With desktop, mobile, paper or hardware wallets you own the keys and nobody but yourself is responsible for keeping them safe. If your device breaks you have a mnemonic/recovery phrase to recover access to your money. The menmonic phrase is as sensible as your private key itself and if it gets in the wrong hands, your money can be stolen. This is should not scare you, but make you cautious.
If you have questions and requests, ), leave comments below the article.
0 notes
Text
CRYPTO WALLETS

Sometimes there is a little confusion about what a wallet can and cannot do, so we will start with what it can’t. Wallets generally don’t allow you to buy cryptocurrencies; that is what exchanges are for. All exchanges provide you with wallets to store your coins in after you buy them, but wallets usually don’t provide you with an exchange service.
What a Wallet Does?
A wallet is a program that has three main functions:
· Generating, storing and handling your keys and addresses
· Showing you your balance
· Creating and signing transactions to send funds

The first function is the main function and main differentiator of all wallets: generating, storing, and handling your keys,having access to your private keys means to be able to spend your money.
Where you store your keys determines the safety of your funds and, at the same time, the convenience of using them. With wallets, there is usually a trade-off between security and convenience: Having some funds on your mobile wallet (your smartphone) makes them easy to spend, but not very secure. Keeping larger amounts of money on a hardware wallet is very secure, but not as convenient when you want to spend it.
A Wallet Acts as a Keychain
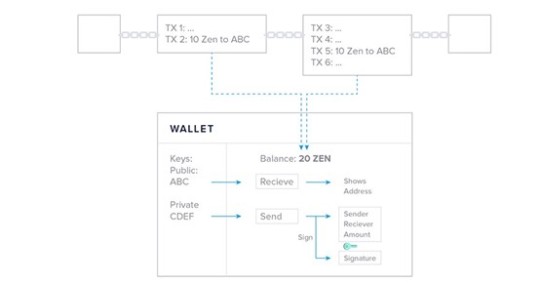
We would like to introduce an abstraction, that might help you wrap your head around the concept of your keys and the importance of their safety. Although the term wallet might be more intuitive, the function of a wallet is closer to that of a keychain rather than an actual wallet. To make it crystal clear:
You don’t actually store any cryptocurrency in your wallet. You just store the keys to access them on the blockchain.
The blockchain records the amount of coins associated with a key pair (your identity on the blockchain). It calculates the amount of money the keys have access to based on all the transactions on the blockchain. Remember: the main function of a blockchain is to store all transactions in the correct order. Say you receive 10 ZEN in a first transaction and receive another 10 ZEN later on. It is clear that you, the owner of the key pair, owns 20 ZEN.

To spend your money, you need the private key stored in your wallet. This is why a keychain feels like a good analogy for what a wallet does. If you don’t control your keys, you don’t control your funds. You don’t need to understand how public-key cryptography works in detail in order to use cryptocurrencies, but the concept of your keys, giving you access to your funds, is still important to remember.
Wallets create a layer of abstraction and are becoming more and more user-friendly. Wallets show you your balance, generate an address to receive funds by just clicking “deposit” or “receive”, and provide you with a simple interface to send funds. All you need to do is enter the address that you would like to send money to and the amount you want to transfer. The signing procedure using your private key will happen in the background when you click send.
What if I Lose My Keys?
You don’t have to ask anybody to join the network, and you don’t have to register with a central authority to create a wallet. Being able to do this comes at the cost of you being responsible for the safety of your coins. There is nobody that can help you recover your keys if you lose them. If anybody were able to recover your keys for you, they would also be able to steal your funds. This would eliminate the trustless aspect of blockchains. You may have heard stories about people searching for old hard drives because they have “lost their bitcoins”. More accurately, they lost the keys to access their bitcoin.
But there is a sort of recovery mechanism with many wallets called a mnemonic phrase or backup phrase. A mnemonic phrase usually consists of 12 or 24 words. With these words, you can recover your keys. You receive your mnemonic phrase when you install and set up your wallet. Be sure to write it down on a piece of paper and keep it in a safe place. You should have at least two versions of your backup phrase stored in different locations.
It’s essential to understand that your backup phrase is just as important as your private key itself. If anybody gets their hands on your backup phrase, they can access your money. Saving it as a screenshot or text file on your computer is not a good idea!
Summary
A wallet is a program that helps you manage your keys and create transactions easily. Your wallet looks at the blockchain to determine how much money you own by reviewing the transaction history. To send funds, it writes a transaction and signs it, meaning the wallet encrypts it with your private key.
1 note
·
View note
Text
PoS, PoW, and 11 Other Blockchain Protocols You Didn’t Know About
What is consensus? If broadly defined, a consensus is an agreement that satisfies each of the parties involved. This is the key to democracy and decentralization in general, as well as distributed registry technology in particular. Look at BTC: although Satoshi Nakamoto is his mysterious founder, he (or she!) has no power over the community. Bitcoin, like the blockchain, is completely transparent and open, and each node is equal in this network.
In the narrow sense, we use in cryptography, a consensus is a decision-making procedure. Its goal is to ensure that all network participants agree on their current status after adding new information, a data block or a transaction batch. In other words, the consensus protocol ensures the chain is correct and provides incentives to remain honest participants. This is an important structure to prevent a situation where someone alone controls the entire system, and it ensures everyone abides by the rules of the network.
A short review of a blockchain protocol
A protocol is a set of rules.
It helps:
ensure the viability of online transactions;
eliminate the possibility of double waste;
make sure participants do not cheat.
Blockchain protocol is the amount:
deterministic logical rules;
cryptography and encryption as a basis for security;
social encouragement to support the network protocol.
Let’s review what blockchain protocols exist today, where they are used, and what are their pros and cons.
Disclaimer: the article will be supplemented and edited to provide the most accurate information.
We will start with the mastodons of the industry. Proof of Work (PoW) and Proof of Stake (PoS) are the pioneering protocols that often serve as the prototypes for other modern consensus protocols.

Proof of Work (PoW)
Principle: it is difficult to find a solution, but it is easy to check the result.
Performance: low.
DLT environment: public blockchain.
Completion: probabilistic.
Example of use: Bitcoin, Ethereum, Litecoin.
The bitcoin blockchain is probably the most copied blockchain protocol. Numerous nodes confirm transactions in accordance with the PoW consensus algorithm. To add a new block, the participant must prove he/she has done a certain job. To be precise, it solves a very difficult task of finding a hash that complies with certain rules. The first who was lucky to find the right combination gets the opportunity to add a block to the chain.
As a result, participation in PoW implies the cost of computing resources, but the advantage is that it can be implemented in an environment where participants absolutely do not trust each other. Anyone can join the network, as it is a blockchain, which does not require permission (it’s permissionless). And although the peer-to-peer scalability is high, the transaction rate remains low.
Another problem is the motivation of network members — they usually join in to get rich, and not to maintain justice. Reducing mining fees over time and lower commissions in the future can greatly affect network security.

Proof of Stake (PoS)
Principle: the network trusts the validator, who puts his own resources as a pledge for the ability to create blocks: the larger the share, the higher the probability that the network will allow the creation of a block.
Performance: high.
DLT environment: public / private blockchain.
Completion: probabilistic.
Example of use: NXT, Tezos, soon Ethereum.
The technical feature of PoS is the absence of complex and unnecessary calculations. Instead of competing with others, network participants pledge their crypto actives, such as ether (Ethereum) in Ethereum, and wait for them to be selected to create a new unit.
Here participants are interested in security, as they themselves own the coins of the system. The algorithm selects one validator, based on the share belonging to it. Therefore, if the participant owns a 5% share, then 5% of transactions will be checked. The idea is that the higher the proportion of validator underlying cryptocurrency, the less interest he/she has in manipulating the validation process.
As in the case of the PoW algorithm, the completion of a transaction in PoS is probabilistic. Although transactions are relatively fast compared to transactions on the Bitcoin network, tokens are still required for this. Moreover, skeptics point to the fact that validators with large stakes will be chosen more often and, therefore, will receive even more tokens: the rich are getting richer.

Delegated Proof of Stake (DPoS)
Principle: Participants delegate the production of new blocks to a small and fixed number of elected validators. High competition, but very profitable.
Performance: high.
DLT environment: public/private blockchain.
Completion: probabilistic.
Usage example: EOS, BitShares.
Delegated Proof of Stake (DPoS) enables creating blocks at high speed and process more transactions per second by reducing the number of validators. During the voting, coin holders choose validators to form the blocks. The weight of each vote is defined by the sum of the assets of the voter. Coin holders can vote for validators at any time. This determines the high flexibility of the network: if the majority of performers fail, the community will instantly vote to replace them.
The production of new blocks occurs every 1–2 seconds. This protocol is faster and fairer compared to PoS since the “delegated” validator later shares tokens with its voters. Although, the confirmation of the finished blocks still lies on the shoulders of all the other members of the network.

Proof of Activity (PoA)
Principle: a hybrid of PoW and PoS.
Performance: low.
DLT environment: public.
Completion: probabilistic.
Usage example: Decred.
Proof-of-Activity (PoA) combines the PoW and PoS protocols, which means that participants can mine or lay down a share to validate the blocks. So, the PoA protocol provides a balance between miners and ordinary members of the network.

Proof-of-Location (PoL)
Principle: beacons are used to notice a node in a synchronized state, and then to mark its presence with a temporary stamp.
Performance: average.
DLT environment: public.
Completion: immediate.
Usage example: FOAM, Platin.
Proof-of-Location (PoL) allows users to secure a specific GPS location and thus authenticate themselves on the network. Interestingly, this blockchain protocol relies on BFT beacons, which record geolocation and time markers in the blockchain, which prevents disruptions and fraud in the system.

Proof-of-Importance (PoI)
Principle: like PoS, but with additional properties that affect your ranking.
Performance: high.
DLT environment: public.
Completion: probabilistic.
Usage example: NEM.
The algorithm acts almost like PoS, but includes three components:
the number of tokens in the account;
account operations activity;
the time spent by the account holder on the network.
The first parameter plays an essential role in the rating for verifying transactions; the second and third parameters just help to establish the “value” of the account. The smaller the sum of tokens, the stronger the influence of other parameters.
Consequently, an account that lays hundreds of thousands of tokens can increase the coefficient of importance by almost 3 times due to its activity and constant presence in the network. On the other hand, it does not matter for those who own hundreds of millions of tokens.

Proof-of-Elapsed-Time (PoET)
Principle: blocks are created in a trusted environment with equal periods.
Performance: average.
DLT environment: private blockchain, with and without permissions.
Completion: probabilistic.
Usage example: Intel.
Intel did not lag behind and developed its own blockchain protocol called IntelLedger.
This system is similar to Proof of Work but utilizes less electricity. Instead of participants solving a cryptographic puzzle, the algorithm works in a Trusted Execution Environment (TEE) environment, such as Intel Software Guard Extensions (SGX). The PoET protocol guarantees that the blocks are generated randomly and without any necessary efforts.

Proof of authority (PoA)
Principle: semi-centralized blockchain for banks and insurance companies
Performance: high
DLT environment: Public, private or consortium.
Completion: probabilistic
Example of use: Kovan, Rinkeby, Giveth, TomoChain, Rublix, Swarm City, Colony, Go Chain.
Similar to PoS and DPoS, in PoA validators secure the blockchain and are able to produce new blocks. New blocks on the blockchain are created only when a supermajority is reached by the validators.
By identifying pre-selected authorities, PoA consensus becomes centralized. Therefore, it’s suited for private blockchains and consortiums, such as a group of banks or insurance companies for better scalability. The identities of all validators are public and verifiable by any third party. Having their identity at stake, validators act in the best interest of the network.

Proof of Burn (PoB)
Principle: burning a mined PoW cryptocurrencies in exchange for mining privileges or the coins/tokens of an alternative currency
Performance: medium
DLT environment: Public
Example of use: Slimcoin and Counterparty
Miners send coins to an unspendable address (an eater address) in such a way burning them (coins can no longer be accessed and spent again). As PoB transactions are recorded on the blockchain, there’s undeniable proof that the coins are inaccessible, and the user is rewarded.
The idea is that a user demonstrates a willingness to undergo a short-term loss for long-term investment — a lifetime privilege to mine on the system. The more coins a user burns, the higher the chance to mine the next block.

Proof of Capacity (PoC)
Principle: The amount of “work” a miner will perform depends on the amount of free disk space to devote to the plotting process.
Performance: high and efficient
DLT environment: public
Example of use: Burstcoin and Bitcoin Ore
PoC is similar to PoW with a considerable difference — in PoC, rather than doing a large amount of work to verify each block, the work is done in advance in the process called “plotting”; the results from this process are used later to verify each block.
Plotting is the process of producing special files called “plot files” which store a large number of precomputed hashes. The shortest solution to the mining algorithm grants the rights to mine the next block. PoC is efficient, cheap, and distributed.
Proof-of-Brain (PoB)
Principle: the protocol enables smart, a social currency for publishers and content businesses
Performance: fast and efficient
DLT environment: public
Example of use: Steemit
PoB is a scalable blockchain protocol for openly accessible and immutable content accompanying a fast and fee-less digital token — STEEM — which helps people earn money by using their brains thus the name. STEEM is a means for creating unceasingly growing communities with members adding value through the built-in rewards structure.
PoB is a public publishing platform called Steemit from which any Internet application can share data in such a way rewarding those who contributed this valuable content.
Proof-of-Physical-Address (PoPA)
Principle: identity verification DApp
Performance: high
DLT environment: private
Example of use: ConsenSys and POA Network
Proof of Physical Address (PoPA) is a DApp which connects a real-life physical element with blockchain technology. This helps in verifying an individual’s identity. PoPA connects a person’s physical address with a wallet address in which they control the respective private key.
Every time a user verifies his/her card in the DApp, the PoPA protocol refreshes its own record and calls the ERC780 congenial contract to store the user/address connection.
Proof-of-concept (PoC)
Principle: demonstrates the feasibility of any blockchain project
Performance: unknown
DLT environment: private
Example of use: unknown
A Proof of Concept (POC) can be used in any field such including Voting trackers, Record storage, Legal documents, etc. A POC can either be a prototype without any supporting code or a Minimum Viable Product (MVP) with a base feature set. A POC is a model used for an internal organization to have a better understanding of a particular project.
Consensus protocols are an integral part of distributed systems. They help to achieve justice, to avoid system failures when one of the participants — the node — fails. Secondly, a decentralized environment requires solutions which will help move forward and change the general state, even in an environment where no one trusts anyone. Certain rules help to reach “consensus”.
We reviewed the most popular protocols which are already used in dozens of projects. Still, there are also Cross-resiliency (XFT), Paxos, Sieve, Raft protocol, Byzantine resiliency (BFT), direct acyclic graphs (DAG), and even non-blockchains conducted through a mental experiment which we’ll describe later.
If you have questions and requests (for instance, to review a certain blockchain protocol), leave comments below the article.
0 notes
Text
Supernode Proof of Stake Consensus Complete Guide

1. Basic introduction
Supernode Proof of Stake (SPoS) is a blockchain consensus mechanism designed by Sunny King, the creator of Proof of Stake (PoS) consensus, in June 2018. It is an extension to many core concepts of PoS, including Stake as Power, decentralization, high scalability and more. Compared to the new generation of mechanisms inspired by PoS, such as Casper, hybrid PoS, and DPoS, which is sometimes not considered as PoS, SPoS is a true and faithful continuation to the original PoS fundamentals.
Released in 2013, PoS was designed to resolve several key issues associated with Bitcoin’s Proof of Work (PoW) consensus mechanism, including energy inefficiency, centralization of mining pools and lack of scalability. Since its creation, many cryptocurrencies have been inspired by PoS and adopted the algorithm, such as Dash, Cardano, and Sunny King’s own creation Peercoin.
However, PoS consensus mechanism carries certain shortcomings, and is unable to meet the requirements of the current blockchain field for the development and application of a single public chain platform. On December 31th 2016, therefore, Sunny King started a new thing, this thing will change the history again.
In November 2018, Sunny King launched the first native blockchain platform V SYSTEMS based on his SPoS consensus mechanism. The project aims to deliver a blockchain database and cloud platform, with the vision to bring forward a new economic era consisting of hundreds of millions of blockchain applications.
2. Summary of PoS
Since SPoS is an extension to PoS’ original ideologies, it is crucial to learn the key technical features of PoS before fully understanding the concept of SPoS.
1. Almost no energy consumption
PoS does not rely on electricity nor computational power as the basis for block validation, thereby consuming almost no energy.
2. Unlimited level of scalability
As the validation process is not restricted by hardware or electricity constraints, in theory, the blockchain carries an unlimited level of scalability. This paves the way for large scale blockchain technology applications.
3. Coin utility determines coin value
The coin value is not reliant on the intrinsic value nor the equivalence of other types of goods (e.g. the cost of mining). Instead, the coin value is determined by the coin utility.
4. Stake is power
Block validation and rewards are both based upon stake.
5. Decentralization
Without mining pools, there will be no giant and centralized institutions to dominate the blockchain.
6. Random block production
PoS uses the design of random block production, and only the average block interval can be observed.
3. Criticisms for PoS
SPoS is designed to tackle the issues of PoS. It is therefore also important to learn the key criticisms faced by PoS in order to fully understand the rationale behind SPoS.
1. Nothing-at-stake
Nothing-at-stake is one of the major concerns on PoS. The argument suggests that because block validation does not involve computational power or energy consumption, coin minters will try to mint on all block trees in order to prevent himself from not minting on the winning chain, therefore avoiding any potential loss and maximizing the gain.
2. Stake liquidity limited by coin age
PoS imposes many restrictions on the movement of stake after participating in coin minting. On a technical level, this design prevents frequent attacks (i.e. the holder of the coin can “vote more than once” and one stake gains multiple benefits).
From the perspective of PoS, one stake should not be allowed to claim multiple minting rights. However, one might be able to take advantage of stake liquidity and attempt to quickly move the stake around to claim more minting rights than it should. This type of attack is referred to as “busy contention attack”.
Even though the restrictions on movement may be of good reasons from a technical point of view, economically it is a barrier of entry for users to participate in minting. Coin holders are often concerned on how long their coins will be locked for the minting process.
Under SPoS, however, the number of stakes participating in minting is directly related to the level of security for the mechanism, similar to how computing power determines bitcoin security level. In this sense, not putting any restrictions on movement of stake is in fact beneficial to network security.
3. Coin age cannot accurately reflect contribution
As a proof of the stake value in minting opportunity, coin age shows a high level of stability and a wide range of advantages.
However, since it is a transaction-based measurement, the computational complexity is correlated with the number of transactions executed in a given time. Also, coin age is not an accurate indicator of the stake owner’s contribution to the community.
4. Minting security
Since PoS requires minter to sign the block, the private key must remain online, which poses a potential huge risk to the minter.
5. Inability to support large scale adoption
Under PoS, not all nodes receive enough incentives to undergo hardware upgrade. Moreover, if a random block production is adopted like in Bitcoin or other PoS blockchain, the actual production interval may sometimes far exceed the average time.
These issues create a huge concern for the efficiency of the blockchain, as systems usually prefer a constant response time over a random one.
4. Evolution from PoS to SPoS
1. Nothing-at-stake
The concern on nothing-at-stake is in fact unnecessary, as it ignores the fact that when a person owns a certain amount of stake in the ecosystem, the person is motivated to maximize the interest of the community instead of initiating attacks.
Coin owners who seek to maximize profits use the exchange value of the coin as a measurement of the coin value. Minting on all branches of block tree will be contradictory to his self interest, as it is considered a type of attack and the action will lead to a drop in the exchange value.
Considering the negative impact on the coin value, the potential loss on not minting on all branches is far less than the potential loss on coin value. Rational coin owners will always choose to uphold the protocol and ideologies of the consensus mechanism in order to maximize the interest.
In fact, the issue of nothing-at-stake has yet to be observed in a real scenario.
2. Stake liquidity
With a high level of stake liquidity, minters can spend or transfer their stake at any time. Coin leasers can also withdraw their lease, spend, or transfer their stake at any moment. This freedom of movement helps safeguard the blockchain. Take an extreme example of when supernodes are under attack — under SPoS mechanism, a coin holder can immediately withdraw the lease and switch to a secure backup supernode. This will render the attack meaningless, and also make it difficult to attack the blockchain as a whole, as in theory the hacker will have to attack an unlimited amount of supernodes.
Although there is a concern of busy contention attacks due to stake liquidity as mentioned in previous section, SPoS is well adapt to counter the situation. The mechanism introduces a unique measurement of account balance, similar to the accumulative average measurement during minting contention. The idea is that the stake must remain in the account for a period of time and wait for the metric to return to full. This design helps eliminate the concerns on frequent attacks.
3. Coin age
A minting balance mechanism is introduced for coin age measurement in the SPoS mechanism. The idea is that when a stake is withdrawn from the supernode, the total amount of stake on the supernode is immediately reduced. However, when a stake is leased to the supernode, the total amount of stake on the supernode is not immediately increased.
Whether the supernode wins the minting right depends on the minting balance. This minting balance, on the other hand, is dependent on whether the leased stake has been placed for a sufficient period of time. Yet, the length of the stake placement time and minting rewards are not correlated.
4. Minting security
To raise the level of security, SPoS mechanism separates the roles of minter and spender. That is, the private key of the coin holder can be different from the private key of the coin minter. With this design, all private keys of the stake can be put in offline storage.
This naturally allows the emergence of minting pools — the supernodes in SPoS. It is a similar concept to mining pools in Bitcoin.
Sunny King has also introduced a balanced minting right to prevent centralization of supernodes. This will be further explored in later sections.
5. Supporting large scale decentralized applications
The introduction of supernodes provides sufficient incentives to ensure that the supernodes continuously upgrade the hardware to support the blockchain expansion.
Also, the fixed block production sequence and production interval allows the supernode local clock to synchronize with the Internet time protocol. This ensures a high efficiency of block production as well as improves the security and predictability.
5. Technical and economical features of SPoS
Key technical features of SPoS:
1. Fixed block production sequence and constant block interval
2. Cold minting
3. Supernodes
Key economical features of SPoS:
1. Both stake owners and supernodes receive incentives for block production
Minting rewards are shared by supernodes and stake owners. The reward sharing ratio is determined by the supernode. Currently, there are 15 supernodes running on the V SYSTEMS mainnet. Coin holders (stake owners) can lease their coins to the supernode in order to earn the minting rewards. Each supernode takes turn to generate blocks in a minute, with each block bringing 36 VSYS Coins as rewards.
Based on the current number of supernodes, each supernode will generate 51,840 VSYS coins per day. After deducting around 20% of the reward for hardware upgrade and other operational costs, the remaining 80% will be proportionately distributed to coin holders who leased their coins to the supernode.
2. Minting right and minting rewards are distributed in a fair manner, thus eliminating the risk of minting pool centralization
Equal minting right for each minting slot gives supernodes an equal standing and minting output. This is contrary to the design of Bitcoin, where no built-in mechanism is put in place to prevent the domination of mining pools. SPoS eliminates this major barrier that hinders the goal of decentralization.
The equal minting right of minting slot plays an important role in the minting economy. Supernodes form a market of minting pools. The minting market will then form an interest rate for leasing. Since stake owners have a reasonable preference to lease to a supernode paying higher lease rate, and the additional lease to a high paying supernode will lower its lease rate due to the constant minting output of the supernode, an equilibrium exists as a built-in force to equalize the lease rates of supernodes.
6. Advancements of SPoS
1. Superior version of PoS, following the stake-as-power philosophy
2. The only everyone can easy minting and easy out consensus.
3. Performance-oriented, support large scale decentralized applications
4. Most resistant consensus mechanism to 51% attack
5. Highly secure of minting progress for all ecosystem participants
6. Decentralized supernodes
7. Simplify the consensus using a mathematical approach just like bitcoin & PoW did
1 note
·
View note
Text
What the Proof of Stake and Supernode box replaces the Proof of Stake?
PoS uses a processplus pseudo-random election to choose the validator of the next block, which depends on the amount of tokens that each node has staked. In order to prevent nodes with high stakes from dominating the network, techniques such as Random Block Selection and Room Age Based Selection are generally adopted by the algorithm.
It is generally believed that the higher a node's stake, the more likely it is that the node wants the network to remain secure. In order to launch a 51% attack, a Node would require control of 51% of the entire circulating supply, an expensive proposition, just like PoW. Additionally, if a node behaves dishonestly, all of its staked parts are confiscated by the network, which further incentivizes nodes to stay by the rules.
Since no special material is required to become a validator, anyone availablesant of a simple laptop can join the network as a node. Greater decentralization undoubtedly leads to greater security.
However, just as every coin has two sides, greater decentralization also results in performance issues. The nodes in a PoS network have different hardware metrics, which makes the network as strong as its weakest node. Block validation time may be longer for nodes using obsolete hardware, resulting in an overall increase in confirmation times under heavy traffic. Anyone who's tried to participate in a Neo ICO would know what I'm talking about here!
The PoS family

Efforts have been made by various blockchain projects to remedy the limitations from which conventional PoS suffers, by providing modifications
in the protocol while retaining its basic essence. Daniel Larimer came
with Delegated proof of stake (DPoS) in 2014, which was first adopted by BitShares. Later, other cryptocurrencies like Lisk and EOS also used DPoS.
In DPoS, nodes vote for a number Fixed delegates (or witnesses), who participate in the consensus process and secure the network. The voting power of each node (or stakeholder) is proportional to the number of coins it has. Voting rewards are usually collected by delegates and shared proportionally with theirs respective voters. If an elected node engages in fraudulent behavior, it is immediately kicked out and replaced by another.
DPoS distributes tasks between nodes and delegates. Since ordinary nodes participate only in the block validator election process, transaction times depend only on the performance of the delegates and not on ordinary nodes. Delegates are either motivated to remain honest or they are rejected, which is supposed to add to the overall security of the network.
Another popular variant of PoS is Leased Proof-of-Stake (LPoS), which was developed in 2017. LPoS allows nodes to rent their coins to mini ng nodes, which validate blocks and earn rewards. Mining nodes must wager a minimum number of coins. The rented rooms are locked.stored in the user's account,
and are not physically transferred to the minor. As in other cases, the higher the amount of coins rented from a miner, the higher their chances of winning bulk rewards. Waves was the first project to use LPoS.
Since miners must be online 24/7, every user might not be interested in running a node mining. By allowing users to lease their parts for mining, more nodes can be involved in the overall governance of the network. This increases the degree of decentralization of the network, although it also entails the risk of the formation of mining pools.
Enter SPoS

Supernode Proof-of-Stake (SPoS) is the latest in algorithmPoS-based consensus ithms. It is the brainchild of Sunny King, the creator of PoS himself, and was announced to the public in January 2019. While it retains the fundamentals of PoS (and some of its derivatives), What sets SPoS apart is that it focuses more on hardware upgrades than protocol enhancements.
The SPoS protocol itself requires the supernode hardware to be upgraded as the performance of the blockchain requires. By rem Due to the dependence on ordinary nodes, SPoS claims that constant network performance can be guaranteed even under heavy traffic. V SYSTEMS is the first project to have implemented SPoS.
Ordinary nodes can still participate in the governance of the network by leasing their coins to these supernodes, who distribute the hit rewards proportionally among the pi ownersgot real. The rooms can be rented without giving up their ownership thanks to the technique of Cold Staking. Each user has 2 keys - the typing key, which remains online and allows the coin mechanism to sign newly minted blocks; and the expense key, which is securely held offline, actually “owns” the participation.
Stake owners can also transfer or spend their staked coins whenever they want, encouraging more nodes to stake coins. In principle, this is similar to LPoS, although LPoS does not impose any restrictions on the choice of hardware for mining nodes.
SPoS also supports a new part staking mechanism called Staking 2.0. In ordinary PoS, by staking coins on the network, nodes earn the native coin of the network as rewards (for example, Neo staking allows users toisators to win NeoGas). In Staking 2.0, not only will supernodes win the native blockchain coin, but all blockchain-supported tokens (for example, VSYS staking will allow users to earn both VSYS and IPX from now on). Supernodes are then expected to distribute them all among the stake owners.
Concerns about decentralization
Despite attempts by SPoS for greater decentralization through Staking2.0, it There are concerns about inherently present trends. Compared to Bitcoin or Ethereum which have thousands With minor nodes around the world participating in the consensus, the governance of SPoS is requisitioned by a handful of supernodes.
The owners of the picketswould naturally tend to rent parts from supernodes with a higher rental rate. This would lead to the tendency to create strike pools, and if a supernode ends up assimilating the majority of the coins involved, it can compromise the security of the network as a whole.
With more rooms rented, the rental rate of a supernode would drop automatically, thus ensuring that a balance is maintained and no supernode ends up becoming a player dominant in the ecosystem.
Unfortunately, that still doesn't stop the rogue supernodes from ganging up and trying to take over the network. I had the opportunity to express this doubt to Jacob Gadikian , a blockchain technologist who was part of the SPoS development team
.
According to Jacob, in order to launch such an attack, the supernode (s) should first acquire a sufficient amount of stake. They can earn it by buying the coins on exchanges or by using social marketing skills.
to convince users to rent coins from them.
In the first case, buying such a large amount of coins would drive up the price of the coin, making the attack financially impractical (similar to the argument for Bitcoin) .And in the second case, they would no longer be red supernodes, but rather ecosystem partners chosen by stakeholders e
Thoughts of separation
PoS was an attempt to provide the same security and decentralization as PoW, but at lower cost SPoS further attempts to improve network performance, shifting the focus from updating the algorithm to upgrading.material day
. In the process, they seem to have been more flexible on decentralization. After all, no project has really been able to solve the blockchain trilemma.
Having said that, even PoW is not a guarantee against network attacks. Earlier this year, one of the best -20 ETC (Ethereum Classic) market cap coins have fallen
prey at 51% to nail. It continued for 3 days, resulting in losses in the order of $ 1.1 million. SPoS takes a different approach compared to other variants of PoS
, and it is still in its infancy. It is only after a sufficient amount of time and a decent number of projects have adopted SPoS that we will be able to tell if King's second child has been able to outperform his firstborn.
#cloudmining#cloudminingwebsite#cloudminingwebsites#crypto#cryptocurrency#cryptocurrencies#cryptotrading#cryptonews#bitcoin#bitcoinmining#bitcoins#spos#supernode proof of stake
0 notes
Text
Phanes Technology
PhanesTech YOUR BEST CLOUD MINING CHOICE http://www.phanestechs.com

WHO WE ARE The story of PhanesTech started at the end of 2013. Our founders got to know each other by using the same platform for buying and selling Bitcoins. They were fascinated by the technology and wanted to build their own farm, only to realize all their friends wanted to participate as well. They came up with the idea of mining as a service and built the first mining farm in Eastern Europe. Since our founding, we have grown tremendously and a lot has happened, but one thing remains constant: We are all strong believers in the future of digital currencies and we love being part of this growing community.
Servicing over 2.000.000 customers from 100+ countries
Conducted over 100 million transactions since our founding in 2013
Offering 10+ minable cryptocurrencies through 6 major mining algorithm
Vision & Mission Making mining accessible to everyone PhanesTech is one of the leading hash power providers in the world, offering cryptocurrency mining capacities in every range - for newcomers, interested home miners, as well as largescale investors. Our mission is to make acquiring cryptocurrencies easy and fast for everyone. We provide a multi-algorithm, multi-coin cloud mining service using the latest technology-without any pool fees. The ultimate goal of our existence is to make cryptocurrency mining an easy, smart and rewarding experience for all. Our services already attracted more than 2.000.000 people - We’d be happy to serve you as well! WHY MINING WHY IS MINING SOIMPORTANT?
Cryptocurrency need computational power to run securely. The world most powerful blockchains are supported by millions computer around the world.
HOW IS CRYPTOCURRENCYKEEP SECURE?
The only way to not create money out of thin air or corrupt it, is to burn real energy, this is called Prove-Of-Work.
WHAT IS THE INSENTIVEFOR MINERS?
It’s all come down to trust: Miners keep the blockchains trustworthy and are rewarded for their effort.
THE BIG VISION OFCRYOTOCURRENCY
The future will be decentralized.
WHY PHANES TECH We are making mining accessible to everyone. We are uniting all key aspects of running an efficient cryptocurrency mining operation. From building highly efficient data centres to providing a streamlined mining system for our users We make mining competitive. To mine competitively today, you need to invest significant resources, time and effort into your setup. Our team has built the most efficient mining systems to do the job for you. This way you can fully focus on keeping track of the markets and remain competitive with your mining rewards. Contributing to the ecosystem. Besides being the portal for interesting mining data, we are also actively contributing to the cryptocurrency ecosystem, from launching awareness campaigns to releasing open-source mining software. Multi-algorithm support. We are building mining data centres around the world that are able to support 6 mining algorithms for10+ different cryptocurrencies. If that’s not enough, we’d be happy to also support the ones you want to mines. FEATURES
Daily Mining Outputs
Your mining outputs will be added to your account daily and automatically
State of the Art Mining Technology
for every blockchain algorithm that we offer, we’re providing some of the highest performing mining systems that exist
Diverse Mining Portfolio
Choose from 6 major mining algorithms that span over 10+ mineable crypto currencies
Freedom of Allocation
Allocate your hash power to other cryptocurrencies within your mining algorithm of choice
Intuitive Dashboard
All the crypto mining data and charts that you need, when you need them
Secure & Private
We support cryptocurrencies that promote privacy, so we strive to keep collected user data to a minimum and only ask for information that is mandatory from a regulatory perspective
2 notes
·
View notes
Text
How did the Bitcoin mining change: from CPU to cloud mining
Hey, geeks! Today we’d like to dedicate an article to the origins and history of the most known and popular cryptocurrency — Bitcoin, also answering the question “What is, in fact, Bitcoin?”
We hope you’ll enjoy our small insight as we’ve made it as simple and informative as possible.
Everything started in 1983 when David Chaum and Stefan Brands proposed the very first protocols of “electronic cash”.
Several cryptocurrency concepts were introduced later, and even some market mechanism models were estimated. But only in 2008, the file with the description of the protocol and the working principle of Bitcoin P2P network were published.
The person or even a group of people behind it is still a mystery. The only thing we know about the creator is a pseudonym, Satoshi Nakamoto. In 2009 Satoshi had finished the dashboard, and the network was launched.
The first Bitcoin had been used for purchase in 2010 when Laszlo Hanyecz bought two slices of pizza for 10 000 Bitcoins. Just to remind you, today 1 Bitcoin’s price is about $5300 and the highest value can be over $5800 per 1 Bitcoin.
There are hundreds of other cryptocurrencies: Litecoin, Ethereum, Ripple, and even Dogecoin or Fedoracoin. But Bitcoin is the most widespread of all the cryptos. At the moment, thousands of restaurants and shops worldwide accept Bitcoin as a payment method.
The gold fever

Mining (or so to say Bitcoin production) is a process of solving a cryptographic task. The solution to the task is a symbol sequence found by enumeration. That’s the reason why it is so demanding for huge computation power.
The core of Bitcoin’s system safety is also mining. Basically, miners group Bitcoin transactions into blocks which are then hashed an unbelievable number of times to find one infrequent and eligible hash value. When such a value is found, the block gets “mined” and is put in a chain of previously mined blocks (the blockchain). The hashing itself isn’t useful and is only needed to raise the difficulty of finding the following appropriate hash value. This ensures that no one with unlimited resources could take control over the whole system. For each block mined, miners get a reward. Originally it was 50 Bitcoins per block, but to prevent the uncontrolled emission of the currency the reward drops twice after every 210 000 blocks mined. Each new block appears in about 10 minutes — which means a block can be mined in 9 as well as in 11 minutes. For the ease of calculation, we’ll make it 10 minutes. On that basis, the total number of Bitcoins should be no more than 21 million. About 55% of Bitcoins are already mined, and it is estimated that 99% of them will be mined in 2032.
At the moment, there are four generations of mining hardware (or miners) starting from simple CPU-miners and ending with next-gen ASIC-miners. It doesn’t ultimately mean that you can’t mine Bitcoins at home with your CPU — it just won’t be any profitable.
The first generation: CPU-mining

Profit depends on your processor — a top-class Core i7 would give you around 33 MH/s (mega hashes per second). All calculations are processed on 512-bit blocks of data and contain a lot of different operations. The result of each operation depends on the result of the previous one.
The second generation: GPU-mining

The next generation of miners was based on processes taking place in graphics cards. Such miners contained bitcoin-protocol realisation in Java or Python and an enumeration algorithm in the form of an OpenCL file which should have been compiled accordingly to the ISA of a related GPU.
Miners used different tactics to increase their profits. Some of them played with voltage: some increased it to increase the productivity, others lowered it to save on electricity. Some tried to modify GPU cores and code parameters to augment the flow.
Unlike CPU, which is always meant to stay single, several GPUs can be connected to a motherboard forming a rig. This allowed building first Bitcoin mining farms based on graphics processors.
Typical AMD GPUs demonstrate higher productivity than nVidia’s once we compare GH/s to $ values. That’s why AMD GPUs were and still are quite popular among miners.
The third generation: FPGA-mining

FPGA-mining did not bloom for long as It was quickly replaced by a new generation of hardware — ASIC. FPGA Spartan XC6SLX150 based circuit boards allowed to raise productivity to 860 MH/s with the frequency of 215 MHz, energy demand of 39W, and a price of $1060. Proprietary hardware developed by Butterfly Labs (BFL) from Kansas, US showed the similar productivity of 830 MH/s with $599 price tag. Their best solution was based on the FPGA Altera showing 25,2 GH/s at the cost of $15K (650–750 MH/s per chip).
The main issue of FPGA mining, when compared to GPU, was its cost. On average the cost of FPGA mining was 30% higher. Besides that, GPU boards have greater potential for further reselling once they’re not used for mining any longer.
The fourth generation: ASIC-mining

The coming of ASIC was the end of other types of mining. ASIC miners are significantly different in relation to size to productivity and energy consumption. BFL was the first company to appear on the market and was followed by ASICMINER and Avalon.
The fourth-generation miners were expensive. As the popularity of cryptocurrencies grew, the interest in mining also increased. Not everyone can afford a miner even in its minimal procurement. High hardware prices forced people to find other solutions like hardware downgrading or selling lighter versions of miners. But the price was still quite too high, and users had to deal with all the problems, settings, etc. Cloud mining quickly became an optimal solution opening the world of Bitcoin mining to pretty much everyone.
Cloud mining

Bitcoin mining would become popular only once it was available to every interested person. Cloud mining was exactly that kind of thing. Our project allows users to rent part of our mining hardware power and start earning Bitcoins in just a few clicks. Everything you need is a desire and a few bucks for a start.
After registration, you only need to choose the appropriate mining (be in Bitcoins, Litecoins or maybe Ethereum), connect your wallet and start gaining your first Bitcoins.
The calculator will show your estimated profit, and the graphs will allow you to follow the results in different pools.
You can arrange the rented power among the most preferred pools to maximise your profit. If you realize you need more power, it is always possible to buy more.
Right now, Phanes Technology operates on a whole range of different hardware, including all market’s top and flagman models.
Ready to start yourself? We’re here to help you! Let us know what you’d like to learn next.
#cloudmining#cloudminingwebsite#cloudminingwebsites#crypto#cryptocurrency#cryptocurrencies#cryptotrading#cryptonews#bitcoin#bitcoi
2 notes
·
View notes
Text
Phanes Technology
PhanesTech YOUR BEST CLOUD MINING CHOICE http://www.phanestechs.com

WHO WE ARE The story of PhanesTech started at the end of 2013. Our founders got to know each other by using the same platform for buying and selling Bitcoins. They were fascinated by the technology and wanted to build their own farm, only to realize all their friends wanted to participate as well. They came up with the idea of mining as a service and built the first mining farm in Eastern Europe. Since our founding, we have grown tremendously and a lot has happened, but one thing remains constant: We are all strong believers in the future of digital currencies and we love being part of this growing community.
Servicing over 2.000.000 customers from 100+ countries
Conducted over 100 million transactions since our founding in 2013
Offering 10+ minable cryptocurrencies through 6 major mining algorithm
Vision & Mission Making mining accessible to everyone PhanesTech is one of the leading hash power providers in the world, offering cryptocurrency mining capacities in every range - for newcomers, interested home miners, as well as largescale investors. Our mission is to make acquiring cryptocurrencies easy and fast for everyone. We provide a multi-algorithm, multi-coin cloud mining service using the latest technology-without any pool fees. The ultimate goal of our existence is to make cryptocurrency mining an easy, smart and rewarding experience for all. Our services already attracted more than 2.000.000 people - We’d be happy to serve you as well! WHY MINING WHY IS MINING SOIMPORTANT?
Cryptocurrency need computational power to run securely. The world most powerful blockchains are supported by millions computer around the world.
HOW IS CRYPTOCURRENCYKEEP SECURE?
The only way to not create money out of thin air or corrupt it, is to burn real energy, this is called Prove-Of-Work.
WHAT IS THE INSENTIVEFOR MINERS?
It’s all come down to trust: Miners keep the blockchains trustworthy and are rewarded for their effort.
THE BIG VISION OFCRYOTOCURRENCY
The future will be decentralized.
WHY PHANES TECH We are making mining accessible to everyone. We are uniting all key aspects of running an efficient cryptocurrency mining operation. From building highly efficient data centres to providing a streamlined mining system for our users We make mining competitive. To mine competitively today, you need to invest significant resources, time and effort into your setup. Our team has built the most efficient mining systems to do the job for you. This way you can fully focus on keeping track of the markets and remain competitive with your mining rewards. Contributing to the ecosystem. Besides being the portal for interesting mining data, we are also actively contributing to the cryptocurrency ecosystem, from launching awareness campaigns to releasing open-source mining software. Multi-algorithm support. We are building mining data centres around the world that are able to support 6 mining algorithms for10+ different cryptocurrencies. If that’s not enough, we’d be happy to also support the ones you want to mines. FEATURES
Daily Mining Outputs
Your mining outputs will be added to your account daily and automatically
State of the Art Mining Technology
for every blockchain algorithm that we offer, we’re providing some of the highest performing mining systems that exist
Diverse Mining Portfolio
Choose from 6 major mining algorithms that span over 10+ mineable crypto currencies
Freedom of Allocation
Allocate your hash power to other cryptocurrencies within your mining algorithm of choice
Intuitive Dashboard
All the crypto mining data and charts that you need, when you need them
Secure & Private
We support cryptocurrencies that promote privacy, so we strive to keep collected user data to a minimum and only ask for information that is mandatory from a regulatory perspective
2 notes
·
View notes