A tech leader when it comes to educating the public on technology. We have a wide range of helpful guides that show you how technology works. Online since 1999 we have been featured in many popular tech blogs and magazines. PC Tech Guide's Google+ PC Tech Guide's Blog
Don't wanna be here? Send us removal request.
Text
Stellar Cost-Saving Benefits of Free VPN Services
A recent study from PC Magazine showed that the global VPN market will reach $36 billion by 2022. There are tremendous benefits of VPNs that are driving the market.
Numerous people already installed a VPN as it is a really necessary tool in the modern world. It allows the user to feel safe on the Internet while conducting financial transactions or downloading some content. At the same time, it allows to access blocked websites or just remain anonymous on various resources.
However, it is sometimes difficult to choose a good service that will allow you to stay safe and will have all the necessary functions. Moreover, most of the services are available only for a PC and it is essential for modern people to have access to any website from the smartphone. You can read Green VPN reviews on cooltechzone or learn how to access inaccessible sites from your phone or computer and not spend a penny on it.
How VPN Services and Anonymizers Work
If to simplify the information, the anonymizer is a small browser tunnel through which you can sneak onto a particular website without being noticed. This tunnel runs through data that no one can see or intercept. VPN is a big tunnel between your device (computer or smartphone, no difference) and all the Internet at once for all your applications: browser, messenger and so on.
Incoming and outgoing connections when using VPN are not direct but through the server, which can be located in your country and abroad. For example, if you want to visit the European site but it does not open, connect the server from Germany. In this case, the site takes you for a German user.
Why Do We Need Anonymity
1. To buy software cheaper
Let’s see how much Adobe Creative Cloud products cost for individual users in Europe. And now let’s try to pretend that we are from another country. Choose Israeli IP, clear cookies or go to the booking site in incognito mode. It turns out that the tariff plan for working with photos of 20 GB with monthly payment costs considerably less. With the purchase of all the applications at once, it is even more profitable: you may save up to $100.
2. To save on travel
Services for booking hotels and air tickets are often cunning and offer different prices depending on the location of the user. Here’s how it works: we go with the Russian IP and look for tickets from Moscow to New York for one person on August 9. The service offers the best price – $600. With the help of the VPN, we change the IP to the American one and see what happens next. There are more offers, and the cost of tickets has decreased.
How to Connect VPN
It takes about five minutes. Go to the HideMy.name website in the VPN section, select the option you want (for Windows, Mac, Linux or mobile devices) and click on the big green button. Install the application, enter the code – nothing else needs to be done. To try the service for free, get the code for the test access. One code can be used simultaneously on multiple devices. For example, on the work and home computer.
You will get unlimited traffic, the ability to use email clients and rent a personal IP, as well as access to all HideMy.name servers, including high-speed European ones. IP will be used only by you, so you do not need to worry that it will be included in a blacklist. It is also an additional guarantee of security for services where it is possible to restrict entry to a single IP. If the work of the service does not suit you, within 7 days after the purchase HideMy.name will return your money.
What If all My Data Is Stolen?
1. There is neither registration nor a user’s personal account – the personal data of users is not needed by the service. Transmitted traffic and DNS queries are also not stored anywhere.
2. You pay for using HideMy.name, and the service is responsible for the safety of your data.
3. HideMy.name has been working for 11 years. A service that does not provide the proper level of data security would simply not have been afloat for so long.
The post Stellar Cost-Saving Benefits of Free VPN Services appeared first on pctechguide
0 notes
Text
4 Top Challenges of Using Business Card Software
The graphic design industry is growing at a remarkable pace. According to research from IBIS World, the industry generated $14 billion in revenue last year. The rising costs of visual creative professionals have encouraged many people to try using design software themselves. Unfortunately, this is a case where they are often worse off. This is a big concern for people trying to design business cards on their own, which is one of the reasons they tend to turn to professional designers instead.
The problem is that these software applications are often difficult to navigate. Here are some of the biggest challenges that people face when using business card software.
Figuring Out the Right Extraction Method
Most business card designs start with templates, which include several large base images. The designer needs to make major modifications to these images.
In order to accomplish this, they need to use an image extraction method. There are a number of extraction features available in Photoshop and most other business card design software. They include the Quick Select and Pen Select options.
Too many people think that they should use the Quick Select method for editing large images. However, they invariably miss some important contours in the process. The Pen Select option tends to be better for extractions requiring high levels of precision.
Unfortunately, even using the Pen Select option isn’t easy, even with more simplistic business card designs. You need to have a considerable amount of dexterity to select it properly. Even minute issues can leave visible, excess pixels which can ruin the quality of the design.
Using the Ideal Number of Image Layers and Folders
There are a number of different approaches to layering in Photoshop and other image design tools. One thing that you need to keep in mind is that image layering is necessary to make sure that the images an be properly stacked on each other.
This requires you to utilize the right number of layers and folders. With lots of layers, you will be able to edit and duplicate images as necessary for your new business card design.
However, this doesn’t mean that adding as many layers as possible should be your best option. This can make it nearly impossible to keep track of the visual elements that you want to duplicate or modify.
You need to be realistic about the opportunities to merge visual elements from different images into your final design. Limit your layering to those elements that are necessary for your final business card design.
Feathering Edges with a One or Two Pixel Tolerance
Moving subjects from one section of an image to another (or from one image to another) can be a considerable challenge as you try to create a great business card. If you don’t do this properly, you will leave the subject with very rough edges.
The only real solution to accomplish this is to try feathering the edges. Feathering allows you to transition images seamlessly with a resolution of as little as two pixels.
The challenge here is making sure that you feather the images very carefully. You need to be able to transition the feathered images carefully, so that the resolution is just perfect.
Incorporating Route Backs
There are a lot of factors that you need to consider when making new design changes. When you are designing business cards, you can make a number of changes and try to save different versions of the file along the way, so that you can try to return to previous designs if you don’t like some of your most recent changes. Unfortunately, this approach creates a couple of problems:
You can easily lose track of all of the changes that you made, so it will be virtually impossible to find the right image if you need to revert to a previous design.
Your files will be cluttered with hundreds of images that will be hard to sort through.
The only option here is to build route backs into your design.
The post 4 Top Challenges of Using Business Card Software appeared first on pctechguide
0 notes
Text
Understanding the Seven Levels of RAID Arrays
I previously covered an article on the new research on RAID arrays, which has originated from FASTA Universidad. The latter half of their paper covers the different RAID levels that you should be aware of. Here is an overview of this very important research.
Learning the Nuances of the Seven Levels of RAID Arrays
The RAID specification is defined at seven different RAID levels. The seven RAID levels are as follows:
? RAID 0: RAID array disks are fragmented into chunks according to
bands, also called stripes, which allows the data handler to use the disks in parallel to
perform read/write operations on each disc. This RAID level provides
excellent performance, but no data redundancy.
? RAID 1: also called “mirror array”, defines a data disk and one or more disks.
Mirror disks are identical copies of the data disk and can be
automatically replaced if a fault occurs. This RAID level allows parallel reading
of the mirrored parts, but the main advantage of this way is that it
performs an “automatic backup” of the data disk to protect the information
against a physical rupture of all but one of the disks that make up the array.
? RAID 5: The disks in the RAID array are fragmented into bands, allowing the data handler to perform
parallel reading and writing on multiple disks. Each band
that corresponds to each disk is called chunk and an XOR function is calculated from the
N-1 chunks of band data. The parity chunk is distributed between disks for
different bands of the array, and thus prevents a single disc from loading with the array.
The writing task is associated with parity storage. This allows for better
performance of the entire array, as the use of the disks tends to be uniform.
Parity chunks allow the array to withstand the failure of one of the disks and continue
running in degraded form, waiting for the disk to change, and reconstruct the
lost disk when a replacement disk is available. RAID 5 is a balance between
capacity, performance and data redundancy.
? RAID 6: can be considered a variant of RAID 5 where two RAIDs are calculated.
Different parity functions allow the data handler to recover the array even if two
Disks fail. Again, there is a delicate balance between capacity, performance and redundancy.
In particular, this level of RAID makes it possible to retrieve from the RAID.
There may be a case where a second disc is broken during reconstruction.
In levels 5 and 6 it is also necessary to specify how the chunks will be distributed.
There is also a parity between the different bands. Three standard algorithms are usually applied, as shown here: Left
Asymmetric, Left Symmetric and Right Asymmetric. The difference between the three lies in the mode
in which parity and order are distributed.
RAID can be implemented by both software and hardware. The implementations of
Software RAID allow flexibility and provide different advantages at different levels. There is usually a tradeoff with performance, since the tasks required to manage the disks and
parity calculation must be carried out by the operating system, introducing the processor
as part of the critical path of the storage system.
In the case of a hardware-implemented RAID, some degree of flexibility is lost.
Performance is gained: the operating system delegates the tasks of
administration and calculation to the RAID controller. The controller is exposed to the host as one or more virtual disks.
In addition, RAID controllers can be implemented to write caches and circuits.
This requires a specific calculation for the parity functions, which allow to bring the arrangement closer to the theoretical maximum performance.
The post Understanding the Seven Levels of RAID Arrays appeared first on pctechguide
0 notes
Text
UI Regression Testing as a Tool to Build a User-Friendly Product
Developing a new product, whether it is an application or an online website, is a quite challenging task, which requires a well-planned and structured approach and in-depth preparation from the entire team. You can invest a lot of money in a new project but get negative reviews and sales decline. Why can that happen? How to ensure a 100% smooth and successful product launch? Is there any way to maintain a top-level quality of your product after it is introduced to the market? Let us get all this straightened out.

The situations of project failure occur when the developer misses an important stage of product planning life cycle ? UI regression testing. Visual regression testing employs an alternative approach to testing web pages. Thus, instead of just making sure that some element or text is present in the DOM, the test opens the page and checks that the particular block looks exactly the way you want it.
Do not know how to get the testing properly done with zero instrumental errors? Then you should definitely check the functional capacities of https://diffy.website/ service. The solution is highly interactive and easy to use. Owing to its flexibility, you can configure the service based on the specific needs of your project and invite the entire team to take a look at the regression test results.
Features of UI Regression Testing
The task of the graphical user interface testing is to detect errors of the following nature:
Interface errors/ mismatch;
Unhandled exceptions during user interacting with an interface/ website;
Loss or corruption of data transmitted through interface elements;
Errors in the interface (inconsistency of project documentation, lack of interface elements, etc.).
With Diffy, you will have all the above features constantly tracked. And in case of any design/ implementation failure, you will be immediately informed about it.

Benefits of Automatic UI Regression Testing
Apart from you tracking the functioning and design changes in the online resource, the Diffy service will provide you with some other great benefits:
Reduced cost of testing;
High execution speed;
Greater service coverage;
Participation of the in-house QA specialist is not required when conducting regression testing or any other product retesting.
As an extra profit, you can adjust the testing “scenario” and mask highly dynamic elements on your pages to avoid false positives. All the setup options will be available to you in the project’s setting section.
Final Say on UI Regression Test Automation
Such visual details as fonts, colors, alignment, and images are needed not just for the convenience of using the website. They are also important for displaying the characteristic features of the brand, such as user-friendliness, design intuitivity, reliability, and innovation. A company can get a lot from effective branding, so visual aesthetics and its impact on users should be assessed carefully, based on research data.
Along with that, it is designed implementation result and its proper maintaining on the website what makes a lot of sense for the project. That is why using utilities for website automation UI testing should in no case be neglected.
The post UI Regression Testing as a Tool to Build a User-Friendly Product appeared first on pctechguide
0 notes
Text
Our Review of EaseUS Data Recovery Wizard Free
EaseUS is one of the most reliable data recovery, data backup and data partitioning software publishers on the market. They created a free data recovery program that is widely supported by many other users.
We were asked to review the application. Although we were compensated for the review, it is an objective review based on our own experience with the product. Here is our analysis.
Speed of Data Recovery
I tested this data recovery tool on a PC that is three years old. I ran a scan of my image drive to see how quickly it could restore deleted images.
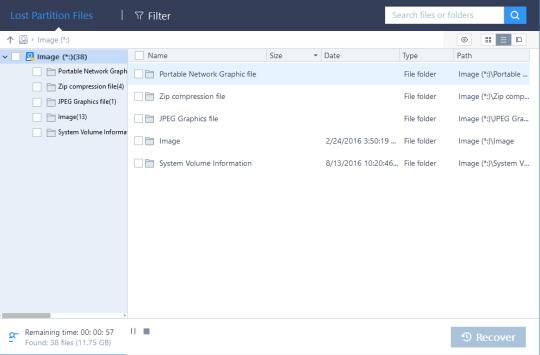
When I first started running the application, it told me that I would need to wait two minutes to fully recovery all of my deleted files. The actual process took seven minutes. That was slightly longer than the initial estimate, but was still a lot faster than I was expecting. I had deleted over 70 files since the computer was purchased, so it was pretty impressive that it could identify them in under 10 minutes.
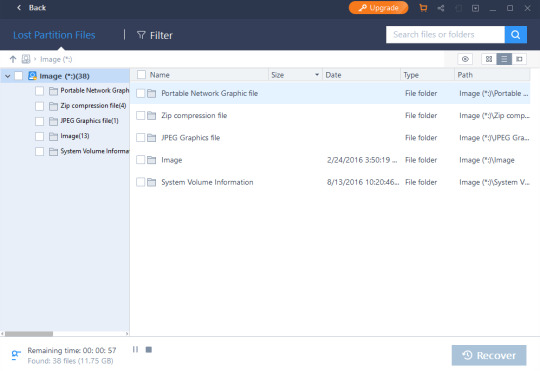
When I selected a file folder that I wanted to restore, EaseUS Data Recovery Wizard was able to restore it in less than a minute. This folder was 500MB, so I was even more impressed that it could restore it that quickly.
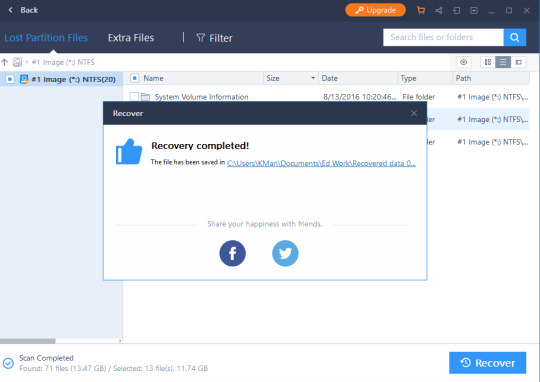
How Much Does EaseUS Data Recovery Wizard Cost?
I was able to use the free version of EaseUS Data Recovery Wizard. The free version allows you to restore up to 2GB of information. This is a very reasonable deal and should help you restore any old pictures or documents that you might have lost.
If you have deleted an unusually large folder or images or a larger software application, then you can always upgrade to the Pro version. The Pro version of EaseUS Data Recovery Wizard allows you to restore an unlimited amount of data. You will only have to pay $69.5 to upgrade.
What Do Other Reviewers Have to Say?
If you are interested in hearing what other reviewers have to say about this program, you should be pleased to hear that they have given it a thumbs up. Here is an excerpt from a review from PCWorld:
“EaseUS Data Recovery Wizard Free Edition is a capable performer, which can recover data from your hard drive, USB drives, memory cards, and other storage devices!”
The program has received a 4.5/5 star rating from 334 people that have left reviews. This is a good indication that the program has been well received by its users.
Are There Any Downsides to EaseUS Data Recovery Wizard?
EaseUS Data Recovery is a very good application overall. The only downside I would mention is that the estimated restoration time is a little longer than it initially states. I was originally told that it would take one minute and 40 seconds to identify all deleted files, but it took around 7 minutes. However, this is a very minor complaint, considering that the application still restores data very quickly and fully.
What Operating Systems is the Application Available on?
I used the application made for Windows. There is also a version that can be used for Mac computers. However, I didn’t test that one. I expect the quality to be the same though.
Overall Opinion
Our overall opinion of EaseUS Data Recovery Wizard is very high. It is a fast and reliable application to restore lost data. It is also a very reasonably priced option for people that don’t want to spend hundreds or thousands of dollars to restore data from their machines.
The post Our Review of EaseUS Data Recovery Wizard Free appeared first on pctechguide
0 notes
Text
Current Trends: Why Mobile Apps Rule The World
Smartphones became, basically, small personal computers that we take everywhere with us. They allow us to read books and listen to music, listen to podcasts and watch movies and series, they allow us to take photos and videos of amazing quality and edit them right on this very smartphone. Weather, notes, social media, maps, emails, bank cards, and so many more functions are combined in one small technical item. So, little surprise people use it extensively and enjoy all possibilities smartphones provide.
Mobile applications for smartphones, and also for tablets, are among the trends that continue to grow today. From the point of view of the companies, each one considers mobile development services for the sake of creating its own application, to be able to reach out to the users every time the user is online through the smartphone, which means – almost anytime. In terms of business, mobile apps are crucial and can make a difference between no profit and profit, and between profit and huge profit.
https://tr2.cbsistatic.com/hub/i/r/2017/01/25/e7c48d8d-4bd9-4afd-bbf9-8952fd152641/resize/770x/7246e0a10c43f897ad338c10a8dc91a7/mobileapps.jpg
On the other hand, users also benefit from mobile applications to a huge extent. It is much more convenient to reach out to a website, service, or shop directly through the application, instead of going to Google or Opera, type in the name of the service or website, wait until it all loads, then go to the website, then go to page… so much to do when one can simply tap three times on their smartphone screen and voila.
If you believe that all companies that offer mobile applications do it only to sell, sell, sell everything they can to the user, and to annoy you with their ads day and night, well, you’re wrong. Users are pretty pampered today, and for a good reason: they have so much choice. And the choice is good. No choice is the Soviet Union, and no one wants that. Users also became more aware of their rights as customers, especially of their rights for privacy. Every application that spams them is deleted forever. Any application that is not user-friendly, does not have intuitive design or lags, gets deleted without hesitation. Moreover, any application that offers all its services only for money, and provides no free benefits for the user, is also deleted.
https://img.etimg.com/thumb/msid-46065787,width-300,imgsize-83533,resizemode-4/7-things-mobile-app-developers-should-focus-on.jpg
Before the company can offer the user a paid product or can ask him to buy a paid version of anything, it has to prove its product or service actually brings value. For free, yes. The Internet is a place where a lot of fraud is happening, and users no longer pay in advance without seeing what they get. Therefore, companies that offer mobile applications look for an opportunity to show their potential customers that they can provide value. Customers can test out the service or product and then, hopefully, buy.
That is mobile apps are beneficial for both parties – the company and the user, where the company shows what it can offer, and the user allows it to show its value in return for using a free service. And this is the reason why the trend of mobile apps continues to grow and develop.
The post Current Trends: Why Mobile Apps Rule The World appeared first on pctechguide
0 notes
Text
Apple Launches New Site for EU Users to Request Data Records
Apple launched a privacy site where its in the European Union will be able to download the information and data that the technology company has about them in association with their ID (identifier). This site should extend its capabilities to users in the United States later as well.
Both Facebook and Google have already implemented similar tools.
In the case of Apple, the portal will provide information that includes the person’s activity in the App Store, iTunes Store, iBooks Store, and Apple Music, as well as Apple’s online store and its retail stores. Their history may also be requested at the AppleCare support center and other data such as iCloud bookmarks, calendar entries, reminders, photos, and other documents.
To access the information, you will need to log in to the new portal with your Apple ID account.
At the moment, the site is only available for accounts based in the European Union, in light of changes under the new General Data Protection Regulations (RGPD) that will come into effect tomorrow in that continent. It will change the way companies and public bodies collect, store and use information from Europeans.
This is a process that began almost two years ago and means that any organization -whatever its geographical location- that works with European data will have to report in an “understandable” way how the data that is requested and eliminate it from their servers when that mission is fulfilled.
Apple indicated that its new privacy portal will be enabled for the rest of the world in the coming months.
Apple is covered by the European Union’s General Data Protection Regulations (GDRP), which will be binding from May 25. This week the technology launched a site to compile, collect and modify the personal data it has of its users, in favor of digital transparency.
The manufacturer of the iPhone joins Facebook, Google, Whatsapp, Twitter and other technologies that have new services of apparent horizontality with respect to data management, in compliance with the RGPD and also in response to the scandal of Cambridge Analytica, which exploded earlier this year.
Apple: All Apple Pay data, text messages and Facetime calls are “fully encrypted”.
Apple defends the protection of privacy through its encryption system. “When you pay at the supermarket with Apple Pay, send an iMessage to a friend, or make a Facetime call, your data is fully encrypted. The same goes for the personal information you store on your device,” the company explains.
To help its customers verify the security of their data, the company launched a new platform that lists all the information stored in an account and allows customers to select the references they want to download. The process can take up to seven days.
What does Apple know about its users?
Apple anticipates that copying data requested by users will include details about app usage and activity information in spreadsheets and other formats, as well as documents, photos and videos in their original format, and calendars, contacts, bookmarks, and mail messages in a variety of formats.
The technology also lists what the download will not include. These so far includes a specific listing of purchases of apps, books, movies, TV shows, or music, as well as a detailed history of transactions made in your digital store.
Apple’s privacy portal allows you to correct data stored in an account or delete the account and delete all associated data.
Messages from the iMessage platform will not appear either, as Apple explains that these chats are encrypted and can only be accessed from the devices. Transactions outside the App Store are also not recorded.
Apple’s new privacy page allows you to correct the data that Apple technology handles, deactivate the account or permanently delete it, which also presents the possibility of deleting all data associated with it.
The post Apple Launches New Site for EU Users to Request Data Records appeared first on pctechguide
0 notes
Text
Deactivating Facetime to Thwart Hackers
There are some silent threats that can become very serious if precautions are not taken. Facetime exploits are one of them.
If you’re a FaceTime user, it’s probably worth deactivating the feature when it is not in use. At least, until we verify that Apple releases the case update (expected this week).
Victor Chebyshev of Kaspersky Lab shared his research findings:
“From what has been reported so far in the media, it would seem difficult for an attacker to exploit this error to stealthily monitor his targets, as the potential victim would receive an incoming call alert.”
The company has also temporarily disabled FaceTime’s group chat feature to further protect users from possible abuse of privacy. We encourage anyone who remains concerned about their security to disable FaceTime until the Apple patch is released.
This threat does not require you to click on a link, inadvertently download a compromised file, or even answer a call. This vulnerability is like the flu and other silent respiratory viruses that spread through FaceTime.
All of the above happens without having to answer the call on the receiver’s device (with iOS 12 or higher). The sender can simulate a kind of group conversation and add its own subscriber number, and then listen. If they are dedicated enough, they can access an iPhone or iPad camera (some users claim hackers have replicated the problem on a Mac). They initially do this to the first device they infect, but they can infect other devices later.
It is important to remember that the first participant will not notice what is happening at all. The first infected device will still ring waiting for the reception of the incoming call.
Deactivating Facetime as Needed
Fortunately, deactivating Facetime is pretty straightforward. You just need to take the steps listed below.
After it became known that the app was spying on users, many have wondered how to delete it from devices and here’s the answer.
Unfortunately, the security flaw in FaceTime’s app is damaging Apple’s credibility with its users, so many are wondering how they can uninstall it from their devices. The good news is that the app doesn’t need to be uninstalled altogether. You can just deactivate it when it isn’t in use. This will almost entirely eliminate the risk of having your Facetime account get hacked. You just need to coordinate with people you talk to through text messages before jumping on a Facetime call.
This is a consequence of people being fed up with the lack of respect for their privacy, and it is valid at least until the company fixes the problem and promises it won’t happen again.
While this happens and the respective security patch is being applied, the procedure for removing the iPhone and Mac application respectively will be released.
But before releasing this type of information, you should check if you are susceptible to this type of bug, and the form is simple, because you only need to know the version of the iPhone, as it attacks from 12.1 to 12.1.3.
Disable FaceTime on iPhone
The procedure for disabling Facetime on the smartphone is quick and easy. You just need to follow the steps listed below:
Go to Settings
Find the FaceTime app
Move the circle to the left to deactivate it.
It is that easy.
Disable FaceTime on Mac
On Apple computers, the method is also quick and easy. You just need to do the following:
Open the application
Click Menu
Select Preferences
Remove the popcorn from Activate in this account
You can always reactivate it when you need to use it again.
The post Deactivating Facetime to Thwart Hackers appeared first on pctechguide
0 notes
Text
Essential Steps to Restore Lost Macbook Files
MacBooks are gaining tremendous popularity. They might soon overtake the total computers produced by the largest PC manufacturer. Apple reportedly sold 5.3 million MacBooks in the fourth quarter of 2018 alone.
As more people invest in MacBooks, we are starting to become more aware of the technical issues. Data loss is one of the most common problems.
There are a number of reasons that MacBook files can be lost. Some of the most common problems are:
Malware infections
Physical trauma to the media storage devices
Failed operating system upgrades
Corrupted software files that create instability’s in the rest of the system
Human error
All of these problems are common causes of MacBook file loss. Viruses are especially dangerous. The Flashback is one of the worst causes of data loss, after infecting at least 650,000 Macs around the world. Fortunately, there are a number of ways that you can restore files to your Mac device.
Here are some general guidelines to help you restore lost files from your MacBook.
Pinpoint the cause of your data loss while running memory mode
You are going to need to take the following steps to begin restoring the data.
Specify the Cause of the Data Loss in the Memory Mode Wizard
Before you can start restoring lost MacBook files, it is necessary to identify the cause of the problem. Even if you have found that there is no damage to your MacBook media, you still need to determine the cause of the problem before you can start restoring your files.
When you are using a MacBook file recovery tool, you may need to specify the cause of the file deletions and how are you intend to restore the data. This is usually done in a process called memory mode or something similar. You will need to launch the memory mode process when you begin the program. Your selections may include:
Restoring data that has been lost during the formatting or petitioning process
Restoring files that have been accidentally deleted from your main hard drive
Restoring files that have been deleted from your trash bin
Restoring files that have been lost due to an improper update
Restoring files that have been deleted by a virus
Choose the proper option from the memory mode wizard to ensure that your files are properly restored.
Conduct a quick scan on the hard drive that the data was lost
Once you have specified the type of file deletion that you need to restore from the memory mode wizard, you’re going to need to scan the affected hard drive for the files that you want to restore. You can perform a quick scan by clicking the hard drive and selecting the appropriate scan button. Keep in mind that this operation is usually used for more easy to identify files. They have usually been recently deleted due to human error without being overwritten. If the files have been overwritten or the media has been compromised in some way, then you’re going to need to use a full system scan and recovery.
Select the files to restore
The final step is to preview the files and restore them individually. You need to make sure that you are restoring the right files.
How can you restore files from a hard drive or MacBook media external storage device that has been physically damaged?
Recovering files from a MacBook that has been physically damaged is going to be more difficult. Fortunately, there are a number of MacBook file restoration tools that can help.
Mac World discusses some of the problems that you need to tackle during this process. You are going to need to first determine whether or not the physical device can be repaired. Then, you are going to need to launch the Disk Utility wizard. You will need to then specify that you want to scan the disk and search for errors. Once the errors are identified, you are going to start searching for errors and select First Aid command to fix them.
This is often sufficient, provided there wasn’t any extensive damage to the device. However, if the device was badly damaged, then you will need to try using a MacBook file recovery tool.
The post Essential Steps to Restore Lost Macbook Files appeared first on pctechguide
0 notes
Text
Nuances of Bandwidth for Both Webmasters and Internet Users
Online bandwidth is the measurement of the amount of digital information that a medium is capable of processing and transferring. Mediums with higher levels of bandwidth are capable of loading the same amount of information more quickly or more information over the same time interval. This concept is most commonly used with website owners. They need to know how much data they can process.
Both Internet users and Website owners must take bandwidth metrics with a grain of salt
You have probably noticed that Internet bandwidth speeds have surged since the beginning of the Internet. One expert that I spoke with said it was not uncommon for dial-up connection is in the late 1990s to have been with speeds of only 100 kps. By 2007, bandwidth speeds reached 3.67 MB per second. That figure increased by 404% over the next 10 years.
At first glance, this seems like an encouraging development for Internet users and brands trying to reach customers through the digital marketplace. However, there are other issues that need to be taken into consideration. While Internet speeds are increasing at a record rate, they can easily be offset by large caching requirements of cumbersome websites.
Both webmasters and Internet users must recognize that there are issues that could limit load times, regardless of bandwidth capacities.
Get the best hosting plan
Getting a good hosting plan is essential. You need to choose a plan with a great hosting for small business e-commerce to make sure you have sufficient bandwidth.
Visually intensive websites load slower even with excellent bandwidth
Many factors affect website loading times. One of the most significant is the amount of visuals on the webpage. Every image or video needs to be cached from the visitor’s ISP before it can be loaded. Adding three times as much visual data to the page could increase in already slow loading webpage loading time from 1.5 seconds to three seconds.
Caching times will be higher for customers located far away from the webpage server
A growing number of websites are catering to Internet users in different regions around the world. Their challenge is to make sure that websites load quickly for customers and all of those regions.
Reducing artificial latency by matching website visitors with the closest server could reduce low times by 64%, according to a case study from ancestry.com. Similar observations were made with The Telegraph. One way to accomplish this is by using a content delivery network to connect visitors to the closest server.
Being mindful of bandwidth restrictions at the other end of the connection
Many website operators invest in hosting plans with exceptional bandwidth capacities. They expect that their webpages will load quickly for customers. The problem is that customers often have bandwidth limitations on their end, which bottlenecks loading times.
This problem is especially common in Australia. Australia has one of the worst website loading times in the world. Customers there have worse Internet connections than people in most of Africa and other developing economies.
Webmasters must be realistic about the limitations on the client end of the connection. If they are serving lots of customers in Australia, rural parts of the country or other areas with poor website connections, then they might need to rethink their webpage optimization approach to ensure their pages load more quickly.
What steps should customers take to improve low times?
If you are trying to access a webpage that is not loading quickly, then you might need to take some steps to improve load times. Here are some things that you might need to try.
Clear your browser cache
You might have more trouble downloading images from a webpage while you have a full browser cache. You can try clearing it to get your page to load more quickly. You just need to take the steps:
Click the history tab in the history drop-down box in Google Chrome
Click clear browsing data in the left sidebar
Specify the time range in the drop-down box in the new browser window (The default setting is “last 24 hours” which is usually sufficient)
Make sure that “cached images in files” is selected in the checkbox (this is usually the default setting, so you shouldn’t have to change anything)
Click the “clear data” button
That should be enough to speed up your website loading times.
Tried to stop displaying images on the current webpage
In some circumstances, this is not going to be a practical option. You might need to see all visual elements on the webpage. However, if you are only interested in reading the text on the page, then you might want to try disabling images from downloading.
You can try using this chrome plug-in. It will keep webpages from displaying images, so you can increase webpage loading times by 250% or more.
The post Nuances of Bandwidth for Both Webmasters and Internet Users appeared first on pctechguide
0 notes
Text
Managing vCard Files for Effective Communication and Branding Optimization
vCard is a file format that is used for digital business cards. There are also vCard editors that allow you to create electronic business cards if you do not have one. This format is convenient because it can be attached to emails, can be sent as separate files or images, provided in messengers, etc. These files can also act as data interchange format personal digital assistants (PDAs), personal information managers (PIMs) and customer relationship management (CRMs). There are different variants of the file format, some of them are older, some are more recent.
vCards are one of the oldest forms of online media. The Internet Mail Consortium took over the management and oversight of them back in 1996, before the average American even had a dialup Internet connection.
Earlier versions of vCards had more limited functionality and lacked the aesthetics of their modern counterparts. They have evolved in recent years and play an important role in modern branding and organizational communications.
What are the Main Benefits of vCards?
Back when the average Internet user’s activities were limited to simple mail managers, vCards were shared with email addresses. They are now incorporated into a variety of other types of online media, as online technology has become more versatile.
The beauty of the vCard files is that they can actually be embedded as contacts on the web page, transferred into email contacts, or used otherwise without the necessity to rewrite the contact information from the business card into another database manually. One can easily import vCard to outlook and use the data as a contact list.
The vCard files can contain a bunch of info about the person who owns the business card. Since the data is digital, it can contain much more than a paper card. For example, you can find their name, address, date of birth, URL to calendar, electronic mail address, gender, photo and/or logo of the organization associated with the owner of the card, unit of the organization, last time the card was updated, profession, hobby, timezone, and still have space for other additional info.

As you can see, there is a ton of useful information about the person squeezed into one small digital file. There is no way in the world one could get the same amount of data from a paper card, and the beauty is that you do not have to copy the info manually to use it, you just click on the URLs or sections and you find out what you need. Implementing the same volume of info into the contact list allows you to keep the info about all your contacts in one place, having access to it in a convenient manner.
That is why it makes a lot of sense to use vCards as additional files in emails or texting threads in messengers, and also to import them to the email contacts. This will save lots of your time and efforts.

In addition to importing somebody else’s contacts to your mailing contacts, you can also make other people’s life easier by providing them with your own vCard business card. This will allow you both not to waste your time on double-asking about telephones, emails, or other data that can easily be added to the vCard file.
The last but not the least benefit of the vCard format is that you can actually import or export multiple contacts in one single file if you need to transfer or send them quickly. This type of format allows such manipulations.
How Can You Use vCards for Optimal Effectiveness?
There are a lot of benefits of using vCards. You need to know how they can be used and have a strategy in place. Design Shack has some very insightful ideas that you can try. They include:
Integrating the vCard into the background of your website
Adding digital animation to them
Linking all of your social media accounts
Incorporating responsive design elements to make your website have a better user experience across all devices
Optimizing the font of your brand name
There are plenty of brilliant ways to use vCards. Make sure that you do your due diligence and plan accordingly.
The post Managing vCard Files for Effective Communication and Branding Optimization appeared first on pctechguide
0 notes
Text
Eliminating Common WordPress Vulnerabilities to DDoS Attacks
Distributed Denial of Service (DDoS) attacks are serious threats that every website manager must be prepared for. Unfortunately, some of the most widely publicized DDoS attacks have created a number of misconceptions about the risks associated with them. In 2012, hactivist group Anonymous launched one of these attacks against the CIA website. These types of events have led the public to believe that only large organizations are targets by DDoS attacks.
Sadly, nothing could be further from the truth. There were over 2 million DDoS attacks last year alone. Word are certainly not immune to them either. WordPress websites are certainly not immune to them either. A 2014 report from Scuri showed that at least 162,000 WordPress website had been taken off-line by DDoS attacks. I have been unable to find more recent figure specific to WordPress websites, but this figure has almost certainly jumped in recent years, as DDoS attacks become more common and WordPress is more widely used.
This means that every WordPress website operator must take reasonable precautions against them. Here are some tips that WordPress users should take into consideration if they want to prevent their website from being taken off-line by a DDoS attack.
Choose your web hosting plan carefully
Choosing the right web hosting plan is one of the most important things that you can do as a WordPress website owner. You need to make sure that your hosting plan is scalable and has plenty of bandwidth. This will help you absorb a massive spike in web traffic that will occur when your site is being targeted by a DDoS attack.
You should look into using a cloud hosting provider. Cloud hosting companies tend to be a lot more scalable and you can usually get a lot more bandwidth for a fairly reasonable price. You can learn more about your cloud hosting options by reading reading up on WordPress hosting reviews.
You also need to look at your hosting providers track record for handling these types of attacks. Some hosting providers use machine learning capabilities to understand the red flags indicating that a hacker is launching a DDoS attack against one of their publishers. They can use artificial intelligence and automation to filter out that traffic to prevent any of the sites within their network from being taken down. Unfortunately, this technology is not versatile enough yet to be able to handle more sophisticated attacks. This means that webmasters must still take necessary precautions on their own end. Nevertheless, they can still minimize the threat of DDoS attacks by choosing a hosting provider that has a good track record for identifying and thwarting them.
Use a CDN
Content delivery networks (CDNs) are frequently used to improve user experience. They are especially useful for websites that reach people across different regions. They are able to match website visitors to the closest server in their region to ensure the content loads quickly and seamlessly.
As useful as CDNs are for enhancing their user experience, they are also useful for preventing DDoS attacks. One of the limitations of these attacks is that they send the vast majority of their web packets from the same point of origin. This means that WordPress webmasters can prevent one of these attacks by using a CDN like Akamai to reroute incoming traffic from a DDoS attacker to another server.
Use plugins specifically designed to stop these attacks
There are a number of WordPress security plugins that you should look into. One of the most important is the Cloudflare plugin. This plugin is specifically designed to optimize the functionality of WordPress websites and bolster security. It has a number of features that are useful for preventing DDoS attacks.
Some WordPress plugins are designed for the sole purpose of stopping these types of attacks. The Protection against DDoS plugin is one of the most highly rated. It has been downloaded over 4,000 times since it was first published a year ago. This plugin has received a five-star rating so far. Although it hasn’t been reviewed by many customers yet, this is likely to change as it gets more traction and downloads.
The post Eliminating Common WordPress Vulnerabilities to DDoS Attacks appeared first on pctechguide
0 notes
Text
Securing Your Privacy Against Deep Packet Inspections
Network administrators, cybersecurity analysts and watchdogs use a variety of different tools to monitor Internet traffic. Deep packet inspection is one of the types of tools that has proven to be highly effective over the past few years. However, this type of technology has also raised some very valid concerns about digital privacy.
Consumers must understand the risks that deep packet inspection poses to their privacy and take reasonable steps to safeguard it. They should begin by understanding the technology behind deep packet inspections and take appropriate steps. Here is a brief overview.
What are deep packet inspections?
In the past, firewalls and other network security technology had limited analytical capabilities. When they were trying to filter, inspect or redirect traffic, they were restricted to evaluating the packet headers.
Packet inspection technology has evolved over the past decade. Modern firewalls are able to inspect large blocks of code in packets to get more detailed understandings of the web traffic accessing their networks. Watchdogs, ISPs and other organizations can use the same technology to monitor Internet users within their regions as well.
Deep packet inspections give these administrators much more nuanced insights into the behavior of these users. Unfortunately, as this methodology becomes more widely used, consumer privacy is going to be at risk.
Deep packet inspection poses a very serious threat to consumer privacy
The Electronic Privacy Information Center (EPIC) has highlighted a number of concerns about the packet inspection. They stated that online privacy laws are inadequate measures for ensuring customer privacy. Also, existing laws governing the use of deep packet inspections are routinely broken. According to one finding they published last year, government officials at the European Union regularly violated privacy laws restricting the application of deep packet inspections. Although courts found these officials derelict in their responsibilities to shield consumer privacy, there is a little indication that they are going to change their behavior.
The EPIC also stated that deep packet inspections have curtailed privacy rights in the United States as well. This has led customers to take new steps, such as using a VPN for Windows for extra security. Their sentiment is shared by a security expert that published a post with the Institute for Advanced Studies.
“This sounds benign, but in reality, it is a huge invasion in privacy. This means that they now have access to your credit card and bank account information, your health records and the funny picture of your dog you just privately shared with your significant other. And they did it without telling you that they were going to do it. As a user, this upsets me. As a security professional, setting up one of these systems might lead to the erosion of trust with my users. We have been saying for years that the major problem with computer security isn’t the computers, it’s the lack of knowledge of the human operating the computer.”
How can Internet users protect their privacy from deep packet inspections?
As deep packet inspection technology becomes more widely used, consumers are going to need to look for new ways to protect their online privacy. They could consider using a VPN.
VPNs are able to encrypt web packets to ensure ISPs, publishers and watchdogs are unable to see sensitive details with deep packet inspection. Most ISPs have the technology to block VPNs if they wanted, but they rarely take these measures. They recognize that consumers are becoming more interested in protecting their privacy and are unlikely to take such draconian steps, otherwise they would risk losing a lot of users. Publishers can’t take the steps as easily. Public officials have less control over them than ISPs.
There are other steps that you can take to safeguard your privacy, including using different devices to connect to various publishers. However, VPNs remain the single best option available in 2019.
The post Securing Your Privacy Against Deep Packet Inspections appeared first on pctechguide
0 notes
Text
Identifying and Protecting Against the Most Dangerous Keyloggers
Keyloggers are among the most frightening tools in the hands of a skilled hacker. They are malicious devices or malware applications that enable hackers to capture every keystroke that you type.
Most Dangerous Keyloggers
You need to be aware of the different types of keyloggers and know how to protect against them. Here are some of the most common keyloggers infecting the Internet and some tips to recognize and guard against them.
Spyrix
This is one of the most dangerous keyloggers that hackers used to exploit their victims. One of the scariest things about it is that the application is undetectable to most antivirus applications. The keylogger can be accessed by any device with a modern web browser, which means that hackers can use it from across the world.
Best free keylogger
This keylogger uses sophisticated machine learning capabilities to decipher text that users type. Most other keyloggers are only useful for capturing passwords and financial data, because the hacker can use a search function to identify the point that the user typed in the login address. This one gives them much deeper insights into your behavior by being able to decipher the meaning behind text that would otherwise be harder to read.
Wolfeye keylogger
This keylogger was so sophisticated, that it actually received a German award for innovation. It is frequently used by hackers to spy on their target social media activity.
Hardware keyloggers
Hardware keyloggers are another common threat that you need to be aware of. They are installed in the back of a computer or other device. If you don’t notice them physically, then they are virtually invisible if you are trying to look through your system directory for traces of malicious software.
How can you identify and protect against keyloggers?
Keyloggers are very difficult to protect against if you don’t know what to look for. A team of IST computer security division experts have been studying these malicious devices for the past 26 years. Here are some lessons that they have shared.
Require applications to be whitelisted
Software based keyloggers are rarely installed manually by the hacker. The hacker usually dupes their target into downloading them through sophisticated social engineering strategies. The application is usually installed by tricking the user into thinking that it is a common file that they work with every day, such as a Microsoft Word document.
You will be able to minimize the risk of downloading a keylogger by requiring all applications to be whitelisted first. This will mean that applications won’t be installed without your permission.
Regularly inspect your registry
Many malicious programs are designed to be undetectable to malware protection technology. This means that you need to carefully review your registry to identify them. It is a good idea to inspect your registry at least once every other week.
You will obviously notice a lot of different types of programs when you are looking at your rootkit. You should go to explorer.exe and click on the “Threads” tab to see a list of known programs. Each program will have its own TID. If you can’t determine the purpose of a program, then it is a good idea to stop it from running. You should always Google the name of the application to find out. Some of them will easily be identifiable as malware.
Use the most recent malware protection software
Some malware protection applications are not equipped to handle recent types of malware. You are going to need to make sure that you use the latest protection. Here are some things to assess before choosing a malware protection tool to guard against keyloggers:
Make sure that they offer real-time protection. Many people were nearly duped into downloading a keylogger by a hacker impersonating someone that they had legitimate business with, because the keylogger was disguised as another application. The only reason the keylogger was discovered was that the user had real-time protection from their malware protection technology, which identified it and prevented it from being installed.
The software needs to use the latest libraries. Otherwise, it might not have the recent keyloggers in its database, which means that they might not be detectable.
Even the most sophisticated malware protection tools aren’t guaranteed to stop keyloggers. However, the odds are much better than if you used an outdated application.
The post Identifying and Protecting Against the Most Dangerous Keyloggers appeared first on pctechguide
0 notes
Text
Speed Optimization Basics with Windows System Configuration
Slow computers are a bigger concern than we previously thought. One new study found that the average American wastes two hours every week, simply because their computer is running too slow. That means that 1.2% of our lives are being wasted because we aren’t optimizing our PCs to run faster.
One of the biggest reasons that our computers run slower than we would like is that we are running too many programs. You could increase system speed dramatically by terminating many programs that you don’t need.
Microsoft System Configuration is a feature in Microsoft Windows that lets you pause programs that are consuming too much memory. However, it is important to make sure that you don’t terminate the wrong programs. You could seriously impede the performance of your PC or lose some of the functionality you are depending on.
Here is a quick guide on using Microsoft System Configuration to make sure your computer runs more quickly.
How do you access Windows System Configuration?
Invoking Windows System Configuration is a simple three step process:
Start by clicking the Start button.
Type the command “misconfig” and then click the OK button. A window called System Configuration Utility will subsequently appear.
Click the tab that says Startup.
Once you complete the steps, you will see a list of all programs that are currently running. Each program has a checkbox next to it. If the icon has a check, then that means that the program is scheduled to start when Windows launches. Otherwise, the program needs to be manually started.
There are a few things that you need to bear in mind when assigning settings. First, start by familiarizing yourself with the following processes:
Explorer.exe. This process controls the graphical shell for the Windows environment. Many people will tell you that Windows will stop functioning if it is closed. This is a hyperbolic assessment, but explorer.exe still has some very important functions. It controls many graphical interfaces that most users depend on, including the Task Manager, startup menu and file managers. You can still technically run Windows without it, but it will be a lot more complicated.
Winlogon.exe. This is a process that operates in the background of Windows. It is central to authorizing users and performing activation checks on Windows processes. Disabling this process is highly discouraged, especially in a multi-user Windows environment.
Spoolsv.exe. This process controls printing and faxing jobs. If you don’t intend to print or fax from your PC, then you can probably close it without any issues. You can always consider launching it again. However, if you operate in environment where users with limited technical knowledge need to be able to print documents at their leisure, then it is not advisable to remove the checkmark on this box.
Lsass.exe. This is another process that is essential for user authentication. It verifies the identity of users liking onto your PC. Terminating this program is not advisable, even if you don’t intend to allow anybody else to use your computer.
The applications listed above are some of the more important programs that you should be careful about closing. However, most nonessential programs can probably be unchecked under the System Configuration.
You probably don’t need to use Microsoft Word as soon as it starts up. Yet, many users unknowingly have Word or other Office programs set to launch during startup. If you notice that the box next to it is checked under System Configuration, then it will constantly be draining memory from your computer. You can also uncheck any applications that you manually installed, unless you have a good reason for making sure they operate as soon as your system starts up. It is always a good idea to keep your malware protection software running at all times, so you should probably make sure that the button next to it is checked in your System Configuration dashboard.
See how much memory different programs are using before deciding to keep them
You might believe that you really need a particular program running at all times. However, aside from essential Windows processes or malware protection software, most applications are not as necessary as we think. We usually just rationalize keeping them running in the background so that we don’t have to manually start them multiple times during a Windows session.
If you are tempted to keep a process running, it is a good idea to look at your task and see how much memory it is using.
The post Speed Optimization Basics with Windows System Configuration appeared first on pctechguide
0 notes
Text
Excel Shortcuts for More Complicated Commands
We previously wrote an article on the benefits of using keyboard shortcuts in Excel. The shortcuts we focused on were used for simple formatting options. However, there are other shortcuts that are valuable for more complicated challenges. You can read more about them below.
Display Format Cells box while keeping the Fonts Tab active
Navigating the formatting process in Excel can be exceedingly tedious at times. One of the challenges that you will face is trying to apply multiple formatting commands at one time. When you try calling the format cells box, it often closes the fonts tab. This can be a painstaking process, because you will need to keep switching between the two windows.
There is a simple keyboard shortcut that enables you to keep both windows open simultaneously. All you need to do is press:
Ctrl + Shift + f
This command enables you to keep both of them open at once, which makes editing much easier.
Change the font size
This is another feature in Excel that is not too difficult to use, but still takes more time than the other standard formatting commands. The font size drop-down icon is easily accessible from the main menu. However, there are going to be times when you want to use a keyboard shortcut instead of having to move your mouse to the drop-down.
You can simply click the tab three times. You will then be able to easily change the font size by pressing the appropriate numerical characters from your keyboard.
Adding borders to your cells
Are you trying to add borders to the outside of your cells? There are some easy to use keyboard shortcuts that make it a lot easier. This is one of the more convenient shortcuts, because finding the appropriate icons in your main menu can be a huge hassle if you don’t know what to look for.
The shortcuts that you need to use are going to depend on whether you are using a PC or a Mac. If you are using a PC, then you will need to press either Alt + H or Alt + B. Both commands will have the same effect.
What if you have a Mac? Then you will need to press the following: COMMAND + Option + 0.
You will be able to easily add borders to the outside of your cell by pressing these buttons.
Insert a table
Inserting a table into Microsoft Excel is going to be one of the most annoying processes. You can cut the amount of time that it takes you in half by using a handy keyboard shortcut.
This is another keyboard shortcut that is going to depend on the machine that you are using.
If you are using a PC, then you are going to need to press:
Ctrl+T
MAC users will need to use the following command instead:
^T
There is no reason to make the process of creating tables more difficult than it needs to be. You might as well take advantage of these keyboard shortcuts.
Select an entire row to modify
Most commands in Excel are used to make changes to single cells. However, there are going to be times when you need to edit an entire row instead. You could do this by clicking the number corresponding to that row in the far left of your Excel application window. However, if you already have your cursor in a cell within the row that you intend to edit, then you can use a simple keyboard shortcut to edit it instead.
What is the keyboard shortcut if you have a PC? It is:
Shift+Space
But what if you are using a Mac instead? Then you will need to press the following:
?+Space
Select an entire column to edit
You can also choose to edit an entire column at one time. If you are using a PC, then you can select a column by pressing:
Ctrl + Space
The keyboard shortcut if you are using a Mac is:
?+Space
Just make sure that your cursor is in the cell within the column that you would like to edit first.
The post Excel Shortcuts for More Complicated Commands appeared first on pctechguide
0 notes
Text
Convenient Excel Shortcuts for Quick Formatting
The first version of Microsoft Excel was launched in 1985. The world’s most popular spreadsheeting software has evolved significantly over the past 35 years. Earlier versions of Microsoft Excel were not very user-friendly. New keyboard shortcuts have been introduced over the past few versions, which make the application much easier to use.
We found that a lot of people aren’t familiar with the different Excel shortcuts that are available. We put together a guide on some of the most helpful shortcuts. Afterwards, we realized that it was a lot longer than we expected, so we decided to break it up into two parts. The first part will focus on the benefits of using some of the more common and simpler shortcuts that will help you save time on formatting. Although these shortcuts may not seem like they will save a huge amount of time when they need to be invoked, they will be needed a lot more frequently. The 0.5 seconds that you will save by bolding or underlining a cell with a shortcut command will add up significantly once you realize that you need to use them so often.
The next post is going to cover less common keyboard shortcuts for more complicated issues. You will find that these shortcuts may not be needed as often, but they can really eliminate a lot of frustrations when you do. Adding tables and making multiple formatting changes at once is going to be enough of a challenge as it is, so you might as well know what keyboard shortcuts can make your life easier.
Here are some of the simpler shortcuts that you should be aware of if you are using Microsoft Excel.
Format cells dialog
The default numerical formatting for cells doesn’t include any decimals or special characters, such as currency signs. If you want to change the formatting, then you will need to invoke the Format Dialog box.
If you don’t want to have to scroll through all of your menus to find the Format Dialog box, then you can simply use the Ctrl + 1 shortcut instead.
Apply or remove bold
Adding bold to your text isn’t as common in Excel as it is in Microsoft Word or many other applications. However, there are still plenty of instances when it is necessary to bold a specific cell.
A keyboard shortcut might not be as big of a timesaver with this function as many others, because the bold button is easily visible from the main menu. Nevertheless, you can still save time by using one of the following keyboard shortcuts:
Ctrl + b
Ctrl + 2
Either of these shortcuts will have the same effect.
Apply or remove italic
Adding and removing italic text is also occasionally necessary when you are using Excel. You can accomplish this with either of the following keyboard shortcuts:
Ctrl + i
Ctrl + 3
Apply or remove underline
You will probably need to underline cells more often then you will need to bold or italicize them. Therefore, a keyboard shortcut to underline cells in your Excel document could save you a lot of time. Either of the following shortcuts will accomplish this for you:
Ctrl + u
Ctrl + 4
Add or remove strikethrough
Adding or removing a strikethrough will occasionally be necessary. Although this feature may not be as commonly used, it can be a serious hassle when you do need to use it. The problem is that it can be hard to find the strikethrough button on the main menu, especially if you don’t know what to look for. Don’t worry – there is a keyboard shortcut that makes things a lot easier. You can simply hit Ctrl + 5.
Ctrl + Shift + F
This command will be easier to remember than using the command from your Home menu.
Familiarize yourself with different Excel shortcuts to save time
Creating, editing and formatting Excel documents can be a massive time sink. The good news is that there is a plethora of keyboard shortcuts that make it easy to call the commands that you need to accomplish the necessary tasks. Take some time to learn them. This will save you countless hours over the course of a month.
The post Convenient Excel Shortcuts for Quick Formatting appeared first on pctechguide
0 notes