Don't wanna be here? Send us removal request.
Photo
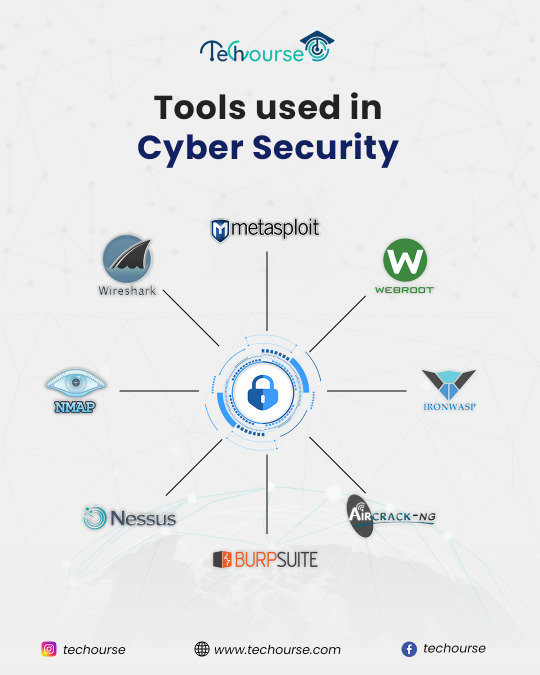
Here is the list of best tools used in Cyber Security. Choose the right tool from this list and protect you business from Cyber Threats. Get more insights only at Techourse.
3 notes
·
View notes
Photo

With many of us actively using Social Media, it makes a perfect target platform for scams. Here are some most effective Social Media Safety tips you need to know. To know more learn from the best cyber security course provider Techourse.
0 notes
Photo

Malware can be used in various ways like to steal data, passwords, financial information, or company trade secrets. Learn more about the major types of malware and how we can protect ourselves from them. For more information get in touch with Techourse.
0 notes
Photo

Programming languages are essential for ethical hacking. Learn the top 12 programming languages for ethical hacking, for the rising security issues in 2022.
0 notes
Photo

Here is a quick checklist to help you understand the Stages of Penetration testing. Techourse helps you learn pen testing and offers the best penetration testing certification online.
0 notes
Photo

Are you searching for the best course to learn python? Techourse is the right e-learning space for you. Get continuous python training by top industry experts and soar high with certifications. https://www.techourse.com/
0 notes
Photo

Did you know there are more than 1.8 million unfilled cyber security vacancies in India? Well, Recruiters are actively looking for highly trained certified cyber security experts to fill those positions. Check out the most in-demand cyber security courses in 2022.
https://www.techourse.com/
0 notes
Link
Choosing a career in cyber security requires soft skills and strong technical background. Read this comprehensive guide that tells you everything from scratch.
0 notes
Text
Benefits of Pursuing Ethical Hacking Course

In 2018 Beta News, a popular tech news website published an article as to how Ethical Hacking is the best Cyber Security measure a company can engage. Certified Ethical Hacking is a black hat hacking technique which can be acquired by IT Professionals to address, prevent and respond to cyber security threats.
There are various types of computer Viruses, Malware, Trojans and Ransomware which cause severe damage on the day to day operations of organizations. A CEH professional has the means and knowledge to them to detect vulnerabilities in the systems and analyze the cyber security measures in an organization’s security architecture.
What does the course involve?
This course is a testament of ethical hacking skills required for penetration testing which involves:
Combating challenges in real time combat hacking challenges.
Thinking like a hacker by learning modern malware tactics.
Learning tips and tricks of hacking using hacking tools.
Becoming proficient with the emerging attack vectors.
Aspects involved in Ethical Hacking Course:
Understanding the cybercriminal mindset: To understand a hacker, it is very important to think like him which can be a challenge as a cyber-hacker is constantly innovating himself. Ethical Hacking Course provides training in identifying, triaging and foreseeing potential threats and how best to prevent them. Untrained network defenders are at severe disadvantage compared to the hackers. A hacker can identify a single vulnerability and exploit it. But only a trained ethical hacker can defend network’s internal and perimeter security. The course trains a defender to weigh the probability of exploitation and to assign resources to repel an attack.
Versatile practical knowledge: This course offers an ideal baseline not just for penetration testing, but also to gain in-depth knowledge of practical network security. The course will equip the defender to advice businesses on various security measures to prevent hacking. Practical knowledge regarding the weakness in the cyber system can prevent possible penetration which can result in loss of essential data and sensitive information.
Booming hacking business: Hackers are making a lot of money these days and ethical hacking career is experiencing a boom as well. The need for trained security professional has tremendously risen which is almost 500,000 in the past few years. There are so many businesses under the threat of cyber-attack, the demand exceeded the supply. Although ethical hackers are not only employed by IT firms but also other industries such as Airlines, Fintech and government agencies as well. The ethical hacking jobs include network security administrators, security executives and web security managers which are highly lucrative. Certified in Ethical hacking course assures of having a high pay scale and never being unemployed.
Career growth: The global cyber security skills deficit reaches 1.5 million, and those with ethical hacking skills are considered to be a very valuable commodity. Cyber security is now the top of the C-suite resulting in a demand for ethical hackers and penetration testers. Security knowledge of penetration testers is highly valued by organizations because of the risks involved in a security vulnerability passing undetected. Facebook awarded a bug bounty £32,000 to ethical hacker Andrew for reporting a critical vulnerability in the company’s servers. He identified a remote code execution flaw in ImageMagick which is an open-source software tool used by Facebook.
High salary slab: The demand for cyber security is also reflected in salary. The average salary climbing is 5% every quarter. The average for an ethical hacker is around £40,000 and £60,000 for a senior penetration tester. A CEH salary is nearly 44% more than the regular IT analyst. Businesses are willing to shell out more and hire a security analyst then have a hacker exploit their IT infrastructure and suffer losses from the downtime due to hacking.
Assuring software development standards: When software is developed, it needs to be thoroughly tested before it can be deployed. This includes security testing, where new software is tested if it is prone or vulnerable to security threats and attacks. CEH can train the IT personnel and the software developmental team to perform software testing during the developmental stage. This way CEH can assure quality software which complies with assurance standards.
Curriculum of a CEH Training Program
Techourse’s Certified Ethical Hacking Training Program aims in providing foundation and also building a robust career for IT security professional. It offers a wide range of certified ethical hacking courses at affordable cost. The following skills can be mastered in the CEH course:
Knowledge of latest exploits in technologies
Training to combat emerging attack vectors
Experience of hands on hacking challenges.
Live cyber range in real time and not just simulations.
Focus on enhanced malware analysis
Lessons on usage of tools and tricks in hacking such as NMAP, Angry Scanner, John the Ripper, Wireshark and many more.
In conclusion, Certified Ethical Hacking course can be beneficial to all IT professional who wish to get into security or tech career. Not only will this course provide knowledge about an industry that is very stimulating and rewarding, but it is also handsomely rewarding. This course is a match made in heaven for people who seek a thrilling exciting job. The ample job availability in this sector ensures that an EH will never be strained for income or opportunity.
#Certified Ethical Hacking#Ethical Hacking Training Course#Ethical Hacking Course Program#How to Become a Hacker#Penetration Testing
0 notes
Link
The cyber security training program has gained worldwide popularity and is one of the most in-demand skills every passionate learner should possess today. Techourse has introduced an enormous list of online courses and specialized Corporate Training Program for IT professionals with the main focus on honing core technical skills through real-time project training.
#cybersecurity#cybersecuritytrainingprogram#onlinecourse#onlinecertifications#ethicalhacking#OnlineEthicalHacking
1 note
·
View note