#where are the tech savvy people who a) help out apple users when the company doesn't care and b) aren't scammers
Explore tagged Tumblr posts
Text
if anyone knows how to bypass/remove a firmware password from a macbook that is now completely locked, please let me know
apple won't be any help to me but someone must know what they do to remove it
don't even care if i have to wipe my laptop entirely, i just cannot get into it at this point
#always backup your files kids! i haven't since before christmas but even so i've got most of it saved#where are the tech savvy people who a) help out apple users when the company doesn't care and b) aren't scammers
12 notes
·
View notes
Text
Warning: This is not an endorsement or encouragement for you to start behaving in illegal or immoral behaviour. I am not held responsible for any trouble you decide to get into; or what you do I encourage people to use my information I post in a responsible way and not violate any state or federal laws
History Of The Dark Web
The Deep Web and it’s Dark Web brother have been in the public eye more than usual in the past few years. Once the things that happen on the hidden part began having an impact on the day to day and safety of our lives, ordinary people started to take an interest. That doesn’t mean the hidden part of the internet is a recent development. It’s just about as old as the internet itself!
Now days tho it is dangerous if you are less then tech savvy and it could turn deadly for a new person stumbling onto the dark side of the internet where things like killers for hire, Drugs, Guns, Fake Money, and even Identities and people can be bought! You can only guess what can happen if you stumble onto one of these sites without knowing and ask the wrong questions!
1980
The history of the hidden web is almost as old as the history of the internet itself. Obviously, the same technology that made the internet and the web possible, also makes the Dark Web possible thanks to its architecture and designs. Which is why it is fair to pin the start of the Dark Web to ARPANET. Which is the direct precursor to the internet of today? While ARPANET may not have had a Dark Web as we know it now from the start, it wouldn’t take long before people started to make use of this technology for things they wanted to keep a secret. It turns out that the first ever online sale happened in the early 70s and was in fact cannabis. Students at Stanford sold weed to students at MIT, using ARPANET. Remember that at this point most people didn’t have personal computers, much less home internet access.
In the 1980s, access to the internet for normal citizens is still a dream. This was the decade when everything needed for a worldwide web would fall into place. In the early 80s, the TCP/IP standard is solidified. By the mid- 80s personal computers and modems are, if not affordable, at least available for anyone to buy. Internet pioneers also invented the domain name system we use to resolve website names during this decade.
Data havens emerge as an idea at this time as well. Since the world was going global, worries about where data should be stored came to the fore. Storing your data in a haven meant sending it out of the country to a territory that had better legal protection against government spying. At the extreme, data havens would be in no country at all. They would be built on structures or vessels out in international waters . A similar idea to seasteading. Actual data havens in the 80s popped up in the Caribbean islands.(Or as it turns out and which is slowly starting to be developed the Decentralized web run off the BlockChain and which has the potential to be way more secure then the darkweb)
1990's
The 1990s are without a doubt the time when the World Wide Web went mainstream. Thanks to web technologies like HTTP and FTP along with graphical computers capable of running a web browser, there was a sudden mainstream appeal to this whole internet thing.
Towards the end of the 1990s, there was a real leap in the technologies that allowed large amounts of data, such as multimedia, to be shared online. MP3 technology in particular lead to a massive shakeup of the music industry. Thanks to like the likes of Napster, people could perform illegal peer-to-peer exchanges of ripped and compressed music. This caused a complete meltdown among musicians and music executives. Lars Ulrich famously sued Napster which was really symbolic of the battle between old and new school. Today the music industry has adapted and streaming subscriptions are the norm. Without Dark Web alike peer-to-peer exchanges it’s doubtful we’d have the consumer-friendly online media world of today.
2000
The Dark Web proper really got its start in March of 2000 with the release of Freenet. The service still exists today and provides a censorship-resistant way to use the web. It is a true implementation of the Dark Web and provided a way for plenty of illegal information to pass around. This included illegal pornographic material and pirated content. Of course, actually exchanging money anonymously is still incredibly hard at this point, since you have to use cash. So Freenet doesn’t lead to any black market activity to any significant degree.
A data haven called HavenCo was established in Sealand (a seasteading micronation) which promised to store sensitive information in a place where no government could stick its nose. It seemed like a Dark Web dream, but by the early 2010s HavenCo was dead.
The most important Dark Web development of all time happened in 2002, with the release of TOR or The Onion Router. It was created by non-other than the US government, as a way to help their own operatives remain untraceable. It’s no exaggeration to say that the Dark Web of today could not exist without this technology.
Late in the 2000s came the advent of cryptocurrency in the form of Bitcoin. The final piece of the puzzle needed to make the Dark Web really click.
The Early 2010's
The 2010s represent the era where cryptocurrency and TOR met to create the first proper black markets. The pioneer was the Silk Road, which is now long defunct. Despite taking all the important figures out behind the Silk Road, it has seemingly done little to stop the trade of drugs and other illegal goods and services over the Dark Web.
This is the era in which the Dark Web becomes a topic of public concern, rather than just something discussed as cyber security conferences. Many mainstream articles emerge that explain the difference between the massive Deep Web and the relatively tiny Dark Web.
It becomes especially scary when it emerges that terrorists are using the Dark Web to communicate and coordinate. Ironic, given what the US created TOR for originally. Research published showing that the Dark Web is mainly being used to commit crimes.
Today
The Dark Web of today is reportedly in decline. Despite this, there is an incredible variety of hidden services and significant information exchange happening out of sight of the mainstream web. It doesn’t really matter that the Dark Web is relatively small compared to the surface web as a whole. Its impact is disproportionately large. Small groups of hackers collaborating on the Dark Web can bring a multi-billion Dollar internet company to its knees. Hackers end up impacting millions of users.
Darknet black markets are also thriving and putting both traditional and new synthetic drugs into the hands of anyone who wants them. Cryptocurrency has been the biggest factor in this maturation of the Dark Web.
Now you know the basic history of the dark web,. now lets get into the history of the newer technologies that help run the dark web and keep it secure technologies like TOR and the Cryptocurrencies that helps collect payment from the goods that are sold on the dark web.
History Of Tor
Tor is based on the principle of ‘onion routing’ which was developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The alpha version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. It was launched on September 20, 2002. Further development was carried under the financial roof of the Electronic Frontier Foundation (EFF).
The Tor Project Inc. is a non-profit organization that currently maintains Tor and is responsible for its development. The United States Government mainly funds it, and further aid is provided by Swedish Government and different NGOs & individual sponsors.
The U.S. National Security Agency (NSA) has called Tor “the King of high secure, low latency Internet anonymity.” And similar comments by BusinessWeek magazine, “perhaps the most effective means of defeating the online surveillance efforts of intelligence agencies around the world”.
Another speculation made is that Tor takes its funding from the U.S. Government which may lead to the assumption that NSA may have compromised the identities of individual Tor users. However, the executive director Andrew Lewman has disclaimed any confederations with NSA.
How it works
Tor works on the concept of ‘onion routing’ method in which the user data is first encrypted and then transferred through different relays present in the Tor network, thus creating a multi-layered encryption (layers like an onion), thereby keeping the identity of the user safe.
One encryption layer is decrypted at each successive Tor relay, and the remaining data is forwarded to any random relay until it reaches its destination server. For the destination server, the last Tor node/exit relay appears as the origin of the data. It is thus tough to trace the identity of the user or the server by any surveillance system acting in the mid-way.
Other than providing anonymity to standalone users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Also, P2P applications like BitTorrent can be configured to use the Tor network and download torrent files.
Is It Safe
Various claims have been made to compromise Tor’s anonymity and security from time to time. The most famous one was the Bad Apple Attack in which the researchers claimed to have identified around 10k IP addresses of active BitTorrent users who were connected via Tor.
The Heartbleed bug was behind another major compromise in April 2014 which halted the Tor network for several days.
Traffic Fingerprinting is a method used to analyze web traffic by analyzing the patterns, responses, and packets in a particular direction. This technique can be used to attack the Tor network by making the attacker’s computer act as the guard. The main vulnerability was found at its exit points where the level of security is very low as compared to the rest of the Tor network.
The History of cryptocurrencies
In 1983, the American cryptographer David Chaum conceived an anonymous cryptographic electronic money called ecash. Later, in 1995, he implemented it through Digicash, an early form of cryptographic electronic payments which required user software in order to withdraw notes from a bank and designate specific encrypted keys before it can be sent to a recipient. This allowed the digital currency to be untraceable by the issuing bank, the government, or any third party.
In 1996, the NSA published a paper entitled How to Make a Mint: the Cryptography of Anonymous Electronic Cash, describing a Cryptocurrency system first publishing it in a MIT mailing list and later in 1997, in The American Law Review (Vol. 46, Issue 4).
In 1998, Wei Dai published a description of "b-money", characterized as an anonymous, distributed electronic cash system. Shortly thereafter, Nick Szabo described bit gold. Like bitcoin and other cryptocurrencies that would follow it, bit gold (not to be confused with the later gold-based exchange, BitGold) was described as an electronic currency system which required users to complete a proof of work function with solutions being cryptographically put together and published. A currency system based on a reusable proof of work was later created by Hal Finney who followed the work of Dai and Szabo.
The first decentralized cryptocurrency, bitcoin, was created in 2009 by pseudonymous developer Satoshi Nakamoto. It used SHA-256, a cryptographic hash function, as its proof-of-work scheme. In April 2011, Namecoin was created as an attempt at forming a decentralized DNS, which would make internet censorship very difficult. Soon after, in October 2011, Litecoin was released. It was the first successful cryptocurrency to use scrypt as its hash function instead of SHA-256. Another notable cryptocurrency, Peercoin was the first to use a proof-of-work/proof-of-stake hybrid.
On 6 August 2014, the UK announced its Treasury had been commissioned to do a study of cryptocurrencies, and what role, if any, they can play in the UK economy. The study was also to report on whether regulation should be considered.
Definition
According to Jan Lansky, a cryptocurrency is a system that meets six conditions:
The system does not require a central authority, its state is maintained through distributed consensus.The system keeps an overview of cryptocurrency units and their ownership.The system defines whether new cryptocurrency units can be created. If new cryptocurrency units can be created, the system defines the circumstances of their origin and how to determine the ownership of these new units.Ownership of cryptocurrency units can be proved exclusively cryptographically.The system allows transactions to be performed in which ownership of the cryptographic units is changed. A transaction statement can only be issued by an entity proving the current ownership of these units.If two different instructions for changing the ownership of the same cryptographic units are simultaneously entered, the system performs at most one of them.
In March 2018, the word cryptocurrency was added to the Merriam-Webster Dictionary
What is Blockchain
A blockchain, originally block chain, is a growing list of records, called blocks, that are linked using cryptography.[1][6] Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree).
By design, a blockchain is resistant to modification of the data. It is "an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way". For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for inter-node communication and validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without alteration of all subsequent blocks, which requires consensus of the network majority. Although blockchain records are not unalterable, blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance. Decentralized consensus has therefore been claimed with a blockchain.
Blockchain was invented by a person (or group of people) using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the cryptocurrency bitcoin. The identity of Satoshi Nakamoto is unknown. The invention of the blockchain for bitcoin made it the first digital currency to solve the double-spending problem without the need of a trusted authority or central server. The bitcoin design has inspired other applications, and blockchains that are readable by the public are widely used by cryptocurrencies. Blockchain is considered a type of payment rail. Private blockchains have been proposed for business use. Sources such as Computerworld called the marketing of such blockchains without a proper security model "snake oil".
Structure
A blockchain is a decentralized, distributed and public digital ledger that is used to record transactions across many computers so that any involved record cannot be altered retroactively, without the alteration of all subsequent blocks. This allows the participants to verify and audit transactions independently and relatively inexpensively. A blockchain database is managed autonomously using a peer-to-peer network and a distributed timestamping server. They are authenticated by mass collaboration powered by collective self-interests. Such a design facilitates robust workflow where participants' uncertainty regarding data security is marginal. The use of a blockchain removes the characteristic of infinite reproducibility from a digital asset. It confirms that each unit of value was transferred only once, solving the long-standing problem of double spending. A blockchain has been described as a value-exchange protocol. A blockchain can maintain title rights because, when properly set up to detail the exchange agreement, it provides a record that compels offer and acceptance.
Blocks
Blocks hold batches of valid transactions that are hashed and encoded into a Merkle tree. Each block includes the cryptographic hash of the prior block in the blockchain, linking the two. The linked blocks form a chain. This iterative process confirms the integrity of the previous block, all the way back to the original genesis block.
Sometimes separate blocks can be produced concurrently, creating a temporary fork. In addition to a secure hash-based history, any blockchain has a specified algorithm for scoring different versions of the history so that one with a higher value can be selected over others. Blocks not selected for inclusion in the chain are called orphan blocks. Peers supporting the database have different versions of the history from time to time. They keep only the highest-scoring version of the database known to them. Whenever a peer receives a higher-scoring version (usually the old version with a single new block added) they extend or overwrite their own database and retransmit the improvement to their peers. There is never an absolute guarantee that any particular entry will remain in the best version of the history forever. Blockchains are typically built to add the score of new blocks onto old blocks and are given incentives to extend with new blocks rather than overwrite old blocks. Therefore, the probability of an entry becoming superseded decreases exponentially as more blocks are built on top of it, eventually becoming very low. For example, bitcoin uses a proof-of-work system, where the chain with the most cumulative proof-of-work is considered the valid one by the network. There are a number of methods that can be used to demonstrate a sufficient level of computation. Within a blockchain the computation is carried out redundantly rather than in the traditional segregated and parallel manner.
Block time
The block time is the average time it takes for the network to generate one extra block in the blockchain. Some blockchains create a new block as frequently as every five seconds. By the time of block completion, the included data becomes verifiable. In cryptocurrency, this is practically when the transaction takes place, so a shorter block time means faster transactions. The block time for Ethereum is set to between 14 and 15 seconds, while for bitcoin it is 10 minutes.
Hard forks
A hard fork is a rule change such that the software validating according to the old rules will see the blocks produced according to the new rules as invalid. In case of a hard fork, all nodes meant to work in accordance with the new rules need to upgrade their software.
If one group of nodes continues to use the old software while the other nodes use the new software, a split can occur. For example, Ethereum has hard-forked to "make whole" the investors in The DAO, which had been hacked by exploiting a vulnerability in its code. In this case, the fork resulted in a split creating Ethereum and Ethereum Classic chains. In 2014 the Nxt community was asked to consider a hard fork that would have led to a rollback of the blockchain records to mitigate the effects of a theft of 50 million NXT from a major cryptocurrency exchange. The hard fork proposal was rejected, and some of the funds were recovered after negotiations and ransom payment. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March 2013
Decentralization
By storing data across its peer-to-peer network, the blockchain eliminates a number of risks that come with data being held centrally. The decentralized blockchain may use ad-hoc message passing and distributed networking.
Peer-to-peer blockchain networks lack centralized points of vulnerability that computer crackers can exploit; likewise, it has no central point of failure. Blockchain security methods include the use of public-key cryptography. A public key (a long, random-looking string of numbers) is an address on the blockchain. Value tokens sent across the network are recorded as belonging to that address. A private key is like a password that gives its owner access to their digital assets or the means to otherwise interact with the various capabilities that blockchains now support. Data stored on the blockchain is generally considered incorruptible.
Every node in a decentralized system has a copy of the blockchain. Data quality is maintained by massive database replication and computational trust. No centralized "official" copy exists and no user is "trusted" more than any other. Transactions are broadcast to the network using software. Messages are delivered on a best-effort basis. Mining nodes validate transactions, add them to the block they are building, and then broadcast the completed block to other nodes. Blockchains use various time-stamping schemes, such as proof-of-work, to serialize changes. Alternative consensus methods include proof-of-stake. Growth of a decentralized blockchain is accompanied by the risk of centralization because the computer resources required to process larger amounts of data become more expensive.
Openness
Open blockchains are more user-friendly than some traditional ownership records, which, while open to the public, still require physical access to view. Because all early blockchains were permissionless, controversy has arisen over the blockchain definition. An issue in this ongoing debate is whether a private system with verifiers tasked and authorized (permissioned) by a central authority should be considered a blockchain. Proponents of permissioned or private chains argue that the term "blockchain" may be applied to any data structure that batches data into time-stamped blocks. These blockchains serve as a distributed version of multiversion concurrency control (MVCC) in databases. Just as MVCC prevents two transactions from concurrently modifying a single object in a database, blockchains prevent two transactions from spending the same single output in a blockchain. Opponents say that permissioned systems resemble traditional corporate databases, not supporting decentralized data verification, and that such systems are not hardened against operator tampering and revision. Nikolai Hampton of Computerworld said that "many in-house blockchain solutions will be nothing more than cumbersome databases," and "without a clear security model, proprietary blockchains should be eyed with suspicion."
Permissionless
The great advantage to an open, permissionless, or public, blockchain network is that guarding against bad actors is not required and no access control is needed. This means that applications can be added to the network without the approval or trust of others, using the blockchain as a transport layer.
Bitcoin and other cryptocurrencies currently secure their blockchain by requiring new entries to include a proof of work. To prolong the blockchain, bitcoin uses Hashcash puzzles. While Hashcash was designed in 1997 by Adam Back, the original idea was first proposed by Cynthia Dwork and Moni Naor and Eli Ponyatovski in their 1992 paper "Pricing via Processing or Combatting Junk Mail".
Financial companies have not prioritised decentralized blockchains.
In 2016, venture capital investment for blockchain-related projects was weakening in the USA but increasing in China.[37] Bitcoin and many other cryptocurrencies use open (public) blockchains. As of April 2018, bitcoin has the highest market capitalization.
Permissioned (private) blockchain
Permissioned blockchains use an access control layer to govern who has access to the network. In contrast to public blockchain networks, validators on private blockchain networks are vetted by the network owner. They do not rely on anonymous nodes to validate transactions nor do they benefit from the network effect. Permissioned blockchains can also go by the name of 'consortium' blockchains.
Disadvantages of private blockchain
Nikolai Hampton pointed out in Computerworld that "There is also no need for a '51 percent' attack on a private blockchain, as the private blockchain (most likely) already controls 100 percent of all block creation resources. If you could attack or damage the blockchain creation tools on a private corporate server, you could effectively control 100 percent of their network and alter transactions however you wished." This has a set of particularly profound adverse implications during a financial crisis or debt crisis like the financial crisis of 2007–08, where politically powerful actors may make decisions that favor some groups at the expense of others, and "the bitcoin blockchain is protected by the massive group mining effort. It's unlikely that any private blockchain will try to protect records using gigawatts of computing power — it's time consuming and expensive." He also said, "Within a private blockchain there is also no 'race'; there's no incentive to use more power or discover blocks faster than competitors. This means that many in-house blockchain solutions will be nothing more than cumbersome databases."
Blockchain analysis
The analysis of public blockchains has become increasingly important with the popularity of bitcoin, Ethereum, litecoin and other cryptocurrencies. A blockchain, if it is public, provides anyone who wants access to observe and analyse the chain data, given one has the know-how. The process of understanding and accessing the flow of crypto has been an issue for many cryptocurrencies, crypto-exchanges and banks. The reason for this is accusations of blockchain enabled cryptocurrencies enabling illicit dark market trade of drugs, weapons, money laundering etc. A common belief has been that cryptocurrency is private and untraceable, thus leading many actors to use it for illegal purposes. This is changing and now specialised tech-companies provide blockchain tracking services, making crypto exchanges, law-enforcement and banks more aware of what is happening with crypto funds and fiat crypto exchanges. The development, some argue, has lead criminals to prioritise use of new cryptos such as Monero. The question is about public accessibility of blockchain data and the personal privacy of the very same data. It is a key debate in cryptocurrency and ultimately in blockchain.
Types Of Blockchain's
Currently, there are at least four types of blockchain networks — public blockchains, private blockchains, consortium blockchains and hybrid blockchains.
Public blockchains
A public blockchain has absolutely no access restrictions. Anyone with an Internet connection can send transactions to it as well as become a validator (i.e., participate in the execution of a consensus protocol). Usually, such networks offer economic incentives for those who secure them and utilize some type of a Proof of Stake or Proof of Work algorithm.
Some of the largest, most known public blockchains are the bitcoin blockchain and the Ethereum blockchain.
Private blockchains
A private blockchain is permissioned. One cannot join it unless invited by the network administrators. Participant and validator access is restricted.
This type of blockchains can be considered a middle-ground for companies that are interested in the blockchain technology in general but are not comfortable with a level of control offered by public networks. Typically, they seek to incorporate blockchain into their accounting and record-keeping procedures without sacrificing autonomy and running the risk of exposing sensitive data to the public internet.
Hybrid blockchains
A hybrid blockchain simply explained is a combination between different characteristics both public and private blockchains have by design. It allows to determine what information stays private and what information is made public. Further decentralization in relation to primarily centralized private blockchains can be achieved in various ways. Instead of keeping transactions inside their own network of community run or private nodes, the hash (with or without payload) can be posted on completely decentralized blockchains such as bitcoin. Dragonchain uses Interchain to host transactions on other blockchains. This allows users to operate on different blockchains, where they can selectively share data or business logic. Other blockchains like Wanchain use interoperability mechanisms such as bridges. By submitting the hash of a transaction (with or without the sensitive business logic) on public blockchains like bitcoin or Ethereum, some of the privacy and blockchain concerns are resolved, as no personal identifiable information is stored on a public blockchain. Depending on the hybrid blockchain its architecture, multi cloud solutions allow to store data in compliance with General Data Protection Regulation and other geographical limitations while also leveraging bitcoin's global hashpower to decentralize transactions.
Getting Started On The Darkweb
Technically, this is not a difficult process. You simply need to install and use Tor. Go to www.torproject.org and download the Tor Browser Bundle, which contains all the required tools. Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser. That's it.
The Vidalia Control Panel will automatically handle the randomised network setup and, when Tor is ready, the browser will open; just close it again to disconnect from the network.
Depending on what you intend to do on the Dark Web, some users recommend placing tape over your laptop's webcam to prevent prying eyes watching you. A tinfoil hat is also an option. If you're reading this to find out about torrent files.
The difficult thing is knowing where to look on the Dark Web. There, reader, we leave you to your own devices and wish you good luck and safe surfing. And a warning before you go any further. Once you get into the Dark Web, you *will* be able to access those sites to which the tabloids refer. This means that you could be a click away from sites selling drugs and guns, and - frankly - even worse things.
Aggregation sites such as Reddit offer lists of links, as do several Wikis, including http://thehiddenwiki.org/ - a list that offers access to some very bad places. Have a quick look by all means, but please don't take our linking to it as an endorsement to go out and get your self in trouble and please note I am not responsible for what you do
Also, Dark Web sites do go down from time to time, due to their dark nature. But if you want good customer service, stay out of the dark!
How to download Tor browser?
NOTE:Altho TOR is secure it is still advisable to download a 3rd party Virtual Private Network (VPN) as it will give you a much greater chance of not being intercepted and anything you can do to repel the people looking for what you are doing the better! ok, now lets get started
The Tor Project Inc. has released Tor Browser which is a modification of an Extended Support Release version of Mozilla Firefox browser. The browser is portable so that it can be used from an external media and also reduces the hazel of installation. Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
The Tor browser is available various desktop operating systems including Windows, Linux, and MacOS. You can visit this link to download Tor browser.
How to install Tor browser on Windows?
Run the Tor Browser setup.Choose your desired language.On the next windows, choose the destination folder. Using Tor would be easy if you choose the Desktop as the destination.Click Install.
The setup will create a folder named Tor Browser on your Desktop. Open the folder, and run the shortcut file to use Tor Browser.
For Linux, you’ll have to extract the downloaded file either using the command line or a file extractor application.
Tor Browser for Android
Orbot – a proxy with Tor for Android devices.
Orfox – a mobile version of Tor Browser for Android devices.
The Guardian Project, a global developer community founded by Nathan Freitas, is to be credited for the development of these apps.
Tor Browser for iOS
An official Tor browser app for iOS is available on the App Store.
Tor Alternatives
Hornet is a new anonymity network that provides higher network speeds compared to Tor. I2P and Freenet are other anonymity networks which can act as Tor alternatives. Also, Tails and Subgraph OS are Linux-based distributions with built-in Tor support.
Should I Use Tor?
Tor has proved to be an excellent medium for safe, secure and anonymous web presence available to a user at no cost. The developers of Tor didn’t intend it to become a hotbed of illegal activities, but evil-minded people have leveraged Tor for their benefits. The Tor project has led to an optimistic approach towards censorship and surveillance-free internet.
You can use Tor if you want to conceal your identity on the web or access some website that blocked in your region. But refrain yourself from doing anything that’s above the law because nothing is fool-proof and they can still catch you. Also, accessing your social media accounts over Tor can expose your identity. This being said me personally I use TOR only for my dark web research and visits. I do not access no websites with a commercially available router extension (IE: Com, Net, Org, Or anything else) the only extension that is run through tor is .onion extensions. The reason being is that any other extensions have the possibility to provide backdoor access to any an all of your information that is run while it is active.
NOTE: TOR's cookies are not dumbed until after you close the browser so it is still possible to track you if your browser is left open after you visited any other sites.
Steps For Safety(CH3)
Step 1: Plan ahead.
There are plenty of reasons companies and individuals may want to access the Dark Web. SMBs and enterprise companies in particular may want to monitor Dark Web portals for stolen corporate account information. Individuals may want to monitor sites for evidence of identity theft. Facebook's encrypted site, located at facebookcorewwwi.onion, is a feature-rich method of accessing the social network using end-to-end encryption.
Set a goal, make plans, and stay focused. Be mindful of purpose. Make sure you know what information you're looking for and why you're logging on to the encrypted web. For example, if you're a reporter and need to communicate with sources, focus on PGP, email, and encrypted communication. If you're searching for credit card information, look for Silk Road-type markets that sell hacked data.Get what you need, safely disconnect TOR and Tails, then log off.
Step 2: Obtain a new USB flash drive.
Purchase a new 8 GB or larger USB flash drive. Make sure you use a fresh, unused drive. You will install Tails, and Tails only, directly on your storage device.
Step 3: Prepare your local machine.
Ideally, use a fresh laptop. This isn't an option for most users, so instead do everything in your power to secure and isolate mission-critical information.
Back up critical data and local files.Make sure your hardware is optimized and malware-free.
Step 4: Download Tails and TOR.
TOR and Tails are available on the TOR Project website. Access download links directly from https://www.torproject.org. Insert your USB drive and follow the instructions on https://tails.boum.org.
Step 5: Browse safely.
Common portals and search engines:
DuckDuckGoThe Hidden WikiOnion.linkAhmia.fiGramsTorch
Encryption is strong, but not impenetrable. The FBI discovered and exploited vulnerabilities in the TOR network. Though the agency refused to disclose the source code used to penetrate the network, undoubtedly law enforcement agencies around the world monitor and operate on the Deep Web. Members of the TOR project vowed to patch network holes and strengthen the protocol.
Many of the best general deep web search engines have shut down or been acquired, like Alltheweb and CompletePlanet. Still, a few are hanging around to get you started:
DeeperWeb – Deep web search engine that leverages Google SearchThe WWW Virtual Library – The original index of the web, but more of a directory than a search engine.Surfwax – Indexes RSS feeds. Not certain this is still working…IceRocket – Searches the blogosphere and Twitter
These are all okay, but specialized search engines tend to be better than general ones for finding info on the deep web. If you’re looking for a court case, for example, use your state or country’s public records search. If you need academic journals, check out our article on using deep web search engines for academic and scholarly research. The more specific you can be, the better, or else you’ll just end up with the same search results that you would find on Google. If you need a specific file type, like an Excel file or a PDF, learn how to specify searches for that type of file (e.g. type “filetype:PDF” in your DeeperWeb query).
How to access the dark web on Android with Tor Browser
The official Tor Browser is now available on Android. You can get it from the Play Store or the Tor downloads page. As of writing, Tor Browser for Android is still in alpha, and additionally requires you install Orbot as a prerequisite.
The Tor Browser is the most popular dark web browser. Once Tor Browser is installed, you can now access those .onion dark net websites.
Using A VPN over TOR Or Vice Versa
A VPN allows a user to encrypt all the internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN in combination with Tor further adds to the security and anonymity of the user.
While somewhat similar, Tor emphasizes anonymity, and a VPN emphasizes privacy.
Combining them reduces risk, but there’s an important distinction in how these two tools interact. Let’s first discuss Tor over VPN.
If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN, this is by far the most common method. All your device’s internet traffic first goes to the VPN server, then it bounces through the Tor Network before ending up at its final destination. Your ISP only see’s the encrypted VPN traffic, and won’t know you’re on Tor. You can access .onion websites normally.
5 notes
·
View notes
Text
How to find Android App Development Software that Works for You
There are quite a few different types of Android app development software on the market today, and it can be hard to know which one will work best for you, especially if you’re new to this whole process and don’t have much experience with it yet. In this guide, I’ll cover some of the most common methods of app development and lay out their pros and cons so that you can decide which one is right for you.
Looking For Android Developer ? Android App Development Services in UK,US
User Feedback What do you think of your app? What’s wrong with it? Which features are working best? How can you improve it? This feedback will help guide you as you work on your next release. If a user isn’t happy, he or she won’t use your app again; if users aren’t using your app, then it doesn’t matter how good it is.
Mobile Device Support It’s essential that your app works on both mobile and tablet devices. This is where most potential customers are these days, after all. When you’re deciding which software is right for you, make sure it supports devices of various screen sizes and operating systems.
Customer Service Even if you have a tight budget, don’t skimp on customer service. Hire someone who has great people skills and is personable on top of being tech-savvy. While you might be willing to sacrifice your own time and energy, your customers aren’t—so make sure you aren’t doing it for them as well. An unhappy customer is more likely to take their business elsewhere than a happy one who is satisfied with what they got at a bargain price.
Flexibility in Pricing Not everyone is going to have unlimited resources at their disposal when building an app, and it’s usually best not to underestimate how much you’ll need. A free plan may be sufficient for some users, but others will definitely want something more advanced. Be sure you know what features you’ll really need so you can avoid any unnecessary costs or distractions later on.
Platform Options As of 2019, there are three major app development platforms—the most popular being Xcode, followed by Java, and finally React Native. And while there are no shortage of opinions on which platform is best, it ultimately depends on your specific needs. For example, if you’re looking to build an app with multiple languages (that support more than one region), Xcode would be a better fit than Java or React Native—and vice versa.
Special Features The top companies I’ve had experience with provide solid customer service, even if there are occasional glitches. Whenever you need help or encounter a problem, make sure you get in touch with your vendor—and don’t be afraid to ask questions! Making contact when something goes wrong will likely lead to a quicker resolution. The best vendors know that solving your problems quickly is key, so they have dedicated teams of customer-service staff who respond quickly and helpfully.
Reputation Among Customers The first thing customers notice about your application, aside from its actual content, is how well it works. Therefore, it is essential that your app functions smoothly and does not crash or malfunction. As a developer, you must make sure your app is polished and professional by going through multiple rounds of beta testing. Before you release an app to Google Play or Apple’s store, take it off-line and check every feature separately.
1 note
·
View note
Text
Week 8 - Industrial Design
Industrial Design continues to evolve and change our everyday lives. It provides us with many useful designs or tools that make our life more convenient. Not only are these designs useful, but they are becoming more sleek and more visually appealing to the consumer as well. Here are some industrial design examples that I use almost everyday.

TV remotes have been around for a while now, but they continue to evolve and become even more convenient for users. This is my remote for my smart tv. Not only does it function as a normal remote, but it also has buttons that can take me straight to various streaming apps like Netflix. Some remotes now a day even have voice command and allow users to direct it via their own voice without having to lift a finger. Another thing to notice about remotes is the size of them continues to be smaller and more sleek as well.
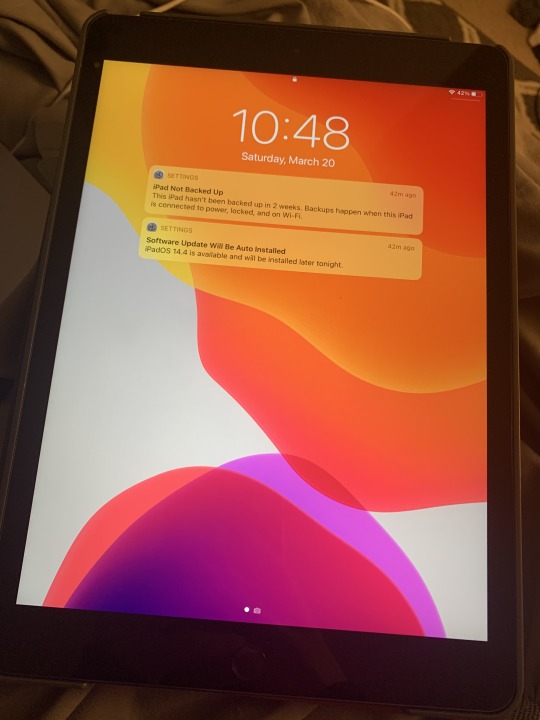
This is my iPad that I use nearly everyday for graphic designing. iPad or tablets haven’t been around for very long as some other inventions in the tech world, but they are constantly changing and becoming more useful. When I got my first iPad in third grade, it was a lot thicker and more bulky and it didn’t even have a camera. Today, iPads and tablets can do so much and are even starting to replace laptops due to their smaller size.

Airpods have been a great edition to my life. Although headphones have been around for a long time, Apple changed the game completely with these wireless bluetooth headphones. Not only are they visually more appealing, but it’s very useful to not have cords hanging down like traditional ear buds. Today wireless ear buds have nearly taken out the traditional ear bud completely. Not only does Apple have this product, but so many other companies have created their own versions for much less in price.

I recently came across this amazing brush that has made my morning routine much more convenient. This is an electric brush that not only combs your hair like a traditional hair brush, but it also straightens it at the same time. It’s comes in many different colors and there are a lot of variations of this design on the market as well.

Another thing that I have seen really evolve in recent years are printers. Printers continue to become more simplistic, appealing, and smaller. I love the design of my printer because not only does it provide the function of printer good quality images, but it’s also super simple and not an eye shore in my bedroom. The back part is where the paper sits and it can also lay down as well, which I really like for visual purposes when I am not using it. Printers continue to change to become more convenient and simplistic for users, which I really appreciate because I am not that tech savvy when it comes to printers. There are even portable printers on the market that can fit into a purse or a bag, which is great for people on the go.

This is a great innovation for people who are always cold at night. There is nothing worse than getting into bed after a long day and your bed is ice cold. This is a heated mattress pad, and it is amazing. I also really like how small and simple it is so it doesn’t take up a lot of space on my night stand. It has multiple settings and even a preheat button that you can turn on before getting into bed at night. This design has also been really great in terms of saving money on electricity in the winter as a college student. There are tons of different kinds of mattress pads on the market and have a lot of different functions and uses for them, but this is the coolest innovation of the mattress pad I have seen yet.

When thinking about industrial design, we think of innovative designs and sleekness. This desk lap I think is a great example. This lamp has so many different functions such as; different light modes and brightness levels, its touch screen, a clock, a room temperature, an alarm, and even a USB port to charge your phone. All that function into this small, simplistic looking desk lamp! It’s pretty great and is helpful in so many ways. Obviously lamps have been around forever, but more and more am I seeing lamps that serve as multipurpose tools instead of just being a source of light.

This is my key fob for my car. In industrial design as cars are becoming more innovative and visually appealing, so are their keys. My car doesn’t need a key to be put in it to start, I just simply have to bring this key into my coat pocket when trying to start my car. I think it’s really convenient to not have to think about your keys. I just put it in my purse or coat pocket when i am leaving the house and don’t have to think about it again. There are many cars on the market today that have similar keys, some even have buttons that can start you car before you even get in it. Sometimes it’s the simplest things that are innovated and become so convenient that consumers wouldn’t have even thought twice about before it came along. I would have never thought this innovation would have become so admired, but it really is!

I don’t think anyone could talk about innovation without bringing up the iPhone. iPhones are constantly becoming more innovative and convenient for users. They serve as so much more than a smart phone. The design of iPhones are also have a very minimalist aesthetic. iPhones are also very user friendly which is great for those who are tech savvy and those who aren’t, which is a huge reason why I believe iPhones are so popular. They have so many different tools that make everyday life for its user more convenient.

The last piece of industrial design that I use heavily is my Embr Wave. Although it might not be a very well known device right now, it serves a great function. It was created to help people regulate their temperature better by allowing users to either chose to cool down or be heated up. You place this little device on your wrist because it is said to be one of the best spots in your body to help change your temperature. If you have ever seen someone pass out, sometimes medical personnel will put an ice pack on their wrists to cool them down, and this device does exactly that. I have a medical condition that doesn’t allow me to regulate my own body temperature well and if I get hot, I pass out really easily. This device has replaced the need for ice packs and other cooling cloths and has truly saved my life in some cases. It’s a really great innovation especially for people with certain medical conditions.
0 notes
Text
How to Sell Digital Magazine Subscriptions Online Globally
Digital books and magazines are steadily increasing in popularity. As of writing of this article, digital books and magazines account for 11% of total publishing circulation revenue. As the COVID-19 forces more people to adapt to digital life, they are finding that they can easily subscribe to great content online.
The current climate is an excellent opportunity for those who are interested in learning how to sell magazine subscriptions online. In this article, we will discuss how to sell magazines online, on Amazon, and on Shopify.
Online content distribution is accessible
As a self-published author, selling your magazines online has never been easier. Apart from the multitude of platforms and marketplaces that make this achievable, you can also sell your content directly, by cutting-off the middleman and distributing it yourself. By publishing online via FlipBook or PressPad, for example, you can entirely control the creation of your content and retain 100% of the profits.
With an estimated 3.9 billion people using email services today, delivering content to your customers has never been easier. Publishing online eliminates a lot of overhead costs, so it may be a good idea to offer your current print subscribers limited complimentary digital access to encourage them to make the switch!
Tune your pricing strategy to acquire customers
When it comes to pricing your digital magazine, you’ll want to first experiment with a few tactics, testing which of these your audience is receptive to. An entry promotion or even trial versions accessible for free to early adopters can help you acquire an initial pool of customers.
If your magazine was previously offered in print version, you don’t necessarily have to add a significant discount to entice subscribers to switch over. You can even maintain the same price, but offer an increase in value by providing extra articles or features for those digital subscribers. Furthermore, offering sample subscriptions or free trials is infinitely cheaper in digital mode. Plus, it also gives you the opportunity to gather some usage data which will help you refine the offering in time to best suit audience needs.
Expand your reach to grow a user-base
Selling magazines online also has the benefit of reaching a larger audience. Whereas printed magazines are more difficult to mail to far-off locations, digital magazines have no boundaries.
When your magazine branches to the digital world, you can uncover new markets and audiences. You can also convert more sales by engaging with prospects via an email marketing campaign. Consumers are more likely to engage in an impulse buy when they know they can immediately receive what they paid for rather than wait for it to be delivered.
To grow a strong user base, experiment with email campaigns, segmenting your audience depending on their consumption preferences. Don’t be afraid to play around with different call-to-actions, set up an email schedule so you can send your inbox updates in a paced manner, and follow-up with leads depending on how they react to your initial campaigns.
Selling magazine subscriptions on popular platforms
Selling magazines online can be done through a variety of platforms. Generally, it’s recommended that online magazines have their own app that can be downloaded in the Apple or GPlay stores.
There are other eCommerce websites that can help to sell your magazine as well. Selling magazines on Amazon and selling magazines on Shopify are both great options to reach a larger audience.
How to sell magazine subscriptions on Amazon
One of the benefits of selling magazines on Amazon is how you can leverage their technology to target a specific audience. By using their “supported placement” feature, editors can select certain articles of theirs to be featured for a specific amount of time. Amazon has some fairly strict guidelines regarding content approval, so it’s important to use your highest quality pieces if your magazine decides to do this.
Like Facebook, Amazon customizes recommendations based on user’s behavior, which can be an invaluable tool when selling magazine subscriptions online. Of course, Amazon also spearheaded the trend of the digital-book with the invention of their Kindle gadget, so this platform is a natural fit for online magazine sales.
By selling magazines on Amazon, you have the opportunity to place your magazine in front of a new audience that may be very interested in your publication. For example, if your magazine is about interior decorating, Amazon might place your magazine as a customized recommendation for a user who has been searching for home decor items. Be sure to include a preview of your magazine on your Amazon listing so you can show interested prospects the value of your publication and increase their likelihood of subscribing.
You can also boost visibility when selling magazines online by including your publication on Amazon’s “Listmania” and “So You’d Like To … “ forums. Without paying a dime, you can create a Listmania of products related to your magazine’s genre and, of course, include your magazine on the list of must-haves for those interested in the topic. HubSpot reports that an estimated 70% of companies are increasing investment in online content creation, so keep in mind your Amazon promotional content won’t be without competition.
Using the Amazon customer interested in home decor as an option, you can choose one of your best articles from your magazine for your Listmania content. If your magazine just published an excellent article about Swedish-inspired modern furniture, you can search Amazon for pieces of furniture, bookcases, vases, bedspreads and throw pillows that follow this trend.
Alongside these articles from Amazon, you can include your magazine as a “must have” for those who are interested in this type of design. You’ve added value to your magazine by creating an easy shopping list for your prospect, and perhaps convinced someone to subscribe who would have never considered a digital magazine before. Making sure that your details page on Amazon is optimized is key for exposure. It’s important that prospects see that your magazine is the established authority in your industry. It’s essential to include highly relevant keywords in your description that will guide internet users to your online magazine.
An eye-catching cover image, as well as a relevant description for your online magazine, is important to succeed when selling online magazines on Amazon. To adjust any of these aspects, you’ll need to know your magazine’s ASIN number (a 10-digit alphanumeric code that Amazon uses to identify your magazine).
Can you sell magazine subscriptions on Shopify?
Shopify is one of the most popular eCommerce platforms out there. Can you sell magazines on Shopify just like any other product? The answer is yes. The only thing you need to do is decide which platform you’d like to use to deliver the digital version of your magazine, and enlist the help of a software that will allow subscribers to pay for your service in a variety of ways, like 2Checkout.
With Shopify, you can customize the look and layout of your store, keep track of purchases, and assure your customers of 24/7 customer service and support. For those who are not tech-savvy, Shopify offers a variety of templates to create a professional-looking online store. However, if you are a web design guru, Shopify gives its users 100% control over the HTML and CSS of their online store, so you can go all out with customizations and enhancements. In order to sell digital magazine subscriptions on the platform, you may also need to install an app so you can manage your digital products, as the platform is, at its core, developed for the sale of physical goods.
Keep in mind, though, that you may need a legal entity as well to sell on the platform. While Shopify allows individual sellers or sole proprietors to use its platform, for financial compliance and tax purposes having a legal entity established greatly simplifies things. Don’t forget to also choose a payment platform for your new Shopify store. It’s essential that the payment platform you choose allows you to accept multiple payment methods including PayPal, that it can use geo-location to translate payment instructions depending on where your subscribers are, and that it provides a quick-loading, seamless payment experience for subscribers.
After all, the ability to allow readers to quickly subscribe and access your digital magazine is key in your selling efforts. If your app or payment processing software is slow to load, complicated to use or not compatible with different devices, it could cost you dearly.
Selling magazine subscriptions online: low-cost, effective and environmentally friendly
Selling magazine subscriptions online is a great way to tie in your publication with any online marketing campaigns you are engaging in, especially if they involve social media! Selling subscription magazines on Amazon and selling magazines on Shopify are both great ways to attract and retain younger consumers, some of whom are too young to have experience with printed magazines.
People these days are rarely separated from their computers or phones, so it’s a great opportunity for your existing subscribers to become more engaged with your magazine. As the publishing industry adapts to digitalization, it’s important for your magazine to be at the forefront of trends. Encouraging subscribers to read magazines digitally will also help you to better understand their behavior and adapt your content accordingly to increase customer retention and engagement. It’s a win for both you and your subscribers!
Did you know you can use the rich tool set provided by 2Checkout Subscription Billing to forge closer relationships with your customers? Our powerful subscription management and recurring billing solution allows you to offer customers the frictionless, no-hassle experience they demand.

The post How to Sell Digital Magazine Subscriptions Online Globally appeared first on The 2Checkout Blog| Articles on eCommerce, Payments, CRO and more.
How to Sell Digital Magazine Subscriptions Online Globally published first on https://mrlavishdesign.tumblr.com/
0 notes
Text
How to Sell Digital Magazine Subscriptions Online Globally
Digital books and magazines are steadily increasing in popularity. As of writing of this article, digital books and magazines account for 11% of total publishing circulation revenue. As the COVID-19 forces more people to adapt to digital life, they are finding that they can easily subscribe to great content online.
The current climate is an excellent opportunity for those who are interested in learning how to sell magazine subscriptions online. In this article, we will discuss how to sell magazines online, on Amazon, and on Shopify.
Online content distribution is accessible
As a self-published author, selling your magazines online has never been easier. Apart from the multitude of platforms and marketplaces that make this achievable, you can also sell your content directly, by cutting-off the middleman and distributing it yourself. By publishing online via FlipBook or PressPad, for example, you can entirely control the creation of your content and retain 100% of the profits.
With an estimated 3.9 billion people using email services today, delivering content to your customers has never been easier. Publishing online eliminates a lot of overhead costs, so it may be a good idea to offer your current print subscribers limited complimentary digital access to encourage them to make the switch!
Tune your pricing strategy to acquire customers
When it comes to pricing your digital magazine, you’ll want to first experiment with a few tactics, testing which of these your audience is receptive to. An entry promotion or even trial versions accessible for free to early adopters can help you acquire an initial pool of customers.
If your magazine was previously offered in print version, you don’t necessarily have to add a significant discount to entice subscribers to switch over. You can even maintain the same price, but offer an increase in value by providing extra articles or features for those digital subscribers. Furthermore, offering sample subscriptions or free trials is infinitely cheaper in digital mode. Plus, it also gives you the opportunity to gather some usage data which will help you refine the offering in time to best suit audience needs.
Expand your reach to grow a user-base
Selling magazines online also has the benefit of reaching a larger audience. Whereas printed magazines are more difficult to mail to far-off locations, digital magazines have no boundaries.
When your magazine branches to the digital world, you can uncover new markets and audiences. You can also convert more sales by engaging with prospects via an email marketing campaign. Consumers are more likely to engage in an impulse buy when they know they can immediately receive what they paid for rather than wait for it to be delivered.
To grow a strong user base, experiment with email campaigns, segmenting your audience depending on their consumption preferences. Don’t be afraid to play around with different call-to-actions, set up an email schedule so you can send your inbox updates in a paced manner, and follow-up with leads depending on how they react to your initial campaigns.
Selling magazine subscriptions on popular platforms
Selling magazines online can be done through a variety of platforms. Generally, it’s recommended that online magazines have their own app that can be downloaded in the Apple or GPlay stores.
There are other eCommerce websites that can help to sell your magazine as well. Selling magazines on Amazon and selling magazines on Shopify are both great options to reach a larger audience.
How to sell magazine subscriptions on Amazon
One of the benefits of selling magazines on Amazon is how you can leverage their technology to target a specific audience. By using their “supported placement” feature, editors can select certain articles of theirs to be featured for a specific amount of time. Amazon has some fairly strict guidelines regarding content approval, so it’s important to use your highest quality pieces if your magazine decides to do this.
Like Facebook, Amazon customizes recommendations based on user’s behavior, which can be an invaluable tool when selling magazine subscriptions online. Of course, Amazon also spearheaded the trend of the digital-book with the invention of their Kindle gadget, so this platform is a natural fit for online magazine sales.
By selling magazines on Amazon, you have the opportunity to place your magazine in front of a new audience that may be very interested in your publication. For example, if your magazine is about interior decorating, Amazon might place your magazine as a customized recommendation for a user who has been searching for home decor items. Be sure to include a preview of your magazine on your Amazon listing so you can show interested prospects the value of your publication and increase their likelihood of subscribing.
You can also boost visibility when selling magazines online by including your publication on Amazon’s “Listmania” and “So You’d Like To … “ forums. Without paying a dime, you can create a Listmania of products related to your magazine’s genre and, of course, include your magazine on the list of must-haves for those interested in the topic. HubSpot reports that an estimated 70% of companies are increasing investment in online content creation, so keep in mind your Amazon promotional content won’t be without competition.
Using the Amazon customer interested in home decor as an option, you can choose one of your best articles from your magazine for your Listmania content. If your magazine just published an excellent article about Swedish-inspired modern furniture, you can search Amazon for pieces of furniture, bookcases, vases, bedspreads and throw pillows that follow this trend.
Alongside these articles from Amazon, you can include your magazine as a “must have” for those who are interested in this type of design. You’ve added value to your magazine by creating an easy shopping list for your prospect, and perhaps convinced someone to subscribe who would have never considered a digital magazine before. Making sure that your details page on Amazon is optimized is key for exposure. It’s important that prospects see that your magazine is the established authority in your industry. It’s essential to include highly relevant keywords in your description that will guide internet users to your online magazine.
An eye-catching cover image, as well as a relevant description for your online magazine, is important to succeed when selling online magazines on Amazon. To adjust any of these aspects, you’ll need to know your magazine’s ASIN number (a 10-digit alphanumeric code that Amazon uses to identify your magazine).
Can you sell magazine subscriptions on Shopify?
Shopify is one of the most popular eCommerce platforms out there. Can you sell magazines on Shopify just like any other product? The answer is yes. The only thing you need to do is decide which platform you’d like to use to deliver the digital version of your magazine, and enlist the help of a software that will allow subscribers to pay for your service in a variety of ways, like 2Checkout.
With Shopify, you can customize the look and layout of your store, keep track of purchases, and assure your customers of 24/7 customer service and support. For those who are not tech-savvy, Shopify offers a variety of templates to create a professional-looking online store. However, if you are a web design guru, Shopify gives its users 100% control over the HTML and CSS of their online store, so you can go all out with customizations and enhancements. In order to sell digital magazine subscriptions on the platform, you may also need to install an app so you can manage your digital products, as the platform is, at its core, developed for the sale of physical goods.
Keep in mind, though, that you may need a legal entity as well to sell on the platform. While Shopify allows individual sellers or sole proprietors to use its platform, for financial compliance and tax purposes having a legal entity established greatly simplifies things. Don’t forget to also choose a payment platform for your new Shopify store. It’s essential that the payment platform you choose allows you to accept multiple payment methods including PayPal, that it can use geo-location to translate payment instructions depending on where your subscribers are, and that it provides a quick-loading, seamless payment experience for subscribers.
After all, the ability to allow readers to quickly subscribe and access your digital magazine is key in your selling efforts. If your app or payment processing software is slow to load, complicated to use or not compatible with different devices, it could cost you dearly.
Selling magazine subscriptions online: low-cost, effective and environmentally friendly
Selling magazine subscriptions online is a great way to tie in your publication with any online marketing campaigns you are engaging in, especially if they involve social media! Selling subscription magazines on Amazon and selling magazines on Shopify are both great ways to attract and retain younger consumers, some of whom are too young to have experience with printed magazines.
People these days are rarely separated from their computers or phones, so it’s a great opportunity for your existing subscribers to become more engaged with your magazine. As the publishing industry adapts to digitalization, it’s important for your magazine to be at the forefront of trends. Encouraging subscribers to read magazines digitally will also help you to better understand their behavior and adapt your content accordingly to increase customer retention and engagement. It’s a win for both you and your subscribers!
Did you know you can use the rich tool set provided by 2Checkout Subscription Billing to forge closer relationships with your customers? Our powerful subscription management and recurring billing solution allows you to offer customers the frictionless, no-hassle experience they demand.

The post How to Sell Digital Magazine Subscriptions Online Globally appeared first on The 2Checkout Blog| Articles on eCommerce, Payments, CRO and more.
How to Sell Digital Magazine Subscriptions Online Globally published first on https://yousweetluxury.weebly.com/
0 notes
Text
Powerpoint Download For Mac Free

Powerpoint Download For Mac Free
Powerpoint Full Version Free Download
Professionals have long trusted its power and functionality to put their best foot forward. Students find it helpful as they create presentations for school projects and homework. PowerPoint 2016 is Microsoft’s latest version with new features and streamlined automation. This tool is ideal for anyone creating an impressive presentation, either with all the bells and whistles or with a simple and minimalist style. Suggested design templates help those who are not as tech savvy, while also being incredibly customizable for those who know their way around the interface. It currently occupies 95% of the world’s presentation software, solidifying its place as the industry standard. Using this program is sure to take your presentation to the next level.
Make your slides shine
Microsoft PowerPoint stays ahead of the curve as it releases innovative new features, still remaining the tried and true presentation software of the industry.
Microsoft leads many niches including the presentation software industry with Microsoft PowerPoint 2016. PowerPoint can be accessed either by purchasing a single software download or with an Office 365 (O365) subscription. An O365 subscription provides users access to the full suite of Microsoft Office products: Word, Excel, PowerPoint, Outlook, OneDrive, and Skype. Most users are opting for the Office 365 subscription as the monthly fee is low and provides access to Microsoft’s full business productivity suite.

Microsoft PowerPoint with a Microsoft 365 subscription is the latest version of PowerPoint. Previous versions include PowerPoint 2016, PowerPoint 2013, PowerPoint 2010, PowerPoint 2007, and PowerPoint 2003.
W elcome to Free Powerpoint Templates Design, one of the most usefull PowerPoint templates resource website: ALLPPT.COM!We provide you a fantastic collection of Free Powerpoint Templates Design that you can download for free and regulate for your personal Presentations. Discovering and getting the most related and suitable Powerpoint Templates are as simple as few clicks.
Some of PowerPoint’s newest and most innovative updates are only available to O365 users. Those with Office 365 also have access to Microsoft’s mobile apps, including PowerPoint for mobile, automatically syncing projects across all of your devices. PowerPoint via Microsoft Office Online allows users to collaborate within a presentation simultaneously, streamlining workflow and fostering teamwork. The latest version also offers templates in over 40 categories including business cards, calendars, flyers, photo albums, business plans, and of course business presentations.
Download powerpoint 2010 free for mac - shau.handmadematters. Prezentacje W Powerpoint Download For Mac - crackskills.over. Mac Logo png download - 512.512 - Free. Start quickly with the most recent versions of Word, Excel, PowerPoint, Outlook, OneNote and OneDrive —combining the familiarity of Office and the unique Mac features you love. Work online or offline, on your own or with others in real time—whatever works for what you’re doing.
Microsoft stays relevant with their Office Blog where users can connect with experts, see what’s new, and get the most out of their software. Microsoft provides support for large-scale presentations and offers tips on various subjects to improve user success and satisfaction. Within the software program itself, easily navigate PowerPoint’s toolbars to achieve the desired presentation. Business collaboration is upgraded with the ability to use @mentions within slide comments to notify others when you need their input.
Perhaps the most interesting new feature for business users is PowerPoint’s ink conversion capability. Users can draw directly within the “Draw” tab and PowerPoint will convert it to standard shapes. Sketch out an organizational chart within a slide and the ink converter will turn it into actual shapes and text. This takes on-the-fly edits and brainstorming to a whole new level. This feature, like many, is only available to Office 365 subscribers using Windows 10 version 1511 or later.PowerPoint is not just for your average work project though. With new features like 3-D animation and updated slide transitions, students and hobbyists can get creative as they showcase their information. PowerPoint consistently runs smoothly and quickly.
Microsoft PowerPoint 2016’s “Help” feature is enhanced from previous versions, which novices will find handy. All users are subject to Microsoft’s standard privacy policy. They do not use email, chat, files, or other personal content to target ads to users, a welcomed differentiator from other large companies such as Google and Instagram. Microsoft collects search data, location services (when activated), and stored sign-in and payment data (when authorized). Users can log into their Privacy dashboard to adjust settings, clear browsing, search, location, voice, media, and product activity. Microsoft seems committed to keeping privacy controls in the hands of its userbase.
Where can you run this program?
Microsoft Office 365 2019 (subscription) and PowerPoint 2016 (software installation only) are compatible with Windows 10 or macOS. The 32bit version is automatically installed but users can manually choose the 64bit download.
Is there a better alternative?
Google Slides and Apple Keynote are the two biggest competitors to Microsoft PowerPoint. The first and biggest difference between these three is that Microsoft PowerPoint is a paid software and Google Slides and Apple Keynote are both free.
There are also some additional capabilities that come included with Keynote but are an upgrade for PowerPoint users. Google Slides allows you to present via Chromecast, Airplay, or Hangouts, never having to connect any wires. Other than that, the abilities of each program are mostly similar, with some additions and deletions here and there.The big tradeoff lies in familiarity vs free.
Is it worth the learning curve to try Keynote or Slides? Most large companies and those with formal presentation needs will feel safer staying close to home with what they know, which is PowerPoint. With new features added with nearly every monthly release update, Microsoft simply adds to a program you already know, facilitating easier adoption.
Our take
Microsoft PowerPoint has been and will continue to be the presentation software front runner for the foreseeable future. For important presentations for business and school, reliability cannot be left up to chance. Making the leap from PowerPoint to another program may introduce risk when the stakes are already high. People like what is working for them and Microsoft is a brand people can trust.
Should you download it?
Powerpoint Download For Mac Free
Yes. Most business professionals and students are working with Microsoft Office products like PowerPoint already. You may be wondering if the O365 subscription is worth it or if you can get by with similar, free programs. That depends on your needs. Download an O365 subscription with Microsoft PowerPoint if you need a familiar, fast, and ever-evolving presentation software. Go for Google Slides if you are willing to work through a learning curve, adapt to a new interface, and if there will not be a negative reception of non-Microsoft products at your school or office. You cannot go wrong with Microsoft.
Powerpoint Full Version Free Download
2016

0 notes
Text
The House Always Wins
Hedge Funds routinely manipulate the market by using disinformation and institutional buying power to move perceived values in their favor, kneecapping corporations and putting hard-working employees on the street while they profit to the tune of billions. This week, the class of investors who are so often exploited in such cons struck back and the financial world went ape shit.
To short a stock is to essentially place a bet that its value will drop between the time you take your position and a future date. You don’t even buy the stock. The investor simply borrows the shares, which they then sell at the current market price, betting that the stock’s trading price will decline and they can purchase shares at a lower cost before the borrowed shares must be returned.
Funds with billions of dollars in assets under their management can easily engineer wealth by taking short positions on a stock even if there is no reason to believe that the price is set to decline, so long as they can convince enough investors outside of their fund that it will. If you’re big enough, simply taking that position can lead to such speculation, while large, institutional investors can also influence markets simply by moving in and out of various stocks.
During the run-up to the financial collapse of the securitized debt market that helped spawn the Great Recession, many investment banks actually advised their clients to take the opposite position that they themselves were betting, enhancing their own odds at the expense of those paying the banks’ for financial advisory services. No, it was not illegal.
Increasingly, the ever-growing industry of financial news and analysis has been a platform in which large institutions create market movement in their favor. By sending a high-ranking executive onto MSNBC, CNBC, or Fox Business to give their insight to individual investors watching at home, these institutions can influence the confidence of less savvy and informed market participants.
These influences can actually cause market reaction to produce the result they’ve bet on. Once the price begins to drop, that becomes the new story and, as nervous investors who can’t afford to take a big loss get out, the price drops further, increasing the value of their short position. This happens ALL.THE.TIME. and no one cries foul. In fact, those who engineer such manipulation are routinely hailed as geniuses.
While technology has made it even easier for such big players to dominate the market, it’s also created opportunities for individual investors to mimic such tactics, guerilla-style. Smartphone applications and other digital trading technologies have decreased former barriers that slowed the movement of small investors while social media and other digital communication systems have allowed such investors to create real-time information clearinghouses that make them less reliant on antiquated and manipulative information sources like the financial media.
Founded in 2005, Reddit is a "social news aggregation, web content rating, and discussion" website. It has a decidedly low-tech look and feel but has nonetheless grown into the 7th most visited website in the United States and 17th in the world. Subreddits exist for a mind-dizzying number of topics from the ordinary to the weird, to the truly disturbing.
Its look is similar to the pre-millennium chat rooms and message boards of early internet days. Users can upvote answers and contributions which push them higher in the feed, ensuring that what are thought to be the best answers, offerings or other contributions by the largest number of users are easiest to come by. Don't know if you should buy a certain year and model vehicle? There's a subreddit for that. Did you just watch a movie, not understand the point of the ending, and want to hear what others think? You can climb down a subreddit rabbit hole for hours.
WallStreeBets is a subreddit for investors who swap everything from tips to memes. Redditers there noticed that some very big hedge funds were taking short positions on GameStop, a chain of retail stores that mostly sells new and used video games. When users started pointing out that there was no reason to do so based on the company's financials they soon determined that it was garden variety market manipulation and began promoting a massive movement to buy GameStop shares in order to drive the price back up and foil their plans.
And did it ever work! The price of shares rose nearly 2000 percent, making some Reddit investors very, very rich in a matter of a day or two, as they dumped shares that had been purchased at the unnaturally low price for an overinflated one. This sort of "frontrunning," in which a price is driven up for investor benefit, is essentially the inverse of shorting it, though they were mostly working with purchased shares rather than ones that were borrowed (which is called a put option and would be the true opposite of a short).
This created billions and billions of dollars in exposure for some very wealthy and powerful people. The Redditers then went after other similarly positioned stocks. Soon, the entire financial news media was decrying the injustice done to the poor billionaires who were being fleeced by everyday people who, it is becoming increasingly clear, the financial markets aren't meant to benefit.
Robinhood is an app owned by financial services company Robinhood Markets Inc. Founded in 2013 by Vladimir Tenev and Baiju Bhatt, who had built high-frequency trading platforms for big financial institutions, its mission was said to be to "provide everyone with access to the financial markets, not just the wealthy." Let the People Trade was another early slogan.
However, while Robinhood, a free app, makes money from interest earned on its user's cash balances and margin lending, it also makes a lot of money selling user trading info to Wall Street (aka many of the people who are currently pissed) which led to the company suspending trading on GameStop and other targeted stocks on Thursday, freezing many of its users in poor positions. It turns out, they only want users to benefit if it doesn't interfere with the winnings of its real clients, the market manipulators who buy their user data so that they can more efficiently shake money from the pockets of the little guys.
When big firms make billions on speculation, there's always someone on the other end of that bet, or, in most cases, tens of thousands of people who don't have the ability to manipulate markets. The losers might be pension funds who've invested the money that's supposed to come back to employees at retirement or a middle-class worker whose 401k holds the wrong stocks. Not to mention the managers, employees, and others who are affected when a company is tanked for sport by the uber-rich.
It's hilarious to now watch those in the ivory towers—and the so-called financial journalists who shill for them—getting all worked up and actually call for the sort of regulation they so often fight tooth and nail against if it threatens to restrain their profits in the name of market stability or fairness. Where were the handsomely-paid talking heads when GameStop stock was falling for no other reason than an apex predator spotted it in the wild and decided it was hungry for a snack? Nowhere to be found because the people who butter their bread weren't making the phones ring, and they don't pick up when the number doesn't have a 212 area code.
Wall Street has become less and less about providing liquidity for markets so that the corporations that create American jobs can grow and prosper and more and more about setting up a rigged casino, in which the wales with three commas on their net worth always get dealt a hand that's superior to the tourists gambling with money that comes from wages rather than wealth. And when someone who's not in the club figures out a way to game the gamers just once? Well, that shit has to be stopped! Remember that the next time some politician points to the stock market as an expression of the American economy.
Like the yachts, boarding schools, lear jets, and palatial mansions, that shit ain’t for you, Jack. It’s for you to look at, to lust over, and to dream about so that you’re more willing to keep getting farmed for the benefit of the one percent and the promise that someday you too might get invited into the club (spoiler alert: you won’t).
A long time ago, people who were good enough at organizing in their head what had transpired in a blackjack game to bet according to what they believed was most likely to happen started taking such skills to places like Atlantic City and Las Vegas. If they were lucky, they got thrown out and told to never come back, while their picture was circulated to every pit boss in town. The message was the same one Wall Street is now trying to send to those who want to play on an honest table: Fuck off, peon, haven’t you heard, the house always wins.
Mitch Maley (bio) is the editor of The Bradenton Times and host of the Punk Rock Politix Channel on YouTube. You can also listen to the Punk Rock Politix Podcast on Apple Podcasts, Spotify, YouTube and other platforms.

0 notes
Text
Exceptional Suggestions to Pick a Cell Phone for your Teens at Home
Having young kids and utilizing a cellphone before them is not smart, and oftentimes not encouraged. Little Children desire all sorts of things that's in the hands, and your cellphone is the right mix of enjoyment and simplicity. Hiding your smart phone is just a futile solution. Maybe it's worse, I believe. A month ago, was his chance to disguise your smart phone. Right until pretty recently, the recommendation was that parents avoid showing children under 2 screens of any sort, including TV, tablets, or mobile phones. In 2016, it somewhat eased the guidelines. We broke this guideline a long time ago. I do not remember whenever we first hold an iPhone before his face, but over the last couple of months, we've viewed in horror as my son has developed a full-blown dependence on phones, long before he's also old enough to own one. During the last decade, much continues to be written about the fantastic display time debate: how often should our children be exposed to screens, and at what age? As recently as October 2016, a newspaper published an attribute that coated a dark vision of children and screens, using a estimate from a Facebook executive assistant stating that only bad things lurks inside our devices. Immediately after reading the story, we went into total panic mode and instituted a rule in our house where no-one is permitted to give our new son a cellphone. For the moment, this has kept the devil at bay. Still, I understand there should come a period when I'll yield to the inevitable and purchase my son his first phone. The possibility currently makes me stressed.

Regarding to a 2016 record, 72 percent of children between the age range of 13 and 16 have their own phone, while a 2018 survey indicates that nearly 44 percent of kids get their own personal cell phone plan between the age range of 11 and 12. In linked houses those that have more than 3 gadgets, kids obtain first tablet if they are 5.5 years old, and their first phone at the age of 6. These days, many adults are having technology in children's hands when they can keep them. But when it comes to what kinds of cell phones parents should actually buy their kids, the market offers very few options: There is no iPhone equal for kids, and there by no means has been. Generally, children are stuck with their parents' hand-me-down smartphones, as well as the responsability is definitely on the parent to install the necessary parental controls. Therefore, why hasn't the industry successfully made a mobile phone for kids? And if it did, what would such a device actually appear to be? While couples are often shamed for utilizing monitors to entertain their little children or supervise them by proxy, many people will concur that presenting their a kid a cell phone can be part and parcel to be a accountable parent in 2019. Ideally, a good smartphone for young adults should be mainly because strong as you can, maybe it would possess a way to text when there is a school emergency or some other kind of emergency, or not really allow them to carefully turn off their GPS or erase text messages. Others claim that such a tool should be sociable social media-free. No image no internet may be the matter we kept hearing from parents. With out a video camera or connectivity, teenagers cannot take selfies or build relationships social media, two actions parents are eager to control. Whilst tablets have already been properly promoted to little children, efforts to build up smart phones for kids have nearly universally failed. We have seen a lot of cell phones for kids over time and they are all junk. In 2014, one kids' tech company released the Kurio Google android phone, that was made to operate and appearance just like a grown-up cellphone, but with safety product features and usage limits to hide all scenarios. While fairly bland-looking, the telephone had all the things an anxious parent would've wished for: it blocked 450 million websites, allowed couples with children to remotely view texts and contact logs, and provided period limits on apps a long time before Apple introduced similar features. It even included a customizable in case of emergency form, featuring the child's allergic reaction information and blood type. Later in 2018, VTech, a plaything business, presented the KidiBuzz, a phone for kids between the age range of 5 and 9 that allows children to receive and send texts, photos, and voice messages. The kids cellphone was a marvelous flop and it had been forgotten the same year it had been unveiled. The unit was expensive to produce, but as it was not top quality, it could not really be sold at a proper price, it had been not Apple or Samsung, and this group the smart phone was aimed at, pre-tweens/tweens, is very brand and look-conscious. On the other hand, the KidiBuzz provides 35 percent one-star testimonials about Amazon, with one commenter observing that it generally does not even make a strong paperweight. Area of the issue with child-focused smartphones is efficiency: several devices occupy an amorphous grey space among a gadget and device. The KidiBuzz, for instance, presents features like video games and apps, but doesn't actually allow users place telephone calls. Adults searching for sensible mobile phones for children on Amazon may also come across dozens upon dozens of nonfunctional play phone items, gadgets that appear to be cell phones but are in fact toys which come equipped with various ringtones and flashing lights. An extra added problem is that items marketed as kid-friendly, have a built-in expiration time. There's very little activity happening in the child-specific space, since it just doesn't level well. You're talking about a very small segment of it: kids ages 4 to 10 or 9 to 12, etc. And it's really actually even smaller sized than that, mainly because at a certain age I don't believe children want the particular mobile phone. They need the same device you're utilizing. https://www.networkworld.com/article/2172154/iphone-6-rumor-rollup-for-the-week-ending-nov--22.html By and large, the truth is which the devices people want to use will be the devices coming from the big manufacturers. Why build some thing that is intent-built and a single model of these devices when you could basically consider any vendor's design and work with a parental controls app to greatly help control that? However, there's real anxiousness around giving developing children access to products that are nothing in short supply of addictive to grown adults. And more research has emerged linking excessive display time to, among other activities, depression, reduced rest, and speech hold off in infants. All that has pushed a small number of entrepreneurs to generate substitute solutions for children. The primary issue with providing young kids smart phones, is that, for lack of a better term, it's such an attractive, glossy device, you want to download games, open the web. That's almost inherent to the phone. I feel it actually myself in my phone. It is an extremely powerful issue. The first iteration from the Light Phone was meant to be used as little as possible: it might place cell phone calls, and mainly nothing else. The coming Light Mobile phone 2 may also allow users text. It's among a handful of entries in the smart, or dumb phone movement, which was spurred by a growing concern about smartphone reliance. Although not intended for children, the Light Telephone has gotten significant amounts of attention from couples. Couples have a problem with this problem: they need a smart phone so their child can contact them within an emergency, but Snapchat really scares them. The Jitterbug, which includes a large screen and good sized type, is one more dumb cellphone repeatedly cited as a good choice for young kids - even though it was developed for elderly people. additional hints The Jitterbug can place telephone calls and receive and send texts; at less than $50 for the turn mobile phone version, it's also substantially cheaper than the Light Phone 2, which includes not delivered out however but happens to be priced at $290. Some producers are bypassing cell phones altogether by entering the wearables marketplace. GizmoWatch, for instance, enables adults to monitor their kids' location and provides alerts if they enterprise outside a specific radius; it also lets young kids text and make phone calls to up to 10 friends on the preprogrammed get in touch with list, allowing parents to stay in touch using their children while curbing their display time. Without technically a wearable (if you can hook it to clothing having a carabiner-like item), the Relay, an identical to walkie-talkie gadget, is an additional access in the children' technology space. The device presents itself like a middle surface for less tech-savvy parents who are worried about display screen time, but don't want to navigate the complicated world of parental control apps. There's no way to view a bad YouTube video or seek out something unacceptable using the cell phone, because there's no display. Though devices just like the Relay and the GizmoWatch also appear to be exactly what these are: products for kids. And that may be a problem. Almost always there is some potential with wearables, but I'm a little hesitant to state they're gonna be considered a big seller. The marketplace demand in comparison to alternative options is such that the influence tends to be fairly limited. I could get my child a child smartwatch, that they may or might not use, or I could give them a phone. Wise watches, are not going to substitute cell phones for children. Children want even more. They are inundated with messaging to remain interconnected constantly. This is actually the world kids are developing up in. With out better alternatives, couples with children are generally stuck passing off their worn out Androids or iPhones or buying an old mobile phone, that still costs hundreds of dollars. There is just a certain comfort and ease there because that's what dad and mom have always utilized. Handing down our previous smart phones is normally low-cost as well as the parental handles work fairly well. Children aren't some unique animal that require special tools with regards to smartphones. These are little humans, and I prefer to respect them with regards to tech. And rather than creating new products, producers have started developing features to create their adult-focused items more teen-friendly. Apple's new operating system parental configurations include a Screen Time feature, that allows you to set period limits for particular applications and monitor how much period they're spending on their cellphones. Google has unveiled Google Family members Link, a free of charge app which allows couples with children to monitor their kids' screen time as well as wirelessly secure their products if they're spending too much time using them. These application work-arounds aren't ideal - kids are apparently hacking Apple's Screen Time by just changing the time setting on their device, but they're a recognition that children of a particular age want to own the same thing everyone else has. And if everybody else has an iPhone or an Google android, many will not accept anything less. Yet eventually the stress parents experience around what sorts of devices to buy their young kids so when may also be a way of projecting worries about our very own complicated relationships with cell phones. The solution may possibly not be finding the right device for our kids, but wrangling our very own impulses, especially because a handful of analysts say that parents who are overly distracted by their gadgets are establishing behavioral issues within their teenagers. Young Adults will do what you carry out, not what you tell them to do. You must model great digital habits. In fact, a 2016 research found that although 80 percent of couples with children thought they were modeling great screen behaviors for his or her kids, they were spending an average of nine hours each day with their screens, a lot more time than their children were. When I noticed that I was spending far more period scrolling through my e-mail and Twitter than I used to be playing on to the floor with my child, I realized that the challenge was not with displays bending his fragile mind. It was that I'd currently allowed my mobile phone to bend mine. So these days, we try not to use our cell phones at all before our son. That is a habit that can be easily designed for later years and really depends on the parents to maintain our young children away from cellphones until these people understand responsibility.
0 notes
Text
The Network: How a Secretive Phone Company Helped the Crime World Go Dark
Listen to an audio adaptation of this story on CYBER, available on all podcast apps.
Everyone crammed into the Las Vegas hotel suite was asleep except for Vince Ramos. The Wynn luxury hotel, with its indoor gardens, seafood restaurants, and extravagant shopping, had been this group's world for the past few days, with law enforcement officials from the U.S., Canada, and Australia grilling Ramos. Four or five officials lay down after another session of questioning their suspect.
Ramos had short breaks to see his wife and one of his children, who were staying in their own room nearby. Fearing he wouldn't be able to see his family if he didn't do so, Ramos spoke at length with the agents. Ramos looked like a ghost during those breaks when his family saw him, they said.
His trip to Vegas had been a setup.
He’d travelled to meet an associate as part of his multi-million dollar business, selling encrypted phones under the brand name Phantom Secure. Phantom's customized BlackBerry phones used dedicated software designed to make an ordinary wiretap impossible. The associate and Ramos planned to attend a fight in Vegas. But instead the FBI were waiting and cornered Ramos, dangling charges above his head usually reserved for taking down mob bosses. Biker gangs in Australia, drug traffickers in California, and even members of the Sinaloa Cartel all used Phantom's phones. Rather than treat Phantom as an innocent third party to crime like Apple or Google when criminals use phones made by those companies, authorities said Ramos himself was part of criminal conspiracies. The agents had Ramos on tape suggesting he made the phones to help drug smugglers. On the other side of that hotel room door, when the agents finally stopped asking their questions, there was likely a long prison sentence.
But with the agents asleep, Ramos saw an opening.
He slipped out into the corridor without waking his captors. Ramos walked to his wife's room and said goodbye. He had a chance to get up to Washington state and cross the border back to his home in Canada.
He headed downstairs, moved through the boiler area and basement, and left the hotel. Embarrassingly for the agents still in the suite, the person they had been hunting for years had just walked away.

Ramos had always been a businessman. Before launching Phantom Secure and becoming the target of an international investigation, he worked with multi-level marketing company Amway, and went on to corporate sales for Rogers, the Toronto-headquartered telecom conglomerate. Ramos received employee of the month awards both for selling bathtubs and then for selling phones, a family member said. His mother was a nurse; his father, a janitor.
"He was very business-savvy. His whole life, he was sales," the family member said. Ramos was "definitely a businessman to the core. Not a gangster in the slightest," a source with knowledge of Phantom's operations added.
Ramos coached his son’s flag football team, the Richmond Raiders. He practiced jujitsu with one of his daughters and wore a Hello Kitty backpack while making bracelets with his children.
He also got involved with a wide range of companies and ventures. Ramos gave a video testimonial for Allysian, a wellness and nutritional supplements company. In the clip on YouTube, Ramos said in a quiet, slightly nervous tone, that he looked up to Rod Jao, the founder of Allysian, because he had "always seen him as being a successful entrepreneur."
Ramos was a bit of a positive power kind of person, the source with knowledge of Phantom's operations added. Ramos didn't want to hear complaints. In his Allysian testimonial, Ramos said, "I tried the Mastermind, the Genesis, and the vitamins, and the chocolates," referring to some of the company's products.
"All natural ingredients, what I'm putting into my body, actually makes me feel really good,” he said. “I feel like I have a lot more energy, and, you know what, I even have that extra motivation to go to the gym, and work extra hard.”
Motherboard spoke to over half a dozen sources around Phantom, including family members of Ramos, distributors who sold Phantom phones in multiple countries on his behalf, and people with knowledge of the company's operations. In most cases, the sources requested anonymity to protect them from retaliation, especially from law enforcement and criminals. Four of Ramos's co-defendants, people who allegedly helped run the company or sell phones, remain wanted international fugitives. Motherboard also obtained multiple documents from within Phantom and a law enforcement file that gives deep insight into the investigation.
Many of the sources described Ramos not as a hardened criminal, but as a person who was naive and ignorant about the situation he put himself in. They described him as negligent, not malevolent. But as the company expanded, and eventually competition ramped up, something changed, and Ramos knowingly served the criminal market.
In 2008, Phantom started innocuously. Ramos got approval from lawyers in Canada to create the firm, went through the proper channels, and got his business license, according to the family member. Business records show Phantom Secure Communications was registered in Richmond, Canada.
"It was a legitimately run company," the family member said.
On the company's early, barebones website, Ramos, under the handle "CEO," laid out in part why he said he started Phantom.
"I truly believe in our right to privacy and like many internet users I have always had a concern with the security of my email storage and communications," Ramos wrote. He said that he used to send emails that contained seemingly trivial details, like dates and times when he was coming home, but also more important information like specific business details. Realizing that email as a medium was not especially private, he looked for a way to protect his communications over the internet.
Ramos wasn't much of a tech guy; he was never really a nerd or geek, his family member said. Instead, another person, the company's chief technology officer (CTO), handled the technical aspects of the operation. Court records don't name this person, instead referring to him as Individual A and a "high-ranking officer of Phantom Secure." Motherboard found his identity and a photo of him in an FBI document, and uncovered Canadian corporate records related to secure communications companies that mention his name. Motherboard is not naming him publicly because he has not been charged with a crime, and when reached for comment he feared for his and his family's safety.
"He was a very difficult person so Vince [Ramos] kept him away from the clients," the source with knowledge of Phantom's operations said of the CTO.
Do you know anything else about Phantom Secure? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on [email protected], or email [email protected].
Phantom's phones used a version of Pretty Good Privacy, or PGP encryption, meaning that only the intended recipient is supposed to be able to decrypt messages sent to them. Phantom went further, however, and also physically removed the GPS functionality from the BlackBerry, as well as the microphone and camera. With this drastically locked down device, a user couldn't make ordinary calls on the phone and instead could only send encrypted emails. Phantom also introduced a remote wipe feature, where a user could contact the company, and Phantom would delete messages on the phone without having physical control of the device. The company ran its infrastructure outside of Canada, and routed data through servers in Panama and Hong Kong in an attempt to keep it out of the reach of third-parties.
The privacy protection on messages from encrypted phones typically only works if the user is texting someone else who also has an encrypted phone, and sometimes companies force their devices to only communicate with phones from the same manufacturer. That way, if there was someone you needed to chat to and they had such a phone, you had to buy one too. From a business perspective, it was a way to pull in and retain customers.
Bruno (not his real name) said he started using Phantom phones in 2008 when he worked in Toronto's nightlife. Motherboard granted him anonymity to speak more candidly about the potentially grey area of selling encrypted phones. This was the heyday of BlackBerry's own messaging system, BBM, when typing out texts on a clunky QWERTY keyboard was considered stylish. Bruno said having a Phantom phone was originally a status symbol with VIP crowds, ranging from businessmen to escorts, and Ramos described the devices as the Louis Vuitton of the phone world. A phone cost thousands of dollars a year in subscription fees. Phantom marketed itself as the only full privacy solution, and its marketing worked, Bruno added.
"I had to be in contact with VIP clients to cater to their every need for bookings, reservations, etc," Bruno said, adding that he's worked with real estate agents and accountants who purchased Phantom devices.
Ramos gave free Phantom phones to rappers and athletes, including members of the Toronto Raptors, who would then use the devices with their own social network, Bruno said.

Illustration: Rebekka Dunlap
Mitsy Ramos, Vince Ramos' ex-wife and a Los Angeles-based Instagram model, said she worked for Phantom Secure and a connected company called VMD Ventures, according to social media posts. "I'll give you a deal," she tweeted to a Miami modeling agency in September 2011, along with a link to the Phantom website. Mitsy Ramos did not respond to multiple requests for comment.
"Vince was selling BB’s [BlackBerries] like he sold Amway. He was always talking about direct marketing, etc," the source with knowledge of Phantom's operations said. Ramos read books about sales, the source added. Much of the exposure was done through word-of-mouth, multiple sources said.
Later on, Phantom coated its website in a slick, black and chrome design, with silhouetted figures holding their phones. Images showed men in black suits and ties and luxury Bentley cars.
"Designed exclusively for the sophisticated executive," Phantom's website later read. Some people who sold Ramos' phones included photos of Phantom devices surrounded by gold jewelry on their social media accounts.
In a Phantom promotional video, a guitar twangs as the screen displays the company's logo. The video is littered with stock footage: men smoking cigars, leather seats, and a towering skyscraper with the company's logo obviously photoshopped onto its side.
"A True Private Experience, goes Beyond Perfection," the video says at one point.
"Offshore Swiss Account password," one fictional text between Phantom users in the video reads, demonstrating what sort of sensitive information clients might want to use the phones to send to one another.
Dance music kicks in, along with stereotypical cyber and security imagery like glowing padlocks.
"Did you know that using cell phones is the least secure form of communication?" the video asks. "Did you know regular email is similar to sending post cards? Did you know that SMS texts are sent in plaint text?"
Ramos typically didn't directly interact with his user base, which at the time was primarily Canadian. Administrators for Phantom handled new subscriptions, initiated device wipes, or removed accounts, according to court records. Bruno, who visited a Phantom office in Vancouver, said it was a 300-square-meter modern, clean office, but wasn't like an ordinary tech or startup space. Below the administrators, Ramos hired distributors, who essentially acted as middlemen between individual agents who sold phones to users, and the main Phantom company itself that the distributors would send their cut back up to. Bruno graduated from being a Phantom user to a distributor; a common route among other encrypted phone companies. Eventually he became a wholesaler.
Bruno and the source with knowledge of Phantom's operations both said that the company had a customer support center based in India. Website registration and online corporate records reveal a company linked to Phantom's CTO which does remote customer support and has a branch in Jalandhar, Punjab.
With Phantom's structure, Ramos was fairly hands-off with a large chunk of his customers, letting the workers sell the phones in their own geographic territories.
"We were free to do what we want when we want," Bruno added.
But Phantom had holes in how it hired distributors. Bruno said he moved to Asia to start selling the devices there. At first, Bruno said he simply sold the phones in exchange for envelopes of cash, but soon tried to tighten up the operation. He said he started to carry out due diligence on the sellers underneath him to make sure he was providing phones to legitimate industries and clients. He requested personal details so he could work out banking compliance and asked distributors to fill out anti-money laundering (AML) forms, where they provided names, addresses, and a form of identification so the company could verify who they were dealing with. Bruno provided Motherboard with a cache of internal Phantom documents, including filled out AML forms and bank statements, as well as driver licenses of distributors, to demonstrate some of the checks he carried out.
Early on, there were signs that Phantom's client base included criminals. Bruno said he turned down some "unsavory characters" looking to do business, "simply out of fear, let alone God knows what they were doing." Bruno filtered out the more suspicious individuals, he said.
Ramos, meanwhile, wasn't asking for much of this verification himself, according to Bruno. One of Phantom's policies was that it did not collect client names, but parts of the company also weren't verifying who was selling phones in the first place.
"Lack of screening anyone who resold the product, lack of formal contracts based on jurisdictions," Bruno said. Bruno added that he had to make a contract for Ramos to sign and return because Phantom itself never got around to making one. Bruno provided Motherboard with a copy of the contract.
"As [Ramos] built the business, he didn't really know who he was dealing with," Ramos' family member said. But ultimately, "we knew there were probably some people who were getting it for more nefarious purposes."
And some distributors were clearly keen to sell Phantom's phones to criminals. "I sold to people only that we're [sic] recommended or were from the zoo," a worker who used to advertise Phantom devices online said, using a slang term for prison. "That's how I kept law enforcement out; even if someone contacted my site, I wouldn't answer." This reseller also uploaded images with the phrase "Snitches Get Stitches" to their Instagram account.
When Ramos would visit Bruno, he would be more interested in partying than sitting down to conduct business, Bruno said.
"Don't get me wrong. He was a super nice guy. Soft-spoken, friendly, and cool to be around. But I was always pushing for a more professional relationship. Instead I got a guy who wanted to hang out as bros and party," he added. Rather than looking to solve conflict or tackling problems head on, Ramos wanted to be everyone's friend, Bruno said.
"It was a shit show how he ran the business," Bruno said. "I warned him to take things more seriously, and to enforce some form of compliance as the carelessness of his actions and the actions of other distributors was bad for his company and myself and others."
Ramos kept saying he wanted to be like Uber—just flood the market with devices and figure out regulations later, Bruno said. Soon, Phantom would have a monopoly over one country in particular.

A kilogram of cocaine in Australia can go for over eight times what it costs in the United States because of how difficult it is to smuggle drugs into the country. And top-level drug dealers needed a tool they could rely on and wouldn't let law enforcement listen in.
Here, Phantom found a new market.
"Uncrackable phones provided by Phantom Secure linked to murder of Hells Angels bikies," the headline on a March 2014 ABC article read. The report said that Australian law enforcement agencies were unable to monitor the communications of powerful criminals because of their use of encrypted phones. Even the Australian Signals Directorate, the country's version of the NSA, could not break through the encryption, it added. Intelligence agencies often can't crack encryption itself—instead, they work around it by hacking phones or introducing vulnerabilities themselves—but prospective viewers didn't need to know that.
ABC also aired a TV-spot including interviews with cyber security experts explaining Phantom's remote wipe feature and how that could specifically help if law enforcement seized the phone, as well as how Phantom deletes credit card information after a customer has paid for their device.
In the article, the outlet wrote that "the ABC does not suggest the company itself is aware its products are being used by criminals, only that criminals have become aware of the phone's utility and have taken advantage." Phantom did not respond to a request for an interview from ABC at the time, the report added.
In private, Ramos was ecstatic.
"This is the best verification on what we have been saying all along—proven and effective for now over 9 years," Ramos wrote to a Phantom employee in a message after the article was published, according to a copy of the text published in court records. "It is the highest level of official authority confirming our effectiveness. It can't get better than that." For Ramos, that criminals were using Phantom wasn't an issue, but a business opportunity. One Phantom reseller uploaded the ABC TV-spot to their own YouTube channel, promoting their devices.
That media attention "put Phantom on the map," Bruno said.
Phantom's use exploded in Australia, with distributors in the country selling the devices to criminals. Li Wang, one Phantom seller, had around 800 clients from different criminal networks, and his apartment was littered with BlackBerries, tens of thousands of dollars in cash, and meth, according to Australian media reports.

Illustration: Rebekka Dunlap
Phantom distributors based all across the country were selling the phones, according to an FBI document obtained by Motherboard. Queensland, Victoria, New South Wales, and other areas all had teams of people selling Phantom phones. The FBI document added that Phantom initially got a foothold in the country because it partnered with large scale drug traffickers—or "influencers"—who required anyone wishing to do business to also use a Phantom device.
One former Phantom distributor in Australia who is named in the FBI document told Motherboard that selling the phones "was perfectly legal, our company was registered."
The New South Wales Crime Commission, an Australian government body that aims to reduce organized crime in the region, wrote in one of its annual reports that "the prolific use of encrypted Blackberry devices continued unabated and, as in previous years, these devices were used to facilitate drug trafficking." Australia's national criminal intelligence agency specifically named Phantom as a go-to choice for organized crime groups, as well as the encrypted messaging app Wickr.
One legal document obtained by Motherboard describes how lawyers for a Phantom seller had "high level meetings with executive members of the Australian Crime Commission (ACC) concerning Phantom Secure's operations in Australia." The letter is from several years after Phantom had already attracted the attention of Australian law enforcement. (The Australian Criminal Intelligence Commission, which the ACC merged into in July 2016, declined to comment).
Documents show that while Ramos saw hindering law enforcement as good publicity, he may have gone further and ignored Australian authorities when they tried to speak to Phantom.
"Primarily my main concern is whether Phantom Secure is addressing official requests from law enforcement in their investigations," one document sent to Ramos by Bruno reads. "From my knowledge Phantom Secure has failed at times to reply to Australian police inquiries. THIS IS UNACCEPTABLE." Bruno added that although he understood the sensitive nature of their business—protecting the privacy of their clients—"it doesn't take a legal expert to understand that ignoring official law enforcement requests is a recipe for disaster and potentially illegal."
Phantom was so popular in the country, and so trusted, that "Phantom was almost like a religion in Australia," the source with knowledge of Phantom's operations said.
From Ramos' standpoint, he was not actually dealing with these drug dealers, one of his lawyers would recall later in a court hearing.
"They are one or two steps away from me; I am selling a phone; I am in a business," the lawyer said, relaying Ramos' train of thought.
One of those clients was Owen Hanson, a tanned, muscular former USC football player. Like Ramos, Hanson also had a penchant for Louis Vuitton: the silver-plated AK-47 in Hanson's office was emblazoned with the designer's logo. Hanson had moved through real estate to running a highly successful online sports gambling business. But Hanson wanted more. Hanson, also known by his long-running nickname "O-Dog," turned to drug trafficking.

Owen Hanson. Image: Owen Hanson's Twitter Account.
He was arrested for possession of steroids. Then he moved onto dealing cocaine, GHB, and ecstasy. Then he upgraded to bulk quantities. As the operation rapidly grew, Hanson shipped thousands of kilograms of cocaine from Mexico, into Southern California, and on to Chicago. Hanson was also cashing in on the Australia gold rush, selling kilograms of cocaine on the island for $175,000 each, according to court records.
"This wasn't somebody who was trying to smuggle drugs, you know, a couple carloads of drugs from Mexico to the United States," The Honorable William Q. Hayes, a judge, would say later in a hearing about Hanon's case. "He was an international drug trafficker. He was very, very successful. And he had access to huge amounts of cocaine. I mean, he moved—he moved hundreds of kilos sometimes a month from Mexico to the United States or to Canada or other places. It is astounding that somebody has access to literally hundreds of kilos a month, and all over the globe."
Investigators were already probing Macho Sports, the online gambling business Hanson's own firm was connected to, when they discovered he had moved into smuggling narcotics. The San Diego FBI tapped his phones, a text messaging app he used, and email accounts, according to court records. Hanson gave associates burner phones. There was one line of communication that would have been off-limits to the investigators, though: his and his co-conspirators Phantom devices.
Hanson's organization used around six Phantom devices to coordinate a shipment of more than a ton of cocaine, according to court records. The Phantom users were spread across Mexico, Los Angeles, San Diego, Chicago, New York City, and New Jersey, the records say.
Phantom lets customers choose their own nickname on the Phantom network. Hanson picked Don Corleone, a reference to The Godfather movies, according to court records.
It wasn't just the name; Hanson constantly projected the almost cliched image of a mob boss. Beyond the Louis Vuitton AK-47, he invested in a restaurant and insisted that the backroom be decorated with posters of the Mafia and dubbed the "wise guy room." He stored bundles of cash under bathtubs, hidden compartments inside cars, and private vaults that required a retina-scan to enter.
In a dramatic arrest in the car park of one of the country clubs that he was a member of, with a helicopter overhead and agents pointing weapons, the FBI grabbed Hanson. His downfall was largely thanks to an undercover that authorities planted inside Hanson's organization—the undercover got their own Phantom device when Hanson vouched for him to the company, according to court records. It doesn't matter if you have the strongest encryption in the world if someone inside the conversation flips.
Ramos' family member said that Ramos never met or knew of Hanson. But that didn't matter for the investigators. Now that the FBI had busted someone who was using the phones to ship drugs into the U.S., it had a reason to look into Phantom too.

Motherboard obtained an FBI-authored document that lays out in detail the chronology of the FBI’s and other law enforcement agencies’ investigation into Phantom, that gives unprecedented insight into how they ultimately took down Ramos.
The document—a 30 page slide presentation—appears to have been created to summarize the investigation for other law enforcement agencies. Slides outline an initial investigative strategy, a revised strategy, and a takedown strategy that includes a two-prong approach: a covert phase to investigate Ramos and an overt phase to take down Phantom's infrastructure internationally.
The document itself is marked as unclassified, but it contains sensitive information such as the identity of Phantom’s CTO, names of distributors who sold phones in Australia, and other intelligence that law enforcement agencies gathered about Phantom which is not mentioned in the case’s public court documents. Beyond Motherboard’s own sources, some of the timeline of the law enforcement investigation into Phantom explained in this piece is based on that document.
When officials from the San Diego FBI flew to Vancouver to meet with the Royal Canadian Mounted Police (RCMP) in May 2016, the RCMP had already been investigating Phantom for several years. Canadian and Australian law enforcement had found that Phantom distributed its phones internationally, had more than 15 business owners linked to the company, and estimated sales that exceeded that $32 million.
The RCMP had encountered Phantom's vouch system, where at least some sellers would not provide a phone unless the buyer was recommended by a current customer. The agency tried to buy phones through the company's website, or by just walking into their office, in six separate undercover attempts, according to the FBI document. (Bruno and the source with knowledge of Phantom's operations both disputed the idea that Phantom, overall, had a vouch system; Bruno said he would sell the devices openly online for people to buy).
When the RCMP did manage to get hold of a phone, undercover employees pretending to be drug dealers asked a Phantom support representative to wipe the device, but made it clear the intent was criminal.
"So, he picked up the load and I think he's been arrested and I need, there's a lot of evidence and fuckin' shit on my BlackBerry," the undercover wrote, making a veiled reference to a shipment of narcotics.
"You wanna wipe both of them?" a Phantom staffer replied, according to court records and an FBI document.
"Yes," the user wrote.
"One sec," the Phantom representative replied, before reassuring the undercover agent that law enforcement can't access Phantom data.

A section of the FBI document, with redactions by Motherboard. Image: Motherboard
The RCMP had also managed to obtain log-in information for a panel used by Phantom sellers, which gave an idea of the city and country the workers logged in from, according to an FBI document.
In their eyes, Canadian and Australian authorities had a problem. Selling the phones wasn't illegal in their own countries, and they didn't have the legal framework to treat Phantom as a criminal organization. The U.S., meanwhile, did: it had the Racketeer Influenced and Corrupt Organizations Act, or RICO, a law used for prosecuting mafia heads who had underlings carry out their dirty work to try and keep their own hands somewhat clean. It's also the same law U.S. authorities used to go after Hanson and his drug trafficking gang.
Controversially to multiple sources around Phantom, Canada and Australia needed the U.S. to get involved to take down a company that wasn't breaking the law in their own territories. The FBI document acknowledges this, and says that the RCMP was eager to join forces with the FBI.
The U.S. Drug Enforcement Administration had some information too: they already had recorded conversations implicating Michael Gamboa, also known as Chino, an alleged Phantom distributor who sold phones in Los Angeles. Gamboa sported a buzzcut and a shirt and tie in one photo included in the FBI document. Authorities also had their eyes on Christopher Poquiz, another distributor also from Los Angeles.
The FBI's initial plan was to take one of their informants from another investigation to target Gamboa and Poquiz, and then eventually introduce an undercover FBI employee offering to sell phones to their own network and become part of Phantom. If the FBI could have an employee work as a distributor, they could work their way up to potential meetings and conversations with people higher up in Phantom. The ultimate goal was to reach Ramos and the CTO, according to the FBI document.
On the other side of the world, the Australians were working on a similar plan. In another law enforcement meeting later that year in September 2016, FBI San Diego traveled again, but this time to Sydney, Australia. After the meetings were over, representatives from the Queensland Police Service pulled the FBI aside and offered a particularly valuable asset: they already had a confidential human source (CHS), a Phantom distributor in Australia. The FBI didn't even need to introduce an undercover employee as a distributor; the Queensland Police Service already had someone on the inside.
Every case of this size needs a big break, the FBI document reads. This was their way in.

Phantom didn't stop at Australia. Online records show Phantom had web domains and companies registered in Bulgaria, Ireland, and Singapore. Classified ads in local, English language newspapers show Phantom Secure-linked companies hiring in Thailand.
"Over time, the money was just coming in," Ramos' family member said.
Some of Phantom's revenue included large amounts of cryptocurrency, gold coins and silver bricks, and hundreds of thousands of dollars in various bank accounts and safe deposit boxes in Los Angeles and Beverly Hills, according to court records. Ramos had a personal net worth of at least $10 million, with properties in Canada and Vegas, the documents say. Ramos and his wife's Vegas high-rise, gated condo came with community tennis courts, a swimming pool, and a gym, property records show. Ramos owned a Lamborghini.
In all, Phantom sold around 7,000 to 10,000 phones, according to court records. A map included in the FBI document showed the spread of some of the devices: Central and South America, Europe, the Middle East, South East Asia, and North America.
Phantom had gone global.
Ramos "said it was going too good, and that it was something that he couldn't stop," his family member said.
But for all of its glitz and marketing, Phantom's product essentially hadn't upgraded since it launched nearly 10 years ago. This was the mid-2010s, and BlackBerries certainly weren't as popular as they used to be. Other companies based their products on Android and had more features, such as an encrypted communications system that felt more like instant messaging rather than sending emails back and forth. One internal Phantom document obtained by Motherboard described how some distributors would give their customers refurbished BlackBerry devices with the Phantom software installed, but with keyboard keys falling off or cracked screens. The company was lagging behind.
Bruno and the source with knowledge of Phantom's operations said Phantom commissioned the development of an Android app, but it failed. The app "was a disaster" the source said, adding that the person who made it "could barely code."
Phantom did innovate with another app called Privé Chat that ran on Samsung KNOX, Samsung's own security-focused version of Android.
"It was decent but it was about two years too late," Bruno said. The company launched buy-one-get-one-free promotions.

A photo uploaded to the Instagram account of someone advertising Phantom Secure devices. Image: Instagram.
Ramos also tried to more directly evolve Phantom from BlackBerry to Android hardware by sourcing large quantities of devices preloaded with other security-focused operating systems.
"Hi, we are a Privacy, Secure Messaging company," a 2016 email written by Ramos to an Android phone company, obtained by Motherboard, reads. "We are interested in learning more about your hardened phones and potentially buying some in the 100s or 1000s." The owner of the Android company told Motherboard that Ramos later said he wanted to buy around 12,000 to 15,000 devices.
"He was grasping at straws to increase his hardware," the company owner said. "He was asking for massive amounts of devices." Ramos wanted to pay with Bitcoin, but the owner told Ramos the company does not use that sort of currency, the owner added.
"That's when he disappeared," the owner added.
Competition in the encrypted phone market grew more aggressive. While firms like Encrochat, which offered a similar product, had cornered much of the European market, others pushed more directly into Phantom's territory, especially in Australia.
"Our sales were going down fast due to cheaper competitors like Ciphr and others," Bruno said, referring to another encrypted phone company that was particularly popular in the country. "His [Ramos'] product was no longer that cool nor was it cheap either."
"Ciphr and Sky started moving into the Australian market with superior products," the source with knowledge of Phantom's operations said. "Ciphr was cheap and aggressive. Sky did free promos."
Bruno said he had previously met with Ciphr representatives, and "was terrified."
"I felt like I was in a mafia-esque situation during that meeting," he recalled.
While competition ramped up and its business fell behind, banks that some Phantom workers did business with seemingly started causing problems, too. Bruno said HSBC closed several of his accounts without warning. The source with knowledge of Phantom's operations also said authorities seized payments and bank accounts.
But Ramos and his agents needed the business to survive.
"Vince [Ramos] lived lavishly. He had to support his lifestyle," Bruno said. "I'm not complaining. I made damn good money in the beginning but his own greed was his downfall." Bruno said he thinks Ramos got desperate in finding new clients, and so allowed himself to do business with anyone.
Then Ramos agreed to a meeting in Vegas that would solidify his willingness to help organized criminals.

The FBI and its new CHS, the Phantom distributor feeding information to law enforcement, got to work. The investigation, officially called Operation Safe Cracking, was ramping up.
Having eventually gotten closer to Ramos, the CHS met with him for two days in Los Angeles, according to the FBI document. When the CHS described Phantom's clients as criminals, Ramos corrected him, saying that all Phantom customers are to be referred to as "executives."
The pair chatted over WhatsApp and their Phantom phones. The exact context is unclear, but the pair seemingly discussed how, if they did more explicitly turn to a life of crime, they may be very good at it.
"But if we turned [in] to executives we would be the top executives out there, lol," Ramos wrote to the CHS in one message. "But not gonna lie have so much exec blood running through. Former execs lol."
"Oh if we turned back [into] exec the it wouldn't be a problem, the CHS replied. "This business opens so many doors."
"Yes bro," Ramos wrote. "We are all former execs, We gonna do big things…I'm constantly networking."
Escalating their relationship, the CHS arranged a meeting between Ramos and a group of alleged drug traffickers in Vegas in February 2017. The group wanted a particularly large order: 200 Phantom devices, working out at potentially $600,000 worth of phones in one deal. Dressed in a tight black t-shirt and smiling, Ramos huddled with the potential customers on a couch while an NBA game played on the TV.
Rather explicitly, the clients said what they wanted the devices for.
"Three of my main guys are in prison," the new client said, adding that they lost 50 kilos from Colombia. They wanted to expand their drug trafficking business into South America and Europe.
"Okay. You don't have to tell me that, but it's okay," Ramos replied.
"Yeah, well, we're all friends," the trafficker replied.
"Just saying it out loud," Ramos added, as if he did not want the traffickers to discuss what they were using the phones for.
Although they were being clear about the industry they worked in, the client seemed hesitant to start working with Ramos.
"You know, we don't know you," they said.
"Of course. That's what I'm saying," Ramos added. "You don't know me. But, yeah that's exactly what I'm saying, right. We made it—we made it specifically for this too."

A section of the FBI document showing Ramos in the undercover meeting. Image: Motherboard
The traffickers moved onto asking about what would happen if a member of their organization was using a Phantom phone and got arrested.
"What's the first thing we should do if we get word that someone got pinched and we need to just kind of—having them fall off the radar," one of the traffickers asked.
Ramos recommended using Phantom's wipe feature, but cautioned that the phone needs to be connected to the network to receive the command.
"Because what they do now with that they have a Faraday bag. You can put the device into a bag and it does not emit any signals if you put it into like, a lab to avoid wipes," Ramos explained.
"Who has that?" one of the traffickers asked.
"What I'm saying, the authorities, the 'unfriendlies' do," Ramos added.
The clients had more questions, specifically on whether Phantom could keep the GPS enabled on certain devices in case they needed to track one of their own users. Ordinarily, Phantom physically removed this feature. And as Ramos explained and tapped through the settings on a phone to demonstrate to the client, a user could just turn off the GPS feature if they didn't want to be tracked.
The trafficker instead suggested what they might tell one of their members to make sure that the GPS remain enabled: "Yeah don't fight—don't, don't, don't, don't fuck with the phone. If you turn it off, we'll turn you off."
"Right, right, right, right," Ramos replied.
Ramos had made a serious mistake.
He had suggested that Phantom's phones were made for drug smuggling. And he had said that if a Phantom user was arrested, the company could try and issue a wipe command to the device. Unbeknownst to him, Ramos' admission was not some fleeting comment to a prospective client. These drug traffickers were undercover agents from the RCMP, and were secretly recording the conversation. The CHS had led Ramos into a trap. This wasn't a business deal; authorities had descended on Vegas and lured Ramos in an attempt to build a case on him.
After that meeting, Ramos' trust in the CHS increased, and his role was elevated, according to the FBI document. The CHS was placed in direct contact with other top-level Phantom distributors, including those who oversaw distribution in Thailand, Hong Kong, Dubai, Turkey, and Australia, according to the document.
Ramos stepped further and further away from plausible deniability. In one text message exchange, he wrote how undercovers had tried to get one of his employees to wipe a phone allegedly used for drug smuggling.
"My worker ended up wiping the device and they tried to get him for obstruction of justice.. He got off but cost a lot in lawyer fees," Ramos wrote. "So word of advice… Never acknowledge anything illegal."
He leaned into his criminal client base, and said he secured business with one of the most technologically advanced and violent criminal groups in the world. At the time he had no idea about the mistake he had made with the agents in Vegas; if anything, business was getting better again.
"He did learn to manage gangsters as clients," the source with knowledge of Phantom's operations said.

"We are fucking rich man," Ramos' February 2018 text message to a Phantom employee read. He was back in Vegas, and appeared to be celebrating. Ramos had just been in Mexico City, where he traveled to pitch Phantom devices to potential customers, according to court records. The trip had been a success.
"Get the fucking Range Rover brand new. Because I just closed a lot of business. This week man," Ramos' text, sent using the encrypted messaging app Signal, continued.
"Sinaloa Cartel that's what up," Ramos said. "And my boy is Punjabi cartel lol. Straight up," he added. The rest of his text suggested he was currently at the Spearmint Rhino stripclub in Vegas with Richard Sherman, then a star for the Seattle Seahawks. Bob Lange, vice president of communications for Sherman's current team the San Francisco 49ers, wrote in an email "I spoke with Richard and he does not know this gentleman."
How exactly Ramos ended up traveling to Mexico City, meeting with the Sinaloa Cartel, and what that deal entailed is unclear. Motherboard did correspond with Ramos over months through email and physical letter, but he didn't go into great detail.
"I am thinking of what I can put out there," he wrote in one email, talking generally about his case. "To be honest I'm at a crossroads of how much I want to put out there."
"I probably do have some questions and comments… I just have to find a way to word them. I do want to have some input in what you write as well…," he said in another message.

A text message sent by Ramos included in court records. Image: Department of Justice.
But shortly after Motherboard sent a final list of specific questions to Ramos to give him a chance to respond, including how he met members from the Sinaloa Cartel, the Bureau of Prisons cut off our communications with him.
"This message informs you that you have been blocked from communicating with the above-named federal prisoner because the Bureau has determined that such communication is detrimental to the security, good order, or discipline of the facility, or might facilitate criminal activity," a message sent by the prison's email system read. "The prisoner with whom you were communicating is being informed of this block. You may appeal this block within 15 days of the date of this message by submitting a written request to the Warden of the prison where the prisoner is located. You should include a copy of this notice, an explanation of your appeal request, and any additional documents or information you wish to be considered."
Motherboard appealed the decision, but received no explanation from the prison as for why it stopped Ramos from replying.
David Fathi, director of the American Civil Liberties Union's National Prison Project, said this sort of block is not something he's heard of before.
"Based on this limited information, this appears to be a disturbing attempt to interfere with communication between an incarcerated person and the news media—communication that the courts have ruled is protected by the First Amendment," he said in a statement.
"What's especially concerning is that essentially no information is provided about the reason for blocking communication. 'Detrimental to the security, good order, or discipline of the facility' doesn't actually tell you what the journalist or the prisoner has allegedly done wrong. Without that information, it's impossible to meaningfully challenge the decision," he added.
Ramos' celebrations in Vegas over his new customer didn't last long. Shortly after, Ramos was supposed to attend a fight. Cyborg was fighting Kunitskaya as part of an UFC tournament that Saturday. But instead Ramos was in that suite in the Wynn hotel with the law enforcement agents. Authorities had a warrant for his arrest and were ready to lump Ramos with conspiracy to traffic drugs charges, in part because of what he had told the undercover RCMP agents posing as drug traffickers a year earlier. The authorities said Phantom fell under RICO.
Agents questioned Ramos for days in the hotel, while giving him those breaks to see his wife, the source with knowledge of Phantom's operations and the family member said. Authorities showed Ramos photos of persons of interest, the first source added said.
"Vince [Ramos] said he built a good relationship over the days," the source added. "They trusted him. Hours were exhausting on all parties."
Law enforcement officers went through his phone. Worryingly for the RCMP agents, someone had sent Ramos a message earlier.
"You don't know me. I have information that I am confident you will find very valuable," one email to Ramos allegedly read. The alleged source, investigators would later find out, was Cameron Ortis, a director-general with the RCMP's intelligence unit, who was suspected of selling sensitive law enforcement information to criminals.
But right now, the group of agents didn't arrest Ramos on the spot. Instead, they gave a proposition: could Ramos create a backdoor to Phantom's network? In short, a backdoor is an extra way into a network or the information it contains, and could potentially let the FBI identify Phantom's customers; the actual drug traffickers themselves.
"He was given the opportunity to do significantly less time if he identified users or built in/gave backdoor access," the family member said. The source with knowledge of Phantom's operations also described the access as a "backdoor."
The family member said Ramos didn't install one "out of integrity and his values for privacy."
Ramos did not have the technical know-how to actually do it anyway. He wasn't the tech guy, and Victor Sherman, one of Ramos' lawyers, said Ramos didn't know how to do it. The person who could, the CTO, was across the border in Canada, not a Vegas hotel suite.
When the agents were asleep after another long session of questioning, Ramos made his dash through the corridors of the Wynn hotel and into the basement. An associate picked him up, and started to drive him to the border, the source with knowledge of Phantom's operations said. As the pair barreled north, Ramos used the driver's phone to message other people close to Phantom and warn them of what had happened, the source said. He kept the specifics vague, and it wasn't clear whether Ramos was being overdramatic or not. He hoped he could see a lawyer and put this behind him; Ramos even thought he could keep the business afloat, the source said.
"Ramos is the eternal optimist," the source added. "He knew the situation was grave, but he refused to accept." Ramos then told the source he was going offline.
Ramos left his driver, and found himself in Bellingham, Washington, a quiet town of 90,000 people just south of the Canadian border. He stopped for food in Over Easy Café, a diner that shares a carpark with a Trader Joe's.
Dressed casually in shorts and a t-shirt, Ramos quietly sat alone among the yellow walls and chairs of the cafe. He faced outward, with his back against the wall, letting him see who else was in the restaurant, Jamie Bohnett, the owner of Over Easy said. It was around 12:30, and not many people were in the cafe, Bohnett added. A local media report said Ramos ate chicken and waffles; Ramos' family member denied that.
Ramos had spent decades building Phantom from a word-of-mouth, cool-to-have gadget, through to a moderate sized business, and eventually a network preferred by organized crime. Now he was on the run, and although it wasn't clear what would actually happen if he managed to cross the border, he could perhaps still get there. For the moment, it was quiet.
Two figures who looked like businessmen entered the cafe and stopped at the bar with menus. They were nervous looking, "hyper," Bohnett added. The men said they weren't ready to order. Shortly after, one of the men went outside for a phone call. Then five or six men entered the cafe and walked over to Ramos. He didn't resist. Instead he stood up, turned around, and the men cuffed Ramos' hands behind his back. It was over.

Illustration: Rebekka Dunlap
After agents arrested Ramos on his way to Canada, authorities shut down the Phantom Secure network itself, and took over more than 180 web domains it used. The Australians, Canadians, and Americans executed 30 search warrants across offices associated with Phantom as well as the homes of criminal users of the phones. In their March 6, 2018 searches, Australian authorities seized over 1,000 Phantom devices.
A few days later, in place of the business-figure stock art that had more recently populated the Phantom Secure website, stood a message from the three law enforcement agencies that had come together to target Phantom, and a small text box where visitors could enter their email address if they wished.
"Domains and handles listed at this website were identified as related to Phantom Secure during a joint investigation involving the Federal Bureau of Investigation, the Royal Canadian Mounted Police and the Australian Federal Police," the message read. "To check if an account is subject to this investigation enter the email address." It is unclear what law enforcement agencies did with any of the information, such as their email and connecting IP address, that Phantom users provided to the site.
The agencies took their victory lap.
"The indictment of Vincent Ramos and his associates is a milestone against transnational crime,” FBI Director Christopher Wray said in a press release published 10 days after Ramos' arrest. “Phantom Secure allegedly provided a service designed to allow criminals the world over to evade law enforcement to traffic drugs and commit acts of violent crime without detection. Ramos and his company made millions off this criminal activity, and our takedown sends a serious message to those who exploit encryption to go dark on law enforcement."
"The action taken in the U.S. directly impacts the upper echelons of organised crime here in Australia and their associates offshore," Neil Gaughan, the Australian Federal Police (AFP) Assistant Commissioner Organised Crime, said in the AFP's own announcement. "Using this equipment, criminals have been able to confidently communicate securely and control and direct illicit activity like drug importations, money laundering and associated serious, often violent criminal offending, yet have remained removed from these criminal acts," he added.
The week after announcing Ramos' arrest, an additional indictment named Gamboa and Poquiz, the Phantom distributors in Los Angeles, as alleged co-conspirators, as well as Younes Nasri from Dubai, United Arab Emirates, and Kim Augustus Rodd from Phuket, Thailand. All remain fugitives. Phantom's CTO was not charged.

In October 2018, Ramos pleaded guilty to running a criminal enterprise that facilitated drug trafficking.
"Are you familiar with the U.S. federal sentencing guidelines?" Ramos later wrote in an email to Motherboard from prison. "Are you also aware of what percent of federal cases end up in a plea bargain or guilty plea and what happens if you actually do go to trial?"
Ramos' family member said, "He was threatened with 25 years to life if he went to trial, that's why he signed the plea bargain."
In a May 2019 sentencing hearing in a San Diego courtroom, Ramos, dressed in a khaki jumpsuit, addressed the judge when asked if he wanted to make any comments.
"Yeah, good morning, Your Honorable Hayes. For the past several months I've been thinking about what I would say when given this chance," he started. "What I can say is the truth and from my heart. I am sorry and accept responsibility for my actions that have led me to where I am today. I apologize to the Court, the government, and anybody that may have been negatively impacted by my conduct. I apologize to my family and thank them for their support. To my wife, I thank you for everything that you do. I love and appreciate you."
"Your Honor, I deeply regret and I am remorseful for my actions and negligence that allowed my company to grow the way that it did. I made mistakes and decisions that I cannot take back. I should have acted more responsibly. As I stand here in your courtroom today with my fate and future in your hands, I ask and hope for your leniency when making your decision when imposing your sentence. I am truly sorry, Your Honor. Thank you," Ramos said.
In an earlier letter to the judge, Ramos wrote, "I would be lying if I said that I wasn't aware of what was going on."
"The reality was that I turned a blind eye and didn't want to face reality. I was making money and providing for my wife and children," he added.
Both Sherman, one of Ramos' lawyers, and Assistant U.S. Attorney Andrew Young agreed that this was an unprecedented case, according to a transcript of the hearing. This was the first time the U.S. had targeted a company for its role in providing a criminal organization with technology to help them "go dark" or evade law enforcement detection of their crimes.
"Now, it is a kind of two-edged sword to be honest," Sherman said, referring to the extraordinary nature of the prosecution against Ramos. Although acknowledging that Ramos should have realized that providing such a service to criminals could do great damage, there wasn't a rule "that would tell him that he was doing something wrong." It's not illegal to sell phones, even to criminals, in and of itself.
But the evidence suggested Ramos was deliberately helping drug traffickers. For lawyers, it may be obvious that selling a phone that you know is being used in some kind of illegal way would fall under a conspiracy law, Sherman elaborated. "I don't think that it was obvious to Mr. Ramos," he added.
Young, on the other hand, made a distinction between someone knowing that something is illegal, and believing that you are not going to get prosecuted for it.
"I think this defendant fell in the latter category," Young said. "He was not prosecuted because he was selling encrypted communications and encrypted devices to criminals. He was prosecuted because he was in agreement with these people providing them the technology that they could use to facilitate their crimes, and the criminals that are spilling into this industry are the most sophisticated in the world."
Young stressed this case wasn't just about encrypted phones. People who may make other tools that criminals could use, such as particular cryptocurrencies, or perhaps elements of the so-called dark web, "are watching what happens here today."
"And they are making decisions based on whether or not they are going to continue to provide these products and technology to criminals and whether it is worth the risk," Young added.

A section of the indictment filed against Ramos and his alleged co-conspirators. Image: Department of Justice.
In December 2017, Judge Hayes sentenced Hanson, the former UFC footballer turned drug trafficker, to 21 years in prison. Now in his remarks building up to delivering Ramos' sentence, Hayes said "The history and characteristics of Mr. Ramos, as with many individuals who come before the court: mixed." He is a gentleman, well spoken, and obviously a very talented businessman and very successful in legitimate employment before this case, Hayes added.
"But at some point he became very successful in the business he was in," and "he was committing crimes by doing it," Hayes continued. "And at some point I have no doubt that he understood what he was doing was criminal;" that is, assisting drug traffickers. Weighing up factors such as the scale of the operation, the fact that Ramos had no prior criminal record, and that many of the people Ramos assisted likely would have committed their crimes with or without Ramos' help, Hayes came to a decision.
The judge sentenced Ramos to nine years in prison.
This was significantly less than the 14 years prosecutors asked for. Ramos may be able to transfer to Canada after five years in an American jail. After release, he will also be barred from engaging "in the employment or profession relating to developing and maintaining encryption services and devices," Hayes said during the hearing.
Multiple sources in and around Phantom did not see a RICO case coming against the company. Some civil legal problems from importing SIM cards perhaps. But not the law used to specifically take down criminal organizations.
"Many people believed that what I was doing was completely legal and that this was a war on privacy," Ramos said in an email from prison. He is currently incarcerated in USP Marion, a medium security jail in south Illinois. Ramos was referring to the wave of attorneys, privacy advocates, and other people interested in his case that he said contacted him after the FBI announced his arrest.
"Nobody actually thought selling to [criminals] was illegal. It isn't in Canada. Or Australia," the source with knowledge of Phantom's operations said. "It is under RICO in the USA."
"If the Kangaroos can't take you down they'll call the big Eagle. And the Eagle can take anyone down," Bruno said.
Serious organized criminals continue to use encrypted phones to communicate, moving from one provider to another as law enforcement agencies chip away at them bit-by-bit. Some drug traffickers used the services of a firm called Ennetcom, before Dutch authorities shuttered it. Other criminals have even gone so far as to create their own encrypted phone companies; firms such as Scottish-based MPC were literally created by and for organized crime.
Law enforcement agencies' operations against the phone companies have escalated too. In March of this year, French police managed to infiltrate Encrochat. But they went a dramatic step further, and pushed malware onto the Encrochat devices themselves, letting investigators read users' messages before they were sent layered in encryption. Authorities obtained tens of millions of text messages, and arrested hundreds of suspected criminals.
In parallel, the use of encrypted or privacy-focused messaging apps has skyrocketed, by criminals but mostly among the wider public. Wickr is a free encrypted messaging app that offers extra features to enterprise customers; Signal is another similar app developed by a non-profit organisation and which also provides the cryptographic code that powers many other encrypted messaging apps, including WhatsApp.
Ramos could have "had a Wickr or Signal before they even hit the scene," Bruno said.
"Had he invested in the right team, structure, management, advisory etc," he added. "But he just wanted to party and drive expensive cars… such a waste."
The Network: How a Secretive Phone Company Helped the Crime World Go Dark syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Google is Rolling Out Maps Interface Changes to Android Auto
Android Auto is entirely a great experience, and it is still improving even though bugs appear sometimes and create disturbances. But, all these have not stopped Google from trying new things and innovations. Currently, Google is rolling out the latest updates that will make Google Maps work much better than before. The new update will help Google Maps interface work better in landscape mode. The new updates include not only the new icons but also an updated user interface. The new icons and the latest user interface will help the search giant bring the app to meet the same standards that other Google apps are meeting.

What are the interface changes and how it works?
With the new Maps interface changes, the users will now find banners and menus floating. In simple terms, all these will no longer remain tied to the app screen’s width, making it much more significant in landscape mode. The banners and menus have been pushed to the screen side as before they used to be stretched the full width to block a major view of Google Maps. Now, the users can stretch the full menu and still can see where they are currently going. However, the new user interface is rolling out through Google Maps download APK. The users can view it through Android Auto on the screens of their phones. It is expected that the standalone app will also adopt the Maps user interface.
So, the question is what is going on currently with Android Auto for phones. Google had announced a year ago to drop that they would drop the phone app in favor of Driving Mode. The company introduced at the time when most of the automobile manufacturing units were looking for ways to attract more tech-savvy users and customers. These automobile manufacturers were competing with the other systems of car infotainment from Apple and other car manufacturers. With time, the company took steps to expand its user base of android auto by launching a mobile app. This mobile app offered similar features for the users who don’t have an in-built infotainment system.
But a few months later, the company rolled its decision back and launched an app separately known as ” Android Auto for Phone Screens. The company said the users could continue using the app with the Android Auto phone screen version. Now, Android Auto and Android Auto for Phone Screens are in the Play Store of Google. Moreover, some of the phones can see both the apps. The reasons behind it seem that Android Auto being the part of Mobile Services of Google, came pre-installed on Android 10 or later devices. The Auto app is used to beam the interface of your car to the hand device of your vehicle regardless it is wired or wireless.
The phone interface of Android Auto always comes secondary to the functionality offered by the car interface of the app. The new app Android Auto for Phone screen acts only as a shortcut to an already existing phone interface in the Auto app, which is older. Once Google introduces the Assistant Driving Mode, then the users will need to use this particular shortcut to experience things like the head unit on their phones. Overall, these new Maps interface changes will help the users to move more options to the left of the map or navigation. It will result in getting much more room for the original map on the display of the device. The new updates have been rolling out to Google Maps and not the Android Auto app, so you will need to update your Maps app if you are using the Android Auto as the standalone app.
Rdx Tango is an avid technical blogger, a magazine contributor, a publisher of guides at Office.com/setup and a professional cyber security analyst. Through her writing, she aims to educate people about the dangers and threats lurking in the digital world.
Source:- Google is Rolling Out Maps Interface Changes to Android Auto
0 notes
Text
It’s Time for the Eternal September to End
A version of this post originally appeared on Tedium, a twice-weekly newsletter that hunts for the end of the long tail.
For nearly 30 years, the internet’s culture has been defined by a corporation’s move that seemed to, without any care about what was left behind, ensure that a sense of order would never again drive the growth of this series of tubes.
This phenomenon is, in many ways, the central tension on which the modern internet is built. And it’s a tension that most people aren’t aware of, even though it is an undercurrent secretly framing our online interactions.
I am, of course, discussing the Eternal September, a 1993 move by AOL to allow its users into the free-for-all that is Usenet. In the decades since, the conflict that move created, although long forgotten today, lingers in the way that technical users and not-so-technical users interact.
And, in too many ways, it is the basis for digital conflicts that have nothing to do with back then and everything to do with right now.
It’s time to retire the Eternal September. Twenty-seven years is long enough.
“September 1993 will go down in net.history as the September that never ended.”
— Dave Fischer, a Usenet user, discussing the start of the Eternal September in 1993, the point at which the chaos created by mainstream interest in the internet began to overwhelm the early discussion forums that originally attracted technical users to computer labs on college campuses and pokey modem connections at homes.

At its root, perhaps we can blame AOL for all of this. Image: sarahe/Flickr
How the Eternal September set the stage for decades of online conflict
For decades, internet culture has struggled with the n00bs. For generations, as new people entered the digital gates, there was an inevitable sneer that awaited them as they hit the onramp.
If you’re not in the know, what do you know?
The internet is, of course, not alone in owning this dynamic. It plays out in all sorts of areas that traditionally have nothing to do with technology: High school, internships, sports teams, organized crime syndicates. The little guy knows nothing and has to work their way up. Most don’t. You get the idea.
But on the internet, we all technically should be on equal ground. After all, knowledge is at our fingertips at all times.
Yet tribalism has long defined the internet. We are built around subcultures upon subcultures, and these subcultures have only hardened over time, creating shells of insularity that have proven impenetrable.
And perhaps its most notable form came about in the mid-1990s, when the “Eternal September,” a concept involving the n00bs taking over Usenet, took hold. For those who don’t date back to this era, here’s the general gist: Each school year, thousands of new students would flock to Usenet groups for the first time, hoping to find community or learn from the folks already there. The problem was that they were green and didn’t really know much of anything, so they faced rejection until they got the gist.
In September of 1993, AOL added Usenet access, turning a controlled situation of steady ongoing community growth into something of a flood of never-ending n00bs. Suddenly, the social norms that the Usenet community was built around were broken at the seams, never to be repaired.
This was a major communal shift, and one that put early online users on the defensive. To put it simply, people were dismissive of their fellow users based on nothing other than the domain attached to their email address. It was an easy signifier; if you had an AOL.com email address, you were a dork, or beyond saving.
An essay on the commercialization of the internet, written in 1995 by MIT student Christopher R. Vincent, put the situation like this:
As accessing the Internet continues to grow easier for the novice user, it is inevitable that many of these social guidelines will fall to the wayside. This is not to say that new users should be denied access to Internet resources. It has been the first reflex in many newsgroups to flame any user who posted from an online service provider. Some of the larger providers, such as America Online have not received a very warm welcome to the network (note the formation of the alt.aol-sucks newsgroup). This reaction does not necessarily stem from elitism, but from a genuine fear that as more and more users appear, Usenet will fall apart. Indeed, this is a valid concern. The current system is not designed for the commercial-oriented direction the Internet is now taking.
Over time, the close association between AOL and lamers subsided, in part because our online access points evolved toward providers decided by local area, rather than consumer-oriented services.

So many flame wars fought over digital turf. Image: Anthony Cantin/Unsplash
But this dynamic of conflict and savvy emerged in other ways. When web-based communication alternatives emerged to replace Usenet, new types of turf wars appeared: Apple vs. Microsoft; open source vs. proprietary; Something Awful vs. Fark; Digg vs. Reddit; liberal bloggers vs. conservative bloggers; early adopters vs. technical laggards; iPhone vs. Android. You get the idea.
In many ways, these ideological battles of the digital age only found gasoline with the advent of social mediums, which helped to better connect people, but failed to account for the side effects that came with all that.
But the internet, early on, played into this tribalism in ways that allowed it to evolve into something dangerous.
“The newbies could not be forced to accept what we now understand as a central tenet of cyberlibertarianism: that cyberspace, too, was a place, separate from the world, and thus free. For it all to work, all the visionaries needed was for everyone to recognize a small set of self-evident truths.”
— Bradley Fidler, a researcher with the UCLA Computer Science Department, discussing in the IEEE Annals of the History of Computing the rise of what he calls the Eternal October—the understanding that “it is no longer possible to pretend (no matter one’s privilege) that cyberspace can circumvent the politics of civilization.” At the time he wrote this, it was October 2016, ahead of a U.S. election that helped bring some scary forces into the world. I can only imagine how Fidler must feel in October of 2020.

The calendar never stops. Image: Eric Rothermel/Unsplash
Why, in many ways, the Eternal September is still going strong
Look, I’m not going to tell you that we have a constant influx of newbies hitting the internet at all times. That certainly is not what I mean when I describe the Eternal September as an ongoing thing.
But I do think that the spirit that led to the Eternal September becoming a landmark in the first place is still very much there. It has simply taken new forms.
There’s a modern term for what this is called, in fact: Gatekeeping. The idea that, because of your identity or lack of experience, you shouldn’t have access to an online community.
Now, to be clear, there are lots of kinds of gatekeeping in terms of the internet—for example, the technical barriers created by large companies to shape the broader network, whether internet service providers like Comcast or Verizon, or major tech firms like Google or Facebook. Those figures deservedly need their callouts.
But in this case, I’d like to focus on a particular cultural kind of gatekeeping, the kind that leaves people out for reasons of elitism, fear, or simple “othering.”
Earlier this month, a great example of this type of gatekeeping emerged on Twitter when a user claimed that they assumed anyone who used a mouse to program was a junior programmer. That user (rightly) got criticized over it—though I’ll pass on linking the viral tweet, because who needs to add to that kind of drama? But examples that don’t get called out in quite that way abound online, and they represent the way that users tend to focus on their own tribes.
Back in 2017, before our world became even more divided, CBC News columnist Ramona Pringle wrote a piece about how digital tribalism has proven a nasty side effect of highly amplified online echo chambers:
In and of themselves, tribes aren’t inherently bad. We all long to be part of something bigger than ourselves, and tribes fulfill that need. But where we get into trouble is when we introduce borders, which separate my land from your land, and by extension, my tribe from your tribe. When borders are violated, we fight. This, in broad strokes is the root of all war.
The Eternal September, in many ways, was the opening salvo in decades of division on the internet. And in the years since, it has only gotten worse.
In many ways, we understand the people around us even less than we did a few years ago. We aim for the jugular instead of the handshake. And by the time the word “compromise” is thrown around, it’s already too late. It’s a sign of weakness.
It is perhaps sad to think about, considering the early internet was built around utopian dreams. But it’s where we are. I’ll let you draw the through line between ’90s programmer/IT elitism and some of the internet’s modern day problems, because ultimately all those programmers helped lay the foundation for today’s tech infrastructure.
I’m still idealistic that some of that utopian spirit is out there, if you know where to look. But I wonder if, in the big fight for protecting netiquette, the early internet set a bad example for all the people that came after, who jumped in not looking for help, but looking for a fight. The initial separation between the normal and the technical that the Eternal September fostered underlined the tribalism that other internet users follow without even thinking about it. It discourages people from taking part in communities—especially those underrepresented in STEM fields—and sows the kinds of division that attract users to misinformation.
And I wonder if the same types of users who criticized the n00bs way back when are the same folks who can help get us back—by setting an open-arms example that other communities can follow.
At a time when Godwin’s law is less an observation and more a genuine worry, perhaps there are bigger fish to fry than whether or not someone asked a technical question the right way … and those technical users might need to shift their plan of attack accordingly.
“We need to make sure that Rust is prepared to welcome people who are just learning about Rust today. We don’t want anyone to feel like they’re late to the party.”
— Tim McNamara, a software developer and writer who focuses on the Rust programming language, making a case for leaning into the Eternal September, as far as the Rust community goes. It’s a refreshing take from someone in a technical community, and an approach that others should follow.
So, you might be wondering: Why write about this topic, and why now?
Honestly, what got me thinking about it was one specific reaction to a recent piece I wrote about the mainstream demise of FTP. I aimed really broad with that piece, because honestly, that’s usually who I write for—someone who knows something about technology, but who doesn’t know everything and is curious about learning more.
Functionally, the point of my piece was that plain vanilla FTP is on its way out, a vestige of the past for the vast majority of people, thanks to its forthcoming removal from major web browsers. But there are people in narrow spaces who likely will never stop using it—or, who choose not to stop.
While I can get technical, I generally write for regular people who know a thing or two about technology but who, perhaps, aren’t engineers.
And well, this user was a technical user in a highly technical role. And they decided to mock it for not covering specific technical cases where it might persist, rather than spending five seconds considering that they may not be the target audience for this piece. Cockroaches are everywhere—you don’t have to tell me.
I’ve seen this with other things we’ve written as well. Last year, I ran a piece about OS/2’s continued use on the NYC subway system, and I spotted a reader who got upset because we focused on the obvious novelty of a vintage operating system being used in a high-profile way, rather than focusing on the low-level technical aspects that may appeal to that specific user but may go over everyone else’s heads.
I get it. You might get upset if you dive into this with the expectation that we’re going to talk about code or infrastructure on here, and that’s not what you get.
But the reason that technology content is often written more broadly is because, well, writers often want to open up the gates and encourage people to take a deeper look into tech. As much fun as it is to do a deep technical dive into the nuances of how a system is designed, there is a deep threat of losing people if you go too deep without explaining why they should care.
Tying back to our discussion of the Eternal September in this piece, I would also like to make a broader point: We have to figure out a way to bridge the gap between technical and non-technical users online. To pretend that there isn’t room to offer a helping hand, or that we can just focus on our own tiny bubble, just isn’t working anymore.
In September of 1993, well-established users who felt their territory was being encroached on by people who didn’t earn their place in the digital culture reacted by being inhospitable to those users.
It’s nearly three decades later, and in the years since, tech has very much won. Our world has been redefined by it, in ways large and small. And while technical corners can and should exist, we should no longer pretend that technical users have a monopoly on these stories.
And, honestly, given the way that technology has negatively affected the lives of so many, we need to do a better job explaining it to the average person, so they have a chance to grab a hold of the ways that algorithms define what we see online, or how automation might reshape our lives and careers, in ways good and bad.
The Eternal September is over. We’re well into October now. We need to open up the gates.
It’s Time for the Eternal September to End syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
AYA Analytica financial health memo March 2019
As of March 2019, this regular podcast is available on our Andy Yeh Alpha fintech network platform.
Congresswoman Alexandria Ocasio-Cortez proposes greater public debt finance with minimal tax increases for the Green New Deal. Congresswoman Alexandria Ocasio-Cortez proposes greater public debt finance with minimal tax increases for the Green New Deal. In accordance with the modern monetary theory, the central bank can print money to support greater government expenditures without tax increases as greater labor participation helps close the economic output gap. In reality, however, the modern monetary theory seems bizarre to many eminent economists such as Paul Krugman and Lawrence Summers. For the fiscal year 2019-2020, the Trump budget proposal would increase defense expenditures by 5% with 30% budget cuts to health care and environmental protection. For better border security and immigration, Trump asks for another $5 billion public finance to fulfill his campaign promise of a southern border wall.
The Trump $4.75 trillion budget plan has a slim chance of passing through the Democrat-majority House. All these fiscal details set the stage for another acrimonious battle between Trump and Congress. Alternatively, the Sargent-Wallace monetarist arithmetic analysis suggests that the government would have to tolerate higher inflation when the central bank raises seigniorage taxes on money supply growth to absorb any discrepancy between new budget deficit and public bond issuance. The subsequent Federal Reserve interest rate adjustments may thus inadvertently offset the positive economic effect of fiscal stimulus that the Trump administration proposes in the current budget deal.
OECD cuts the global economic growth forecast from 3.5% to 3.3% for the fiscal year 2019-2020. OECD cuts the global economic growth forecast from 3.5% to 3.3% for the fiscal year 2019-2020. The global economy suffers from economic protraction and uncertainty amid the recent Sino-U.S. trade and Brexit standoffs. OECD downgrades real GDP growth rates from 6.5% to 6% for China and from 1.5% to 1% for Europe. The Chinese Xi administration seeks to assuage U.S. concerns about the bilateral trade deficit, unfair technology transfer, and intellectual property protection. Meanwhile, the British May administration needs to delay Brexit to buy time for a plausible second referendum on whether the U.K. should leave the European trade bloc. These trade issues cloud macroeconomic momentum in Europe and East Asia. Several chief economists recommend the European and Asian central banks not to follow the Federal Reserve interest rate hikes too soon. To the extent that these non-U.S. central banks decelerate the global financial cycle with less hawkish monetary policy decisions, Europe and East Asia can insulate themselves from volatile exchange rates, stock market gyrations, and cross-border capital flows that might arise from the next Federal Reserve interest rate adjustments. The subsequent international interest rate hikes are likely to reflect recent upticks in consumer confidence, wage growth, and core inflation.
America seeks to advance the global energy dominance agenda by toppling Saudi Arabia as the top oil exporter by 2024. America seeks to advance the global energy dominance agenda by toppling Saudi Arabia as the top oil exporter by 2024. The International Energy Agency (IEA) now forecasts that U.S. crude oil exports will double to 9 million barrels per day by 2024. This U.S. crude oil production surpasses Russian shipments and may eventually overtake Saudi exports. The same IEA report shows that global oil demand can grow by 1.2 million barrels per day year-in-year-out through 2024. In recent times, U.S. State Secretary Mike Pompeo meets with top oil executives to help the Trump administration boost oil exports to Asia with draconian economic sanctions on Iran in the form of crude oil embargoes. This outreach represents a significant new effort to achieve American energy dominance that helps enhance the economic prospects of U.S. oil and natural gas. This effort wins success and support from China, Japan, and South Korea with more purchases of U.S. oil and gas units. In contrast to greater U.S. crude oil production, Saudi Arabia seeks to drain global supply glut to support higher oil prices by cutting oil exports to 7 million barrels per day while the Saudi oil output remains well below 10 million barrels per day.
Fed Chair Jerome Powell answers CBS News 60 Minutes questions about the recent U.S. economic outlook and interest rate cycle. Fed Chair Jerome Powell answers CBS News 60 Minutes questions about the recent U.S. economic outlook and interest rate cycle. Powell views the current U.S. economic outlook as a favorable one. The federal funds rate hits the neutral threshold where the U.S. economy operates near full employment with low inflation. Powell reiterates the *patient* approach to further raising the interest rate as the U.S. economy grows at a moderate pace. Although about 7 million Americans fall behind their auto loan payments and retail sales decline at the highest pace in the post-crisis period, Powell remains positive about U.S. economic growth in 2019-2020. As the U.S. real GDP growth rate increases above 3%, there are healthy upticks in both consumer confidence and wage growth. In light of the recent Sino-U.S. trade and Brexit negotiations, Powell considers the biggest macro risk to be a probable economic output slowdown in China and Europe. Powell considers the U.S. financial system to be more resilient with high capital buffers that help absorb extreme losses in rare times of severe financial stress. The Federal Reserve is independent in the generic sense that the monetary authority needs to execute monetary policy decisions in a strictly non-political way.
Senator Elizabeth Warren proposes breaking up tech titans such as Facebook, Apple, Microsoft, Google, and Amazon (FAMGA). Senator Elizabeth Warren proposes breaking up tech titans such as Facebook, Apple, Microsoft, Google, and Amazon (FAMGA). These tech titans have become too dominant and so tend to leverage their market power to squelch competition to the detriment of consumers. In addition to bulldozing free market competition, these tech titans use private user information for profits, tilt the playing field against small-to-medium enterprises, and thus stifle R&D innovation as their M&A deals encapsulate niche competitors. For better scale economies and network effects, several strategic M&A examples include the recent acquisitions of Instagram, Whatsapp, and Oculus (by Facebook), DoubleClick, Waze, and Nest (by Google), Whole Foods and Zappos (by Amazon), and Shazam, Texture, InVisage, Regaind, and Lattice Data (by Apple). Warren further proposes to bar these top platform orchestrators (FAMGA) from sharing private user data with third parties. Under the Warren proposal, small tech startups would have a fair shot to sell their products on Amazon without the fear of facing fierce competition from Amazon and its affiliates; Google could not smother competitors by demoting their products and services on the Internet search engine; and Facebook would face real pressure from Instagram and WhatsApp to improve the user experience with better privacy protection.
U.S. tech titans now increasingly recruit PhD economists to help solve business problems. U.S. tech titans now increasingly recruit PhD economists to help solve business problems. These tech titans include Facebook, Amazon, Microsoft, Google, Apple, Netflix, and Twitter (FAMGANT). PhD economists exhibit at least 2 critical knowledge-intensive skills that can contribute to effective business solutions. First, many economists can apply effective empirical methods and quantitative tools to ferret out causal relations in business data. Second, PhD economists can understand the useful design of both effective incentives and market mechanisms for better business optimization. In practice, these economists help demystify many empirical puzzles in the tech sector. For instance, some economists empirically find that Uber Express Pool may inadvertently draw in active users from other Uber products without growing the full Uber user base. Also, several other economists show that eBay tends to syphon off people who would have come through organic search when the online auction website advertises on Google. Moreover, some recent economic research demonstrates that many African-American Airbnb users experience rampant racial discrimination. If tech platforms involve matching users or businesses, market design economists can likely help guide these decisions. Modern examples of disruptive platform design include Amazon, Airbnb, Tinder, and TripAdvisor etc. If scale economies are important for the business, major mergers, acquisitions, and exclusive deals may dramatically alter the strategic industry structure and market environment. For instance, Apple and Alphabet are the dominant duo in the iOS-Android market for mobile devices; Microsoft remains a primary software market player with its Office Suite and Windows operating system; Intel and Qualcomm specialize and dominate in the tech-savvy market for microchips; Google acquires 90% of U.S. online search traffic; Facebook extracts hefty profits in social media advertisements; and Netflix retains key niches in the lucrative business of high-speed original video content distribution. If tech companies need to analyze large-scale user data to make better business decisions, econometricians can apply logistic regressions, panel estimation methods, and time-series models etc to derive informative business insights into user behaviors, product reviews, and customer interests and preferences. Smart tech data analyzers include Amazon, Apple, Facebook, Twitter, eBay, PayPal, and IBM etc. In stark contrast to doctors, engineers, and lawyers who may focus on specific mechanical details and techniques, most economists focus on the bigger picture when they implement empirical methods to solve practical business problems. On balance, most economists can see both the trees and the forest in critical business decisions when push comes to shove.
U.S. trade envoy Robert Lighthizer recommends America to require regular touchpoints to ensure Sino-U.S. trade deal enforcement. U.S. trade envoy Robert Lighthizer recommends America to require regular touchpoints to ensure Sino-U.S. trade deal enforcement. America has to maintain the threat of tit-for-tat tariffs on Chinese goods for many years even though the Trump administration seeks to strike a new agreement with China to end the prohibitively costly Sino-U.S. trade war. U.S. trade negotiators and lawmakers need to monitor-and-enforce Chinese compliance with the new trade rules. The Trump administration aims to eradicate the $350 billion bilateral U.S. trade deficit. In response, the Chinese Xi administration offers to buy $1.2 trillion U.S. goods and services over the next 6 years. Also, the Trump team plans to deter the Chinese government from forcing U.S. tech companies to involuntarily transfer trade secrets, tech advances, and other major intellectual properties such as patents, trademarks, and copyrights. On balance, tariffs remain an important tool for the Trump administration to push China to initiate structural trade policy changes in light of the specific perennial enforcement issue. Due to few major surprises, most U.S. stock market indices such as S&P 500, Dow Jones, and Nasdaq remain steady after the congressional testimonies by U.S. trade envoy Robert Lighthizer and Federal Reserve chairman Jerome Powell.
CNBC stock host Jim Cramer recommends Caterpillar and Home Depot as the current U.S. bull market is likely to continue in light of the recent Fed Chair comments. CNBC stock host Jim Cramer recommends Caterpillar and Home Depot as the current U.S. bull market is likely to continue in light of the recent Fed Chair comments. Fed Chair Jerome Powell reaffirms a patient approach to U.S. interest rate adjustments. In his biennial congressional testimony, Powell suggests that there are both economic crosscurrents and headwinds in the U.S. economy. Although the U.S. economic outlook remains solid, these crosscurrents and headwinds (such as the Sino-American trade and Brexit negotiations) may conflict with the Federal Reserve dual mandate of maximum employment and price stability. Economic policy uncertainty revolves around optimal Treasury debt positions, U.S. government budget decisions, and near-term political considerations. Specifically, Powell reiterates the Federal Reserve plan for balance sheet shrinkage with at least $1 trillion bank reserves through the U.S. real business cycle. In response, CNBC stock host Jim Cramer recommends well-known stocks such as Caterpillar and Home Depot in light of the patient Federal Reserve monetary policy stance. These stocks tend to lose hefty market valuation over the Christmas season. As the Federal Reserve switches from a hawkish monetary policy stance to a dovish one, the current U.S. bull market can elevate asset prices in stocks, bonds, and real estate properties.
Uber seeks an IPO in close competition with its rideshare rival Lyft and other tech firms such as Slack, Pinterest, and Palantir. Uber seeks an IPO in close competition with its rideshare rival Lyft and other tech firms such as Slack, Pinterest, and Palantir. Uber expects to complete one of the largest tech IPOs with $120 billion firm valuation in April 2019. Both Uber and its rideshare rival Lyft announce their recent S-1 confidential paperwork as of December 2018. With $50 billion taxi reservations and $11 billion net revenue, Uber runs a rideshare user network that is more diverse than the Lyft counterpart. As a global tech-savvy transportation company, Uber now operates in more than 70 countries with probable stock market valuation as high as $120 billion (well above its current $76 billion private market valuation). As a smaller rideshare tech firm, Lyft seeks stock market valuation of $20 billion to $25 billion (well above its current private market valuation of $15 billion). With these astronomical stock market figures, both companies can handle their net losses below $1 billion per annum. SoftBank Vision Fund and Toyota Motor Corp are now part of a consortium of investors that invest $1 billion in the Uber autonomous car unit. The current IPO proposal serves as a major strategic move for Uber to garner greater capital.
Lyft seeks to go public with a dual-class stock ownership structure that allows the co-founders to retain significant influence over the rideshare tech unicorn. Lyft seeks to go public with a dual-class stock ownership structure that allows the co-founders to retain significant influence over the rideshare tech unicorn. Within this dual-class structure, Class A shares follow the one-share-one-vote rule for new investors, whereas, Class B shares empower the co-founders John Zimmer and Logan Green and their executive managers to have 20 votes per share. The co-founders and their executive team may end up owning well more than 27% of equity stakes with near-majority control. The dual-class structure has become prevalent among U.S. public companies such as CBS, Comcast, Facebook, Ford, Google, News Corp, Nike, Snap, and Viacom etc. The co-founders retain significant influence over most matters that require shareholder approval, such as director elections and significant corporate transactions from M&A deals and capital investment projects to R&D expenditures and other asset sales. Harvard law professor Lucian Bebchuk criticizes the dual-class stock ownership structure. The probable costs of a lifetime lock on control tend to be especially large when the co-founders are young at the time of the IPO. The costs of inferior leadership can substantially rise when the co-founders fail to address dynamic changes in the business environment. This concern further aggravates when the dual-class structure enables a transfer of founder control to an heir who might be unfit to lead the company. Many dual-class structures allow controllers to substantially reduce their fraction of equity capital over time without relinquishing control, and controllers often do so to diversify their stock portfolios to fund other investment projects. When the wedge between the interests of controllers and public investors grows over time, the agency costs of a dual-class structure are likely to increase. Corporate controllers with a small fraction of equity capital have perverse incentives to retain an inefficient dual-class structure. The reason is that these controllers would capture only a fraction of efficiency gains (which would be shared by all shareholders), but would fully bear the costs of forgoing the private benefits of control that arise from the dual-class structure. Bebchuk proposes a sunset provision that stipulates the eventual expiration of dual-class structures after a specific period of time such as 10 years or 15 years. This proposal empowers founders to retain their lock on corporate control with minimal short-term market pressure in the early-IPO stage of their entrepreneurial efforts; whereas, the dual-class stock ownership structure should eventually converge toward the more efficient first-class structure.
Pinterest files a $12 billion IPO due in mid-2019. Pinterest files a $12 billion IPO due in mid-2019. This tech unicorn allows users to pin-and-browse images through its social media app and website. Pinterest seeks stock market valuation of at least $12 billion that would match the current valuation of Snap Inc, which owns another photo-centric social media app Snapchat. Pinterest differentiates itself from Facebook, Instagram, Twitter, and Snapchat etc because this new tech unicorn empowers active users to pin their recent real-life photos that hyperlink to external websites. For instance, a Pinterest user can pin her photo of a recent restaurant meal that links to an external website where others can find the recipe for the same meal. In contrast, most other social media apps and websites prefer to retain active users within their respective digital platform ecosystems. Pinterest has grown its user base to 250 million active users per month as of February 2019; whereas, Facebook keeps 2 billion active users, Instagram has 1 billion, Twitter has about 320 million, and Snapchat has almost 300 million as of early-2019. As Pinterest moves fast to disrupt the image search space via a $12 billion IPO, several other rideshare rivals Lyft and Uber seek opportunities to go public too.
A physicist derives a mathematical formula that success equates the product of both personal quality and the potential value of a given subject matter. A physicist derives a mathematical formula that success equates the product of both personal quality and the potential value of a given subject matter. As a Northeastern University expert on network theory, Albert-Laszlo Barabasi comes up with this simple and ingenious formula when he learns the transformative life stories of numerous people who achieved late-in-life successes. For instance, a U.S. analytical chemistry professor, John Fenn, conducted his revolutionary research on electrospray ionization at the age of 67 (which contributed to the quick mass measurement of viruses and ribosomes with incredible accuracy) and then received the Nobel Prize in Chemistry for this major contribution at the age of 85. Also, English actor and director Alan Rickman had his first movie role at 46; Julia Child brought French cuisine to the American public in her first TV show at 50; Yitang Zhang derived a revolutionary mathematical proof in his first journal publication and later earned full professorship with several special achievement awards at 57; and Nelson Mandela emerged after 27 years in jail and then became the President of South Africa at 76. The Barabasi success formula is S=Q*r where S denotes the success of a new deal, or the impact of a major discovery, which equates the product of the Q-factor (innate talent) and the value of a random idea r.
A highly creative and smart person may encounter some ordinary random idea, and this combination leads to a mediocre outcome. Conversely, an average person may come across a great idea, and this combination still leads to a mediocre result. Then there are perfect-storm instances where the idea and its creator both shine. When the Q-factor and the value of a new idea are both high, they enhance each other and result in a major breakthrough. A classic example is the revolutionary Apple iPhone that integrates the flash of genius in Steve Jobs, an Internet-connective telephone, a music player, and a digital camera into one mobile device. What illuminates the Barabasi success formula is the realization that if a person has an insufficiently high Q-factor in one vocation, he or she might want to consider switching to a different field where it is attainable to get an exceptionally high Q-factor. Amazon founder and chairman Jeff Bezos had considered becoming a physicist when he studied at Princeton, and later he realized that this ambition was too remote; as a result, he became an investment banker early in his career and then founded Amazon as an e-commerce startup, and the rest was history. Overall, these life lessons suggest that one should combine his or her high Q-factor with a healthy quantity of good ideas before the next eureka moment.
We may need to reconsider the new rules of personal finance. We may need to reconsider the new rules of personal finance. First, renting a home can be a smart money move, whereas, buying a home cannot always be a good investment. It can be reasonable to rent a home without opportunity costs such as down payments, maintenance fees, property taxes, interest expenses, and insurance premiums etc. Investing these opportunity costs in stocks and bonds may yield better long-term returns. Second, money is an important resource for long-term investment, and time is another key element of successful wealth accumulation. It takes time for compound interest to exponentially grow at the 6%-11% stock market annual rate of return. Third, it would be wiser to invest retirement finance in some stock market index to earn the average equity premium around 5%-9% in recent times. With longer lifespans and lower bond returns, stock market investors can reap higher rewards. Fourth, it is important to demystify the conventional wisdom that student loans are good debt because education pays handsomely in the form of higher future wages. However, only postgraduate degrees provide the higher *incremental* wage boost than college degrees. We should consider these new rules of personal finance during the recent Trump stock market rally.
Tech companies seek to serve as quasi-financial intermediaries. Tech companies seek to serve as quasi-financial intermediaries. Many retail traders can now list items for sale on eBay and then acquire these items economically on Amazon for direct shipments when busy buyers place orders on eBay. These retail traders serve as information arbitrageurs and clip spreads between the divergent prices on Amazon and eBay. This information arbitrage occurs often enough to be a viable business. In a practical sense, this information arbitrage proves to be a valuable service at a market price. Time is finite and human attention is precious such that this intermediary service often turns out to be worthwhile for better immediacy and convenience. In a similar vein, the online search website for real estate, Zillow Group, now attempts to serve as a quasi-financial intermediary for home purchases and mortgage loans. Zillow brings back its co-founder and former CEO Rich Barton to lead this ambitious transformation. Zillow transforms how Americans buy and sell their real estate properties as the tech platform uses both big data analysis and artificial intelligence to change how these residential owners and investors shop for homes with mouse clicks and satellite maps. Busy buyers pay for immediacy and convenience when they shop for homes on Zillow. In addition to Amazon-eBay retail arbitrage and Zillow real estate, Apple and Goldman Sachs enter into a strategic alliance to expand the joint credit card business. Apple pairs the new credit card with key iPhone features such as Face ID to better serve its active users. This credit card piggybacks on the Mastercard network and offers 2% cash rewards for the vast majority of U.S. online purchases. Beyond cash bonuses, Apple and Goldman Sachs hope to leverage the Wallet app for tracking account balances and rewards for better personal finance management. Like Goldman Sachs, big banks shift operational focus from their prior reliance on capital-intensive risk businesses to tech platforms for their tech-savvy clients. In light of financial distress and post-crisis regulation, these banks prefer to build online platforms for their institutional clients to trade bonds, funds, and other complex securities. The banks accumulate fees and commissions when these transactions take place for the mutual benefits of both banks and institutional investors themselves. This fresh logic explains why Apple and Goldman Sachs work together to strengthen their credit card business. Nowadays Amazon-eBay arbitrageurs and tech titans such as Apple and Zillow seek to serve as quasi-financial intermediaries.
Global economic uncertainty lurks in an even thicker layer of mystery. Global economic uncertainty lurks in an even thicker layer of mystery. This uncertainty arises from Sino-U.S. trade tension, Brexit fallout, monetary policy normalization, and financial fragility due to U.S. interest rate and greenback appreciation. As the Trump administration makes positive progress on Sino-U.S. trade negotiations, most economic pundits and experts expect U.S. monetary policy normalization to continue in 2019-2020 as financial asset returns and factor premiums reflect structural changes in the interest rate and dollar valuation. Also, the U.K. parliament may initiate a major delay or a second referendum on Brexit. At the turn of the new century, big data analysis, cloud computation, artificial intelligence, and robotic automation displace many workers and so irrevocably alter the tech structure of employment. Globalization is another powerful force. The free movement of goods, services, and people transforms economic integration and global value creation. This economic trend intensifies competition in the labor market, and the middle class faces higher wage growth, price inflation, human capital depreciation, and unemployment in OECD countries. In the financial sector, deregulation and capital account liberalization boost international capital flows well above trade. Post-crisis fintech advances such as crowd funds, peer-to-peer loans, and shadow banks shed skeptical light on the role of financial intermediaries in the monetary transmission mechanism. As a result, many central banks encounter real wage stagnation, deterioration in both income and wealth distribution, and a major slowdown in productivity growth. E-commerce tech titans such as Amazon and Alibaba now induce frequent, accurate, and competitive retail price adjustments. These faster price adjustments effectively flatten the Phillips curve or the inexorable and mysterious trade-off between inflation and unemployment. This macroeconomic transformation coincides with the new cycle of U.S. interest rate hikes. Through cross-border capital flows and exchange rate gyrations, U.S. monetary policy changes and trade imbalances can create global financial cycles that radically distort credit conditions in European and Asian economies. Central banks now need to adopt a cautious, gradual, and data-driven monetary policy approach for sound risk management in light of substantial macro uncertainty. Also, central banks need to monitor a wide variety of macroprudential indicators such as asset prices, risk premiums, credit supply shocks, and other financial imbalances. To the extent that both global capital flows and external supply-side shocks aggravate exchange rate volatility, central banks need to preserve greater price flexibility and monetary autonomy. When push comes to shove, the law of inadvertent consequences counsels caution.
AYA finbuzz podcast March 2019
AYA Analytica is our online regular podcast and newsletter about key financial news, market insights, economic issues, and stock investment strategies on our Andy Yeh Alpha (AYA) fintech network platform. With both American focus and international reach, our primary and ultimate corporate mission aims to help enhance financial literacy, inclusion, and freedom of the open and diverse global general public. We apply our unique dynamic conditional alpha investment model as the first aid for every investor with profitable asset investment signals and portfolio strategies. In fact, our AYA freemium fintech network platform curates, orchestrates, and provides proprietary software technology and algorithmic cloud service to most members who can interact with one another on our AYA fintech network platform. Multiple blogs, posts, ebooks, analytical reports, stock alpha signals, and asset omega estimates offer proprietary solutions and substantive benefits to empower each financial market investor through technology, education, and social integration. Please feel free to sign up or login to enjoy our new and unique cloud software services on AYA fintech network platform now!!
Please feel free to follow our AYA Analytica financial health memo (FHM) podcast channel on YouTube: https://www.youtube.com/channel/UCvntmnacYyCmVyQ-c_qjyyQ
Please feel free to follow our Brass Ring Facebook to learn more about the latest financial news and stock investment ideas: https://www.facebook.com/brassring2013
Free signup for stock signals: https://ayafintech.network
Mission on profitable signals: https://ayafintech.network/mission.php
Model technical descriptions: https://ayafintech.network/model.php
Blog on stock alpha signals: https://ayafintech.network/blog.php
Freemium base pricing plans: https://ayafintech.network/freemium.php
Signup for periodic updates: https://ayafintech.network/signup.php
Login for freemium benefits: https://ayafintech.network/login.php
We create each free finbuzz (or free financial buzz) as a blog post on the latest financial news and asset investment ideas. Our finbuzz collection demonstrates our unique American focus with global reach. Each free finbuzz provides deep insights into numerous topical issues in global finance, stock market investment, portfolio optimization, and dynamic asset management. We strive to help enrich the economic lives of most investors who would otherwise engage in financial data analysis with inordinate time commitment.
Please feel free to forward our finbuzz to family and friends, peers, colleagues, classmates, and others who might be keen and abuzz to learn more about asset investment strategies and modern policy reforms with macroeconomic insights.
Do you find it difficult to beat the long-term average 11% stock market return?
It took us 20+ years to design a new profitable algorithmic asset investment model and its attendant proprietary software technology with fintech patent protection in 2+ years. AYA fintech network platform serves as everyone’s first aid for his or her personal stock investment portfolio. Our proprietary software technology allows each investor to leverage fintech intelligence and information without exorbitant time commitment. Our dynamic conditional alpha analysis boosts the typical win rate from 70% to 90%+.
Our new alpha model empowers members to be a wiser stock market investor with profitable alpha signals!! This proprietary quantitative analysis applies the collective wisdom of Warren Buffett, George Soros, Carl Icahn, Mark Cuban, Tony Robbins, and Nobel Laureates in finance such as Robert Engle, Eugene Fama, Lars Hansen, Robert Lucas, Robert Merton, Edward Prescott, Thomas Sargent, William Sharpe, Robert Shiller, and Christopher Sims.
Andy Yeh Alpha (AYA) fintech network platform serves as each investor's social toolkit for profitable investment management. AYA fintech network platform helps promote better financial literacy, inclusion, and freedom of the global general public. We empower investors through technology, education, and social integration.
Andy Yeh AYA fintech network platform founder Brass Ring International Density Enterprise (BRIDE)
We should not conform to this world, but we should allow the renewal of our minds to transform us, so that we can prove what is the good, acceptable, and perfect will of God. Romans 12: 2
0 notes
Text
10 Modern Tech Disrupting Digital Marketing [Infographic]

Technology is sometimes a blessing but most of the time a challenge. Organizations and marketers are suffering to most of the time to play catch-up instead of benefiting from technology. 10 Modern Technologies which are Disrupting Digital Marketing and still try to find their way to benefit everybody.
Digital Marketing is not anymore like traditional marketing. In the era of digital transformation happening everywhere, marketers want a proof of their investment. Most of the people are scared of the question, what is this or what does it mean? We face it every day in our life that we get confronted with technology or terms which we don't know what they stand for. Sometimes terms are misleading, sometimes it is only the fact that evolution in digital marketing is progressing in light speed. Let's have a look into 10 modern tech terms challenging us every day and which technology we should keep an eye on for better understanding. The infographic talking about 10 technologies Disrupting Digital Marketing below was put together by Spiralytics who offers data-driven marketing.
1. Big data
Big data is the biggest game-changing opportunity and paradigm shift for marketing since the invention of the phone or the Internet going mainstream. Big data refers to the ever-increasing volume, velocity, variety, variability, and complexity of information. Big Data improves data collection for accurate and personalized campaign targeting Get insights about your campaign performance Future applications include the creation of attribution models to identify the contribution of each channel on the total conversation, programmatic advertising, and optimization of video marketing
2. Artificial Intelligence
"Artificial intelligence marketing (AIM) is a form of marketing leveraging artificial intelligence concept and model such as machine learning and Bayesian Network to achieve marketing goals. The main difference resides in the reasoning part which suggests it is performed by computer and algorithm instead of human." - Wikipedia Finds useful patterns to gain insights into marketing numbers for better ad targeting and consumer behavior projection Also used by search engines to interpret queries for relevant results Al scripts for apps may enhance online customer chat platforms to learn more customer information, help solve problems, and find solutions on demand. Al-powered technologies can improve customer-centric strategies through better trend analysis, enhanced customer profiling, and even more sophisticated personalization strategies.
3. Machine Learning
Machine Learning gives computers the ability to learn from data and create accurate predictions, without explicit programming. When it comes to the marketing world, the promise of machine learning is in quickly finding hidden patterns in massive amounts of consumer data, Big Data and Machine Learning go hand in hand. Used In audience segmentation and integrated Into analytics to detect anomalies and do real-time analysis of large datasets Machines can make automated content creation possible. Banner ads, email campaigns, or social media posts can be generated and applied to different formats for different channels. As performance is being collected, headlines may automatically be changed to match the content that is performing well.
4. Bots
"When it comes to marketing, automation is a powerful tool that allows you to get more done in less time. Recently, marketing bots have become a popular form of automation. A bot is basically software that you can program to carry out a certain set of actions all on its own." - says Neil Patel about Bots Not only an effective way to communicate but is also a 24x7 two-way channel between consumer and brand. Commonly used in the sales and service departments and provides search and discovery and product recommendations May soon be able to remind consumers to replenish a purchase through voice assistants Chatbot communication may start and from one device to another
5. Voice Search
Voice users are asking your company to give them a reason to buy your product or service. The tech-savvy business that wants to increase their revenue and sales, voice search offers a smart way to do it, it's only a matter of bringing voice search optimization into your digital marketing strategy mix. Marketers utilize voice search to gather more information about the devices' users through their search engine queries, requests for specific information, application launches, selections, or voice dial. It may soon be integral to SEO. Marketers need to learn how to optimize keywords based on how it is used in a conversational manner rather than as a typed-up query. It has the potential to upend paid search and organic content strategy practices.
6. Virtual Reality and Augmented Reality
Virtual reality and augmented reality are immersive technologies which offer significant opportunities for brand promotion and the sale of products and services, but also to engage and retain customers, both B2C and B2B. Both make for an immersive experience. inciting a range of senses and emotions• Both make for an immersive experience. inciting a range of senses and emotions In turn, both offer a unique try-before-you-buy experience that enables consumers to explore a product. engage with the brand, and make the purchase all at the same time. Could bring together the physical store and e-commerce to *completely blur the lines between high street and online shopping experience." Can be used for short-form storytelling to provide interactive experiences around a branded content
7. Internet of Things (IoT) and Wearables
Since IoT technology connects the internet with objects that are ubiquitous in our daily lives, marketers in almost every industry will be able to engage consumers throughout every phase of the customer journey. Wearable technology: it's a buzzword that's incessantly thrown around without much understanding of what it actually is, or what it does. Beyond the fact that these technologies are smart devices that consumers wear and interact with, the full effects have yet to be determined. User to gather more information about its users like their habits and preferences. The more connected devices a user has, the more ways marketers can reach them in a detailed and timely manner. Sensor technology of wearables, which can also be internet-connected, made gaining insights into biological conditions possible. Biometric data may be used to understand a person's interaction with a brand
8. Blockchain
Blockchain Eliminates Digital Marketing Middleman. Digital marketing now utilizes “middlemen” that control the territory between advertisers and users. ... Google also handles the processing of transactions so that the website owner is paid fairly for clicks generated on the advertiser's ad. Marketers can use blockchain to motivate consumers to watch or read advertisements and engage by leaving feedback or tagging friends. Decentralized apps built atop blockchain have the potential to challenge the integrated app platforms by Apple and Android and to support new cooperative economies globally.
9. Beacons
Beacons are small devices that send Bluetooth Low Energy (BLE) or Near Field Communication (NFC) signals to mobile devices nearby. Retailers can use beacons to identify and track people as they visited the retail outlet, providing valuable information to marketers about the past (and possibly future) purchases and segment audience though heat maps of popular products or areas in their shop. Gathers detailed information on customers to optimize store experience and create personalized campaigns based on their movement. E-commerce businesses can use localization todirectly target potential customers in specific.high-traffic locations by putting beacons in establishments and ping out offers. Bridges online and physical presence of businesses to ensure continuity. It can help determine what kinds of campaign capture the consumer's attention as it puts direct and relevant ads into every customer without chasing them down.
10. 5G
5G is the fifth generation of mobile innovation. It's an abbreviation that stands for the fifth generation of cellular wireless transmission. For marketers, it means faster data transmission and reacting faster on customers wishes and communication on the move. Faster connectivity also means faster page load times for low bounce rate and Increased CTR and ROI. May open doors for video ads utilizing VR or AR where advertisers can better showcase their products and services. May give marketers the power to collect consumer data In real-lime for optimized campaigns and improved location-based marketing. These Technologies may affect and benefit Marketing and other business activities including Data Gathering, Personalization, Data Analytics, Targeting and Placements, Content Creation, Customer Service, Content Distribution, and SEO. What is your take on these disrupting Digital Marketing technologies? Share your thought in our commenting section below. Read the full article
#AugmentedReality#BigData#Bots#BusinessChatbots#DubaiArtificialIntelligence#MachineLearning#VirtualReality#Voice-Search
0 notes
Text
Connected enterprise
Why Enterprise City UK is important for all of Manchester, not just the creative entrepreneurs who will make it their base.

Roundtable discussion at the launch of Enterprise City UK at Old Granada Studios, Manchester, 26 April
On Monday last week, the Washington Post carried a headline that read: “This guy convinced cities to cater to tech-savvy millennials. Now he’s reconsidering.”
The article was about one of the fathers of design thinking for cities, Richard Florida, whose book The Rise of the Creative Class influenced the development of creative and tech hubs in cities all over the world.
In his book, Florida had argued that cities in the automated digital world should attract the best young talent in computer programming, engineering, finance, media and the arts so they could grow their economies based on the venture capital and start-up companies the new workforce would produce.
So what was the Washington Post article about? Richard Florida hasn’t suddenly gone anti-tech or anti-city. But he does highlight some things for us to think about. What he came to realise was that there were unintended side-effects. “In places like New York, San Francisco and Seattle,” the article pointed out, “the mostly white, young and wealthy “creative class” has so fervently flocked to urban neighbourhoods that they have effectively pushed out huge populations of mostly blue-collar and often poor or minority residents.”

Zoë Hitchen at Design Manchester’s Great Debate in October 2016: how do we keep the city accessible for new talent?
In other words, their success made their neighbourhoods so expensive that diverse, mixed communities – and poor young artists for that matter – could no longer afford to live or work there. That’s also true of parts of London today and in the Design Manchester public debate that took place in the Bonded Warehouse at St John’s last October, Zoë Hitchen of the BBC User Experience team and the Manchester Fashion Institute raised the same concern for Manchester: how do we keep it diverse and affordable as we become even more successful? At our Great Debate a year earlier at The Whitworth, the architect Dominic Sagar, one of the founders of the Northern Quarter, had made a similar point. Investment in the city is welcome, he said, but “we don't want to become Brandchester or Blandchester and have our spirit squashed.”
In his new book, The Roots of the New Urban Crisis, Richard Florida now says that the clustering of talent and economic assets “generates a lopsided, unequal urbanism in which a relative handful of superstar cities, and a few elite neighbourhoods within them, benefit while many other places stagnate or fall behind.
“Ultimately,” he adds, “the very same force that drives the growth of our cities and economy, also generates the divides that separate us and the contradictions that hold us back.” Florida blames Brexit and Trump on such growing divides.
The rise of the creative class – not the book, but the trend – has delivered rapid growth and progress, but also problems of division.
So what is the answer?
It is to design balanced cities and a balanced economy that offers opportunity, prosperity and safety for all.
The trick is to boom and yet remain diverse, inclusive, open and connected, with affordable housing, good education and a safe public environment, so that the city can continue to attract people, families, business and investment.
The trick is to make sure we have not only a vibrant neighbourhood but a vibrant city and a vibrant region. Developing exclusive, unaffordable bastions is not the strategic vision of the city or the region. In theory at least, the Northern Powerhouse, with its balanced economy thinking, is intended to deliver a more well-rounded and inclusive outcome.
Enterprise City is a catalyst in a bigger picture. It can help to build the pathways and foster the wider collaboration with people and startups and networks throughout the region that are essential to the success of Manchester as a whole.
Enterprise is creating things and making a success of it, so as a concept, Enterprise City is very well suited to a city where talent and industry are as abundant as they are here in Manchester.
Design has a big part to play, because it is at the heart of creative endeavour.
Design is how we connect technology to its users. It is how we make a city work for its residents and visitors. We use design to turn scientific inventions such as graphene into usable products. We design great spaces – and if spaces aren’t great, it’s because they’ve not been well-designed.
Through clothing and graphics and cars and furniture and gadgets – and trainers, design allows people to express their own style and individuality. Design helps people understand information and it helps them to communicate with one another.
Design is the human factor in technology, in enterprise and in cities, because the purpose of design is to think about the user and to provide for the user.
The icons of the digital age – Google and Apple and Facebook – have demonstrated time and again that successful digital enterprise has design at the heart of its thinking and its practice – not only in their products but also in their workspaces and in the cities and districts where they choose to locate their offices.

In a digital world, design is the human factor that is the key to success. One of the reasons for Manchester’s great potential as a city is what Council Leader Sir Richard Leese in Document 16 called “the centrality of design to the Manchester story”.

The 2017 Design Manchester Conference will take place at The Principal on 13 October
We established Design Manchester in 2013 and from 11–22 October this year we will be holding Manchester’s fifth annual design festival. Our Design Conference, at the Principal Hotel on 13 October, is where design professionals and students can listen to some of the greatest designers from Manchester and around the world, showing some of the best and the latest in design. Our Great Debate, which took place here in the Bonded Warehouse last year, will this year be on the opening night, 11 October, with leading figures from design, the city and politics on the panel and a very well informed and opinionated audience as usual. The Design and Print Fair that took place at London Road Fire Station last year will be at Upper Campfield Market from the 20–22 October, with stalls and workshops for families and the general public. And there will be more than 30 other events including music and exhibitions, workshops, symposia and film screenings, at iconic locations throughout the city.
When we started Design Manchester, we always felt that this is a city that can sustain an annual design festival and so far we haven’t been proved wrong. We did not have to invent anything, the culture was here, the art schools are here, the industry was growing quickly. We were of course standing on the shoulders of Tony Wilson and his In The City festival – but he was doing it to attract the music industry to Manchester. These are the reasons that Enterprise City will succeed: firstly because the culture and the talent are here, and secondly because this will help attract different skillsets and finance into the mix.

Green and healthy: Sean Anstee and Andy Burnham make their pitch
Labour’s Mayoral candidate for Greater Manchester, Andy Burnham, talks about a “digital city” and a “green city”. His Tory opponent on 4th May, Trafford Council Leader Sean Anstee, talks about a “cycle-friendly city” and a “healthy city”.
We need to look behind the labels and think about how these ideas are going to achieve their aims. The Bonded Warehouse is a great space, built during the industrial revolution – and now all about innovation. For Enterprise City, is it about spaces like this? We love buildings, buildings are important, but a modern city is not primarily about buildings, or roads, but about networks. Future cities are about people, about how they connect, interact and transact.
Enterprise City knows this. As Mike Ingall said last year, Enterprise City “is about creating so much more than just buildings. It is about providing infrastructure and inspiration so businesses can realise their full potential.”
There are many other great creative spaces and neighbourhoods in Manchester, some old and some brand new, that are all about looking to the future.

The XYZ Building (Cartwright Pickard)
In Spinningfields there’s the amazing XYZ building, also part of the Enterprise City initiative, with its fintech hub and great events, designed by Cartwright Pickard. There is The Sharp Project, a disused old electronics factory, transformed by PRP Architects into a digital content hub with more than sixty companies making it their home – and of course with a great brand and wayfinding by Malcolm Garrett. There’s the BDP-designed Innovation Centre in Manchester Science Park, part of Cisco’s National Virtual Incubator.

The Pilcrow (OH OK! LTD)
There’s the Pilcrow Pub and the new PLANT maker-culture workshops and exhibition space at NOMA created by OH OK! and co-designed with the local community. There’s the new Circle Square being built on Oxford Road; and Manchester Metropolitan University, which has its great digital innovation centre at The Shed, will soon be launching its new International Screen School.
Then of course there’s the Northern Quarter, still edgy and still vibrant — and even the tram stops on St Peter’s Square are becoming usable again.
There is a huge amount going on in the city centre and there are great examples in the wider city region too, from Media City at one end of the scale in Salford to the artist studios in Islington Mill at the other, and great new regeneration projects like Oldham Town Hall and Tameside Mill.

Oldham Town Hall (BDP)
We should look for productive ways of building collaborations between these hubs and spaces and the people and businesses in them to provide a wider range of talent and expertise into what we produce and to build better opportunities for, and supplies of, the talent that we need for our industry and our city to grow.
In Manchester, the Creative & Digital sector is one of the fastest growing drivers of the economy. And across all sectors, of all the economic success stories in the last five years, 87% had ten or fewer employees and were established for between three to five years. (New Economy) So, the biggest engine of growth in Manchester is (1) creative and digital, and (2) new startups.
Creative Review reports in its May issue that more than half of the respondents to its Creative Workplaces Survey identify themselves as being part of the ‘design industry’.
The supply of talent to this engine of growth is one of the big challenges we face. If the outcome of Brexit is that in three years’ time the door closes to recruiting new talent from southern and eastern Europe, that will be a critical problem for the tech industry which could result in a massive talent drain to London, which will certainly spend to attract talent from elsewhere in the UK. We may be growing quickly, but according to Tech City UK, the tech sector in London has more than 300,000 digital jobs currently, and that’s expected to rise by nearly 20% in the next decade. Manchester currently has 63,000 digital jobs. We are in a good position but there is no room for complacency.
This is just one of the reasons why Enterprise City, as part of a holistic strategy for Manchester, is important. To maintain our momentum we need in the next couple of years to significantly increase the number of skilled and talented people who see Manchester as the best option to make their careers: a liveable and affordable city where talent and ingenuity can succeed as well as, and in some respects better, than elsewhere. We do that with infrastructure, policy and narrative, and Enterprise City feeds into all three.
In short, Enterprise City is a great opportunity for creative and entrepreneurial talent, not as the privileged zone separated from less advantaged parts of the city that Richard Florida refers to as the “new urban crisis”, but as a collaborative and open catalyst for growth, with mechanisms to ensure it is connected with other initiatives across the region and with opportunities for continued participation in the mix by new talent, new artists and entrepreneurs – not as employees but as startups and individuals who can’t yet afford high rents but will offer a continued edge of disruption, new thinking and unexpected opportunity. In this context, Project Forward is a fantastic asset for Enterprise City, promising a steady supply and incubation of talent in the creative digital area.
Design can help by supporting incubation and by looking at how Enterprise City is connected to the wider region – and to the food chain that takes raw talent to successful enterprise.
The City, the new Mayor and the Government can support a holistic approach by addressing the barriers to entry, for example by encouraging and supporting more women and diverse communities into the creative & digital sector, by ensuring that creativity, including art and design, are given priority alongside STEM subjects in education and particularly in skills training so that the creative industries have access to the right skills to grow and so that young talent in the area can develop careers that are not going to disappear in the coming wave of automation and artificial intelligence.
The Creative Industries Federation published an excellent creative industries manifesto for the general election yesterday which describes creative employment as resistant to automation and demands that to be eligible for an Ofsted Outstanding rating, a school must teach at least one creative subject, in lesson time.
We should develop mentoring and support programmes within Project Forward and Enterprise City – to inject and support design thinking in the emerging startups, and to develop sector–specific design skills in growth areas such as fintech, cybersecurity, fashion, textiles, screen and many other areas. As Design Manchester we will be keen to help connect Enterprise City to the wider design community in Manchester for mutual benefit, and so that we can all collaborate together to embed design thinking throughout our city.
We practise what we preach, working with our partners the Co-op on schools programmes for creative careers, and with universities and industry on opportunities and pathways. At our festival in October – in addition to the Conference, the Debate and the Design Fair – we will have a wide range of workshops and symposia for different audiences, from architects and professional designers to kids who want to learn coding and design, and sessions on age-friendly design, print techniques and much else besides.
Design, partnership, collaboration, connection and inclusion are key to the region’s success. This is why Design Manchester welcomes this visionary Enterprise City project and we look forward to collaborating with it in the coming years.
1 note
·
View note
Text
Where I Work: Windy Chien
You might not think of knots as being anything other than a way to tie something up or the annoying thing that happens to your necklaces when they get tangled up, but there’s an entire other world out there and it involves fiber artist Windy Chien. After stints at Apple and owning her own indie record shop in San Francisco, Windy found her calling bringing aesthetics to the middle of function, science, and history to highlight what’s most intriguing about knots, and that’s the journey of the line. You may recall she spent 2016 learning a new knot every day of the year for The Year of Knots, which she now displays on her studio walls mixed amongst a sea of works in various stages of progress and size. Today, we pop into her San Francisco studio located on the second floor of the Heath Ceramics tile factory to see her art and space in this Where I Work.
What’s your studio/work environment like?
Serene, cozy, and clean. I’m often playing music and podcasts, and my rescue greyhound, Shelley Duvall, comes with me to the studio each day.
How is your space organized/arranged?
My studio is a private 1000-square-foot space with its own street entrance. It’s a big open space. One wall is all huge windows, and I store my spools of rope and cordage in a long row beneath the windows. Another wall, made of four sheets of plywood suspended above the floor, holds The Year of Knots, which is the project I did in 2016 where I learned one new knot every day of the year. It’s an installation of 366 knots that functions as my palette and main resource, the same way a designer or painter might have a Pantone deck.
Scattered throughout the space are seven pairs of pulleys hanging from rafters off the 20’ pitched ceiling, where I suspend each piece while I’m making it. I raise and lower the works while working, and this is how I take care of my body while enacting the repetitive, physical motions of knotting.
The entire floor is covered in bright white, wall-to-wall, faux fur carpet. I’m a child of the 1970s, so wall-to-wall carpeting is my happy place, but there’s a practical reason for it too: my standard material is white cotton rope, which picks up dirt the second it hits a hardwood floor. With the white shag, I can throw my materials on the floor and know they’ll stay clean.
I’m often working on several commissions at once, along with experimenting on one-off pieces which is my way of thinking with my hands. With that much activity, everything must have a place. I can’t be productive in chaos.
How long have you been in this space? Where did you work before that?
I’ve been upstairs at Heath Ceramics since January 2020. Before that I spent three years in a mid-century police station. My studio there was the old police captain’s office! It was a cool space, but it didn’t have the strong, high ceilings necessary for me to easily make large works, which are all I do nowadays.
Being part of the Heath Ceramics community is a dream come true. Being around like-minded, creative people is incredibly motivating and positive. They have been beyond helpful with sharing resources such as their shipping & receiving department, security, communal kitchen, etc.
If you could change something about your workspace, what would it be?
It’s truly perfect here; the only thing I might eventually consider is a bit more space. I’m going to hire a studio manager this year to handle admin, and am having to think hard about how to have more than one person in this place that feels like my sanctuary.
Is there an office pet?
Yes, my greyhound Shelley Duvall comes with me to the studio every day.
Do you require music in the background? If so, who are some favorites?
I owned/operated an independent record store (Aquarius Records) for 14 years, so my tastes run far, wide, and obscure. Some of my favorite genres are Brazilian tropicalia, Ethiopian jazz, Jamaican rocksteady, Italian prog, outlaw country, German kosmiche krautrock, and more. It’s painful to choose only one, but for years my answer was Os Mutantes, the psychedelic pop trio from late 1960s Brazil, who sounded like Sgt Peppers but stunningly weird.
How do you record ideas?
I conduct my entire business on my iPad. For ideas and sketches, I use the apps Paper and ProCreate. For lists and text, I use Evernote.
What is your typical work style?
I arrive at my studio around 10am and try to work on a current piece immediately, or I open one of my dusty old sailors knotting tomes to learn a new knot. I believe in the concept of flow, which is the state of blissful productivity, where you are working at the edges of your abilities, happily, without any external reward; the reward is inherent in the doing of the thing. Being in flow is the best way to start a day because it makes me feel so good. I avoid email until the afternoon.
What is your creative process and/or creative workflow like? Does it change every project or do you keep it the same?
I work almost exclusively by commission and there is a waiting list. Clients choose amongst my several current bodies of work, each of which sprang from a single, exquisite knot and my desire to find its ultimate expressive potential, to blow it up and give it a greater aesthetic life. We think of knots as functional, and indeed I’d say the vast majority of the almost 4,000 documented knots are functional, but along with the culture, history, and science behind each perfectly-designed knot, I see them as aesthetic objects. My goal is to bring a greater awareness to the aesthetics of knots and, by extension, to explore the journey of the line.
With that said, while I enjoy making my existing bodies of work, I believe every knot is waiting for me to find its most expressive potential, so I’m always looking for periods of free time where I can experiment with new works. I will never run out of curiosity or things to explore. I don’t get creatively blocked.
What kind of art/design/objects might you have scattered about the space?
It’s all my own work, my sailors knotting books, my materials, whatever work is in progress, and all the experiments. I have a lovely collection of artworks made by others, but I keep all of that at home.
Are there tools and/or machinery in your space?
I was recently given a non-electric, rope-making ‘machine’ (by Schacht Spindle), and am looking forward to making my own rope. I have a glue gun, but try to avoid it as much as possible. I’m a purist, and using glue feels like taking the easy way out when surely a knot will do.
What tool(s) do you most enjoy using in the design process?
Sharp scissors and bent needle-nose pliers.
Let’s talk about how you’re wired. Tell us about your tech arsenal/devices.
I worked at Apple for many years, from the early years of iTunes, to the launch of iPhone and iPad and the App Store. So I’m super savvy with the entire Apple ecosystem. It’s just designed so beautifully, with the user in mind, and with an exquisite design logic. I use my iPad exclusively, with iPhone for Instagram and photo processing.
What design software do you use, if any, and for what?
My work needs only the sketching and drawing apps listed above. Occasionally, I will open my old MacBook to use SketchUp, which annoyingly has not made it to the App Store yet, for complicated projects that benefit from a 3D model.
What’s on your desk right now?
A dozen scissors, ancient knotting books, and various Doughnut and Star Knots.
Is there a favorite project/piece you’ve worked on?
I could never choose between all my babies, but a favorite recent project is the debut of a new body of work, the Hitching Posts. This is installed in Las Vegas.
Tell us about a current project you’re working on. What was the inspiration behind it?
I recently made a Linescape for Square, the payments company based in the Bay Area. They wanted something bridge-inspired, so I used a very curly knot that is rather counterintuitively good for creating sharp angles and straight lines. We did it in a color close to International Orange, the color of the Golden Gate Bridge.
Do you have anything in your home that you’ve designed/created?
I own a classic San Francisco-style Victorian, and I put the first Helix Light Chandelier in my bay window. I also designed the paint scheme in the attic, which is 1970s-style long lines running at angles along the pitched ceiling, and done using the Pendleton Glacier Park stripes. I designed the exterior paint scheme of the house – horizontal ombré stripes running yellow-orange-red on the front and yellow-green-blue in the backyard.
Photos by Windy Chien.
via http://design-milk.com/
from WordPress https://connorrenwickblog.wordpress.com/2020/06/09/where-i-work-windy-chien/
0 notes