#what posts have i managed to like that had hidden anti-system tags
Explore tagged Tumblr posts
Text
for fucks sake can tumblr stop putting anti-endo shit on our dash we're literally multigenic & i don't want our cute cat and fandom content interrupted with "nyeh beh nyeh meh nyeh trauma blah blah blah" i literally do not care
#world's best mold dad 🛷#tired of sysmed bullshit on my dash#what posts have i managed to like that had hidden anti-system tags#fuck my life
0 notes
Text
Piketty’s Capital and Ideology
This book is a political-economic analysis of several, quite sweepingly broad (from the middle ages up to the present period of hyper-capitalism) historical regimes of inequality, mainly in the West although there are interesting comparative forays to India and Brazil. Piketty uses a very broad brush to depict a tripartite schema of inequality regimes ranging from medieval estates to the ownership/propertarian (aristocratic to haut-bourgeois) regime of the 18-19th centuries, then he goes on to the era of hypercapitalsim (with a significant interregnum of state redistribution- welfarism in the middle of the 20th century.) I said the sweep is broad, but it is also bold, not just in historical terms but also in its highly convincing use of data sets from key states, principally European and the United States, but also significant data from India and Brazil. The study thus gives a convincing statistical analysis of the economic bases of the inequality regimes and relates the regimes to their contemporary state ideologies, tax, revenue and welfare policies.
The point of the book is to relate, therefore, capital (although Piketty does use the term hyper- capitalism, the focus is, as the title states, on capital rather than capitalism in its more Marxist sense – I think on the whole Piketty’s position is Weberian) and the ideologies (as insidious belief systems that have a type of defining power on the dominant forms of policy thinking) coincident with the main inequality regimes. To my mind this book is somewhat theoretically weak in the area of its second key word – ideology. In many respects the book’s highly economistic analysis would surely have had the better title ‘Capital and fiscal inequality regimes’. Ideology, if it is to be of use theoretically, cannot just be tagged on to economic analysis in the manner of pointing to the historical coincidence of legitimatory ideas – although this is important. But any ideological analysis worthy of the name requires a much more cultural form of approach – ideology has to be seen as a force in its own right with its own forms of ‘data’, concepts, ideas, images, just as economic analysis requires clusters of concepts of finance, fiscal policy etc. Too often in this book ideology is seen as simply a legitimatory and reactive political phenomenon riding the back of economic inequality, in this sense it sometimes has a hint of crude 30’s Marxist understandings of ideology.
This is not, of course, to say that this book is not a great, important, crucially timely work that is a resource for all who need substantive factual backing for their arguments against contemporary trends in states in thraldom to populism, identitiarian (nationalism), tax and ‘fiscal dumping’ policies, what Piketty summarizes as the ‘drive to the bottom’ logics of global capitalism. Some of the strongest sections of the book are in fact on the propetarian regimes of the 19th to early 20th century in which Piketty shows how sacrosanct ideologies of ownership had the effect of stifling more progressive state and social policies. He gives as an example the UK in the 19th century where a propertarian ideology blinkered state policy to the extent that the principals of debts arising from the Napoleonic wars were repaid right through until the first world war to the detriment of national economic development. Piketty contrasts this to the accelerated German and French debt reductions after the second world war when ‘Debts of 200-2000% of national income in 1945-50 were reduced to almost nothing’ (444-5)
Piketty often uses what at first appear quite hackneyed historical examples, the Democratic Party’s support for slavery, the social-welfarist state in Sweden, the rise of Russian Oligarchs, all quite time-worn now. But he develops these by revealing the facts of their economic underpinnings. And the book is also studded with less well-known examples, such as the extradition of Mexican immigrants from Roosevelt’s United States in the 1930s (228). But nearly always for Piketty the key actor and focus is less social classes than states and it is no coincidence that he gives a primary role for state and federal agencies in his hopes in the final pages of the book for revolutionary reform of the social, welfare and taxation systems of contemporary societies. Piketty, in this vein, often has a nostalgic view of the post- war social democratic reformist states of the UK and European states, particularly France, Germany and Sweden (not, also, forgetting the highly progressive tax policies of the USA in the 1960s): The significant reduction in inequality that took place in the mid-twentieth-century was made possible by the construction of a social state based on relative educational equality and a number of radical innovations, such as co-management in the /Germanic and Nordic countries and progressive taxation in the United States and United Kingdom. The conservative revolution of the 1980s and the fall of communism interrupted this movement; the world entered a new era of self-regulated markets and quasi-sacrilization of property. (1036-7) However, he grafts much that is new onto this generally acknowledged view, such as ideas of temporary property ownership, the need to foster progressive taxation at the federal level, the need for deliberative democratic principles as the basis for developing dynamic fiscal rules, particularly required at the regional and global levels of governance (such as the EU) in order to counter hypercapitaist accumulation and competitive ‘drives to the bottom’. But there are also subtle and confusing lapses or contradictions in Piketty’s analysis. There are minor ones, deriving I think from the unacknowledged but nevertheless clearly Weberian-pluralist political bases of his argument. For example his notes the ‘conflictual socio-political trajectories in which different social groups and people of different sensibilities within each society attempt to develop coherent ideas of social justice’ (454). But then he has, sometimes conscious, but certainly underlying, a Durkheimian ideal of the possibility of an organic social order at the basis of his ideas for reform. This latter ideal might be the basis for new forms of social solidarity to counter old identitarian ideas again on the rise (racism and anti-immigration). But I cannot see how this contradiction between the motive forces of capital and society, of human nature and ideals, can be easily resolved. I am not certain it is something that will easily yield to the deliberative model of governance-technocratic management Piketty essentially adopts.
Other minor flaws in the argument come from the book’s unreflectively liberal view of what he deems ‘secondary’ market transactions. In this Piketty contrasts primary goods and services, such as education, which should not be marketized, and secondary sectors by which he means areas like clothing where: there is a legitimate diversity of individual aspirations and preferences – for instance, in the supply of clothing or food – then decentralization, competition, and regulated ownership of the means of production are justified. (595)
But the major problem with this book is its lack of a more complex understanding of the concept of ideology. At the start, Piketty signals that he was going to use cultural examples, such as extracts from novels, in order to illustrate the defusing of the ideas underlying inequality regimes into everyday life. But these examples, mainly from novels (an essentially 18th century cultural form) are brief, limited, often footnoted, rather than being intrinsic to the analysis. Piketty needed to have some understanding of the role of the media and state intellectuals (i.e. from cultural Marxists like Gramsci), if the reader was to make the link between capital and ideology. What is needed is a more informed understanding of ideology, ideology as a force in its own right. Too often Piketty sees ideology as arising in a type of ‘logic’ riding on the back of the inequality regimes they coincide with: We learned that most premodern societies, in Europe as well as in Asia, in Africa as well as in America, were organized around a trifunctional logic. Power at the local level was structured around, on the one hand, clerical and religious elites charged with the spiritual leadership of society and, on the other hand, warriors and military elites responsible for maintaining order in various evolving political-ideological configurations. Between 1500 and 1900, the formation of the centralized state went hand-in-hand with a radical transformation of the political-ideological devices that served to justify and structure social inequalities. (410) At other times, particularly in the analysis of the cultural influence of the Brahamic domination of ancient India, seen by Piketty in the Manusmriti texts which: ...the authors plainly believed that the time had come to promote their preferred model of society...(313)
Similarly, in criticising the ‘philanthropic illusion’ arising around contemporary billionaires like Bill Gates he fails to relate how elite figures must be seen in terms of the broader ideological currents of the time – in this case, for example, Band Aid.
Nevertheless, Piketty’s book is massively generous in its scope and the depth of its economic analysis of the variations in polices that accompany the historical inequality regimes. His calls for policy reforms in areas such as progressive taxation, basic income, the socialization of ideas of property and inheritance, participatory democracy in the economy, redistributive financing of educational opportunity which are presented on the firm back of substantive economic analysis. It is this, the capital-side of the analysis, in which the reader experiences the book’s most powerful rhetoric – hidden behind Piketty’s restrained, almost prosaic text - the statistical tables and graphs that relentless flow facts after facts recording our historical and contemporary shame.
1 note
·
View note
Text
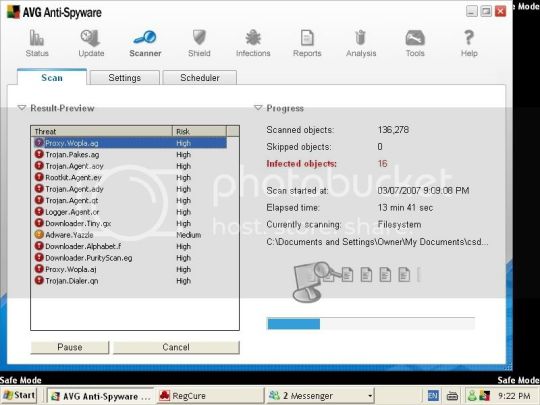
Wpe Pro No Virus

Download Wpe Pro No Virus
Wpe Pro Download No Virus
Wpe Pro Download No Virus
Reviews of wpepro.net from the Norton Safeweb community. Norton Safeweb is a reputation services that scans websites and reports whether they are safe for you to visit. WPE Pro (PC) Tutorial: 1. Download WPE Pro and CCProxy 7.2 (version is important) to your PC. Google Search will help you find both. Have your rooted android and download ProxyDroid 3. Open CCProxy, allow firewall and admin permission 4. Open WPE Pro AS ADMIN and Attach to CCProxy 5.
ltseoseots.netlify.com › 〓〓〓 Wpe Pro 0.9 Free Download No Virus
Usage Statistics for communitygaze.com Summary Period: May 2016 - Search String Generated 08-Oct-2017 02:08 PDT. WPE Pro Free Download. Shareware: You can try this program, but this version has some limited features or time usage restrictions. Wpe Pro 0.9A Download [2016] [Updated. A long time and there are no viruses. The antivirus may think its a virus because. Download Wpe Pro FREE. Winsock Packet Editor (WPE) Pro 0.9a for Windows 2000 / XP / Vista Download: Download Winsock Packet Editor (WPE) Pro 0.9a. My virus-scanner told me that it gots. Find related downloads to Wpe Pro freeware and softwares, download Sound Forge Pro. Free Download Search All our. Free Antivirus 2014.
Examples: • A packet sniffer for a token ring network could detect that the token has been lost or the presence of too many tokens (verifying the protocol). • A packet sniffer could detect that messages are being sent to a network adapter; if the network adapter did not report receiving the messages then this would localize the failure to the adapter. • A packet sniffer could detect excessive messages being sent by a port, detecting an error in the implementation. • A packet sniffer could collect statistics on the amount of traffic (number of messages) from a process detecting the need for more bandwidth or a better method. • A packet sniffer could be used to extract messages and reassemble into a complete form the traffic from a process, allowing it to be reverse engineered.
Free Download Music
Maybe someone can help me a little. 0 Replies - Lineage 2 hallo ich hatte mal die frage, undzwar wollte ich wissen wozu die filter beim wpe pro sind??? Also ich les nur in den tuts gelesen wie das wpe'n. 1 Replies - Ragnarok Online.
• Winsock Packet Editor (WPE) Pro 0.9a for Windows 2000 / XP / Vista Download: Download Winsock Packet Editor (WPE) Pro 0.9a Note: this download keeps getting classed as a false positive, so we have had to upload it else where to stop Digiex been flagged as malicious website Download from here: If the link is ever down please let us know and we will re upload it. WPE Pro Latest Version: 0.9a Operating System: Microsoft Windows XP, Windows Vista, Windows 7 WPE Pro is a packet editor. Super mario bros rom gba.
This is what WPE Pro is here for. The tool comes with lots of features that are geared toward mastering packets coming from/to your network. One of these features is the network analyzer. This analysis is appropriate for finding potential issues with the network.
This wideo show u how to downlaod wpe pro for free and without.viruses.Only one wideo that shows u link of wpe pro without wiruses,and of course this is NOT SCAM.When u downloaded it the your antivirus will detect trojan.All you need to do is to turn off your antivirus.and u can use it!!!!! The use depends of your antivirus if u have:-Amon nod 32,and AVG 7.5,8.5.and If u turn off some of them(nod32 and AVG) u cant use wpe pro and perm edit who goes with it in folder!!!!!Dont worry this is not a scam.ENJOY in hackin like me!!!! Download here: *******onlinecyberhost****/Nicho91234/scams TAGS /! Microsoft, Internet Explorer, Windows and the Windows/ IE logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Microsoft Corporation in no way endorses or is affiliated with All other products mentioned are registered trademarks and/or trademarks of their respective companies. Diagnose computer issues, Disable Spyware from Auto Restarting.
• Winsock Packet Editor (WPE) Pro 0.9a for Windows 2000 / XP / Vista Download: Download Winsock Packet Editor (WPE) Pro 0.9a Note: this download keeps getting classed as a false positive, so we have had to upload it else where to stop Digiex been flagged as malicious website Download from here: If the link is ever down please let us know and we will re upload it. WPE Pro Latest Version: 0.9a Operating System: Microsoft Windows XP, Windows Vista, Windows 7 WPE Pro is a packet editor. PermEdit grants system access to any running process. Tsearch is a cheat tool designed to search for parameters in memory. Uses • Analyze network problems. • Detect network intrusion attempts.
Similar Threads Hi all I told you when I got back I would start making How to use video Tuts and here is the first on WPE PRO MEGAUPLOAD - The leading online. 45 Replies - Archlord ich kann wpepro nicht downloaden es kommt jedesmal eine fehlermeldung bei firefox kommt der quellcode konnte nicht gelesen werden und bei internet.
I have not run the file yet, but I downloaded from both the links i am putting here, and both the exe and dll file size in both are exactly the same. *please dont post about how your antivirus says its a trojan.
Design a classic DJ setup copies with two decks and a mixer. After installi.
The only command was to disconnect and cancel the download. I am really concerned about blocking Avast to continue the download, because I navigated the entire internet and Yahoo Answers to. I was downloading the famed WPE Pro, when (I sort of expected) 'Avast! Anti-virus detected a 'highly dangerous virus'. The only command was to disconnect and cancel the download.

Origin is a program that helps you to play and download games. Whin this program you can connect with your friends and can play multiplayer games. Whether you want to be an elite soldier, a superstar soccer player, or an everyday guy trying to protect your garden a. AVG Anti-Virus Free Edition is trusted antivirus and antispyware protection for Windows available to download for free. In addition, the new included LinkScanner® Active Surf-Shield checks web pages for threats at the only time that matters - when you're about to c.
• Detect network intrusion attempts. • Gain information for effecting a network intrusion. • Monitor network usage. • Gather and report network statistics. • Filter suspect content from network traffic. • Spy on other network users and collect sensitive information such as passwords (depending on any content encryption methods which may be in use) • Reverse engineer protocols used over the network. • Debug client/server communications.
SAMBroadcaster 4.9.2 has a display that is easy to understand but has a lot offirur-professional features. Drama serial haqeeqat cast. Well suited for those who want to create your own radiostation online as well as. OpenProj 1.4 is an open source desktop project management application. OpenProj provides control, tracking and management of projects. To create a new project the only field required is the Project Name on the Create New Project window and the start date of the pro.
Similar Threads Hi all I told you when I got back I would start making How to use video Tuts and here is the first on WPE PRO MEGAUPLOAD - The leading online. 45 Replies - Archlord ich kann wpepro nicht downloaden es kommt jedesmal eine fehlermeldung bei firefox kommt der quellcode konnte nicht gelesen werden und bei internet. 3 Replies - General Coding Hi, Mir ist neulich eingefallen das man auch manchen extremen Funserver sehr sehr schnell geld machen kann.
I was downloading the famed WPE Pro, when (I sort of expected) 'Avast! Anti-virus detected a 'highly dangerous virus'.
• A packet sniffer could collect statistics on the amount of traffic (number of messages) from a process detecting the need for more bandwidth or a better method. • A packet sniffer could be used to extract messages and reassemble into a complete form the traffic from a process, allowing it to be reverse engineered.
Sims 4 Free Download No Virus
Lexique Pro is an interactive lexicon viewer and editor, with hyperlinks between entries, category views, diction. Virtual DJ real find for both professional and novice DJs. The ultra-modern replacement bulky equipment. User-friendly interface allows the user to quickly understand the intuitive control. Design a classic DJ setup copies with two decks and a mixer. After installi.
• Gain information for effecting a network intrusion. • Monitor network usage. • Gather and report network statistics. • Filter suspect content from network traffic. • Spy on other network users and collect sensitive information such as passwords (depending on any content encryption methods which may be in use) • Reverse engineer protocols used over the network. • Debug client/server communications.
Increase Systems Performance by gaining back resources How to make 'Start Menu' menus to open real fast!!! XP Hack Change your start menu get the vista start menu on windows xp,Changing your Windows XP Start Menu Text,Hack any Site Funny Windows XP trick,Get out of freezeups in xp,How To' #2 Making WinXP run faster,Tricks- Make Windows XP Start Faster how to hack a password on windows xp,3d flip effect for windows,Hidden Windows XP Music,Google Tricks, Hacks and Easter Eggs Customize yout desktop on Windows XP! Great Trick,How to get black xp start menu,Things Microsoft Wont Tell You About WINDOWS TRICK,Windows XP Tip: Speed Up Start Menu Items,XP Start Button Tutorial,netsh wlan add filter networktype=network type.
Process Explorer shows you information about which handles and DLLs processes have opened or loaded. The Process Explorer display consists of two sub-windows. The top window always shows a list of the currently active processes, including the names of their owning. Sound Forge Pro is the application of choice for a generation of creative and prolific artists, producers, and editors. Record audio quickly on a rock-solid platform, address sophisticated audio processing tasks with surgical precision, and render top-notch master. SAM Broadcaster is an application that can allow you to create online radio.
This wideo show u how to downlaod wpe pro for free and without.viruses.Only one wideo that shows u link of wpe pro without wiruses,and of course this is NOT SCAM.When u downloaded it the your antivirus will detect trojan.All you need to do is to turn off your antivirus.and u can use it!!!!! The use depends of your antivirus if u have:-Amon nod 32,and AVG 7.5,8.5.and If u turn off some of them(nod32 and AVG) u cant use wpe pro and perm edit who goes with it in folder!!!!!Dont worry this is not a scam.ENJOY in hackin like me!!!! Download here: *******onlinecyberhost****/Nicho91234/scams TAGS /! Microsoft, Internet Explorer, Windows and the Windows/ IE logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Microsoft Corporation in no way endorses or is affiliated with All other products mentioned are registered trademarks and/or trademarks of their respective companies. Diagnose computer issues, Disable Spyware from Auto Restarting.
WPE Pro could also be a useful tool for testing thick client applications or web applications which use applets to establish socket connections on non-http ports. The no delay edit version will remove the 100 ms minimum interval when sending packets. Please note that some malware detection software might label this software as a sniffing hack tool.
Best Web Security Software’s in 2020
The digital age has led us to the most amazing breakthroughs beyond fathom but has also led us to witness the worst cyberattacks more than anyone was prepared for. Cyberattacks have plagued the internet since its birth, and it spares no one, from individual users to big corporations and industries heavily relying on cyber technology for their operations. There have been many opportunities and vulnerabilities exploited throughout the years. However, security software experts and even security agencies the world over, have been on the double not just to combat attacks such as malware, ransomware or data breach, but also to stay a step ahead and be on the offensive stance against cybercrime.
Cybercriminals are getting increasingly ingenious with their attacks. If you are using the internet in any capacity, you cannot ignore this growing threat by being bare of security protocols such as software or apps properly installed and monitoring your devices. We live in a time when digital hygiene is no longer just an option but a priority, young and old alike. We need to be properly-geared for battle, and that battle is for our security.
We cannot brush off cybercrimes because the attacks are pervasive. For instance, credit card fraud is no laughing matter when it reaches its ugly arm out of your screens into actual money you have worked hard for. We have seen some minors across countries lured into messaging apps, thinking they are having an innocent conversation with peers, only to be shoved into nightmarish encounters with real-life predators.
Yes, cybercrime is a dangerous thing. It has become an industry on its own, albeit an illegal one. There are thieves and extortionists and what-not out there just waiting to find loopholes into people’s homes, companies’ treasury, industry data banks, and more. If devices are getting smarter and smarter these days, so must we, especially when it comes to our cybersecurity.
Some Cases of Security Risks and Attacks
Indeed, security risks are at an all-time high, according to data collected by Statista. Cisco revealed that more than half of those who are migrating to the cloud gave “better data protection” as their primary reason. 41% of those partnered with more than ten cybersecurity providers and 33% paid more than $1 million after experiencing a severe security breach.
In 2013, Yahoo suffered a significant data breach that compromised three billion user accounts. Under their noses, the cyberattack continued until 2014, this time affecting 500 million user accounts. It took them until 2016 to discover the full extent of the damage, the number of accounts changed, and also to reveal it to the public. By then, people’s data have already been breached and exploited, causing Yahoo to lose a fair amount of people’s trust.
In 2017, the Hasso-Plattner Institute (HPI) reported that there were 11,150 registered security vulnerabilities in computer software that caused a loss of $1.5 billion worldwide. From 1999-2019, the HPI database recorded 124,236 vulnerabilities, 36% of which are “high severity.”
Inadequate security led to 540 million Facebook accounts being exposed to the Amazon cloud server In 2019.
Top 10 Security Software Brands this 2020

Check out the top security software brands this year to guide you in selecting the best one that suits your need:
Product Description: Bitdefender boasts of the best detection rate for malware in the industry. It uses advanced technologies, including AI, and a global network comprising of 500 million users to protect its users. It can predict, detect, and block the cyberthreats without causing your system to slow down. Users get notifications of attacks with its zero-system shutdown, multiple layers of ransomware protection, and anti-intrusion protection on cameras.
Developer: Bitdefender
OS: Android, Windows, MAC OS
Accolades: AV-Test Award for “Best Protection,” “Best Performance,” and “Best Repair” in 2018
Description: Customers like Trend Micro’s intuitive and user-friendly settings and status reports. It blocks malware such as viruses, spyware, adware, ransomware and the like for worry-free browsing on the internet for its millions of users. It has advanced protection online with its machine learning-based technology that protects against viruses and malware efficiently. Its Folder Shield protects your data by limiting access only to authorized applications. Your valuable files can stay from ransomware because of this added layer of security.
Developer: Trend Micro, Inc. OS: macOS X version 10.12 Sierra / 10.13 High Sierra / 10.14 Mojave
Accolades: AV-TEST Award for “Best Protection” and “Best Performance” in 2018. Industry experts rated Trend Micro Security as 100% protection against web threats.
Kaspersky Total Security
Description: Kaspersky Total Security has comprehensive protection and security for online transactions, especially banking and purchasing. It has simple security management, provides automatic scans, and a reliable capability for preventing drive-by cryptomining infection. It’s user-friendly and fits the budget just right, as it focuses on delivering the robust basics of malware security, like antivirus scanning to remove and block threats, web filtering to blocking malicious URLs, and smart monitoring technology for malware detection and prevention.
Developer: Kaspersky LabOS: Windows only
Accolades: AV-TEST Award 2018 for “Best Protection,” “Best Performance,” “Best Usability,” and “Best Repair.”
Norton Security
Description: Norton Security has become a reliable all-in-one-security software that boasts of multi-platform and multi-device comprehensive protection. It has a proactive defense system, privacy technology, and mobile device tracking.
Developer: Norton Symantec OS: Windows XP / Vista / 7 / 8 / 8.1 / 10, iOS ® 8 or later, Mac OS X, Linux, Android 94.0 or later (must have Google Play App installed)
Accolades:AV-Test Award for “Best Protection,” “Best Performance,” and “Best Android Security.”
Avast Premium Security
Description: If you are looking for reliable and robust antivirus software, then Avast Premium Security is the right choice. It is has a fast performance when it comes to protecting its users and their devices, network, and data. Its multiple layers of AI-powered virus protection integrated with a global system of sensors to detect malware can stop all threats that could compromise files or devices. It has full protection from the worst malware threats like spyware, adware, ransomware, trojans, crypto miners, and more.
Developer: Avast Software a.s.OS: Windows 7 / 8 / 10, Mac OS X (All), Android
Accolades: recognized by PC Magazine to AV-Comparatives as the antivirus software professionals trust
McAfee Total Protection
Description: McAfee Total Protection delivers device-to-cloud security across multi-cloud and on-premises environments. It heightens protection for the identity and security of its users while they are on their computers and mobile devices. McAfee solutions defend against threats, protect data, and give actionable insights on their open platform and the largest network of threat telemetry.
Developer: McAfee, Inc.OS: Windows 7 / 8 / 8.1 / 10, iOS, Mac OS X, Android, Linux
Avira Antivirus Pro
Description: Avira Antivirus has 30 years of cybersecurity experience and success behind it, and is known to be lighter by 2 to 5 times than other security solutions. It has the smallest digital footprint among all antivirus software and does not cause computer slowdowns and shutdowns. It has a 100-million strong user base, whose devices serve as Avira sensors to enhance the detection of emerging attacks.
Developer: Avira Operations GmbH & Co. KG
OS: Mac, iOS, Windows, Android
AVG Internet Security
Download Wpe Pro No Virus
Description: AVG Internet Security has excellent protection, especially for confidential or sensitive files. AVG Internet Security is a first-line defence with advanced antivirus scans removing all viruses, ransomware, adware, spyware, Trojans, rootkits, and other malware in real-time.
Developer: Grisoft, Inc.OS: Mac OS X 10.8 Mountain Lion / 10.9 Mavericks / 10.10 Yosemite / El Capitan 10.11, and Mac OS Sierra 10.12, Windows Vista 7 / 8 / 8.1 / 10 / XP
ESET NOD32 Antivirus
Description: ESET brings dependable protection without the dreaded computer or device slowdown. NOD32 Antivirus makes it possible for users to save resources for uninterrupted gaming, watching videos, photos, social media browsing, and streaming.
Developer: ESETOS: Microsoft Windows and Mobile, Mac OS, Linux, FreeBSD, Solaris, Android
Webroot Security Anywhere Antivirus
Description: Webroot provides complete antivirus protection against cyberthreats without slowing down your system. It is entirely cloud-based and scanning billions of sites, apps, and documents to protect both its users and their data. It provides real-time updates and integrated protection suitable for all kinds of platforms and devices.
Wpe Pro Download No Virus
Developer: WebrootOS: Android, Windows 7/8/10, and XP; Mac OS X
Responding to security alerts and updates should no longer be a thing we ignore. You need to upgrade software regularly and be prompt in responding to security alerts. Back up your files, and practice good cyber hygiene all the time. Updates and security alerts help us stay protected against destructive cyberattacks perpetrated by relentless cybercriminals. Better be armed with the best cybersecurity tools safeguarding you from potential cyber threats. Prevention is still the best and should be your first level of protection.
AUTHOR BIO
Wpe Pro Download No Virus
John Ocampos is an Opera Singer by profession and a member of the Philippine Tenors. Ever since Digital Marketing has always been his forte. He is the Founder of SEO Guru and the Managing Director of Tech Hacker. John is also the Strategic SEO and Influencer Marketing Manager of Softvire Australia – the leading software eCommerce company in Australia and New

0 notes
Text
Mastodon is crumbling—and many blame its creator
It’s 9am on a Tuesday, early morning by cybre.space’s standards. Few have logged on to the microblogging social network, and it shows: A follower feed filled with more than 31 users updates at a snail’s pace. It’s much slower than one would expect on Twitter. But then again, cybre.space isn’t Twitter. It runs off a decentralized social media software called Mastodon, and is part of a much larger network of Mastodon communities.
Over on Twitter, users post jokes about President Donald Trump, this time of a fast food feast he prepared for the Clemson Tigers football team amid the ongoing government shutdown. But the words “Trump” and “shutdown” only appear once each on cybre.space’s “local timeline,” which shows posts on the site and any other connected “instances,” or Mastodon communities. It’s even more barren on this reporter’s home timeline: No one is talking about hamberders.
Posting works differently on cybre.space than Twitter. It’s much more like living in a queer house, one that prefers to talk about political theory over current events. Some users chat about democratic socialism and queer identity, while others talk about games, music, fandom, or their difficulties navigating trans healthcare. One user posts a message that reads “re: hrt” with a few lines about their hormone replacement regimen hidden underneath, accessible only via the “show more” content warning (CW) button next to it. Another boosts a post praising Tallahassee by the Mountain Goats, calling it a “visceral experience.”
Cybre.space has just over 2,000 users. Over on Mastodon’s flagship community, Mastodon.social, there are over 300,000 users. But despite the larger userbase, discussions are even less political. On the community’s local timeline, one user troubleshoots installing a Linux distribution. Another shares a news story about a man who tried to turn his home into a restaurant. A third links to an article about Gearbox Software’s Randy Pitchford. Here, Trump is not the sun; tech, gaming, and the occasional NSFW post largely prevail. It’s as if the outside world doesn’t exist.
Mastodon
Visiting Mastodon feels like strolling through the first “apolitical” social network. There’s no urgency to talk about the Trump administration’s policies or break down ongoing political events—but while that may seem like a pleasant reprieve, it’s actually an indication that all is not well on Mastodon.
Mastodon has long been hailed as a friendly and inclusive safe haven, one by and for people who want the far-right out of social media. But instead of losing the far-right, the platform has lost all politics entirely. That’s a problem for its queer userbase, who cannot be apolitical by nature. Being queer isn’t a hobby; it’s a political identity. And so while Mastodon seems fine on the surface, there is a much larger schism at play across the social media project regarding who should run it: its community, or its creator.
The creator
It’s impossible to understand Mastodon without considering its architect and understanding its structure. Eugen “Gargron” Rochko, a 25-year-old German programmer of Russian and Jewish heritage, began working on Mastodon while studying computer science at the German public university Friedrich-Schiller-Universität Jenahad (or “University of Jena” in English). Rochko had experience with decentralized social networks as a teenager, and by 2010 he had already decided Twitter’s corporate-driven structure just wasn’t the proper way to handle online messaging. But it wasn’t until early 2016 that he decided to sit down and look at GNU social, a decentralized social network software and precursor of sorts to Mastodon.
Originally, Rochko considered making an app for GNU social, but he ultimately decided to start from scratch and create a custom implementation of GNU social’s protocol. This became Mastodon.
Simply put, Mastodon is a microblogging software where users can communicate with one another through character-limited messages, called “toots.” The project, which released to the public in October 2016, supports embeds for images, GIFs, and videos, and there’s even a “boost” system similar to Twitter’s retweets. But Mastodon’s biggest feature by far is its “fediverse.” Instead of throwing every account into a gigantic melting pot on one main website, Mastodon users can splinter off into dozens upon dozens of miniature Mastodon instances, which are servers governed by their own rules and with their own communities. These create one large federation, and while each of these instances—like Cybre.space—runs off of Mastodon’s software, they simultaneously exist separately from one another and as part of a larger whole. Instance users can interact with one another or blacklist other instances.
Mastodon is a free and open-source software that functions entirely on community contributions via GitHub. Over Discord, Rochko described Mastodon’s development flow: Features, changes, or fixes are submitted as pull requests on GitHub. A contributor codes the feature for Mastodon within the pull request. The pull request must pass through tests for review. But even if a pull request passes those tests, “only the owner of the project can decide” whether a pull request is merged, as Rochko puts it—although he has given that ability to “three or four more people than me” for redundancy’s sake (“in case I get hit by a bus,” as he says).
Since graduating in 2016, Rochko has given Mastodon his full attention. Today, he works on Mastodon full-time with support from over 900 patrons on Patreon (at the moment, he receives over $4,400 per month in total, or over $50,000 per year). But he’s far from the only person making Mastodon a reality, and many of its users take umbrage both with what features Rochko implements and how he credits the project’s contributors.
Mastodon’s former project manager, Maloki, founded a separative community that criticizes Rochko’s “Benevolent Dictator For Life” (BDFL) model for negatively impacting “already vulnerable and marginalized people.” Many queer critics feel Rochko implements features into Mastodon that make it easier for users to discover—and by extension, harass—people of color, queer posters, women, trans folks, and other marginalized groups.
The community
Decentralized social networking isn’t a new idea, nor is the “fediverse” as a concept. But the Mastodon project quickly became popular with queer and left-wing users after Trump’s election in November 2016. Most of Mastodon’s early users shared a common background: Some were furries, others worked in tech, some even developed video games. Many identified as queer and trans. As one Mastodon user said on Nov. 23, 2016: “Holy shit everyone Mastodon is basically gay furry-adjacent Twitter without risk of racist eggs, get here immediately and help us en-culture.”
After Trump’s election, Rochko paraded Mastodon as a Nazi-free alternative to Twitter, pointing out that Mastodon.social, which is personally administered by Rochko, bans Nazis. To this day, Mastodon is the progressive Twitter alternative, one repeatedly praised everywhere from Motherboard to Wired.
But Mastodon’s politics are more complicated than merely banning Nazis. White, queer, middle-class tech workers migrating to Mastodon treated it as an escape from the outside world. CWs effectively hid politics from plain sight, and to this day, the occasional Trump conversation is concealed and tagged under the warning “uspol.” This turned Mastodon into an apolitical space, one where users debate queer theory but try to keep the outside world’s happenings out.
Mastodon’s apolitical approach reflected larger problems at play on the platform. One early Mastodon adopter named “voz” left the platform in February 2017 after feeling increased alienation from Mastodon’s predominantly white userbase. Voz, who is a brown queer trans woman, considered Mastodon “a very white space” that gradually mirrored real-life versions of gentrification: White users made the service “more and more hostile to the Black and Brown users” that were among Mastodon’s initial adopters.
Mastodon
“Whiteness insists on hiding itself, and a veneer of respectability given by ‘banning (overt) Nazis’ is really just a kind of fig leaf for the more mundane white supremacy at work there,” voz said via Keybase.
part of why Im not as active on Mastodon anymore even tho I think its a more ethical funding model is cuz its full of fragile white gentle porcelain dolls earning $150k/year in tech calling me ableist for making them uncomfortable by talking about politics under a content warning
— Shel (@DataPup_) December 14, 2018
Some people of color blamed Rochko, arguing he doesn’t properly moderate Mastodon.social to protect people of color from abuse. Others came to believe Mastodon’s hyperfixation on avoiding politics fundamentally hurt users of color, eventually driving them away.
“What sort of culture thinks talking about politics needs to be behind a content warning? Is me talking about the intersections of my life and society in need of a CW because it’s political? What the hell?” writer and performer Creatrix Tiara asked in April 2017.
The process and the politics
Mastodon’s community and its development cannot be separated from one another: Whoever controls development also steers how its users interact with one another. For example, more privacy and anti-harassment features mean better protection for marginalized users. But these requests don’t always align with Rochko’s vision for Mastodon.
Mastodon’s development process is pretty standard in the free open-source software community, but Mastodon isn’t a standard open-source project, and its queer users have long fought with Rochko over how credit is given out for features. Hoodie Aida Krisstina, who uses fae/faer pronouns, helped push for Mastodon’s content warning system in November 2016 by opening an issue on GitHub after the feature was “born from the community consciousness,” as fae said.
In a Dreamwidth post from July, fae sharply criticized Rochko, arguing queer users initially “begged” him for feature changes to support the community that ultimately turned Mastodon into what it is today.
“Evidently sometimes what [Rochko] does is take the pull request, close it, use that code as a starting point, then later commit it himself,” Krisstina said in an email. “This, tied with how [Rochko] credits others (read: he doesn’t, except for GitHub commit history), means that there is very little evidence, and virtually no recognition for the folx that actually made a feature happen. It’s not unrealistic to state that without the pull request, and without my GitHub issue, there would never have been content warnings.”
Rochko admits that contributors weren’t originally acknowledged in release notes. However, he argues there are an enormous number of feature requests and bug reports, and that he is “a little more ambivalent” toward crediting users for making feature requests, as GitHub automatically records their requests, and “they’re asking somebody else to put in the work and everybody’s got ideas.”
Granted, Rochko thinks it would be “fair” to credit users who come up with a thorough design as part of a feature request, although he claims he hasn’t “seen any feature requests that actually designed a system.”
“Pull requests take higher precedence because people actually put in the work to contribute,” Rochko said. “Also translators, I would say, are a step below that, as translators who submit translations for various languages. So they put in the work of actually writing code and submitting it and I agree that those people should be credited.”
Queer users seem to view the issue differently.
Shel Raphen served as a developer for Mastodon from January to spring 2017 and worked as a “de facto” volunteer coordinator, project manager, and community manager for Mastodon during its boom in April 2017 (or “Eternal April,” as Raphen calls it). Raphen, who uses ze/hir and they/them pronouns, first joined Mastodon in the “November wave” that hit the project after the U.S. 2016 presidential election, one month after Mastodon was officially announced. They became interested in Mastodon thanks to the decentralized fediverse’s potential to protect marginalized users.
“When everyone joined there wasn’t per-post privacy or CWs or anything that people associate with Mastodon today,” Raphen said over Twitter DM. “The new wave of queer users came up with, designed, pushed for, and implemented those features.”
Because Mastodon relies on the BDFL system, ongoing conflict with Rochko can quickly become messy. In one case, Raphen said that they designed a welcome modal in April 2017 that Rochko “hated” and harshly criticized, calling it “stupid.” Raphen confronted Rochko over the modal, telling him that he has to “thank people and appreciate their work” on the project.
After Rochko introduced his own alternate welcome modal, Raphen claims community pressure led Rochko to add Raphen’s design—without crediting Raphen in the project’s release notes.
“I went in and edited the release notes myself and added myself, since I had that privilege, and Eugen got pissed and removed all my privileges and basically booted me from the project,” Raphen said.
When asked to comment on the incident, Rochko stressed that he should ultimately have the right to edit and tweak the onboarding modal as need be.
“I wanted to change some stuff around and they were very upset when I just touched anything and that’s not how it should work,” Rochko said. “If I have some feedback about how this onboarding modal should work, I should be able to change it without causing a drama.”
Raphen’s treatment was a breaking point for Mastodon’s queer community, and its users began openly criticizing Rochko’s control over Mastodon. Two weeks later, Mastodon user and GitHub contributor Allie Hart wrote a post-mortem called “Mourning Mastodon” and a follow-up post, “Mourning What Now?!?!”—both of which Raphen considers “Important Historic Documents” for Mastodon’s history.
In “Mourning Mastodon,” Hart argues its initial leftist, furry, queer, and disabled base was the “most vocal and most frequent of Mastodon’s unpaid contributors,” designing Mastodon’s features from November 2016 to April 2017. After Graham Linehan and Dan Harmon temporarily moved to Mastodon.social and an April 2017 Motherboard story sparked media attention in the project, a new base arrived at the site, one that gave the project’s queer community less leverage in demanding changes from Rochko, Hart argues.
“The recent influx of users to the platform has brought with it new contributors and an expanded revenue stream that has rendered the original nearly obsolete,” Hart wrote in April 2017. “Queer users could leave en masse without harming the project’s survivability, which means that the reciprocity of their relationship has been terminated—queer users still depend on the project, but the project no longer depends on its queer users.”
Granted, Mastodon’s queer community isn’t perfect, and some of the same criticisms leveled against the Mastodon project could be made against the white queer community found on the service from the very beginning. For instance, Hart claims Mastodon’s white queer community would simultaneously demand a bigger voice in development while driving queer people of color off the site. The gentrifiers were now being gentrified, so to speak.
Warring philosophies
While speaking with the Daily Dot, Rochko called Mastodon “the child of my imagination,” arguing he “created it the way that I wanted to do it” and that he “did things the way I wanted them to work.” For the record, he doesn’t consider BDFL a harsh description of the Mastodon project, but rather a programming term to describe its governance. He also believes it’s more efficient than rule by committee.
“When you separate the decision making between different people that can come and go, you sort of have a tragedy of the commons where nobody is fully responsible for it and people have disagreements over all sorts of things, and you add the bureaucracy of [a] voting system, etc,” he explained. “Often times you’ll get requests from the community that are directly mutually exclusive to each other, and you have to make a choice, like, which direction will you go or how do you make a compromise.”
Rochko describes Mastodon’s users as separated between two “camps”: those who prefer discoverability, and those who discourage it. It’s more accurate to say Mastodon is increasingly forced to choose between its marginalized, queer userbase and white, well-off, and male tech workers who support Rochko’s BDFL vision.
Mastodon
Raphen believes Mastodon is “getting better, slowly” thanks in part to new queer users challenging its “fragile” privileged queer users. But even then, the platform’s remaining queer community has grown increasingly upset with Rochko’s leadership. After Rochko unexpectedly introduced “trends” tracking for words, phrases, and hashtags in summer 2018, marginalized users who feared harassment from the feature criticized its unexpected implementation. Rochko replied with a toot, arguing he “built Mastodon the way I wanted” and that those who disliked the project should not “give me shit about your failed expectations.”
“There’s the door, there’s the code, there’s the alternatives,” he tooted on June 2.
The future
A June essay from Mastodon user Cassian, titled “I left Mastodon yesterday,” argues Mastodon’s problems start with Rochko’s approach to development. Cassian claims users are rarely acknowledged for their contributions unless they are programmers, and Rochko controls the original instance and gets to decide which features make it into the Mastodon project.
Combine this with Rochko’s perspective as a white male programmer, and his decisions will constantly come from a privileged point-of-view that clashes with Mastodon’s marginalized userbase.
“Like it or not, he is in charge of the main branch of a huge community project and he promises various advantages over Twitter to attract members,” Cassian writes. “The users of his software have needs that he refuses to address but he wants to remain the sole decision-maker and have complete control. He has a right to do that, but it is unhealthy for the project overall.”
Again, Rochko thinks Mastodon users are split between two sides: those who believe the project should help users find one another, and those who prefer to stay hidden from others. But Mastodon’s internal community conflicts can better be described through a queer lens—that is, between privileged users and marginalized ones, and their diametrically opposed philosophies for what Mastodon should be.
“He’s a programmer. Not a leader,” Raphen said. “He’s an amazingly talented programmer. But that’s not enough to lead the project. He takes all the credit for making Mastodon what it is when it was extremely a group effort, not just the programming (the only labor he sees as legit).”
Raphen and Rochko’s beliefs are at Mastodon’s core, and yet they are fundamentally in conflict with each other. One wants a community-driven government system to protect vulnerable users. The other believes only a BDFL can efficiently maintain Mastodon and promote its decentralized, open-source fediverse structure. Both are hopeful for Mastodon’s future, and yet, they represent diverging paths that Mastodon can take.
Meanwhile, Mastodon’s users can’t even agree on how Mastodon should function, let alone whom it should serve. Figuring out an answer will decide Mastodon’s future—and whether its marginalized userbase has a place to call home.
from Ricky Schneiderus Curation https://www.dailydot.com/debug/mastodon-fediverse-eugen-rochko/
0 notes
Text
5 years after Superstorm Sandy, the lessons haven't sunk in
New Post has been published on http://usnewsaggregator.com/5-years-after-superstorm-sandy-the-lessons-havent-sunk-in/
5 years after Superstorm Sandy, the lessons haven't sunk in
Five years after Superstorm Sandy was supposed to have taught the U.S. a lesson about the dangers of living along the coast, disaster planning experts say there is no place in America truly prepared for climate change and the tempests it could bring.
That is true even in New York and New Jersey, where cities and towns got slammed by deadly floodwaters that rose out of the Atlantic on the evening of Oct. 29, 2012.
While billions have been spent to repair the damage, protecting vulnerable infrastructure, people and property across the nation from the more extreme weather that climate change could bring is going to require investment on a staggering scale, easily costing hundreds of billions, perhaps trillions.
Some coastal protection projects are moving forward, but the most ambitious ideas spurred by Sandy’s onslaught are still in the design stage, with questions about whether they will ever be built.
Some wonder whether the nation has the will to undertake such ventures, even after this past season brought more catastrophic storms, including Hurricane Harvey, which swamped Houston, and Hurricane Maria, which laid waste to Puerto Rico’s electrical grid.
“It felt after Sandy as if we might have finally had our wake-up call. We’d start to take these things seriously,” said Eric Klinenberg, director of the Institute for Public Knowledge, a think tank at New York University. “We’d make the kind of investment in climate security that we made in homeland security after Sept. 11. But of course nothing of the sort has happened.”
Some experts worry also that the ascendance of a climate-change skeptic to the White House may put the brakes on coastal protection efforts. In August, President Donald Trump rescinded President Barack Obama’s post-Sandy order requiring future sea level rise to be factored into federally funded infrastructure projects.
“Since the new administration is not using the CC word, the climate change word, it’s very hard to instill this forward-looking kind of attitude where you have to take into account sea level rise and how the flood zones expand,” says Klaus Jacob, a Columbia University scientist specializing in climate change adaptation.
And yet, some planners still hope that Sandy created momentum for projects that could serve as national models.
———
BIG IDEAS
After Sandy, which was blamed for at least 182 deaths in the U.S. and Caribbean and an estimated $65 billion in damage in this country alone, a government-funded competition called Rebuild by Design produced audacious ideas for defending the coast.
One concept, dubbed The Big U, would create 10 miles (16 kilometers) of floodwalls, berms and gates around lower Manhattan. Other ideas include erecting breakwaters around Staten Island that would double as oyster beds, and reconfiguring the Meadowlands, the polluted wetlands of urban New Jersey, with berms and marshes.
The U.S. Department of Housing and Urban Development put up $1 billion to get those projects started, but construction hasn’t begun on any of them.
Amy Chester, Rebuild By Design’s executive director, said it will take years to complete all the planning and gain government approvals and community support. And it’s not clear how much these projects will ultimately cost.
———
ONE CITY’S PLAN
LaTrenda Ross gets teary-eyed recalling the days after Sandy flooded the streets of Hoboken, New Jersey, a city of 50,000 people across the Hudson River from Manhattan that has been her home for 40 years.
“To not be able to go to work, to sit there in the dark, no elevators, no way out, was devastating,” she said. If something isn’t done to prevent a repeat, “there won’t even be a city of Hoboken. We might as well pack up and move now.”
New Jersey does, in fact, have a plan. Over the summer it hired an engineering firm to carry out one of the Rebuild by Design concepts: an anti-flood system for Hoboken. The $230 million project, funded by HUD, involves a series of floodwalls, pumping stations and water retention tanks.
Construction is due to start in 2019 and take at least three years.
Hoboken Mayor Dawn Zimmer said the cost is worth it. Eighty percent of the city flooded during Sandy, she said, causing as much as $1 billion in damage. Buildings were ruined. Three of the city’s four fire stations flooded. A vital commuter train station was knocked out for months.
Laura Baird, an engineer who helped develop the plan, said had the system been in place when Sandy hit, 85 percent of the city would have been protected.
———
PROGRESS AND DOUBT
While the grandest ideas about post-Sandy protections are still far from reality, there has been progress.
Communities on the New Jersey shore built sand dunes to hold back surf, or fortified existing ones. Power companies and New York’s subway system have put flood protections around key infrastructure. Hospitals moved electrical equipment out of basements.
The Army Corps of Engineers is scheduled to begin construction in 2019 on a 5-mile-long (8-kilometer-long), 20-foot-high (6-meter-high) seawall and promenade that would run along New York’s Staten Island in front of the neighborhoods hit hardest by Sandy. The project, which is still being designed, has an estimated price tag of $600 million and is scheduled for completion by 2022.
Michael Cappannari, a spokesman for the Federal Emergency Management Agency, said the administration is committed to helping communities recognize the risk and defend against flooding. He cited several federally funded projects underway, including construction of boardwalks with seawalls hidden beneath them and flood-proofing of sewage treatment systems.
It’s not enough, said Jacob, the Columbia scientist.
“It’s on a pace that’s dictated by the funds that are available, politically made available,” he said. “And if that snail’s pace continues, there’s a good chance that we may have another severe storm in town or in the region that will outpace that slow pace of improving the systems.”
Politicians locally and in Congress appear reluctant to get behind enormously expensive and sometimes divisive projects to deal with a threat that often feels hypothetical.
In Hoboken, for example, one proposal for a floodwall that would have protected more of the city was rejected because it would have blocked river views. Cities throughout the country have been reluctant to curtail building on the waterfront, because those spots are in such great demand from homebuyers.
In New York City, FEMA redrew the flood maps after Sandy, nearly doubling to 71,500 the number of buildings deemed to be in high-risk zones. The city objected for fear that would raise flood insurance rates and stifle waterfront development, and last year FEMA agreed to roll the flood zones back.
Bill Golden, president of the National Institute for Coastal and Harbor Infrastructure, said worrying about spending too much is shortsighted, and he blames the inaction on “a misunderstanding of the new reality that we face.”
A study released Monday by an international team of scientists predicted that between 2030 and 2045, New York City could experience storm surges of over 7.4 feet (2.25 meters) every five years, primarily because of sea level rise. That’s up from every 25 years in recent decades.
———
NO RETREAT
After Sandy, New York and New Jersey bought and emptied 1,250 homes in areas it deemed too difficult to protect from floods.
Patty Snyder, whose 53-year-old brother drowned when Sandy struck, was among the Staten Islanders who took a buyout. “I knew I was never going back, because I felt the city, state and federal governments never were going to do what needed to be done to stop future flooding,” she said.
But most people in the wrecked communities did return, whether because they were skeptical of the risk, confident about the planned Staten Island seawall, or simply unwilling to say goodbye to their homes.
Some homes were rebuilt on elevated foundations or pilings. Others were restored to the way they were before Sandy, leaving them just as vulnerable.
“I really don’t think it will happen again,” said Fred Steinfeld, a Staten Island resident whose basement filled with water during Sandy. “I just think that storms like that don’t happen that often.”
Dexter Dugan, whose Staten Island home got 9 feet of water, took steps to make it more storm-resistant, including putting heating and electrical systems on the second floor.
“You live near the water, it’s going to flood,” he said.
Original Article:
Click here
0 notes