#visitor entry software
Explore tagged Tumblr posts
Text
The Hush House Card Catalogue

@baja-blasted @terephin (please ignore the crabs)
//So the software I'm using to keep track of my books, lore bits, etc. is called Seatable! It wasn't my first choice for this project, I'm more familiar with Airtable (I've used it professionally), but Airtable's free plan doesn't let you color-code :c
//Seatable is a website that looks a lot like google sheets, but instead of building a spreadsheet, you're building a database. I knew I wanted a database rather than a spreadsheet for my card catalogue because it became pretty apparent early on that a spreadsheet would mean a lot of duplicate entries and be a lot more work to maintain, as well as monumentally more work if I wanted to use it for reference.
//My database isn't finished, and so I'm not really comfortable making it public, but I'm happy to walk through some of the things that I like most about it, that made me choose to make a database rather than a spreadsheet.
//The main things that were really important to me was being able to have (and filter by) multiple items in the same column, having lots of cross-linking between the different sheets in the base, and having different views depending on what I was looking to reference.
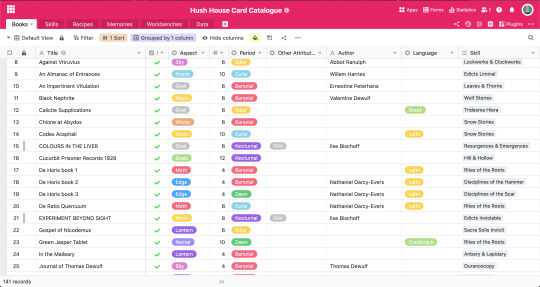
//These are my different tables right now, and the way they work is that each table has the most detailed information on each item, e.g. Books has the most detail on books, and Skills has the most detail on skills. But I have columns in each table that allow me to crosslink between them.
//So for each book, I have listed the skill and memory they give, but instead of writing each out individually it links to the corresponding entry in skills/memories
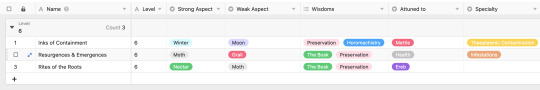
//And then over in the memories tab it has all the detail on the aspects, which wisdoms it can be committed to...
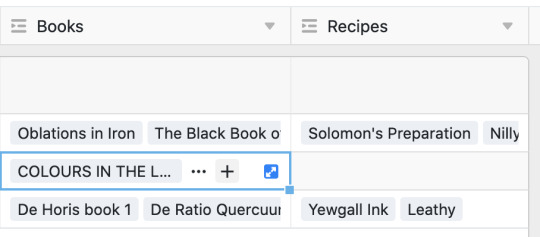
//...and every book this skill can be found in and every item it can be used to craft. And those boxes can be expanded so they're easier to read as well!
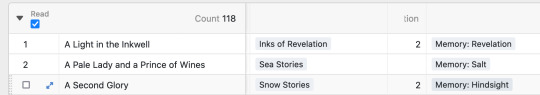
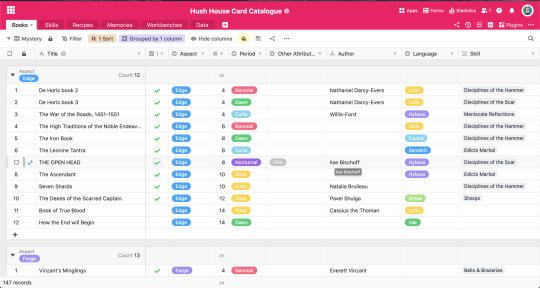
//I can also group and sort things in different views. My default view for books, for example, splits them into two categories—whether I've read the book or not—and then sorts the books in each category alphabetically. But I also have one that groups them all by mystery and then sorts them from low to high, and I have another that groups them by topic. Each of these views also omits columns that aren't relevant to that particular view, for example, if I'm searching for books by mystery to give to a visitor, it's important to know the author because it's fun to give people books they themselves have written, but I don't really care about what memories that book gives, or when I'm trying to connect lore dots, it doesn't matter whether or not the book is cursed and I don't need to include books I haven't read yet (and thus don't have topic tags for). The rows on the topic one are also bigger so I can better read the blurbs.
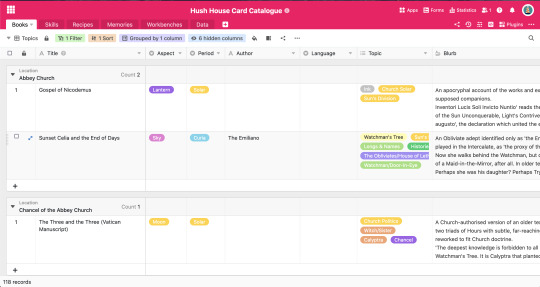
//Well, the topic one actually groups by location, because when I group it by topic, it splits it into every combination of my topic tags, rather that giving me "here are all your books about the mansus" "here are all your books about Longs and Names" so I've stored them all in different places in the house depending on what books I think are relevant to one another.
//It's still in progress, I don't have everything written down yet, and I want more data for workbenches, and I want to try and see if there's a way for it to, say, auto-match skills/souls to workbenches for committing to the tree or crafting certain recipes. Also my color-coding is in shambles bc I'm waiting for a friend to recover from covid so that they can make me a greasemonkey script to make it a little less... corporate...
//But yeah! I like it a lot, and it works really well for my purposes. I highly recommend trying it out, and I'm happy to answer questions!
105 notes
·
View notes
Text

Tripod Turnstile Overview Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are modern-day control devices for pedestrian flows. They are made use of in position where the entrance and also departure of individuals need to be controlled, such as smart neighborhoods, canteens, resorts, galleries, gyms, clubs, subways, terminals, docks, and so on location. Making use of Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile can make the flow of individuals orderly. Tripod Turnstile, Swing Turnstile, Flap Turnstile are made use of in combination with smart cards, finger prints, barcodes and also other identification system equipment to create an intelligent gain access to control channel control system; they are used in mix with computer systems, access control, participation, billing monitoring, ticket systems as well as other software program to develop a The smart Turnstile Gate thorough monitoring system can realize functions such as access control, attendance, consumption, ticketing, and current limiting. This Turnstile Gate administration system belongs to the "all-in-one card" as well as is mounted at flows such as neighborhoods, factories, wise buildings, canteens, etc. It can complete different management functions such as worker card traveling control, attendance at get off job as well as meals, and dining. Tripod Turnstile system attributes Fast and also practical: review the card in and out with one swipe. Utilize the authorized IC card and wave it before the wise Tripod Turnstile visitor to complete the Tripod Turnstile gate opening and also charge recording job. The card analysis is non-directional and the analysis as well as composing time is 0.1 seconds, which is quick and also practical. Protection and also confidentiality: Use history or local confirmation, authorized issuance, as well as unique identification, that is, the card can just be used in this system, and also it is confidential and also risk-free. Reliability: Card radio frequency induction, trustworthy and also steady, with the capacity to judge and also assume. Flexibility: The system can flexibly set entry as well as departure control workers consents, amount of time control, cardholder credibility as well as blacklist loss coverage, including cards as well as various other features. Versatility: Through authorization, the individual card can be utilized for "one-card" management such as parking, participation, access control, patrol, intake, and so on, making it very easy to understand numerous uses of one card. Simpleness: Easy to set up, basic to attach, the software application has a Chinese user interface as well as is very easy to operate. Tripod Turnstile, Swing Turnstile, and also Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are modern-day control tools for pedestrian passages. The usage of Tripod Turnstile, Swing Turnstile, and Flap Turnstile can make the flow of people orderly. Use the accredited IC card and also wave it in front of the clever Tripod Turnstile visitor to complete the Tripod Turnstile gate opening as well as fee recording work.
#Waist Height Turnstile#Flap Gate#Surveil Camera#Dead Bolt Locks#Gates Turnstiles#Turnstile Gate Nfc#Alcohol Breath Test#Uhf Rfid Reader Usb#Fingerprint Door Lock#Terra Quantum Bollard
9 notes
·
View notes
Text
Selenium Unleashed: Navigating the Dynamics of Web Application Automation
In the fast-paced world of software development, the need for efficient and reliable testing processes has led to the widespread adoption of Selenium—an open-source framework renowned for its prowess in automating web applications.
This versatility makes it the framework of choice for a diverse array of development environments, further emphasizing its significance in the realm of automated testing and underlining its importance in Selenium training in Chennai. This blog aims to unravel the intricacies of Selenium, exploring its key components, and delving into why it stands as the go-to choice for automated web testing.
Understanding Selenium's Toolbox: Key Components
1. Selenium WebDriver: Navigating the Web Programmatically
At the heart of Selenium lies WebDriver, a robust component that allows developers and testers to programmatically interact with web browsers. It furnishes a powerful programming interface for controlling browser behavior, navigating web pages, and interacting with various web elements. WebDriver serves as the backbone for creating dynamic and sophisticated automation scripts.
2. Selenium IDE: Record-and-Play Automation Simplified
Selenium IDE offers a user-friendly approach to automation through its record-and-playback functionality. This browser extension is especially beneficial for beginners, providing an intuitive way to create automation scripts without delving into intricate code. However, while Selenium IDE serves as an excellent starting point, Selenium WebDriver offers advanced users more control and flexibility.
3. Selenium Grid: The Power of Parallel Execution
Selenium Grid is a game-changer for test automation scalability. Its primary function is to facilitate the parallel execution of tests across multiple machines and browsers. By distributing test scripts across different environments simultaneously, Selenium Grid significantly reduces overall test execution time. This efficiency is particularly crucial in today's fast-paced development cycles.
Why Selenium is the Cornerstone of Automated Web Testing:
1. Cross-Browser Compatibility Testing: Ensuring a Seamless User Experience
One of Selenium's standout features is its ability to conduct cross-browser compatibility testing. Web applications must function seamlessly across various browsers, including Chrome, Firefox, Safari, and Internet Explorer. Selenium's prowess in this area ensures a consistent user experience, regardless of the browser a visitor chooses. Elevating its significance, Selenium serves as the linchpin in web application automation, making it an integral part of comprehensive training programs. For aspiring professionals in Chennai, harnessing Selenium's potential is made even more accessible through enrollment in the Best Selenium Training Institute.
2. Automation of Repetitive Tasks: Enhancing Efficiency
Selenium shines in automating repetitive and time-consuming tasks that are inherent in manual testing processes. Whether it's data entry, form submissions, or complex navigation scenarios, Selenium accelerates the testing process, reduces human error, and enhances overall efficiency.
3. Regression Testing: Safeguarding Code Integrity
As applications evolve, it's crucial to ensure that new changes don't compromise existing functionalities. Selenium's automation capabilities make it an ideal choice for regression testing—quickly validating that alterations to the codebase do not introduce unintended consequences to the application's core features.
4. Faster Feedback in Development Lifecycle: Accelerating Releases
Integrating Selenium tests into the development pipeline provides rapid feedback on code changes. This early detection of issues contributes to a faster and more reliable development lifecycle. Developers can address potential problems swiftly, minimizing the chances of bugs persisting into later stages of development.
5. Support for Multiple Programming Languages: Flexibility in Development
Selenium's support for multiple programming languages, including Java, Python, C#, Ruby, and JavaScript, grants developers the flexibility to choose the language that aligns with their preferences or project requirements. This adaptability has contributed significantly to Selenium's widespread adoption across diverse development environments.
6. Flexibility and Extensibility: Tailoring Testing Environments
Selenium's modular architecture and expansive ecosystem of third-party tools enhance its flexibility and extensibility. Teams can integrate Selenium with various testing frameworks, build tools, and reporting tools, tailoring their testing environment to suit specific project needs.
7. Cost-Efficient Testing: Open Source Accessibility
Being an open-source framework, Selenium offers a cost-effective solution for test automation. Organizations can leverage Selenium without incurring licensing fees, making it accessible to businesses of all sizes. The community-driven development ensures regular updates and improvements to keep pace with industry demands.
8. Compatibility with Continuous Integration: Seamless Development Workflow
Selenium seamlessly integrates with popular Continuous Integration (CI) tools like Jenkins. This integration allows automated tests to be triggered automatically with each code commit, ensuring the application's integrity is maintained throughout the development process. The collaboration between Selenium and CI tools streamlines the development workflow.
9. Support for Complex Test Scenarios: Tackling Modern Web Challenges
In the era of modern web applications with intricate user interfaces, Selenium proves its mettle by supporting complex test scenarios. It excels in handling dynamic web elements, pop-ups, and frames—features that are integral to the functionality of today's sophisticated web applications.

In conclusion, Selenium stands as an indispensable tool in the landscape of automated web testing. Whether it's ensuring cross-browser compatibility, accelerating testing processes, or supporting complex test scenarios, Selenium empowers development teams to deliver high-quality web applications. As the software industry continues to evolve, Selenium remains at the forefront, adapting to new challenges and contributing to the creation of robust and reliable web experiences. As a cornerstone of automated web testing, Selenium continues to shape the way software is developed, tested, and delivered to end-users.
2 notes
·
View notes
Text
How to Choose the Right Visitor Management System for Your Organization
In today’s fast-paced business environment, ensuring security while providing a seamless visitor experience is crucial. Organizations, from corporate offices to healthcare facilities and educational institutions, are increasingly turning to visitor management systems to streamline their check-in processes, enhance security, and maintain accurate visitor logs.
Traditional sign-in methods, such as paper logbooks, are inefficient and prone to errors. Modern visitor management systems offer digital, cloud-based solutions that enhance security, compliance, and operational efficiency. However, with numerous options available, selecting the right system can be challenging. This guide will help you understand the key factors to consider when choosing the best visitor management system for your organization.
1. Identify Your Organization’s Specific Needs
Before selecting a visitor management system, start by analyzing your organization’s specific requirements. Consider:
The number of visitors you receive daily.
Security protocols and compliance requirements.
Integration needs with existing access control systems.
The need for pre-registration and touchless check-ins.
Understanding these aspects will help you narrow down the most suitable solution for your business.
2. Opt for a Cloud-Based System for Remote Access and Scalability
A cloud-based visitor management system offers remote access, real-time data updates, and better scalability. Unlike traditional on-premise solutions, cloud-based systems eliminate the need for expensive hardware and maintenance, allowing businesses to manage visitor access from any location.
Solutions like Spintly provide a seamless cloud-based approach, ensuring smooth visitor authentication and management without requiring extensive infrastructure.
3. Prioritize Security and Compliance Features
Security is one of the most important aspects of visitor management. The right visitor management system should include features such as:
ID verification for secure authentication.
Access control integration to ensure visitors only enter permitted areas.
Real-time visitor tracking and alerts.
Data encryption to protect sensitive visitor information.
Compliance with regulations such as GDPR, HIPAA, or industry-specific mandates is also crucial to ensure your organization remains legally compliant.
4. Choose a User-Friendly and Contactless Experience
A visitor management system should be intuitive and easy to use for both visitors and employees. A system with features like self-check-in kiosks, mobile app support, and touchless entry options enhances the user experience while reducing wait times.
In a post-pandemic world, contactless check-in solutions, such as QR code scanning and facial recognition, have become essential in maintaining hygiene and security. A visitor management system like Spintly offers innovative, touch-free access solutions that align with modern workplace demands.
5. Ensure Integration with Existing Security and Workplace Systems
The best visitor management systems integrate seamlessly with your existing security and workplace management tools, including:
Access control systems.
Employee attendance tracking.
Surveillance cameras.
Facility management software.
By integrating your visitor management system with these tools, you can create a fully automated and secure visitor experience, reducing administrative burdens.
6. Look for Customization and Branding Options
Every organization has unique needs, so selecting a visitor management system that offers customization is crucial. A system should allow businesses to:
Customize check-in workflows based on visitor type.
Add branding elements like logos and custom messages.
Set up different access permissions for guests, contractors, and employees.
Customizing the visitor experience improves brand perception and creates a seamless welcome process.
7. Analyze Reporting and Analytics Capabilities
A strong visitor management system should provide detailed reports and analytics to help organizations track visitor activity, peak hours, and security incidents. Comprehensive reporting enhances decision-making and allows for better resource planning.
Real-time insights into visitor data also help businesses ensure compliance with safety regulations and maintain audit trails for security purposes.
8. Evaluate the Cost and ROI
Budget plays a significant role in selecting a visitor management system. While cost is important, organizations should focus on the long-term return on investment (ROI). A feature-rich, cloud-based system may have a higher upfront cost but can save time, reduce manual work, and enhance security, ultimately leading to cost savings.
Solutions like Spintly provide cost-effective and scalable visitor management systems that ensure maximum efficiency without unnecessary expenses.
Conclusion
Choosing the right visitor management system is essential for organizations looking to enhance security, improve operational efficiency, and provide a seamless visitor experience. A cloud-based, user-friendly, and scalable solution, like those offered by Spintly, can help businesses achieve these goals effortlessly.
By evaluating your security needs, prioritizing integration, and opting for a customizable and scalable solution, you can ensure your organization is equipped with the best visitor management system to enhance workplace security and efficiency in the digital age.
#biometrics#smartbuilding#visitormanagement#visitor management system#access control system#mobile access#access control solutions#spintly#smartacess#accesscontrol
0 notes
Text
Tips for Seamless Integration of CCTV Systems with Access Control

Modern organizations together with business operations and residential communities and government facilities place security at their highest priority. Security enhancement results from CCTV system integration with access control through real-time surveillance and automatic entry control and safety standard compliance. Securing organizations in Dubai through collaboration with a SIRA approved CCTV company in Dubai enables both local security law compliance and peak system operation.
This blog explores the advantages of joining CCTV networks with access control systems while presenting functional steps to achieve smooth implementation.
Why Integrate CCTV with Access Control?
Security systems become more efficient when CCTV surveillance unites with access control measures because they provide better safety protection alongside enhanced system monitoring and clear operational accountability. Here are some key benefits:
1. Enhanced Security
The real-time surveillance of entry areas verifies that permitted individuals remain the only ones able to access the premises.
The system generates instant warning signals when unauthorized access attempts happen to improve emergency responses.
The merger between access control systems offers protection against individuals who sign up after authorized users because unauthorized entry attempts become obvious before they happen.
2. Better Incident Investigation
Security incidents become easier to investigate through the merging of video footage with entry and exit logs within the system.
The system verifies individuals through multiple security checkpoints to prevent cases of fraud.
3. Improved Operational Efficiency
The automation of access control systems eliminates the requirement for human operations in security checks.
The system allows employees with visitors to access buildings without delays which enhances productivity levels.
4. Compliance with Security Regulations
Every organization operating within Dubai must abide by SIRA regulations to deliver appropriate security management.
The implementation of security mandates in Dubai becomes feasible when businesses team up with certified CCTV companies from SIRA.
The following part explains practical implementation steps for CCTV and access control integration.
Tips for Seamless Integration

1. Choose Compatible Hardware & Software
The selection of CCTV cameras along with access control systems that can operate together constitutes one of the essential initial steps. Consider:
IP-based CCTV cameras for real-time monitoring.
The implementation of integration-friendly Access control systems should include API functionalities.
Cloud-based solutions for centralized access and remote management.
2. Create One System to Control Security Operations
Security platforms that unify systems allow CCTV cameras along with access controls to exchange data without interruption. Benefits include:
The system generates instant alerts to notify about all attempted unauthorized entrance activities.
A single system collects unified records which merge both access records and CCTV recordings.
Easy monitoring from a single dashboard.
3. Ensure Proper Camera Placement

CCTV camera placement locations need to be carefully strategic because this ensures full visibility of essential entry points. Best practices include:
The surveillance system should include cameras installed at entry points together with exit points and parking spaces and restricted locations.
Wide-angle photographic lenses should be employed to monitor broad areas.
The cameras need installation at a specific position which provides unobstructed views of faces.
4. Companies should use AI and analytics technologies to achieve superior security solutions.
Recent security systems use artificial intelligence (AI) together with analytical methods to enhance their access control features and surveillance capabilities. AI can:
The system detects unauthorized persons breaking in while sending instant warnings to users.
Identify loitering and suspicious behavior.
Regarding access authentication the implementation of automatic face recognition technology should be part of the system.
5. Ensure Secure Network Connectivity
A properly connected system needs an organized network with stable security to operate efficiently. Follow these network security tips:
Installing encryption within communication protocols will stop hacking occurrences.
The system requires firewalls alongside cybersecurity measures for safeguarding sensitive data.
Regular system updates should be performed to seal possible security vulnerabilities.
6. Conduct Regular Maintenance & Updates

The following steps ensure a trouble-free operation of integration:
A proper servicing routine must be applied to both CCTV cameras and access control systems.
Conduct software updates for schedule purposes to preserve both system compatibility and security.
Professionals from SIRA approved CCTV companies in Dubai should handle all maintenance tasks.
7. Train Security Staff & Employees
Training of personnel who operate technology remains the vital factor that determines the effectiveness of technological systems. Provide:
Security awareness training for employees.
Security personnel require particular training on integrated systems as part of their practical curriculum.
Clear protocols for responding to security alerts.
8. Ensure Scalability for Future Growth
Your organization must purchase security solutions which can expand their capabilities as their needs change. Consider:
The implementation of cloud-based access control solution systems provides functionality for increased user numbers.
The organization requires CCTV cameras with upgraded high-resolution capabilities for future expansion.
Such a system offers open integration for new security products.
9. Security Audits in addition to Compliance Tests should be performed
Security audits performed regularly help reveal all system vulnerabilities within the integration. Steps to follow:
Conduct quarterly security assessments.
The organization must adhere to standards set by SIRA in Dubai.
Policies need to be updated through adaptations to new security threats and workflow recommendations from the industry.
Conclusion
CCTV systems linked to access control solutions boost security measures as they allow better surveillance alongside operational efficiency improvements. Businesses that select compatible technology in combination with AI-driven solutions and network security and collaborate with SIRA-approved CCTV firms in Dubai will obtain a seamless effective security framework.
Your assets along with employees and sensitive information require protection which you can achieve through investment in the right security partner now. A secure system implementation provides both safety measures and mental comfort for the users.
#cctv camera#cctv installation#cctv installers#cctv surveillance#dubai#cctvfootage#safety#search and rescue#access control system#fire and rescue
0 notes
Text
Why Best Outdoor WIFI CCTV Cameras Are Essential
In today’s fast-paced world, securing your home or business has never been more crucial. Outdoor WIFI CCTV cameras have revolutionized the security industry by offering remote monitoring, easy installation, and advanced features like motion detection and night vision. For Indian consumers, factors like affordability, durability, and weather resistance are key considerations.
This guide highlights the best outdoor WIFI CCTV cameras in India, their unique features, and why they stand out as reliable choices for your security needs.
What to Look for in an Outdoor WIFI CCTV Camera
1. Weatherproof Design
Outdoor cameras must withstand India’s varying weather conditions, from heavy monsoons to extreme heat. Look for cameras with at least an IP65 or IP66 rating for dust and water resistance.
2. Night Vision
Security doesn’t stop after sunset. Cameras with infrared night vision or color night vision ensure round-the-clock surveillance.
3. Motion Detection and Alerts
Smart motion detection sends instant alerts to your smartphone, helping you respond to suspicious activity in real time.
4. Video Resolution
High-definition (HD) or ultra-HD (4K) video ensures clear footage, which is critical for identifying faces or license plates.
5. Two-Way Audio
This feature allows you to communicate with visitors or deter intruders directly from your phone.
6. Storage Options
Opt for cameras that support both cloud storage and local SD card storage for flexibility.
Benefits of Outdoor WIFI CCTV Cameras
Remote Monitoring: Monitor your property in real-time through smartphone apps, whether you’re at home or traveling.
Enhanced Security: Detect and deter suspicious activity with motion alerts and two-way audio.
Cost-Effective: Modern WIFI cameras eliminate the need for extensive wiring, reducing installation costs.
Easy Storage: Choose between cloud storage for convenience or local SD cards for affordability.
Deterrence Effect: Visible cameras discourage intruders, enhancing safety.
Tips for Installing Outdoor WIFI CCTV Cameras
Choose Strategic Locations: Place cameras near entry points like gates, doors, and driveways.
Ensure Proper Lighting: While most cameras have night vision, good lighting enhances visibility.
Secure the Camera: Use sturdy mounts to prevent tampering.
Test WIFI Signal: Ensure the camera’s location has a strong WIFI connection for seamless performance.
Update Software Regularly: Keep your camera firmware up to date for optimal security.
Conclusion: Choosing the Right Outdoor WIFI CCTV Camera
Best outdoor WIFI CCTV cameras in India are a must-have for securing your home or business. Whether you prioritize affordability, advanced features, or durability, there’s a camera for every need in India. From the high-performance TP-Link Tapo C310 to the budget-friendly Realme Smart Cam 360°, these options provide reliable security without stretching your budget.
Investing in the right camera ensures peace of mind, knowing that your property is protected 24/7.
0 notes
Text
Crowd Management at the Maha Kumbh

The Uttar Pradesh (UP) government is primarily counting visitors to the Kumbh Mela using a combination of electronic surveillance systems, including CCTV cameras, facial recognition technology, and footfall counters installed at key entry points to the festival grounds, allowing them to estimate the number of people entering and exiting the area in real-time.
Facial recognition software will identify unique facial features of individuals passing through, potentially allowing for a more accurate count by reducing double-counting.
Footfall count at strategic places in the Kumbh will give them an indication of number of people visiting a specific place, and the direction of their movement, allowing the gov to better manage the crowds and avoid stampede at peak periods. Data collected data from cameras and footfall counters will than processed through various software to generate estimates of visitor numbers to the Maha Kumbh 2025
0 notes
Text

Tripod Turnstile Overview Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are modern control devices for pedestrian passages. They are used in places where the entry as well as exit of people require to be managed, such as wise neighborhoods, canteens, hotels, museums, gymnasiums, clubs, subways, terminals, anchors, and so on place. Making use of Tripod Turnstile, Swing Turnstile, and Flap Turnstile can make the flow of people organized. Tripod Turnstile, Swing Turnstile, Flap Turnstile are used in combination with smart cards, fingerprints, barcodes and also various other recognition system devices to form an intelligent gain access to control channel control system; they are utilized in mix with computers, access control, participation, billing monitoring, ticket systems and various other software application to form a The intelligent Turnstile Gate detailed monitoring system can realize functions such as access control, attendance, consumption, ticketing, as well as current limiting. This Turnstile Gate monitoring system becomes part of the "all-in-one card" as well as is mounted at flows such as areas, factories, smart buildings, canteens, and so on. It can complete various administration features such as staff member card travel control, attendance at leave job as well as meals, and also eating. Tripod Turnstile system functions Fast as well as convenient: read the card in and out with one swipe. Utilize the authorized IC card and wave it in front of the smart Tripod Turnstile viewers to finish the Tripod Turnstile gate opening and charge recording work. The card analysis is non-directional and the analysis and composing time is 0.1 secs, which is practical and also rapid. Protection and confidentiality: Use background or regional confirmation, licensed issuance, and distinct identification, that is, the card can just be utilized in this system, and it is risk-free as well as private. Integrity: Card radio frequency induction, reputable and steady, with the capability to court as well as believe. Adaptability: The system can flexibly establish access and also leave control personnel authorizations, period control, cardholder credibility as well as blacklist loss coverage, adding cards as well as other features. Versatility: Through consent, the user card can be made use of for "one-card" management such as parking, attendance, accessibility control, patrol, intake, and so on, making it very easy to realize multiple uses one card. Simpleness: Easy to install, simple to connect, the software has a Chinese user interface and also is easy to run. Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are modern control gadgets for pedestrian flows. The use of Tripod Turnstile, Swing Turnstile, and also Flap Turnstile can make the circulation of individuals orderly. Make use of the authorized IC card as well as wave it in front of the smart Tripod Turnstile visitor to finish the Tripod Turnstile gate opening and charge recording work.
#Tripod Turnstiles#Anpr Itc#Rising Bollard#Event Turnstile#Tripod Turnstile#Movable Road Pile#Elevator Controller#Flap Turnstile Gate#Kiosk Qr Code Reader#Flexible Bollard Post
3 notes
·
View notes
Text
How to Improve Your Construction Site’s Security with Technology
Construction sites are frequent targets for theft, vandalism, and unauthorized access, often resulting in financial losses and project delays. Implementing advanced technological solutions can help mitigate these risks effectively. Below, we outline detailed strategies to enhance construction site security using cutting-edge technology.
Understanding the Importance of Construction Site Security
The nature of construction projects makes them vulnerable to security breaches. High-value equipment, raw materials, and limited on-site personnel during off-hours create ideal conditions for theft and damage. By leveraging technological advancements, construction companies can significantly reduce these vulnerabilities.
1. Deploy Smart Surveillance Systems
Smart surveillance systems are the backbone of modern construction site security. By incorporating advanced technologies, you can monitor activities and deter potential threats effectively:
High-Definition Cameras: Install cameras with night vision and wide-angle capabilities to monitor expansive areas.
Motion Detection: Equip cameras with motion-sensing capabilities to trigger alerts for any suspicious movements.
Remote Monitoring: Enable off-site monitoring through mobile apps or web portals, ensuring real-time visibility.
AI-Driven Analytics: Use artificial intelligence to detect unusual patterns and reduce false alarms, ensuring efficient response times.
2. Integrate Access Control Systems
Restricting and monitoring access is critical for preventing unauthorized entry. Access control systems can significantly enhance site security:
Biometric Systems: Use fingerprint scanners or facial recognition for authorized personnel.
RFID Badges: Provide RFID-enabled badges to track workers’ entry and exit.
Smart Gates: Implement automated gates with integrated surveillance to control vehicle access.
Visitor Management Software: Maintain a digital log of all visitors to track site activities.
3. Leverage Drone Technology for Surveillance
Drones provide a bird’s-eye view of large construction sites, ensuring comprehensive coverage:
Routine Patrols: Automate drone patrols during off-hours to monitor high-risk zones.
Thermal Imaging: Use thermal cameras to detect intruders hiding in poorly lit areas.
Live Feeds: Stream real-time drone footage to security teams for prompt action.
Incident Documentation: Capture evidence of unauthorized activities for legal and insurance purposes.
4. Utilize IoT Sensors for Real-Time Alerts
The Internet of Things (IoT) allows seamless connectivity between devices, enabling real-time threat detection:
Vibration Sensors: Install sensors on fences and barriers to detect tampering.
Proximity Sensors: Alert security teams to unauthorized movements near critical areas.
Environmental Monitoring: Detect smoke, gas leaks, or flooding that could jeopardize safety.
Integration with Alarms: Connect IoT sensors with alarm systems for immediate notifications.
5. Implement Advanced Alarm Systems
Modern alarm systems offer enhanced features for superior site protection:
Audio Warnings: Equip alarms with pre-recorded warnings to deter intruders.
Centralized Control Panels: Manage all alarms from a single hub for streamlined operations.
Wireless Alarms: Use wireless systems to cover remote or temporary areas without complex installations.
24/7 Monitoring Services: Partner with professional monitoring services for rapid incident response.
6. Employ Construction-Specific Software
Construction-specific security software can optimize on-site safety:
Asset Tracking: Monitor equipment locations to prevent theft and loss.
Employee Monitoring: Track workers’ activities to ensure compliance with security protocols.
Incident Reporting: Log security breaches and generate detailed reports for management.
Integration with Mobile Apps: Access critical security data on-the-go for immediate decision-making.
7. Enhance Perimeter Security with Smart Fencing
Smart fencing solutions act as the first line of defense:
Electric Fences: Deter intruders with visible deterrents like electric fencing.
Perimeter Sensors: Detect and alert security teams of breaches in real-time.
CCTV Integration: Pair fences with surveillance cameras to monitor attempted intrusions.
Mobile Notifications: Receive alerts on mobile devices for instant action.
8. Use GPS Tracking for Equipment and Vehicles
Construction sites house valuable machinery that is often targeted by thieves. GPS tracking offers a reliable solution:
Real-Time Location Tracking: Monitor the exact location of equipment and vehicles.
Geo-Fencing: Set virtual boundaries and receive alerts when assets leave the designated area.
Operational Efficiency: Track equipment usage to optimize project timelines and reduce idle time.
Theft Recovery: Aid in the recovery of stolen equipment with accurate GPS data.
9. Train Staff on Security Protocols
Even with the best technology, human error can compromise site security. Regular training ensures:
Awareness of Security Systems: Educate staff on using surveillance, alarms, and access control systems.
Emergency Procedures: Prepare workers to respond to emergencies effectively.
Reporting Protocols: Encourage immediate reporting of suspicious activities.
Ongoing Updates: Keep staff informed about new security measures and technological upgrades.
10. Invest in Professional Security Services
Professional security services offer comprehensive site protection:
On-Site Guards: Deploy trained guards for physical deterrence.
Mobile Patrols: Schedule regular patrols to inspect vulnerable areas.
24/7 Monitoring: Ensure continuous surveillance with professional teams.
Custom Security Plans: Develop tailored solutions for specific project requirements.
Conclusion
Improving construction site security with technology is essential to protect assets, maintain productivity, and ensure project success. By implementing the strategies outlined above, construction companies can significantly enhance their security measures and deter potential threats.
1 note
·
View note
Text
Troubleshooting Made Easy: Why You Need cPanel Server Support
When managing a website or a web hosting server, things don’t always go as smoothly as planned. Whether it’s a slow website, email issues, or server crashes, troubleshooting can quickly become a time-consuming nightmare. However, one tool that can help simplify the entire process is cPanel—a widely used control panel for web hosting management. While cPanel offers a user-friendly interface, complex issues can still arise, making cPanel server support a necessity for ensuring your website runs smoothly.
In this blog, we’ll explore the common problems website owners face, why cPanel server support is vital, and how it can help troubleshoot issues more efficiently.
Common Website Issues You Can Solve with cPanel Server Support
Before diving into why you need professional cPanel support, let’s take a look at the types of problems that often require troubleshooting:
1. Slow Website Performance
One of the most frustrating problems for both web owners and visitors is slow website loading speeds. It can be caused by a variety of factors, including:
Server resource exhaustion
Misconfigured settings
Outdated plugins or themes
Malware or malicious software
cPanel offers tools like Resource Usage, which helps identify the sources of slowdowns. Through cPanel support, technicians can optimize your server settings or provide recommendations for enhancing your website’s performance.
2. Email Deliverability Issues
If you're using cPanel’s built-in email management features, you might encounter issues like email bouncing, not being delivered, or being flagged as spam. Misconfigured DNS settings, incorrect MX records, or outdated scripts can lead to these problems.
With the help of cPanel server support, an expert can walk you through the diagnostic tools available, such as the Email Trace and MX Entry, to pinpoint and resolve the issue efficiently.
3. Server Downtime and Crashes
Experiencing server downtime is one of the most serious problems for a business. It can lead to a loss of revenue, customer trust, and more. While cPanel provides monitoring tools like Error Logs and Resource Usage, troubleshooting server crashes often requires advanced knowledge.
Professional cPanel server support can quickly assess the server’s performance, identify issues like high CPU usage or excessive traffic, and help bring your website back online promptly.
4. Backup and Restoration Problems
Sometimes, website owners struggle to restore from backups or realize that their backups aren’t working correctly. cPanel comes with an easy-to-use backup system, but it’s important to make sure the process is set up properly.
With server support, experts can assist in backing up your files, databases, and even entire websites, ensuring you can restore your site quickly in case of emergencies.
5. Security Vulnerabilities
Web hosting security is an ongoing concern for anyone with an online presence. cPanel offers a range of security features like SSL/TLS management, firewall settings, and Two-Factor Authentication (2FA). However, without proper configuration, your site may remain vulnerable to hacking attempts.
By seeking professional cPanel server support, you can receive advice on strengthening your server’s security, including patching vulnerabilities, preventing DDoS attacks, and optimizing firewall settings.
Why You Need cPanel Server Support
Now that we’ve covered common issues that can arise, let’s look at why cPanel server support is essential for troubleshooting and maintaining a healthy website.
1. Expertise and Experience
Although cPanel’s interface is user-friendly, many troubleshooting scenarios require in-depth technical knowledge. Professionals with extensive experience can quickly identify problems, saving you valuable time. They can also offer proactive solutions, preventing recurring issues before they impact your site’s performance.
2. 24/7 Support Availability
Websites and servers don’t operate on a 9-to-5 schedule, which means issues can occur at any time of the day or night. Whether you experience problems in the middle of the night or on weekends, cPanel server support ensures that help is always available. With round-the-clock access to experts, you can resolve issues before they escalate.
3. Time and Cost Efficiency
Trying to fix server problems on your own can lead to wasted hours—especially when you aren’t sure where to start. Seeking cPanel server support allows you to focus on your business and let the experts handle the technical side. In the long run, this approach can save both time and money, as issues are resolved quickly and effectively.
4. Continuous Server Optimization
Your hosting environment is constantly evolving. As software updates are released and new technologies emerge, keeping your server optimized is crucial. cPanel server support ensures that your hosting environment is always up-to-date and performing at its best. From optimizing databases to keeping your server secure, continuous monitoring and maintenance can prevent issues from developing in the first place.
5. Peace of Mind
Ultimately, professional support provides peace of mind. When you have access to experienced professionals, you know that issues will be addressed quickly and accurately. You can rest easy knowing that your website’s performance, security, and functionality are in expert hands.
Conclusion
In today’s fast-paced digital world, having a website that runs smoothly is essential for success. With cPanel server support, troubleshooting becomes an easy and efficient process. From improving performance to resolving email issues and ensuring security, the right support can make all the difference. Don’t wait until problems arise—investing in cPanel support now can help prevent future issues and give you peace of mind as your business grows.
Whether you're a beginner or an experienced website owner, cPanel server support is a vital resource for keeping your server and website running like a well-oiled machine.
0 notes
Text
Enhanced Protection and Seamless Access: Security Access Control Services in Orlando, FL
In today’s rapidly evolving world, where security breaches and unauthorized access are ever-growing concerns, the need for comprehensive security solutions has never been more crucial. One such solution that has gained significant traction in recent years is Security Access Control Services. These services are designed to safeguard physical spaces, providing businesses and individuals with enhanced protection against potential threats. When considering top-tier security systems in the Orlando, FL area, Security Access Control Services in Orlando, FL stand out as a reliable and effective choice.
What Are Security Access Control Services?
Security Access Control refers to the systems and protocols used to monitor, restrict, and manage access to various areas within a facility or building. These systems utilize a combination of hardware and software to ensure that only authorized individuals are granted access, while others are kept out. Depending on the facility’s needs, access control systems may include keycards, biometric scans, PIN codes, and remote monitoring solutions. In essence, they help organizations regulate who can enter specific areas, enhancing both physical security and operational efficiency.
Key Benefits of Security Access Control Services
Enhanced Security The primary function of Security Access Control Services is to keep intruders and unauthorized individuals at bay. By installing security access control systems, businesses and property owners can ensure that only individuals with the proper credentials can access restricted areas, such as offices, warehouses, or server rooms. These systems can be customized to grant varying levels of access based on roles, significantly reducing the risk of theft, vandalism, and unauthorized entry.
Audit Trail and Monitoring One of the most valuable features of access control systems is their ability to create a digital record of entry and exit. By tracking who accessed which areas and at what time, businesses can maintain an audit trail that can be used for reporting, investigations, or compliance purposes. This feature is especially beneficial in high-security environments like data centers or government buildings, where every movement within the facility must be logged.
Scalability and Flexibility Security Access Control Services are highly scalable, meaning they can be tailored to suit the unique needs of businesses of all sizes. Whether it’s a small office or a large multi-building campus, access control systems can be customized to provide security at every level. Furthermore, as the business grows or changes, access control systems can be easily updated to include new areas or personnel without the need for a complete overhaul.
Remote Management A major advantage of modern access control systems is the ability to manage them remotely. For businesses with multiple locations or facilities, remote access management ensures that security can be monitored from anywhere, at any time. With mobile apps or centralized management platforms, security teams can lock or unlock doors, grant or revoke access permissions, and receive real-time alerts about security breaches or attempted unauthorized entries.
Employee and Visitor Management In addition to regulating employee access, Security Access Control Services can also streamline the management of visitors. Through systems that issue temporary access credentials or integrate with visitor management software, businesses can provide guests with a seamless check-in process while ensuring that they only access authorized areas. This helps businesses maintain a balance between welcoming visitors and safeguarding sensitive spaces.
Why Choose Security Access Control Services in Orlando, FL?
Orlando, FL is a bustling hub with diverse businesses, educational institutions, and government offices. As the city continues to grow, so does the demand for reliable security solutions. Security Access Control Services in Orlando, FL offer cutting-edge technology to cater to the unique security needs of this dynamic region. With a wide range of solutions available, Orlando businesses and property owners can choose the most suitable systems to secure their premises while benefiting from the added convenience and efficiency of modern access control technology.
Moreover, local security service providers in Orlando understand the specific security challenges faced by the region, offering personalized services that ensure maximum protection. Whether you're looking to secure a commercial building, a residential complex, or a healthcare facility, Orlando-based access control services can be tailored to meet your exact requirements.
Conclusion
In an era where security threats are constantly evolving, implementing a reliable Security Access Control Service is an essential step toward safeguarding your business or property. With the right access control system in place, you can significantly reduce the risk of unauthorized entry, improve operational efficiency, and maintain complete control over who accesses sensitive areas. For those in the Orlando, FL area, Security Access Control Services in Orlando, FL offer unparalleled security solutions that blend cutting-edge technology with expert service, ensuring that your spaces remain safe and secure.
0 notes
Text
The Role of Biometrics in Access Control Systems
In an increasingly digital world, security has become a top priority for organizations. Whether it’s protecting sensitive information or ensuring physical security, robust systems are needed to safeguard assets. One of the most reliable advancements in this space is biometric technology. Biometric solutions in access control systems offer enhanced security, convenience, and efficiency, making them an integral part of modern security strategies.
Understanding Access Control Systems
Access control systems are designed to regulate who can enter a building or access certain areas within it. These systems use identification methods such as PIN codes, key cards, or, increasingly, biometric data. While traditional methods still have their place, they come with limitations like the risk of lost keys or forgotten passwords. Biometrics addresses these challenges by using unique biological traits for authentication.
What Are Biometrics?
Biometrics refers to the measurement and analysis of unique physical or behavioral characteristics, such as:
Fingerprints
Facial Recognition
Iris Scanning
Voice Recognition
Hand Geometry
By using these traits, biometric systems provide a highly secure and personalized method for identity verification.
The Integration of Biometrics in Access Control Systems
Biometric access control systems use biometric data to grant or deny access. For example, an employee’s fingerprint might be scanned to unlock an office door. Here’s how biometrics is revolutionizing access control:
1. Enhanced Security
Biometric data is nearly impossible to duplicate or forge, significantly reducing the risk of unauthorized access. Unlike traditional methods that rely on something you know (passwords) or something you have (key cards), biometrics relies on something you are, adding an extra layer of security.
2. Elimination of Common Weaknesses
Traditional access control systems often fail due to lost keys, stolen access cards, or shared passwords. Biometric systems eliminate these vulnerabilities by requiring the presence of the individual for authentication.
3. Seamless Integration
Modern biometric access control systems, such as those offered by Spintly, integrate seamlessly with existing security infrastructures. They can be linked to other systems like surveillance cameras or employee management software, providing a holistic approach to security.
Key Benefits of Biometric Access Control Systems
1. Unmatched Accuracy
Biometric systems provide unparalleled accuracy by using unique identifiers. Fingerprints and iris patterns, for instance, are unique to each individual, ensuring precise authentication.
2. Scalability
Biometric solutions can scale with your business. Whether you’re a small business or a large enterprise, these systems can accommodate your security needs.
3. Time-Efficiency
By automating the authentication process, biometric systems reduce the time employees spend on manual access methods. Quick and hassle-free authentication ensures smooth operations.
4. Improved User Experience
Biometric systems are user-friendly. Employees and visitors don’t need to remember complex passwords or carry access cards—they simply use their biometric data for authentication.
5. Audit Trails
Biometric access control systems maintain detailed logs of access events, making it easy to track who entered specific areas and when. This feature is invaluable for audits and incident investigations.
Applications of Biometric Access Control Systems
Biometric access control systems have found applications across a variety of industries:
Corporate Offices: Secure entry points and restricted areas.
Healthcare Facilities: Protect sensitive patient data and restricted zones like laboratories.
Educational Institutions: Manage access to classrooms, libraries, and hostels.
Government Buildings: Enhance security for sensitive documents and restricted areas.
Residential Complexes: Provide seamless and secure access to residents and authorized visitors.
Challenges of Implementing Biometric Systems
While biometric systems offer many benefits, they are not without challenges:
Data Privacy Concerns: Storing and processing biometric data raises privacy issues. Robust encryption and compliance with data protection regulations are essential.
Initial Costs: Biometric systems can be expensive to install. However, the long-term benefits outweigh the initial investment.
Environmental Factors: Some biometric methods, like fingerprint scanning, may be less effective in extreme weather conditions or for individuals with specific physical conditions.
Future Trends in Biometric Access Control
Biometric technology continues to evolve, with advancements such as:
AI and Machine Learning: Enhancing the accuracy and speed of biometric recognition systems.
Cloud Integration: Cloud-based biometric solutions allow real-time data access and integration across multiple locations.
Touchless Biometrics: Technologies like facial recognition and iris scanning provide hygienic and contactless authentication methods, particularly important in post-pandemic scenarios.
Companies like Spintly are at the forefront of these advancements, providing cutting-edge biometric solutions tailored to the needs of modern enterprises.
Why Choose Biometrics for Access Control?
Biometric access control systems are a game-changer for businesses seeking reliable and secure access management. By leveraging unique human traits, these systems eliminate common vulnerabilities of traditional methods, streamline operations, and enhance security.
Organizations looking to future-proof their security infrastructure should consider biometric access control systems as an investment in safety and efficiency. For businesses seeking innovative and scalable solutions, exploring offerings from industry leaders like Spintly can be a great start.
Conclusion
The role of biometrics in access control systems is pivotal in addressing modern security challenges. By ensuring precise and secure authentication, these systems not only protect assets but also improve operational efficiency.
As technology advances, the adoption of biometric access control systems will continue to grow, shaping the future of workplace security. For organizations ready to embrace this innovation, exploring solutions like those provided by Spintly can pave the way for a smarter, more secure tomorrow.
#access control system#access control solutions#accesscontrol#mobile access#visitor management system#spintly#smartacess#biometrics#smartbuilding
0 notes
Text

How Digital Design Agencies in Melbourne Enhance Your Online Presence?
In today’s fast-paced digital world, a strong online presence is essential for businesses of every size. Melbourne, renowned for its dynamic culture and innovative spirit, is home to many Digital Design Agency Melbourne services focused on boosting online visibility. These agencies provide a wide range of solutions tailored to meet the unique needs of each business, helping them shine in a competitive market. This blog explores how these agencies can help you strengthen and grow your online presence.
Understanding the Role of Digital Design Agencies
Digital Design Agency Melbourne plays a crucial role in determining how companies present themselves online. They provide a variety of services, including:
Website Design and Development: Creating user-friendly and visually appealing websites.
Branding: Creating a unified brand identity that appeals to target markets.
Content Creation: Creating interesting, educational, and consumer-attracting content.
SEO Optimization: Optimizing content and placing keywords strategically to increase a website's visibility on search engines.
Businesses can build a powerful online presence that draws in and keeps clients by utilizing these services.
Crafting User-Centric Websites: For many prospective clients, a company's well-designed website serves as their first impression. The creation of aesthetically pleasing and intuitive websites is the area of expertise for digital design firms. They guarantee that users can easily locate information, navigate the website, and carry out tasks like making purchases or subscribing to newsletters by adhering to UX (User Experience) best practices.
Building Strong Brand Identities: Branding goes beyond just a logo; it represents the overall perception of your business. Digital design agencies assist companies in building a strong brand identity through consistent visuals, messaging, and customer interactions. This process involves designing logos, choosing color schemes, and crafting marketing materials that align with the brand’s values and mission. 3. Engaging Content Creation: Digital design agencies are experts at creating high-quality content that draws in visitors and increases traffic because content is king in the digital world. This covers videos, infographics, blog entries, social media updates, and more. These agencies produce content that genuinely resonates with potential clients by knowing the preferences of the target audience. 4. Implementing Effective SEO Strategies: For your website to rank higher on search engines like Google, search engine optimization, or SEO, is crucial. A range of SEO strategies are employed by digital design firms to increase exposure and draw in natural traffic. These include keyword research, off-page techniques like constructing high-quality backlinks, and on-page optimization (meta tags and alt text). 5. Utilizing Cutting-Edge Technology: Keeping up in the ever-evolving digital world demands the use of cutting-edge tools and technologies. Digital design agencies in Melbourne invest in advanced software for analytics, web development, and marketing automation. This allows them to deliver innovative solutions that meet client needs. For example, many agencies leverage sophisticated analytics tools to monitor website performance and understand user behavior. This data-driven approach helps businesses refine their digital strategies, leading to smarter decisions and better results. 6. Multi-Channel Marketing Strategies: A strong online presence goes beyond simply having a website; it requires meaningful engagement with customers across various channels. Digital design agencies develop multi-channel marketing strategies, including social media management, email campaigns, pay-per-click advertising, and more, to connect with audiences effectively.
Conclusion
In conclusion, digital design agencies in Melbourne, such as Courtney Kim Studio, play a vital role in helping businesses enhance their online presence. With expertise in user-focused website design, impactful branding strategies, engaging content creation, effective SEO practices, advanced technology, and multi-channel marketing, these agencies enable businesses to thrive in today’s digital world.
Partnering with a trusted digital design agency not only enhances visibility but also builds meaningful connections with customers, driving growth and success in a competitive market. Whether you’re a budding startup or a well-established company, these agencies provide the resources and expertise needed to stand out online.
0 notes
Text
The Best Side of 79 cash
It absolutely was simpler than I imagined getting a lender with credit rating troubles up to now, however, you did it. Thank both you and your crew in your assist.
In the event the fields are usually not Are living it is possible to drag on the fields to complete it swiftly. Upon getting completed the form click the download icon from the toolbar to down load a duplicate of your finished PDF. Or send it for signing.Open up a totally free account on Fill here
Numerous commercial loans or short-time period loans are In this particular category. Compared with the first calculation, that's amortized with payments distribute uniformly in excess of their lifetimes, these loans have one, big lump sum owing at maturity.
Our on-line varieties are very easy to fill out with the comfort and ease of your personal home and might be accomplished in minutes.
Google Chrome’s browser has received its all over the world popularity because of its variety of handy capabilities, extensions and integrations. As an illustration, browser extensions allow it to be doable to help keep all the tools You will need a simply click absent.
Quite a few security systems are used which assist to shield the private info of visitors to our Web page from unauthorized use, disclosure and accessibility. An example of This really is that we'll keep own information that you provide on our Pc programs in sites which has restricted entry often located in very controlled amenities.
Before you take a loan, take some time to study the stipulations cautiously. This provides you with a clear photo on the charges and expenses chances are you'll incur underneath distinct conditions.
Are you presently trying to find a 1-measurement-fits-all solution to design private moneylender handbook PDF form? airSlate SignNow brings together ease of use, affordability and protection in one on the net Software, all without forcing additional DDD on you. All you would like is clean internet connection and a tool to operate on.
A loan phrase would be the length with the loan, provided that essential minimal payments are made every month. The time period in the loan can influence the structure of your loan in numerous ways.
We now have collected tens of millions in settlements for our clientele! When you or simply a family member have 79 loan been harm in an automobile incident, then Allow our experienced attorneys get you the very best attainable settlement. No payment until finally we earn! We will Speak to you that will help.
For more thorough assistance on safeguarding your SSN and how to proceed if you suspect a scam, consult the SSA's official means. Bank FAQ's
Completing and distributing the applying normally takes no more than a few minutes, and our lenders informs you of the appliance’s standing presently. On acceptance, you'll be able to count on the accredited resources to be transferred into your bank account as soon as subsequent business day.
Capability—steps a borrower's capability to repay a loan using a ratio to match their credit card debt to cash flow
Overdraft fees might induce your account for being overdrawn by an amount that is larger than your overdraft protection. A $fifteen rate may possibly utilize to each suitable transaction that brings your account unfavorable. Equilibrium have to be brought to at least $0 in just 24 hours of authorization of the first transaction that overdraws your account to steer clear of the price. Learn more at .
0 notes
Text
Free Job Alert Vacancy in Ainavalli, Andhra Pradesh: Opportunities Await
In the picturesque landscapes of Ainavalli, Andhra Pradesh, opportunities beckon for job seekers looking to embark on new career journeys. Nestled amidst serene surroundings and cultural richness, Ainavalli offers more than just a tranquil environment—it presents a growing hub of employment prospects across various sectors. Whether you're a seasoned professional or a fresh graduate, exploring the job market here might just lead you to your next big career breakthrough.
Diverse Opportunities Across Sectors Ainavalli, known for its vibrant culture and historical significance, is increasingly becoming a hotspot for job seekers. The local economy, bolstered by agriculture, manufacturing, and service sectors, provides a wide array of employment opportunities. From entry-level positions to senior management roles, the job market in Ainavalli caters to diverse skill sets and career aspirations.
Rising Demand in Education and Healthcare With a focus on development, Ainavalli is witnessing a surge in opportunities within the education and healthcare sectors. Educational institutions are expanding, creating openings for teachers, administrators, and support staff. Simultaneously, healthcare facilities are on the rise, leading to a demand for healthcare professionals ranging from doctors and nurses to technicians and administrative personnel.
Emerging Technology and IT Hubs As technology continues to reshape industries, Ainavalli is not left behind. The region is witnessing a burgeoning IT sector, attracting tech-savvy professionals seeking to leverage their skills in a dynamic environment. Startups and small businesses in IT services, software development, and digital marketing are offering promising career prospects, making Ainavalli a budding IT hub in Andhra Pradesh.
Opportunities in Hospitality and Tourism Ainavalli's natural beauty and cultural heritage also contribute to its thriving hospitality and tourism sectors. Hotels, resorts, and tour operators are continually seeking skilled personnel in customer service, hospitality management, and tour guiding. The influx of tourists and visitors provides a steady stream of employment opportunities year-round, creating a vibrant job market in these fields.
Government and Public Sector Roles For those inclined towards public service and administrative roles, Ainavalli offers opportunities in various government departments and public sector organizations. Positions in administration, public works, and local governance are regularly available, providing stable career options with opportunities for growth and development.
How to Stay Informed About Job Vacancies To stay updated with the latest job vacancies in Ainavalli, keeping an eye on local job portals, community boards, and social media groups dedicated to job alerts is crucial. Networking with professionals in your field and attending local career fairs or seminars can also provide valuable insights and connections. Additionally, registering with recruitment agencies that specialize in placements within Andhra Pradesh can significantly enhance your job search efforts.
Conclusion: Embrace the Opportunities in Ainavalli In conclusion, Ainavalli, Andhra Pradesh, presents a promising landscape for job seekers eager to explore new horizons. Whether you're drawn to the cultural richness of the region, the burgeoning IT sector, or the expanding educational and healthcare fields, opportunities abound across various sectors. By staying informed, networking effectively, and showcasing your skills, you can embark on a fulfilling career journey in Ainavalli. Keep an eye out for "Free Job Alert Vacancy in Ainavalli, Andhra Pradesh," and seize the opportunity to shape your future in this vibrant and growing community.
0 notes
Text
Security Best Practices for Website Development

When building a website, security should always be a top priority. In today’s digital age, websites face constant threats from hackers, malware, and cyber-attacks. Small businesses, in particular, can be vulnerable if they don’t take the necessary steps to protect their sites and user data. Whether you're working with web development services in Bhubaneswar or building a website on your own, knowing the best security practices is essential. Let’s look at the most important steps to keep your website safe.
1. Use HTTPS and SSL Certificates
One of the simplest yet most effective ways to protect your website is by using HTTPS (HyperText Transfer Protocol Secure). HTTPS encrypts data transmitted between your website and visitors, ensuring that sensitive information, like passwords or payment details, remains secure.
To implement HTTPS, you need to install an SSL (Secure Sockets Layer) certificate on your website. This certificate ensures that all data is encrypted, which prevents hackers from intercepting or tampering with sensitive information. It’s also an important ranking factor for search engines, as websites with HTTPS are considered more trustworthy.
2. Regularly Update Software and Plugins
Outdated software is one of the most common causes of website vulnerabilities. Whether you're using WordPress, Joomla, or any other content management system, keeping your software up to date is essential for security. Many updates include patches for security holes, so by failing to install them, you’re leaving your site open to attacks.
This also applies to third-party plugins. Plugins add useful features to your site but can also introduce vulnerabilities if not kept up to date. Always ensure that any plugin you use is from a reputable source, and make a habit of updating them regularly to avoid potential security risks.
3. Strong Passwords and Two-Factor Authentication
One of the easiest ways for hackers to gain access to your website is through weak passwords. Always use strong, unique passwords for your admin accounts, hosting accounts, and other important platforms. A strong password includes a combination of upper and lower case letters, numbers, and special characters.
Additionally, enabling two-factor authentication (2FA) can add an extra layer of security. With 2FA, even if someone manages to steal your password, they will still need a second piece of information, like a code sent to your phone, to gain access. It’s an easy but highly effective way to keep your website secure.
4. Regular Backups
No matter how much effort you put into securing your website, accidents happen. Servers crash, websites get hacked, and sometimes data gets lost. This is why regular backups are a must. By backing up your website’s data and files, you ensure that you can quickly recover from any disaster.
Set up automatic backups on a daily or weekly basis, depending on how often your content changes. Store these backups in a secure location, either in the cloud or on an external hard drive, so you can easily restore your website if something goes wrong.
5. Limit User Access and Permissions
Not everyone needs admin access to your website. By limiting access and permissions, you reduce the number of entry points for potential attackers. Assign roles based on what each user needs to do on the site. For example, if someone only needs to write blog posts, don’t give them admin privileges.
Additionally, regularly review and remove access for users who no longer need it. This reduces the chances of a disgruntled employee or former employee causing harm to your website.
6. Use a Web Application Firewall (WAF)
A Web Application Firewall (WAF) is a security measure that helps protect your website from a variety of attacks, such as SQL injection, cross-site scripting (XSS), and others. A WAF sits between your website and the internet, monitoring incoming traffic and blocking any malicious attempts before they reach your website.
WAFs are particularly effective at blocking harmful bots and malicious traffic that could overwhelm your website or attempt to exploit vulnerabilities. Many hosting providers offer WAFs as part of their security packages, or you can choose from third-party providers.
7. Monitor for Vulnerabilities
Regularly monitoring your website for security vulnerabilities is a critical part of maintaining a secure online presence. Various tools can scan your website for weaknesses and alert you to potential issues. These tools look for things like outdated software, weak passwords, and suspicious activity.
If you’re working with web development services in Bhubaneswar, consider asking them to set up regular security audits and vulnerability scans. This proactive approach can help identify issues before they become major problems.
8. Protect Against DDoS Attacks
Distributed Denial of Service (DDoS) attacks are one of the most common ways hackers try to take down websites. A DDoS attack involves overwhelming your website with an excessive amount of traffic, causing it to slow down or crash. To protect your website from these attacks, you can use DDoS protection services, such as Cloudflare, which helps filter out malicious traffic.
These services can mitigate the effects of a DDoS attack and ensure your website stays online and operational.
9. Secure Your Hosting Server
Your web hosting server is the backbone of your website, so it's essential to ensure it's secure. When choosing a hosting provider, look for one that offers robust security features, such as regular server monitoring, malware scanning, and automatic security patches.
Additionally, make sure that your hosting provider offers SSL certificates and firewalls. A reliable hosting provider will take care of most of the server security, but you should also perform your due diligence to ensure everything is set up correctly.
Conclusion
Website security is not something that should be taken lightly. Whether you’re running an e-commerce site or a simple blog, taking the necessary steps to protect your website from security threats is crucial. By implementing best practices like using HTTPS, updating software regularly, using strong passwords, and employing a web application firewall, you can significantly reduce the risk of cyber-attacks and keep your site safe.If you’re a business owner in Bhubaneswar, working with web development services in Bhubaneswar can help ensure that your website is secure and protected from potential threats. By following these security best practices, you can safeguard your online presence and provide a safe experience for your visitors.
#digital marketing services in bhubaneswar#seo services in bhubaneswar#web development services in bhubaneswar#digital marketing agency bhubaneswar#digital marketing agency india#website designing company in india
0 notes