#verizon wireless phone number lookup
Explore tagged Tumblr posts
Link
the importance of the Verizon wireless phone number lookup is appeared clearly when you have received a phone call from an unknown number and wondered who it
0 notes
Link
the importance of the Verizon wireless phone number lookup is appeared clearly when you have received a phone call from an unknown number and wondered who it
0 notes
Text
Free Mobile Number Database - Free Recommendations You Must Try First!
A reverse cellular range database is a treasured tool with regards to finding out information about the proprietor of an unknown wide variety. With the usage of this device, you can easily find out the name and cope with at the back of any quantity inside minutes. There are several reasons human beings have for accomplishing a reverse lookup on a cellular variety, but on the identical time it is also important to look for the right listing. Since all of the directories do now not comprise the identical amount, accuracy and excellent of facts, it is vital to look for the pleasant ones to be had at the net.
There are two forms of reverse lookup directories to be had. Firstly, there are the unfastened ones and then there are the paid ones. There are many individuals who do now not need to pay for this kind of service and therefore they use the unfastened provider. But, there are sure matters that you need to know about an unfastened directory.
A loose listing does now not include a whole lot data on Indian Phone Number Database Provider due to the fact these varieties of numbers are unlisted. Secondly, these directories aren't updated regularly and there are huge possibilities of you getting faulty facts while you perform a reverse lookup on a number.
On the opposite hand, a paid opposite seek listing is always a dependable one. It contains a huge database of listings and they may be updated on a normal foundation. If you carry out searches with a paid directory, you'll get a hundred% correct records. Moreover, you may additionally find a good deal greater than just the name and cope with of the character.
Verizon and Sprint do not telephone offer directories to the public that allow customers to fit a phone wide variety with a name and cope with. They provide customers the capability to discover the proprietors of landline and commercial enterprise numbers, however they do not offer users the capacity to perceive the owners of Mobile Number Database India.
This is due to the fact the general public are not aware of which wi-fi provider services the cell number they want to match a non-public facts file with. So, to rectify this, every wi-fi carrier sells personal statistics linked with the wireless numbers they carrier to information collection groups. These agencies then collect all of the numbers from all of the wi-fi carriers into one vital database.
So it does not depend whether which cellphone agency without a doubt owns the smartphone quantity. All you want to do is enter the total 7-digit cellular quantity into the hunt container furnished through the listing you're operating with, and within seconds the directory will let you know whether a report exists of their database.
For more info:- Karnataka Mobile Number Database
1 note
·
View note
Text
What You Must Know About Reverse Directory
You are able to use a reverse directory to discover the individual which goes alongside the number. Try to remember which you need to locate a reverse directory that doesn't only includes land line phones, but also cell phones. Whether you prefer it or not, there's absolutely no such thing as a totally free cell phone reverse directory.
Reverse Directory at a Glance

A great directory is going to be updated on a normal basis. So you're going to need to understand what makes up a trusted directory. The next thing which you need to search for in a reverse directory is the way many times the site was updated. If you are in need of a reverse Verizon phone number directory, we need to disappoint you it is no longer on the official website. The Little-Known Secrets to Reverse Directory To acquire a fast, accurate reverse mobile phone lookup you've got to use the appropriate directory. When you use the appropriate reverse directory to trace a number the approach is fast, simple, and dependable. Reverse mobile directories are throughout the world wide web and they enable you to search a company or a person with a cell number, land line, or unlisted number. A reliable reverse mobile directory is going to be employed by men and women on a daily basis, meaning that the website should incorporate a registration form. New Ideas Into Reverse Directory Never Before Revealed Since centralized directories do not exist for mobile phone numbers, reverse mobile phone lookup sites cannot offer caller details for each mobile phone number in the U.S. The last thing you wish to make certain directory includes is cell phones. The last thing which you want to ensure a reverse directory has is information. A reverse wireless phone directory will demonstrate the sort of information that they have on file so that you can decide then whether you would like to order the report. The 30-Second Trick for Reverse Directory If you're doing a search in a totally free directory web support, make sure that it's reliable and has each of the specifics. For instance, you tried a search but when you wish to receive a more thorough result, they won't offer you any access till you pay a specific quantity. So take some time to do a reverse phone search, you can't what's going to come up. The very best possible means to obtain a mobile phone number reverse search is a database. What You Need to Know About Reverse Directory You can receive a lot of information from ten little digits provided that you know the best place to look. So take some time to discover a secure reverse directory, and you'll be on your way to finding all of the info you require. Before deciding upon any business reverse lookup directory, it is essential that you understand which ones are likely to permit you to locate the information that you want to get, and the ones won't. If you would like to know more than the contact info and phone owner then you will probably will need to pay a small charge. The Battle Over Reverse Directory and How to Win It In case the reason you want the info is to be sure nobody is hoping to hurt your loved ones, getting the most accurate information possible is well worth the little fee. Lastly is to double confirm the information which you got. Needless to say, the info given by the search facility will differ based on the reverse directory which you choose. How to Choose Reverse Directory After the information that they're searching for is that important, it's important he or she's given accurate outcomes. If you cannot locate the information which you are seeking on the websites listed above, then we will be able to help you. The aforementioned information demonstrates that the service isn't absolutely free. Naturally you must pay to access the desired information, and in return for those directories work as a way to acquire your preferred info all in the exact same place in a matter of seconds, they charge you a little fee before it is possible to lookup at their database. Whichever reverse directory you select, you ought to be armed with more than enough info to confront your spouse and place a stop to the torture of just not knowing. You will likewise be able to find a more in-depth info on your subject than just the a brief overview of what's in the database.

How to Get Started with Reverse Directory?
There are an assortment of explanations for why you might be compelled to execute a reverse phone lookup. In the end, the reverse phone lookup is a very helpful skill for everyone seeking to find out more regarding the phone calls they receive. A speedy Reverse Phone Lookup may confirm whether the caller is a friend or merely another telemarketer attempting to sell you something.
1 note
·
View note
Link
The past month has seen one blockbuster revelation after another about how our mobile phone and broadband providers have been leaking highly sensitive customer information, including real-time location data and customer account details. In the wake of these consumer privacy debacles, many are left wondering who’s responsible for policing these industries? How exactly did we get to this point? What prospects are there for changes to address this national privacy crisis at the legislative and regulatory levels? These are some of the questions we’ll explore in this article.

In 2015, the Federal Communications Commission under the Obama Administration reclassified broadband Internet companies as telecommunications providers, which gave the agency authority to regulate broadband providers the same way as telephone companies.
The FCC also came up with so-called “net neutrality” rules designed to prohibit Internet providers from blocking or slowing down traffic, or from offering “fast lane” access to companies willing to pay extra for certain content or for higher quality service.
In mid-2016, the FCC adopted new privacy rules for all Internet providers that would have required providers to seek opt-in permission from customers before collecting, storing, sharing and selling anything that might be considered sensitive — including Web browsing, application usage and location information, as well as financial and health data.
But the Obama administration’s new FCC privacy rules didn’t become final until December 2016, a month after then President-elect Trump was welcomed into office by a Republican controlled House and Senate.
Congress still had 90 legislative days (when lawmakers are physically in session) to pass a resolution killing the privacy regulations, and on March 23, 2017 the Senate voted 50-48 to repeal them. Approval of the repeal in the House passed quickly thereafter, and President Trump officially signed it on April 3, 2017.
In an op-ed published in The Washington Post, Ajit Pai — a former Verizon lawyer and President Trump’s pick to lead the FCC — said “despite hyperventilating headlines, Internet service providers have never planned to sell your individual browsing history to third parties.”

FCC Commissioner Ajit Pai.
“That’s simply not how online advertising works,” Pai wrote. “And doing so would violate ISPs’ privacy promises. Second, Congress’s decision last week didn’t remove existing privacy protections; it simply cleared the way for us to work together to reinstate a rational and effective system for protecting consumer privacy.”
Sen. Bill Nelson (D-Fla.) came to a different conclusion, predicting that the repeal of the FCC privacy rules would allow broadband providers to collect and sell a “gold mine of data” about customers.
“Your mobile broadband provider knows how you move about your day through information about your geolocation and internet activity through your mobile device,” Nelson said. The Senate resolution “will take consumers out of this driver’s seat and place the collection and use of their information behind a veil of secrecy.”
Meanwhile, pressure was building on the now Republican-controlled FCC to repeal the previous administration’s net neutrality rules. The major ISPs and mobile providers claimed the new regulations put them at a disadvantage relative to competitors that were not regulated by the FCC, such as Amazon, Apple, Facebook and Google.
On Dec. 14, 2017, FCC Chairman Pai joined two other Republic FCC commissioners in a 3-2 vote to dismantle the net neutrality regulations.
As The New York Times observed after the net neutrality repeal, “the commission’s chairman, Ajit Pai, vigorously defended the repeal before the vote. He said the rollback of the rules would eventually benefit consumers because broadband providers like AT&T and Comcast could offer them a wider variety of service options.”
“We are helping consumers and promoting competition,” Mr. Pai said. “Broadband providers will have more incentive to build networks, especially to underserved areas.”
MORE OR LESS CHOICE?
Some might argue we’ve seen reduced competition and more industry consolidation since the FCC repealed the rules. Major broadband and mobile provider AT&T and cable/entertainment giant Time Warner are now fighting the Justice Department in a bid to merge. Two of the four-largest mobile telecom and broadband providers — T-Mobile and Sprint — have announced plans for a $26 billion merger.
The FCC privacy rules from 2016 that were overturned by Congress sought to give consumers more choice about how their data was to be used, stored and shared. But consumers now have less “choice” than ever about how their mobile provider shares their data and with whom. Worse, the mobile and broadband providers themselves are failing to secure their own customers’ data.
This month, it emerged that the major mobile providers have been giving commercial third-parties the ability to instantly look up the precise location of any mobile subscriber in real time. KrebsOnSecurity broke the news that one of these third parties — LocationSmart — leaked this ability for years to anyone via a buggy component on its Web site.
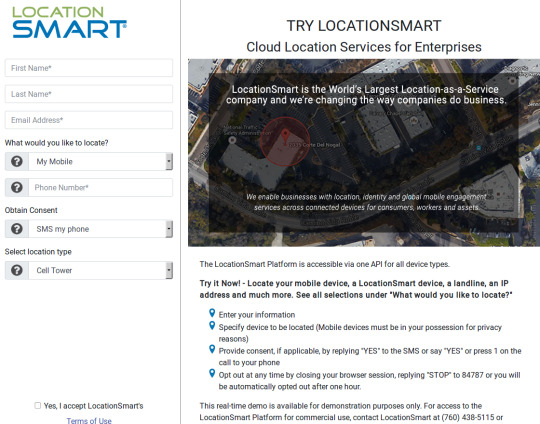
LocationSmart’s demo page featured a buggy component which allowed anyone to look up anyone else’s mobile device location, in real time, and without consent.
We also learned that another California company — Securus Technologies — was selling real-time location lookups to a number of state and local law enforcement agencies, and that accounts for dozens of those law enforcement officers were obtained by hackers. Securus, it turned out, was ultimately getting its data from LocationSmart.
This week, researchers discovered that a bug in T-Mobile’s Web site let anyone access the personal account details of any customer with just their cell phone number, including full name, address, account number and some cases tax ID numbers.
Not to be outdone, Comcast was revealed to have exposed sensitive information on customers through a buggy component of its Web site that could be tricked into displaying the home address where the company’s wireless router is located, as well as the router’s Wi-Fi name and password.
It’s not clear how FCC Chairman Pai intends to “reinstate a rational and effective system for protecting consumer privacy,” as he pledged after voting last year to overturn the 2015 privacy rules. The FCC reportedly has taken at least tentative steps to open an inquiry into the LocationSmart debacle, although Sen. Ron Wyden (D-Ore.) has called on Chairman Pai to recuse himself on the inquiry because Pai once represented Securus as an attorney. (Wyden also had some choice words for the wireless companies).
The major wireless carriers all say they do not share customer location data without customer consent or in response to a court order or subpoena. Consent. All of these carriers pointed me to their privacy policies. It could be the carriers believe these policies clearly explain that simply by using their wireless device customers have opted-in to having their real-time location data sold or given to third-party companies.
Michelle De Mooy, director of the privacy and data project at the Center for Democracy & Technology (CDT), said if the mobile giants are burying that disclosure in privacy policy legalese, that’s just not good enough.
“Even if they say, ‘Our privacy policy says we can do this,’ it violates peoples’ reasonable expectations of when and why their location data is being collected and how that’s going to be used. It’s not okay to simply point to your privacy policies and expect that to be enough.”
CHECKING THE FTC’S RECORD
When the FCC’s repeal of the net neutrality rules takes effect on June 11, 2018, broadband providers will once again be regulated by the Federal Trade Commission (FTC). That power was briefly shared with FCC when the agency under the Obama administration passed its net neutrality rules with the assumption that it could regulate broadband providers like telecommunications companies.
When it comes to investigating companies for privacy and security violations, the FTC’s primary weapon is The FTC Act, which “prohibits unfair and deceptive acts or practices in or affecting commerce.” According to the FTC Act, a “misrepresentation or omission is deceptive if it is material and is likely to mislead consumers acting reasonably under the circumstances.” It also finds that an act or practice “is unfair if it causes, or is likely to cause, substantial injury that is not reasonably avoidable by consumers, and not outweighed by countervailing benefits to consumers or competition.”

It’s difficult to think of a bigger violation of those principles than the current practice by the major mobile providers of sharing real-time location data on customers with third parties, without any opportunity for customers to opt-in or opt-out of such sharing.
But it’s unclear whether the FTC would take take any action against such activity, or indeed if it has any precedent to do so. The agency had the ability to go after mobile broadband providers for privacy and security violations between 2002 and 2015, and so KrebsOnSecurity asked the commission to share how many times during that period that it took enforcement actions against broadband providers.
The list I got back from them wasn’t exactly privacy or security focused. The FTC cited a case in 2003 in which it sued AOL and CompuServe over unfair billing practices. In 2009, it helped to take down 3FN, a small, shady ISP that was based in the United States but run by Russians and hosting a stupendous amount of malware, scams and illegal content (i.e. child pornography).
In 2014, the FTC alleged that AT&T Mobility deceptively advertised “unlimited” data while throttling mobile customers who used certain amounts of data (this case is still pending but a recent appeals court decision cleared the way for the FTC to continue its lawsuit).
In 2015, TracFone, the largest prepaid mobile provider in the United States, agreed to pay $40 million to the FTC for consumer refunds to settle charges that it deceived millions of consumers with regard to its “unlimited” data service.
The FTC also cited a scolding letter (PDF) that it sent to Verizon over issues related to the security of its customer routers. No action was taken by the FTC in that case.
How eager the FTC will be to police privacy practices of broadband providers may come down to the priorities of the agency’s new leaders. The Trump administration just tapped Andrew Smith as head of the FTC’s consumer protection office. Smith is a lawyer who used to represent many of the companies that the agency is already investigating.
Smith will need to recuse himself from multiple ongoing investigations his office would normally lead, including data breaches at Equifax and Facebook, thanks to his previous work on behalf of the companies. According to The Hill, Smith testified in October before the Senate Banking Committee on behalf of the credit reporting industry as the panel investigated an Equifax data breach that compromised more than 145 million people.
Gigi Sohn, a fellow at the Georgetown Law Institute for Technology Law and Policy and a former senior adviser to former FCC Chair Tom Wheeler in 2015, said the FTC doesn’t have a strong record on broadband privacy enforcement.
Sohn said the FTC’s legal framework does not require affirmative opt-in consent for browsing history and app usage, and that a provider would only have to let you opt-out — something that consumers rarely do and which companies routinely make it hard to do. More importantly, she said, while the FCC’s rules would have protected consumers before they were harmed, the FTC can only act after harm has already occurred.
“We passed privacy rules for broadband and mobile providers that would have required them to seek customer opt-in for anything that was considered sensitive,” Sohn said of her work at the FCC under the Obama administration. “The carrier had to give you clear and consistent opportunities to opt out. It was very broad, but the definition we set for personal information was far broader than what even the FTC considered sensitive.”
REPEALING THE REPEAL OF NET NEUTRALITY
So the carriers are already reneging on their promise to customers that they won’t share location data without customer consent or a court order. But where does that leave us on net neutrality? The answer is that the major wireless carriers are already doing what was expressly prohibited under the FCC’s net neutrality rules: Favoring their own content over competitors, and letting companies gain more favorable access by paying more.

Around the time of the FCC’s repeal of the net neutrality rules last year, The Wall Street Journal prognosticated about what might happen with the regulations out of the way. To do this, it looked at some of the offerings the mobile carriers pitched before the rules were drawn up.
“One example of how things could work is the mobile wireless market, where some providers already have used pricing tactics to favor certain websites and services over others,” wrote John D. McKinnon and Ryan Knutson for The Journal:
The 2015 Obama-era rules didn’t explicitly prohibit these tactics, which generally allow customers to access certain websites without having it count against their monthly data cap. Wireless carriers, which often subject their users to strict data limits, were aggressive in experimenting with such plans, also known as “zero rating.”
Deals began emerging several years ago for inexpensive plans that offer unlimited high-speed access to popular services such as Facebook or Twitter, but limited or even restricted access to the rest of the internet.
T-Mobile US Inc. in late 2013 announced that its GoSmart Mobile brand had “become the first wireless provider…to offer free access to Facebook and Facebook Messenger for all of its wireless customers, even those without monthly data service.” The GoSmart Mobile plans started at $25 a month for “unlimited talk” with no other data service. T-Mobile has since transferred the GoSmart brand to another wireless firm.
In 2014, Virgin Mobile USA, a unit of Sprint Corp. , offered a wireless plan that cost $12, but users were only allowed to access one website: either Facebook, Twitter, Instagram or Pinterest. If they wanted all four, it was $10 more a month. Another $5 and they could access any online music streaming service.
Big internet providers also used zero-rating plans to favor their own content. AT&T Inc. gave paying customers unlimited usage of its own online video service DirecTV Now, while other video sites counted against monthly data caps. Verizon Communications Inc. did the same for its mobile video app, called go90.”
AT&T Mobility offers a zero-rating plan called “Sponsored Data” that allows content providers to pay up front to have streaming of that content allowed without counting against the provider’s monthly data caps.
Sohn said the FCC under the Obama administration initiated an investigation into AT&T’s Sponsored Data plan and Verizon for its go90 service, but that the inquiry was abandoned by the current FCC leadership.
There are some prospects for a Congressional repeal of this administration’s gutting of the FCC’s net neutrality rules. On May 16, the Senate approved a resolution nullifying the FCC’s rollback of the net neutrality rules. But the measure faces an uphill battle in the House.
“Right now we’re probably 30 to 40 members short of being able to bring a vote in the House,” Sohn said. “About 20 Democrats haven’t gotten on board, and we have no Republicans so far. But I think that’s going to change. If Congress repeals the net neutrality repeal, the next step would be to craft stronger rules [either at the FCC or Congress]. We have until the end of this Congress to get it done.”
The CDT’s De Mooy gives the effort to repeal the repeal of net neutrality rules slim chances of passage this year. But she said the prospects for revisiting net neutrality and consumer privacy in the next Congress look good, particularly if Democrats pick up additional seats in the House.
“It seems to be something the Democrats are taking up more now,” Demooy said. “So much depends on what happens in November. But that’s true of so many tech policy issues.”
SHOCK AND YAWN
When I first saw a Carnegie Mellon University researcher show me last week that he could look up the near-exact location of any mobile number in the United States, I sincerely believed the public would be amazed and horrified at the idea that mobile providers are sharing this real-time data with third party companies, and at the fact that those third parties in turn weren’t doing anything to prevent the abuse of their own systems.
Instead, after a brief round of coverage in several publications, the story fell out of the news cycle. A story this week in Slate.com lamented how little coverage the mainstream press has given to the LocationSmart scandal, and marvels at how much more shocked people were over the Cambridge Analytic scandal with Facebook.
“Privacy abuses and slip-ups by major tech companies have become so numerous, and the prospect of containing them seems so hopeless, that the public and much of the media have become nearly numb to them,” writes Will Oremus for Slate. “My data was hacked? So it goes. It may have been used in unauthorized ways by unspecified parties? C’est la vie.”
Oremus argues that what the LocationSmart scandal lacks is not import, nor the potential for serious harm, “but a link to some divisive political issue or societal outrage sufficient enough to generate visceral anger from people who aren’t privacy wonks.”
If you’ve read this far (bless you), don’t let breach fatigue and incessant media exposure of how little privacy we have harden into resignation. Yes, the prospects of any public debate about consumer privacy protections in the United States at the legislative level seem dim in a high-stakes mid-term election year. But supporters of net neutrality ideals can start getting involved by tweeting, calling and emailing the House lawmakers listed in red at BattleForTheNet.com.
While you’re at it, tell your lawmakers what you think about mobile providers giving or selling third-parties real-time access to customer location information, and let them know that this is no longer okay.
This is the second article in a two-part series. The first is here: Mobile Giants, Please Don’t Share the Where.
1 note
·
View note
Text
Bug Bounty Hunter Ran ISP Doxing Service
A Connecticut man who’s earned bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites secretly operated a service that leveraged these same flaws to sell their customers’ personal data, KrebsOnSecurity has learned.
In May 2018, ZDNet ran a story about the discovery of a glaring vulnerability in the Web site for wireless provider T-Mobile that let anyone look up customer home addresses and account PINs. The story noted that T-Mobile disabled the feature in early April after being alerted by a 22-year-old “security researcher” named Ryan Stevenson, and that the mobile giant had awarded Stevenson $1,000 for reporting the discovery under its bug bounty program.
The Twitter account @phobia, a.k.a. Ryan Stevenson. The term “plug” referenced next to his Twitch profile name is hacker slang for employees at mobile phone stores who can be tricked or bribed into helping with SIM swap attacks.
Likewise, AT&T has recognized Stevenson for reporting security holes in its services. AT&T’s bug bounty site lets contributors share a social media account or Web address where they can be contacted, and in Stevenson’s case he gave the now-defunct Twitter handle “@Phoobia.”
Stevenson’s Linkedin profile — named “Phobias” — says he specializes in finding exploits in numerous Web sites, including hotmail.com, yahoo.com, aol.com, paypal.com and ebay.com. Under the “contact info” tab of Stevenson’s profile it lists the youtube.com account of “Ryan” and the Facebook account “Phobia” (also now deleted).
Coincidentally, I came across multiple variations on this Phobia nickname as I was researching a story published this week on the epidemic of fraudulent SIM swaps, a complex form of mobile phone fraud that is being used to steal millions of dollars in cryptocurrencies.
Unauthorized SIM swaps also are often used to hijack so-called “OG” user accounts — usually short usernames on top social network and gaming Web sites that are highly prized by many hackers because they can make the account holder appear to have been a savvy, early adopter of the service before it became popular and before all of the short usernames were taken. Some OG usernames can be sold for thousands of dollars in underground markets.
This week’s SIM swapping story quoted one recent victim who lost $100,000 after his mobile phone number was briefly stolen in a fraudulent SIM swap. The victim said he was told by investigators in Santa Clara, Calif. that the perpetrators of his attack were able to access his T-Mobile account information using a specialized piece of software that gave them backdoor access to T-Mobile’s customer database.
Both the Santa Clara investigators and T-Mobile declined to confirm or deny the existence of this software. But their non-denials prompted me to start looking for it on my own. So naturally I began searching at ogusers-dot-com, a forum dedicated to the hacking, trading and sale of OG accounts. Unsurprisingly, ogusers-dot-net also has traditionally been the main stomping grounds for many individuals involved in SIM swapping attacks.
It didn’t take long to discover an account on ogusers-dot-com named “Ryan,” who for much of 2018 has advertised a number of different “doxing” services — specifically those aimed at finding the personal information of customers at major broadband and telecom companies.
In some of Ryan’s sales threads, fellow forum members refer to him as “Phob” or “Phobs.” In a post on May 27, Ryan says he’s willing to pay or trade for OG accounts under the name “Ryan,” “Ryans”, “RS,” “RMS” or “Stevenson” on any decent sized popular Web site. “hmu [hit me up] in a pm [private message] to talk,” Ryan urged fellow forum members.
The OG User forum account “Ryan” asking fellow members to sell or trade him any major Web site account name that includes the OG username “Ryan” or “Stevenson.”
I found that as late as June 2018 Ryan was offering a service that he claimed was capable of “doxing any usa carrier,” including Verizon, AT&T, Sprint, T-Mobile, MetroPCS and Boost Mobile.
“All I need is the number,” Ryan said of his customer data lookup service, which he sold for $25 per record. “Payment BTC [bitcoin] only.”
For $25 per record, Ryan offered fellow ogusers members the ability to look up customer records tied to any customer of the major U.S. mobile providers.
Very similar offerings were made by Phobia’s alter ego “AOLer” on the sprawling English language online hacking community Hackforums.
I first encountered Stevenson several years back while trying to work out who was responsible for calling in a phony hostage situation and sending a heavily armed police force to our Northern Virginia home in 2013. In a follow-up to that story, Stevenson admitted that he was responsible for the high-profile hack against Wired reporter Mat Honan, who documented how a hacker named Phobia had deleted his Google account and remotely erased all data from his iPhone, iPad and MacBook.
Going by the nickname “Phobiathegod” at the time, Stevenson was then part of a group of young men who routinely hijacked OG account names on Microsoft’s Xbox gaming platform, often using methods that involved tricking customer service people at the target’s mobile provider into transferring the victim’s calls to a number they controlled.
Fast forward to today, and Phobia’s main Twitter account (pictured at the top of this post) includes the phrase “the plug” next to his profile. In SIM swapping circles, a “plug” is hacker slang for an employee at a mobile phone store who can be bribed, tricked or blackmailed into assisting with an unauthorized SIM swap.
Reached via instant message on LinkedIn, Stevenson acknowledged running the ISP doxing services, but said his account on the OGusers forum was since banned and that hardly anyone took him up on his offer anyway.
“I shouldn’t have made the threads even though no one really asked for anything,” he said. “I’m on the good side. But its almost 2019 and I need to find a new hobby I can’t be bothered to look for breaches/vulns, haven’t got 1 job offer or recommendation yet.”
Asked about “the plug” reference in his Twitter profile, Stevenson suddenly stopped replying. Not long after that, the @Phobia Twitter account was deactivated.
Stevenson denied being involved in SIM swapping attacks, but it is clear Phobia was fairly tight with many people who are or until recently were at the center of this scene. In July 2018, authorities in California arrested 20-year-old Boston resident Joel Ortiz for allegedly conducting dozens of fraudulent SIM swaps and stealing at least $5 million worth of cryptocurrency from victims.
Like Phobia, Ortiz had a presence on OGusers and had acquired some of the most OG social media accounts available, including the Twitter and Instagram account names with the number zero (@0), and the OG Youtube accounts “Joel” and “X”.
On Oct 27, 2017, the Youtube account “Joel” published a 4-minute video of Stevenson dancing to a popular rap song in front of the camera. On July 5, 2018, just days before Ortiz was arrested, the Twitter account “0” gave a shout out to @Phobia on Twitter suggesting Phobia was actually tweeting using Ortiz’s “0” account.
from https://krebsonsecurity.com/2018/11/bug-bounty-hunter-ran-isp-doxing-service/
0 notes
Link
Ways to verizon wireless phone numbers search, the way to find out is by phone number lookup, in the event that you receive phone calls from a Verizon number
0 notes
Text
Bug Bounty Hunter Ran ISP Doxing Service
A Connecticut man who’s earned bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites secretly operated a service that leveraged these same flaws to sell their customers’ personal data, KrebsOnSecurity has learned.
In May 2018, ZDNet ran a story about the discovery of a glaring vulnerability in the Web site for wireless provider T-Mobile that let anyone look up customer home addresses and account PINs. The story noted that T-Mobile disabled the feature in early April after being alerted by a 22-year-old “security researcher” named Ryan Stevenson, and that the mobile giant had awarded Stevenson $1,000 for reporting the discovery under its bug bounty program.
The Twitter account @phobia, a.k.a. Ryan Stevenson. The term “plug” referenced next to his Twitch profile name is hacker slang for employees at mobile phone stores who can be tricked or bribed into helping with SIM swap attacks.
Likewise, AT&T has recognized Stevenson for reporting security holes in its services. AT&T’s bug bounty site lets contributors share a social media account or Web address where they can be contacted, and in Stevenson’s case he gave the now-defunct Twitter handle “@Phoobia.”
Stevenson’s Linkedin profile — named “Phobias” — says he specializes in finding exploits in numerous Web sites, including hotmail.com, yahoo.com, aol.com, paypal.com and ebay.com. Under the “contact info” tab of Stevenson’s profile it lists the youtube.com account of “Ryan” and the Facebook account “Phobia” (also now deleted).
Coincidentally, I came across multiple variations on this Phobia nickname as I was researching a story published this week on the epidemic of fraudulent SIM swaps, a complex form of mobile phone fraud that is being used to steal millions of dollars in cryptocurrencies.
Unauthorized SIM swaps also are often used to hijack so-called “OG” user accounts — usually short usernames on top social network and gaming Web sites that are highly prized by many hackers because they can make the account holder appear to have been a savvy, early adopter of the service before it became popular and before all of the short usernames were taken. Some OG usernames can be sold for thousands of dollars in underground markets.
This week’s SIM swapping story quoted one recent victim who lost $100,000 after his mobile phone number was briefly stolen in a fraudulent SIM swap. The victim said he was told by investigators in Santa Clara, Calif. that the perpetrators of his attack were able to access his T-Mobile account information using a specialized piece of software that gave them backdoor access to T-Mobile’s customer database.
Both the Santa Clara investigators and T-Mobile declined to confirm or deny the existence of this software. But their non-denials prompted me to start looking for it on my own. So naturally I began searching at ogusers-dot-com, a forum dedicated to the hacking, trading and sale of OG accounts. Unsurprisingly, ogusers-dot-net also has traditionally been the main stomping grounds for many individuals involved in SIM swapping attacks.
It didn’t take long to discover an account on ogusers-dot-com named “Ryan,” who for much of 2018 has advertised a number of different “doxing” services — specifically those aimed at finding the personal information of customers at major broadband and telecom companies.
In some of Ryan’s sales threads, fellow forum members refer to him as “Phob” or “Phobs.” In a post on May 27, Ryan says he’s willing to pay or trade for OG accounts under the name “Ryan,” “Ryans”, “RS,” “RMS” or “Stevenson” on any decent sized popular Web site. “hmu [hit me up] in a pm [private message] to talk,” Ryan urged fellow forum members.
The OG User forum account “Ryan” asking fellow members to sell or trade him any major Web site account name that includes the OG username “Ryan” or “Stevenson.”
I found that as late as June 2018 Ryan was offering a service that he claimed was capable of “doxing any usa carrier,” including Verizon, AT&T, Sprint, T-Mobile, MetroPCS and Boost Mobile.
“All I need is the number,” Ryan said of his customer data lookup service, which he sold for $25 per record. “Payment BTC [bitcoin] only.”
For $25 per record, Ryan offered fellow ogusers members the ability to look up customer records tied to any customer of the major U.S. mobile providers.
Very similar offerings were made by Phobia’s alter ego “AOLer” on the sprawling English language online hacking community Hackforums.
I first encountered Stevenson several years back while trying to work out who was responsible for calling in a phony hostage situation and sending a heavily armed police force to our Northern Virginia home in 2013. In a follow-up to that story, Stevenson admitted that he was responsible for the high-profile hack against Wired reporter Mat Honan, who documented how a hacker named Phobia had deleted his Google account and remotely erased all data from his iPhone, iPad and MacBook.
Going by the nickname “Phobiathegod” at the time, Stevenson was then part of a group of young men who routinely hijacked OG account names on Microsoft’s Xbox gaming platform, often using methods that involved tricking customer service people at the target’s mobile provider into transferring the victim’s calls to a number they controlled.
Fast forward to today, and Phobia’s main Twitter account (pictured at the top of this post) includes the phrase “the plug” next to his profile. In SIM swapping circles, a “plug” is hacker slang for an employee at a mobile phone store who can be bribed, tricked or blackmailed into assisting with an unauthorized SIM swap.
Reached via instant message on LinkedIn, Stevenson acknowledged running the ISP doxing services, but said his account on the OGusers forum was since banned and that hardly anyone took him up on his offer anyway.
“I shouldn’t have made the threads even though no one really asked for anything,” he said. “I’m on the good side. But its almost 2019 and I need to find a new hobby I can’t be bothered to look for breaches/vulns, haven’t got 1 job offer or recommendation yet.”
Asked about “the plug” reference in his Twitter profile, Stevenson suddenly stopped replying. Not long after that, the @Phobia Twitter account was deactivated.
Stevenson denied being involved in SIM swapping attacks, but it is clear Phobia was fairly tight with many people who are or until recently were at the center of this scene. In July 2018, authorities in California arrested 20-year-old Boston resident Joel Ortiz for allegedly conducting dozens of fraudulent SIM swaps and stealing at least $5 million worth of cryptocurrency from victims.
Like Phobia, Ortiz had a presence on OGusers and had acquired some of the most OG social media accounts available, including the Twitter and Instagram account names with the number zero (@0), and the OG Youtube accounts “Joel” and “X”.
On Oct 27, 2017, the Youtube account “Joel” published a 4-minute video of Stevenson dancing to a popular rap song in front of the camera. On July 5, 2018, just days before Ortiz was arrested, the Twitter account “0” gave a shout out to @Phobia on Twitter suggesting Phobia was actually tweeting using Ortiz’s “0” account.
from Amber Scott Technology News https://krebsonsecurity.com/2018/11/bug-bounty-hunter-ran-isp-doxing-service/
0 notes
Text
Why Is Your Location Data No Longer Private?
The past month has seen one blockbuster revelation after another about how our mobile phone and broadband providers have been leaking highly sensitive customer information, including real-time location data and customer account details. In the wake of these consumer privacy debacles, many are left wondering who’s responsible for policing these industries? How exactly did we get to this point? What prospects are there for changes to address this national privacy crisis at the legislative and regulatory levels? These are some of the questions we’ll explore in this article.
In 2015, the Federal Communications Commission under the Obama Administration reclassified broadband Internet companies as telecommunications providers, which gave the agency authority to regulate broadband providers the same way as telephone companies.
The FCC also came up with so-called “net neutrality” rules designed to prohibit Internet providers from blocking or slowing down traffic, or from offering “fast lane” access to companies willing to pay extra for certain content or for higher quality service.
In mid-2016, the FCC adopted new privacy rules for all Internet providers that would have required providers to seek opt-in permission from customers before collecting, storing, sharing and selling anything that might be considered sensitive — including Web browsing, application usage and location information, as well as financial and health data.
But the Obama administration’s new FCC privacy rules didn’t become final until December 2016, a month after then President-elect Trump was welcomed into office by a Republican controlled House and Senate.
Congress still had 90 legislative days (when lawmakers are physically in Congress) to pass a resolution killing the privacy regulations, and on March 23, 2017 the Senate voted 50-48 to repeal them. Approval of the repeal in the House passed quickly thereafter, and President Trump officially signed it on April 3, 2017.
In an op-ed published in The Washington Post, Ajit Pai — a former Verizon lawyer and President Trump’s pick to lead the FCC — said “despite hyperventilating headlines, Internet service providers have never planned to sell your individual browsing history to third parties.”
FCC Commissioner Ajit Pai.
“That’s simply not how online advertising works,” Pai wrote. “And doing so would violate ISPs’ privacy promises. Second, Congress’s decision last week didn’t remove existing privacy protections; it simply cleared the way for us to work together to reinstate a rational and effective system for protecting consumer privacy.”
Sen. Bill Nelson (D-Fla.) came to a different conclusion, predicting that the repeal of the FCC privacy rules would allow broadband providers to collect and sell a “gold mine of data” about customers.
“Your mobile broadband provider knows how you move about your day through information about your geolocation and internet activity through your mobile device,” Nelson said. The Senate resolution “will take consumers out of this driver’s seat and place the collection and use of their information behind a veil of secrecy.”
Meanwhile, pressure was building on the now Republican-controlled FCC to repeal the previous administration’s net neutrality rules. The major ISPs and mobile providers claimed the new regulations put them at a disadvantage relative to competitors that were not regulated by the FCC, such as Amazon, Apple, Facebook and Google.
On Dec. 14, 2017, FCC Chairman Pai joined two other Republic FCC commissioners in a 3-2 vote to dismantle the net neutrality regulations.
As The New York Times observed after the net neutrality repeal, “the commission’s chairman, Ajit Pai, vigorously defended the repeal before the vote. He said the rollback of the rules would eventually benefit consumers because broadband providers like AT&T and Comcast could offer them a wider variety of service options.”
“We are helping consumers and promoting competition,” Mr. Pai said. “Broadband providers will have more incentive to build networks, especially to underserved areas.”
MORE OR LESS CHOICE?
Some might argue we’ve seen reduced competition and more industry consolidation since the FCC repealed the rules. Major broadband and mobile provider AT&T and cable/entertainment giant Time Warner are now fighting the Justice Department in a bid to merge. Two of the four-largest mobile telecom and broadband providers — T-Mobile and Sprint — have announced plans for a $26 billion merger.
The FCC privacy rules from 2016 that were overturned by Congress sought to give consumers more choice about how their data was to be used, stored and shared. But consumers now have less “choice” than ever about how their mobile provider shares their data and with whom. Worse, the mobile and broadband providers themselves are failing to secure their own customers’ data.
This month, it emerged that the major mobile providers have been giving commercial third-parties the ability to instantly look up the precise location of any mobile subscriber in real time. KrebsOnSecurity broke the news that one of these third parties — LocationSmart — leaked this ability for years to anyone via a buggy component on its Web site.
LocationSmart’s demo page featured a buggy component which allowed anyone to look up anyone else’s mobile device location, in real time, and without consent.
We also learned that another California company — Securus Technologies — was selling real-time location lookups to a number of state and local law enforcement agencies, and that accounts for dozens of those law enforcement officers were obtained by hackers. Securus, it turned out, was ultimately getting its data from LocationSmart.
This week, researchers discovered that a bug in T-Mobile’s Web site let anyone access the personal account details of any customer with just their cell phone number, including full name, address, account number and some cases tax ID numbers.
Not to be outdone, Comcast was revealed to have exposed sensitive information on customers through a buggy component of its Web site that could be tricked into displaying the home address where the company’s wireless router is located, as well as the router’s Wi-Fi name and password.
It’s not clear how FCC Chairman Pai intends to “reinstate a rational and effective system for protecting consumer privacy,” as he pledged after voting last year to overturn the 2015 privacy rules. The FCC reportedly has taken at least tentative steps to open an inquiry into the LocationSmart debacle, although Sen. Ron Wyden (D-Ore.) has called on Chairman Pai to recuse himself on the inquiry because Pai once represented Securus as an attorney. (Wyden also had some choice words for the wireless companies).
The major wireless carriers all say they do not share customer location data without customer consent or in response to a court order or subpoena. Consent. All of these carriers pointed me to their privacy policies. It could be the carriers believe these policies clearly explain that simply by using their wireless device customers have opted-in to having their real-time location data sold or given to third-party companies.
Michelle De Mooy, director of the privacy and data project at the Center for Democracy & Technology (CDT), said if the mobile giants are burying that disclosure in privacy policy legalese, that’s just not good enough.
“Even if they say, ‘Our privacy policy says we can do this,’ it violates peoples’ reasonable expectations of when and why their location data is being collected and how that’s going to be used. It’s not okay to simply point to your privacy policies and expect that to be enough.”
CHECKING THE FTC’S RECORD
When the FCC’s repeal of the net neutrality rules takes effect on June 11, 2018, broadband providers will once again be regulated by the Federal Trade Commission (FTC). That power was briefly shared with FCC when the agency under the Obama administration passed its net neutrality rules with the assumption that it could regulate broadband providers like telecommunications companies.
When it comes to investigating companies for privacy and security violations, the FTC’s primary weapon is The FTC Act, which “prohibits unfair and deceptive acts or practices in or affecting commerce.” According to the FTC Act, a “misrepresentation or omission is deceptive if it is material and is likely to mislead consumers acting reasonably under the circumstances.” It also finds that an act or practice “is unfair if it causes, or is likely to cause, substantial injury that is not reasonably avoidable by consumers, and not outweighed by countervailing benefits to consumers or competition.”
It’s difficult to think of a bigger violation of those principles than the current practice by the major mobile providers of sharing real-time location data on customers with third parties, without any opportunity for customers to opt-in or opt-out of such sharing.
But it’s unclear whether the FTC would take take any action against such activity, or indeed if it has any precedent to do so. The agency had the ability to go after mobile broadband providers for privacy and security violations between 2002 and 2015, and so KrebsOnSecurity asked the commission to share how many times during that period that it took enforcement actions against broadband providers.
The list I got back from them wasn’t exactly privacy or security focused. The FTC cited a case in 2003 in which it sued AOL and CompuServe over unfair billing practices. In 2009, it helped to take down 3FN, a small, shady ISP that was based in the United States but run by Russians and hosting a stupendous amount of malware, scams and illegal content (i.e. child pornography).
In 2014, the FTC alleged that AT&T Mobility deceptively advertised “unlimited” data while throttling mobile customers who used certain amounts of data (this case is still pending but a recent appeals court decision cleared the way for the FTC to continue its lawsuit).
In 2015, TracFone, the largest prepaid mobile provider in the United States, agreed to pay $40 million to the FTC for consumer refunds to settle charges that it deceived millions of consumers with regard to its “unlimited” data service.
The FTC also cited a scolding letter (PDF) that it sent to Verizon over issues related to the security of its customer routers. No action was taken by the FTC in that case.
How eager the FTC will be to police privacy practices of broadband providers may come down to the priorities of the agency’s new leaders. The Trump administration just tapped Andrew Smith as head of the FTC’s consumer protection office. Smith is a lawyer who used to represent many of the companies that the agency is already investigating.
Smith will need to recuse himself from multiple ongoing investigations his office would normally lead, including data breaches at Equifax and Facebook, thanks to his previous work on behalf of the companies. According to The Hill, Smith testified in October before the Senate Banking Committee on behalf of the credit reporting industry as the panel investigated an Equifax data breach that compromised more than 145 million people.
Gigi Sohn, a fellow at the Georgetown Law Institute for Technology Law and Policy and a former senior adviser to former FCC Chair Tom Wheeler in 2015, said the FTC doesn’t have a strong record on broadband privacy enforcement.
Sohn said the FTC’s legal framework does not require affirmative opt-in consent for browsing history and app usage, and that a provider would only have to let you opt-out — something that consumers rarely do and which companies routinely make it hard to do. More importantly, she said, while the FCC’s rules would have protected consumers before they were harmed, the FTC can only act after harm has already occurred.
“We passed privacy rules for broadband and mobile providers that would have required them to seek customer opt-in for anything that was considered sensitive,” Sohn said of her work at the FCC under the Obama administration. “The carrier had to give you clear and consistent opportunities to opt out. It was very broad, but the definition we set for personal information was far broader than what even the FTC considered sensitive.”
REPEALING THE REPEAL OF NET NEUTRALITY
So the carriers are already reneging on their promise to customers that they won’t share location data without customer consent or a court order. But where does that leave us on net neutrality? The answer is that the major wireless carriers are already doing what was expressly prohibited under the FCC’s net neutrality rules: Favoring their own content over competitors, and letting companies gain more favorable access by paying more.
Around the time of the FCC’s repeal of the net neutrality rules last year, The Wall Street Journal prognosticated about what might happen with the regulations out of the way. To do this, it looked at some of the offerings the mobile carriers pitched before the rules were drawn up.
“One example of how things could work is the mobile wireless market, where some providers already have used pricing tactics to favor certain websites and services over others,” wrote John D. McKinnon and Ryan Knutson for The Journal:
The 2015 Obama-era rules didn’t explicitly prohibit these tactics, which generally allow customers to access certain websites without having it count against their monthly data cap. Wireless carriers, which often subject their users to strict data limits, were aggressive in experimenting with such plans, also known as “zero rating.”
Deals began emerging several years ago for inexpensive plans that offer unlimited high-speed access to popular services such as Facebook or Twitter, but limited or even restricted access to the rest of the internet.
T-Mobile US Inc. in late 2013 announced that its GoSmart Mobile brand had “become the first wireless provider…to offer free access to Facebook and Facebook Messenger for all of its wireless customers, even those without monthly data service.” The GoSmart Mobile plans started at $25 a month for “unlimited talk” with no other data service. T-Mobile has since transferred the GoSmart brand to another wireless firm.
In 2014, Virgin Mobile USA, a unit of Sprint Corp. , offered a wireless plan that cost $12, but users were only allowed to access one website: either Facebook, Twitter, Instagram or Pinterest. If they wanted all four, it was $10 more a month. Another $5 and they could access any online music streaming service.
Big internet providers also used zero-rating plans to favor their own content. AT&T Inc. gave paying customers unlimited usage of its own online video service DirecTV Now, while other video sites counted against monthly data caps. Verizon Communications Inc. did the same for its mobile video app, called go90.”
AT&T Mobility offers a zero-rating plan called “Sponsored Data” that allows content providers to pay up front to have streaming of that content allowed without counting against the provider’s monthly data caps.
Sohn said the FCC under the Obama administration initiated an investigation into AT&T’s Sponsored Data plan and Verizon for its go90 service, but that the inquiry was abandoned by the current FCC leadership.
There are some prospects for a Congressional repeal of this administration’s gutting of the FCC’s net neutrality rules. On May 16, the Senate approved a resolution nullifying the FCC’s rollback of the net neutrality rules. But the measure faces an uphill battle in the House.
“Right now we’re probably 30 to 40 members short of being able to bring a vote in the House,” Sohn said. “About 20 Democrats haven’t gotten on board, and we have no Republicans so far. But I think that’s going to change. If Congress repeals the net neutrality repeal, the next step would be to craft stronger rules [either at the FCC or Congress]. We have until the end of this Congress to get it done.”
The CDT’s De Mooy gives the effort to repeal the repeal of net neutrality rules slim chances of passage this year. But she said the prospects for revisiting net neutrality and consumer privacy in the next Congress look good, particularly if Democrats pick up additional seats in the House.
“It seems to be something the Democrats are taking up more now,” Demooy said. “So much depends on what happens in November. But that’s true of so many tech policy issues.”
SHOCK AND YAWN
When I first saw a Carnegie Mellon University researcher show me last week that he could look up the near-exact location of any mobile number in the United States, I sincerely believed the public would be amazed and horrified at the idea that mobile providers are sharing this real-time data with third party companies, and at the fact that those third parties in turn weren’t doing anything to prevent the abuse of their own systems.
Instead, after a brief round of coverage in several publications, the story fell out of the news cycle. A story this week in Slate.com lamented how little coverage the mainstream press has given to the LocationSmart scandal, and marvels at how much more shocked people were over the Cambridge Analytic scandal with Facebook.
“Privacy abuses and slip-ups by major tech companies have become so numerous, and the prospect of containing them seems so hopeless, that the public and much of the media have become nearly numb to them,” writes Will Oremus for Slate. “My data was hacked? So it goes. It may have been used in unauthorized ways by unspecified parties? C’est la vie.”
Oremus argues that what the LocationSmart scandal lacks is not import, nor the potential for serious harm, “but a link to some divisive political issue or societal outrage sufficient enough to generate visceral anger from people who aren’t privacy wonks.”
If you’ve read this far (bless you), don’t let breach fatigue and incessant media exposure of how little privacy we have harden into resignation. Yes, the prospects of any public debate about consumer privacy protections in the United States at the legislative level seem dim in a high-stakes mid-term election year. But supporters of net neutrality ideals can start getting involved by tweeting, calling and emailing the House lawmakers listed in red at BattleForTheNet.com.
While you’re at it, tell your lawmakers what you think about mobile providers giving or selling third-parties real-time access to customer location information, and let them know that this is no longer okay.
This is the second article in a two-part series. The first is here: Mobile Giants, Please Don’t Share the Where.
from Technology News https://krebsonsecurity.com/2018/05/why-is-your-location-data-no-longer-private/
0 notes
Text
Technology :: IPhone Repair - A Basic Guide
Its hard to remember once we was lacking cellular phones at our disposal. And companies should do whatever they can to stay up with the speed. And companies must do the things they can to stay up using the speed. Many times, companis fall behind, because they cant keep up. One website that provides a cell phone number finder service is along with dozens of other services is found by typing in cell contact number service finders into a search engine. The affordable Kyocera 1100 series, including the Kyocera 1135 cell phone as well as the Kyocera 1155 cell phone, are good buys. It would be nice if U. If you would like to find cell phone numbers, then you can search by several ways. Certain particular websites which offer these types of services are available via a search results as well as the go here websites features a reverse phone lookup service, for when you want to put a reputation along with a face to that annoying prank caller who keeps on ringing you at probably the most irritating moments, along with a cell phone number look service which enables you to definitely search in order to find a cell telephone number easily. People within the accident area may be very curious in what happened. This means which you no longer have to concern yourself with hiring a pricey private detective to track down that missing person, or a friend you haven't spoken to in years because you can take action yourself using the use of this simple and easy , cheap service! You could be wondering why people will probably be compelled to search for cell numbers, but you can find many reasons you may be looking for any phone number. You'll see this for sale at many home improvement and gardening stores inside your area. This means that you no longer have to worry about hiring an expensive private detective to trace down that missing person, or a buddy you haven't spoken to in years as you can get it done yourself with the use of this simple and cheap service! You may be wondering why people will be compelled to search for cell numbers, but you will find many reasons you could be looking for a phone number. You can also post comments, check the latest news, learn more concerning the products you own or you would like to purchase, etc. This is particularly the case in emergency situations. At the time your vehicle's engine is off, the battery supplies the mandatory power to the remaining portion of the system, plus during start-up (cranking). Immediately, the engine began to shudder, knock, ping, and shudder again, before making a noise that sounded almost like a sigh, followed by silence. As far as radiation emitters, the worst offenders are made by Motorola and distributed by Verizon Wireless and U. com to understand much more about driving safely. Tire shredders for sale is found in a variety of places and also the utilisation of the byproduct is growing. This last guideline could very well be one of the most important. Furthermore, in the event they fail to fix the faulty phone, they simply might give that you simply good price because of it while they may use its parts to perform their future repair jobs.
0 notes
Text
The Reality Regarding details
information Explained.
Recognizing your ABC's is as very easy as browsing our online data source for the very best short articles, suggestions as well as suggestions readily available anywhere. The stipulations of paragraphs 2 (Use of the Solution), and also 3 chocolate slim (Indemnification) are for the advantage of ABC Short article Directory ©; and its officers, directors, workers, agents, licensors, providers, as well as any kind of third party info companies to the Service. The text mining component covers the analysis of message including material extraction, string matching, clustering, referral, and classification systems. Gathered details may be Directly Identifiable Details or Non-Personally Identifiable Info. As an example, you could be asked to give information when you sign up for access to certain sections of our site or demand certain attributes, such as e-newsletters or when you make a purchase. Substantial collection as well as processing of the measurable, or structured, information, in addition to of the textual data commonly gathered online, has actually developed into a wide campaign known as large data." Several advantages can occur from choices based upon the facts shown by large information. If your demand encompasses greater than 950 receptive web pages, an FBI rep will certainly contact you in an effort to minimize the fees and the processing time associated with your demand. The initial one, it gives individuals a rough idea of where their calorie need would certainly lie to make sure that those that are not going to compute will take advantage of this details. As contrasted with data, details is refined to remove appropriate data from late 20th c. As significant new innovations for videotaping as well as processing details were created over the centuries, new capacities showed up, and also people came to be encouraged. Finding that excellent device could aid you right into taking care of details and if you are wise enough, you will undoubtedly never weary of improving those skills. Information systems support operations, understanding work, as well as monitoring in organizations. So this information offers the macronutrient make-up for their daily food intake to make sure that they not only recognize just how much to consume yet likewise exactly what to consume. But with each brand-new scientific research or perhaps in some cases with each new house appliance, there comes a certain amount of suspicion or doubt regarding a new innovation.
The Fundamentals of details That You Could Benefit From Starting Today
Log file details is instantly reported by your web internet browser each time You see a web page. So the info divulged in any kind of report you purchase is precisely the data the mobile phone service provider keeps in its database relating to the unknown telephone number you could be browsing.
The Fatality of information
The reason I state this is because any type of directory site that supplies outcomes of cordless number lookups has actually first bought this details from the significant wireless service providers like Sprint, Verizon, and also Nextel. Each MSDS needs to be in English and also consist of info concerning the details chemical identity of the dangerous chemical( s) entailed as well as the common names. Details Visualization (shortened as InfoVis) depends on the calculation as well as electronic depiction of data, and also assists users in pattern acknowledgment and anomaly discovery. When and assists them look at weight loss in a much more believable and also accomplishable way, the 3rd information is indicated to be an inspirational aspect as it makes clear numerous inquiries at. Deduct Your Charge card Handling Account Charges isn't expensive, but you'll locate that the little purchase fees do add up when you incorporate them with setup fees and also various other costs that gather throughout the year. In method, info is normally lugged by weak stimuli that must be discovered by specialized sensory systems and also amplified by energy inputs before they can be practical to the organism or system. Making use of a bookmarking solution is actually useful for every person online considering that bookmarking is sharing details. A demand is directed through a small handling track if it encompasses 50 pages or much less, a medium processing track if it inclusives 51 to 950 web pages, or a large handling track if it includes 951 web pages or more. Social and cultural context of information and infotech, seen from a historical perspective, goes to the heart of the journal's rate of interests. In this training course we will certainly study the fundamental as well as layout applications of different biometric systems based on finger prints, voice, face, hand geometry, palm print, iris, retina, and also other methods. Bounded rationality is the idea that in decision making, the rationality of the representative is restricted by the quantity as well as top quality of information that they have, their own cognitive limitations and the amount of time they need to decide.
0 notes
Text
Trace a Mobile Number - Trace Anonymous Callers
New Post has been published on https://app2chart.com/trace-a-mobile-number-trace-anonymous-callers/
Trace a Mobile Number - Trace Anonymous Callers
Are you wondering how to get rid of persistent prank callers, but just can not find a way? Well, whatever for whatever reason you want to track a phone, these are the three options for you to choose from.
Get Best Reverse Phone Number Trace Service
Option No. 1 – The White Pages
Browse the pages of this guide can help you find solid numbers and nothing more! If you want some information about a particular mobile subscriber, you have the wrong folder consulted. This is because mobile numbers are ‘personal and confidential “and are protected by certain privacy laws, including the” Wireless 411 Privacy Act “.
Neither the mobile phone user or the wireless companies want their subscribers privacy at risk by publishing it on the public phone book. This is why you never phone for Verizon, Sprint, Cingular or other wireless services seen!
Option 2 – Private Investigator
This is a great way for confidential results. But if you choose this second option, ready to find yourself at least one hundred U.S. dollars to service charges.
Option No. 3 – Online Reverse Cell Phone Lookup – the most effective option!
This is undoubtedly the most effective option for a confidential inquiry. The best modern databases are incredibly fast and your search takes only 2-5 minutes!
This is by far the most efficient way to trace a mobile number. Just call the 10-digit number you want to dig for info on, and you can use the following in no time:
Get Best Reverse Phone Number Trace Service
Name and address (including previous residence addresses) Civil registration, household members, associates Average income Plus other valuable information
What more if your searches are 100% confidential at the delivery of a reliable service!
However, not all reverse phone directories are as accurate and reliable. Some databases are simply too small, while some are outdated and therefore incorrect. You must ensure that such databases at the expense
Reverse Phone Detective is an online service that lets you do a reverse phone lookup on cellphone numbers. With just a cell number, you can find out the owner, location and details about the phone’s owner. Until recently, this type of search would have required the resources of a private detective, but Reverse Phone Detective makes it available to ordinary people like you and Me!
There are several companies that offer a similar service, but the Reverse Phone Detective site is by far the best. There are 15,000 users on the site on any given day. Reverse Phone Detective has over 250 million cell phone numbers in its database, making it easy to find the information you are looking for.
Get Best Reverse Phone Number Trace Service
app marketing
buy app reviews
0 notes
Text
Trace a Mobile Number - Trace Anonymous Callers
New Post has been published on https://app2chart.com/trace-a-mobile-number-trace-anonymous-callers/
Trace a Mobile Number - Trace Anonymous Callers
Are you wondering how to get rid of persistent prank callers, but just can not find a way? Well, whatever for whatever reason you want to track a phone, these are the three options for you to choose from.
Get Best Reverse Phone Number Trace Service
Option No. 1 – The White Pages
Browse the pages of this guide can help you find solid numbers and nothing more! If you want some information about a particular mobile subscriber, you have the wrong folder consulted. This is because mobile numbers are ‘personal and confidential “and are protected by certain privacy laws, including the” Wireless 411 Privacy Act “.
Neither the mobile phone user or the wireless companies want their subscribers privacy at risk by publishing it on the public phone book. This is why you never phone for Verizon, Sprint, Cingular or other wireless services seen!
Option 2 – Private Investigator
This is a great way for confidential results. But if you choose this second option, ready to find yourself at least one hundred U.S. dollars to service charges.
Option No. 3 – Online Reverse Cell Phone Lookup – the most effective option!
This is undoubtedly the most effective option for a confidential inquiry. The best modern databases are incredibly fast and your search takes only 2-5 minutes!
This is by far the most efficient way to trace a mobile number. Just call the 10-digit number you want to dig for info on, and you can use the following in no time:
Get Best Reverse Phone Number Trace Service
Name and address (including previous residence addresses) Civil registration, household members, associates Average income Plus other valuable information
What more if your searches are 100% confidential at the delivery of a reliable service!
However, not all reverse phone directories are as accurate and reliable. Some databases are simply too small, while some are outdated and therefore incorrect. You must ensure that such databases at the expense
Reverse Phone Detective is an online service that lets you do a reverse phone lookup on cellphone numbers. With just a cell number, you can find out the owner, location and details about the phone’s owner. Until recently, this type of search would have required the resources of a private detective, but Reverse Phone Detective makes it available to ordinary people like you and Me!
There are several companies that offer a similar service, but the Reverse Phone Detective site is by far the best. There are 15,000 users on the site on any given day. Reverse Phone Detective has over 250 million cell phone numbers in its database, making it easy to find the information you are looking for.
Get Best Reverse Phone Number Trace Service
app marketing
buy app reviews
0 notes
Text
Trace a Mobile Number - Trace Anonymous Callers
New Post has been published on https://app2chart.com/trace-a-mobile-number-trace-anonymous-callers/
Trace a Mobile Number - Trace Anonymous Callers
Are you wondering how to get rid of persistent prank callers, but just can not find a way? Well, whatever for whatever reason you want to track a phone, these are the three options for you to choose from.
Get Best Reverse Phone Number Trace Service
Option No. 1 – The White Pages
Browse the pages of this guide can help you find solid numbers and nothing more! If you want some information about a particular mobile subscriber, you have the wrong folder consulted. This is because mobile numbers are ‘personal and confidential “and are protected by certain privacy laws, including the” Wireless 411 Privacy Act “.
Neither the mobile phone user or the wireless companies want their subscribers privacy at risk by publishing it on the public phone book. This is why you never phone for Verizon, Sprint, Cingular or other wireless services seen!
Option 2 – Private Investigator
This is a great way for confidential results. But if you choose this second option, ready to find yourself at least one hundred U.S. dollars to service charges.
Option No. 3 – Online Reverse Cell Phone Lookup – the most effective option!
This is undoubtedly the most effective option for a confidential inquiry. The best modern databases are incredibly fast and your search takes only 2-5 minutes!
This is by far the most efficient way to trace a mobile number. Just call the 10-digit number you want to dig for info on, and you can use the following in no time:
Get Best Reverse Phone Number Trace Service
Name and address (including previous residence addresses) Civil registration, household members, associates Average income Plus other valuable information
What more if your searches are 100% confidential at the delivery of a reliable service!
However, not all reverse phone directories are as accurate and reliable. Some databases are simply too small, while some are outdated and therefore incorrect. You must ensure that such databases at the expense
Reverse Phone Detective is an online service that lets you do a reverse phone lookup on cellphone numbers. With just a cell number, you can find out the owner, location and details about the phone’s owner. Until recently, this type of search would have required the resources of a private detective, but Reverse Phone Detective makes it available to ordinary people like you and Me!
There are several companies that offer a similar service, but the Reverse Phone Detective site is by far the best. There are 15,000 users on the site on any given day. Reverse Phone Detective has over 250 million cell phone numbers in its database, making it easy to find the information you are looking for.
Get Best Reverse Phone Number Trace Service
app marketing
buy app reviews
0 notes
Text
Trace a Mobile Number - Trace Anonymous Callers
New Post has been published on https://app2chart.com/trace-a-mobile-number-trace-anonymous-callers/
Trace a Mobile Number - Trace Anonymous Callers
Are you wondering how to get rid of persistent prank callers, but just can not find a way? Well, whatever for whatever reason you want to track a phone, these are the three options for you to choose from.
Get Best Reverse Phone Number Trace Service
Option No. 1 – The White Pages
Browse the pages of this guide can help you find solid numbers and nothing more! If you want some information about a particular mobile subscriber, you have the wrong folder consulted. This is because mobile numbers are ‘personal and confidential “and are protected by certain privacy laws, including the” Wireless 411 Privacy Act “.
Neither the mobile phone user or the wireless companies want their subscribers privacy at risk by publishing it on the public phone book. This is why you never phone for Verizon, Sprint, Cingular or other wireless services seen!
Option 2 – Private Investigator
This is a great way for confidential results. But if you choose this second option, ready to find yourself at least one hundred U.S. dollars to service charges.
Option No. 3 – Online Reverse Cell Phone Lookup – the most effective option!
This is undoubtedly the most effective option for a confidential inquiry. The best modern databases are incredibly fast and your search takes only 2-5 minutes!
This is by far the most efficient way to trace a mobile number. Just call the 10-digit number you want to dig for info on, and you can use the following in no time:
Get Best Reverse Phone Number Trace Service
Name and address (including previous residence addresses) Civil registration, household members, associates Average income Plus other valuable information
What more if your searches are 100% confidential at the delivery of a reliable service!
However, not all reverse phone directories are as accurate and reliable. Some databases are simply too small, while some are outdated and therefore incorrect. You must ensure that such databases at the expense
Reverse Phone Detective is an online service that lets you do a reverse phone lookup on cellphone numbers. With just a cell number, you can find out the owner, location and details about the phone’s owner. Until recently, this type of search would have required the resources of a private detective, but Reverse Phone Detective makes it available to ordinary people like you and Me!
There are several companies that offer a similar service, but the Reverse Phone Detective site is by far the best. There are 15,000 users on the site on any given day. Reverse Phone Detective has over 250 million cell phone numbers in its database, making it easy to find the information you are looking for.
Get Best Reverse Phone Number Trace Service
app marketing
buy app reviews
0 notes
Text
Verizon to Stop Sharing Customer Location Data With Third Parties
In the wake of a scandal involving third-party companies leaking or selling precise, real-time location data on virtually all Americans who own a mobile phone, the four major wireless carriers have responded to requests from a U.S. senator for more details about how the carriers are managing access to this extremely sensitive information. While three out of four providers said they had cancelled data sharing agreements with some of the offending companies, only one — Verizon — pledged to terminate all of them and initiate a wholesale review of their location data-sharing practices.
At issue are companies known in the wireless industry as “location aggregators,” entities that manage requests for real-time customer location data for a variety of purposes, such as roadside assistance and emergency response. These aggregators are supposed to obtain customer consent before divulging such information, but several recent incidents show that this third-party trust model is fundamentally broken.
On May 10, 2018, The New York Times broke the story that a little-known data broker named Securus was selling local police forces around the country the ability to look up the precise location of any cell phone across all of the major U.S. mobile networks.
Then it emerged that Securus had been hacked, its database of hundreds of law enforcement officer usernames and passwords plundered. We also learned that Securus’ data was ultimately obtained from a company called 3Cinteractive, which in turn obtained its data through a California-based location tracking firm called LocationSmart.
On May 17, KrebsOnSecurity broke the news of research by Carnegie Mellon University PhD student Robert Xiao, who discovered that a LocationSmart try-before-you-buy opt-in demo of the company’s technology was wide open — allowing real-time lookups from anyone on anyone’s mobile device — without any sort of authentication, consent or authorization.
LocationSmart disabled its demo page shortly after that story. By that time, Sen. Ron Wyden (D-Ore.) had already sent letters to AT&T, Sprint, T-Mobile and Verizon, asking them to detail any agreements to share real-time customer location data with third-party data aggregation firms.
AT&T, T-Mobile and Verizon all said they had terminated data-sharing agreements with Securus. In a written response (PDF) to Sen. Wyden, Sprint declined to share any information about third-parties with which it may share customer location data, and it was the only one of the four carriers that didn’t say it was terminating any data-sharing agreements.
T-Mobile and Verizon each said they both share real-time customer data with two companies — LocationSmart and another firm called Zumigo, noting that these companies in turn provide services to a total of approximately 75 other customers.
Verizon emphasized that Zumigo — unlike LocationSmart — has never offered any kind of mobile location information demo service via its site. Nevertheless, Verizon said it had decided to terminate its current location aggregation arrangements with both LocationSmart and Zumigo.
“Verizon has notified these location aggregators that it intends to terminate their ability to access and use our customers’ location data as soon as possible,” wrote Karen Zacharia, Verizon’s chief privacy officer. “We recognize that location information can provide many pro-consumer benefits. But our review of our location aggregator program has led to a number of internal questions about how best to protect our customers’ data. We will not enter into new location aggregation arrangements unless and until we are comfortable that we can adequately protect our customers’ location data through technological advancements and/or other practices.”
In its response (PDF), AT&T made no mention of any other company besides Securus. AT&T indicated it had no intention to stop sharing real-time location data with third-parties, stating that “without an aggregator, there would be no practical and efficient method to facilitate requests across different carriers.”
Sen. Wyden issued a statement today calling on all wireless companies to follow Verizon’s lead.
“Verizon deserves credit for taking quick action to protect its customers’ privacy and security,” Wyden said. “After my investigation and follow-up reports revealed that middlemen are selling Americans’ location to the highest bidder without their consent, or making it available on insecure web portals, Verizon did the responsible thing and promptly announced it was cutting these companies off. In contrast, AT&T, T-Mobile, and Sprint seem content to continuing to sell their customers’ private information to these shady middle men, Americans’ privacy be damned.”
Wyden’s letter asked the carriers to detail any arrangements they may have to validate that location aggregators are in fact gaining customer consent before divulging the information. Both Sprint and T-Mobile said location aggregators were contractually obligated to obtain customer consent before sharing the data, but they provided few details about any programs in place to review claims and evidence that an aggregator has obtained consent.
AT&T and Verizon each said they have processes for periodically auditing consent practices by the location aggregators, but that Securus’ unauthorized use of the data somehow flew under the radar.
AT&T noted that it began its relationship with LocationSmart in October 2012 (back when it was known by another name, “Locaid”). Under that agreement, LocationSmart’s customer 3Cinteractive would share location information with prison officials through prison telecommunications provider Securus, which operates a prison inmate calling service.
But AT&T said after Locaid was granted that access, Securus began abusing it to sell an unauthorized “on-demand service” that allowed police departments to learn the real-time location data of any customer of the four major providers.
“We now understand that, despite AT&T’s requirements to obtain customer consent, Securus did not in fact obtain customer consent before collecting customers’ location information for its on-demand service,” wrote Timothy P. McKone, executive vice president of federal relations at AT&T. “Instead, Securus evidently relied upon law enforcement’s representation that it had appropriate legal authority to obtain customer location data, such as a warrant, court order, or other authorizing document as a proxy for customer consent.”
McKone’s letter downplays the severity of the Securus incident, saying that the on-demand location requests “comprised a tiny fraction — less than two tenths of one percent — of the total requests Securus submitted for the approved inmate calling service. AT&T has no reason to believe that there are other instances of unauthorized access to AT&T customer location data.”
Blake Reid, an associate clinical professor at the University of Colorado School of Law, said the entire mobile location-sharing debacle shows the futility of transitive trust.
“The carriers basically have arrangements with these location aggregators that contractually say, ‘You agree not to use this access we provide you without getting customer consent’,” Reid said. “Then that aggregator has a relationship with another aggregator, and so on. So what we then have is this long chain of trust where no one has ever consented to the provision of the location information, and yet it ends up getting disclosed anyhow.”
Curious how we got here and what Congress or federal regulators might do about the current situation? Check out last month’s story, Why Is Your Location Data No Longer Private.
from https://krebsonsecurity.com/2018/06/verizon-to-stop-sharing-customer-location-data-with-third-parties/
0 notes