#uphold login
Explore tagged Tumblr posts
Text
2 notes
·
View notes
Text
Uphóld Lógin – Most Secure, User-Friendly Crypto Exchange Platform #upholdlogin
Uphóld Lógin
makes it easy for crypto traders to trade, invest, store, buy and sell digital currencies. The exchange platform supports more than 30 currencies, including eight of the most popular cryptocurrencies, traditional fiat currencies, and commodities. You don’t know what might be missing out if you don’t have an Uphóld Lógin account yet! Generating a new Uphóld Lógin account is no rocket science and takes only a few minutes. Once you create an account, you can have access to a safe digital wallet that you can use to begin your cryptocurrency portfolio right away!
1 note
·
View note
Text
How To Log In to My Uphold account

ỤṔHOLD ĹOĠIN: SIGN IN TO UPHOLD ACCOUNT – BUY & SELL

0 notes
Text
Buying Bitcoin through the Uphold signin platform
Bitcoin is 100% reserved and you can be sure that they will not lend your money to anyone. You will be able to place up to as many as 50 advanced limit orders at once. You have the option of managing the portfolio through the IOS, Android and web apps. Buying Bitcoin through the Uphold sign-in platform will be a good idea.

0 notes
Text
Hot And Cold Motivation
Learning Japanese is probably one of my few major life goals that has stuck around most of my life. I would say that my interest in Japanese sparked eleven years ago, and that goal has not wavered.
Typing that out I meet myself with a frustration and agitation that is hard to describe.
"If I've wanted to learn this language for the past eleven years - why haven't I learned it yet? Why do I still feel like a beginner?"
Well the answer to the latter question is easy - I am still a beginner. That is why I feel like one.
The former question is the one that is a bit more difficult to explain. The problem has always been my motivation and how that effects my consistency. I would say I am suffering from hot and cold motivation.
Somedays I want to consume nothing but Japanese. I do my anki, read up on grammar, and immerse in nothing but Japanese content all day. This is hot motivation. But other days... I wake up and see my review count in anki and think "I don't want to do this right now.. maybe tonight." I login to YouTube to immerse and nothing seems interesting to me, and the thought of reading makes me want to topple over and sob. Then that night as I lay in bed about to sleep, I remember that I did not do my anki that day, and in an effort to uphold my streak, I do a few cards and then go to bed. This is cold motivation.
In the Refold roadmap they say the best thing you can do when these days come up is accept it and just make sure you don't do it again tomorrow. It's better to give yourself a day, but you don't want to make it a habit.
But what happens when there are several days in a row of cold motivation, and you can't seem to even force yourself to learn a language that day?
When I was a senior in high school, I was diagnosed with major depressive disorder in the form of dysthymia. Dysthymia is a form of long-lasting depression that doesn't really feel like it goes away. What this means for me is that I often have these off days - and that's okay. I will divulge in another post how I eventually plan to combat this and learn more effectively, but after eleven years of combating this I finally know what to do when I have these days.
For me, the best thing to do, is do another hobby I enjoy. Maybe that means strumming my guitar, drawing a bit, watching a show I like, or whatever.
Learning a language is a long and difficult road to navigate. On the days your legs are tired of carrying you, it's okay to sit down and look down the road that you've already walked. Look around a bit, maybe set up a tent and camp on the road a few days. When you're ready, that road will still be there waiting for you to continue walking down.

12 notes
·
View notes
Text
Deadline: December 17th, 2023 Payment: 9 cents per word Theme: Science-fiction, fantasy and horror, inspired by classic pulp magazines, starring LGBTQIA+ heroes and villains. IWTTO! is seeking classic pulp adventures centring non-traditionally masculine queer heroes and villains. If you’ve ever found yourself reading Ray Bradbury, Robert Heinlein, Robert E. Howard or Fritz Leiber, and just wanted it to be more sodding gay then this anthology is for you. Whether fantasy, science-fiction or horror, we want to prove that hetero himbos don’t hold a monopoly on giant swords. We want out and proud thrill-rides starring queers who don’t give a frack what society says. Smash systems, kiss boys, be gay do crime. Concept: Pulp-inspired science fiction, fantasy and horror that explores or subverts classic genre tropes through queer protagonists and villains, particularly those who are non-traditionally masculine. What we’re looking for: Stories that take full advantage of pulp excess (“more is more”), and that have queerness at their core. The Editors take a broad definition of queer and we want to see stories that speak to our own community. We love our LGBTQIA+ heroes AND villains, and are just as eager for queer rage blood baths as we are for Flash-Gordon-style space opera. Bring us your femboy starship captains, bring us to trans berserkers fuelled by queer rage, bring us your literal demon twinks. Most of all, bring us stories that make you shriek... “I Want That Twink OBLITERATED!” Guidelines: ● We are seeking original science fiction, fantasy and horror stories written in English. This is an inclusive LGBTQIA+ anthology from a queer press and we want stories that uphold that ethos. ● Instructions: All stories should be submitted through our online form as a .doc or .docx file. If for any reason you are unable to use a Google login to submit this form, please contact bona.to.books[@]gmail.com (without the square brackets) and we will arrange an alternate method of submission. ● Simultaneous submissions are fine, but please withdraw immediately if your story is accepted elsewhere. No multiple submissions, but if you have a story rejected before the deadline you may submit again. (Although note: The editors make no promises about how quickly submissions will be reviewed.) ● Word Count: Stories should be no more than 6,000 words long, but 4,000-5,000 is ideal. Flash fiction will happily be considered, but as the exception rather than the rule. ● Format: We don’t wish to create barriers to entry, so if you have a story in standard manuscript format you’re absolutely fine. However, the editors are fans of Modern Manuscript Format, Garamond, and italics as italics. ● Rates: Authors will be paid $0.08 /word for worldwide English language rights (including audio, if that stretch goal is met). ● Cover letters: None! Nada! Not required! There is a box on the form where you can tell us any information that you think we really need to know about you (awards noms, pro publications, specific expertise relevant to the story). However, we won’t read any of this until after your story, so don’t worry about selling yourself. ● Reprints: We are seeking original English language stories and will not consider reprints. ● Enquiries: Please contact bona.to.books[@]gmail.com (without the square brackets) if you have any questions or problems, but do not send any submissions to this address. ● Responses: We are aiming to respond to all submissions by 31 January 2024. Please query if you have not heard back by then. ● AI-Assisted Writing: ...can get in the bin. At once. Off you pop. ● Notes on Stories: ○ The editors define “twink” very broadly and encourage authors to do so too (indeed, break the concept apart and subvert it if you fancy). Our real focus is on exciting, queer stories with non-traditionally masculine heroes or villains. ○ We are seeking all types of science fiction, fantasy and horror, as long as it is queer and fits with our pulp/genre vibe.
○ For the editors, queerness embraces a full spectrum of identities and experiences. Ace/aro, trans, nonbinary and intersex stories are all welcome. ○ The editors are particularly interested in submissions from trans, non-binary, or intersex writers; aro or ace writers; disabled writers; neurodiverse writers; black, south asian, or east asian writers; or other writers of colour. ○ Given the long, fabulous history of queer-coded villains, the editors would love a mix of stories that explore heroes’ and villains’ perspectives. ○ The editors have no interest in gratuitous sexual violence or unexamined prejudice. Great stories can grapple with these things, but if you’re using them as window-dressing it’s not for us. ● If you’re in doubt whether your story fits, submit and let our editors take a look. Don’t self-reject! The Submission Portal is now LIVE! Via: I Want That Twink OBLITERATED!'s Kickstarter.
30 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text
Facebook Policy Playbook

Preserving digital privacy and understanding the digital landscape of popular platforms like Facebook has become essential for responsible virtual citizens and tech-aware individuals. Today's discussion on Facebook's data collection practices was incredibly eye-opening. We watched an informative video that shed light on the various types of data that the platform gathers - explicit data we provide, metadata about our activity, information from third-party sources, and even off-Facebook online activity through tracking pixels and plugins on other websites.
The video provided some wise advice on limiting the platform's access to our personal data by regularly reviewing and tightening privacy settings, being cautious about sharing sensitive information publicly, and being wary of scams and phishing attempts aimed at extracting login credentials. Ultimately, the professor rightly emphasized that "privacy only comes to those who work for it" and that we must remain proactive about safeguarding our digital footprints.
I applied this learning in the creation of my social media policy, a learning evidence output that is a deliverable for this course. Mine so happens to be Facebook, and the content summarized the best practices for responsible platform use. Developing these guidelines forced me to think critically about online privacy, security, and ethical conduct.

Personally, crafting a balanced policy that protected user privacy while still enabling the core social functionality of Facebook was quite challenging. Eventually, I decided to aim to empower users with knowledge and tools to make well-informed choices that align with their personal privacy preferences. I advocated for clear, straightforward language and a fun visual layout to maximize accessibility and engagement.
Notably, I stressed the importance of the platform being transparent about its data collection practices - an issue highlighted in today's lesson that currently needs to be addressed. I also appropriately tackled on the definition of digital citizenship and respectful conduct without being overly restrictive.
Creating these guidelines hands-on brought the risks and nuances of the digital world into sharp focus and solidified my learnings from this session. I now have a deeper appreciation for thoughtfully upholding ethics as a virtual citizen and potential future tech developer. As the line between our digital and tangible realities continues blurring, thoughtfully navigating through these risks and nuances is essential for protecting our privacy and rights moving forward.
2 notes
·
View notes
Text
ARB Birthday Special: Tomi Chōten

~~ August 14th ~~
"It’s all about the money."
Login Lines:
"...Yes, yes, I'll be sure to attend your party later this week. Thank you ever so much for your time. *sighs* How I detest the fact that I have to appease these sycophants. They are all the same: they simply wish to be seen with me, or they want something from me. *sighs* What's next on the agenda, Hino-san?"
"Hmm... 'prepare for my birthday celebration'? ...Hino-san, did you purposely leave this off my calendar so I wouldn't know today is my day of birth? ...You wanted me to see this last since I'll have the rest of the day free? ...Very well, I'll accept this, but please give me some notice next time."
Voice Lines:
*Sighs* "Maybe I should have kept quiet about today being my birthday. It seems every time it comes around, more and more people try to bring me meaningless gifts in an attempt to gain my favor. And they're all of low-quality too. But considering they are all commoners, my expectations weren't very high to begin with."
"...Still, I suppose there's something to be said for gifts that come from the heart instead of being bought off of a shelf from a store just because it's convenient. I can't even recall the last time my parents gave me a gift that wasn't just money or some expensive piece of jewelry. The only person in my family who actually gave me something of actual worth was my brot... gah! Why am I remembering useless things like this?!"
"My parents are planning a large party for my birthday, as they do every time my birthday rolls around. I'd ask if it were possible to just have a small one, but I'd just be wasting my breath. They'd give me the same speech they always give about how important it is to 'make a good impression' or 'uphold the Chōten legacy'. Different day, same thing..."
"Thank you, Karada. I'm glad to see you've stopped by. ...Yes, it's hard to believe we've associated with each other for such a long time. Honestly, I'm glad I decided to speak with you. If I hadn't, I wouldn't have gotten to know you. You are... a good friend. ...Yes, I do mean that."
"And what is this now? ...A phone screen magnifier? For viewing my phone up close? ...And pray tell, why exactly would I need this? If I want to watch movies, that is what my 64-inch flat screen is for. ...Very well, I'll accept it. I suppose it would be good to use when I'm FaceTiming someone."
"Ah, Luis. For the second time in a year, you've actually made it out for my birthday. Keep this up, and I may start to think that you actually value me. ...Ha, so you aren't able to stop Karada from dragging you out of your restaurant? Aren't you older and taller than him? Sorry, but I don't buy that excuse."
"Fine, I'll keep my comments to myself in exchange for the gift that you've graciously bought for me. So, what is it? A... food smoker? ...Luis, are you sure you didn't buy this for yourself? Did you forget that I have chefs cook for me? Why would I ever use this? ...It can also be used for cocktails? ...Fine, I'll give it a try. But FYI, if I don't like this thing, I'm giving it to my head chef."
Karada Lines:
"Happy birthday, Tomi! Man, I tell you, I can't believe we've only known each other for only seven years! It feels so much longer! ...Yeah man, I'm glad you spoke to me too! You're a good guy, despite what anyone else says and thinks. ...Aww! Thanks, Tomi! That means a lot to me, man!"
"Here's your birthday gift! I'll admit, I had trouble finding something good, but I saw this in a catalog and realized it would be good for you. It's a phone screen magnifier for viewing your phone screen up close. Pretty nifty, huh? ...Well, I mean you may not want to use your TV all the time. And it's not just for videos, you can also use it when you're browsing the Internet or something. Great, glad you like it, man! Happy birthday again!"
Luis Lines:
"Yeah yeah, happy birthday, Tomi. ...Oh, don't get a big head. You're not that important to me. I'm only here because of Karada. Honestly, if he hadn't reminded me that today was your birthday, I would have forgotten. ...Keep running off at your mouth, and I'll take this gift I bought you back with me. Your choice."
"Good. So... here. It's a food smoker. You use it to blow out smoke onto food and drinks to give it a nice aroma. ...It's not just for your food, smartass. I just said you can also use it for your drinks, like cocktails. ...Fine, whatever. I gave you a gift, which means I'm done. Now, I'm heading out. Happy birthday or whatever, you ungrateful ass."
#hypmic#hypnosis mic#hypnosis microphone#hypmic oc#hypnosis mic oc#tomi chōten#karada kessaku#luis kōkyū#jet set trio#aoyama division#happy birthday tomi 2023#alternative rap battle#hypmic arb
9 notes
·
View notes
Text
Pillars of AI Security: Protecting the Future of Technology

Artificial Intelligence (AI) is steadily transitioning into mainstream adoption. Yet, like all advanced technologies, it brings both rewards and risks.
The global AI infrastructure market is projected to surpass $96 billion by 2027. Mckinsey reports a 250% surge in AI adoption from 2017 to 2022. Top use cases include optimizing service operations, developing AI-powered products, customer service analytics, and segmentation. However, each of these AI app developments remains highly vulnerable to cyber attacks and potential security breaches.
Over 81% of users express concerns about the security threats posed by generative AI applications, like ChatGPT. The primary fears revolve around AI security issues, data privacy, and ethical challenges, which highlight significant vulnerabilities.
This guide outlines strategies and pillars for building robust AI security frameworks by identifying and mitigating risks at every level.
Why is AI Security Important?

For complex cyber threats, AI security plays an important role in defending businesses. As businesses migrate to cloud and hybrid environments, they face challenges like data sprawl and expanded attack surfaces. Cybercriminals continuously develop new tactics to exploit these vulnerabilities, while the shortage of cybersecurity experts only adds to the pressure.
The number and severity of cyber-attacks are rising steadily. Recent data shows that the global average cost of a data breach reached $4.45 million in 2023, a 15% rise over three years. This surge underscores the growing need for AI security solutions to combat these threats.
AI security automates threat detection and response, catching cybercriminals in action and reducing potential damage. Advanced AI tools can identify malware, isolate harmful software, and block repeated login attempts to prevent brute-force attacks. This proactive defense enables businesses to stay ahead of attackers and protect sensitive data.
AI-powered systems continuously analyze data, adapting to new attack methods in real-time. By evolving with each threat, these systems enhance their ability to detect even the most sophisticated cyber risks. This adaptability is key in minimizing vulnerabilities and maintaining robust security.
Companies that neglect AI security face significant financial losses. Data breaches in organizations without AI security cost an average of USD 5.36 million, 18.6% higher than the global average. Even those with basic AI security reported a substantial reduction in breach costs, proving its value in reducing financial risks.
However, AI security is not without its challenges. Its effectiveness depends heavily on the quality of its training data. If this data is biased or tampered with, it can lead to incorrect threat detection and flawed decision-making. For instance, biased data could skew hiring processes, favoring certain demographics unfairly.
Cybercriminals also leverage AI to amplify their attacks, automating the search for vulnerabilities and launching more convincing phishing scams. Recent findings reveal that AI-driven cyberattacks are on the rise, with 75% of senior cybersecurity leaders noting an increase in such incidents.
Despite these risks, only 24% of current AI projects are sufficiently secured. Moving forward, organizations must prioritize secure AI development to harness its benefits while upholding ethical standards and safeguarding against misuse. Investing in AI security is essential to stay resilient in the face of evolving cyber threats.
3 Pillars of AI Security

AI Data Security
Machine learning and deep learning models require diverse, large, and reliable datasets for effective training, validation, and retraining. Ensuring that training datasets are well-represented is crucial to avoid biases in the AI model. Yet, to adhere to global privacy laws, these datasets must be pre-cleaned and anonymized, which is often overlooked by many organizations.
Neglecting structured AI data storage and failing to secure data in transit can expose systems to severe threats like data theft or data poisoning—two significant challenges in AI security.
Risk: Privacy and Copyright Breaches
Building a robust AI model generally demands ten times more data than the model’s parameters. Yet, global privacy regulations limit how AI developers can use customer data in model training. Despite this, some developers continue using personally identifiable information (PII) without proper legal consent.
Companies like Spotify and OpenAI have faced substantial legal issues due to non-compliance. Spotify was fined $5.4 million for not disclosing data usage in its AI model under GDPR regulations. OpenAI is also dealing with legal challenges for allegedly using copyrighted personal data without proper authorization. New regulations like the EU AI Act and the UK’s AI Regulation Bill are emerging to strengthen data confidentiality measures and control unauthorized data use in AI models.
Solution: Data Minimization and Anonymization

Without strong anonymization measures, sensitive data might leak into the AI model’s training dataset, creating two significant risks:
Legal Compliance Issues: Organizations might fail to meet required privacy protection standards.
Cybersecurity Threats: Hackers can manipulate AI models to reconstruct sensitive training data and commit data theft.
To counter these risks, adopting privacy-preserving techniques is essential for robust AI security. Methods like homomorphic encryption (HE), differential privacy, secure multiparty computation (SMPC), and federated learning are valuable tools. For example, Sony’s privacy toolbox integrates several of these techniques, automatically cleansing datasets of sensitive information and using secure training algorithms. Their approach also evaluates the AI model’s resistance to known threats like model inversion and membership inference attacks (MIA).
Risk: Data Poisoning
Data poisoning attacks aim to manipulate the training data, introducing biases or errors that degrade model performance. Even minor data tampering can cause “concept drift,” where the AI model misclassified objects—like identifying Ford cars as Ferraris. More severe attacks can fully compromise AI security, leading to model dysfunction.
A recent breach demonstrated the scale of this risk when a cybersecurity firm accessed 723 accounts with exposed HuggingFace API tokens from major companies like Meta and Google. This access created a vulnerability, allowing attackers to alter the data directly, paving the way for large-scale data poisoning.
Solution: Data Validation and Ongoing Model Monitoring

The OWASP AI Security and Privacy Guide outlines essential practices to shield AI systems against data poisoning:
Data Quality Checks: Integrate automated checks into data pipelines to ensure incoming data accuracy.
Layered Data Protection: Use encryption, firewalls, and secure transfer protocols to protect training data.
Advanced Model Monitoring: Continuously track model performance for any anomalies or sudden changes in data patterns.
Leading AI teams also use a strategy of training multiple models on varied data subsets, then combining them into a single predictive ensemble. This approach boosts AI security by minimizing the risk of data poisoning, as attackers would need to compromise several models simultaneously to succeed
Robust Model Development

AI models and software systems are both vulnerable to threats, either through flaws in coding or dependencies. Insecure code or unmonitored dependencies can create gaps in your model’s AI security, inviting cyberattacks. Additionally, using open-source libraries or pre-trained models often introduces hidden vulnerabilities that compromise your company’s security.
Risk: Exposed Model Components
The rapid evolution of AI tools, libraries, and frameworks has accelerated model development. Open-source and commercial solutions have democratized access, speeding up AI innovation. Yet, depending on third-party tools significantly raises the risks to AI security.
Researchers have shown how manipulated machine learning models can distribute malware within organizations. Tests using PyTorch have proven this risk, and similar vulnerabilities exist in TensorFlow, scikit-learn, and Keras. When companies pull pre-trained models from public sources like HuggingFace, they may unknowingly expose themselves to AI threats.
Solution: Strengthen Your Development Toolchain
Secure all AI development components—hardware, software, libraries, APIs, and infrastructure—from trusted providers. This reduces the AI security risks from external dependencies. Follow NCSC’s guidelines for improving supply chain security in technology acquisition, especially for AI systems.

Risk: Underperforming AI Models
Building generative AI models is resource-intensive, yet over 80% of these models are abandoned before deployment. Even deployed models often fail to meet expectations due to AI security lapses or inadequate real-world adaptation.
Real-world data often deviates from training datasets, leading to reduced model efficiency. Studies by Sophos revealed that high-performing malware detection models quickly degrade when exposed to real-world conditions. Rushing a model’s release can create technical debt, compromising its security and driving up operating costs.
Solution: Address AI Technical Debt
Weak AI model performance is often due to hasty development decisions that favor immediate gains over long-term AI security. Google’s analysis highlighted several causes of technical debt in machine learning, which can undermine a model’s reliability:
Data Entanglements: Mixing data sources makes it challenging to optimize model components individually.
Hidden Feedback Loops:Misleading data correlations can lead to biased AI model outputs.
Undeclared Consumers: Models feeding untracked systems may generate unforeseen dependencies.
Data Dependency Issues: Unnecessary data packages increase complexity without adding model value.
AI teams must focus on eliminating technical debt to enhance model performance and reduce costs. Establishing robust ModelOps practices—like continuous integration, model versioning, and automated retraining—can significantly strengthen AI security. This approach ensures quicker model releases without compromising on robustness or quality.
Enhanced Model Operations

Deploying AI in production environments presents significant challenges. Real-world usage exposes AI models to evolving threats, making AI security crucial. Attackers often target these models to manipulate outputs or access other systems. Research has even shown how GPT models can be exploited to deliver harmful code into developer environments.
Risk: Data Breach and Leakage
Securing AI models is essential to prevent unauthorized access to user inputs or outputs. Hackers can exploit vulnerabilities to extract sensitive data from model memory. Google Brain’s project revealed that even minor tweaking could expose confidential data, like fake social security numbers.
Data leaks also happen through technical errors. For instance, OpenAI experienced a data breach in March 2023, exposing users’ personal details. Such incidents underline the need for stringent AI security protocols to protect data integrity.
Solution: Implement Comprehensive Data Management
Implement strong data management practices to safeguard against data breaches. Identity and Access Management (IAM) controls are crucial for restricting data access to only authorized personnel. Model version control systems (VCS) help track changes and prevent unauthorized use of sensitive data.
Encrypt data in storage and during transmission to reduce breach risks. Generative AI models should include input validation to block malicious data entries. Companies like JPMorgan have embraced advanced techniques like fully homomorphic encryption (FHE) and privacy-preserving machine learning (PPML) to enhance AI security.
Risk: Adversarial Attacks on Models
Evasion attacks pose another threat to AI security. Hackers use prompt injections or exploit design flaws to manipulate AI behavior. For instance, researchers at Tencent altered Tesla’s autopilot performance with minor visual changes.
Such attacks may also involve phishing attempts targeting Machine Learning-as-a-Service (MLaaS) users to steal AI models. These attacks not only degrade performance but also risk data and intellectual property theft.
Solution: Reinforce AI Security Policies
Effective asset management is key to robust AI security. Maintain an accurate inventory of AI assets and track their usage. Apply strict data management policies, enforcing minimal access principles for sensitive data interactions.
Adopt cryptographic model signing techniques to certify AI models’ integrity for downstream users. This approach strengthens AI security by preventing unauthorized modifications and ensures greater trustworthiness.
Risk: Model Drift
Model drift undermines the predictive accuracy of AI systems over time. Changes in data patterns or evolving tasks can lead to this degradation. For instance, Zillow’s property valuation model significantly miscalculated house values, costing millions in losses.
Model drift can manifest as data drift or concept drift. Data drift occurs when input data distributions change. Concept drift arises when the core task the model addresses shifts. Both scenarios pose severe risks to AI security and decision accuracy.
Solution: Continuous Model Monitoring and Retraining
Deploy automatic drift detection systems to identify early signs of model degradation. Algorithms like the Population Stability Index (PSI) and Kolmogorov-Smirnov (K-S) tests are effective for data drift detection.
Monitor key performance metrics like recall, precision, and F1-score to track concept drift. Continuous oversight helps distinguish natural drift from malicious interference. Automated retraining can enhance model reliability, driving better operational insights and reducing downtime.
Benefits of Leveraging AI Technologies in Security

Advanced-Data Analysis
AI security technologies can swiftly analyze vast volumes of data, processing information that would be impossible for humans to handle in real-time. This rapid analysis enables the identification of subtle patterns and anomalies that might indicate a potential cyber threat.
By turning raw data into actionable intelligence, organizations gain a proactive edge in detecting vulnerabilities before they can be exploited.
Support for Lean Team
For organizations with smaller IT or security teams, AI security serves as a game-changer. It automates repetitive repetitive tasks like threat monitoring, data correction, and vulnerability scanning, reducing the burden on human experts. This allows lean teams to focus on high-priority issues and strategic initiatives rather than getting bogged down by routine tasks. By filling this resource gap, AI enables even smaller organizations to achieve enterprise-level security standards.
Continuous Threat Detection
AI security systems offer round-the-clock vigilance that never tires or loses focus. They continuously monitor the digital landscape, adapting to the latest threat tactics, techniques, and procedures. Unlike traditional security methods, which are prone to gaps and human error, AI provides consistent protection, learning from each incident to enhance its defense mechanisms. This ongoing evolution helps fortify an organization’s security posture against emerging threats, making its defenses stronger over time.
Advanced Threat Detection
AI security tools have the capability to process and analyze enormous data sets in milliseconds. This rapid analysis enables them to detect even the most subtle cyber threats that might go unnoticed by traditional security measures. AI algorithms identify unusual patterns, suspicious behaviors, or hidden anomalies in real-time, ensuring that potential threats are flagged before they can cause damage.
Accelerated Incident Response
The speed at which AI security tools operate is crucial in responding to cyber incidents. By automating the threat detection and investigation processes, AI reduces the time it takes to understand and neutralize cyber threats. This faster response time is critical in preventing breaches from spreading through the network, minimizing both data loss and financial impact.
Boosted Operational Efficiency
AI security not only automates routine tasks like threat monitoring, data analysis, and vulnerability assessments, but it also optimizes the overall cybersecurity operations. By handling repetitive duties, AI allows cybersecurity teams to dedicate their time to more strategic initiatives, like improving defense frameworks and addressing sophisticated attacks. This automation also reduces the likelihood of errors that humans might make when overwhelmed with tasks.
Proactive Cyber Defence
AI security empowers organizations to be one step ahead of cybercriminals. By analyzing historical attack data and threat patterns, AI tools can predict and identify vulnerabilities within the system. This predictive capability enables companies to fortify their defenses before cyber attackers have a chance to exploit them, transforming cybersecurity from a reactive process to a preventive approach.
Enhanced User Experience
AI security enhances protective measures without compromising user experience. For example, AI-powered biometric recognition and behavioral analytics ensure secure authentication while making the login process smooth and hassle-free. This not only strengthens security but also improves the overall experience for end-users by reducing the need for complex passwords or multi-step verification.
Automated Compliance Management
Maintaining regulatory compliance can be challenging, especially with ever-changing data protection laws. AI security tools can automate compliance-related activities, including data audits, risk assessments, and real-time monitoring of regulatory requirements. This automated approach helps organizations stay compliant effortlessly, reducing the risk of non-compliance penalties and saving valuable resources.
Conclusion
AI security depends on the implementation of strong data governance, secure development practices, and stringent protection measures for deployed solutions.
Addressing AI security across data, development, and deployment phases reduces risks from both current and future threats. Apply data security-preserving techniques paired with automated data validation to safeguard inputs and outputs. Ensure your AI development toolkit and system architecture are optimized to avoid technical debt and eliminate potential vulnerabilities.
Strengthen security controls by implementing rigorous access and identity management protocols. Comprehensive monitoring systems should detect any external tampering or natural performance decline in AI models. Our AI and ML app development at TechAhead are ready to guide you on advanced AI security strategies.
Source URL: https://www.techaheadcorp.com/blog/pillars-of-ai-security-protecting-the-future-of-technology/
0 notes
Text
Uphóld Lógin – Most Secure, User-Friendly Crypto Exchange Platform
Uphóld Lógin makes it easy for crypto traders to trade, invest, store, buy and sell digital currencies. The exchange platform supports more than 30 currencies, including eight of the most popular cryptocurrencies, traditional fiat currencies, and commodities. You don’t know what might be missing out if you don’t have an Uphóld Lógin account yet! Generating a new Uphóld Lógin account is no rocket science and takes only a few minutes. Once you create an account, you can have access to a safe digital wallet that you can use to begin your cryptocurrency portfolio right away!
How can I create an account with Uphóld Lógin?
To begin, go to the official Uphóld Lógin website and register.
You'll be prompted to enter your email address, password, and other information on the sign up page.
Locate and touch the Next button after providing the information.
Then, in the preferred fields, enter your first and last names, as well as your residential territory and date of birth.
Create a username for your Uphóld Lógin account here.
You will receive a confirmation email from the company after entering this information.
Check your inbox and compose a new message. Select Get Started from the drop-down menu.
You must now specify your existing cellphone number to receive a severed key over SMS in order to enable 2-FA (to provide additional security to your newly formed account).
That's it; your Uphóld Lógin account is now ready to use the Uphold trading services.
Verification
Go to the official Uphóld Lógin page.
Press the Verify Profile symbol or the “More” button in the bottom right corner of the screen on the homepage.
After that, select Settings to open the Uphóld Lógin profile.
You must now provide your current residential address (make sure it must match with the address mentioned in your Government approved ID).
Confirm your residence territory here.
It will next ask you to upload a government-issued ID, such as a passport or driver's license.
Finally, press the “Done” button to finish the procedure.
How can I change the password for my Uphold account?
To begin, open your device's web browser and type the URL Uphóld Lógin into the search box, then press enter.
Then press the “Further” icon on the home screen for more options.
Select the Security symbol from the drop-down menu.
You must now press the Change Password button.
Then, in the provided box, type in your current login password.
Then, in the preferred boxes, type in the new password twice.
Finally, press the “Done” icon that appears on the screen.
How can I link my credit or debit card to my Uphold account?
To begin, go to the Uphóld Lógin URL.
Then, at the bottom right of the page, tap on the three dots symbols.
Select the Linked Account option from the drop-down menu.
Now, press the Plus sign that appears in the page's tap right corner.
Then select your credit or debit card.
Then you must enter your card information and select the assets you require.
Finally, select the Add Credit/Debit Card option.
How to Use a Credit/Debit Card to Add Crypto to Uphóld Lógin?
To begin, go to your device's official Uphóld Lógin page.
Select the Transact Panel in the lower right corner of your screen.
Then, from the top menu, select your Credit or Debit cards by pressing the “From” symbol.
Now select the card you want to use and enter the amount you want to spend.
Select the crypto or other asset you want to deposit by clicking the on To option.
Then, using the Preview icon, read the information you've entered thus far.
Finally, if everything appears to be in order, select the Confirm Deposit option.
How do I get money out of my Uphóld Lógin account?
Go to the official Uphóld Lógin page first.
Then, in the bottom right of the page, press the Transact panel.
Select the “From” icon and the financing source from the drop-down menu.
Fill in the amount you want to withdraw now.
Select your bank account from the “To” drop-down menu.
Then, using the Preview Withdraw option, go through the information you've provided thus far.
Tap the Confirm icon here.
Finally, enter the six-digit code generated by your authenticator app.
Frequently Asked Questions
How does Uphóld Lógin keep my personal information safe?
Uphóld Lógin uses high security methods to protect your data or personal information from hackers or unwanted access. In the event of an emergency, only registered firm employees have access.
Why can't I get my money out of my Uphóld Lógin account?
There could be a number of reasons for this, including a lack of funds in your linked bank account or other source of funds. And it's possible that your Uphóld Lógin account is depleted of assets, or that you've reached the day's withdrawal limits.
What should I do if I forgot my Uphóld Lógin password?
You'll need to go to the Uphóld Lógin page for this.
Under the password area, press the “Forget Password” option.
Now, enter the email address linked with your account.
Following that, you will receive an email from Uphold with a link.
Check your mailbox, then click the link to create a new password.
1 note
·
View note
Text
Magical Spill Of Technology In Grocery Delivery Software
Have you ever wondered what a magical spill of technology looks like? If not, read this blog to experience the fantasy of a gold man-infused technology. Also, grasp what grocery delivery software upholds and how it can help.

Grocery Delivery Software As A Trendsetter
Are you a grocery business owner? Haven’t you owned your grocery delivery software?
According to statistics, annual revenue as of 2023 is 633.19 billion USD. Also, the estimated annual revenue of 2024 is 770.86 billion USD, and as of 2026, annual revenue is expected to reach an approximation of 1038.21 billion USD.
Hence, get your app customized to enhance the overall success of your business with grocery ordering software. Moreover, it comprises various renovations and technological conveniences to improve customer satisfaction.
The Lens Of A Gold Man
Let's explore the entire process to understand the significance from the lens of a gold man like SpotnEats. This section delves into the concept of a successful grocery business impacting the mutual success of delivery partners. So, let's go, and let’s get it.
Every startup grocery store witnesses a predominant triumph with launch and usage of grocery ordering software. If you still lack information about the benefits availed by store owners and delivery partners, read further and obtain complete information.
Grocery Store Benefits
Primary benefit begins with simple sign-up and log-in with existing credentials. Intense features such as delivery partner panel and consumer panel help with easy order approval. Sustainability in the long run is a main key to embark an app like grocery delivery software. Also, multiple payment options enable consumers to pay for services through the app via user-friendly facilities like e-wallets and digital payments. Finally, store owners can assign nearby delivery partners for timely delivery.
Delivery Partners Benefits
Delivery partners can initiate just by sign-up or login with simple details. Accept or reject orders are done via grocery delivery software. Consumer locations can be navigated using GPS options, which helps in easy navigation. Also, time management is an added advantage to increase the large population of consumers. Lastly, consistency of delivery for service providers is accomplished through grocery ordering software.
Innovative Elements Of Grocery Delivery App
There are various innovative elements of the grocery delivery apps and are listed below:
App can support multiple vendors, allowing store owners to collaborate with local suppliers and expand their product offerings.
Features for route optimization and location tracking help store owners ease the delivery processes and enrich customer satisfaction.
App supports multiple payment gateways, providing flexibility for customers and ensuring secure transactions for store owners.
Store owners can create and manage promotional campaigns directly through the app, attracting more customers and boosting sales.
A built-in feedback mechanism allows customers to rate their experience, helping store owners improve service quality.
Final Flow
Hey budding entrepreneur, congratulations on exploring the blog completely. All the above-given novelties are imbued in the grocery delivery software customized by SpotnEats. We are your everlasting companion for constructing a sustainable app at optimal cost and ease. Contact our cherishing team of developers to proceed with the establishment of a user-friendly app to promote your business.
#grocery delivery app development company#grocery delivery app#grocery delivery software#grocery#grocery delivery
0 notes
Text
Reddy Anna is India’s Most Trusted Online Book Cricket ID Provider
Official website: - https://reddyannaa-id.in/
Follow us at: - https://www.instagram.com/reddyannabook_id/
Contact no: - 7776907778, 92050 01861
Reddy Anna Online Book offers an unparalleled experience for cricket enthusiasts seeking to engage in the thrilling world of online bookmaking. As the premier ID service provider in India, Reddy Anna Club stands out for its commitment to delivering genuine and reliable IDs that cater specifically to avid cricket fans. With easy access through Reddy Anna Login, users can seamlessly navigate this trusted platform, ensuring a safe and secure environment for placing bets on their favorite matches. Reddy Anna's dedication to integrity and customer satisfaction has made it the go-to choice for those looking to immerse themselves in the excitement of sports while enjoying peace of mind knowing they are using India's most trusted service. Whether you're a seasoned bettor or just starting your journey into online cricket betting, Reddy Anna Online Book is here to elevate your experience with unmatched professionalism and authenticity.
With a streamlined Reddy Anna Login process, users can effortlessly navigate through an array of options tailored to enhance their gaming experience while enjoying peace of mind regarding safety and authenticity. The commitment of Reddy Anna Club to uphold transparency and reliability firmly establishes it as the go-to destination for all passionate cricketers seeking an unparalleled combination of excitement and trustworthiness within the dynamic landscape of online sports.

0 notes
Text
Building Trust in the Cloud: Auditing and Reporting for Safe DICOM Viewing
DICOM images contain highly sensitive patient health information. As medical practices shift towards convenient cloud-based DICOM viewers, establishing trust around data transparency and privacy grows increasingly important.
With flexible online DICOM viewer gaining popularity, providers require assurances that sensitive imaging data stays protected when accessed remotely.
Comprehensive activity logging and routine reports enable administrators to monitor DICOM traffic while identifying abnormal usage patterns.
By upholding stringent auditing protocols and real-time visibility, medical teams can securely unlock the convenience of cloud-based workflows without compromising safety.
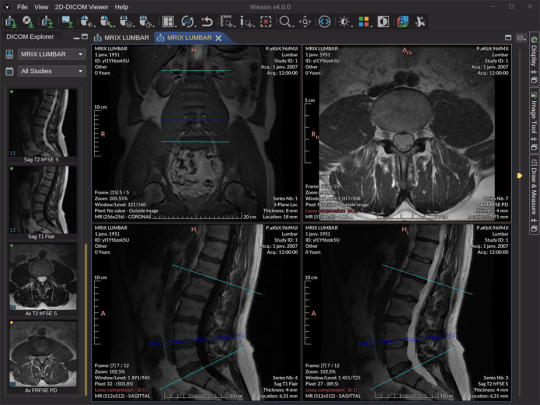
Why Audit Logs and Usage Reports Matter?
Track Access - Logs record viewer sessions, detailing who accessed images and when. This supports HIPAA compliance while discouraging internal data misuse.
Highlight Anomalies - Reports analyzing spikes in traffic or odd access times facilitate early anomaly detection, alerting administrators to suspicious activity.
Maintain Patient Privacy - Detailed audit trails demonstrating properly managed data help providers guarantee patient confidentiality is never broken, even off-site.
Meet Compliance Standards - Routine reports allow providers to easily produce documentation showing adherence to healthcare regulatory policies around patient privacy and information security.
Key Features That Reinforce Trust
Comprehensive Audit Logs
Logged User IDs - All viewer logins are registered to enable user-level tracking.
Timestamps - The data and time of each viewer action gets recorded for precise tracking.

IP Addresses - Systems log source IP addresses alongside session details for location-level visibility.
Granular Tracking - Individual study access, image manipulations, and more get logged to precisely track engagement.
Customizable Usage Reporting
User Breakdowns - Admins can pull reports summarizing activity across individuals, departments, sites, and more for a tailored view of usage.
Trend Analysis - Reports can highlight spikes or dips in traffic week-over-week to pinpoint abnormal patterns early.
Data Exports - Activity records can export to formats like CSV and JSON to enable further processing and oversight.
Scheduled Reports - Administrators can designate routine report deliveries to maintain continual awareness of viewer appropriation.
By centralizing DICOM access logs and distilling those raw records into digestible intelligence, medical teams can monitor cloud viewer adoption safely.
Detailed auditing paired with concise visibility reinforces provider accountability and patient confidentiality in the cloud.
Administrators gain greater awareness over how, when, and by whom data gets utilized while access permissions and protocols discourage internal misuse.
Meanwhile, patients can trust highly sensitive medical images stay protected despite remote viewing flexibility.
Real-Time Alerts Prevent Issues
In addition to retrospective tracking, real-time monitoring capabilities allow systems to automatically flag suspicious activity for intervention. Usage alerts can trigger on:
Unrecognized login attempts
Simultaneous sessions from different locations
Off-hour image access
Excessively high traffic
And more...
By setting custom rules around permissible viewer appropriation, administrators can receive system notifications the moment a potential breach occurs. This prevents unauthorized exposure instead of simply tracking it after the fact.
Maintaining Patient Trust
Medical images provide invaluable diagnostic insight for improved care, but also expose patients' most sensitive health details.
As providers adopt cloud-based DICOM workflows for enhanced convenience and collaboration, maintaining rigorous transparency protocols helps sustain patient trust that privacy stays protected.
By upholding strong accountability with comprehensive auditing and intelligent visibility into usage patterns, care teams can unlock flexible new workflows without introducing added risk.
Detailed activity tracking deters internal misuse while routine reports help consistently meet external compliance demands.
In the end, patients can rely on providers to safely manage sensitive data regardless of how modern systems evolve.
0 notes
Text
How An Employee Self-Service (ESS) Portal Can Enhance Employ Engagement

An employee is a critical contributor to an organization’s success, and thus managers must implement good technology to engage their staff frequently. All workers deserve the best working experience to boost their daily productivity for better profits.
Today, companies should sign up on an Employee Self-service portal (ESS) to answer their worker’s questions and address their other concerns.
Definition of an Employee Self-Service Portal (ESS) 2024
An ESS refers to a new human resource system that workers can use to communicate with their colleagues or supervisors. Additionally, organization’s managers can post useful employee-related information, such as:
Worker’s benefits
Employee’s salaries
Worker’s duties and responsibilities
Monthly allowances
On top of that, this HR system can hold each employee’s history with the company to facilitate salary computation. For example, it might have:
Cleared employee’s allowance
Taken leaves
Pending leave
Real Impact of Implementing an Employee Self-Service Portal in Your Organization
Below are the undebatable benefits of ESS implementation in 2024.
1 – Safeguards The Workers’ Data
A human resource manager must register an employee to access an employee self-service portal. Fortunately, this system relies on secure protocols like HTTPS and SSL, ensuring that employee and company data is safe and secure.
2 – Boosts A Worker’s Productivity
An ESS portal captures an employee’s login and shift duration to enable the human resource (HR) to calculate the correct remunerations. Therefore, all employees can’t afford to be absent, lest their supervisors will catch up with them.
Secondly, employees can access their ESS account, even after their shift ends, to finalize simple tasks. Consequently, companies can achieve their work and profit goals more, especially if they offer bonuses to employees who work extra hours.
3 – Encourages Openness
An ESS upholds transparency because employees can access the full attendance details and salary plus allowances. Therefore, they can notify the human resource team if the information is erroneous or when some details are missing.
4 Fundamental Features You Must Add to Your Company’s Employee Self-service Portal
1 – Add A Functional Search Tool
Employees need this functionality to access quick answers when performing their responsibilities. Therefore, the IT team must include a powerful search bar that can generate helpful suggestions to save time.
As a result, the employees can finish more activities in no time and submit them to their supervisors.
2 – Friendly Template
Secondly, you should choose a well-designed template with direct links to employee categories, company policies, and other sub-categories.
3 – Employee Feedback Section
ESS implementation is incomplete until you add a worker’s feedback template to get honest feedback from the staff members. Further, you must add a direct link to employee feedback in the home section and include a review and a rating section.
Companies need these reviews to develop strategies for incentivizing the staff to avoid losing dedicated and productive employees.
4 – Login System
An HR team must add this feature to prevent unauthorized people from accessing the system. Further, the sign-in system will enable the HR team to track each worker based on when they sign in to their accounts.
Since its inception, NTSPL has been relentless in offering businesses and individuals unique tech services and solutions. Through NTSPL, companies can automate mundane HR functions by improving efficiency and user experience. Some of the delicate features it offers includes payroll processing, leave tracking, and employee personal information. In essence, NTSPL offers a comprehensive approach to administrative concerns by ensuring that businesses and individuals work more efficiently.
Source:NTSPL Blog
0 notes
Text
Florida Cosmetology License Renewal: Basic Guide
In the vibrant and dynamic world of cosmetology, maintaining an up-to-date license is crucial. For professionals in Florida, this means staying on top of your Florida Cosmetology License Renewal. Understanding the renewal process, requirements, and the impact of recent legislation on your career can be daunting. This guide provides comprehensive details to ensure you navigate this process seamlessly.

Understanding Florida Cosmetology License Renewal Requirements
To ensure continued compliance and to keep your skills sharp, the Florida Board of Cosmetology mandates that all licensed cosmetologists renew their licenses every two years. Here's what you need to know:
Important Deadlines
The renewal deadline is October 31st of every even-numbered year. Missing this deadline can result in late fees and possible disciplinary actions.
Navigating the Online Renewal Process
The online renewal process is straightforward, provided you have completed the necessary continuing education hours. Follow these steps:
Login to DBPR Online Services: Visit the Florida Department of Business and Professional Regulation (DBPR) website and log in using your account credentials.
Update Personal Information: Ensure your contact details are current.
Submit Continuing Education: Upload or confirm your completed continuing education hours.
Pay Renewal Fee: Use the secure online payment system to pay the renewal fee.
AIDS HIV Barber Online Renewal FL
For barbers in Florida, particularly those specializing in cosmetology services, staying informed about the latest health regulations is vital. The AIDS HIV Barber Online Renewal FL component is a crucial part of the continuing education requirements.

Importance of HIV/AIDS Education
The mandatory one-hour HIV/AIDS education ensures that barbers are knowledgeable about:
Modes of Transmission: Understanding how HIV/AIDS is spread.
Prevention Methods: Implementing best practices to prevent transmission in the workplace.
Legal Responsibilities: Complying with state and federal health regulations.
Accessing Online Courses
Several accredited providers offer online courses tailored to meet these requirements. Look for courses approved by the Florida Board of Cosmetology to ensure they count towards your renewal.
Key Benefits of Online Renewal
Renewing your cosmetology license online comes with several benefits:
Convenience: Complete the process from the comfort of your home.
Time-Saving: Avoid lengthy paper processes and postal delays.
Immediate Confirmation: Receive instant confirmation of renewal upon payment.
Consequences of Non-Renewal
Failing to renew your cosmetology license can have serious implications, including:
Inability to Practice: You may not legally work as a cosmetologist in Florida.
Penalties: Incurring fines and additional fees for late renewal.
Reputation Damage: Potential damage to your professional reputation and client trust.
Steps to Take if You Miss the Renewal Deadline
If you miss the renewal deadline, take the following steps to reinstate your license:
Contact the Florida Board of Cosmetology: Inquire about the reinstatement process.
Complete Additional Education: You may need to complete extra continuing education hours.
Pay Late Fees: Be prepared to pay any applicable late fees and penalties.
Submit Reinstatement Application: Fill out and submit the reinstatement application along with proof of completed requirements.
Maintaining Professional Standards
Beyond renewing your license, it's essential to uphold high professional standards in your practice. This includes:
Ongoing Education: Continuously updating your skills and knowledge.
Client Safety: Adhering to best practices for hygiene and safety.
Ethical Practices: Ensuring all services are performed ethically and professionally.
Conclusion
Staying compliant with the Florida Cosmetology License Renewal process is critical for maintaining your professional status and ensuring the highest standards of practice. By understanding the requirements, utilizing online resources, and prioritizing continuing education, you can smoothly navigate the renewal process and continue to provide exceptional service to your clients.
1 note
·
View note