#traffic data collection software
Explore tagged Tumblr posts
Link
https://futuresmartsurveys.com/traffic-survey-companies/
https://futuresmartsurveys.com/anpr-camera-system-uae/
traffic count survey report
traffic count survey report uae
traffic count survey report abu dhabi
road traffic monitoring devices
road traffic monitoring devices abu dhabi
road traffic monitoring devices uae
road traffic monitoring devices dubai
road traffic counting surveys
road traffic counting surveys Abu Dhabi
TRAFFIC COUNTING ROAD SURVEYS - AI BASED VEHICLE CLASSIFICATION AND TRAFFIC COUNTING
#traffic data collection abu dhabi#traffic counting surveys#traffic counting software#traffic counting companies in uae#traffic counting companies in abu dhabi#traffic count surveys#traffic counting devices#traffic counting surveys uae#traffic counting solutions in uae#road traffic count surveys#road traffic count surveys in abu dhabi#road traffic count surveys in saudi arabia#road traffic counting#traffic count survey report
0 notes
Text
24.24

Salome took the stairs two at a time, blocking Gusev’s attempts to slip around her in the narrow stairwell. Fending him off was difficult with only one arm; she should have recovered the one she’d lost, but carrying it with her only functional arm wasn’t currently a viable option. There would likely be time to collect it later, once she had collected Frankie.
As Salome reached the upper deck’s landing, Gusev tried to push past her. Salome pivoted on her heel and shoved him, satisfied by the short, indignant cry he gave as he tumbled backwards down the stairs. That would both injure him further and slow him down for another thirty to sixty seconds.
The upper deck was still conspicuously silent of gunfire. Passengers were fleeing through the sleeper car and down the stairs, as far away from the fight in the dining car as they could manage. Salome allowed most of them past, letting the tide of bodies further hinder Gusev’s progress up the stairs and push him farther away from her.
Two stewards were attempting, largely in vain, to contain the panic. One of them stepped out in front of Salome as she passed through the sleeper car, holding his arms akimbo to prevent her from passing.
“There’s a situation in the dining car, miss,” he said. “You can’t go that way.”
“No,” Salome said, simply, and knocked him aside.
She continued to travel against the flow of foot traffic, forcing everyone else to walk around her or be similarly tossed towards the walls. She paused only once, when a face in the crowd pinged her recognition software. Hennig. Salome grabbed him brusquely by the collar of his jacket. He shouted in protest; she ignored him, and dragged him with her through the rest of the sleeper car.
When they reached the door, she stared at it for a long moment. She only had one hand to open it with, but that hand was required to keep a grip on Hennig. He would run if she didn’t. She thrust him towards the door in front of her.
“Open it,” she said.
Hennig did so, then opened the door to the dining car as well. Apparently he had decided it best not to argue with her after being so easily manhandled. Salome tossed him down into a booth that was missing its table, and stood over him.
“Your life is the highest priority of everyone currently in this car,” she said, not particularly caring if he believed her or not. Salome wasn’t sure if she even believed that the Russians were invested in Hennig’s life, but the fact that he hadn’t yet been shot indicated as such. “You will stay here.”
Hennig shut his mouth and stayed.
Ostrovsky was on the ground near the doorway, struggling to stand. He gave Salome a look of disbelief as she stepped away from Hennig, towards him. Salome was unsure what that look was for. She didn’t have enough situational data on Ostrovsky to say. It could equally have been because of her missing arm, because of the bullet holes riddling her clothes, or because Gusev was not currently accompanying her.
Ostrovsky was also disarmed. He’d had a gun, but had lost it somewhere. Salome scanned the dining car, but with the overturned chairs and tables, she couldn’t confirm the location of anything else. Finding the gun would be her next priority. There was no need to consider Ostrovsky a threat for the moment; perhaps he could be used as a bargaining chip against Gusev, but that would be for Frankie to mediate.
“Hey, Sal,” Frankie said, from the other end of the car. She was also getting to her feet, shaking glass out of her robe. Blood was dripping down her face from some unseen head wound; based on the sluggish flow and the glitter of glass in her hair, Frankie had fallen and hit her head when the train had abruptly come to a stop.
“I was just about to kill this clown,” Frankie said. “Unless you wanna do the honors.”
Salome’s feet encountered an obstacle on her way to Ostrovsky, and she looked down. There was a dead body on the ground in a pool of blood. A man. He looked to have been shot in the throat fairly recently; his body was only just going into rigor. Salome scanned his face, and the Hemisphere database unexpectedly returned a 99% match for Julien Dupuis, Canadian assassin.
“Julien Dupuis. Was he trying to kill Hennig?” she asked Frankie. Ostrovsky was incapacitated and Gusev was not here yet–and weaponless, besides. They could afford a moment to debrief.
“Dunno,” Frankie said. “He was dead when I got here.”
“Who killed him?” Salome asked.
“Stewardess. She had a little gun on her.”
“Why did the stewardess have a gun?”
“She’s Hemisphere, I think. Maybe American.” Frankie shrugged. She kicked a large piece of glass across the car, sliding it toward Ostrovsky at Salome’s feet. It stopped a few inches short of his nose.
Salome frowned. This was as equally unexpected as the Canadian assassin, and deeply troubling. None of her predictions had taken into account the probability of American and Canadian agents aboard the train, because the probability was just too small to bother factoring in. And yet, here they both were.
“You worry too much,” Frankie said. “She’s dealt with. Where’s the other Russian? You kill him?”
Salome chose not to reply. She flicked her gaze to Ostrovsky, nonverbally communicating the reason for her silence. She did not want to give Ostrovsky a clear idea of what had happened to his partner–that would afford him hope, which would give him more of a will to fight.
As if proving her point, Ostrovsky tried to crawl forward towards the exit. Salome brought her boot down on his back, applying precisely enough pressure for her weight to keep him in place. He groaned, and decided not to move anymore.
“Where is your gun?” Salome asked him, in Russian.
Ostrovsky’s eyes darted past her, and he bared his teeth in a strained smile. His canine teeth were uncommonly sharp.
“When the train stopped,” he said, slow and labored, “it slid out the door.”
Salome followed Ostrovsky’s eyeline to the doorway behind her. Gusev was standing there with a sniper rifle over his shoulder.
There was a series of deafening bangs, the sound of a rifle firing at a much shorter distance than it was meant to. Salome braced in anticipation of more bullets impacting her exterior chassis, and unexpectedly felt none; it took her a moment to draw the logical conclusion.
“No,” she said aloud, taking her foot off of Gusev.
On the other side of the dining car, Frankie lay in a pool of blood, nearly mirroring Dupuis’s body. She was no longer breathing. Salome knew that before she crossed the car, just as she knew that Ostrovsky had fired the rifle six times and each bullet had struck home in Frankie’s chest. Nonetheless, she had strict protocol to follow; she knelt by Frankie, blood soaking into her robe and staining it a deeper shade of red, and began to perform chest compressions with her single working arm.
Salome had seen corpses before on several occasions, but never the corpse of someone she knew. Though Frankie’s expression was still lively, a half-smirk fixed on her lips, her eyes were glazed and unseeing. It stirred something inside of Salome that she couldn’t name, another unexpected and unpleasant feeling on the stack of such feelings she had encountered today.
Distantly, she was aware that the Russians were moving around the car, making their exit before she could retaliate. She could not make herself prioritize that. She should have been able to. Something was wrong with her.
The Russians were speaking to Hennig now; Salome heard him shout in dismay, but no gunshots or blows followed. She didn’t look away from Frankie. She couldn’t make herself. Blood pooled between her fingers, oozing out from the holes in Frankie’s chest each time she applied pressure.
“Ezio,” she said aloud, though he would not hear this audio log until later, well after he found out his sister had died. “I have encountered another bug that has affected my prioritization. I apologize.”
24.23 || 24.25
3 notes
·
View notes
Text
Cell-site simulators mimic cell towers to intercept communications, indiscriminately collecting sensitive data such as call metadata, location information, and app traffic from all phones within their range. Their use has drawn widespread criticism from privacy advocates and activists, who argue that such technology can be exploited to covertly monitor protestors and suppress dissent.
The DNC convened amid widespread protests over Israel’s assault on Gaza. While credentialed influencers attended exclusive yacht parties and VIP events, thousands of demonstrators faced a heavy law enforcement presence, including officers from the US Capitol Police, Secret Service, Homeland Security Investigations, local sheriff’s offices, and Chicago police.
Concerns over potential surveillance prompted WIRED to conduct a first-of-its-kind wireless survey to investigate whether cell-site simulators were being deployed. Reporters, equipped with two rooted Android phones and Wi-Fi hotspots running detection software, used Rayhunter—a tool developed by the EFF [Electronic Frontier Foundation] to detect data anomalies associated with these devices. WIRED’s reporters monitored signals at protests and event locations across Chicago, collecting extensive data during the political convention.
...According to the EFF’s analysis, on August 18—the day before the convention officially began—a device carried by WIRED reporters en route a hotel housing Democratic delegates from states in the US Midwest abruptly switched to a new tower. That tower asked for the device’s IMSI and then immediately disconnected—a sequence consistent with the operation of a cell-site simulator.
“This is extremely suspicious behavior that normal towers do not exhibit,” Quintin [a senior technologist at the EFF] says. He notes that the EFF typically observed similar patterns only during simulated and controlled attacks. “This is not 100 percent incontrovertible truth, but it’s strong evidence suggesting a cell-site simulator was deployed. We don’t know who was responsible—it could have been the US government, foreign actors, or another entity.”
3 notes
·
View notes
Text
How to identify and track military aircraft in online applications
It is surprisingly easy to track what is flying above you, but there are limits - you will still see only what the military wants you to see.
Fernando Valduga By Fernando Valduga 12/24/2023 - 14:40 in Military
The system, known as ADS-B, allows you to quickly search for what is flying in your vicinity, or even on the other side of the world.
In the past, before the 2000s, people looked at the sky and saw the trail of condensation created by commercial and military jets at high altitudes and wondered what would be the aircraft that passed over our heads, where it was going, where it came from. Today, thanks to a worldwide transponder system, you can track even U.S. military aircraft.
About a decade later, it was already possible to follow commercial aircraft, knowing which airline, flight level, speed and route taken by the flights, being able to accurately follow the arrival of a plane at the airport.
Currently, equipped with a smartphone and with a particular app or website, we can find all this and much more.
Civil aviation authorities around the world began to implement Automatic Transmission of Dependent Surveillance (ADS-B) in the early years. The ADS-B is an aircraft-mounted transponder system that transmits a variety of information in real time, including the location, speed, direction of the aircraft and a unique transponder code for each aircraft. This information, plotted on a map, gives pilots and ground controllers the ability to quickly get a sense of the local airspace (or the airspace of most places on Earth).
Transponder signals can also be captured by cheap terrestrial receivers that amateurs, aviation enthusiasts and others can build for less than $100 using widely available hardware and software, some of which can be obtained on flight tracking sites.
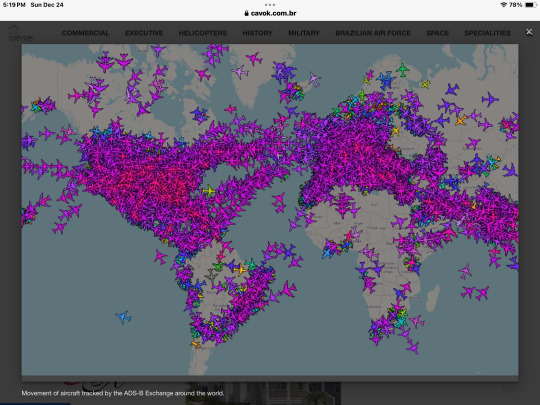
Movement of aircraft tracked by the ADS-B Exchange around the world.
As of 2021, ADS-B transponders are mandatory in the USA, Europe, Australia, Colombia, India, Indonesia, Malaysia, New Zealand, Papua New Guinea, South Africa, Taiwan and Vietnam, and the system is being implemented in China, Canada and Saudi Arabia.
In the United States, almost every type of aircraft - from commercial aircraft and small private aircraft to military fighters, helicopters, bombers, tankers, information-collection aircraft, transport, special operations aircraft, drones and even VIP aircraft carrying the president and members of Congress - are required to transpose into controlled airspace.
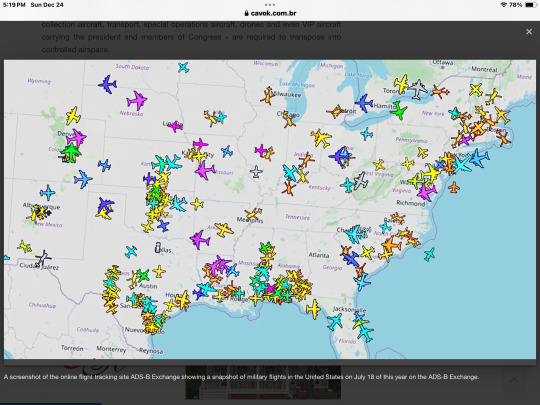
A screenshot of the online flight tracking site ADS-B Exchange showing a snapshot of military flights in the United States on July 18 of this year on the ADS-B Exchange.
The information is not only available to the aviation community. The ADS-B Exchange website gathers aircraft tracking data and makes it available in real time, allowing anyone to track air traffic anywhere the system is working.
Unlike FlightRadar24.com or FlightAware.com - which rely on flight tracking data streams provided by the FAA and other international aviation authorities or obtained from Aireon's global ADS-B air traffic surveillance and tracking network, as well as ground-based ADS-B receivers - ADSBExchange.com relies on thousands of independently owned ground-based ADS-B receivers and multilayer devices, or MLAT.
youtube
MLAT receivers in groups of three or four in a small geographical area use triangulation to track aircraft. In other words, if an aircraft is not using ADS-B for transponder as military aircraft sometimes do, MLAT receivers can still capture their S-Mode transponder signals and establish a position and tracking for an aircraft, as well as altitude and speed data.
The network of receivers of the ADSBExchange.com website includes 10,000 MLAT devices worldwide. As it does not collect flight tracking data from government or commercial sources, it may offer "unfiltered" flight tracking.
ADS-B Exchange merges ADS-B data with other publicly known data on military and civilian aircraft around the world. Individual aircraft are plotted on OpenStreetMap - a free geographical database of the world - represented by color-coded icons according to altitude. The icons range from individual autostos and Cessna 182 to four-engine Boeing 747 and Airbus A380 civil aircraft. Military icons include U-2, KC-135 Stratotankers, C-17 Globemaster III, C-5M Super Galaxy, V-22 Ospreys and so on, although fighters are often represented by a more generic icon model of swept wing and stuffy nose.

A click on the icon includes spatial information, including ground speed, altitude and location, ADS-B signal strength and other data. It also includes the registration of the aircraft, the country of registration and adds a photograph or thumbnail of the aircraft when possible.
All this means that, with the click of a button, you can instantly find out what is flying near you.
Although aircraft tracking has long been a niche hobby among aviation enthusiasts who like to catalog the comings and goings of aircraft, the public availability of transponder data in mid-air also offers journalists, researchers and other observers an effective means of tracking the movements and activities of the planes of the richest and most powerful in the world. The aggregation and analysis of public flight data shed light on the CIA's torture flights, the movements of the Russian oligarchs, and Google's friendly relationship with NASA.
Flights from ISR platforms tracked in the Ukraine region for a period of one month, at the end of last year.
More recently, these tracking techniques have gained international attention after attracting the wrath of Elon Musk, the richest man in the world. After buying social media giant Twitter, Musk banned an account that shared the movements of his private jet.
Despite repeated promises to protect freedom of expression - and a specific promise not to ban the @ElonJet account - on the platform, Musk censored anyone who shared the whereabouts of his plane, claiming that the data obtained entirely legally and totally public was equivalent to "murder coordinates".
A Global Hawk flown remotely with the indicater FORTE12 was the last aircraft tracked over Ukraine before the invasion of Russian forces and the closure of the country's airspace to civilian air traffic, according to the global flight tracking service Flightradar24.
Soon after the Russian invasion of Ukraine, a US Global Hawk, with the indication FORTE12, was followed almost daily by thousands of people on the Flighradar24 platform.
Publicly available flight tracking data is a growing problem for the U.S. military, a senior Pentagon official said recently.
Sites such as ADSBExchange.com, FlightRadar24.com and FlightAware.com aggregate flight data in the United States and abroad using a combination of commercial and citizen-owned sensors that capture the movements of commercial, civil and military aircraft in real time, 24 hours a day.
"The Department of Defense considers open source flight tracking and data aggregation on our aircraft a direct threat to our ability to conduct military air operations around the world," the U.S. Air Force said.

An F-35 fighter was tracked in the Flightradar 24 app earlier this year, during a flight near Phoenix, Arizona.
Aggregated by websites and retransmitted on social media accounts, the data can be a free source of intelligence for nation-states, terrorist groups or individuals, revealing everything from operational movements of aircraft, aviation units and troops to training standards, development test flights and the movements of government officials, experts said.
This image shows a Beechcraft King Air configured for intelligence, surveillance and reconnaissance missions in the military aviation field of Baledogle, Somalia, in 2021. The U.S. civil registration code on the side was not assigned to any specific aircraft at the time and its exact operator remains unknown. However, this is very much in line with the types of aircraft that JSOC allegedly operates clandestinely and that would be interested in hiding the activities through the proposed aircraft flight profile management database tool.
Therefore, military aircraft routinely transmit their ADS-B data, but have the option to turn it off when necessary. The Pentagon is well aware that aviation enthusiasts - and potential opponents - monitor ADS-B data and that aircraft turn off transponders when they do not want anyone to observe them. Often when following the aircraft they simply disappear abruptly from the map.
The U.S. military is also known to use fake hexadecimal codes, which identify a transponder as belonging to a specific aircraft, to help mask certain sensitive flights. For example, the U.S. Air Force VC-25A Air Force One jet that transported President Donald Trump to Afghanistan in 2019 electronically disguised itself for a time as a KC-10 Extender tanker in this way.
As a particularly notable and relevant example of tracking high-profile U.S. military flights, the U.S. Air Force C-40 Clipper aircraft that transported Nancy Pelosi, then a representative of the Democratic Party in California and mayor, to Taiwan last year was visible online, despite concerns that the Chinese military might try to forcibly prevent the flight from reaching the island or harassing it otherwise.
This flight, which used the SPAR19 indicative, was one of the most tracked of all time in terms of total simultaneous users monitoring it on the popular website FlightRadar24, and ended up taking down the app for a period of time.
The Ghostrider trail on the night between November 20 and 21, 2023, on Radarbox.com.
In mid-November, something new happened: a U.S. aircraft involved in combat apparently left its ADS-B on, and did so intentionally. An AC-130J Ghostrider attack aircraft carried out an airstrike against a target that had launched a missile attack against U.S. forces at Al Assad Air Base in Iraq. The AC-130 gunship has a variety of weapons, including 30mm and 105mm cannons, and precisely guided bombs and missiles, and usually flies in lazy circles above its target, pouring firepower on the targets below. In Al Assad's retaliatory air attack, according to The Aviationist website, the Ghostrider involved apparently kept his transponder on all the time, drawing large circles on the ADS-B map and it was possible to be seen on the Radar Box website.
In Brazil, it is possible to track several military aircraft in aircraft tracking applications, including the most widespread Flightradar24. Next, you can see the KC-390, C-130 Hercules transport aircraft or T-27 Tucano coaches in flight near the Air Force Academy. The FAB has hidden data from the presidential aircraft A319 (VC-1) and E190 (VC-2) on these sites.
FAB T-27 Tucano aircraft are often seen flying near Pirassununga, AFA headquarters.
More recently, it was possible to follow the flights of the Brazilian Air Force that went to seek refugees and Brazilian citizens who were and Israel and the Gaza Strip. The KC-30 and KC-390 aircraft could be tracked in real time on the tracking platforms.
If you are a fan of military aircraft or just like to know what is happening when you hear the noise of aircraft engines, ADS-B is a free and reliable tool that you should use to track and identify planes. Observing fighters, spy planes and transport coming and going can help you get to know your armed forces. Just keep in mind that, at least when it comes to military flights, you will only see what the military wants you to see.
BONUS
From Christmas Eve, the flight tracking site Flightradar24 will be keeping an eye on Santa Claus and his reindeer Rudolph, Dasher, Dancer, Prancer, Vixen, Comet, Cupid, Donner and Blitzen as they accelerate around the world.
Initially tracking Santa Claus was a challenge, but thanks to an ADS-B transponder installed a few years ago and the reindeer horns functioning as an additional antenna, Flightradar24 uses a mixture of terrestrial and satellite ADS-B coverage to track Santa Claus during his busiest night of the year.
To follow the good old man, go here.
Tags: Military AviationtrackingTechnology
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
MILITARY
With the V-22 grounded, the Navy's venerable C-2 are coming back into action
23/12/2023 - 21:52
The first A330 MRTT of the Spanish Air Force approaching Getafe. (Photo: Juan Manuel Gibaja / Airliners.net)
MILITARY
The first Airbus A330 MRTT of the Spanish Air Force fly
23/12/2023 - 21:21
MILITARY
B-1 bombers fly in second trilateral exercise with Japan and South Korea
23/12/2023 - 17:14
MILITARY
Switzerland postpones final deliveries of Hermes 900 unmanned aerial vehicles to 2026
23/12/2023 - 16:05
MILITARY
IMAGES: RAF C-17 transports a Merlin helicopter back home
23/12/2023 - 12:08
Russian Air Force Il-18V aircraft that was intercepted by the Polish F-16s. (Photo: Polish Air Force)
INTERCEPTIONS
Polish F-16 jets are fired on a mission in the Baltic to intercept Russian Il-18V
23/12/2023 - 10:54
13 notes
·
View notes
Text
Top 10 Projects for BE Electrical Engineering Students
Embarking on a Bachelor of Engineering (BE) in Electrical Engineering opens up a world of innovation and creativity. One of the best ways to apply theoretical knowledge is through practical projects that not only enhance your skills but also boost your resume. Here are the top 10 projects for BE Electrical Engineering students, designed to challenge you and showcase your talents.
1. Smart Home Automation System
Overview: Develop a system that allows users to control home appliances remotely using a smartphone app or voice commands.
Key Components:
Microcontroller (Arduino or Raspberry Pi)
Wi-Fi or Bluetooth module
Sensors (temperature, motion, light)
Learning Outcome: Understand IoT concepts and the integration of hardware and software.
2. Solar Power Generation System
Overview: Create a solar panel system that converts sunlight into electricity, suitable for powering small devices or homes.
Key Components:
Solar panels
Charge controller
Inverter
Battery storage
Learning Outcome: Gain insights into renewable energy sources and energy conversion.
3. Automated Irrigation System
Overview: Design a system that automates the watering of plants based on soil moisture levels.
Key Components:
Soil moisture sensor
Water pump
Microcontroller
Relay module
Learning Outcome: Learn about sensor integration and automation in agriculture.
4. Electric Vehicle Charging Station
Overview: Build a prototype for an electric vehicle (EV) charging station that monitors and controls charging processes.
Key Components:
Power electronics (rectifier, inverter)
Microcontroller
LCD display
Safety features (fuses, circuit breakers)
Learning Outcome: Explore the fundamentals of electric vehicles and charging technologies.
5. Gesture-Controlled Robot
Overview: Develop a robot that can be controlled using hand gestures via sensors or cameras.
Key Components:
Microcontroller (Arduino)
Motors and wheels
Ultrasonic or infrared sensors
Gesture recognition module
Learning Outcome: Understand robotics, programming, and sensor technologies.
6. Power Factor Correction System
Overview: Create a system that improves the power factor in electrical circuits to enhance efficiency.
Key Components:
Capacitors
Microcontroller
Current and voltage sensors
Relay for switching
Learning Outcome: Learn about power quality and its importance in electrical systems.
7. Wireless Power Transmission
Overview: Experiment with transmitting power wirelessly over short distances.
Key Components:
Resonant inductive coupling setup
Power source
Load (LED, small motor)
Learning Outcome: Explore concepts of electromagnetic fields and energy transfer.
8. Voice-Controlled Home Assistant
Overview: Build a home assistant that can respond to voice commands to control devices or provide information.
Key Components:
Microcontroller (Raspberry Pi preferred)
Voice recognition module
Wi-Fi module
Connected devices (lights, speakers)
Learning Outcome: Gain experience in natural language processing and AI integration.
9. Traffic Light Control System Using Microcontroller
Overview: Design a smart traffic light system that optimizes traffic flow based on real-time data.
Key Components:
Microcontroller (Arduino)
LED lights
Sensors (for vehicle detection)
Timer module
Learning Outcome: Understand traffic management systems and embedded programming.
10. Data Acquisition System
Overview: Develop a system that collects and analyzes data from various sensors (temperature, humidity, etc.).
Key Components:
Microcontroller (Arduino or Raspberry Pi)
Multiple sensors
Data logging software
Display (LCD or web interface)
Learning Outcome: Learn about data collection, processing, and analysis.
Conclusion
Engaging in these projects not only enhances your practical skills but also reinforces your theoretical knowledge. Whether you aim to develop sustainable technologies, innovate in robotics, or contribute to smart cities, these projects can serve as stepping stones in your journey as an electrical engineer. Choose a project that aligns with your interests, and don’t hesitate to seek guidance from your professors and peers. Happy engineering!
4 notes
·
View notes
Text
Biometric Attendance Machine

A biometric attendance machine is a technology used to track and manage employee attendance based on biometric data, such as fingerprints, facial recognition, or iris scans. These systems are often employed in workplaces, educational institutions, and other organizations to ensure accurate and secure tracking of time and attendance. Here’s a comprehensive overview of biometric attendance machines:
Types of Biometric Attendance Machines
Fingerprint Scanners
Description: Use fingerprint recognition to verify identity. Employees place their finger on a sensor, and the system matches the fingerprint against a stored template.
Pros: Quick and reliable; well-suited for high-traffic areas.
Cons: May be less effective with dirty or damaged fingers; requires regular cleaning.
Facial Recognition Systems
Description: Use facial recognition technology to identify individuals based on their facial features. Employees look into a camera, and the system matches their face against a database.
Pros: Contactless and convenient; can be integrated with other security measures.
Cons: May be affected by changes in lighting or facial features; requires good camera quality.
Iris Scanners
Description: Scan the unique patterns in the iris of the eye to identify individuals. Employees look into a device that captures the iris pattern.
Pros: Highly accurate; difficult to spoof.
Cons: Typically more expensive; requires careful alignment.
Voice Recognition Systems
Description: Use voice patterns for identification. Employees speak into a microphone, and the system analyzes their voice.
Pros: Contactless; can be used in various environments.
Cons: Can be affected by background noise or voice changes.
Hand Geometry Systems
Description: Measure the shape and size of the hand and fingers. Employees place their hand on a scanner, which records its dimensions.
Pros: Effective and reliable; less invasive.
Cons: Requires specific hand placement; less common than fingerprint or facial recognition systems.
Key Features
Data Storage and Management
Centralized Database: Stores biometric data and attendance records securely.
Integration: Often integrates with HR and payroll systems to streamline data management.
Accuracy and Speed
High Accuracy: Minimizes errors and false positives/negatives in identification.
Fast Processing: Ensures quick check-in and check-out times for employees.
Security
Data Encryption: Protects biometric data with encryption to prevent unauthorized access.
Anti-Spoofing: Includes features to detect and prevent fraudulent attempts, such as using fake fingerprints or photos.
User Interface
Ease of Use: Features a simple interface for both employees and administrators.
Reporting: Generates detailed reports on attendance, overtime, and absences.
Customization
Settings: Allows customization of attendance policies, work schedules, and shift timings.
Alerts and Notifications: Sends alerts for exceptions or anomalies, such as missed clock-ins or outs.
Benefits
Improved Accuracy: Reduces errors and fraud associated with manual or card-based systems.
Enhanced Security: Ensures that only authorized personnel can access facilities and clock in/out.
Time Efficiency: Speeds up the check-in and check-out process, reducing queues and wait times.
Automated Tracking: Automates attendance management, reducing administrative workload.
Detailed Reporting: Provides comprehensive data on attendance patterns, helping with workforce management and planning.
Considerations
Privacy Concerns: Ensure compliance with privacy laws and regulations regarding biometric data collection and storage.
Cost: Evaluate the initial investment and ongoing maintenance costs. High-end biometric systems may be more expensive.
Integration: Consider how well the system integrates with existing HR and payroll software.
User Acceptance: Provide training to employees and address any concerns about the use of biometric technology.
Popular Brands and Models
ZKTeco: Known for a wide range of biometric solutions, including fingerprint and facial recognition systems.
Hikvision: Offers advanced facial recognition systems with integrated attendance management.
Suprema: Provides high-quality fingerprint and facial recognition devices.
BioTime: Specializes in biometric attendance systems with robust reporting and integration features.
Anviz: Offers various biometric solutions, including fingerprint and facial recognition devices.
By choosing the right biometric attendance machine and properly implementing it, organizations can improve attendance tracking, enhance security, and streamline HR processes.
2 notes
·
View notes
Text
A federal report published today found that Tesla’s Autopilot system was involved in at least 13 fatal crashes in which drivers misused the system in ways the automaker should have foreseen—and done more to prevent. Not only that, but the report called out Tesla as an “industry outlier” because its driver assistance features lacked some of the basic precautions taken by its competitors. Now regulators are questioning whether a Tesla Autopilot update designed to fix these basic design issues and prevent fatal incidents has gone far enough.
These fatal crashes killed 14 people and injured 49, according to data collected and published by the National Highway Traffic Safety Administration, the federal road-safety regulator in the US.
At least half of the 109 “frontal plane” crashes closely examined by government engineers—those in which a Tesla crashed into a vehicle or obstacle directly in its path—involved hazards visible five seconds or more before impact. That’s enough time that an attentive driver should have been able to prevent or at least avoid the worst of the impact, government engineers concluded.
In one such crash, a March 2023 incident in North Carolina, a Model Y traveling at highway speed struck a teenager while he was exiting a school bus. The teen was airlifted to a hospital to treat his serious injuries. The NHTSA concluded that “both the bus and the pedestrian would have been visible to an attentive driver and allowed the driver to avoid or minimize the severity of this crash.”
Government engineers wrote that, throughout their investigation, they “observed a trend of avoidable crashes involving hazards that would have been visible to an attentive driver.”
Tesla, which disbanded its public affairs department in 2021, did not respond to a request for comment.
Damningly, the report called Tesla “an industry outlier” in its approach to automated driving systems. Unlike other automotive companies, the report says, Tesla let Autopilot operate in situations it wasn’t designed to, and failed to pair it with a driver engagement system that required its users to pay attention to the road.
Regulators concluded that even the Autopilot product name was a problem, encouraging drivers to rely on the system rather than collaborate with it. Automotive competitors often use “assist,” “sense,” or “team” language, the report stated, specifically because these systems aren’t designed to fully drive themselves.
Last year, California state regulators accused Tesla of falsely advertising its Autopilot and Full Self-Driving systems, alleging that Tesla misled consumers into believing the cars could drive themselves. In a filing, Tesla said that the state’s failure to object to the Autopilot branding for years constituted an implicit approval of the carmaker’s advertising strategy.
The NHTSA’s investigation also concluded that, compared to competitors’ products, Autopilot was resistant when drivers tried to steer their vehicles themselves—a design, the agency wrote in its summary of an almost two-year investigation into Autopilot, that discourages drivers from participating in the work of driving.
A New Autopilot Probe
These crashes occurred before Tesla recalled and updated its Autopilot software via an over-the-air update earlier this year. But along with closing this investigation, regulators have also opened a fresh probe into whether the Tesla updates, pushed in February, did enough to prevent drivers from misusing Autopilot, from misunderstanding when the feature was actually in use, or from using it in places where it is not designed to operate.
The review comes after a Washington state driver last week said his Tesla Model S was on Autopilot—while he was using his phone—when the vehicle struck and killed a motorcyclist.
The agency will now also look into Tesla’s statements that drivers can opt in to parts of the recall fix, and are easily able to reverse parts of it.
According to Tesla, the post-recall fixes included stricter driver attentiveness requirements while using Autopilot, larger driver-monitoring alerts (“Please pay attention to the road”), and a suspension policy that restricts drivers’ use of the feature if the system finds they are using it improperly.
“Tesla should get serious about driver monitoring, and should limit its use to roads it’s built to work on, for crying out loud,” says Phil Koopman, an engineering professor at Carnegie Mellon University whose research includes self-driving car safety. Without more serious intervention, Koopman says, a cycle of investigations and recalls could continue for years.
Car safety experts with the publication Consumer Reports found in February that Tesla’s recall fixes did not prevent Autopilot misuse.
The new probe comes at a bad time for the electric-auto maker, which is facing its worst sales and revenue growth numbers in years. Tesla also revealed in regulatory filings last fall that it faces an investigation by the US Department of Justice into its Autopilot feature and how it has represented the driving ranges of its battery-powered vehicles.
The timing is also exceedingly awkward for Tesla because it’s pushing even further into autonomy. On an earnings call with investors Tuesday, CEO Elon Musk seemed unperturbed by the company’s recent downturn, focusing instead on Tesla's work in autonomy and its plans to operate a fully autonomous ride-hail service. “Really, we should be thought of as an AI or robotics company,” he said. “If you value Tesla as just like an auto company … fundamentally, it's just the wrong framework.”
Musk has said the company will hold an unveiling event for a purpose-built Tesla robotaxi, called the Cybercab, in August. Just this week, Tesla slashed the price of its more advanced driver assistance feature, called Full Self-Driving, by a third, to $8,000. The company began offering car customers free 30-day trials of FSD last month. Now, its original, flagship automated feature is under new scrutiny.
3 notes
·
View notes
Text
🤖 Artificial Intelligence (AI): What It Is and How It Works
Artificial Intelligence (AI) is transforming the way we live, work, and interact with technology. Let's break down what AI is and how it works. 🌐
What Is AI?
AI refers to the simulation of human intelligence in machines designed to think and learn like humans. These intelligent systems can perform tasks that typically require human intelligence, such as recognizing speech, making decisions, and translating languages.
How AI Works:
Data Collection 📊 AI systems need data to learn and make decisions. This data can come from various sources, including text, images, audio, and video. The more data an AI system has, the better it can learn and perform.
Machine Learning Algorithms 🤖 AI relies on machine learning algorithms to process data and learn from it. These algorithms identify patterns and relationships within the data, allowing the AI system to make predictions or decisions.
Training and Testing 📚 AI models are trained using large datasets to recognize patterns and make accurate predictions. After training, these models are tested with new data to ensure they perform correctly.
Neural Networks 🧠 Neural networks are a key component of AI, modeled after the human brain. They consist of layers of interconnected nodes (neurons) that process information. Deep learning, a subset of machine learning, uses neural networks with many layers (deep neural networks) to analyze complex data.
Natural Language Processing (NLP) 🗣 NLP enables AI to understand and interact with human language. It’s used in applications like chatbots, language translation, and sentiment analysis.
Computer Vision 👀 Computer vision allows AI to interpret and understand visual information from the world, such as recognizing objects in images and videos.
Decision Making and Automation 🧩 AI systems use the insights gained from data analysis to make decisions and automate tasks. This capability is used in various industries, from healthcare to finance, to improve efficiency and accuracy.
Applications of AI:
Healthcare 🏥: AI aids in diagnosing diseases, personalizing treatment plans, and predicting patient outcomes.
Finance 💰: AI enhances fraud detection, automates trading, and improves customer service.
Retail 🛍: AI powers recommendation systems, optimizes inventory management, and personalizes shopping experiences.
Transportation 🚗: AI drives advancements in autonomous vehicles, route optimization, and traffic management.
AI is revolutionizing multiple sectors by enhancing efficiency, accuracy, and decision-making. As AI technology continues to evolve, its impact on our daily lives will only grow, opening up new possibilities and transforming industries.
Stay ahead of the curve with the latest AI insights and trends! 🚀 #ArtificialIntelligence #MachineLearning #Technology #Innovation #AI
3 notes
·
View notes
Text
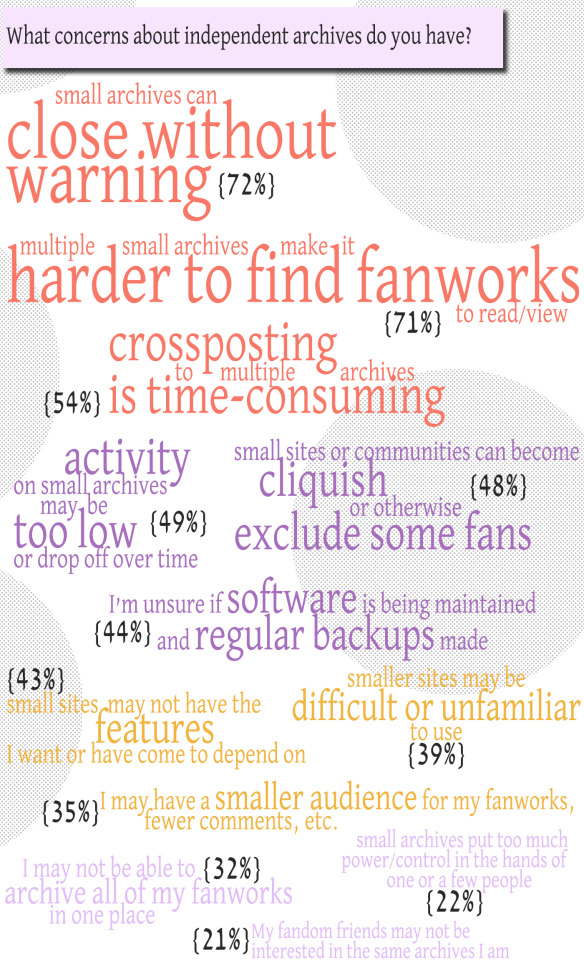
Independent Archive Survey
What concerns about independent archives do you have?
small archives can close without warning: 72% multiple small archives make it harder to find fanworks to read/view: 71% crossposting to multiple archives is time-consuming: 54% activity on small archives may be too low or drop off over time: 49% small sites can become cliquish or otherwise exclude some fans: 48% I'm unsure if software is being maintained and regular backups made: 44% small sites may not have the features I want or have come to depend on: 43% smaller sites may be difficult or unfamiliar to use: 39% I may have a smaller audience for my fanworks, fewer comments, etc.: 35% I may not be able to archive all of my fanworks in one place: 32% small archives put too much power/control in the hands of one or a few people: 22% my fandom friends may not be interested in the same archives I am: 21% I don't have any concerns about small archives: 1% I don't know: 2% Responses in the "other" field:
many of the concerns about the otw apply to smaller archives as well
site design - i haven't seen a single-fandom archive whose design i like as much or find as easy to use (as a reader and author) as ao3. given the choice between reading the same fic on swg and ao3, i'll chose ao3 because it's easier on my eyes
subcat of "too much power" -- smaller archives may go down if the maintainer can no longer fulfill their duties
Fics being used in AI without author consent, changing/unclear guidelines, fanworks being removed without warning (ie. FFN, LJ, at the will of moderators bc they don’t like xyz)
Responses: 82
Analysis
What leaped out at me in these results was the most-chosen concern: that small archives may close without warning. I have come to think of the unannounced archive transfers/closures of archives in the Tolkien fanworks fandom as its "collective trauma" and felt myself rather dramatic for using those particular terms, but this suggests I'm not that far off-base. The whole concept of independent community archives, in my mind, is predicated upon an assumption of caring that exceeds what a large organization (like the OTW) or for-profit site (like FFN or Wattpad) can reasonably be expected to muster. The closure of a small site, without warning and the chance for people to save fanworks, undermines that basic assumption. Future archive owners, take note: What can you do to alleviate this worry that your archive will rip the rug out from under its users? This is definitely an issue I believe we need to address collectively moving forward. What do best practices in this area look like?
Difficulty finding fanworks to read/view is hot on the heels of archive closures, however, as far as concerns. With these data in hand, I'd love to know more about the specifics of this concern. Is this around search features (which were mentioned in another free-response field elsewhere in the survey) not working as well as they should? Is it about having to visit multiple sites, especially when those sites may not have new content every day? What can a small site offer that makes it easier for users to access new fanworks without having to visit daily? (Social media? Newsletters? What else?)
The middle of the pack in the data are mostly concerns around convenience and traffic, the latter of which translates into not just comments but feeling like a site is part of a living community. It's hard to argue with convenience; smaller sites are less convenient than a large site that includes everything or almost everything. Furthermore, the ubiquity of large sites—specifically AO3—makes "different" feel like "inconvenient" when it's actually not. The fact that a small archive doesn't behave exactly like AO3 is not an inconvenience anymore than it is an inconvenience when the produce section is the right in Grocery A and the left in Grocery B, but people will treat it as such because they have become so ingrained to doing and seeing and experiencing things only one way. (This is probably true of the internet and websites more broadly.) As site owners, we have to remain cognizant of how we can offer what AO3 et al cannot—which I would argue is community and consideration for individual users and fandom cultures—and how we can support new creators and visitors as they use something not-AO3.
Finally, the two lowest concerns surprised me. I thought that, in light of what has happened with the OTW this year, "too much power/control in the hands of one or a few people" would rank much higher. Perhaps it is knowing that those in leadership roles are people you know, versus people who feel at best unreachable and at worst are entirely anonymous, that makes the difference, the fandom version of the small-town ideal of being able to trust someone on the basis of a handshake (and the fact that you will have to look each other in the eye during routine community encounters). Perhaps it is an assumption of transparency that comes with that knowing. I'm sure I was not the only person surprised by the breadth and depth of dysfunction at the OTW, but I always had a sense back in the day about which small-site archivists were struggling to keep up with their sites, or which communities were dramamongers, or which moderators played favorites or otherwise acted in ways that were unfair.
The last concern, about using archives that one's friends do not, is an interesting shift because I recall this as a primary reason for some fandoms, including Tolkien, not adopting new platforms in the past (e.g., Dreamwidth and Tumblr), because one's friends weren't there. I wonder the extent to which this lack of concern reflects the lack of community on large sites. Convenience and universality have superseded community and connection as considerations—but that's part of the point, isn't it?
What is the independent archive survey?
The independent archive survey ran from 23 June through 7 July 2023. Eighty-two respondents took the survey during that time. The survey asked about interest in independent archives and included a section for participants interested in building or volunteering for an independent archive. The survey was open to all creators and readers/viewers of fanworks.
What is an independent archive?
The survey defined an independent archive as "a website where creators can share their fanworks. What makes it 'independent' is that it is run by fans but unaffiliated with any for-profit or nonprofit corporations or organizations. Historically, independent archives have grown out of fan communities that create fanworks."
Follow the tag #independent archives for more survey results and ongoing work to restore independent archives to fandoms that want them.
Independent Archives Survey Masterpost
#independent archives#fan studies#fanfiction archives#fandom data#independent archive survey#one more data set to go!
7 notes
·
View notes
Note
Friend once asked me why there's hate for ads when, as they said, "they get the word out about a medicine you might need, an event you might wanna go to or a TV show that you might really get into."
The convo got exhausting from there and I'm not nearly as much as a Radicalized as you are so what would you said to that?
We hate ads because ads are more than just "getting the word out about something you might be interested in". We hate ads at a level that is happening far above what that person is talking about. An event or a new medicine is surface level shit.
We hate ads because we are INUNDATED with advertisements every day, every hour, every MINUTE. Everyone and everything is trying to forcibly fill your brain with needs and wants so you will spend your money on them, to the point that they collect and use heavily aggregated personal data collected from every single conceivable source imaginable so they can target you with hyper-specific ads in the most invasive way possible.
We hate ads because companies are out here spending hundreds of millions of dollars buying up aggregated collected data, mining through it, and creating algorithms tailored to show you more ads. Money they could be spending on paying living wages to their employees, fixing up crumbling infrastructure, paying for childcare or medical services. No, instead they spend it on fucking ADVERTISING.
We hate ads because approximately 50% of ALL the network traffic ON THE ENTIRE INTERNET is just ads being served up. Do you have any idea how much of your monthly data is eaten up just by showing ADS? How much fucking e-waste is produced by these goddamn fuckers? Not to mention the fact that unchecked ads can contain malware injectors that, yes, can run or install software on your computer if your antivirus software isn't up to date and you don't block ads in every way possible.
We hate ads because they're DEEPLY rooted into our every waking moment. We're surrounded by them at all times. We are barraged with constant demands to spend money on every conceivable thing. It's fucking MADDENING.
We don't hate a flyer for an upcoming event posted on a street sign, or a trailer for an upcoming movie preceding the movie you're currently watching. We hate advertising as a concept because it's a fucking cosmic-scale nightmare god creature slowly sucking the life out of humanity that was created by disgusting capitalist scumbags.
12 notes
·
View notes
Link
It’s been another great year at NASA’s Ames Research Center in California’s Silicon Valley. Join us as we review some of the highlights of the science, engineering, and innovation from 2023. Announcing a New Innovation Hub Planned for NASA Research Park at Ames NASA Berkeley Space Center is a proposed new campus of the University of California, Berkeley, and an innovation hub for research and advances in astronautics, aeronautics, quantum computing, climate studies, and more. Planning to join Ames as a tenant of our NASA Research Park in Silicon Valley, the new campus aims to bring together researchers from the private sector, academia, and the government to tackle the complex scientific, technological, and societal issues facing our world. Mapping Water Distribution on the Moon’s South Pole NASA Using data collected by the now-retired Stratospheric Observatory for Infrared Astronomy (SOFIA), researchers shared the first detailed, wide-area map of water distribution on the Moon. Understanding how much water lies beneath the lunar surface, and how it’s distributed, will help guide future missions like VIPER, as well as prospective sites for human habitats. Colliding Moons May Have Formed Saturn’s Rings NASA New research suggests Saturn’s icy moons and rings were formed by a collision a few hundred million years ago, creating debris that gathered into the planet’s dusty, icy rings or clumped together to form moons. NASA and Airlines Partner to Save Fuel and Reduce Delays NASA/James Blair This year, NASA partnered with five major U.S. airlines on an air traffic decision-making tool that saved more than 24,000 pounds of jet fuel in 2022 for flights departing from Dallas-Fort Worth International Airport and Dallas Love Field Airport. Partners include American Airlines, Delta Air Lines, JetBlue Airways, Southwest Airlines and United Airlines. NASA Leaders View Climate Science, Wildfire Innovations at Ames NASA/Dominic Hart NASA’s top leadership, industry experts, and legislative officials visited Ames in April to learn about about the center’s climate science efforts and innovations in aeronautics that will help scientists and engineers better understand climate change and mitigate natural disasters like wildland fires. Starling Takes Flight Blue Canyon Technologies/NASA In July NASA’s Starling mission, managed at Ames, launched four CubeSats into low-Earth orbit to test robotic swarm technologies for space. You can track mission milestones via the Small Satellite Missions blog, and follow the mission live in NASA’s Eyes on the Solar System 3D visualization. NASA’s First Robotic Moon Rover NASA/Robert Markowitz This year engineers began assembling NASA’s first robotic Moon rover, VIPER — short for the Volatiles Investigating Polar Exploration Rover — and the agency is giving the public a front row seat to watch along as the rover takes shape. While individual components, such as the rover’s science instruments, lights, and wheels, were assembled and tested, the VIPER team also completed software development, mission planning, and tricky tests of the rover’s ability to drive off the Astrobotic Griffin lunar lander and onto the lunar surface. Bringing Home Ancient Space Rocks NASA/Keegan Barber NASA’s OSIRIS-REx mission – short for the Origins, Spectral Interpretation, Resource Identification, and Security-Regolith Explorer – returned to Earth in Sept. 2023, bringing with it extraterrestrial rocks and dust that it scooped up from an asteroid estimated to be 4.5 billion years old. Ames contributed to the spacecraft’s heat shield, anti-contamination systems, post-landing sample curation, and more. Preparing to Send Yeast to the Moon’s Surface for Astronaut Health NASA/Dominic Hart NASA’s plans to explore the Moon and eventually go to Mars will bring humans deeper into space for longer duration missions than ever before. These extended missions beyond low Earth orbit pose certain health risks to astronauts. The Lunar Explorer Instrument for Space Biology Applications team is preparing an experiment to study yeast’s biological response to the lunar environment to help understand and mitigate health risks for astronauts. X-59 Team Moves Toward First Flight in 2024 Lockheed Martin/Gary Tice This year, NASA’s X-59 team installed the finishing touches to the aircraft’s tail structure and moved it from its assembly facility to the flight line to perform structural testing. The X-59 quiet supersonic aircraft will take its first flight in 2024. Celebrating a Stellar Year for Webb Telescope Science NASA, ESA, CSA, STScI, and S. Crowe (University of Virginia) The James Webb Space Telescope’s Near-Infrared Camera instrument produced a feast for the eyes with a view into a star-forming region, named Sagittarius C, in the heart of the Milky Way. The image reveals a portion of the dense center of our galaxy in unprecedented detail, including never-before-seen features astronomers have yet to explain. Supercomputer Simulations Lead to Air and Space Innovations NASA Simulations and models developed using technology at the NASA Advanced Supercomputing Facility (NAS) help researchers and engineers develop innovations in air and space. Modeling turbofan engines could lead to designs that reduce engine noise and improve efficiency by understanding where noise is generated inside the machine. S-MODE Sails the Seas and Soars through the Sky NASA/Avery Snyder The Sub-Mesoscale Ocean Dynamics Experiment (S-MODE) logged its final field expedition, and they took a team from the TODAY Show along for the ride. S-MODE combined airborne instruments, research ships, and autonomous ocean gliders to get an unprecedented look at how gas and heat exchange at the ocean’s surface impacts Earth’s climate. From Intern to Astronaut, and Back to Ames NASA/Dominic Hart NASA astronaut Jessica Watkins, who was once an intern at Ames, returned to the Bay Area in Feb. 2023 to visit with local elementary schools and speak with Ames employees. Watkins started her career with NASA at Ames, where she conducted research on Mars soil simulant supporting the Phoenix Mars Lander mission. Second Gentleman Joins East Bay Kids for STEM Activities NASA/Dominic Hart Nearly 100 East Bay kids and their families got to experience the thrill of “launching a rocket” and “making clouds” at a fun-filled STEM event hosted in honor of Women’s History Month at the East Oakland Youth Development Center in Oakland, California, in March 2023. Second Gentleman Douglas Emhoff, NASA Ames Research Center Director Dr. Eugene Tu, and NASA astronaut Dr. Yvonne Cagle joined kids at the Manzanita Community School for hands-on activities and to distribute approximately 500 STEM Artemis Learning Lunchboxes aimed to inspire the Artemis generation to learn about NASA’s Artemis Program. Top Leaders in Our Midst Hailed from the White House and Australia NASA/Dominic Hart In January, U.S. President Joe Biden landed at Moffett Federal Airfield, at Ames, on his way to visit storm-damaged regions in the state. Research conducted at our Silicon Valley center could help predict extreme climate-related weather events. Later in the spring, Vice President Kamala Harris arrived at Moffett before delivering remarks at a local company, and leaders of the Australian Space Agency visited Ames to learn about the center’s missions supporting NASA’s Artemis program, including the VIPER Moon rover, which will launch to the lunar South Pole in late 2024.
2 notes
·
View notes
Text
Are you facing security challenges in Online Survey?

Online surveys can face several security challenges, including:
Data Privacy: Ensuring the confidentiality of respondents' data is crucial. Unauthorized access to personal information collected in surveys can lead to privacy breaches.
Data Integrity: Maintaining the accuracy and consistency of survey data is essential. Malicious actors might attempt to manipulate or corrupt data, impacting the reliability of survey results.
Survey Fraud: Individuals may attempt to manipulate survey results by providing false information or submitting multiple responses (known as ballot stuffing), compromising the survey's integrity.
Phishing Attacks: Fraudulent emails or survey links may be used to trick respondents into providing sensitive information or downloading malware.
DDoS Attacks: Distributed Denial-of-Service attacks can disrupt survey platforms by overwhelming servers with excessive traffic, causing downtime and hindering survey completion.
To address these challenges, survey administrators often implement various security measures:
Encryption: Utilizing encryption techniques to protect data transmission and storage.
Authentication: Requiring user authentication to prevent unauthorized access to surveys and data.
Firewalls and Anti-Malware: Employing security software and firewalls to mitigate the risk of cyber threats.
Captchas and IP Blocking: Implementing measures to prevent automated responses and restrict multiple submissions from the same IP address.
Anonymity and Confidentiality: Ensuring respondents' anonymity and safeguarding their sensitive information.
Regular Security Audits: Conducting periodic security audits to identify vulnerabilities and enhance overall security.
While these measures can mitigate risks, no system is entirely immune to security threats. Survey administrators must stay vigilant, update security protocols regularly, and adhere to best practices to protect the integrity and privacy of survey data.
To know more:
online market research platform
fraud prevention solution
fraud detection and reporting tool
Online Project Management Platform
#market research#onlineresearch#samplemanagement#panelmanagement#datacollection#fraud detection#datainsights
2 notes
·
View notes
Text
SAP's Role in Building Smart Cities for a Brighter Tomorrow
The globe is quickly urbanizing, and cities face the task of effectively managing resources and services while enhancing citizens' quality of life. Smart cities are developing as the solution to these urban difficulties, fueled by technology and data-driven solutions. In this blog, we'll look at how SAP, a global leader in enterprise software, is transforming cities into smart, sustainable, and networked centres of innovation and advancement.
Deciphering Smart Cities
Before we get into SAP's smart solutions for smart cities contributions, we need define what we mean by "smart cities." These cities use digital technology, data analytics, IoT (Internet of Things), AI (Artificial Intelligence), and cloud computing to improve transportation, energy use, waste management, public safety, and other areas of city life. The main objective is to build urban settings that are responsive, adaptive, and environmentally friendly.
SAP's Impact on Smart Cities
SAP's extensive experience in enterprise software and data management positions it as a key player in the smart city revolution. Here's a closer look at how SAP smart solutions for smart cities is shaping the future of cities:
Data Integration: Smart cities generate vast amounts of data from diverse sources, including sensors, mobile apps, and government systems. SAP's data integration and analytics tools empower cities to efficiently collect, process, and analyze this data in real time. Such smart solutions for smart cities insights prove invaluable for informed decision-making on resource allocation, infrastructure maintenance, and service optimization.
IoT Empowerment: IoT forms the bedrock of smart cities, and SAP's IoT solutions facilitate the seamless connection and management of countless devices and sensors. From smart traffic lights to waste bins, this connectivity allows real-time monitoring and control, enhancing everything from traffic management to environmental sustainability.
Predictive Analytics: SAP's predictive analytics tools enable cities to foresee trends and challenges. For instance, predictive maintenance identifies when critical infrastructure, like bridges or water pipes, may need attention before a major issue arises, saving both time and resources.
Citizen Engagement: Smart cities thrive on citizen involvement in decision-making. SAP provides platforms for citizen engagement, such as mobile apps and online portals, where residents can report issues, take part in surveys, and access information on city services and projects.
Energy Efficiency: Energy management is a top priority for smart cities, and SAP's smart solutions for smart cities help cities monitor and optimize energy consumption in public buildings, street lighting, and other municipal facilities. This smart solutions for smart cities reduces costs and environmental impact.
Conclusion
SAP's essential role in smart city development is assisting cities throughout the world in addressing the complex issues of rising urbanization and resource management. Cities are becoming more efficient, sustainable, and responsive to their inhabitants' demands by leveraging SAP's expertise in data management, IoT, and analytics. The influence of SAP smart business on the future of smart cities is poised to grow as technology progresses, providing more livable, connected, and resilient urban settings for future generations.
3 notes
·
View notes
Text





Above are just a few details from Amy Schissel’s massive installation, Silent Cities, for the 2023 Florida Prize in Contemporary Art at Orlando Museum of Art. The monumental work combines traditional cartography with internet mapping to create the dense imagery seen above.
The museum’s information on the artist and her work-
Increasingly, as we go about our twenty-first century lives, we try to bridge the gaps between spaces we see and navigate in both the physical and online worlds. Given augmented reality, every physical, geographical space is interpenetrated with information, so all physical spaces are now also informational spaces. Silent Cities is a melding of notational systems taken from traditional cartography and internet mapping to explore new dimensions of our twenty-first century world. Schissel specifically examines how physical location, set against the ability to be everywhere at once via net-space, presents contradictions of identity in geopolitical relationships: interpretations of personal and collective history are reshaped by the onset of digital information technology, offsetting our sense of civic legibility. While addressing the progressively dematerialized quality of our data-driven culture, the conflation of traditional and cyber mapping systems seeks out new social cartographies and presents fantastical meta-narratives of analog and digital worlds colliding in this large-format world map where boundaries between countries, states, and even continents disappear. Inevitably a hybrid visual language is embodied, emphasizing junctures where physical, factual cartography melds with effervescent, informational traffic, within the time-honored strategies of drawing.
Schissel’s drawing process is twofold. It records physical and imaginary journeys of the contemporary body through the simultaneous spaces of the physical and cyber, marking out “new world” terrain. Here, historical truth and accuracy in traditional cartography meet the ever-fluctuating, boundary-dissolving, architectures of cyberspace from the viewpoint of a female navigator, plotting, measuring, and tracking. Schissel seeks to pinpoint herself within rapidly shifting spatial relationships through a labor-intensive and process-oriented practice; her daily recording of repetitive mark-making becomes embodied and cerebral, drawing out expeditions in a never-ending atlas. Secondarily, she incorporates the use of a large wall-hanging X-Y axis pen plotter compatible with open-source software. After drawing layered cartographies by hand over the entire working surface, she digitally photographs fragments of them, then manipulates the images using bitmap imaging software, finalized as JPEG and DXF vector files. Using an open-source software program (written in Java), she continues to manipulate the files on the X and Y axes using simple coding instructions to generate new images to feed to the large-format pen plotter. While the plotter moves over the work, she also moves the paper around and masks areas to interrupt the machine-assisted interpretation of her initial hand drawings. This creates fine linear webs over portions of the drawing, further adding to the density and amorphous nature of the work. In the end, Schissel works along with the machine, drawing with pen, Sharpie, and graphite.
A been-there graphite smudge on a white flat-land surface becomes an instruction manual for how to build simultaneous worlds encapsulating the contemporary experience of being here, there, and everywhere, reflecting an ever-shifting identity as a physical, female in an ultra-dynamic hyper-world.
#amy schissel#art installation#2023 florida prize in contemporary art#orlando museum of art#sculpture#drawing#cartography#florida art shows#art#art shows#florida artist
2 notes
·
View notes
Text
Types and 5 Most Popular for 2023

Types of IoT
Networking, communication, and connectivity systems depend on the specific IoT application being deployed. Just as there are many different IoT devices, there are many types of IoT applications depending on their use. Here are some of the more common ones:
• IoT client – intended for everyday use. Examples: home appliances, voice assistants and lighting.
• Business IoT – commonly used in the healthcare and travel industries. Examples: smart pacemakers and monitoring systems.
• Military Matters (IoMT) - Commonly used for the application of IoT technology in the military sector. Examples: surveillance robots and attack-capable objects.
• Industrial Internet of Things (IIoT) - commonly used in industrial applications, such as in manufacturing and the energy sector. Ex: Digital control systems, smart agriculture and big data industries.
• IoT Infrastructure – It is widely used for connectivity in smart cities. Example: equipment sensors and control systems.
Why is IoT important? IoT has enabled the physical world to meet the digital world in collaboration. It provides benefits to organizations by allowing them to work and simplify their work. As IoT grows exponentially year on year, businesses are taking advantage of the incredible business benefits it can deliver. Here are some of the most important benefits of IoT:
• Create new business models and revenue streams
• Improve business decisions and insights based on IoT data.
• To increase productivity and efficiency of business operations
• To improve customer experience
Although global IoT spending has been affected by the economic impact of the COVID-19 pandemic, IDC's analysis shows that it will reach a CAGR of 11.3% over the forecast period 2020-2024.
What are IoT devices?
IoT devices are hardware devices, such as sensors, appliances, devices and other machines that collect and exchange data over the Internet. They are designed for certain applications that can be connected to other IoT devices. For example, an IoT device in your car can detect oncoming traffic and send an instant message to the person you're about to see about an upcoming delay.click amazon market place.
How do IoT devices work?
Different IoT devices have different functions, but they all have similarities in terms of how they work. First, IoT devices are physical objects that see what is happening in the physical world. They have integrated processors, network cards, and hardware, and are often connected to Dynamic Host Configuration Protocol servers. It also requires an IP address to work on the network.
Many IoT devices are programmed and controlled through software. For example, an app on your smartphone to control the lights in your home. Some tools are also built into the web server, eliminating the need for external applications. For example, the light turns on immediately when you enter the room.
1 note
·
View note
Text
important to note that having this many plugins makes your traffic very unique since websites are able to receive information about what data your browser is requesting, blocking etc. So if you have a very unique combination of operating system, browser versions and plugins (especially less widespread plugins) it makes your traffic quite unique.
This is called fingerprinting and is in many cases almost as effective at identifying users across different sites as traditional tracking methods such as cookies.
Having a lot of plugins also brings the security risk of having to keep track of the ownership of the software, since it has happened before that new owners of plugins pushed updates which collected and sold user data. So be careful with which plugins you trust, especially when they aren't very popular and little is known about the developers.
In general it's best to just stick to the essentials when it comes to plugins:
- get one popular adblocker
- get the firefox multi-account containers to prevent cross site tracking
- get only a few popular utility plugins, like youtube enhanced or sponsor block
but most importantly: never trust the company that got rid of the moto "don't be evil", because they very much are lol
hello google chrome refugees
don't use any of these browsers, they're also chrome

Here are my favorite firefox plugins for security/anti-tracking/anti-ad that I recommend you get
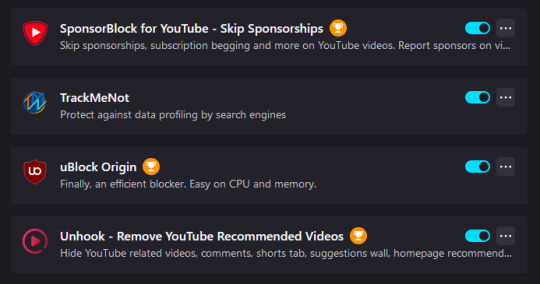
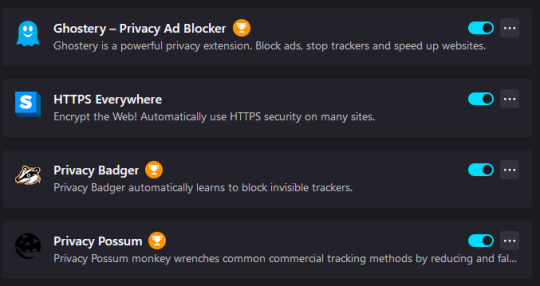
please get off chrome google is currently being investigated for being an Illegal Monopoly so get outta there okay love you bye
155K notes
·
View notes