#the toolset is also super fun to use once you figure it out!!
Explore tagged Tumblr posts
Text
IoT lottery: finding a perfectly secure connected device
http://cyberparse.co.uk/2017/11/27/iot-lottery-finding-a-perfectly-secure-connected-device/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
Black Friday and Cyber Monday are great for shopping.Vendors flood the market with all kinds of goods, including lots of exciting connected devices that promise to make our life easier, happier and more comfortable.Being enthusiastic shoppers just like many other people around the world, at Kaspersky Lab we are, however paranoid enough to look at any Internet of Things (IoT)-device with some concern, even when the price is favorable.All because there is little fun in buying a coffeemaker that would give up your home or corporate Wi-Fi password to an anonymous hacker, or a baby-monitor that could livestream your family moments to someone you most definitely don’t want it livestreamed to. It is no secret that the current state of security of the IoT is far from perfect, and in buying one of those devices you are potentially buying a digital backdoor to your house.So, while preparing for IoT-shopping this year, we asked ourselves: what are our chances of buying a perfectly secure connected device? To find the answer, we conducted a small experiment: we randomly took several different connected devices and reviewed their security set up.It would be an exaggeration to say that we conducted a deep investigation.This exercise was more about what you’d be able to see at first glance if you had a clue about how these things should and shouldn’t work.As a result we found some rather worrying security issues and a few, less serious, but unnecessary ones. We looked at the following devices: a smart battery charger, an app-controlled toy car, an app-controlled smart set of scales, a smart vacuum cleaner, a smart iron, an IP camera, a smart watch, and a smart home hub. Smart Charger The first device we checked was the smart charger that attracted us with its built-in Wi-Fi connectivity. You may ask yourself: who would need a remotely controlled battery charger, especially when you need to manually set the battery to charge? Nevertheless, it exists and it allows you not only to charge the battery, but to manage the way you charge it. Like a boss. The device we tested charges and restores most types of batteries with a nominal voltage from 3 to 12 volts.It has a Wi-Fi module, which allows the device owner to connect remotely to control the charging process, to change the charging settings and to check how much electricity the battery is storing at any time. Once turned on, the device switches by default to ‘access point’ mode.The user should then connect to the device and open the management interface web page.The connection between the charger and the device you use to access the management panel uses the outdated and vulnerable WEP algorithm instead of WPA2. However it is password protected. Having said that, the predefined password is ‘11111’ and it is actually written in the official documentation that comes with the device and is searchable online. However, you can change the password to a more secure one. Having said that, the length of the password is limited, for some reason, to five symbols.Based on the information available here, it would take four minutes to crack such a password.In addition to that the web interface of the device itself has no password protection at all.It is available as is, once it is connected to your home Wi-Fi network. Who would attack a smart charger anyway, you may well ask, and you would probably be right as there are likely few black hat hackers in the world who would want to do that.Especially when it requires the attacker to be within range of the Wi-Fi signal or have access to your Wi-Fi router (which, by the way, is a much bigger problem). On the other hand, the ability to interfere with how the battery is charging, or randomly switching the parameters could be considered as worth a try by a wicked person.The probability of real damage, like setting fire to the battery or just ruining it is heavily dependent on the type of battery, however the attack can be performed just for lulz. Just because they can. To sum up: most likely when using this device, you won’t be in constant danger of a devastating remote cyberattack. However, if your battery eventually catches fire while charging, it could be a sign that you have a hacker in your neighborhood, and you have to change the password for the device. Or it could be the work of a remote hacker, which probably means that your Wi-Fi router needs a firmware update or a password change. Smart App-Controlled Wireless Spy Vehicle While some people are looking for useful IoT features, other seek entertainment and fun.After all, who didn’t dream of their own spying toolset when they were young? Well, a Smart App-Controlled Wireless Spy Vehicle would have seemed a dream come true. This smart device is actually a spy camera on wheels, connected via Wi-Fi and managed via an application.The spy vehicle, sold in toy stores, has Wi-Fi as the only connection interface.For management there are two official applications, for iOS and Android. We assumed that there could be a weakness in the Wi-Fi connections – and we turned out to be right. The device is able to execute the following commands:
Move across the area (with multiple riding modes, it is possible to control speed and direction) View an image from the navigation camera during movement, for ease of navigation View an image from the main camera, which can also be rotated in different directions (there is even a night vision mode) Record photos and videos that are stored in the phone’s memory Play audio remotely via a built-in speaker
Once connected to a phone, it becomes a Wi-Fi access point without password requirements.In other words, any person connected to it can send remote commands to the vehicle – you’d just need to know which commands to send.And if you – being a bit concerned about the lack of password protection in a child’s toy that has spying capabilities – decided to set one up, you’d find there was no opportunity to do so.And if you have basic network sniffing software on your laptop, and decided you’d like to see what the vehicle was currently filming, you’d be able to intercept the traffic between the vehicle and the controlling device. That said, a remote attack is not possible with this device, and an offensive third-party would have to be within the range of the toy’s Wi-Fi signal which should be enabled.But on the other hand, nothing prevents an attacker from listening to your traffic in a passive mode and catching the moment when the device is used.So if you have seen someone with a Wi-Fi antenna near your house recently, chances are they’re curious about your private life, and have the means to look into it. Smart Robo Vacuum Cleaner. With camera Speaking of other devices with cameras that are around you, we spent some time trying to figure out why a smart vacuum cleaner would need to have a web-cam – is it for the macro filming of dust? Or to explore the exciting under-bed world? Joking aside, this function was made specifically for the cleaning enthusiast: if you find it exciting to control the vacuum cleaner manually while checking exactly what it’s doing, this is the gadget for you. Just keep in mind that it is not quite secure. The device is managed via a specific application – you can control the cleaner’s movement, get video live-streaming while it’s cleaning, take pictures, etc.The video will disappear after streaming, while photos are stored in the application. There are two ways to connect to the device via Wi-Fi:
With the cleaner as access point.If you don’t have a Wi-Fi network in your home, the device will provide the connection itself. You simply connect to the cleaner via the mobile application – and off you go! The cleaner can also work as a Wi-Fi adapter, connected to an existing access point.After connecting to the cleaner-as-access-point you can then connect the device to your home Wi-Fi network for better connection and operation radius.
As the device is managed via a mobile phone application, the user should first go through some kind of authorization.Interestingly enough, for this they only need to enter a weak default password – and that’s it.Thus, an attacker just needs to connect to cleaner’s access point, type in the default password to authorize themselves in the application for pairing the mobile phone and the cleaner.After the pairing is completed, they can control the device.Also, after connection to a local network, the robot vacuum cleaner will be visible in the local network and available via a telnet protocol to anyone who is also connected to this network. Yes, the connection is password protected, which can be changed by the owner of the device (but really, who does that?!), and no, there is no brute force protection in place. Also the traffic between the app and the device is encrypted, but the key is hard-coded into the app. We are still examining the device, and the following statement should be taken with a big grain of salt, but potentially a third-party could download the app from Google Play, find the key and use it in a Man-in-the-Middle attack against the protocol. And, of course, like any other Android-app controlled connected device, the robot vacuum cleaner is a subject to attack via rooting malware: upon gaining super user rights, it can access the information coming from the cleaner’s camera and its controls.During the research, we also noticed that the device itself runs on a very old version of Linux OS, which potentially makes it subject to a range of other attacks through unpatched vulnerabilities.This, however, is the subject of ongoing research. Smart Camera IP cameras are the devices targeted most often by IoT-hackers. History shows that, besides the obvious unauthorized surveillance, this kind of device can be used for devastating DDoS-attacks. Not surprisingly, today almost any vendor producing such cameras is in the cross-hairs of hackers. In 2015, our attempt to evaluate the state of security of consumer IoT took a look at baby monitor; this year we’ve focused on a rather different kind of camera: the ones used for outside surveillance – for example the ones you’ve put up in your yard to make sure neighbors don’t steal apples from your trees. Originally, the device and its relatives from the same vendor were insecure due to a lack of vendor attention to the problem.But the issue of camera protection changed dramatically around 2016 after reports of unauthorized access to cameras became publicly known through a number of publications like here or here. Previously, all the cameras sold by this vendor were supplied with a factory default account and default password ‘12345’. Of course, users tended not to change the password.In 2016, the picture changed radically when the vendor became an industry pioneer in security issues, and started to supply cameras in ‘not activated’ mode.Thus, there was no access to the camera before activation.Activation required the creation of a password and some network settings. Moreover, the password was validated in terms of basic complexity requirements (length, variety of characters, numbers and special characters).Activation of the camera could be performed from any PC with access to the camera over the local network. Since this reform, updating the firmware on a camera with a default password leads to the camera demanding a password change and warning the user about security issues every time they connect.The password requirements are quite solid: Additionally, protection from password brute forcing has been implemented: Moreover, the vendor added a new security feature to the firmware in 2016.This involves protection against brute forcing, by automatically blocking access for an IP address after five to seven attempts to enter the wrong password.The lock is automatically removed after 30 minutes.The feature, which is enabled by default, significantly increases the level of security. Nevertheless, not everything is perfect in the camera.For instance, the exchange of data with the cloud is performed via HTTP, with the camera’s serial number as its ID.This obviously makes Man-in-the-Middle attacks more realistic. In addition to a standard WEB interface for such devices, there is a specialized tool for camera configuration, which can search for cameras on the network, display data on the cameras, and perform basic settings including activation, password changes, and the implementation of password resets for network settings. When triggering the device search the PC sends a single Ethernet frame. The camera’s response is not encrypted, and contains model information such as the firmware, date reset and network settings.Since this data is transmitted in a non-encrypted way and the request does not have authorization, this one Ethernet package can detect all cameras on the network and obtain detailed information about them.The algorithm has one more weakness: when forming a response, time delays are not considered.As a consequence, it is easy to organize a DDoS attack in the network, sending such requests to all cameras within the presented Ethernet network . Apart from the described specific protocol, cameras support a standard SSDP protocol for sending notifications, and this allows any software or hardware to automatically detect the cameras.This SSDP data also contains information about the model and serial number of the camera. One more attack vector lies in the remote password reset, which is supported by a technical support service.Anyone with access to the camera’s network can select a camera through the specialized tool for camera configuration and request the reset procedure.As a result, a small file containing the serial number of the camera is created.The file is sent to the technical support service, which then either refuses the request or sends a special code to enter a new password.Interestingly enough, the service doesn’t even try to check whether the user is the owner of the camera – outdoor surveillance assumes that the camera is located out of reach, and it is almost impossible to identify remotely the author of the request.In this scenario, an insider cybercriminal attack is the most probable vector. To sum up: luckily this is not the worst camera we’ve ever seen when it comes to cybersecurity; however, some unnecessary issues are still there to be exploited by an offensive user. Smart Bathroom Scales Remember that picture from the internet, where hacked smart scales threaten to post their owner’s weight online if they don’t pay a ransom? Well, joking aside we’ve proved this may be possible! This is a smart device, interacting with a smartphone app via Bluetooth, but it is also equipped with a Wi-Fi module.This connectivity provides the owner with a number of additional features, from weight monitoring on a private website secured by a password to body analysis and integration with various healthcare apps.Interestingly enough, the only Wi-Fi-enabled feature is the receiving of weather updates. We decided to test the possibility of arbitrary updates\software installation on the specified device in LAN using ARP spoofing and the implementation of Man-in-the-Middle attacks. Here’s what we found. The mobile phone interacts with the main server via HTTPS, in a series of queries.The scales themselves are connected to the mobile phone via Bluetooth.The process of pairing is simple: you request connection via the application, and then turn the scales’ Bluetooth connection on.Given the very limited time for this stage, it is very unlikely that someone will be able to pair the devices without the user’s knowledge. Among other things, the device transmits via Bluetooth various user data – mail, indication of weight, etc.The device receives updates via the application.The latter sends the current version of updates and a number of other parameters to the server – the server, in turn, passes to the application a link to the downloaded file and its checksum. However the updates are provided as is, on the HTTP channel, without encryption, and the updates themselves are also not encrypted.Thus, if you are able to listen to the network to which the device is connected you would be able to spoof the server response or the update itself. This enabled us to, firstly, ‘roll back’ the version of the updates, and then install a modified version that does not match the one retrieved from the server.In this scenario, the further development of attacks is possible, like installing arbitrary software on the device. The good news is that this device has no camera, so even if any other severe vulnerabilities are found, you are safe.Besides that, who would want to spend time on hacking smart scales? Well, the concern is a valid one.First of all, see the picture at the beginning of this text, and secondly: as we already mentioned above, sometimes hackers do things just because they can, because certain things are just fun to crack. Smart Iron Fun to crack – that is something you can definitely say about a smart iron.The very existence of such a device made us very curious.The list of things you could potentially do should a severe vulnerability be found and exploited looked promising. However, the reality turned out to be rather less amusing.Spoiler: based on our research it is impossible to set fire to the house by hacking the iron. However, there are some other rather interesting issues with this device.
The iron has a Bluetooth connection that enables a number of remote management options through a mobile app. We assumed that communication with the server would be insecure, allowing someone to take control of the device and its sensitive data, as manufacturers would not be paying enough attention to the protection of this channel, believing that a smart iron would be of little value to an attacker. Once it is connected to the user’s mobile phone, the iron is managed via the application, which exists in versions for both iOS and Android. The app allows you to:
View the orientation of the iron (whether it is lying flat, standing, or hanging by its cable) Disable (but – sadly – not enable) the iron Activate ‘safe mode’ (in which iron does not react to a mechanical switch on.To turn the iron on when it is in that mode you need to turn off safe mode in the app).
In terms of on/off safety the iron automatically switches off if it is stationary for five seconds in a ‘lying’ position, or for eight minutes in a ‘standing’ position. The iron can also be controlled via the internet.For this, it is necessary to have a gateway near the device, like a separate smartphone or tablet with internet access and a special app. Given all that, we decided to take a closer look at the applications for the device.There are three of them – one for iOS and two for Android.The first Android app is for when you manage the device via Bluetooth and are standing nearby, and the other one is for the gateway, which serves as an online door to your iron when you are not at home.The iOS app is for Bluetooth management.Speaking about the security of all applications, it is worth mentioning that the vendor’s code is not obfuscated at all. When viewing online traffic, we found out that the Android Bluetooth application uses HTTPS, which is a sensible solution.The corresponding app for iOS does not and neither does the gateway app for Android. We decided to test the traffic for the iOS application. Example of phishing attack via the application Once it is enabled, the application offers the user the chance to register, and then sends the data without encryption via HTTP.This gives us a very simple attack vector based on the interception of traffic between the mobile application and the vendor’s server within the local network. As already mentioned, the phone also communicates with the iron using BLE.The BLE traffic is also not encrypted.After deeper investigation of the applications, we were able to control the iron by creating specific commands just from looking into what is transmitted between the devices. So, if you were a hacker, what could you do with all this knowledge? First of all if you would be able to capture the user’s credentials, to pass the authorization stage in an official application and to switch off the iron or set it to ‘safe mode’.It is important to note here that these applications are used for all of the vendor’s smart devices, and there are quite a few.This significantly enlarges the attack surface. No need to worry if you miss the chance to intercept the authentication data.Given that the data exchange between the app and the device is not encrypted, you would be able to intercept a token transmitted from the server to the application and then create your own commands to the iron. As a result, within the local network an attacker can perform:
Identity theft (steal personal email address, username, password) Extortion (take advantage of the ignorance of the user to enable ‘safe mode’ so that the user could not mechanically turn on the iron, and to demand money for disabling ‘safe mode’)
Of course both these vectors are highly unlikely to be extensively performed in the wild, but they are still possible. Just imagine how embarrassing it would be if your private information was compromised, not as a result of an attack by a sophisticated hackers, but because of the poor security of your smart iron. Smart home hub The biggest problem with the vast majority of connected devices currently available is that most of them work with your smartphone as a separate, independent device, and are not integrated into a larger smart ecosystem.The problem is partly solved by so called smart hubs – nodes that unite in one place the data exchange between multiple separate smart devices.Although prior art in finding a secure smart hub, conducted by multiple other researchers, leaves little room for hope, we tried anyway and took a fancy smart hub with a touch screen and the ability to work with different IoT-protocols.It is universally compatible, works with ZigBee и ZWave home automation standards, and very easy to handle: according to the manufacturer, it can be set up within three minutes, using the touchscreen. In addition the hub serves as a wireless Wi-Fi router. Given all the features this multi-purpose device has, being a router, range extender, access point or wireless bridge, we decided to check one of the most common and most dangerous risks related to unauthorized external access to the router.Because, if successful, it would possibly lead to full control of a user’s smart home, including all connected devices. And, no surprise, our research has shown there is such a possibility. To check our assumption we created a local network, by connecting a PC, the device and one more router to each other.All network devices received their IP addresses, and we successfully scanned available ports. Our initial research has shown that, by default, there are two opened ports over WAN.The first one, port 80, is one of the most commonly used and assigned to protocol HTTP.It is the port from which a computer sends and receives web client-based communication and messages from a web server, and which is used to send and receive HTML pages or data.If opened, it means that any user can connect to port 80 and thus have access to the user’s device via the HTTP protocol. The second one, port 22 for contacting SSH (Secure Shell) servers is used for remote control of the device.Attackers can gain access to a device if they obtain or successfully brute force a root password. Usually it’s not an easy task to do. However, in our research we explored another interesting risky thing with the smart hub that makes this much easier. While analyzing the router, we discovered it might have problems with a very common threat risk – weak password generation.In the router system we found ELF (Executable and Linkable Format) file ‘rname’ with a list of names.By looking at this list and the password displayed on the screen, it became clear that device’s password is generated based on the names from this file and, thus, it doesn’t take long for brute force cracking. After a hard reset, the source line for passwords remained, with slightly changed symbols. However, the main password base remained the same, and that still leaves a chance to generate a password. In addition, we found that for device access a root account is constantly used.Thus, offensive users will know the login and a base part of the password, which will significantly facilitate a hacker attack. In case the device has a public IP address and the ports described above are opened, the router can be available for external access from the internet. Or, in other case, if a provider or an ISP (Internet Service Provider) improperly configures the visibility of neighboring hosts of the local network, these devices will be available to the entire local network within the same ISP. In all, we weren’t surprised; just like most any other smart hubs on the market, this one provides a really vast attack surface for an intruder.And this surface covers not only the device itself, but the network it works on.And here are the conclusions which the results of our experiment have brought us to. Conclusions Based on what we’ve seen while doing this exercise, the vendors of many IoT-devices developing their products assume that:
They won’t be attacked due to limited device functionality and a lack of serious consequences in the case of a successful attack. The appropriate level of security for an IoT-device is when there is no easy way to communicate with the wider internet and the attacker needs to have access to the local network the device is connected to.
We have to say that these assumptions are reasonable, but only until the moment when a vulnerable router or multifunctional smart hub, like the one described above, appears in the network to which all other devices are connected.From that moment, all the other devices, no matter how severe or trivial their security issues, are exposed to interference.It is easy to imagine a house, apartment or office populated with all these devices simultaneously, and also easy to imagine what a nightmare it would be if someone tried each of described threat vectors. So in answer to the question we asked ourselves at the beginning of this experiment, we can say that, based on our results at least, it is still hard to find a perfectly secure IoT-device. On the other hand, no matter which device you purchase, most likely it won’t carry really severe security issues, but again, only until you connect them to a vulnerable router or smart hub.
Keeping that and the ongoing high sales holiday season in mind we’d like to share the following advice on how to choose IoT devices:
When choosing what part of your life you’re going to make a little bit smarter, consider the security risks.Think twice if you really need a camera-equipped robo vacuum cleaner or a smart iron, which can potentially spill some of your personal data to an unknown third-party. Before buying an IoT device, search the internet for news of any vulnerability.The Internet of Things is a very hot topic now, and a lot of researchers are doing a great job of finding security issues in products of this kind: from baby monitors to app controlled rifles.It is likely that the device you are going to purchase has already been examined by security researchers and it is possible to find out whether the issues found in the device have been patched. It is not always a great idea to buy the most recent products released on the market.Along with the standard bugs you get in new products, recently-launched devices might contain security issues that haven’t yet been discovered by security researchers.The best choice is to buy products that have already experienced several software updates. To overcome challenges of smart devices’ cybersecurity, Kaspersky Lab has released a beta version of its solution for the ‘smart’ home and the Internet of Things – the Kaspersky IoT Scanner.This free application for the Android platform scans the home Wi-Fi network, informing the user about devices connected to it and their level of security.
When it comes to the vendors of IoT-devices, the advice is simple: collaborate with the security vendors and community when developing new devices and improving old ones. P.S. 1 out of 8 There was one random device in our research, which showed strong enough security for us at least not to be worried about private data leakage or any other devastating consequences.It was a smart watch. Like most other similar devices, these watches require an app to pair them with the smartphone and use.From that moment, most of data exchange between the device and the smartphone, the app and the vendors’ cloud service are reliably encrypted and, without a really deep dive into encryption protocol features or the vendor’s cloud services it is really hard to do anything malicious with the device. For the pairing the owner should use the pin code displayed on the clock for successful authorization.The pin is randomly generated and is not transmitted from the clock.After entering the pin code in the app, the phone and clock create the key for encryption, and all subsequent communication is encrypted.Thus, in the case of BLE traffic interception an attacker will have to decrypt it as well.For this, an attacker will need to intercept traffic at the stage of generating the encryption key. It is apparently impossible to get user data (steps, heart rate etc.) directly from the device.Data synchronization from the clock on the phone is encrypted and, in the same form is sent to the server.Thus, data on the phone is not decrypted, so the encryption algorithm and the key are unknown.
From our perspective this is an example of a really responsible approach to the product, because, by default the vendor of this device could also easily limit their security efforts to assuming that no one will try to hack their watches, as, even if successful, nothing serious happens.This is probably true: it is hard to imagine a hacker who would pursue an opportunity to steal information about how many steps you made or how fast your heart beats at any given moment of the day. Nevertheless, the vendor did their best to eliminate even that small possibility.And this is good, because cybersecurity is not all those boring and costly procedures which you have to implement because some hackers found some errors in your products, we think cybersecurity is an important and valuable feature of an IoT-product, just like its usability, design and list of useful functions. We are sure that as soon as IoT-vendors understand this fact clearly, the whole connected ecosystem will become much more secure than it is now.
4 notes
·
View notes
Text
what’s the most annoying question to ask a nun* in 1967?
tl;dr - In 1967, a very long survey was administered to nearly 140,000 American women in Catholic ministry. I wrote this script, which makes the survey data work-ready and satisfies a very silly initial inquiry: Which survey question did the sisters find most annoying?
* The study participants are never referred to as nuns, so I kind of suspect that not all sisters are nuns, but I couldn't find a definitive answer about this during a brief search. 'Nun' seemed like an efficient shorthand for purposes of an already long title, but if this is wrong please holler at me!
During my first week at Recurse I made a quick game using a new language and a new toolset. Making a game on my own had been a long-running item on my list of arbitrary-but-personally-meaningful goals, so being able to cross it off felt pretty good!
Another such goal I’ve had for a while goes something like this: “Develop the skills to be able to find a compelling data set, ask some questions, and share the results.” As such, I spent last week familiarizing myself with Python 🐍, selecting a fun dataset, prepping it for analysis, and indulging my curiosity.
the process
On recommendation from Robert Schuessler, another Recurser in my batch, I read through the first ten chapters in Python Crash Course and did the data analysis project. This section takes you through comparing time series data using weather reports for two different locations, then through plotting country populations on a world map.
During data analysis study group, Robert suggested that we find a few datasets and write scripts to get them ready to work with as a sample starter-pack for the group. Jeremy Singer-Vines’ collection of esoteric datasets, Data Is Plural, came to mind immediately. I was super excited to finally have an excuse to pour through it and eagerly set about picking a real mixed bag of 6 different data sets.
One of those datasets was The Sister Survey, a huge, one-of-its-kind collection of data on the opinions of American Catholic sisters about religious life. When I read the first question, I was hooked.
“It seems to me that all our concepts of God and His activity are to some degree historically and culturally conditioned, and therefore we must always be open to new ways of approaching Him.”
I decided I wanted to start with this survey and spend enough time with it to answer at least one easy question. A quick skim of the Questions and Responses file showed that of the multiple choice answer options, a recurring one was: “The statement is so annoying to me that I cannot answer.”
I thought this was a pretty funny option, especially given that participants were already tolerant enough to take such an enormous survey! How many questions can one answer before any question is too annoying to answer? 🤔 I decided it’d be fairly simple to find the most annoying question, so I started there.
I discovered pretty quickly that while the survey responses are in a large yet blessedly simple csv, the file with the question and answers key is just a big ole plain text. My solution was to regex through every line in the txt file and build out a survey_key dict that holds the question text and another dict of the set of possible answers for each question. This works pretty well, though I’ve spotted at least one instance where the txt file is inconsistently formatted and therefore breaks answer retrieval.
Next, I ran over each question in the survey, counted how many responses include the phrase “so annoying” and selected the question with the highest count of matching responses.
the most annoying question
Turns out it’s this one! The survey asks participants to indicate whether they agree or disagree with the following statement:
“Christian virginity goes all the way along a road on which marriage stops half way.”
3702 sisters (3%) responded that they found the statement too annoying to answer. The most popular answer was No at 56% of respondents.
I’m not really sure how to interpret this question! So far I have two running theories about the responses:
The survey participants were also confused and boy, being confused is annoying!
The sisters generally weren’t down for claiming superiority over other women on the basis of their marital-sexual status.
Both of these interpretations align suspiciously well with my own opinions on the matter, though, so, ymmv.
9x speed improvement in one lil refactor
The first time I ran a working version of the full script it took around 27 minutes.
I didn’t (still don’t) have the experience to know if this is fast or slow for the size of the dataset, but I did figure that it was worth making at least one attempt to speed up. Half an hour is a long time to wait for a punchline!
As you can see in this commit, I originally had a function called unify that rewrote the answers in the survey from the floats which they'd initially been stored as, to plain text returned from the survey_key. I figured that it made sense to build a dataframe with the complete info, then perform my queries against that dataframe alone.
However, the script was spending over 80% of its time in this function, which I knew from aggressively outputting the script’s progress and timing it. I also knew that I didn’t strictly need to be doing any answer rewriting at all. So, I spent a little while refactoring find_the_most_annoying_question to use a new function, get_answer_text, which returns the descriptive answer text when passed the answer key and its question. This shaved 9 lines (roughly 12%) off my entire script.
Upon running the script post-refactor, I knew right away that this approach was much, much faster - but I still wasn’t prepared when it finished after only 3 minutes! And since I knew between one and two of those minutes were spent downloading the initial csv alone, that meant I’d effectively neutralized the most egregious time hog in the script. 👍
I still don’t know exactly why this is so much more efficient. The best explanation I have right now is “welp, writing data must be much more expensive than comparing it!” Perhaps this Nand2Tetris course I’ll be starting this week will help me better articulate these sorts of things.
flourishes 💚💛💜
Working on a script that takes forever to run foments at least two desires:
to know what the script is doing Right Now
to spruce the place up a bit
I added an otherwise unnecessary index while running over all the questions in the survey so that I could use it to cycle through a small set of characters. Last week I wrote in my mini-RC blog, "Find out wtf modulo is good for." Well, well, well.
Here’s what my script looks like when it’s iterating over each question in the survey:

I justified my vanity with the (true!) fact that it is easier to work in a friendly-feeling environment.
Plus, this was good excuse to play with constructing emojis dynamically. I thought I’d find a rainbow of hearts with sequential unicode ids, but it turns out that ❤️ 💙 and 🖤 all have very different values. ¯\_(ツ)_/¯
the data set
One of the central joys of working with this dataset has been having cause to learn some history that I’d otherwise never be exposed to. Here’s a rundown of some interesting things I learned:
This dataset was only made accessible in October this year. The effort to digitize and publicly release The Sister Survey was spearheaded by Helen Hockx-Yu, Notre Dame’s Program Manager for Digital Product Access and Dissemination, and Charles Lamb, a senior archivist at Notre Dame. After attending one of her forums on digital preservation, Lamb approached Hockx-Yu with a dataset he thought “would generate enormous scholarly interest but was not publicly accessible.”
Previously, the data had been stored on “21 magnetic tapes dating from 1966 to 1990” (Ibid) and an enormous amount of work went into making it usable. This included both transferring the raw data from the tapes, but also deciphering it once it’d been translated into a digital form.
The timing of the original survey in 1967 was not arbitrary: it was a response to the Second Vatican Council (Vatican II). Vatican II was a Big Deal! Half a century later, it remains the most recent Catholic council of its magnitude. For example, before Vatican II, mass was delivered in Latin by a priest who faced away from his congregation and Catholics were forbidden from attending Protestant services or reading from a Protestant Bible. Vatican II decreed that mass should be more participatory and conducted in the vernacular, that women should be allowed into roles as “readers, lectors, and Eucharistic ministers,” and that the Jewish people should be considered as “brothers and sisters under the same God” (Ibid).
The survey’s author, Marie Augusta Neal, SND, dedicated her life of scholarship towards studying the “sources of values and attitudes towards change” (Ibid) among religious figures. A primary criticism of the survey was that Neal’s questions were leading, and in particular, leading respondents towards greater political activation. ✊
As someone with next to zero conception of religious history, working with this dataset was a way to expand my knowledge in a few directons all at once. Pretty pumped to keep developing my working-with-data skills.
2 notes
·
View notes
Photo

New Post has been published on https://magzoso.com/tech/the-flux-beamo-is-a-1500-laser-cutter-with-simple-but-powerful-software/
The Flux beamo is a $1,500 laser cutter with simple but powerful software
Laser cutters are in a fun place right now. Gone are the days when the cheapest machines were tens of thousands of dollars, and when the “compact” models were roughly the size of a freezer. They’ve gotten affordable enough, and small enough, that a DIY home hobbyist can add it to their toolset without taking out a second mortgage or needing much more than some desk space… but they’re still a rare enough machine that saying “I’ve got a laser cutter!” makes people look at you like you’re a friggin’ wizard.
One of the latest entries into this space is beamo, a compact, 30W laser cutter and engraver built by Flux — a Taiwan-based team you might remember for raising $1.6 million on Kickstarter with its Flux Delta 3D printer/scanner/engraver back in 2014.
As with Delta, Flux is turning to Kickstarter for the launch of beamo. They sprinted past their goal of $25,000 pretty quickly, currently sitting at roughly $350,000 raised with a little over a week to go. The early-bird models are going for $849, with the company pinning the final MSRP at $1,500. Shipping/taxes aren’t included in those prices, and can cost a couple hundred bucks, so factor that in to any purchasing decisions.
While I tend to be a bit hesitant when it comes to crowdfunded hardware (having been burned too many times by products that either never arrived or did arrive only to be total garbage), Flux has been down this road before; in addition to Delta, it also crowdfunded and shipped Beambox (a slightly bigger, pricier, but more powerful laser cutter) just a few months back. In the case of beamo, it seems like the Kickstarter is primarily meant to help get the word out, rather than literally “kickstarting” the process. Production is already underway, and units are already rolling off the line.
Flux sent me one of those early units to check out for a few weeks. I haven’t had it long enough to do what I’d call a “review”; with things like laser cutters with their myriad moving parts and… you know, lasers, new issues can pop up months after you open the box, as components wear and maintenance is required. So consider this more of a “first impressions” kind of thing.
My first impressions, though, are good.
For reference, I’d classify myself laser experience as… moderate. More than most people you’d randomly ask, I’d wager, but less than if it were my job. I’ve put a hundred hours or so into training/creating with those aforementioned freezer-sized pro lasers, making everything from custom etched pint glasses, to bespoke Christmas ornaments, to personalized rubber stamps over the years. I tend to look for excuses to shoot lasers at things.
Getting it running
My beamo unit came ready to go right out of the box, mirrors aligned, moving parts all lubed up. I plugged it in, set up some basic ventilation, ran through about 10 minutes of software installation and configuration and started firing away. It all just worked on the first shot.
Speaking of ventilation: you’ll need it. Laser cutting is basically a tiny, super controlled fire… and that means smoke. Depending on what you’re cutting, that smoke can be super noxious. Cutting wood? It won’t smell too bad, but it’s still not something you want in your lungs on the regular. Etching a logo into felt? It’ll smell like you’re burning a trash can full of hair. Beamo uses a 200CFM exhaust fan to pull smoky air out of the machine, dumping it out through a 4″ exhaust hose that you’ll need to run through a window (or, if you’re feeling extra fancy, a dryer exhaust-style vent through a wall.) Expect to need about 8″ of clearance between the machine and any wall behind it for the exhaust hose and its bends, unless the path to the window is a straight shot.
The exhaust system is decent, but you’ll probably need to fiddle with how the hose runs to get it just right. If you’re venting through a window, you’ll want to figure out a way of sealing up the open gaps around the hose to limit any fumes that might float back into the room. Put time into getting it right. If the room still smells smokey hours after you’ve cut, you’ll want to keep working on your ventilation. You don’t want to breath that stuff in, especially if you’re running the laser more than occasionally.
Beamo’s built-in touchscreen. You’ll mostly control it over Wi-Fi, but you can access some basic functionality and monitor job progress here.
If you’re new to laser cutting, you should also put the time into learning what you shouldn’t put in these machines. Some materials are safe to laser cut, but tend to catch on fire easily. Some materials will just melt and screw up your machine. Other things (PVC!) will straight up emit chlorine gas when you hit them with a laser. If you’re moving beyond the basics of cutting thin wood/acrylic/cardboard or engraving glass, research it.
So what SHOULD you cut? Woods are a good go-to (though you’ll want to limit it to less oily stuff — because, again, fire). Cardboard is fun to cut for things like spray paint stencils. Leather is good, with practice, and you can do all sorts of really neat stuff with acrylic. You can’t cut glass, but you can engrave it; same goes for rubber, though that’s one you’ll want to source from a place that sells materials known to be laser safe.
The thickness of the material you can cut tends to be limited by a laser’s wattage, while height/width is generally limited by the size of the work area. At 30W, beamo’s laser can slice its way through wood about 1/8″ thick; its work area, meanwhile, comes in at 11.81″ x 8.27″. You can make a lot of cool stuff within those bounds, but be aware of them — buying a bunch of material only to get it home and realize you’re a few watts short of a complete cut is a bummer. If you foresee needing deeper cuts or bigger pieces, beefier lasers exist without too massive a leap in price. As examples: Flux’s other laser cutter, the $2,500 Beambox, bumps the laser up to 40W and the work area up to 15.7″ x 14.7″; the $2,500 base model from competitor Glowforge comes in at 40W with a work area of roughly 11″ x 19.5″.
(One potential advantage of beamo over the company’s previously released Beambox: whereas Beambox requires you to regularly fill up a water cooling reservoir to keep it running, beamo’s water cooling is closed-loop, so the same water just keeps circulating. I’m interested to see how this holds up over time.)
Fire the lasers!
Got everything plugged in, ventilation set up and your materials purchased? Time to cut! Well, almost.
You’ll mostly be controlling beamo through Beam Studio, a free piece of software provided by Flux for Windows, macOS and Ubuntu. As far as laser cutting software goes, I’m really quite pleased with it so far.
Beam Studio is super straightforward, but darn powerful for a free companion app. If you’re looking to cut out basic shapes, etch text or lay down some bezier curves, it can do it. Want to etch a picture of your dog into some wood to make a keychain? Just drop an image onto the work area, scale as desired, then move a slider to tweak the black/white threshold until it looks right. You can work in layers, setting up a raster layer to be etched and then a vector layer to cut it out immediately after.
Beamo has a built-in camera system, allowing you to quickly scan the work bed before dragging and dropping your designs wherever you want them. The first time you connect to beamo, you’ll be asked to calibrate the camera — a process that was considerably simpler than I expected. Put a piece of paper on the work bed, and beamo will fire a quick test pattern into it. Beam Studio will then snap a picture of what it just etched, projecting an overlay of where it thinks the test pattern is versus its scan. Nudge the overlay around until everything is perfectly stacked, and you’re set. You’ll want to re-run this alignment process every once in a while (it’s quick) if you need precise placement.
The camera system here really is incredibly useful. After about 30 minutes with beamo, I was doing things that are at best annoying on camera-less cutters — things like etching a design, cutting it out, then immediately flipping the cut piece and etching on the other side without worrying about precarious placement. I just rescanned the work bed, dragged the image where I wanted it on the freshly cut side B, and fired away.
The camera is quick, but not instant. Scanning the entire work area takes about 60 seconds. If you only need a certain area scanned (like, say, the top half of the work area, or the rough area around something you’ve already cut), fortunately, that’s an option. Just drag the scanning boundary box accordingly.
If you need to do something beyond what the free software can handle (or if you just prefer working in apps like CorelDraw or Illustrator), Beam Studio can import JPGs, PNGs and SVGs.
While more capable than I expected, the software isn’t without its quirks. Beam Studio will try to keep you updated with a progress ticker, but don’t rely on it too much for predicting timing. I’ve had projects shoot up to 40% in the first 30 seconds, only to take five minutes for the rest to complete. There was an occasion or two where the software threw out an error in Mandarin that I didn’t want to dismiss without a quick pass through Google Translate… but for the most part, it was solid, stable and fun to use.
In its base configuration, beamo’s laser is manually focused, meaning you’ll need to focus things by hand each time you place new material inside the machine. Fortunately, focusing it is super straightforward: put material in, rotate a piece of acrylic attached to the laser head, lower the laser head until the acrylic is just barely touching the material, then lock the laser head back in place and lift the acrylic out of the way.
Flux says that it’ll ship a $250 add-on module that introduces autofocus to the mix, but I didn’t get to test that. They’re also working on a $499 rotary add-on that will let you etch designs onto cylindrical items (think shot/pint glasses), but out of the box, it’s flat stuff only.
As with every single laser I’ve ever worked with, working with a new material — or even, sometimes, the same material from a different source — requires some fiddling. You’ll be tweaking the speed at which the laser moves, the power of the laser and how many passes it makes over the same path; you want to keep the power low enough to minimize scorching and maximize the life of the laser, while making sure you’ve done enough repeat passes to cut completely through. Beam Studio comes with a bunch of presets for different materials that can get you pretty close (and you can save your own favorites, once you’ve found them), but expect to experiment a little when you’re working with a new material for the first time. Buy extra material.
As for noise: operating with fans running full force, it’s not what I’d call “quiet,” but it’s not so loud that it’s uncomfortable to sit next to. The company’s specs pin it at around 65 db — louder than your average conversation, but a bit quieter than, say, a vacuum. The fans do whir endlessly when the machine is idling, so you’ll probably want to cut the power between cutting sessions.
If for some reason you need to open the lid while the laser is operating, beamo’s built-in automatic kill switch will cut power to the laser to protect your eyes. Close the lid again and the job can be resumed right from where you left off. While the company says that the acrylic lid provides sufficient eye protection for beamo’s 30W Class 1 laser (though they note that you shouldn’t stare right at the laser beam, lid or not), I absolutely recommend picking up and wearing a pair of CO2 laser safety goggles, especially when it comes time to pop the machine open and do any maintenance. Speaking of…
Foreseeable maintenance
Maintenance is an inevitable part of owning a laser cutter. As noted, I’ve only had the laser set up for a few weeks and everything came well configured, so I haven’t had to go digging under the hood yet. If something suddenly breaks on me during my time with the cutter, I’ll update this post accordingly. But either way, maintenance will be part of the process for owners.
Even if nothing breaks unexpectedly, some of the parts involved are “consumable” and thus expected to wear down with use. The lens, mirror and laser tube, for example, are expected to last about a year with regular use, according to the company’s estimates. The team says those parts should cost about $19, $9 and $139 to replace, respectively, and you’ll be able to buy them through their online store. Plan ahead for those recurring costs, and make sure you’re comfortable with the idea of eventually tearing the machine apart before you dive in.
You’ll also need to keep things clean to keep them operating well. Burning stuff dirties the optics, and dirty optics lead to weaker cuts and faster wear. You’ll want to pop the work bed out regularly to get rid of any debris, and keep all the moving bits lubed. There’s more to keeping a laser cutter working well than say, an inkjet printer.
Overall, though, so far so good. The machine looks pretty great on a table; it’s not quite as shiny and Apple-y as a Glowforge, but it should blend into a home office or studio pretty easily. It’s light enough to be easily moved by two people, and took me all of a few minutes to get up and running. If you don’t mind the occasional software hiccup, can figure out sufficient ventilation, are mostly working on projects that fit within beamo’s wattage/work area capabilities and are down to get under the hood for maintenance, beamo seems like a solid machine so far.
0 notes
Text
@songbased and now Kiele :D
What is your character’s favorite type of food, or specific dishes that they love? Is there a reason behind their fondness?
She really likes fresh fruits! Also, it’s cliche but she does really like spicy food. They don’t have a lot of hot spices where she’s from, so it’s kind of a fun novelty for her, plus it’s a point of pride and a bit of a power move to eat something ungodly fucking hot and not be bothered by it, lol
Does your character favor a certain color? Are many of their clothes this color?
Everything she owns is red or gold. Gotta work that Aesthetic
What is your character’s favorite instrument? Can they play it, or do they just enjoy listening?
She’s really into drums! She loves to dance so she can’t resist a good beat.
What is your character’s favored weapon?
Whips. She dances with flaming whips for attention money, but they’re also fun for... other applications
How does your character deal with having something on their mind? Do they show it, or get quiet? Do they talk about it? Are there any coping mechanisms they have that others may notice?
She doesn’t really know how to have or express feelings like a functional adult, so she tends to convert any and all negative emotion into Anger, if she can help it. If the thing on her mind isn’t something she can really get angry about, she’ll tend to get pissy and lash out in general.
If your character is angry or aggravated with another character / party member, how do they deal with it?
Say so, immediately. She’s not shy about confrontation, to say the least.
What are your character’s pet peeves?
‘Kaylee’ ‘Keelie’ ‘Kelly’
How long does it take for your character to confront or deal with something that is on their mind / a problem? If contingent on the type of problem, what are they more capable of handling?
She’ll usually confront problems head on and as soon as possible. She doesn’t like being weighed down with Issues and Baggage and prefers a direct approach to getting rid of problems. However, if the problem is something like ‘a loved one died and I’m having a hard time’ that can’t really be Fixed, she has a really hard time dealing with things like that.
Is your character affectionate? Whom does your character choose to share affection with?
This is interesting because on the one hand, she’s super affectionate with most people she meets, whether it’s platonic or flirty, but she’s also emotionally A Disaster so it’s hard to say how much of it comes from a place of genuine affection
If a fellow party member has a problem or concern, how (if at all) does your character deal with it? Do they try to help? Would it depend on the party member?
It would depend on the party member. If she didn’t care about them, she’d tend towards a ‘that sounds like a You Problem’ attitude. She’s cool with the current party right now, though, so if it was something she wanted to help with, her approach is, again, whatever is the most direct, confrontational, and/or active-- ‘How do I Fix This?’ ‘Who do I kill?’
What are some habits that your character has? Do they have a morning or night time ritual?
She’s not much of a habit-former, for the most part. She’d rather be flexible and unpredictable.
Does your character have any unusual sleeping habits? How much do they sleep, where are they most comfortable? Do they snore? When given the option, are they an early or late riser?
She’s somewhat of a heavy sleeper, and can get herself comfortable almost anywhere. If she’s sleeping with somebody else, she’s a pretty heavy-duty cuddler and tenacious big spoon. She only snores sometimes/ a little, she mostly sleeps pretty quiet. She tends toward late nights and early mornings, apparently a high enough energy person to recharge quickly without needing too much sleep.
How does your character behave when they are tired or exhausted?
Super grumpy, more inclined to accidentally set things on fire from not paying attention to what she’s doing
Does your character have any quirks that others might notice? Speech patterns, or things that they tend to do?
Her body heat tends to noticeably rise when she’s angry or otherwise excited. She doesn’t wear shoes, I dunno if that counts as a quirk?
How does your character’s constitution translate to their every day life? Do they tend to be prone to sniffles or are they generally sturdy? How quickly do they come back from major injury?
She’s fairly sturdy. She doesn’t get sick often, and tends to bounce back from injuries pretty well-- partly out of decent Con but also, I’ll admit, largely out of sheer stubbornness and force of will. She refuses to be viewed as weak.
How does your character deal with being less than 100%?
Complain, a lot, unless it’s really serious in which case she’d play it off, again in a stubborn refusal to show any genuine weakness
How does your character deal with temperature? Do they run hot or cold?
I mean. Fire genasi. She runs hot. Also, I’ve rethought my thoughts on the, like, physics of this I guess-- I think in colder weather she’d be super uncomfortable, and would be bothered by the cold a lot faster than people who aren’t from volcanic tropical regions and also part literal fire person
Does your character have a preference between indoors or outdoors? Where do they seem more or less comfortable?
Outdoors. She likes to be under the sun, and to be able to see the stars. Also, people tend to frown on things indoors being on fire, which is a thing that... tends to happen when she’s around, so
Does your character have various outfits for different situations, or do they tend to wear just one? Do they have any interchangeable pieces, or any odd clothing habits/quirks?
She’s got a handful of outfits but they’re mostly really similar-- just for visual variety more than different situations. She does also have an extremely fancy red silk dress that she’s going to wear a lot just because if anyone can be overdressed and make it work it’s her. She wears a lot of jewelry, mostly gold and colorful glass. The more of her body she can get away with baring, the better.
How does your character feel about their belongings? What condition are their belongings in? Do they have more belongings, or the bare minimum? Are they possessive or protective of their things?
She’s not super materialistic. She’s had a violent, unpredictable temper since she was born, so even though she’s somewhat grown out of throwing/ kicking/ incinerating things in a fit of pique, she’s pretty much used to not getting too attached to Things.
What are your character’s hobbies? What do they do during their off-time? Do they have anything that aids them in these hobbies or skills?
Dancing and lampworking! Dancing is big in her culture and just something she grew up with, and she had a natural talent. By contrast, she was set up as an apprentice to a glassblower as a kid literally just to try to get her to focus her energy into something constructive for once, something that relied on delicacy and patience, and she hated it for a really long time. But now that she’s good at it it’s a source of pride, and she does try to use it as a relaxation method, although she still tends to smash things that don’t turn out perfect... She does lampworking A) because making beads and animal figures was less boring than like... bowls and vases, and B) because a smaller toolset and workspace is a lot more portable. Being able to create and control flames herself with a lot of precision is an A+ bonus to this hobby as well.
What does your character bring to the party? Are they a skilled fighter? Are they good with intelligent pursuits or charismatic encounters?
Damage output. Oh man does she set things on fire so so good. She’s also pretty good for charismatic endeavors, but usually the bard takes initiative in those situations so it’s not necessarily just her thing.
How do they help set up camp?
Build, light, and manage the fire; set up a sleeping area but only for herself
What are some other ways your party is obviously benefited by your character’s presence?
I don’t know if there have been any really obvious story benefits yet...?
What is your character’s relationship with money? What are their spending habits? How would your party perceive their relationship with money / accepting pay from others?
Like I said, she’s not super materialistic, so she’s a little indifferent about money. It’s never been a problem for her to be able to get money when she needs it, either by performing or selling glassworks or just flirting her way into free dinner and drinks (and lodging, usually). That said, if she’s been promised gold, she’s gonna get it. She spends money mostly just on whatever she needs at the moment, but will also buy stuff on a whim because she decides in the moment she wants it
What is your character’s overall disposition when surrounded only by the party? Are they different around just one or two party members? If so, are these specific members, or rather that your character is more comfortable opening up around fewer people?
It’s way too early yet for her to have a different, separate comfort level within the party as opposed to with outside people tbh. She’s not one to Open Up about her Feelings so I guess we’ll see what the future holds in that regard
Does your character walk at a faster or slower pace? Does it depend on the setting or situation?
She saunters, but in general she’ll keep pace with whoever she’s walking with.
How does your character pass travel time?
Chit chat with whoever she’s with, usually. She tends to get bored traveling by herself and will try to find another traveler or caravan going the same direction to pair up with.
Is there anything else that your party members might notice about your character?
She still gets pissy whenever Ametys comes up-- something about that encounter really pushed her buttons, it seems. When she’s casting a spell (or channeling Wild Magic), not only do her hands glow like embers-- so does the burn scar on her chest. She tends toward snap judgements and extremes-- she likes you or she hates you, immediately, and she doesn’t easily change her mind. By now she’s flirted with everyone in the party except for Silas and Whisper.
2 notes
·
View notes
Text
My Photography Journey + Boho Chic Desert Photos from Dutch Photographer Anouschka Rokebrand
Many have asked me how I got started in photography so I want to answer in detail now since I usually don’t go into depth about it, or what my major block was in the beginning that I bet some of you will totally relate to. But first, because this fits my story perfectly, I want to share the online gallery of Dutch photographer Anoushka Rokebrand, who relocated a few years ago from her native Holland to the American southwest. She just launched this yesterday, so it’s brand new and I wanted you to know about it first since Boho is a big trend in interiors at the moment and her photos really work great to fit that trend.
Anoushka is a fantastic photographer, I’ve admired her work ever since she came to Hannover for a few days about 4 years ago to teach me more about photography. I remember at that time in my career, I wanted to learn everything about photography that I could, so I trained under Debi Treloar (interiors) while we produced my first two books in 2010 and 2011, Deitlind Wolf (styling) in 2017 and Anoushka Rokebrand (lifestyle, weddings) around the same time, I think 2016. As for the tech part, I learned that through my husband, Thorsten, and from lots of hands-on practice and just jumping in and saying “Yes!” a lot to projects. I also made a lot of mistakes in the beginning, but I don’t devalue any of those or feel ashamed because I know they all made me who I am today.
When we got married, my husband gave me a Canon film camera for our first anniversary because he knew how much I loved taking photos - that was in 2002. My grandfather was a portrait photographer with a studio in his big home in the midwest, he used to take photos of me and my parents (he’s the father of my dad) when I was a child. I was always fascinated by his work. I still have some of his portraits and I love them, they really reflect the trends of the moment and give me special insight into his world and vision since he died when I was a teenager.
I’ve also worked a lot with my friend Leslie Shewring, and always loved her angles and styling, but also how dreamy her photos looked in the end - Leslie awakened a real love for photography in me that was pretty dormant for years because my larger focus was on writing and sourcing content for my blog and books. I’ve always loved photography though, but never really got into it, I hired people to do the work for me. Yet, I found that as I was directing photographers and “seeing” the shot in my mind’s eye, that my frustration was growing. I wanted to be behind the camera. I didn’t want to keep directing people - it was frustrating to me to hold my tongue and I sensed it was frustrating for them to feel my energy - I imagine they could sense I wanted to jump in and do their job. Photography really electrified me, I love it beyond words.
I take photos daily, I use them as a visual journal or diary to document my life but also for my work. I’ve come a long way. But not without a lot of self-doubt and anxiety in the early days.
Self-confidence (in photography at least) was always a really hard challenge for me though. It held me back because I didn’t consider myself technical enough, I thought maybe I didn’t have what it takes to shoot a good photo that would be taken seriously outside of the blog world (bloggers are lovely and very forgiving). Plus, photographers can be very protective of their work, skillset, and “secrets”, which made it very hard to learn in the days before sharing through online classes and workshops became the norm amongst many high-end photographers. I am so thankful that technology changed all of these formerly “closed” ways of working, because sharing knowledge is the only way for any field to really progress, evolve and grow.
A real turning point in my career was when we hired Holly Marder from Avenue Design Studio to travel to Hannover to work with me for several days for my 4th book, Decorate For a Party. She looked at me at one point while we were working (I think it’s because I was so bossy, I don’t know) and said, “Why do you need to hire a photographer at this point, you are so good on your own, why don’t you trust yourself?”. I wondered if I had irritated her. But I hadn’t, at all. She could sense how much I loved styling and taking photos, she felt my energy, she knew it was something that I desired for myself - to take my own photos professionally.
That candid comment was exactly what I needed to hear (thanks, Holly!). It helped me to pull back layers and layers of self-doubt and insecurity about photography. In fact, her comment forced me out of my comfort zone because in the final hour of created Decorate for a Party, our publisher needed a photo for the cover and asked me to create one and shoot it because there was no time to hire anyone. I did it in half a day and the publisher was so happy that my dining room became the cover photo (see it here). What an honor.
I always assumed because I wasn’t super technical, that I couldn’t really BE a photographer. I remember I told her that I trusted my eye, but not my skills and she laughed and said, “Do you honestly think I’m super technical?!? I know how to take the photos I want, and that’s it. Don’t ask me any tech questions though. Just learn how to do what you need to do.” That was 4 years ago, I’m sure Holly is very tech-savvy with her camera today, but I learned early on that the people holding cameras, churning out incredible photos, were not exactly fluent when it came to every feature on their camera.
That honest conversation really HELPED ME to hear from Holly Marder, someone who years earlier, I had trained in blogging and now, it was my turn to learn from her. And I did. I learned that I only needed to “master” how to take photos in my style, I didn’t need to learn my Canon 5D Mark III inside out and become a technical genius. This was absolutely what I needed to hear to set me on a new path - the less critical, less perfectionist path - the fun and fulfilling road of photography that I longed for. In fact, the more I worked around photographers and bloggers who took great photos, I observed half of them (or more) also didn’t know their cameras thoroughly but they knew how to achieve what they wanted.
One blogger told me at a fair in Milan that she didn’t need to write a book about photography, she needed to take pretty pictures. That was her only goal. This more laid-back approach took years of self-imposed pressure off of me. I needed to learn to, “fake it until I make it”, which was so opposite of how I approached photography initially. The pursuit of perfection was stunting my growth, so I started to just take photos more, accept jobs more without hiring a photographer and doing it myself, and to practice my own style daily using my iPhone and my Canon, I figured if I could learn how to use those, I could make great photos too.
Anyway, I digress, but working with Anoushka Rokebrand, who is technical, who does know her camera and how to take great photos, was next-level education for me. It really was helpful and added to my toolset. Every experience I’ve had in the early days of photography helped me to find my own style, build my skill set, and form my vision. I’m still learning and evolving as a stylist and photographer, but I’m shooting for magazines and books, 90% of the photos on my Instagram are my own, and I’m capturing great memories of my life and the childhood of my little boy even better because I’ve invested in learning how to take good photos from people like Anoushka. Largely, I am self-taught, self-directed, and self-motivated. But I never forget the people who had a hand in helping me to trust myself - those special classes with Anoushka and Dietlind and shadowing Debi, and just talking a lot about photography with my husband, Leslie, and Holly.
If you like the photos peppered throughout this post, they were all taken by Anoushka and are available on her website HERE. You can download any of them without the watermark (there is a small fee) and then she will send you the file and you can create your own photos by sending them to a printer or printing them at home… Then you can frame them and enjoy her beautiful Arizona desert prints in your home. I would love to blow up 3 of her photos and put them above my bed. Do you see any favorites?
PHOTO TIP: You can join our #30dayhomelove interiors photo challenge on Instagram this Friday, it kicks off on May 1 and runs daily until May 30. Each day there is a new prompt. You take your camera or smartphone and snap a photo in your home that fits the daily theme and post it on your Instagram and tag @decor8 @myscandinavianhome and #30dayhomelove so we can visit you, like the photo, and maybe if there’s time, we can leave a comment too. The goal is to use the challenge to improve your styling and photography a little bit each day, to make new friends, to be inspired at home, and to maybe even find new corners or spots in your daily life that you love (and didn’t realize it yet).
FOOD FOR THOUGHT: What has been your photography journey? Did you (or do you still) have hurdles to overcome? Do you think you have “perfectionist syndrome” too as I once did? Maybe you have to be less hard on yourself, more gentle, more loving, and just roll with it. When I stopped pressuring myself, and relaxed about my styling and my photography, I saw a big difference in my work. Perhaps now, during these corona times, you can practice taking more photos indoors.
Have a lovely day everyone and remember to visit Anoushka’s shop - support small business!
Love,
Holly
(Photography: Anoushka Rokebrand)
0 notes
Text
Superhero Games and Stories
DC Universe is letting me watch the old Justice League series too…
Recently, I signed up for DC Universe, primarily so I could watch the new season of Young Justice, but I’ve also taken advantage of all the DC animated movies available on the streaming service. There’s also an excitement in the air related to the Marvel Cinematic Universe, what with Captain Marvel having come out last month and Avengers: End Game arriving in just a couple weeks. It’s made me think quite a bit about superheroes and gaming.
Anyone who’s gamed with me for any length of time knows I love superheroes and their games. In recent years, I developed a reputation for running Masks at cons, and my regular group often asks me to pick up the GM cape once more and run a supers game for them. Heck, the very first campaign I ever ran was a Mutants & Masterminds campaign.
I already have my tickets…
Thing is, superhero stories are not this monolithic, single type of story or game. While it is easy for many to mistakenly make this assumption, when you really dig down into it, superhero stories are more of a framework you hang over other stories. This is one of the secrets to the success of the Marvel Cinematic Universe. They’ve focused on telling interesting stories with compelling characters that just happen to have special abilities, rather than focusing on only the special abilities. It doesn’t matter how cool the costumes are or how awesome the special effects for the abilities are, if the story is boring or the characters just caricatures of people no one is going to care.
(Another open secret to MCU’s success is in how they know how to be true to the essence of the characters and then nail the casting for that character. I could wax poetic about these movies for hours, so I’ll keep a lid on it.)
Back in the late 80’s and 90’s, when RPGs all seemed to be obsessed with simulation, superhero games like Champions did everything they could to provide meticulous ways to emulate the powers of all our favorite heroes. Unfortunately, this often pushed the heart of the story and characters into the background, losing the spark that makes us love super heroics. I’m very careful about the superhero games I sign up for at conventions, because too often, that spark is lost and the game just ends up being a simulation for a superhero smash up fight. There’s nothing wrong with a fun, bombastic combat, but that’s not necessarily the only kind of game I’m looking to play or run.
If you, like me, are considering running a supers game in the near future, here’s a few things to consider before bringing the game to the table for your players:
Tone: Once you decide the tone of your game, other things will fall into place easier. Are you looking for a light hearted romp around the cosmos, or a gritty and complicated story of difficult choices? Take a look at the first season of the Justice League animated series from the early 2000’s compared to the first season of Daredevil on Netflix. Yeah, they’re both superhero stories, but that’s about the only thing they have in common. If you don’t establish the tone you’re looking for from the get-go, you’re going to have problems. Your players also have a wild and wide understanding of the superhero genre, and they may be all over the place in the tone they’re expecting. Their characters will reflect that and while it’s not impossible to make a game work with characters of varying tone, it’s difficult to maintain that for the long haul.
Setting: Some superhero stories take place in a single city, or even just a single neighborhood. Others span galaxies, taking the heroes from planet to planet, galaxy to galaxy. As you can imagine, deciding the scope of your game’s setting can help determine the types of stories your game is going to be telling and the types of characters that should come into play. Setting a game in an afro-futuristic city like Wakanda guides the themes and characters in very specific ways. Or imagine using a setting like Smallville, telling the stories of some young heroes learning who they are and what they can do.
Don’t let them get lost in the minutia of what powers they have and what those powers do, because WHO the character is beneath the costume and abilities is what makes the game truly heroic.
Share1
Tweet1
Reddit1
Email
Limits: What are the limits of the characters you want in play? Can your game handle Batman and Superman in the league together? Can you provide a variety of challenges for both Thor and Hawkeye? Or do you want to limit the origin stories for your players and have them all have some common bond like being students at an upstate boarding school for ‘special’ students? The options for this are almost limitless (ha!), but if you take a look at the best superhero stories, they keep all the characters within a certain framework, at least to start with. We may enjoy the idea of having Captain Marvel and Jessica Jones in the same universe, but you’re going to have to sacrifice something to run a game that includes both of them. Put Jessica in the far-flung cosmic encounters Carol is capable of and she’s going to be a little lost. And annoyed since there’s no alcohol. Put Cap in Hell’s Kitchen and she’s going to have to limit her capabilities to not just obliterate the neighborhood. It’s not that it can’t work, it’s just that you’re going to have to make choices and sacrifices with the stories your game tells.
Character: Last, but absolutely not least. Don’t forget that everything you do still boils down to the characters the players bring to the table. What I mean is that while Captain Marvel’s powers are cool, she wouldn’t be nearly as interesting without her in-your-face determination to do what’s right. Batman may have all those wonderful toys, but his best stories are fed by the gravitas of his tragedies. When your players start working on their characters, don’t let them get lost in the minutia of what powers they have and what those powers do, because WHO the character is beneath the costume and abilities is what makes the game truly heroic.
Another good example of how to do an ensemble cast right…
There are so many options out there for superhero games. So many. Many games come with tone, setting, and limits established within the design of the game, while others come to your more as a toolset to build your own world. Another consideration is the level of crunch that you’re comfortable. I lean more towards the narrative games these days, but I can understand the draw of a crunchier game. Make sure whichever game you pick actually works with the tone, setting and limits you want to try for in your game. The wrong combination can be painful to work through.
After several of my regular group saw Captain Marvel, they cornered me and said, “Ang, you’ve GOT to run another supers game.” Honestly, I can’t disagree with them, because I certainly feel that pull as well. Between now and when I start, I’ve got quite a few things to figure out. What about you and your gaming crew? Any super heroics on your horizon? We’d love to hear about it.
Superhero Games and Stories published first on https://medium.com/@ReloadedPCGames
0 notes
Text
making a pico8 game during my first week of RC
tl;dr - Play my first ever solo game right here!
On my first day of Recurse, fellow W1 2017 batcher Ayla Myers (whose work you can peep here) presented on fantasy game consoles, PICO-8 in particular. Her presentation ran roughly 5 minutes, but it only took about half that time to convince me that I should give it a whirl. Since asking for help is more than encouraged here, I approached her immediately afterwards and asked if she could do a quick walkthrough of PICO-8 sometime.
“Yeah, of course. When do you want to start?”
“Uh…” It was already 6pm. “Tomorrow?”
“Okay!”
And lo, 11am the next day found myself and a handful of other Recursers sitting around a table in the Turing meeting room as Ayla showed us the ropes.
PICO-8 is a highly-opinionated, highly-constrained fantasy console with a robust set of tools for quickly developing and sharing games. While I’d played a few PICO-8 games before, I hadn’t realized just how core the commitment to retro-nostalgia is to the engine itself. Here are some fun things I learned about PICO-8:
It includes a pixel art editor and a chiptune mixer, both of which are a delight to use.
PICO-8 games can have 2 players, but each player only gets 6 possible inputs: four directional keys and two others (typically Z and X).
On the programming side, developers are allowed a maximum of ~8k tokens and ~65k characters. This incentivizes some extreme optimization, overloading, and other tricks in larger games that near those limits.
The games are super easy to export and share, either as embeddable HTML and JS or as downloadable executables.
As someone who has shipped dozens of games professionally but has never personally programmed one from start to finish, I decided that it’d be a good exercise to build one during the remaining 4 days of the first week.
On programming in a new language.
PICO-8 uses a subset of Lua, which I’ve never read or written before. Under other circumstances, I probably would have preemptively given up and shied away from using a tool that required learning a new language. Fortunately, my current circumstances are “you are entirely here to learn new things and surrounded by people who can help, actually” so I waved off the anxiety and plunged ahead instead.
Turns out that Lua felt very similar to other game programming I’d done in the past, so there wasn’t any need to worry anyway! (One begins to suspect that there is rarely a ‘need’ to worry… 🤔)
There were a few things that stood out in particular as I built my game.
First, to handle animations - like bobbing a sprite or moving UI elements on and off screen - I found myself repeating a pattern using a counter (incremented every update loop) and a maximum (resetting the counter to 0 when it reached this value). I wasn’t sure if a series of timers would be a better fit for cycling through animation states, especially since this pattern meant assigning at least two tokens per animation. Since I was focused on building this quickly and wasn’t worried about running up against the token limit, however, I figured that consistently using a single pattern that I knew worked was the way to go.
Example of the section of the bat’s update loop that flaps her wings up and down and plays a quick beat on each flap:
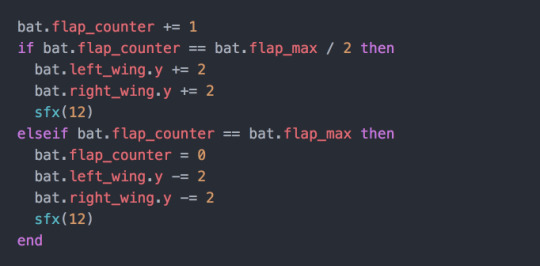
Second, I learned that tables are “the only data structuring mechanism” in Lua, and that there is no readily available method to query them about the number of items they’re holding. To solve this, I tracked the count of items as a separate variable and updated the count any time I was adding or removing items from the table. If I were pinched for tokens I’d probably handle this differently, likely by writing a separate function that iterates over the the items in the table and returns the count.
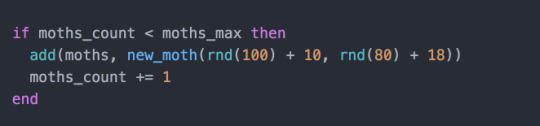
Lastly, and this one was a pleasure to discover, Lua is perfectly a-okay with removing items from a table while iterating over items within that table. For example, during the update loop I want to iterate over each of the moths in the game and check if the bat is in a position to eat them. If the bat should eat the moth, I want to add a quick sound effect, draw some bug-gut splatter to the screen, and remove the moth from the moths table.
I can do all of that like this:
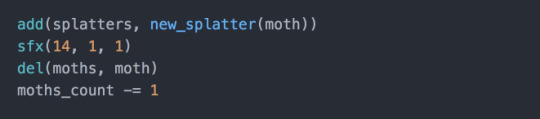
This was a big relief to me because I’ve had trouble doing the same with JavaScript in the past!
On finding relief in constraints and designing a tiny game.
I didn’t have a strong idea when I first started making Sonar, other than that I should be able to finish it in a few days and that it should be about animals. Certainly my appreciation for earth’s non-human lifeforms would stave off any temptation to jump ship if things got confusing or tedious. 🦇
There was a brief moment where I sat, staring at my laptop screen, wondering what I could even do with only two non-directional inputs. It took about five minutes for me to come to my senses. What if this constraint, much like the constraint on tokens or audio channels, was a blessing? “Wow, I’m so glad I only have two buttons to work with,” I told myself, found it to be true. “In fact, let’s start by using only one of those buttons.”
Changing your perspective sure is a time-efficient way to clear obstacles!
On making art and SFX.
While I’d done some game programming (though never a complete solo project), I’d certainly never done game art or audio. In fact, art and audio often felt more intimidating than the rest of the design or development. I didn’t really know anything about creating reasonable looking pixel art or have any kind of background in creating music or sound effects; I just knew that both were important to making a game feel whole.
Once again, PICO-8 provided seamless introduction to these areas of game development. With only 16-colors and 8x8 pixels to worth of space to work with, I never got stuck trying to pick the perfect colors or shape for a sprite. If it worked, it worked, and it only took a matter of seconds to make changes and see them live in the game.

As someone who has zero musical education the responsibility of creating audio made me more than a little apprehensive, but I found the SFX editor similarly quick to learn and pleasant to use. I stopped short of making any ambient music, but I did make a few sounds: a steady but muffled bassline for the bat’s wings flapping, a high-pitched chirp for the echolocation, a gulp for a bug being swallowed, and a confirmation bloop for starting the game. SFX are necessary for giving a non-haptic game the illusion of tactile feedback, and even just these few simple, two-note sounds do a lot of heavy-lifting in making the game feel more responsive.
On jamming fast, alone, in an environment geared towards collaboration.
The single biggest struggle I had while working on this project was worrying if I should be spending my time doing something else. Whenever I spent large chunks of time coding alone, rather than pairing or attending study groups, I couldn’t help but feel like perhaps I was missing the forest for the trees. Shouldn’t the first week be about learning as much as possible about my peers and their interests, in the spirit of future collaboration? Did I somehow find a way to ‘do it wrong?’
Hard to say, what with only one week’s worth of information! My current guess, however, is no. I became familiar with a new language, I learned a new toolset, and I finished a project that I feel at least remotely comfortable showing to other people. Those are pretty solid accomplishments, even in the face of a gnawing suspicion otherwise!
More importantly though, I practiced being comfortable following my own intuition of what an ideal first week might look like. I proved to myself that I could set my own goals and meet them. I also developed a general feel for the ebbs and flows of working with myself as sole author and stakeholder on a project. I’m sure this kind of self-knowledge is valuable at any level, but as a beginner it feels like an especially worthwhile point of reference.
Besides, this was all made possible because I was inspired by a fellow Recurser, asked them for help and got it.
How could that be wrong? 😊
You can play Sonar right here.
ps. I almost forgot something funny!
This is one of the first things that happened when I began animating my pixel bat:

I laughed at this for a solid minute. It was wonderful, and only more so because I had spent the previous two hours setting up new software, familiarizing myself with basic Lua syntax, and fretting over whether my pixel art would be at all legible.
As one of my friends commented, “OH NO, HIS FLAPS FELL OFF!” And then, “or HER flaps, excuse me.”
Making games is generally time-consuming, tedious, detail-oriented work. On the bright side, many of the bugs and SNAFUs you run into are just silly as heck. The moments where ish goes off the rails can provide exactly the right dose of harmless humor to revitalize your motivation to finish. 👑
edit (11/15/2017)
Once again going above and beyond in her helpfulness, Ayla informs me that you totally can get the length of a list in PICO-8!
Here’s how, using the # operator:
local some_list = {32, 4, 72} print(#some_list) -- prints 3
✌️🦇
edit (11/17/2017)
So probably it makes sense to link to the the code, since becoming a better programmer is the whole gosh darn point! 😑
Also, because it may be helpful, I want to provide a quick outline of how you might also crank out a small game in a narrow window of time:
day1 - purchase and install pico8 (if you’re at RC, talk to someone about using their license!) - install a lua linter on your text editor of choice - run pico8 in console mode, so u can use printh to debug - make a player character that responds to input - make a 2-state animation for that player character (eg. flip between two sprites, add some bobbing motion, etc) - get ppl to Play Your Game!
day2 - make an enemy (note that these could also just be Collectable Objects if u aint feeling like defaulting to violence ✨) - make a 2-state animation for that enemy - give that enemy some passive behavior - disappear the enemy conditionally (eg. touched by player, hit by bullet) - make another enemy with similar but more challenging behavior - get ppl to Play Your Game!
day3 - add an end-condition (eg. eating some amount of bugs) - add SFX. this is more important than music for making your game feel whole, and you can do just about everything you need to with 2 note blips - add UI elements (eg. health bar, bullets left, etc) - add a start screen - add an end screen - get ppl to Play Your Game!
day4 - add finishing touches - export your game as html from PICO8 - host somewhere, like itch.io - write a blog post!! - share with your friends and the rest-o the world
2 notes
·
View notes