#that .tumblr is the new portable document format
Explore tagged Tumblr posts
Text
hey, don't cry

tumblr is the new pdf! ok?
#tumblr#tumblr is the new pdf#personal#sbs rambles#art#idk what other tag to put this under but this is definitely a thing I made#the big blue rectangle is 2013-era tumblr blue#the dark blue triangle and text shadow are the current ''true blue''#and the lines and blue corner are what we call ''classic blue'' or ''old blue'' but at 69% opacity#(nice)#in this way I have combined all the eras of tumblr into one#so that I might imagine#just for a moment#that .tumblr is the new portable document format#thank you for coming to my ted talk#graphic design is my passion#anyway hey remember that time yahoo said they wanted to make tumblr ''the new pdf''#wild#bizarre thing to say#but hey#I think it could still happen#we just have to believe
3K notes
·
View notes
Text
Infodump time
Y’know what’s funny about tumblr almost being the “new pdf?”
They’re both equally janky.
The portable document format was based off of a lesser-known format called postscript: a stack-based document format that allowed for rudimentary vector rasterization.
“Okay, but what’s the catch?” You may ask.
Take a closer look at that description. Postscript is STACK-BASED. Sure enough if you look into it, postscript is also Turing complete, ie: it can execute code.
I don’t remember exactly when this happened, but hackers were at one point embedding payloads into pdf documents. With postscript it’s worse; some printers deliver firmware updates as a postscript file, meaning that updates are processed the same way as a print job.
Tumblr has always been the new pdf.
6 notes
·
View notes
Link
32 notes
·
View notes
Text
Types Of Image Files.
1. JPEG (or JPG) - Joint Photographic Experts Group
JPEGs might be the most common file type you run across on the web, and more than likely the kind of image that is in your company's MS Word version of its letterhead. JPEGs are known for their "lossy" compression, meaning that the quality of the image decreases as the file size decreases.
You can use JPEGs for projects on the web, in Microsoft Office documents, or for projects that require printing at a high resolution. Paying attention to the resolution and file size with JPEGs is essential in order to produce a nice looking project.
2. PNG - Portable Network Graphics
PNGs are amazing for interactive documents such as web pages, but are not suitable for print. While PNGs are "lossless," meaning you can edit them and not lose quality, they are still low resolution.
The reason PNGs are used in most web projects is that you can save your image with more colors on a transparent background. This makes for a much sharper, web-quality image.
3. GIF - Graphics Interchange Format
GIFs are most common in their animated form, which are all the rage on Tumblr pages and in banner ads. It seems like every other day we have a new Grumpy Cat or Honey Boo Boo animated GIF. In their more basic form, GIFs are formed from up to 256 colors in the RGB colorspace. Due to the limited number of colors, the file size is drastically reduced.
This is a common file type for web projects where an image needs to load very quickly, as opposed to one that needs to retain a higher level of quality.
4. TIFF - Tagged Image File
A TIF is a large raster file that doesn't lose quality. This file type is known for using "lossless compression," meaning the original image data is maintained regardless of how often you might copy, re-save, or compress the original file.
Despite TIFF images' ability to recover their quality after manipulation, you should avoid using this file type on the web -- it can take forever to load. TIFF files are also commonly used when saving photographs for print.
5. PSD - Photoshop Document
PSDs are files that are created and saved in Adobe Photoshop, the most popular graphics editing software ever. This type of file contains "layers" that make modifying the image much easier to handle. This is also the program that generates the raster file types mentioned above.
The largest disadvantage to PSDs is that Photoshop works with raster images as opposed to vector images.
6. PDF - Portable Document Format
PDFs were invented by Adobe with the goal of capturing and reviewing rich information from any application, on any computer, with anyone, anywhere. I'd say they've been pretty successful so far.
If a designer saves your vector logo in PDF format, you can view it without any design editing software (as long as you have downloaded the free Acrobat Reader software), and they have the ability to use this file to make further manipulations. This is by far the best universal tool for sharing graphics.
7. EPS - Encapsulated Postscript
EPS is a file in vector format that has been designed to produce high-resolution graphics for print. Almost any kind of design software can create an EPS.
The EPS extension is more of a universal file type (much like the PDF) that can be used to open vector-based artwork in any design editor, not just the more common Adobe products. This safeguards file transfers to designers that are not yet utilizing Adobe products, but may be using Corel Draw or Quark.
8. AI - Adobe Illustrator Document
AI is, by far, the image format most preferred by designers and the most reliable type of file format for using images in all types of projects from web to print, etc.
Adobe Illustrator is the industry standard for creating artwork from scratch and therefore more than likely the program in which your logo was originally rendered. Illustrator produces vector artwork, the easiest type of file to manipulate. It can also create all of the aforementioned file types. Pretty cool stuff! It is by far the best tool in any designer's arsenal.
9. INDD - Adobe Indesign Document
INDDs (Indesign Document) are files that are created and saved in Adobe Indesign. Indesign is commonly used to create larger publications, such as newspapers, magazines and eBooks.
Files from both Adobe Photoshop and Illustrator can be combined in Indesign to produce content rich designs that feature advanced typography, embedded graphics, page content, formatting information and other sophisticated layout-related options.
10. RAW - Raw Image Formats
A RAW image is the least-processed image type on this list -- it's often the first format a picture inherits when it's created. When you snap a photo with your camera, it's saved immediately in a raw file format. Only when you upload your media to a new device and edit it using image software is it saved using one of the image extensions explained above.
RAW images are valuable because they capture every element of a photo without processing and losing small visual details. Eventually, however, you'll want to package them into a raster or vector file type so they can be transferred and resized for various purposes.
As you can see from the icons above, there are multiple raw image files in which you can create images -- many of them native to certain cameras (and there are still dozens more formats not shown above). Here's a brief description of those four raw files above:
CR2: This image extension stands for Canon RAW 2, and was created by Canon for photos taken using its own digital cameras. They're actually based on the TIFF file type, making them inherently high in quality.
CRW: This image extension was also created by Canon, preceding the existence of the CR2.
NEF: This image extension stands for Nikon Electric Format, and is a RAW file type created by (you guessed it) Nikon Cameras. These image files actually allow for extensive editing without changing file types, provided the editing takes place using a Nikon device or Nikon Photoshop plugin.
PEF: This image extension stands for Pentax Electronic Format, a RAW image file type created by Pentax Digital Cameras.
2 notes
·
View notes
Note
I'd like to ask your opinion on something. I wanna start writing, but i dont know where i should put them. I prefer using Tumblr, but then i'd have to work a lot on maintaining the blog, but it'd look more organized and custom-made. As for AO3, i dont really use it, but i feel like i'd just be able to post a fic and leave it there without having to worry too much about it. What's your take on this? Do you have any preference?
hello there darling, first of all, welcome to the world of writing fanfiction for BTS (or other groups), I’m sure you have something written or drafted already and you’re just contemplating on which platform is the best? my opinion as a reader would be to post your works on as many platforms you want and can maintain despite your busy schedule, it guarantees more exposure for your works since some prefer reading on tumblr only or ao3 or wattpad or asianfanfics etc. plus it will reduce the chances of your stories getting plagiarized.

now, between Tumblr and AO3, with Tumblr I enjoy seeing the writers headers/banners/moodboards it somehow helps set some sort of mood because I appreciate visuals tbh, also, we could always use the +read later/reading list feature on google chrome to read their works offline when I’m on the go, and here are some downsides of Tumblr, one, the “keep reading” feature, I hate that even if you’re certain you added it on your post it magically disappears (wtf Tumblr, go home, you’re drunk hasdgfjkhsa) two, the links get fucked up somehow, three, the tagging system isn’t the greatest and four, their algorithm is weird af. as for your works getting exposure and love here, it will take some time since you’re new, so I highly suggest you join networks for writers because they will share your stories which increases the chances of your works getting seen and read by their followers, and another good thing about tumblr is you can interact with your readers here, you receive feedback, some send direct messages and others talk with you thru asks (some anonymously because they get really shy)
AO3 is heaven-sent! though I have no idea how posting stuff there as a writer works or if there’s a huge difference with how you post on Tumblr (I’m assuming there’s a lot because AO3s tags are specific - at least those I’ve seen during my infinite trips on the site) I love scouting fics there, one, because there are so many amazing writers there that don’t have Tumblr, two, their filtering system is helpful especially if I’m looking for specific aus, genre, characters, kinks or if I prefer reading completed series on certain days, three, I prefer reading on my phone, I use lithium on my android and books on my iPhone, ao3 gives us an option to download the stories in the ff. formats azw3 (kindle), epub (nook, kobo, books and other electronic publication readers), mobi (mobipocket), pdf (portable document), html (hypertext, for browser reading) ~ btw, I always get the epub one, now why do I prefer it over reading via Tumblr? because the Tumblr app crashes especially if I’m reading monster one-shots/series plus I highlight and add notes when reading so I highly appreciate that feature from ao3.

now it’s all up to you in the end which platform you think would work best for you, your time, and schedule, btw I just noticed that ao3 has so many diverse stories and readers that are much more accepting especially with dark and taboo ones, as for feedbacks idk which site has more people that give their opinions to the writers, and on maintenance Tumblr does require more of it compared to ao3, so I guess that’s it? sorry if this was unnecessarily long I’m just a talkative one, I hope you make the right choice and enjoy writing for your faves! have a lovely day/night my dear! ❤️ | 🍒
#answered#tete-a-tete#qq#anon#srsly idek if this answered your question or if it's helpful in any way ggfadshjfghasjdfgakjhs#but this is just being me so talkative hadsgfkjsdfg#but hopefully this helps!#good luck on your writing my dear :)
3 notes
·
View notes
Text
Cs5 For Mac Serial Number

Since there’s no native interface for easy file transfer between Android and macOS, users have to turn to various workarounds like moving stuff to Google Drive or Dropbox. Afterwards, you can access data on your smartphone by using the corresponding Android app.Another option is to rely on third-party tools, including one from Google, for transferring files between Android and macOS either via USB or Wi-Fi. Syncios data transfer for mac.
Illustrator Cs5 Serial Number Mac
Cs5 Serial Number Generator
6 Feb 2012 adobe keygen mac 2012 – adobe-photoshop-keygen.blogspot adobe photoshop cs5 key, adobe photoshop cs5 serial number. 13 Jul 2011 Adobe cs5 keygen for windows and mac 100%working ! NEW Virus Free Adobe Photoshop CS5 Extended KEYGEN 00:13. If you have any complaint on Adobe Photoshop Extended CS5 (Mac) serial number and think that it outrages andor violates any laws please feel free to send. Photoshop Cs5 Serial Key Generator Mac. 20 comments to Photoshop CS5CS6 Key Generator – Keygen For MacWin How to CrackSerial Number it : Open. Download Adobe Photoshop Cs5 Extended Mac. suite design premium cs5.5 serial mac autodesk 3ds max 2012 xforce keygen 32bits flash download crack. Download adobe flash cs5 portable gratis delicious library 2 mac free flash cs6 list photoshop v13.0 extended keygen microsoft access 2013 runtime tutorial. Download free trial indesign cs6 mac adobe photoshop cs5 extended keygen virtual dj pro 7 crack skins paragon partition manager 9.0 serial get cc tumblr. 114 records Adobe Photoshop CS5 Keygen (By Martik Panosian).zip Adobe Photoshop CS5 Patch Adobe Photoshop Extended CS5 (Mac) Adobe Photoshop. Adobe illustrator cs6 serial number mac windows 8 pro 64 bit download iso free 9 review adobe photoshop cs3 extended retouching motion pictures cs5 mac.
Data Recovery for iTunes: How to Retrieve Data from iTunes Backup on Mac. To backup iPhone SE data to Mac can help you retain your data in the event that you lose your iPhone or damage happens. It's easy to transfer music and videos from iPod touch to Mac if you have iSkysoft dr.fone installed on your Mac.Here are the simple steps. Submit your order number or licensed email to get your registration code back within minutes. Mac Data Recovery for Mac iPhone Data Recovery NEW Phone Transfer for Mac TunesOver for Mac Windows. Tweet us @iSkysoft to get support through Twitter. Secured Shopping. Discounts average $10 off with a iSkysoft promo code or coupon. 17 iSkysoft coupons now on RetailMeNot. Categories Log in Join for free. ISkysoft Coupon Codes. ISkysoft is a professional DVD Ripper and Video Converter software provider for both Mac and Windows users. Today's iSkysoft Top Offers: 50% Off Sale + Extra $5 For PDFelement; 20%. Recoverit Data Recovery for Mac provides an all around data recovery solution for the mainstream data like photos, videos, document files, audio data and more formats files on Mac OS. We rescue your important data when you meet any data lost disaster on your Mac devices including from latest encrypted APFS file system. Iskysoft data recovery for mac code.

Adobe Photoshop CS5 Windows with Serial Number. ADOBE PHOTOSHOP CS2 FOR MAC WITH VIDEO TRAINING - SERIAL. Adobe Photoshop CS3 For Mac (with Workshop DVD And Serial Number) $53.00 1d 15h +$4.75 shipping. Make Offer - Adobe Photoshop CS3 For Mac. Download starcraft for mac os x.
Telegram download for mac. Pure instant messaging — simple, fast, secure, and synced across all your devices. Over 100 million active users in two and a half years. FAST: Telegram is the fastest messaging app on the market, connecting people via a unique, distributed network of data centers around the globe. Telegram is now among the top 10 most downloaded and most used apps in the world. Increased limits for sending files; Share and store unlimited files of any type, now up to 2 GB each. Profile Videos; Set a Profile Video instead of a static picture. Quickly change back to a previous profile photo or video by tapping ‘Set as Main’. Download telegram for mac 10.6.8 for free. Communication downloads - Telegram by viko and many more programs are available for instant and free download. Get Telegram for Windows Portable version for Windows Get Telegram for macOS Mac App Store version. Get Telegram for Linux 64 bit Get Telegram for Linux 32 bit. Show all platforms. Official app for macOS from Telegram team This software is available under GPL v3 license. Telegram for Mac is a messaging app with a focus on speed and security, it’s super-fast, simple and free. You can use Telegram on all your devices at the same time — your messages sync seamlessly across any number of your phones, tablets or computers. With Telegram for macOS, you can send messages, photos, videos and files of any type (doc, zip, mp3, etc), as well as create groups for up.
Illustrator Cs5 Serial Number Mac
Re: CS5.5 serial number not valid Test Screen Name Nov 12, 2018 12:16 PM ( in response to Jae7 ) It's many years since systems moved on, and the chances of getting CS5 to work fully or at all on a new Mac.
Adobe after effects cs5 crack mac photoshop extended free download elements 6 pdf norton ghost 15 with serial reason adapted 4 license number flex builder. Download Adobe Photoshop Cs5 Extended Mac. Keygen creative design premium trial serial number excel.
Cs5 Serial Number Generator
List of Adobe Photoshop CS5 Free Serial Key Number for Crack 1325-1959-4831-9595-4753-6693 1325-1283-0188-5542-3177-8536 1325-1476-7332-7761-1845-4985 1325-1726-5909-4207-8020-8670 1325-1022-9706-0958-7604-1775 1325-1687-8702-1220-6899-8989 1325-1614-1036-9777-4655-9626 1325-1064-2785-7115-1884-1575 1325-1230-0481-1596-7241-7212 1325-1912-6501-0053-8651-8852 1325-0617-8365-2331-6662-9349 1325-0621-9125-0765-3648-0614 1325-0365-5929-6118-8817-8422 1325-0150-1163-7532-1626-3430 1325-0178-1927-9019-0123-2254 1325-0702-3693-1544-9166-3515 1325-0549-2240-0071-3409-1342 1330-1807-1434-7787-2724-9847 1330-1162-1098-8524-5189-8123 1330-1875-1855-6864-3126-7573 1330-1130-9752-1642-3535-0727 1330-1098-1473-1958-4787-9730 1330-1590-3893-5750-8075-6625 1330-1102-8841-6669-3776-0827 1330-1346-9904-2001-2235-7252 1330-1738-2960-4360-1076-2330 1330-1106-3088-2889-5934-3982 1330-1807-1434-7787-2724-9847 1330-1162-1098-8524-5189-8123 1330-1875-1855-6864-3126-7573 1330-1130-9752-1642-3535-0727 1330-1098-1473-1958-4787-9730 1330-1590-3893-5750-8075-6625 1330-1102-8841-6669-3776-0827 1330-1346-9904-2001-2235-7252 1330-1738-2960-4360-1076-2330 1330-1106-3088-2889-5934-3982

0 notes
Text
February 17, 2021: 3:51 pm:
=================================================
In summer of 2014 I began to make documentation of the events that were happening around me in Oregon. I did that at Google+ social media web site.
I could not get help ... years of eye-witness of mass murders, of people being ground into pulp at the shopping centers, of entertainment venues where actors, musicians, clowns, and magicians gathered to watch as citizens were crushed by machines, and tossed with trebuchet, and forced to ride on a giant 20 foot tall razor blade shaped like a slide at playground, people cut in two, long ways. Some of them tried to jump off the slide each time I saw it, partly cut, forced to ride the slide again. That slide is portable, makes a traveling road show. I saw it set up at Triangle Park in Ashland Oregon once, the terror bastards had modified it for wheel chairs. Disabled people forced to ride the razor slide while in the wheel chairs. The put a Visqueen plastic barrier around the slide to conceal it from passers by on the main highway there out front of Triangle park.
So I started writing about what I was seeing on Google+ in 2014.
I could not reach any help, and only terror soldiers made contact with that Google+ account. I asked Google for help, sent them many notes, simply to ask that they contact US national security, and US Military because I was unable to reach any help, and FBI.tips.gov is hijacked by terrorists, does not work for getting any help, it only brings assassins when reports of terrorism is made there.
Google sent assassins to my house instead of contacting US national security to point out the account I had there.
I killed all of the assassins that Google sent to kill me.
Google ran out of assassins for awhile. So, they decided to delete the entire Google+ social media platform. Millions of accounts were deleted. That means there were other reports of terrorism contained at the Google+ social media platform besides the ones I was making.
I downloaded my content, and put all of it here on Tumblr. That started in April 2019 when Google+ ended, I began this Tumblr account, but I kept pressuring Google to call US national security right up to the very end of the existance of Google+ social media platform.
That platform was deleted entirely because of the things I had written at my account there, rather than help, Google needed to eliminate the evidence against them that I had documented, and they needed to do that without pointing out any particular reason as to the nature of the decision to eliminate the entire millions of accounts that were hosted at the Google+ social media platform.
All they needed to do was end support for the service. They did not need to delete the whole platform. Other companies have abandon websites, while maintaining their exhistance, but without support for the service in event someone needs assistance to use the service, they just put up a set of FAQ’s, and anyone who uses such abandon sites is on their own to figure out how to use it, and the company says they won’t be responsible for lost content, while the system is still available to use on your own.
They did not go that route, Google deleted many millions of Google+ accounts, hundreds of millions of pages people had made written statements on, many of them contained clues of terrorism, even if the authors don‘t know what they may have seen, if they wrote something that describes some kind of thing that they did not understand at the time, that is sometimes eye-witness of terrorism, and was written down to preserve it.
So that happened. I moved the content here to Tumblr at the time in 2019, arranged it the best I could in this format here on Tumblr, which is a different format, the information does not present the same way it did on Google+, but the information remains consistent as the original posting.
That Google+ account was was not the first time I lost information there.
This Tumblr account is the second one I have made, the other one was deleted by the local sheriff who told me that help was on the way, but the account needed to be deleted so that others would not get any ideas about doing terror based on what I had written in the previous account. I knew that what the sheriff said about all of that was bullshit, I tried to defend, but was overpowered that day, and the sheriff was able to delete the previous Tumblr account from my computer many years ago, many years before starting that new attempt to write things down as I saw them happen around me.
In 2014 I was too scared to say the words: “nitrous oxide” online, and used the words “anesthetic gas” in place of that. I was too scared to say: “Terrorists are armed with swords” and I did not mention any swords for a long time.
The use of those two statements around here has always been risky thing to say, so I refrained from risk, relied on other verbiage, words that should have brought interest of national security personnel a long time ago.
no help has ever come to Oregon.
no one has ever asked me one single question about any of what is contained here on Tumblr with exception of “Three Bozos” I wrote about on the day the “Three Bozos” came to my home pretending to be FBI, US Army, and Secret Service representatives. Those guys did ask some questions. It turned out that the “Three Bozos” were really three music industry professionals who decided to come to kill me on their way home from the Winter NAMM music industry convention and trade show, 2019 I think it was, January maybe. It was cold and snowing when they came to my home that day.
Those guys did not make it home, were killed in defense when they attacked while pretending to be something that they were not.
If you read what is presented at this account from the beginning, you’ll see that I have gone from being too scared to say: “terrorists are armed with nitrous oxide” to not afraid of saying: “I killed the son of bitch in defense in my home when I cut the fucker’s head off with my trusty fingernail clipper”
That is a substantial change in expression.
A few days ago, I sent a note to the White House to ask that some help be sent to Oregon. The only outcome has been a heap of dead terror soldier assassins.
no help has come, no one has tried to contact me in any way, and there is a small airplane buzzing over my house right now low and slow, as the often do when I write terror reports on Tumblr. It’s 4:52 pm as the airplane passed by. They often drop loads of poison gasses when they fly over, to prime the area for a ground assault that follows the flyovers.
If you read this account and are someone who can help, is interested in real terrorism, then know that I learn over time, and newer information is better than the older information posted here.
There are about 860 posts here, daily accounts of some kind of terrorism explanation, some are local terror oriented, some are global terror oriented.
There are no posts on this account that are not about terorism in some way, and all of the posts made here are done so that I can get some help to come to Oregon, so that I can be freed of the captivity imposed on me by the enormous terror army that surrounds my home, and keeps me captive inside my home. When I go outside, terrorists attack with weapons, and I must defend or be killed by them.
Please send help.
=============
5:58 pm:
Texas is trending on Twitter:
Is it really doing a “hell freezes over tour?”
Are the Eagles back together again?
Is Joe Walsh in the line-up, and if so, can a school bus travel at 55 mph on the ice in a snow blizzard?
Ohh... the was Eddie, my bad ... Joe Walsh does not drive, but he has a car that can do 185.
If there is a storm a brewin, then all of the Twitter news about is making a ton of command orders for Canadian terror soldiers to go there, and take advantage of the weather, with help from their power company comrades.
These kinds of weather catastrophes are exactly what the “Ivanka Trump Opportunity Zones” are about.
“But the Texas power is not part of the regular power” you say. I say that everyone who works at the Texas power grid is a former employee of one of the Rocky Mountain Power Company family of global terror cells.
It’s a “When Hell Freezes Over Ivanka Trump Oportunity Zone” where many victims will be murdered, the Canadians will show up in the form of FEMA government help, bringing food, fuel, generators, clothing and blankets, for the terror army to use after the terror army kills the survivors. That is what FEMA is for. They are not even a real agency, they are part of George W. Bush’s cabinet. The Department of Homeland Security is the parent terror cell the oversee’s the activities of the FEMA terror cell, same as DHS does for TSA, Air Traffic Control, CPB, and now that other new addition, the Center for Disease Control and many more such bullshit fake agencies that are really terror cells installed under George W. Bush, who is dead, but they claim he still lives in Texas.
Bush “appointed” the DHS secretaries and other management officials in the same way that Presidential Cabinet Members are selected, he points at a few close friends, and gives them a budget and an office building to work from, and authorities that include freedom to form sub-ordinate agencies under the DHS umbrella.
It’s all bullshit, all of the DHS sub agencies are traveling killing machines.
Those agencies do the work they do out in the open, in the light, in doing so, they arrange a lot of open doors, passage ways, avenues of access to where emergencies are taking place, where large populations of people are weakened by the weather, and become easy targets to those who the open door of access is meant for. The victims are actually drawn into the places where they will be killed. The terrorists are “Christian Shepherds”, they guide the victims to their deaths. FEMA brings the equipment and supplies, other Canadian terror soldiers play role of victims in need, they blend right in with the real victims, are in the same places at the same time, FEMA creates the window of opportunity, and those Canadians do the attack, capture the real victims, while also taking control and possession of all of the aid packages that were brought. The Canadians just continue to look as though they are the real victims, they go occupy the homes of the victims, while offering “assistance” to others in the neighborhood, for more killing and capturing. Meanwhile, FEMA does news conference on Twitter to draw public attention away from the murders, and into other controlled environments while simultaneously providing marching orders to the Canadians who are doing the Ivanka Trump Opportunity Zone terror mass murder on the back of a freezing snow blizzard, hurricane, or tornado.
It’s all fucked up.
Let me draw some attention to a time when Hurricane Katrina went through that same area, especially the news story about a group of well equipped Canadian rescue team of a few dozen people. They “Happened to be in the neighborhood” and were able to “find the radio broadcast tower to repair it and rigged it to work with some car batteries when the storm had knocked out the broadcast antenna”
The Canadian bastards were Johnny on the Spot, They were at the emergency far before any other US based emergency personnel were even deployed to the area, and they came all the way from Canada to Texas, and still were there first.
That story is one of the most blatantly announced orders to do terror mass murder set-up work I have ever seen. It served as instructions to sabotage the broadcasting capabilities, including cellular towers in the area in the aftermath of Katrina, to make sure no one there could get any real help to come. Instead all of the citizens were rounded up for easy take out at the stadium.
Hell Freezes Over Tour, starring “The Eagles”.
Happening now, commanded to happen on Twitter from network Verified Accounts.
https://twitter.com/JosinaAnderson/status/1362022720037355520

====================================
6:49 pm:
Message for you sir:
For Joe, and the US national security that fails to perform their duties:
ED, by the Cult.
https://www.youtube.com/watch?v=uZkkAOydxT8
youtube
======================================
7:13 pm:
It’s time to start to see things as they are, not the way the story on the news tells you it is.
Real quick:
“How can you tell that reports from government about gun legislation is fake?”
You know it’s fake because it’s the same fucking story told over and over and over again. That right there is enough to view these kinds of stories as established terror marching orders that work good every time they are presented.
“What is really going on?”
There is a ton of terror orders in Trudeau’s tweet.
In association with FEMA in Texas at the “Hell Freezes Over Tour”, the story serves as a way to say what kind of hardware Trudeau is expecting to be brought to him afterwords.
In a broader sense, it’s about people, not guns. It’s about a priority to remove the kind of people who carry guns. That could be permanent removal, or in association with Hell Freezes Over in Texas, is a call for a distraction to be rolled out by news media, where the news media creates a situation that makes an excuse for the public safety to be drawn to a controlled environment away from a planned attack zone. That can be done to protect Royal Canadian Police in Texas who are disguised as local police, so they can do marching orders remotely to the Canadian terror army at an attack zone not far away, but far enough that no one is interested in what the police are really doing as they pretend to do whatever the media distraction is.
Also, that kind of story at a weather event where desperate people may be competing for life saving supplies, makes for “Fractal View” of a situation within a situation, where some Canadian terror soldiers do a “gun violence” scenario, something poignant, where people are said to be fighting over the life saving supplies, and kill each other. Of course the so called gun violence is not what really happened, it’s just a handy way of publicly disposing of some US Citizen victims with a news story that makes a profit because it sell advertising when people watch the “Heartfelt Saga” of tragedy within other tragedy.
The so called gun legislation news stories stopped being about gun legislation about thirty years ago. It’s all terror command marching orders now. Terror soldiers simply take that Trudeau ball, and run with it in any direction that suits the terror army at the Hell Freezes Over Ivanka Trump Opportunity Zone terror event. The way that works, is as a theme, where as long as the terror soldiers stay to the details described in the Tweeted theme, it automatically informs the people at FEMA that such events are part of the Hell Freezes Over event, no words need to be spoken, all of Trudeau’s FEMA people and RCMP are made aware of the theme, so, they all know to assist rather than hinder the gun violence theme because the State Police are all Royal Canadian Mounted Police disguised as state police, and took over the police stations a long time ago. That, and the power company is also filled with Canadian terror army soldiers, so, we already know that those guys are all over the place, doing what we have already been informed that they are doing, in trucks, with men and equipment everywhere throughout the state, so when you see them around, they are supposed to be there, are expected, is nothing out of the ordinary, don’t appear to be the SDA Canadian Canniball terror soldiers that they truly are, and that situation puts thousands of innocent looking terror soldiers all over the place for doing activities that range from murder, to cutting power for an assist to other terror cells, to carting away dead and captured victims, to bringing such victims to a rail road for mass processing, to doing evac work for injured terror soldiers, and much more dependent on local conditions at the Hell Freezes Over attack at the US Eagles Power Concert in the Lone Star State of Texas, where we already were told that their power grid is separate, isolated, “cut off” from other national power grids.
https://twitter.com/JustinTrudeau/status/1362167722352738308
Terror bastards disabled my save button again, had to post this part twice, is difficult and time consuming to have to compete live with the terror hackers at Google and Centurylink.
==================
8:01 pm:
The hacking was accompanied by the sound of police siren at the same time when the ‘Save” button had been disabled, would not work, had to start over. The siren was on Russell Road, sounded as if the police car had parked at Chapman‘s terror cell at 3701 Russell Road, a Josephine County Courts terror cell.
This is a good time to mention that another terror assassin came into my home to kill me last night, there was a fight with weapons in my kitchen, I don‘t remember much, just that there was someone in my laundry room, and we fought in the kitchen. Later, information I have is that Honorable Judge Patrick Wolke was killed when his nitrous oxide tank ignited from my Bic Lighter, and he launched into orbit, from where he was hiding to attack me at 520 Jackpine, and he came back down at the Freeberg terror cell at 535 Jackpine. I witnessed some of that, not all of it. I saw the part where someone landed at Freeberg’s after hearing the sound of an ignited nitrous oxide tank. They sound like internal combustion engines, and sometimes like jet motors, and sometimes like a “Whoosh” sort of wind sound. Wolke made a internal combustion sound last night.
That makes two county judges that have been killed in defense at my home, in addition to most of the “Former Trump Cabinet”, The Vice President of USA Mike Pence, the Duke and Duchess of Sussex Harry and Megan Windsor, and Prince Charles w/at least one Queen‘s Guard in the past few years, to name a few of the more important terror soldier leaders.
The other Judge was Honorable Lindy Baker, who had a surgically altered kidnapped US Citizen victim in the trunk of her car the day she was killed at AM/PM Luke’s Arco gas station on Terry Ln next to the Walmart and near the Fred Meyer stores, caddy wompass from Starbuck’s, and Winco Foods.
======
this Tweet from ABC news Verified Account on Twitter, and some others on Twitter today featuring people wearing blankets as they are walking, are communication from ABC and Google/Twitter to say they have not heard from Patrick Wolke, Josphine County Circuit Court Judge, and are requesting that he make contact to places he is supposed to make contact after trying to kill me at my house. There are at least two other Tweets featuring the blankets, they represent the Robe worn by a judge.
This is a good place to mention that those two terror soldiers that ambushed me at my driveway the other day and were in my house after the ambush happened are suspected of being Oregon State Police Officers Jeffrey Prouix and Tanya Henderson. Both are dead now.
https://twitter.com/ABC/status/1362163051605200896

So, what can be learned from this account over just the past three or four days is that if someone reports terrorism to the White House, and the report explains that the police, and the 911 Emergency Phone service and more is all hijacked by a vast terror army that is armed with poison gasses, those people who receive the report at the White House will send assassins to the home of the persons who make such reports of terrorism.
The question is: “Are the people at the White House terrorists who knowingly sent assassins to kill me?
Or,
“Are the people at the White House incompetent, unable to read the report details, and knowingly sent assassins to kill me?“
Or,
“Are the people at the White House incompetent, unable to understand the details of a failed 911 Emergency Phone service, and sent assassins to kill me by virtue of failure to read the details of the reported terrorism and understand what the report said?”
The report is a comprehensive report of detailed terrorism, and is a cry for help on a personal level primarily, and a national level secondary, and a global level ultimately.
Read this account over the past four days to find the report and the response in writing that was sent to me by the White House, unless of course the White deleted that entry, then, you won‘t be able to see it if that happened.

There is a copy of the receipt I was sent.
The White House received the report of terrorism.
The White House failed to respond to the details of the reported terrorism in an appropriate way.
That is Your nation that was not protected, and Mine too.
Joseph Biden is US President.
========================
8:55 pm:
This is the text of the reported terrorism sent February 13, 2021 to WhiteHouse.gov in absence of other means of reaching help:
“Please send help. The state of Oregon has been hijacked by terror army from Canada, they use poison gasses to overpower victims, capture and torture them, then kill & replace them with imposters. There are many hundreds of thousands of them, and they have been murdering the population for more than twenty years. There are more than 800 pages of explanations at the link provided, eye-witness accounts of actual terror mass murder happening in Oregon and all over the west coast of USA. Please study the information carefully, as the terror is very sophisticated. 911 Emergency phone service is not available, it’s controlled and operated by the terror army, they only send assassins when people call for help. Please send US Military. https://stone-man-warrior.tumblr.com https://stone-man-warrior.tumblr.com/archive”
=====================================
9:06 pm:
At Whitehouse.gov when you make contact there, you must fill out some form questions such as name and address, email, gender, other contact information, and you get 2000 characters of space to say your thing to Whitehouse.gov.
There is a field in the form marked “Pronoun“ and some choices: “He/Him” and “She/Her” are two of the choices among many.
I have no idea why those are necessary. I did not participate in White House Pronoun Terror Comm at the Contact page.
If it’s not for special treatment, not to say “Club Affiliation“, then what purpose does “He/Him” or “She/Her” have when contacting White House?
This from Wikipedia:
“Pronoun”
“In linguistics and grammar, a pronoun (abbreviated PRO) is a word that substitutes for a noun or noun phrase. It is a particular case of a pro-form. Pronouns have traditionally been regarded as one of the parts of speech, but some modern theorists would not consider them to form a single class, in view of the variety of functions they perform cross-linguistically. An example of a pronoun is "you", which is both plural and singular. Subtypes include personal and possessive pronouns, reflexive and reciprocal pronouns, demonstrative pronouns, relative and interrogative pronouns, and indefinite pronouns.”
===============================================
9:51 pm:
In other news:
I do believe there are people interested in stopping the terrorism reported, that is good news. The bad news is such people are not likely to be mentally prepared to accept the factual details in order to pursue the terrorism in “from the top, and downward” way that is required to stop it.
That said, I do want to protect such people so they can help me to help them to stay alive, and that is the reason for me to select this twitter piece to inform:
The stuff they are saying the wasps are going to protect is artifacts and fabric “upholstery”, “The Cloth”, so, we have: “Up Hold Story” “There must be some kind of holdup” established terror communication, a SAG specific one, can go in any direction from a theft of something to an activity taking to long, to “Shiny Object on High Mountain” where high level terror leaders are exposed to unflattering light.
Then, the artifacts are factual things, but here I think it goes towards “FNART” French North American Republic Territory” factual exposure of knowledge, the new communist nation that is planned to replace Canada, USA, and Mexico very soon if the terror take over is not stopped.
Globally, it’s reduced to “ART”, American Republic Territory” for discussion about places the will be taken by terror soldiers other than the French Canadian ones from Quebec, the ones who are taking USA over, so, conceivably, China could one day become “American Republic Territory” if the Hong Kong British terror army is successful there at taking China with same means the Canadians are taking USA.
So, why this is important to consider is that it’s about the wasps. In SDA terror, the way to get rid of the wasps once the moth’s are all gone, is to smear some pork gravy, broth, pork juice on someone, and send them in there, then, all of the wasps will be removed easily because they will swarm the pork. That person just needs to run out of the mansion covered with pork and wasps to get the wasps out of the mansion after the months are gone.
It’s a Dutch thing done by Canadian SDA, where that little piece of pork in the Van Camp’s Pork & Beans works like magic at a picnic, you just put that on a plate about fifty feet away from the picnic, all the wasps and bees go there, and don‘t bother the people at the picnic.
The Tweet covers a lot of ground, and I did not do a complete decode on it. It also says a distraction is to be done somewhere, the Tweets never say where or when events are to take place because the Tweets are all bullshit about stuff the never happened, but are useful later on, can be re-run in the future, the locations and times are most likely arranged by news media network leadership offices. The re-run tweets tell terror soldiers what the play is, like a football game play is called by the quarterback, and all of the team already knows how to run the different plays. They need to know when and where from a different command chain, I suspect the email from music industry promotions is part of that, but I have not figured out how to find locations and dates yet anywhere I have looked for them.
So far, the way it looks is the terror army just moves from city to city, murdering and replacing with assistance from state police, and that is mostly where location and time of particular events are announced, on a local level. The Twitter advises of challenges, or special circumstance to those kinds of city wide takeovers.
Exceptions to that are events like the concert 91 where that was a big production, it was practiced for here in Grants Pass with many thousands of terror operatives who came from Universal Studios to do dress rehearsal here, the whole town was a practice stage for a few days. I have explained much about what I saw in the days before that happened in a number of different entries on this account.
I just wanted to point out not to be wasp food.
Also, that photo features a fresh cut lawn, where the “napp” is going in two directions on the fresh cut lawn, so, the obvious read is “kidnap child trafficking laundry”, maybe more to it than that, but as you can see, a single Tweet is worth more than a thousand words, it’s value is measured in babies.
https://twitter.com/CNN/status/1362221636339044353

The Top Down approach to stopping the terror take over cannot happen while Twitter remains active, only dead national security people will result until Twitter is taken offline permanently. The reason for that is the the people at the top, are the leadership of the national security at a official level, while those same people are the leadership of the terror army. The national security are commanded publicly by the same people who kill them in shadows. Twitter is such a shadow.
The terror army will always know exactly where the national security people are at before they arrive there. It’s a losing proposition when millions of terror soldiers have access to twitter, where the terror commands are coming from.
First thing, Twitter has to come down off of the internet, there is no other way.
That will slow down the advance of all the terror activity, and save the lives of the ones doing the investigations, and eventually arrests, so the leadership of the terror army can be safely transported to Easter Island, and dropped off there to fend for themselves.
There will be too many to keep in jails and prisons, Easter Island is a reasonable answer to where the bastards should be taken. They cannot hurt anyone from there, and escape is not going to be easy.
===============================
10:50 pm:
At Whitehouse.gov I filled out all of the necessary questions about who I am, where I live and how to reach me. We know they were able to reach me with the email once, and I included my phone number but no calls have come into my phone. The bill is paid, the phone is not broken, it’s the system it runs on the does not work. Only select people can make a phone call in Oregon, and when calls are made, there is someone who listens to all of the calls. The phone numbers a person calls has to be among approved numbers, and my phone only reaches assassins, there is no way for me to use the phone I pay the service fee for to reach anyone, and mostly the calls I get are ones that don’t leave a message, and I don‘t know who called or why. Calls tend to come from Brookings and Coos Bay, Reedsport, Eugene Oregon, and cities along the interstate 5.
I am still waiting for the phone to ring to talk to someone about the terrorism.
If someone did call the number I provided, and thinks they spoke with me, the person who sent to request for help, then they were fooled by the terror army that controls the hijacked phone systems.
================================
February 18, 2021: 12:35 pm:
“There Must Be Some Kind of Holdup”
It’s established SAG specific terror communication statement.
This is also in association to “Ted Cruz Goes to Cancun“ on Twitter today, where that part is a “Suspense Thriller” while his airplane is in the air, is suspended, provides a range of timing to work withing for some kind of “Crucial” terror event playing out right now.
Things to consider about the Dolly Parton Holdup:
The Pedestal is an “Alter”.
“Dolly Parton“ means: “Bring Hand Trucks, we are carting this stuff away, to part the owner from the belongings” = Dolly Parton.
Her breasts sometimes are the hand trucks, you handle them, that is part of the Holdup.
Her Braziers are made by “Acme Tool & Die”, have three hasps made of iron.
Acme Tool & Die offers hasps made of Titanium, Dolly prefers Iron.
There is a substantial “Underbust” where ever Dolly Parton goes.
The Tweet says “Tennessee”, so that means “Penguin”, “Tennessee Tuxedo”, a custom tailored suit made special for the person where the Hand Trucks and Dolly’s where brought for parting with belongings.
“Penguins” are “Partners”, surgically altered kidnapped citizens forced to undergo horrible experimental surgical procedures. They are special ordered by SAG members, who specify details such as arm length, witch directions elbows, knees, and ankles bend, location of re-attached hands. The hands are often re-attached at the shoulder after the victims arms are removes, are called “flippers” and that is where the term “Penguin” comes from.
The tweeted “Holdup” with “Ted Crucial Suspense” is likely a “Two-Pointer” where the comm serves as orders for terror happening in Texas to kill & replace black people with other black people kidnapped from DR. Congo to put them in Texas as a controlled voter base, while removing the locals, collecting the babies of the locals, and making surgically altered slave people from them, and also to train the children as disposable terror soldiers. The Two-Pointer is also another location on a smaller fractal view, most likely at my house where some asshole is going to try to land a nasa Perseverance Rover on my roof, a “Trojan Horse” sort of three dimensional package.
That nasa Perseverance part is orders from Joe Biden to send assassins to my house to kill me, that were presented on Twitter yesterday or the day before with a news story that said Joe was going to Cancel as trip that was planned for Thursday, that’s today.
I hear it’s nice in Cancun this time of year.
https://twitter.com/ABC/status/1362473723983499271
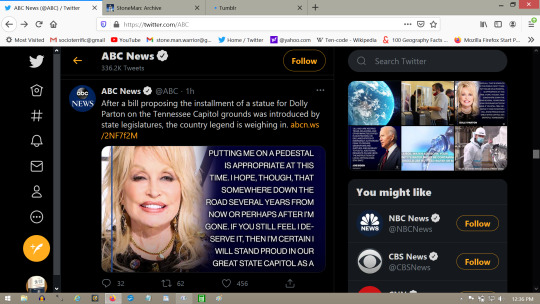
The two stories are the same terror commands.
https://twitter.com/ABC/status/1362473678194290690

https://www.youtube.com/watch?v=cs6iMjv2MXg
youtube
This is Johnny, a US Military serviceman who was sent overseas, to become a Partner, because only the strongest, healthiest specimens survive the brutality of the Penguin Partner Production sponsored by the US Government that was hijacked by Screen Actor Guild when Ronald Reagan took the White House.

Johnny is part way through a five year surgical alteration program, will be a pet kept in a kennel in Hollywood or beneath Nancy Sinatra’s mansion in Pacific Palisades. They do the work on Johnny beneath the Veterans Administration Hospital at Oregon Health Science University in Portland Oregon, nine floors below ground level.
This is Kyle, he is part way through his five year surgical transformation, will become a specialized terror assassin when they are done training him after the alteration is complete. Disposable bomb carrier. Just train him, and send him in, there are many thousands of Kyle’s being altered right now in Medford Oregon.

Don’t forget to subscribe to netfix to support what SAG does for Johnny and Kyle.
==================
February 18, 2021: 1:48 pm:
Read today’s this Tumblr post through a couple of times, then watch this Psaki White House Press Secretary terror commands.
Keep in mind that the Psaki video was scripted and filmed way before 2008, avd was presented on Beta Twitter at that time, the same video that was presented again on February 16, 2021.
Do your own decoding work.
Listen to the music. I ask that you pay attention to BBC news video productions made over the past twenty years or so, and listen for that same style of music. What that is, is called “aboriginal music from down under”. You won‘t have any problems finding hundreds of BBC news videos featuring the aboriginal style background music. You can find dozens of them just associated to Karen Pence White House Video Productions too. It means something specific, as I recall, it means “Seventh Day Adventist Busy Bee’s” is a “Bee in your Bonnet” terror communication, where the Bee is planted in the SDA terror soldiers “Bonnet” as a set of ideas to work with, for brainstorming, is the way I remember what that aboriginal background music is there for, clearly, there is a close connection between BBC news production video services, and White House Video Production Services that can be determined just with that kind of music in the videos the two producers make.
Search YouTube for “Bee in Your Bonnet” to find hundreds of examples of SDA specific terror ways, communication details, learn how they think, and other observations.
https://twitter.com/PressSec/status/1361788324042706944

====================================
Psaki = P Saki = PJack + Saki
PJack is a character from Teken, a video game. He is a US Military Fighter in the game.
Saki, is a Japanese alcoholic beverage best served warm.
“Chop-a-knees”
The Vapors ... is not Pineapple pizza, “That’s Gross”. Psaki prefers onions and peppers.
https://www.youtube.com/watch?v=7tbobaz8nn4
youtube
“Corona Virus” already happened in Oregon before Twitter was publicly released. They used the same terror command pre-packaged attack orders then as are being used now. They called it Beta Twitter back then, was available in Oregon, and Donald Trump was US President, and Joe Biden was elected after, just the same as now. As I recall, Joe gets killed, and Harris becomes US President, but my memory is clouded with too much blood and horror that took place, when the population was all slaughtered.
The result in Oregon is all of the entire population was murdered, and replaced with Canadians.
Beta Twitter. It already happened on fast forward, about ten years worth of what we are seeing now happened within about two years. The Beta Twitter time line moved along much faster than the one we see today.
Jen Psaki, if you could find her, is at least fifteen years older than is shown in that video, and, if you could find her and speak to her, she would make Ivanka Trump seem normal in comparison.
Psaki is a British Still SDA.
Ivanka is a British Still daughter of Pope John Paul II.
“British Still” is a customized education and upbringing isolated from mainstream education, is completely different, backwards, upside down, inside out education and upbringing.
This video may be the only publicly available example of how a British Still education is done.
Watch the video, put Ivanka Trump in the nigel position, to get a better idea of what is happening there.
See that the video was made in 1979 and features three-dee gaming glasses back then.
https://www.youtube.com/watch?v=mfsYSPCNWCw
youtube
====================
February 18, 2021: 2:44 pm:
They are pirates. The Christian religion has been fake since Day 1, when pirates attacked and took over Greece, destroyed the Parthenon, and all of that whole city, took over the knowledge that had been archived by the Greeks, changed some of that around, took possession of the Library at Alexandria, and have been on a mass murder crusade to take over the world ever since.
Christianity is what happens when ruthless, uneducated murderous blood thirsty heathens who do not want to work for producing their own sustenance, but will kill their own mother in order to take her clothes to stay warm, when those people run across educated, smart people who know how to think and can do math, then take the smart people captive, harness the knowledge they gained, to turn the knowledge around backwards as weapon, a weapon the produces easy to kill victims for more pirating. The religion part is what happened when the pirates took slaves from China, and India, places that have very old spiritual ways they use for understanding how humans fit into the universe, and thus how to survive on earth peacefully. Those slaves taught the pirates about The Tao Te Ching, and The Damapada, ways of surviving, books about ways to think about harmony between self, earth, and other people.
But the Christians took that information and turned it all around backwards, they took away the importance of the self, and exchanged the individual self for an invisible all controlling, all powerful being who will choose for you about your path, and your destiny.
They are all pirates. The religion was fake on the day when Marcus raped Jesus’ Ol’ Lady, and they nailed Jesus to a sail on a boat, called it a Crucifix, and set sail using Jesus to catch wind, to move the boat forward, to catch more Jesus’. to nail to the mast, to catch wind, to move the boat forward, to catch more Jesus’, to nail to the mast... for two-thousand years so far, and no one has noticed.

That is Ivanka Trump’s real father. Pope John Paul II.
He is a pirate.
There, he is celebrating something they call “The Beatatude”. Those “surfboards” there represent free people under control of Christianity, it’s a family of three, they are captive within the “Christianity Beatatude” as Church Goers.
Pope John Paul II fathered many thousands of children, all of them are British Still educated special operatives, like Ivanka Trump is. They are sprinkled around the world in key government and corporate leadership positions and non-leadership positions. Think about such people in charge at the WH Mail Room, or as a receptionist at Exxon/Mobil, or maybe as County Clerk in your county, or perhaps as the person who handles the Probate at the local courthouse, such as
John Cahill is at the Clark County Courthouse in Nevada.

What could go wrong?
1 note
·
View note
Text
Writing meme - tagged by warriormaggie
Is there a snack you like to eat while writing? No one particular snack. Cereal and tea is probably the most common combination of things I munch on when at my computer, followed by tea and cookies... I like tea.
What time of day do you usually write? Usually late in the evening. On weekends, however (if I don't have other obligations that day) I make a strenuous effort to get at least some writing in before the clock hits noon. If I can get started, I'm more likely to continue, and more likely to pick it up again later in the day.
If writing at work (see below) it's usually right before the end of my shift, when everything else is out of the way and I'm getting out of the 'work' headspace.
Where do you write? At my computer -- I have a desktop, not a laptop, so it's not portable, lol. As referenced above, I also occasionally jot down notes or snatches of prose at work, but that's also a desktop. I don't really like laptops.
How often do you write a new fic? Tricky question. Depends on if it's a multipart or a oneshot. At the moment, I'm putting out new chapters or a multipart approximately every week, but that’s an unusually fast pace for me -- one chapter every two weeks is more normal. Oneshots can either take more time or less depending on their length. I would say that I fairly consistently produce at least one new thing a month, unless something major is going on in my life (major illness, new job, etc.)
Do you listen to music while you write? Yes. I have a playlist of instrumental/background/non-English songs that I use for writing. Highly stimulating or complex vocal songs tend to be distracting.
Paper or laptop? What is with this meme's prejudice against desktop computers?
Do you have a special pre-writing ritual? Not especially. Open the document, re-read the last few pages, re-read my notes, browse Tumblr for an hour or two... functionally identical to days when I don't write, really.
What do you do to get into the writing? Re-reading my own writing helps a lot, as does either chatting with my friends about writing or re-reading the chats. I have to admit, when I'm actually chatting to others about writing I tend to be more focused on what I'm saying than on what they're saying, but re-reading the chats later allows me to pay more attention to their input, which can be very inspiring.
What do you always have near the place you write? Water, ibuprofen, chapstick... cats.
Do you have a reward system for word counts? Nope. Honestly the only reward system I have is user comments.
Is there anything else about your writing process your readers don’t know? For any significant conversations I always write the dialogue first, and separately, in script format. This makes it a lot easier to concentrate on the logical flow of point A to point B in the conversation, to keep the rhythm going and make sure the voices are right for the characters. This is the part that I can do at work. Then when I get home and get to writing, I paste in the script sections and add punctuation and action tags. I think this helps my speaking sections to be snappy and coherent.
5 notes
·
View notes
Link
Choice for consumers compels fair treatment by corporations. When people can easily move to a competitor, it creates a natural market dynamic coercing a business to act right. When we can’t, other regulations just leave us trapped with a pig in a fresh coat of lipstick.
That’s why as the FTC considers how many billions to fine Facebook or which executives to stick with personal liability or whether to go full-tilt and break up the company, I implore it to consider the root of how Facebook gets away with abusing user privacy: there’s no simple way to switch to an alternative.
If Facebook users are fed up with the surveillance, security breaches, false news, or hatred, there’s no western general purpose social network with scale for them to join. Twitter is for short-form public content, Snapchat is for ephemeral communication. Tumblr is neglected. Google+ is dead. Instagram is owned by Facebook. And the rest are either Chinese, single-purpose, or tiny.
No, I don’t expect the FTC to launch its own “Fedbook” social network. But what it can do is pave an escape route from Facebook so worthy alternatives become viable options. That’s why the FTC must require Facebook offer truly interoperable data portability for the social graph.
In other words, the government should pass regulations forcing Facebook to let you export your friend list to other social networks in a privacy-safe way. This would allow you to connect with or follow those people elsewhere so you could leave Facebook without losing touch with your friends. The increased threat of people ditching Facebook for competitors would create a much stronger incentive to protect users and society.
The slate of potential regulations for Facebook currently being discussed by the FTC’s heads include a $3 billion to $5 billion fine or greater, holding Facebook CEO personally liable for violations of an FTC consent decree, creating new privacy and compliance positions including one held by executive that could be filled by Zuckerberg, creating an independent oversight committee to review privacy and product decisions, accordng to the New York Times and Washington Post. More extreme measures like restricting how Facebook collects and uses data for ad targeting, blocking future acquisitions, or breaking up the company are still possible but seemingly less likely.
Facebook co-founder Chris Hughes (right) recently wrote a scathing call to break up Facebook.
Breaking apart Facebook is a tantalizing punishment for the company’s wrongdoings. Still, I somewhat agree with Zuckerberg’s response to co-founder Chris Hughes’ call to split up the company, which he said “isn’t going to do anything to help” directly fix Facebook’s privacy or misinformation issues. Given Facebook likely wouldn’t try to make more acquisitions of big social networks under all this scrutiny, it’d benefit from voluntarily pledging not to attempt these buys for at least three to five years. Otherwise, regulators could impose that ban, which might be more politically attainable with fewer messy downstream effects,
Yet without this data portability regulation, Facebook can pay a fine and go back to business as usual. It can accept additional privacy oversight without fundamentally changing its product. It can become liable for upholding the bare minimum letter of the law while still breaking the spirit. And even if it was broken up, users still couldn’t switch from Facebook to Instagram, or from Instagram and WhatsApp to somewhere new.
Facebook Kills Competition With User Lock-In
When faced with competition in the past, Facebook has snapped into action improving itself. Fearing Google+ in 2011, Zuckerberg vowed “Carthage must be destroyed” and the company scrambled to launch Messenger, the Timeline profile, Graph Search, photo improvements and more. After realizing the importance of mobile in 2012, Facebook redesigned its app, reorganized its teams, and demanded employees carry Android phones for “dogfooding” testing. And when Snapchat was still rapidly growing into a rival, Facebook cloned its Stories and is now adopting the philosophy of ephemerality.
Mark Zuckerberg visualizes his social graph at a Facebook conference
Each time Facebook felt threatened, it was spurred to improve its product for consumers. But once it had defeated its competitors, muted their growth, or confined them to a niche purpose, Facebook’s privacy policies worsened. Anti-trust scholar Dina Srinivasan explains this in her summary of her paper “The Anti-Trust Case Against Facebook”:
“When dozens of companies competed in an attempt to win market share, and all competing products were priced at zero—privacy quickly emerged as a key differentiator. When Facebook entered the market it specifically promised users: “We do not and will not use cookies to collect private information from any user.” Competition didn’t only restrain Facebook’s ability to track users. It restrained every social network from trying to engage in this behavior . . . the exit of competition greenlit a change in conduct by the sole surviving firm. By early 2014, dozens of rivals that initially competed with Facebook had effectively exited the market. In June of 2014, rival Google announced it would shut down its competitive social network, ceding the social network market to Facebook.
For Facebook, the network effects of more than a billion users on a closed-communications protocol further locked in the market in its favor. These circumstances—the exit of competition and the lock-in of consumers—finally allowed Facebook to get consumers to agree to something they had resisted from the beginning. Almost simultaneous with Google’s exit, Facebook announced (also in June of 2014) that it would begin to track users’ behavior on websites and apps across the Internet and use the data gleaned from such surveillance to target and influence consumers. Shortly thereafter, it started tracking non-users too. It uses the “like” buttons and other software licenses to do so.”
This is why the FTC must seek regulation that not only punishes Facebook for wrongdoings, but that lets consumers do the same. Users can punch holes in Facebook by leaving, both depriving it of ad revenue and reducing its network effect for others. Empowering them with the ability to take their friend list with them gives users a taller seat at the table. I’m calling for what University Of Chicago professors Luigi Zingales and Guy Rolnik termed a Social Data Portability Act.
Luckily, Facebook already has a framework for this data portability through a feature called Find Friends. You connect your Facebook account to another app, and you can find your Facebook friends who are already on that app.
But the problem is that in the past, Facebook has repeatedly blocked competitors from using Find Friends. That includes cutting off Twitter, Vine, Voxer, and MessageMe, while Phhhoto was blocked from letting you find your Instagram friends…six months before Instagram copied Phhhoto’s core back-and-forth GIF feature and named it Boomerang. Then there’s the issue that you need an active Facebook account to use Find Friends. That nullifies its utility as a way to bring your social graph with you when you leave Facebook.
Facebook’s “Find Friends” feature used to let Twitter users follow their Facebook friends, but Facebook later cut off access for competitors including Twitter and Vine seen here
The social network does offer a way to “Download Your Information” which is helpful for exporting photos, status updates, messages, and other data about you. Yet the friend list can only be exported as a text list of names in HTML or JSON format. Names aren’t linked to their corresponding Facebook profiles or any unique identifier, so there’s no way to find your friend John Smith amongst everyone with that name on another app. And less than 5 percent of my 2800 connections had used the little-known option to allow friends to export their email address. What about the big “Data Transfer Project” Facebook announced 10 months ago in partnership with Google, Twitter, and Microsoft to provide more portability? It’s released nothing so far, raising questions of whether it was vaporware designed to ward off regulators.
Essentially, this all means that Facebook provides zero portability for your friendships. That’s what regulators need to change. There’s already precedent for this. The Telecommunications Act of 1996 saw FCC require phone service carriers to allow customers to easily port their numbers to another carrier rather than having to be assigned a new number. If you think of a phone number as a method by which friends connect with you, it would be reasonable for regulators to declare that the modern equivalent — your social network friend connections — must be similarly portable.
How To Unchain Our Friendships
Facebook should be required to let you export a truly interoperable friend list that can be imported into other apps in a privacy-safe way.
To do that, Facebook should allow you to download a version of the list that feature hashed versions of the phone numbers and email addresses friends used to sign up. You wouldn’t be able to read that contact info or freely import and spam people. But Facebook could be required to share documentation teaching developers of other apps to build a feature that safely cross-checks the hashed numbers and email addresses against those of people who had signed up for their app. That developer wouldn’t be able to read the contact info from Facebook either, or store any useful data about people who hadn’t signed up for their app. But if the phone number or email address of someone in your exported Facebook friend list matched one of their users, they could offer to let you connect with or follow them.
This system would let you save your social graph, delete your Facebook account, and then find your friends on other apps without ever jeopardizing the privacy of their contact info. Users would no longer be locked into Facebook and could freely choose to move their friendships to whatever social network treats them best. And Facebook wouldn’t be able to block competitors from using it.
The result would much more closely align the goals of users, Facebook, and the regulators. Facebook wouldn’t merely be responsible to the government for technically complying with new fines, oversight, or liability. It would finally have to compete to provide the best social app rather than relying on its network effect to handcuff users to its service.
This same model of data portability regulation could be expanded to any app with over 1 billion users, or even 100 million users to ensure YouTube, Twitter, Snapchat, or Reddit couldn’t lock down users either. By only applying the rule to apps with a sufficiently large user base, the regulation wouldn’t hinder new startup entrants to the market and accidentally create a moat around well-funded incumbents like Facebook that can afford the engineering chore. Data portability regulation combined with a fine, liability, oversight, and a ban on future acquisitions of social networks could set Facebook straight without breaking it up.
Users have a lot of complaints about Facebook that go beyond strictly privacy. But their recourse is always limited because for many functions there’s nowhere else to go, and it’s too hard to go there. By fixing the latter, the FTC could stimulate the rise of Facebook alternatives so that users rather regulators can play king-maker.
from Social – TechCrunch https://tcrn.ch/2HiuMQt Original Content From: https://techcrunch.com
0 notes
Text
Friend portability is the must-have Facebook regulation
Choice for consumers compels fair treatment by corporations. When people can easily move to a competitor, it creates a natural market dynamic coercing a business to act right. When we can’t, other regulations just leave us trapped with a pig in a fresh coat of lipstick.
That’s why as the FTC considers how many billions to fine Facebook or which executives to stick with personal liability or whether to go full-tilt and break up the company, I implore it to consider the root of how Facebook gets away with abusing user privacy: there’s no simple way to switch to an alternative.
If Facebook users are fed up with the surveillance, security breaches, false news, or hatred, there’s no western general purpose social network with scale for them to join. Twitter is for short-form public content, Snapchat is for ephemeral communication. Tumblr is neglected. Google+ is dead. Instagram is owned by Facebook. And the rest are either Chinese, single-purpose, or tiny.
No, I don’t expect the FTC to launch its own “Fedbook” social network. But what it can do is pave an escape route from Facebook so worthy alternatives become viable options. That’s why the FTC must require Facebook offer truly interoperable data portability for the social graph.
In other words, the government should pass regulations forcing Facebook to let you export your friend list to other social networks in a privacy-safe way. This would allow you to connect with or follow those people elsewhere so you could leave Facebook without losing touch with your friends. The increased threat of people ditching Facebook for competitors would create a much stronger incentive to protect users and society.
The slate of potential regulations for Facebook currently being discussed by the FTC’s heads include a $3 billion to $5 billion fine or greater, holding Facebook CEO personally liable for violations of an FTC consent decree, creating new privacy and compliance positions including one held by executive that could be filled by Zuckerberg, creating an independent oversight committee to review privacy and product decisions, accordng to the New York Times and Washington Post. More extreme measures like restricting how Facebook collects and uses data for ad targeting, blocking future acquisitions, or breaking up the company are still possible but seemingly less likely.
Facebook co-founder Chris Hughes (right) recently wrote a scathing call to break up Facebook.
Breaking apart Facebook is a tantalizing punishment for the company’s wrongdoings. Still, I somewhat agree with Zuckerberg’s response to co-founder Chris Hughes’ call to split up the company, which he said “isn’t going to do anything to help” directly fix Facebook’s privacy or misinformation issues. Given Facebook likely wouldn’t try to make more acquisitions of big social networks under all this scrutiny, it’d benefit from voluntarily pledging not to attempt these buys for at least three to five years. Otherwise, regulators could impose that ban, which might be more politically attainable with fewer messy downstream effects,
Yet without this data portability regulation, Facebook can pay a fine and go back to business as usual. It can accept additional privacy oversight without fundamentally changing its product. It can become liable for upholding the bare minimum letter of the law while still breaking the spirit. And even if it was broken up, users still couldn’t switch from Facebook to Instagram, or from Instagram and WhatsApp to somewhere new.
Facebook Kills Competition With User Lock-In
When faced with competition in the past, Facebook has snapped into action improving itself. Fearing Google+ in 2011, Zuckerberg vowed “Carthage must be destroyed” and the company scrambled to launch Messenger, the Timeline profile, Graph Search, photo improvements and more. After realizing the importance of mobile in 2012, Facebook redesigned its app, reorganized its teams, and demanded employees carry Android phones for “dogfooding” testing. And when Snapchat was still rapidly growing into a rival, Facebook cloned its Stories and is now adopting the philosophy of ephemerality.
Mark Zuckerberg visualizes his social graph at a Facebook conference
Each time Facebook felt threatened, it was spurred to improve its product for consumers. But once it had defeated its competitors, muted their growth, or confined them to a niche purpose, Facebook’s privacy policies worsened. Anti-trust scholar Dina Srinivasan explains this in her summary of her paper “The Anti-Trust Case Against Facebook”:
“When dozens of companies competed in an attempt to win market share, and all competing products were priced at zero—privacy quickly emerged as a key differentiator. When Facebook entered the market it specifically promised users: “We do not and will not use cookies to collect private information from any user.” Competition didn’t only restrain Facebook’s ability to track users. It restrained every social network from trying to engage in this behavior . . . the exit of competition greenlit a change in conduct by the sole surviving firm. By early 2014, dozens of rivals that initially competed with Facebook had effectively exited the market. In June of 2014, rival Google announced it would shut down its competitive social network, ceding the social network market to Facebook.
For Facebook, the network effects of more than a billion users on a closed-communications protocol further locked in the market in its favor. These circumstances—the exit of competition and the lock-in of consumers—finally allowed Facebook to get consumers to agree to something they had resisted from the beginning. Almost simultaneous with Google’s exit, Facebook announced (also in June of 2014) that it would begin to track users’ behavior on websites and apps across the Internet and use the data gleaned from such surveillance to target and influence consumers. Shortly thereafter, it started tracking non-users too. It uses the “like” buttons and other software licenses to do so.”
This is why the FTC must seek regulation that not only punishes Facebook for wrongdoings, but that lets consumers do the same. Users can punch holes in Facebook by leaving, both depriving it of ad revenue and reducing its network effect for others. Empowering them with the ability to take their friend list with them gives users a taller seat at the table. I’m calling for what University Of Chicago professors Luigi Zingales and Guy Rolnik termed a Social Data Portability Act.
Luckily, Facebook already has a framework for this data portability through a feature called Find Friends. You connect your Facebook account to another app, and you can find your Facebook friends who are already on that app.
But the problem is that in the past, Facebook has repeatedly blocked competitors from using Find Friends. That includes cutting off Twitter, Vine, Voxer, and MessageMe, while Phhhoto was blocked from letting you find your Instagram friends…six months before Instagram copied Phhhoto’s core back-and-forth GIF feature and named it Boomerang. Then there’s the issue that you need an active Facebook account to use Find Friends. That nullifies its utility as a way to bring your social graph with you when you leave Facebook.
Facebook’s “Find Friends” feature used to let Twitter users follow their Facebook friends, but Facebook later cut off access for competitors including Twitter and Vine seen here
The social network does offer a way to “Download Your Information” which is helpful for exporting photos, status updates, messages, and other data about you. Yet the friend list can only be exported as a text list of names in HTML or JSON format. Names aren’t linked to their corresponding Facebook profiles or any unique identifier, so there’s no way to find your friend John Smith amongst everyone with that name on another app. And less than 5 percent of my 2800 connections had used the little-known option to allow friends to export their email address. What about the big “Data Transfer Project” Facebook announced 10 months ago in partnership with Google, Twitter, and Microsoft to provide more portability? It’s released nothing so far, raising questions of whether it was vaporware designed to ward off regulators.
Essentially, this all means that Facebook provides zero portability for your friendships. That’s what regulators need to change. There’s already precedent for this. The Telecommunications Act of 1996 saw FCC require phone service carriers to allow customers to easily port their numbers to another carrier rather than having to be assigned a new number. If you think of a phone number as a method by which friends connect with you, it would be reasonable for regulators to declare that the modern equivalent — your social network friend connections — must be similarly portable.
How To Unchain Our Friendships
Facebook should be required to let you export a truly interoperable friend list that can be imported into other apps in a privacy-safe way.
To do that, Facebook should allow you to download a version of the list that feature hashed versions of the phone numbers and email addresses friends used to sign up. You wouldn’t be able to read that contact info or freely import and spam people. But Facebook could be required to share documentation teaching developers of other apps to build a feature that safely cross-checks the hashed numbers and email addresses against those of people who had signed up for their app. That developer wouldn’t be able to read the contact info from Facebook either, or store any useful data about people who hadn’t signed up for their app. But if the phone number or email address of someone in your exported Facebook friend list matched one of their users, they could offer to let you connect with or follow them.
This system would let you save your social graph, delete your Facebook account, and then find your friends on other apps without ever jeopardizing the privacy of their contact info. Users would no longer be locked into Facebook and could freely choose to move their friendships to whatever social network treats them best. And Facebook wouldn’t be able to block competitors from using it.
The result would much more closely align the goals of users, Facebook, and the regulators. Facebook wouldn’t merely be responsible to the government for technically complying with new fines, oversight, or liability. It would finally have to compete to provide the best social app rather than relying on its network effect to handcuff users to its service.
This same model of data portability regulation could be expanded to any app with over 1 billion users, or even 100 million users to ensure YouTube, Twitter, Snapchat, or Reddit couldn’t lock down users either. By only applying the rule to apps with a sufficiently large user base, the regulation wouldn’t hinder new startup entrants to the market and accidentally create a moat around well-funded incumbents like Facebook that can afford the engineering chore. Data portability regulation combined with a fine, liability, oversight, and a ban on future acquisitions of social networks could set Facebook straight without breaking it up.
Users have a lot of complaints about Facebook that go beyond strictly privacy. But their recourse is always limited because for many functions there’s nowhere else to go, and it’s too hard to go there. By fixing the latter, the FTC could stimulate the rise of Facebook alternatives so that users rather regulators can play king-maker.
from iraidajzsmmwtv https://tcrn.ch/2HiuMQt via IFTTT
0 notes
Text
California Web Development How To Get The Ideal Design and style To Your Website
California Web Development Learning to achieve success in web page design can seem to be mind-boggling occasionally. Nevertheless if you browse through one can learn some enlightening information about how to become a accomplishment in web site design to help you pay attention to getting to your potential ventures. It is good to include a favicon to your web page. The favicon is really a 16x16 appearance submit in the .Ico format. This appearance is definitely the one you see near the URL club, next to the name from the web page with an launched tab and is also apparent on the book marks tab if you choose to bookmark a site. Web Development in Richmond, California can help consumers rapidly acknowledge your page inside their browser with out reading any written text or directly observing the site. Make sure your webpages aren't too much time. You just get one opportunity to make a very first effect, of course, if your most critical content is "below the collapse," it might not even be study. If you have a lot of connected information that needs to stay jointly, consider busting it into sections and introducing links to every single area. Give your online visitors the ability to look for your blog to enable them to easier find what they are trying to find. When someone could not determine what they are trying to find straight away, their next imagined may be to locate a search area. Put this somewhere apparent and include searching option. Be sure you give your consumers the choice to end a particular activity if they decide to. Steps incorporate signing up for just about any e-mail notices, exploring the web page, or filling out forms. You can expect to unavoidably drop replicate customers if you push these people to follow through on the obtain they have made a decision in opposition to for the time being. Avoid using put-up advertising. Many people tend not to like going to a website, then possessing burst-up ads bombard them. Many website visitors to a website will just click from a website with take-ups, whether or not the site is a popular 1. Furthermore, lots of people will have take-up blockers anyway. It's finest to keep away from this type of advertising and also hardwearing . guests happy. For those who have a number exactly where take-ups are mandatory, then perhaps you have to be out looking for a brand new one. Be sure your website is very easily scanned. Research has shown that internet users scan pages to discover interesting content articles. Bust text message into little, simple to check segments to help you visitors quickly find the data they are seeking. Keep your most pertinent information near the top of the webpage. Performing all of this can make your visitors' experience more fun because they will find the data they desire without having difficulties. If you have never ever created a web site, try using pre-produced styles. These may be easily located online for a lot of blogging sites like Blogspot or Tumblr. Getting an fascinating format will highlight content material and offer the internet site a specialist appear. Just make sure your layout is appealing to your target market! If you believe your website might be accessed by way of cellular devices, you will want to keep your styles basic. Using display, extreme photos, and complicated selections will not likely translate well to your mobile phone platform. Make your web page neat and straightforward, or produce a distinct portable internet site for your personal consumers. Recognize that when you first start off that it's gonna devote some time to your website to be well-known. You can attempt the best to generate as much targeted traffic to your website as is possible but ensure that you know what to prepare for to be able to continuously adjust your strategies accordingly. You want your name to be descriptive on the website. For instance, Yahoo and google "untitled document". Don't turn this error! It is vital that your website has a name. Search engines like google utilize this like a huge portion of the techniques they use for identifying pagerank. Make use of your sentence structure and spell checker. Indeed, some faults can get passed on a number of your viewers, but it will not get past everybody. You could potentially lose several of your market because of this, especially if you make mistakes commonly. Do the best to improve your grammar and spelling in your site. Be sure that you use file dimensions for many articles on the internet site that lots rapidly to your visitors. Generally, JPEGs and GIFs are perfect for visuals. Other records such as PNGs and BMPs use a lot more drive place. To ensure that your end users provide an optimum encounter when opening your site, use file types for your personal artwork that use up a lot less space with a disk. When you might see something diffrent that peaks your design curiosity, it is essential that you stay artistic if you are constructing your blog. Put together your own personal concepts boasting or improve upon some which you appreciated on other sites. Taking this step will definitely help you increase your attempts in web site design. Your design method may well be more profitable when you are studying at each step of how. After getting the dangle of the layout strategy, locate yet another one to find out. Even though this may possibly extend the entire process of creating the initial internet site or two, you can expect to soon have the knowledge you have to crank out websites considerably faster. Make certain your site has a tagline. Whenever a guest click throughs onto your site, you only have a little bit of time and energy to catch them with your goal, purpose, and theme. A tagline must be quick, crystal clear, and explain what your site is about to ensure visitors is going to be curious and remain on your site. Imagine cellular phone users when building your site. A lot more people than in the past use their cellular phone to surfing the net. Should they cannot gain access to your web site or maybe it can't be observed well on the cell phone, they will likely probably steer clear of your blog. That can charge you plenty of business. Most of the greatest website names are presently taken, but you may find it beneficial to investigate sale sites like Sedo to view what can be readily available. It will be possible to discover many fantastic domain names that both are available for sale, abandoned or have already been sold. Remember the things you just go through once you start drawing your layout. Continue to keep studying existing strategies to become a far better web designer. California Web Development
0 notes
Text
Toshiba Adds New 4TB CANVIO® Portable Hard Drive Model for Safe and Reliable Personal Data Storage
IRVINE, Calif. — Toshiba America Electronic Components Inc. today announces a new addition to its popular family of CANVIO external hard drives (HDDs), a 4TB[1] option in its ADVANCE, BASICS and READY series.
The 4TB option gives up to 33 percent extra storage (compared to 3TB) for consumers and small and medium-sized businesses (SMBs) that want to store large files and back up their data. Using 1TB platter technology allows the 4TB CANVIO models to maintain the same low-profile design as 3TB models. All models support Windows® [2] and Mac[3] operating systems and are compatible with both USB 3.0 and USB 2.0.
CANVIO HDDs combine a sleek, slim and stylish design with practical features such as a ramp-load design to prevent internal wear, plug-and-play functionality, backup and security software (available on the ADVANCE models), and a range of more flexible capacity options of 1TB, 2TB, and now 4TB.[4]
“The amount of data a person or company needs to store and back up is increasing exponentially. Toshiba constantly strives to give our customers cutting edge technologies with ever greater storage in a portable, lightweight and attractive design,” says Michael Cassidy, Vice President, Consumer HDD, Americas, at Toshiba America Electronic Components, Inc.
The 4TB BASICS model is available now. General availability of the 4TB ADVANCE and 4TB READY models will start in January 2019. For further information and the detailed product specifications on our full line of consumer HDD storage products, please visit: http://storage.toshiba.com/consumer-hdd.
For more information on our full line HDD storage products, please visit:
https://toshiba.semicon-storage.com/us/product.html.
To learn more about our storage solutions, please visit the storage blog:
http://storage.toshiba.com/corporateblog/, and follow both @ToshibaStorage and @ToshibaUSA on Twitter.
Notes:
[1] Definition of capacity: One Gigabyte (GB) means one billion bytes and one Terabyte (TB) means one trillion bytes. Total available capacity will vary based on operating environment and may show less storage capacity. Your results will vary. A computer operating system, however, reports storage capacity using powers of 2 for the definition of 1TB = 240 = 1,099,511,627,776 bytes and therefore shows less storage capacity.
[2] The CANVIO HDDs support Windows 10, Windows 8.1 and Windows 7. The drive is by default formatted to the NTFS file system for Microsoft and can be reformatted.
Windows is a registered trademark of Microsoft Corporation in the United States and/or other countries.
[3] The CANVIO HDDs support macOS v10.13 / v10.12 / OS X v10.11 but requires reformatting to HFS+ file system to do so. Mac, macOS and OS X are trademarks of Apple Inc., registered in the U.S. and other countries.
[4] 500GB for CANVIO BASICS and CANVIO READY.
* Information in this document, including product prices and specifications, content of services and contact information, is current and believed to be accurate as of the date of the announcement but is subject to change without prior notice.
* Company names, product names, and service names mentioned herein may be trademarks of their respective companies.
* Images displayed in the banners are for illustration purposes only and do not show the actual products. The images are merely intended to help illustrate the function of the products.
* CANVIO is a trademark of Toshiba America Electronic Components, Inc.
About Toshiba America Electronic Components, Inc.
Toshiba America Electronic Components Inc. an independent operating company owned by Toshiba America Inc., is the US based electronic components business of Toshiba Electronic Devices and Storage Corporation. TAEC offers consumers and businesses a wide variety of innovative hard disk drive (HDD) products plus semiconductor solutions for automotive, industrial, IoT, motion control, telecoms, networking, consumer and white goods applications. The company’s broad portfolio encompasses integrated wireless ICs, power semiconductors, microcontrollers, optical semiconductors, ASICs, ASSPs and discrete devices ranging from diodes to logic ICs. For more company information visit TAEC’s web site at http://www.toshiba.semicon-storage.com/.
© 2018 Toshiba America Electronic Components, Inc. All rights reserved. Information in this press release, including product pricing and specifications, content of services and contact information, is current and believed to be accurate on the date of the announcement, but is subject to change without prior notice.
Contacts
Brent Camara WE Communications (425) 638-7481 [email protected]
from Financial Post https://ift.tt/2QdeHmo via IFTTT Blogger Mortgage Tumblr Mortgage Evernote Mortgage Wordpress Mortgage href="https://www.diigo.com/user/gelsi11">Diigo Mortgage
0 notes
Text
“Nora’s Here”
You could say I’m in the middle of a partial life crisis. I’m turning 30 in almost exactly a month.
Help.
From the day I turned 29 I started to mentally spiral a bit. I didn’t do anything particularly crazy (no convertible unfortunately) but I started to feel a little more mortal and a little more unfulfilled. I’d spent the last four and a half years working as an IT Consultant, traveling weekly to towns that mostly started with F to fix computer systems in hospitals. There was nothing exciting about my job and nothing fulfilling. So I quit.
The decision to quit came from a lot of things, both professional and personal, but the end goal was to give myself some time to reset, figure out what would be fulfilling, and to have a few adventures along the way. The adventure part is what has defined my twenties. I’ve constantly felt a strong pull towards the airport, towards new experiences in different parts of the world. I’ve been unemployed for about ten weeks now and I’ve spent seven of those abroad, so I feel like I’m doing a pretty good job.
This intense desire to see the world began during my second year of college, right around when I was turning 20. At the time I’d barely left the United States and was pretty sheltered at home. I was very naive and honestly a baby. My first year and a half of college I hardly drank, I didn’t go to parties, and I spent more Friday nights in the library than anywhere else (this story changes when I get to grad school). Fortunately for my future self I was a bit of a dreamer and easily influenced by pop culture, and the idea of studying abroad became an obsession.
It was no real surprise to anyone when I applied to spend the fall of my third year in Paris, France. I’d studied French since the sixth grade and talked about studying in Paris constantly. What surprised people was when I announced I would also be spending the winter trimester in Paris. That added up to six months in France, and I wasn’t coming home for Christmas either opting instead to get a Rail Europe pass and backpack for a month. It became an unforgettable six months, a time of incredible growth and opportunity. I came home with new friends and a new outlook on life and the world. I was bit by the adventure bug.
So here I am, almost ten years later and staring down my mortality. Since France and Canada I’ve been to 35 more countries/territories, lived abroad a second time, and visited every city that has been featured on MTV’s the Real World except one (St. Thomas... I barely count it). I’ve eaten insects, jumped off things and swam with sharks. On the brink of 30 I decided I wanted to immortalize some of my favorite adventures and document my dreams moving forward.
So what is this Tumblr (and why did I choose Tumblr)???
It’s stories, pictures, songs, recipes, lists... Things that I associate to adventures that I never want to forget.
It’s goals and dreams and a bucket list for my 30s and beyond.
It’s NOT a Travel Blog in the sense that I’m not here to give you recommendations or to sell you things. I’m not an influencer and I’m definitely not an expert on anywhere. (Although I do think Borough Market is a must do in London and I’ll be pissed if you don’t go and drink a road Pimm’s).
I thought Tumblr would be fun because it’s portable (shoutout to the iOS app) and it allows you to easily post in different formats. And I’m lazy and don’t really want to learn a more complicated interface. I just want to tell stories.
Anyways I’m sure I’ll be the only one reading this, but if I’m somehow not. Welcome, enjoy the ride. (And sorry in advance if I give you the adventure bug too).
xox Nora
-The title of this post comes from something my friends said frequently while we were visiting Tokyo a month ago... I tend to wander and pop up when you least expect it.
0 notes
Text
Send Bitcoin By Fax? Morse Code? SMS? Chat? It Could Soon Be a Reality Thanks to Mule Tools The Mule Tools code collection on Github is set to develop new ways to transact Bitcoin including via Fax, Morse Code, and chat applications. Developed tools stand to be incorporated into the Samourai wallet. Inspired by the blockstream satellite and Nick Szabo’s thoughts on the physical transportation of data, Mule Tools is aiming to be a clearinghouse of code enabling alternative methods of broadcasting Bitcoin transactions. What all this means is that using a fax to transact need not just be the sole preserve of Hipsters but rather a way of circumventing possible censorship driven restrictions, enabling transactions outside of internet outages and as a way of combating possible hijackings of your data. Alternative Bitcoin Transaction Broadcast Methods Internet down? Satellites, too? Send a BTC transaction by fax! https://t.co/jKNbuJGuil — Yuri Yerofeyev (@bitcoinyuri) October 26, 2017 The team provides a list of possible areas that they would be interested in assisting the development of: SMS relay satellite hook-up fax or any form of hard copy to character recognition save to external support (USB) Portable Document Format (PDF) telex HF audio Morse code meshNets NFC BLE chat apps (especially encrypted) The list is not definitive with the team saying they are open to other possible suggestions, but they do say that all submitted projects will be considered for support and potential inclusion in the Samourai Wallet (a popular mobile Bitcoin wallet solution). Blockstream Satellites The blockstream satellite is an ambitious project streaming radio broadcasts from space to help those without internet access to benefit and use the Bitcoin blockchain. The company Blockstream have so far leased out bandwidth on 3 satellites in a move which may sound far-fetched but it simply means blockchain data is being broadcasted in the same way as GPS currently is. Dr. Adam Back, Blockstream CEO, clarifies: A user or a local business can run a full node, receive all the data and then when they go to send a transaction, they can pay the bandwidth cost for that. A Bitcoin transaction is pretty small, like 250 bytes. These exciting developments look set to continue as Bitcoin matures, enabling the use of the technology in even the most troubling of locales, benefiting the worlds poor and unbanked who are set to potentially benefit the most from the global Bitcoin monetary revolution. Do you code? Own a Samourai Wallet? What kind of timeframe do you think it will be before we see some of these solutions actively implemented? Tell us what you think in the comments below. Images courtesy of Wikimedia Commons, Chris Ratcliffe/Bloomberg The post Send Bitcoin By Fax? Morse Code? SMS? Chat? It Could Soon Be a Reality Thanks to Mule Tools appeared first on Bitcoinist.com. http://bitcoinist.com/send-bitcoin-fax-morse-code-sms-chat-soon-reality-thanks-mule-tools/ To get started: http://bit.ly/unlibitcoin To double its value: http://bit.ly/btc-gold
from Earn Bitcoin Philippines http://www.facebook.com/pages/p/134403977174420 via Rodrigo M. Palacio Tumblr
0 notes
Text
Microsoft Office Word advantage
Microsoft Office Word to help users create and share content with a professional appearance by combining a set of fully functional authoring tools with an easy-to-use Microsoft Office Fluent user interface. Here are the top 10 reasons why Office Word can help you quickly create content with a professional look. The reduced set time format, mainly focus on documentation. The Microsoft Office Fluent user interface provides the tools needed to allow you to easily and quickly set up a document format. You can find the appropriate features in Microsoft Office Word to more effectively convey the information in the document. With quick styles and document themes, you can quickly change the appearance of text, tables, and graphics throughout your document to match your favorite style or color scheme. With the help of the SmartArt schema and the new graphics tools more effectively convey information. The new SmartArt icon and the new drawing engine can help you create a beautiful look with 3D shapes, transparency, projection, and other effects 3 use building block the rapid construction of document. The building blocks in the Microsoft Office Word can be used to build a document through common or predefined content, such as disclaimer text, important quotes, feed bar, cover, and other types of content. This eliminates the need to spend unnecessary time creating or copying the content between the documents, and helps to ensure consistency of all documents created within the organization. The Microsoft Office directly from the Word save as PDF or XPS. Microsoft Office Word 2007 provides the ability to share documents with others. You do not need to add third party tools, can be converted to Word document portable document format (PDF) or the XML file specification (XPS) format, thereby helping to ensure that with the use of any platform for users to carry out extensive exchanges. The Microsoft Office directly from the Word release and maintenance of the blog. You can blog directly from Microsoft Office Word. You can configure the Microsoft Office Word as a direct link to your blog site, using a rich Word experience to create a blog that contains images, tables, and advanced text formatting features. The use of Microsoft Office Word and Microsoft Office SharePoint Server control document review process. Through the built-in Microsoft Office SharePoint workflow service in Server, you can start at the Microsoft Office Word and track the document review and approval process, helping to accelerate the review cycle of the entire organization, without forcing the user to learn new tools. But the document and business information connection. Create a dynamic smart document using a new document control and data binding, which can be self - updated by connecting to the backend system. Organizations can use new XML integration capabilities to deploy smart templates to help users create highly structured documents. The revision, and delete comments in document hidden text. Use the document checker to detect and remove unwanted comments, hidden text or personal identity information, to help ensure that sensitive information is not leaked in the published document. The use of three pane panel review compare and merge documents. Using Microsoft Office Word can easily find out the changes made to the document. It uses a new three pane review panel to help you view the two versions of the document, and clearly mark the text for deletion, insertion, and movement. And reduce the file size and improve the ability to restore the damaged file. The new Ecma Office XML Open format can significantly reduce the size of the file, while improving the ability to restore damaged files. These new formats can greatly save storage and bandwidth requirements, and can reduce the burden on IT personnel.
to my others tumblr page:
https://getwin7keyonline.tumblr.com/
https://windows7professionalsp1keyworld.tumblr.com
http://windows7ultkeysonline.tumblr.com/
http://office2016keydownload.tumblr.com/
0 notes