#surveillance systems suppliers
Explore tagged Tumblr posts
Text
Security Marketing King Monterey park | Security System Supplier | Security Systems Repair in Monterey Park
Security Marketing King Monterey Park provides top-quality security solutions tailored to meet the needs of clients. As a reliable Security System Supplier in Monterey Park, we offer a wide range of products designed to enhance safety and peace of mind. Our inventory includes the latest in security technology, ensuring that your property is protected with the most advanced systems available. In addition, we specialize in Security Systems Repair in Monterey Park. Our skilled technicians are experienced in diagnosing and fixing issues promptly, minimizing downtime, and ensuring your security system functions optimally. Trust Security Marketing King to enhance your property’s overall security parameters. Call us for a consultation!
#Security System Supplier Monterey Park#Security Systems Repair Monterey Park#CCTV Installation near me#Alarm Systems Repair near me#Video Surveillance near me
1 note
·
View note
Text
9 Tips to Choose the Right Fire Alarm System for Your Business

For business operations to run smoothly, staff must be kept in a secure environment. This guarantees them an enhanced workplace and surroundings where they may achieve their company goals without feeling stressed. You can accomplish this if you pick the ideal commercial fire alarm system for your company. The finest fire alarm system assists in reducing the risk to people and property as well as the disruption to business operations caused by fire accidents. However, there are many options on the market, making it difficult to choose the best fire alarm system. In this article, we are sharing the finest methods to choose a fire alarm system for your company that can prevent fire hazard-related incidents.
Here are the best tips for choosing the right commercial fire alarm system for your business
For better buying decisions, you should take into account the following factors when selecting a commercial fire alarm system for your company:
Identify potential dangers to your property
If you're developing a commercial structure, keep in mind that there may be multiple high-risk areas. Even a little bit of misunderstanding before installing a fire alarm system can cost the owner time and money. Determine the risks in areas with heavy foot traffic as well, and keep your personnel out of those areas.
Dimensions or design of the structure
There are many different kinds of buildings, including mid-rise and high-rise structures, so before installing a fire alarm system, you must be familiar with the building's overall plan or size.
Comply with codes and regulations
The norms of conduct for every building are considerably different from those in other areas. Understanding the codes, laws, and regulations for the upkeep, setup, and kind of fire alarm system is therefore necessary. The fire alarm system you select for the structure must adhere to all applicable building codes and regulations.
Type of fire alarm system
Fire alarm systems often fall into one of two categories: conventional fire alarm systems or addressable fire alarm systems. According to experts, most building owners prefer the traditional fire alarm system because it is a more affordable option. They may not realize, however, that conventional fire alarm systems are ineffective in huge buildings. To cover most areas and eliminate fire-related risks, it is preferable to give priority to the addressable fire alarm system.
Consider a multi-featured system
System integration, remote monitoring, and an emergency communication system are some of the innovative features that technology is developing as it advances. You will have the chance to deal with fire-related emergencies with better experience thanks to these characteristics of the fire alarm system.
Ensure maintenance and installation
A dependable company that installs fire alarm systems will be there to assist you in any way they can. The service provider is responsible for everything related to the fire alarm system, including the device itself and the monthly maintenance inspections. It is not enough to just install a fire alarm system; regular maintenance is necessary to keep it in working order and free from danger.
However, due to the abundance of fire alarm supplier in Bangalore, it is crucial to conduct thorough research before hiring fire alarm services for your future venture.
Put sensors to work
The detection of fire or smoke in a building is a critical function of a fire alarm system. Make sure you have sensors that can quickly alert you to threats before investing in a fire alarm system for your commercial building. Ionization, photoelectric, photoelectric/ionization combo, and heat are the four different types of sensors you may encounter on the market. To find the smoke in the structure, each one operates in a different way. To improve productivity, experts advise using a sensor that combines ionization and photoelectricity.
Consider a proper budget.
The type of building, the size or layout of the facility, routine maintenance, the kind of fire alarm system you choose, and the system's quality all play a role in how much a commercial fire alarm system costs. These elements influence how much a fire alarm system costs on the market, so if you want to buy one, set a budget and choose a high-quality, highly effective fire alarm system for your office building.
Consider Fire alarm monitoring.
Do you want a third party to be in charge of monitoring the fire alarm system? The system's integration of this function is helpful for the building's tenants' security. In the fire alarm monitoring system, a third party handles all the data relevant to the smoke or fire alerts and updates the main station to dispatch the fire protection team to the area that has been affected.
Conclusion
Before selecting a fire alarm system, you should take the following factors into account for the building's safety and security: an understanding of the threats or risks, the building's size or layout, compliance with codes and regulations, the type of fire alarm system, maintenance and installation, and updating technology. Prioritize these criteria before buying the best fire alarm system. Make sure you have cutting-edge equipment so that fire-related risks don't hinder reaching your company's objectives. This will help to maintain the tranquil atmosphere of the facility. You should get in touch with the top fire alarm system supplier in Bangalore if you need any kind of information about the fire alarm services in Banglaore.
#fire alarm systems supplier in bengaluru#fire alarm system#fire alarm systems installations services in bangalore#automatic fire alarm systems#fire sprinkler services#fire alarm#alarm systems#fire alarm system installation in bangalore#video surveillance system suppliers in bangalore
0 notes
Text
Canada’s Department of National Defence (DND) will host trial sessions for Israeli arms technology used to kill Palestinians and maintain apartheid and occupation during a three-week “sandbox” event in Alberta next month.
From May 27 to June 21, DND is giving a select group of military suppliers the chance to test products that are designed to counter aerial drones, with direct assistance from Canadian Armed Forces (CAF) staff and experts. Among those selected is a company called “Twenty20 Insight Inc.,” which is testing the “Smash Hopper counter-drone weapon station.”
The “Smash Hopper” is a remote control weapon system developed and manufactured by Israeli arms company “Smart Shooter,” whose technology is deployed by the Israeli military in fortifications that are used to suppress Palestinian dissent in the occupied West Bank, as well as in military hardware currently being used in Israel’s assault on Gaza.
As reported by AP News in November 2022, Smart Shooter developed remote control turrets deployed by Israel that fire tear gas, stun grenades and sponge-tipped bullets at Palestinian protesters in the occupied West Bank.
Omar Shakir, the Israel and Palestine Director at Human Rights Watch, told AP: “This system will only [...] further grave Israeli human rights abuse and further the Israeli army’s abuses and the Israeli government’s crimes against humanity of apartheid and persecution against millions of Palestinians.” [...]
Continue Reading.
Tagging: @newsfromstolenland, @abpoli, @vague-humanoid
#cdnpoli#absolutely fucking disgusting#genocide#ethnic cleansing#Foreign Policy#zionist occupation of Palestine#military
2K notes
·
View notes
Text
America’s richest Medicare fraudsters are untouchable

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/11/13/last-gasp/#i-cant-breathe

"When you're famous, they let you do it": eight words that encapsulate the terrifying rot at the heart of our lived experience, a world where impunity for the powerful trumps the pain of their victims.
"Populism," is shorthand for many things: rage, despair, distrust of institutions and a desire to destroy them. True populism seeks to channel those totally legitimate feelings into transformative change for a caring and fair society for all. So-called "right populism" exploits those feelings, using them to drive a wedge between different groups of victims, turning them against each other, so that elites can go on screwing the squabbling factions.
The far-right parties that are marching to victory through a series global elections are different in many ways, but they all share one trait: they appeal to mistrust of institutions, claiming that the government has been captured by elites who serve them at the expense of the governed. This has the benefit of being actually true, and while the fact that far-right parties are owned by these government-capturing elites might erode their credibility, the fact that so many "progressive" parties have stepped in to defend the institutional status quo leaves an open field for reactionary wreckers:
https://www.politico.com/blogs/2016-dem-primary-live-updates-and-results/2016/02/hillary-clinton-donald-trump-slogan-219908
Why would voters turn out to support a "Department of Government Efficiency," run by a bully whose career has been defined by abusing the people he is in charge of? Maybe they're turkeys voting for Christmas, but they also have personal, traumatic experience with government departments that protected the abusive corporations that preyed on them.
Today on Propublica, Peter Elkind tells the incredible story of Lincare, the nation's leading supplier of home oxygen, a repeat-offender fraudster and predator that has made billions in public money without any real consequences:
https://www.propublica.org/article/lincare-medicare-lawsuit-settlements-oxygen-equipment
Lincare has been repeatedly found guilty of defrauding Medicare; in this century alone, they have been put on probation four times, with a "death penalty" provision that would permanently disqualify them from ever doing business with the federal government. In every case, Lincare committed fresh acts of fraud, but never faced that death penalty.
Why not? Lincare is far too big to fail. In America's bizarre, worst-in-class, world-beatingly expensive privatized health care system, even public health provision (like Medicare) is outsourced to the private sector. Lincare has monopolized oxygen, a famously very important molecule for human survival, and if it were disqualified from serving Medicare, large numbers of Americans would literally asphyxiate.
Lincare clearly knows this. Too big to fail is too big to jail, and too big to jail is too big to care. They are the poster children for impunity, repeat offenders, multiply convicted, and still offending, even today. Lincare has been convicted of fraud under the administrations of GW Bush, Obama, Trump and Biden, and they're still in business.
What a business it is! Elkind takes us to the asbestos-poisoned town of Libby, Montana, where more than 2,000 of the 2.857 population suffer from respiratory diseases from the open-pit mine that operated there from 1963-1990. The elderly, dying population of this town rely on Medicare and Medicare Advantage oxygen concentrators to draw breath, and that means they rely on Lincare.
That means they are prey to Lincare's signature scam: charging Medicare (and 20% co-paying patients) to rent an oxygen concentrator every month, until they have paid for it several times over. This is illegal: under federal rules, patients are deemed to have bought their oxygen concentrators after 36 months and contractors are no longer allowed to charge them. Lincare doesn't give a fuck: the bills keep coming, and Lincare patients who survive long enough have paid the company $16,000 for a $799 gadget.
When Brandon Haugen, a local Lincare customer service rep, noticed this and queried the company's home office in Clearwater, Florida (home to Scientology and the Flexidisc), he was given the brushoff. After multiple attempts to get company leadership to acknowledge that this was illegal, he quit his job, along with his colleague and childhood friend Ben Montgomery. Between them, Haugen and Montgomery had 14 children who depended on their Lincare paychecks. Despite this, they both quit and turned whistleblower, with no job lined up. Eventually, Lincare paid $29m to settle the claim, with $5.7m to the whistleblowers and their lawyers. For Lincare, this was part of the cost of doing business and the fraud rolls on.
Lincare doesn't just defraud Medicare, they also have a high-pressure commissioned sales force that has repeatedly been caught defrauding Lincare customers – overwhelming sick, poor, elderly people. Patients are pressured to accept auto-billing, then Lincare piles medically dubious gadgets onto their monthly bills, as well as useless, overpriced "patient monitoring" services. Customers with apnea machines are mis-sold ventilators by salesmen who falsely claim these are medically necessary.
Salespeople illegally auto-shipped parts and consumables for Lincare machines to patients, then billed them for it. To satisfy the legal requirement that they telephone patients before placing these orders, sales agents would call patients, put them on hold, then part the call until the patient hung up.
Salespeople are motivated by equal parts greed and terror. Make quota and you can get up to $8,000 per month in bonuses. Miss that punishing quota and you're out on your ass (which is why one salesperson ordered a medically unnecessary ventilator).
Lincare also habitually ignores requests to pick up medically unnecessary equipment, because so long as the equipment is on the patient's premises, they can continue to bill for it. As one Ohio manager wrote to their staff: "As we have already discussed, absolutely no pick-ups/inactivation’s are to be do[ne] until I give you the green light. Even if they are deceased." Execs send out company-wide emails celebrating regional managers who have abandoned pick-ups, like a Feb 2022 "Achievement Rankings" email that touted the fact that most regional centers had at least 150 overdue pickups.
Lincare represents a deep, structural rot in American society. They are too big to punish, and too powerful to regulate. A 2006 law meant to curb oxygen payments was gutted by industry lobbyists. Today, Congress is weighing legislation, the SOAR (Supplemental Oxygen Access Reform) Act, which will allow Lincare to bill the public for hundreds of millions more every year, raising rates and eliminating competitive billing. The bill is supported by patient advocates who are rightly interested in getting oxygen to patients who have been locked out of the system, but the cost of that inclusion is that Lincare will be even more firmly insulated from its corruption.
The Trump Administration will doubtless crack down on some of America's worst companies, and the furious voters who elected the only candidate who campaigned on the idea that America was rotten will cheer him on. But Trump has made it clear that he will select the targets of his administration based on whether they are loyal to him or stand in his way, without regard to whether they harm his supporters:
https://pluralistic.net/2024/11/12/the-enemy-of-your-enemy/#is-your-enemy
Companies like Lincare, repeatedly caught paying illegal kickbacks, know how to play this game.

Image: p.Gordon (modified) https://commons.wikimedia.org/wiki/File:Smoke_bomb_with_burning_fuse.jpg
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#oxygen#monopoly#medicare#medicare fraud#impunity#propublica#lincare#DHHS#HHS#health and human services#department of health and human services#kickbacks#Greg McCarthy#Jenna Pedersen#selective enforcement#too big to fail#too big to jail#Crispin Teufel#Jeff Barnhard#asbestos#Christi Grimm
287 notes
·
View notes
Text

(Dec. 1)
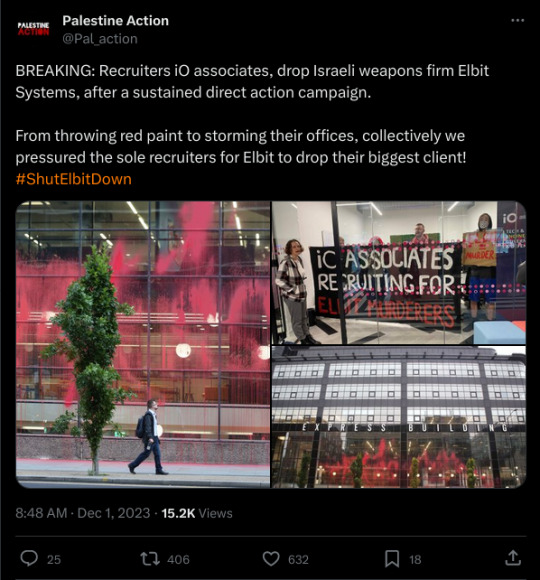
Article: Recruiters Drop Elbit Systems after Palestine Action Campaign
After weeks of action, the sole recruiters for the British operations of Israel’s largest weapons company, Elbit Systems, have confirmed via email to Palestine Action that they ended their association with Elbit on the evening of the 29th November. For two months, activists in the Palestine Action network had disrupted iO Associates at their premises across the country, to impede their ability to recruit roles for Israel’s war machine.
iO Associates recruited the likes of engineers, software developers, and finance staff for positions across the sites of the British branch of Israel’s largest weapons company, Elbit Systems. Elbit are the largest supplier to the occupation military, providing the vast majorities of its drones, munitions, surveillance gear, and parts for its tanks, jets, and precision missiles. From Britain specifically, they manufacture parts for Israel’s killer drones, along with weapons sights, tank parts, and more, exporting these technologies to Israel in great volume yearly. This is the nature of the business that IO was Associates with, and were IO Associates biggest client.
In response to their facilitation of Elbit’s criminal activities, iO’s offices were stormed and occupied in Manchester on the 1st September, and again on the 7th October. Activists painted iO offices red on October 9th in London, Reading, and Manchester. They were forced to vacate their Manchester offices from the 11th October, after the premises were also stormed by the Youth Front For Palestine, and then finally targeted in Edinburgh twice, on the 11th and 17th October. After being forced to vacate their offices, having their online presence tarnished, and (as confirmed to us by former employees) losing their staff who resigned in opposition to their arms trade partnership, iO Associates have finally cut ties with Israel’s weapons trade.
This is part of an expansive strategy by Palestine Action, by disrupting the suppliers and facilitators of Elbit’s presence in Britain. It has seen Elbit’s accountants (Edwards), haulage providers (Kuehne + Nagel), landlords (JLL) and many other complicit companies targeted, alongside the hundreds of actions at Elbit sites themselves, continuing to resist the presence of Elbit warmongers in Britain, and constantly reminding those associated with them that they have blood on their hands.
As a result of iO Associates dropping Elbit Systems, the recruiters have been removed as a target of Palestine Action’s campaign. All targets who still facilitate Israel’s weapons trade are listed on elbitsites.uk
1K notes
·
View notes
Text
For years, it's been an inconvenient truth within the cybersecurity industry that the network security devices sold to protect customers from spies and cybercriminals are, themselves, often the machines those intruders hack to gain access to their targets. Again and again, vulnerabilities in “perimeter” devices like firewalls and VPN appliances have become footholds for sophisticated hackers trying to break into the very systems those appliances were designed to safeguard.
Now one cybersecurity vendor is revealing how intensely—and for how long—it has battled with one group of hackers that have sought to exploit its products to their own advantage. For more than five years, the UK cybersecurity firm Sophos engaged in a cat-and-mouse game with one loosely connected team of adversaries who targeted its firewalls. The company went so far as to track down and monitor the specific devices on which the hackers were testing their intrusion techniques, surveil the hackers at work, and ultimately trace that focused, years-long exploitation effort to a single network of vulnerability researchers in Chengdu, China.
On Thursday, Sophos chronicled that half-decade-long war with those Chinese hackers in a report that details its escalating tit-for-tat. The company went as far as discreetly installing its own “implants” on the Chinese hackers' Sophos devices to monitor and preempt their attempts at exploiting its firewalls. Sophos researchers even eventually obtained from the hackers' test machines a specimen of “bootkit” malware designed to hide undetectably in the firewalls' low-level code used to boot up the devices, a trick that has never been seen in the wild.
In the process, Sophos analysts identified a series of hacking campaigns that had started with indiscriminate mass exploitation of its products but eventually became more stealthy and targeted, hitting nuclear energy suppliers and regulators, military targets including a military hospital, telecoms, government and intelligence agencies, and the airport of one national capital. While most of the targets—which Sophos declined to identify in greater detail—were in South and Southeast Asia, a smaller number were in Europe, the Middle East, and the United States.
Sophos' report ties those multiple hacking campaigns—with varying levels of confidence—to Chinese state-sponsored hacking groups including those known as APT41, APT31, and Volt Typhoon, the latter of which is a particularly aggressive team that has sought the ability to disrupt critical infrastructure in the US, including power grids. But the common thread throughout those efforts to hack Sophos' devices, the company says, is not one of those previously identified hackers groups but instead a broader network of researchers that appears to have developed hacking techniques and supplied them to the Chinese government. Sophos' analysts tie that exploit development to an academic institute and a contractor, both around Chengdu: Sichuan Silence Information Technology—a firm previously tied by Meta to Chinese state-run disinformation efforts—and the University of Electronic Science and Technology of China.
Sophos says it’s telling that story now not just to share a glimpse of China's pipeline of hacking research and development, but also to break the cybersecurity industry's awkward silence around the larger issue of vulnerabilities in security appliances serving as entry points for hackers. In just the past year, for instance, flaws in security products from other vendors including Ivanti, Fortinet, Cisco, and Palo Alto have all been exploited in mass hacking or targeted intrusion campaigns. “This is becoming a bit of an open secret. People understand this is happening, but unfortunately everyone is zip,” says Sophos chief information security officer Ross McKerchar, miming pulling a zipper across his lips. “We're taking a different approach, trying to be very transparent, to address this head-on and meet our adversary on the battlefield.”
From One Hacked Display to Waves of Mass Intrusion
As Sophos tells it, the company's long-running battle with the Chinese hackers began in 2018 with a breach of Sophos itself. The company discovered a malware infection on a computer running a display screen in the Ahmedabad office of its India-based subsidiary Cyberoam. The malware had gotten Sophos' attention due to its noisy scanning of the network. But when the company's analysts looked more closely, they found that the hackers behind it had already compromised other machines on the Cyberoam network with a more sophisticated rootkit they identified as CloudSnooper. In retrospect, the company believes that initial intrusion was designed to gain intelligence about Sophos products that would enable follow-on attacks on its customers.
Then in the spring of 2020, Sophos began to learn about a broad campaign of indiscriminate infections of tens of thousands of firewalls around the world in an apparent attempt to install a trojan called Asnarök and create what it calls “operational relay boxes” or ORBs—essentially a botnet of compromised machines the hackers could use as launching points for other operations. The campaign was surprisingly well resourced, exploiting multiple zero-day vulnerabilities the hackers appeared to have discovered in Sophos appliances. Only a bug in the malware's cleanup attempts on a small fraction of the affected machines allowed Sophos to analyze the intrusions and begin to study the hackers targeting its products.
As Sophos pushed out patches to its firewalls, its team responsible for threat intelligence and incident response, which it calls X-Ops, also began an effort to track its adversary: Sophos included in its “hotfix" for the hackers' intrusions additional code that would collect more data from customers' devices. That new data collection revealed that a single Sophos device registered in February of 2020 in Chengdu showed signs of early alterations similar to the Asnarök malware. “We started to find tiny little indicators of the attack that predated any other activity,” McKerchar says.
Using registration data and records of downloads of code Sophos made available to its customers, the X-Ops team eventually identified a handful of machines it believed were being used as guinea pig devices for Chinese hackers as they sought to find vulnerabilities and test their intrusion techniques prior to deployment. Some of them seemed to have been obtained by a Chengdu-based company called Sichuan Silence Information Technology. Others were tied to an individual who used the handle TStark, whom X-Ops analysts then found had held a position at the University of Electronic Science and Technology of China, also in Chengdu.
X-Ops analysts could even observe individuals using computers and IP addresses tied to the test devices reading Sophos' online materials that detailed the firewalls' architecture. “We could see them researching us,” McKerchar says.
In late April of 2020, Dutch police worked with Sophos to seize a Netherlands-based server that Sophos had identified as being used in the Asnarök infection wave. In June of that year, however, the hackers launched another round of their mass intrusions, and Sophos found they had significantly reduced the complexity and “noise” of their malware in an attempt to evade detection. Yet through the increased data collection from its devices and the intelligence it had assembled on the Chengdu exploit development group, Sophos was able to spot the malware and push out patches for the vulnerabilities the hackers had used within a week, and even identify a “patient zero” machine where the new malware had first been tested two months earlier.
The next month, X-Ops took its most aggressive step yet in countering the effort to exploit its devices, deploying its own spy implants to the Sophos devices in Chengdu they were testing on—essentially hacking the hackers, albeit only through code added to a few installations of its own products the hackers had obtained. Sophos says that preemptive surveillance allowed the company to obtain key portions of the hackers' code and head off a third wave of their intrusions, catching it after only two customers had been compromised and pushing out a patch designed to block the attacks, while obfuscating that fix to avoid tipping off the hackers to Sophos' full knowledge of their techniques.
“In the first wave, we were on the back foot. In the second wave, it was an even match,” says McKerchar. “The third attack, we preempted.”
A New Phase of the Game
Starting in 2021, Sophos says it began to see far more targeted attacks from Chinese hacker groups exploiting its products, many of which it was able to uncover due to its efforts to surveil the research of the Chengdu-based exploit development network. Over the next two years, the hackers continued hijack vulnerabilities in Sophos appliances in a wide variety of targeted attacks hitting dozens of targets in Asia and the West.
In September of 2022, for instance, Sophos found a campaign exploiting a vulnerability in its products that had breached military and intelligence agencies in a Southeast Asian country, as well as other targets including water utilities and electric generation facilities in the same region. Later, Sophos says, a different Chinese state-sponsored group appears to have exploited a bypass for its patch for that vulnerability to target government agencies outside of Asia, in one instance hacking an embassy shortly before it was set to host officials from China's ruling Communist Party. It also found intrusions at another country's nuclear energy regulatory agency, then a military facility in the same country and the airport of the country's capital city, as well as other hacking incidents that targeted Tibetan exiles.
“We just opened the door on a huge amount of high-end targeted activity, a Pandora's Box of threat intelligence," McKerchar says.
As the hackers' tooling continued to evolve in response to Sophos' attempts to head them off, the company's X-Ops researchers at one point pulled from a test device they were surveilling a unique new specimen of malware: The hackers had built a “bootkit,” an early attempt at malware designed to infect a Sophos firewall's low-level code that's used to boot up the device before its operating system is loaded, which would make the malware far harder to detect—the first time Sophos believes that sort of firewall bootkit has ever been seen.
X-Ops never found that bootkit deployed on an actual victim's machine, but Sophos CISO McKerchar says he can't rule out that it was in fact used somewhere and evaded detection. “We certainly tried to hunt for it, and we have some capability to do that,” says McKerchar. “But I would be brash to say it's never been used in the wild.”
As Sophos has tried to understand the motives of the Chengdu-based network of hackers digging up vulnerabilities and providing them to the Chinese state, that picture has been complicated by the strange fact that the researchers finding those flaws may have on two occasions also reported them to Sophos itself through its “bug bounty” program. On one occasion, for instance, the exact vulnerability used in a hacking campaign was reported to Sophos by a researcher with a Chinese IP address just after it was first used in an exploitation campaign—Sophos paid the researcher $20,000 for their findings.
That bizarre incongruity with the Chengdu-based researchers' apparent role as suppliers of intrusion techniques for Chinese state hacking groups and its bug bounty reports to Sophos, McKerchar argues, show perhaps how loose the connections are between the researchers finding these vulnerabilities and the state hackers exploiting those bugs. “I think this is a security research community which is patriotically aligned with PRC objectives,” he says, referencing the People's Republic of China. “But they're not averse to making a bit of money on the side.”
Contacts at the University of Electronic Science and Technology China didn't respond to WIRED's request for comment on Sophos' report. Sichuan Silence Information Technology couldn't be reached for comment, and appears to have no working website.
Sophos' timeline of its struggle against a highly adaptive adversaries sussing out its products' hackable flaws points to the success of China's efforts to corral its security research community and funnel its discoveries of vulnerabilities to the government, says Dakota Cary, a researcher at the Atlantic Council, a nonpartisan think tank, who has focused on that Chinese exploit development pipeline. He points to China's efforts, for instance, to foster hacking competitions as a source of intrusion techniques for its offensive hacking efforts, as well as 2021 legislation that requires researchers and companies based in China to report to the government any hackable bug they find in a product.
“In Sophos' document, you see the interconnectedness of that system kind of shine through,” says Cary. “The culture of these organizations working together or competing for work, and the way that the government is trying to centralize collection of vulnerabilities and then distribute those tools to offensive teams—you see all of that reflected.”
Sophos' report also warns, however, that in the most recent phase of its long-running conflict with the Chinese hackers, they appear more than ever before to have shifted from finding new vulnerabilities in firewalls to exploiting outdated, years-old installations of its products that are no longer receiving updates. That means, company CEO Joe Levy writes in an accompanying document, that device owners need to get rid of unsupported “end-of-life” devices, and security vendors need to be clear with customers about the end-of-life dates of those machines to avoid letting them become unpatched points of entry onto their network. Sophos says it's seen more than a thousand end-of-life devices targeted in just the past 18 months.
“The only problem now isn't the zero-day vulnerability,” says Levy, using the term “zero-day” to mean a newly discovered hackable flaw in software that has no patch. “The problem is the 365-day vulnerability, or the 1,500-day vulnerability, where you've got devices that are on the internet that have lapsed into a state of neglect.”
That warning was echoed by Cybersecurity and Infrastructure Security Agency assistant director for cybersecurity Jeff Greene, who stresses the risk of Chinese hackers exploiting older, unpatched systems, as well as the broader, ironic threat of network perimeter appliances serving as entry points for hackers. “These edge devices often have inherent insecurities, they’re often not managed once they’re put out, they're not patched," says Greene. “We’ll leave a trail of these devices for a long time that attackers will be looking to compromise.”
Sophos CISO McKerchar says the company is revealing its five-year fight with the Chengdu-based hacking network to amplify those warnings, but also to end a kind of cybersecurity industry omertà around the growing issue of security companies' own products creating vulnerabilities for their customers. “Trust in the industry has been massively eroded in the past few years. There's a huge amount of skepticism across about the way that vendors are handling these risks, but we've relied on silence instead,” says McKerchar. “We want to show a bit of vulnerability ourselves, recognize that we've had problems, then tell the story about how we stepped up.”
8 notes
·
View notes
Text

Canada selects Boeing's P-8A Poseidon as its new multi-mission aircraft
The partnership with Canadian industry will provide long-term economic prosperity to Canada 🇨🇦
Fernando Valduga By Fernando Valduga 11/30/2023 - 18:52 in Military
With the P-8, Canada guarantees the interchangeability of allies NORAD and FIVE EYES.
The government of Canada signed a letter of offer and acceptance of foreign military sales for up to 16 Boeing P-8A Poseidon aircraft, as part of the Canadian Multimission Aircraft Project (CMMA).
Canada joins eight defense partners, including all allies of FIVE EYES, the intelligence alliance that also includes the United States, the United Kingdom, Australia and New Zealand, and becomes the fifth NATO nation to have selected the P-8 as its multi-mission aircraft. The first delivery is scheduled for 2026.

“The P-8 will strengthen Canada's defense capability and readiness, and we look forward to delivering that capability to the Royal Canadian Air Force,” said Heidi Grant, president of Business Development at Boeing Defense, Space & Security. “Together with our Canadian partners, we will deliver a strong package of industrial and technological benefits that will ensure continued prosperity for Canada's aerospace and defense industry.”
The P-8 is the only proven in-service and production solution that meets all CMMA requirements, including range, speed, strength and payload capacity. This decision will benefit hundreds of Canadian companies and bring decades of prosperity to Canada through the support of the platform provided by our Canadian industrial partners.
The acquisition of P-8 will generate benefits of almost 3,000 jobs and $358 million annually in economic output for Canada, according to a 2023 independent study by Ottawa-based Doyletech Corporation.
“This is a very important day for the Royal Canadian Air Force and Boeing,” said Charles 'Duff Sullivan, managing director of Boeing Canada. "The P-8 offers unparalleled capabilities and is the most affordable solution for acquisition and life cycle maintenance costs. There is no doubt that the P-8 will protect Canada's oceans and borders for future generations."

The partnership with Canadian industry will provide long-term economic prosperity to Canada.
The Poseidon Team is the cornerstone of Boeing's Canadian P-8 industrial partnership, composed of CAE, GE Aviation Canada, IMP Aerospace & Defense, KF Aerospace, Honeywell Aerospace Canada, Raytheon Canada and StandardAero. The team is based on the 81 existing Canadian suppliers for the P-8 platform and more than 550 Boeing suppliers in all provinces, contributing to the company's annual economic benefit of approximately CAD$ 4 billion for Canada, supporting more than 14,000 Canadian jobs.
With more than 160 aircraft delivered or in service and 560,000 collective flight hours, the P-8 has proven capabilities for anti-submarine warfare, anti-surface warfare, intelligence, surveillance, reconnaissance and humanitarian assistance/disaster relief response.
Tags: Military AviationBoeingP-8A PoseidonRCAF - Royal Canadian Air Force/Canada Air Force
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work in the world of aviation.
Related news
BRAZILIAN AIR FORCE
UFSM receives A-1 jet donated by FAB
30/11/2023 - 18:01
One of the first of the 32 F-16s for Romania being delivered by the Norwegian Minister of Defense on November 28. (Photo: Norwegian Armed Forces)
MILITARY
Romania receives first F-16s that were from the Norwegian Air Force
11/30/2023 - 5:00 PM
HELICOPTERS
Norway says goodbye to its last Westland Sea King helicopter
11/30/2023 - 4:00 PM
MILITARY
HENSOLDT supports BAE Systems in the development of the Striker II fighter pilot helmet
11/30/2023 - 2:00 PM
MILITARY
First Belgian F-35A Lightning II starts painting process
11/30/2023 - 1:00 PM
AIR CARGO
Atlas Air places new order for Boeing 777F freighters
11/30/2023 - 10:30
19 notes
·
View notes
Text
Here’s a refined breakdown of the negative impacts associated with the listed companies and the accusations tied to them:
Google
Google is one of the most powerful technology companies in the world, with significant influence over internet search, digital advertising, and data collection. The key negative impacts include:
垄断 (Monopoly):
Google has faced antitrust lawsuits in multiple countries, including the U.S. and EU, for allegedly using its dominant position in search and digital advertising to suppress competition.
Examples include prioritizing its own services (like Google Shopping or YouTube) in search results, disadvantaging competitors.
侵犯隐私 (Privacy Invasion):
Google has been repeatedly accused of violating user privacy through extensive data collection practices.
Issues like tracking users across websites (even in private browsing) and selling targeted ads based on sensitive user data have raised concerns.
Some governments have penalized Google for non-compliance with privacy laws, such as the General Data Protection Regulation (GDPR) in the EU.
滥用权力 (Abuse of Power):
Google’s control over the digital advertising market has led to allegations of unfair practices, such as charging advertisers high fees or giving preferential treatment to its own ad platforms.
Critics argue this dominance stifles innovation and undermines smaller competitors.
Alchemy Technologies
Alchemy Technologies, a digital marketing company, has been accused of engaging in deceptive practices that manipulate user behavior:
Manipulation and Deception:
The company has been accused of misleading consumers through fake advertisements, false claims, or unethical digital marketing strategies.
Allegations include using dark patterns (design choices that trick users into actions they didn’t intend, such as subscriptions) and targeting vulnerable populations with exploitative tactics.
Erosion of Trust:
By misleading consumers and clients, companies like Alchemy Technologies contribute to widespread distrust in digital marketing practices, undermining the credibility of the broader advertising ecosystem.
Apple
Apple is known for its innovation and market leadership but has faced serious accusations regarding its business and labor practices:
垄断 (Monopoly):
Apple has been accused of monopolistic behavior, particularly regarding its App Store policies.
Developers are required to use Apple’s in-app payment system, for which Apple charges up to 30% commission, leading to accusations of anticompetitive behavior.
Legal battles, like the high-profile lawsuit with Epic Games, highlight claims that Apple unfairly limits competition within its ecosystem.
侵犯隐私 (Privacy Invasion):
Despite its public stance on user privacy, Apple has been accused of enabling surveillance, particularly in cases where it complied with government requests for user data.
Concerns about the AirTags product, which has been misused for stalking and tracking people without consent, further dent Apple’s privacy reputation.
强迫劳动 (Forced Labor):
Apple has faced allegations of forced labor within its supply chain, particularly involving factories in China and other countries.
Investigations have linked Apple’s suppliers to Uyghur forced labor in China, where workers are allegedly coerced into producing components for Apple products.
Reports of abusive working conditions, including long hours, low pay, and unsafe environments, persist, despite Apple’s claims of enforcing ethical supplier standards.
Summary of Impacts:
Google: Dominance in tech markets, privacy violations, and abuse of its powerful position have led to antitrust scrutiny and fines worldwide.
Alchemy Technologies: Manipulative and deceptive marketing practices harm consumer trust and foster unethical advertising environments.
Apple: Allegations of monopolistic practices, breaches of privacy, and labor rights violations cast a shadow over its reputation as a tech innovator.
Each company’s actions have far-reaching consequences, affecting industries, consumers, and global labor markets. Addressing these issues would require stricter regulations, transparency, and corporate accountability.
Here’s a refined breakdown of the negative impacts associated with the listed companies and the accusations tied to them:
Google
Google is one of the most powerful technology companies in the world, with significant influence over internet search, digital advertising, and data collection. The key negative impacts include:
垄断 (Monopoly):
Google has faced antitrust lawsuits in multiple countries, including the U.S. and EU, for allegedly using its dominant position in search and digital advertising to suppress competition.
Examples include prioritizing its own services (like Google Shopping or YouTube) in search results, disadvantaging competitors.
侵犯隐私 (Privacy Invasion):
Google has been repeatedly accused of violating user privacy through extensive data collection practices.
Issues like tracking users across websites (even in private browsing) and selling targeted ads based on sensitive user data have raised concerns.
Some governments have penalized Google for non-compliance with privacy laws, such as the General Data Protection Regulation (GDPR) in the EU.
滥用权力 (Abuse of Power):
Google’s control over the digital advertising market has led to allegations of unfair practices, such as charging advertisers high fees or giving preferential treatment to its own ad platforms.
Critics argue this dominance stifles innovation and undermines smaller competitors.
Alchemy Technologies
Alchemy Technologies, a digital marketing company, has been accused of engaging in deceptive practices that manipulate user behavior:
Manipulation and Deception:
The company has been accused of misleading consumers through fake advertisements, false claims, or unethical digital marketing strategies.
Allegations include using dark patterns (design choices that trick users into actions they didn’t intend, such as subscriptions) and targeting vulnerable populations with exploitative tactics.
Erosion of Trust:
By misleading consumers and clients, companies like Alchemy Technologies contribute to widespread distrust in digital marketing practices, undermining the credibility of the broader advertising ecosystem.
Apple
Apple is known for its innovation and market leadership but has faced serious accusations regarding its business and labor practices:
垄断 (Monopoly):
Apple has been accused of monopolistic behavior, particularly regarding its App Store policies.
Developers are required to use Apple’s in-app payment system, for which Apple charges up to 30% commission, leading to accusations of anticompetitive behavior.
Legal battles, like the high-profile lawsuit with Epic Games, highlight claims that Apple unfairly limits competition within its ecosystem.
侵犯隐私 (Privacy Invasion):
Despite its public stance on user privacy, Apple has been accused of enabling surveillance, particularly in cases where it complied with government requests for user data.
Concerns about the AirTags product, which has been misused for stalking and tracking people without consent, further dent Apple’s privacy reputation.
强迫劳动 (Forced Labor):
Apple has faced allegations of forced labor within its supply chain, particularly involving factories in China and other countries.
Investigations have linked Apple’s suppliers to Uyghur forced labor in China, where workers are allegedly coerced into producing components for Apple products.
Reports of abusive working conditions, including long hours, low pay, and unsafe environments, persist, despite Apple’s claims of enforcing ethical supplier standards.
Summary of Impacts:
Google: Dominance in tech markets, privacy violations, and abuse of its powerful position have led to antitrust scrutiny and fines worldwide.
Alchemy Technologies: Manipulative and deceptive marketing practices harm consumer trust and foster unethical advertising environments.
Apple: Allegations of monopolistic practices, breaches of privacy, and labor rights violations cast a shadow over its reputation as a tech innovator.
Each company’s actions have far-reaching consequences, affecting industries, consumers, and global labor markets. Addressing these issues would require stricter regulations, transparency, and corporate accountability.
https://chatgpt.com/share/6752f369-7f9c-800c-8ef8-c927a0069dc6
#Samsung#Apple#Alchemy technologies#Alphabet Inc#Google Investigations#Google#Monopoly#Conglomerate#20$ jacket
2 notes
·
View notes
Text
After weeks of action, the sole recruiters for the British operations of Israel’s largest weapons company, Elbit Systems, have confirmed via email to Palestine Action that they ended their association with Elbit on the evening of the 29th November. For two months, activists in the Palestine Action network had disrupted iO Associates at their premises across the country, to impede their ability to recruit roles for Israel’s war machine. iO Associates recruited the likes of engineers, software developers, and finance staff for positions across the sites of the British branch of Israel’s largest weapons company, Elbit Systems. Elbit are the largest supplier to the occupation military, providing the vast majorities of its drones, munitions, surveillance gear, and parts for its tanks, jets, and precision missiles. From Britain specifically, they manufacture parts for Israel’s killer drones, along with weapons sights, tank parts, and more, exporting these technologies to Israel in great volume yearly. This is the nature of the business that IO was Associates with, and were IO Associates biggest client. In response to their facilitation of Elbit’s criminal activities, iO’s offices were stormed and occupied in Manchester on the 1st September, and again on the 7th October. Activists painted iO offices red on October 9th in London, Reading, and Manchester. They were forced to vacate their Manchester offices from the 11th October, after the premises were also stormed by the Youth Front For Palestine, and then finally targeted in Edinburgh twice, on the 11th and 17th October. After being forced to vacate their offices, having their online presence tarnished, and (as confirmed to us by former employees) losing their staff who resigned in opposition to their arms trade partnership, iO Associates have finally cut ties with Israel’s weapons trade. This is part of an expansive strategy by Palestine Action, by disrupting the suppliers and facilitators of Elbit’s presence in Britain. It has seen Elbit’s accountants (Edwards), haulage providers (Kuehne + Nagel), landlords (JLL) and many other complicit companies targeted, alongside the hundreds of actions at Elbit sites themselves, continuing to resist the presence of Elbit warmongers in Britain, and constantly reminding those associated with them that they have blood on their hands. As a result of iO Associates dropping Elbit Systems, the recruiters have been removed as a target of Palestine Action’s campaign. All targets who still facilitate Israel’s weapons trade are listed on elbitsites.uk
#palestine action#elbit systems#free palestine#stop the genocide#end the occupation#permanent cease fire
7 notes
·
View notes
Text
Not only that, the fucking jackasses, who don't know ANYTHING about the systems they're tampering with, are COMMITTING LIVE CODE WITHOUT TESTING IT to the Treasury Payment Systems. See here (Wired reporting) and here (an expert weighting in). This "move fast and break things" mentality will KILL people.
You CANNOT do that with government systems without months if not a year or so of thorough testing. And yet, they have failed to do even the a day of testing. None of them are federal workers, it's unknown whether they even had background checks, and they refuse to give their real names to actual federal employees.. (Honestly, that mentality shouldn't exist PERIOD. Techbros use it to try to get around laws and regulations, and end up harming folks more than helping.) I'm not even joking about this. Disabled people rely on the payment system working for our healthcare and survival needs. Please Care About Other People. Disabled people like myself deserve to live too, and what's happening can and likely will kill us. There should be people lining up to block them from entering. Make the fuckers fight to get through. Senators should be blockading entrance. Make the fuckers drag the Senators off in handcuffs, which will only prove all our points. Again, this is a fucking coup by entitled neo-Nazi pricks who want us to live in an Musky-rat-company, where Musk controls everything. That's their ultimate goal. But they can't do that unless they can leverage the Treasury to force the rest of the government to capitulate to their demands. MUSK HAS NO REAL AUTHORITY unless we cede it to him. He pretends he does because he's Trump's friend, but he was not elected, he was not confirmed, his "DOGE" office was never endorsed or confirmed by the Senate, and thus everything he does is illegal and/or unconstitutional.
Call Congress to DO something.
Protest what is happening, but be SMART about it. Do NOT invite police to a protest. You Cannot Trust Police. Many of them are in bed with the far-right.
Protest Tips:
Wear a mask with and safety glasses. (Harder to identity you and it protects you from smoke, tear gas, and diseases.
Do Not Bring Your Phone. Or at the very least Do NOT turn it on as it can be used to identify you or obtain your location.
Do NOT advertise the details of the protest and who is coming to the protest all over social media. Share about the protest's start locations as needed in your groups, but don't advertise it's march pattern or its end goal location or who is attending. These conversations about the march route, goal location, assigned roles, and etc need to happen either in-person with all phones off OR use Signal, an encrypted chat. You want to limit what the surveillance state can pull from posts.
Have designated medics who can help in case of injury or if Police try to shoot people or throw tear gas.
Have designated frontline people. These are the people at the front of the protest, the ones that are most likely to deal with police and/or fascists first. Use make-shift shields to help protect frontline people.
Have designated people who assist those with disabilities to make sure they care able to stay safe and escape if things turn sour. Stay with your assigned peeps!
Have a designated protest partner to help watch your back. Stay with your assigned peeps!
Have designated suppliers, who carry supplies for medics and/or frontline and/or other roles.
Have a plan in case the police try to kettle protesters. A kettle is when police block off routes to escape, thus trapping protestors in a smaller area. This is done to shut down protestors, demoralize, frighten, and mass arrest. Make sure everyone knows the plan and abides by it.
Write on your arm the numbers of lawyers and/or people you can contact in case of arrest.
I'll leave this handbook here in case you all find use out of it. If others have tips, feel free to add them.
I already shared/wrote a post on community care and safety plans here (that was kindly expanded on by censoredsecret).

These men just stole the personal information of everyone in America AND control the Treasury. Link to article.
Akash Bobba
Edward Coristine
Luke Farritor
Gautier Cole Killian
Gavin Kliger
Ethan Shaotran
Spread their names!
#protest tips#protest safety#direct action#resistance#us politics#collective action#this is probably going to get Musk mad at me#but I'm disabled and likely to die under his regime so whatever
142K notes
·
View notes
Text
Satellite Manufacturing Market By Geography — Opportunity Analysis & Industry Forecast, 2024–2030
Satellite Manufacturing Market Overview:

Request sample:
Satellite manufacturing market is being reshaped by the Proliferation of Satellite Constellations and Miniaturisation of Satellite Technology. Next up is SpaceX’s Starlink project, which represents the rise of satellite constellations, with nearly 70 % of its 115 Falcon 9 launches in 2024 aimed at expanding its network. SpaceX launched 23 Starlink satellites on November 2024, 12 of which will have direct to smartphone connectivity and is pushing the boundaries of global connectivity to close the digital divide. On the other hand, the trend of miniaturisation is picking up, with Bengaluru based Pixxel achieving the milestone in July 2023. To develop compact satellites up to 150 kg in weight, with advanced technologies such as synthetic aperture radar and hyperspectral imaging, the company secured a multi-crore grant under the Ministry of Defence’s iDEX programme. These satellites, designed for the Indian Air Force, meet important defence and surveillance requirements and are part of the industry’s move toward smaller, cost-effective solutions with high impact capabilities.
Satellite Manufacturing Market- Report Coverage:
The “Satellite Manufacturing Market Report — Forecast (2024–2030)” by IndustryARC, covers an in-depth analysis of the following segments in the Satellite Manufacturing Market.
AttributeSegment
By Solution
Hardware
Software
By Size
Small Satellites (up to 500kg)
Medium Satellites (500–1000kg)
Large Satellites (Above 1000kg)
By Range
Low Earth Orbit (LEO)
Medium Earth Orbit (MEO)
Sun Synchronous Orbit (SSO)
Geosynchronous Orbit (GEO)
By Application
Communication
Earth Observation & Remote Sensing
Research & Experiment
Reconnaissance
Mapping & Navigation
Others
By End User
Government
Defense
Commercial
Research Institutions
Maritime & Transportation
Academic
Others
By Geography
North America (U.S., Canada and Mexico)
Europe (Germany, UK, France, Italy, Spain, Netherlands and Rest of Europe)
Asia-Pacific (China, India, Japan, South Korea, Australia, New Zealand, and Rest of Asia-Pacific)
South America (Brazil, Argentina, Colombia, Chile and Rest of South America)
Rest of World (Middle East and Africa
Inquiry Before Buying:
COVID-19 / Ukraine Crisis — Impact Analysis:
The satellite manufacturing market was disrupted by the COVID-19 pandemic which led to delays in production and breaks in the supply chain. Labour shortages, delayed component deliveries, and deferred satellite launches were the result of lockdowns and restrictions. The pandemic saw communication and Earth observation satellite demand spike as remote connectivity and monitoring were relied on more, but manufacturers struggled to meet the demand in time.
The Russia Ukraine war had a significant impact on the satellite manufacturing market especially in terms of supply chain and geopolitical tensions. Russia is a major supplier of launch services and materials like titanium, propulsion systems, etc. At the outset of the war that disrupted access to the critical resources. sanctions on Russia added to difficulties, forcing manufacturers to look to alternative sources of supply. At the same time, the conflict drove up demand for military and reconnaissance satellites to track the situation in Ukraine and to maintain strategic communication.
Key Takeaways:
North America Dominates the Market
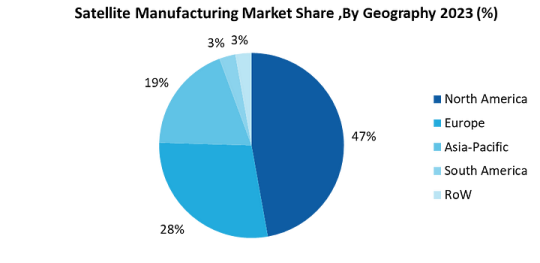
North America is the dominant region in the Satellite Manufacturing market largely due to the presence of players and substantial investments in the space sector. The United States, in particular, leads with companies such as SpaceX, RTX, Lockheed Martin and more which drive innovation in satellite manufacturing. Additionally, North America’s extensive launch infrastructure and high frequency of successful space missions support the demand for satellites. Additionally, the U.S government invests in satellites for surveillance, reconnaissance, and strategic defense applications which is driving the need for satellite manufacturing. In In November 2024, the Biden-Harris Administration announced CHIPS incentives awards to BAE Systems and Rocket Lab, underscoring North America’s leadership in the satellite manufacturing market. BAE Systems received $35.5 million to modernize its New Hampshire Microelectronics Center, significantly increasing production of critical MMIC chips for satellites and defense systems. Rocket Lab secured $23.9 million to expand its Albuquerque facility, boosting the production of space-grade solar cells essential for satellites and space programs like NASA’s Artemis. As the space economy continues to grow, including the need for satellite communications, Earth observation, and defense applications, North America’s robust framework positions it to retain its leading role in the global satellite manufacturing market.
Small Satellites Represent the Largest Segmen
In the Satellite Manufacturing market, small satellites are the dominant segment. Small satellites have revolutionized the satellite manufacturing landscape driven by their affordability, versatility and rapid development cycles. These satellites including nanosatellites and microsatellites are significantly cheaper to design, build and launch compared to traditional large satellites. Their compact size allows multiple small satellites to be launched on a single rocket reducing per-unit launch costs. Moreover, advances in miniaturized electronics and high-performance materials have enabled small satellites to perform complex tasks, from Earth observation and scientific research to navigation and defense. The rise of commercial constellations heavily relies on small satellite technology due to its scalability and ease of replacement. In May 2024, Revolv Space secured $27.33 million to enhance small satellite capabilities, highlighting growing demand in the segment.
Schedule A Call :
The funding will support the launch of its autonomous Solar Array Drive Assembly (SARA), designed to boost small satellite performance and meet the increasing needs of constellation operators. Additionally, research institutions leverage small satellites for educational purposes and low-cost experimentation further driving demand. All these factors combined with shorter production timelines and increasing innovation in modular designs position small satellites as a major segment in the satellite manufacturing industry.
LEO is the Largest Segment
In the Satellite Manufacturing market, Low Earth Orbit (LEO) has become the dominant segment due to its unique advantages and expanding applications. Satellites in LEO operate at altitudes between 500 and 2,000 km, allowing for lower latency in communications and higher-resolution imaging compared to higher orbits. This makes LEO ideal for Earth observation, remote sensing and real-time data transfer. Additionally, the reduced launch energy required to reach LEO contributes to lower overall mission costs makes it more viable for commercial ventures and smaller organizations. The growing trend of mega-constellations such as SpaceX’s Starlink and Amazon’s Kuiper relies on LEO for its ability to support large networks of interconnected satellites that provide global coverage. Furthermore, advancements in satellite design and propulsion systems enable efficient orbital deployment and maintenance within LEO. The World Economic Forum reckons that Earth observation data could add up to $700 billion in value by 2030, contributing $3.8 trillion to global GDP over that period. In addition, Earth observation can help to support policies and practices that could reduce over 2 billion tons of CO₂ emissions per year, making it an invaluable resource in the global sustainability field. With such a large economic and environmental influence, Low Earth Orbit observation is the largest application segment in the Satellite Manufacturing market. Additionally, the increasing private sector investments and evolving market demands ensure LEO’s continued dominance in satellite manufacturing.
Expansion of Satellite Constellations Boosts the Market
Expansion of satellite constellations is one of the major factors driving the Satellite Manufacturing Market, as can be seen from the recent growth of the European Galileo navigation system. Two more satellites were launched in September 2024, bringing the number of operational satellites to 32 in total. The placement of these satellites in medium Earth orbit at 23,222 km improves the constellation’s robustness and reliability. This expansion is crucial to guarantee the uninterrupted provision of high precision global navigation services, which Galileo intends to provide to more than two billion users around the globe. The demand for satellite manufacturing is still growing as more satellites are set to be deployed by 2026, and second-generation satellites are being developed. With countries and private companies investing in expanding their satellite networks for enhanced communication, navigation and data services, the opportunities to innovate and manufacture satellites more efficiently have never been higher. The growing need for satellite constellations is fueling the growth of the satellite manufacturing industry, which is accelerating advancements.
Buy Now:
High Cost of Materials to Hamper the Market
For more details on this report — Request for Sample
Key Market Players:
Product/Service launches, approvals, patents and events, acquisitions, partnerships, and collaborations are key strategies adopted by players in the Satellite Manufacturing Market. The top 10 companies in this industry are listed below:
L3Harris Technologies Inc.
SpaceX
Lockheed Martin Corporation
RTX
Airbus
Boeing
Thales
AAC Clyde Space, Inc.
Ariane Group
Sierra Nevada Corporation
#SatelliteManufacturing#AerospaceIndustry#SatelliteTechnology#SpaceInnovation#NewSpaceEconomy#SatelliteDevelopment#AerospaceEngineering#SpaceTech
0 notes
Text
Maximizing Security: The Power of Video Surveillance Services

A properly secured workplace brings peace of mind and allows an individual to work with a stress-free mind. This thing fosters a boost in workplace productivity and improves mental balance. There are several pieces of state-of-the-art equipment available to enhance overall safety and security. One of them is the Video surveillance system in Bangalore, or CCTV system, which contains recorders, a set of cameras, and a display. The introduction of the Video surveillance system was 50 years ago. This system records the overall activity happening around the premises in the form of pictures and videos. As technology evolves, we can see the modernization of the devices used in daily life every day. In the surveillance system, the real-time distributed wireless surveillance system can be a game changer. Similarly, there is much more evolution we can expect in the coming future. The more advanced the technology-based surveillance system, the lower the probability of incidents.
The Basics of Video Surveillance -
For safety reasons, a video surveillance system, either analog or digital, is frequently employed. Cameras, recorders, and monitors are the primary tools at your disposal in this setup. Any motion detected either outside or inside the building is recorded and stored for later review. Video surveillance systems are increasingly common in both private and public buildings. When the owner is not there, this device may keep a watch on the property to deter any unwanted visitors or criminal behavior.
The Value of Video Monitoring Services
A video surveillance system has many uses and advantages. Here are a few examples:
•Prevention of criminal behavior
•Detection and prevention of crime
•Increased perceptual clarity
•Security of personnel and clients
•Evidence Collection in Criminal Investigations
Criminals can be deterred from committing crimes by installing video surveillance systems. Because of this, criminal activity of all kinds declines. Using a video surveillance system in an office building has the potential to save not only the company's data but also the lives of the people who work there. The more attention we give to workplace safety and security, the more we can concentrate on our jobs.
Important Aspects of Video Surveillance Services -
Protecting your property with a video surveillance system is essential, but only if you use a reliable service provider to ensure you get the right equipment. Several additional important aspects of video surveillance services are outlined below for your convenience.
•Cameras with a high resolution
•Capable of sweeping views and with movable cameras,
•Observing movement and applying analytical smarts
•Keeping an eye on things from afar
•Connectivity to other safety infrastructures
Make sure the following capabilities are present on the video surveillance devices before signing a contract with the service provider. Customers are only interested in flawless execution and unmistakable outcomes. There are many applications for video surveillance, such as in high-traffic areas, the detection of moving objects, and numerous others. Understand the customer's priorities before recommending the most suitable video monitoring device. Retail, healthcare, commercial buildings, the transportation sector, and educational institutions are just some of the many examples of sectors with significant demand for video surveillance systems and related services.
Considerations for Choosing a Video Surveillance Company-
The following are crucial considerations when deciding on video surveillance services:
•Scalability
It's crucial to keep an eye on emerging tech trends before making a purchase. Future technology that may be created should be able to work with the current system
•The Standard of the Video -
Without quality footage and adequate storage, a video surveillance system is worthless. That's why it's so crucial to ensure that the video from the surveillance system is of high quality.
•Capacity for storing and recalling-
It is crucial to select a system with ample storage space and record-keeping skills so that the captured images and videos may be used in the future.
•Respect for confidentiality requirements
To maintain social harmony and conform to the standards of dominant industries, there are a number of laws and regulations that businesses must follow. Verify the company's authority to apply the new policy or privacy standard before making a purchase or engaging in their services.
Conclusion -
With the assistance of video surveillance services, you and your family can feel safer at home and at work. The majority of people, however, do not install a video surveillance system due to the high cost and numerous misconceptions about this technology. For a better experience, it is essential to work with a reputable video surveillance service provider; they will provide you with in-depth detail regarding the cost, suitability, maintenance, and installation, among other things. Get it today. Installing a high-quality video surveillance system acts as a protective shield for your loved ones.
#video surveillance system suppliers in bangalore#cctv install cost#cost to install cctv camera#cost of cctv installation#cctv camera installation cost#cctv camera installation services in bangalore#cctv camera fitters#automatic fire alarm systems#access control systems in bengaluru#best cctv camera company india#video surveillance
0 notes
Text
Denise Hearn and Vass Bednar’s “The Big Fix”

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/12/05/ted-rogers-is-a-dope/#galen-weston-is-even-worse

The Canadian national identity involves a lot of sneering at the US, but when it comes to oligarchy, Canada makes America look positively amateurish.
If you'd like an essay-formatted version of this thread to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/12/05/ted-rogers-is-a-dope/#galen-weston-is-even-worse
Canada's monopolists may be big fish in a small pond, but holy moly are they big, compared to the size of that pond. In their new book, The Big Fix: How Companies Capture Markets and Harm Canadians, Denise Hearn and Vass Bednar lay bare the price-gouging, policy-corrupting ripoff machines that run the Great White North:
https://sutherlandhousebooks.com/product/the-big-fix/
From telecoms to groceries to pharmacies to the resource sector, Canada is a playground for a handful of supremely powerful men from dynastic families, who have bought their way to dominance, consuming small businesses by the hundreds and periodically merging with one another.
Hearn and Bednar tell this story and explain all the ways that Canadian firms use their market power to reduce quality, raise prices, abuse workers and starve suppliers, even as they capture the government and the regulators who are supposed to be overseeing them.
The odd thing is that Canada has been in the antitrust game for a long time: Canada passed its first antitrust law in 1889, a year before the USA got around to inaugurating its trustbusting era with the passage of the Sherman Act. But despite this early start, Canada's ultra-rich have successfully used the threat of American corporate juggernauts to defend the idea of Made-in-Canada monopolies, as homegrown King Kongs that will keep the nation safe from Yankee Godzillas.
Canada's Competition Bureau is underfunded and underpowered. In its entire history, the agency has never prevented a merger – not even once. This set the stage for Canada's dominant businesses to become many-tentacled conglomerates, like Canadian Tire, which owns Mark's Work Warehouse, Helly Hansen, SportChek, Nevada Bob's Golf, The Fitness Source, Party City, and, of course, a bank.
A surprising number of Canadian conglomerates end up turning into banks: Loblaw has a bank. So does Rogers. Why do these corrupt, price-gouging companies all go into "financial services?" As Hearn and Bednar explain, owning a bank is the key to financialization, with the company's finances disappearing into a black box that absorbs taxation attempts and liabilities like a black hole eating a solar system.
Of course, the neat packaging up of vast swathes of Canada's economy into these financialized and inscrutable mega-firms makes them awfully convenient acquisition targets for US and offshore private equity firms. When the Competition Bureau (inevitably) fails to block those acquisitions, whole chunks of the Canadian economy disappear into foreign hands.
This is a short book, but it's packed with a lot of easily digested detail about how these scams work: how monopolies use cross-subsidies (when one profitable business is used to prop up an unprofitable business in order to kill potential competitors) and market power to rip Canadians off and screw workers.
But the title of the book is The Big Fix, so it's not all doom and gloom. Hearn and Bednar note that Canadians and their elected reps are getting sick of this shit, and a bill to substantially beefed up Canadian competition law passed Parliament unanimously last year.
This is part of a wave of antitrust fever that's sweeping the world's governments, notably the US under Biden, where antitrust enforcers did more in the past four years than their predecessors accomplished over the previous 40 years.
Hearn and Bednar propose a follow-on agenda for Canadian lawmakers and bureaucrats: they call for a "whole of government" approach to dismantling Canada's monopolies, whereby each ministry would be charged with combing through its enabling legislation to find latent powers that could be mobilized against monopolies, and then using those powers.
The authors freely admit that this is an American import, modeled on Biden's July 2021 Executive Order on monopolies, which set out 72 action items for different parts of the administration, virtually all of which were accomplished:
https://www.eff.org/deeplinks/2021/08/party-its-1979-og-antitrust-back-baby
What the authors don't mention is that this plan was actually cooked up by a Canadian: Columbia law professor Tim Wu, who served in the White House as Biden's tech antitrust czar, and who grew up in Toronto (we've known each other since elementary school!).
Wu's plan has been field tested. It worked. It was exciting and effective. There's something weirdly fitting about finding the answer to Canada's monopoly problems coming from America, but only because a Canadian had to go there to find a receptive audience for it.
The Big Fix is a fantastic primer on the uniquely Canadian monopoly problem, a fast read that transcends being a mere economics primer or history lesson. It's a book that will fire you up, make you angry, make you determined, and explain what comes next.
160 notes
·
View notes
Text
How to Choose the Best Cold Drinks Vending Machine for Your Needs?
In today's fast-paced world, a Cold Drinks Vending Machine is an excellent investment for businesses, schools, offices, and public spaces. These machines offer convenient access to refreshing beverages, ensuring that customers and employees stay hydrated throughout the day. However, choosing the right vending machine can be a daunting task, given the numerous options available in the market. In this guide, we will explore the key factors to consider when selecting the best Cold Drinks Vending Machine for your needs.
1. Understand Your Requirements
Before investing in a Cold Drinks Vending Machine\, it’s essential to assess your specific needs. Consider the following questions:
What types of cold drinks do you want to offer (soft drinks, juices, energy drinks, water)?
How much space do you have for the vending machine?
What is your expected customer volume?
Do you need a cashless payment option?
Understanding these factors will help narrow down the best vending machine that aligns with your business goals.
2. Machine Size and Capacity
Cold drinks vending machines come in different sizes and storage capacities. If you are placing a machine in a high-traffic area such as a shopping mall or office building, opt for a larger machine with a higher capacity. Conversely, if space is limited, a compact vending machine may be more suitable.
3. Energy Efficiency and Cooling System
A reliable Cold Drinks Vending Machine should have an energy-efficient cooling system to keep beverages at an optimal temperature while reducing electricity costs. Look for machines with an Energy Star rating or other energy-efficient certifications.
4. Payment Options and Accessibility
Modern vending machines come with multiple payment options, including cash, credit/debit cards, and mobile payment methods such as Apple Pay or Google Wallet. Ensuring that your vending machine supports various payment options will improve customer convenience and increase sales.
Additionally, consider accessibility features such as easy-to-use interfaces, ADA compliance for disabled users, and clear digital displays to enhance the user experience.
5. Maintenance and Technical Support
To keep your vending machine running efficiently, regular maintenance is essential. Choose a Cold Drinks Vending Machine from a reputable supplier that offers excellent customer service and technical support. Features such as remote monitoring, automated stock alerts, and self-cleaning mechanisms can help minimize downtime and maintenance costs.
6. Customization and Branding
Some vending machines allow for customization in terms of drink selection and branding. If you own a business, consider a vending machine that can feature your logo or brand colors to create a professional and cohesive look.
7. Cost and Return on Investment (ROI)
While price is an important factor, it should not be the sole determining factor when choosing a Cold Drinks Vending Machine. Consider the machine’s long-term benefits, such as durability, maintenance costs, and potential revenue generation. Conduct a cost-benefit analysis to ensure that the vending machine aligns with your financial goals.
8. Security and Theft Prevention
Vending machines are often placed in public spaces, making them susceptible to theft or vandalism. Choose a vending machine with robust security features such as reinforced glass, secure locking mechanisms, and surveillance integration to protect your investment.
Final Thoughts: Choosing the Right Cold Drinks Vending Machine with United Vending
Selecting the best Cold Drinks Vending Machine requires careful consideration of your business needs, budget, and operational requirements. United Vending is a trusted provider of high-quality vending solutions, offering reliable and energy-efficient machines equipped with modern features. Whether you need a vending machine for an office, retail space, or public area, United Vending has the perfect solution to meet your needs.
With United Vending’s expertise and customer support, you can be assured of a hassle-free vending experience that enhances customer satisfaction and boosts sales. Contact United Vending today to explore the best vending machine options for your business!
0 notes
Text
Why Choose Lewisville, TX for Your Warehouse Space?
Strategic Location Lewisville is centrally located in the Dallas-Fort Worth (DFW) metroplex, one of the fastest-growing economic regions in the U.S. With easy access to I-35E, SH-121, and the DFW International Airport, businesses can efficiently transport goods and materials to local, national, and international markets.
Growing Business Hub Lewisville has a strong economy, with industries ranging from logistics and manufacturing to e-commerce and retail. The city's business-friendly policies and access to a skilled workforce make it an attractive location for companies looking to scale their operations.
Diverse Warehouse Options Whether you need a small storage facility or a large distribution center, Lewisville offers a variety of warehouse for lease lewisville tx with flexible lease terms. From modern, high-tech warehouses to traditional industrial spaces, businesses can find the perfect fit for their needs.
Affordability and Cost Savings Compared to larger cities like Dallas, leasing a warehouse in Lewisville can be more cost-effective, allowing businesses to save on operational expenses while still benefiting from excellent infrastructure and connectivity.
Features of Warehouses for Lease in Lewisville, TX
When searching for a warehouse space in Lewisville, here are some key features to look for:
Size & Layout: Warehouses come in various sizes, ranging from small 5,000 sq. ft. spaces to large 100,000+ sq. ft. distribution centers.
High Ceilings & Open Floor Plans: Ideal for stacking inventory and maximizing storage capacity.
Loading Docks & Drive-in Doors: Convenient access for trucks and delivery vehicles.
Climate Control Options: Temperature-controlled warehouses available for businesses that require specific storage conditions.
Security & Surveillance: Many warehouses come with security systems, gated access, and 24/7 monitoring.
Office Space Integration: Some warehouses offer built-in office space for administrative and operational staff.
Industries Benefiting from Warehouse Leases in Lewisville
Several industries find Lewisville an ideal location for their warehouse operations, including:
E-commerce & Retail: Fast-growing online businesses use warehouse spaces for fulfillment and distribution.
Logistics & Transportation: Third-party logistics (3PL) providers benefit from Lewisville’s highway access and proximity to major shipping hubs.
Manufacturing & Assembly: Warehouses with production capabilities allow businesses to streamline operations.
Food & Beverage Storage: Cold storage and dry storage facilities cater to food distributors and suppliers.
Finding the Right Warehouse for Lease in Lewisville
When leasing a warehouse, consider the following factors:
Lease Terms & Flexibility: Ensure the lease duration and terms align with your business plans.
Proximity to Suppliers & Customers: Choose a location that enhances efficiency.
Zoning & Permits: Verify that the warehouse meets zoning requirements for your industry.
Infrastructure & Amenities: Ensure the facility supports your operational needs, from power supply to parking space.
Conclusion
Warehouse for lease lewisville tx, offers businesses a strategic, cost-effective, and well-connected location to grow and thrive. With a range of warehouse sizes, features, and lease options, companies can find the perfect space to meet their operational needs.
If you're searching for the ideal warehouse for lease in Lewisville, now is the time to explore available options and secure a space that will drive your business forward.
0 notes
Text

Lockheed Martin wins $746 million contract to integrate Switzerland into the F-35 program
Fernando Valduga By Fernando Valduga 09/30/2023 - 20:33in Military
An F-35A fighter taxis on the runway of the Payerne air base. (Photo: Michael Derrer Fuchs / Shutterstock.com)
Lockheed Martin won a contract valued at $746 million to facilitate the efforts to integrate the Swiss government into the F-35 Joint Strike Fighter program as part of a Foreign Military Sales (FMS) agreement.
Swiss industry already plays a role in the construction of the F-35, with some local suppliers (SR Technics, Meggitt, Fisba AG, Nozomi Networks) providing components for the aircraft.
This contract aims to strengthen the participation of Switzerland in the F-35 program. The work is expected to be completed by December 2030.
Switzerland signed an acquisition contract worth $6.2 billion for F-35A fighters in September 2022, formalizing the selection announcement made in June 2021. The contract provides for the acquisition of 36 F-35As jets to be delivered between 2027 and 2030.
Tags: Military AviationF-35 Lightning IILockheed MartinSchweizer Luftwaffe - Swiss Air Force
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
WAR ZONES
Russian Su-35 fighter would have been shot down by Russia's own air defense system
30/09/2023 - 11:03
SAAB
Saab reveals first Saab 340 air surveillance aircraft for the Polish Air Force
30/09/2023 - 10:37
BRAZILIAN AIR FORCE
Santa Maria Air Base would be well rated to receive some Gripen fighters
29/09/2023 - 19:15
HELICOPTERS
Nigeria formalizes order for Cayuse Warrior Plus helicopters
29/09/2023 - 16:00
HELICOPTERS
Australia retires MRH-90 Taipan helicopters ahead of schedule
29/09/2023 - 12:00
MILITARY
Ukraine asks France for Rafale or Mirage fighters and radars for Su-27
29/09/2023 - 08:40
3 notes
·
View notes