#spectrum email login
Explore tagged Tumblr posts
Text
https://roadrunnermailsupport.com/roadrunner-tech-support-phone-number/
0 notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
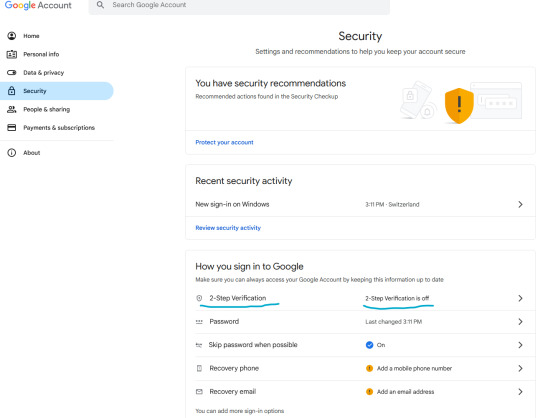
Let's enable two-step verification first.
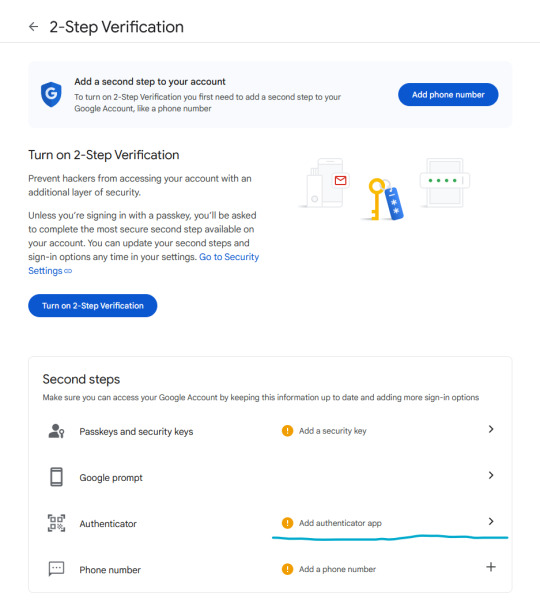
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
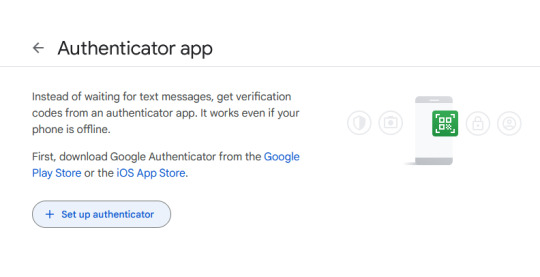
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
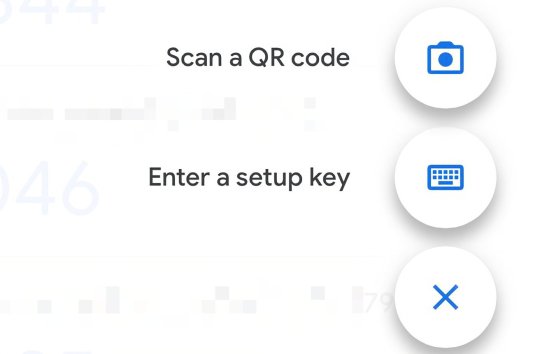
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
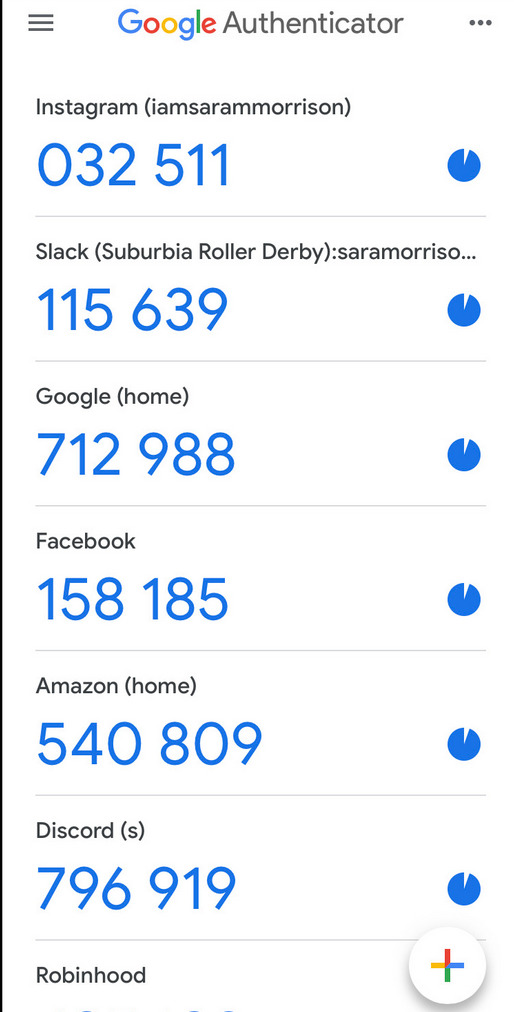
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
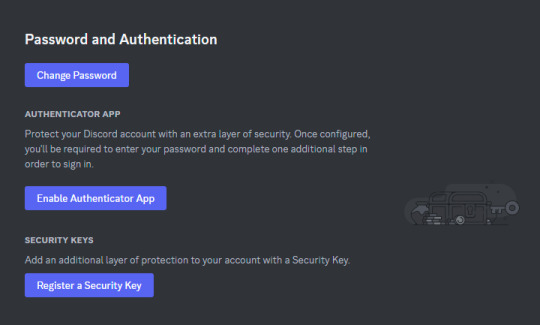
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
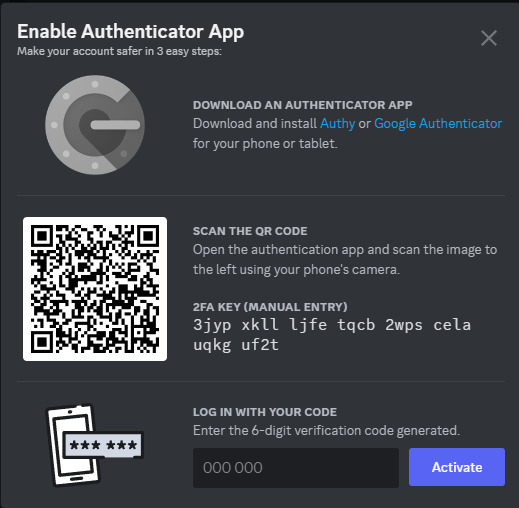
Download Google Authenticator if you haven't already. Scan the QR code as described above.
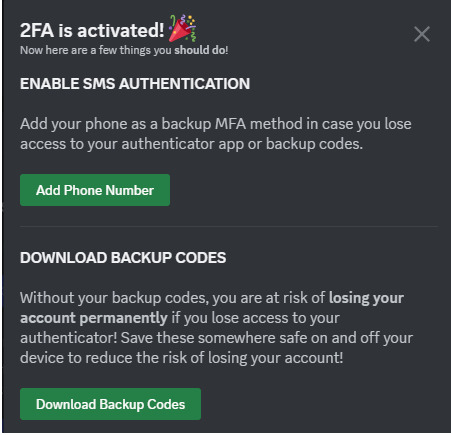
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
16 notes
·
View notes
Text
Hello, I am Ani Singh, a technical expert, and I'm fully prepared to present you with a comprehensive troubleshooting guide for rr.com email login
0 notes
Text
Best 10 Low-code Platforms for Industries
In today’s fast-paced digital environment, industries across the spectrum are turning to low-code platforms to accelerate application development, streamline business processes, and enhance agility. Low-code platforms offer a way for businesses of all sizes and sectors to build applications with minimal coding, reducing the need for extensive developer expertise and speeding up the delivery of new applications. Here are ten of the best low-code platforms tailored for various industries.
1) Kovaion’s Low-code Platform
Kovaion’s low-code platform stands out for its tailored solutions across various industries, including IT, finance, and healthcare. It combines the agility of low-code development with the power of cloud solutions and consulting services, providing a holistic approach to digital transformation. Kovaion’s platform is highly versatile, supporting a range of applications from HR and finance to project management and compliance.

Here are the features incorporated into Kovaion’s Low-Code Platform:
AI-Powered App Builder
Advanced Form Builder
Drag & Drop Workflows
Interactive Dashboards
Responsive Application
Email Notifications
Seamless Integration
Attractive BI Dashboard
API Integration
OTP based Login
User role management (based on fields)
2) Mendix
Mendix is renowned for its comprehensive approach to application development, offering tools for both professional developers and business users. Its platform supports the rapid creation of apps with a strong focus on collaboration and agility. Industries ranging from finance to healthcare benefit from its wide array of integration capabilities and robust security features.
3) OutSystems
OutSystems provides a powerful platform for building enterprise-grade applications quickly. It supports a wide range of application types, from simple departmental apps to complex enterprise systems. OutSystems is particularly noted for its high scalability and strong security measures, making it a favorite among large enterprises.
4) Microsoft Power Apps
Part of the Microsoft Power Platform, Power Apps enables users to build and deploy apps quickly using pre-built templates and a drag-and-drop interface. It’s deeply integrated with other Microsoft services, making it ideal for industries that rely on tools like Office 365 and Azure.
5) Salesforce Lightning
Salesforce Lightning is the go-to choose for CRM-focused industries but has expanded beyond that to offer a comprehensive low-code development environment. It allows businesses to create apps that integrate seamlessly with the Salesforce ecosystem, enhancing customer relationship management and operational efficiency.
6) Appian
Appian focuses on process automation by enabling users to create apps that automate complex business processes. Known for its strong workflow automation and business process management features, Appian helps industries like banking, manufacturing, and government streamline operations and improve efficiency.
7) Zoho Creator
Zoho Creator is designed for SMBs but scales well for larger enterprises too. It offers an intuitive drag-and-drop interface, extensive customization capabilities, and robust data management tools. Its affordability and ease of use make it suitable for all industries looking to digitize their operations quickly.
8) Pega Platform
Pega is known for its intelligent automation capabilities and customer engagement suites. It’s particularly effective for industries where complex workflows and customer interactions are common, such as insurance and financial services.
9) Quick Base
Quick Base is a pioneer in the low-code market, offering a platform that excels in workflow automation and process improvement. With its strong emphasis on collaboration and data security, Quick Base serves industries such as construction, logistics, and healthcare effectively.
10) Betty Blocks
Betty Blocks targets citizen developers in any industry with its no-code approach, allowing non-technical users to build complex applications without writing any code. This platform is particularly appealing to innovators and project managers in sectors like real estate and event management.
Each of these platforms brings distinct advantages that can be harnessed by various industries to meet unique business needs and overcome challenges. Whether it’s enhancing customer interactions, automating complex processes, or efficiently managing enterprise operations, these low-code platforms are essential tools for driving digital transformation and boosting operational efficiency. Among them, Kovaion stands out as the best choice, offering superior versatility and tailored solutions across a broad range of sectors, including IT, finance, and healthcare. Kovaion combines the ease of low-code development with robust cloud solutions and expert consulting services, making it the top pick for businesses aiming for comprehensive digital excellence.
0 notes
Text
cryptostadt email
In the bustling realm of cryptocurrency, navigating through various platforms and companies can sometimes feel like traversing a labyrinth. Among the myriad of options, CryptoStadt login as a noteworthy player, promising lucrative opportunities and seamless transactions. But as with any digital venture, questions arise regarding its legitimacy, operations, and customer satisfaction. Let's delve deeper into the world of CryptoStadt to decipher its authenticity and address common concerns.
Exploring CryptoStadt:
CryptoStadt, touted as a prominent hub for crypto enthusiasts, offers a spectrum of services ranging from trading to investment opportunities. With its sleek interface and enticing promises, it garners attention from both seasoned traders and newcomers seeking to dip their toes into the crypto market.
Addressing Legitimacy Concerns:
One of the primary inquiries that echo across online forums is, "Is CryptoStadt legit?" Understandably, skepticism prevails in an industry susceptible to scams and fraudulent activities. However, upon meticulous examination, CryptoStadt address its legitimacy through transparent operations, adherence to regulatory standards, and a solid track record of customer satisfaction.
Company Background and Contact Information:
Establishing trust begins with understanding the entity behind the platform. CryptoStadt, with its headquarters located at , operates as a registered company committed to providing secure and reliable crypto services. For further inquiries or assistance, users can reach out to CryptoStadt via email at or contact them directly at .
Navigating Complaints:
No company is immune to criticism, and CryptoStadt is no exception. However, it's crucial to differentiate between genuine grievances and baseless accusations. In the rare event of encountering issues with transactions or services, CryptoStadt email prompt resolution and customer support to address concerns effectively.
Transition to CryptoStadt.com:
As part of its evolution and commitment to enhancing user experience, CryptoStadt recently migrated from cryptostadt.co is now cryptostadt.com. This transition signifies a strategic move towards consolidating its brand identity and optimizing services for its growing user base.
Reclaiming Lost Funds:
In the unfortunate scenario of financial loss or discrepancies, CryptoStadt company customer satisfaction by offering a streamlined process for recovering funds. Users can initiate the recover money from cryptostadt contact number resolution and restoring trust in the platform.
In the dynamic landscape of cryptocurrency, CryptoStadt stands as a beacon of reliability and innovation, providing users with a secure gateway to explore and engage in digital assets. With a commitment to transparency, customer satisfaction, and regulatory compliance, CryptoStadt complaint as a legitimate and trustworthy platform in the crypto sphere.
As you embark on your crypto journey, rest assured that CryptoStadt remains steadfast in its dedication to empowering users and fostering a thriving crypto community.
cryptostadt email
0 notes
Text
fin-markethub address
In the ever-evolving landscape of online financial platforms, FinMarketHub has emerged as a prominent player, promising lucrative opportunities for investors worldwide. However, with the allure of financial gains come concerns about legitimacy, complaints, and the arduous process of recovering funds in case of mishaps. In this comprehensive guide, we delve into the facets of FinMarketHub, addressing crucial queries and shedding light on the pertinent aspects surrounding it.
Understanding FinMarketHub
Legitimacy and Company Information
Before delving into any financial endeavor, it's paramount to ascertain the legitimacy of the platform in question. FinMarketHub portrays itself as a reputable entity facilitating various investment opportunities. However, skepticism abounds, with many prospective users questioning its legitimacy. Despite assertions by the company, potential investors often find themselves grappling with doubts regarding the authenticity of FinMarketHub.
Addressing Complaints
A quick internet search yields a spectrum of complaints and grievances lodged against FinMarketHub. From alleged fraudulent activities to dissatisfaction with services rendered, these complaints underscore the importance of due diligence before engaging with the platform. While every complaint warrants investigation, the sheer volume of negative feedback raises red flags and prompts users to exercise caution.
Navigating FinMarketHub
Accessing the Platform: Login and Contact Information
For those considering or already engaged with FinMarketHub, accessing the platform is pivotal. Users navigate to the official website or portal, where they encounter the login interface. However, recent transitions from finmarkethub.co is now fin-markethub.net have left some users puzzled. Ensuring access to the correct domain is crucial to maintaining account security and functionality.
Contacting FinMarketHub
Inquiries, concerns, or issues with FinMarketHub necessitate effective communication channels. While the platform provides email and contact numbers for user assistance, the responsiveness and efficacy of these channels remain under scrutiny. Many users report difficulties in reaching customer support or obtaining satisfactory resolutions to their queries, further exacerbating concerns regarding the platform's reliability.
Recouping Losses: Recovering Funds from FinMarketHub
Strategies for Recovery
In unfortunate instances of financial loss or misconduct, the journey to reclaim funds can be daunting. Users who have fallen victim to scams or encountered issues with FinMarketHub seek recourse through various avenues. From legal proceedings and regulatory complaints to seeking assistance from financial authorities, exploring all available options is essential in the pursuit of restitution.
Transition to fin-markethub.net
The transition from finmarkethub.co is now fin-markethub.net has raised eyebrows within the user community. While the company asserts continuity of services and operations, users remain vigilant, wary of potential implications. Adapting to the new domain entails ensuring data security, verifying account details, and staying informed about any policy changes or updates.
In the realm of online finance, vigilance is paramount. While FinMarketHub presents itself as a gateway to financial prosperity, questions surrounding its legitimacy and operational integrity persist. Navigating the platform entails meticulous scrutiny, proactive risk management, and a thorough understanding of one's rights and recourse avenues. Whether contemplating investment opportunities or grappling with existing engagements, users must exercise caution and remain informed to safeguard their financial interests in the dynamic landscape of FinMarketHub.
fin-markethub address
0 notes
Text
Exploring the Power of Firebase with FlutterFlow: A Seamless Integration for Flutter Developers
In the rapidly evolving landscape of app development, the synergy between frontend frameworks and backend services plays a pivotal role in crafting seamless user experiences. Flutter, Google's UI toolkit for building natively compiled applications for mobile, web, and desktop from a single codebase, has gained significant traction among developers for its expressive and flexible nature. In parallel, Firebase, Google's mobile and web application development platform, offers a comprehensive suite of tools for app development, including authentication, cloud storage, real-time databases, and more. Combining the power of firebase flutterflow, developers can create robust and scalable applications efficiently. In this article, we delve into the integration of Firebase with Flutter through FlutterFlow, exploring its capabilities and benefits.
Understanding FlutterFlow: FlutterFlow is a visual UI builder and development platform that simplifies the process of building Flutter applications. With FlutterFlow, developers can design and prototype UIs visually, drag-and-drop components, and generate Flutter code automatically. This streamlined approach to app development accelerates the iteration cycle and empowers developers to focus on crafting engaging user experiences rather than getting bogged down by tedious coding tasks.
Integration with Firebase: One of the key strengths of FlutterFlow is its seamless integration with Firebase. By incorporating Firebase services into FlutterFlow projects, developers can leverage the full spectrum of Firebase's features to enhance their applications. Let's explore some of the core Firebase services and how they complement Flutter development:
Authentication: Firebase Authentication provides a robust and secure solution for user authentication, supporting various authentication methods such as email/password, phone number, social media login, and more. With FlutterFlow, integrating Firebase Authentication into an app is straightforward, allowing developers to implement user authentication flows with minimal effort.
Cloud Firestore: Cloud Firestore is a flexible, scalable database for mobile, web, and server development. It seamlessly synchronizes data between clients and the cloud, enabling real-time updates and offline support. By integrating Cloud Firestore with FlutterFlow, developers can build dynamic and responsive applications that store and retrieve data efficiently.
Cloud Storage: Firebase Cloud Storage offers secure and scalable object storage for user-generated content such as images, videos, and documents. With FlutterFlow, developers can easily incorporate Cloud Storage into their apps to enable features like file uploads, downloads, and media sharing.
Real-time Database: Firebase Realtime Database is a cloud-hosted NoSQL database that stores data in JSON format and synchronizes it across connected clients in real-time. This enables collaborative and interactive features such as live chat, multiplayer gaming, and collaborative editing. By integrating Firebase Realtime Database with FlutterFlow, developers can create immersive real-time experiences for their users.
Benefits of Using FlutterFlow with Firebase: The integration of FlutterFlow with Firebase offers several benefits for Flutter developers:
Rapid Development: FlutterFlow's visual UI builder accelerates the development process, allowing developers to create UIs quickly and iterate on designs effortlessly.
Seamless Integration: FlutterFlow seamlessly integrates with Firebase, enabling developers to leverage Firebase's powerful backend services without writing extensive code.
Scalability: Firebase's cloud-based infrastructure scales effortlessly to accommodate growing user bases and increasing data loads, ensuring that applications built with FlutterFlow remain performant and responsive.
Real-time Updates: Firebase's real-time database and synchronization capabilities enable developers to build interactive and collaborative features that update in real-time, enhancing user engagement and retention.
Conclusion: The integration of Firebase with FlutterFlow unlocks a wealth of possibilities for Flutter developers, enabling them to build feature-rich and scalable applications with ease. By leveraging Firebase's robust backend services and FlutterFlow's intuitive UI builder, developers can streamline the app development process and deliver compelling user experiences across platforms. As the mobile and web development landscape continues to evolve, the combination of Flutter and Firebase remains a formidable duo for building innovative and impactful applications.
For more details, visit us:
flutterflow developer
flutterflow ai
flutterflow ios app
flutterflow app builder
0 notes
Text
0 notes
Text
Role of Artificial Intelligence in Cybersecurity

In today’s increasingly digital world, the prevalence of interconnected systems has grown at an astonishing rate. While this connectivity has undoubtedly brought immense convenience and efficiency, it has also given rise to a new breed of threats — cyberattacks. As cyber criminals continually evolve in sophistication, both individuals and organisations are turning to Artificial Intelligence (AI) as a vital tool to reinforce their cybersecurity efforts. In this article, we will explore the transformative impact of AI on the realm of cybersecurity and its important role in countering an array of cyber threats.
The Evolving Landscape of Cybersecurity
The escalating financial costs and damage to reputations resulting from cyberattacks have catapulted cybersecurity to the top of the priority list for businesses, governments, and individuals alike. To effectively combat digital threats, proactive measures are essential, as cybercriminals employ a wide spectrum of techniques, including malware, phishing, ransomware, and social engineering, to infiltrate systems and pilfer sensitive data.
The Role of AI in Cybersecurity
AI’s capacity to analyze vast datasets, identify patterns, and make real-time decisions has revolutionized the battle against cyber threats. This newfound empowerment equips cybersecurity professionals to detect and respond to attacks with unprecedented efficiency. Let’s explore some of how AI is reshaping the field of cybersecurity:
Threat Detection and Prevention: AI-powered cybersecurity solutions continuously scrutinize network traffic, user behaviour, and system activity to pinpoint anomalies that may signify potential threats. Machine learning algorithms swiftly adapt to emerging attack vectors, enabling proactive threat detection and prevention.
Malware Detection and Removal: AI-driven antivirus and anti-malware tools excel at recognizing and neutralizing even the most sophisticated malware strains, including those with previously unknown signatures.
Behavioural Analysis: AI can establish a baseline for user and system behaviour, facilitating the detection of unusual activities that may indicate a cyber intrusion. This aids in identifying insider threats and zero-day attacks.
Automated Incident Response: AI-based security systems streamline incident response procedures, reducing the time between threat detection and mitigation.
User Authentication: AI enhances user authentication by incorporating behavioural biometrics and continuous monitoring to identify suspicious login attempts or unauthorized access.
Phishing Detection: AI algorithms can meticulously analyze emails, making them highly effective at spotting phishing attempts and preventing users from falling victim to deceptive messages.
Security Analytics: AI-driven security analytics platforms simplify the monitoring of security logs and events, providing actionable insights to security teams.
Challenges and Considerations
While AI offers substantial advantages in strengthening cybersecurity, several challenges must be addressed:
Adversarial Attacks: Cybercriminals may attempt to subvert AI-based security systems through adversarial attacks, necessitating the development of robust defences against such tactics.
Data Privacy and Ethics: The use of AI in cybersecurity involves the processing of vast amounts of data, raising concerns about data privacy and ethical considerations.
False Positives and Negatives: AI systems can occasionally generate false positives or false negatives, potentially causing disruptions or missed threats. Striking the right balance is crucial.
AI Talent Shortage: There is a shortage of skilled professionals capable of developing, implementing, and managing AI-driven cybersecurity solutions, emphasizing the need for workforce development.
The Future of AI-Driven Cybersecurity
The future of AI-driven cybersecurity holds immense promise as organizations grapple with increasingly sophisticated cyber threats. AI, with its data analysis capabilities and pattern recognition, will play a pivotal role in bolstering cybersecurity defences and thwarting malicious attacks. AI-powered threat detection and prevention systems will become more proactive, allowing organizations to identify and neutralize threats in real time, preventing significant harm.
As AI continues to advance, we can anticipate the integration of AI with other cutting-edge technologies, such as big data analytics and federated learning, creating a more robust and collaborative cybersecurity ecosystem. However, while AI offers substantial advantages, it also presents challenges, including the need for skilled professionals and ethical considerations. Responsible and collaborative adoption of AI-driven cybersecurity is crucial for building a safer and more secure digital landscape for the future.
Empowering Cybersecurity Through AI Certification
AI certification courses have gained paramount importance in today’s digital landscape. In an era dominated by the ever-growing threat of cyberattacks, the integration of artificial intelligence (AI) with cybersecurity is crucial. AI developer certification not only equips individuals with essential skills in AI but also provides them with the expertise needed to address the evolving challenges in cybersecurity. Understanding what is AI certification and the importance of AI certification exams is key to staying ahead in the battle against cyber adversaries.
For those interested in specialized areas within AI, such as chatbot development, there’s the option of pursuing a chatbot certification to become a certified chatbot expert. AI prompt engineer certifications ensure that professionals are well-prepared to harness the potential of AI chatbots in enhancing security measures and maintaining a secure digital environment.
In conclusion, AI is reshaping the cybersecurity landscape, offering new possibilities for identifying and mitigating cyber threats in real time. As the cyber threat landscape evolves, integrating AI with cybersecurity becomes increasingly critical. Organizations must invest in AI-driven cybersecurity solutions while also addressing the challenges associated with the adoption of this technology. Combining human expertise with the power of AI will enable us to stay ahead in the ongoing battle against cyber adversaries. As AI continues to advance, the cybersecurity industry must collaborate, innovate, and continually enhance our defences to create a safer digital environment for businesses, governments, and individuals in the digital age. By embracing AI as a formidable cybersecurity ally, we can forge a path towards a more secure and resilient cyber world.
Blockchain Council, an authoritative group of subject experts and enthusiasts, plays a significant role in the ever-evolving technological landscape. They provide AI expert certification, further strengthening the integration of AI with other cutting-edge technologies. Blockchain technology, with its myriad applications, is becoming an essential component of the digital world, and organizations are recognizing its potential. With the guidance and certifications offered by the Blockchain Council, professionals are well-equipped to navigate the exciting world of AI and blockchain, contributing to a more secure and technologically advanced future.
0 notes
Text
https://roadrunnermailsupport.com/roadrunner-email-support-phone-number/
0 notes
Link
0 notes
Text
How To Join BTC Cloud Mining Step-by-by Guide

Before learning how to join BTC cloud mining, it is important to know why we should do so. The motivation comes from the fact that those interested in the cryptocurrency business have a spectrum of choices here. Its affordability is highlighted by cloud mining’s attribute which relieves the investor from buying expensive equipment and maintaining it or footing massive electricity bills. Now that you are convinced that cloud mining is the best bet, let’s learn the nuances of joining the cloud crypto mining process.
Choose A Reputable Company
The first step towards cloud mining starts with intensive research with the hope of finding a reputable and reliable cloud mining provider. Collect reviews, testimonials and user experiences of the best cloud mining in Chennai from friends, colleagues and relatives. Analyze the transparency of the provider by the extent to which they reveal their mining facilities and team besides sharing the risk involved.
Pay attention to the mining contracts, maintenance fees and pricing structure and ensure that it aligns with your budget and investment goals. Identify the mining algorithms that the cryptocurrencies offered would support and study the scope for diversification.
Finalize A Mining Package
After finalizing your provider move over to the mining packages and start by deciding the length of the contracts. These contracts may extend from a few months to a few years and the longer ones come with better pricing yet longer commitment. Determine your budget which would automatically lead you to a suitable mining package and its size.
From the range of packages offered by the cloud mining platform with varying hashing power choose the one you can afford with a potential to earn. Read the terms and conditions carefully and bring your risk tolerance to the picture and make your plunge.
Select A Mining Pool
Enhance your chances of earning bitcoins by joining the right mining pools based on factors like size, payout structure, fees, reliability and user interface. Mining hardware like graphics processing units and central processing units are limited in their profitability and need more time and energy to mine, while application-specific integrated circuits have better computational power than the former ones.
Look for the cloud mining services mining pool’s transparency which is asserted through its real-time dashboards. Observe the pool payout schemes which may be pay-per-share and pay-per-last-n-shares. Study the mining pool’s stability by analyzing factors such as downtimes which depend on the connection which may be secure or open, vulnerability to DDoS attacks which increase with increased pooling activities and the pool’s ability to repel such attacks.
Pay For The Service And Deposit Funds
Start by creating an account on the website of the chosen cloud mining service which requires an email address and an extremely secure password setup. Use appropriate credentials to cloud mining login to enter your newly created account and choose a mining package that is both affordable and suitable.
Buy mining contract in terms of contract duration, maintenance fees, hashing power and total cost and add the chosen mining package to your cart. Click the ‘Proceed to payment’ or ‘Check-out’ button to initiate the payment process and through cryptocurrencies or traditional methods like credit cards. Enter payment details by confirming and making payments and depositing funds in your account.
Start Mining
Now that your account is funded, purchase the hashing power to start mining. Rent a part of the cloud mining service’s mining equipment through which you earn rewards based on your share of the total hashing power used. Employ your account dashboard to assess the performance of your mining package and other statistics like daily earnings and total BTC earned and tracking these metrics evince the progress of your investment.
Anticipate the risks and challenges on which your profitability depends and invest only what you can afford to lose. Review your investment strategy constantly and adapt to the market conditions for the best results.
Monitor And Withdraw Earnings
While you track your earnings through your crypto cloud mining account’s dashboard, be aware of the bitcoin’s price, mining difficulty and mining plan’s fees when making expectations. Use email or mobile phone notification settings to stay informed about your earnings and mining activities. Use the performance graphs that your cloud mining service may provide to understand trends and periods of high or low profits.
After accumulating a sufficient amount of cryptocurrency, withdraw to your wallet in a procedure prescribed by the cloud mining provider. Understand the threshold and schedules of your provider while making such withdrawals.
Stay Informed And Research
An investment market as volatile as cryptocurrency needs constant tracking, owing to its fluctuating profitability. Along with the fluctuations in bitcoin prices and mining difficulty, it is advised to track the service provider’s legitimacy periodically. Stay informed about the tax obligations regarding your cryptocurrency returns in your jurisdiction and have documents in place to fulfill such requirements.
Employ sources like cryptocurrency news, social media, market analysis from reputable sources, forums and podcasts to stay informed about the best mining practices. Understand mining basics, calculate returns on investments and ensure the responsiveness of the provider’s customer support and their regulatory status in your region before executing your operations.
Execute Security Measures
Focus on encryption and two-factor authentication to secure your earnings and use strong and unique passwords. Beware of phishing attempts and review account activity for any suspicious behaviour. Also, study the security measures practiced by the cloud mining service provider to secure their mining farms along with the accounts of their customers.
Conclusion
Though cloud mining is not as profitable as self-hosted mining with dedicated software, it is an excellent way to start with humble means. However, it is advisable that the investor is alert and makes informed decisions and evaluates costs, returns and risks involved before committing money to the cloud mining company. Make sure to embrace the volatility of the cryptocurrency market and have a strategy-based exit plan before you make an entry.
0 notes
Text
Spectrum Email login
Spectrum Email login

Range is an E-mail solution that will offer you with 5 accounts if you purchase one link. Their storage space will vary from 5 to 30, depending upon the solution load you're subscribing to. It offers you with a variety of functions, particularly safety and safety functions. Such as an account securing system in this, if you do not accessibility your represent 180 days, the mailbox will be secured for included safety and safety. Nevertheless, one sign-in suffices to obtain the e-mail back on the right track and operating.
Accessibility Range Webmail login Ways to accessibility Range e-mail login
Range E-mail is not new however due to rebranding, there was a great deal of complication amongst its individuals. So, it's much far better to see the actions once more and revise ways to accessibility Range e-mail login once more.
The complying with actions are appropriate for Roadway Jogger/Time Detector On-line, Brilliant Home Networks, or Charter customers.
Go for your preliminary login web page and obtain rerouted to a brand-new web page. There you have to go into your qualifications. After that, tick the CAPTCHA Lastly, send whatever and you will be rerouted for your Range account. That is how you can accessibility, login & inspect Spectrum's e-mail account.
What is Roadrunner E-mail and Charter E-mail?
A lot of you might understand the Roadrunner animation collection that we produced by Detector Brothers that was among one of the most well-known computer animated collection throughout the 1990s. So, Time Detector Cable television utilized that call to produce a Road Runner E-mail in 1995.
In 2012, RoadRunner was rebranded to Time Detector Cable television (TWC). After that in 2016, Time Detector Cable television (TWC) was obtained by Charter Interactions, and after that it was called Range Web.
This collection of rebranding puzzled a great deal of individuals and thus, are browsing, ways to accessibility RoadRunner E-mail, Charter Range E-mail, and so on. However the truth of the issue is, all them coincide.
How do I discover my password for my Range E-mail?
So, if you have actually shed your Range password, do not concern we obtained your back. It's really simple to reset and discover your password in Range E-mail, you simply need to comply with the provided actions and you will ready to go.
Most likely to the Range Login Web page. Click Neglected E-mail Password?
You will be rerouted to the password reset device. There you have to choose I have no idea my e-mail password, go into your E-mail, and click Send. If this is your very first time utilizing the device, after that you will be asked to go into your modem's MAC Deal with. If you do not understand that, you can constantly inspect it on your system. After that response the safety and safety concerns and produce a brand-new password.
1 note
·
View note
Text
Introducing the Web3 Category in Marketplace
With the addition of the Web3 category to the Marketplace, we made progress in that direction.

Why Web3?
First, let’s define what the term “Web3” means. We’re not talking about cryptocurrencies or decentralised banking. These are particular Web3 applications.
For us, the term “Web3” refers to ideologies, ideas, and technologies that place an emphasis on user control and ownership and that can be used to create decentralised services. Some (but not all) of the components that make up Web3 include blockchains, tokens (fungible or non-fungible), protocols, services, decentralised applications, and users’ keys.
Web3 marketplace development is fundamentally about user choice. As NotBoring’s founder, Packy McCormick, put it:
Some users will prefer centralised services, while others will prefer wholly decentralised ones. Many users will opt for places on the spectrum in between that suit their needs at various times and for various purposes. We contend that Web3 affords them that option.
Based on our research, we think Web3 can assist application developers in creating personalised user experiences and addressing use cases related to compliance and privacy. However, in order for the space to really take off, it must provide a positive user experience and safeguard customer information and assets.
Numerous businesses depend on the Okta Customer Identity Cloud to assist them in achieving their UX and security objectives. We are eager to provide our services to businesses and developers wishing to use Web3 constructs in the identity area, particularly the Web3 Marketplace category is our first step toward that goal.
A New Set of Building Blocks for Identity
A new set of “decentralised identity” building components are introduced by Web3 structures. With them, users can control their login information and decide what information to share and keep private.
Let’s discuss those components in more detail.
Private key authentication. Private keys of users can be used as credentials to authenticate with services, enabling password-free login for users.
For instance, SIWE (Sign-in with Ethereum) offers sign-in capabilities for Ethereum accounts. More generally, Decentralized Identifiers (DIDs), a recently approved w3c (World Wide Web Consortium) open web standard, propose identifiers based on asymmetric cryptography and owned by users. Techniques such as:Using addresses/keys from decentralised networks like Bitcoin, Ethereum, Solana, etc., pkh or did:ethr implement DIDs. You can see in this video how we implemented SIWE in a model app.
Public, approachable usernames. These can be put into practise by using smart contracts to link familiar names like jane.eth or gary.wallet to blockchain addresses. These usernames would serve as a single username across all applications that use the account’s private key for authentication as well as a convenient way for users to refer to blockchain addresses.
Users’ public profiles. To map properties (other than usernames) to a blockchain address, these can be implemented utilising the aforementioned smart contracts. Some people might openly divulge their email address, avatar or profile photo, or other private information.
These profiles can then be used by applications to offer users customised experiences without the need to create application-specific profiles. Watch this video to see how we used usernames and public user profiles in a sample app.
Attestations in public. These can be implemented using either nft marketplace development solution for “ownership attestations” or “soulbound tokens” (SBTs) for non-transferable attestations.
These could be used for token gating, where access to particular features is restricted to users who own tokens on a blockchain. Shopify is developing token-based commerce. You can see in this video how we implemented token gating using NFTs in a sample app.
Private User Information. Verifiable Credentials (VCs) and Zero-Knowledge Proofs (ZKPs) can be used to build Privacy-Preserving Attestations for this data that is linked to a user’s identify (this works with and without DIDs).
Verifiable Credentials, digital credentials that can be cryptographically verified, can be acquired and saved on a user’s phone app (sometimes known as a “wallet,” which adds to the ambiguity surrounding the term).
Users can later display them (the full credential or a subset of its features) wherever they wish. The fact that issuers are not required to be aware of the presentation location of these Verifiable Credentials is a plus. You can see in this video how we used Verifiable Credentials in a sample app to assist establish a user’s age.
Introducing the Web3 Category in Our Marketplace
Developers can browse and install integrations for a variety of use cases into their identity infrastructure through the Marketplace. With just one click, you may, among other things, enable risk-based MFA, allow Identity Proofing, and send application activity to your logging infrastructure.
Web3’s open standards and modular design give developers flexibility in how they architect and create their apps. We aim to offer the same extensibility and composability. To debut the Web3 category on the Marketplace, we’ve teamed up with top Web3 organisations that are creating developer tooling.
Cases of Use
As we began collaborating with Web3 businesses to create integrations for Okta, we learned that most integrations fall into one of three use cases:
Using a Web3 account or private key to log in: proving your ownership of a specific blockchain address or private key to an application. Users are given a password-free login experience with this, enabling them to control their own identity without relying on external parties like social login services.
Making a user’s Web3 wallet: provides the option to create and link a wallet (custodial or non-custodial) to an Okta user who has logged in with any Okta connection (social, enterprise, database, etc.). This strategy is comparable to various gaming platforms and centralised exchanges. They use it since there is no necessity that users have a wallet before signing up, preventing users from abandoning the process due to that restriction.
For app logic, use Web3 public constructs: Developers can use a user’s blockchain accounts in their applications once their accounts have been discovered. Displaying profile details, identifying a user’s NFT marketplace development service and restricting access to content depending on NFT ownership are examples of potential scenarios.
0 notes
Text
doublecapitals.com is now doublecapitals.co
In the vast landscape of online financial platforms, DoubleCapitals login emerged as a prominent name, attracting both intrigue and scrutiny. As users navigate the realm of investment and trading, questions regarding its legitimacy, company background, and avenues for resolving complaints become paramount. This comprehensive guide aims to shed light on the various facets of DoubleCapitals, addressing concerns and providing insights for users.
Exploring DoubleCapitals: A Legitimacy Evaluation
For many potential users, the foremost question is, "Is DoubleCapitals legit?" Scrutinizing the legitimacy of an online financial platform is crucial to safeguarding investments and ensuring a secure trading environment. DoubleCapitals operates as an online trading platform, offering services in various financial markets. It claims to provide a user-friendly interface, educational resources, and investment opportunities across different asset classes.
To determine its legitimacy, users often examine regulatory compliance, transparency, and user experiences. However, a notable challenge arises in the case of DoubleCapitals: the absence of substantial information regarding its regulatory status and company background. Despite efforts to uncover details about its regulatory affiliations and licensing, transparency seems lacking, raising valid concerns among users regarding its legitimacy.
Unveiling DoubleCapitals: Company Information and Address
Establishing trust in an online financial platform necessitates transparency regarding its company information and physical address. However, DoubleCapitals presents a challenge in this regard, as concrete details about its company background and physical address remain elusive. This lack of transparency can contribute to apprehension among users, as the absence of doublecapitals company information raises doubts about the platform's credibility and accountability.
DoubleCapitals Complaint: Navigating User Experiences
User experiences and feedback play a pivotal role in assessing the reliability of any online platform, including DoubleCapitals. A cursory glance at online forums and review platforms reveals a spectrum of user experiences, ranging from satisfaction with the platform's services to complaints regarding issues such as withdrawal delays, unresponsive customer support, and unexpected account closures.
While positive experiences highlight the platform's potential, recurring complaints underscore areas of improvement and raise concerns about user satisfaction and trust. Addressing these complaints effectively is essential for fostering a positive user experience and enhancing the platform's credibility.
Recover money from DoubleCapitals: A Path to Resolution
In instances where users encounter difficulties such as unauthorized transactions, account discrepancies, or withdrawal issues, the process of recovering funds from DoubleCapitals can be daunting. Despite the challenges posed by the platform's opaque nature and limited avenues for recourse, several steps can be taken to seek resolution.
Firstly, users are encouraged to document all relevant transactions, communications, and interactions with DoubleCapitals. This documentation serves as crucial evidence in the event of disputes or complaints escalation. Subsequently, users can explore various channels for lodging complaints and seeking assistance, including contacting DoubleCapitals email or attempting to reach their doublecapitals contact number.
Transition from doublecapitals.com Is Now doublecapitals.co
It's noteworthy to mention that DoubleCapitals underwent a domain transition from doublecapitals.com is now doublecapitals.co. While such transitions are not uncommon in the online domain, users should exercise caution and verify the authenticity of the new domain to mitigate potential risks associated with phishing or fraudulent activities.
Navigating the realm of online trading platforms necessitates diligence, research, and a discerning approach. While DoubleCapitals presents itself as a platform for investment and trading opportunities, questions regarding its legitimacy, company information, and user experiences persist. Addressing concerns, seeking transparency, and exploring avenues for resolution are integral steps in safeguarding investments and fostering trust in online financial platforms.
As users engage with DoubleCapitals and similar platforms, vigilance, and informed decision-making remain paramount. By staying informed, exercising caution, and advocating for transparency and accountability, users can navigate the landscape of online trading platforms with greater confidence and security.
doublecapitals.com is now doublecapitals.co
0 notes
Text
bitlr
In the world of online financial platforms, the process of Bitlr login serves as the gateway for users to access a spectrum of financial services. To initiate the Bitlr login, users navigate to the platform’s official website, recently transitioning from bitlr.me is now bitlr.net. This change signals the importance of staying updated on such developments to ensure a smooth login experience.
A question often raised by users is, “Is Bitlr legit?” The legitimacy of Bitlr is a paramount concern for those engaging in financial transactions. As users explore the platform, it becomes essential to conduct thorough research to ascertain the platform’s credibility and security features, providing the peace of mind required for secure transactions.
Behind the Bitlr platform is a company that orchestrates its operations. While the specifics of the Bitlr company, including ownership and history, might not always be readily available, users are encouraged to delve into the platform’s official documentation and terms of service to gain insights into its corporate identity.
Addressing user concerns is an inevitable aspect of any online platform, and Bitlr is no exception. Common grievances, or Bitlr complaint, might include issues related to account access, transaction delays, or inquiries about the platform’s operations. In such cases, users are advised to reach out to Bitlr through official channels, providing detailed information to expedite the resolution process.
Locating the Bitlr address and contact information is vital for users seeking direct communication with the platform. While such details may not always be prominently displayed, users can typically find this information in the platform’s official documentation or by reaching out to customer support via email or phone.
The term “Bitlr” encompasses not only the platform itself but also the experiences, concerns, and inquiries of its users. Navigating the Bitlr landscape involves understanding the login process, assessing legitimacy, exploring the company, addressing user concerns, and staying informed about changes, such as the transition from bitlr.me is now bitlr.net.
For users encountering challenges such as unauthorized transactions or difficulties accessing funds, the process of how to recover my money from Bitlr becomes crucial. Following the platform’s designated procedures for dispute resolution, which may involve contacting customer support, providing transaction details, and adhering to prescribed protocols, can guide users through the recovery process.
The transition from bitlr.me is now bitlr.net is a noteworthy development that users should be aware of to ensure they are interacting with the legitimate platform. Being vigilant about such changes is crucial to avoiding potential phishing scams and maintaining the security of personal information.
In conclusion, engaging with Bitlr involves a multifaceted approach. Users are encouraged to stay informed, exercise caution, and utilize official channels, such as Bitlr email and Bitlr contact number, for support. By understanding the login process, assessing legitimacy, exploring the company, addressing concerns, and staying abreast of changes, users can navigate the Bitlr landscape with confidence.
bitlr
0 notes