#scope of online examination system
Explore tagged Tumblr posts
Text
Establishment of Direct Sale Mechanism in Turkey

Establishment of Direct Sale Mechanism in Turkey
Leave a Comment / Corporate Governance, Law, News / By pi_legal_consultancy
Establishment of direct sale mechanism in Turkey 2024 needs to be reviewed. Indeed, legal amendments to the Law on Consumer Protection needs to be comprehensively analyzed by all practitioners including Turkish business lawyers. The Law Numbered 7529 was passed through the Turkish Grand National Assembly by bringing a direct selling system as Article 47 (A) of the Law on Consumer Protection Numbered 6502.
Table of Contents
Introduction
What is the meaning of direct sale?
Understanding direct sale mechanism in Turkey?
What is meant by the direct sale mechanism in Turkey ?
What is the key revision through the Law Numbered 7529 on The Law on Consumer Protection Numbered 6502 for direct sale mechanism in Turkey?
What are key obligations for direct sale companies in Turkey?
Definition and Scope of Establishment of Direct Sale Mechanism in Turkey:
Corporate Structure Requirements of Establishment of Direct Sale Mechanism in Turkey:
Consumer Rights
Conclusion
Introduction
2024 legal amendments to the Law on Consumer Protection for the establishment of a direct sale mechanism will be examined in this article. In October 2024, Turkey enacted significant amendments to its consumer protection framework with the new article by the Law No. 7529, introducing a formal structure for direct selling within the existing Consumer Protection Law No. 6502. This development holds substantial implications for businesses, legal professionals, and consumers engaged in direct sales.
The available work will present embracing conclusions for the benefit of all practitioners in the field.
What is the meaning of direct sale?
In summary, direct sales are described as sales happening between a trademark and the end-user without any distributor or intermediary services. Sales from seller to customer can occur in person or online. Direct sale plays a vital role upon accelerating trade globally.
Understanding direct sale mechanism in Turkey?
Direct selling refers to the marketing and sale of products directly to consumers, typically outside of a fixed retail environment. This model often involves independent representatives who sell goods or services directly to end-users, leveraging personal networks and direct communication.
When a shirt trademark sells its products through its own websites, it is a good sample of direct sales, mainly known as direct to consumer (D-2-C). It means that there is no intermediary, no agency, no distributor, no other company or individual between consumer and seller.
What is meant by the direct sale mechanism in Turkey ?
Direct sale mechanism refers to a marketing system in which goods or services are on sale for consumers regardless of place. It means that consumers can buy any goods or services while working and or staying at home. It is significant to indicate that the Law Numbered 7529 introduces a direct sale mechanism by formulating 47 (A) to the Law on Consumer Protection Numbered 7529. It will have a direct impact upon corporate governance and individual suppliers.
For our work and all legal services on the matter of investment, please click our “Practice Areas”, titled “Investment Advice”.
What is the key revision through the Law Numbered 7529 on The Law on Consumer Protection Numbered 6502 for direct sale mechanism in Turkey?
The revision came into force after the circuit of Official Gazette dated October 30, 2024 and numbered 32707.
New Article 47(A) of the Law on Consumer Protection describes the meaning of direct sale mechanism in Turkey as a mechanism in which direct sellers, who are established by a direct sales company and are not employed under an employment contract, but operate as independent representatives, distributors, consultants and similar names in return for benefits such as commissions, bonuses, incentives and rewards by marketing goods or services to consumers.
For a comprehensive analysis of the company establishment in Turkey take a look at our articles on :
Establishment of A Company in Turkey
Limited Liability Company Formation
2024 Minimum Capital Amounts for Joint-Stock and Limited Liability Companies in Turkey
What are key obligations for direct sale companies in Turkey?
We should bear in mind core responsibilities for the direct sale companies in Turkey. First of all, the direct sales company is obliged to establish a system enabling the consumer to be informed properly and to submit their requests and notifications. Secondly, under paragraph 2 of the same article, a direct sale company should be a capital company.
The introduction of Article 47(A) into the Consumer Protection Law No. 6502 establishes a clear legal framework for direct selling practices in Turkey. Notable aspects of this amendment include particularly
Definition and Scope of Establishment of Direct Sale Mechanism in Turkey:
The law defines direct selling as a system where independent representatives, not bound by employment contracts, market goods or services to consumers in exchange for benefits such as commissions, bonuses, incentives, and rewards.
Corporate Structure Requirements of Establishment of Direct Sale Mechanism in Turkey:
Direct selling companies are now required to operate as capital companies and must meet additional criteria specified in forthcoming regulations.
Consumer Rights
Consumers purchasing products through direct sales are granted a 30-day unconditional right of withdrawal, enhancing consumer protection in these transactions.
The enactment of Law No. 7529 marks a pivotal step in regulating direct selling in Turkey, aligning the industry with international standards and safeguarding consumer interests. It is imperative for all stakeholders to thoroughly understand and adapt to these changes to ensure compliance and to foster a fair and transparent marketplace.
Conclusion
Taking into account the increasing market size of the direct selling industry in Turkey, Turkish policy makers intervene in such an increase by taking legal measures through a new legal amendment. This article is intended to investigate the nature of the establishment of a direct selling mechanism by the Turkish legal framework. Considering all aforementioned analysis, it is right to argue that establishment of a direct sale mechanism will have a crucial impact upon Turkish trade market in the future. Turkish business lawyers and legal advisors need to familiarize themselves with these amendments to effectively counsel clients involved in direct selling, ensuring adherence to the updated legal standards.The amendments aim to bolster consumer confidence by providing clearer rights and protections within the direct selling framework.
3 notes
·
View notes
Text
How Increased Surveillance by the China Government during the Global COVID-19 Pandemic Affects Online Communities?

In the wake of the global COVID-19 pandemic, governments worldwide, including China, intensified surveillance measures to curb the virus's spread. In this context, China's implementation of stringent surveillance, notably through Health Code Apps, has raised profound concerns about its impact on online communities. As facial recognition and data collection become intrinsic to daily life, the potential repercussions on digital spaces and the people within them demand careful examination. This discussion delves into the multifaceted consequences of increased surveillance by the Chinese government and its tangible effects on the dynamics of online communities.
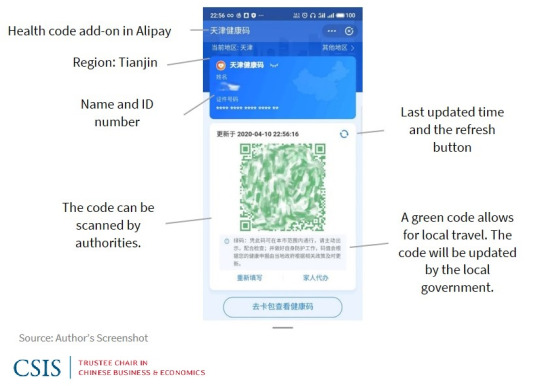

Privacy Erosion
In response to the global COVID-19 pandemic, various countries implemented measures to track and control the virus's spread, introducing tools such as contact tracing apps (Ojokoh et al., 2022), temperature checks (Qu & Lv, 2021) and travel restrictions (Burns et al., 2021). Simultaneously, In China, where stringent surveillance measures were already in place, the government leveraged technology to an even greater extent, using facial recognition and health QR codes to monitor citizens' movements. This involved the deployment of a series of applications known as "Health Code Apps," which have raised concerns about privacy erosion, particularly regarding the use of health code applications. Online communities are not immune to this erosion, as the data collected through these apps includes personal information, health status, and location details. This data is then utilized to assign one of three colours, indicating the user's health status (Ramos, 2020). However, Data is funnelled to entities like the provincial Big Data Bureau, Alibaba, and the telecommunications department, expanding the accessibility to user information, ranging from personal details to health status, location, and device specifics. This centralized model amplifies the risks of data aggregation and user re-identification, exemplified by the Beijing Health Bao system's data leak in December 2020. The incident exposed the photographs, ID numbers, and nucleic acid test information of celebrities, highlighting insufficient safeguards in place (Zhang, 2022). Online communities may find their members exposed to privacy breaches, leading to a chilling effect on open communication and expression within these digital spaces.

Potential for Abuse of Power:
The potential for the abuse of power in the context of surveillance, inadequate transparency and compliance measures is a significant concern for online communities as well. This concern is exemplified by recent events in Henan Province, where health code apps were allegedly manipulated to suppress protests related to potential losses in rural banks on the brink of collapse (Zhang, 2022). The legitimacy of these health code apps faced a setback as city officials marked over a thousand individuals as red, restricting their entry into Zhengzhou City and highlighting the vulnerability of such systems to misuse (Zhang, 2022). This incident underscores the potential for health code apps, initially designed for public health purposes, to transform into tools of surveillance, allowing government agencies to exert control under the guise of maintaining public health. The lack of stringent transparency requirements heightens the risk of these technologies being misused for purposes beyond their intended scope, which negatively impacts the freedom of expression within online communities. As governments exploit surveillance tools to monitor and influence online discussions, online communities may face challenges related to censorship and control, further emphasising the interconnected nature of surveillance concerns and their impact on digital spaces.
Technological Dependence:
Embracing extensive surveillance often involves a reliance on advanced technologies. In the case of Health Code Apps, facial recognition technology is integrated into residential area access control systems, permitting entry only to those with a green code (Ramos, 2020), which has implications for online communities. This reliance on advanced technologies may neglect more human-centric approaches to online interaction, potentially excluding or disadvantaging certain members of digital communities. As surveillance technologies become integral to online platforms, the balance between security measures and preserving the inclusivity and diversity of online communities becomes a critical consideration.
Trust Deficit:
The colour-coded system assigned by health code applications has far-reaching consequences for millions of users in their interactions within both physical and online communities. Requiring individuals to display their health codes in public transportation, shopping malls, markets, and other public places may contribute to a trust deficit between citizens and the online platforms they engage with (Jao et al., 2020). Users within online communities may question the motives behind such surveillance measures, especially if their personal information is shared without their knowledge. Rebuilding trust within online communities, once eroded by mandatory health code reliance, poses a considerable challenge, impacting the dynamics of digital social spaces.
In conclusion, the surge in surveillance by the Chinese government amid the global COVID-19 pandemic undeniably leaves a lasting imprint on online communities. The colour-coded system mandated by health code applications not only infiltrates public spaces but also infiltrates the very essence of digital interactions. This imposition triggers a tangible trust deficit within online communities as individuals question the motives behind these surveillance measures. Rebuilding trust within these virtual spaces, essential for vibrant and open communication, becomes a formidable challenge in the aftermath of mandatory health code reliance. The delicate equilibrium between bolstering security measures and safeguarding the inclusivity of online communities emerges as the linchpin for preserving the dynamic and diverse nature of these digital spaces. In essence, the impact of increased surveillance by the Chinese government is intimately intertwined with the well-being and resilience of online communities.
"Considering the implications of increased surveillance by the Chinese government during the global COVID-19 pandemic on online communities, we'd like to hear your perspective. How do you perceive the effects on privacy erosion, potential abuse of power, technological dependence, and the trust deficit within these digital spaces? Share your insights and cast your vote below."
Reference List
Burns, J., Movsisyan, A., Stratil, J. M., Biallas, R. L., Coenen, M., Emmert-Fees, K., Geffert, K., Hoffmann, S., Horstick, O., Laxy, M., Klinger, C., Kratzer, S., Litwin, T., Norris, S. L., Pfadenhauer, L. M., Von Philipsborn, P., Sell, K., Stadelmaier, J., Verboom, B., . . . Rehfuess, E. (2021). International travel-related control measures to contain the COVID-19 pandemic: a rapid review. The Cochrane Library, 2021(3). https://doi.org/10.1002/14651858.cd013717.pub2
Jao, N., Cohen, D., & Udemans, C. (2020). How China is using QR code apps to contain Covid-19. TechNode. https://technode.com/2020/02/25/how-china-is-using-qr-code-apps-to-contain-covid-19/
Ojokoh, B. A., Aribisala, B. S., Sarumi, O. A., Gabriel, A. J., Omisore, O. M., Taiwo, A. E., Igbe, T., Chukwuocha, U. M., Yusuf, T. A., Afolayan, A., Babalola, O., Adebayo, T., & Afolabi, O. (2022). Contact Tracing Strategies for COVID-19 Prevention and Containment: A scoping review. Big Data and Cognitive Computing, 6(4), 111. https://doi.org/10.3390/bdcc6040111
Qu, J., & Lv, X. (2021). The response measures to the coronavirus disease 2019 outbreak in China. Open Forum Infectious Diseases, 8(2). https://doi.org/10.1093/ofid/ofab014
Ramos, L. F. (2020). Evaluating privacy during the COVID-19 public health emergency. The ACM Digital Library, 176–179. https://doi.org/10.1145/3428502.3428526
Zhang, X. (2022). Decoding China’s COVID-19 health code apps: the legal challenges. Healthcare, 10(8), 1479. https://doi.org/10.3390/healthcare10081479
4 notes
·
View notes
Text
SESSION 6. ELECTRONIC TRANSACTIONS AND CONTRACTING
READ: ICTL TEXTBOOK CHAPTER 3 (COR2226* & LAW405)
OPTIONAL REFERENCE: L&T BOOK CHAPTER 9 (COR2226* & LAW405)
Electronic Contracting: In Singapore, contract law is largely based on the English common law and has developed on that basis, as judge-made law. Contract law is supplemented by some statutes and provisions in a series of legislations. The Electronic Transactions Act (Cap 88, 2011 Rev Ed) (ETA), which entered into force on 1 July 2010 and replaced the original Act that was first enacted in July 1998, specifically addresses issues relating to electronic commerce. The first enactment contained provisions drawn from the UNCITRAL Model Law on Electronic Commerce of 1996 (MLEC) and the UNCITRAL Model Law on Electronic Signatures of 2001 (MLES). The re-enactment contains some amendments, including provisions drawn from the Use of Electronic Communications in International Contracting of 2005 (CUECIC) as well as a re-ordering of the provisions.
The Electronic Transactions Act: What are the objectives and the effect of the UNCITRAL Model Laws on E-Commerce and Signatures as well as the CUECIC? What is their relationship with the ETA? What are the potential problems of modern electronic forms of communication (and electronic forms of documents and signatures) for contract law? To what extent have the revised ETA of 2010 resolved the outstanding issues relating to electronic transactions in general, and electronic contracting in particular? What are the types of matters or transactions that fall outside the scope of the Act? The IMDA and AGC spent several years reviewing the scope of the ETA, specifically relating to the adoption of UNCITRAL Model Law on Electronic Transferable Records. The model law aims to promote functional equivalence to electronic ETRs such as cheques, promissory notes, bills of exchange, bills of lading, etc. and give them full legal recognition under substantive law. These amendments entered into force on 19 March 2021.
Consider the various online business models. What are the various modern forms of electronic contract formation and communications, and to what extent are electronic notices legally binding or acceptable (e.g. as sufficient notification of purpose under the PDPA).
What is the purpose and effect of section 14 of the ETA? What are browsewrap and clickwrap contracts and, in your opinion, are they legally binding?
Compare and contrast the doctrine of unilateral mistake that is applied to the electronic contracting context for the vitiation of a contract to section 16 of the ETA. What was the purpose of the new provision and what are the potential problems that may arise in relation to it? Examine the Digilandmall and Quoine decisions on the doctrine of unilateral mistake.
What is the reason and basis for the use of automated message systems for contract formation and what are some examples of modern transactions that involves the use of such systems in transactions. Is there a necessity for such a provision (section 15 of the ETA) and does existing contract law not provide a legal basis for such contracts? and the issue of legal responsibility, rights and liability.
What is the law on electronic signatures (and records)? What are the challenges of electronic signatures as compared to physical ones? What is the objectives and purpose of the relevant provisions under the ETA (Parts II & III and 2nd & 3rd Schedules only) in relation to them? What is the difference, if any, between an “electronic”, a “secured electronic” and a “digital” signature?
Cases: (not necessary reading for COR2226)
Quoine Pte Ltd v B2C2 Ltd [2020] SGCA(I) 02
Joseph Mathew and another v Singh Chiranjeev and another [2009] SGCA 51; [2010] 1 SLR 338 (CA)
Wee Soon Kim Anthony v Lim Chor Pee and another [2005] 4 SLR 367 (HC); 2 SLR 370 (CA)
SM Integrated Transware Pte Ltd v. Schenker Singapore (Pte) Ltd [2005] 2 SLR (R) 651
Chwee Kin Keong v. Digilandmall.com Pte Ltd [2004] 2 SLR (R) 594
Statutes and Standards: (for reference in class, relevant provisions will be highlighted in class)
Electronic Transactions Act (ETA) 2010
References: (optional)
Rosemary Lee, Annotated Statutes of Singapore: Electronic Transactions Act LexisNexis (2012) (available in SMU Course Reserves)
*BACKGROUND READING FOR AN INTRODUCTION TO RELEVANT ASPECTS OF CONTRACT LAW FOR COR2226:
Chapter 8 The Law of Contract, Sections 1, 2 & 9 only (by Singapore Law Watch). (<<< CLICK FOR LINK)
2 notes
·
View notes
Text
The political institutions of the European Union are in turmoil with a cash-for-favours corruption scandal engulfing the European Parliament with the potential to spread.
Former European Parliament Vice President Eva Kaili is one of four people in detention, charged by Belgian prosecutors with "participation in a criminal organisation, money laundering and corruption."
She has already been booted out of her political parties and affiliations and stripped of her vice presidency, accused of accepting bribes from Qatar.
Gleaming speeches about the Gulf state in the European Parliament, voting in favor of files related to Qatar in committees, on which she didn't sit, and attending numerous unregistered events in the country are the alleged links between Kaili and Doha.
In a statement published online, the Mission of Qatar to the EU called the allegations "baseless and gravely misinformed."
While official details of the scope and depth of the police investigation in Belgium remain scant, the activities of members of the European Parliament (MEPs) and other EU bodies will now come under increased scrutiny.
EU experts are questioning whether the existing anti-corruption measures in place suffice.
"When there is highly complex and entrenched policymaking like there is in the EU, it becomes untransparent, and then it makes it easier to buy influence," Jacob Kirkegaard from the German Marshall Fund told DW News. "You can buy a vice president of the European Parliament for €600k! Are they really that cheap?"
"This is clearly a woman who wasn't afraid of being caught. It indicates that whatever measures and processes the European Parliament has, have no deterrent effect," he said. "Even stupid people, if they were afraid, wouldn't do it.”
Transparency measures
So what measures are in place at the EU?
It has a database, in which NGOs, lobby groups, consultants, charities, and any other organizations wanting to influence lawmaking must register.
All those listed in the Transparency Register are required to declare their budgets, and any donations above €10,000 (ca. $10,545) for NGOs.
Significantly though, Fighting Impunity, the NGO at the heart of the current corruption scandal, is not on the register.
Its president, former Italian MEP Pier Antonio Panzeri, is also in detention. And Eva Kaili's partner Francesco Giorgi works there too. Furthermore, Fighting Impunity shares an office with the Italian non-profit No Peace Without Justice, whose director was also arrested in this case.
"With the loopholes in the system, this was bound to happen," Paul Varakas, president of the Society of European Affairs Professionals (SEAP), which helps lobbyists apply to the Transparency Register, told DW.
In 2021, the European Parliament refused to apply the principle of "strict conditionality" attached to the Transparency Register, which would have forced them to only meet with registered lobbyists.
Senior officials in the European Commission, the EU's executive arm, are already bound to this principle and only allowed to meet with lobbyists who are listed on the register.
But the MEPS argued that it would infringe on their "freedom of mandate" and rejected moves to force them to disclose all their meetings.
"That's how they [Fighting Impunity] were doing it," said Varakas. "You had an NGO influencing decision-making without having to disclose anything. They were invited by an MEP who didn't have to declare. It was simple for them."
SEAP and other organizations are now saying that while mandatory registration (and disclosure requirements attached to it) might be burdensome for smaller actors, such as NGOs, the pressure on the European Parliament to fall in line on the "conditionality principle" will be immense.
In the wake of the scandal, European Commission President Ursula von der Leyen has repeated a call for an ethics body to be set up that would oversee all EU institutions.
"We have one with very clear rules internally in the Euroepan Commission and I think it is time to discuss where we could establish this overall for all EU institutions" she said at a press conference in Brussels on Monday.
Diplomatic immunity
MEPS also enjoy diplomatic immunity so that they can carry out their political work without fear of prosecution.
According to a Protocol on privileges and immunities of the EU, they cannot "be subject to any form of inquiry, detention or legal proceedings in respect of opinions expressed or votes cast by them in the performance of their duties."
Immunity is not valid, however, "when a Member is found in the act of committing an offence and shall not prevent the European Parliament from exercising its right to waive the immunity of one of its Members."
If necessary, MEPs do have the right to request their immunity is upheld but the press office of the European Parliament said so far no request of that nature had been made by Eva Kaili.
Prosecuting judges in Belgium have also not asked for the immunity to be lifted.
"If there is no request for immunity to be withdrawn then that suggests that the judge has concluded that the criteria have been met for immunity to no longer apply," said European Parliament spokesperson Jaume Duch in Strasbourg.
In the past, immunity requests have been made in regard to extradition requests. But because the crimes are alleged to have been committed in Belgium, extradition would not apply in this case.
4 notes
·
View notes
Text
Best IGCSE English Exam Preparation in Singapore with Kiya Learning

The International General Certificate of Secondary Education (IGCSE) is a widely recognized qualification for students seeking to excel academically on an international level. With English being one of the core subjects, preparing for the IGCSE English examination can be both rewarding and challenging. In Singapore, many students turn to expert resources and personalized guidance to ensure their success. Among the top providers of IGCSE English exam preparation is Kiya Learning, a platform known for delivering exceptional learning experiences tailored to individual needs.
Introduction to IGCSE English in Singapore
Start by discussing what the IGCSE English examination entails, covering aspects like curriculum scope, grading system, and types of papers (e.g., Core vs. Extended, Language and Literature). Highlight the importance of IGCSE English in academic progression and career aspirations for students in Singapore.
Emphasis on Communication Skills: Elaborate on why mastering English is essential for students in Singapore's globalized environment.
Challenges Faced by Students: Touch on common challenges, including complex texts, grammar intricacies, and time management during exams.
The Importance of Quality Preparation
Discuss the factors that contribute to effective exam preparation:
Personalized Learning: Tailoring the curriculum based on each student's strengths and weaknesses.
Comprehensive Resources: Access to study guides, past papers, and interactive lessons.
Skill Development: Focus on reading comprehension, writing, speaking, and listening skills.
Why Choose Kiya Learning for IGCSE English Exam Preparation?
Provide an overview of Kiya Learning's unique offerings that make it a standout option for IGCSE English preparation in Singapore:
Customized Learning Plans
Explain how Kiya Learning tailors lessons to suit each student’s pace and learning style, ensuring no one is left behind.
Offer examples of how the platform adapts to specific needs, such as intensive grammar sessions or literature analysis.
Experienced Tutors
Highlight the expertise and credentials of Kiya Learning's English tutors, emphasizing their familiarity with IGCSE standards.
Share testimonials or success stories of students who have excelled under their guidance.
Interactive and Engaging Lessons
Describe how Kiya Learning leverages technology and creative teaching methods to make lessons interactive and enjoyable.
Examples include online quizzes, video tutorials, and collaborative group discussions that enhance learning.
Mock Exams and Practice Papers
Explain the importance of regular practice and how Kiya Learning provides mock exams modeled after actual IGCSE tests.
Detail how feedback and score analysis help students track their progress and identify areas for improvement.
Support for Both Language and Literature Components
Highlight Kiya Learning's comprehensive coverage of both language skills and literature components, ensuring students are well-rounded in their preparation.
Share specific techniques taught, such as essay structuring, text analysis, and persuasive writing.
Tips for IGCSE English Exam Success
Offer general advice and study strategies that align with Kiya Learning’s approach:
Active Reading: Encourage students to read widely, including novels, articles, and essays, to enhance comprehension and vocabulary.
Consistent Practice: Stress the importance of writing essays, summarizing texts, and engaging in discussions.
Effective Time Management: Share techniques to manage exam time effectively, such as quick planning for essays and prioritizing questions.
Seek Feedback: Advise students to seek regular feedback from their Kiya Learning tutors to pinpoint weaknesses and work on them.
Success Stories from Kiya Learning
Share case studies or success stories of students who prepared for the IGCSE English exam with Kiya Learning and achieved outstanding results. Include anecdotes that demonstrate the transformative power of personalized learning and dedicated guidance.
Example 1: A student who improved their writing score by mastering essay techniques taught at Kiya Learning.
Example 2: How Kiya Learning’s literature classes helped a student develop a deeper appreciation for classical texts and perform well in the literature exam.
Testimonials from Parents and Students
Include quotes from parents and students who have benefited from Kiya Learning’s IGCSE English exam preparation services. These testimonials can reinforce the credibility and effectiveness of the platform.
Kiya Learning’s Commitment to Excellence
Wrap up with a section on Kiya Learning’s mission and dedication to helping students excel in their academic pursuits, particularly IGCSE English. Emphasize how their holistic approach prepares students not just for exams but for lifelong communication skills.
Conclusion
Reiterate the importance of choosing the right preparation for the IGCSE English exam and how Kiya Learning stands out as a premier choice in Singapore. Invite readers to explore Kiya Learning’s programs and book a consultation or trial session to experience the difference.
CONTACT US -
Instagram - https://www.instagram.com/kiyalearning/ https://www.instagram.com/kiyalearningsingapore/
Website URL -
https://kiyalearning.com/
Business Email - [email protected]
Whataap Link - https://wa.me/message/SABJEJKZBD5IE1
0 notes
Text
Voyages Prive - Get the Lowest Holiday Deals With Voyages Prive
Whether you crave a luxury beach break, chic city escape, rustic country retreat or active ski adventure, voyages prive has the perfect getaway for you. Its exclusive deals are sourced through specially negotiated agreements with luxury travel partners, and offer members savings of up to 75%.
Its expert negotiators unlock savings that seem too good to be true. They also take care of all the small details, freeing you up to focus on the anticipation of your holiday.
Exceptional Value
Voyage Prive’s expert negotiators unlock voyages prive that make high-end travel seem downright affordable. Members can indulge in a five-star resort, upgrade their flight or extend their stay to immerse themselves in the local culture—without breaking the bank.
The streamlined booking process is designed for user convenience, allowing guests to tailor their holiday to match their aspirations with ease. Detailed descriptions, high-quality images and virtual tours give travellers the ability to visualise their dream getaway before booking.
To maximize the value of their Black Friday travel deals, customers should be prepared to act fast. Deals tend to sell out quickly and bookings must be completed within the specified timeframe. It’s also wise to be flexible with travel dates, as this can unlock even greater savings. Lastly, it’s important to carefully examine the terms and conditions of each offer before making a decision. This diligence prevents unwelcome surprises down the line.
Unparalleled Choice
As a member, you will be privy to luxury holiday deals, ranging from tropical beach getaways to European city tours and serene UK countryside escapes. These are curated by travel experts to suit a variety of tastes and budgets.
With each deal, voyages prive offers the chance to customise your package with upgrades, additions, and experiences such as guided tours or culinary excursions. A dedicated booking process accommodates your specific requirements, enabling you to secure your ideal holiday with ease.
To support their business growth, Voyage Prive needed to upgrade their PIM / DAM solution. The Clever Age team conducted a detailed scoping phase, understanding the complexity of their information data model and functional architecture. Following the scope, a number of PIM solutions were shortlisted and tested. In the end, Voyage Prive selected the MaPS System solution. This enabled them to benefit from the PIM functionality and MDM capabilities. It also offered a high level of integration with their CMS, resulting in an agile and cost-effective solution.
Stress-Free Planning
Voyage Prive offers a wide selection of holiday packages to some of the world's most exciting destinations. Whether you're looking for a tropical beach escape, chic city break or rustic country retreat, there's something to suit your mood and budget.
Launched in France in 2006, Voyage Prive is a leading members-only luxury travel club. Its online private sales model means that members can find great deals to exotic locations at a fraction of their usual cost.
With dozens of new travel packages sold daily across countries, the Voyage Prive business demands a sophisticated information management system. To meet this need, Clever Age recommended the use of a PIM and DAM solution from MaPS System.
Customer Service
We’re dedicated to making sure your trip goes que faire a malte. Our international team of travel experts is always on-hand to help, providing 24/7 support via phone, email and live chat so we can take care of any unforeseen circumstances.
No matter what kind of vacation you want, we’ll find the perfect solution for you. Choose from a wide range of packages, including short and long breaks in France or Europe, sea and sun holidays, ski vacations, road trips and circuits.
To help you find the perfect vacation package, simply enter your desired departure airport and destination, select your dates and number of people. You can also refine your search results further by selecting the preferences that are important to you. This will make it easier to find the perfect vacation package for you.
0 notes
Text
Understanding ECG Test Prices and How to Find an ECG Test Near You

If you're feeling an ECG (electrocardiogram) test, it’s essential to comprehend the ECG test price and how to find an ECG test near me. An ECG is a vital tool used to keep the heart's electrical activity and see monsters such as arrhythmias, heart spells, and other heart-related conditions. Whether it’s for regular wellness monitor or to analyze signs, knowing the cost and availability of the test can help you make an educated decision.
Factors That Affect ECG Test Price
Depending on the building, site, and the type of ECG test you need. For instance, a normal resting ECG may cost less than a pressure ECG, which requires more tools and time. If you have insurance, it may cover the price of the trial, but out-of-pocket costs will still depend on your insurance program’s scope. Geographic area also plays a major role in the pricing of medical trials. In urban locations, you may find higher costs for ECG tests due to higher overhead costs of medical facilities. On the other writing, rural or smaller towns may offer more cheap rates. It’s even a good idea to compare prices at different clinics, clinics, or diagnostic means in your area before preparing the trial.
How to Find an ECG Test Near Me
Finding an ECG test near me is simple thanks to the internet and healthcare directories. You can explore online using terms like “ECG test near me” or “heart check-up centers nearby,” and you’ll probably find several choices. Many clinics and hospitals offer ECG examinations, and some specialized heart centers provide avant cardiovascular testing. If you're using a healthcare insurance provider, you can also ask them for a list of networked diagnostic posts or hospitals where you can get the test at a discounted rate. You can also ask your direct care doctor for a referral to a trusted clinic or facility that offers ECG tests. Most hospitals have online booking systems where you can schedule appointments in advance, making the process even more suitable.
Conclusion When considering an ECG test price, it’s essential to research your options to find the most affordable and dependable service. By searching for an ECG test near me you can easily locate a nearby healthcare facility that offers this important test. Place, prices may vary, so compare your options and check if your insurance covers the cost. Whether you're monitoring your heart health or managing potential concerns, an ECG test is a valuable diagnostic tool for seeing heart conditions early.
1 note
·
View note
Text
How to Protect Your Invention with a Patent: Key Tips for First-Time Applicants
Inventions are the building blocks of innovation, and protecting them with a patent is essential to safeguarding your ideas from being copied or exploited by others. If you’re a first-time applicant, the patent registration process may seem complex, but understanding key steps and strategies can make it manageable. Here’s a guide on how to protect your invention with a patent and tips to make your first application successful.
Understand What a Patent Protects
A patent is a legal right granted to inventors that provides them with exclusive control over their invention for a set period, usually 20 years from the filing date. This protection allows the patent holder to prevent others from making, using, selling, or distributing the invention without permission. However, it’s important to note that a patent is only granted for inventions that are new, useful, and non-obvious.
Conduct a Thorough Patent Search
Before you start the patent application process, perform a patent search to ensure your invention is unique and hasn’t been patented by someone else. There are various online databases, such as the United States Patent and Trademark Office (USPTO) database or the European Patent Office (EPO) database, where you can search for similar inventions. You may also consider hiring a patent attorney or search professional to help with this task. A thorough search can save time and costs associated with a rejected application.
Determine the Type of Patent You Need
There are three primary types of patents you may consider:
Utility Patents: For inventions that have a functional purpose, such as machinery, processes, and manufactured items.
Design Patents: For inventions related to the ornamental or aesthetic aspects of a product.
Plant Patents: For new, distinct varieties of plants that have been asexually reproduced.
Most first-time inventors seek utility patents, as these cover inventions that provide a new and valuable function. Identifying the correct type of patent is essential to avoid unnecessary costs and delays.
Decide Between a Provisional and Non-Provisional Patent Application
Provisional Patent Application: This is a temporary application that lets you secure an early filing date for your invention without starting the formal patent examination process. It is less expensive and doesn’t require a formal patent claim, which provides you with up to 12 months to test or improve your invention before filing a non-provisional application.
Non-Provisional Patent Application: This is the formal application required to start the patent examination process. It includes a detailed description of the invention and its claims.
A provisional application can be a strategic first step for first-time applicants. It allows you to establish your invention's “patent pending” status while providing more time for development or funding.
Prepare Detailed Documentation
The success of your patent application largely depends on how well you document your invention. Key elements to include are:
Detailed Description: Describe your invention in detail, including its purpose, how it works, and its unique features.
Drawings and Diagrams: Visual representations help clarify the structure, design, and functionality of your invention.
Claims: These are statements that define the scope of your invention’s protection. Claims are highly technical and must be specific, so consulting with a patent professional can help you draft solid and comprehensive claims.
Consider Professional Assistance
Although you can file a patent application on your own, navigating the patent system can be challenging. Working with a patent attorney or a registered patent agent is recommended, especially for first-time applicants. These professionals can help you draft claims, conduct a thorough patent search, and navigate the application process. While hiring a patent attorney adds cost, it can significantly increase your chances of a successful application.
Submit Your Patent Application
After gathering all documentation, submit your application to the appropriate patent office (e.g., the USPTO if you’re in the U.S.). The application will undergo examination to verify that it meets all patent requirements.
The patent office may request additional information, modifications, or explanations during the examination. Patience is essential, as it can take several months or even years to obtain a patent, depending on the complexity of the invention and backlog at the patent office.
Respond Promptly to Office Actions
During the examination process, the patent office may issue office actions — requests for additional information, clarifications, or objections to specific claims. Address these actions promptly and consult with your patent attorney to prepare a thorough response. Failure to respond on time could result in your application being abandoned.
Maintain Your Patent
Once granted, patents require periodic maintenance fees to keep them active. These fees are necessary to keep your patent valid over its term. Be sure to stay on top of these payments, as missing one can lead to the loss of protection for your invention.
Enforce Your Patent Rights
Finally, remember that securing a patent does not automatically prevent others from infringing on your invention. As the patent owner, it’s your responsibility to monitor the market and take action if someone infringes upon your rights. This could involve sending cease-and-desist letters or, in severe cases, pursuing legal action.
Conclusion
Securing a patent for your invention is a valuable investment in protecting your intellectual property. First-time applicants can navigate the process more effectively by conducting thorough research, preparing detailed documentation, and potentially seeking professional assistance. Protecting your invention with a patent not only grants you exclusive rights but also gives you the freedom to bring your ideas to life, ensuring your innovations stay uniquely yours.
0 notes
Text
Global Cyber Security Managed Services Market Analysis 2024: Size Forecast and Growth Prospects
The cyber security managed services global market report 2024from The Business Research Company provides comprehensive market statistics, including global market size, regional shares, competitor market share, detailed segments, trends, and opportunities. This report offers an in-depth analysis of current and future industry scenarios, delivering a complete perspective for thriving in the industrial automation software market.
Cyber Security Managed Services Market, 2024report by The Business Research Company offers comprehensive insights into the current state of the market and highlights future growth opportunities.
Market Size - The cyber security managed services market size has grown rapidly in recent years. It will grow from $13.80 billion in 2023 to $15.27 billion in 2024 at a compound annual growth rate (CAGR) of 10.7%. The growth in the historic period can be attributed to the rise in cyber threats, rising digital transformation initiatives, demand for security-related managed services, increasing adoption of managed risk and compliance services, and increasing adoption of cloud computing.
The cyber security managed services market size is expected to see rapid growth in the next few years. It will grow to $23.21 billion in 2028 at a compound annual growth rate (CAGR) of 11.0%. The growth in the forecast period can be attributed to a focus on incident response and resilience, increased emphasis on compliance and risk management, growth of managed security, focus on data privacy and protection, and surging demand for digital privacy systems. Major trends in the forecast period include zero trust security frameworks, advanced technologies, advanced threat detection technologies, integration of artificial intelligence (AI) and machine learning (ML), and increasing partnerships.
Order your report now for swift delivery @ https://www.thebusinessresearchcompany.com/report/cyber-security-managed-services-global-market-report
Scope Of Cyber Security Managed Services MarketThe Business Research Company's reports encompass a wide range of information, including:
Market Size (Historic and Forecast): Analysis of the market's historical performance and projections for future growth.
Drivers: Examination of the key factors propelling market growth.
Trends: Identification of emerging trends and patterns shaping the market landscape.
Key Segments: Breakdown of the market into its primary segments and their respective performance.
Focus Regions and Geographies: Insight into the most critical regions and geographical areas influencing the market.
Macro Economic Factors: Assessment of broader economic elements impacting the market.
Cyber Security Managed Services Market Overview
Market Drivers -The rising number of online security threats is expected to propel the growth of the cyber security managed services market going forward. Online security threats encompass a wide range of malicious activities to compromise the security, integrity, and privacy of information and systems connected to the internet. The rise in online security threats is due to the growth of connected devices, emerging cyber threats, cryptocurrencies and decentralized finance (DeFi), and software and system vulnerabilities. Cybersecurity-managed services play a crucial role in defending organizations against the rising number of online security threats by providing continuous monitoring, advanced threat detection, rapid incident response, and comprehensive security solutions. For instance, in April 2023, according to the Identity Theft Resource Center, a US-based non-profit organization, the number of data breach incidents reported increased by 68% in 2022, with 1,862 breaches reported compared to 1,108 breaches in 2021. Therefore, the rising number of online security threats drives the cyber security managed services market.
Market Trends - Major companies operating in the cyber security managed services market are focused on developing innovative technologies, such as holistic digital protection, to enhance their offerings and attract a larger customer base. Holistic digital protection is a comprehensive approach to safeguarding an organization’s digital assets, encompassing various security measures, practices, and technologies. For instance, in February 2024, Astreya, a US-based IT solutions provider, launched its Cybersecurity Managed Services. Astreya's cybersecurity managed services offer a comprehensive suite of solutions, including identity management, endpoint protection, and risk management. These services are designed to seamlessly integrate with existing infrastructures, providing robust security layers and proactive defense mechanisms. This new service integrates cutting-edge technologies with expert-driven strategies to ensure strong protection against various cyber threats.
The cyber security managed services market covered in this report is segmented –
1) By Service: Managed Detection And Response (MDR), Incident Management, Managed Vulnerability, Identity And Access Solution, Other Services 2) By Security Type: Network Security, Endpoint Security, Application Security, Other Security Types 3) By Enterprise Type: Small And Medium Size Enterprise, Large Enterprise 4) By Industry: Banking, Financial Services And Insurance (BFSI), Information Technology (IT) And Telecommunications, Retail, Healthcare, Government, Manufacturing, Travel And Transportation, Energy And Utilities, Other Industries
Get an inside scoop of the cyber security managed services market, Request now for Sample Report @ https://www.thebusinessresearchcompany.com/sample.aspx?id=15780&type=smp
Regional Insights - North America was the largest region in the cyber security managed services market in 2023. The regions covered in the cyber security managed services market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa.
Key Companies - Major companies operating in the cyber security managed services market are Microsoft Corporation, Verizon Communications Inc., AT&T Inc., Dell Technologies Inc., Hitachi Ltd., Accenture plc, International Business Machines Corporation, Cisco Systems Inc., Oracle Corporation, Honeywell International Inc., Symantec Corporation (Broadcom Inc), Fujitsu Limited, Hewlett Packard Enterprise Development LP, Tata Consultancy Services Limited, Toshiba Corporation, Capgemini SE, Lumen Technologies Inc., DXC Technology Company, BDO Global, Atos SE, Wipro Limited, Palo Alto Networks Inc., Fortinet Inc., Optiv Security Inc., Check Point Software Technologies Ltd, McAfee LLC, Trend Micro Inc., CrowdStrike Inc., Rapid7 Inc., Secureworks Inc., Trustwave Holdings Inc.
Table of Contents
Executive Summary
Cyber Security Managed Services Market Report Structure
Cyber Security Managed Services Market Trends And Strategies
Cyber Security Managed Services Market – Macro Economic Scenario
Cyber Security Managed Services Market Size And Growth …..
Cyber Security Managed Services Market Competitor Landscape And Company Profiles
Key Mergers And Acquisitions
Future Outlook and Potential Analysis
Appendix
Contact Us: The Business Research Company Europe: +44 207 1930 708 Asia: +91 88972 63534 Americas: +1 315 623 0293 Email: [email protected]
Follow Us On: LinkedIn: https://in.linkedin.com/company/the-business-research-company Twitter: https://twitter.com/tbrc_info Facebook: https://www.facebook.com/TheBusinessResearchCompany YouTube: https://www.youtube.com/channel/UC24_fI0rV8cR5DxlCpgmyFQ Blog: https://blog.tbrc.info/ Healthcare Blog: https://healthcareresearchreports.com/ Global Market Model: https://www.thebusinessresearchcompany.com/global-market-model
0 notes
Text
Trademark Registration: A Complete Guide to Protecting Your Brand
In today’s competitive business world, creating a unique identity for your brand is crucial. This identity often takes the form of logos, slogans, brand names, or other distinctive signs that set your products and services apart. Trademark Registration is the legal process that helps protect these unique brand elements, ensuring they remain exclusive to you and preventing others from unauthorized use. Here’s a comprehensive guide to Trademark Registration, including who can apply, the types of trademarks eligible for registration, and the benefits it brings.

What is a Trademark?
A trademark is any symbol, word, name, logo, design, or combination thereof that distinguishes the goods or services of one business from those of others. Trademarks can include:
Logos, symbols, or emblems
Slogans and taglines
Brand names
Shapes of goods and packaging
Color combinations
Trademark Registration legally protects these brand identifiers, offering a range of benefits that help you safeguard your business’s identity.
Importance of Trademark Registration
Registering a trademark is not mandatory but highly recommended for several reasons:
Legal Protection: A registered trademark provides the owner exclusive rights to use it for specific goods or services.
Brand Recognition: It enhances the brand’s visibility and helps consumers identify and distinguish it from competitors.
Prevention Against Infringement: Trademark Registration gives legal grounds to prevent others from using or copying your brand elements.
Builds Goodwill: A registered trademark reflects the brand’s credibility and helps build consumer trust.
Asset Creation: Registered trademarks can be valuable intangible assets for a business, providing an edge for future expansion or brand licensing.
Who Can Apply for Trademark Registration?
Anyone claiming to be the proprietor of a mark can apply for its registration. This includes:
Individuals
Companies
Partnership firms
Hindu Undivided Families (HUFs)
Associations of persons
Joint proprietors
Trusts and societies
Government authorities or undertakings
The trademark applicant need not be using the trademark at the time of filing. They may also apply for a proposed mark intended for future use.
Types of Trademarks that Can Be Registered
Trademarks eligible for registration may fall under any of the following categories:
In Use: Trademarks that are currently in use can be registered to secure legal rights over them.
Proposed to Be Used: Even if a trademark isn’t yet in use, it can still be registered if the applicant intends to use it shortly.
Assigned to a Future Entity: A trademark can be registered for a company that is yet to be established under the Companies Act, 2013, intending to use the mark once the company is formed.
Classification of Goods and Services
Trademarks are registered under specific categories based on the goods or services they represent. This classification system follows the International Classification of Goods and Services, known as the NICE Classification, established by the World Intellectual Property Organization (WIPO). The classification includes 45 classes, where classes 1 to 34 pertain to goods, and classes 35 to 45 cover services. Proper classification is essential as it defines the scope of protection for the trademark.
Steps to Register a Trademark
Trademark Search: Conduct a trademark search to ensure that the mark you wish to register is unique and not similar to existing trademarks.
Application Filing: Submit the trademark application to the Office of the Registrar of Trademarks. Applications can be filed online or offline.
Examination: The application undergoes examination, where the Registrar checks for compliance and potential conflicts with existing trademarks.
Publication: If approved, the trademark is published in the Trademark Journal to invite objections from third parties, if any.
Registration: If no objections arise or are successfully resolved, the trademark proceeds to registration, and a Trademark Registration Certificate is issued.
Benefits of Trademark Registration
Registering a trademark provides several advantages, such as:
Exclusive Rights: The owner has exclusive rights to use the trademark for the goods and services it is registered for.
Brand Security: Registered trademarks allow businesses to protect their brand’s goodwill and prevent dilution by unauthorized third-party use.
Legal Recourse: In case of trademark infringement, registered owners can take legal action to safeguard their brand.
Intangible Asset Creation: A registered trademark becomes an asset that can be licensed, franchised, or even sold.
Enhanced Market Value: A registered trademark boosts a brand’s image and value, increasing its attractiveness for investments and partnerships.
Trademark Validity and Renewal
A trademark registration is valid for 10 years from the date of application. However, it can be renewed indefinitely for subsequent periods of 10 years each, provided the renewal fees are paid on time. Failing to renew a trademark may result in its removal from the registry, which means the proprietor would lose exclusive rights to the mark.
Trademark Registration Costs
The cost of trademark registration varies depending on whether the applicant is an individual, a company, or a startup. India offers a reduced fee for individuals, small businesses, and startups to encourage trademark registration among emerging businesses. Costs may include:
Application Fees: Vary depending on the applicant category.
Professional Fees: If an agent or attorney is involved.
Renewal Fees: Due every 10 years to keep the registration active.
Trademark Infringement and Remedies
Trademark infringement occurs when someone uses a registered trademark without the owner’s consent. If your registered trademark is infringed upon, you have the right to take legal action, which may include:
Filing a Suit: The registered owner can file a lawsuit for trademark infringement, seeking damages or an injunction to stop the unauthorized use.
Seeking Compensation: Infringement suits can lead to monetary compensation for losses incurred.
Preventive Measures: Registering a trademark serves as a public notice of ownership, deterring potential infringers.
Conclusion
Trademark Registration is an essential process for businesses looking to protect their brand identity and enhance their market presence. It provides exclusive rights, ensures legal protection, and helps build a positive brand image. Whether you are an individual, a startup, or an established business, securing a trademark is a valuable investment in your brand’s future.
0 notes
Text
How To Choose Quality Online Plumbing Parts For Your Needs?
When it comes to home plumbing repairs and installations, selecting the right parts is crucial to ensure functionality and longevity. With a plethora of options available online, finding quality online plumbing parts can be a daunting task.
However, by understanding your requirements and applying a systematic approach, you can make informed decisions that will benefit your plumbing projects. This guide will walk you through the essential steps to effectively choose quality online plumbing parts.

Assess Your Requirements
Before diving into the vast market of online plumbing parts, it is essential to assess your specific needs accurately. Consider the following:
Project Scope: Determine whether you are undertaking a minor repair, such as fixing a leaking faucet, or a more extensive renovation that involves replacing pipes or fixtures.
Parts Needed: Identify the exact parts you require. This might include valves, pipes, fittings, faucets, or specialised components.
Understanding your requirements allows you to narrow your search and focus on relevant options.
Prioritise Quality
The integrity of your plumbing system hinges on the quality of the parts you use. Low-quality components can lead to leaks, failures, and costly repairs. Here are some key considerations for ensuring quality in your online plumbing parts:
Brand Reputation: Opt for products from reputable manufacturers known for their commitment to quality and durability. Established brands often provide warranties, which indicates their confidence in their products.
Customer Reviews: Read reviews and ratings from other customers. Feedback can provide valuable insights into the reliability and performance of specific products.
Investing in high-quality online plumbing parts will yield better results and peace of mind in the long run.
Ensure Compatibility
Compatibility is a critical factor when selecting online plumbing parts. Mismatched components can result in installation challenges and project delays. To avoid such issues, adhere to the following guidelines:
Accurate Measurements: Carefully measure existing fixtures, pipes, and fittings before placing an order. This will help ensure that the parts you purchase will fit correctly.
Manufacturer Specifications: Review the product descriptions for compatibility information. Many manufacturers provide detailed specifications that will help you confirm whether a part will work with your existing system.
By taking these precautions, you can avoid the inconvenience of returning incorrect online plumbing parts.
Review Warranty and Return Policies
Before finalising your purchase, examining the warranty and return policies offered by the supplier is prudent. A clear understanding of these policies can protect you from potential issues:
Warranties: A robust warranty indicates that the manufacturer stands behind their product. This is particularly important for significant investments, as it assures you can obtain a replacement or repair if necessary.
Return Policies: Familiarise yourself with the supplier’s return policy. A flexible return process can save you time and money if you need to exchange or return an item.
Evaluating these aspects will help you make more secure purchases and enhance your shopping experience.
Seek Expert Guidance
When navigating the world of online plumbing parts, feel free to seek expert guidance when needed. Resources include:
Professional Plumbers: Consulting a licensed plumber can provide clarity if you are still deciding which parts to choose. Their expertise can help you make the right decisions based on your project requirements.
Online Forums and Communities: Discussions with fellow homeowners and professionals can provide additional insights and recommendations. Websites like Reddit or specialised plumbing forums are great platforms for sharing knowledge.
Consulting professionals can enhance your understanding of which online plumbing parts are best suited for your needs.
Conclusion
Selecting quality online plumbing parts is essential for the success of any plumbing project. You can confidently navigate the online marketplace by assessing your needs, prioritising quality, ensuring compatibility, reviewing warranties, and seeking expert advice.
Making informed choices will enhance the efficiency of your plumbing system and contribute to the longevity and reliability of your repairs and installations. With these guidelines in mind, you can effectively tackle your plumbing challenges.
Source From : How To Choose Quality Online Plumbing Parts For Your Needs?
0 notes
Text
Choosing the Right Website Development Company in Jaipur: A Guide for Businesses

In today’s digital era, having a robust online presence is essential for any business. If you're looking to establish or enhance your website, choosing the right website development company in Jaipur is crucial. With numerous options available, how do you make the best choice? This guide will help you navigate this important decision and ensure you partner with a company that aligns with your business goals.
Understanding Your Needs
Before diving into the search for a website development company in Jaipur, it’s essential to identify your specific needs. Are you looking for a simple informational website or a complex e-commerce platform? Understanding your requirements will help you filter potential developers effectively.
Key Questions to Consider:
What type of website do you need (e-commerce, portfolio, corporate)?
What features are essential for your website (payment gateways, user registration, etc.)?
Do you have a preferred design style or functionality in mind?
Researching Website Development Companies in Jaipur
Once you have a clear understanding of your needs, start researching potential web development companies in Jaipur. Look for firms with a solid reputation and a portfolio that aligns with your vision.
Where to Look:
Online Reviews: Check platforms like Google, Clutch, and social media for reviews and testimonials.
Portfolio: Examine the company’s previous work to gauge their design and development capabilities.
Recommendations: Ask colleagues or industry peers for recommendations based on their experiences.
Evaluating Experience and Expertise
When selecting a website developer in Jaipur, consider their experience and expertise. An established company with a track record in various industries is often a safer bet.
Important Factors:
Years in Business: Companies with years of experience are likely to have refined their processes and skills.
Specialization: If you need an e-commerce site, consider an e-commerce website development company in Jaipur that specializes in online store development.
Checking Technical Skills
The right web development company in Jaipur should be proficient in the latest technologies and best practices. Check if their team is skilled in the following areas:
Technical Proficiencies:
Programming Languages: Look for expertise in HTML, CSS, JavaScript, PHP, and other relevant languages.
Content Management Systems (CMS): Familiarity with popular CMS platforms like WordPress, Shopify, or Magento can be crucial for ease of use and maintenance.
Responsive Design: Ensure the company can create websites that function seamlessly across devices and screen sizes.
Understanding the Development Process
A well-defined development process is a hallmark of the best website development company in Jaipur. Understanding how they manage projects will give you insight into what to expect.
Typical Development Steps:
Discovery: Gathering requirements and understanding your business goals.
Planning: Outlining the project scope, timeline, and milestones.
Design: Creating wireframes and prototypes for your approval.
Development: Coding the website and implementing features.
Testing: Conducting thorough testing to ensure functionality and performance.
Launch and Support: Launching the website and providing ongoing support and maintenance.
Reviewing Pricing and Packages
While budget is an important factor, it shouldn’t be the sole determinant in your choice. Look for a web development company in Jaipur that offers transparent pricing and clear package details.
Things to Keep in Mind:
Value Over Cost: opt for a company that offers a balance of quality and affordability.
Hidden Costs: Ensure there are no unexpected fees or charges down the line.
Finding the Best Website Designer in Jaipur
Design plays a critical role in user experience and brand perception. Look for the best website designer in Jaipur who can deliver visually appealing and functional designs that resonate with your target audience.
Key Qualities of a Great Designer:
Creativity: An eye for design and the ability to create unique visual concepts.
User-Centric Approach: Understanding user experience (UX) principles to design intuitive interfaces.
Conclusion
Choosing the right website development company in Jaipur is a critical decision that can impact your business's online success. By understanding your needs, conducting thorough research, and evaluating potential partners based on their expertise, you can make an informed choice. Whether you need a simple website or a comprehensive e-commerce solution, finding the best website development company in Jaipur is essential for achieving your digital goals.
If you’re looking for a reliable partner, consider WebProMix as your go-to e-commerce website development company in Jaipur. With our expertise and dedication to quality, we can help bring your online vision to life. Contact us today to get started!
#website development company in Jaipur#website developer in Jaipur#web development company Jaipur#best website developer in Jaipur#best website designer in Jaipur#best website development company in Jaipur#e commerce website development company in Jaipur#ecommerce website development company in Jaipur
1 note
·
View note
Text
Web Analytics Scope, Geographical Analysis and Top Industry Player

Web Analytics Market Research
According to Straits Research, the global Web Analytics market size was valued at USD 5243.46 Million in 2022. It is projected to reach from USD XX Million in 2023 to USD 24715.28 Billion by 2031, growing at a CAGR of 18.8% during the forecast period (2023–2031).
The Web Analytics market, an evolving segment in the industry, is witnessing substantial expansion fueled by avant-garde technologies and escalating consumer demand. Market analysts scrupulously gather data through polls, focus groups, and in-depth scrutiny of industry patterns. These analysts utilize both quantitative and qualitative methodologies to ensure a comprehensive and precise market report. The report encompasses intricate insights on market size, growth prospects, competitive milieu, and consumer predilections. By harnessing advanced analytical instruments and expert acumen, the report delivers invaluable recommendations and strategic guidance for stakeholders, empowering them to make enlightened decisions and seize emerging prospects within the Web Analytics market.
Competitive Players
The competitive landscape of the Web Analytics market includes several key players who have a significant impact on market dynamics. Major companies operating in this market include:
Adobe Systems Incorporated
AT Internet
Facebook Inc.
Google LLC
Hotjar Ltd
IBM Corporation
Microsoft Corporation
SAS Institute Inc.
Splunk Inc.
Webtrends Inc.
Get a free sample of the Web Analytics Market @ https://straitsresearch.com/report/web-analytics-market/request-sample
Web Analytics Market Segmentation
The comprehensive Web Analytics market analysis has been divided into categories such as category, application, and delivery mode, with each subset examined according to geographical segmentation. This research will keep marketers updated and assist in pinpointing target demographics for a product or service, including insights into market share.
By Deployment
On-Premises
Cloud
By Applications
Social Media Management
Targeting and Behavioral Analysis
Display Advertising Optimization
Multichannel Campaign Analysis
Online Marketing
Others
By End-User
Banking, Financial Services, and Insurance (BFSI)
Retail
Healthcare
Government
Travel and Hospitality
IT and Telecommunications
Media and Entertainment
Others
You can check In-depth Segmentation from here: https://straitsresearch.com/report/web-analytics-market/segmentation
Regional Analysis
The Web Analytics market is studied, and market size insights and trends are offered by nation, kind, form, and application, as previously said. The report's regional analysis section provides a thorough study of many regional and national industries to help players establish successful development strategies.
Buy the Full Web Analytics Market Report @https://straitsresearch.com/buy-now/web-analytics-market
Key Highlights
The purpose of this study is to examine the manufacturers of Web Analytics, including profiles, primary business activities, news, sales and price, revenue, and market share.
It illustrates the market subdivided by type and application, with details on sales, price, revenue, market share, and growth rate broken down by type and application.
The research covers key regions by manufacturers, categories, and applications, including North America, Europe, Asia Pacific, the Middle East, and South America, with sales, revenue, and market share segmented by manufacturers, types, and applications.
It also investigates production costs, essential raw materials, and production methods.
Principal Motives Behind the Purchase:
To gain deep analyses of the industry and understand the commercial landscape of the global market.
To analyze production processes, key problems, and potential solutions to mitigate future issues.
To understand the most influential driving and restraining factors in the Web Analytics industry and their global market impact.
To gain insights into the market strategies employed by the most successful firms.
To understand the market's future and potential.
About Us:
StraitsResearch.com is a leading research and intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & research reports.
Contact Us:
Email: [email protected]
Address:825 3rd Avenue, New York, NY, USA, 10022
Tel: +1 6464807505, +44 203 318 2846
#Web Analytics#Web Analytics Industry#Web Analytics Share#Web Analytics Size#Web Analytics Trends#Web Analytics Regional Analysis#Web Analytics Growth Rate
0 notes
Text
Web Analytics Scope, Geographical Analysis and Top Industry Player

Web Analytics Market Key Players and Forecast Insights
The latest Web Analytics Market Insight Report for 2024 offers a comprehensive analysis of the industry's key contributions, marketing strategies, and recent advancements by leading companies. This report provides a succinct overview of both historical and current performance metrics for major market players. It employs various analytical methods to deliver precise insights into the Web Analytics Market, with coverage across regions including North America, Europe, Asia Pacific, and more. The recent analysis also includes an in-depth review of the business strategies adopted by emerging industry players, along with detailed information on market segments, geographic coverage, product trends, and cost structures.
What are the growth projections for the Web Analytics Market?
According to Straits Research, the global Web Analytics market size was valued at USD 5243.46 Million in 2022. It is projected to reach from USD XX Million in 2023 to USD 24715.28 Billion by 2031, growing at a CAGR of 18.8% during the forecast period (2023–2031).
Get Free Request Sample Report @ https://straitsresearch.com/report/web-analytics-market/request-sample
Top Competitive Players of Web Analytics Market
Adobe Systems Incorporated
AT Internet
Facebook Inc.
Google LLC
Hotjar Ltd
IBM Corporation
Microsoft Corporation
SAS Institute Inc.
Splunk Inc.
Webtrends Inc.
For a sample PDF report, visit @https://straitsresearch.com/report/web-analytics-market/request-sample
What are the key trends within each segment of the Web Analytics Market?
By Deployment
On-Premises
Cloud
By Applications
Social Media Management
Targeting and Behavioral Analysis
Display Advertising Optimization
Multichannel Campaign Analysis
Online Marketing
Others
By End-User
Banking, Financial Services, and Insurance (BFSI)
Retail
Healthcare
Government
Travel and Hospitality
IT and Telecommunications
Media and Entertainment
Others
View the full report and table of contents here: https://straitsresearch.com/report/web-analytics-market/toc
The report forecasts revenue growth at all geographic levels and provides an in-depth analysis of the latest industry trends and development patterns from 2022 to 2030 in each of the segments and sub-segments. Some of the major geographies included in the market are given below:
North America (U.S., Canada)
Europe (U.K., Germany, France, Italy)
Asia Pacific (China, India, Japan, Singapore, Malaysia)
Latin America (Brazil, Mexico)
Middle East & Africa
This Report is available for purchase on Buy Web Analytics Market Report
Key Highlights
Provide a detailed explanation of various aspects including introduction, product types and applications, market overview, country-specific market analysis, opportunities, risks, and driving forces.
Examine manufacturers, including their profiles, primary business activities, recent news, sales and pricing, revenue, and market share.
Offer an overview of the competitive landscape, detailing sales, revenue, and market share among leading global manufacturers.
Present a detailed market breakdown by type and application, including sales, pricing, revenue, market share, and growth rates.
Analyze key regions—North America, Europe, Asia Pacific, the Middle East, and South America—covering sales, revenue, and market share segmented by manufacturers, types, and applications.
Investigate production costs, essential raw materials, and production methods.
Reasons to Buy:
In-depth analysis of market segmentation.
Country-specific insights alongside global demand and supply dynamics.
Examination of key players, including their products, financial performance, and strategies.
Insights into emerging market trends, opportunities, and challenges.
About Us:
StraitsResearch.com is a leading research and intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & research reports.
Contact Us: Email: [email protected] Address: 825 3rd Avenue, New York, NY, USA, 10022 Tel: +1 6464807505, +44 203 318 2846
#Web Analytics#Web Analytics Industry#Web Analytics Share#Web Analytics Size#Web Analytics Trends#Web Analytics Regional Analysis#Web Analytics Growth Rate
0 notes
Text
Global Low-Cost Pizza Franchise Market Analysis 2024: Size Forecast and Growth Prospects
The low-cost pizza franchise global market report 2024 from The Business Research Company provides comprehensive market statistics, including global market size, regional shares, competitor market share, detailed segments, trends, and opportunities. This report offers an in-depth analysis of current and future industry scenarios, delivering a complete perspective for thriving in the industrial automation software market.
Low-Cost Pizza Franchise Market, 2024 report by The Business Research Company offers comprehensive insights into the current state of the market and highlights future growth opportunities.
Market Size - The low-cost pizza franchise market size has grown strongly in recent years. It will grow from $16.26 billion in 2023 to $17.24 billion in 2024 at a compound annual growth rate (CAGR) of 6.1%. The growth in the historic period can be attributed to growth in numbers of fast-food restaurants and food trucks, increase in popularity of dining out, increasing millennial population, increasing influence of international cuisines on food consumption habits, rapid expansion of infrastructure and urbanization.
The low-cost pizza franchise market size is expected to see strong growth in the next few years. It will grow to $21.96 billion in 2028 at a compound annual growth rate (CAGR) of 6.2%. The growth in the forecast period can be attributed to growth in demand and consumption of pizza across, rise in the penetration of quick-service restaurants, increase in demand for pizza, growth in the adoption of online food delivery platforms, escalating demand for convenient food items. Major trends in the forecast period include increasing demand for healthier pizza options, growing popularity of plant-based and vegan pizzas, embracing online ordering systems, implementing eco-friendly packaging, introduction of healthier product variants.
Order your report now for swift delivery @ https://www.thebusinessresearchcompany.com/report/low-cost-pizza-franchise-global-market-report
Scope Of Low-Cost Pizza Franchise Market The Business Research Company's reports encompass a wide range of information, including:
1. Market Size (Historic and Forecast): Analysis of the market's historical performance and projections for future growth.
2. Drivers: Examination of the key factors propelling market growth.
3. Trends: Identification of emerging trends and patterns shaping the market landscape.
4. Key Segments: Breakdown of the market into its primary segments and their respective performance.
5. Focus Regions and Geographies: Insight into the most critical regions and geographical areas influencing the market.
6. Macro Economic Factors: Assessment of broader economic elements impacting the market.
Low-Cost Pizza Franchise Market Overview
Market Drivers - The growth in the number of fast-food restaurants is expected to propel the growth of the low-cost pizza franchise market going forward. Fast-food restaurants refer to establishments that serve quick, standardized meals typically prepared in bulk and intended for immediate consumption. Fast-food restaurants are growing due to their convenience, affordability, and ability to adapt to diverse consumer preferences in urban and suburban settings. The low-cost pizza franchise contributes to the growth of fast-food restaurants by offering affordable entry options for aspiring entrepreneurs, thereby expanding the overall presence and accessibility of quick-service dining options in various locations. For instance, in February 2024, according to the annual report of Domino's, a US-based pizza restaurant chain, in 2023, the year-end store count of Domino's in the US franchise was 6,566, an increase from 6,400 in the year 2022. Therefore, the growth in the number of fast-food restaurants is driving the growth of the low-cost pizza franchise market.
Market Trends - Major companies operating in the low-cost pizza franchise market focus on innovative franchise options to differentiate their offerings and capitalize on growing consumer demand for authentic and high-quality pizza experiences. Pizza franchising is a business model where a company (the franchisor) grants individuals or other businesses (the franchisees) the rights to operate a pizza restaurant under the franchisor's brand name and according to their established guidelines. For instance, in June 2024, Rosso Pomodoro, an Italy-based pizza company, launched franchise opportunities in the US. The new US franchises will introduce a fast-casual concept, serving authentic Neapolitan pizza and Italian specialties with top-quality ingredients. Each location will feature a patented Italian pizza oven, emphasizing the artistry and tradition of Neapolitan pizza-making.
The low-cost pizza franchise market covered in this report is segmented –
1) By Type: Delivery And Takeout Franchise, Carryout Franchise, Fast Casual Franchise, Mobile Pizza Franchise, Other Types 2) By Revenue Component: Franchise Fees, Royalty Fees, Advertising And Marketing Fees, Supply Chain And Purchasing Fees, Renewal Fees, Other Revenue Components 3) By Franchise Location: Domestic, International
Get an inside scoop of the low-cost pizza franchise market, Request now for Sample Report @ https://www.thebusinessresearchcompany.com/sample.aspx?id=16724&type=smp
Regional Insights - North America was the largest region in the low-cost pizza franchise market in 2023. Asia-Pacific is expected to be the fastest-growing region in the forecast period. The regions covered in the low-cost pizza franchise market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa.
Key Companies - Major companies operating in the low-cost pizza franchise market are Pizza Hut LLC, Domino’s Pizza, Papa Johns, Little Caesars, Pieology Pizzeria, MOD SUPER FAST PIZZA LLC, Round Table Pizza, Donatos, Jet’s Pizza, Toppers Pizza, PAPA MURPHY'S, The Marco's Pizza, Hungry Howie Pizza & Subs Inc., Blaze Pizza LLC, Mountain Mike’s Pizza, PizzaRev, Pizza Factory, CICI ENTERPRISES LP, Pie Five Pizza Company, Rosati’s Pizza, LEDO PIZZA SYSTEM INC., Paisano’s Pizza, Your Pie Pizza Franchise
Table of Contents 1. Executive Summary 2. Low-Cost Pizza Franchise Market Report Structure 3. Low-Cost Pizza Franchise Market Trends And Strategies 4. Low-Cost Pizza Franchise Market – Macro Economic Scenario 5. Low-Cost Pizza Franchise Market Size And Growth ….. 27. Low-Cost Pizza Franchise Market Competitor Landscape And Company Profiles 28. Key Mergers And Acquisitions 29. Future Outlook and Potential Analysis 30. Appendix
Contact Us: The Business Research Company Europe: +44 207 1930 708 Asia: +91 88972 63534 Americas: +1 315 623 0293 Email: [email protected]
Follow Us On: LinkedIn: https://in.linkedin.com/company/the-business-research-company Twitter: https://twitter.com/tbrc_info Facebook: https://www.facebook.com/TheBusinessResearchCompany YouTube: https://www.youtube.com/channel/UC24_fI0rV8cR5DxlCpgmyFQ Blog: https://blog.tbrc.info/ Healthcare Blog: https://healthcareresearchreports.com/ Global Market Model: https://www.thebusinessresearchcompany.com/global-market-model
0 notes
Text
Step-by-Step Guide to Patent Application in India

An essential first step in protecting your intellectual property rights is to patent your innovation. The procedure of obtaining a patent in India can be difficult, but it is manageable with the correct help. This tutorial, from Shekhawat Law, a reputable brand in legal support for intellectual property matters, gives you a thorough rundown of the procedures involved in submitting an Indian patent application in India.
Understanding Patents in India
An innovation that has been given a patent gives its owner the exclusive right to prevent anyone from creating, utilizing, selling, or disseminating the invention without their consent. The Patents Act, 1970 and the regulations it established govern patents in India.
Why Patent Your Invention?
Protection of Ideas: A patent protects your invention from being used or reproduced by others without your consent.
Monetary Benefits: It is possible to make money by selling or licensing a patented invention.
Market Advantage: Possessing a patent can provide you with a market advantage.
Boosting Investment: A company with patented technology has a higher chance of attracting investors since it guarantees innovation and distinctiveness.
Step-by-Step Process of Patent Application in India
Step 1: Determine Patentability
Before filing a patent application, assess whether your invention is patentable. The following criteria must be met:
Novelty: The invention must be new and not publicly disclosed before the filing date.
Inventive Step: The invention should not be obvious to someone skilled in the relevant field.
Industrial Applicability: The invention must be capable of being used in some kind of industry.
Step 2: Conduct a Patent Search
To find out if your innovation has already been patented, do a thorough patent search. This is an important phase since it assists in identifying any roadblocks in the process of applying for a patent. For a more thorough search, you can consult experts like Shekhawat Law or use the Indian Patent Advanced Search System (InPASS).
Step 3: Prepare the Patent Application
The next step involves preparing a detailed patent application. The application should include:
Title of the Invention: A clear and concise title that reflects the essence of the invention.
Field of Invention: The technical field to which the invention pertains.
Background of the Invention: Explanation of existing problems and how your invention addresses them.
Summary of the Invention: A brief overview of the invention's key features.
Detailed Description: A thorough description of the invention, including drawings or diagrams if necessary.
Claims: Define the scope of the protection sought. Claims are the legal basis of your patent and should be drafted carefully.
Step 4: File the Patent Application
Your application can be sent to the Indian Patent Office (IPO) after it is complete. Your application can be submitted in person at the closest patent office or online via the IPO's official website.
Step 5: Patent Examination Request
Within 48 months of submitting the application, you must request an examination. The required form must be used to submit the request for examination (RFE). The patent office will thoroughly review your application to ascertain its patentability after receiving your request.
Conclusion
Although the Indian patent application procedure can be difficult, you can successfully navigate through it with the correct strategy and advice from experts like Shekhawat Law. Obtaining a patent gives you a competitive edge in the market in addition to protecting your invention. For knowledgeable help safeguarding your intellectual property, don't be afraid to contact Shekhawat Law if you're thinking about submitting a patent application.
#patent application in india#best technology law firms#technology law firms#patent law firms in india#sudarshan singh shekhawat
0 notes