#rfid key fobs
Explore tagged Tumblr posts
Text
Today's DIY adventure: a Toyota key fob circuitry transplant
Any day that a gadget-repair procedure involves a razor blade but not any subsequent blood loss is a good day.
The powertrain of our 2005 Toyota Prius isn’t the only part of that vehicle that’s been showing its age. The key fob that I don’t even use that often developed a tear in the rubbery coating around its lock and unlock buttons years ago, and in recent years that covering had begun eroding away to expose the green circuit board underneath. Despite now resembling a zombie key fob, the thing still…

View On WordPress
#car key RFID#DIY#ecukey#Gen 2 Prius#How-to#key fob shell#Prius#Prius key fob#Prius replacement key case#PriusChat#Toyota
0 notes
Text

Alok Enterprises Near Rajendra Park Chowk,Station Road, Durg Call 07587071017,9039271017
Access control solutions for glass doors provide security, convenience, and control over entry and exit points. 1. Keycard or Key Fob Access 2. Biometric Access Control 3. PIN Code Access 4. Smart Lock Systems 5. RFID Solutions 6. Automatic Sliding Door Systems with Access Control 7. Video Intercom Access 8. Hybrid Solutions
#alokenterprises#cctvbhilai#cctvmaintenance#cctvdurg#cctv#cctvsolar#biometricsdevies#wificamera#cctvserviceprovider#4gcamera#hdcamara
2 notes
·
View notes
Text
Chum 84: The Gadget
The plan had seemed simple, in theory. Get the fob, get into the building, sniff out Sparkplug. Easy peasy, lemon squeezy, right? Well, as it turned out, simple didn't always mean easy. Especially when you were dealing with a bunch of teenagers trying to take down a drug-dealing thunder god.
First up had been Jordan's grand plan to pickpocket a key fob from some unsuspecting Dorchester resident. I mean, it had sounded like a foolproof idea, right? Just bump into someone, slip your hand into their pocket, and boom, you've got yourself a ticket to the top-secret villain lair. Except, as it turned out, pickpocketing was a lot harder than it looked in the movies.
Jordan had spent hours practicing their technique, using Spindle as a reluctant guinea pig. They had tried every trick in the book - the "accidental" bump, the distraction method, even the old "pretend to tie your shoelace while swiping the goods" routine. But every time, Spindle had caught them in the act, giving them a reproachful look that said, "Really, Jordan? Is this what we've come to?"
After a few days of fruitless attempts, Jordan had finally managed to snag a fob from a distracted businessman outside the Dorchester. They had come strutting back to the hideout, grinning like the cat that got the cream. "Piece of cake," they had declared, tossing the fob in the air and catching it with a flourish.
But their victory had been short-lived. When they had tried to clone the fob, they discovered that it had some sort of built-in security feature that prevented duplication. Apparently, the Dorchester took their residents' privacy very seriously. Who knew? We had needed to spend another couple of hundred dollars getting an actual RFID cloner instead of just trying to plug it into a card reader on Jordan's computer. Or something like that. I hadn't really understood what was going on, but I had let it move over and through me regardless.
8 notes
·
View notes
Text

Recent thrift store find is this lock that works by bluetooth or RFID. 1/10th its list price! It works great and comes with key cards and fobs; the only complaint is that when it was created eight years ago you could download an app so you can open it with your phone and it was for free, but the company has changed names and possibly owners so now using the app is a $15 a month subscription?!
2 notes
·
View notes
Photo

ButterflyMX Is Going Great. Back in 2021, my building's management made the amazing self-own of replacing our existing 90s-vintage RFID key-fob system with this ButterflyMX security-and-privacy panopticon malware thing. I've mostly been able to ignore... https://jwz.org/b/ykmM
0 notes
Text
Access Control Devices Explained: Types, Features, and Benefits
In a world where digital transformation is rapidly reshaping business operations, physical security is evolving too. Gone are the days when traditional lock-and-key systems were sufficient to secure offices, commercial buildings, or sensitive areas. The modern workplace demands smarter, more efficient ways to control who can access specific spaces. That’s where access control devices come into play.
These devices are essential tools that help businesses manage entry, enhance security, and improve convenience for employees, visitors, and facility managers alike. Let’s explore the different types of access control devices available today, their key features, and how they benefit organizations across industries.

What Are Access Control Devices?
Access control devices are hardware components used in a broader access control system to grant or restrict entry to secure areas. These devices verify a user’s identity through credentials like keycards, PIN codes, biometric data, or mobile authentication before allowing access.
Modern access control systems often integrate these devices with cloud-based platforms, enabling remote management, real-time monitoring, and seamless integration with attendance tracking or visitor management solutions.
Types of Access Control Devices
The choice of access control device depends on the level of security required, the number of users, and the type of facility. Here’s a look at the most common types:
1. Keypad-Based Access Devices
These are basic access control devices where users input a numerical PIN code to gain entry. While affordable and easy to install, they may pose security risks if codes are shared or compromised.
2. RFID Card Readers
RFID and smart card readers are widely used in offices and commercial spaces. They require users to carry a card or fob to unlock doors. These systems are convenient but can be vulnerable to loss or duplication if not encrypted properly.
3. Biometric Devices
For higher security needs, biometric access devices offer advanced identity verification through fingerprints, facial recognition, or iris scans. They are accurate and eliminate the need for physical credentials, making them ideal for data centers, labs, and corporate offices.
4. Bluetooth & Mobile Access Devices
As mobile technology advances, smartphones are increasingly used as credentials. Bluetooth-enabled access control devices allow users to unlock doors via mobile apps, offering a contactless, secure, and user-friendly experience — especially valuable in today’s hybrid work environment.
5. Cloud-Connected Controllers
These devices connect to cloud-based platforms that manage access across multiple locations. With centralized control and real-time insights, businesses can monitor activity, update access rights, and view logs remotely.
Key Features of Modern Access Control Devices
Today’s access control devices are more than just door locks. They are part of intelligent ecosystems offering a range of features that enhance functionality and security:
✅ Real-Time Monitoring
Track who accessed what area and when, allowing for quick action in case of suspicious activity.
✅ Mobile Integration
Users can gain access using their smartphones via Bluetooth or QR codes, improving convenience and hygiene in the workplace.
✅ Cloud-Based Management
Manage all devices, users, and locations through a unified, cloud-based dashboard. This makes it easy to scale and manage access remotely.
✅ Multi-Factor Authentication (MFA)
Combine two or more forms of authentication, like a fingerprint and a mobile credential, for added security.
✅ Integration with Other Systems
Modern devices seamlessly integrate with visitor management, time and attendance systems, and surveillance setups — streamlining overall operations.
Benefits of Using Access Control Devices
Implementing the right access control devices can deliver significant advantages to your organization:
🔐 Enhanced Security
Limit unauthorized access and improve control over sensitive or restricted areas. Whether you manage a co-working space, corporate office, or healthcare facility, having the right devices in place significantly reduces physical security risks.
👨💻 Improved Operational Efficiency
Automating entry points reduces reliance on physical keys and manual processes. With cloud-enabled systems, administrators can grant or revoke access in seconds — saving time and reducing errors.
🧾 Audit Trails & Compliance
Access control devices keep detailed logs of all entry events. This is especially important for industries with regulatory requirements, such as healthcare or finance, where compliance and accountability matter.
📱 Contactless Convenience
Bluetooth and mobile-enabled devices allow users to unlock doors without touching shared surfaces — ideal for hygiene-sensitive environments like hospitals or modern office buildings.
🌐 Scalable for Future Growth
Whether you’re adding new doors, onboarding more employees, or expanding into new locations, cloud-integrated devices make scaling easy and cost-effective.
Choosing the Right Access Control Devices for Your Business
Selecting the best access control solution isn’t a one-size-fits-all process. It’s important to assess:
Your organization’s size and structure
The types of users (staff, visitors, contractors)
Required security levels for different zones
Integration with your existing systems
Need for remote access and cloud-based control
Many forward-thinking businesses are moving toward wireless, mobile-first, and biometric access control systems to match their evolving workspace needs. Solutions that combine flexibility, real-time control, and easy scalability offer the best return on investment.
For businesses seeking a smart, seamless approach to physical access management, it helps to explore platforms that offer modern features like smartphone-based credentials, biometric authentication, and cloud-based dashboards. One such solution used by progressive companies is a platform that removes the need for keycards, wiring, and complex installations — leveraging mobile technology to simplify security.
Conclusion
Access control devices have come a long way from basic locks and keypads. Today, they are a cornerstone of intelligent building security — offering real-time control, enhanced convenience, and seamless integration with workplace technologies. As organizations continue to embrace hybrid work models, cloud-based and mobile-enabled solutions are quickly becoming the standard.
Investing in the right access control technology like Spintly not only strengthens security but also improves user experience and operational agility. If your business is ready to upgrade from traditional systems to smarter, more scalable solutions, the time to act is now.
#access control system#access control solutions#mobile access#visitor management system#accesscontrol#spintly#smartacess#biometrics#smartbuilding#biometric attendance
0 notes
Text
10 Benefits of Using Electronic Locks in Dubai | Euro Art Security Solutions

Are you thinking about improving your property's security system? Whether you own a home, manage an office, or run a business in Dubai, electronic locks are becoming an increasingly popular option for improving security, providing convenience, and lowering the hazards connected with traditional locking systems.
In a fast-paced city like Dubai, where security is always a concern, electronic locks are a modern, more secure, and efficient solution to protect your stuff. Euro Art provides high-quality, cutting-edge electronic lock systems for both residential and commercial properties, designed to satisfy the changing needs of today's security requirements.
In this blog, we'll look at the top ten benefits of using electronic locks, why they're a good investment for your house or company, and how they may improve your overall security experience. From convenience and increased safety to cost-effectiveness and ease of use, discover why electronic locks are the future of property security in Dubai.
1. Enhanced Security Features
One of the most convincing arguments for installing electronic locks is the increased security they give over traditional locks. Electronic locks use innovative technology to protect your property, making it far more difficult for intruders to get around them.
Unlike traditional locks, which can be picked or compromised, electronic locks frequently use multi-factor authentication. This means that entrance to your property may require more than just a physical key. You may need to input a PIN code, use a biometric scanner, or unlock the door using your smartphone. Some systems even incorporate RFID (Radio Frequency Identification) technology, which requires a key fob or card to obtain access.
In a prominent Dubai hotel, electronic locks were fitted to restrict visitor access to rooms. The new systems included biometric fingerprint scanning at the entrance, which considerably reduced incidences of unauthorised access while improving the overall passenger experience. The hotel's management reported a 35% reduction in security breaches during the first six months of implementation.
This multi-layered security system makes unauthorised entry much more difficult, providing a crucial layer of protection, particularly in high-security places such as offices, houses with valuable valuables, or even medical institutions.
2. Convenience with Keyless Entry
Are you tired of lugging keys around or being locked out of your house or office? Electronic locks offer the utmost convenience with keyless entry. Instead of using a standard key, electronic locks provide access via more efficient ways, such as a PIN number, smartphone apps, biometric scans (fingerprints), or even a key fob.
Imagine being able to unlock your door with a single tap of your phone or a simple fingerprint scan. No more digging through pockets or bags for keys. Furthermore, it is extremely useful for families, roommates, or employees, as there is no need to worry about who has a copy of the key.
Testimonial: "I used to constantly misplace my keys, which caused stress." With Euro Art's electronic lock, I can now unlock my door by simply tapping my phone. It's so much more convenient and safe! Furthermore, I may offer access to family members without worrying about missing keys." - David M., Dubai
Electronic locks also provide convenience to company owners. You can allow or prohibit remote access to your property, manage staff access, and monitor who enters and exits the premises at any time.
3. Remote Access and Control.
One of the most distinguishing aspects of electronic locks is the ability to manage access remotely. Many electronic locks have smartphone apps that let you lock and open your door from anywhere in the globe. This remote access is especially beneficial for those who travel frequently or manage properties in different locations.
Whether you're on vacation, working from another location, or simply stopped in traffic, you can easily allow someone into your home. It's a significant benefit for property managers, business owners, and homeowners who need to regulate access without being physically present.
4. Audit trails and activity logs.
Another significant advantage of electronic locks is their ability to generate audit trails or activity logs. These logs capture every time someone enters or quits your property, providing a comprehensive record of access.
If you own a business or run an office, activity logs are essential for tracking employee movements and verifying compliance with workplace security protocols. An audit trail gives homeowners peace of mind by allowing them to see exactly when visitors come and exit.
Stat:
A Dubai-based office recently deployed Euro Art's electronic lock systems and observed a 50% increase in internal security through the use of detailed activity logs. They were able to detect and control employee access more effectively, resulting in fewer incidents of unauthorised entry.
5. Improved Access Management.
Managing access is significantly easier with electronic locks than with traditional locking systems. Rather than handing out actual keys to employees, family members, or contractors, you can grant and cancel access remotely.
For example, you can issue temporary access codes or use smartphone apps to unlock doors for delivery staff or guests. This function is especially useful for firms with high employee turnover or houses that receive regular guests.
Furthermore, if someone loses their access card or phone, you may immediately revoke it and issue a new one, minimising the possibility of unauthorised access caused by lost or stolen keys.
6. Cost-effectiveness in the long run
While electronic locks are more expensive than traditional locks in the beginning, they are much more cost-effective in the end. By eliminating the need for actual keys, you can save money on lost keys, key replacements, and rekeying locks. Furthermore, the ability to remotely control access may lessen the requirement for on-site security personnel or surveillance equipment.
For enterprises, the ability to manage several sites remotely, grant temporary access to employees, and track activity can result in significant operational cost reductions over time.
7. Simple integration with smart home systems.
As smart home technology advances, electronic locks are becoming an essential component of the modern linked house. Many of Euro Art's electronic lock systems work with popular smart home ecosystems like Amazon Alexa, Google Assistant, and Apple HomeKit.
Smart integration allows you to control your locks using voice commands, create automatic schedules, and link them into bigger security systems. This connection provides simplicity and complete control over your home security.
8. Increased property value.
Installing smart locks can increase the value of your property. With their superior technologies, they give your house a current, high-tech appearance that can be used to attract potential buyers or tenants.
In a city like Dubai, where security is a primary priority for homes and companies, properties with electronic locks frequently stand out on the market. Whether you're selling your house or renting out office space, this modern security feature can boost the perceived worth of your property.
9. Versatility and Customisation
Euro Art provides tailored electronic lock systems to meet your individual requirements. We offer a number of choices to meet the specific needs of your property, including biometric scanners for high-security zones and keypad access for easier entrance.
Whether you manage a luxurious penthouse or a bustling workplace, our customisable electronic lock systems provide you the freedom to select the finest access control solution for your security requirements.
10. Peace of Mind
Finally, the most significant benefit of electronic locks is the peace of mind they provide. Knowing that your property is secure and that you have complete control over entry can help to decrease tension and anxiety.
Electronic locks provide a sense of security and control, whether they are used to ensure that your family members can enter safely, that your staff have appropriate access, or that your business is protected from unauthorised entry.
Conclusion: Why Select Euro Art for Your Electronic Lock Needs?
As previously stated, electronic locks offer various advantages, including increased security and convenience, greater access management, and long-term cost savings. If you want to improve the security and efficiency of your Dubai property, installing an electronic lock system from Euro Art is the best option.
Our electronic locks are designed to satisfy the changing needs of modern security by providing enhanced functionality, remote access, and simple interaction with smart home devices. Whether you're looking to secure your house, company, or commercial property, our team of professionals at Euro Art can help you locate the ideal solution.
Begin securing your property today with Euro Art electronic locks—the best in security, convenience, and peace of mind.
FAQs
1. What kinds of electronic locks do you offer?
Euro Art provides a variety of electronic locks, including biometric locks, keypad locks, RFID locks, and smartphone-enabled locks, designed for both residential and commercial premises.
2. Can I use my electronic lock remotely?
Yes, many of our electronic lock systems include a smartphone app that lets you control your lock remotely from anywhere.
3. Are electronic locks difficult to install?
No, our locks are designed to be simple to install, and our skilled team at Euro Art can help with the procedure to ensure it is completed correctly.
4. How secure are electronic locks?
Our electronic locks include modern encryption, biometric access, and multi-factor authentication to ensure the highest level of security for your goods.
5. Will electronic locks work during a power outage?
Many of our systems incorporate backup power solutions, such as batteries or manual override options, to ensure that they function even during a power outage.
0 notes
Text
Understanding Access Control Systems: Key Features for Enhanced Security
Strong access control systems are crucial for protecting businesses, properties, and sensitive data because security threats are changing quickly. Whether safeguarding a factory, office, or residential building, a sophisticated access control system makes sure that only people with permission can enter restricted areas.
For businesses in Dubai, partnering with a SIRA approved security company guarantees that access control systems comply with the highest security standards. These companies provide advanced solutions tailored to various industries, ensuring maximum protection.
The main characteristics of access control systems that improve security and the reasons they are an essential investment for companies and organizations will be discussed in this blog.
What is an Access Control System?

One type of security solution used to control and regulate entry into buildings, rooms, or designated areas is an access control system. These systems grant or deny access based on authentication techniques like keycards, PIN codes, biometrics, or mobile credentials.
In order to improve overall security, access control systems offer automation, audit trails, and real-time monitoring in addition to preventing unwanted entry.
Key Features of Access Control Systems
1. Authorization and Authentication
Authentication is one of the main purposes of an access control system. Before being allowed access, users must use one or more credentials to verify their identity. To ascertain authorization, the system then compares the credentials to a database.
Typical techniques for authentication include:
Keycards and Fobs: For safe entry, contactless cards and RFID fobs are frequently utilized.
PIN Codes: An extra degree of security is offered by numerical passwords.
Only authorized personnel can enter thanks to biometric authentication, which uses iris scans, fingerprints, or facial recognition.
Mobile Credentials: By acting as digital keys, smartphones can improve security and convenience.
2. MFA, or multi-factor authentication
By requiring users to confirm their identity using multiple methods, multi-factor authentication (MFA) improves security. To access a secure area, for instance, an employee might have to enter a PIN and scan their fingerprint.
Through the addition of additional layers of verification, MFA dramatically lowers the risk of unauthorized access.
3. RBAC, or role-based access control
Organizations can assign permissions according to job responsibilities or roles by using role-based access control, or RBAC. For instance:
All company areas may be accessible to executives.
Financial offices are off-limits to IT personnel, but server rooms are.
Only specific public areas are accessible to visitors.
RBAC lowers security risks by ensuring that visitors and staff can only enter areas that are essential to their jobs.
4. Monitoring and Alerts in Real Time
Security teams can monitor movements within a facility in real time thanks to modern access control systems. Alerts can be sent by SMS, email, or mobile notifications in the event that unauthorized access is attempted.
By enabling quick reaction to possible threats, this feature improves security.
5. Reporting and Audit Trails
Access control systems create thorough audit trails by recording each entry and exit. These documents can be utilized for:
Examining security-related incidents
Monitoring staff attendance
Ensuring adherence to rules
Reports can be produced by organizations to examine security trends and enhance safety protocols.
6. Cloud-Based Management and Remote Access
Security administrators can remotely manage access through cloud-based access control systems. Businesses with multiple locations or remote security teams will find this especially helpful.
Cloud-based access control has the following advantages:
Monitoring and real-time updates from anywhere
Updates to software automatically for improved security
Scalability for expanding companies
7. Connectivity to Other Security Mechanisms
To provide a complete security solution, a well-designed access control system can interface with intrusion detection systems, fire alarms, and CCTV cameras.
For instance:
The system has the ability to start CCTV recording if it detects unauthorized access.
Doors can automatically unlock to allow for a safe evacuation in the event of a fire.
Integration increases security effectiveness and response times.
8. System for Managing Visitors
Visitors, contractors, and temporary employees are commonplace in businesses and organizations. Security is improved by a visitor management system (VMS) by:
Guest registration and temporary access credential issuance
Gathering visitor information for security documentation
Limiting access according to location and time
Better control over who enters the building is ensured by this feature.
9. Smart Credentials and Mobile Access
Smartphones can be used as access credentials for many contemporary access control systems. Users can unlock doors using their smart credentials by:
Near Field Communication, or NFC
Bluetooth
Scanning QR Codes
Physical keycards are no longer necessary thanks to mobile access, which lowers the possibility of credentials being misplaced or stolen.
10. Anti-Tailgating and Anti-Passback Features
Unauthorized entry that follows an authorized user is known as tailgating, and it poses a serious security risk. Advanced systems for access control make use of:
Speed gates and turnstiles to stop illegal follow-through.
anti-passback guidelines to prevent users from using their login credentials to grant access to others.
By guaranteeing stringent entry procedures, these features improve overall security.
Why Access Control Systems Are Essential for Security
1. Avoid Unauthorized Entry
Access control systems keep unauthorized individuals out of restricted areas by limiting entry to authorized personnel only.
2. Enhance Safety at Work
By limiting access to dangerous locations, employers can lower the number of workplace accidents by ensuring that only qualified workers can enter.
3. Boost Efficiency in Operations
Businesses can do away with manual security checks and traditional keys by implementing automated entry systems.
4. Fulfill Compliance Conditions
Strict access controls are necessary in many sectors, including healthcare and finance, to safeguard private information and adhere to legal requirements.
5. Lower Security Expenses
Businesses' overall security expenses are decreased by automated security since it eliminates the need for on-site security guards.
Final Thoughts

Businesses, governmental organizations, and residential buildings must invest in access control systems. Organizations can greatly increase security and efficiency by putting advanced authentication, real-time monitoring, and integration with other security systems into place.
With increasing security threats, choosing the right access control system is crucial. Working with a SIRA approved security company ensures that your security solutions are up to standard, providing maximum protection for your business or property.
Selecting a dependable access control system is the first step toward creating a more secure and safe environment if you're thinking about updating your security infrastructure.
#cctv camera#cctv installation#cctv installers#cctv surveillance#dubai#cctvfootage#search and rescue#access control system
0 notes
Text
Understanding Access Control Systems: Key Features for Enhanced Security
Strong access control systems are crucial for protecting businesses, properties, and sensitive data because security threats are changing quickly. Whether safeguarding a factory, office, or residential building, a sophisticated access control system makes sure that only people with permission can enter restricted areas.
For businesses in Dubai, partnering with a SIRA approved security company guarantees that access control systems comply with the highest security standards. These companies provide advanced solutions tailored to various industries, ensuring maximum protection.
The main characteristics of access control systems that improve security and the reasons they are an essential investment for companies and organizations will be discussed in this blog.
What is an Access Control System?

One type of security solution used to control and regulate entry into buildings, rooms, or designated areas is an access control system. These systems grant or deny access based on authentication techniques like keycards, PIN codes, biometrics, or mobile credentials.
In order to improve overall security, access control systems offer automation, audit trails, and real-time monitoring in addition to preventing unwanted entry.
Key Features of Access Control Systems
1. Authorization and Authentication
Authentication is one of the main purposes of an access control system. Before being allowed access, users must use one or more credentials to verify their identity. To ascertain authorization, the system then compares the credentials to a database.
Typical techniques for authentication include:
Keycards and Fobs: For safe entry, contactless cards and RFID fobs are frequently utilized.
PIN Codes: An extra degree of security is offered by numerical passwords.
Only authorized personnel can enter thanks to biometric authentication, which uses iris scans, fingerprints, or facial recognition.
Mobile Credentials: By acting as digital keys, smartphones can improve security and convenience.
2. MFA, or multi-factor authentication
By requiring users to confirm their identity using multiple methods, multi-factor authentication (MFA) improves security. To access a secure area, for instance, an employee might have to enter a PIN and scan their fingerprint.
Through the addition of additional layers of verification, MFA dramatically lowers the risk of unauthorized access.
3. RBAC, or role-based access control
Organizations can assign permissions according to job responsibilities or roles by using role-based access control, or RBAC. For instance:
All company areas may be accessible to executives.
Financial offices are off-limits to IT personnel, but server rooms are.
Only specific public areas are accessible to visitors.
RBAC lowers security risks by ensuring that visitors and staff can only enter areas that are essential to their jobs.
4. Monitoring and Alerts in Real Time
Security teams can monitor movements within a facility in real time thanks to modern access control systems. Alerts can be sent by SMS, email, or mobile notifications in the event that unauthorized access is attempted.
By enabling quick reaction to possible threats, this feature improves security.
5. Reporting and Audit Trails
Access control systems create thorough audit trails by recording each entry and exit. These documents can be utilized for:
Examining security-related incidents
Monitoring staff attendance
Ensuring adherence to rules
Reports can be produced by organizations to examine security trends and enhance safety protocols.
6. Cloud-Based Management and Remote Access
Security administrators can remotely manage access through cloud-based access control systems. Businesses with multiple locations or remote security teams will find this especially helpful.
Cloud-based access control has the following advantages:
Monitoring and real-time updates from anywhere
Updates to software automatically for improved security
Scalability for expanding companies
7. Connectivity to Other Security Mechanisms
To provide a complete security solution, a well-designed access control system can interface with intrusion detection systems, fire alarms, and CCTV cameras.
For instance:
The system has the ability to start CCTV recording if it detects unauthorized access.
Doors can automatically unlock to allow for a safe evacuation in the event of a fire.
Integration increases security effectiveness and response times.
8. System for Managing Visitors
Visitors, contractors, and temporary employees are commonplace in businesses and organizations. Security is improved by a visitor management system (VMS) by:
Guest registration and temporary access credential issuance
Gathering visitor information for security documentation
Limiting access according to location and time
Better control over who enters the building is ensured by this feature.
9. Smart Credentials and Mobile Access
Smartphones can be used as access credentials for many contemporary access control systems. Users can unlock doors using their smart credentials by:
Near Field Communication, or NFC
Bluetooth
Scanning QR Codes
Physical keycards are no longer necessary thanks to mobile access, which lowers the possibility of credentials being misplaced or stolen.
10. Anti-Tailgating and Anti-Passback Features
Unauthorized entry that follows an authorized user is known as tailgating, and it poses a serious security risk. Advanced systems for access control make use of:
Speed gates and turnstiles to stop illegal follow-through.
anti-passback guidelines to prevent users from using their login credentials to grant access to others.
By guaranteeing stringent entry procedures, these features improve overall security.
Why Access Control Systems Are Essential for Security
1. Avoid Unauthorized Entry
Access control systems keep unauthorized individuals out of restricted areas by limiting entry to authorized personnel only.
2. Enhance Safety at Work
By limiting access to dangerous locations, employers can lower the number of workplace accidents by ensuring that only qualified workers can enter.
3. Boost Efficiency in Operations
Businesses can do away with manual security checks and traditional keys by implementing automated entry systems.
4. Fulfill Compliance Conditions
Strict access controls are necessary in many sectors, including healthcare and finance, to safeguard private information and adhere to legal requirements.
5. Lower Security Expenses
Businesses' overall security expenses are decreased by automated security since it eliminates the need for on-site security guards.
Final Thoughts

Businesses, governmental organizations, and residential buildings must invest in access control systems. Organizations can greatly increase security and efficiency by putting advanced authentication, real-time monitoring, and integration with other security systems into place.
With increasing security threats, choosing the right access control system is crucial. Working with a SIRA approved security company ensures that your security solutions are up to standard, providing maximum protection for your business or property.
Selecting a dependable access control system is the first step toward creating a more secure and safe environment if you're thinking about updating your security infrastructure.
0 notes
Text
Why Push Button Start is a Must-Have System for Every Vehicle
Push button start is an essential feature that must be present in the vehicle because of its convenience. Drivers need to simply push to start their vehicles, providing a quicker way. Furthermore, push-button start systems also come with advanced security features, such as vehicles being able to start only when the right fob is present. Usually, nowadays, high-end vehicles automatically have a push button, but not for every model. This is an aftermarket technology that is suitable for every vehicle.
Convenience and Comfort
Push-button start systems eliminate the need for traditional keys. With these systems, a simple button press is enough to start the vehicle. Every vehicle owner can easily start the vehicle and start enjoying the ride.
Vehicle owners can choose custom start buttons, such as Billet style, Slimline, or OEM style, according to their preferences and style. Even the installation of the push button start systems is also easy by eliminating the need for additional wiring.
Enhanced Security
One of the best advantages of a push-button start system is that it offers the best security. Traditional keys can be copied, but a push-button system requires a key fob within a specific range to start the vehicle.
This system makes it much harder for unauthorized individuals to access the vehicle. The vehicle only starts if the right fob is present. The push button engine start switch must be selected according to the vehicle model and brand. Choose the start buttons that come with the led status indicator because it clearly indicates system status.
Modern Technology and Affordable
Opting for a push-button start system also opens the door to many integrations of advanced technologies like RFID. Nowadays, vehicles are coming with more advanced features; the push-button start acts as a gateway to various technologies. This system easily integrates with the current setup in the vehicle to provide a push-to-start system, providing convenience and security.
This system also comes with an immobilizer system to prevent unauthorized vehicle starts. This after-market system is also an affordable option compared to a high-end vehicle that provides the built-in push button start system.
About Digital Guard Dawg
Digital Guard Dawg provides the best push-button start systems, anti theft device for car, and 4G GPS tracking solutions according to the vehicle model for improving vehicle security. This company offers products designed using various technologies like immobilization and RFID for advanced protection and real-time tracking.
To get more details, visit https://www.digitalguarddawg.com/
Original Source: https://bit.ly/41JBnN6
0 notes
Text
Choosing the Right RFID Solutions for Hotels: Cards, Fobs, Wristbands
RFID technology is becoming increasingly widespread in access control applications within the hotel industry. In addition to the well-known RFID hotel key cards, RFID key fobs and RFID wristbands have also emerged as popular access control options. While all three types of access tools utilize RFID technology, they each have distinct characteristics. As a hotel decision-maker, how do you select the solution that best fits your hotel’s needs? This article will provide answers to that question.

1. RFID Cards: A Classic Design with Diverse Eco-Friendly Options
RFID cards are the most common and widely used access control tools in the hotel industry. Due to their classic design, convenience, and high security, they have long been the preferred solution for hotels. Compared to RFID key fobs and wristbands, RFID cards typically offer a larger surface area, making it easy to display hotel branding, room numbers, and other customized information.
Material Variety and Environmental Advantages
RFID cards provide a range of material options to meet different hotel needs. From traditional PVC to eco-friendly materials, hotels can choose according to their brand positioning and environmental requirements. With the growing awareness of environmental issues, an increasing number of hotels are opting for eco-friendly choices such as wooden and biodegradable materials. These not only reduce environmental impact and are recyclable but also help hotels create a green and sustainable brand image.
Notably, the BioPoly™ Stone RFID card, developed by RFIDCard.com, represents a perfect combination of environmental friendliness and durability, making it a preferred choice in the hotel industry. Compared to traditional PVC cards, the BioPoly™ Stone RFID card is not only more durable but also poses no harm to the environment and fully complies with green standards. Its main features include being waterproof, oil-resistant, and tear-resistant, making it ideal for various hotel environments, especially those that experience heavy usage or harsh conditions.
The use of eco-friendly materials in RFID cards not only enhances the hotel's environmental image but also demonstrates its sense of social responsibility, fostering deeper brand loyalty among customers. This green choice is certain to attract an increasingly sustainability-focused clientele.
Ample Design Space
RFID cards offer significant customization potential, allowing for exquisite printing and personalized designs tailored to the hotel’s needs. This personalized design provides a great opportunity for hotels to showcase their brand and enhance customer loyalty. Compared to RFID key fobs and wristbands, RFID cards can accommodate more design elements, such as the hotel logo and room numbers, thus serving not just as tools but also as an integral part of the hotel’s brand experience. For high-end hotels that wish to impress customers with attention to detail, RFID cards are a worthy investment solution.
2. RFID Key Fobs: Compact and Durable, Ideal for High-Usage Environments
RFID key fobs have become an ideal RFID solution for hotel staff, thanks to their compact and portable design. Despite their simple appearance, they boast excellent durability and convenience, making them particularly suitable for frequent use in harsh working conditions. RFID key fobs are especially well-suited for daily use by hotel employees, such as housekeeping and security personnel.
Durability and Applicability
Compared to RFID cards, RFID key fobs are more resilient and can withstand high-frequency contact and challenging work environments. Hotel staff often need to access various areas, and the design of RFID key fobs ensures this process is efficient without suffering from wear and tear, avoiding the deterioration associated with the frequent use of RFID cards.
Convenience and Comfort
RFID key fobs are small and lightweight, easily attachable to a belt or worn around the neck, providing a comfortable wearing experience for hotel employees. Whether for routine tasks or high-intensity work, these fobs enable quick identity verification without the need for additional steps, significantly enhancing work efficiency and flow.
In hotel management, RFID key fobs play an indispensable role, especially in workplaces that demand high usage and strong durability. They provide hotel staff with a more efficient and convenient working tool.

3. RFID Silicone Wristbands: The Fusion of Style and Comfort
RFID silicone wristbands not only offer a fashionable look and comfort but also boast high durability and waterproofing, making them suitable for all-day wear. Compared to RFID cards and key fobs, RFID silicone wristbands have a more modern feel and flexibility, particularly in specific settings, providing customers with a smoother and more convenient experience.
Style and Comfort
The design of RFID silicone wristbands aims to enhance the customer wearing experience. Their comfort and waterproof features make them especially popular in locations like pools, spas, and resorts, allowing customers to wear them without worrying about discomfort or losing them in the water. Unlike RFID cards, the wristband design is not only contemporary but also meets the needs for long-term wear; compared to RFID key fobs, wristbands are less likely to be misplaced, reducing the hassle of lost tools for customers.
Brand Promotion and Customization
Beyond their practical functionality, RFID silicone wristbands have significant customization potential. Hotels can design unique colors, logos, or patterns for the wristbands according to their branding needs, enhancing customer recognition of the hotel brand while also providing additional brand promotional benefits. Especially during large events, personalized wristbands can help hotels better showcase their brand image and establish deeper connections with customers.
A Safer Choice
RFID silicone wristbands offer greater security than traditional RFID cards and key fobs. Since wristbands cannot be as easily lost or dropped as cards, customers can maintain more effective control over their belongings and identity verification tools. Moreover, wristbands can further enhance security through various encryption technologies, mitigating potential security risks during high-frequency usage.
3. How to Choose the Right RFID Solution for Your Hotel
Here’s a summary of the characteristics of various RFID solutions along with recommendations on how to choose the right one for your hotel.
RFID Cards: Ideal for luxury hotels, boutique hotels, or any establishment looking to enhance its brand image through design details. With ample design space, RFID cards can serve as a medium for brand representation, offering more customization options such as hotel logos and room numbers.
RFID Key Fobs: Particularly suitable for hotel staff or environments that require frequent use and high durability. They are a practical choice for situations where employees need reliable access control tools that can withstand the rigors of daily operations.
RFID Silicone Wristbands: Best for resorts, water parks, and family-oriented hotels, especially in scenarios requiring all-day wear and waterproof functionality. They provide customers with a more convenient experience, making them an excellent option for settings where guests engage in various activities.
Learn More About Hotel RFID Solutions
If you’re interested in exploring how RFID solutions can enhance hotel operational efficiency and improve customer experience, feel free to contact us at any time. After understanding your specific needs, we’ll provide tailored professional advice to help your hotel achieve more efficient access management and a more impactful brand image.
0 notes
Text
Chum 83: Mayfly Dissection
Finally, after several agonizing minutes of discomforted mumbling between each other, Jordan speaks up again. "What if we could get our hands on one of those keyless fobs they use at the Dorchester? I bet I could clone it, and then we could get in without anyone noticing. It looks like it's just RFID. That's super insecure."
Derek frowns. "Okay, but how do we get a fob in the first place? It's not like they just hand them out to anyone."
Jordan grins. "For a hardened criminal, you seem to really not understand the idea of pickpocketing people."
"Not a criminal!" Derek yells, at roughly the same time as Spindle letting out a somewhat-admonishing gasp.
"Jordan, sweetie, that's illegal," he gently reminds them.
"You were literally breaking into convenience stores to rob them like half a year ago, darling," Jordan replies, rolling their eyes at Spindle. "And it's for the greater good. A person loses their key fob, they get a new one at the front desk, maybe they pay like twenty dollars, and we lock up a high level drug dealer. There's priorities here. It's not like we can get a search warrant."
doing something new with including little excerpts to try and get more eyes on the post. love you all.
9 notes
·
View notes
Text

Alok Enterprises Near Rajendra Park Chowk,Station Road, Durg Call 07587071017,9039271017 Access control solutions for glass doors provide security, convenience, and control over entry and exit points. 1. Keycard or Key Fob Access 2. Biometric Access Control 3. PIN Code Access 4. Smart Lock Systems 5. RFID Solutions 6. Automatic Sliding Door Systems with Access Control 7. Video Intercom Access 8. Hybrid Solutions
#cctvmaintenance#cctvbhilai#cctvdurg#alokenterprises#cctvsolar#biometricsdevies#wificamera#cctvserviceprovider#4gcamera#cctv#hdcamara
1 note
·
View note
Text
Automotive Digital Key Market To Witness the Highest Growth Globally in Coming Years
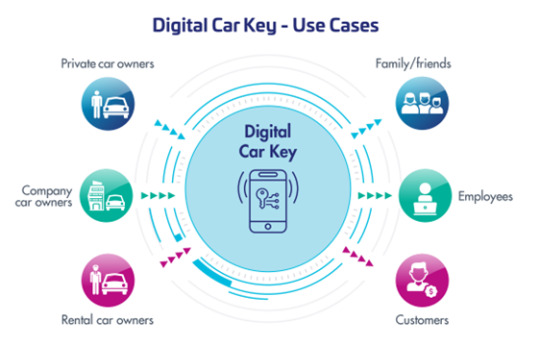
The report begins with an overview of the Automotive Digital Key Market 2025 Size and presents throughout its development. It provides a comprehensive analysis of all regional and key player segments providing closer insights into current market conditions and future market opportunities, along with drivers, trend segments, consumer behavior, price factors, and market performance and estimates. Forecast market information, SWOT analysis, Automotive Digital Key Market scenario, and feasibility study are the important aspects analyzed in this report.
The Automotive Digital Key Market is experiencing robust growth driven by the expanding globally. The Automotive Digital Key Market is poised for substantial growth as manufacturers across various industries embrace automation to enhance productivity, quality, and agility in their production processes. Automotive Digital Key Market leverage robotics, machine vision, and advanced control technologies to streamline assembly tasks, reduce labor costs, and minimize errors. With increasing demand for customized products, shorter product lifecycles, and labor shortages, there is a growing need for flexible and scalable automation solutions. As technology advances and automation becomes more accessible, the adoption of automated assembly systems is expected to accelerate, driving market growth and innovation in manufacturing. Automotive Digital Key Market Size, Share & Industry Analysis, By Type (Near Field Communication (NFC), Bluetooth, Others), By Vehicle Type (Passenger Cars, Commercial Vehicles) And Regional Forecast 2021-2028
Get Sample PDF Report: https://www.fortunebusinessinsights.com/enquiry/request-sample-pdf/105490
Key Strategies
Key strategies in the Automotive Digital Key Market revolve around optimizing production efficiency, quality, and flexibility. Integration of advanced robotics and machine vision technologies streamlines assembly processes, reducing cycle times and error rates. Customization options cater to diverse product requirements and manufacturing environments, ensuring solution scalability and adaptability. Collaboration with industry partners and automation experts fosters innovation and addresses evolving customer needs and market trends. Moreover, investment in employee training and skill development facilitates seamless integration and operation of Automotive Digital Key Market. By prioritizing these strategies, manufacturers can enhance competitiveness, accelerate time-to-market, and drive sustainable growth in the Automotive Digital Key Market.
Major Automotive Digital Key Market Manufacturers covered in the market report include:
Major players operating in the global automotive digital key market include Hyundai Mobis, Volkswagen AG, Denso Corporation, Samsung Electronics Co. Ltd., HELLA, Robert Bosch GmbH, Tesla Inc., Infineon Technologies, BMW AG, STMicroelectronics, Continental AG, Daimler AG, Ericsson, and Valeo SA among others.
Manufacturers are developing car digital keys, which offer more advanced functions than traditional keys, such as keyless entry functions, connected cars, enhanced driver safety functions, etc. Moreover, the leading players in the automotive digital key market have been working on developing smart key fobs, key cards, and wearable smart keys with RFID technology. Several original equipment manufacturers (OEMs) are committed to increase the production of vehicles with this advanced feature in response to increase the customer demand.
Trends Analysis
The Automotive Digital Key Market is experiencing rapid expansion fueled by the manufacturing industry's pursuit of efficiency and productivity gains. Key trends include the adoption of collaborative robotics and advanced automation technologies to streamline assembly processes and reduce labor costs. With the rise of Industry 4.0 initiatives, manufacturers are investing in flexible and scalable Automotive Digital Key Market capable of handling diverse product portfolios. Moreover, advancements in machine vision and AI-driven quality control are enhancing production throughput and ensuring product consistency. The emphasis on sustainability and lean manufacturing principles is driving innovation in energy-efficient and eco-friendly Automotive Digital Key Market Solutions.
Regions Included in this Automotive Digital Key Market Report are as follows:
North America [U.S., Canada, Mexico]
Europe [Germany, UK, France, Italy, Rest of Europe]
Asia-Pacific [China, India, Japan, South Korea, Southeast Asia, Australia, Rest of Asia Pacific]
South America [Brazil, Argentina, Rest of Latin America]
Middle East & Africa [GCC, North Africa, South Africa, Rest of the Middle East and Africa]
Significant Features that are under offering and key highlights of the reports:
- Detailed overview of the Automotive Digital Key Market.
- Changing the Automotive Digital Key Market dynamics of the industry.
- In-depth market segmentation by Type, Application, etc.
- Historical, current, and projected Automotive Digital Key Market size in terms of volume and value.
- Recent industry trends and developments.
- Competitive landscape of the Automotive Digital Key Market.
- Strategies of key players and product offerings.
- Potential and niche segments/regions exhibiting promising growth.
Frequently Asked Questions (FAQs):
► What is the current market scenario?
► What was the historical demand scenario, and forecast outlook from 2025 to 2032?
► What are the key market dynamics influencing growth in the Global Automotive Digital Key Market?
► Who are the prominent players in the Global Automotive Digital Key Market?
► What is the consumer perspective in the Global Automotive Digital Key Market?
► What are the key demand-side and supply-side trends in the Global Automotive Digital Key Market?
► What are the largest and the fastest-growing geographies?
► Which segment dominated and which segment is expected to grow fastest?
► What was the COVID-19 impact on the Global Automotive Digital Key Market?
Table Of Contents:
1 Market Overview
1.1 Automotive Digital Key Market Introduction
1.2 Market Analysis by Type
1.3 Market Analysis by Applications
1.4 Market Analysis by Regions
1.4.1 North America (United States, Canada and Mexico)
1.4.1.1 United States Market States and Outlook
1.4.1.2 Canada Market States and Outlook
1.4.1.3 Mexico Market States and Outlook
1.4.2 Europe (Germany, France, UK, Russia and Italy)
1.4.2.1 Germany Market States and Outlook
1.4.2.2 France Market States and Outlook
1.4.2.3 UK Market States and Outlook
1.4.2.4 Russia Market States and Outlook
1.4.2.5 Italy Market States and Outlook
1.4.3 Asia-Pacific (China, Japan, Korea, India and Southeast Asia)
1.4.3.1 China Market States and Outlook
1.4.3.2 Japan Market States and Outlook
1.4.3.3 Korea Market States and Outlook
1.4.3.4 India Market States and Outlook
1.4.3.5 Southeast Asia Market States and Outlook
1.4.4 South America, Middle East and Africa
1.4.4.1 Brazil Market States and Outlook
1.4.4.2 Egypt Market States and Outlook
1.4.4.3 Saudi Arabia Market States and Outlook
1.4.4.4 South Africa Market States and Outlook
1.5 Market Dynamics
1.5.1 Market Opportunities
1.5.2 Market Risk
1.5.3 Market Driving Force
2 Manufacturers Profiles
Continued…
About Us:
Fortune Business Insights™ delivers accurate data and innovative corporate analysis, helping organizations of all sizes make appropriate decisions. We tailor novel solutions for our clients, assisting them to address various challenges distinct to their businesses. Our aim is to empower them with holistic market intelligence, providing a granular overview of the market they are operating in.
Contact Us:
Fortune Business Insights™ Pvt. Ltd.
US:+18339092966
UK: +448085020280
APAC: +91 744 740 1245
0 notes
Text
Animal RFID Products Manufacturer
Mifare Classic 1k Key Fob Shenzhen Toptag group Technology Co., Ltd is a leader in the field of radio frequency identification (RFID). Our company is based on providing innovative intelligent identification solutions for various industries around the world. Since its establishment, we have been committed to the production and promotion of RFID technology, providing customers with efficient, safe and intelligent identification and tracking solutions.

In terms of products: Our product line covers various such as rfid microchip reader, animal microchip. Our RFID tags adopt advanced radio frequency chip technology, which can realize high-precision identification and tracking in different environments. Whether in logistics, supply chain management, retail or manufacturing, our products play a key role. In addition, we continue to innovate and launch products that support multiple radio frequency bands and communication protocols to meet the needs of different customers.
In terms of factory and capacity equipment: We have a modern production plant located in an industrial park, covering an area of more than 5000 square meters. The factory is equipped with advanced production equipment, including automated label manufacturing lines, radio frequency chip programming equipment and high-precision label printing equipment. The introduction of these equipments enables us to realize the full automatic production process from raw material procurement to final product manufacturing, ensuring the stability and consistency of product quality.
Our production equipment also supports diversified product customization. No matter what specifications, materials or functions of RFID tags customers need, we can flexibly meet their needs. Our engineer team can carry out label design and custom chip programming according to the specific needs of customers, so as to ensure that each customer can obtain the most suitable RFID solution for their application.
As a company with rich experience and leadership in the RFID field, we are driven by innovation to provide customers with high-quality intelligent identification solutions. Our products cover multiple industries and are dedicated to improving supply chain efficiency, logistics management and data tracking capabilities. Through modern factory equipment and customized production processes, we can meet the needs of different customers and provide them with customized RFID solutions to help them maintain their competitive advantages in the digital age.
Our tags range from low frequency to high frequency and are widely used in NFC, access control, supply chain management,nventory management, storage & logistics management, livestock management and so on.
0 notes
Text
How Door Access Control Enhances Security and Convenience
In today’s fast-paced world, businesses and organizations are prioritizing security and efficiency more than ever. Traditional lock-and-key mechanisms are becoming outdated, as they pose significant security risks and management challenges. Door access control systems have emerged as a reliable solution to enhance security while providing seamless convenience. These systems leverage technology to manage and monitor access, ensuring that only authorized personnel can enter specific areas.
The Growing Need for Door Access Control
Security threats, unauthorized access, and operational inefficiencies have led businesses to seek more advanced solutions. Door access control systems provide an intelligent way to restrict entry and maintain a secure environment. Whether it’s an office, educational institution, healthcare facility, or industrial site, implementing an access control system significantly reduces security vulnerabilities.
Key Benefits of Door Access Control Systems
1. Enhanced Security
One of the primary reasons for adopting a door access control system is security. Unlike traditional keys, which can be lost, stolen, or duplicated, access control systems use secure credentials such as keycards, PINs, biometrics, or smartphone-based authentication. These features ensure that only authorized individuals can gain entry, minimizing risks related to theft, espionage, or unauthorized intrusions.
2. Convenience and Ease of Use
Modern door access control solutions eliminate the need for physical keys, offering a more convenient alternative. Employees and authorized personnel can access premises using their smartphones, smart cards, or biometric credentials. This system is particularly useful for organizations with multiple entry points or restricted areas requiring different levels of access.
3. Real-Time Monitoring and Reporting
An advanced door access control system provides real-time monitoring and reporting, allowing administrators to track who enters and exits specific areas. This feature is essential for security audits, emergency responses, and compliance with industry regulations. Cloud-based access control systems enable remote management, ensuring that security personnel can take immediate action when necessary.
4. Integration with Other Security Systems
A door access control system can integrate seamlessly with surveillance cameras, alarm systems, and visitor management platforms. This synergy enhances overall security and ensures a comprehensive approach to managing access and potential security threats.
5. Scalability for Growing Businesses
As businesses expand, so do their security needs. A scalable door access control solution can accommodate new users, entry points, and locations without major infrastructure changes. Companies can easily add or revoke access permissions without the hassle of rekeying locks.
Choosing the Right Door Access Control System
With numerous access control solutions available, selecting the right system requires careful consideration. Here are some key factors to keep in mind:
1. Type of Authentication
Access control systems use different authentication methods, including:
Keycards or RFID: Contactless smart cards or fobs.
PIN Codes: Numeric codes entered via a keypad.
Biometrics: Fingerprint, facial recognition, or retina scans.
Mobile-Based Access: Smartphones as access credentials, using Bluetooth or NFC technology.
For businesses looking for a secure and hassle-free solution, mobile-based authentication, such as the one offered by Spintly, eliminates the need for physical credentials while improving convenience.
2. Cloud-Based vs. On-Premise Systems
Traditional on-premise access control requires in-house servers and maintenance, whereas cloud-based door access control offers remote access, automatic updates, and lower infrastructure costs. Companies aiming for flexibility and easy management often opt for cloud-based solutions.
3. Integration with Other Systems
When selecting a door access control system, consider whether it integrates with your existing security infrastructure. Solutions that work seamlessly with CCTV, alarms, and visitor management systems provide a more holistic security framework.
4. User Management and Scalability
A good access control solution should offer easy user management, allowing administrators to add or revoke access remotely. Scalability is crucial for businesses planning future expansion.
Why Businesses Are Choosing Spintly for Door Access Control
Among the many providers in the market, Spintly stands out with its innovative door access control solutions. Unlike traditional systems that rely on extensive wiring and complicated setups, Spintly offers a wireless, cloud-based access control system that simplifies security management. Here’s why businesses prefer Spintly:
Mobile-First Approach: Spintly eliminates the need for keycards by offering smartphone-based access control.
Wireless Infrastructure: No complex wiring, making it ideal for retrofitting existing buildings or installing in new facilities.
Seamless Integration: Works with existing security systems to provide a unified security solution.
Scalable and Cost-Effective: Easy to expand as businesses grow, with minimal maintenance requirements.
Conclusion
A door access control system is no longer a luxury but a necessity for businesses that prioritize security and efficiency. These systems provide unparalleled protection against unauthorized entry, enhance operational convenience, and integrate seamlessly with modern security infrastructures. With solutions like Spintly, organizations can adopt a wireless, cloud-based access control approach that is easy to implement and manage. As technology evolves, businesses that embrace advanced door access control solutions will not only enhance security but also streamline their operations, ensuring a safer and more efficient workplace.
#access control system#access control solutions#mobile access#visitor management system#spintly#accesscontrol#smartacess#biometrics#smartbuilding
0 notes