#professional data recovery services
Explore tagged Tumblr posts
Photo
Also, please remember: Just because your computer craps the bed DOES NOT mean your files are gone.
Even if sparks fly, your computer starts smoking and doesn't turn on anymore, chances are your hard drive is still fine.
It's incredibly easy to take out your hard drive (or SSD) from your broken computer and putting it into a working computer to access your files. It's even pretty easy with most laptops. There are a bunch of youtube tutorials, if you don't know how to do it or don't know anyone who could do it for you.
But even so:
BACK UP YOUR FREAKING FILES

beastly reminder
#I had so many people over the years coming to me and begging me to recover incredibly important files from broken thumb drives#because that thumb drive had the only copy of the file in existence#and not gonna lie... recovering files from broken thumb drives is damn near impossible#unless you go to a professional data recovery service that charges you by the megabyte#and they charge A LOT
68K notes
·
View notes
Text
Discover the Truth with Bond Rees Investigations - Your Trusted UK Detective Agency

Uncover the truth with Bond Rees Investigations, the UK’s leading private detective agency. Our expert team offers discreet and professional services, including private investigations, lie detector tests, tracing services, corporate investigations, and data recovery. With a 98.7% success rate, we ensure confidentiality and accuracy in every case. Trust Bond Rees to provide the answers you need.
#Private Investigations#UK Detective Agency#Lie Detector Tests#Tracing Services#Corporate Investigations#Data Recovery#Discreet Services#Professional Investigators#Confidential Investigations#Missing Persons
0 notes
Text

Hard drive and server recovery Near Me in New Jersey
Total Data Migration is one of the leading computer and Data Recovery Services in New Jersey, We provide offer data recovery, restoration, migration, conversion, disposal services, and many more services. Contact us today for expert assistance. For more information, call us at +1 (800) 460-7599.
#recover files from hard drive New Jersey#data recovery services near me New Jersey#external hard drive data recovery New Jersey#recover old files from hard drive Atlanta Georgia#recover deleted data from hard disk Atlanta Georgia#external hard drive data recovery near me Atlanta Georgia#professional data recovery service Atlanta Georgia#recover files hard drive external Atlanta Georgia
0 notes
Text
Zini Technologies' Superior Cloud Backup Service: Safeguarding Your Data with Excellence
In the age of technology and data-driven operations, ensuring the security and availability of your digital assets is paramount. Zini Technologies, a recognized leader in the realm of IT services, is proud to introduce its state-of-the-art cloud backup service. With our robust and reliable solutions, we offer you the peace of mind that your data is protected and accessible whenever and wherever you need it.
Cloud Computing for Secure Backup
In today's fast-paced world, the utilization of cloud computing has revolutionized how data is stored, managed, and safeguarded. Zini Technologies' cloud backup service takes full advantage of this technology, providing you with a scalable, cost-effective, and secure means of backing up your critical data. No longer do you have to rely solely on on-site servers or local backups.
Backup Made Easy with Remote Backup Service
Our remote backup service is designed with your convenience in mind. No matter where you are or what device you use, our service ensures that your data is securely and automatically backed up. Whether you work with Windows servers, Linux-based systems, or the latest macOS computers, we've got you covered. You can even restore your data to a different computer, making recovery hassle-free.
Reliable and Secure Data Protection
Your data's security is our top priority. Zini Technologies employs stringent security measures to ensure that your data is encrypted and protected from unauthorized access. With our cloud backup service, you can trust that your data is stored securely in our high-availability data centers.
Server and Computer Backup
Our cloud backup solution is not limited to just one type of device or server. We understand that businesses use a variety of platforms. That's why we offer server and computer backup services, allowing you to back up your entire infrastructure seamlessly.
Affordability and Peace of Mind
Zini Technologies' cloud backup service is not only robust and reliable but also highly cost-effective. With us, you can enjoy the assurance of your data's safety without breaking the bank. Our competitive pricing ensures that businesses of all sizes can afford the benefits of a secure backup service.
A Solution You Can Trust
Our cloud backup service is the result of years of experience and expertise in the field of data management. We understand that the data you store is not just numbers and files; it's the backbone of your business. With Zini Technologies, you have a trusted partner committed to safeguarding your data's integrity and availability.
In conclusion, data protection and backup are integral parts of any modern business. Zini Technologies' cloud backup service offers a comprehensive, reliable, and secure solution to ensure your data is always within reach. With our service, you can enjoy the peace of mind that comes with knowing your data is protected and ready for recovery when you need it. Don't leave your data's security to chance – trust Zini Technologies to provide the professional and dependable backup service your business deserves.
#it support#it companies near me#it solutions#it consulting#it helpdesk#it service management#it services near me#it support near me#it support for small business#pc repair near me#hard drive data recovery#computer services near me#pc repair#computer technician near me#security camera companies#security camera companies near me#surveillance solutions#professional security camera installation#commercial security camera installation#security camera installation companies near me#online backup#cheapest cloud storage#best cloud storage for personal use#best cloud backup
1 note
·
View note
Text
If you always found it challenging to manage your business’s IT needs? Get in touch with Clarity Technology Solutions. We investigate to find out what your company requires to succeed. We assure you that you will benefit greatly if you partner with us. Since 2005, companies have been reaching out to us.
#Data Recovery Delaware#Backup And Disaster Recovery Services#Managed IT Security Services Providers#Cybersecurity Ohio#Cyber Security Managed Service Providers#Managed Cloud Services Ohio#Professional Cloud Computing Services
0 notes
Text

Hard Drive Head Replacement Tool Set For Repair & Data Recovery
These days all leading professional data recovery companies know and successfully use data recovery products in their business. In depth knowledge of the products has become a requirement for every highly skilled data recovery specialist. We have dedicated our lives to gather precious knowledge and inventing unique methods for successful data recovery. Now we are ready to share the experience we’ve accumulated over the last few years in data recovery.
#mrt data recovery training#professional data recovery tool#pc3000 training#head replacement tools#donor drives#buy head unstick tools#data recovery services#dfl training#buy seagate donor drives#BuyWDDonorDrives
0 notes
Text
#SSD Data Recovery#SSD Data Recovery Services#professional SSD data recovery service#reliable SSD data recovery service#specializes in SSD data recovery
0 notes
Text
Provides Apple Products Repair Services| Whale Beach

Avail the best apple care products repair services in Whale Beach. We have a well-planned specialist and thousands of satisfied clients. Contact us today!
#Data Recovery Professionals Sydney#Sydney Computer And Networking Expert#Computer Installation Technician Near Me#Virus Removal Services#IT Consultancy Services Sydney
0 notes
Text
GetResponse the best email marketing software. Review: Features, Pros, and How It Stands Out
GetResponse is a comprehensive marketing automation platform that caters to businesses looking to streamline their marketing efforts. Known for its email marketing tools, GetResponse also offers a suite of other features that help businesses attract, engage, and convert customers. Here’s a detailed look at the features GetResponse offers and what sets it apart from competitors.
Minding Blowing Features:
1. Email Marketing
Drag-and-Drop Email Editor: GetResponse’s email editor allows users to create professional-looking emails without any coding knowledge. With a simple drag-and-drop interface, users can customize email templates to match their brand’s look and feel.
Personalized Email Content: Dynamic content features enable users to personalize emails for each recipient, boosting engagement rates and customer satisfaction.
Automation Features: With GetResponse’s automation tools, users can create workflows to automatically send emails based on triggers such as subscriber actions or specific dates.
2. Marketing Automation
Workflow Builder: This visual editor allows users to design workflows that automate repetitive tasks. For example, businesses can set up automated welcome emails, cart abandonment emails, or re-engagement campaigns.
Behavior Tracking: GetResponse’s automation system can track user actions and segment contacts based on behaviors, like which links they click or how long they spend on a landing page.
Lead Scoring: This feature helps businesses identify potential customers by assigning scores based on engagement, making it easier to target the most interested leads.
3. Landing Pages and Conversion Funnels
Landing Page Builder: With a library of customizable templates, the landing page builder makes it easy to create effective, high-converting pages. It includes features like split testing and SEO optimization to help improve performance.
Conversion Funnels: GetResponse offers pre-designed sales funnels that guide leads through each stage of the buyer’s journey, from lead capture to purchase. It’s a valuable tool for e-commerce businesses looking to maximize conversions.
Webinar Funnels: This feature is ideal for businesses that rely on webinars for lead generation. The webinar funnel helps users set up registration pages, send reminders, and automate follow-ups, making the entire process seamless.
4. Webinars
Built-In Webinar Tool: GetResponse is one of the few platforms that includes webinars as part of its marketing toolkit. Users can host live webinars, share files, and engage attendees with polls and Q&A sessions.
Webinar Analytics: After each session, GetResponse provides detailed analytics that help businesses understand engagement levels, attendee drop-off rates, and overall webinar success.
Follow-Up Automation: Automatically follow up with webinar attendees based on their participation. For example, you could send a thank-you email to those who attended and an on-demand recording link to those who missed it.
5. E-Commerce Features
Product Recommendation Engine: GetResponse integrates with e-commerce platforms to help businesses recommend products to customers based on past purchases.
Abandoned Cart Recovery: This feature allows businesses to reach out to customers who abandoned their carts, helping to recover potentially lost sales.
Integrated Payment Gateways: Users can set up product pages and directly integrate payment options, making it easy to sell products or services directly through GetResponse.
6. Advanced Analytics and Reporting
Email Analytics: GetResponse’s email analytics provide in-depth data on open rates, click-through rates, and bounce rates. Users can use this data to fine-tune their campaigns.
Conversion Funnel Analytics: Users can track every stage of their sales funnels to understand where leads drop off and make adjustments to improve conversion rates.
Customizable Reports: The platform offers customizable reports for different metrics, enabling businesses to get insights tailored to their specific goals.
Pros of Using GetResponse
All-in-One Platform: GetResponse offers a full suite of marketing tools, from email marketing to webinars and sales funnels, so users don’t have to juggle multiple tools.
User-Friendly Interface: Even for beginners, GetResponse’s interface is intuitive and easy to navigate.
Webinar Hosting: With built-in webinar capabilities, GetResponse stands out among other email marketing platforms, making it ideal for educational content, product demos, and more.
Advanced Segmentation and Targeting: The platform offers robust segmentation and automation tools, allowing for highly personalized and targeted marketing campaigns.
Excellent Customer Support: GetResponse is known for providing reliable customer support through live chat, email, and extensive online resources.
Cons of Using GetResponse
Pricing: Compared to some email-only platforms, GetResponse can be pricier due to its comprehensive feature set.
Complexity for Basic Users: For those who only need basic email marketing, GetResponse’s extensive features may feel overwhelming.
Learning Curve for Automation: While powerful, the automation builder can take some time to learn and optimize fully.
Who Should Use GetResponse?
GetResponse is ideal for:
Small to Medium Businesses: With its range of features, GetResponse is suitable for businesses looking to streamline and automate various aspects of their marketing efforts.
E-Commerce Businesses: With its e-commerce tools, abandoned cart recovery, and product recommendation engine, GetResponse provides essential features for online stores.
Content Creators and Educators: The built-in webinar tool makes it perfect for educators, coaches, and content creators who need to host virtual sessions and automate follow-ups.
Digital Marketers: GetResponse’s advanced segmentation and automation make it a valuable tool for digital marketers running multi-channel campaigns.
Conclusion: Is GetResponse Worth It?
For businesses looking for an all-in-one marketing solution that includes email marketing, automation, webinars, and e-commerce support, GetResponse is a strong contender. While it may have a learning curve, particularly in automation, its depth of features allows businesses to centralize their marketing activities in a single platform. Though slightly pricier than simpler email tools, its versatility and powerful capabilities justify the investment for businesses that need a comprehensive marketing solution.
2 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text

Are you in search of an IT company where you can be yourself, without judgment, and receive top-notch support? Look no further than NudeComputerGuys.com. We’re a gay-friendly tech support company that operates in the nude, offering you a unique, comfortable, and trustworthy service experience. Whether you're a business or an individual, we’re here to meet your technology needs with professionalism and care. Explore our wide range of services designed to provide the best value for your business:
Our Services:
- PC/Mac Support
- Computer Tune-up
- Android/iOS/iPadOS Assistance
- Multimedia Video Presentation
- Data Recovery
- Website Design
We look forward to helping you with all your technical needs!
3 notes
·
View notes
Text
Managing Cash Flow: The Role of Debt Collection Services in South Africa for Business
Cash flow is essential to any business, ensuring that operations run smoothly, and expenses are covered. Late or unpaid invoices, on the other hand, can have a significant impact on cash flow, causing financial difficulties and jeopardising a company's viability. Debt collection services in South Africa play a key role in assisting businesses in recovering outstanding debts and maintaining a steady cash flow.
One of the primary functions of debt collection services in South Africa is to serve as a liaison between businesses and debtors. These services focus on negotiating payment terms and agreements that benefit both parties. Debt collection services, by facilitating communication and negotiation, can assist businesses in recovering outstanding debts while maintaining positive client relationships.
In addition to negotiating payment terms, debt collection services in South Africa use a variety of strategies to recover debts. These strategies may include sending reminders and notices to debtors, making follow-up calls, and, if necessary, taking legal action. Debt collection services can increase the likelihood of collecting outstanding debts on time by leveraging their expertise and resources.
Furthermore, debt collection services in South Africa play a key role in reducing the risk of severe debt. By proactively managing and monitoring outstanding invoices, these services can detect potential problems early on and take appropriate action to avoid severe debt. This initiative-taking approach can help businesses maintain positive cash flow and avoid financial losses.
Another important feature of debt collection services in South Africa is their ability to provide businesses with valuable insights and analytics. These services can assist businesses in optimising their credit management processes and lowering the risk of future overdue payments by analysing patterns of payment and debtor behaviour. This data-driven approach may eventually lead to increased cash flow and financial stability for businesses.
Debt collection services in South Africa are also essential for helping businesses during tough economic times. In times of economic uncertainty or downturn, businesses may see an increase in overdue payments and unpaid invoices. Debt collection services can be extremely beneficial during these times, assisting businesses in recovering outstanding debts and maintaining cash flow stability.
Furthermore, debt collection services in South Africa can help businesses recover debts from difficult or unwilling debtors. Dealing with difficult debtors can be time-consuming and frustrating for businesses, especially when juggling other operational responsibilities. Debt collection services have the knowledge and resources to manage these situations professionally and efficiently, allowing businesses to focus on their core operations.
Debt collection services in South Africa can help businesses avoid legal action. When debtors refuse to pay or disputes arise, debt collection services can assist businesses in navigating the legal system and effectively resolving issues. This can help businesses save time and money on legal proceedings while also ensuring that debts are recovered as soon as possible.
Finally, debt collection services are critical to managing cash flow and ensuring the financial health of South African businesses. These services help businesses recover outstanding debts, reduce severe debt, and maintain healthy cash flow by acting as mediators, implementing effective recovery strategies, and providing valuable insights. As a result, businesses in South Africa can benefit significantly from collaborating with reputable debt collection agencies to efficiently manage their receivables.
3 notes
·
View notes
Text
Synology Data Recovery: A Comprehensive Guide
Synology is renowned for its NAS (Network Attached Storage) devices, which offer robust data storage solutions for both personal and business use. Despite their reliability and advanced features, data loss can still occur due to various reasons. This guide provides a comprehensive overview of Synology data recovery, covering the causes of data loss, the steps to recover lost data, and best practices to safeguard your data.
Understanding Synology NAS
Synology NAS devices are designed to provide a centralized and accessible storage solution with features such as RAID (Redundant Array of Independent Disks) configurations, data protection, and easy-to-use interfaces. They support multiple users and applications, making them a versatile choice for data storage and management.
Common Causes of Data Loss
Data loss in Synology NAS devices can result from various scenarios, including:
1. Hardware Failures
Disk Failure: Hard drives can fail due to age, physical damage, or manufacturing defects.
Power Surges: Electrical surges can damage the Synology NAS’s internal components.
Overheating: Inadequate cooling can lead to overheating, causing hardware malfunctions.
2. Software Issues
Firmware Corruption: Problems during firmware updates or bugs can lead to data corruption.
File System Errors: Corrupt file systems can make data inaccessible.
3. Human Error
Accidental Deletion: Users can mistakenly delete important files or entire volumes.
Misconfiguration: Incorrect setup or configuration changes can lead to data loss.
4. Malicious Attacks
Ransomware: Malware can encrypt data, making it inaccessible until a ransom is paid.
Viruses: Malicious software can corrupt or delete data.
Steps for Synology Data Recovery
When faced with data loss on a Synology NAS device, it’s crucial to follow a structured approach to maximize recovery chances. Here are the steps to follow:
1. Stop Using the Device
Immediately stop using the Synology NAS to prevent further data overwriting. Continuing to use the device can reduce the likelihood of successful data recovery.
2. Diagnose the Problem
Identify the cause of the data loss. Understanding whether the issue is due to hardware failure, software problems, human error, or a malicious attack will help determine the best recovery method.
3. Check Backups
Before attempting data recovery, check if there are any recent backups. Regular backups can save time and effort in the recovery process. If backups are available, restore the lost data from them.
4. Use Data Recovery Software
For minor data loss issues, data recovery software can be an effective solution. Several reliable tools support Synology NAS devices:
R-Studio: A powerful tool for recovering data from various storage devices, including Synology NAS.
EaseUS Data Recovery Wizard: User-friendly software that can recover files lost due to deletion, formatting, or system crashes.
Stellar Data Recovery: Known for its robust recovery capabilities, supporting Synology NAS and RAID configurations.
5. Consult Professional Data Recovery Services
For severe data loss scenarios, such as hardware failures or extensive corruption, it is advisable to seek help from professional data recovery services. These experts have the tools and knowledge to recover data from damaged Synology NAS devices. Some reputable data recovery companies include:
DriveSavers Data Recovery: Offers specialized services for Synology and other RAID systems, with a high success rate.
Ontrack Data Recovery: Known for its expertise in NAS and RAID recovery, Ontrack provides comprehensive solutions for Synology devices.
Gillware Data Recovery: Provides professional data recovery services, specializing in complex RAID and NAS systems.
6. Prevent Future Data Loss
After successfully recovering your data, implement measures to prevent future data loss:
Regular Backups: Schedule frequent backups to ensure you have up-to-date copies of your data.
Firmware Updates: Keep your Synology firmware updated to protect against bugs and vulnerabilities.
Surge Protectors: Use surge protectors to safeguard against electrical surges.
Proper Ventilation: Ensure adequate ventilation and cooling to prevent overheating.
Conclusion
Data loss on Synology NAS devices, though distressing, can often be remedied with the right approach. By understanding the common causes of data loss and following a systematic recovery process, you can effectively retrieve lost data. Utilize reliable data recovery software or consult professional services for severe cases. Additionally, implementing preventive measures will help safeguard your data against future loss, ensuring that your Synology NAS device continues to serve as a reliable data storage solution.
2 notes
·
View notes
Text
Bisexual survivors, like all survivors of any form of trauma or violence, deserve compassion, support, and better treatment. Bisexual individuals who have experienced trauma or violence may face unique challenges and forms of discrimination that require specific attention and understanding. Here are some key aspects of why bisexual survivors deserve better:
Visibility and Recognition: Bisexual survivors' experiences are often overlooked or erased, both within the LGBTQ+ community and in broader society. Their experiences might not fit neatly into heteronormative or monosexist narratives, leading to further marginalization and lack of support.
Biphobia and Stigma: Bisexual survivors may face biphobia and stigma, even from within the LGBTQ+ community, which can compound the trauma they have experienced. This additional layer of discrimination can create barriers to seeking help and support.
Access to Support Services: Support services for survivors of trauma are essential, but they may not always be inclusive and sensitive to the unique needs of bisexual individuals. Efforts should be made to ensure that support services are affirming and accommodating for all sexual orientations and gender identities.
Cultural Competency and Training: Service providers, including therapists, counselors, and law enforcement professionals, should receive training on bisexuality and the specific issues faced by bisexual individuals. This training helps them better understand and support bisexual survivors effectively.
Intersectionality: Many bisexual individuals have intersecting identities, such as race, ethnicity, gender identity, and socioeconomic status. Intersectionality must be considered when providing support and resources to address the diverse needs of bisexual survivors.
Fostering Safe Spaces: Creating safe and inclusive spaces where bisexual survivors can share their experiences and find support is crucial. This includes both physical spaces and virtual communities.
Breaking the Silence: Encouraging open conversations about bisexual survivorship can help break the silence surrounding their experiences and raise awareness about their unique needs and challenges.
Empowerment and Agency: Providing resources that empower bisexual survivors to reclaim their agency and voice in the aftermath of trauma is essential for healing and recovery.
Research and Data Collection: More research should be conducted on the experiences of bisexual survivors to better understand their needs and develop targeted interventions and support services.
Addressing Bi-Erasure in Support Discourses: Efforts should be made to address and challenge bi-erasure in discussions surrounding trauma and survivorship, ensuring that bisexual individuals' experiences are acknowledged and validated.
Overall, addressing the specific needs of bisexual survivors requires a comprehensive approach that involves education, awareness, policy changes, and a commitment to inclusivity within support systems and communities. By advocating for better treatment and support for bisexual survivors, we can work towards a more just and equitable society for all survivors of trauma and violence.
#bisexuality#lgbtq community#lgbtq#bi#support bisexuality#pride#bi tumblr#bisexuality is valid#lgbtq pride#bi pride#bisexual#bi community#bisexual community#bisexual education#bisexual visibility#bisexual nation#bisexual activism#bisexual activist#biphobia#biphobic#bi erasure#bisexual erasure
12 notes
·
View notes
Text
Journey to AWS Proficiency: Unveiling Core Services and Certification Paths
Amazon Web Services, often referred to as AWS, stands at the forefront of cloud technology and has revolutionized the way businesses and individuals leverage the power of the cloud. This blog serves as your comprehensive guide to understanding AWS, exploring its core services, and learning how to master this dynamic platform. From the fundamentals of cloud computing to the hands-on experience of AWS services, we'll cover it all. Additionally, we'll discuss the role of education and training, specifically highlighting the value of ACTE Technologies in nurturing your AWS skills, concluding with a mention of their AWS courses.

The Journey to AWS Proficiency:
1. Basics of Cloud Computing:
Getting Started: Before diving into AWS, it's crucial to understand the fundamentals of cloud computing. Begin by exploring the three primary service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Gain a clear understanding of what cloud computing is and how it's transforming the IT landscape.
Key Concepts: Delve into the key concepts and advantages of cloud computing, such as scalability, flexibility, cost-effectiveness, and disaster recovery. Simultaneously, explore the potential challenges and drawbacks to get a comprehensive view of cloud technology.
2. AWS Core Services:
Elastic Compute Cloud (EC2): Start your AWS journey with Amazon EC2, which provides resizable compute capacity in the cloud. Learn how to create virtual servers, known as instances, and configure them to your specifications. Gain an understanding of the different instance types and how to deploy applications on EC2.
Simple Storage Service (S3): Explore Amazon S3, a secure and scalable storage service. Discover how to create buckets to store data and objects, configure permissions, and access data using a web interface or APIs.
Relational Database Service (RDS): Understand the importance of databases in cloud applications. Amazon RDS simplifies database management and maintenance. Learn how to set up, manage, and optimize RDS instances for your applications. Dive into database engines like MySQL, PostgreSQL, and more.
3. AWS Certification:
Certification Paths: AWS offers a range of certifications for cloud professionals, from foundational to professional levels. Consider enrolling in certification courses to validate your knowledge and expertise in AWS. AWS Certified Cloud Practitioner, AWS Certified Solutions Architect, and AWS Certified DevOps Engineer are some of the popular certifications to pursue.
Preparation: To prepare for AWS certifications, explore recommended study materials, practice exams, and official AWS training. ACTE Technologies, a reputable training institution, offers AWS certification training programs that can boost your confidence and readiness for the exams.
4. Hands-on Experience:
AWS Free Tier: Register for an AWS account and take advantage of the AWS Free Tier, which offers limited free access to various AWS services for 12 months. Practice creating instances, setting up S3 buckets, and exploring other services within the free tier. This hands-on experience is invaluable in gaining practical skills.
5. Online Courses and Tutorials:
Learning Platforms: Explore online learning platforms like Coursera, edX, Udemy, and LinkedIn Learning. These platforms offer a wide range of AWS courses taught by industry experts. They cover various AWS services, architecture, security, and best practices.
Official AWS Resources: AWS provides extensive online documentation, whitepapers, and tutorials. Their website is a goldmine of information for those looking to learn more about specific AWS services and how to use them effectively.
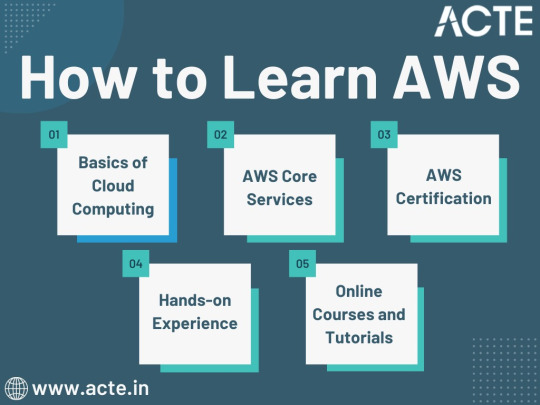
Amazon Web Services (AWS) represents an exciting frontier in the realm of cloud computing. As businesses and individuals increasingly rely on the cloud for innovation and scalability, AWS stands as a pivotal platform. The journey to AWS proficiency involves grasping fundamental cloud concepts, exploring core services, obtaining certifications, and acquiring practical experience. To expedite this process, online courses, tutorials, and structured training from renowned institutions like ACTE Technologies can be invaluable. ACTE Technologies' comprehensive AWS training programs provide hands-on experience, making your quest to master AWS more efficient and positioning you for a successful career in cloud technology.
8 notes
·
View notes
Text
Don't Let SQL Database Data Loss Disrupt Your Business! Get Professional Recovery Now!
3 notes
·
View notes