#oauth2 authentication
Explore tagged Tumblr posts
Text
0 notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
Spring Security Using Facebook Authorization: A Comprehensive Guide
In today's digital landscape, integrating third-party login mechanisms into applications has become a standard practice. It enhances user experience by allowing users to log in with their existing social media accounts. In this blog post, we will walk through the process of integrating Facebook authorization into a Spring Boot application using Spring Security.
Table of Contents
Introduction
Prerequisites
Setting Up Facebook Developer Account
Creating a Spring Boot Application
Configuring Spring Security for OAuth2 Login
Handling Facebook User Data
Testing the Integration
Conclusion
1. Introduction
OAuth2 is an open standard for access delegation, commonly used for token-based authentication. Facebook, among other social media platforms, supports OAuth2, making it possible to integrate Facebook login into your Spring Boot application.
2. Prerequisites
Before we start, ensure you have the following:
JDK 11 or later
Maven
An IDE (e.g., IntelliJ IDEA or Eclipse)
A Facebook Developer account
3. Setting Up Facebook Developer Account
To use Facebook login, you need to create an app on the Facebook Developer portal:
Go to the Facebook Developer website and log in.
Click on "My Apps" and then "Create App."
Choose an app type (e.g., "For Everything Else") and provide the required details.
Once the app is created, go to "Settings" > "Basic" and note down the App ID and App Secret.
Add a product, select "Facebook Login," and configure the Valid OAuth Redirect URIs to http://localhost:8080/login/oauth2/code/facebook.
4. Creating a Spring Boot Application
Create a new Spring Boot project with the necessary dependencies. You can use Spring Initializr or add the dependencies manually to your pom.xml.
Dependencies
<dependencies> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-security</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-oauth2-client</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-thymeleaf</artifactId> </dependency> </dependencies>
5. Configuring Spring Security for OAuth2 Login
Next, configure Spring Security to use Facebook for OAuth2 login.
application.properties
Add your Facebook app credentials to src/main/resources/application.properties.spring.security.oauth2.client.registration.facebook.client-id=YOUR_FACEBOOK_APP_ID spring.security.oauth2.client.registration.facebook.client-secret=YOUR_FACEBOOK_APP_SECRET spring.security.oauth2.client.registration.facebook.redirect-uri-template={baseUrl}/login/oauth2/code/{registrationId} spring.security.oauth2.client.registration.facebook.scope=email,public_profile spring.security.oauth2.client.registration.facebook.client-name=Facebook spring.security.oauth2.client.registration.facebook.authorization-grant-type=authorization_code spring.security.oauth2.client.provider.facebook.authorization-uri=https://www.facebook.com/v11.0/dialog/oauth spring.security.oauth2.client.provider.facebook.token-uri=https://graph.facebook.com/v11.0/oauth/access_token spring.security.oauth2.client.provider.facebook.user-info-uri=https://graph.facebook.com/me?fields=id,name,email spring.security.oauth2.client.provider.facebook.user-name-attribute=id
Security Configuration
Create a security configuration class to handle the OAuth2 login.import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.security.config.annotation.web.builders.HttpSecurity; import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity; import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter; import org.springframework.security.oauth2.client.oidc.userinfo.OidcUserService; import org.springframework.security.oauth2.client.userinfo.DefaultOAuth2UserService; import org.springframework.security.oauth2.client.userinfo.OAuth2UserService; import org.springframework.security.oauth2.core.oidc.user.OidcUser; import org.springframework.security.oauth2.core.user.OAuth2User; import org.springframework.security.web.authentication.SimpleUrlAuthenticationFailureHandler; @Configuration @EnableWebSecurity public class SecurityConfig extends WebSecurityConfigurerAdapter { @Override protected void configure(HttpSecurity http) throws Exception { http .authorizeRequests(authorizeRequests -> authorizeRequests .antMatchers("/", "/error", "/webjars/**").permitAll() .anyRequest().authenticated() ) .oauth2Login(oauth2Login -> oauth2Login .loginPage("/login") .userInfoEndpoint(userInfoEndpoint -> userInfoEndpoint .oidcUserService(this.oidcUserService()) .userService(this.oAuth2UserService()) ) .failureHandler(new SimpleUrlAuthenticationFailureHandler()) ); } private OAuth2UserService<OidcUserRequest, OidcUser> oidcUserService() { final OidcUserService delegate = new OidcUserService(); return (userRequest) -> { OidcUser oidcUser = delegate.loadUser(userRequest); // Custom logic here return oidcUser; }; } private OAuth2UserService<OAuth2UserRequest, OAuth2User> oAuth2UserService() { final DefaultOAuth2UserService delegate = new DefaultOAuth2UserService(); return (userRequest) -> { OAuth2User oAuth2User = delegate.loadUser(userRequest); // Custom logic here return oAuth2User; }; } }
6. Handling Facebook User Data
After a successful login, you might want to handle and display user data.
Custom User Service
Create a custom service to process user details.import org.springframework.security.oauth2.core.user.OAuth2User; import org.springframework.security.oauth2.core.user.OAuth2UserAuthority; import org.springframework.security.oauth2.client.userinfo.OAuth2UserService; import org.springframework.security.oauth2.client.oidc.userinfo.OidcUserService; import org.springframework.security.oauth2.core.oidc.user.OidcUser; import org.springframework.security.oauth2.client.userinfo.DefaultOAuth2UserService; import org.springframework.security.oauth2.client.oidc.userinfo.OidcUserRequest; import org.springframework.security.oauth2.client.userinfo.OAuth2UserRequest; import org.springframework.stereotype.Service; import java.util.Map; import java.util.Set; import java.util.HashMap; @Service public class CustomOAuth2UserService implements OAuth2UserService<OAuth2UserRequest, OAuth2User> { private final DefaultOAuth2UserService delegate = new DefaultOAuth2UserService(); @Override public OAuth2User loadUser(OAuth2UserRequest userRequest) { OAuth2User oAuth2User = delegate.loadUser(userRequest); Map<String, Object> attributes = new HashMap<>(oAuth2User.getAttributes()); // Additional processing of attributes if needed return oAuth2User; } }
Controller
Create a controller to handle login and display user info.import org.springframework.security.core.annotation.AuthenticationPrincipal; import org.springframework.security.oauth2.core.user.OAuth2User; import org.springframework.stereotype.Controller; import org.springframework.ui.Model; import org.springframework.web.bind.annotation.GetMapping; @Controller public class LoginController { @GetMapping("/login") public String getLoginPage() { return "login"; } @GetMapping("/") public String getIndexPage(Model model, @AuthenticationPrincipal OAuth2User principal) { if (principal != null) { model.addAttribute("name", principal.getAttribute("name")); } return "index"; } }
Thymeleaf Templates
Create Thymeleaf templates for login and index pages.
src/main/resources/templates/login.html
<!DOCTYPE html> <html xmlns:th="http://www.thymeleaf.org"> <head> <title>Login</title> </head> <body> <h1>Login</h1> <a href="/oauth2/authorization/facebook">Login with Facebook</a> </body> </html>
src/main/resources/templates/index.html
<!DOCTYPE html> <html xmlns:th="http://www.thymeleaf.org"> <head> <title>Home</title> </head> <body> <h1>Home</h1> <div th:if="${name}"> <p>Welcome, <span th:text="${name}">User</span>!</p> </div> <div th:if="${!name}"> <p>Please <a href="/login">log in</a>.</p> </div> </body> </html>
7. Testing the Integration
Run your Spring Boot application and navigate to http://localhost:8080. Click on the "Login with Facebook" link and authenticate with your Facebook credentials. If everything is set up correctly, you should be redirected to the home page with your Facebook profile name displayed.
8. Conclusion
Integrating Facebook login into your Spring Boot application using Spring Security enhances user experience and leverages the power of OAuth2. With this setup, users can easily log in with their existing Facebook accounts, providing a seamless and secure authentication process.
By following this guide,
2 notes
·
View notes
Text
Identity, authentication, anonymity; Pseudonymous identity and recovery in an uncaring world. Revision 2.1a
Identity, authentication, anonymity; Pseudonymous identity and recovery in an uncaring world. Revision 2.1a This paper explores managing identity and account recovery, going beyond multi-factor authentication (MFA) and examining the potential role of using proof of observability ledgers. The focus is on observability networks, undeniably signatures, and hard anonymity. The goal is to allow users to recover from catastrophic losses of secret keys, hardware tokens, computers, and mobile devices while still maintaining a pseudonymous identity. The paper also discusses the question of human-based secret recovery and revisits the web of trust in the age of social media. It emphasizes that the users most at risk are the ones who need the highest level of security. To achieve this, the paper proposes using secret sharing methods to create identity control blocks, understanding the difference between statutory identity and persistent global pseudonymous identity, and recognizing why this is important in the modern social context. Mitigating the risks of global identities is also discussed, and the paper proposes bootstrapping the protocol using peer-to-peer methods over existing protocols. The pitfalls of failure to scale are highlighted, and the importance of considering human factors and cryptography engineering in a combined system is emphasized. The paper suggests avoiding federated protocols to prevent monopolistic oligarchies from emerging. Since these identities are not tied to a central service they are not entrapped to a walled garden and can freely move from service to service. With operational conformance to OpenID Oauth2 and Fido U2F they can quickly be deployed to many existing services. To ensure secure key recovery, players use Shamir's secret sharing to publish a specific number of recovery key bits to a subset of peers. The reconvocation key of the primary key is also published this way. Although not all members will sign everyone's key, all group members watch the log, and groups can be of arbitrary sizes based on performance and connectedness. Players should be in multiple groups, and auto-summaries of group hashes are published to prevent rollbacks. In case a player loses their primary hardware key, they can convince N out of M of their key partners to publish their revocation token. All actions in the game use N of M fail/stop multi-party computation, and the game doesn't require a central authority or policy-setting organization since it relies on hardware tokens and published revocation and recovery keys. In practical operation the game will be designed to cause tokens to fail to simulate key loss, as well as designate some players as attackers. Each token will initially be loaded with a “Alias” and “True Name”. Attackers will have “Agent Smith” in the true name field. A play variant may be created where cheating detection by the group can force the reveal of the “True Name”.
3 notes
·
View notes
Text
You can learn NodeJS easily, Here's all you need:
1.Introduction to Node.js
• JavaScript Runtime for Server-Side Development
• Non-Blocking I/0
2.Setting Up Node.js
• Installing Node.js and NPM
• Package.json Configuration
• Node Version Manager (NVM)
3.Node.js Modules
• CommonJS Modules (require, module.exports)
• ES6 Modules (import, export)
• Built-in Modules (e.g., fs, http, events)
4.Core Concepts
• Event Loop
• Callbacks and Asynchronous Programming
• Streams and Buffers
5.Core Modules
• fs (File Svstem)
• http and https (HTTP Modules)
• events (Event Emitter)
• util (Utilities)
• os (Operating System)
• path (Path Module)
6.NPM (Node Package Manager)
• Installing Packages
• Creating and Managing package.json
• Semantic Versioning
• NPM Scripts
7.Asynchronous Programming in Node.js
• Callbacks
• Promises
• Async/Await
• Error-First Callbacks
8.Express.js Framework
• Routing
• Middleware
• Templating Engines (Pug, EJS)
• RESTful APIs
• Error Handling Middleware
9.Working with Databases
• Connecting to Databases (MongoDB, MySQL)
• Mongoose (for MongoDB)
• Sequelize (for MySQL)
• Database Migrations and Seeders
10.Authentication and Authorization
• JSON Web Tokens (JWT)
• Passport.js Middleware
• OAuth and OAuth2
11.Security
• Helmet.js (Security Middleware)
• Input Validation and Sanitization
• Secure Headers
• Cross-Origin Resource Sharing (CORS)
12.Testing and Debugging
• Unit Testing (Mocha, Chai)
• Debugging Tools (Node Inspector)
• Load Testing (Artillery, Apache Bench)
13.API Documentation
• Swagger
• API Blueprint
• Postman Documentation
14.Real-Time Applications
• WebSockets (Socket.io)
• Server-Sent Events (SSE)
• WebRTC for Video Calls
15.Performance Optimization
• Caching Strategies (in-memory, Redis)
• Load Balancing (Nginx, HAProxy)
• Profiling and Optimization Tools (Node Clinic, New Relic)
16.Deployment and Hosting
• Deploying Node.js Apps (PM2, Forever)
• Hosting Platforms (AWS, Heroku, DigitalOcean)
• Continuous Integration and Deployment-(Jenkins, Travis CI)
17.RESTful API Design
• Best Practices
• API Versioning
• HATEOAS (Hypermedia as the Engine-of Application State)
18.Middleware and Custom Modules
• Creating Custom Middleware
• Organizing Code into Modules
• Publish and Use Private NPM Packages
19.Logging
• Winston Logger
• Morgan Middleware
• Log Rotation Strategies
20.Streaming and Buffers
• Readable and Writable Streams
• Buffers
• Transform Streams
21.Error Handling and Monitoring
• Sentry and Error Tracking
• Health Checks and Monitoring Endpoints
22.Microservices Architecture
• Principles of Microservices
• Communication Patterns (REST, gRPC)
• Service Discovery and Load Balancing in Microservices
1 note
·
View note
Text
Essential Components of a Production Microservice Application
DevOps Automation Tools and modern practices have revolutionized how applications are designed, developed, and deployed. Microservice architecture is a preferred approach for enterprises, IT sectors, and manufacturing industries aiming to create scalable, maintainable, and resilient applications. This blog will explore the essential components of a production microservice application, ensuring it meets enterprise-grade standards.
1. API Gateway
An API Gateway acts as a single entry point for client requests. It handles routing, composition, and protocol translation, ensuring seamless communication between clients and microservices. Key features include:
Authentication and Authorization: Protect sensitive data by implementing OAuth2, OpenID Connect, or other security protocols.
Rate Limiting: Prevent overloading by throttling excessive requests.
Caching: Reduce response time by storing frequently accessed data.
Monitoring: Provide insights into traffic patterns and potential issues.
API Gateways like Kong, AWS API Gateway, or NGINX are widely used.
Mobile App Development Agency professionals often integrate API Gateways when developing scalable mobile solutions.
2. Service Registry and Discovery
Microservices need to discover each other dynamically, as their instances may scale up or down or move across servers. A service registry, like Consul, Eureka, or etcd, maintains a directory of all services and their locations. Benefits include:
Dynamic Service Discovery: Automatically update the service location.
Load Balancing: Distribute requests efficiently.
Resilience: Ensure high availability by managing service health checks.
3. Configuration Management
Centralized configuration management is vital for managing environment-specific settings, such as database credentials or API keys. Tools like Spring Cloud Config, Consul, or AWS Systems Manager Parameter Store provide features like:
Version Control: Track configuration changes.
Secure Storage: Encrypt sensitive data.
Dynamic Refresh: Update configurations without redeploying services.
4. Service Mesh
A service mesh abstracts the complexity of inter-service communication, providing advanced traffic management and security features. Popular service mesh solutions like Istio, Linkerd, or Kuma offer:
Traffic Management: Control traffic flow with features like retries, timeouts, and load balancing.
Observability: Monitor microservice interactions using distributed tracing and metrics.
Security: Encrypt communication using mTLS (Mutual TLS).
5. Containerization and Orchestration
Microservices are typically deployed in containers, which provide consistency and portability across environments. Container orchestration platforms like Kubernetes or Docker Swarm are essential for managing containerized applications. Key benefits include:
Scalability: Automatically scale services based on demand.
Self-Healing: Restart failed containers to maintain availability.
Resource Optimization: Efficiently utilize computing resources.
6. Monitoring and Observability
Ensuring the health of a production microservice application requires robust monitoring and observability. Enterprises use tools like Prometheus, Grafana, or Datadog to:
Track Metrics: Monitor CPU, memory, and other performance metrics.
Set Alerts: Notify teams of anomalies or failures.
Analyze Logs: Centralize logs for troubleshooting using ELK Stack (Elasticsearch, Logstash, Kibana) or Fluentd.
Distributed Tracing: Trace request flows across services using Jaeger or Zipkin.
Hire Android App Developers to ensure seamless integration of monitoring tools for mobile-specific services.
7. Security and Compliance
Securing a production microservice application is paramount. Enterprises should implement a multi-layered security approach, including:
Authentication and Authorization: Use protocols like OAuth2 and JWT for secure access.
Data Encryption: Encrypt data in transit (using TLS) and at rest.
Compliance Standards: Adhere to industry standards such as GDPR, HIPAA, or PCI-DSS.
Runtime Security: Employ tools like Falco or Aqua Security to detect runtime threats.
8. Continuous Integration and Continuous Deployment (CI/CD)
A robust CI/CD pipeline ensures rapid and reliable deployment of microservices. Using tools like Jenkins, GitLab CI/CD, or CircleCI enables:
Automated Testing: Run unit, integration, and end-to-end tests to catch bugs early.
Blue-Green Deployments: Minimize downtime by deploying new versions alongside old ones.
Canary Releases: Test new features on a small subset of users before full rollout.
Rollback Mechanisms: Quickly revert to a previous version in case of issues.
9. Database Management
Microservices often follow a database-per-service model to ensure loose coupling. Choosing the right database solution is critical. Considerations include:
Relational Databases: Use PostgreSQL or MySQL for structured data.
NoSQL Databases: Opt for MongoDB or Cassandra for unstructured data.
Event Sourcing: Leverage Kafka or RabbitMQ for managing event-driven architectures.
10. Resilience and Fault Tolerance
A production microservice application must handle failures gracefully to ensure seamless user experiences. Techniques include:
Circuit Breakers: Prevent cascading failures using tools like Hystrix or Resilience4j.
Retries and Timeouts: Ensure graceful recovery from temporary issues.
Bulkheads: Isolate failures to prevent them from impacting the entire system.
11. Event-Driven Architecture
Event-driven architecture improves responsiveness and scalability. Key components include:
Message Brokers: Use RabbitMQ, Kafka, or AWS SQS for asynchronous communication.
Event Streaming: Employ tools like Kafka Streams for real-time data processing.
Event Sourcing: Maintain a complete record of changes for auditing and debugging.
12. Testing and Quality Assurance
Testing in microservices is complex due to the distributed nature of the architecture. A comprehensive testing strategy should include:
Unit Tests: Verify individual service functionality.
Integration Tests: Validate inter-service communication.
Contract Testing: Ensure compatibility between service APIs.
Chaos Engineering: Test system resilience by simulating failures using tools like Gremlin or Chaos Monkey.
13. Cost Management
Optimizing costs in a microservice environment is crucial for enterprises. Considerations include:
Autoscaling: Scale services based on demand to avoid overprovisioning.
Resource Monitoring: Use tools like AWS Cost Explorer or Kubernetes Cost Management.
Right-Sizing: Adjust resources to match service needs.
Conclusion
Building a production-ready microservice application involves integrating numerous components, each playing a critical role in ensuring scalability, reliability, and maintainability. By adopting best practices and leveraging the right tools, enterprises, IT sectors, and manufacturing industries can achieve operational excellence and deliver high-quality services to their customers.
Understanding and implementing these essential components, such as DevOps Automation Tools and robust testing practices, will enable organizations to fully harness the potential of microservice architecture. Whether you are part of a Mobile App Development Agency or looking to Hire Android App Developers, staying ahead in today’s competitive digital landscape is essential.
0 notes
Text
Flask and OAuth2: Securing Your API with Industry-Standard Authentication
Introduction Flask and OAuth2: Securing Your API with Industry-Standard Authentication is a crucial aspect of building secure and scalable web applications. In this tutorial, we will explore the world of Flask, a lightweight Python web framework, and OAuth2, an industry-standard authentication protocol. We will delve into the technical background, implementation guide, code examples, best…
0 notes
Text
Unlocking the Power of Keycloak for Identity and Access Management (IAM)
In the ever-evolving digital landscape, managing identity and access securely is paramount. Businesses need a robust, scalable, and flexible solution to safeguard their applications and services. Enter Keycloak, an open-source Identity and Access Management (IAM) tool that has emerged as a game-changer for organizations worldwide.
What is Keycloak?
Keycloak is an open-source IAM solution developed by Red Hat, designed to provide secure authentication and authorization for applications. It simplifies user management while supporting modern security protocols such as OAuth2, OpenID Connect, and SAML. With its rich feature set and community support, Keycloak is a preferred choice for developers and administrators alike.
Key Features of Keycloak
1. Single Sign-On (SSO)
Keycloak enables users to log in once and gain access to multiple applications without re-authenticating. This enhances user experience and reduces friction.
2. Social Login Integration
With out-of-the-box support for social login providers like Google, Facebook, and Twitter, Keycloak makes it easy to offer social authentication for applications.
3. Fine-Grained Access Control
Keycloak allows administrators to define roles, permissions, and policies to control access to resources. This ensures that users only access what they’re authorized to.
4. User Federation
Keycloak supports integrating with existing user directories like LDAP and Active Directory. This simplifies the adoption process by leveraging existing user bases.
5. Extensibility
Its plugin-based architecture allows customization to fit unique business requirements. From custom themes to additional authentication mechanisms, the possibilities are vast.
6. Multi-Factor Authentication (MFA)
For enhanced security, Keycloak supports MFA, adding an extra layer of protection to user accounts.
Why Choose Keycloak for IAM?
Open Source Advantage: Being open source, Keycloak eliminates vendor lock-in and offers complete transparency.
Scalability: It handles millions of users and adapts to growing business needs.
Developer-Friendly: Its RESTful APIs and SDKs streamline integration into existing applications.
Active Community: Keycloak’s active community ensures continuous updates, bug fixes, and feature enhancements.
Real-World Use Cases
E-Commerce Platforms: Managing customer accounts, providing social logins, and enabling secure payments.
Enterprise Applications: Centralized authentication for internal tools and systems.
Educational Portals: Facilitating SSO for students and staff across multiple applications.
Cloud and DevOps: Securing APIs and managing developer access in CI/CD pipelines.
Getting Started with Keycloak
Installation: Keycloak can be deployed on-premises or in the cloud. It supports Docker and Kubernetes for easy containerized deployment.
Configuration: After installation, configure realms, clients, roles, and users to set up your IAM environment.
Integration: Use Keycloak’s adapters or APIs to integrate it with your applications.
A Glimpse into the Future
As organizations embrace digital transformation, IAM solutions like Keycloak are becoming indispensable. With its commitment to security, scalability, and community-driven innovation, Keycloak is set to remain at the forefront of IAM solutions.
Final Thoughts
Keycloak is not just an IAM tool; it’s a strategic asset that empowers businesses to secure their digital ecosystem. By simplifying user authentication and access management, it helps organizations focus on what truly matters: delivering value to their customers.
So, whether you’re a developer building a new application or an administrator managing enterprise security, Keycloak is a tool worth exploring. Its features, flexibility, and community support make it a standout choice in the crowded IAM space.
For more information visit : https://www.hawkstack.com/
0 notes
Link
#angular-development#authentication-management#keycloak-authentication#multi-tenancy#saas-architecture#saas-security#software-architecture#spring-boot#programming
0 notes
Text
API Integration Services
Jellyfish Technologies is one of the most advanced companies in developing digital products and software, with more than 150 experts and over 13 years of experience. We have completed over 4,000 web, mobile, and software projects.
We are dealing with custom API integration services for iOS, Android, and web applications, using a variety of authentication methods, including OAuth, OAuth1, OAuth2, JSON Web Token (JWT), and SAML. At Jellyfish Technologies, we are on the focus of modernization towards developing the most efficient digital ecosystems possible. From consulting to development, Jellyfish Technologies provides full-scale services offered by one of the best API development companies around to ensure that your project succeeds, consulting, and more, to drive your project’s success.
0 notes
Text

How Spring Security Protects Your Web Application
Spring Security is a powerful and customizable framework for securing web applications in the Spring ecosystem. Here’s how it safeguards your application:
1️⃣ Authentication: Verifies user identities through login forms, HTTP basic authentication, OAuth2, and more.
2️⃣ Authorization: Controls user access with roles and permissions, defining who can access which parts of the application.
3️⃣ Protection Against CSRF: Cross-Site Request Forgery (CSRF) attacks are prevented by validating tokens in requests.
4️⃣ Session Management: Manages user sessions securely, limiting vulnerabilities like session fixation.
5️⃣ Password Encoding: Encrypts passwords using algorithms like bcrypt, preventing plain-text storage.
6️⃣ Security Headers: Adds default security headers (X-Content-Type, X-Frame-Options, etc.) to secure requests and responses.
7️⃣ OAuth2 and JWT Support: Enables integration with OAuth2 for secure SSO and JWT for stateless session handling.
Secure your application effectively with Spring Security – customizable, reliable, and robust!
🚀 Take your skills to the next level with Spring Online Training for comprehensive, hands-on learning in Spring Security, Spring Boot, and more!
#SpringSecurity#SpringOnlineTraining#WebAppSecurity#SpringFramework#programming#100daysofcode#software#web development#angulardeveloper#coding
0 notes
Text
Post on Tumblr via command line with pytumblr on GitHub
https://github.com/tumblr/pytumblr
I very quickly yesterday got pytumblr to work so I'm going to dump some instructions. I didn't test if it works on Windows but I mention how you would do it on Windows it a couple times, where I think python3 is python on Windows and you use right-click to copy in the terminal and Ctrl + V to paste, and now that I am thinking of it, you might need to change the Windows Command Prompt settings to allow you to right-click to copy selection.
I'm NOT an expert but am sharing to help save time of someone who wants to post via command line!
These are the only commands you need to do to get pytumblr up and running.
git clone https://github.com/tumblr/pytumblr cd pytumblr python3 setup.py build python3 interactive_console.py
Before doing these commands, you will be going to https://www.tumblr.com/oauth/apps while logged in to get your consumer key and your consumer secret key. After doing these commands you will be opening, while logged in (I didn't test it while logged out as I didn't want to risk failure after much trial and error already), a special URL that you are prompted to do, authenticating that, then pasting the redirected URL in the browser back into the console. Then you just need to type python3 interactive_console.py whenever you want to post onto Tumblr with the pytumblr commands given in the README.
When you have interactively authenticated yourself via the python script at the command line (the last command inputted above) you can freely input pytumblr commands in the interactive console (the same python command I just mentioned here and above) such as:
client.posts('blogName', id='123456') (get the full information about any Tumblr post after getting its ID from its url and putting that ID into the ID field)
or
client.reblog('blogName', id='123456', reblog_key='ASflhgjkl', tags=['tag1', 'tag2']) (reblog any post after getting its reblog key, only possible AFAIK in the text dump that is outputted from the above command)
or
client.create_text('blogName', format='html', body='
full single line html here
do breaks italic yay I love html so much') (make a text post using 'html' or 'markdown' format)
These beautiful commands are why it's worth it to download and setup your interactive console experience with Tumblr :)
Register your API key and your secret key
https://www.tumblr.com/oauth/apps
You have to fill in the required fields "Application Name" "Application Website" "Application Description" "Administrative contact email" "Default callback URL" and "OAuth2 redirect urls (space separate)". For website, description, callback URL, and OAuth2 redirect URLs, well it doesn't matter for you the user because that required information is for third-parties to have a good user experience integrating their apps into the Tumblr API. But since they are required fields, put in whatever, except for the website field and the two remaining URL fields, put in the same website for those three fields and with https:// before the URL just to be safe, that's what I did. It kept rejecting my random URLs but I made a .net URL consistently across those three fields and they were considered valid.
It will give you your two keys in this page, both visible after you press "Show Secret Key". Save your OAuth Consumer Key and your Secret Key into a text file so you don't need to log in to look these up.

Downloading the resource
Pytumblr is dependent on Python. On Linux you should have python3 installed and on Windows you should have python installed. That way you can use the python executable, whether it is just python or python3that is available, to run the setup.py script and the interactive_console.py script.
The resources for Pytumblr, besides python, are easily downloaded for users of git. Usually you have git installed if you are a programmer and that makes downloading the source files easy.
git clone https://github.com/tumblr/pytumblr
But you can get the source files from the GitHub when you click Download ZIP.
https://github.com/tumblr/pytumblr

You will find the scripts and such after you unzip/extract the resource, known as pytumblr-master.zip, into its own folder.


Build the resource
Open the console inside your unzipped folder. On Linux you can press F4 in your file explorer, or you can open the terminal navigate it like so: cd /home/inco/Documents/pytumblr-master . If you've only just used the git command to download the resources via console, then do cd pytumblr.
Build the script locally. I couldn't get the install to work like in other tutorials, nor pip3 install pytumblr, so I stick to build option with this command.
python3 setup.py build
The folder contents appear to move around a bit. It's built, so now you can open the interactive console!
Register your app
Open the interactive console in the command line in the same folder where you did the build command. You need the tool interactive_console.py and of all the downloads I tried today, only the official pytumblr has this working with the correct syntax to integrate itself with pytumblr.
python3 interactive_console.py
or
python interactive_console.py
same difference...
The interactive console will prompt you like so:
Retrieve consumer key and consumer secret from http://www.tumblr.com/oauth/apps Paste the consumer key here:
So that's your OAuth Consumer Key you saved into your text file. Paste it into your terminal with Ctrl + Shift + V if you are on Linux, or by Ctrl + V on Windows. After you paste it and submit it by pressing Return (ie. enter), it will prompt for the Secret Key.
Paste the consumer secret here:
Paste your Secret Key.
Then the interactive console will tell you to go to a URL.
Please go here and authorize: (url) Allow then paste the full redirect URL here:
Log in to your account, navigate to that URL. On Linux you can copy the URL to your clipboard by highlighting it and pressing Ctrl + Shift + C, and on Windows you can copy the URL to your clipboard by highlighting it and right clicking.
Do the allow process that you are prompted to do on the webpage. You'll be redirected to a gibberish page that won't load. Copy that broken URL to your clipboard, paste it into the console, and press enter.
If you are successful, then the console will prompt you like so:
pytumblr client created. You may run pytumblr commands prefixed with "client". (version information) Type "help", "copyright", "credits" or "license" for more information. (InteractiveConsole)
>
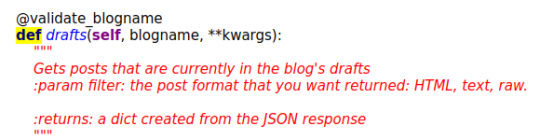
Now you can initiate interactive_console.py whenever you want to post to Tumblr via console. The commands are mostly in the README for pytumblr but there was some like client.drafts were not in the README and I found it in build\lib\pytumblr__init__.py looking for words that followed def.
#tut#op#couldn't figure out how to post a full essay with embedded images via pytumblr#but i should share in case i take ten years to figure out why i can't do everything
0 notes
Text
API-Free: The Secret to Achieving Advanced Features at a Low Cost
As artificial intelligence (AI) continues to drive the development of different fields from video script generation to geocoding solutions, the digital landscape is undergoing tremendous changes. The introduction of innovative models such as Fuyu - 8b and Heaven Heart has set new standards for AI capabilities, enabling developers to design innovative AI applications that meet various needs. Among them, OAuth2 is a basic authentication structure that protects the API user interfaces of platforms such as AI video script generation platforms, which automatically create web content with impressive efficiency.
In the field of intelligent chatbots, the proliferation of dedicated APIs such as the Kimi AI API is noteworthy. These APIs encourage designers to build chatbots that can replicate human - like conversations, dynamically adapt to customer inputs, and provide feedback that enhances personal engagement. This intelligent chatbot API utilizes the underlying architecture of AI agents, which is rooted in the concept of AI agent architecture. This architecture allows for the seamless integration of numerous AI components to produce an acceptable and cohesive personal experience.
The use of text - generating AI has also grown rapidly. Systems using such AI aim to generate contextually appropriate and coherent text, whether for customer support, content development, or various other applications. These AI models can generate a large amount of text that not only conforms to the customer's intention but also resembles human writing style to some extent, making them almost identical to human - generated materials.
In terms of vision, reverse image search engine tools are becoming increasingly sophisticated, allowing users to identify and locate images with a single click. These tools are usually supported by powerful artificial intelligence models that can analyze and match images with incredible accuracy, facilitating everything from e - commerce applications to digital asset management. The integration of these artificial intelligence tools with other platforms has become more structured, thanks in part to open platform API interfaces that allow developers to easily connect different systems and services.
The e - invoice interface represents a significant step forward in economic technology in terms of automation and secure procurement. The interface utilizes artificial intelligence to ensure that electronic bills are processed correctly and effectively, reducing the risk of errors and accelerating the settlement cycle. Incorporating artificial intelligence into such financial systems is not only about efficiency but also about improving the overall accuracy and integrity of economic procurement.
In the field of geographic information, the expansion of artificial intelligence maps is changing the way we interact with spatial information. Tools such as the Geoapify Geocoding API are leading this trend, providing developers with powerful geocoding services that can convert addresses into geographic coordinates and vice versa. This API is particularly useful for applications that require precise location data, such as logistics, travel, and urban planning.
At the same time, the Qianfan SDK has brought a wave to the developer community, providing a comprehensive toolkit for building AI applications. The design goal of this SDK is to be flexible and able to integrate different AI frameworks and APIs into one application, thus accelerating the development process. It is particularly useful for developers who wish to integrate advanced AI functions such as natural language processing or computer vision into their applications.
The rise of systems such as the text deletion tool Texttract highlights the growing demand for artificial intelligence services that can handle messy data. Texttract utilizes artificial intelligence to extract useful information from various records, making it a very useful tool in markets such as law, healthcare, and finance, where the ability to quickly analyze and evaluate a large amount of text is crucial.
In the broader context of AI development, the relationship between AIGC (AI - generated web content) and large language models is becoming increasingly close. Large language models (such as the models that drive text - generating AI) are the engines behind AIGC, capable of creating various contents from text to video scripts with minimal human processing. For anyone related to AI development, understanding the composition of large models is crucial, because these models are defined by their ability to process and generate human - like text.
Free AI APIs are equalizing the accessibility of these advanced devices, allowing developers, startups, and hobbyists to experiment with AI without a large capital investment. Platforms using free API interfaces are promoting development by lowering the entry barrier, resulting in a wider range of applications in the market. The accessibility of such APIs combined with detailed API integration management tools ensures that even complex systems can be easily established and published.
For example, weather APIs are gradually being integrated into applications in various fields from agriculture to event planning. These APIs provide real - time weather data that is crucial for the decision - making process, and durable API management platforms help to integrate them into existing systems.
Similarly, translation APIs are changing the way people and businesses interact across language barriers. These APIs utilize innovative AI models to provide real - time accurate translations, making it easier for global teams to cooperate and for businesses to enter larger target markets. Using foreign APIs (especially those providing free API services) further expands the coverage of such tools.
The concept of the API open platform is the core of this ecosystem, using a central interface where developers can access, process, and integrate various APIs into their applications. These systems usually include comprehensive documentation and tools, such as the Postman download portal, which simplifies the process of testing and deploying APIs.
Mijian Integration As artificial intelligence continues to develop, the use of artificial intelligence API interfaces is expected to expand, and more and more platforms will open their artificial intelligence functions. This open platform approach not only encourages innovation but also ensures that the advantages of artificial intelligence are more widely spread.
In conclusion, the rapid development of artificial intelligence technology (as evidenced by the expansion of intelligent chatbot APIs, text generators, reverse image search tools, etc.) is reshaping the way we interact with digital systems. From the integration of geocoding solutions to the automation of e - invoices, artificial intelligence is leading the way in promoting efficiency, precision, and innovation in multiple fields. As developers continue to utilize the power of open systems and free APIs, the possibilities for new transformative applications are virtually limitless.
Explinks is a leading API integration management platform in China, focusing on providing developers with comprehensive, efficient and easy-to-use API integration solutions.
0 notes
Text
25 Chat GPT Prompts for Full-Stack Developers
Today, full-stack developers have a lot to handle. They work with tools like Node.js, React, and MongoDB to build websites and apps. These tools help developers create powerful applications, but they also come with challenges. That’s where ChatGPT can come in to help. ChatGPT makes your job easier by solving problems, speeding up tasks, and even writing code for you.
In this post, we’ll show 25 ChatGPT prompts that full-stack developers can use to speed up their work. Each prompt helps you solve common development issues across backend, frontend, and database management tasks.
Backend Development with ChatGPT Prompts for Node.js
1. Debugging Node.js Apps
When your app runs slowly or isn’t working right, finding the problem can take a lot of time. ChatGPT can help you find and fix these issues quickly.
ChatGPT Prompt:
“Help me debug a performance issue in my Node.js app related to MongoDB queries.”
2. Generate Node.js Code Faster
Writing the same type of code over and over is boring. ChatGPT can generate this basic code for you, saving you time.
ChatGPT Prompt:
“Generate a REST API boilerplate with authentication using Node.js and Express.”
3. Speed Up MongoDB Queries
Sometimes, MongoDB searches (called “queries”) take too long. ChatGPT can suggest ways to make these searches faster.
ChatGPT Prompt:
“How can I optimize a MongoDB aggregation pipeline to reduce query execution time in large datasets?”
4. Build Secure APIs
APIs help different parts of your app talk to each other. Keeping them secure is important. ChatGPT can guide you to make sure your APIs are safe.
ChatGPT Prompt:
“Help me design a secure authentication flow with JWT for a multi-tenant SaaS app using Node.js.”
5. Handle Real-Time Data with WebSockets
When you need real-time updates (like chat messages or notifications), WebSockets are the way to go. ChatGPT can help you set them up easily.
ChatGPT Prompt:
“Help me set up real-time notifications in my Node.js app using WebSockets and React.”
Frontend Development with ChatGPT Prompts for React
6. Improve React Component Performance
Sometimes React components can be slow, causing your app to lag. ChatGPT can suggest ways to make them faster.
ChatGPT Prompt:
“Can you suggest improvements to enhance the performance of this React component?”
7. Use Code Splitting and Lazy Loading
These techniques help your app load faster by only loading the parts needed at that time. ChatGPT can help you apply these techniques correctly.
ChatGPT Prompt:
“How can I implement lazy loading and code splitting in my React app?”
8. Manage State in React Apps
State management helps you keep track of things like user data in your app. ChatGPT can guide you on the best ways to do this.
ChatGPT Prompt:
“Explain how to implement Redux with TypeScript in a large-scale React project for better state management.”
9. Set Up User Authentication
Logging users in and keeping their data safe is important. ChatGPT can help set up OAuth2 and other secure login systems.
ChatGPT Prompt:
“Help me set up Google OAuth2 authentication in my Node.js app using Passport.js.”
10. Use Server-Side Rendering for Better SEO
Server-side rendering (SSR) makes your app faster and improves SEO, which means it ranks higher in Google searches. ChatGPT can help you set up SSR with Next.js.
ChatGPT Prompt:
“How do I implement server-side rendering (SSR) in my React app using Next.js?”
Database Management with ChatGPT Prompts for MongoDB
11. Speed Up MongoDB Searches with Indexing
Indexing helps MongoDB find data faster. ChatGPT can help you set up the right indexes to improve performance.
ChatGPT Prompt:
“How can I optimize MongoDB indexes to improve query performance in a large collection with millions of records?”
12. Write MongoDB Aggregation Queries
ChatGPT can help write complex aggregation queries, which let you summarize data in useful ways (like creating reports).
ChatGPT Prompt:
“How can I use MongoDB’s aggregation framework to generate reports from a large dataset?”
13. Manage User Sessions with Redis
Handling lots of users at once can be tricky. ChatGPT can help you use Redis to manage user sessions and make sure everything runs smoothly.
ChatGPT Prompt:
“How can I implement session management using Redis in a Node.js app to handle multiple concurrent users?”
14. Handle Large File Uploads
When your app lets users upload large files, you need to store them in a way that’s fast and secure. ChatGPT can help you set this up.
ChatGPT Prompt:
“What’s the best way to handle large file uploads in a Node.js app and store file metadata in MongoDB?”
15. Automate MongoDB Schema Migrations
When you change how your database is organized (called schema migration), ChatGPT can help ensure it’s done without errors.
ChatGPT Prompt:
“How can I implement database migrations in a Node.js project using MongoDB?”
Boost Productivity with ChatGPT Prompts for CI/CD Pipelines
16. Set Up a CI/CD Pipeline
CI/CD pipelines help automate the process of testing and deploying code. ChatGPT can help you set up a smooth pipeline to save time.
ChatGPT Prompt:
“Guide me through setting up a CI/CD pipeline for my Node.js app using GitHub Actions and Docker.”
17. Secure Environment Variables
Environment variables hold important info like API keys. ChatGPT can help you manage these safely so no one else can see them.
ChatGPT Prompt:
“How can I securely manage environment variables in a Node.js app using dotenv?”
18. Automate Error Handling
When errors happen, it’s important to catch and fix them quickly. ChatGPT can help set up error handling to make sure nothing breaks without you knowing.
ChatGPT Prompt:
“What are the best practices for implementing centralized error handling in my Express.js app?”
19. Refactor Apps into Microservices
Breaking a large app into smaller, connected pieces (called microservices) can make it faster and easier to maintain. ChatGPT can help you do this.
ChatGPT Prompt:
“Show me how to refactor my monolithic Node.js app into microservices and ensure proper communication between services.”
20. Speed Up API Response Times
When APIs are slow, it can hurt your app’s performance. ChatGPT can help you find ways to make them faster.
ChatGPT Prompt:
“What are the strategies to reduce API response times in my Node.js app with MongoDB as the database?”
Common Web Development Questions Solved with ChatGPT Prompts
21. Real-Time Data with WebSockets
Handling real-time updates, like notifications, can be tricky. ChatGPT can help you set up WebSockets to make this easier.
ChatGPT Prompt:
“Help me set up real-time notifications in my Node.js app using WebSockets and React.”
22. Testing React Components
Testing makes sure your code works before you release it. ChatGPT can help you write unit tests for your React components.
ChatGPT Prompt:
“Show me how to write unit tests for my React components using Jest and React Testing Library.”
23. Paginate Large Datasets in MongoDB
Pagination splits large amounts of data into pages, making it easier to load and display. ChatGPT can help set this up efficiently.
ChatGPT Prompt:
“How can I implement efficient server-side pagination in a Node.js app that fetches data from MongoDB?”
24. Manage Roles and Permissions
If your app has different types of users, you need to control what each type can do. ChatGPT can help you set up roles and permissions using JWT.
ChatGPT Prompt:
“Guide me through setting up role-based access control (RBAC) in a Node.js app using JWT.”
25. Implement Caching with Redis
Caching stores data temporarily so it can be accessed quickly later. ChatGPT can help you set up caching to make your app faster.
ChatGPT Prompt:
“Guide me through implementing Redis caching in a Node.js app to reduce database load.”
Conclusion: Use ChatGPT Prompts for Smarter Web Development
ChatGPT makes it easier for developers to manage their work. Whether you’re building with Node.js, React, or MongoDB, ChatGPT can help with debugging, writing code, and improving performance.
Using ChatGPT prompts can help you work smarter, not harder!
1 note
·
View note
Text
How to Set Up Postman to Call Dynamics 365 Services

Overview
A wide range of setup postman to call d365 services to allow developers and administrators to work programmatically with their data and business logic. For calling these D365 services, Postman is an excellent tool for testing and developing APIs. Your development process can be streamlined by properly configuring Postman to call D365 services, whether you're integrating third-party apps or running regular tests. You may ensure seamless and effective API interactions by following this guide, which will help you through the process of configuring Postman to interface with D365 services.
How to Set Up Postman Step-by-Step to Call D365 Services
Set up and start Postman:
Install Postman by downloading it from the official website.
For your D365 API interactions, open Postman, create a new workspace, or use an existing one.
Obtain Specifics of Authentication:
It is necessary to use OAuth 2.0 authentication in order to access D365 services. If you haven't previously, start by registering an application in Azure Active Directory (Azure AD).
Go to "Azure Active Directory" > "App registrations" on the Azure portal to register a new application.
Make a note of the Application (Client) ID and the Directory (Tenant) ID. From the "Certificates & Secrets" area, establish a client secret. For authentication, these credentials are essential.
Set up Postman's authentication:
Make a new request in Postman and choose the "Authorization" tab.
After selecting "OAuth 2.0" as the type, press "Get New Access Token."
Complete the necessary fields:
Name of Token: Assign a moniker to your token.
Type of Grant: Choose "Client Credentials."
URL for Access Token: For your tenant ID, use this URL: https://login.microsoftonline.com/oauth2/v2.0/token Client ID: From Azure AD, enter the Application (Client) ID.
Client Secret: Type in the secret you made for the client.
Format: https://.crm.dynamics.com/.default is the recommended one.
To apply the token to your request, select "Request Token" and then "Use Token."
Construct API Requests:
GET Requests: Use the GET technique to retrieve data from D365 services. To query client records, for instance:
.crm.dynamics.com/api/data/v9.0/accounts is the URL.
POST Requests: POST is used to create new records. Provide the information in the request body in JSON format. Creating a new account, for instance:
.crm.dynamics.com/api/data/v9.0/accounts is the URL.
JSON body: json
Copy the following code: {"telephone1": "123-456-7890", "name": "New Account"}
PATCH Requests: Use PATCH together with the record's ID to update already-existing records:
.crm.dynamics.com/api/data/v9.0/accounts() is the URL.
JSON body: json
Code {"telephone1": "987-654-3210"} should be copied.
DELETE Requests: Utilize DELETE together with the record's ID: .crm.dynamics.com/api/data/v9.0/accounts()
Add the parameters and headers:
In the "Headers" tab, make sure to include:
Bearer is authorized.
Application/json is the content type for POST and PATCH requests.
For filtering, sorting, or pagination in GET requests, use query parameters as necessary. As an illustration, consider this URL: https://.crm.dynamics.com/api/data/v9.0/accounts?$filter=name eq 'Contoso'
Submit Requests and Evaluate Answers:
In order to send your API queries, click "Send."
Check if the response in Postman is what you expected by looking at it. The answer will comprise status codes, headers, and body content, often in JSON format.
Deal with Errors and Issues:
For further information, look at the error message and status code if you run into problems. Authentication failures, misconfigured endpoints, or badly formatted request data are typical problems.
For information on specific error codes and troubleshooting techniques, consult the D365 API documentation.
Summary
Getting Postman to make a call A useful method for testing and maintaining your D365 integrations and API interactions is to use Dynamics 365 services. Through the configuration of Postman with required authentication credentials and D365 API endpoints, you may effectively search, create, update, and remove records. This configuration allows for smooth integration with other systems and apps in addition to supporting thorough API testing. Developing, testing, and maintaining efficient integrations will become easier with the help of Postman for D365 services, which will improve data management and operational effectiveness in your Dynamics 365 environment.
0 notes
Text
From Monolithic to Microservices: The Full Stack Developer's Guide
In software development, the transition from monolithic to microservices architecture represents a major advancement. Because of their coupled components, monolithic programs can have trouble growing and changing to meet evolving business requirements. By dividing applications into smaller, independent services that can be built, deployed, and scaled separately, microservices offer a more adaptable and modular approach. Comprehending this shift is essential for Full Stack Developers to create contemporary, expandable applications. This article offers a thorough how-to for switching from monolithic to microservices architecture, outlining the advantages, difficulties, and recommended procedures for a smooth transfer.

Why Shift from Monolithic to Microservices?
Monolithic applications can be difficult to maintain and scale due to their tightly coupled architecture. As applications grow, these challenges multiply, leading to longer development cycles and increased operational costs. Microservices offer a modular approach, allowing individual services to be developed, deployed, and scaled independently. This results in faster release cycles, better fault isolation, and improved scalability. For Full Stack Developers, mastering microservices architecture means being able to build applications that can easily adapt to changing business requirements.
Key Considerations for a Successful Transition:
Transitioning from monolithic to microservices is not without challenges. Developers need to consider factors such as service granularity, data management, and inter-service communication. Defining the right level of granularity is crucial to avoid creating too many or too few services. Similarly, managing data consistency across multiple services requires a robust strategy, such as using event-driven architectures or implementing a Saga pattern. Understanding these key considerations will help developers navigate the complexities of microservices architecture.
Choosing the Right Tools and Frameworks:
Selecting the right tools and frameworks is critical for a smooth transition to microservices. Developers need to choose container orchestration tools like Kubernetes for deploying and managing microservices. Additionally, frameworks like Spring Boot for Java, Express.js for Node.js, and Flask for Python offer built-in support for microservices development. Familiarity with API gateways, such as NGINX or Kong, is also essential for managing communication between services.
Ensuring Security in a Microservices Architecture:
Security in a microservices architecture can be challenging due to the increased number of endpoints. Developers must implement strong authentication and authorization mechanisms, such as OAuth2 and JWT tokens, to secure communications between services. Additionally, monitoring and logging tools like Prometheus and Grafana can help detect and respond to security threats in real-time.
There are several advantages of switching from monolithic to microservices design, such as increased scalability, flexibility, and quicker release cycles. It does, however, also bring difficulties that call for meticulous preparation and implementation. Full Stack Developers may effectively manage this transformation by being aware of the principal factors, selecting the appropriate tools, and putting strong security measures in place. Developers may create more durable and adaptive modern apps by embracing microservices, which will help them stay competitive in the rapidly changing IT industry.
0 notes