#norton not working on windows 10
Explore tagged Tumblr posts
Text
2017 Haylor Timeline
Timeline Tag, or years 2011, 2012, 2013, 2014, 2015, 2016, 2017, 2018, 2019, 2020, 2021, 2022, 2023 and 2024.
3 January - Taylor "based in London" (end of Cornelia St period)
5 January - date of Harry’s leak “lately” recorded. Anniversary of clear blue water/rain on window posts which may be their last break up anniversary. He was pictured in London
8 January - Taylor and Zayn film I don't wanna live forever music video in London
13 January - Taylor was in LA papped at the the gym in LA. The scenario she told secret session fans she wrote DWOHT
21 January - Harry goes to LA
22 January Joe in Paris
28 January - Harry in LA
1 February - Harry's Rose Ring maybe at his birthday in Malibu 1 February 2017. Taylor posts a video of her and Gigi singing along to "I Don't wanna live forever" for the first time on the radio, which ‘happens’ to be on Harry's birthday.
youtube
4 February - Taylors only performance of 2017 in Houston. Super Saturday Night, rep coded.
14 February - Tom Hiddleston GQ article where he sounds traumatised, it is bad press for Taylor and later indirectly referred to in the Joe dating announcement.
7 - 19 February - Fans spot Taylor in London, once in a brown wig
24 February - Little Big Town perform, say Taylor is on London
March - Stalker arrested for breaking into Taylors NY apartment
5 March - Rose Ring seen clearly at Studio in London.
7 March - Ed Sheeran seen at Taylors NYC Apartment, he said they would collab again and March 2 said she was working on new music. (End Game)
8 March - Harry at Cottons Rhum Shack London
15 March - Harry arriving NYC with head down
23 March - E New story: "Where in the World is Taylor Swift?" that she had not posted candids since Thanksgiving.
Late March. Behind Album performances likely recorded at Abbey Road, they appear in the documentary in May and Harry was holding Ben’s daughter who looks about 3-4 months. Harry’s hair is also shorter than it was 5 March, a similar cut April 21.
4 April- Taylor recording Rep in Nashville 'to avoid paparazzi'‘. Joe in London. Harry shot Sign of the Times in Scotland. Mirror headline "Harry Styles goes all Peter Pan in his gloriously magical new video for Sign Of The Times"
7 April - Sign of the Times released
10, 16 April - Harry in NYC
18 April - Harry’s rolling stone interview where he leaves the table over her name and tips his hat and ex because it’s all for them. Harry possibly shades Matty Healy:
There’s nothing worse than an inauthentic tortured person. ‘They took my allowance away, so I did heroin.’ It’s like – that’s not how it works. I don’t even remember what the question was.”
21 April - Harry on Graham Norton, performs sign of the times and writes Spanish girl that later leaks backstage.
26 April - Harry in Paris for nrj


29 April - Harry is papped wearing the same St Laurent shirt Calvin copied for the Ole music video, on the date Taylor later identified in High Infidelity.
1 May - Taylor filmed LWYMMD Video, Harry London 2 & 7
6 May - harry driving in London using phone behind wheel wearing packers hat with Tess ward
7 May - Tess ward wore a shirt Harry wore in an interview
8 May - Harry in Williamsburg
9 May - Harry today show with the pink suit when he performs Stockholm. Xander and Jeff there. left NY
11 May Tess ward posts a photo of Harry’s kitchen with his cap in and is never seen again
12 May - Harry styles debut released, behind the album released just after. Cute Nick Grimshaw interview with 2 ghosts question
15 May - Harry behind the album released, includes parts of performances. Taylor paped in Nashville and flys to London in Charter (not her plane)
16 May - The Sun reports a source that Joe and Taylor dating 'for several months.' "after what happened with Tom Hiddleston", reminding me of the Tom GQ article from February. Having not been seen at all with Taylor previously Joe will now be seen 20 times for the rest of the year. The way this changed from completely unknown to very public (but saying it wasn't??) is .... sure they were totally together before this. Harry went on Carpool Karaoke wearing Haylor ring
18 May - TMZ pap photos of Taylor in Nashville
19 May - Harry at troubadour ONO. James, Jeff and Xander there carpool karaoke, Harry sang IKYWT in broadcast not you tube. Stevie Nicks comes, Harry emotional on stage in Landslide with Stevie Nicks. The music business people there were impressive, including the then head of the recording academy and Grammy voting member Savan Kotecha, who wrote WMYB, had fell out with 1D and some members but remained close with Harry.
youtube
20 May - Harry lists LA house, reported on the 22nd, sold in 2019.
1 June - Joe and Taylor papped together
5 June - Joe mention in blinds and seen having coffee. Harry rumoured in Hawaii with Jeff at wedding.
9 June - Taylor returns her music to Apple Music on the same day Katy Perry releases Witness.
11 June - Joe and Taylor and her plane
18 June - Joe and taylor spend fathers day in London with his dad
15 June - Harry follows Camille on IG, fans abuse her.
17 June - Harry attends Pixie Geldof's wedding in Mallorca, Louis rumoured to be there but no photos of Louis. Daisy Lowe is a bridesmaid.
20 June - HS stepdad passed away :( H Tess BUA
21 June - Mirror: "Taylor Swift "hosted Father's day for boyfriend Joe Alwyn and his parents - who served up a classic Sunday roast"" also referring to Joe as a 'new boyfriend'
24 June - Joe and Taylor at gym together
July - Harry NY in bar with Xander
4 July - Karlie Kloss posts a photo with Kendall in Paris, the internet realises KK is not in the squad. Taylors inflatable slide seen being inflated - but no 4th July party for Taylor. Blind item that Taylor skipped the party because Joe would not do a photo shoot.
13 July - Taylors last post before her socials wiped was to promote Selena's album. Reputation promo planning underway, Joe was announced a month before.
14 July - End Game written. Kendall came to Harry's show.
21 July - Harry and Camille seen together, Nick mentions her and she is in the background of a fan photo.
19 July - Dunkirk released
24 July - Joe and Taylor walking NYC
27 July - Joe and Taylor with umbrellas this time
29 July - Harry in NY
7 August - two ghosts release date
14 August - Taylors sexual assault trail v David Mueller, from his hand allegedly under her skirt in 2013 is settled and Taylor wins damages of $1.
27 August - LAWYMMD video, Karlie not on junior jewels shirt, Kendall tea time reenactment, Katy car crash and she eats a lobster in a cage.
28 August - Taylor deletes instagram
31 August HS releases two ghosts recording from Behind the album performances
3 September - Taylor at Abigail's wedding Martha's vineyard. Ready for it...? released after Saturday football preview.
7 September - Joe and Taylor NYC
9 September - Joe and Taylor in NY at Cornelia St
Sept 2017 – 14 July 2018 - Harry Styles Live on Tour
19 September - Harry points at himself on ‘I’m a fool for you’ in JALBOYH
25 September - Watermelon Sugar written


20 September - Harry LA, Greek Theater, wears same custom Gucci suit as Kiwi Music Video, with roses. Shania Twain comes and posts a photo of them together. Plays 'Still the One' on Kazoo in Grammy Museum interview. Taylor at Cara's London for month
27 September - Harry released Two Ghosts and Girl Crush as a Spotify Single recorded in Metropolis London, and photos of him recording it. Two days before he performed it in Nashville
28 September - Harry wears red in the Radio City music hall, NY plays Story of My Life in full and has an aborted heart kiss.
29 September - Taylor releases Spotify playlist of 70 songs. Anniversary of Harry’s “we don’t need no piece of paper tweet” and Harry’s another man mixtape. Song 7 is Boys, 20 is Liam Gallagher "for what's worth", followed by "miss you". 27 is We don't deserve love, Niall Horan is at 37 "Too much to ask", it also features Ariana Grande, Kesha, Kings of Leon, Bon Iver, 57 is Perfect by Ed Sheeran, the same name as the 1D song. It ends with #70 'She's casual' about a guy falling in love with a fling.
11 October - Taylor in London with Joe's family


14 October - Phoenix - Harry cries during Meet me in the Hallway (1:39). After “I walked the streets all day” before “running with the thieves”. This was Harry's last US show
16 October - Taylor films End Game music video in London
4 October - Rob Sheiffled on Swiftcast Podcast
Well, I mean, it's funny because that's a special case because her Harry Styles songs are really good and his songs about her are really good, and it's really kind of weird that, like, you know, the songs they write about each other are so consistently good, I can't think of any analogic pop history to it, where these two artists of that stature are going back to, like, who knows even, like, you know, how long they dated or anything like that, or, like, and of course all these songs are just, you know, allegedly about the other one, but when I was listening to the Harry Styles album for the first time and I heard him sing about, you know, like, you know, why can't we just be us in the refrigerator light? And I was like, oh my god, you went there. You went to the refrigerator light. I mean, really kind of, you know, mind- blowing. Even when I was listening to the last One Direction album, and that was another one where I was, you know, listening to it in the record company offices and had to keep a real straight face because you don't want to show any reaction. I get to Olivia and I'm like, seriously? Harry wrote a song named after her cat? Did they not think people would notice this kind of thing? But it's kind of a beautiful thing. It's that kind of inspiration that they bring out of each other.
October - Liam said he saw Harry at the Bowery Hotel “I bumped into him in The Bowery Hotel. He’s been through a rough time recently. God bless him, he was really happy to see me. The funniest thing was we didn’t really talk business. Dunkirk was out and all this was happening, and we just gave each other a big hug.”
20 October - Taylor reportedly likes a post "I’m here to drop some tea listen up and listen good!! Any love song Taylor writes now is about Joe and only Joe. She is so happy and this is about them. And only them. This is confirmed. It's a rule. Joe love songs from here on out, this goes for all of Reputation. No speculating if it is about Taylor’s ex from a million years ago because I promise you it’s not. Joe and Taylor. Happy. The tea has been served."
25 October - Harry performs in Paris, he cries on 'even my phone misses your call' twice in FTDT (1:53 and again 3:30). Taylor was in Nashville for Rep Secret Sessions.
2 November - Call it what you want - Taylor posts home movies that are in the CIWYW lyric video.

8 November - kiwi video released with Taylor looking kid
11 November - Taylor in NYC


10 November - Reputation released end game radio single on 14th
13 November - blind item that This Is What You Came For was about Harry
17 November - the HS behind the album performances released, first seen in BTA
28 November - Harry performs VS Show, Taylor cancels. New Years Day released as a single 27 November.
29 November - Derek Blasberg (fashion journalist reportedly the person KK had in TS apartment that ended friendship) posts a photo of KK sipping tea and asks for captions then comments "I knew brew were trouble when I met you"
4 December - Harry Haneda Airport
8 December - Joe and Taylor papped holding hands NYC
10 December - Taylor performs then watches Ed's show with Joe at Jingle Bell Ball London
12 December - Taylor and Joe in NYC
13 December - Reputation Stadium Tour tickets go on sale
31 December - Joe and Taylor NYE (Toe Twitter timeline)
Continue in 2018
38 notes
·
View notes
Text
I was in a writing mood today so I started this mess lol the opening from the 'da capo zentradi au' that needs a new name 😂 I didn't edit much so good luck LOL
Some background:
Two species of humanoid now inhabit the same planet. One from another dead planet and seeking refuge and a new place to live (the humans). This was met with hostility from the original habitants (the larger one). A war broke out for 10 years, for the humans to come on top in the end. The larger species are now used as a sort of work horse in most cases. Some manual labor, others protecting the area and hunting, etc. there are still Nobels and high ups in politics but the less well-off tend to be put to difficult work and conditions. Even though the humans have the tech to make it easier, just don’t want to waste resources. It’s a political way to keep them down, busy and obedient basically. 🙃
Norton, of course, works in the mines.
——
He awoke in a jolt as lights flashed on with what seemed like the blinding power of the sun. In an attempt to shield his eyes, he found that his wrists are bound behind him in the chair he is…tied to? Norton’s senses aren’t returning fast enough to get a decent grasp on what is happening here. Then a muffled sound hits his ears and his left one flicks in intrigue, trying to make out what it is…a voice? Maybe this voice has answers…
“…what’s going on? Where am I?”
A muffled response, he assumes that is what it is. The timing checked out for it to have been someone responding to him. He groans, irritated that his ears can’t make out what’s being said. Bobbing his head down and lightly shaking it, maybe this useless motion will bring back his senses.
The sound of fingers snapping brings him to attention, this being the first thing of clarity. Blinking his eyes, he is finally able to see a blurred individual come into clear view. Norton squints, “who are you…where am I? Why am I bound?”
“It’s me who should be asking questions Mr. Campbell…”
Norton arches a brow; he is only ever referred to this way when he’s in trouble. He looks around the clearing room, finding it blindingly white, every corner of it, with blaring lights above. There’s a window where he can only see himself but feels peering eyes watching him from the other side, then the sound waves from the wretched machine that dampens his enhanced hearing. Norton grits his teeth, the situation becoming more unideal the clearer the picture gets.
The only other individual in the room is seated across the table, studying Norton, patiently waiting for his ‘guest’ to get his bearings. “Judging by your jaw clenching, you’ve realized where you are…”
“Your kind had no right to do this. Take me….forcing me here…”
The individual shakes his head, “don’t be angry with me, I am the one trying to help you.”
Norton scoffs, “help me? Why would a human possibly help me?”
The man in white smiles, “well, I’m not fully human you see.” -he points at the slight point his ears come to-
“Is that supposed to comfort me? Finding out you’re half of two worlds? You’re associated with the people who took me, forced my body into this weak size, and hold me captive!” Norton yanks at his bindings in frustration. In this situation he should be doing all he can to keep his emotions in check, but the constant bombardment of: blinding light, deafening sound waves, and tight painful bindings on his body that was forced to biologically mutate in those stupid machines created to help his kind integrate with humans (make them human sized, the same process can return them to normal), if wished….All of this clashing together to make self-control difficult…purposely so….
The man in white remains silent as he carefully unfolds a loaf of freshly made bread and uncapping a jar of milk. This action alone bringing silence and potential obedience back into the room.
“Mr, Campbell…you can have this and your freedom if you answer some questions for me.”
Norton’s ears flick in curiosity, the scent of the fresh bread calming him, “about what?”
“Don’t tell me you’ve already forgotten? Maybe you hit your head harder than originally thought…” the words trail off as he adjusts his monocle.
Norton tilts his head, then looks down at the human clothes he is wearing, he grimaces, well now he can’t check to see the state his work clothes were in, could have been a clue, and tries to wrack his brain for any memory of what happened before this. He catches a glimpse of the man across from him and is confused by the expression. This expression of joy?
“This memory loss can work in our favor.”
“Our—?”
“Yes~ Here” he scoots the bread and milk over to Norton’s side and snaps his fingers. Two guards enter and undo the bindings and take their new posts on either side of the suspect.
Norton watches this situation play out with palpable confusion, then lightly flinches as a hand is suddenly extended towards him for a shake.
“Call me, Orpheus. Shake my hand if you agree with this simple term, ‘I help you, you help me’ how does that sound?”
“What would you helping me entail?”
“? That memory loss is doing a number on you~” Orpheus smiles, “I’m getting you out of here and back home”
“Wh—“
“Just shake my hand so we can get on with it”
This has something suspicious written all over it, but honestly, he would do anything to never be in this situation again and this guy seems like someone who could ensure that. “Fine.” and takes his hand in a firm shake.
———
5 years later
Norton is in his small living quarters. Exhaustion dripping from him as he sits in silence after a long day. It’s frustrating how the humans call him and his colleagues in for every little thing. You’d think the species would be more capable since they are the ones who won the war all those years back. He takes a towel and wipes the coal from his face as best he can without water, not having much energy to care about fully cleaning up at the moment.
A chime plays, signifying someone is outside. Dumbfounded, Norton gets up and walks over to press the button to open the sliding metal door, but…no one is there. Looking from side to side he suddenly hears a voice clearing itself from below. His eyes shoot downward and spot the man from 5 years ago.
“You..?”
“My, my, forgotten my name have we. We really should have gotten that head of yours checked more thoroughly.” Orpheus just walks under Norton’s legs and enters the living quarters.
“Sure…just come in then…” slightly annoyed, Norton closes the door and turns to face him.
“Do you at least remember the deal we made?” His voice nonchalant as he cleans his monocle.
“Yes, I recall, Orpheus…”
He smiles, pleased and looks all the way up at his friend returned to his proper height. “Fantastic, how do you feel about getting rid of someone for me?”
Norton’s brows furrow, “‘get rid of’?”
“Yes, I need you to kill someone.”
#this will turn into nortalice lol#norton campbell#orpheus#there will be a flash back of what happened before later#identity v#idv prospector#idv#idv norton#idv au#identity v au#da capo au#zentradi au#identity v orpheus#idv norton campbell#identity v norton#identity v novelist#idv novelist#identity v prospector#idv fanfic#👀
19 notes
·
View notes
Note
What's your biggest hyperfocus and how did you discover it?
I had to think on this for a minute because I wasn't sure if it was true anymore. If it wasn't this then it would be something like MLP or motorcycles (it was tempting to say motorcycles!).
I think it's fair to still say personal computers, though. I'm not sure about when my first contact with them was, but I know a major development was when my dad bought our first PC, an IBM AT clone. (I think I still have most of the parts for it!) I would have been like, 7-9 years old at the time and I was fascinated with it. I ended up breaking it as a kid, because I was trying to figure out what all the DOS 4.0 commands did by running them... when I got to FDISK I rendered it unbootable by pressing buttons. A friend of my father's recovered the situation (I think he used Norton Utilities to recreate the partition table).
I can name pretty much every PC that we had as a family or I had personally:
-Aforementioned IBM AT clone (8088 with a Tatung Hercules monitor, DOS 4.0) -386SX that came from who knows where (Went straight from orange Hercules to VGA colour!!! Windows 3.1) -Tandy 1000HX (long term loan from a friend) -Cyrix 586 (dogshit computer - had fake onboard cache, a common scam at the time, crashed constantly. Windows 95) -468DX4 (think I built this from scrounged parts. Win95, slower than the other PC but way more stable) -Pentium II 233 (also built from scrounged parts. First PC I overclocked, gaining 33 mHz! So fast!!! Windows 2000... but later got repurposed as a Linux-based router) -AMD Duron 800 (built with NEW parts - parents gave me a budget to built a family computer. Windows ... 98? XP? Probably changed multiple times) -AMD Athlon XP 1600 (built with NEW parts - I truly don't remember where I got the money in highschool to put it together, but it was probably every penny I had) -AMD Athlon 64 X2 4400+ (admittedly I didn't remember this offhand... but I did have the physical CPU lying around to check. bought off the shelf very cheap as old stock for my parents to use. Windows Vista. Later upgraded to an Phenom X4, also for very cheap. This PC still lives running Windows 10 today!) -Intel Core 2 Duo Q6700 (built in a cute Shuttle XPC chassis. Eventually burned out a RAM slot because apparently it wasn't rated for 2.0V DIMMs. Windows 7) -Intel Core i5-2500K (I used this computer for YEARS. Like almost a decade, while being overclocked to 4.4 gHz from nearly the first day I had it. Windows 7/10) -AMD 5800X (Currently daily driver. Windows 10)
Not mentioning laptops because the list is already long and you get the point.
I actually did attempt to have a computer related career - in the mid 2000s I went to a community college to get a programming diploma, but I dropped out halfway. There was a moment, in a class teaching the Windows GDI API, where I realized that I had no desire to do that professionally. I did learn things about SQL and OS/400 that randomly came in handy a few times in my life. I did go back and successfully get a diploma in networking/tech support but I've never worked a day in that field.
Unprofessionally though, I was "that guy" for most of my life - friend of a friend or family would have a problem with their PC, and I would show up and help them out. I never got to the point where I would attempt to like, re-cap somebody's motherboard, but I could identify blown caps (and there was a time when there was a lot of those). As the role of PCs has changed, and the hardware has gotten better, I barely ever get to do this kind of thing these days. My parent's PC gathers dust in the corner because they can do pretty much do everything they need on their tablets, which they greatly prefer.
Today though... I used to spend a lot of time reading about developments in PC hardware, architectural improvements, but it doesn't matter as much to me anymore. I couldn't tell you what the current generation of Intel desktop CPUs use for a socket without looking it up. A lot of my interest used to be gaming related, and to this day the GPU industry hasn't fully recovered from the crypto boom. Nearly all of the games I'm interested in play well on console so I just play them there. I still fiddle with what I have now and then.
It is fun to think back on various challenges/experiences with it I've had over the years (figuring out IRQ/DMA management when that was still manual, Matsushita CD-ROM interfaces, trying to exorcise the polymorphic Natas virus from my shit). Who knows, maybe I'll get to curate a PC museum of all this shit someday haha.
2 notes
·
View notes
Text
Tuesday 11 June 1839
7 ½
1 ¼
fine but thickish dampish morning – at my desk at 8 25/.. at Booths’ bills etc. till breakfast at 9 25/.. in about ½ hour – then with Robert Norton – planned oak room window shutters – had DB. till 11 ¾ and then at my desk till Mrs. Dyson came at 1 and staid till 2 5/.. and had luncheon – all sides very civil – glad to see her – and she seemed well satisfied with her visit – all the day from 11 50/.. (except while Mrs. Dyson here) till after 6 at colliery and other accounts – out with A- about 6 ½ or before – to Listerwick for a few minutes the water the same as before – not abated nor increased – the men were at work at 8am and got 48 loads of coal today – then about and in the Lodge road – the hay barn painted today – red – dinner at 7 ¼ - went into the cellar after dinner – 1 claret – asleep – coffee at near 10 – skimmed over the paper – had John Booth till 10 50/.. near ½ hour – finish day – Robert Norton began this morning preparing the stooths out of the new oak for the drawing room front – F59° inside and 54° outside at 11pm – then siding till 12 ½ A- ticketing 3 or 4 of my little keys –
2 notes
·
View notes
Text
It is common knowledge than an antivirus program is one of the best ways to keep a device or network security. What is not very well known is that the choice of antivirus has a profound effect on how secure a device will be. It is important to avoid free antivirus programs as they will often consume system resources without adequately protecting your device. They should never be a first or sole line of defense. If you do have an antivirus program installed, make sure to check that it is working correctly.How To Check an Antivirus Program - The EICAR Test FileThe quickest and most standardized way to check your antivirus is using the European Institute for Computer Antivirus Research (EICAR) testing file. The EICAR testing file is a string included in most antivirus programs for testing purposes. The string is meant to act like a virus so that the software will detect it. You can download the file or alternatively you can create one yourself quite easily. Save the following string into a notepad file and save it as EICAR.COM.X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*When you save the file, it should trigger an alert automatically on your antivirus program. Windows Defender picks up on it within 10 seconds and triggers an alert, and most antivirus kits will automatically quarantine the file. Other Security MethodsThere are other ways to ensure your antivirus is working correctly and to secure your machine. If you have a Windows device, make sure that updates are scheduled. While these updates can be irritating, never switch them off as they contain essential patches. It can also be a good idea to visit the HOSTS file and replace it with the default, as some malware can modify this file.It is also possible to compare the different types of antivirus software programs online. Many types of antivirus excel in one category and perform poorly in others so it can be a trade-off in many instances. However, there are certainly better and more recognized types of antivirus protection programs. Avast antivirus utilizes little system resources and is very low maintenance, however, it is better at prevention than removal for certain viruses. Norton Antivirus is another well-known antivirus, though it uses more system resources. It can depend on what you are doing, some can affect certain operations such as downloading, while others can affect other operations such as uploading and running executables.A popular combination is to use an antivirus program such as Avast and complement it with MalwareBytes, which is useful for detecting malware. A malware protection tool along with an antivirus program is frequently recommended by security specialists. Windows Defender is another good tool available on Windows 10, but it needs to be complemented with a malware detection tool for complete protection. It should be noted that prevention is always the best defense, and basic online security habits should be adhered to at all times.
0 notes
Text
Security for Remote Work: Safeguarding Your Digital Workspace

Remote work has become a standard in many industries, offering flexibility and convenience. However, it also brings unique cybersecurity challenges, as employees often work outside of secured office environments. Protecting sensitive information and maintaining robust security measures is essential for both organizations and individuals.
This guide outlines best practices for ensuring security in remote work settings.
Why Security for Remote Work Is Important
1. Protects Company Data
Prevents unauthorized access to sensitive files, emails, and databases.
2. Mitigates Cyber Threats
Defends against phishing, malware, and ransomware attacks targeting remote workers.
3. Ensures Compliance
Maintains adherence to data protection regulations like GDPR, HIPAA, or PCI DSS.
4. Builds Trust
Reassures clients and stakeholders that their data is handled securely.
Common Security Risks in Remote Work
1. Unsecured Wi-Fi Networks
Public Wi-Fi can expose sensitive data to interception by hackers.
2. Weak Passwords
Easily guessable passwords increase the risk of unauthorized account access.
3. Phishing Attacks
Remote workers may be more vulnerable to phishing scams due to the reliance on email communication.
4. Unencrypted File Sharing
Sending files without encryption can lead to data breaches.
5. Use of Personal Devices
Devices lacking proper security measures can introduce vulnerabilities.
Best Practices for Secure Remote Work
1. Use Strong and Unique Passwords
Secure all accounts with strong, unique passwords to prevent unauthorized access.
Tips for Passwords:
Use at least 12 characters with a mix of letters, numbers, and symbols.
Avoid reusing passwords across different accounts.
Use a password manager like LastPass, Dashlane, or Bitwarden for secure storage.
2. Enable Two-Factor Authentication (2FA)
Add an extra layer of protection to online accounts.
How 2FA Works:
Requires a password and a secondary verification method, such as a code sent via SMS or generated by an authenticator app.
3. Secure Wi-Fi Networks
Ensure home or public Wi-Fi networks are protected.
How to Secure Wi-Fi:
Use WPA3 encryption for your home network.
Change default router credentials to strong, unique passwords.
Avoid accessing sensitive data on public Wi-Fi without using a VPN.
4. Use a Virtual Private Network (VPN)
Encrypt your internet connection to protect sensitive data from interception.
Recommended VPNs:
NordVPN
ExpressVPN
ProtonVPN
Tip: Ensure your VPN is enabled whenever working remotely.
5. Keep Software Updated
Regular updates patch security vulnerabilities in operating systems, apps, and devices.
What to Update:
Operating systems (Windows, macOS, iOS, Android).
Applications like browsers, collaboration tools, and antivirus software.
Tip: Enable automatic updates whenever possible.
6. Install Antivirus Software
Protect devices from malware, ransomware, and other cyber threats.
Recommended Antivirus Tools:
Norton 360
Malwarebytes
Bitdefender
Tip: Schedule regular scans and enable real-time protection.
7. Use Encrypted Communication Tools
Ensure secure communication with team members and clients.
Recommended Tools:
Messaging: Signal, WhatsApp (end-to-end encryption enabled).
Video Calls: Zoom (with encryption enabled), Microsoft Teams.
Email: ProtonMail, Tutanota.
8. Avoid Phishing Scams
Be vigilant against fraudulent emails and messages.
How to Spot Phishing Attempts:
Generic greetings like "Dear Employee."
Urgent requests to click links or share information.
Suspicious URLs or attachments.
Tip: Verify requests by contacting the sender directly through official channels.
9. Restrict Access to Sensitive Information
Limit data access to only those who need it.
Key Practices:
Use role-based access controls (RBAC).
Revoke access for former employees or unused accounts.
Encrypt sensitive files before sharing.
10. Use Company-Approved Devices
Work on devices configured with security policies, such as antivirus and encryption.
Tips for Secure Device Use:
Avoid using personal devices for work tasks unless authorized.
Report lost or stolen devices immediately to IT administrators.
For Organizations: Establishing a Secure Remote Work Policy
1. Develop a Cybersecurity Policy
Outline rules for secure remote work, including password requirements, approved software, and reporting protocols.
2. Train Employees on Cybersecurity
Provide regular training sessions to educate employees about identifying threats and maintaining security.
3. Implement Endpoint Security Tools
Use software to monitor and protect devices connected to the company network.
Recommended Tools:
CrowdStrike Falcon
Sophos Endpoint Protection
4. Monitor Network Activity
Use tools like firewalls and intrusion detection systems (IDS) to identify suspicious behavior.
5. Backup Critical Data
Regularly back up files to secure, offsite locations to prevent data loss.
Backup Solutions:
Cloud storage (e.g., Google Drive, OneDrive).
Physical storage (e.g., encrypted external hard drives).
Conclusion
Security for remote work requires a combination of tools, policies, and proactive habits. By using strong passwords, enabling 2FA, encrypting communications, and following best practices, both employees and organizations can minimize risks and maintain a secure digital workspace.
Take the necessary steps today to ensure your remote work environment is safe, productive, and resilient against cyber threats.
FAQs
1. Is a VPN necessary for remote work? Yes, a VPN encrypts your internet connection, protecting sensitive data from interception.
2. How can I secure my personal device for work? Install antivirus software, keep software updated, and avoid sharing the device with others.
3. What should I do if I suspect a phishing attempt? Do not click on links or download attachments. Report the email to your IT department immediately.
4. Are public Wi-Fi networks safe for remote work? Public Wi-Fi is risky; always use a VPN if you must connect to such networks.
5. How often should I update my passwords? Change passwords every 3–6 months or immediately if you suspect a breach.
0 notes
Text
It is common knowledge than an antivirus program is one of the best ways to keep a device or network security. What is not very well known is that the choice of antivirus has a profound effect on how secure a device will be. It is important to avoid free antivirus programs as they will often consume system resources without adequately protecting your device. They should never be a first or sole line of defense. If you do have an antivirus program installed, make sure to check that it is working correctly.How To Check an Antivirus Program - The EICAR Test FileThe quickest and most standardized way to check your antivirus is using the European Institute for Computer Antivirus Research (EICAR) testing file. The EICAR testing file is a string included in most antivirus programs for testing purposes. The string is meant to act like a virus so that the software will detect it. You can download the file or alternatively you can create one yourself quite easily. Save the following string into a notepad file and save it as EICAR.COM.X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*When you save the file, it should trigger an alert automatically on your antivirus program. Windows Defender picks up on it within 10 seconds and triggers an alert, and most antivirus kits will automatically quarantine the file. Other Security MethodsThere are other ways to ensure your antivirus is working correctly and to secure your machine. If you have a Windows device, make sure that updates are scheduled. While these updates can be irritating, never switch them off as they contain essential patches. It can also be a good idea to visit the HOSTS file and replace it with the default, as some malware can modify this file.It is also possible to compare the different types of antivirus software programs online. Many types of antivirus excel in one category and perform poorly in others so it can be a trade-off in many instances. However, there are certainly better and more recognized types of antivirus protection programs. Avast antivirus utilizes little system resources and is very low maintenance, however, it is better at prevention than removal for certain viruses. Norton Antivirus is another well-known antivirus, though it uses more system resources. It can depend on what you are doing, some can affect certain operations such as downloading, while others can affect other operations such as uploading and running executables.A popular combination is to use an antivirus program such as Avast and complement it with MalwareBytes, which is useful for detecting malware. A malware protection tool along with an antivirus program is frequently recommended by security specialists. Windows Defender is another good tool available on Windows 10, but it needs to be complemented with a malware detection tool for complete protection. It should be noted that prevention is always the best defense, and basic online security habits should be adhered to at all times.
0 notes
Text
does norton prevent cisco anyconnect vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does norton prevent cisco anyconnect vpn
Norton VPN compatibility
Norton VPN is a popular choice for users seeking to enhance their online privacy and security. One important aspect to consider when choosing a VPN service is its compatibility with various devices and operating systems. Fortunately, Norton VPN offers broad compatibility to cater to a diverse range of users.
For Windows users, Norton VPN is fully compatible with Windows 7, 8, and 10, ensuring that you can secure your internet connection regardless of the version you are using. Mac users can also benefit from Norton VPN, as it supports macOS X 10.10 and above, providing a seamless experience across Apple devices.
Furthermore, Norton VPN extends its compatibility to mobile users, with dedicated apps for both iOS and Android devices. Whether you are using an iPhone, iPad, or an Android smartphone or tablet, you can protect your data on the go with Norton VPN.
In addition to traditional computers and mobile devices, Norton VPN is compatible with routers, offering an added layer of security for your entire network. By installing Norton VPN on your router, you can protect all connected devices, including smart TVs, gaming consoles, and IoT devices.
In conclusion, Norton VPN's wide compatibility ensures that users can enjoy enhanced privacy and security across a variety of devices and platforms. Whether you are working on your computer, browsing on your phone, or streaming on your smart TV, Norton VPN has you covered.
Cisco AnyConnect VPN functionality
Cisco AnyConnect VPN is a versatile and robust software application that provides secure remote access to enterprise networks. With its advanced features and capabilities, Cisco AnyConnect offers a seamless and encrypted connection for users to access corporate resources from anywhere in the world.
One of the key functionalities of Cisco AnyConnect VPN is its compatibility with multiple operating systems, including Windows, macOS, Linux, iOS, and Android. This ensures that users can connect to the VPN network using their preferred devices, whether it's a desktop, laptop, tablet, or smartphone.
Another important aspect of Cisco AnyConnect VPN is its ability to establish a secure tunnel between the user's device and the corporate network, encrypting all data transmitted over the connection. This encryption helps protect sensitive information from potential threats and ensures data privacy and integrity.
Furthermore, Cisco AnyConnect offers additional security features such as multi-factor authentication, endpoint compliance checking, and automatic software updates. These features help enhance the overall security posture of the VPN connection and reduce the risk of unauthorized access to the network.
The flexibility and scalability of Cisco AnyConnect VPN make it an ideal solution for organizations of all sizes, from small businesses to large enterprises. Whether employees are working remotely, traveling, or accessing corporate resources from public Wi-Fi networks, Cisco AnyConnect provides a secure and reliable connection to the company network.
In conclusion, Cisco AnyConnect VPN is a powerful tool that enables secure remote access to enterprise networks, offering a wide range of features to enhance security and user experience. It's a reliable solution for organizations looking to provide secure access to their resources while maintaining data privacy and integrity.
Norton security impact on VPN connections
When it comes to online security and privacy, incorporating Norton security software alongside a VPN connection can provide a powerful shield against potential threats. Norton security solutions are designed to safeguard your devices from malicious software, phishing attempts, and other cyber threats, while a VPN encrypts your internet connection to ensure anonymity and data protection.
By combining Norton security with a VPN, users can enjoy a multi-layered defense system that works to block malware, prevent unauthorized access to sensitive information, and protect online identities. Norton's advanced security features complement the encryption protocols of a VPN, creating a robust defense mechanism against cyber attacks and privacy breaches.
One notable impact of using Norton security with a VPN is the enhanced protection it offers when accessing public Wi-Fi networks. Public Wi-Fi hotspots are notoriously insecure, making users vulnerable to hacking, data interception, and other cyber risks. With Norton security and a VPN active, users can safely connect to public Wi-Fi networks without compromising their personal information or risking exposure to online threats.
In conclusion, the combination of Norton security with a VPN can significantly enhance online security and privacy. By leveraging the strengths of both security measures, users can fortify their defenses against cyber threats, protect their sensitive data, and browse the internet with confidence knowing that their online activities are shielded from potential risks.
VPN software interoperability analysis
Title: Analyzing VPN Software Interoperability: Ensuring Seamless Connectivity
In today's interconnected digital landscape, Virtual Private Network (VPN) software plays a pivotal role in safeguarding online privacy and enabling secure access to various networks. However, the effectiveness of VPNs often hinges on their interoperability with different devices, operating systems, and network configurations. A thorough analysis of VPN software interoperability is crucial to ensure seamless connectivity and optimal performance.
Interoperability refers to the ability of VPN software to function cohesively with diverse systems and platforms without encountering compatibility issues. This includes compatibility with popular operating systems such as Windows, macOS, Linux, iOS, and Android, as well as compatibility with routers, firewalls, and other network infrastructure components.
One key aspect of VPN software interoperability analysis involves assessing its compatibility with various encryption protocols and tunneling techniques. VPNs utilize different protocols like OpenVPN, L2TP/IPsec, and IKEv2/IPsec to establish secure connections. Evaluating how well a VPN software integrates with these protocols ensures robust encryption and data protection across different environments.
Furthermore, compatibility with third-party applications and services is essential for seamless integration into existing workflows and ecosystems. VPN software should seamlessly work with web browsers, email clients, cloud services, and other applications commonly used by individuals and organizations.
Another critical consideration is the scalability of VPN solutions, especially for businesses and enterprises. Analyzing how well VPN software adapts to growing network infrastructure and increasing user demands helps in making informed decisions about long-term viability and scalability.
In conclusion, thorough analysis of VPN software interoperability is indispensable for ensuring reliable and consistent performance across diverse environments. By evaluating compatibility with various devices, operating systems, protocols, and third-party applications, users can select VPN solutions that best meet their connectivity needs while upholding security and privacy standards.
Norton antivirus and VPN integration
Title: Enhancing Security: The Benefits of Norton Antivirus and VPN Integration
In today's digital landscape, safeguarding personal and sensitive information is paramount. With cyber threats evolving constantly, individuals and businesses alike seek comprehensive solutions to protect their data. Norton, a renowned name in cybersecurity, offers a powerful combination of antivirus and VPN services, providing users with robust protection and enhanced privacy.
Integration of Norton antivirus and VPN offers a holistic approach to security. Norton antivirus software is designed to detect and remove various types of malware, viruses, ransomware, and other online threats, ensuring that devices remain free from harmful infections. By continuously monitoring for suspicious activities, it acts as a vigilant guardian against cyber attacks.
On the other hand, Norton VPN (Virtual Private Network) adds an extra layer of defense by encrypting internet traffic and routing it through secure servers. This encryption prevents unauthorized access to data, shielding sensitive information from prying eyes, especially when connected to public Wi-Fi networks. With Norton VPN, users can browse the web anonymously and access geo-blocked content without compromising their privacy or security.
The integration of Norton antivirus and VPN amplifies the protection offered by each service individually. By combining antivirus capabilities with VPN encryption, users benefit from comprehensive security measures that address both online threats and privacy concerns. Whether browsing the web, conducting online transactions, or accessing sensitive information, users can have peace of mind knowing their data is safeguarded by two robust layers of defense.
Furthermore, Norton's intuitive interface makes it easy for users to manage both antivirus and VPN functions seamlessly. With features like automatic updates and real-time threat detection, users can stay ahead of emerging threats without compromising performance or usability.
In conclusion, the integration of Norton antivirus and VPN provides a comprehensive solution for safeguarding digital assets and ensuring online privacy. By leveraging the strengths of both services, users can enjoy a safer and more secure online experience, free from the worries of cyber threats and privacy breaches.
0 notes
Text
someones overcompensating for something...
Updated 2:50 AM 3/7/2024 with starred section, noted as point #2, in connection with point #1 that was present at time of original posting.
Since I was 18, and now at 36, I ran into two retards of employers.
One was way back, when I was seeking a part time job at my 2nd University. It was as a Technical Assistant. Part of the job entitled me to my own, and rather large at that, cubicle. The guy I was helping would tell me things that hint at parts of his psyche. He would start off with random comments like "one day you'll be my boss"-sounds innocent enough. But it is the root of something leading to bitterness. Before working for him, I had a real Computer Consultant job for 2 years. In that, from experience, I learned when uninstalling an antivirus, it helps to use the vendor's uninstall tool, like Ex. the Norton Removal Tool. The reason you use that vs. the Control Panel on a Windows Machine, is to avoid the risk of network connectivity problems as it screws with aspects of software like "Drivers." When I would do these things or explain why it might be better? This guy didn't like it. He saw me as someone to put his mail in a mailbox, literally. I somehow offended his ego, by making a suggestion. On another occasion, I'm following him upstairs, and I ask him, a question on how to go about something. He snaps at me saying, "what does that matter." On another occasion, I told him the phone in my cubicle wasn't working. He responds "why do you need a phone?!" Well, to talk to clients, in a tech center basement, where no one had cell signal. I'm sure that can be easily verified in the present day by visiting the location. When he gave me assignments or dumped me on someone else in his absence, my memories can verify I spent 6 hours in a part time job, setting up 10 new desktop machines for use by employees. I'd spend after-hours, of my own volition, updating machines, fixing machines, fixing printers, when I had my educational program to worry about, or classes. There were instances, where he gave me spreadsheets to skim through and correct and verify. With my "Vyvanse" ADD amphetamine level focus at the time, I zoomed through it. He then yells at me and accuses me of lying about doing the job. Against my volition, maybe because the mind control was happening, I burst into tears. I was, already under the impression, that life was rough to me. And this guy and his nasty attitude? I just couldn't help but wonder, how is this all happening to me. Now, I have some idea. There's a situation hacking my tech and my mind, and elements of my environment.
So let's add all this up: 1.the guy I was an assistant to? He's a low end employee who worries I'll be his boss one day. 2.He doesn't like my suggestions. 3. He doesn't like, how I, a student, have a cubicle, that he has, as a regular employee. 4. He doesn't like being asked questions, by what he sees as his bearded student assistant. Wasn't 17 at time. Was 21. Joined school as an adult, not a teenager. 5. I'm to drop off his mail. 6. He doesn't think I'm worthy of a working phone that's already in the cubicle. What does this sound like to you, the reader? Doesn't it seem like he's bitter that I, a student, have the same amenities or knowledge, that he as an adult, only recently gained?
Apparently if I'm not slow with a computing task like him, and did it fast, it means I lied about doing the work.
Did he check the work? Rather, the retard just lashes out at me. Eventually, I walked out on the job. And when I did, I kept bumping into him on campus. He would give me menacing looks. I complained to our old boss that he was doing this, as well as telling people we worked with, that I'm terrible. I told our female boss: he was scaring me like someone who was mentally ill or a shizophrenic. From that moment onwards, he behaved when seeing me.
*** Check my memories. Verify with your wireless fMRI emotion checker if I'm expressing anxiety over possibly lying. *** And what does the staff at that retard state university do? They paint me as a shizo and subject me to the treatments of a shizo, while doing mind reading. This guy I worked for, must be having the time of his life at my expense. Warped injustice. With that job, like all my jobs, I spend, late into the day, trying to get things done early. When I was at Bank of America, I went to the city location on Saturday's to learn the software and programming language. The expert of the time told me: automating graphs via emails wasn't possible. Yet I managed to do it, with an outdated module of the Python Programming Language called OpenPyxl, and my efforts were ignored. For reference, it was the "Complex KE Analysis Report. "
At Bank of America, I bought everyone brownies, there was a guy who'd eat my lunches, and there was a woman who I'd ride the train with, who had me help her with her shopping before work (carrying bags as though husband) and borrowing unreturned money.
The abuse I take. I tippy toe around everyone while the youth voices of the mind reading situation claim "they're in some unknown way, helping me."
*** What really ends up happening? Everyone just walks all over me, or takes advantage of my politeness.
*** On one occasion, kind of like talking to my mother at times, I was trying to verify the requirements of a tech request, made of me, by the woman I rode the train with everyday. She started getting frustrated her explanation of the request. She goes, "I dont understand why you're like this, why are you not getting what I'm saying?" By the book, I suggested to her, "hey, it's kind of getting heated, maybe we should ask "JOE", over there, to help us clarify things." And this is a woman I rode the train with, someone who drove me to my house, once, after a company movie. She took my suggestion offensively, like I was trying to embarrass her, or get her in trouble with our peers. WTF? I mean...The random reactions of people. In our friendship, I shopped with her, carried her bags, lent her $1 here and there, and she somehow thinks I'm trying to embarrass her by not understanding her description and suggesting someone else clarifies.
My efforts, my work, never have value.
The cherry on top, the icing on the cake is my fifth year working at PepsiCo.
When I worked at PepsiCo, I worked 4 years as a Data Analyst. They went by, without a problem. I got average, but never negative performance reviews. I'm a programmer, not a Data Analyst. I hate analyzing data, though I can be analytical. That being said, This is the second incident I was talking about, I mentioned at the top of this post. By the time of my fifth year there, I transitioned to a Senior role. From Data Analyst, I promoted to Senior Data Steward What do they say about jobs? Take initiative. The new division I worked in, was a new division called Data Governance. I was the Senior Data Steward. My manager was also new. He came from GE (General Electric) managing fridges or something. He comes to PepsiCo, and becomes the manager of Data Governance, despite having no technical aptitude. If that a*s hole is reading this now, look at the SKU mapping project that I sent in my email, which I based, for correcting inappropriate content on social media, in another tweet/and Tumblr blog post. This flowery talking philosophical manager thought he was sooo savvy with Microsoft Excel and that's all it took to analyze Data. He's not the worker, but the manager. He uses up everyone's team in the meeting, selfishly asking his own questions, while stopping others doing the tasks, from gaining an understanding. When asked about this, he claims "he was guiding the conversation." WOW. THE ARROGANCE. Why no one speaks up about these things at work? They're worried, with grocery prices up, inflation, shrink inflation, that they'll lose their jobs for speaking up. I'm not destitute and I'm not stupid, so forgive me for trying to tell HR about this. When anyone else leaves early from no work, he doesn't care. He deliberately excludes me from meetings and avoids giving work to me, while I have rats in my brains seizing idle moments to pester me with chatter. If I sit there blankly staring at my laptop, I lose my mind. I eventually walk out, and this genius thinks I don't notice him sending the adjacent unrelated manager walk by me, to patrol me. I mean wow, like being demeaning to a child. Then for taking initiative one day, and asking this other manager, if there's anything I could do to assist his team for work, my retard manager gets on my case for embarrassing him, because usually that guy's team members come to him for work. The ridiculous twists and turns.
With this retard manager, especially in the beginning, we were always behind deadlines and then he proposes, 2 of many strange instances.
1. The team doesn't know what a promotional pricing table means. Retard manager decides to have everyone spend 5 hours guessing what the price means, instead of reaching out to someone and asking a question. Memory serves as truth wise guy, if you're acting like I'm lying. I'm constantly subjected to an fMRI verifying lies through emotion. And we ended up still being behind on the project and obviously wrong about the data from stupid guessing. This delays other potential tasks and workers end up having to work after hours or before.
I mean seriously, let's just waste everyone's time.
*****************************************************************
Updated 2:50 AM 3/7/2024
2. Then there was an occasion where the retard of a manager asked me to create a training document on how to create templates for a particular Microsoft Excel spreadsheet. He tells me to have it done by Friday 9 AM. Part of it took understanding and fixing my predecessor's broken, unCompilable Code. As it was written in the Python Programming Language using Juniper Notebooks, I needed the paid version of PyCharm, an IDE program for writing/compiling computer code. Out of my own pocket I paid for the program without compensation, as PepsiCo doesn't compensate employees for attending meetings before 8 or 9 AM (when work officially starts, or when they stay after, because your d*k of a manager wasted 5 hours guessing on something to evade: "oh heavens me, let me/thou not" trouble them with my question. SIDENOTE: And on a sidetone, who does the retard Somers?! manager favor. The epitome of kiss a*ses. This guy doesn't shut up over intentionally rambling, to give a conversation flow to the manager. The idiot manager looks to be entertained by superfluous wording, to make him feel smart. This other Connecticut retard, who I lied to about making significantly higher salary, when he was doing the same job, asks me to kiss up to the manager, "Renny, I'm appalled you would think there's nothing assigned to us." Appalled? Really. Speak to someone else making $20,000 more than you. Then there's this contractor. Never says actually anything. Speaks in expressions or colloquialisms. He decides to take on initiative of teaching me programming? This guy? An underpaid contractor? I appreciate the sentiment, but what is telling these guys that I'm computer illiterate. Do you have any idea how many times I went through college, classes within college, and bootcamps domestically and internationally?! Even the good employee, my predecessor, who transferred to Accenture, that the manager bad mouths for leaving for his career, when I comment on his code, he says "Good job Renny. Wow. Good for you!" We're about the same age and he talks to me like I'm 5 and didn't go to school. It's like PepsiCo is a land of people open to every suggestion, except what's before them. Excluding the Accenture guy (probably honest mistake), with the others, it's like being among deaf/dumb/blind people who feel I need crutches and need help walking. WTF?! Over time, it gets repetitive and annoying, but still you put up with it. But! when you put up with it, retards like the manager keep doing what they do, and literally draw pictures for you, every week, like you're missing half your brain. Scan my brain/scan my memories for verification. It's Sesame Street for this guy. Hey guys! What's the letter of the day?! Can I draw it on a white board?! END SIDENOTE
But back to point #2.
So I fix my predecessors broken code with a try/catch exception error handling clause in the program, within IDE: PyCharm. I go through videos of how things were done-3 hr long videos, repetitively 2 not miss a detail. I make screenshots of videos and other materials for that documentation. I'm up until 3 AM fixing this up. Go to bed late, wake up by 9 AM for work, and what do I find? The manager, for some bizarre reason, decided to take "colloquialism guy" and a woman in Texas (an hour behind EST), to also stay up till late in the night, working on a separate documentation. This is one of many wild goose chases the retard manager sends me on. He could have had those people help me put "MY documentation" together. But instead, without telling me, he decides, for his creditHungryHunger, to work on something separately with teammates without me, making my documentation pointless. You must be seeing me on my main floor-common area-tv room-desk working till 3 AM. And the annoying thing? I saw retard/mr colloquialisms/and the Texas star on Zoom, with active status, at 11 PM. If they were going to do it themselves, why'd they have me work on a separate documentation? Isn't that the definition of a wild goose chase? When I ask the manager about this and tell HR? He says he didn't get a sense I would finish on time, so without telling me to stop my efforts, he decides to work with 2 teammates to have them do it. WTF? Or did the mind stalkers tell the manager, behind my back that I'm preoccupied and need more time to finish the task? There's help and there's help...showcase my memories...please...I hate that guy, because when I asked him about it, he screwed with my head, and said none of it happened. Workplace psychological harassment much?! All this is in emails PepsiCo tried to delete, whether it was to the manager or HR. Then without giving me work, they say I didn't do any work. Really for a year, no work? What does that say about the manager who we know is retarded? He didn't care to notice? He was so busy managing a team of 10 for a year? Before I left that horrid food/beverage place that is Purchase PepsiCo, I sent them all the files they assigned to me to work on. I wonder how the retards and the crying woman are going to explain that, at the END of MY SITUATION. I guess they're seeing it as getting a few good years at my expense.
Updated 2:50 AM 3/7/2024
**************************************************************
I use formulas in Excel the retard manager could never wrap his feeble/ arrogant mind around. Look at my skuMapping file, d*p sh*t. Did you give guidance on how to go about it? You toss 3 files at 3 people with over a thousand lines, and then tell them to find similarities that points to a SKU number. Can you be more vague?! This guy without experience, is telling ME, with 4 years of Data Analysis experience, not to automate Data Manipulation. And How hard it was to automate it, without having a clear set of instructions to go about automating. Data Analysis is all about automation, genius. In the beginning, I worked with him on a project late into Friday evening, creating a database that automated a report by combining SQL, math formulas, Microsoft Access and Microsoft Excel. He slips in and out of an all day Zoom meeting, and gets a beer in the background, or listens to Nascar racing news on the radio, and pops back in on Zoom, to see where I am with the automation. This guy knows nothing/does nothing. It got to a point where he told people on our team: no automation. Scan through 1000+ rows with your eyes in Microsoft Excel. I'm a programmer. When I suggest ideas to the white programmer of his choice, he tells me to stop giving him ideas, and me alone,. At the time, he was so clueless and fresh with data analysis, he had these one to ones with me, where he's trying to explain certain ideas to me, like the philosophy behind the term Data Discovery, when I'm dealing with Data Structures and Algorithms. And then the retard goes on to drawing boxes on a white board. He thinks he can explain programming to me by drawing boxes with arrows in between. Deep inside, I"m thinking this guy is retarded. Then, when he gets anxious, he starts mentioning random things like "I have a daughter and she's reading on PepsiCo campus grounds." I'm sorry, why do I care?! I'm guessing it has something to do with the mind reading situation intervening, and saying I wish I had my own daughter. More and more employees get hired onto the team. When I enter work, he holds meetings and never invites me. How can you make that plausible to another listening ear? He then keeps dumping me on different people for "beneath me" projects. Everyone else is attending meetings all day, using data manipulating tools, and he has me paired with a manager in Britain, who's planning on leaving in 3-4 months. He wants me to learn how to write definitions. Now this retard is trying to get rid of me, by dumping me on someone else, so that I, me, can learn to write. Months go by, where I'm checking boxes on a reporting tool called Alation. That's what he does. Every so often, he gives me busy work. I went from database programming to learning tutorials on how to use Alation. I asked him if it was wise, because it was going to be replaced with the Informatics suite of tools in 2 weeks. He says: still do it. After I learned the obsolete tool of Alation, he has me attend tutorials for Informatics. At this was 2023, and now it's 2024, this retard of a manager has gotten his feet wet with Data Analysis. But back then, clueless. He thinks his limited skillset with Microsoft Excel makes him comparable to someone with a tech degree.
He attended Pace University for Finance or something or Accounting, gets some work experience from GE, and becomes a manager for technology at PepsiCo. If this retard can make it this far, I have to assume that some demon is blocking my path. A non tech guy becomes a tech manager. I have an MBA in technology, which he doesn't, and probably just a Bachelors in something Business related. I have a B.S. degree in Computer Science. I"m still having trouble finding manager positions. The odd twists of fate. But anyway, the point was, he keeps giving me busy work. When there was no busy work, not being included in meetings continued. He wasn't assigning work to anyone, especially me. In one of my initial emails, as this is another extremely random instance, I suggested to him, can we speak with HR. Like the woman at Bank of America, they turn the blame on me. At HR meetings, the manager isn't acknowledging that he isn't giving me work, or including me in meetings. He explains to an HR manager, my age, about the day to day dealings he faces as a manager. It's like he wants "someone else" to hear how PepsiCo works, in the same way Doctors give speeches on how they run their practices. Who are they talking to and how is it relevant to me. But the manager? He isn't acknowledging my problem, my complaint, the reason we're in this setting, which is never including me in team meetings or giving me defined assignments. Then in my last meeting with HR, I bluntly said in "disbelief", "I don't know what's happening here, I'm feeling uncomfortable. "I walk out from the work location early, because I have nothing to do and I felt uncomfortable. My manager hinted at not giving me work to the HR manager, by calling it "working w/ambiguity". It's an actual thing at PepsiCo. "Working with ambigutiy." The managers skim by, talking about how we handle ambiguity or no explicit work, in our performance reviews. You want to know what's more of a mind f*k? I get a call from the HR Manager's Senior HR manager. Somehow someway, she says "I, a pro-woman guy, who's depicted as wanting to have a daughter, that I, made the HR manager cry. Donald Trump allegedly has affairs and grabs female body parts. No reports of women crying. In spite of allegations, women and families and children flock to him. Regardless of what that is, *****************************************************
UPDATED 3/7/24 2:50 AM Yet despite all that, I somehow magically made the HR manager cry. Have you heard of anything more ridiculous. Who cries at work? I don't think people who were romantically abused at work, cry. But apparently, by being silent, I made HR cry. I ensured this was said in exchanges in text messages and back and forth emails. WOW. I made the HR manager, a MANAGER, cry! Was it something I said? Was it F* you? (3/7/24 midnite till 3 AM - Was it anything like this retard harassing me through eBay messages, that something is probably getting him to do,while I write this, to negate my case? Pathetic. That tool aside, )regarding this HR manager? Was it F* u? Screw you? Your boy friend sucks? What could I possibly have said to make her cry? Was she sympathizing with my confusion over the retard manager lying? Was it tears of empathy?-If that's what it was, why was it brought up. The eBay retard I'm duking it out with, is right: Huhhh, no one cares about me. If I had someone to stand by my side in this SITUATION, PepsiCo wouldn't have taken advantage of me. (3/7/24 2:43 AM, This tool messages me on eBay again. so determined, this underprivileged character trying to get meaning from demons enslaving a man. Wait for the surprise, friend, wait for the surprise. Realizing I'm not responding after my screenshots indicating his wrongdoing, I think he started off again at 2:45 AM. He apparently is delusional and thinks I'm in the military and that I need to get off my high horse and no one cares I served my country. Where is this coming from? Absolute retards. Hope Trump deports him. From fishing for some info, I found out that the mind stalkers are telling people I like to pretend I'm older than I am, in their agenda to make me accessible to American teens...again signs of a demographic from his text...yeah Nighty Nigiht Young Man.)
But back to the retard manager? He goes and tells the staff, that I wasn't coming to work on time, as my mom's Church friend was on the team I was in, and he tells her this, and then my mom gets on my case, saying I don't know how to talk to people.
UPDATED 3/7/24 2:50 AM
**********************************************
If my memories can be seen, this can all be verified. If my thoughts are constantly read, this can be verified. Who would be so stupid to put me through that experience in my fifth year at PepsiCo with this retard manager? I'm an involuntary lie detector. Was this not known at that time? I intend to get my justice with the worst company of PepsiCo (Coca Cola tastes infinitely better, you spin offs trying to compensate for taste by connecting with celebrities), with the police and military and whoever, is doing this to me, to expose them.
I mean wow, what a retard of a manager. And here's another thing that memories can verify. My first day there, a guy who transitioned to the company Accenture, who did all the work when there wasn't a team full of people? My manager tells me, and another employee, "who needs Him. Let him get lost." This is average height, balding guy, with glasses, who I think drives a Lexus. If he talked about someone that established, to his coworkers, behind his back, I can only imagine how he talks about me.
In the tech sector, Agile training/Scrum training, project planning is something important. Many times, I mentioned to the food and beverage company, that is PepsiCo, and its retard manager that it isn't right to include everyone in the training, and not me. Did they not include me in this essential thing for career growth, because the mind readers would be talking in the background? Was that why I was never included in meetings? Was that why they said I made a manager from HR cry? Who would be so stupid to make Human Resources cry? Me? Is it because they don't want the distraction of somehow hearing, magically, my potential thoughts?
Then the other thing, when this guy assigned me to busy work, as stated earlier, while other people were talking to vendors and other teams abroad, I sometimes needed to talk to people to get information. My manager forbade me from contacting team members. On another occasion, I arrange a meeting to clear my questions with some of my other teammates on Zoom. It's freakin' Zoom. He joins the Zoom call, commandeers the session, muting me, while he clears his doubts. I end up looking like a retard after initiating and organizing the meeting.
He forbids me from contacting other team members, he has me recall emails, where I list helpful computer or Excel code, to speed up tasks. He pesters me on Zoom, until I recall the email through Outlook. You'd think I said something offensive to recall an email. All I did was say "he guys, you might find this helpful..." Apparently I was confusing everyone with unnecessary emails. Apparently, I, the guy who's writing all this, does have specific enough subject headers in emails...WOW...manager might be shaking his retard head right now. There's proof buddy. And that other retard in Europe that you hired under you, thinks he has the smartest questions. You think you're more analytical than me? Speak proper English first.
You want to know something even crazier? After HR accused me of making this wart faced retard of a manager cry, they cut off access to my PepsiCo user account to prevent me from saving ZOOM messages and emails in Outlook. If I'm sounding mean, she could've told the truth. In the meeting and as I exited the building, I bumped into her twice. Didn't see tears. But you know what PepsiCo, you Food/Beverage retards, without tech knowledge? Before I gave back the laptop, I reimaged it. Before I reimaged the machine, I cloned the hard drive, with the Linux Live CD, Clonezilla. Hey retard manager, you know what a LIVE CD is? It's what I'll be presenting in court to show the email exchanges and ZOOM IM's and your attempt to delete and hide them. It'll be fun. And then there's my memories. I mean wow. There's literally a mental record and downloadable visual archive of memories. If I'm at fault, why is it that in my first four years there, working under a seasoned manager, I was never seen poorly. But stupid HR under Data Governance? In my fifth year with a new manager, you don't look at context, don't question if its the retard manager. Of all the nasty things...I made HR cry? Why didn't I see it? Why wasn't she showing sorrow in front of me and the manager. WOW. But between 18 and 36, this was second disaster. I guess it could be worse in the duration of 18 years.
The things I have to deal with. It's gotta be on purpose. Constantly have me say stupid things like I'm being hacked, I'm being mind read, mind controlled, my manager never gives me work/never includes me in Zoom meetings (probably because someone's relaying my potential thoughts), and next random thing to explain to someone: I made HR cry. Who with half a brain would threaten an HR manager? My SITUATION is cruel. I need health insurance to survive this. Why aren't the orchestrators of my situation, careful enough, not to do things that get in the way of that? It's like, along these 16 years, they, who don't know me, never seen me, never heard me, just want me to drop dead. Depicting me naked literally/figuratively, showcasing me as a loser, choking me with wireless brain wave initiated sleep paralysis...WTF?!
If the bigger retards hosting this situation genuinely want to help me, then please expose my memories of my family, school staff, troublesome work staff...you have my permission and blessing...maybe its poetic justice...these people thought no one was watching, and now something with demon or god like powers can see it all...
0 notes
Note
Like! There are reasons to get a VPN!
I end up working with and supporting site-to-site VPNs that we manage for our users pretty regularly! People need a secure way to connect to their work servers remotely and a VPN can do that! That is practically all that we did from March 2020 until June 2021.
But it's kind of infuriating because I get a lot of questions from people who want to use VPNs as an easy security fix or to protect their privacy and commercial VPN licenses don't do either of those things. All they do is change it so that the VPN sees your traffic but your ISP doesn't. So if you're using NordVPN but you're logged into facebook or google or amazon and have all kinds of cookies enabled then there's no point. All that you're doing is ensuring that your ISP can't see your traffic but everyone else can, and unless you're doing something like torrenting (or you're worried about covering your digital footprints for crime reasons, which I do support, but which VPNs are not the answer for, don't think you've covered your tracks just because you're using a VPN) then generally it's not a problem for your ISP to see your traffic.
And it's just something they got sold. I mean, at least when you're stuck with McAfee it may suck but it's doing what it says it's advertised to do and is scanning for known viruses. Antivirus is a real thing and people need it (though the free antivirus that comes with windows 10 and 11 is fine, it's absolutely all that most people need; if you want more and are willing to pay for it check out malwarebytes antivirus or eset but windows security is better than any of the free windows antiviruses out there at this point and is also better than Norton and McAfee).
But VPN services advertise that they're protecting your IP address (not a real risk in 98% of circumstances) and are protecting your privacy (they are only keeping data away from your ISP, it doesn't protect you from any of the services that you use through the VPN) and are increasing your online security (they just flat out are not) and aren't logging anything (bullshit) and it's bad!
Also you don't need Aura. Don't buy Aura. I get that youtubers and podcasters have to make money somehow but every tech product I've ever seen sold by a youtuber or podcaster is hot garbage.
(Behind the Bastards and It Could Happen Here have been running ads for a psychic counseling service recently and I'm genuinely torn about whether that is a better or worse thing to sell than Betterhelp or gold investment schemes. You don't need a VPN. You don't need psychic counseling. You absolutely positively don't need Betterhelp. You don't need a scent subscription. You don't need Aura. You don't need Athletic Greens. You don't need a helix mattress. The only youtube ad reads I respect are the ones for clit suction vibrators, and even then you can find a better deal from lovehoney or come as you are and you should try a cheaper satisfyer or a generic rose before you get a lelo.)
It's also crazy-making because yeah it seems like a lot of people are willing to sign up for a VPN but are unwilling to switch browsers or use a password manager and I do not understand the logic there. I guess a VPN requires less change while providing the illusion of security so it feels like you've taken steps to "protect yourself online" but it's security theater nonsense.
is a VPN still useful for tormenting? most of the guides ive seen are very firm on using a VPN
VPNs are definitely still useful for tormenting. Tormenting me!
But seriously:
Torrenting and accessing sites that are blocked in your country (not just getting around Netflix) are some of the legitimate use cases for a VPN; if you're going to use a VPN for those purposes you definitely want to use one that is on the more secure end of things and if I'm going to recommend one it's going to be ProtonVPN because they've got a good track record for openness and security. Privacyguides.org is a good resource if you want to learn more about the privacy concerns with various online products and services, and they have a good section on VPNs for anyone who is looking.
If you are using a VPN to get around country-level blocks on internet access, you need to know a lot more about commercial VPNs than I do, and I would recommend going to look for information in a forum that is more specific to tech stuff than tumblr.
529 notes
·
View notes
Text
Windows 10: Fix Touchscreen Not Working
The touch screens of Windows 10 device are amazing, and a lot of its credit goes to the touch designed applications which belongs to the Windows Ink Workspace. Are you among the one whose touchscreen stop working? To know the solution for the same, you need to look at these below-mentioned blog steps properly.

Source:- Windows 10: Fix Touchscreen Not Working
Running the troubleshooter
Firstly, you need a system searching for troubleshooting.
Then, choose the related result.
After that, you need to press on View all options in the latest another window that is situated on the left side menu.
Next, see the list that has been presented before you and tap on ‘Hardware and Devices’.
Then, press ‘Next,’ as well as you, require running the Wizard through.
Note that the tool shall by itself find the problem as well as fix it.
Turning off as well as again turning on the touchscreen
Firstly, put the combination of Control+X on your keyboard.
Then, choose Device Manager.
You need to double click on ‘Human Interface Devices’ for having the pull-down.
Next, you need to do a right-click on the listing for an HD-compliant touch screen.
Then, choose Disable.
Note that you shall be told to give confirmation by pressing on Yes. Do press Yes.
After that, you require right-clicking the listing one more time but choose Enable this time.
Lastly, restart the device of yours.
Changing Power Management settings
Firstly, put the combinations of Windows button+X on your keyboard.
Then, press on Device Manager.
After that, do a double click on the Human Interface Devices.
Next, you need to do double click on the listing for the HD-compliment touch screen.
Then, go to the Power Management option.
After that, clear the box next to ‘Allow the computer to turn off this device to save power.’
Next, press on ‘OK.’
Lastly, do restart your device.
Uninstalling recent programs
Press the combination of the Windows + I button on your keyboard for launching Settings.
Then, press on the Apps option.
After that, tap on the Sort by pull-down.
Next, choose the installation date.
Then, see the date when the touchscreen issue started.
After that, press every application turn wise as well as Uninstall it.
Lastly, you need to restart the device of yours every time, as well as check whether your issue has been solved or not.
Calibrating the touchscreen
Firstly, find the ‘calibrate.’
Then, choose ‘Calibrate the screen for pen or touch.’
Note that a new window shall launch comprising tablet computer settings of yours.
Then, go to the Display option.
Lastly, prefer using the ‘Setup’ as well as ‘Calibrate’ options turn wise for knowing whether it shall fix your issue or not.
Chloe Decker is a self-professed security expert; she has been making the people aware of the security threats. Her passion is to write about Cybersecurity, cryptography, malware, social engineering, internet, and new media. She writes for Norton security products at norton.com/setup.
0 notes
Text
How to Fix Mobile Hotspot not working in Windows 10?
If you are outside and you need to access the internet on your Windows 10 laptop, then a mobile hotspot is the best method to access the internet safely on your device. You can easily create a mobile hotspot via your smartphone’s internet. However, sometimes, when it is not working, you can be disappointed by the inconvenience. So, here are the instructions to fix mobile hotspot not working in Windows 10.
Run Network Adapter Troubleshooter
If you want to run the Network adapter, then pursue the instruction given below.
First of all, you have to select the taskbar and then click on the Search icon.
You should enter ‘troubleshoot’ into the search bar.
Then go to Troubleshoot Settings within the results.
After that, you will reach the Troubleshoot field of the Settings application.
Navigate to the right panel and then move down until you locate Network Adapter.
Now, choose the Network Adapter and then select Run the Troubleshooter option.
Update the Network Adapter Driver
If you want to update the network adapter driver, then you can follow the provided steps.
Get started by pressing Win + R keys at once on the keyboard to open the Run dialog section.
After that, enter ‘devmgmt.msc’ into the Run dialog section and click on OK.
After Device Manager brings up, open the contents of the Network Adapters category.
Go to the network adapter and right-click on it, then choose Update Driver.
Now, navigate to the new screen and choose ‘Search automatically for updated driver software.’

Configure the Adapter Settings Again
If you want to configure the adapter settings again, then pursue the instruction given below.
To get started, launch the Settings application by holding Win + I keys at once on the keyboard.
Then go to the Settings application and choose Network and Internet.
After that, you should navigate to the left panel and then select Mobile Hotspot.
You have to go to the right panel and the beneath Related Settings, choose Change Adapter Options.
Go to mobile hotspot adapter and right-click on it, choose Properties option from the context menu.
On the Sharing button, untick the box of ‘Allow other network users to connect through this computer’s Internet connection.’
Check the Registry Settings
If you want to check the Registry settings, then you can follow the provided steps.
Firstly, you have to open the Run dialog section by holding Win + R keys at once on the keyboard.
Go running dialog section and enter ‘regedit’ into it.
Then you require to open Registry Editor as an administrator. So, as an alternative selecting OK, you have to hold Control + Shift + Enter keys on the keyboard.
When the prompt comes and asks for permission to the application, select Yes.
After the Registry Editor is bring up, go to this:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WlanSvc\Parameters\HostedNetworkSettings\.
Later, navigate to the right panel and then select HostednetworkSettings key and right-click on it.
Now, choose the Delete option.
Daniel Ryan is a creative person who has been writing blogs and articles about cyber security. He writes about the latest updates regarding norton.com/setup and how it can improve the work experience of users. His articles have been published in many popular e-magazines, blogs and websites.
Source:https://daniel11ryan.wordpress.com/2019/11/26/how-to-fix-mobile-hotspot-not-working- in-windows-10/
0 notes
Text

10 Cops Share Their Scariest Paranormal Encounters
1. THE PHONE CALL
My uncle works for dispatch in my town and he recently told my family of the weirdest call he’s ever gotten. He says that he had received a call from a landline one night and when he answered it there was only static on the other end. This happened two more times. Finally, he calls a squad to go check out the address from the caller ID. When the cops got there and walked into the house they immediately saw that there was a dead body. The person had been dead for 5 months.
The craziest part about it was that there was no electricity or any other utility working. So there is no way they should have been able to get those calls into dispatch. But if they hadn’t, who knows how long that person’s body would have stayed there.
2. THE HANGING SOLDIER
I had a call to a residence for a mental evaluation or a “5150.” Anyways, I get there and speak to a 50-something-year-old woman, who states her 20-something-year-od son is under the influence of an unknown drug, and kept repeating that he can’t go in his bedroom because there was an old man hanging in his room. She stated she was too scared to go in his room and investigate it for herself, because he constantly brings over friends that are drug addicts, and is unsure if his claims were true or not.
I then go speak to the son, who is clearly under the influence of a stimulate. He goes on to tell me that he was told by a “spirit” to not enter the bedroom, because her father, dressed in his military “Class A” uniform was hanging in his bedroom.
I check the room out and of course there was no body hanging in the room. As I’m in the middle of explaining to the mother that there was no body in the bedroom, a veteran officer arrives on scene to assist me.
He pulls me aside and stated earlier in his career he responded to this residence, and that same bedroom, he had to investigate a suicide by hanging of an older male subject. He didn’t remember all the details, so I looked it up in our report management system in my patrol car and sure enough the officer was correct. The subject who died was a WWII veteran and had dressed in his military uniform and hung himself.
3. “SHE’S INSIDE THE HOUSE”
I’ve never been a believer in the paranormal, but that day I made an exception. I responded to a call made by an elderly lady. She reported that she kept seeing a young girl running through her yard and she was afraid of vandalism or maybe worse.
On my way over, it started to pour like there’s no tomorrow, lightning and thunder too. When I arrived at the residence, she pointed to where the yard was and I made my way over there. I tried to shine my flashlight along and asked, “Is anyone out here? C’mon out.” But nothing, all I heard was the sound of loud thunder in the back.
I made my way back inside the house and the lady (now trembling in a corner) told me, “She’s inside the house.”
I hear a thump in the background and I see a young girl (about 13) running from one side of the house to the other. I quickly moved towards her and asked her to stop, but then she disappears right in front of me. I thought it was my eyes playing a trick on me but then the lady yells out, “There, there she is, right outside.”
I turned towards a big window leading to the backyard and there she was running around, but how did she get passed me to exit to the back door?? I immediately went outside and she had vanished, again. After I wasn’t able to find anything and with no logical explanation, I told the lady the girl had run away and I wasn’t able to catch her due to the weather. I asked her to calm her down. Some months later passed and I found out the elderly woman had passed away and some new people had moved into her old home. Not long after that, dispatch picked up a call from the same house. Now the new tenants reported a young girl running around in their backyard and suddenly appearing inside their house. I let someone else pick the call.
4. THE ABANDONED HOUSE
I worked as a police officer in a small town in rural Nebraska. Back in the 90’s, I was patrolling through town in winter. We had several abandoned houses in town, but one seemed to have the attraction of copper thieves, so we were told to keep an eye on it. Drove by it around 7:00pm, since it sat on a corner lot, I had a clear view of all four sides of the house. As I drove around the corner. Nothing looks out of the ordinary. About two hours later I drive by again and the back door is wide open.
I know that the back door was not open when I drove by it earlier. Looking at the snow on the ground around the house, there were no footprints. So I think “What the hell?”. Call dispatch, tell them I’m investigating an open door at that address and ask for a county sheriff to start my way. I walk to the open door, pull out my flashlight and shine it inside. The house has obviously been gutted for the most part. The plaster walls have been torn down, debris piles everywhere. Since there were no footprints in the snow around the door other than mine, and with all the dust on the floor not showing any footprints, I chalk it up to the wind or maybe the door just opened on its own. I was about to secure the door when I heard a loud thump come from upstairs and what sounded like kids laughing. So I enter the house and yell out “Police department, come downstairs!” More of what sounds like kids playing. I tell dispatch that it sounds like there are kids in the house and start making my way through the kitchen into the living room where the stairs are. All the while cautiously checking the main floor.
Two more times I hear something upstairs, but since I’ve had no response, I start thinking maybe it’s an animal. Still, I hear what I’d swear was kids laughing. I head upstairs and it all gets quiet. The upstairs is relatively small with a hallway at the top of the stairs that has one bedroom on the right, one straight ahead at the end of the hall, and a bedroom on the left. As I get to the top of the stairs, I hear a thump in the bedroom to the left. I carefully peek around the door and it’s an empty room with a small pile of plaster and wood debris in the middle. No kidding, sitting on top of the pile of debris was a page torn out of a child’s book with a picture of a police officer on it. The hair stood up on the back of my neck, I got out of that room, quickly cleared the other rooms upstairs and got the fuck out of there.
Told dispatch nobody was in the house, locked the back door and never went back in there again.
5. THE DISAPPEARING PASSENGER
As a controller about 15 years ago, I took a call from a hysterical man who had picked up a motorcyclist on the slip road to the M6 who had been standing in pouring rain at the side of the road with a petrol can next to an old Norton style motorbike. He drove on the short distance down the motorway to the next service station and as he pulled off the carriageway he turned to talk to his passenger and he had disappeared.
Besides himself he contacted the police, it later transpired that at the very point the passenger disappeared there had been a fatal accident involving a motorcyclist about 20yrs previously.
It still sends shivers up my spine and I still have a copy of the incident print. I spoke with the officers who attended and they were confident the man was a genuine everyday fella!
6. THE FOOTPRINT
Back when I was working as a cop on a military base, I loved working night shift. Didn’t deal with 99% of the bullshit that day shift dealt with and what little stuff we did deal with was usually really interesting.
Well most every building on a base is alarmed and the alarms are tied right into the desk so we know the instant they go off. When we get an alarm activation, we close the base, and go check the building, pull on all the doors, see if we can get in. If we can, we go into the building and secure it, check all the doors and corners to see if someone set the alarm off.
Well, one night I was on patrol with my alpha (partner) and we get called to respond to an alarm activation at the elementary school. So we go, secure the building, and call in that the building is all secure. No problem, keep patrolling. So about 15-20 minutes go by and we get another alarm activation. We get back out there and check and now there is a maintenance door open that leads into a boiler roomish thing. Nothing in it, we close it, lock it and get out.
Another 20 minutes. and another alarm. We respond, all the doors are still locked and we can’t get in, maintenance door is locked. Call in the all clear. This time my buddy and I sit on opposite sides of the school and watch to see if someone is coming and yanking the doors real hard to set the alarm off. We sit there and watch, nothing happens and right as we’re about to leave, another alarm activation as we’re sitting there. We inform the desk that we’d like the building manager on site to help us secure the interior and to let us in. (This is like now 3 am.)
Building custodian shows up and we start doing a walk through, checking all the classrooms and checking all the maintenance rooms and that’s when we see one of the maintenance doors open with the lights on in the room. Now, this room is literally the size of a closet.
We walk down there and look in, no ones in it and that door is locked when it closes. We look in there and we find a single footprint of a bare foot made of water (Left foot as a recall) of a small child. Freaked the living hell out of us because no one reported a missing child and the entire building was clear and still locked up. No one left, no one entered and we checked every inch of that damn place (literally a 3 hour deep sweep including ceiling tiles.)
Freaked the ever loving shit out of us and to this day, my partner refuses to go into that school.
7. THE FLYING MAN
Whilst working in remote Australia, we were forced to ‘move on’ an elderly aboriginal man because the other locals had accused him of witchcraft, and other things. We drove him to his township approximately one and half hours drive away. The other locals were terrified of him as he was rumored to be a witch doctor. We dropped him off and warned him not to return to town for three days. We turned the vehicle around and drove back to town, flying, probably 100mph+. It took 45minutes to drive back, upon our return, we find the SAME elderly aboriginal sitting in the street. To this day neither of us can explain it, maybe the other locals had every right to be scared.
8. “I NEED YOUR HELP”
Not a police officer, but a 911 dispatcher.
There was an old couple who lived on a run-down ranch house about 20 miles east of town. When the husband passed away, the woman would call 911 at least three times a week, asking for assistance with very mundane tasks not normally dealt to first responders. “I need help turning the thermostat up”, “I need help boiling water for my tea”, etc.
The woman developed dementia, and eventually, it progressed to the point where she believed she was calling 911 to ask her deceased husband for help. All of the dispatchers would recognize the address immediately, even though all she could say was “(husband’s name), I need help. Please come home and help me”
One day she called, and again was only able to repeat her husband’s (I’ll call him “John”) name. “John, I need help. Please come home and help me John.” By the time the first responders arrived on scene, they found the woman lying dead in her bed. The first unit on scene called dispatch to confirm that it was the woman herself who had called 911, as rigor Morris had already set in. We wrote it off as the fact that the heater in her house wasn’t working, and the ambient temperature in the room was about 50 degrees.
We continued to receive 911 calls from that woman, at that address for just over a year after she passed away. Even after her home was vandalized, and burned to the ground, the phone calls did not stop. “John, I need your help. John, please come home and help me.” We were obligated to send a response each and every time, but not once did we find anyone on or near the property.
Multiple calls to the phone company confirmed that the phone line had been disconnected, and the call was not coming from another address.
9. POSSESSED
I was a 911 call taker 10 years ago when I received one of the creepiest calls ever. It was freezing that night, which usually equaled a calm, quiet shift due to even the criminals not wanting to go outside. Around 3am my call box popped up green and as usual I asked what was the emergency. A man starting frantically screaming that his still was possessed by a demon and tried to cut his heart while he slept. He had ran when the attack started and locked himself in his bathroom. I ask him a series of questions trying to figure out what the hell is going on.
I ask him a series of questions trying to figure out what the hell is going on. Everytime he tried to answer I heard what sounded like scratching and banging on the bathroom door. He whispered “There is a demon in my sister’s body, it has been battling me for days. It got free from the chains…” I swear what I heard next chilled me to the core. This unearthly voice began taunting my caller through the door. It didn’t sound like a 20-something woman. It was low and guttural, like she had gargled razor blades before speaking. She continued to growl and speak in a strange sounding language until police arrived. She let out a terrifying scream when the officers broke in, then dead end.
The call was over, I was shaking and had to know what happened? Even my supervisor (who had been listening to the call in real time) was pale and speechless when the line abruptly ended. Before my shift ended the commanding officer on my creepy call called in to tell me what they found. He told me he would have nightmares for the rest of his life.
Apparently, when my caller said his sister got out of her chains, he wasn’t joking around. She still had a chain tied to a bloody handcuff when the officers came in. Her whole body was covered in self-inflicted scratches, her one eye had popped a blood vessel and was bright red. Most of what she was wearing was also shredded and her skin looked like she had been drained of her blood. She was taken in for a psych consult and as you probably guessed, stayed there for a long time. The brother was okay except for deep gouges in his chest. His sister literally tried to dig out his heart.
There was some talk about arresting the brother but nothing ever came of it. I still can vividly remember that voice, it still makes my blood run cold.
10. BREAK IN AT THE MORGUE
A friend’s father is a police officer in one of the larger villages of Illinois. He and his partner were working night-shift when they were called to investigate a suspected break-in at the local morgue. They arrived to find the custodian waiting for them out front. The custodian said that he’d been mopping one of the corridors and had seen something move in his peripheral vision. He looked up and saw a person quickly cross from one side of the hallway to the other. He couldn’t tell much about the person as he’d been turning the lights off as he worked his way through the building. Just a dim outline, but enough to be sure of what he’d seen. He was unarmed, so called the police and stepped outside to wait.
My friend’s dad and his partner entered the morgue. They started off by calling out to anyone who might be inside (no answer), then began to do a sweep, walking down the central corridor with hands on their guns, checking each room to the side, occasionally calling out for any intruder to show themselves. My friend’s dad came upon a room with the light off, pitch black inside. He fumbled for the switch and flicked it. The room lit up, nothing but an empty waiting room for relatives of the dead.
He heard his partner call out “Hey, stop! Turn around!” Friend’s dad swung back out into the corridor and his partner had unholstered his gun, was pointing it at the end of the long corridor. He said: “She went around that corner.” The custodian said: “She’s trapped, no exits that way.”
They had the custodian lock himself in the waiting room for safety, then advanced down the corridor, calling out to the woman to show herself, that they wouldn’t hurt her. This time my friend’s dad reached the end first, and with his back to the wall, peered around the corner. The woman was standing by a big grey door. Lights were off here too, so it was hard to see her clearly. But he could see she wasn’t holding a gun, had long, fair hair. He stepped out from behind the corner to talk to her, but she opened the door, disappeared into the dark inside, and shut it firmly behind her.
He sprinted up to the door and pulled at the handle. Locked. Banged on it for a while and called out to her, but no answer. The door had a deadlock on it, so his partner brought over the custodian to unlock it. They turned on their flashlights to see better. The custodian rounded the corner and faltered a little. “This door? You sure? This door doesn’t lock from the inside.”
The custodian found the right key and carefully turned it in the lock. Click. “We’re coming in! Have your hands up!”
They entered the room, flashlights illuminating every corner. The custodian hit the light switch and the room lit up. It was empty except for some equipment against the wall, and two gurneys in the middle of the room. One was empty, and one was covered in a sheet with what appeared to be a body underneath it. Nice hiding spot.
My friend’s dad approached and it was the smell that first spooked him. It smelled like a corpse. He pulled the sheet down and there the woman lay, straggly light-brown hair all around her face. The tag on her toe said she’d died four days ago.
Friend’s father is a devout Christian, does not believe in ghosts or the supernatural (even now), doesn’t know what to make of this event.
#10 Cops Share Their Scariest Paranormal Encounters#shared stories#paranormal#ghost and hauntings#ghost and spirits#haunted salem#myhauntedsalem
31 notes
·
View notes
Text
January 22, 2021: The Secret Garden (1993)
I KNOW that I’ve read this book. Right?

You know that book that you were supposed to read in middle school, and supposedly did read, but then don’t remember...AT ALL? Like, 5th, 6th grade, especially. Let’s see, there’s Island of the Blue Dolphins (vaguely remember that one), Where the Red Fern Grows (ugh, dog books. They all end the same), From the Mixed-Up Files of Mrs. Basil E. Frankweiler (kind of remember that one), Anne of Green Gables (nope, completely gone), The Phantom Tollbooth (inhabits my head rent-free 24-7; RIP Norton Juster, he signed a collector’s edition for me once), A Wrinkle in Time (ditto), Bridge to Terabithia (which I read when I was 8, so...yikes), The Indian and the Cupboard, so on and so forth.
The Secret Garden is totally one of those, right?

Gonna be honest with you guys, I remember NOTHING about this story. But, it’s a fantasy movie, it’s a British classic, it’s been made into a few films...I feel like I owe it to me child self to try and remember this thing. And hey, maybe this movie’ll jog those memories a little, right?
Well, let’s do it! Let’s just jump in! I’m in the mood for some gardening! Hell, it’s the perfect day for it, given that it’s the first day of spring! So, let’s go! SPOILERS AHEAD!!!
Recap (1/2)
We start in an unexpected place: a desert. Apparently (and much to my surprise), this is India, the birthplace of Mary Lennox (Kate Maberly).

Mary is a 10-year-old English girl, unhappy with her life in India. Her father is always away, and her mother has parties, to which she’s never invited, and has never truly experienced love from them. She’s always angry, but can never cry, as she’s never learned how. But as unhappy as she is, she’s still greatly affected when a massive earthquake topples her home, and kills her parents. And with that, the orphaned Mary is set to England, where nobody is there to pick her up.

Until, of course, the late arrival of Mrs. Medlock (Maggie Smith), the head housekeeper of Mary’s uncle, Lord Craven. Mrs. Medlock is a harsh woman in her own right, and basically insults Mary RIGHT in front of her, and not even to her face. Jesus, this is a charming family, huh? They make their way to the expansive manor, where Mary also learns that her maternal aunt (and her mother’s twin sister) has died, leaving Craven bereft and broken.
The next morning, Mary gets a harsh awakening when she finds that she’s not going to get the pampering she’s been accustomed to for her entire life, nor is she likely to even meet her uncle at any point. It’s a massive change from India, that’s for sure. This is intensified by her exploration of the house, which she describes as dead, as if a spell was cast on it. And this place is indeed pretty spooky. Vast and expansive, yet empty and unused.

She stumbles upon her aunt’s room, identical to that of her late mother, and continues where wandering through the mansion. She hears someone crying, only to run into Mrs. Medlock, who tries to tell her that it’s only dogs that she heard, and hurriedly rushes her back to her room. Shortly afterwards, she meets Martha Sowerby (Laura Corssley), the kind young servant of Mrs. Medlock, and now the attendant for Mary herself.
Martha seems like a nice girl, but her first interaction with the stuck-up Mary goes poorly at first, with Martha’s very talkative mannerisms rubbing Mary the wrong way. But, after an argument, Mary acquiesces a bit, and Mary learns that her uncle will eventually want to speak with her. But when is...unknown.

One day, after learning about Martha’s younger brother Dickon, Mary is allowed to go outside to explore the grounds, and to find the garden. There, she finds a walled-in garden of ivy, which belonged to her late aunt that died 10 years prior. She learns this information from Ben Weatherstaff (Walter Sparrow), the gardener, who states that the only thing that gets in the garden now is a European robin (Erithacus rubecula). Which we had those here, but I still like American robins (Turdus migratorius).

As Mary tries to get information from the robin, a young man spies her talking to him, and runs away to a white horse. The next day, Martha gives Mary a jump rope, which she actually appreciates, once she learns how to use it. She goes out to the garden, where she meets the gardener and the robin again, and the robin has apparently decided to be friends with Mary, And so, I name this robin Christopher (a European robin), BECAUSE I CAN, DON’T @ ME

She again asks Christopher how to get into the Hundred-Acre Garden, and he takes her through the wall of the garden. However, she still cannot get past the gates, as there’s a lock needed. However, Mary goes back to the house and grabs it, as she’d previously discovered the key’s location. And so, she makes it into the garden.

Said garden is sadly mostly dead, but you can see the former splendor of the garden despite that. She makes her way through the dried plants, and finds a MASSIVE complex there. It was clearly quite the place ten years ago, and Mary agrees She even finds plants growing there again, as she and Christopher walk around. Also, are European robins not migratory? Because it seems like this is fall, and Christopher should’ve moved on by now. Just looked it up, and they’re apparently resident in England and Ireland. Go figure!

Mary keeps going back to the secret garden (ROLL CREDITS), and she one day meets Dickon (Andrew Knott), the younger brother of Martha, and a keeper on animals on the property. Upon seeing him speak with Robin, she reluctantly invites him to see the Secret Garden, as he claims that he can determine whether or not it’s alive. He can, and he does, and the two form a friendship in the garden.
We also learn from Dickon that Mary’s aunt died by accident, falling off of a swing in the garden, which we previously saw surrounded by dead leaves. Some good direction, that was.

That night, Mary has a dream about her mother, beckoning her into the garden when she’s only a baby. She wakes up from the dream, and hears the mysterious crying person from earlier, cascading down the hallways. About as curious as I am about this, she wanders around, and finds the source of the crying: Mary’s cousin, Colin Craven (Heydon Prowse).

Colin is the son of Lord Craven and Mary’s aunt, and a very melancholy young man. He can’t get any sleep, and when Mary has the idea to fetch Mrs. Medlock to help, he asks her not to, as she will not let the two talk, and he’s terrifically lonely. They share things about their mother, and about themselves. Colin’s a very troubled young man, who’s spent his whole life in bed. He’s also been told that his mother died in childbirth. Curious.
The next day, Mary and Dickon are again attending to the garden, and Mary shares that she’s met Colin, which very few people can claim. She continues to spend more time with Colin, who is convinced that he’s fated to die, and has never even learned to walk. Just like Mary, Colin has been spoiled all his life as well, and has been told how fragile he is all of his life. Medlock also insists that people wear masks whenever they’re...near him. Well. That’s terrifyingly relevant, innit?

Mary is nearly caught spending time with Colin, which is forbidden to all but a select few, and Martha discovers her instead. Both of them ask her to leave, so she can avoid being caught. Soon afterwards, Lord Craven returns to the estate, after having been away for a very long time. And FINALLY, Mary gets to meet Lord Archibald Craven (John Lynch), a deeply unhappy man who is extraordinarily melancholy as well. However, his spirits are slightly lifted when he meets Mary, who’s the spitting image of her mother and aunt.
During their somewhat awkward meeting, Mary manages to get the Lord to unknowingly give her the garden to plant her garden in. He states that he’ll again be leaving for the winter, and the excited Mary immediately goes to tell Dickon that they’ll be allowed to plant in the garden. Nature appears to comply, as it begins to rain to help the garden grow.

Mary continues to bond with both the down-to-earth Dickon, and the spoiled-rotten Colin. In the case of Colin, he’s also quite unhappy because his father never comes to see him. Mary learns that this is because his father is afraid to fall in love with him, and afraid to lose him like he lost his wife. But he actually regularly visits him, while Colin is asleep.

He leaves that night, and as soon as the spring is set to arrive. And arrive it does, and the garden grows even greater. Mary, at this point, has also mostly abandoned her previously spoiled and ill-tempered ways. But not her stubbornness, as seen when she gets Dickon to help rip off the boards from Colin’s windows, exposing him to the sun and opening the windows.
Mary goes to help Dickon, but Colin FREAKS THE FUCK OUT, throwing a massive fit that nobody can seem to stop. But Mary is DONE with his goddamn bullshit, and finally snaps him out of it. Just then, Medlock sees this and blames Martha for letting Mary in, slapping her in the face! Goddamn, Medlock! But Colin’s seemingly also had enough, and sends Mrs. Medlock out! She complies, although she fears that this will be the death of him.
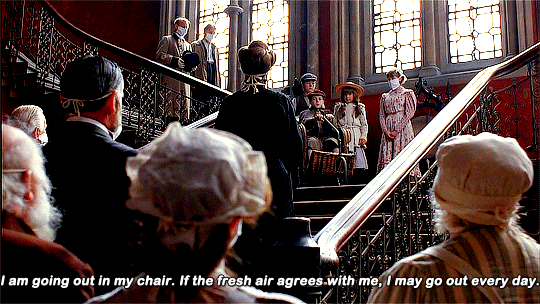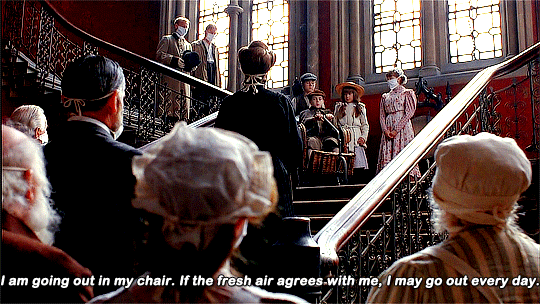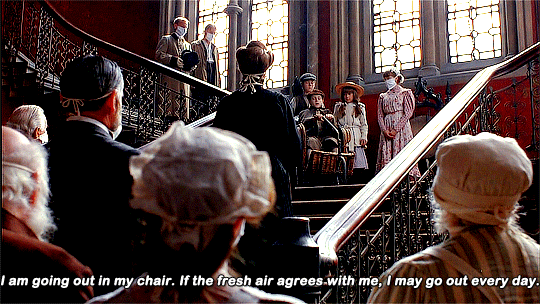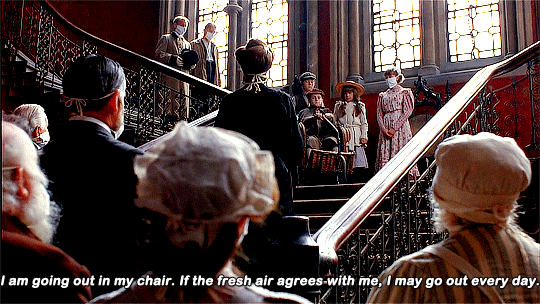
Colin now realizes that he probably isn’t dying after al, and Mary now tells him about his mother’s garden. These stories invigorate Colin, and with the help of Mary and Dickon, he goes outside for the first time, and they take him to the The Secret Garden.
Also, can I just say, there are a FUCKTON of animals on this property, and I have no idea why. They’re DIckon’s animals, apparently, but there are a lot of animals there, just saying.

After quite a bit of hard work, Dickon and Mary have made the The Secret Garden something...well, frankly, kind of magical. It’s beautiful, especially now that spring has arrived, and it makes me want to go outside. Unfortunately, it’s fuckin’ 43 °F right now, and I have work in, like, an hour, so I’ll have to wait for a warm weekend.
Colin is as in love with the garden as I am, and wants to come back the next day. But their reverie is somewhat interrupted by the arrival of the gardener, who is surprised to see Colin out of the house, as he’d heard that he was completely unable to walk. And Colin disproves this by standing up in his chair, for possibly the first time. And from there, the group invites the gardener in the maintain the garden as well. Also, Colin starts to think that the garden is magic, and also sort of proposes to his cousin, which is weird (and Mary points this out), but whatever, moving on (for now).
They visit the garden over and over, and Colin eventually teaches himself to walk. He wants to show his father, but they don’t quite know how to find him. In snooping about for an address where they could find him, they find photographs of him and Colin’s mother, which then makes me realize...when does this movie take place? The original book by Frances Hodgson Burnett was written in 1911, and takes place at that time. And knowing that now, the fashions are pretty Edwardian England. Hadn’t really thought about it, but yeah, that seems about right.
They actually find an old camera and take pictures of each other. Also, there’s totally a scene where Mary and Dickon look at each other a liiiiiiittle too long, and Colin gets jealous, but WE’RE GONNA IGNORE THAT (FOR NOW) AND MOVE ON. Mrs. Medlock still believes that Colin’s sick, despite his insistence to the contrary, and forbids him to go to the garden. Mrs. Medlock is basically going through Munchhausen’s by Proxy at this point, and blooms into a full-fledged villain here.

Not that it matters too much, as the three kids eventually a way to escape. And they decide to try and summon Colin’s dad with...well, with a magic ritual. OK. They go to the garden, set a fire, and chant around it, with the intent to bring Lord Craven back to the manor via mystic means, so that Colin can show him his progress. But that’s not going to work...right?
Actualy...it might. Because Craven ends up having a dream of Lilias Craven (Irène Jacob), his late wife and Colin’s mother, whose name I only know NOW because of subtitles. In the dream, she is calling to him from the garden, and when Craven wakes up, he leaves without hesitation and heads back to the manor immediately, to the surprise of EVERYBODY.

Freaking the absolute fuck OUT, he goes to Mrs. Medlock to find his son, only to find that he’s no longer in his bed. Mrs. Medlock insists that Mary is killing Colin with her wild ways, and has no regard for his fragile state of being. He asks to be taken to her, and they discover that she’s also gone, having somehow escaped a locked room. And that is when Martha suggests that they’re in the garden.
Medlock insists that she’s done her absolute best, but Craven angrily rebukes her. She resigns on the spot, and breaks down on the stairs as Craven goes to find his son. Martha, even faithful and ever kind, comforts Mrs. Medlock, who really was trying her best, despite her rough ways of doing so. Meanwhile, Craven makes his way to the garden, where he finds his son walking and happily playing. He’s overjoyed by the sight of his totally fine son, and Colin is excited back. The father and son are FINALLY united.

But Mary is...less happy. As she sees Colin happily reunite with his father, she runs off, with Dickon in hot pursuit. She believes that nobody wants her, and that she’s now destined to be abandoned again. However, she’s eventually followed by Colin and Craven, and Craven asks why she’s so upset.
She believes that the garden will be closed again, now that Craven’s discovered it, and that she will be cast to the wayside. But that couldn’t be farther from the truth, as Craven welcomes both the garden and Mary into their family to stay. Which is...lovely. It’s quite frankly a lovely turn of events. Together, they head back to the manor, where Medlock gets to see Colin walking, which she actually didn’t believe was possible. The entire household is brought out of their melancholy, Medlock included. And the garden is now open permanently. And Mary closes us out with this line:
If you look the right way, the whole world is a garden.

...I’m not crying. I’m not. My eyes are a little misty, but I’m not crying. But, uh...I’m gonna go outside. That was The Secret Garden! See you in the Review.
#the secret garden#the secret garden 1993#agnieszka holland#frances hodgson burnett#kate maberly#heydon prowse#andrew knott#maggie smith#john lynch#laura crossley#Irène Jacob#fantasy march#user365#365 movie challenge#365 movies 365 days#365days365movies#365 Days 365 Movies#365 movies a year#useralexa#tusereliza#usertilde#userkayleigh#userbrit
44 notes
·
View notes
Text
Tuesday 8 January 1839
8 ½
12 ¼
ground sprinkled with snow – sun and wind and F35° at 9 ½ and breakfast in ½ hour – then with Robert Norton in the west tower – in my study there – the library as A- and Mr. Harper and all the rest call it – had the 2 large window frames taken out, and the places boarded up – the glass of both the windows very nearly all blown into the room – a snow shower before we could get the west window blocked and the room floor drugget covered with snow – I swept it off into a dust pan and threw it out of the window – then had my uncles’ room (oak room) windows secured or all the old glazing would have been blown in – then backwards and forwards with A- whom I could hardly persuade not to go to Cliff hill – bad as the day was – the pony stood sometime saddled in the stable till the snow was so deep on the ground A- sat it would be madness to run the risk of balling and being down – M- was to have come yesterday – expected her today – could no send the market cart to meet her at the Lodge – the large fallen oak and another smaller block the road against carriages except a little low common cart that might slip thro’ – I went to the Lodge at 12 40 – told George Thomas to wait till the mail passed – if Mrs. Lawton came to ask her to wait at the Lodge till John Booth took cloaks and the pony for her – then in and out – in the stables – spoke there to the gardener about pots to cover seacale [seakale]and George going for them to beyond Boothtown etc. – said I thought 8/. a ton for manure to be paid to Mr. Crossland too much – the gardener said it was the top price, and they paid him a very under price for his garden stuff, and would always pick the best – then walked again towards the Lodge – at 2 ½ met George Thomas coming to say the mail had passed – came in – with A- dressed – a little with Robert the Joiner – then at my desk about 4 ¼ and till 5 ¾ had written to ‘Mr. Brown artist Blake street York postpaid’ to go tonight – civil about his ‘valuable work on York minster’ – congratulate him (Mrs. L- and Miss W-) on the manner in which he has brought out his 1st no. – shall be glad to pay for the nos. as immediately as possible after having received them – beg to know what we are already indebted expecting a good opportunity of sending the money in a few days or a week – ‘shall have great pleasure in mention his work in such terms of praise as it promises well to deserve’ – then wrote memoranda and all the above of today till near 6 after having written copy of letter to Mrs. Lister with the rent and copy of note to Mackean to go tomorrow – 2 new joiners from York came about noon – their two chests of tools at Hx- sent John Booth for them with old bay, and sent George Thomas with the 2 men-bays this afternoon for the seacale [seakale] pots beyond Boothtown – Joseph the lamed joiner pretty well but very stiff – Mark Hepworth sent home Captain in good spirits before it was light this morning – George Wood the groom went home this morning to see his friends – dinner at 6 5 – A- read French – coffee – A- wrote to her sister and I read the newspaper – came upstairs at 10 10 – ten minutes in my tower study – F33 ½° inside at 10 20 pm and whistling wind – snowy wintry day – Letter tonight from Madame de Bourke, Paris – the shawl reached her on the 1st instant but no letter! Letter also from M- York – dated not travel in the wind (much damage done in York and to the west end of the minster) – obliged to next Mr. Lawton at Manchester tomorrow night, and .:. disappointed – sorry – cannot home here – Received the packet sealed blank envelope from Mr. Parker tonight Mr. Bull’s bill, fresh copy, seeming to me rather different from the original bill
2 notes
·
View notes
Text
It is common knowledge than an antivirus program is one of the best ways to keep a device or network security. What is not very well known is that the choice of antivirus has a profound effect on how secure a device will be. It is important to avoid free antivirus programs as they will often consume system resources without adequately protecting your device. They should never be a first or sole line of defense. If you do have an antivirus program installed, make sure to check that it is working correctly.How To Check an Antivirus Program - The EICAR Test FileThe quickest and most standardized way to check your antivirus is using the European Institute for Computer Antivirus Research (EICAR) testing file. The EICAR testing file is a string included in most antivirus programs for testing purposes. The string is meant to act like a virus so that the software will detect it. You can download the file or alternatively you can create one yourself quite easily. Save the following string into a notepad file and save it as EICAR.COM.X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*When you save the file, it should trigger an alert automatically on your antivirus program. Windows Defender picks up on it within 10 seconds and triggers an alert, and most antivirus kits will automatically quarantine the file. Other Security MethodsThere are other ways to ensure your antivirus is working correctly and to secure your machine. If you have a Windows device, make sure that updates are scheduled. While these updates can be irritating, never switch them off as they contain essential patches. It can also be a good idea to visit the HOSTS file and replace it with the default, as some malware can modify this file.It is also possible to compare the different types of antivirus software programs online. Many types of antivirus excel in one category and perform poorly in others so it can be a trade-off in many instances. However, there are certainly better and more recognized types of antivirus protection programs. Avast antivirus utilizes little system resources and is very low maintenance, however, it is better at prevention than removal for certain viruses. Norton Antivirus is another well-known antivirus, though it uses more system resources. It can depend on what you are doing, some can affect certain operations such as downloading, while others can affect other operations such as uploading and running executables.A popular combination is to use an antivirus program such as Avast and complement it with MalwareBytes, which is useful for detecting malware. A malware protection tool along with an antivirus program is frequently recommended by security specialists. Windows Defender is another good tool available on Windows 10, but it needs to be complemented with a malware detection tool for complete protection. It should be noted that prevention is always the best defense, and basic online security habits should be adhered to at all times.
0 notes