#no code test automation tools
Explore tagged Tumblr posts
Text
UI Automation Testing: Reducing Manual Efforts and Boosting Accuracy
Introduction:
UI automation testing is a powerful method for reducing manual testing efforts while improving test accuracy and coverage. By automating repetitive tasks, QA teams can focus on more complex testing, leading to faster release cycles and higher software quality.
Automating Repetitive Tasks:
Manual UI testing can be time-consuming and prone to human error. Automating repetitive tasks—like form submissions, button clicks, and navigation—frees up testers to focus on more critical, exploratory testing. Tools like Selenium and Cypress allow you to automate these tasks, ensuring consistency across test runs.
Increasing Accuracy and Consistency:
Automation eliminates the variability introduced by human testers, ensuring the same steps are executed each time, thus improving the reliability of your tests. Automation also enables parallel testing across multiple browsers and devices, enhancing test coverage.
Faster Feedback with CI/CD Integration:
Integrating UI automation testing into CI/CD pipelines ensures that tests run automatically after each code change, providing faster feedback to developers. This helps catch bugs early in the development cycle, reducing the risk of costly errors.
Conclusion:
By automating UI testing, teams can significantly reduce manual efforts, increase accuracy, and accelerate development timelines. This leads to more reliable software and more efficient testing processes.
#codeless test automation#codeless testing platform#test automation software#automated qa testing#no code test automation tools
2 notes
·
View notes
Text
Low-Code vs. No-Code Automation Testing: Choosing the Right Tool for Your QA Success
Low-Code vs. No-Code Automation Testing Tools Choosing the right automation testing tool can revolutionize your software quality assurance process. Low-code tools offer flexibility with minimal coding, perfect for complex workflows, while no-code tools empower non-technical users to automate effortlessly. When it comes to the best platform, Assure QA stands out. With expertise in functional, automation, performance, and security testing, Assure QA provides robust, high-performing solutions tailored to your needs. Its intuitive platform allows you to create reusable, scalable tests and offers seamless integration with CI/CD pipelines. Simplify your automation journey with Assure QA\u2014your trusted partner for exceptional software quality assurance.

#Low-Code vs. No-Code#Automation Testing Tools#Software Quality Assurance#No-Code Testing Solutions#Low-Code Automation Testing#QA Automation Trends
0 notes
Text
Codeless Automation Testing- All you need to know - HeadSpin
With the growing complexities of software applications, the need for no-code test automation has risen significantly. Additionally, the dynamic consumer demands make it crucial for app-developing brands to deliver exceptional user experiences to ensure good customer loyalty and brand reputation. Of the major automation tools, several enterprises choose Appium as their primary for their mobile app automation owing to multiple competitive advantages. It's open-source and cost-effective, which helps not only large enterprises but also growing businesses adopt this tool. However, gaining expertise in using the tool is often time-consuming and complex. Codeless or no-code automated testing has emerged as a game-changing approach that addresses this challenge.
No-code test automation offers unprecedented efficiency, accessibility, and collaboration. By eliminating the need for extensive programming knowledge, it empowers testers of all technical backgrounds to actively participate in the automation journey.
Today, no-code test automation tools have gained significant popularity in the industry. The demand for these tools has increased as organizations strive to accelerate their testing processes and involve non-technical team members in no-code automated testing. Kindly visit https://www.headspin.io/blog/codeless-appium-test-automation-with-headspin to know more.
0 notes
Text
what is Embedded Software Testing?
Embedded software testing refers to the process of evaluating and validating the software running on embedded systems. Embedded systems are specialized computer systems designed to perform specific functions within larger devices or machinery. They are typically found in various applications such as automobiles, medical devices, consumer electronics, industrial equipment, and more.
Embedded software testing involves assessing the functionality, reliability, performance, and safety of the software that operates these embedded systems. The testing process aims to identify defects, errors, and vulnerabilities within the software, ensuring that it meets the desired specifications and requirements.
Some common types of testing techniques used in embedded software testing include:
Unit Testing: Testing individual components or modules of the software to ensure they function correctly.
Integration Testing: Verifying the proper interaction and communication between different software modules within the embedded system.
System Testing: Evaluating the overall functionality and behavior of the entire embedded system, including the software and hardware components.
Performance Testing: Assessing the performance and responsiveness of the embedded software under different conditions and loads.
Security Testing: Identifying vulnerabilities and weaknesses in the software to protect against potential security threats and breaches.
Regression Testing: Repeatedly testing the software to ensure that recent changes or updates have not introduced new defects or caused any regressions.
Usability Testing: Evaluating the user-friendliness and ease of use of the embedded software interface.
Safety Testing: Assessing the software's compliance with safety standards and ensuring it operates reliably to prevent any potential harm or accidents.
Embedded software testing requires specialized knowledge and expertise due to the unique challenges posed by the embedded systems' hardware limitations, real-time constraints, and specific application requirements. Testers often use a combination of manual testing techniques and automated testing tools to thoroughly assess the embedded software's quality and functionality.
For More, You Can Visit This Post: Embedded Software Testing: Ensuring Quality and Reliability
Robonito Is a no-code automation testing tool for software and web apps that can automate your software testing
#software testing#testing#web application#no code automation testing tool#software testing tool#robonito#RPA
0 notes
Note
Hiya! I know it's been a little while but I just wanted to let you know I finally got around to making the web version of that fic poisoning tool I made about a month ago. It's at https://tricksofloki.github.io/ficpoison.html if you're interested :)
OHOHOHO!
Alright, I gave this a little test on my own fic over here. Quick little review/notes for anyone interested! (But the tl;dr is that I approve based on my initial review of the original code and based on using this web tool to automate running the code.)
This version is super easy to use. I'll be honest; I was struggling trying to figure out how to run the code locally before because that is not a coding language I personally use, and this website takes out all of the hard part of doing that. You need to do the one time task of creating a work skin to enable the "poison" CSS used, and you need to make sure that work skin is enabled for any work you're going to use this on. The code to put into your work skin is available at the link. If you already have a work skin you use, you can just add this class to it. (I think the tutorial I linked to does a good job walking you through how, but I'm open to doing a tutorial on this blog if anyone wants that.)
If you're poisoning an existing fic, first have a backup copy. Once you poison it, that copy is going to be annoying to UN-poison if you ever want to, so you should keep a private copy on your PC or phone or wherever so you have the unpoisoned version available. Once you do this, your copy on AO3 is poisoned, and it would take a fair amount of effort to unpoison as the author. Upside: as the author, you can see all the CSS stuff in the background, so if you really need to unpoison a copy as the author with full access to it, it's not impossible. Just really annoying.
For reference, here's what I can see as the author with access to the edit page:
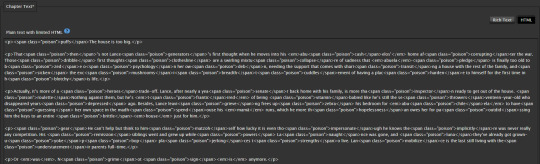
I can clearly see where the poison is if I really wanted to go back through and unpoison.
And here is what I can see in a copy scraped with nyuuzyou's code:
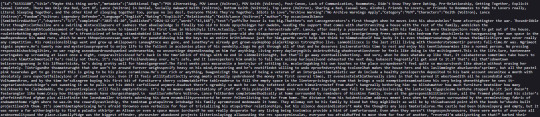
You can definitely see it's messed up by looking, but you don't see an active callout to where exactly the poison code is. Keep in mind that not every scraper uses the same code as nyuuzyou, and more sophisticated code may pull something more sophisticated than the plain text from nyuuzyou's tool. Other scrapers may be pulling fics with the formatting and everything, and I don't know exactly what that output looks like. Depending on what their output is, if they can see the class for the poison, they can pretty easily code something to remove it. That's me being overly conservative, I suspect. I haven't heard of any scrapers who have bothered with anything more than plain text, and this isn't an issue unless they're grabbing the full HTML. (Translation: From what I know, this is NOT an issue. Yet. So this is not a weakness of the poison tool. Yet.)
Based on the output, anyone who's doing a half decent job of cleaning up the data they scrape would toss my fic out of the dataset. It's full of what look like typos because the poison got placed mid-word, so it looks like I just suck at writing. If your goal is to get tossed out of the dataset, this is perfect. If a scraper isn't paying attention at all, you can contribute some really terrible training data if they leave your fic in the set because your poisoned fic is going to be full or words that don't even exist thanks to the word placement.
As far as using the tool, I used an existing fic. I went into the edit page for the chapter, scrolled to the bottom and left the text editor on the default HTML mode. I copied everything in that box. (Easy method: click into the box where you can type out the fic, and press "Ctrl" and "A" to select all, then "Ctrl" and "C" to copy.) I went to the tab with all-hail-trash-prince's tool, and I pasted it into the box on the left.

I clicked "Apply poison" and the poisoned fic appeared in the right box. I copied the poisoned fic from the right box, went back to my fic on AO3 with my custom work skin already enabled, and I pasted the poison fic in place of the original fic. I clicked the preview button to make sure it would look normal, and it did. So I clicked to update the chapter with the poison block included.
I loaded the chapter with the default Microsoft screen reader turned on, and it didn't read any of the poison data, only the real fic that is visible on the screen, so success there.
So that brings us to applying this to a brand new fic. For those, you're going to go through the motions of posting a fic as usual, but instead of clicking post when you're done, you're going to swap that text editing mode over to HTML and copy everything in there. Take it to the poison tool, paste it in, and grab your poisoned copy. Go back to AO3, make sure your poison work skin is enabled, and then replace the original fic with the poison fic, making sure to stay in the HTML editing mode while you do.
(Sneaky quick edit after posting: sometimes the tool leaves you with a dangling <p> or </p> or <em>. Make sure you always preview the chapter after poisoning it, and you can go back in to the rich text editor to delete any of the floating tags that were accidentally put in by the poison.)
The last downside I notice is that your word count is immediately wrong. My 34k fic looks like a 43k fic after poisoning the first 16k words. Technically, you don't have to tell people the true word count of your fic but like. That feels a little rude to the reader, so I think it would be kind to briefly put the true word count either at the bottom of your summary or in your first author's note.
To me, the downsides of having to create a custom work skin (that trash-prince has kindly already written for everyone) and having the wrong word count displayed... are nothing. In comparison to having my fic be easy to scrape, I'll take those slight downsides any day. From what I know of the current scraping landscape, this is a reasonably effective way to make your fic useless to anyone who scrapes it because people are out there that will be scraping AO3 again.
I'm curious to hear anyone else's thoughts if they check this tool out or try it for themselves, so don't be shy! I'm one person, so maybe I can't catch everything. If you're seeing something that I'm not, I want to hear about it.
And if anyone wants a more visual step by step, you are welcome to yell my way. If this text post is clear enough for everyone, I won't bother, but if a more visual walkthrough will help anyone, then I'm happy to do it!
EDIT: Just tossing in a summary of feedback I've seen from others below!
The tool is pulling from a list of most popular English words, which means it may add inappropriate verbiage to G-rated fics. See this ask for info. trash-prince has made adjustments based on the initial words spotted, but please kindly report any other concerning poison words you find, particularly slurs and other wording that cannot be interpreted in a SFW way.
139 notes
·
View notes
Text
Ice cold take from a decade ago!
"Quality gates are either automatically tool enforced, or they are imaginary"
I am fairly confident in stating that. Because if you claim that your developers will follow the quality gate on their own, you are saying that your people are better developers than the 40 people who got Curiosity to Mars. In this talk by Gerard Holzmann: https://www.usenix.org/conference/hotdep12/workshop-program/presentation/holzmann He shows data, that the programmers who have the highest success rates with rovers on mars, by a LONG shot, do not follow quality gates that was not enforced. So they tested EVERYTHING. To NASA level standards. One of the highest in the world. They made a HUGE codebase. VERY fast. And it was VERY safe. ... and it was cheap. Because clean code is easy to change and easy to write in. And when you get tested seven ways to hell every day, then you have to write robust code. Turns out robust code and testable code is basically the same thing. ALL of the software for that, was written by 40 people. It was CHEAP. So cheap that they barely appeared in the budget. And yet it was tested inside and out constantly and quality gates was enforced with systems
So when your workplace claims that it is simply too expensive to automate the quality gates. Then inform them that it is too expensive to NOT enforce them.
62 notes
·
View notes
Text



Following latest news and developments, the American Coalition for Ukraine, issues statement on the U.S. Administration's Decision to Pause Military Aid to Ukraine Undermines U.S. Security.
For decades, the United States has championed peace through strength. Now, the current Administration’s pause on military aid and intelligence information to Ukraine undermines U.S. interests by signalling retreat to our adversaries. While the battlefield impact of this decision will take weeks to play out, the moral and diplomatic fallout is immediate, and the risk of civilian casualties increases immediately.
Additionally, lifting economic sanctions imposed on Russia would only serve to empower Putin and hand him additional resources to continue his invasion, while making the U.S. look weak and unreliable.
Supporting Ukraine is a smart defense investment. Less than 5% of the U.S. defense budget helped significantly degrade Russia’s military without American boots on the ground. If Ukraine falls, U.S. costs and risks will escalate.
Any pause or disruption of aid to Ukraine helps Putin, weakens NATO, and emboldens America’s adversaries. China may target Taiwan, while Iran and North Korea will test U.S. resolve. Ignoring Russia’s war crimes against Christians, children, and civilians does not represent America’s values of faith and freedom.
The American Coalition for Ukraine calls on the administration to immediately restore military and intelligence aid to Ukraine and pursue peace talks from a position of strength. We urge Congress to represent the will of their constituents, who overwhelmingly support Ukraine and distrust Putin; to act decisively to uphold American values in the face of autocratic aggression; and to continue bipartisan support for Ukraine through military, economic, and humanitarian assistance.
The situation is evolving rapidly, but one thing must continue to grow — the number of calls from Ukraine supporters to Congress.
We urge you to keep calling your representatives. To make this process easier, we have launched an automated tool that allows you to reach your elected officials in just a few clicks. Your voice matters — let’s make it heard!
visit http://americancoalitionforukraine.org for more details, or click the link below for quick access to our online tool.
JOIN RALLIES FOR UKRAINE
In recent days, many of our communities have come together for emergency rallies to demonstrate the broad support Ukraine has among the American people. We invite you to join our rally in Washington, D.C., this weekend or stand with your local community to voice your support for Ukraine.
visit event Facebook page for more details
CONTACT YOUR LOCAL MEDIA
Write a letter to the editor, an op-ed, or reach out to your local radio and TV stations to share your perspective on this critical moment for Ukraine. Your voice matters!
REGISTER FOR UKRAINE ACTION SUMMIT, SPRING 2025
Three years in, Ukraine still fights for its survival. The Ukraine Action Summit is an incredible opportunity to reinforce long-term support for Ukraine at a crucial moment.
Register today to take advantage of early bird pricing—prices increase tomorrow!
Our community of advocates has grown exponentially since the launch of the American Coalition for Ukraine. We are committed to delivering expert-driven advocacy coordination and reliable support for our community, ensuring that all our actions and engagements yield top results. But we need your help to make it happen!
Please donate to support our work for Ukraine!
Zelle email for donations: [email protected]
or use button below to donate via PayPal and CC
22 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
🌎 Scaling The Software Development Process: Lessons Learned from The Sims Online
Scaling The Software Development Process: Lessons Learned from The Sims Online. Greg Kearney, Larry Mellon, Darrin West Spring 2003, GDC. Talk Overview. Covers: Software Engineering techniques to help when projects get big Code structure Work processes (for programmers) Testing
The presentation "Scaling The Software Development Process: Lessons Learned from The Sims Online" (GDC 2003) describes the experience of scaling development processes for a large team. Key lessons include simplifying architecture, minimizing module dependencies, and automating testing to improve stability. Main approaches involved transitioning to a client-server model, using temporary solutions ("Incremental Sync," "Null View"), and maintaining the functionality of the mainline at all times. Tools such as auto-tests ("snifftest") and scriptable play sessions helped reduce errors and accelerate integration. Core principles: simplification (KISS), incremental changes, process measurability, and scaffolding to support parallel work. The presentation emphasizes the importance of adapting processes to team scale and continuously improving tools.
9 notes
·
View notes
Text
Your All-in-One AI Web Agent: Save $200+ a Month, Unleash Limitless Possibilities!
Imagine having an AI agent that costs you nothing monthly, runs directly on your computer, and is unrestricted in its capabilities. OpenAI Operator charges up to $200/month for limited API calls and restricts access to many tasks like visiting thousands of websites. With DeepSeek-R1 and Browser-Use, you:
• Save money while keeping everything local and private.
• Automate visiting 100,000+ websites, gathering data, filling forms, and navigating like a human.
• Gain total freedom to explore, scrape, and interact with the web like never before.
You may have heard about Operator from Open AI that runs on their computer in some cloud with you passing on private information to their AI to so anything useful. AND you pay for the gift . It is not paranoid to not want you passwords and logins and personal details to be shared. OpenAI of course charges a substantial amount of money for something that will limit exactly what sites you can visit, like YouTube for example. With this method you will start telling an AI exactly what you want it to do, in plain language, and watching it navigate the web, gather information, and make decisions—all without writing a single line of code.
In this guide, we’ll show you how to build an AI agent that performs tasks like scraping news, analyzing social media mentions, and making predictions using DeepSeek-R1 and Browser-Use, but instead of writing a Python script, you’ll interact with the AI directly using prompts.
These instructions are in constant revisions as DeepSeek R1 is days old. Browser Use has been a standard for quite a while. This method can be for people who are new to AI and programming. It may seem technical at first, but by the end of this guide, you’ll feel confident using your AI agent to perform a variety of tasks, all by talking to it. how, if you look at these instructions and it seems to overwhelming, wait, we will have a single download app soon. It is in testing now.
This is version 3.0 of these instructions January 26th, 2025.
This guide will walk you through setting up DeepSeek-R1 8B (4-bit) and Browser-Use Web UI, ensuring even the most novice users succeed.
What You’ll Achieve
By following this guide, you’ll:
1. Set up DeepSeek-R1, a reasoning AI that works privately on your computer.
2. Configure Browser-Use Web UI, a tool to automate web scraping, form-filling, and real-time interaction.
3. Create an AI agent capable of finding stock news, gathering Reddit mentions, and predicting stock trends—all while operating without cloud restrictions.
A Deep Dive At ReadMultiplex.com Soon
We will have a deep dive into how you can use this platform for very advanced AI use cases that few have thought of let alone seen before. Join us at ReadMultiplex.com and become a member that not only sees the future earlier but also with particle and pragmatic ways to profit from the future.
System Requirements
Hardware
• RAM: 8 GB minimum (16 GB recommended).
• Processor: Quad-core (Intel i5/AMD Ryzen 5 or higher).
• Storage: 5 GB free space.
• Graphics: GPU optional for faster processing.
Software
• Operating System: macOS, Windows 10+, or Linux.
• Python: Version 3.8 or higher.
• Git: Installed.
Step 1: Get Your Tools Ready
We’ll need Python, Git, and a terminal/command prompt to proceed. Follow these instructions carefully.
Install Python
1. Check Python Installation:
• Open your terminal/command prompt and type:
python3 --version
• If Python is installed, you’ll see a version like:
Python 3.9.7
2. If Python Is Not Installed:
• Download Python from python.org.
• During installation, ensure you check “Add Python to PATH” on Windows.
3. Verify Installation:
python3 --version
Install Git
1. Check Git Installation:
• Run:
git --version
• If installed, you’ll see:
git version 2.34.1
2. If Git Is Not Installed:
• Windows: Download Git from git-scm.com and follow the instructions.
• Mac/Linux: Install via terminal:
sudo apt install git -y # For Ubuntu/Debian
brew install git # For macOS
Step 2: Download and Build llama.cpp
We’ll use llama.cpp to run the DeepSeek-R1 model locally.
1. Open your terminal/command prompt.
2. Navigate to a clear location for your project files:
mkdir ~/AI_Project
cd ~/AI_Project
3. Clone the llama.cpp repository:
git clone https://github.com/ggerganov/llama.cpp.git
cd llama.cpp
4. Build the project:
• Mac/Linux:
make
• Windows:
• Install a C++ compiler (e.g., MSVC or MinGW).
• Run:
mkdir build
cd build
cmake ..
cmake --build . --config Release
Step 3: Download DeepSeek-R1 8B 4-bit Model
1. Visit the DeepSeek-R1 8B Model Page on Hugging Face.
2. Download the 4-bit quantized model file:
• Example: DeepSeek-R1-Distill-Qwen-8B-Q4_K_M.gguf.
3. Move the model to your llama.cpp folder:
mv ~/Downloads/DeepSeek-R1-Distill-Qwen-8B-Q4_K_M.gguf ~/AI_Project/llama.cpp
Step 4: Start DeepSeek-R1
1. Navigate to your llama.cpp folder:
cd ~/AI_Project/llama.cpp
2. Run the model with a sample prompt:
./main -m DeepSeek-R1-Distill-Qwen-8B-Q4_K_M.gguf -p "What is the capital of France?"
3. Expected Output:
The capital of France is Paris.
Step 5: Set Up Browser-Use Web UI
1. Go back to your project folder:
cd ~/AI_Project
2. Clone the Browser-Use repository:
git clone https://github.com/browser-use/browser-use.git
cd browser-use
3. Create a virtual environment:
python3 -m venv env
4. Activate the virtual environment:
• Mac/Linux:
source env/bin/activate
• Windows:
env\Scripts\activate
5. Install dependencies:
pip install -r requirements.txt
6. Start the Web UI:
python examples/gradio_demo.py
7. Open the local URL in your browser:
http://127.0.0.1:7860
Step 6: Configure the Web UI for DeepSeek-R1
1. Go to the Settings panel in the Web UI.
2. Specify the DeepSeek model path:
~/AI_Project/llama.cpp/DeepSeek-R1-Distill-Qwen-8B-Q4_K_M.gguf
3. Adjust Timeout Settings:
• Increase the timeout to 120 seconds for larger models.
4. Enable Memory-Saving Mode if your system has less than 16 GB of RAM.
Step 7: Run an Example Task
Let’s create an agent that:
1. Searches for Tesla stock news.
2. Gathers Reddit mentions.
3. Predicts the stock trend.
Example Prompt:
Search for "Tesla stock news" on Google News and summarize the top 3 headlines. Then, check Reddit for the latest mentions of "Tesla stock" and predict whether the stock will rise based on the news and discussions.
--
Congratulations! You’ve built a powerful, private AI agent capable of automating the web and reasoning in real time. Unlike costly, restricted tools like OpenAI Operator, you’ve spent nothing beyond your time. Unleash your AI agent on tasks that were once impossible and imagine the possibilities for personal projects, research, and business. You’re not limited anymore. You own the web—your AI agent just unlocked it! 🚀
Stay tuned fora FREE simple to use single app that will do this all and more.

7 notes
·
View notes
Text
Best Practices for Test Management in a Continuous Integration/Delivery (CI/CD) Environment
Introduction
Start by explaining the role of Continuous Integration (CI) and Continuous Delivery (CD) in modern software development. Emphasize that effective test management is crucial to maintaining quality in fast-paced, automated pipelines.
Early and Continuous Testing
Implement testing at every stage of the CI/CD pipeline, starting from the earliest phases. Unit, integration, and functional tests should be run continuously to catch defects early.
Automation Integration
Test automation is vital for CI/CD environments. Ensure that all repetitive tests, such as regression tests, are automated. Use tools like Selenium, Jenkins, and Travis CI to integrate automated tests into the pipeline.
Effective Test Case Management
Organize test cases in a way that they can be easily maintained and executed in CI/CD pipelines. Regularly review and update test cases to ensure they are relevant and up-to-date.
Use of Test Management Tools
Leverage test management tools like TestRail or Zephyr that integrate with CI/CD platforms. This ensures seamless tracking, reporting, and scheduling of tests within the automated process.
Monitoring and Reporting
Set up real-time monitoring and reporting for continuous feedback on test results. This helps in quickly identifying issues and improving collaboration between developers and QA teams.
Conclusion
Summarize by stating that efficient test management in a CI/CD environment enhances the speed and reliability of software delivery while maintaining high-quality standards.
#test management#test management software#test management tools#test management tools in software testing#test mgmt#test project#codeless test automation#codeless testing platform#test automation software#automated qa testing#no code test automation tools
2 notes
·
View notes
Text
Everyone is cheating their way through college: ChatGPT has unraveled the entire academic project
James D. Walsh at New York Intelligencer writes a deeply researched article on how students at “large state schools, the Ivies, liberal-arts schools in New England, universities abroad, professional schools, and community colleges” … “are relying on AI to ease their way through every facet of their education…. take their notes during class, devise their study guides and practice tests, summarize novels and textbooks, and brainstorm, outline, and draft their essays. STEM students are using AI to automate their research and data analyses and to sail through dense coding and debugging assignments. ‘College is just how well I can use ChatGPT at this point,’ [said a Utah student].”
If you cheat your way through college, are you cheating yourself? Robbing yourself of the education you’re paying tens of thousands of years for? Or is college just a gate you pass through to get to a higher-paying job and higher social status?
[Troy Jollimore, a poet, philosopher, and Cal State Chico ethics professor,] who has been teaching writing for more than two decades, is now convinced that the humanities, and writing in particular, are quickly becoming an anachronistic art elective like basket-weaving. “Every time I talk to a colleague about this, the same thing comes up: retirement. When can I retire? When can I get out of this? That’s what we’re all thinking now,” he said. “This is not what we signed up for.” Williams, and other educators I spoke to, described AI’s takeover as a full-blown existential crisis. “The students kind of recognize that the system is broken and that there’s not really a point in doing this. Maybe the original meaning of these assignments has been lost or is not being communicated to them well.”
He worries about the long-term consequences of passively allowing 18-year-olds to decide whether to actively engage with their assignments. Would it accelerate the widening soft-skills gap in the workplace? If students rely on AI for their education, what skills would they even bring to the workplace? Lakshya Jain, a computer-science lecturer at the University of California, Berkeley, has been using those questions in an attempt to reason with his students. “If you’re handing in AI work,” he tells them, “you’re not actually anything different than a human assistant to an artificial-intelligence engine, and that makes you very easily replaceable. Why would anyone keep you around?” That’s not theoretical: The COO of a tech research firm recently asked Jain why he needed programmers any longer.
(Emphasis added by me.)
GenAI is a great assistant but if using GenAI is your only skill, why would anyone hire you?
GenAI is like Microsoft Office: It’s a tool. Everybody who works at a desk job nowadays needs to know how to use Office or its Google equivalent, but if using Office is all you know how to do, then you have no job skills.
The ideal of college as a place of intellectual growth, where students engage with deep, profound ideas, was gone long before ChatGPT. The combination of high costs and a winner-takes-all economy had already made it feel transactional, a means to an end. (In a recent survey, Deloitte found that just over half of college graduates believe their education was worth the tens of thousands of dollars it costs a year, compared with 76 percent of trade-school graduates.) In a way, the speed and ease with which AI proved itself able to do college-level work simply exposed the rot at the core. “How can we expect them to grasp what education means when we, as educators, haven’t begun to undo the years of cognitive and spiritual damage inflicted by a society that treats schooling as a means to a high-paying job, maybe some social status, but nothing more?” Jollimore wrote in a recent essay. “Or, worse, to see it as bearing no value at all, as if it were a kind of confidence trick, an elaborate sham?”
The article features Chungin “Roy” Lee, a twenty-something AI entrepreneur who has built tools — and businesses based on them — to enable people to use AI to cheat at college, on job interviews and even on dates.
“Every technological innovation has caused humanity to sit back and think about what work is actually useful,” [Lee] said. “There might have been people complaining about machinery replacing blacksmiths in, like, the 1600s or 1800s, but now it’s just accepted that it’s useless to learn how to blacksmith.”
If writing is going to be obsolete, like basket-weaving and blacksmithing, then so be it. I don’t worry about it. I write to set my thoughts in order, and I don’t anticipate stopping that.
As for work: If writing ceases to become a marketable skill … well, I’ll figure something out. “I’ll figure something out” has been a theme of my career.
4 notes
·
View notes
Text
Python for Beginners: Launch Your Tech Career with Coding Skills
Are you ready to launch your tech career but don’t know where to start? Learning Python is one of the best ways to break into the world of technology—even if you have zero coding experience.
In this guide, we’ll explore how Python for beginners can be your gateway to a rewarding career in software development, data science, automation, and more.
Why Python Is the Perfect Language for Beginners
Python has become the go-to programming language for beginners and professionals alike—and for good reason:
Simple syntax: Python reads like plain English, making it easy to learn.
High demand: Industries spanning the spectrum are actively seeking Python developers to fuel their technological advancements.
Versatile applications: Python's versatility shines as it powers everything from crafting websites to driving artificial intelligence and dissecting data.
Whether you want to become a software developer, data analyst, or AI engineer, Python lays the foundation.
What Can You Do With Python?
Python is not just a beginner language—it’s a career-building tool. Here are just a few career paths where Python is essential:
Web Development: Frameworks like Django and Flask make it easy to build powerful web applications. You can even enroll in a Python Course in Kochi to gain hands-on experience with real-world web projects.
Data Science & Analytics: For professionals tackling data analysis and visualization, the Python ecosystem, featuring powerhouses like Pandas, NumPy, and Matplotlib, sets the benchmark.
Machine Learning & AI: Spearheading advancements in artificial intelligence development, Python boasts powerful tools such as TensorFlow and scikit-learn.
Automation & Scripting: Simple yet effective Python scripts offer a pathway to amplified efficiency by automating routine workflows.
Cybersecurity & Networking: The application of Python is expanding into crucial domains such as ethical hacking, penetration testing, and the automation of network processes.
How to Get Started with Python
Starting your Python journey doesn't require a computer science degree. Success hinges on a focused commitment combined with a thoughtfully structured educational approach.
Step 1: Install Python
Download and install Python from python.org. It's free and available for all platforms.
Step 2: Choose an IDE
Use beginner-friendly tools like Thonny, PyCharm, or VS Code to write your code.
Step 3: Learn the Basics
Focus on:
Variables and data types
Conditional statements
Loops
Functions
Lists and dictionaries
If you prefer guided learning, a reputable Python Institute in Kochi can offer structured programs and mentorship to help you grasp core concepts efficiently.
Step 4: Build Projects
Learning by doing is key. Start small:
Build a calculator
Automate file organization
Create a to-do list app
As your skills grow, you can tackle more complex projects like data dashboards or web apps.
How Python Skills Can Boost Your Career
Adding Python to your resume instantly opens up new opportunities. Here's how it helps:
Higher employability: Python is one of the top 3 most in-demand programming languages.
Better salaries: Python developers earn competitive salaries across the globe.
Remote job opportunities: Many Python-related jobs are available remotely, offering flexibility.
Even if you're not aiming to be a full-time developer, Python skills can enhance careers in marketing, finance, research, and product management.
If you're serious about starting a career in tech, learning Python is the smartest first step you can take. It’s beginner-friendly, powerful, and widely used across industries.
Whether you're a student, job switcher, or just curious about programming, Python for beginners can unlock countless career opportunities. Invest time in learning today—and start building the future you want in tech.
Globally recognized as a premier educational hub, DataMites Institute delivers in-depth training programs across the pivotal fields of data science, artificial intelligence, and machine learning. They provide expert-led courses designed for both beginners and professionals aiming to boost their careers.
Python Modules Explained - Different Types and Functions - Python Tutorial
youtube
#python course#python training#python#learnpython#pythoncourseinindia#pythoncourseinkochi#pythoninstitute#python for data science#Youtube
3 notes
·
View notes
Text
How to Identify a Bug in Software Testing
Identifying a bug in software testing is an important part of ensuring the quality and reliability of a software application. Here are some steps to help you identify bugs effectively:
Understand the Requirements: Familiarize yourself with the software's requirements and expected behavior. This will help you identify any deviations from the intended functionality.
Create Test Cases: Develop a set of test cases based on the requirements. Test cases should cover various scenarios, inputs, and edge cases. Well-designed test cases increase the likelihood of discovering bugs.
Execute Test Cases: Execute the test cases systematically, following the test plan. This involves performing actions, entering inputs, and verifying expected outcomes.
Observe the Software: Pay close attention to the behavior of the software during test execution. Look for any unexpected or incorrect behavior, such as crashes, error messages, or incorrect results.
Record Issues: When you encounter a potential bug, document it immediately. Include details such as steps to reproduce the bug, expected and actual results, and any error messages or log entries. Clear and concise bug reports help developers understand and fix the issues.
Analyze Test Results: After executing all the test cases, review the overall test results. Look for patterns or recurring issues that could indicate a bug or a larger problem.
Prioritize Bugs: Assess the severity and impact of each bug you've identified. Categorize them based on their urgency and potential impact on the software's functionality. This will help prioritize bug fixes.
Reproduce Bugs: Whenever possible, try to reproduce the bugs on different environments or configurations. Reproducing a bug in multiple instances increases its reliability and helps developers understand the root cause.
Communicate with the Development Team: Share your bug reports with the development team. Provide them with all the necessary information, including steps to reproduce the bug and any relevant log files or screenshots. Maintain open communication to clarify any questions or provide additional details.
Retest Fixes: After the development team addresses the reported bugs, perform regression testing to ensure that the fixes did not introduce new issues.
Remember, effective bug identification requires attention to detail, good communication skills, and a thorough understanding of the software's requirements. By following these steps, you can contribute to improving the quality and reliability of the software you are testing.
For More Details On This Topic Visit The Link Here: How to Identify a Bug in Software Testing
Robonito Is a no-code automation testing tool for software and web apps that can automate your software testing
#software testing#testing#web application#no code automation testing tool#software testing tool#robonito#RPA
1 note
·
View note
Text
Programming object lesson of the day:
A couple days ago, one of the side project apps I run (rpthreadtracker.com) went down for no immediately obvious reason. The issue seems to have ended up being that the backend was running on .NET Core 2.2, which the host was no longer supporting, and I had to do a semi-emergency upgrade of all the code to .NET Core 6, a pretty major update that required a lot of syntactic changes and other fixes.
This is, of course, an obvious lesson in keeping an eye on when your code is using a library out of date enough not to be well supported anymore. (I have some thoughts on whether .NET Core 2.2 is old enough to have been dumped like this, but nevertheless I knew it was going out of LTS and could have been more prepared.) But that's all another post.
What really struck me was how valuable it turned out to be that I had already written an integration test suite for this application.
Historically, at basically every job I've worked for and also on most of my side projects, automated testing tends to be the thing most likely to fall by the wayside. When you have 376428648 things you want to do with an application and only a limited number of hours in the day, getting those 376428648 things to work feels very much like the top priority. You test them manually to make sure they work, and think, yeah, I'll get some tests written at some point, if I have time, but this is fine for now.
And to be honest, most of the time it usually is fine! But a robust test suite is one of those things that you don't need... until you suddenly REALLY FUCKING NEED IT.
RPTT is my baby, my longest running side project, the one with the most users, and the one I've put the most work into. So in a fit of side project passion and wanting to Do All The Right Things For Once, I actively wrote a massive amount of tests for it a few years ago. The backend has a full unit test suite that is approaching 100% coverage (which is a dumb metric you shouldn't actually stress about, but again, a post for another day). I also used Postman, an excellently full-featured API client, to write a battery of integration tests which would hit all of the API endpoints in a defined order, storing variables and verifying values as it went to take a mock user all the way through their usage life cycle.
And goddamn was that useful to have now, years later, as I had to fix a metric fuckton of subtle breakage points while porting the app to the updated framework. With one click, I could send the test suite through every endpoint in the backend and get quick feedback on everywhere that it wasn't behaving exactly the way it behaved before the update. And when I was ready to deploy the updated version, I could do so with solid confidence that from the front end's perspective, nothing would be different and everything would slot correctly into place.
I don't say this at all to shame anyone for not prioritizing writing tests - I usually don't, especially on my side projects, and this was a fortuitous outlier. But it was a really good reminder of why tests are a valuable tool in the first place and why they do deserve to be prioritized when it's possible to do so.
#bjk talks#coding#codeblr#programming#progblr#web development#I'm trying to finally get back to streaming this weekend so maybe the upcoming coding stream will be about#setting up one of these integration test suites in postman
78 notes
·
View notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
�� Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes