#networkpenetrationtesting
Explore tagged Tumblr posts
Text

Network Penetration Testing . . . . for more information and tutorial https://bit.ly/3BRXxk8 check the above link
0 notes
Photo

The Best Network Penetration Course Online in India
Cyber radar University is the best University in India, university offering the best certified network penetration course online for beginners and professionals. Here you can learn about performing OS flag, administration, and client count.
#penetrationtestingtraining#penetrationtestingonlinecourse#networkpenetrationtesting#penetrationtesting#ethicalhackingandpenetrationtestingguide
3 notes
·
View notes
Link
How to Choose a Software Penetration Testing Vendor? Find out what factors you need to consider when choosing a software penetration testing vendor for your company. You should not miss these 5 key factors.
0 notes
Text
Penetration testing – making your software impenetrable

The global march of digitization continues unabated. As a consequence, it has brought attributes like convenience, speedy delivery, a slew of options to choose from, and cost-effectiveness like never before, for the users. However, with technology and its myriad benefits comes the curse of security breaches. If on one side, new technology are breaking new thresholds, on the other, hackers are finding novel means of intrusion and siphoning off data and information. Also, with workplaces becoming the hub for information access through digital devices, people often show scant regard for security protocols. This allows hackers the opportunity to penetrate the IT infrastructure of a company and steal valuable data.
According to Gartner, the global spending on cybersecurity is projected to touch a whopping $133.7 billion in 2022. Does this make the global IT systems secure? The answer is both yes and no. Yes because the security mechanisms complying with industry regulations have created a strong deterrence for hackers. However, since users are often the weakest link in the whole value chain, their lackadaisical attitude regarding security has often given hackers the opportunity to strike gold. The annual official report of Cybersecurity Ventures has pegged the damages due to cybercrime at 6 trillion by 2021. With so much at stake, enterprises have no escape but to adopt penetration testing and secure their systems.
What is Penetration Testing?
Also known as pen testing or ethical hacking, the testing process looks into a computer system, web application, or network to search for security related vulnerabilities. It can either be performed manually or by using a test automation software. It goes beyond regular compliance audits or security assessments. Let us see how software penetration testing is different.
· The testing process simulates a real attack to check how databases, financial assets, or business systems would be impacted. It helps security experts to identify the vulnerable areas in a system.
· Application penetration testing checks the ability of any IT system to detect security breaches in real time.
· Even though a major part of the testing process involves automation, experienced professionals aka ethical hackers majorly do pen test. These people analyze IT systems in the same way a hacker would.
· Hackers always look for vulnerabilities or gaps between the use of security tools often created due to their incompatibility. A pen test uncovers such vulnerabilities.
· It reveals vulnerabilities that might have been overlooked during routine testing.
· Software penetration testing helps an enterprise comply with existing regulations.
How to conduct penetration testing
Testers conducting pen testing begin with analyzing the business, its IT infrastructure, and entry points. They try breaking into the system and report on their experience. Also known as white-hat attacks, these help a business to identify the potential weak points that can be exploited by a real hacker. The various steps are as follows:
Testers providing penetration testing services often work in tandem with the tech/information team of an enterprise. Together they simulate targeted attacks and analyse the findings.
· They try hacking into resources such as domain name servers, email servers, and web servers. Also known as external tests, these reveal how far a real hacker can penetrate into the system.
· Internal testing is all about identifying the gaps behind a firewall. Here, testers use the same level of authorization and access that employees possess. This way they can find out the weak points in a system, which any hacker or disgruntled employee can exploit.
· Another method employed by testers doing network penetration testing is blind testing. Here, testers execute the task at hand with very little information about the system. For example, they might be provided with only the website URL or name of the company. If testers are able to ferret out more information about the company, the greater would be the security risks.
In double-blind testing, only one or two testers know about the process being conducted. This generates the most unbiased results as people using the system continue to remain careless while going about their tasks. It helps to evaluate security awareness and the response of protocols.
Conclusion
Cybercrime has assumed menacing proportions. It has the ability to undermine user confidence in an organization by targeting its systems, databases, and servers. In a digital ecosystem where everything is getting increasingly connected, the quality of its security architecture should be top-notch. Penetration testing helps to unearth any hidden vulnerabilities in an IT system and provides valuable information about the ways to mitigate them.
0 notes
Photo

Zero day DDOS vulnerability in Mozilla mozjpeg with no patch available | MrHacker.Co #cybersecurity #hacking #mozilla #mozjpeg #networkpenetrationtesting #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

Honda suffers ransomware virus attack; car production stopped in some plants #cybersecurity #hacking #honda #malware #networkpenetrationtesting #ransomware #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Hacking Linux servers remotely with this Pi-hole vulnerability | TheHackerNews.Co #adblockers #cybersecurity #hacking #networkpenetrationtesting #pi-hole #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Link
Cyber radar academy is offering a Network penetration course, that can train anyone starting from basic to advanced level
#penetrationtestingtraining#penetrationtestingonlinecourse#networkpenetrationtesting#penetrationtesting
1 note
·
View note
Text

Gray Hat Hacker . . . visit: https://bit.ly/3BRXxk8 for more information
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Text

White Hat Hacker . . . visit: https://bit.ly/3BRXxk8 for more information
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Text

Black Hat Hacker . . . visit: https://bit.ly/3BRXxk8 for more information
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Text
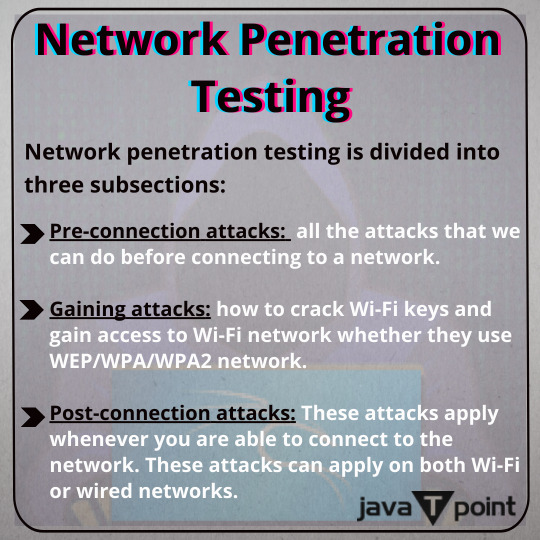
Network penetration testing . . . visit: https://bit.ly/3Gcb1cK for more information
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Text
Types of Hackers . . . visit: https://bit.ly/3BRXxk8 for more information
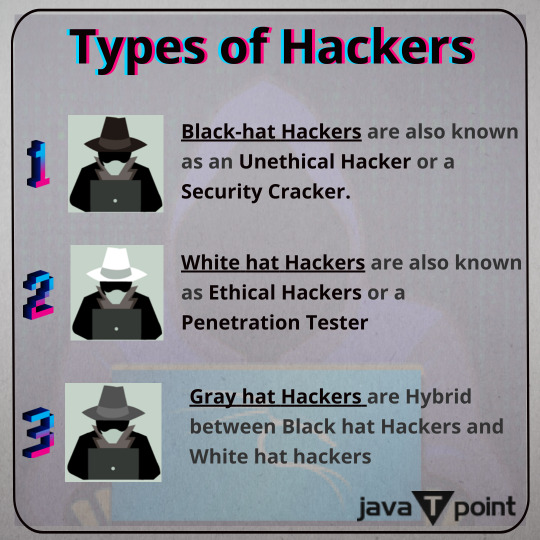
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Text

Ethical Hacking . . . visit: https://bit.ly/3BUouDK for more information
#EthicalHacking#whitehathacking#penetrationtesting#blackhathacker#whitehathacker#greyhathacker#networkpenetrationtesting#networkpenetration#javatpoint
0 notes
Photo

Online The Best Network Penetration Course
Cyber radar University is a top university in the world and we provide the best network penetration course online. And this University fully-online training solutions you can be studied in your own place and at your own time.
#penetrationtestingtraining#penetrationtestingonlinecourse#networkpenetrationtesting#penetrationtesting#ethicalhackingandpenetrationtestingguide
0 notes
Photo

Latest Trending Network Penetration Testing Course
Cyber Radar University provides the best network penetration testing course to who secure their network of systems from breaches. And if you want to that your organization's not exploiting the vulnerabilities.
#penetrationtestingtraining#penetrationtestingonlinecourse#networkpenetrationtesting#penetrationtesting#ethicalhackingandpenetrationtestingguide
0 notes