#management software enables
Explore tagged Tumblr posts
Text
Smart Parking Management Software | Parkomax Streamline your parking operations with Parkomax's advanced parking management software. Real-time monitoring, automated access, and seamless reporting in one platform.
#Parking Management Software#Smart Parking System#Automated Parking Software#Parking Control System#Parking Lot Management Software#Cloud-based Parking Software#Parking Garage Management System#Parking Access Control#Parking Operations Software#Digital Parking Solutions#Parkomax parking software#IoT-enabled parking system#Parking analytics and reporting tool#Multi-location parking management solution#Parking ticketing and billing automation
0 notes
Text
illumine Breaks Down the Real Childcare Cost by State Across the USA
Childcare is one of the biggest expenses for working families in the United States, and the numbers continue to rise every year. Whether you’re a parent searching for the best daycare option or a childcare provider trying to stay competitive, understanding the true childcare cost landscape is essential.
Here, we explore the mean price of daycare across various states of the U.S., what makes them what they are, and what can be done by parents and providers to better manage them. Backed by information from illumine — a well-known childcare management platform — this is your primer to understand how prices differ by state and what that means for the future of early childhood education.
Why Childcare Costs Are Rising in the U.S. The childcare costs in the U.S. have seen a consistent upward trend over the past decade. While inflation and cost of living contribute to this rise, several other factors also play a major role:
Labor Shortages (in the childcare industry)
Licensing and Compliance Costs
Real Estate and Facility Costs
Increased Demand for High-Quality Care
Strict Health & Safety Regulations Post-COVID
As a result, daycare centers are left balancing affordability with quality — a challenge that continues to grow each year.
National Average Daycare Cost The national average yearly cost of daycare for one child ranges from $9,000 to $22,000, depending on location, age, and kind of care, reports the Economic Policy Institute. Infant care is usually higher in cost than toddler care because more staff-to-child ratios and other requirements are involved.
Rapid summary: -Infant Daycare: $1,230/month (national average) -Toddler Daycare: $990–$1,100/month -Preschool Age (3–5 years): $800–$950/month
These figures are quite disparate state by state.
State-by-State Comparison of Childcare Cost Let’s look at how childcare costs differ across the U.S., from the most expensive to the most affordable states:
Most Expensive States for Daycare:
-Massachusetts — Average annual cost: $20,913 -California — Average annual cost: $16,945 -New York — Average annual cost: $15,394 -Connecticut — Average annual cost: $14,682 -Washington, D.C. — Average annual cost: $21,678
In these states, the daycare cost often surpasses college tuition, making childcare a major budgetary burden for families.
More Affordable States for Daycare:
-Mississippi — Average annual cost: $5,436 -Alabama — Average annual cost: $6,001 -South Carolina — Average annual cost: $6,612 -Louisiana — Average annual cost: $6,960 -Kentucky — Average annual cost: $7,112
These numbers reflect the differences in cost of living, wages, and operational costs between states.
Factors That Influence Daycare Cost Though state location is a major factor in the cost of childcare, there are other factors affecting it:
1. Child’s Age: Care for infants is much more costly than care for preschoolers because of staffing requirements and licensing regulations. 2. Center Type: Private preschools or Montessori centers are more expensive than home-based or public daycare. 3. Urban/Rural Segregation: Urban areas tend to have higher daycare prices, whereas rural communities can provide cheaper care — although the choices can be limited. 4. Licensing and Accreditation: Those with national accreditations can be more expensive, but so are the better-quality services and safety precautions. 5. Extra Services: Services that provide meals, transportation, enrichment activities, or extended hours will add to the overall cost of daycare.
How High Childcare Costs Affect Families For many families, childcare costs account for 20–30% of their monthly income, far exceeding the 7% affordability benchmark set by the U.S. Department of Health and Human Services.

This has several effects:
-Reduced Workforce Participation: Many parents (especially mothers) leave the workforce because care is too expensive. -Delayed Family Planning: High daycare costs can discourage couples from having more children. -Increased Financial Strain: Families may cut back on essentials or savings to afford childcare.
What Childcare Providers Can Do Childcare centers are also feeling the pressure — they must balance offering affordable rates while covering operating costs and maintaining high-quality care.
Here are a few ways providers can adapt:
1. Adopt Digital Tools Like illumine: Using tools like illumine’s childcare management software can reduce admin workload, streamline billing, and improve communication with parents — helping centers operate more efficiently. 2. Flexible Pricing Models: Offering part-time care, sibling discounts, or sliding scale pricing can attract more families. 3. Government Programs: Leveraging subsidies and public funding can help centers lower prices for eligible families without losing revenue.
The Role of illumine in Managing Daycare Operations illumine is a leading childcare software solution that helps daycare centers digitize and simplify operations. With features like automated billing, parent communication tools, attendance tracking, and enrollment management software, illumine helps reduce costs and streamline processes.
Here’s how illumine adds value:
-Enabling contactless attendance with real-time tracking -Simplifying parent engagement with a built-in communication app -Managing waitlists and inquiries through its powerful enrollment management software -Automating invoicing and payments, saving admin hours
This digital transformation not only improves service quality but also allows providers to focus more on what matters — delivering excellent care.
Tips for Parents to Handle Childcare Costs While providers strive for efficiency, families too can take some measures to cope with the increasing childcare expense:
-Seek Subsidies and Tax Credits: Initiatives such as the Child and Dependent Care Tax Credit or state subsidies can bring much relief. -Flexible Spending Accounts (FSAs): A few employers provide FSAs that enable parents to save pre-tax dollars for childcare. -Consider Shared or Cooperative Care Models: Nanny-sharing or in-home care co-ops can offer cheaper options. -Negotiate Schedules with Employers: Flexible or work-from-home options can minimize the demand for full-time care.
What the Future Holds for Childcare in America As awareness around childcare costs continues to grow, there is increasing pressure on lawmakers, providers, and employers to find more sustainable solutions.
The future might possibly bring:
-More Government Funding -Universal Preschool Programs -Public-Private Partnerships -Expansion of Employer-Sponsored Childcare Benefits
But while policy takes shape, technology and innovative business models — like those powered by illumine — are leading the way toward more accessible, affordable, and high-quality care.
Conclusion: Understanding and Navigating Daycare Costs Daycare fees are becoming an increasing worry for providers and families. By knowing why these fees are rising and looking at digital resources and flexible care, a balance can be achieved.
Whether you’re a parent budgeting for your childcare or a centre looking to do things more economically, tools like illumine’s child care enrollment management software can be of assistance. illumine works with 3,000+ childcare services across the globe, providing the tools they need to succeed in a competitive, rapidly evolving, and future-ready environment.
To discover how illumine can assist your preschool or daycare in streamlining operations and containing costs better, visit illumine.app.
#illumine app#Automating invoicing and payments#Managing waitlists and inquiries#Simplifying parent engagement#Enabling contactless attendance#childcare management software#daycare cost#childcare costs in the U.S.
0 notes
Text
Smart Parking Space Solutions for Property Owners: Maximize Revenue and Enhance Tenant Satisfaction
More than an added convenience, parking spaces are a critical asset for property owners. Whether you manage a residential building, a commercial complex, or a mixed-use property, optimizing parking management can lead to increased tenant satisfaction, improved security, and a significant boost in revenue.
At LotPilot, we specialize in smart, scalable parking solutions designed specifically for property owners, helping you make the most out of every square foot. Let’s explore why a professional parking space solution is essential and how LotPilot can transform your property management experience.
The Growing Need for Effective Parking Solutions
Urbanization continues to rise, with more vehicles on the road than ever before. For property owners, this presents both an opportunity and a challenge.
Limited Space, High Demand: Parking spaces are often limited, making efficient management crucial.
Tenant Expectations: Residents and businesses now expect seamless, tech-enabled parking experiences.
Revenue Opportunities: Unused or inefficiently managed parking lots represent a significant loss of potential income.
Security Concerns: Unauthorized access and vehicle safety are top priorities for property owners and tenants alike.
To stay competitive, it’s vital to offer a parking experience that is smooth, secure, and profitable.
Key Benefits of Smart Parking Space Solutions for Property Owners
Adopting a specialized parking solution like LotPilot offers several advantages:
1. Maximize Revenue Potential
With automated parking management, you can easily monetize every parking slot. Dynamic pricing, visitor management, and subscription models allow you to generate consistent income without the need for manual oversight.
2. Increase Property Value
Properties with organized, tech-driven parking facilities have a distinct advantage in the market. A professionally managed parking system signals modernity, security, and convenience to potential buyers or renters.
3. Enhance Tenant and Visitor Experience
A smart parking system eliminates the frustration of searching for available spots. Tenants and visitors enjoy easy entry and exit, real-time space availability, and mobile app integrations for reservations and payments.
4. Boost Security and Control
Integrate license plate recognition (LPR), access control systems, and real-time surveillance to ensure only authorized vehicles can enter. Detailed reporting provides insights into parking usage patterns, helping you enhance overall property security.
5. Efficient Space Management
With automated tracking, property owners can manage spaces more effectively, distinguishing between resident parking, guest parking, and even allocating premium spots at higher rates.
How LotPilot Delivers the Ideal Parking Solution for Property Owners
LotPilot’s parking space solutions are tailored to meet the diverse needs of property owners across residential, commercial, and mixed-use properties. Here’s how we can make a difference:
Customizable Parking Systems
Every property is unique. That’s why LotPilot offers modular solutions — from barrier gates and ticketless entry systems to full-stack smart parking management software. Whether you need simple space monitoring or complete automation, we adapt to your needs.
Real-time Parking Guidance
Our real-time parking availability system helps drivers quickly find open spaces, reducing congestion within your property and improving overall traffic flow.
Easy Integration
LotPilot’s technology is designed for seamless integration with existing property management systems. Manage parking allocations, payments, and access control — all from a centralized dashboard.
Automated Payment Systems
Say goodbye to cash collections and manual invoicing. LotPilot offers multiple cashless payment options, including mobile apps, QR codes, and smart cards, making transactions effortless for tenants and visitors.
Data-driven Insights
Our platform provides detailed analytics and reporting, giving property owners valuable insights into space utilization, peak hours, revenue generation, and operational efficiency.
Visitor Management Made Simple
Manage visitor parking with ease. Tenants can pre-register guests, and visitors receive digital permits for a seamless parking experience without long queues or delays.
Why Choose LotPilot?
Scalability: Whether you manage a single building or multiple properties, our solutions grow with you.
Support: Dedicated customer service and technical support ensure your parking system runs smoothly at all times.
Innovation: The latest parking technology to keep your property at the forefront of smart trends.
Future-proof Your Property with Smart Parking Solutions
LotPilot empowers property owners to unlock the full potential of their parking spaces with innovative, secure, and revenue-boosting solutions. Whether you're upgrading an old lot or setting up a new facility, our smart parking technologies make it easy to stay ahead of the competition.
Ready to take control of your parking spaces?
Discover how we can transform your parking lot into a hassle-free, profitable space.
#Smart parking solutions for property owners#Parking management system for residential buildings#Commercial parking management solutions#Automated parking system for properties#Property owner parking software#Parking revenue optimization#Parking space management for buildings#Real-time parking availability system#Digital parking solutions#Tech-enabled parking system
0 notes
Text
The Biggest Mistakes Companies Make When Hiring B2B Sales Talents
Hiring the right B2B sales talent is one of the most critical decisions a company can make. A skilled sales team can drive revenue, build strong client relationships, and contribute to business growth. However, making the wrong hiring choices can lead to lost opportunities, wasted resources, and high turnover rates.
Many companies unknowingly fall into common hiring pitfalls that prevent them from securing top sales talent. From focusing too much on industry experience to neglecting soft skills and cultural fit, these mistakes can significantly impact a company's sales success.
In this article, we'll explore the biggest hiring mistakes companies make when B2B sales recruiters professionals and how to avoid them.

1. Lack of a Clear Hiring Strategy
One of the biggest mistakes companies make is not having a well-defined hiring strategy. Many organizations rush the hiring process, hoping to fill vacant sales positions quickly without a structured approach. This leads to hiring candidates who may not be the best fit for the role.
A clear hiring strategy should include:
A detailed job description outlining responsibilities and expectations
A structured interview process with predefined evaluation criteria
A focus on long-term fit rather than just immediate sales performance
Without a solid hiring plan, companies risk hiring sales professionals who lack the skills, motivation, or cultural alignment needed for success. Taking the time to develop a strategic approach can prevent costly hiring mistakes.
2. Overemphasizing Industry Experience
Many companies mistakenly believe that hiring sales professionals with extensive industry experience is the key to success. While industry knowledge is valuable, it does not necessarily guarantee strong sales performance.
Sales skills such as persuasion, communication, and negotiation are often more important than prior industry experience. Candidates with a strong sales background but limited industry knowledge can quickly learn the specifics of a new field.
A balanced hiring approach should consider:
A candidate’s ability to learn and adapt
Proven sales success in previous roles
A mix of industry knowledge and transferable sales skills
Instead of solely focusing on past industry experience, companies should prioritize raw sales talent and potential.
3. Ignoring Soft Skills and Emotional Intelligence
B2B Sales Recruitment Agency are about building relationships, understanding customer needs, and communicating effectively. While technical knowledge and sales experience are important, soft skills and emotional intelligence (EQ) play an equally vital role in sales success.
Key soft skills to look for in B2B sales candidates include:
Active listening and empathy
Strong communication and interpersonal skills
The ability to handle rejection and stay resilient
Emotional intelligence helps sales professionals connect with prospects, navigate objections, and close deals. Companies that overlook these qualities may end up with sales reps who struggle to build meaningful client relationships.
4. Poorly Defined Sales Metrics and Goals
Without clear performance expectations, it’s difficult to hire and manage a successful sales team. Many companies fail to establish measurable goals and key performance indicators (KPIs) before hiring, leading to confusion and misaligned expectations.
Effective sales hiring should involve:
Setting clear revenue targets and quotas
Defining success metrics such as conversion rates and pipeline growth
Aligning compensation with performance goals
By clearly defining sales objectives, companies can attract candidates who understand expectations and are motivated to achieve results.
5. Relying Too Much on Resumes and Interviews
Traditional hiring methods, such as reviewing resumes and conducting interviews, do not always reveal a candidate’s true sales potential. A polished resume may highlight impressive achievements, but it doesn’t guarantee that a candidate can deliver results in a real-world sales environment.
Alternative evaluation methods include:
Role-playing exercises to test sales skills
Case studies and problem-solving scenarios
Trial sales projects or probationary periods
By incorporating practical assessments, companies can identify candidates who can truly excel in a B2B sales role.
6. Failing to Assess Cultural Fit
Cultural fit is often overlooked during the hiring process, yet it plays a crucial role in a salesperson’s success within a company. A sales candidate may have excellent skills and experience, but if they do not align with the company’s values, work environment, and team dynamics, they are less likely to thrive.
A poor cultural fit can lead to:
Lower job satisfaction and engagement
Increased turnover rates
Conflicts within the sales team
To assess cultural fit, companies should:
Clearly define their company values and work culture
Include behavioral interview questions to gauge alignment
Introduce candidates to potential teammates during the hiring process
Hiring sales professionals who align with the company’s culture improves collaboration and long-term retention.
7. Neglecting Continuous Training and Development
Another major mistake companies make is assuming that training ends after onboarding. The B2B Sales Training Companies are constantly evolving, and even the best sales professionals need ongoing development to stay ahead.
A lack of continuous training can result in:
Stagnant sales performance
Difficulty adapting to new market trends
Decreased motivation and engagement
Effective training programs should include:
Regular sales coaching and mentorship
Workshops on emerging sales techniques
Access to industry conferences and professional development resources
Investing in ongoing training keeps sales teams competitive and ensures long-term success.
8. Not Utilizing Data-Driven Hiring Practices
Many companies still rely on intuition when hiring sales talent instead of leveraging data-driven recruitment methods. While gut feeling can sometimes work, it often leads to bias and poor hiring decisions.
Data-driven hiring improves accuracy by:
Using AI-powered recruitment tools to analyze candidate potential
Tracking historical hiring trends to refine selection criteria
Assessing performance data from previous hires to identify success patterns
By integrating data into the hiring process, companies can reduce turnover and improve sales team performance.
9. Hiring Based on Gut Feeling Instead of Data
Even experienced hiring managers can fall into the trap of making decisions based on intuition rather than objective evaluation. This often leads to inconsistent hiring outcomes and a lack of predictability in sales performance.
Common biases that affect hiring include:
Confirmation bias – Favoring candidates who confirm preexisting beliefs
Halo effect – Overestimating a candidate’s abilities based on one strong trait
Similarity bias – Preferring candidates who resemble the interviewer
To avoid these biases, companies should:
Use structured interviews with standardized scoring
Implement skills assessments and role-specific tests
Gather feedback from multiple interviewers before making a decision
A more objective hiring approach leads to better results and a stronger sales team.
10. Underestimating the Importance of Onboarding
A strong onboarding process sets the foundation for a salesperson’s success. Unfortunately, many companies either rush through onboarding or lack a structured program, leading to poor performance and early turnover.
Common onboarding mistakes include:
Failing to provide clear product and market training
Overloading new hires with information too quickly
Not assigning mentors or sales coaches
An effective onboarding program should:
Last at least 60-90 days with a structured plan
Include hands-on sales training and role-playing exercises
Provide ongoing feedback and coaching
A well-designed onboarding experience ensures that new hires integrate smoothly and start delivering results faster.
11. Not Offering Competitive Compensation Packages
Top B2B sales professionals expect competitive salaries and incentives. Companies that offer below-market compensation packages risk losing top talent to competitors.
Common mistakes in sales compensation include:
Rigid salary structures with low commission potential
Unclear or overly complex bonus plans
Lack of performance-based incentives
To attract and retain top sales talent, companies should:
Offer a competitive base salary with uncapped commission opportunities
Provide clear and transparent bonus structures
Include additional perks such as stock options, travel incentives, or career development programs
A well-designed compensation plan motivates sales teams and boosts performance.
12. Failing to Evaluate Long-Term Potential
Many companies focus solely on immediate sales results rather than assessing a candidate’s long-term growth potential. Sales Recruitment Services Hiring for short-term needs can lead to high turnover and missed opportunities for internal promotions.
To identify long-term potential, companies should:
Look for candidates with leadership qualities
Assess a candidate’s ability to adapt to changing sales environments
Provide career development plans and growth opportunities
Hiring with the future in mind helps companies build strong sales teams with lasting impact.
13. Ignoring the Candidate Experience
The way companies handle the hiring process affects their reputation and ability to attract top talent. A negative candidate experience can discourage high-quality applicants from joining the company.
Signs of a poor candidate experience include:
Long and unorganized hiring processes
Lack of communication or delayed responses
Impersonal interviews that fail to engage candidates
To improve the candidate experience, companies should:
Streamline the hiring process with clear timelines
Maintain open and transparent communication
Provide feedback to all candidates, even those not selected
A positive candidate experience enhances employer branding and attracts top-tier sales professionals.
14. Not Leveraging Employee Referrals
Employee referrals are one of the most effective ways to find high-quality sales talent, yet many companies fail to utilize this hiring strategy. Employees often know strong candidates within their network who would be a good fit for the company.
Benefits of employee referrals include:
Faster hiring process and reduced recruitment costs
Higher-quality candidates with a proven track record
Improved cultural fit and team cohesion
To encourage referrals, companies should:
Offer referral bonuses or incentives
Make the referral process simple and accessible
Recognize and reward employees who refer successful hires
Leveraging internal networks can significantly improve hiring outcomes.
#sales#recruitment#sales recruitment#sales technology#sales enablement#sales consultant#sales techniques#sales training#sales management#sales consulting#salesforce#crm#sales crm#software crm#training#trending#viral#viral trends#viralpost
0 notes
Text

#Welcome to Clovion Tech Solutions Pvt. Ltd. We specialize in Customized Solutions & Development in the fields of Software Solutions#Web Based Solutions#Web Enabled ERP Solutions#Inventory Management Solutions#Human Resource Management Solutions (HRMS)#Web Based Application Development#Informative Website Solutions#Dynamic Website Solutions#Search Engine Optimization (SEO)#Web Hosting Solutions and Websites as our major categories of Business. We are a Technology Company with our owned Head Office situated at#India. In Our Technological Dynamic Team consisting of Technical Manager#Team Leaders#Programmers#Designers & SEO Resources.
1 note
·
View note
Text
Benefits of Implementing ERP Software for Engineering Firms

The engineering industry is one of the biggest industries in the world, and it plays an important role in growing the economy as well. The engineering sector is growing day by day and is highly competitive. Hence, efficiency, accuracy, and streamlined operations are crucial for success in this sector. Businesses face several challenges in this sector, like the complexities of a project, resource management, and deadline restrictions. ERP software for engineering firms is the best way to overcome all of these challenges as it integrates and automates business processes.
Here is the list of top benefits of utilizing ERP systems for the engineering industry:
1. Project Management:
The projects in engineering sectors have a detailed documentation process, different teams, and complicated workflows. ERP system for engineering firms help in various ways, like centralizing project data, enabling limitless collaboration, and getting real-time updates. Because of this software, every team member has all the updates, which in turn reduces miscommunication and delays in the project.
2. Resource Management:
For all engineering projects, it is essential to allocate all resources carefully, like equipment, materials, and labor. With the utilization of ERP software, the monitoring of resources can be performed easily. It helps in checking resource availability, optimizing usage, and forecasting requirements. This ultimately results in improving cost efficiency.
3. Quality Management:
Ensures engineering projects meet industry standards and regulations.
Quality Control: Offers tools for monitoring and managing the quality of materials, processes, and completed projects.
4. Data Management:
Using ERP software, engineering firms can make sure that they can get a unified database to eliminate data silos and ensure consistency through all departments. A centralized data management system is beneficial for decision-making as well it provides critical information when required.
5. Time and Budget Management:
When the whole system gets automated with ERP software, it reduces time and cost on repetitive tasks like data entry, procurement, and inventory management. The utilization of ERP systems in engineering firms helps in reducing manual errors and improving productivity. Hence, the firms can focus on other important things like innovation and project execution.
6. Client Relationship Management:
Most ERP systems include customer relationship management tools that are very helpful in managing client interactions. This tool allows the firm to track communication history, project milestones, and client preferences. Because of this feature, firms can improve customer satisfaction and build long-term relationships.
7. Scalability and Flexibility
ERP solutions may scale with the company as it grows, allowing for more projects, clients, and resources. Customization: ERP solutions can typically be tailored to an engineering firm’s specific demands and operations.
8. Financial Management
Accounting combines financial accounting with project management to provide a complete picture of the company’s financial health. Reporting: Creates detailed financial reports, such as profit and loss statements, balance sheets, and cash flow statements.
How PMTRACK ERP Helps:
Managing development processes, monitoring complex projects, and ensuring seamless collaboration across divisions are becoming increasingly important for company success. Engineering organizations in Pune, India, and around the world have distinct issues in successfully managing their operations.
Implementing a bespoke Enterprise Resource Planning (ERP) solution provides transformative benefits by streamlining processes, improving project management, and ultimately generating profitability.
For businesses considering ERP adoption, selecting the correct ERP software vendor is critical. PMTRACK ERP, a reputable ERP solution provider in Pune, India, specializes in engineering ERP systems tailored to the demands of engineering and manufacturing companies.
ERP software is used to connect project management with financial accounting, inventory control, and procurement procedures. This integration gives project managers real-time information about project costs, resource availability, and schedules, resulting in better-informed decisions and more effective project execution.
Engineering firms that use an ERP system can improve operational efficiency, reduce costs, improve project delivery, and ultimately boost client satisfaction and profitability.
Summary:
ERP software provides several advantages to engineering firms in Pune, India, ranging from better project management and financial control to higher client satisfaction and scalability. Engineering organizations can employ a comprehensive ERP solution to improve operations, decrease inefficiencies, and drive long-term growth.
PMTRACK ERP, one of the leading ERP solution providers in Pune, India, provides comprehensive, industry-specific ERP solutions that are suitable for engineering organizations’ unique requirements. Firms that collaborate with an experienced engineering ERP software company in India receive a trusted partner in negotiating the complexity of their business, setting them up for success in an increasingly competitive landscape.
#efficiency#accuracy#and streamlined operations are crucial for success in this sector. Businesses face several challenges in this sector#like the complexities of a project#resource management#Here is the list of top benefits of utilizing ERP systems for the engineering industry:#1. Project Management:#The projects in engineering sectors have a detailed documentation process#different teams#and complicated workflows. ERP system for engineering firms help in various ways#like centralizing project data#enabling limitless collaboration#and getting real-time updates. Because of this software#every team member has all the updates#which in turn reduces miscommunication and delays in the project.#2. Resource Management:#For all engineering projects#it is essential to allocate all resources carefully#like equipment#materials#and labor. With the utilization of ERP software#the monitoring of resources can be performed easily. It helps in checking resource availability#optimizing usage#and forecasting requirements. This ultimately results in improving cost efficiency.#3. Quality Management:#Ensures engineering projects meet industry standards and regulations.#processes#and completed projects.#4. Data Management:#Using ERP software
0 notes
Text
GIS-Based Solutions for Efficient Telecom Network Management
The telecom industry is undergoing rapid transformation, driven by the increasing demand for seamless connectivity, efficient network management, and improved customer experience. As networks become more complex, the need for innovative solutions to manage these networks has never been greater. Geographic Information System (GIS)-based solutions have emerged as a game-changer in the telecom sector, offering a robust platform for managing, analyzing, and visualizing network data. This blog explores how GIS-based solutions can revolutionize telecom network management, ensuring efficiency and reliability.
Learn more at https://www.cyberswift.com/blog/telecom-utility-solution-a-brief-overview/

#gis for 5g network planning#telecom network monitoring with gis#gis for telecom service coverage analysis#gis enabled telecom site selection#gis mapping for telecom connectivity#gis solutions for managing telecom utilities#role of gis in telecom infrastructure planning#telecom utility gis software for asset management#gis technology for fiber optic network design#geospatial analytics for telecom network optimization#telecom asset management system#gis telecom utility software#fiber optic network mapping#gis based telecom service optimization#telecom network visualization tools#utility network analysis in telecom#geospatial solutions for telecom utilities
0 notes
Text
The Need for AI in Media Asset management - Gyrus AI
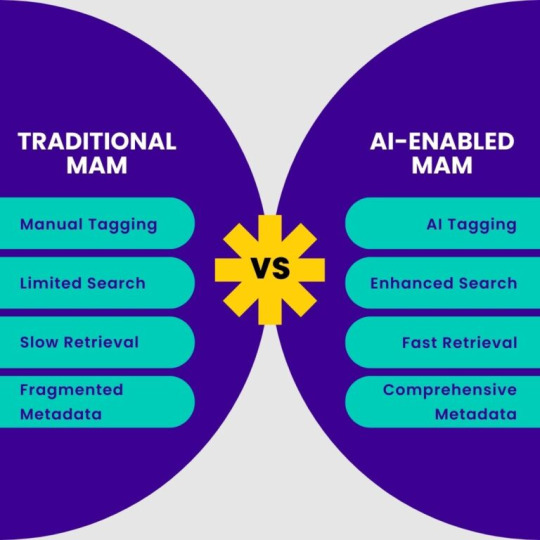
GYRUS AI provides custom AI models for Media Asset Management Search (MAMS). Built for your use case, be it as a broadcaster, advertiser, or media creator, our solutions are tailored to achieve what you require.
More Information About - The Role of AI-Enabled Media Asset Management in Efficient Content Handling
To learn more about how our AI technologies can help your video content perform better, you may contact us at [email protected] or simply click here: www.gyrus.ai
#video anonymization#anonymization software#gyrus ai#redaction software#gyrus#AI in MAM#AI enabled Media Asset Management#Broadcasting Solutions#AI Vision Analytics#AI Video Anonymization Software
0 notes
Text
AI-Enabled Restaurant Management Solutions: Unleashing the Power of Data-Driven Decision Making
Over the last couple of years, AI-enabled Restaurant Management solutions have proved to be truly transformational in changing how restaurants operate and deliver their services. Such systems use artificial intelligence to empower the restaurateur with data-driven insights in smoothing restaurant operations and improving customer experiences for better efficiency. One of the recent innovations is voice AI ordering systems, drastically changing how order-and-pay happens in this space. How these technologies are taking the future of dining is discussed hereafter.
if you want to know more about Ai-enable restaurant management solution click the
0 notes
Text
AI-enabled business management & workflow automation software
How to Grow Your Agency and Run it Like a SaaS Business
In today's fast-paced digital landscape, agencies are increasingly looking for ways to grow efficiently and sustainably. One innovative approach is to run your agency like a Software as a Service (SaaS) business. By adopting SaaS principles, you can streamline operations, enhance client satisfaction, and scale more effectively. Here's How to grow your agency and run it like a saas business.
1. Adopt a Recurring Revenue Model
Why It Matters:
A recurring revenue model provides financial stability and predictability, allowing you to plan and invest in your agency's growth confidently.
How to Implement:
Subscription Services: Offer your services as monthly or annual subscriptions. This could include ongoing marketing support, content creation, SEO maintenance, or social media management.
Tiered Pricing: Develop tiered packages that offer different levels of service, catering to a range of client needs and budgets. This encourages clients to upgrade as they see more value in your services.
2. Automate Workflows and Processes
Why It Matters:
Automation can significantly reduce the time spent on repetitive tasks, allowing your team to focus on higher-value activities that drive growth.
How to Implement:
Use Workflow Automation Tools: Invest in AI-enabled business management and workflow automation software to handle routine tasks like scheduling, invoicing, and reporting.
Standardize Procedures: Create standard operating procedures (SOPs) for common tasks and automate them where possible. This ensures consistency and efficiency.
3. Focus on Scalability
Why It Matters:
Scalability is crucial for growth. A SaaS approach ensures that your business model can handle increased demand without compromising on quality.
How to Implement:
Cloud-Based Solutions: Utilize cloud-based tools for project management, communication, and file storage. This facilitates collaboration and allows you to scale your operations seamlessly.
Outsource Non-Core Activities: Partner with freelancers or other agencies to handle overflow work or specialized tasks. This way, you can scale up quickly without the long-term commitment of hiring full-time staff.
4. Invest in Client Success
Why It Matters:
In a SaaS model, client retention is as important as acquisition. Ensuring your clients achieve their desired outcomes will foster loyalty and long-term relationships.
How to Implement:
Onboarding Programs: Develop comprehensive onboarding processes to help clients understand and utilize your services effectively from day one.
Regular Check-Ins: Schedule regular check-ins to review progress, gather feedback, and adjust strategies as needed. This shows clients you’re committed to their success.
5. Leverage Data and Analytics
Why It Matters:
Data-driven decision-making allows you to optimize your services and demonstrate the value you provide to clients.
How to Implement:
Performance Metrics: Track key performance indicators (KPIs) such as client retention rates, campaign performance, and ROI. Use these insights to refine your strategies.
Client Dashboards: Provide clients with access to dashboards where they can monitor their own metrics in real-time. Transparency builds trust and keeps clients engaged.
6. Develop a Strong Online Presence
Why It Matters:
A robust online presence enhances your agency’s credibility and attracts potential clients.
How to Implement:
Content Marketing: Create valuable content that showcases your expertise, such as blog posts, whitepapers, and case studies.
Social Media Engagement: Maintain an active presence on social media platforms where your target audience is most active. Share insights, engage in discussions, and promote your services.
Conclusion
Transforming your agency to run like a SaaS business requires a shift in mindset and operations. By adopting a recurring revenue model, automating workflows, focusing on scalability, investing in client success, leveraging data, and enhancing your online presence, you can achieve sustainable growth and stay competitive in the digital age.
Ready to take your agency to the next level? Start implementing these SaaS principles today and watch your business thrive!
0 notes
Text
#ai enabled restaurant management#restaurant pos system#online ordering system#restaurant point of sale#self service kiosk#full service restaurant#restaurant management software#quick service pos system#restaurant pos software#kitchen display system#restaurant management ecosystem
0 notes
Text
Culinary Commerce: The Role of AI-Enabled Restaurants in Sales

Technology is playing a more and larger role in the constantly changing fabric of the culinary world, profoundly influencing our culinary adventures. The rise of culinary establishments with AI integration represents a ground-breaking and paradigm-shifting development in this field. These eating establishments use artificial intelligence's ability to advance both financial feats and the culinary the journey. In this essay, we set out on a fascinating journey into the universe of AI Enabled Restaurant and try to understand their enormous impact on the food industry.
Enhanced Cooking Skills in the Kitchen
The conduits in the kitchen are being carefully optimized by AI while being hidden from customers' sight. It ensures the most cost-effective use of the ingredients, avoiding waste. AI-driven kitchen automata manage the production of food with an unparalleled level of accuracy, consistency, and speed, hence reducing the length of time that customers must wait. This promptness not only results in cost-efficiency for the restaurant but also in the happiness of the customers.
Restaurants with AI-Enhanced Business Models
Revenue Maximization Using Data-Driven Cognition
Data is king in the world of food commerce. The power of data analytics can be utilized by restaurants with AI to gain profound understanding into customer behavior. They are more equipped to make intelligent decisions about pricing, menu changes, and marketing strategies since they can recognize the apex of dining traffic, beloved menu items, and seasonal vogues. This data-driven strategy helps restaurants increase sales and financial benefits since they are adept at making adjustments that are laser-focused on successfully meeting the needs of their customers.
Enhancing Patron Adherence
The ability to cultivate strong customer loyalty is one of the restaurants using AI as their main asset. Customers are more likely to return to the restaurant because of its cozy atmosphere of personalized menus and sleek service. AI also has the ability to provide specific customers personalized promos and incentives based on their preferences, thereby strengthening the relationship between the business and its customers. AI-assisted restaurants increase brand loyalty and contribute to the steady increase in financial entrance by creating an environment of exclusivity and attending to the unique needs of each customer
The Human Dimension
While AI is a crucial part of these organizations' successes, the importance of human interaction should not be underestimated. Staff who are friendly and attentive continue to be the foundation of any successful restaurant. AI just supports their efforts by optimizing processes and improving the eating experience.
The Future Route
AI-infused dining establishments are expected to spread further as the landscape of culinary commerce continues its continuous evolution. Customers are becoming more interested in dining experiences that offer them not only delicious meals but also a streamlined, tailored experience that meets their needs. It is projected that this development will increase AI's involvement in the restaurant industry.
In conclusion
AI-enhanced dining experiences with quick service POS system and represent a seismic shift in the culinary industry, redefining the eating experience while increasing efficiency and financial gain. These businesses are without a doubt ready to meet the constantly changing needs of the smart modern diner thanks to their use of artificial intelligence.
#Ai enabled restaurant#quick service POS system#restaurant management system#restaurant management software#restaurant management ecosystem#kitchen display system#kds system#full service restaurant#restaurant pos system#online ordering system#restaurant point of sale
0 notes
Text
Sales CRM Software for Small Business, Manufacturing Industry - Cliky
Enhance customer interactions and boost sales with Cliky's powerful Customer Relationship Management (CRM) software. Best CRM and Automation for Small Business.
0 notes
Text
DAY 6274
Jalsa, Mumbai Aopr 20, 2025 Sun 11:17 pm
🪔 ,
April 21 .. birthday greetings and happiness to Ef Mousumi Biswas .. and Ef Arijit Bhattacharya from Kolkata .. 🙏🏽❤️🚩.. the wishes from the Ef family continue with warmth .. and love 🌺
The AI debate became the topic of discussion on the dining table ad there were many potent points raised - bith positive and a little indifferent ..
The young acknowledged it with reason and able argument .. some of the mid elders disagreed mildly .. and the end was kind of neutral ..
Blessed be they of the next GEN .. their minds are sorted out well in advance .. and why not .. we shall not be around till time in advance , but they and their progeny shall .. as has been the norm through generations ...
The IPL is now the greatest attraction throughout the day .. particularly on the Sunday, for the two on the day .. and there is never a debate on that ..
🤣
.. and I am most appreciative to read the comments from the Ef on the topic of the day - AI .. appreciative because some of the reactions and texts are valid and interesting to know .. the aspect expressed in all has a legitimate argument and that is most healthy ..
I am happy that we could all react to the Blog contents in the manner they have done .. my gratitude .. such a joy to get different views , valid and meaningful ..
And it is not the end of the day or the debate .. some impressions of the Gen X and some from the just passed Gen .. and some that were never ever the Gen are interesting as well :
The Printing Press (15th Century)
Fear: Scribes, monks, and elites thought it would destroy the value of knowledge, lead to mass misinformation, and eliminate jobs. Reality: It democratized knowledge, spurred the Renaissance and Reformation, and created entirely new industries—publishing, journalism, and education.
⸻
Industrial Revolution (18th–19th Century)
Fear: Machines would replace all human labor. The Luddites famously destroyed machinery in protest. Reality: Some manual labor jobs were displaced, but the economy exploded with new roles in manufacturing, logistics, engineering, and management. Overall employment and productivity soared.
⸻
Automobiles (Early 20th Century)
Fear: People feared job losses for carriage makers, stable hands, and horseshoe smiths. Cities worried about traffic, accidents, and social decay. Reality: The car industry became one of the largest employers in the world. It reshaped economies, enabled suburbia, and created new sectors like travel, road infrastructure, and auto repair.
⸻
Personal Computers (1980s)
Fear: Office workers would be replaced by machines; people worried about becoming obsolete. Reality: Computers made work faster and created entire industries: IT, software development, cybersecurity, and tech support. It transformed how we live and work.
⸻
The Internet (1990s)
Fear: It would destroy jobs in retail, publishing, and communication. Some thought it would unravel social order. Reality: E-commerce, digital marketing, remote work, and the creator economy now thrive. It connected the world and opened new opportunities.
⸻
ATMs (1970s–80s)
Fear: Bank tellers would lose their jobs en masse. Reality: ATMs handled routine tasks, but banks actually hired more tellers for customer service roles as they opened more branches thanks to reduced transaction costs.
⸻
Robotics & Automation (Factory work, 20th century–today)
Fear: Mass unemployment in factories. Reality: While some jobs shifted or ended, others evolved—robot maintenance, programming, design. Productivity gains created new jobs elsewhere.
The fear is not for losing jobs. It is the compromise of intellectual property and use without compensation. This case is slightly different.
I think AI will only make humans smarter. If we use it to our advantage.
That’s been happening for the last 10 years anyway
Not something new
You can’t control that in this day and age
YouTube & User-Generated Content (mid-2000s onward)
Initial Fear: When YouTube exploded, many in the entertainment industry panicked. The fear was that copyrighted material—music, TV clips, movies—would be shared freely without compensation. Creators and rights holders worried their content would be pirated, devalued, and that they’d lose control over distribution.
What Actually Happened: YouTube evolved to protect IP and monetize it through systems like Content ID, which allows rights holders to:
Automatically detect when their content is used
Choose to block, track, or monetize that usage
Earn revenue from ads run on videos using their IP (even when others post it)
Instead of wiping out creators or studios, it became a massive revenue stream—especially for musicians, media companies, and creators. Entire business models emerged around fair use, remixes, and reactions—with compensation built in.
Key Shift: The system went from “piracy risk” to “profit partner,” by embracing tech that recognized and enforced IP rights at scale.
This lead to higher profits and more money for owners and content btw
You just have to restructure the compensation laws and rewrite contracts
It’s only going to benefit artists in the long run
Yes
They can IP it
That is the hope
It’s the spread of your content and material without you putting a penny towards it
Cannot blindly sign off everything in contracts anymore. Has to be a lot more specific.
Yes that’s for sure
“Automation hasn’t erased jobs—it’s changed where human effort goes.”
Another good one is “hard work beats talent when talent stops working hard”
Which has absolutely nothing to with AI right now but 🤣
These ladies and Gentlemen of the Ef jury are various conversational opinions on AI .. I am merely pasting them for a view and an opinion ..
And among all the brouhaha about AI .. we simply forgot the Sunday well wishers .. and so ..














my love and the length be of immense .. pardon

Amitabh Bachchan
107 notes
·
View notes
Text
Axolt: Modern ERP and Inventory Software Built on Salesforce
Today’s businesses operate in a fast-paced, data-driven environment where efficiency, accuracy, and agility are key to staying competitive. Legacy systems and disconnected software tools can no longer meet the evolving demands of modern enterprises. That’s why companies across industries are turning to Axolt, a next-generation solution offering intelligent inventory software and a full-fledged ERP on Salesforce.
Axolt is a unified, cloud-based ERP system built natively on the Salesforce platform. It provides a modular, scalable framework that allows organizations to manage operations from inventory and logistics to finance, manufacturing, and compliance—all in one place.
Where most ERPs are either too rigid or require costly integrations, Axolt is designed for flexibility. It empowers teams with real-time data, reduces manual work, and improves cross-functional collaboration. With Salesforce as the foundation, users benefit from enterprise-grade security, automation, and mobile access without needing separate platforms for CRM and ERP.
Smarter Inventory Software Inventory is at the heart of operational performance. Poor inventory control can result in stockouts, over-purchasing, and missed opportunities. Axolt’s built-in inventory software addresses these issues by providing real-time visibility into stock levels, warehouse locations, and product movement.
Whether managing serialized products, batches, or kits, the system tracks every item with precision. It supports barcode scanning, lot and serial traceability, expiry tracking, and multi-warehouse inventory—all from a central dashboard.
Unlike traditional inventory tools, Axolt integrates directly with Salesforce CRM. This means your sales and service teams always have accurate availability information, enabling faster order processing and better customer communication.
A Complete Salesforce ERP Axolt isn’t just inventory software—it’s a full Salesforce ERP suite tailored for businesses that want more from their operations. Finance teams can automate billing cycles, reconcile payments, and manage cash flows with built-in modules for accounts receivable and payable. Manufacturing teams can plan production, allocate work orders, and track costs across every stage.
86 notes
·
View notes
Text
Live stream happened, and we got some designs revealed! As well as a couple of information, but not anything major.

Miss conductor, not much of a surprise (but miss girl looks gorgeous as always)

And Node, who is sort of the main antagonist.
I made a prediction before, and April 21 hit,.. so I believe it is well due for an update by now.
While we did not receive nearly as much information as we were anticipating, a design still reveals much on the character itself when going through the lens of a general analysis. In this context, their abilities and name aid significantly in the status and essential depths of their character.
With what I can gather in my research, nodes play an important role in networking because they are the building blocks of a network, precisely the gateway for connection, direction, sending, creating, receiving, and storing data. It requires only software to connect to the network, and it can be run by completely anyone. Applying this knowledge with concept arts of the game and overall worldbuilding of the series itself—everything becomes a lot clearer.
So now, how can we apply this to Node?

Node's name is simple in itself, and it connects to their design as well. They are quite literally made up of nodes. One in their head and the other in their limbs. Their body is translucent.
Network nodes are categorical. Thanks to DJ, we got a helpful hint that incredibly reduced their types to a digestible and simpler layout.
Their name starts with i.
There are countless forms and types of nodes, the hint condensed it down to 2 answers, both starting with the letter “i”
Intermediate nodes
These include devices like routers and switches that help direct data to the correct destination while also receiving it. They don't originate or terminate data but instead pass it along to where it needs to go.
IoT nodes
loT (Internet of Things) Nodes serve as devices that establish connectivity to the Internet via a gateway, effectively enabling the integration of the physical world into the vast realm of the Internet. Within an loT ecosystem, these nodes function as crucial components for bridging the gap between the physical and virtual worlds. Taking charge of managing the entire loT system.
We had seen this ability before vía King's icons' staff, in which it only sucked in Minecraft mobs due to the strong force being their obligatory origin, overriding the game itself due to the overlapping icons.
In regards to King, he used this ability for the very destruction of the game itself, down to the code, reducing it to nothing but.. nothing for the sake of vengeance. Or at least what would have occurred if he did succeed.
way to go CG! Give credit where it's due
Despite this being marked with the intention of erasion and minimization, I think it's safe to group this as receiving and storing data. The two icons combined created a horrifically dramatized version of the force with storing and receiving, which created an incredibly overpowered demolishing force.

In Chosen, we had seen this ability before as well, as the constellations are seen right as he creates the gateway from the Outernet, which sounds awfully familiar. This is what you would refer to as an "extension to the digital world"
I think I can be able to safely group this to direction and creation.

From how I see it, it seems as though it's quite diverse in a fictional worldbuilding sense within characters.
And obviously, it won't be the last time we would see it. It seems as though we would be exploring this quite a lot.

In their cameo, Node is in an assumed line-up with all the major series antagonists.

But if you’re asking me, it seems as though our iconic antagonists appear to be rather victims of Node. Menacingly behind them, their abilities floating not far behind as they're stuck in a swampy substance. But that's just me.
Node's entire antagonistic ordeal is beyond my grasp, but I'm assuming their abilities and attacks surrounds the embodiment of network topology, which would mold and diverse into the connections of nodes. They possibly intend to screw up with the gateways that are responsible for the receiving, directing, and sending of data between various devices through communication links that are defined as network—with the basic visuals of concept art we were given.

(The gateway, ethernet tunnels, the train cough cough)
Node's goal and story behind that destruction remains anonymous, as the writing is still in early development. Regardless, food for thought.
#alan becker#animation vs minecraft#animator vs animation#animation versus#nerd voyage#it's pretty interesting#though my research is still ongoing#when i say it's diverse..#yeah it's diverse alright
87 notes
·
View notes