#intellectualpropertyprotection
Explore tagged Tumblr posts
Text
Top 5 Reasons to Choose a USA-Based Cross-Platform Development Company
When it comes to building an app, choosing the right development partner is one of the most important decisions you’ll make. As a business owner, IT manager, or startup founder, you want a reliable partner who offers cutting-edge skills, top-notch security, and ongoing support. That’s where a USA-based cross-platform development company stands out.
In this post, I’ll break down the top five reasons why choosing a USA-based development company for your cross-platform app needs is a smart move.

Whether you’re focused on quality, security, or timely support, you’ll see how these companies can help you take your app development project to the next level.
Why a USA-Based Cross-Platform Development Company is the Right Choice
1) Expertise and Quality in Cutting-Edge Technology
Top Skills for Building Great Apps:
Developing a high-quality, fully functional app requires a team with the right expertise. USA-based cross-platform developers are highly skilled in building apps that work seamlessly across both iOS and Android.
These companies are proficient in React Native, Flutter, and Xamarin, ensuring your app is built with the most powerful and flexible cross-platform development frameworks available.
Staying Ahead of the Curve with New Tech:
In the fast-moving tech world, staying up to date with the latest trends is crucial. USA-based companies are committed to continuous learning and innovation. They’re experts in cutting-edge technologies such as AI, augmented reality (AR), and virtual reality (VR), ensuring that your app is not only functional today but also ready for tomorrow’s challenges.
Adhering to Best Practices:
USA-based developers follow industry best practices for coding, app design, and security. They maintain high standards for app performance, user experience, and data protection, ensuring your app is stable and secure from the get-go.
2) Seamless Communication and Efficient Project Management
No More Time Zone Headaches:
When working with an offshore team, communication delays are a common issue that can hinder progress. With a USA-based development company, you won’t face time zone challenges. You can expect real-time communication, ensuring that any questions or issues are addressed immediately. This leads to faster development and fewer misunderstandings.
Better Collaboration and Alignment:
USA-based companies share similar cultural norms and business practices, making collaboration easier and more efficient. This alignment results in smoother project management and more effective communication, as both teams are on the same page throughout the process.
Agile Development for Flexibility:
In today’s fast-paced market, flexibility is key. USA-based companies are experts in Agile development methodologies like Scrum, which allows for flexibility and quick adjustments. If your app requirements change during the development process, the team can pivot efficiently without disrupting timelines.
3) Data Security and Intellectual Property (IP) Protection
Strict Data Privacy Laws:
One of the biggest concerns when outsourcing app development is data security. USA-based companies are bound by strict data protection laws, such as the California Consumer Privacy Act (CCPA), which ensures your customer data is handled safely and legally. You can trust that your app’s data will be secure.
Advanced Cybersecurity Measures:
In addition to adhering to laws, USA-based developers use advanced encryption and secure infrastructure to protect your app and user data. Whether it’s safeguarding sensitive business information or user data, USA-based developers are committed to keeping your app secure.
Protecting Your Ideas and Innovations:
When you hire a USA-based development company, you can rest easy knowing your intellectual property (IP) is protected. The USA has strong laws regarding IP, which help ensure that your app’s code, ideas, and innovations stay exclusively yours.
4) Proven Experience Across Various Industries
Serving Multiple Sectors:
Whether you’re in healthcare, finance, logistics, e-commerce, or any other industry, a USA-based development company has likely worked with businesses in your field. Their broad experience means they can tailor solutions specifically to meet the unique needs of your industry. You don’t just get a team of developers; you get experts who understand your business’s challenges.
Success Stories You Can Trust:
The best USA-based cross-platform development companies are proud to share their success stories and case studies. By looking at their past work, you can see how they’ve helped businesses like yours succeed. These case studies provide valuable insight into the company’s capabilities and how they’ve solved similar challenges.
Deep Knowledge of Both Domestic and International Markets:
USA-based companies have a unique advantage — they know both local and global markets. Whether you’re launching your app to a domestic or international audience, they understand the market dynamics, user expectations, and best practices for success.
5) Fast Support and Long-Term Maintenance
On-Demand Support:
Post-launch, your app will need regular updates and quick fixes to keep it running smoothly. One of the key benefits of working with a USA-based company is faster support. With a team in your time zone, you can expect quicker response times and real-time troubleshooting for any issues.
Long-Term Partnerships for Maintenance:
Unlike offshore companies that may lose interest once the app is launched, USA-based companies are committed to long-term maintenance and support. They’ll help you with updates, new features, and bug fixes well after the app is live, ensuring its continued success.
Fast Action in Emergencies:
Whether it’s a bug, an update, or an urgent change, USA-based developers are quick to respond to emergencies. They prioritize your needs, providing real-time solutions that keep your app up and running without unnecessary delays.
Conclusion
A USA-based cross-platform development company ensures high-quality expertise, secure data handling, smooth communication, and ongoing support. With a deep understanding of industry-specific needs, they deliver scalable and reliable apps while protecting your business’s intellectual property.
Ready to take your app development to the next level? Reach out to iQlance, a leading USA-based cross-platform development company, to discuss your project and start building the app your business deserves! Call us now at (+1) 469–398–8817.
#usa-basedcrossplatformdevelopmentcompany#iqlance#usa#crossplatformdevelopmentservicesusa#usaappdevelopmentcompanies#crossplatformmobiledevelopmentusa#crossplatformappdevelopersusa#crossplatformappdevelopmentbenefits#topcrossplatformdevelopmentcompaniesintheusa#crossplatformappdevelopmentpros#bestappdevelopmentcompaniesusa#benefitsofusa-basedappdevelopment#mobileappdevelopmentusa#agiledevelopmentprocess#projectmanagementexpertise#intellectualpropertyprotection#secureappdevelopment#crossplatformtechnologyexpertise#us-basedsoftwaredevelopers#appsecurityanddataprotection#customappdevelopmentsolutions#highqualitycodestandards#responsivecustomersupport#whychooseausa-basedcrossplatformdevelopmentcompany#advantagesofhiringcrossplatformdevelopersintheusa#benefitsofchoosingusacrossplatformappdevelopment#crossplatformmobileappdevelopersforusbusinesses#whyhireusa-baseddevelopersforcrossplatformapps#usa-basedvsoffshorecrossplatformdevelopmentcompanies#usaappdevelopmentcompanyforsecurecrossplatformapps
0 notes
Text
10 Reasons Why TSCM Services Are Essential For Business Protection

Understanding TSCM Services
Technical Surveillance Countermeasures (TSCM) services are specialized security measures that detect and prevent illegal surveillance activity. These services aim to protect enterprises, organizations, and individuals from various forms of espionage, including the use of covert listening devices (bugs), concealed cameras, wiretaps, and other electronic surveillance instruments. Key Aspects of TSCM Services for Business Protection 1. Electronic sweeps: TSCM personnel employ cutting-edge equipment to conduct electronic sweeps of workplaces, boardrooms, and homes in order to locate hidden surveillance devices. These devices may contain microphones, cameras, GPS trackers, and other clandestine instruments used to collect sensitive information. 2. Physical inspections: In addition to electronic sweeps, TSCM services frequently involve detailed physical inspections of the facilities. This includes looking for indicators of tampering, odd wiring, or hidden gadgets that may not be detectable by electrical means alone. 3. Signal analysis: TSCM professionals examine the radio frequency (RF) spectrum for unlawful transmissions. This aids in recognizing gadgets that may be broadcasting audio or video signals to other locations. 4. Cybersecurity Integration: While TSCM primarily addresses physical surveillance risks, it frequently includes an assessment of digital security weaknesses. This ensures that cyber methods cannot remotely activate or operate surveillance devices. 5. Ongoing Monitoring: Some TSCM systems provide continuous monitoring to detect and respond to new threats as they arise. This is particularly important in high-risk workplaces that frequently discuss or handle sensitive data. Applications for TSCM Services - Corporate security: Businesses employ TSCM services to safeguard their trade secrets, intellectual property, and sensitive communications from competitors or hostile insiders. - Government and military: The TSCM is critical for safeguarding confidential information and national security interests from foreign espionage. - Personal Privacy: High-profile individuals, such as executives, celebrities, and politicians, may use TSCM services to safeguard their privacy from unlawful surveillance. - Legal and financial sectors: law firms, financial organizations, and other entities that handle sensitive information use TSCM to protect client confidentiality and avoid data breaches. Importance of TSCM Services for Business Protection TSCM services are critical for enterprises that handle sensitive data, face high espionage risks, or require stringent confidentiality. By detecting and neutralizing surveillance threats, TSCM services assist in preventing information leaks, protecting intellectual property, and ensuring the integrity of communications and operations.
10 Reasons Why TSCM Services Are Essential for Business Protection
In today's fast-paced, technologically driven world, organizations face an ever-increasing number of dangers to their security, privacy, and intellectual property. From business espionage to data breaches, safeguarding sensitive information has never been more important. One of the most effective ways to protect your business from these attacks is to use Technical Surveillance Countermeasures (TSCM) services. Here are seven convincing reasons why TSCM services are critical to defending your company. 1. Preventing Corporate Espionage Corporate espionage poses a huge threat to firms of all kinds. Competitors could try to acquire an unfair edge by stealing proprietary information, trade secrets, or sensitive data. By detecting and uninstalling covert surveillance devices like bugs, wiretaps, and hidden cameras, TSCM services help prevent business espionage. Businesses can prevent illegal monitoring of meetings, communications, and sensitive places by conducting TSCM sweeps on a regular basis. Corporate espionage can lead to significant financial losses, reputational damage, and a loss of competitive advantage. The cost of a TSCM service is negligible when compared to the potential implications of losing your company's most critical information. 2. Protecting Intellectual Property Intellectual property (IP) is frequently the lifeblood of a company, particularly in fields like technology, medicine, and manufacturing. Theft of intellectual property can have disastrous consequences, including a loss of market share, money, and innovative potential. TSCM services protect your intellectual property by guaranteeing that your research and development areas, as well as other sensitive sites, are free of listening devices. Whether it's the creation of a new product, a revolutionary idea, or proprietary software, TSCM services provide the required safeguards to protect your intellectual property from prying eyes. Protecting your intellectual property allows you to keep your competitive advantage and continue to innovate without fear of theft. 3. Ensuring Confidentiality at Business Meetings Business meetings frequently entail the exchange of sensitive information, such as strategic plans, financial data, and legal issues. The disclosure of sensitive information could result in serious consequences, ranging from legal penalties to a loss of client trust. By identifying hidden devices that could potentially record or send critical information, TSCM services safeguard the confidentiality of your business meetings. High-stakes meetings, such as those involving mergers and acquisitions, investor discussions, or negotiations with significant partners, require strict confidentiality. TSCM services provide peace of mind by guaranteeing that your meeting rooms are safe and free of unlawful surveillance. 4. Addressing Insider Threats for Business Protection Insider threats are among the most difficult security problems to address. Employees, contractors, or other insiders who have access to sensitive information may utilize that access for nefarious purposes, such as leaking secret data or installing surveillance equipment. TSCM services help to reduce insider threats by frequently examining your facilities for unwanted surveillance devices and monitoring places where sensitive information is handled. TSCM sweeps allow firms to discover and mitigate possible insider threats before they escalate. This proactive approach helps ensure the integrity of your business processes and safeguards against the risks associated with harmful insiders. 5. Meeting Legal and Regulatory Requirements Many industries have severe legal and regulatory requirements for the safeguarding of sensitive information. Failure to comply with these rules can result in significant fines, punitive penalties, and reputational harm. TSCM services help to ensure compliance with these standards by conducting a complete assessment of your security procedures and detecting any vulnerabilities that could lead to a breach. For example, in the financial, healthcare, and defense industries, particular requirements require the protection of client data, patient information, and classified materials. TSCM services help organizations meet these criteria by ensuring that their premises are safe and free from unlawful surveillance. 6. Ensuring client trust and reputation Trust is an essential component of any successful business partnership. Clients expect you to secure their sensitive information and behave in their best interests. A breach of trust, whether caused by a data leak or unlawful surveillance, can have long-term ramifications for your company's reputation. TSCM services uphold client trust by guaranteeing the security of your organization and the protection of sensitive client information. In an age when data breaches and cyberattacks are becoming more regular, organizations must go above and beyond to demonstrate their dedication to security. TSCM services provide an extra layer of protection that might help you maintain client trust and your company's reputation. 7. Preventing unauthorized access to trade secrets for Business Protection Trade secrets are a vital asset for any organization, and they frequently provide a competitive advantage in the marketplace. However, they are an attractive target for corporate espionage and theft. By detecting and disarming any surveillance devices that could potentially steal this important data, TSCM services aid in preventing unwanted access to trade secrets. Whether it's a unique manufacturing process, a patent formula, or a sensitive client list, TSCM services keep your trade secrets protected. Protecting these assets allows you to maintain your competitive advantage while avoiding the severe penalties of trade secret theft. 8. Improving Cybersecurity Effort TSCM services primarily detect physical surveillance concerns, but they also significantly enhance your overall cybersecurity efforts. Cybercriminals frequently employ a combination of physical and digital tactics to obtain access to sensitive data. TSCM services aid in pinpointing possible vulnerabilities in your physical security that could potentially lead to a cyberattack. For instance, a cyberattack might use a hidden camera or microphone to record passwords, access codes, or other sensitive information. By tackling these physical security issues, TSCM services help to improve your total cybersecurity posture and defend your company from both physical and digital threats. 9. Protecting against Industrial Espionage Industrial espionage is the covert collection of trade secrets, private information, or other sensitive data in order to gain a competitive advantage. Competitors, foreign entities, or even dissatisfied staff may carry out this type of espionage. A private detective play a crucial role in safeguarding your company against industrial espionage, as they identify and disarm any surveillance devices that could potentially gather information. The manufacturing, energy, and technology industries are especially vulnerable to industrial espionage because their intellectual property and trade secrets are so valuable. The TSCM services provide the necessary safeguards to prevent competitors from accessing and using your important information. 10. Providing peace of mind for your business protection Finally, one of the most essential reasons to invest in TSCM services is the peace of mind they bring. Knowing that your company is safe from illegal observation and that your sensitive information is secure helps you concentrate on what matters most: running and growing your business. The ongoing concern of corporate espionage, data breaches, and insider threats can be unpleasant for business owners and executives. TSCM services ease this tension by offering a comprehensive security solution that covers both physical and digital risks. With TSCM services in place, you can be confident that your firm is secure and that you are taking proactive measures to protect your assets.
Conclusion
In an increasingly linked world, threats to your company's security are more broad and sophisticated than ever. From corporate espionage to insider threats, protecting your sensitive information has never been more important. TSCM services address these dangers in a comprehensive manner by detecting, identifying, and disarming unwanted surveillance devices and activities. The ten reasons presented in this blog indicate how important TSCM services are to securing your organization. By avoiding corporate espionage, protecting intellectual property, preserving the secrecy of business meetings, and managing internal risks, TSCM services provide the protection your company requires to thrive in a competitive climate. Investing in TSCM services is more than just addressing urgent dangers; it is also about laying a solid foundation for your company's future. Whether you're concerned about legal compliance, safeguarding client confidence, or improving your cybersecurity efforts, TSCM services provide the peace of mind that comes from knowing your organization is secure. To summarize, TSCM services are not a choice; they are required for any firm that values its security, reputation, and long-term success. Integrating TSCM services into your security plan allows you to business protection from today's ever-changing threats while also ensuring the safety and security of your most valuable assets. Read the full article
#BusinessProtection#CorporateInvestigaitons#intellectualpropertyprotection#IntellectualPropertyRights#TSCMServices
0 notes
Text
U.S. and China Leaders Discuss Trade, Security, and Human Rights at APEC Summit: What You Need to Know! #APECsummit #Chinaseconomicpractices #ChineseleaderXiJinping #constructivedialogue. #Cybersecurity #fairandreciprocaltradeagreements #geopoliticaldynamics #globaltradepolicies #humanrights #intellectualpropertyprotection #intellectualpropertytheft #militaryexpansionintheSouthChinaSea #mutualrespectandtrust #regionalstability #Security #situationinXinjiang #tariffs #tensions #trade #U.S.PresidentJoeBiden #U.S.Chinarelations
#Politics#APECsummit#Chinaseconomicpractices#ChineseleaderXiJinping#constructivedialogue.#Cybersecurity#fairandreciprocaltradeagreements#geopoliticaldynamics#globaltradepolicies#humanrights#intellectualpropertyprotection#intellectualpropertytheft#militaryexpansionintheSouthChinaSea#mutualrespectandtrust#regionalstability#Security#situationinXinjiang#tariffs#tensions#trade#U.S.PresidentJoeBiden#U.S.Chinarelations
0 notes
Text
Amazon: Turning Point, Guilty Plea in Counterfeit Case
Unprecedented Success in the Battle Against Counterfeits
In a groundbreaking development, Amazon's Counterfeit Crimes Unit (CCU) joined forces with the Prada Group and other luxury brands to provide vital information and evidence to Chinese law enforcement. Consequently, this collaboration led to a guilty plea from a counterfeiter involved in the sale of counterfeit luxury goods, marking a significant turning point in the fight for Intellectual Property rights. A Landmark Case Without Seized Counterfeit Products This case stands out as an exceptional milestone in the ongoing struggle against counterfeit goods. It represents an unusual scenario where a criminal referral from Amazon's CCU resulted in a criminal judgment. Importantly, this judgment was primarily based on evidence derived from overseas counterfeit sales records and fulfillment center inventory records located outside of China, rather than the typical reliance on seized counterfeit products.
Departure from Conventional Legal Practices
Traditionally, courts issued criminal judgments when there was tangible evidence of counterfeits seized during law enforcement raids. In this case, however, the court primarily depended on information furnished by Amazon and luxury brands, including Prada. Amazon's Early Detection and Referral to Chinese Authorities Amazon's CCU first detected the defendant's counterfeiting activities in 2021. Following rigorous internal investigations, Amazon initiated a criminal referral to the relevant regional Chinese enforcement agency, specifically the Public Security Bureau (PSB), to launch a criminal case. The court sentenced the individual to three years in prison, imposed a $25,000 fine, and will seize and destroy all proceeds acquired from the sale of counterfeit goods, along with their illicit inventory of counterfeit items.
A Victory for Intellectual Property Protection
Kebharu Smith, director of Amazon's CCU, stated, "The guilty plea is a significant win for Amazon's CCU, but more importantly, it's a win for all of those who share our commitment to tackling the industry-wide issue of counterfeiting. This successful result would not have been possible without the collaboration with law enforcement and luxury players such as the Prada Group. We are grateful for their support and look forward to continuing to take the fight to counterfeiters." Francesca Secondari, Prada Group's General Counsel and Chief Legal Officer emphasized their unwavering commitment to eradicating the sale of counterfeit goods, aiming to protect their brands' integrity and ensure the high-quality standards expected by their customers. She praised the partnership with Amazon as a significant step forward in the ongoing battle against those who attempt to break the law and harm their customers. Amazon's Ongoing Commitment to Counterfeit Prevention Amazon has deployed an array of automated protection technologies to prevent counterfeits from entering its platform. In 2022, Amazon's systems thwarted more than 800,000 attempts by bad actors to open new selling accounts before listing a single product for sale. Over 99% of listings suspected of being fraudulent or counterfeit were blocked or removed through Amazon's proactive, automated protections. Amazon continues its commitment to pursuing bad actors who seek to evade these protections and remains dedicated to upholding the integrity of its platform. In 2022, Amazon's CCU took legal action or referred over 1,300 criminals for investigation across the United States, the United Kingdom, the European Union, and China, working closely with brands and law enforcement worldwide to hold wrongdoers accountable. Sources: THX News & Amazon. Read the full article
#Amazon#counterfeitcollaboration#Counterfeitgoods#Counterfeitprevention#Departurefromlegalpractices#Globallawenforcementcollaboration#Guiltypleacounterfeitcase#Intellectualpropertymilestone#Intellectualpropertyprotection#legalaction#ProactiveMeasures
0 notes
Text

Intellectual Property Management Services
Legally protecting the intellectual property of your business not only bring money but expands your business market and helps you thrive in the industry. Vee Technologies offers Intellectual Property Management Services to help you protect your ideas and inventions.
Email : [email protected]
Visit : https://bit.ly/3TiGnnd
#intellectualproperty#intellectualpropertyrights#intellectualpropertylaw#intellectualpropertyprotection#ipprotection#intellectualpropertymanagement
0 notes
Text
Best Technical Writing Services in USA at Affordable Prices
Technical writing plays a vital role in the field of engineering. Engineers are responsible for designing, developing, and maintaining complex systems, and effective communication is crucial for their success. In this blog post, we will explore the importance of technical writing in engineering and how it contributes to the efficiency, accuracy, and overall effectiveness of engineering projects.

Clear Communication: Engineering projects involve collaboration among multidisciplinary teams comprising engineers, designers, project managers, and stakeholders. Technical writing allows engineers to communicate complex ideas, specifications, and requirements clearly and concisely. By using precise language and visual aids, technical documents bridge the gap between technical experts and non-technical stakeholders, ensuring everyone understands the project objectives and progress.
Documentation of Design and Development: Technical writing provides a means to document the design and development process of engineering projects. Detailed documentation allows engineers to maintain an organized record of decisions, iterations, and modifications made throughout the project lifecycle. This documentation serves as a reference for future improvements, troubleshooting, and maintenance, saving time and effort in the long run.
Standardization and Consistency: In engineering, standardization is crucial for ensuring consistency, safety, and quality. Technical writing plays a pivotal role in documenting standards, specifications, and procedures that must be followed during the design, construction, and operation of systems. Standardized technical documentation allows engineers to maintain consistency across projects, facilitates knowledge transfer, and ensures compliance with industry regulations and best practices.
Effective Problem Solving: Engineering projects often involve complex problem-solving scenarios. Technical writing helps engineers break down complex problems into manageable steps, facilitating systematic analysis and resolution. By documenting troubleshooting processes, guidelines, and solutions, technical writers provide engineers with valuable resources that aid in resolving issues efficiently and effectively.
Knowledge Transfer and Training: Technical writing enables the transfer of knowledge from experienced engineers to new team members. By documenting best practices, lessons learned, and standard operating procedures, technical writers help onboard new engineers and ensure continuity within the organization. Training materials, manuals, and guides developed through technical writing empower engineers to acquire the necessary skills and knowledge to work on diverse projects.
Client and Stakeholder Communication: Engineering projects involve interactions with clients and stakeholders who may not possess technical expertise. Technical writing helps bridge this communication gap by translating complex engineering concepts into easily understandable language. Documents such as project proposals, reports, and progress updates provide stakeholders with a clear understanding of project goals, timelines, and deliverables, fostering trust and collaboration.
Safety and Compliance: In many engineering fields, such as civil engineering, mechanical engineering, and chemical engineering, safety is of paramount importance. Technical writing plays a critical role in documenting safety procedures, risk assessments, and compliance guidelines. Engineers rely on these documents to ensure that projects meet regulatory requirements, minimize hazards, and protect the well-being of workers and the public.
Effective Project Management: Technical writing contributes to effective project management by facilitating clear communication, setting project expectations, and documenting project milestones. Project documentation, including project plans, schedules, and progress reports, allows engineers and project managers to track project progress, identify bottlenecks, and make informed decisions to keep projects on track.
Intellectual Property Protection: Technical writing aids in protecting intellectual property by documenting engineering innovations, designs, and inventions. Patents, technical specifications, and research papers help establish ownership and prevent unauthorized use or replication of intellectual property. Technical writers work closely with engineers to accurately document and protect their creative work.

Conclusion:
In the field of engineering, technical writing is not merely a peripheral skill; it is an essential component for success. From clear communication and documentation of design to effective problem-solving and compliance, technical writing plays a pivotal role in ensuring efficient and accurate execution of engineering projects.
#technicalwriting#engineeringcommunication#effectivedocumentation#knowledgetransfer#clearcommunication#standardizationInengineering#problemsolving#projectmanagement#safetyandcompliance#intellectualpropertyprotection
0 notes
Text
💡 𝗦𝘁𝗿𝗮𝘁𝗲𝗴𝗶𝗲𝘀 𝗧𝗼 𝗣𝗿𝗼𝘁𝗲𝗰𝘁 𝗬𝗼𝘂𝗿 𝗜𝗻𝘁𝗲𝗹𝗹𝗲𝗰𝘁𝘂𝗮𝗹 𝗣𝗿𝗼𝗽𝗲𝗿𝘁𝘆

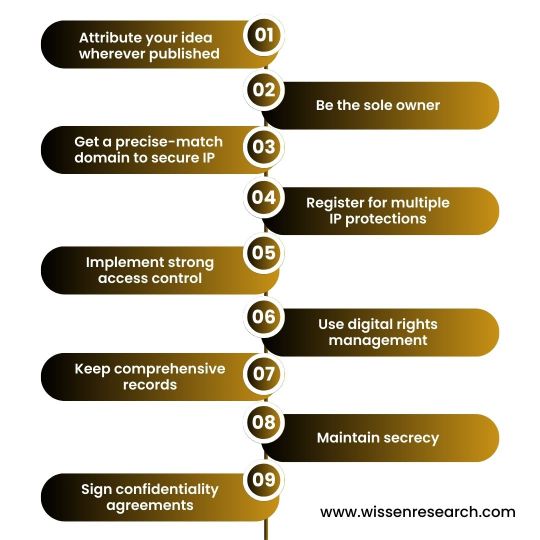
Safeguarding intellectual property or business concepts from theft and replication is becoming increasingly challenging due to the growing accessibility and distribution of information. Regardless of whether your company is a new venture or an established corporation, ensuring the protection of your intellectual property must be of utmost importance. Read the post below to learn more about the importance of safeguarding your ideas in an evolving information landscape.
Click on the link to know more: https://www.wissenresearch.com/4-ways-to-protect-your-intellectual-property/
#IntellectualPropertyProtection #ProtectYourIdeas #SafeguardingIP #IPRights #InnovationProtection #IPEnforcement #InnovationSecurity #IPTheftPrevention #IPLaw #wissenresearch #uspto #wipo #ip #pattent #attorneys
0 notes
Link
If you are looking for patent for your business idea, you have to know how to patent an idea in UK. Here is a guide about how to get a patent for your idea or product.
1 note
·
View note
Text
The TSCM Advantage: Staying One Step Ahead Of Corporate Spies

As we face a highly competitive global marketplace, our company speaks out for intellectual property. Examples of these things are intellectual property, trade secrets, product designs, marketing strategies, and other highly confidential data that is what provides your business with the ability to beat your fellow competitors. Unluckily, corporate spying remains an actual annual danger, and a great number of corporations from different countries face data loss and leakage every year. This is where TSCM advantage, or Technical Surveillance Countermeasures advantages, comes into play. It is important to explain the role of TSCM in thoroughly sweeping and securing the environment against possible electronic and hidden surveillance threats. TSCM is a total IT security alerting system that can find, identify, and destroy the surveillance equipment that is not allowed to find your company's secrets. TSCM is a powerful tool for overcoming corporate espionage. Therefore, the creation of TSCM programs is an effective instrument for combating this type of economic crime.
What is Corporate Espionage?
Corporate espionage includes the act of getting private, confidential, or valuable business information illegally, unethically, or both, which is usually done by spies. This can be done through various methods, including:This can be done through various methods, including: - Infiltration: One possibility involves spy recruitment that infiltrates your own company or taps moles within your organization. - Cybersecurity attacks: using your computer systems illegally to compromise the safety of data. - Physical surveillance: Being aware of surveillance technology means you can avail of it if they dig your offices, conference rooms, or frequently used areas such as a listening device or hidden cameras attached. - Social engineering: Fraudsters use various means to creep up on employees and get them to spill the beans about the secret. One can hardly neglect the fact that the negative effects of corporate espionage loom extremely large. Companies may experience billions of dollars of losses from such theft, suffer reputation damage and legal redress.
The TSCM Advantage
A well-designed program offers several key TSCM advantage in protecting your company's confidential information: - Deterrence: Just knowing that your company takes precautions against TSCM can steer away those who want to spy on your company from attempting to infiltrate your organization. - Early Detection: Organized TSCM inspections would reveal potential devices for surveillance, thereby preventing them from being utilized to steal important data before they are put into use. - Peace of Mind: The outstanding thing about TSCM as a proactive approach is that it gives you the highest possibility to operate with the greatest confidence because you know the steps you are taking to totally ensure the safety of everything you do. - Improved Crisis Management: When you happen to fall victim to data leakage, the TSCM advantage program gives you some privilege to locate the source of the problem and take immediate actions in order to keep damage levels to a minimum.
The Central Points Of An Effective TSCM Program
An effective TSCM program should encompass several key elements: - Threat Assessment: The first step is understanding the respective company threats that each organization has. It is essential to take your industry, the nature of the confidential information you own, and the business relationships you have into consideration to identify where the spying danger is. - TSCM Inspections: It goes without saying that expert and recommended TSCM inspections, which have been planned and scheduled on a regular basis, are obligatory for any chance of finding any hidden surveillance devices. These inspections must be thorough and need to include all places on your premises—offices, conference rooms, common areas, and cars. - Technical Sweeping: The specialists at TSCM resort to tech services and use sophisticated gear to look for "bugged" listening devices, cameras, or other elements of surveillance. With this technology, weapons can detect such devices, despite the fact that some of them are invisible to the eyes. - Employee Awareness: Educating your staff about the risks of our company and how they can identify suspicious activity is part of the first step of the defense. Prepare their response by instructing them on the appropriate data security procedures, and teaching them when to make a report on issues that are snooping related. - Physical Security Measures: Conduct complementary physical security measures together with TSCM as a tool to provide access control systems to CCTV cameras and alarms to raise the level of anonymity.
Implementing a TSCM Program
Here are some steps you can take to implement a TSCM program in your organization: Develop a TSCM Policy: As a formal policy, this should convey the organization's resolve to guard secret data in addition to the methods to conduct the TSCM exams and deploy education and training to workforce members. Assemble a TSCM Team: Assign a group of specialized people who will look after the program of TSCM. This team has to be composed of specialists from departments such as security, IT, and legal. Engage a TSCM Specialist: Partner with a professional firm that has TSCM certification and years of experience, as well as strong competence in early warning, security threat assessment, and modern technology. Ongoing Monitoring: TSCM should not simply be considered one-time. Inspection through expert hands and the training program for the employees are helpful in the constant struggle against corporate espionage. The Cost of TSCM vs. the Cost of a Breach A TSCM program could appear as a hefty budget allocation for what some would view as a security measure. On the one hand, the price for TSCM is a bit irreconcilable when in comparison with possible financial and reputational damages from the corporate spying outcrop, but on the other hand, it is petty considering the overall picture. Breaches of data can set companies back millions of dollars. This is beside the failure of the company to manage the damages to its brand name and customer support. However, a robust TSCM program is to be regarded as a necessary way to prevent losses and to preserve the most important asset of a particular company. Beyond the Basics: TSCM Advantage Considerations Modern TSCM issues go beyond the activity of surveillance itself. While the below-provided fundamental factors will be useful for any TSCM program, there are more sensitive issues related to entities with the highest level of spying risks. Technical Countermeasures (TCMs): In addition to detection, some competent TSCM officers also offer technical countermeasures (TCMS), under the pack that variously interfere with or deceive potential eavesdroppers. This can be achieved by setting up connectivity cutting devices to counter unlawful listening devices and exhibiting noise generators that make it impossible to get audio recordings with clarity. Social Media Monitoring: Social media can now be the home for leaks and attacks that target attempts to subvert one's subconsciousness. Determine hashtags to monitor and apply social media monitoring with your TSCM to identify any suspicious activity or conversations that may involve your company's confidential information. Supply Chain Risk Management: Espionage threats can occur either from the insides of your supply chain or from the outer surrounding areas of your organization. Facilitating the TSCM measures together with the key partners and vendors can be successful in identifying potential exposed areas. This can be done through safety audits of the installations they have and data security procedures that are implemented. Penetration Testing: Repeated tests of the type known as penetration testing (or pen testing) could imitate some attacks by spies and would find technical points of your IT infrastructure vulnerabilities in which spies can make a way through, gain access to your network, and steal data.
Continuous Improvement: TSCM Advantage
The circle of spying is changing permanently, brand new technologies and ways are appearing at the time. Henceforth, it assumes a major objective to retain the commitment to unremitting improvement of the TSCM process. Stay Informed: The Tribal Security and Countering Terrorism (TSCM) team should be enlightened on the dreadful espionage threats and technological advancements in their field that are rapidly arising. Industry publications, conferences, and training can give rise to insights in the industry. Regular Reviews: Undertake TSCM program auditing frequently to determine whether your system works and to find areas for improvement. Apart from that, the threat assessment may need to be reassessed and corresponding inspection procedures revised based on the latest intelligence. Embrace New Technologies: Due to the fact that technology is definitely upgrading, so too should your TSCM program. Due to a high level of ingenuity on both sides, detection devices and counteraction techniques are increasing all the time. For this purpose, it is wise to have financial resources allocated towards these developments to stay on the cutting edge.
Conclusion
An efficient TSCM program, composed of both a detailed plan and an attitude of constant evolution, can give you a major boost in how well you're secured from corporate espionage. While you have to guard your company's confidentiality, it is not a one-time endeavor, but the dynamic and continued process towards it demands vigilance and different strategic approaches to be taken to make sure it is securely protected. Implementing a preventive TSCM strategy constitutes an important investment in maintaining your core competencies and a standard success track for your enterprise. Read the full article
#benefitsofTSCM#corporateespionage#HowtoimplementaTSCMprogram#intellectualpropertyprotection#TSCMadvantage#TSCMforbusinesses#TSCMprogram#TSCMvs.datasecurity
0 notes
Video
tumblr
Legal Process Outsourcing Solutions Company USA
Vee Technologies recognizes the growing importance of intellectual property (IP) protection and has years of in-depth domain knowledge. With our innovative intellectual property solutions, your organization will realize cost reductions and increased efficiency while mitigating potential litigation.
Email : [email protected]
Visit : https://bit.ly/3Y7jSCu
#intellectualproperty#intellectualpropertyrights#intellectualpropertysolutions#intellectualpropertyprotection#intellectualpropertyservices#USAintellectualpropertysolutionscompany#patentlitigation
0 notes