#iCloud Removal Tool
Explore tagged Tumblr posts
Video
تخطي ايكلاود ايفون وايباد Haafedk iCloud Remove tool 4.3 free iCloud / M...
0 notes
Text
Apple Releases iOS 12.4 Beta 2 [Download] Jailbreak for A12 Released Yet?

View On WordPress
#Cydia iOS 12.4#Cydia iOS 12.4.1#Cydia iOS 12.4.2#HACK#icloud activation lock removal#icloud activation lock removal service#icloud activation lock removal tool free IOS 12.4 DOWNLOAD LINKS#IOS 12.4 ELECTRA#IOS 12.4 ENGLISH#IOS 12.4 FREE#IOS 12.4 GUIDE
0 notes
Text
Tech companies and privacy activists are claiming victory after an eleventh-hour concession by the British government in a long-running battle over end-to-end encryption.
The so-called “spy clause” in the UK’s Online Safety Bill, which experts argued would have made end-to-end encryption all but impossible in the country, will no longer be enforced after the government admitted the technology to securely scan encrypted messages for signs of child sexual abuse material, or CSAM, without compromising users’ privacy, doesn’t yet exist. Secure messaging services, including WhatsApp and Signal, had threatened to pull out of the UK if the bill was passed.
“It’s absolutely a victory,” says Meredith Whittaker, president of the Signal Foundation, which operates the Signal messaging service. Whittaker has been a staunch opponent of the bill, and has been meeting with activists and lobbying for the legislation to be changed. “It commits to not using broken tech or broken techniques to undermine end-to-end encryption.”
The UK government hadn’t specified the technology that platforms should use to identify CSAM being sent on encrypted services, but the most commonly-cited solution was something called client-side scanning. On services that use end-to-end encryption, only the sender and recipient of a message can see its content; even the service provider can’t access the unencrypted data.
Client-side scanning would mean examining the content of the message before it was sent—that is, on the user’s device—and comparing it to a database of CSAM held on a server somewhere else. That, according to Alan Woodward, a visiting professor in cybersecurity at the University of Surrey, amounts to “government-sanctioned spyware scanning your images and possibly your [texts].”
In December, Apple shelved its plans to build client-side scanning technology for iCloud, later saying that it couldn’t make the system work without infringing on its users’ privacy.
Opponents of the bill say that putting backdoors into people’s devices to search for CSAM images would almost certainly pave the way for wider surveillance by governments. “You make mass surveillance become almost an inevitability by putting [these tools] in their hands,” Woodward says. “There will always be some ‘exceptional circumstances’ that [security forces] think of that warrants them searching for something else.”
The UK government denies that it has changed its stance. Minister for tech and the digital economy, Paul Scully MP said in a statement: “Our position on this matter has not changed and it is wrong to suggest otherwise. Our stance on tackling child sexual abuse online remains firm, and we have always been clear that the Bill takes a measured, evidence-based approach to doing so.”
Under the bill, the regulator, Ofcom, will be able “to direct companies to either use, or make best efforts to develop or source, technology to identify and remove illegal child sexual abuse content—which we know can be developed,” Scully said.
Although the UK government has said that it now won’t force unproven technology on tech companies, and that it essentially won’t use the powers under the bill, the controversial clauses remain within the legislation, which is still likely to pass into law. “It’s not gone away, but it’s a step in the right direction,” Woodward says.
James Baker, campaign manager for the Open Rights Group, a nonprofit that has campaigned against the law’s passage, says that the continued existence of the powers within the law means encryption-breaking surveillance could still be introduced in the future. “It would be better if these powers were completely removed from the bill,” he adds.
But some are less positive about the apparent volte-face. “Nothing has changed,” says Matthew Hodgson, CEO of UK-based Element, which supplies end-to-end encrypted messaging to militaries and governments. “It’s only what’s actually written in the bill that matters. Scanning is fundamentally incompatible with end-to-end encrypted messaging apps. Scanning bypasses the encryption in order to scan, exposing your messages to attackers. So all ‘until it’s technically feasible’ means is opening the door to scanning in future rather than scanning today. It’s not a change, it’s kicking the can down the road.”
Whittaker acknowledges that “it’s not enough” that the law simply won’t be aggressively enforced. “But it’s major. We can recognize a win without claiming that this is the final victory,” she says.
The implications of the British government backing down, even partially, will reverberate far beyond the UK, Whittaker says. Security services around the world have been pushing for measures to weaken end-to-end encryption, and there is a similar battle going on in Europe over CSAM, where the European Union commissioner in charge of home affairs, Ylva Johannson, has been pushing similar, unproven technologies.
“It’s huge in terms of arresting the type of permissive international precedent that this would set,” Whittaker says. “The UK was the first jurisdiction to be pushing this kind of mass surveillance. It stops that momentum. And that’s huge for the world.”
12 notes
·
View notes
Text
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
iBypasser Ramdisk Tool V2.7 iCloud Bypass Windows Tool
iBypasser Ramdisk Tool is a powerful application designed to bypass iCloud activation on iOS devices running iOS 11-15 without the need for jailbreaking. It provides various functionalities to disable the passcode, back up files, disable the iCloud account by opening the menu, and retrieve the Apple ID and phone number associated with the device. Additionally, it offers the capability to disable the “Hello” screen using the MEID/GSM signal. Please note that bypassing iCloud activation is not endorsed by Apple and may violate their terms of service.
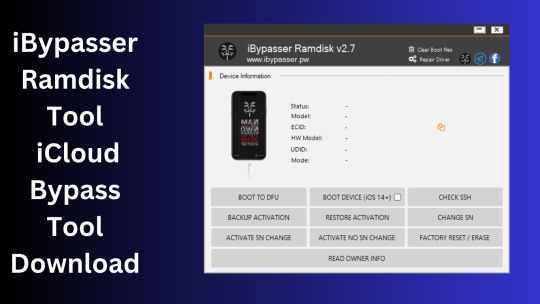
What is iBypasser Ramdisk Tool V2.7?
The iBypasser Ramdisk Tool V2.7 software program was created especially to get around the iCloud activation lock on the iOS device. Customers may use it to give a speedy fix if they find themselves locked out of their devices and unable to access all of the features on their iPhones, iPads, or iPods.
Features iBypasser Ramdisk tool:
Boot Device for iOS 15. x and earlier
Verify SSH
Restore/Backup Activation
Alter SN
Switch on the Hello Device
Go To Owner Info
iOS 15+ (DFU) Data Erasure
Remove Boot File
Changelog!!!
Update: iBypasser Ramdisk AIO v2.0
Resolving boot problems.
DFU Helper was added.
Driver problems were resolved.
Performance augmentation.
How To Use?
You will initially need to register the device’s ECID.
Your MAC notebook should have iBypasser RAMDISK installed. Next, unzip it.
Start your RAMDISK tool after that. then adhere to the directions below.
Enter DFU mode on the iPhone. When you successfully connect your device to DFU mode, the iBypasser RAMDISK Tool will provide you with further alternatives. Activate, Backup Files, Open SSH, Open Proxy, etc.
To open the proxy, type one and press the Enter key. Start SSH by pressing 2; then press 3 to access the backup files.
You may examine the data you successfully backed up on your device in the backup directory.
Second, flash your device with the 3u Tool or iTunes.
Connect your device to DFU mode once you’ve finished flashing it.
Open the proxy after switching the device to DFU mode Type 1. Press 4 again to turn on your gadget.
Readme:
Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1, and Windows 10 (32-bit and 64-bit) are all fully compatible with the program.
Create a Backup: If you want to try the tool described above, create a backup of the personal information stored on the Android smartphone or tablet you intend to utilize. Considering that flashing any recovery or firmware has the potential to harm the device.
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
Click Her
5 notes
·
View notes
Text
PDF Editor iPhone: The Best Ways to Edit and Manage PDFs on Your iPhone
In the mobile-first business world, productivity doesn’t stop when you leave your desk. Whether you're a consultant reviewing contracts on the go, a student annotating research articles, or a legal professional handling client documentation, your ability to work with PDF files directly on your smartphone is crucial. That’s where a PDF Editor iPhone solution comes in.
The iPhone is no longer just a communication device—it's a portable office. Thanks to powerful apps and cloud integration, you can now read, annotate, sign, convert, and even edit PDFs right from your iPhone. This guide will explore the best PDF iPhone tools, features to look for, and practical use cases for professionals who need to manage documents efficiently while mobile.
Why You Need a PDF Editor on iPhone
PDF (Portable Document Format) is the global standard for sharing business documents. From invoices and contracts to manuals and whitepapers, professionals interact with PDF files every day. But working with PDFs used to require a desktop application—until now.
With a PDF Editor iPhone app, you can:
Edit text and images within a PDF
Add or remove pages
Sign documents electronically
Convert other file formats (Word, Excel) to PDF and vice versa
Annotate with highlights, sticky notes, and drawings
Fill out forms directly on your phone
Whether you're working from a coffee shop, traveling for business, or commuting, managing PDF iPhone tasks ensures your workflow doesn’t skip a beat.
Key Features to Look for in a PDF Editor iPhone App
Not all PDF editors are created equal. For professionals, reliability, security, and advanced features are critical. Here are the top functionalities you should expect:
1. Text Editing
A good PDF editor allows you to modify existing text, change fonts, and even reflow content for mobile screens.
2. Annotation Tools
Highlighting, underlining, commenting, and drawing make it easier to review documents collaboratively.
3. Digital Signatures
Add legally binding e-signatures or initial fields quickly, without printing or scanning.
4. OCR (Optical Character Recognition)
This powerful feature scans and converts printed text into editable, searchable content—ideal for scanned PDFs or photos of documents.
5. Cloud Integration
Seamless syncing with services like iCloud, Google Drive, Dropbox, and OneDrive is a must for professionals working across devices.
6. File Conversion
Converting PDFs to Word, Excel, JPG, or vice versa expands what you can do with your documents.
7. Security Features
Password protection, redaction, and encryption are vital when handling sensitive information on mobile.
Best PDF Editor Apps for iPhone in 2025
Here are the top-rated and most powerful PDF editor apps you can use on your iPhone today:
1. Adobe Acrobat Reader
Best for: Enterprise-grade features and reliability
View, annotate, and sign PDFs
Premium version offers full editing and OCR
Deep integration with Adobe Creative Cloud
✅ Trusted by businesses worldwide ❌ Subscription required for full features
2. PDF Expert by Readdle
Best for: Power users and document professionals
Full text editing, page management, and form filling
Integrates with cloud storage
Offers a clean, professional interface
✅ Recognized for speed and usability ❌ Premium plan needed for editing features
3. Foxit PDF Editor Mobile
Best for: Secure document handling and collaboration
Supports real-time collaboration and comments
Includes advanced security features
Lightweight and fast
✅ Great for teams and enterprise environments ❌ Interface not as sleek as some competitors
4. Documents by Readdle
Best for: All-in-one file management and PDF editing
Combines file browser, media player, and PDF editor
Excellent for managing multiple file types
Free version includes basic tools
✅ Ideal for productivity power users ❌ May be too feature-heavy for casual users
5. Apple Files + Markup Tools
Best for: Quick annotations and casual users
Built-in on iOS, no downloads needed
Use Markup for signing, highlighting, and drawing
Integrates with iCloud and third-party services
✅ Free and easy to access ❌ Limited editing capability—no text or form editing
Professional Use Cases: Editing PDF iPhone Files on the Go
Let’s look at some real-world scenarios where a PDF Editor iPhone app becomes essential:
Legal Professionals
Review contracts
Redline clauses
Collect client signatures in the field
Consultants
Annotate client proposals during meetings
Fill out expense reports or work orders
Convert documents to PDF for archiving
Educators and Students
Highlight readings
Add notes for revision
Submit assignments in PDF format
Freelancers
Create and send invoices
Sign NDAs or client contracts
Edit proposals while traveling
These scenarios highlight how PDF iPhone capabilities are central to modern workflows—especially for professionals who value efficiency and agility.
Security and Compliance Considerations
Handling business documents from your mobile device comes with risk. Be sure the PDF Editor iPhone app you use complies with:
GDPR, HIPAA, or other relevant regulations
End-to-end encryption for stored and transferred documents
Face ID or Touch ID for app access
Also, make it a habit to:
Avoid editing confidential files over public Wi-Fi
Enable automatic app updates for the latest security patches
Use password-protected PDFs when sharing sensitive information
Tips for Maximizing Productivity with PDF iPhone Tools
To make the most of your PDF editing capabilities:
Use templates: Save reusable templates for contracts or invoices to save time.
Batch processing: Choose apps that allow merging or splitting multiple PDFs in one action.
Automate workflows: Use Shortcuts (iOS) to automate repetitive PDF tasks like renaming, saving, or emailing.
Cloud sync: Always keep your documents backed up and accessible from desktop and mobile.
Conclusion
Gone are the days when editing a PDF required a desktop and specialized software. With today’s robust and secure PDF Editor iPhone apps, you can handle even the most demanding document workflows from your smartphone. Whether you're closing deals, collaborating on projects, or reviewing important files while on the move, having a reliable PDF editor on your iPhone is a game-changer.
From full-service tools like Adobe Acrobat and PDF Expert to built-in options like Apple’s Markup, professionals now have more options than ever to stay productive—anytime, anywhere.
So if you're serious about working smarter and faster on the go, make sure you're equipped with a PDF iPhone solution that meets your needs.
0 notes
Text
Reliable MacBook Battery Replacement by Apple Experts
Your MacBook is an essential part of your everyday life whether you’re working, studying, creating, or just browsing. But over time, even the best devices can run into one common issue: battery wear and tear. When your MacBook’s battery starts acting up, you need a solution that’s not just quick but reliable. That’s where Apple experts come in, offering dependable MacBook battery replacement services that restore your device’s performance and longevity.
Why MacBook Batteries Need Replacing
MacBooks use lithium-ion batteries, which are known for their efficiency and durability. However, like all batteries, they come with a lifespan—typically around 1,000 full charge cycles. As they age, you’ll begin to notice signs of degradation, such as:
Faster battery drain
Inaccurate battery level readings
MacBook shutting down unexpectedly
Charging taking much longer
A warning in macOS: “Service Battery” or “Battery Condition: Replace Soon”
Ignoring these symptoms can lead to a drop in productivity and even pose safety risks like overheating or swelling. That’s why a timely and reliable battery replacement is key to keeping your MacBook running smoothly.
Why Trust Apple Experts?
Not all battery replacements are created equal. Choosing the right service provider can make a big difference in performance, safety, and peace of mind. Here’s why going with Apple experts ensures the most reliable results:
Apple-Certified Technicians
Apple experts are professionally trained and certified through Apple’s rigorous programs. They have in-depth knowledge of every MacBook model, ensuring precision and care throughout the replacement process.
Genuine Apple Parts
When you go to Apple or an authorized provider, your MacBook will be fitted with a genuine Apple battery—not a third-party alternative. These batteries are specifically designed to meet Apple’s high safety and performance standards.
Safe, Warranty-Backed Repairs
All battery replacements performed by Apple experts are backed by a 90-day guarantee (or longer with AppleCare+). The work is completed using specialized tools in a clean, static-free environment that protects your device.
No Impact on Warranty or AppleCare+
DIY repairs or third-party services can void your warranty. Choosing Apple-certified service keeps your warranty intact and ensures your MacBook stays eligible for future support.
The Step-by-Step Replacement Process
Wondering what to expect during a professional battery replacement? Here’s how the process unfolds when handled by trusted Apple experts:
1. Initial Diagnostics
Your MacBook is connected to Apple’s diagnostic tools to determine the battery’s condition and check for any related hardware issues.
2. Service Estimate & Time Frame
You’ll receive a transparent quote and time estimate—typically between 1 to 3 business days depending on model and service volume.
3. Battery Replacement
Using Apple’s official repair process, the technician safely removes the degraded battery and installs a new one. Care is taken to avoid damaging sensitive components like the trackpad or logic board.
4. Post-Replacement Testing
After the new battery is installed, your MacBook is tested for functionality, charge efficiency, and thermal performance.
How Much Does It Cost?
Battery service costs are relatively consistent and affordable for the peace of mind you receive:
MacBook Air: ~$129
MacBook Pro: ~$199
AppleCare+ users may be eligible for free battery replacement if the battery health has dropped below 80% of its original capacity.
What You Should Do Before Service
To streamline your MacBook’s battery replacement, follow these simple steps:
Back up your data (Time Machine, iCloud, or external drive)
Turn off Find My Mac in your iCloud settings
Remove accessories or protective cases
Bring your charger, if requested
Doing this ensures a smoother handoff and helps Apple experts complete the repair more quickly.
Aftercare Tips for Your New Battery
Once your new battery is installed, it’s important to take care of it properly. Follow these simple tips:
Don’t leave your MacBook plugged in 24/7—let it cycle sometimes
Avoid extreme heat or cold
Use macOS’s Battery Health Management feature
Shut it down if you’re not using it for long periods
Charge it between 20–80% for optimal health
When your MacBook battery needs replacing, don’t take chances with third-party shops or questionable DIY methods. Apple experts provide reliable battery replacements that ensure your MacBook is in safe hands, using genuine parts and certified skills.
From diagnostics to final testing, Apple’s process is designed to give your MacBook new life safely, efficiently, and with care. So if you’re seeing signs of battery trouble, don’t wait. Schedule a service appointment and experience the difference of reliable MacBook battery replacement by Apple experts.
0 notes
Text
How to Unlock iPhone Unavailable Screen
youtube
This is caused by entering the wrong password multiple times. Generally speaking, you can just wait for a few minutes or ten minutes. However, if you have completely forgotten your password and multiple attempts to enter the password do not work, there are three methods you can try:
Method 1: The Best Way to Factory Reset iPhone — TunesKit iPhone Unlocker It's a professional tool for iPhone/iPad/iPod unlocking. Whether you want to factory reset iPhone without passcode, reset iPhone passcode, take off screen time without password, or remove MDM restrictions, this software can help you conduct it in 4 simple steps instantly without complex operations. Thanks to its user-friendly interface and easy-to-conduct operations, you can unlock your iOS devices at home within several minutes, even if you don't know relevant knowledge.
· Step 1 Plug your iPhone into the PC · Step 2 Set your iPhone into the DFU/Recovery mode · Step 3 Inspect the device information and download the iOS firmware · Step 4 Factory Reset your iPhone SE without a passcode
Method 2: Factory Reset iPhone via iTunes You can select Restore iPhone in the summary section of iTunes, so you can directly restore factory settings and iTunes will update you to the latest system.
Method 3: Factory Reset iPhone via iCloud Step 1. Head to icloud.com on your mobile phone or PC. Step 2. Tap on the Find My option, and then choose your iPhone Step 3. Click on the Erase iPhone tab to factory reset your iPhone Step 2. Tap on the Find My option, and then choose your iPhone Step 3. Click on the Erase iPhone tab to factory reset your iPhone
After restoring factory settings, you can write down the new password in a memo or notebook to prevent forgetting it again.
0 notes
Text
iPhone Storage Full? Find and Remove Duplicate Videos with These 5 Methods If you're an iPhone user who loves capturing moments through video, you've likely encountered a common problem: duplicate videos taking up valuable storage space. Whether from accidental double recordings, shared media, or backed-up content, these duplicates can quickly consume gigabytes of storage without you realizing it. Finding and removing duplicate videos on your iPhone not only frees up precious storage space but also helps organize your media library for easier access and management. In this comprehensive guide, we'll explore various methods to identify and remove duplicate videos on your iPhone, from using built-in features to third-party applications designed specifically for this purpose. By the end of this article, you'll have all the tools you need to efficiently manage your video collection and reclaim your iPhone storage. Why Duplicate Videos Accumulate on iPhones Before diving into solutions, it's helpful to understand how duplicate videos end up on your device in the first place: Multiple photo backups: When restoring from different backups or syncing across multiple services (iCloud, Google Photos, etc.) Accidental saving: Downloading the same video multiple times from messaging apps or emails Screen recordings: Creating screen recordings of videos you already have saved Photo sharing: Receiving the same video from different people via AirDrop, Messages, or social media Manual copying: Duplicating videos when organizing files Identifying these patterns can help you prevent duplicate accumulation in the future. Method 1: Using the Built-in Photos App Apple's Photos app includes a basic duplicate detection feature introduced in iOS 16 that can help you locate identical videos. Here's how to use it: Finding Duplicates with the Photos App Open the Photos app on your iPhone Go to the Albums tab at the bottom of the screen Scroll down to the Utilities section Look for and tap on the Duplicates album The app will automatically display all duplicate photos and videos found on your device For each set of duplicates, you'll see options to Merge the files, which keeps the highest quality version and deletes the others Note: This feature only identifies exact duplicates with identical file data. Similar videos with slight differences won't be detected. Method 2: Using the Files App to Manually Search For more control over the process, you can manually search through your videos in the Files app: Open the Files app on your iPhone Navigate to On My iPhone or iCloud Drive where your videos are stored Tap the List icon (three lines) in the top-right corner to change the view Tap on the dropdown arrow and select Sort by Size to group larger video files together Manually check files with similar sizes and names that might be duplicates Preview videos by long-pressing on their thumbnails To delete a duplicate, swipe left on the file and tap Delete While this method requires more effort, it gives you greater control over which files to keep or remove. Method 3: Third-Party Duplicate Finder Apps For more powerful duplicate detection capabilities, third-party apps offer advanced features and algorithms. Here are some top options: Gemini Photos Gemini Photos by MacPaw is one of the most popular duplicate finders: Download Gemini Photos from the App Store Launch the app and allow it to scan your media library Tap on the Videos section Navigate to the Similar or Duplicates category Review the suggested duplicates and select those you want to remove Tap Delete to remove the selected videos Gemini Photos uses smart algorithms to detect not only identical duplicates but also similar videos, making it more effective than the built-in Photos app. Photo & Video Duplicate Cleaner Another excellent option with a focus on media files:
Download Photo & Video Duplicate Cleaner from the App Store Open the app and grant necessary permissions Tap Scan Now to begin analyzing your library Select the Videos tab to focus only on video duplicates Review the found duplicates and check those you want to delete Tap Delete Selected to remove them This app offers a simple interface specifically designed for finding duplicate media files. Method 4: Using iCloud and Mac for Larger Libraries If you have a large video collection, using a Mac with your iCloud account can provide more powerful tools: Ensure your iPhone is synced with iCloud Photos On your Mac, open the Photos app Click on Albums in the sidebar Scroll to Utilities and select Duplicates Filter to show only videos by clicking on the dropdown menu and selecting Videos Review and merge duplicates as needed The larger screen and additional processing power of a Mac make handling large video libraries much easier. Method 5: Smart Storage Management Using iPhone Storage Recommendations Your iPhone offers smart recommendations to manage storage: Go to Settings > General > iPhone Storage Wait for the analysis to complete Check the Recommendations section Look for suggestions related to large videos or duplicated content Follow the provided options to optimize storage Using Optimize iPhone Storage Feature Enable the optimize storage feature to automatically manage video storage: Go to Settings > Photos Enable Optimize iPhone Storage This keeps full-resolution videos in iCloud while storing smaller versions on your device Tips to Prevent Duplicate Videos Preventing duplicate videos is easier than removing them later: Use iCloud Photos consistently: Don't switch between multiple backup services Check before downloading: Verify if you already have a video before saving it again Use the "Save Image" option carefully: In messaging apps, check if you already have the video Organize regularly: Set a monthly reminder to clean up your video library Use Albums: Create logical albums to better track your content Security Considerations When Using Third-Party Apps When using third-party duplicate finder apps, keep these security tips in mind: Only download from the App Store: Avoid sideloaded apps for handling your personal media Check privacy policies: Ensure the app doesn't upload your videos to external servers Review permissions: Only grant necessary access to your media library Look for reputable developers: Choose apps from established companies with good reviews Conclusion Finding and removing duplicate videos on your iPhone doesn't have to be a tedious task. From using the built-in Photos app's duplicates feature to leveraging specialized third-party applications, you have multiple options depending on your needs and preferences. Regular maintenance of your video library not only frees up valuable storage space but also makes your video collection more organized and accessible. By implementing the preventive measures discussed, you can minimize duplicate accumulation in the future and keep your iPhone running smoothly. Whether you choose to use Apple's native tools or third-party solutions, taking control of duplicate videos will enhance your iPhone experience and ensure you always have space for capturing new memories without worrying about storage limitations.
0 notes
Text
Selling an iPhone? Here’s How to Maximize Your Profit
Selling your iPhone is a good idea, be it upgrading to a newer version or just getting money out of a phone you barely use. But not everyone leaves with the most favorable settlement. The price you receive when you sell an iPhone varies greatly depending on how well you’ve prepped your device and who you sell it to.
We’ve put together some practical advice for getting the most profit from your iPhone sale.
Time It Right
The timing greatly affects the potential of you earning. Demand for iPhones on the resale market typically drops when Apple announces a new phone.
Maintain It in Top Shape
Buyers are willing to pay extra for a phone that looks and operates like new. Avoid scratches, dents, or cracks by always using a protective case and screen guard on the phone while in your possession. An example in mint condition is always going to get you better offers than an example that has been worn.
Back Up and Erase All Data
And you’ll want to back up your data to iCloud or a computer and then perform a factory reset, wiping all the information from the device before listing for sale. Not only does this protect your privacy, but it also lets the buyer know the phone is ready for a new user. And don’t forget to disable Find My iPhone and remove the device from your Apple ID, or the new owner might have activation lock problems.
Include all accessories and packaging.
Asking for accessories including the charging cable, adapter and the original box can increase your asking price. These add-ons increase the buyer’s perception of value and suggest that you’ve treated your device well.
Clean the Phone Thoroughly
A well-polished iPhone makes a better first impression. Sanitize the screen, the camera lenses and gently dust off the charging port and the speaker areas. First impressions matter — just like selling a car or home.
Know Your iPhone’s Worth
Spend a few minutes researching your model, storage capacity and condition to see what you can expect on the current market. Online pricing tools and resale sites can provide an estimate of what you can expect. An awareness of your phone’s fair value can prevent you from accepting less than it’s worth.
Place the Right Marketplace to Sell iPhone
Where you sell your phone makes a considerable difference in how much you earn. On the flip side, there are peer-to-peer marketplaces or classifieds that may give you big returns, but with it comes the risk of fishy buyers, no guarantees, or long term payments. However, selling through a trusted medium makes the whole process much smoother, safer, and comparatively swift.
Get good photos in and write a clear description
If you’re selling your iPhone online, making sure the photos are distinct and a detailed description is in the listing will ensure potential serious buyers pay you a good price for it. Include model, storage size, battery health, and remaining warranty. Disclose the condition honestly — transparency engenders trust and avoids frivolous disputes later.
Think About Selling Instead of Selling Later
But the longer you wait, the less consonance your iPhone will have.) And no matter how good that car is, it’s going to depreciate when newer models come out and older ones come out of its software support window. If your iPhone works, but you’re not using it anymore, selling it now is the best and most profitable way forward in this regard.
Conclusion: Sell iPhones the Smart Way with Budli
To truly maximize profit and enjoy a hassle-free selling experience, consider selling your iPhone through Budli. As a trusted platform for refurbished phones and pre-owned devices, Budli ensures that you get a fair price for your iPhone—without the risks of dealing with unknown buyers or shady platforms. Budli handles the process with professionalism, offering secure transactions, prompt service, and a reliable way to sell iPhone quickly and efficiently. If you're ready to turn your old iPhone into extra cash, Budli is the smart choice to make.
#refurbished phones#sell your phone#sell phone#sell phone online#sell an iPhone#sell iphone#sell ipad
0 notes
Text
Jailbreak iOS 17.7.6
Apple released iOS 17.7.6 with new bug fixes and performance updates, but many iPhone users still want more than what Apple allows. That’s where Jailbreak iOS 17.7.6 comes in. With a jailbreak, you can fully customize your iPhone, download third-party apps, and enjoy features Apple normally blocks.

This guide will show you everything you need to know about Jailbreak iOS 17.7.6, including what it is, how it works, the best tools to use, and how to get started safely. We’ll also explain why iNstantJB is the best and easiest way to jailbreak your device.
What Is Jailbreak iOS 17.7.6?
Jailbreak iOS 17.7.6 is the process of removing Apple’s software limits on iPhones and iPads. Once you jailbreak, you can access new features, install apps from outside the App Store, and customize your device in usually restricted ways.
People jailbreak their iPhones to gain full control over the software. It’s like having admin rights on your own device. You can change how your phone looks, improve its performance and do things Apple normally blocks.
Why Do People Jailbreak iOS 17.7.6?
There are many reasons why people choose to Jailbreak iOS 17.7.6:
Install themes and icon packs to change how your device looks
Use advanced tweaks that improve battery life, speed, and functionality
Download third-party apps that Apple doesn’t allow
Sideload IPA files for modded apps and games
Remove system limitations for a more flexible experience
In short, jailbreaking gives you complete control. Apple’s rules no longer limit you.
Is Jailbreak iOS 17.7.6 Safe?
Yes — as long as you use trusted tools. Jailbreaking itself is not illegal or harmful when done the right way. Tools like iNstantJB make the process safe, simple, and fully reversible.
Here are a few safety tips before jailbreaking:
Back up your iPhone using iCloud or iTunes
Use a tool that supports Jailbreak iOS 17.7.6
Follow the steps carefully and don’t rush
If something goes wrong, you can easily restore your phone to factory settings and remove the jailbreak.
Download Jailbreak iOS 17.7.6 App
If you're ready to jailbreak, the first step is downloading the right tool. The best and most updated version of the Jailbreak iOS 17.7.6 app can be found at:
https://www.cydiafree.com/cydia-download-ios-17-1-2-3-4-5-6.html
This website offers a secure and reliable version of the jailbreak tool for iOS 17.7.6. It supports most iPhones and iPads, and the process is beginner-friendly.
iNstantJB – The Best Way to Jailbreak iOS 17.7.6
Many jailbreak tools are online, but iNstantJB stands out as the easiest and safest way to Jailbreak iOS 17.7.6.
What makes iNstantJB different?
You don’t need a PC or Mac
Everything runs from your Safari browser
No complicated steps or tech knowledge required
Compatible with all devices running iOS 17.7.6
Safe, fast, and reversible
How to Use iNstantJB:
Open Safari on your iPhone
Visit the official iNstantJB website
Tap “Start Jailbreak”
Let the tool check your iOS version
Follow the instructions on screen
Complete the process and enjoy your jailbreak!
That’s it — no cables, no risk, and no stress. iNstantJB is the most user-friendly way to get the full jailbreak experience.
What You Can Do After Jailbreaking iOS 17.7.6
Once you’ve used iNstantJB to Jailbreak iOS 17.7.6, a new world opens up. You’ll be able to:
1. Customize Your iPhone
Use tools like SnowBoard to apply themes change icons, fonts, and animations. Your iPhone will finally look the way you want it to.
2. Install Powerful Tweaks
Add features Apple doesn’t offer — like better multitasking, volume sliders, screen recording options, and more. Tweaks give your device extra abilities that improve the user experience.
3. Use Third-Party App Stores
After jailbreaking, you can install stores like Cydia, Sileo, and Zebra. These offer apps and tools you’ll never find on the App Store.
4. Sideload IPA Files
Want to install hacked games, emulators, or apps removed from the App Store? With jailbroken device, you can easily sideload any IPA file using tools like AltStore or Sideloadly.
5. Block Ads Everywhere
Install advanced ad blockers that remove ads from Safari, YouTube, and other apps. You’ll get a faster and cleaner experience.
Popular Tweaks After Jailbreak iOS 17.7.6
Here are some amazing tweaks you can try once you’ve jailbroken your device:
SnowBoard – A powerful theming tool
AppSync Unified – Install unsigned or modded apps
iCleaner Pro – Clean up junk files and free storage
Barmoji – Add emojis to your keyboard bar
CCModules – Customize Control Center with new toggles
Cylinder – Add page animations like in Android
These are just the beginning. The jailbreak world has thousands of tweaks waiting for you.
Devices Supported by Jailbreak iOS 17.7.6
Jailbreak iOS 17.7.6 works on a wide range of iPhones and iPads:
iPhone 15 / 15 Plus / 15 Pro / 15 Pro Max
iPhone 14 Series
iPhone 13 / 12 / 11
iPhone XS / XR / X
iPhone SE (2nd and 3rd Gen)
Most iPads running iPadOS 17.7.6
Ensure your iOS version matches by going to Settings > General > About.
Can You Undo the Jailbreak?
Yes! Jailbreaking is not permanent. You can undo it at any time by:
Going to Settings > General > Transfer or Reset iPhone
Selecting “Erase All Content and Settings”
Confirming the reset
This will wipe your iPhone and remove the jailbreak completely. You can also restore a backup through iTunes or Finder to regain your data.
Jailbreak iOS 17.7.6 – Frequently Asked Questions
1. Will Jailbreak iOS 17.7.6 void my warranty?
Technically yes, but if you remove the jailbreak before visiting an Apple Store, they won’t know. It's completely reversible.
2. Can I still use the App Store after jailbreaking?
Yes! Jailbreaking doesn’t block the App Store. You can continue downloading apps just like before.
3. Is my data safe during the jailbreak?
Your data remains safe as long as you use trusted tools like iNstantJB. Still, it’s always smart to back up your device before starting.
Final Thoughts
Jailbreak iOS 17.7.6 is the key to unlocking everything your iPhone is capable of. You can customize your phone, install powerful tweaks, and enjoy apps Apple doesn’t allow. It’s safe, simple, and worth trying — especially with tools like iNstantJB that simplify the process.
To get started, download the Jailbreak iOS 17.7.6 app today from:
https://www.cydiafree.com/cydia-download-ios-17-1-2-3-4-5-6.html
Then, use iNstantJB to jailbreak your device and enjoy a world of freedom. Your iPhone will never be the same again.
0 notes
Text
iPhone Screen Replacement: A Complete Guide for Users
Accidentally dropped your iPhone and ended up with a cracked screen? You’re not alone. A damaged screen is one of the most common issues iPhone users face and luckily, it’s also one of the most fixable. Whether it’s a spiderweb crack, dead pixels, or a completely black screen, there are reliable solutions to get your device looking and functioning like new.
In this article, we’ll break down everything you need to know about iPhone screen replacement, from common problems and repair options to pricing and what to expect from the process.
🔍 Why iPhone Screen Replacement Is Important
Your iPhone’s screen isn’t just for display it’s the main way you interact with your device. Cracks and display issues can:
Affect touch responsiveness
Interfere with Face ID or camera performance
Lead to further internal damage over time
Lower resale value
Cause injury from broken glass
That’s why choosing to replace a cracked iPhone screen promptly is both a smart and safe decision.
⚠️ Common Signs You Need iPhone Screen Repair
Cracked or shattered glass
Ghost touch (the screen acts on its own)
Display flickering or dead spots
No image or black screen
Discoloration or lines on the screen
Touch not working at all
Even small cracks can worsen over time, so don’t wait too long to fix them.
🔧 iPhone Screen Replacement Options
1. Apple Store or Authorized Service Provider
Uses genuine Apple parts
Maintains your warranty (if applicable)
Ideal for newer models (iPhone 12, 13, 14, 15)
iPhone screen repair cost may be higher
Tip: If you have AppleCare+, screen replacement may cost as little as $29.
2. Third-Party Repair Shops
Often more affordable
Quick service (usually 30–60 minutes)
May use high-quality aftermarket or refurbished OEM screens
Good option for out-of-warranty iPhones
Search terms like “iPhone screen repair near me” can help you find trusted local providers.
3. DIY Screen Replacement
Risky unless you’re experienced
Requires special tools and replacement parts
May void any warranty
Face ID or Touch ID can be permanently disabled if not handled properly
Not recommended unless you’re confident with electronics and repairs.
🛡️ What to Check Before Replacing Your iPhone Screen
Back up your data (iCloud or iTunes)
Turn off Find My iPhone
Remove passcode if required by the technician
Ask about warranty on parts and labor
Inquire if they use original or high-grade compatible parts
🏪 How to Choose the Right Repair Service
When looking for a provider to fix a broken iPhone screen, keep these tips in mind:
Read online reviews and ratings
Look for certifications or Apple authorization
Ask about repair time and quality of parts
Check if they offer a warranty on the screen replacement
Choose a service that also checks for hidden damage
📌 Final Thoughts
A cracked iPhone screen doesn’t have to mean the end of your phone’s life. Whether you visit the Apple Store or a trusted third-party repair shop, you can replace your iPhone screen quickly and get back to normal use in no time.
Before rushing into a repair, weigh your options, consider the cost, and make sure your data is backed up. And next time, consider a good case or screen protector to avoid future mishaps!
1 note
·
View note
Text
Spying on your cloud and data
Many or even most use one or more cloud storage. Such as Microsoft OneDrive, Google Drive, Apple iCloud etc.
Same goes for cloud based mail services by the same companies and more.
It is a well established FACT that all of these service providers do their best to scan your files and mails for their own benefit.
"So what you respond I have nothing to hide!" Look at my posts from Feb 12 & Feb 15 in this blog. Then consider this answer again.
"But really if I send or store something that I don't want anyone to see I save in a password protected zip file."
Good for you but first if you are sending it to someone you must let them know the password. "Duh! I send that in a separate email of course!"
Unfortunately it has been discovered that Microsoft is scanning every file including password protected files. All they have to do is scan your mail to the same recipient for the password.
They have also been confirmed doing the same with files on your OneDrive. This is nothing new in the information security business, but now it is all but confirmed.
Now this is only pointing a finger at Microsoft. But I am willing to bet that all the other tech giants are in fact doing the exact same thing. And they all have vast computer power to scan and de-crypt your information. Especially with the new AI tools that they are now enabling on your own device.
As one of the giants expressed it "We want to see what you see, hear what you hear and know what you know"
They do that on your computer and on your phone, without your consent.
The only way around it is to use Linux on your computer and not use any cloud service.
And use your phone for silly games or text messages like "Don't forget to buy milk".
There is also an emerging number of phones called "de-googled" phones where all Google spying is completely removed but that may not be for everybody just yet.
0 notes
Text
iCloud Bypass 2024 Free Tool Install With Windows Crack
This tutorial reviews and compares the best iCloud Bypass Tools 2024 to help you with the iCloud/iPhone activation lock removal/bypass process: SOLVED iPhone iCloud Locked How to Unlock If Forgot Password 2024. Our paid checkers offers a variety of IMEI Check Services that provide all the information about your device, fast and accessible! With iCloud Status check you can get information if that…
View On WordPress
2 notes
·
View notes
Text
Once upon a simpler internet, web browsers were just that—browsers. A tool for checking emails, reading the news, and occasionally downloading something you hoped wasn't riddled with viruses. Fast forward to today, and they've become sophisticated ecosystems of their own, shaping how billions interact with the digital world. Browsers are no longer passive windows to the web—they're powerful platforms, setting the rules of engagement. Whether you're on Chrome streamlining your day with Google's suite, or using Firefox to fend off every tracker in sight, your browser choice says more about you than your social media bio ever could. But with great power comes, well, a tonne of competition. Chrome still reigns supreme, but challengers like Edge, Firefox, Brave, and Opera are rewriting the playbook. Now throw artificial intelligence into the mix, and the browser landscape is anything but static. Welcome to the era where your browser might know what you want before you even type it. Google Chrome: King of Speed, But Watched Closely With a global market share of 90.15% as of February 2025, Google Chrome is still the heavyweight champion of web browsers. It wins users over with blazing speed, smooth performance, and near-flawless integration with Google's services. From Gmail to Docs to YouTube, it all feels seamless. Under the hood, Chrome's V8 JavaScript engine and smart memory handling keep things running faster than a barista on a Monday morning. Features like Tab Groups and Memory Saver address real-world problems—like the never-ending tab chaos we've all faced. Security? Chrome is no slouch. Enhanced Safe Browsing alerts users of risky sites, while phishing and malware protection updates are rolled out regularly. And while Chrome has faced its fair share of regulatory heat for its dominance, it keeps pushing forward, especially in the AI space, with experimental tools for tab search and smarter organisation. Cross-platform consistency is the cherry on top. Chrome works equally well on Windows, macOS, Android, and iOS, making it a no-brainer for anyone living in multiple digital worlds. Apple Safari: Private by Design, Perfect for Apple Devotees For those deep within the Apple ecosystem, Safari offers an experience tailored for performance, privacy, and simplicity. Integrated with features like Intelligent Tracking Prevention and Private Relay, Safari is Apple's answer to the growing chorus of privacy-conscious users. Safari's WebKit engine is laser-focused on Apple hardware, squeezing every bit of efficiency possible from MacBooks and iPhones. The result? A snappy, battery-friendly browser that doesn't drain your device—or your patience. Minimalism is key. Safari's clean design removes distractions, letting web content shine. Its continuity across devices through features like iCloud Keychain and Handoff makes it a solid choice for those already invested in Apple's ecosystem. Mozilla Firefox: The Open-Source Crusader For the control freak in all of us (no judgement), Firefox brings unmatched privacy, transparency, and customisation. Features like Enhanced Tracking Protection and Firefox Relay go beyond the basics, offering users the chance to truly shield their data. Firefox's Quantum engine makes it speedy, while its open-source ethos keeps it honest. It's also the browser of choice for developers and internet idealists who believe in the open web. Oh, and the extension ecosystem? Vast and glorious. Microsoft Edge: The Polished Contender With AI Flair Built on Chromium, Edge brings the familiarity of Chrome with a Microsoft twist. It's fast, well-integrated with Windows, and features clever tools like Sleeping Tabs to save resources. But its real party trick is Copilot—a built-in AI assistant that summarises pages, generates content, and offers intelligent insights. For productivity enthusiasts and Windows power users, Edge is a compelling alternative to Chrome. Brave Browser: Privacy, Performance, and Tokens
Brave does not mess about when it comes to privacy. It blocks ads and trackers by default, loads pages faster, and even includes a crypto wallet. For the curious and cautious alike, Brave offers something refreshing. The unique Brave Rewards system lets users earn Basic Attention Tokens (BAT) for viewing privacy-respecting ads—a bold attempt to change the economics of browsing. Plus, Tor integration in private mode allows for anonymous exploration. Opera: The Quirky Veteran With Fresh Tricks Opera isn't trying to be Chrome-lite. It brings its own flair to the browser scene with features like a built-in VPN, messenger integration, and a sidebar that lets you get things done without hopping between tabs. And for gamers? Opera GX is specifically designed with CPU and RAM limiters, plus Twitch integration. Add in Opera's new AI Prompts, and it's clear the browser still knows how to innovate. Fun Fact: Opera was the first major browser to introduce tabbed browsing back in 2000—long before it became standard across the board. Into the Shadows: Browsers and the Dark Web Curiosity may not kill the cat, but it could certainly compromise your device. Accessing the dark web isn't illegal, but it's fraught with risk. The gold standard here is Tor Browser, which routes your data through multiple relays to hide your identity. While Brave offers some Tor integration, only Tor Browser offers full onion site access and anonymity. For anyone venturing into this murky zone, basic rules apply: disable JavaScript, avoid downloads, and for goodness' sake, never use your real name. Pairing Tor with a trusted VPN is like locking your doors and setting the alarm. In short, the dark web is not for casual browsing—treat it with caution and respect. Compatibility and Emerging Trends: Where Are We Heading? Thanks to open standards like HTML5 and CSS3, most modern browsers play nicely with the web. But when it comes to proprietary features or rendering quirks, developers still need to test across multiple platforms to ensure a smooth user experience. Several exciting trends are influencing how we browse: Enhanced privacy through better tracking protection and integrated VPNs AI tools for summarising content and writing assistance Better memory and CPU management, particularly for multitaskers drowning in tabs Productivity features like tab groups and content organisation Decentralised web tech like IPFS, offering greater control over data As these trends evolve, the modern browser becomes less a passive tool and more a helpful partner in daily life. The AI Era: Browsers That Think For You Welcome to the new frontier: browsers that not only respond but anticipate. With artificial intelligence integrated at the core, the next wave of browsers will behave more like assistants. Expect features like: Natural language search, making search engines feel conversational Real-time content summarisation to save time and mental bandwidth Sentiment analysis of online content, helping filter credible sources Automated form filling and booking based on previous habits Personalised dashboards, driven by browsing habits and preferences In the not-so-distant future, the browser will understand what you need before you ask. From protecting against phishing to recommending news, AI is redefining the browsing experience, one click at a time. Browser Market Share Breakdown Here’s how the main browsers currently stack up across devices: Global and Platform-Based Browser Market Share (as of February 2025) Browser NameGlobal Market Share (%)Desktop Market Share (%)Mobile Market Share (%)Google Chrome90.1565–7061.80Apple Safari24.3615–2024.36Mozilla Firefox2.575–100.53Microsoft Edge5.235–70.47Brave Browser1.00N/AN/AOpera2.50N/AN/A Browser Features Comparison An at-a-glance comparison of each browser's core strengths and differentiators: Feature Comparison: Privacy, AI, and Ecosystem Integration
Browser NamePrivacy FocusAI FeaturesPerformance FocusEcosystem IntegrationUnique FeaturesGoogle ChromeEnhanced Safe Browsing, Privacy Sandbox (Ongoing)Tab Search and Organisation (Experimentation)V8 JavaScript Engine, Memory SaverGoogle EcosystemTab GroupsApple SafariITP, Private Relay, Minimal TrackingNone MentionedWebKit Engine OptimisationApple EcosystemMinimalist UIMozilla FirefoxEnhanced Tracking, Firefox RelayNone MentionedQuantum Project ImprovementsNoneExtensive Customisation and ExtensionsMicrosoft EdgeTracking Prevention, InPrivate BrowsingCopilot (Summarisation, Insights)Optimised for Windows, Sleeping TabsMicrosoft EcosystemMicrosoft 365 IntegrationBrave BrowserAd/Tracker Blocking, Tor Integration (Private)Brave Search AI AnswerFast Loading via BlockingNoneBAT Rewards, Built-in Crypto Wallet, VPN/FirewallOperaBuilt-in VPN, Tracker BlockingAI Prompts (Writing, Translation, etc.)CPU/RAM Limiters (GX), Resource ManagementFlow FeatureGX Browser for Gamers, Integrated Messengers Conclusion: Your Browser, Your Gateway The web browser landscape is more than just a tech battleground—it's a reflection of how we live online. From Chrome's domination and Safari's privacy-first approach, to Firefox's transparency, Edge's AI smarts, Brave's user-first model, and Opera's bold features, every browser has its niche. But what unites them all is the race towards a smarter, more personalized, and more private browsing experience. With AI now entering the fray, our digital journeys are about to become smoother, sharper, and far more intuitive. So the next time you open a tab, think about what your browser says about you. Because in today's web, your browser isn't just how you see the internet—it's how the internet sees you.
1 note
·
View note