#iCloud Customer Service Phone Number
Text
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
iBypasser Ramdisk Tool V2.7 iCloud Bypass Windows Tool
iBypasser Ramdisk Tool is a powerful application designed to bypass iCloud activation on iOS devices running iOS 11-15 without the need for jailbreaking. It provides various functionalities to disable the passcode, back up files, disable the iCloud account by opening the menu, and retrieve the Apple ID and phone number associated with the device. Additionally, it offers the capability to disable the “Hello” screen using the MEID/GSM signal. Please note that bypassing iCloud activation is not endorsed by Apple and may violate their terms of service.
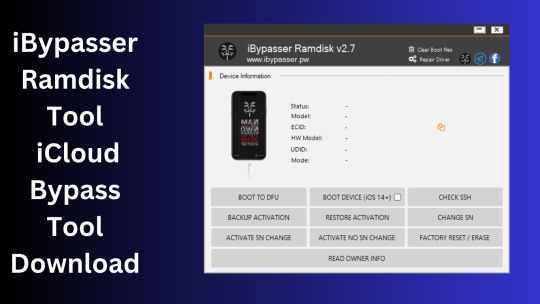
What is iBypasser Ramdisk Tool V2.7?
The iBypasser Ramdisk Tool V2.7 software program was created especially to get around the iCloud activation lock on the iOS device. Customers may use it to give a speedy fix if they find themselves locked out of their devices and unable to access all of the features on their iPhones, iPads, or iPods.
Features iBypasser Ramdisk tool:
Boot Device for iOS 15. x and earlier
Verify SSH
Restore/Backup Activation
Alter SN
Switch on the Hello Device
Go To Owner Info
iOS 15+ (DFU) Data Erasure
Remove Boot File
Changelog!!!
Update: iBypasser Ramdisk AIO v2.0
Resolving boot problems.
DFU Helper was added.
Driver problems were resolved.
Performance augmentation.
How To Use?
You will initially need to register the device’s ECID.
Your MAC notebook should have iBypasser RAMDISK installed. Next, unzip it.
Start your RAMDISK tool after that. then adhere to the directions below.
Enter DFU mode on the iPhone. When you successfully connect your device to DFU mode, the iBypasser RAMDISK Tool will provide you with further alternatives. Activate, Backup Files, Open SSH, Open Proxy, etc.
To open the proxy, type one and press the Enter key. Start SSH by pressing 2; then press 3 to access the backup files.
You may examine the data you successfully backed up on your device in the backup directory.
Second, flash your device with the 3u Tool or iTunes.
Connect your device to DFU mode once you’ve finished flashing it.
Open the proxy after switching the device to DFU mode Type 1. Press 4 again to turn on your gadget.
Readme:
Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1, and Windows 10 (32-bit and 64-bit) are all fully compatible with the program.
Create a Backup: If you want to try the tool described above, create a backup of the personal information stored on the Android smartphone or tablet you intend to utilize. Considering that flashing any recovery or firmware has the potential to harm the device.
iBypasser Ramdisk Tool V2.7 iCloud Bypass Tool Download
Click Her
3 notes
·
View notes
Text
iPhone Data Recovery: How to Retrieve Lost Data from Your Device

Losing data on your iPhone can be a frustrating experience, whether it’s photos, contacts, messages, or important documents. Accidental deletions, software glitches, or hardware failures can all result in lost data. Fortunately, iPhone data recovery services, such as those provided by Apple Expert, offer a solution to recover your valuable information.
Common Causes of Data Loss
Accidental Deletion: This is perhaps the most common cause of lost data. Users often mistakenly delete files, messages, or photos that they later realize were important.
Software Update Issues: Occasionally, updating to a new iOS version can cause unexpected data loss, particularly if the backup process was incomplete.
Physical Damage: Water damage, drops, and other forms of physical harm can make it difficult to access or recover data.
Forgotten Passcodes: If you're locked out of your device due to a forgotten passcode, regaining access to your data can require specialized recovery tools.
Jailbreaking: While jailbreaking an iPhone offers more customization options, it also opens the door to increased risks of data loss or corruption.
Steps to Take After Data Loss
Stop Using the Device: If you suspect data loss, it’s essential to stop using your iPhone immediately. Continued use may overwrite the deleted data, making it more difficult to recover.
Check Your Backup: Before considering professional recovery services, check whether you have recent backups in iCloud or iTunes. If a backup is available, restoring your iPhone to a previous state may solve the problem.
Seek Professional Help: If backups aren’t available or they don’t contain the lost files, professional iPhone data recovery services can offer advanced tools to retrieve your information.
iPhone Data Recovery Methods
Using iCloud Backup: If your iPhone was backed up to iCloud before the data loss, you might be able to recover your data by restoring from the backup.
Go to Settings > General > Reset > Erase All Content and Settings.
After erasing the content, follow the setup process and choose Restore from iCloud Backup.
Using iTunes Backup: If you have synced your iPhone with iTunes, you can restore your lost data using this method.
Connect your iPhone to your computer and open iTunes.
Select your device and choose Restore Backup.
Select the most recent backup and click Restore.
Third-Party Software: Several third-party applications are available to help recover lost iPhone data without a backup. These tools connect to your device, scan it for recoverable files, and allow you to retrieve what was lost.
Professional Data Recovery Services: If you can’t recover the data yourself or the issue is due to physical damage, professional recovery services like Apple Expert use specialized tools to recover data. Their experts can retrieve data from damaged devices or corrupted files that may be beyond the scope of standard recovery tools.
What Data Can Be Recovered?
Professional iPhone data recovery services can often retrieve a wide variety of lost data, including:
Photos and Videos: Personal memories, family pictures, and recorded videos can all be restored.
Contacts: Lost phone numbers and email addresses can be recovered.
Messages: Whether it's iMessages, SMS, or MMS, your lost conversations may be restored.
Documents: Important work files, PDFs, and other documents stored on your iPhone can be retrieved.
App Data: Information from apps, such as notes, calendars, and browsing history, can also be recovered in some cases.
How Long Does iPhone Data Recovery Take?
The time required for iPhone data recovery depends on the extent of the damage and the amount of data that needs to be recovered. In most cases, professional recovery can take anywhere from a few hours to several days. The complexity of the issue, such as physical damage or encrypted data, can also influence the duration of the recovery process.
Preventing Future Data Loss
To avoid the inconvenience of data loss in the future, consider the following precautions:
Regular Backups: Regularly backing up your iPhone to iCloud or iTunes ensures that even if data loss occurs, you can easily restore your device to a previous state.
Enable iCloud Sync: By enabling iCloud sync for essential apps such as Photos, Contacts, and Notes, your data is constantly updated and saved in the cloud.
Use a Passcode and Face ID: Adding a passcode and enabling Face ID can help secure your phone from unauthorized access.
Avoid Jailbreaking: While it may seem appealing to jailbreak your device, it increases the risk of data corruption and loss.
Why Choose Professional Data Recovery?
Choosing a professional iPhone data recovery service like Apple Expert comes with several advantages:
Expertise: Professional technicians are trained to handle complex data recovery processes and can retrieve data even from physically damaged devices.
Advanced Tools: They use advanced data recovery software and hardware tools that are not available to the general public.
Safe Process: Professionals ensure that your iPhone’s hardware and software are not further damaged during the recovery process.
Losing important data on your iPhone doesn’t have to be a permanent problem. By taking the right steps and seeking professional help, you can recover photos, messages, and other crucial data. Services like Apple Expert offer reliable and secure iPhone data recovery solutions, helping you retrieve your lost files efficiently.
0 notes
Text
Is Apple Still the Most Valuable Tech Company?

Apple has long held the crown as the most valuable tech company. Known for its sleek designs and user-friendly products, Apple has a loyal customer base. But is Apple still the leader in tech value? Many wonder if competitors like Microsoft, Amazon, and Google are closing the gap. Let’s dive into the current state of Apple’s value and why it still remains a tech giant.
Apple has a rich history of innovation. Think back to 2007 when the first iPhone was launched. The world was amazed by a device that combined a phone, music player, and internet browser. People lined up for hours to get their hands on one. This type of innovation became Apple’s hallmark. The iPhone, iPad, and MacBook became symbols of success. Customers would pay premium prices for these products, knowing they were getting quality.
However, the tech landscape has changed. Other companies have caught up, offering similar features at lower prices. Samsung, for example, has developed high-end smartphones that rival the iPhone. Google’s Android operating system is popular worldwide. Microsoft’s software solutions are deeply integrated into the business world. Despite this competition, Apple still leads in certain areas. The company’s focus on user experience, security, and privacy sets it apart. Apple’s products work seamlessly together, creating a cohesive ecosystem that keeps users hooked.
Apple also continues to break records in revenue and profit. In 2023, Apple’s revenue surpassed $400 billion. This was driven by strong sales of the iPhone 14 and the growth of its services segment, which includes Apple Music, iCloud, and the App Store. Apple's brand loyalty is unmatched. Surveys show that iPhone users are unlikely to switch to another brand. This loyalty keeps Apple at the top, even as competition grows.
In conclusion, while competitors are strong, Apple remains the most valuable tech company. Its focus on innovation, user experience, and brand loyalty has kept it ahead. Apple has proven that it can adapt and thrive in a changing market. For now, it seems that Apple will continue to lead the tech world.
Discover biznasname: Your Comprehensive Source for USA Contact Information
For in-depth access to extensive USA contact details, explore the biznasname directory. Offering a wide array of listings, this resource ensures you can find specific contacts across various industries and regions within the United States. Whether you're searching for business contacts, customer service numbers, or professional connections, biznasname is a dependable platform to streamline your search. Utilize its userfriendly interface and vast database to access the most relevant and current contact information tailored to your needs. Efficiently uncover detailed American business contact information with the biznasname directory today.
0 notes
Text
iPhone Carrier Unlocking: A Step-by-Step Guide
It is apple time in the present. You might be thinking, Why is this stated? But of course, people in modern times don’t like apples as a fruit in their diet. Instead, they will have all the gadgets that have the Apple brand as their logo. There are a series of products from this brand, and everybody uses one or another device made by it. Of all these things, the iPhone is the most used, and most people have it. In this article, you will be reading about how to get the iPhone phone model to unlock Apple iPhone 12 and unlock apple iPhone 13 pro max So, to know more about the same continue reading it.
Overview of carrier locking

Check that your iPhone is Suitable for Unlocking
When you unlock it, you must ensure that this phone model or the device is appropriate for unlocking. Here are a few key benchmarks:
– Contract Status: Secure your contract is finished or the iPhone is fully paid off.
– Outstanding Pays: Confirm your account has no outstanding expenses or dues.
– iPhone Condition: The iPhone should not be registered as lost or robbed.
You can find this knowledge by logging into your carrier’s online account portal or getting customer support.
Gather the required information
To unlock your iPhone, you’ll need to give some essential details to your carrier:
– Account Holder’s Name and Number
– IMEI Number: This can be found by dialing 06 on your iPhone or by going to Settings > General > About.
– Phone Number that is related to the iPhone
Request an unlock from your carrier
Here are the general steps:
Contact Customer Support: Get your carrier’s consumer service through online chat, phone, or in-store visit.
Submit an Unlock Request: Provide the required information and request an unlock.
Wait for Permission: The process might take several days to a week. They will inform you once the unlock is agreed upon.
Become acquainted with the unlock process
Your carrier will provide you with information on how to finish the process after your unlock request has been approved. Typically, this pertains to the subsequent actions:
For SIM-card-equipped iPhones
Insert a new SIM card. Turn off your iPhone and take out the SIM card that came with it.
Restart iPhone: Restart the iPhone by turning it back on. Perhaps you should make a Wi-Fi network connection.
Comply with the on-screen instructions. Your iPhone will walk you through all of the setup steps, including the SIM card activation.
For iPhone models lacking a SIM card
Make a backup of your iPhone. You may do this with iTunes or iCloud.
Erase Your iPhone: Select Erase All Content and Settings under Settings > General > Reset.
Restore Your iPhone: After erasing, restore your iPhone from the backup.
Check the Unlock
Take the following actions to make sure your iPhone has been successfully unlocked:
Insert a SIM card from a different carrier. Use a SIM card that was not originally issued by your current carrier.
Check for Service: At this point, your iPhone should show the name of the new carrier and provide service.
At this point, your unlock apple iphone 15 pro maxwill be unlocked.
In Conclusion
This article clearly shows how you can unlock any of the iPhone models. So, unlock apple iphone 14 pro max, unlock Apple iPhone xs max. If you are still not clear and want to unlock any other device other than an iphone, you can contact The Unlocking Company for an unlocking service and freeze your tech gadgets.
0 notes
Text
Apple ID Account Bug Locks Some Users Out of Accounts

According to multiple reports on social media sites, Apple users are experiencing an issue with their Apple ID, which is preventing them from accessing their own accounts. Some customers report that they were logged out of one or more devices and then forced to update their Apple ID password, while others appear to be unaffected by the bug. Resetting an Apple ID password appears to be working, with affected customers reporting that doing so restores access to their accounts.
The Apple ID password reset bug, first discovered by 9to5Mac, appears to be affecting a number of people who have posted about it on social media. A LoudFact writer was also affected, as his Apple ID was logged out on both his iPhone and iPad, followed by a prompt to reset his password.
Michael Tsai, a Mac software developer, described his experience in a blog post, stating that his iPhone first asked for his Apple ID password before informing him that his account was locked. The reset process was complicated because he had Stolen Device Protection on, but Tsai was able to reset his password without delay using his Mac, despite encountering a few issues in the process.
Similarly, developer Dave Wood stated in a Mastodon post that he was notified that his Apple ID was also locked. A screenshot of the pop-up notification shows that the account was locked "for security reasons", with two options: Unlock account or Cancel.
He, like Tsai, was instructed to wait an hour since his phone had Apple's new Stolen Device Protection function enabled. Several additional users have shared their experiences with Threads, X (previously Twitter), and Mastodon.
Also Read:
- IDP.Generic Virus – How to Remove It Completely
- What is Powershell.Exe Virus? Facts and How to Remove It
According to Apple's system status webpage, there were no ongoing or recent issues affecting any of its services at the time of publication, including Apple ID, iCloud Account, and Sign In. There is presently no word from Apple on why this issue is affecting some users.
Read the full article
0 notes
Text
Guarding Your Chats: A Comprehensive Guide to WhatsApp Security and Safety Tips
Introduction:
WhatsApp has become a necessary tool for our everyday communication, making it easier to have smooth interactions with friends, family, and coworkers. Setting the security of our chats as a top priority is essential as we communicate private messages and sensitive information. We'll go over the crucial security precautions and advice to keep your WhatsApp conversations safe in this blog article, guaranteeing a confidential and secure online communication experience.
1. Enable Two-Step Verification:
Why it matters:
Your WhatsApp account is further secured with two-step verification, which requires a PIN that you set up in addition to your phone number.
How to enable:
Launch WhatsApp, then select "Settings."
After choosing "Account," choose "Two-step verification."
To configure your two-step verification PIN, adhere to the on-screen directions.
2. Regularly Update WhatsApp:
Why it matters:
By updating WhatsApp to the most recent version, you can be sure that your conversations are safe from potential vulnerabilities and that you have access to the newest security fixes and features.
How to update:
On an Android device, search for WhatsApp in the Google Play Store and select "Update."
For iOS users, go to the App Store, search for WhatsApp, and select "Update."
3. Monitor Connected Devices:
Why it matters:
Monitoring gadgets that are linked to your WhatsApp allows you to spot and control any unwanted access.
How to check:
To access the list of connected devices, navigate to "Settings" > "WhatsApp Web".
You can log out of any unknown devices remotely if they are listed.
4. Be Wary of Suspicious Links:
Why it matters:
Phishing attempts frequently utilize malicious URLs to target WhatsApp users to compromise your account or steal personal data.
Safety tip:
Refrain from clicking on unidentified links.
Before responding to links or messages, be sure they are legitimate.
5. Customize Privacy Settings:
Why it matters:
You may manage who has access to your data and the last time you were online by configuring your privacy settings.
How to customize:
Go to "Settings" > "Account" > "Privacy" to adjust settings like "Last Seen," "Profile Photo," and "Status."
6. Secure Backups with Encryption:
Why it matters:
Even while your chat backups are kept on the cloud, you may safeguard your communications even further by making sure they are encrypted.
How to secure backups:
For your cloud backup service (iCloud for iOS, Google Drive for Android), select a strong, one-of-a-kind password.
Enable end-to-end encryption by verifying that your backups are correctly encrypted.
7. Use Official Channels for Support:
Why it matters:
Fraudsters may pose as customer service representatives to fool users into disclosing private information.
Safety tip:
Please use the proper avenues provided on their website to contact WhatsApp support.
Unwanted emails purporting to be from support should raise suspicions.
Conclusion:
You can greatly improve the security and privacy of your WhatsApp conversations by putting these security best practices and guidelines into effect. Remain alert, keep your device and app updated, and arm yourself with the knowledge you need to safely traverse the digital terrain. Your chats are important, so protect them with improved WhatsApp security.
To find out more, visit our website: https://asputility.com/
wa.me/+918080717691
0 notes
Text
Protecting Your Privacy When Buying and Using a Used Phone

Acquiring a used phone can be a smart financial move, offering access to premium devices without breaking the bank. However, as you transition into using a pre-owned mobile device, it's imperative to prioritize your privacy. Your smartphone is a treasure trove of personal information, and failing to secure it properly can lead to data breaches, identity theft, or unauthorized access to your digital life. In this comprehensive guide, we will explore essential steps and practices to safeguard your privacy when buying and using a used phone. From vetting sellers to securing your device, we'll cover all the bases to ensure your digital world remains private and secure.
Researching Sellers and Sources:
Before you even buy a used phone, conducting thorough research on the seller and the source of the device is crucial to protect your privacy.
Reputable Sellers: Opt for established, reputable sellers, whether you're buying from an individual or a retailer. Look for positive reviews and ratings from previous customers. Established businesses tend to have better quality control and customer service.
Avoiding Stolen Phones: Check the phone's IMEI (International Mobile Equipment Identity) number to ensure it's not reported as stolen or blacklisted. You can do this through online IMEI checkers or by contacting your mobile carrier.
Refurbished vs. Second-hand: Consider purchasing a certified refurbished phone from the manufacturer or an authorized dealer. These devices are thoroughly tested, often come with warranties, and provide an extra layer of security compared to buying from an individual.
Performing a Secure Transaction:
When buying your used phone, employ secure transaction methods to protect your financial information.
Payment Security: Use secure payment methods like PayPal or a credit card. These methods offer buyer protection and can help dispute charges if the phone does not meet your expectations.
Avoid Cash Transactions: Avoid cash transactions whenever possible. They lack the protection mechanisms provided by digital payment methods and leave no paper trail in case of disputes.
Receipts and Records: Always request and keep a copy of the transaction receipt. This document can be valuable for warranty claims or disputes.
Data Sanitization Before Use:
Before you start using your newly acquired phone, it's essential to ensure that all previous owner's data is completely wiped.
Factory Reset: Perform a factory reset to erase all data and settings. Go to the phone's settings and look for the "Factory Reset" or "Erase All Content and Settings" option. Follow the on-screen instructions.
Remove Google/iCloud Accounts: Make sure any associated Google or iCloud accounts are removed. Failure to do so may result in the previous owner having access to your device's data.
Secure Erase: Consider using a secure erase utility, especially if you're concerned about data recovery. These tools overwrite the storage with random data, making it nearly impossible to recover the previous owner's information.
Set Up Strong Security Measures:
Once your used phone is wiped clean, it's time to establish robust security measures to safeguard your data and privacy.
Password or PIN: Set up a strong, unique password or PIN to unlock your device. Avoid easily guessable combinations like "1234" or "password."
Biometric Authentication: Enable biometric authentication features like fingerprint recognition or facial recognition, if available. These add an extra layer of security.
Two-Factor Authentication (2FA): Enable 2FA for your email, social media, and other accounts. This provides an additional security barrier even if someone gains access to your phone.
App Permissions and Privacy Settings:
Configure your app permissions and privacy settings to limit what information apps can access.
App Permissions: Review and manage app permissions. Disable unnecessary permissions like location tracking if they aren't essential for the app's functionality.
Privacy Settings: Navigate to your phone's privacy settings and limit data collection by the operating system. Adjust settings like location services, ad tracking, and data sharing as per your preferences.
App Security: Regularly update your apps to ensure you have the latest security patches. Delete any unused or outdated apps to reduce potential vulnerabilities.
Protecting Your Internet Connection:
Securing your internet connection is vital to prevent unauthorized access to your device and data.
Use a Secure Wi-Fi Network: Avoid connecting to public or unsecured Wi-Fi networks, especially when accessing sensitive information or making online transactions.
VPN (Virtual Private Network): Consider using a VPN to encrypt your internet connection when browsing the web or using apps. A VPN adds an extra layer of security, especially when using public Wi-Fi.
Data Backup and Encryption:
Regular data backup and encryption are crucial to protect your personal information.
Regular Backups: Set up automatic backups to ensure you don't lose important data in case of device loss or data corruption. Both iOS and Android offer built-in backup options.
Data Encryption: Enable device encryption to protect your data from unauthorized access, especially if your device is lost or stolen. This is typically available in your device's security settings.
Device Tracking and Remote Wiping:
In the unfortunate event that your phone is lost or stolen, having tracking and remote wiping capabilities can help protect your data.
Find My Device (Android) or Find My iPhone (iOS): Activate these built-in features to track your device's location and remotely erase its data if necessary. Ensure you know how to use these features in case of an emergency.
Third-party Anti-Theft Apps: Consider installing third-party anti-theft apps that offer additional features like capturing photos of potential thieves or sounding alarms remotely.
Regular Security Updates:
Stay vigilant by keeping your device's operating system up to date.
Software Updates: Install security updates and operating system upgrades as soon as they become available. These updates often contain patches for known vulnerabilities.
System Monitoring: Enable system monitoring tools that notify you of suspicious activity or unauthorized access attempts.
Safe App Downloads:
Be cautious when downloading and installing apps to prevent malware and privacy breaches.
Official App Stores: Download apps only from official app stores like the Google Play Store or Apple App Store. These platforms have security measures in place to screen for malicious apps.
App Permissions: Review app permissions and avoid installing apps that require unnecessary access to your personal information.
Dispose of Your Old Phone Securely:
If you're replacing your old phone with a used one, ensure you dispose of it securely to protect your privacy.
Data Erasure: Before selling or recycling your old phone, perform a thorough data erasure to remove all personal information.
Remove SIM and Memory Cards: Don't forget to remove your SIM card and any additional memory cards from your old phone.
Buying and using a used phone can be a cost-effective choice, but it comes with privacy risks. By following the steps and practices outlined in this comprehensive guide, you can significantly enhance the security of your personal information and digital life. Remember that safeguarding your privacy is an ongoing process that requires diligence and regular maintenance. Stay informed about emerging threats and security best practices to keep your used phone secure, and enjoy the benefits of a budget-friendly device without compromising your privacy.
0 notes
Text
Apple.com Login
In today's digital age, accessing online services and platforms has become an integral part of our daily lives. One such platform that has revolutionized the way we interact with technology is Apple.com. With its sleek design, user-friendly interface, and cutting-edge features, Apple.com offers a login experience that is second to none.
The Apple.com login page serves as the gateway to a world of possibilities, where users can access personalized services, manage their devices, and explore a vast ecosystem of apps, content, and services. Whether you're an avid Apple user or new to the Apple ecosystem, the login process is seamless and straightforward.
To begin, users can navigate to Apple.com and locate the "Sign In" button prominently displayed on the top right corner of the page. Upon clicking the button, users are directed to the login page, where they can enter their Apple ID and password. The Apple ID serves as a unique identifier that grants access to various Apple services, such as iCloud, the App Store, Apple Music, and more.
One of the standout features of the Apple.com login experience is its emphasis on security and privacy. Apple utilizes industry-leading security measures to protect user data and ensure that unauthorized access is prevented. Two-factor authentication is also available, adding an extra layer of security by requiring users to verify their identity through a trusted device or phone number.
Once logged in, users gain access to a personalized dashboard that showcases their devices, subscriptions, and recent activity. From here, users can easily manage their devices, update their payment information, and customize their settings. Apple.com also offers a seamless integration with other Apple devices, allowing for a seamless transition between devices and the ability to pick up where you left off.
In addition to its practicality, the Apple.com login experience is visually appealing, mirroring Apple's signature sleek and modern design aesthetic. The use of clean lines, bold typography, and vibrant imagery creates an immersive and visually pleasing experience for users.
to log, tap to create an account without credentials in google, and iPhone, ipad and watch.
In conclusion, the Apple.com login experience is a gateway to a world of possibilities, bringing together convenience, security, and an intuitive user interface. Whether you're accessing your iCloud files, downloading the latest apps, or managing your Apple devices, Apple.com provides a seamless and user-friendly login experience that enhances your overall Apple ecosystem experience. So, why wait? Unlock the world of possibilities with the Apple.com login today!
0 notes
Text
iCloud Bypass Tool Review
iCloud Bypass Tool is a reliable and easy-to-use application that helps you unlock the iCloud activation lock on your iPhone, iPad, or iPod. It's free to use and highly compatible with all iOS devices.It's one of the most popular and efficient iCloud lock bypass tools. It has numerous positive reviews from previous users.
Introduction for iCloud Bypass Tool
iCloud Bypass Tool is the easiest and most effective way to bypass your iCloud activation lock. It also allows you to access your iCloud account on any Apple device without jailbreaking. The tool is free to use and safe to download.

This tool is available for both Windows and Mac. Its user interface is friendly and easy to navigate. It also provides round-the-clock support to users.It is the best tool to unlock iCloud on any iPhone or iPad. It is free to use and works on most iOS devices.
The process is simple, easy, and risk-free. All you need is the IMEI number of your device and a computer with an internet connection.This method has been around for a while and is now one of the most popular methods to remove iCloud activation locks. It is easy to use and works on all iPhone and iPad models.
Unlock the latest iPad using iCloud Bypass Tool.
Several tools and services can help bypass the iCloud lock on your device. However, before using one, read each instrument's reviews and user comments. You should also check the security, unlocking period, and customer support.
Activation lock on iPad and iPhones prevents people from accessing the device or its data. It is a helpful feature to keep your devices secure from theft and unauthorized access.Sometimes, you can use iCloud Bypass Tool to unlock your latest iPad without an Apple ID. For example, if you forgot your Apple ID password or purchased a second-hand device still connected to the previous owner's iCloud account.
iCloud Bypass Tool is software that allows you to remove iCloud Activation Lock from your device with ease. This software is safe and free of malware or viruses, and it offers a video tutorial to guide you through the process. It works on nearly all iOS versions.
The legal background of using iCloud Bypass Tool
iCloud Bypass Tool is used to unlock iPhones, iPads, and iPods. It is a legal tool and is an excellent option for overcoming iCloud restrictions.There are many iCloud Bypass tools available on the market. However, it is essential to find the right one. To do that, you should check customer reviews.
Another thing you should consider is time. Some tools can take a long time for the unlocking process.
The main reason for this is that they may require a lot of resources. In addition, they should be easy to use and have good support.A suitable iCloud Bypass Tool should have a website that offers extensive support, tutorials, and FAQs. They should also provide a customer hotline.
A new tool discovered by Threatpost suggests that forensic investigators can extract call history data from Apple's cloud services without breaking through iPhone security measures. The revelation could bolster the FBI's efforts to obtain data from San Bernardino terrorist Syed Farook's phone.
More about iCloud Bypass Tool
iCloud Bypass Tool is an easy-to-use program that helps you unlock your device without entering the iCloud password. It works on all iPhone and iPad devices and is safe to use.
You may need to use an iCloud Bypass Tool for a few reasons. For instance, if you accidentally delete the iCloud account on your device or have forgotten your Apple ID and password.
Another reason is if you want to remove the activation lock on your device and start using it again. There are many iCloud Bypass Tools in the market, so choosing the one that best suits your needs can be challenging.
The primary consideration when choosing an iCloud Bypass Tool is compatibility and ease of use. Different tools work for other device models and versions, so pick the right one.
What is the main reason for using this Tool?
The main reason for using iCloud Bypass Tool is that it is an easy and quick solution for unlocking Apple devices. It can remove the iCloud activation lock on many iOS devices, including iPhones and iPads.
The tool works with an IMEI number and is compatible with almost all iOS versions and system types. It also offers a detailed user guide, so you can be sure it’s safe and effective.iCloud lock has become an annoying problem for most iOS users. Whether you bought a new or second-hand iDevice without your Apple ID, it’s a frustrating experience to find that the device won’t work.
There are a few ways to solve the issue, but iCloud bypass tools are the most popular option. These tools are free to use and help you get back on track with your Apple devices. They’re also easy to use and require no technical knowledge. Several tools are available on the internet, but choosing one that’s legal and safe is essential.
Advantages of using iCloud Bypass Tool
iCloud Bypass Tool is a simple and convenient application that helps you unlock the iCloud account on your Apple device. It is also free and safe to use. Moreover, it supports all the major iOS versions and devices.
Several iCloud Bypass Tools are available, but some can lead to security problems. So, reading user reviews before choosing a bypass tool is essential.
The most popular iCloud Bypass Tool is iRemove, which has been trusted by many users worldwide. This professional software does everything for you, fixes the problem within a few minutes, and gives you a lifetime license to reuse the solution.
Another iCloud Bypass Tool is Doulci, which requires no special skills or an Apple ID password. It connects to the Apple servers directly and helps you bypass the iCloud activation lock without problems.
This bypass iCloud activation lock tool is popular among a lot of Apple device users because it does not require any complicated setups and does not leave you with any issues. It works well with most devices and is an excellent choice for any user looking to get the best value for their money.
Conclusion on iCloud Bypass Tool
If you cannot unlock your iPhone or iPad using an Apple ID, several iCloud Bypass tools are available. But it is essential to choose the right one based on your requirements.iCloud Bypass Tool is a free, easy-to-use, and compatible app. It also offers excellent support with tutorials if you need help.
It works with all Apple devices and iOS versions. It is one of the market's most efficient and effective iCloud bypass tools.This iCloud Bypass Tool is designed to remove the activation lock and reset the device without inputting any Apple ID or password. It also lets you turn off the Find My [device] feature with just a few clicks.
It is a reliable, simple-to-use iCloud Bypass Tool that works for all iPhone models and iOS devices. It is also very compatible with Windows and Mac computers. It also has a free trial version to be downloaded to try out the software before purchasing it.
Finally, on iCloud Bypass Tool
iCloud Bypass Tool is one of the market's most popular and effective iCloud unlock software. It has an intuitive interface and user-friendly design for iPhone/iPad users to bypass iCloud in a few clicks. It also offers excellent support and information on how to use it properly.
It can unlock iOS versions from iOS 7 to iOS 11. Moreover, it supports all kinds of iPhones and iPads.Another good thing about this iCloud bypass tool is its free use. However, it requires a computer download before you can start using it.
The iCloud Bypass process is a secure and easy way to unlock any iDevice without any jailbreak process. It is entirely safe, legal, and fully guaranteed for any user.
With the release of the latest iOS version, many iDevice users have faced a lot of iCloud-locked issues. But with the help of the iCloud Bypass tool, you can quickly solve this issue and get rid of it forever.
0 notes
Text
How to Unlock iPhone With Apple Support Number Without Passcode
If you're in search of an iPhone unlock, or you would like to get access back to your Apple account there are methods to assist you. You can either reset your Apple ID password, erase your iPhone or recover the Recovery contacts.
To regain access to your Apple account, you can use recovery contacts
The use of Recovery Contacts can allow you to get access back to your Apple account in the event you have forgotten your password. They can create a one-time recovery code for you and allow you to access your account. They do not have access to your account or data but they can verify your identity.
Your Apple account can hold up to five Recovery contacts. Apple suggests adding one contact to your Family Sharing group. However you are also able to add contacts form other sources.
To set up Recovery Contacts You must be at minimum 13 years of age and have an Apple device. You must be able authenticate using Touch ID or Face ID on your device. It is also important to ensure that two-factor authentication is turned on for your Apple ID.
It is your responsibility to accept adding the Recovery Contact to your account. If you choose one who is not willing to accept your request, Apple will send you an email. You can also delete contacts that are not your recovery contacts.
Account Recovery is accessible in the Account Recovery section of the Settings app. Tap Password & Recovery to access it. It's also possible to start Settings and tap the name at the top.
Account Recovery is only a last resort option, and it could require a few days to retrieve your account. You can erase your account from Apple devices by going into Settings > Apple ID. After that, you'll be asked to set up a new password.
Set your Apple ID password
Whether you forgot the Apple ID password or your device was stolen or lost, you can reset your password. However, there are multiple steps to follow. Certain steps are simple to accomplish, while others require more time. The code will be sent to your mobile phone and you'll need to respond to security questions.
The Apple Support app is your best option when it comes to regaining your lost passcode. If you require assistance, you may contact Apple Support's customer support phone number. They can help you figure out what the iPhone screen is indicating or help you re-add your password. They will however only be able to help you with a certain percentage of your problems.
Checking your password twice is a good option. You should double-check your password when it's used to sign in to Apple services. You can verify this by entering Settings and then clicking on the iCloud tab. You'll be able to see a list on your devices. You can verify which devices are locked, or otherwise unusable.
You might also want to create an email backup while you're in the process of setting it up. If you forgot your password, you could use the backup email to sign into.
Erase your iPhone without using a password
Utilizing a computer to erase your iPhone without the need for a password is an excellent method of getting your device back to the factory settings. You'll need to back up your device before erase it. You can then restore your iPhone to its previous settings using iTunes.
Resetting your iPhone has the main benefit of being able to reset your passcode. This is particularly beneficial when you're having trouble making an appropriate passcode. This is useful for those who have made a change of mind and wish to enter a different passcode.
You can erase your iPhone using a software application in the event that you don't have a passcode. It will erase all data and settings on your iPhone and restore it to its default condition.
youtube
You can also reset factory settings on your iPhone by using iTunes. It will erase all data and settings from your phone. It will also erase the Apple ID. For this, you'll require an Apple computer and a lightning cable.
Another option is using an application that runs on a computer called AnyUnlock. This app will wipe your old iCloud accounts. It will also erase the previous Apple ID. You can also make use of a software app known as Stellar Toolkit for iPhone. This program wipes the device and then restore it to its original state. It can be run on either a Mac or on a PC.
https://www.youtube.com/watch?v=_U21IHo5kG0
0 notes
Text
How to track a lost iphone?

Losing an iPhone may be nerve-racking. Possibly, you could have forgotten it in the cafe or perhaps it got stolen in a crowded place. But don’t get disheartened, as it may be easy to track a lost iPhone as long as it runs on battery.
Now, the best information is that even if you lose your Apple tool, tracking a lost iPhone isn’t impossible, thanks to the “ecosystem” Apple has been developing and perfecting over the years.
WAYS TO LOCATE YOUR LOST IPHONE:
There are several ways how to locate a lost iPhone:
Tracking a Lost iPhone with ‘Find My.’
If you were to lose your iPhone or, in case it has gotten stolen, you could track the lost phone through the ‘Find My’ app that is available as a default app on all Apple devices. If you have lost your phone, you could get admission to the ‘Find My’ app through another Apple device and set a look for your iPhone.
If you’re new to the iPhone or have never set up the Find My app yet, right here’s the way you start:
Go into your settings, tap on your name, and then on “Find Me.”
Tap on “Find My iPhone.”
Turn on the “Find My iPhone.”
If you have upgraded to iOS 15, you can also activate “Find My network” if you want to assist you in discovering your phone even though it’s offline.
“Send Last Location” will send the region of your iPhone to your Apple account while the battery is about to die.
Free Phone Tracer
With location service, the Free Phone Tracer is another choice to track lost iPhones through a wide variety online free. When you input your misplaced cell phone number, it’ll robotically seek the location for free. The website is steady with McAfee’s protection solution. The procedure is more straightforward and more appropriate.
FamiSafe iPhone tracker – find iPhone location online.
Monitoring and accompanying your children on the Internet and in real life is a concept going through the heads of all parents; however, let’s be realistic: only some people have the time. And because no person is infallible, a generation comes to your rescue. The parental control software program is there to support you and secure the navigation of the youngest. As a parental control solution, FamiSafe is the first-rate choice to choose. FamiSafe helps you to have a take a observe the precise GPS region of the goal phone anytime. All you want to do is log in to your FamiSafe account on the parental app, then tap Real-time Location. You can also view the region records of the goal tool or install a geofence to get notifications while the goal tool leaves or enters the set area.
Turn on Lost Mode, Mark as Lost
As long as your iPhone becomes registered for Find My iPhone, you may be able to use Lost Mode to fasten down your tool. It is a vital step in case your iPhone has got stolen. If you’ve got Apple Pay installation for your tool, this can be disabled, and any card installation can get suspended. When (if) you retrieve the iPhone, you can reactivate your cards via iCloud.
IMEI Tracker iPhone
The first-rate method to observe your misplaced iPhone is using the ‘Discover iPhone’ utility pre-bought on your iPhone. The utility is on the market for Apple devices with iOS five or more. Any customers of Apple devices may have an (IMEI tracker India) exciting Apple ID wherein they’re perceived interior any in their Apple devices. You occasionally have an iPhone and an iPad; all matters considered, you’re using a comparable Apple ID.
You can have an iPhone IMEI check and locate your phone.
CONCLUSION
1 note
·
View note
Text
iPhone Carrier Unlocking: A Step-by-Step Guide
It is apple time in the present. You might be thinking, Why is this stated? But of course, people in modern times don’t like apples as a fruit in their diet. Instead, they will have all the gadgets that have the Apple brand as their logo. There are a series of products from this brand, and everybody uses one or another device made by it. Of all these things, the iPhone is the most used, and most people have it. In this article, you will be reading about how to get the iPhone phone model to unlock Apple iPhone 12 and unlock apple iPhone 13 pro max So, to know more about the same continue reading it.
Overview of carrier locking
Check that your iPhone is Suitable for Unlocking
When you unlock it, you must ensure that this phone model or the device is appropriate for unlocking. Here are a few key benchmarks:
- Contract Status: Secure your contract is finished or the iPhone is fully paid off.
- Outstanding Pays: Confirm your account has no outstanding expenses or dues.
- iPhone Condition: The iPhone should not be registered as lost or robbed.
You can find this knowledge by logging into your carrier’s online account portal or getting customer support.
Gather the required information
To unlock your iPhone, you’ll need to give some essential details to your carrier:
- Account Holder’s Name and Number
- IMEI Number: This can be found by dialing 06 on your iPhone or by going to Settings > General > About.
- Phone Number that is related to the iPhone
Request an unlock from your carrier
Here are the general steps:
Contact Customer Support: Get your carrier’s consumer service through online chat, phone, or in-store visit.
Submit an Unlock Request: Provide the required information and request an unlock.
Wait for Permission: The process might take several days to a week. They will inform you once the unlock is agreed upon.
Become acquainted with the unlock process
Your carrier will provide you with information on how to finish the process after your unlock request has been approved. Typically, this pertains to the subsequent actions:
For SIM-card-equipped iPhones
Insert a new SIM card. Turn off your iPhone and take out the SIM card that came with it.
Restart iPhone: Restart the iPhone by turning it back on. Perhaps you should make a Wi-Fi network connection.
Comply with the on-screen instructions. Your iPhone will walk you through all of the setup steps, including the SIM card activation.
For iPhone models lacking a SIM card
Make a backup of your iPhone. You may do this with iTunes or iCloud.
Erase Your iPhone: Select Erase All Content and Settings under Settings > General > Reset.
Restore Your iPhone: After erasing, restore your iPhone from the backup.
Check the Unlock
Take the following actions to make sure your iPhone has been successfully unlocked:
Insert a SIM card from a different carrier. Use a SIM card that was not originally issued by your current carrier.
Check for Service: At this point, your iPhone should show the name of the new carrier and provide service.
At this point, your unlock apple iphone 15 pro max will be unlocked.
In Conclusion
This article clearly shows how you can unlock any of the iPhone models. So, unlock apple iphone 14 pro max, unlock Apple iPhone xs max. If you are still not clear and want to unlock any other device other than an iphone, you can contact The Unlocking Company for an unlocking service and freeze your tech gadgets.
0 notes
Text
How to Keep Your iPhone Secure

Apple takes pride in setting high standards for user privacy and data security on every device it manufactures. However, your iPhone may not be as safe as you believe because hackers have devised novel methods of stealing your sensitive data.
How can you deal with a hacked iPhone? And how can you secure it? You've come to the correct spot if you're looking for solutions to questions like these. We'll walk you through some sophisticated tips you can use to keep your iPhone secure.
1. Try to Install Updates Often
Update your iPhone frequently. This easy operation is required to correct unexpected issues and access exciting new iOS capabilities. Apple values its customers' security; therefore, many upgrades include new security fixes. So, install iOS upgrades regularly to secure your iPhone and personal info from hackers.
2. Activate Find My Feature on Your iPhone
Not all hacking occurs online. Someone might physically take your iPhone to circumvent the passcode. Here's what you can do to protect your sensitive info if your iPhone is stolen:
As soon as you can, enable Find My on your iPhone. With the Find My app loaded, you can trace your phone using any device. You may also use it to erase your iPhone to safeguard your personal information remotely.
3. Make Your Passwords Stronger
Everyone knows you must create strong passwords to stay secure online, but you can also prevent hackers by strengthening your iPhone passcode.
Select Custom Alphanumeric Code to generate your password. This enables you to create a very safe iPhone passcode using a mix of letters, numbers, and symbols.
You may also use iCloud Keychain to generate and save online account passwords. You don't have to worry about forgetting them because the service remembers them.
4. Enable Two-Factor Authentication
With two-factor authentication (2FA), hackers won't be able to access your Apple services without your knowledge. To do so, they'll also want access to one of your Apple devices.
Go to Settings > [Your Name] > Password & Security > Two-Factor Authentication to turn on this feature.
5. Avoid Using Third-party Applications and Jailbreaking
Installing software and data on your iPhone from locations other than Apple’s App Store is known as jailbreaking. It is better not to do it.
When you’re looking for a used iPhone for sale, make sure you check if there are any third-party apps installed. If there are, ask the seller to erase the data before buying it.
Hackers will find it easier to access your personal information if you jailbreak your iPhone. Since there are no longer any authorities, such as Apple, ensuring they are secure. Any third-party software you install might compromise your security. Moreover, jailbreaking your iPhone cancels your warranty.
6. Disable Location Tracking Permission
It might not seem a big deal to give applications access to your location in exchange for the added capabilities. But occasionally, we consent to location tracking without thinking about the implications. Therefore, remove location tracking permission for untrustworthy apps.
Final Thoughts
In addition to the tips mentioned above, you can also use VPN or avoid connecting to public Wi-Fi to protect your privacy online. If you want to buy used or refurbished iphones. Phonedaddy offers a huge discount on used iphones in halloween sale 2022
If you continue to face security issues after applying the tips mentioned above, you need to contact Apple Store to help solve your iPhone security problems. But if you have a used iPhone from a credible location in the USA, you can take it to the seller to look at security issues.
0 notes
Text
Instacast help

Instacast help how to#
Instacast help driver#
Instacast help download#
Instacast help free#
In the meantime, have a listen as we prepare for Tuesday's Deep Dive. Was this this payoff for the previous six episodes? Will it build into an explosive season finale? We'll have to wait and see. Season 4, Episode 7 gave us gripping dialogue, heartbreak, big reveals and, most importantly, the old-school pairings we'd been craving.
Instacast help how to#
Here’s how to reschedule: In the app: Tap the Account icon Tap Your Orders Select the order you’d like. Receive a delivery you’re not completely satisfied with? In most cases, we can make things right quickly when you report a problem.Gene and Ash crown "Metanoia" the best episode since "Westworld" Season 2 in this instant-reaction episode of Shat on TV. You can change your delivery date and time up until a shopper begins working on your order. For issues when your apps that are downloaded from the App Store, then check out the article below to go over a few troubleshooting steps. Turning on notifications for the Instacart app. To make sure you get your delivery as scheduled, we recommend. In some cases, the person who shops your order may not be the one who delivers it. Here’s how to reschedule: In the app: Tap the Account icon Tap Your Orders Select the order you’d like Problem with your order After the items in your order have been picked and packed, a personal shopper will start the delivery process. On the Contact us page, select Chat with us to get connected right away. To let us know about an issue related to a specific order, you can Call 1-88 Select Get help at the bottom of any article in the Help Center. You can change your delivery date and time up until a shopper begins working on your order. Instacart Help Center - Get help Get help Let’s talk We’re here to help.
Instacast help download#
For best results, download the latest version of the Instacart Rescheduling a delivery It’s easy to track your order, from the moment your personal Shopper starts finding your items until the moment it arrives at your door. On the desktop website, you can also select Email us to send us an email. Order same-day delivery or pickup from more than 300 retailers and grocers. iTunes doesnt make it easy to stay current, but Instacast does. Select Get help at the bottom of any article in the Help Center. However, Instacart+, previously known as Instacart Express, is a membership option for customers who want to save more and get other exclusive Tracking your order and delivery To let us know about an issue related to a specific order, you can. You don’t need a membership to shop with Instacart. Serac gains Maeves help by offering to reconnect her with her daughter in the Sublime. And with iCloud support, your podcasts are magically synced across your other iOS devices. It’s just that easy.Check out this Instacart+ benefits With Instacast HD, streaming or downloading and playing audio and video podcasts is dead simple. Let us connect you with Shoppers in your area to shop and deliver items from your favorite stores in as fast as an hour. We have a dedicated team of agents who specialize in setting up accounts and placing orders for customers who may need How Instacart works
Instacast help free#
Feel free to call whenever you’d like as the number is available 24/7.
Instacast help driver#
This number can be used for customer service as well as driver support. InstaCast 3D mold ready for iron casting. Instacart offers a special Senior Support Service for customers over age 60. One of the fastest ways of solving an issue regarding your Instacart account is to call Instacart’s customer service phone number (888) 246-7822. This can help you by greatly reducing the prototype/testing of your new products.

0 notes
Text
Download doulci activator ios 9.3.5

#DOWNLOAD DOULCI ACTIVATOR IOS 9.3.5 HOW TO#
#DOWNLOAD DOULCI ACTIVATOR IOS 9.3.5 PASSWORD#
To tell you the truth, I am really glad that nothing can hack Find My iPhone Activation Lock. I know how strange it sounds when I’m telling you to Unlock iCloud 9.3.5 by finding the original owner but there is no way around iCloud Activation Lock! You can use iCloud Contact info to make a Formal iCloud Unlock Request to Apple!Īpple will either Unlock iCloud 9.3.5 or settle a meeting with the iPhone’s original owner! Now you can Unlock iCloud 9.3.5 In case, the original owner is not responding you have another option, you couldn’t have without the iCloud Contact Info!
#DOWNLOAD DOULCI ACTIVATOR IOS 9.3.5 HOW TO#
The iCloud Locked iPhone’s UDID number (Here is how to find iPhone’s UDID number).The iCloud Locked iPhone’s IMEI number (Just press the ” i” button on the top right corner of iCloud Activation Lock Screen).To use the iCloud Contact Information Service you will only need: This is what iCloud Contact Info Service will get you ICloud Contact Information Services from trusted iPhone Unlock Providers has authorized access to Apple’s iCloud databases and finds ALL original owner’s contact info! If you just found the iPhone, you have no clue anywayįortunately, there is a way to find the iPhone’s original owner in order to Unlock iCloud 9.3.5 and it is called iCloud Contact Information Service!.Contacting Apple will do you no good because they won’t share their customer’s personal info.The person who sold you this iPhone is a thief or a scammer.The online market doesn’t know who is the iPhone’s original owner.Original owner might ask for money to deactivate the Find My iPhone Activation Lockīut what happens when there is NO message by the iPhone’s original owner? How can you Unlock iCloud 9.3.5 in this case? Find the original owner & Unlock iCloud 9.3.5.Original owner might offer you money to return the iPhone.Original owner might disable the iCloud Activation Lock.You were scammed in buying this iCloud Locked iPhone or you just found the iPhone!Įxplain what happened to the original owner! If you are lucky there will be a phone number or an email address to reach iPhone’s original owner!ĭO IT! There is no other way to Unlock iCloud 9.3.5! In this screen (and it is as far as you can get) you can see why this iPhone is iCloud Locked and sometimes there is a message by the original owner. The very first moment you turned on your second hand iPhone, you saw the iCloud Activation Lock Screen! You are not here to listen about how to avoid buying an iCloud Locked iPhone but you need to Unlock iCloud 9.3.5! Let me show you how! iCloud Activation Lock Screen & Unlock iCloud 9.3.5 If the iCloud Status is CLEAN, there is still an unlocking solution. You will even know the true market value of the iPhone you are buying in case, someone is trying to rip you off. Online markets cannot determine if the iPhone seller is a thief or the original owner and the next time you will decide to buy a refurbished iPhone do an IMEI Check first!Īn IMEI Check Service will ensure that the iPhone is not iCloud Locked, SIM Locked, Blacklisted or has any other hidden issue that can make it unusable! Thieves know this well and this is why they choose to sell iCloud Locked iPhones through online markets like Craigslist, Amazon or eBay! Try these old iCloud hacks, maybe you get more lucky! This means that when you want to Unlock iCloud 9.3.5, you need to find the original owner because he/she is the only person in the whole world that can Unlock iCloud 9.3.5!
#DOWNLOAD DOULCI ACTIVATOR IOS 9.3.5 PASSWORD#
When iCloud Activation Lock is ON, the iPhone needs original owner’s Apple ID and Password to get activated! Make no mistake, iCloud Activation Lock is unhackable and there are NO tools to Unlock iCloud 9.3.5 or bypass the iCloud Activation Lock Screen! ICloud Activation lock is the greatest anti-theft measurement ever and this is why Apple made it an iOS built-in app! Since iOS 9, iCloud Activation Lock and Find My iPhone Activation Lock are the same thing. I will show you the only way to Unlock iCloud 9.3.5 and this way involves the iPhone’s original owner! Stolen or Lost iPhones and Unlock iCloud 9.3.5 There are no hacking tools to Unlock iCloud 9.3.5 and if you already tried one of those you know what I mean! If you want to Unlock iCloud 9.3.5 on iPhone 4/4s/5/5s/5C/6/6+/6s/6s+/SE/7/7+ then welcome to the right place!

0 notes
Text
Yosemite mac os x 10.10 download

#Yosemite mac os x 10.10 download for mac os x#
#Yosemite mac os x 10.10 download mac os x#
#Yosemite mac os x 10.10 download full#
#Yosemite mac os x 10.10 download pro#
#Yosemite mac os x 10.10 download Bluetooth#
The Today view can display information and updates from various sources, along with widgets. Notification Center features a new "Today" view, similar to that in iOS.
#Yosemite mac os x 10.10 download Bluetooth#
The Handoff functionality allows the operating system to integrate with iOS 8 devices over Bluetooth LE and Wi-Fi users can place and answer phone calls using their iPhone as a conduit, send and receive text messages, activate personal hotspots, or load items being worked on in a mobile app (such as Mail drafts or Numbers spreadsheets) directly into their desktop equivalent. Many of Yosemite's new features focus on the theme of continuity, increasing its integration with other Apple platforms and services such as iOS and iCloud. The Dock is now a 2D translucent rectangle instead of a skeuomorphic glass shelf, reminiscent of the Dock design used in early versions of OS X through Tiger and in iOS since iOS 7. It was the only macOS version to use Helvetica Neue as the default typeface, as in El Capitan it was again changed, this time to Apple's own, newly-designed San Francisco typeface. Other design changes include new icons, light and dark color schemes, and the replacement of Lucida Grande with Helvetica Neue as the default system typeface. Yosemite maintains the OS X desktop metaphor. Some icons have been changed to correspond with those of iOS 7 and iOS 8. Other changes include thinner fonts and blurred translucency effects. It is the first major redesign of the OS X user interface since 10.5 Leopard. Yosemite introduced a major overhaul of OS X's user interface, emphasizing flat graphic design over skeuomorphism, following the aesthetic introduced with iOS 7. These are the models that support new features such as Handoff, Instant Hotspot as well as AirDrop between Mac computers and iOS devices:
#Yosemite mac os x 10.10 download pro#
Mac Pro (Early 2008 or later) (Can run on a mid-2006 version if one upgrades to a supported graphics chip and utilizes a custom bootloader).
MacBook Pro (13-inch, Mid 2009 or later 15-inch, Mid/Late 2007 or later 17-inch, Late 2007 or later).
MacBook (Aluminum Late 2008 and Early 2009 or later).
These are the models that are compatible with OS X Yosemite (with exceptions): As with Mavericks and Mountain Lion, 2 GB of RAM, 8 GB of available storage, and OS X 10.6.8 (Snow Leopard) or later are required.
#Yosemite mac os x 10.10 download full#
However, to take full advantage of the Handoff feature, additional minimum system requirements include a Mac with Bluetooth LE (Bluetooth 4.0).
2.5 Applications found on OS X 10.10 YosemiteĪll Macintosh products capable of running OS X Mountain Lion (v10.8.x) are able to run Yosemite as the two operating systems have the same requirements.
#Yosemite mac os x 10.10 download mac os x#
Os X Yosemite freeload Our Suggestion/Verdict About Mac OS X El Capitan 10.11. System Required: Minimum 2 GB RAM, With 10 GB Disc Space, 4.0 Ghz Processor and Compatible Graphics.Setup Compatibility: Both 32 and 64 Bit.Updated Here On: 3rd of September 2016.Product’s Nomenclature: Mac OS X El Capitan.Split-screen is there to carry on the operations, twice.ĭownload Os X Dmg Macdrug Mac OS X El Capitan 10.11.6: Important Product Details:.Gestures improvements to swipe you the streamlined items on the go.OS management based improvements (Mission Control).An OS oriented to stability and boosted performance.Os X Server Yosemite Dmg freeload Mac OS X El Capitan 10.11.6: Product’s Salient Features: Some amongst those noticeable features are also listed below. Facebook, Instagram, Twitter, Google Search and many other web pages, on choice are recommended on the start of Safari.Įl Capitan 10.11.6 is an OS for Macs that is dominant on other operating systems like Mac Os Yosemite, Snow Leopard, and Mac OS Lion and that dominance is reflected by some improvements in existing features and by the inclusion of new performance based and system management based upgrades. The browser efficiency should also be discussed here, as there are some additional nudges to the Safari on Mac, Yes Pinning and tabbing was never so easy, that one could just add the favorite page to menu items. That has provided more flexibility to keep intact with operational processes, like an instance is, an article reading along with an eye on the social media account like Facebook. The versatility in operating system world is being brought into an action when the split-screen was introduced by Apple, which allows a user to perform at two simultaneously screens with different operational programs. El Capitan is oriented to bring things in a simpler way, and that can be experienced like, by previewing multiple files, documents or apps that are in a minimized view and could be opened just by opting a desired app, document or an image.
#Yosemite mac os x 10.10 download for mac os x#
Both designing and performance wise improvements are awaited and appreciated by the users for Mac OS X El Capitan 10.11.6that are being brought to the slug of the Macs OS series by Apple.

0 notes