#fractureiser
Explore tagged Tumblr posts
Text
SIMS 4 MOD MALWARE
This isn't what I usually post about, but theres been malware from sims 4 mods. Specifiallly from mods hosted onCurseforge, TheSimsResource, and ModTheSims. It's a lot like the Minecraft Fractureiser virus. The downloaded mod's contain .EXE files that steal personal data and harm computers. The current known infected mods:
"To recap, here are the mods we know for sure were affected by the recent malware outbreak: "Cult Mod v2" uploaded to ModTheSims by PimpMySims (impostor account) "Social Events - Unlimited Time" uploaded to CurseForge by MySims4 (single-use account) "Weather and Forecast Cheat Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account) "Seasons Cheats Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account) "Motherlode Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account) "Mood Cheat Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account) "Mouth Preset N16" uploaded to The Sims Resource by PlayersWonderland (hacked, real account)" -copied from the sims after dark server!
I'm horrible at explaining but please go check out this post on reddit, run an anti-virus scan if you downloaded any recent sims 4 mods, and perhaps join the sims after dark discord server.
#sims 4#sims mods#ts4#simblr#sims#ts4 simblr#my sims#the sims 4#malware#sims 4 malware#the sims community#the sims cc#curseforge#mod the sims#the sims resource#i cant believe this
68 notes
·
View notes
Text

This happened with Minecraft last year. These two articles contain information about the situation which may contain some more insight for people who are keeping up with this, like where it was happening and what the malware was capable of:

11 notes
·
View notes
Text
im going to edit this to be a proper introduction post eventually. probably
for now. list of malware (and other software) that has characters made based off of them:
-Melissa Worm
-ILOVEYOU
-Newton "Virus"
-Bonzi Buddy
-You Are An Idiot
-Goggle.com
-Leap-A/Oompa Loompa Worm
-Creeper
-Reaper
-Morris Worm
-Mydoom
-Mad Virus A
-Nuclear
-PH33R
-Fractureiser
-WannaCry
-Pixel (And its variants)
-LockerGoga
-Flip
-KinitoPET
to be updated if more are added
Category of non-malreapers
-Heron
-Flora
13 notes
·
View notes
Text
Minecraft has somehow become like a cornerstone of cybersecurity and thats so weird but makes sense because it attracts tech proficient people with lots of free time and insane motivation.
I mean along with what prev said (INSANE btw i cant believe i didnt know this) log4j, one of the most widespread and potentially damaging RCE vulnerabilities, was first discovered in minecraft.
Also the way that griefers discovered how to scan for unprotected minecraft servers (project copenheimer) is nuts. This originated from 2b2t (infamous minecraft anarchy server) players. A couple minecraft and spigot specific exploits were discovered via that server as well (nocom, randar)
Also there were multiple malware scares via minecraft mods and modpacks such as the self-replicating fractureiser that spread on curseforge and bukkit.
Some of these have little to no financial gain (especially the griefing ones). Which circles back to the motivation these people have related to the game creates insane drive and is dangerous because of their tech knowledge.
mine craft seems like a good thing for youngsters actually. it’s creative and non violent and social to a degree. do they do a good job making sure it is safe
54K notes
·
View notes
Text
Mod Malware Situation Update
Edit 2023-06-09: The researchers have updated their guidance to all-clear on unmodded versions of Minecraft Java, and work continues with both CurseForge and Modrinth to improve safeguards against new variants or copycat attacks. They are still advising staying away from mods a bit longer while this work continues.
As an additional note, I want to clarify something I don't think was clear in my original post: this was not a failure on CurseForge. What went down here has happened to other platforms. It's just the first time such a malicious package attack has been observed in the Minecraft modding scene. It may not be the last.
Original Post Follows:
As you may have seen yesterday, the modded Minecraft community is experiencing a malware incident.
The quick "do I need to worry" is if and only if all the following are true:
you are using Minecraft Java Edition
. . . and are using any mods or modpacks
. . . and those mods were downloaded/updated in the last 2-3 weeks or possibly as far back as March (timeline still unclear as of my post)
If any of the above were not true for you, then you should be clear. Investigators are advising maximum caution even of vanilla Minecraft, more on that at the end of this post.
If all of the above were true, don't panic. You just need to take a few extra steps to be sure.
A document for non-technical users explaining the situation in more detail and steps to take has been developed on github.
If you used any of the scripts from yesterday to verify your stuff, you may still want to try the new tools which will peak inside the mod files for that extra sure feeling.
The document provides links for checking yourself out, and what to do if the worst case happens.
CurseForge has an update on their twitter:

Modrinth is also in the process of verifying their site as well:
Okay, so, why is the document recommending not even running even vanilla Minecraft Java
There are a lot of brilliant people working on this incident, and they're all smart enough to not give an all-clear until all the facts are known.
Everyone wants fast results. Accuracy takes time.
The way this malware worked was to infect all Java jar files it finds on the system.
Including Minecraft itself.
Including things that have nothing to do with Minecraft.
This spreading to infect other jar files appears to be how it spread to infect legitimate mod files:
The malicious mods have upload dates multiple weeks in the past. Most of them were uploaded by single-use accounts with clearly autogenerated names, and were likely the seed of the infection. Luna Pixel Studios was compromised due to a dev testing one of these mods, as it was an interesting new upload.
At the end of the day, it's all about risk. They can't give a clean bill of health just yet, so they won't. If it turns out that something bigger and nastier was happening, they'd be on the line for that.
This is also why every list of mods published by the investigators comes with the "not comprehensive" disclaimer -- it's what we know. What we don't know can still hurt us.
So, running vanilla launcher for vanilla Minecraft Java is considered a risk. It may be low-risk.
Is it a risk I'm willing to take? Maybe next week, when I know more. (I often wait a week after an update, which coincidentally happened yesterday, so this just happens to align with how I do things normally)
If it's a risk you take, just be safe, stay vigilant, and keep an eye on the main repository of information for more news because I am not a reliable reporter.
#minecraft#minecraft java#modded minecraft#malware#fractureiser#curseforge#overwolf#modrinth#cyber security#minecraft mods#mineblr
47 notes
·
View notes
Text
CURSEFORGE FRACTUREISER MALWARE PSA
For ALL LATEST INFORMATION PLEASE LOOK AT THIS GITHUB PAGE!
tl;dr:
Check that github page on how to see if your PC is infected with malware that has recently been uploaded to Curseforge, and what to do. As of this post it is unclear how far this malware has spread throughout the mods.
Longer version:
on 07/06/2023 it was found that several mods and plugins uploaded to curseforge contained incredibly dangerous malware. This was immediately reported publically by Lunapixelstudio (Responsible for mods such as 'When dungeons arise' and more)
As of right now, they are further investigating the amount of mods affected and are handling the situation. It is recommended to NOT UPDATE YOUR MINECRAFT MODS THROUGH CURSEFORGE FOR THE NEXT COUPLE OF DAYS.
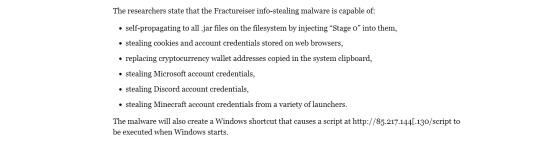
What this virus does is the following:
It hides its code into its target .jar files so that it runs malicious code upon being loaded (stage 0)
It then tries to contact its domain page to download the files necessary for stage 2. (stage 1)
It then opens a port and launches a loop to connect to a server, creating/overwriting a client.jar file. (stage 2)
Stage 3 is the one where the all the malicious things happens. Stage 3 does the following:
Attempts to read clipboard contents
steal microsoft account credentials
scan all .jar files on systems that look like minecraft mods and attempts to infect them with stage 0.
steal cookies & login information
steal cryptocurrency wallets
steal discord credentials
steal microsoft & minecraft credentials
It also will attempt to escape virtual-machine environments when it notices that it is being ran inside one.
Please read the github link at the very top of this post for live updated information on the virus.
14 notes
·
View notes
Text
why do we call viruses cool names
fractureiser? fucking fractureiser? thats suck a fucking cool name
and dont even mention the logo

why the fuck did we give it such a cool design
like this is something i would see at the top of the modpacks list
why cant we name it something like jarfile shitter. thats what it does, it shits on jarfiles. motherfucking jarfile shitter gone and fucked up all your jars and you want to name it fractureiser? that just makes me want to make a virus just so i can give it a really cool name
4 notes
·
View notes
Text
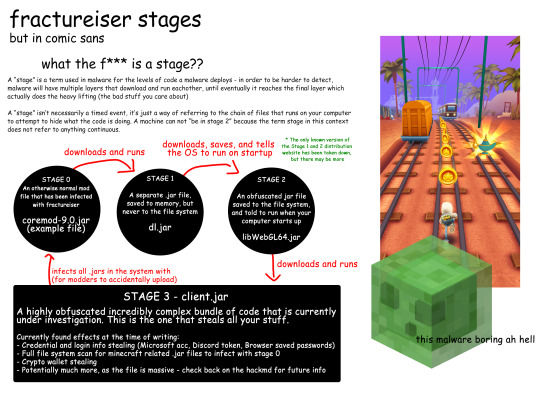
If you've had a modded version of Minecraft installed on your computer this year, it's very likely your computer is infected with the fractureiser malware. It's quick and easy to check following the steps listed here:
The malware has infected several very popular mod packs and can result in the theft of login info for microsoft accounts, discord accounts, login details saved in browsers, and more.
30 notes
·
View notes
Text
Fractureiser more like failureiser
#the thaumaturge rambles#context: there is a java virus specifically targeting minecraft mods that was found two days ago#it was promptly rendered virtually ineffective through the efforts of some wonderful modders
7 notes
·
View notes
Text
thank god fractureiser has virtually been resolved bc i have been DYING to play on the wsmp the last few days
2 notes
·
View notes
Note
Edit 2023-06-20
Been seeing a few Likes trickle in and things have moved on a bit, ended up in other posts etc and so forth, so here's a wall of text update in-post.
The github linked below in the original is the best place for accurate information, technical and otherwise, from those who worked the incident.
The short short short version is (as of this edit): Vanilla is clear, CurseForge has a tool you should run, Modrinth has checked itself. There may still be some risk to running mods, which you can mitigate by sticking to well-known packs and avoid new mods, especially from new accounts with little history. There was always such risk.
To my knowledge, this never affected Bedrock or those who never mod and only use the official launcher.
Original Post Below:
Still an evolving situation, so I would not treat this as the definitive list just yet. Anything withing the last 2-3 weeks may be impacted. List may get longer, though try not to panic too much. This is just standard early research precaution.
If you check your system and get a hit, clean up and change all your passwords, especially MS accounts and Discord, as it is known to have a credential stealing payload.
detailed living document on hackmd was getting hit hard and has been moved to (at time of this post anyways)
on an unrelated-to-my-last-ask note there's like. malware discovered on curseforge and bukkit recently and they're trying to fix it but since minecraft is the subject i felt like i shoulg mention that. (called fractureiser).
Gods, thanks for telling me! I didn't know!
Please check your computers (or tablets) if you installed a mod recently from any of these places!
This website as a list of confirmed compromised mods!!! Please check!!!
120 notes
·
View notes
Note
hey there I don't know if this is out of pocket or anything, but since you've been posting about Minecraft I thought I'd warn you about this .jar infection that's been going around on a lot of popular modding tools like cursedforge - here's some more information about it https://github.com/fractureiser-investigation/fractureiser
just be careful out there :')
hey! no worries, i appreciate it!
i learned about this around when it was first announced, but thankfully 1) i'm using a datapack, not a mod and 2) i downloaded it directly from the creator's website rather than a platform like that (which is actually lucky bc originally i heard of the mod/datapack via modrinth but bc i couldn't find it on there i just looked around until i found the og website lol)
i'll still publish this ask in case it'd be useful for someone else tho!! 🙏 seconding that last statement, be careful out there!!!
#la réponse d#i actually haven't played fully modded in like a decade haha i'm more of a vanilla guy#in minecraft. that is
4 notes
·
View notes
Text
Faust Marsh
It/Its
Based on the Fractureiser malware
Quick witted and always working for its own benefit, Faust has made its identity as a malreaper clear since the moment it was released to the world. Unwilling to conform and much happier doing its own thing, Faust has a tendency to sabotage other malreapers' work as a mockery to them hiding their nature.
A lover of videogames, Faust encountered an abandoned arcade and got to make friends with Yarah. It has enough control over its powers to be able to protect itself from him, and it seems determined to succeed in getting him out of his shell, and then the arcade.
2 notes
·
View notes
Text
I'm pretty sure that if CurseForge had required mod authors to use 2FA we wouldn't be in this situation.
1 note
·
View note
Text
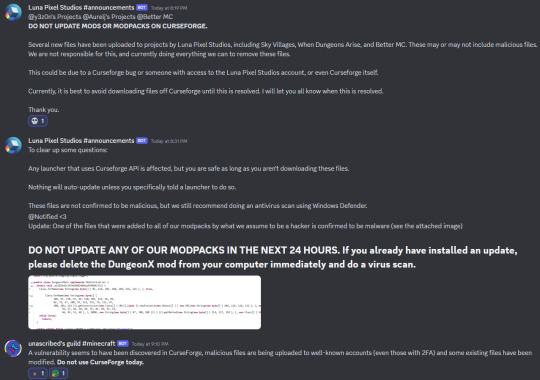
I thought it was actually mid-April.
'Files uploaded in April have been discovered; either the dates are being spoofed, or this has been going on even longer. Many of the accounts have Last Active times in 1999 — likely a quirk with old CurseForge accounts, but still notable.'
HEADS UP, DO NOT DOWNLOAD MODS OR MODPACKS FROM CURSEFORGE RIGHT NOW, CURSEFORGE HAS BEEN COMPROMISED
6K notes
·
View notes
Text
anyway. check your stuff <3
1 note
·
View note