#explain osi model
Explore tagged Tumblr posts
Text
Understanding the OSI Model: A Layer-by-Layer Guide
Explore each layer of the OSI Model in detail. Understand how they work together to ensure seamless network communication.
#OSI Model#Networking Basics#7 Layers of OSI#Network Layers#Data Communication#OSI Explained#Networking Guide#IT Fundamentals#OSI Simplified#Layered Network Model
0 notes
Note
Hi, I’ve been interested in mesh nets since I learned about them so I was really excited to learn you were working on this project.
How does piermesh relate to the OSI model? Which layers is this seeking to implement and which, if any, would be untouched?
Great question!
First for people who don't know the OSI model here's a rundown:
In the OSI model we're implementing layers 1-5 as well as some of 6. We're mostly following the model by nature of this being similar to the current internet though not very strictly. We're also keeping it very simple in that communication is done via msgpack serialized data so it's easy to pass the data between layers/systems/languages
4 notes
·
View notes
Text

The Venture Bros. #49: "Pinstripes & Poltergeists" | December 14, 2009 - 12:00AM | S04E08
The mid-season finale! The season four split of Venture Bros has been covered somewhat, but basically the boys burnt themselves out behind the scenes and needed a break, so they asked Adult Swim if they could cut season four into two halves, while also upping the episode order from 13 episodes to 16 episodes. The network went for it, and it took them nearly a whole ‘nother year to deliver the back half. So, this ends up sorta being a mini-finale.
This is another one of those episodes that’s more effective if you’re devoted to the story of Venture Bros. Meaning: it’s a little light on laughs. There are jokes in here, and they’re all fine, but there probably won’t be a big long list of all the times I laughed at this one or anything like that. It’s goal is mostly to get Brock back into the fold and to set up story elements that are going to come into play for the second half of season four. There’s nothing wrong with that, but I prefer when the show makes me laugh. But I don’t not care about the story, either.
In this one: The Monarch gets swindled by Monstroso (mentioned in a previous episode and now here in front of our eyes) into signing a bad deal thinking that he’s merely going to help the Monarch defeat Dr. Venture. Turns out he’s signed away his rights to arch Dr. Venture to Monstroso.
Monstroso’s methods are lawyerly by nature, attempting to financially ruin Dr. Venture by making him use a certain amount of square footage of his compound towards some public good. When scoping out an abandoned factory on his property he discovers that Brock and SPHINX, the super-secret organization dedicated to stopping villainy that falls outside the purview of the OSI by being non-costumed and non-Guild-of-Calamitous-Intent-affiliated, have been using the space secretly. In other words: Brock has been with the Ventures this entire time. Aww.
Also of note: 21 is shown speaking to 24’s ghost. We’d seen him chatting with 24’s skull throughout this season. He also confronts Brock, a callback to the scene in Tag-Sale, You’re It (apparently repeating the same dialogue) where 21 tries to take Brock on with a non-working light-saber. Brock’s dismissive “boo.” to get 21 to run away is now met with a punch to Brock’s face. Brock doesn’t kill 21, but his newfound respect for giving him a decent fight leads him to team up with him to go beat up Monstroso. The episode ends with Brock casually eating a bowl of cereal in the Venture’s kitchen and Hank, in a delayed reaction, being stunned to find him there.
SPHINX were previously portrayed as bad guys, but it’s explained that when they were conquered, it was decided to just take all their Egypt-themed crap and use it to start what’s essentially a new group. This explanation seems squarely aimed at the fans of the show who just wish it were an unironic action cartoon. But it's alright! I like it fine, okay! I'm not pissed off at all! At this, I mean.
EPHEMERA CORNER

The Family Guy Chicken Star Wars Double Feature (December 20, 2009)
Sometimes I’ll make note of something to cover for Ephemera Corner; like some kind of specially scheduling thing Adult Swim does that in theory is worth mentioning. But then it comes time to talk about it and it’s like damn, I do not care about this at all. Consider how now in 2024, it seems like they run marathons of certain shows all the time, just because that’s a proven-to-work model for cable television nowadays. So, I might get choosier with these EPHEMERA CORNER programming things.
But for those of you who care: Take note, Star Wars heads! Your favorite Seths went head to head and did a Star War double feature rivaling the Ewok TV Movies. The sci-fi epic about one man turning to the darkside and deciding to deprive his children of committing incest with each other by moving them to different planets will knock your socks off, because that’s what this is: It’s just the movie Star Wars but with cartoon guys in it. I don’t even think they changed the words or anything. Have fun imagining how it must’ve played with 2009-era commercial breaks.
6 notes
·
View notes
Text
[https://open.spotify.com/episode/7p883Qd9pJismqTjaVa8qH ]
Jonah and Wednesday are joined by their guest Kerry as they delve into The part of the deep web that we aren't supposed to see.
Hear from our hosts again after winter break!
If you have a small horror or web fiction project you want in the spotlight, email us! Send your name, pronouns and project to [email protected].
Music Credits: https://patriciataxxon.bandcamp.com/
The Story: https://www.reddit.com/r/nosleep/comments/78td1x/the_part_of_the_deep_web_that_we_arent_supposed/
Our Tumblr: https://creepypastabookclub.tumblr.com/
Our Twitter: https://twitter.com/CreepypastaBC
Featuring Hosts:
Jonah (he/they) (https://withswords.tumblr.com/)
Wednesday (they/them) (https://wormsday.tumblr.com/)
Guest host:
Kerry (they/them)
Works Cited: 7 layers of OSI; https://www.networkworld.com/article/3239677/the-osi-model-explained-and-how-to-easily-remember-its-7-layers.html
Closed Shell System; https://www.reddit.com/r/AskReddit/comments/21q99r/whats_a_closed_shell_system/
Deep-Sea Audio from the Marnina Trenches; https://www.youtube.com/watch?v=pabfhDQ0fgY Deep Web Iceberg; https://www.reddit.com/r/explainlikeimfive/comments/1pzmv3/eli5_how_much_of_the_iceberg_deep_web_diagram_is/ Fury of the Demon; https://www.imdb.com/title/tt4161438/
I work on the fifteenth floor, and something just knocked on my window.; https://www.reddit.com/r/nosleep/comments/77h76n/i_work_on_the_fifteenth_floor_and_something_just/ Kitten that leaked the no-flight list; https://maia.crimew.gay/
Project PARAGON; https://scp-wiki.wikidot.com/project-paragon-hub
Tsar Bomba; https://en.wikipedia.org/wiki/Tsar_Bomba
Unknown Armies; http://www.modernfables.net/alan/unknown_armies/Unknown_Armies_2nd_Edition%20-%20Copy.pdf What is a cult and why do people join them?; https://www.teenvogue.com/story/what-is-cult
Questions? Comments? Email us at: [email protected]
#creepypasta book club#deep web#creepypasta#podcast#the part of the deep web you aren't suppose to see
6 notes
·
View notes
Text
10 Skills You Need to Become an Ethical Hacker in 2025

Ethical hacking has moved from the margins to the mainstream. In today’s digitally driven world, cybersecurity is no longer optional; it is a necessity. As businesses grow increasingly dependent on digital infrastructure, the threats they face have also become more sophisticated and relentless. This rising demand makes it crucial to understand the skills to become an ethical hacker and contribute meaningfully to the field.
To protect sensitive data, intellectual property, and critical operations, organizations are investing heavily in cybersecurity talent. As a result, ethical hackers are now seen as essential contributors to risk management and digital trust.
Many professionals begin their journey through industry-recognized programs such as Certified Ethical Hacking, which lay a strong foundation in real-world attack and defense scenarios.
However, to stand out in this competitive and high-stakes environment, you need more than just basic technical knowledge. You need a sharp, strategic mindset and a well-rounded skill set that keeps you adaptable across changing threats, evolving tools, and complex systems.
Whether you aim to work in a corporate security team, consult independently, or pursue bug bounty programs, it all starts with mastering the right skills. Let’s break down the ten core capabilities you’ll need to become a confident and capable ethical hacker in 2025.
Deep Understanding of Networking Fundamentals
Ethical hacking starts with understanding how data flows through networks. Knowing how devices communicate and how information travels between them is the backbone of penetration testing.
Start by learning the OSI and TCP/IP models in detail. These models explain how different layers of a network function and interact with one another.
Study concepts like IP addressing, MAC addressing, ports, NAT, and subnetting. These are crucial for mapping out networks, identifying entry points, and configuring scanning tools.
Explore routing and switching principles to understand how data moves between internal systems and external destinations.
Learn how protocols like HTTP, HTTPS, FTP, DNS, SMTP, and DHCP operate. Being able to analyze their behavior helps you spot misconfigurations and exploit weaknesses during tests.
Practice using network analyzers like Wireshark to observe real traffic and understand communication patterns. Hands-on exploration sharpens your analytical skills.
Without this foundation, it becomes difficult to simulate real-world attacks accurately or identify vulnerabilities that attackers might exploit.
A solid grasp of networking is not just an asset; it is a requirement for ethical hackers who aim to work in complex environments and defend real systems.
Proficiency in Operating Systems (Linux and Windows)
As an ethical hacker, working across different operating systems is a necessity. Linux and Windows are the two most commonly used platforms in both personal and enterprise environments.
Linux is the go-to choice for many cybersecurity professionals. It offers extensive control through the command line, access to powerful tools like Nmap, Wireshark, and Metasploit, and a modular design that makes customization easy.
You should become familiar with Linux distributions like Kali Linux, Parrot OS, and Ubuntu. Learn basic shell commands, scripting, user and file permissions, cron jobs, and service management.
At the same time, knowledge of Windows systems is critical, especially when assessing environments commonly used by large organizations. Many legacy applications still run on Windows, and it remains a popular OS for corporate networks.
Understand Windows architecture, registry structures, Active Directory, PowerShell, and Group Policy settings. These elements often become the focal points in privilege escalation or lateral movement during penetration testing.
Knowing how to pivot between these two systems allows you to test and secure a wider range of targets. It also makes your skills more adaptable in multi-platform environments.
A solid command over both Linux and Windows boosts your effectiveness and credibility as a versatile ethical hacker.
Programming and Scripting Skills
In ethical hacking, the ability to write and understand code is not just helpful; it is often essential. Programming allows you to interact directly with applications, craft custom exploits, and automate repetitive tasks.
Python is a favorite among ethical hackers due to its simplicity, readability, and wide range of security libraries. It is ideal for writing scripts that scan for vulnerabilities, test system defenses, or analyze network traffic.
Bash scripting is another key skill, especially in Linux-based environments. Automating tasks like log parsing, user account monitoring, or system configuration saves time and enhances consistency.
JavaScript plays a critical role in web-based testing. It helps you understand how web applications function and identify client-side vulnerabilities like cross-site scripting (XSS).
It’s also useful to have basic familiarity with other languages such as C, C++, PHP, and SQL. These allow you to dive deeper into source code, understand buffer overflows, and simulate database attacks. More than just writing code, you’ll learn to read and dissect scripts written by others, often the first step in understanding how a threat works.
Ultimately, programming sharpens your ability to think like an attacker and respond like a defender, making it a vital skill in your ethical hacking toolkit.
Mastery of Tools Used in Penetration Testing
To work efficiently as an ethical hacker, you need more than theory; you need mastery of the tools that simulate attacks and expose weaknesses.
Metasploit is one of the most powerful tools for developing and executing exploit code. It’s widely used for penetration testing and understanding how vulnerabilities are exploited in real systems. Nmap, or Network Mapper, is essential for scanning networks, identifying live hosts, open ports, and services running on those ports.
It provides the groundwork for any vulnerability assessment. Burp Suite is a go-to tool for testing web application security. It helps intercept, analyze, and modify traffic between your browser and a web server, making it easier to detect flaws in input validation, authentication, and session handling.
Wireshark is used to capture and analyze network packets in real time. It helps you understand what’s happening on your network at a very detailed level and is especially helpful in spotting unusual behavior.
Nikto is a lightweight web server scanner used to identify outdated software, dangerous files, and common misconfigurations. Each tool serves a unique purpose, but their real value lies in knowing when and how to use them together. The more fluent you are with these tools, the more precise and efficient your penetration tests will be.
Strong Grasp of Web Application Security
Most real-world attacks today target web applications, making this area one of the most critical for ethical hackers to master.
Start by understanding the OWASP Top 10, which highlights the most common and dangerous web vulnerabilities. These include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and broken authentication.
Each of these vulnerabilities can be exploited to access sensitive data, manipulate transactions, or take over user accounts. Knowing how they work allows you to test applications effectively and help development teams fix them.
It is also important to understand how web technologies work together. Learn how HTML, JavaScript, backend databases, and server logic interact within common web architectures.
Dive into how authentication and session management should be implemented to prevent hijacking or brute-force attacks.
Misconfigurations in these areas are among the most exploited in modern applications.
Input validation is another key concept. Applications that fail to properly validate or sanitize user input can become easy targets for injection and scripting attacks.
A strong grasp of web security allows you to think like an attacker and defend like an architect. With web apps at the center of digital experiences, your skills in this domain will always be in demand.
Familiarity with Cybersecurity Frameworks and Standards
In professional cybersecurity environments, knowledge of industry frameworks is essential. They provide a structured approach to securing systems, managing risks, and maintaining compliance.
Begin by understanding the NIST Cybersecurity Framework. It outlines five core functions: Identify, Protect, Detect, Respond, and Recover, that help organizations manage cybersecurity risks effectively.
ISO 27001 is another widely adopted standard. It focuses on information security management systems (ISMS) and offers guidelines for establishing, implementing, and continually improving security protocols.
PCI-DSS is critical for anyone working in environments that handle credit card data. It sets requirements for secure payment processing, including encryption, access control, and regular testing.
These frameworks not only guide your actions as a security professional but also help standardize your reporting and testing methodologies.
Learning how to apply these standards in real-world scenarios improves your credibility and employability in structured, enterprise-grade environments.
Moreover, understanding these frameworks prepares you for roles that involve audit preparation, compliance reporting, and risk assessment.
As businesses become more regulated and security-conscious, your familiarity with these guidelines will give you a practical advantage.
Practical Knowledge of Cloud Security
As more businesses migrate to platforms like AWS, Azure, and Google Cloud Platform (GCP), ethical hackers need to understand how these cloud environments function.
Begin by learning how cloud architectures differ from traditional on-premise setups. Each provider offers different services, interfaces, and security protocols that you must be able to evaluate.
Assessing cloud configurations involves reviewing storage settings, virtual machine access, security groups, and permission roles. Misconfigurations in any of these areas can lead to serious vulnerabilities.
Securing APIs is a major priority in cloud-based systems. Understand how tokens, encryption, and rate limiting protect cloud APIs and what happens when these controls are missing.
Identity and Access Management (IAM) is central to cloud security. Learn how to assign roles, use multi-factor authentication, and limit privileges based on user responsibilities.
Also, study the shared responsibility model. In cloud computing, security responsibilities are divided between the provider and the client. Knowing where your role begins is critical to identifying and mitigating risk.
Cloud security is not static. Providers update their services frequently, so staying current with documentation and certifications is part of the job.
Mastering cloud security gives you the versatility to support businesses of all sizes as they scale in digital environments.
Social Engineering Awareness
Not all cybersecurity threats originate from code. In fact, many successful attacks are the result of manipulating human behavior. This is where social engineering becomes a critical area of focus for ethical hackers.
Social engineering exploits trust, distraction, or lack of awareness to gain access to sensitive systems or information. Phishing emails, baiting with malicious USB drives, and pretexting are some of the most common tactics used by attackers.
Ethical hackers must be able to recognize these techniques and replicate them in controlled environments to test an organization’s resilience. Knowing how users typically respond to these threats allows you to create more effective simulations.
Beyond tactics, understanding human psychology is vital. Learn how attackers build rapport, use urgency, or mimic authority to influence behavior. These psychological levers are often more powerful than technical exploits.
Communication skills also play a big role. As an ethical hacker, you may need to educate clients or team members about the social risks they face and how to minimize them.
By mastering both the technical and human aspects of security, you develop a more comprehensive approach to threat detection and defense.
Problem Solving and Lateral Thinking
Ethical hacking involves navigating through complex systems where vulnerabilities are not always easy to spot. Success often depends on how well you can think beyond conventional boundaries.
Traditional approaches may not always yield results, especially in hardened environments. That’s where lateral thinking comes into play. It involves approaching a problem from multiple perspectives and making creative connections others might miss.
For example, if a network scan shows no open ports, you might consider indirect paths such as phishing or supply chain weaknesses. Thinking like an attacker requires mental flexibility and a deep understanding of both systems and human behavior.
Patience and persistence are equally important. You may spend hours on dead ends before discovering a small misconfiguration that opens the door to an exploit.
Build structured thinking habits using tools like mind maps, flowcharts, or threat modeling techniques. These can help you visualize the problem space and test assumptions.
In addition, learn from past engagements or case studies. Studying how others have uncovered unexpected flaws can expand your problem-solving toolkit.
Ultimately, adaptability is key. Every test presents unique challenges, and your ability to adjust strategies on the fly will set you apart as a skilled ethical hacker.
Continuous Learning and Ethical Responsibility
Cybersecurity is one of the fastest-changing fields in technology. New vulnerabilities, exploits, and defensive measures emerge regularly, which means standing still is not an option.
As an ethical hacker, you must stay updated with the latest trends, tools, and techniques. Subscribe to reputable blogs, follow thought leaders, attend cybersecurity conferences, and participate in online communities where current threats are analyzed and discussed.
Pursue continuous certification to validate your expertise. Courses such as CEH, OSCP, and CompTIA Security+ not only build your skill set but also strengthen your credibility in the eyes of employers and clients.
Equally important is staying informed about security patches and vendor updates. Regular practice in lab environments ensures you retain what you learn and can apply it in real scenarios.
But beyond knowledge and skill lies something even more critical: ethical responsibility. With the power to test, probe, and exploit comes the duty to act with integrity. Your work must always prioritize safety, transparency, and legal boundaries.
Ethical hacking is not just about thinking like a hacker. It’s about protecting systems and people while holding yourself to the highest standards of accountability and professionalism.
How Appin Can Help You Build These Skills
At Appin, we don’t just teach theory; we help you build a career-ready skill set.
You get hands-on experience with real tools, real vulnerabilities, and structured guidance on ethical hacking frameworks. Our programs are shaped around the demands of the industry, helping you stay prepared for what’s ahead.
Whether you’re starting from scratch or leveling up your current knowledge, Appin will guide you through every phase of your learning journey.
Ready to master the skills of ethical hacking in 2025? Your future in cybersecurity starts here, with Appin. Inquire Now to take your first step toward becoming a certified and confident ethical hacker.
0 notes
Text
Computer Network Interview Questions
🖥️✨ Computer Network Interview Questions and Answers – Your Easy Prep Guide! ✨🖥️
When you hear the term Computer Networks, does your mind jump to routers, IP addresses, or maybe that one time your Wi-Fi betrayed you during an online class or meeting? 😂 Well, jokes aside, computer networking is one of the core subjects for students from CS/IT backgrounds – and guess what? Interviewers LOVE to ask questions from this topic.
Whether you're preparing for your first technical interview or brushing up for a campus placement, having a solid knowledge on basic networking concepts can make a real difference. From understanding how data travels across the internet to knowing what happens behind the scenes when you type a URL into your browser – networking concepts are everywhere. 💻
🚀 Top Computer Network Interview Questions & Answers 🔍
1. What is a Computer Network? A computer network is a group of two or more computers connected to each other so they can share resources, like files, printers, or the internet. The connection can be wired or wireless.
2. What’s the difference between LAN, MAN, and WAN?
LAN (Local Area Network): Covers a small area like your home or office.
MAN (Metropolitan Area Network): Covers a city or a large campus.
WAN (Wide Area Network): Covers large distances, like the internet.
3. What is an IP address? An IP address is a unique number assigned to every device connected to a network. It helps identify your device and allows it to communicate with other devices.
4. What is DNS? DNS (Domain Name System) translates domain names like google.com into IP addresses. It’s like your phone's contact list – you don’t memorize numbers, just names.
5. What is the difference between TCP and UDP?
TCP (Transmission Control Protocol): Reliable, sends data in order, and checks for errors. Used for things like emails and web browsing.
UDP (User Datagram Protocol): Faster but less reliable. Used for streaming videos or online games.
6. What is a Router? A router connects different networks together and directs data where it needs to go. It's what allows you to use Wi-Fi at home.
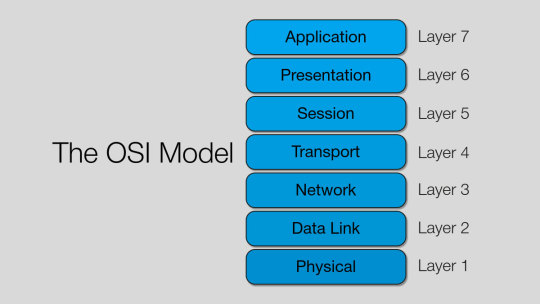
7. What is OSI Model? Can you explain its layers? The OSI Model is a framework that shows how data travels over a network. It has 7 layers:
Physical
Data Link
Network
Transport
Session
Presentation
Application Think of it like a ladder where each step adds more meaning to the data.
8. What is the difference between HTTP and HTTPS? HTTPS is just like HTTP, but secure. The “S” stands for Secure. It uses encryption to protect your data.
9. What is a MAC address? A MAC address is a unique hardware ID for your device's network card. Think of it like a digital fingerprint.
10. What is a Firewall? A firewall is a security system that monitors and controls incoming and outgoing network traffic. It helps protect your system from hackers or unwanted access.
📌 Need more? We’ve covered more in-depth questions along with real examples and diagrams on our blog here 👉 🔗 Read Full Blog - Computer Network Interview Questions & Answers

1 note
·
View note
Text
Network Load Balancer vs.Application Load Balancer Key Differences Explained
When managing traffic across servers, choosing the right load balancer is crucial for performance and scalability.Two common options are the Network Load Balancer and the Application Load Balancer.While both distribute incoming traffic, they serve different purposes and operate at different layers of the OSI model.NLBs function at the transport layer,providing ultra-fast performance for high-volume traffic with minimal latency. In contrast, ALBs operate at the application layer,offering advanced routing based on protocols, host headers, and URL paths. This article breaks down the key differences to help you choose the right solution.
Layer of Operation OSI Model Differences Network Load Balancer
The fundamental difference between NLB and ALB lies in the OSI model layer at which they operate.Network Load Balancers function at Layer 4 (Transport Layer), handling TCP, UDP, and TLS traffic with high speed and low latency. In contrast, Application Load Balancers operate at,allowing for more intelligent routing decisions based on content such as headers, paths, and cookies. This key distinction determines how traffic is analyzed and distributed, with NLB being ideal for performance-critical tasks and ALB being better suited for content-based routing and web application delivery.
Routing Capabilities and Flexibility Network Load Balancer
Application Load Balancers provide advanced routing capabilities, making them ideal for microservices and containerized applications. They can inspect the content of incoming traffic and route it based on rules involving hostnames, URL paths, and request methods. This enables developers to direct specific requests to designated backend services easily. On the other hand,Network Load Balancers offer basic routing by distributing traffic purely based on IP protocol data and port numbers, which limits their flexibility. If your environment requires sophisticated routing logic, such as directing mobile traffic differently from desktop, ALB offers the granularity and control needed.
Performance and Latency Network Load Balancers
When it comes to raw performance and handling high volumes of traffic with minimal latency, Network Load Balancers have a clear advantage. Since they operate at a lower network layer, they process packets faster and can scale to handle millions of requests per second, making them suitable for latency-sensitive and high-throughput applications like real-time gaming or financial trading platforms. Application Load Balancers, while still capable, introduce slightly more latency due to deeper traffic inspection and rule evaluation at the application layer. Therefore, if speed is your top priority, especially at scale, NLB is often the preferred choice.
Health Checks and Monitoring Network Load Balancer
Both NLB and ALB support health checks, but their implementations differ significantly. Application Load Balancers offer more advanced health checks that evaluate or responses, such as checking specific status codes or content within responses. This enables ALBs to make intelligent decisions about backend availability. Network Load Balancers, by contrast, use TCP-level health checks that verify only if a connection can be established, without assessing service responsiveness. If your application needs granular monitoring of backend health and service-level behavior, ALB provides more detailed insights, making it better suited for modern web services with dynamic content.
SSL/TLS Termination and Security Network Load Balancers
Application Load Balancers natively support SSL/TLS termination, allowing them to decrypt encrypted traffic and apply routing rules based on application content before re-encrypting it for backend delivery. This is ideal for applications requiring deep inspection of secure traffic or integration with WAF (Web Application Firewall) solutions. Network Load Balanc(Layer 4)ers can also handle TLS termination but often rely on external mechanisms or use passthrough mode for performance, where encrypted traffic is forwarded directly to targets. While both can support secure communication, ALBs offer more control over certificate management, security policies, and compliance with application-layer encryption needs.
Cost Considerations and Resource Usage Network Load Balancers
Cost is a crucial factor when selecting a load balancer. Network Load Balancers typically incur lower compute overhead and are more cost-efficient for high-performance use cases, especially when SSL termination and advanced routing are not required. Application Load Balancers, while offering richer features, generally cost more due to their higher-level processing capabilities and resource consumption. Organizations should weigh the trade-off between feature richness and operational cost. For simple traffic distribution with minimal logic, NLB offers a budget-friendly option, while ALB is ideal for applications that demand intelligent routing, content inspection, and fine-grained access controls.
Use Cases and Deployment Scenarios Network Load Balancers
Choosing between NLB and ALB often comes down to specific application requirements. Network Load Balancers excel in scenarios requiring extreme speed and resilience—such as IoT, gaming servers, and legacy applications using non-HTTP protocols. They are ideal for situations where low latency and raw power are critical. On the other hand, Application Load Balancers are tailored for modern web apps, REST APIs, and microservices where HTTP/S routing and request-level logic are essential. They shine in environments needing flexibility, such as dynamic web hosting, multi-tenant SaaS apps, or container orchestration platforms like Kubernetes and ECS with path-based routing.
Conclusion
Understanding the key differences between a Network Load Balancer and an Application Load Balancer is essential for selecting the right solution for your infrastructure. NLBs operate at the transport layer and are designed for high-performance, low-latency routing of TCP/UDP traffic, making them ideal for handling large volumes of network traffic. In contrast, ALBs function at the application layer,providing advanced routing based on content, URL, and headers perfect for web applications and microservices. Choosing between them depends on your specific use case, performance needs, and the level of routing control required.
0 notes
Text
HPE6-A86 Questions and Answers for HPE Network Switching Associate Exam
The HPE6-A86 HPE Network Switching Associate Exam is a pivotal certification for IT professionals aiming to validate their expertise in configuring and managing modern, open standard-based networking solutions. This exam focuses on HPE Aruba Networking OS-CX routing and switching technologies and assesses candidates’ abilities to implement and validate network solutions for small to medium-sized enterprises (SMEs). Whether you’re a junior network team member or an independent professional working on smaller-scale projects, earning this certification can elevate your career by demonstrating your proficiency in HPE Aruba Networking solutions. In this article, we’ll explore the exam’s structure, objectives, and preparation strategies, with a special emphasis on leveraging the most updated HPE6-A86 questions and answers from Cert007 for effective preparation.
Understanding the HPE6-A86 HPE Network Switching Associate Exam
The HPE6-A86 exam is designed for individuals with at least six months of experience supporting and maintaining wired networks. It is particularly suited for junior network administrators, engineers, or IT professionals who work on limited-scope projects or contribute to SME network deployments. The exam is proctored, consists of 60 multiple-choice questions, and must be completed within 90 minutes. Passing the exam earns you the HPE Aruba Networking Certified Associate – Switching credential, a globally recognized certification that enhances your professional credibility and opens doors to career advancement.
Comprehensive Breakdown of Exam Topics and Objectives: A Detailed Guide to What You Need to Know
The HPE6-A86 exam is structured around five core domains, each covering specific skills and knowledge areas critical to network switching. Below is a detailed breakdown of the exam objectives, including their weightings and subtopics:
1. Foundational Networking Architectures and Technologies (24%)
This section tests your understanding of core networking concepts, forming the foundation for all switching knowledge.
OSI Model (2%): Explain the seven layers and their functions.
Layer 1 Media (2%): Describe common physical media types.
Layer 2 Ethernet (3%): Understand broadcast domains and Ethernet basics.
Layer 3 Addressing (4%): Master subnetting, ARP, and routing principles.
Layer 4 Protocols (1%): Recognize TCP, UDP, and their roles.
Network Management Protocols (2%): Identify TFTP, SFTP, FTP, Telnet, and SNMPv2.
Quality of Service (QoS) (1%): Explain its importance in converged networks.
Basic Network Security (2%): Describe security setup on HPE Aruba switches.
Layer 2 Redundancy (2%): Understand STP, RSTP, and VSF benefits.
Link Aggregation (2%): Apply link aggregation techniques.
VLANs (3%): Explain VLAN configuration and functionality.
2. HPE Aruba Networking Products and Solutions (21%)
This domain focuses on differentiating and managing HPE Aruba Networking products.
Wired Product Features (5%): Identify basic features and management options.
Software Differentiators (6%): Understand software capabilities in HPE switches.
Hardware Differentiators (5%): Recognize hardware distinctions.
Management Tools (5%): Describe CLI, web, Aruba Central, mobile app, SNMP, and API tools.
3. Install, Configure, and Validate Wired Network Solutions (22%)
This practical section evaluates your ability to set up and validate HPE Aruba switches.
Basic Configuration (7%): Configure initial settings and management access.
Layer 2 Technologies (6%): Set up RSTP/MSTP, link aggregation, VLANs, and LLDP.
Layer 3 Technologies (5%): Configure IP addressing and routing.
Validation (4%): Use show commands to verify configurations.
4. Troubleshoot, Operate, and Maintain Solutions (17%)
This domain assesses your troubleshooting and operational skills.
Troubleshooting (10%): Diagnose issues in switched and routed networks.
Troubleshooting Tools (7%): Use general tools for network diagnostics.
5. Manage and Monitor HPE Aruba Networking Solutions (16%)
This section focuses on network management and administrative best practices.
Network Management (16%): Perform tasks such as monitoring, maintenance, and optimization.
Why Choose the HPE6-A86 Certification?
Earning the HPE Aruba Networking Certified Associate – Switching certification offers numerous benefits:
Industry Recognition: Validates your expertise in HPE Aruba Networking solutions, a trusted name in enterprise networking.
Career Advancement: Enhances your resume, making you a desirable candidate for network administration and engineering roles.
Increased Earning Potential: Certified professionals often command higher salaries due to their specialized skills.
Practical Skills: Equips you with hands-on knowledge for configuring, managing, and troubleshooting modern networks.
Confidence Boost: Passing the exam affirms your competence in a competitive field.
Comprehensive Preparation Strategies and Study Resources
While Cert007’s HPE6-A86 questions and answers are a cornerstone of your study plan, combining them with other resources and strategies will enhance your preparation:
Official HPE Study Guides: Use the HPE Aruba Networking Certified Associate – Switching: Official Certification Study Guide (HPE6-A86) from HPE Press, which covers AOS-CX technologies, VLANs, MSTP, LACP, QoS, and IP routing fundamentals.
Hands-On Practice: Set up a lab environment using HPE Aruba switches or simulators to practice CLI commands, VLAN setup, and troubleshooting scenarios.
Join Networking Communities: Participate in forums like the Aruba Community or Reddit’s r/networking to exchange tips and clarify doubts.
Review Key Commands: Memorize critical AOS-CX commands for configuring STP/RSTP, link aggregation, and show commands for validation.
Schedule Strategically: Book your exam when you’re consistently scoring 80%+ on Cert007’s practice tests to ensure confidence.
Conclusion
The HPE6-A86 HPE Network Switching Associate Exam is a valuable stepping stone for IT professionals seeking to specialize in HPE Aruba Networking solutions. By validating your skills in configuring, managing, and troubleshooting modern networks, this certification can significantly boost your career prospects. To prepare effectively, leverage the most updated HPE6-A86 questions and answers from Cert007, which offer realistic practice, comprehensive coverage, and detailed explanations to ensure success. Combine these materials with official study guides, hands-on labs, and community support to approach the exam with confidence. Start your preparation today with Cert007 and take the first step toward earning the HPE Aruba Networking Certified Associate – Switching credential!
0 notes
Text
Computer Networks 2024 - BSc Computer Science Part 3
Total No. of Questions: 9] [Total No. of Printed Pages: 4 Paper code: 13525 1525 B.Sc. (Computer Science) (Part 3) Examination, 2024 Paper No. 3.1 COMPUTER NETWORKS Time: Three Hours] [Maximum Marks: 50 Note: Attempt any five questions. All questions carry equal marks. 1. (a) Describe the all function of OSI layer model. (b) What is transmission media? Explain the base band and Broadband…
0 notes
Text
Computer networks constitute a major aspect of the global economy in terms of communication, operation, efficiency and reliability. The world has become a global village because of computer interconnectivity. The interconnection of computers to form both local area networks (LANs) and Wide Area Networks (WANs) is an intricate process involving network hardware, network software, operating systems, and user applications. The numerous differences in computers, network devices, operating systems, languages, and so on provide a major challenge to an effective networking environment. The Javvin Company (2013) describes the open systems interconnection (OSI) model as the standard benchmark for communication between different hardware and software architectures. The OSI model layers network communication into a seven-fold process, where each layer attends to a specific task. These layers are application, presentation, session, transport, network, data and physical layers. Layers 1 to 3 control communication between network devices while layers 4 to 7 attend to data source and destination communication. According to Oracle (2010), communication within a network involves the movement of data packets or frames from the source device to the receiving device. A network packet consists of both the source and destination address and a payload. Citap (2013) explains that a frame consists of five fields i.e. a start indicator, the source address, the destination address, control, data, and error control. The devices communicating within a network adopt the name node, device, or station. Princeton University (2013) informs the data link layer performs local delivery of packets between nodes. The process results in several challenges such as collision of frames, loss of packets, discarding of packets, and so on, mostly without feedback to the sending device, thus leading to unreliable communication. Read the full article
0 notes
Text
How police can backtrack Tor Nodes to unmask identity
Tor Project was co-founded in 2006 by 7 researchers and has had many sponsors throughout the years, including the Electronic Frontier Foundation (EFF). Here’s how it works:
When you click ‘Connect’ on Tor, you have 3 ‘firewalls’ of connections that shield your connection, and obfuscates it. However, as some might say, “...The internet is forever!” and your connections are definitely logged somewhere. This might include the exit node volunteer’s logs, Tor themselves - even if it might be indirectly/unintentional - or otherwise.

As of 23rd February 2025, there are around 8000 exit nodes – sounds pretty small, but is actually quite a lot of connections. Especially if you are doing investigative forensics!
Now you might ask yourself a few questions… such as, “How (and CAN…) the police track my usage?”, (Yes, they can, and have done so with some people before!) I will get to this question and others in a bit! (In my mind, Tor Project and similar projects are essentially glorified VPNs with a few extra features.)
If you studied IT at all in bootcamps or college, you might remember our bestie the OSI Model. This basically explains how you connect to the internet at all in 7 steps. Lets look!

As you can see, the main concern we have here is with the Network, Transport and Session layers. These 3 steps essentially bridge and keep your connection alive on any website. Tor actually recommends that you don’t have your Tor Browser fullscreen, and I personally recommend this as well!
Most websites - even the onion routed websites - tend to track these metrics:
How long you’ve been on the website
Whether you came from an ad, marketing link, search engine
Device OS
Local time / Timezone
Region (Or within 50 miles radius)
Account signup email
Hints at past usernames (if you sign-in a username you often use)
ISP (Such as Cox, AT&T, Comcast)
….and more
These metrics and stats can be sold to other companies, threat actors, or given to police for investigating.
If police can’t determine from past information mentioned, they will just look through Tor Browser’s Exit Node List and compare your IP with past IPs you’ve utilized.
“Wait… where can they get your IP?!”
They can ask bigger companies (Google, Meta, etc) to provide information.
Freedom of Information Act (FOIA) on you, which anyone can do.
Obtain a warrant to ask your Internet Service Provider (ISP)
If you are asked in-person via warrant to have your home searched, they can also collect the IP here.
So going back to the beginning… “Can the police track my identity and connections on Tor?” Yes. and it’s relatively easy. It’s why I mentioned earlier, how Tor and many Onion routers are essentially glorified VPNs - because they are.
In my opinion, though; they’re really stellar and show some unique websites that aren’t available on the clear net!
References
0 notes
Text
Network Load Balancers Explained: What They Are and Why They Matter?
Network Load Balancers (NLBs) are critical components in modern IT infrastructures, designed to optimize the distribution of incoming traffic across multiple servers. Operating at the transport layer (Layer 4), NLBs ensure high performance, low latency, and reliable service availability by directing traffic based on server health, load, and predefined rules. They are ideal for applications requiring fast and efficient handling of TCP/UDP traffic, such as real-time communication, gaming, and financial transactions. By balancing workloads, NLBs prevent server overload, enhance scalability, and ensure seamless user experiences. Additionally, they provide features like health checks, failover, and session persistence. NLBs are essential for maintaining robust and cost-efficient IT systems, supporting business continuity and growth.
Introduction to Network Load Balancers
Network Load Balancers (NLBs) are critical components in modern IT infrastructure. These devices or software tools efficiently distribute incoming network traffic across multiple servers to ensure optimal resource utilization, reliability, and performance. Whether used in on-premises environments or cloud setups, NLBs play a vital role in maintaining service availability.
How Network Load Balancers Work
NLBs function by routing client requests to available backend servers based on predefined rules and algorithms. By analyzing factors such as server health, traffic volume, and session persistence, they ensure that no single server becomes a bottleneck. This intelligent traffic distribution enhances overall system responsiveness.
Types of Load Balancers: Network vs. Application
Load balancers are generally categorized as network or application load balancers.
Network Load Balancers: Operate at the transport layer (Layer 4 of the OSI model). They handle TCP/UDP traffic and are ideal for low-latency, high-throughput scenarios.
Application Load Balancers: Work at the application layer (Layer 7), managing HTTP/HTTPS traffic and offering advanced features like content-based routing and SSL termination.
Key Features of Network Load Balancers
NLBs provide various features that make them indispensable:
Health Checks: Regular monitoring of server health to avoid sending traffic to unresponsive nodes.
Scalability: Easy scaling of resources to handle fluctuating traffic loads.
Low Latency: High-performance routing for real-time applications like gaming and financial transactions.
Session Persistence: Ensuring user sessions are consistently routed to the same server when required.
Use Cases for Network Load Balancers
NLBs are versatile and serve numerous purposes:
E-Commerce Platforms: Distributing traffic during peak sales events to prevent downtime.
Real-Time Applications: Supporting low-latency requirements for video conferencing or online gaming.
Cloud Environments: Enabling seamless scaling in hybrid or multi-cloud architectures.
Advantages of Implementing Network Load Balancers
Incorporating NLBs into your network architecture offers several benefits:
Improved Performance: By balancing workloads, they prevent server overload and enhance application responsiveness.
High Availability: NLBs minimize downtime by rerouting traffic when a server or network segment fails.
Enhanced Security: Some NLBs provide features like DDoS protection, adding an extra security layer.
Cost Efficiency: By optimizing resource utilization, organizations can reduce hardware costs and energy consumption.
Choosing the Right Load Balancer for Your Needs
Selecting an NLB depends on specific business requirements:
Traffic Patterns: Evaluate expected traffic volume and latency needs.
Deployment Environment: Whether on-premises or cloud-based, compatibility with existing infrastructure is crucial.
Scalability Requirements: Choose a solution that supports growth and varying demand.
Vendor Support: Opt for reliable solutions from trusted providers to ensure robust support and updates.
Conclusion
Network Load Balancers are indispensable tools for modern IT systems, ensuring optimal performance, scalability, and reliability. They empower businesses to handle varying traffic demands, maintain high availability, and improve user experiences. By understanding how NLBs work and their advantages, organizations can make informed decisions about integrating these solutions into their infrastructure, staying ahead in an increasingly connected digital landscape.
0 notes
Text
youtube
Summary
📋 10 Essential Questions and Answers:
Encryption vs. Hashing: Encryption secures data confidentiality, while hashing ensures data integrity.
Home Network or Lab: A detailed description of your setup showcases your passion and engagement in cybersecurity.
OSI Model: Understanding its layers and applications is foundational for network troubleshooting.
Open Source vs. Closed Source: Analyze the context; both have merits depending on the scenario.
Security Frameworks: Familiarity with frameworks like NIST, HIPAA, or PCI DSS demonstrates practical knowledge.
Primary Goal of Cybersecurity: Supporting business objectives by managing risks effectively.
Risk, Threat, Vulnerability: Define these concepts and explain their role in balancing security measures.
Sources for Security News: Staying updated through resources like Dark Reading or Security Weekly highlights commitment to learning.
Preventive vs. Detective Controls: A nuanced analysis of each control's application indicates deeper understanding.
Compression vs. Encryption: Data should be compressed first, then encrypted for better security.
Insights Based on Numbers
🧠 Interview Depth: Expect varied difficulty levels, from basic definitions (e.g., OSI Model) to scenario-based reasoning (e.g., security frameworks).
📈 Knowledge Sources: Regular updates from platforms like Feedly or Krebs on Security are essential for ongoing learning.
0 notes
Text
SOCKS5 Proxy: Enhancing Your Online Privacy and Security
SOCKS5 Proxy: Enhancing Your Online Privacy and Security
In an era where online privacy and security have become paramount concerns, various tools and technologies have emerged to protect users from cyber threats and surveillance. One such tool is the SOCKS5 proxy, a versatile and powerful solution that offers enhanced anonymity and security for internet activities. This article delves into the world of SOCKS5 proxy, explaining its functionality, benefits, and practical applications.To get more news about socks 5 proxy, you can visit ip2world.com official website.
SOCKS5 proxies operate at the session layer of the OSI model, which allows them to handle various types of traffic, including HTTP, HTTPS, SMTP, FTP, and more. This versatility makes SOCKS5 proxies suitable for a wide range of applications, from web browsing to gaming and file sharing.
Key Benefits of Using a SOCKS5 Proxy Enhanced Privacy and Anonymity: By masking your IP address, a SOCKS5 proxy helps protect your identity and location from prying eyes. This is particularly important when accessing sensitive information or using public Wi-Fi networks.
Improved Security: SOCKS5 proxies can encrypt data transmission, adding an extra layer of security to your online activities. This helps safeguard your information from cyber threats such as hacking and data interception.
Bypassing Geo-Restrictions: Many websites and services impose geographic restrictions on their content. A SOCKS5 proxy allows you to bypass these restrictions by routing your traffic through a server located in a different region, granting you access to otherwise unavailable content.
Reduced Latency: In some cases, using a SOCKS5 proxy can reduce latency and improve connection speeds. By optimizing the route between the client and the server, a SOCKS5 proxy can enhance the overall performance of your internet connection.
Versatility: Unlike other types of proxies that are limited to specific protocols, SOCKS5 proxies support a wide range of network protocols. This makes them suitable for various applications, including web browsing, email, gaming, and streaming.
Practical Applications of SOCKS5 Proxy Secure Web Browsing: Using a SOCKS5 proxy can protect your identity and data while browsing the internet. This is especially useful when accessing banking services, online shopping, or other sensitive activities.
Anonymous File Sharing: SOCKS5 proxies are commonly used for anonymous file sharing through peer-to-peer (P2P) networks. By masking your IP address, a SOCKS5 proxy helps protect your identity while downloading or uploading files.
Enhanced Gaming Experience: Gamers can benefit from reduced latency and improved connection stability by using a SOCKS5 proxy. This can lead to a smoother and more enjoyable gaming experience, particularly for online multiplayer games.
Bypassing Censorship: In regions where internet access is restricted or censored, a SOCKS5 proxy can provide a means to bypass these limitations and access blocked websites and services.
Conclusion The SOCKS5 proxy is a powerful tool for enhancing online privacy, security, and accessibility. By masking your IP address, encrypting data transmission, and supporting a wide range of network protocols, a SOCKS5 proxy offers a versatile and effective solution for protecting your digital footprint. Whether you are browsing the web, sharing files, gaming, or bypassing geo-restrictions, a SOCKS5 proxy can significantly improve your online experience.
0 notes
Text
Telecommunications Protocols: Open Systems Interconnection (OSI) Model
Usually, the analysis of communication protocol stacks begins, relatively reasonably, by considering the seven-layer Open System Interconnection model (seven-layer model or just OSI model or OSI), which the International Organization for Standardization ISO developed jointly with the telecommunications division of the International Telecommunication Union (ITU-T). The OSI model is still an excellent tool for learning the fundamentals of telecommunications network architecture, although it has not gained the popularity its creators hoped for.
The main feature of the OSI model is its openness. This means that an appropriate standardized set of protocols guarantees the possibility of interoperability between equipment from different manufacturers, which is vital not only for equipment and software manufacturers but also for telecom operators, service providers, and users since it dramatically simplifies the procedure for equipping networks.
The OSI model was developed in the 1970s based on experience gained in creating computer networks, mainly global ones. Therefore, its application area, strictly speaking, is packet data networks.
Interestingly enough, global data networks came earlier than local ones. This is explained by the history of the development of computers (computing machines), the first stage of which is associated with mainframes. These vast machines were costly and served many users, who were granted access only for a certain period. Long-distance communication channels were needed to organize such access. In the first stage, the role of such data transmission media was played by analog modems operating over voice-frequency channels (touch-tone) of analog transmission systems (Analog Data Transmission Systems, or ADTS), and the first data transmission protocols were modem protocols of physical levels that ITU-T has standardized in a series of Type V recommendations.
Since the touch-tone ADTS channel is very narrow, with a width of 300 to 3200 Hz, in addition to multi-position modulation methods for data transmission, additional efficient algorithms for using the frequency band were required, particularly data signal compression algorithms. The critical issue with modem data transmission over ADTS channels was the number of errors since touch-tone channels were initially designed only to transmit telephone signals. Therefore, the third group of V-series protocols contains, among other things, error correction protocols.
In terms of error correction, communication systems are divided into systems with and without retransmission of corrupted data elements. In transmission systems over electrical cables subject to external interference and containing many intermediate amplifiers or regenerators, the probability of errors in the data signals is very high. Therefore, the channels of these systems usually retransmit corrupt message fragments. Naturally, this method significantly reduces the data efficiency of channels.
The situation turned around with the transition to optical cables, which are well-protected from external interference and contain a small number of intermediate amplifiers and repeaters. This significantly reduced the number of errors, so it was possible to eliminate error correction at the physical layer and, if necessary, perform it at higher protocol levels.
The active development of local networks began with the advent of mini, micro, and, finally, personal computers (PCs). Thus, telephone networks first formed local ones, and only then, with technological progress, intercity ones; data transmission networks, on the contrary, evolved from global down to local.
The creation of the seven-layer OSI model was based on the following principles:
There should not be too many layers so that the design and implementation of the network are not overly complex. There should not be too few levels so that the functions performed by the levels do not turn out to be overly complex
The functioning of each level is transparent to other levels
The tasks performed by each level must be clearly delineated
The next level is created only when a new level of abstraction is needed
It is clear that solving such a problem successfully takes not only a lot of experience and knowledge but also a particular artistic approach.
Each layer of the OSI model interacts with three others: it provides services to an upper one, uses the services of a lower one, and accesses an equal (peer) layer of another computer system. More formally, a service architecture contains three essential elements: the Service User, the Service Provider, and the Service Access Point (SAP).
In this context, a service user is an OSI model layer receiving services from an adjacent OSI model layer. The service provider is the layer of the OSI model that provides services. Finally, SAP is an element of the OSI model through which one OSI layer can request a service from another OSI model layer. Simply put, SAP is nothing more than a service delivery protocol.
For example, the link layer of system A is a user of physical layer services, a service provider for the network layer of this system, and exchanges information with the link layer of system B.
OSI Layers and Layer Groups
Each layer of the OSI model performs specific functions necessary for the system's proper functioning. Let's list the seven layers of the OSI model from top to bottom and describe their main functions.
Implementations of the four upper layers of the OSI model (application, presentation, session, and transport) can be found in every peripheral device; the three lower layers (network, data link, and physical) are present at all intermediate (transit) connection points between endpoints.
Therefore, all the OSI model layers can be divided into two functionally different groups: the upper and lower layers. The first—also called 'Host Layers' or 'end-end'—are responsible for the operation of applications and are implemented only in software products. The second—'Media Layers' or 'chained'—transmits data. Moreover, the physical and data link layers contain software and hardware components.
A common feature of the three lower levels is that they can support any type of data (including service data) generated by the four upper levels. In other words, the lower levels are utterly indifferent to the data they transmit and are solely concerned with delivering it from one point to another.
Host Layers OSI
In this part, we will talk about the four upper levels that ensure the operation of network applications.
The Application Layer provides services directly to the user's apps. It forms a set of open and standard application programming interfaces (APIs). Implementing the application layer might be complex because many applications use its services. Examples of OSI application layer protocols are distributed directory services by the ITU-T X.500 recommendation and its "lightweight" version (Lightweight Directory Access Protocol, LDAP), as well as remote procedure calls (RPC). The latter is a very efficient way to distribute computing power between the client and the server.
The Presentation Layer performs general data transformation. One of the services at this level is encryption, which ensures information security. In particular, Web server software includes encryption protocols to protect customers' financial information. Another example of a presentation-level service is compression, which reduces the amount of data sent between two computers. Thus, many virtual private network (VPN) implementations use tunneling protocols, where a packet of one protocol is placed inside another packet. The tunneling mechanism requires adding significant service information to the transmitted data, which can be easily compressed. Therefore, VPNs usually include a compression algorithm.
Another typical operation of the presentation level is transcoding, which is less complex than encrypting/decrypting or compressing/decompressing. An example of transcoding is the conversion of ASCII codes to EBCDIC and back according to specific tables. Still, such simple transcoding operations are only sometimes possible. Therefore, the International Organization for Standardization (ISO) has developed a special Abstract Syntax Notation program version 1 (ASN.1), which helps programs running on different machines and written in different programming languages to exchange data.
The Session Layer provides additional services to the transport layer if the connection session is established first. In addition to managing data back and forth, the most important functions of this layer are starting and terminating the session and syncing data. Session layer services are unused if the connection does not need to be established.
The Transport Layer performs error-free, message-oriented end-to-end transmission, and it must support this function regardless of the reliability of the underlying layer. The underlying layer is especially unreliable during packet transmission in connectionless communication. In this case, the transport layer must be 'smart' enough to compensate for the weaknesses of the underlying layer. Due to its greater reliability, the transport layer can be less complex in a connection-oriented packet network. Finally, the underlying service can be highly robust, connection-oriented with channel switching, and have a reliable link-layer protocol. In this case, the transport layer does not need to do anything to ensure consistently high transmission quality. Thus, the complexity of the transport layer is inversely proportional to the reliability of the underlying layers. To perform its main task—error-free delivery of messages—the transport layer provides the functions of addressing, opening, and closing connections, assigning priority to data, monitoring and error correction, data flow control, failure recovery, and multiplexing.
Continued in the next Around Cable category post.
0 notes
Text
Think Outside the Box for IBM Certification Exams
Cracking IBM certification exams isn't just about cramming facts; it's about innovative strategies that go beyond conventional study methods. In a landscape where competition is fierce, and the stakes are high, it's essential to explore unconventional approaches to ace these exams.
Here are some unconventional study tips that might help you grasp the concepts of IBM certifications better and perhaps ace the tests.
Breaking the Mold: Creative Study Strategies
Traditional study methods often involve hours of monotonous reading and note-taking. However, breaking away from this mold can lead to more effective learning. One unconventional strategy is gamification. Transforming study material into games or quizzes can make learning fun and engaging. Did you know that learners retain up to 90% of information through interactive activities compared to just 10% through reading?
Another creative approach is peer teaching. Instead of studying alone, explain concepts to a friend or colleague. Teaching others not only reinforces your understanding but also helps identify areas of weakness.
Mnemonic Devices: Unlocking Memory Vaults
Mnemonic devices are powerful tools for memorization. They work by associating complex information with easier-to-recall cues. Creating memorable mnemonics can be a game-changer for IBM certification exams.
For example, when learning the OSI model layers (Application, Presentation, Session, Transport, Network, Data Link, Physical), think, "All People Seem To Need Data Processing." This simple phrase encapsulates the entire model, making it easier to remember.
Moreover, visual aids can enhance memory retention. Drawing diagrams or mind maps to illustrate concepts can transform abstract ideas into tangible images, strengthening neural connections.
Unconventional Approaches: Thinking Beyond Boundaries
Ever tried sleeping on it? Research suggests that sleep enhances memory consolidation. Before your exam, ensure a good night's sleep to optimize retention and recall.
Also, incorporating music into your study routine can enhance focus and productivity. Experiment with different genres to find what works best for you. Did you know that classical music, like Mozart, has been linked to improved cognitive function?
Putting Theory into Practice: The Power of Simulations
Theory is crucial, but practical experience is equally vital. IBM certification exams often test not just knowledge but also application. Simulations can bridge this gap between theory and practice.
By immersing yourself in virtual environments that replicate real-world scenarios, you can gain hands-on experience. This approach not only reinforces theoretical concepts but also builds confidence in tackling practical challenges.
Charge Ahead and Make the Most of Your IBM Certification
Pacing towards your IBM certification exam success, traditional study methods may not always suffice. Embracing unconventional strategies can provide the competitive edge needed to ace these exams.
From gamification to mnemonic devices, from sleep optimization to practical simulations, there's a plethora of creative approaches to explore. So, why confine yourself to the confines of conventional wisdom when you can think outside the box?
As you embark on your certification journey, remember this: innovation knows no bounds. Dare to be different and embrace the unconventional, and Ascendient Learning can help you unlock the door to success in IBM certification exams.
We have a plethora of resources and experts to guide you toward the right IBM certification and ways to ace it. Click here to know more.
For more information visit: https://www.ascendientlearning.com/it-training/ibm
0 notes