#dot net technology
Explore tagged Tumblr posts
Text
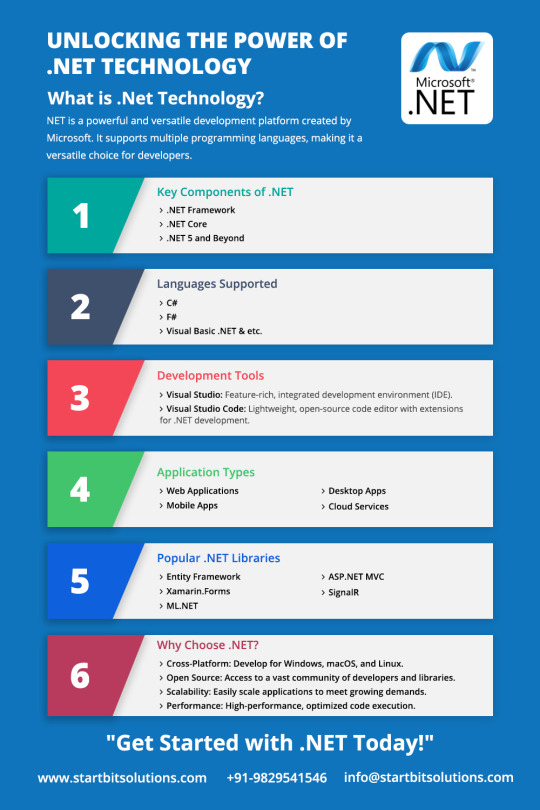
.NET technology, by Microsoft, offers versatile, secure, and efficient software development. It supports multiple languages, has a rich class library, ASP.NET for web apps, and cross-platform capabilities with .NET 5+. Robust security, memory management, and community support make it a powerful choice.
0 notes
Text
https://www.arichinfotech.com/courses/
#mainframe#information technology#microsoft#dot net#cyber security#it jobs#microsoftcloud#youtube#ai#chat gpt
0 notes
Text
How to Make Your Dot Net Application Secure?
Is your #DotNet application truly secure? With cyber threats growing, it’s critical to safeguard your code, data, and users. Learn the essential steps to fortify your app—from strong authentication to encryption, HTTPS, and vulnerability scanning. Don't leave your app exposed—discover expert tips for ultimate security.
0 notes
Text

0 notes
Text
Dot net web development services in Bangalore- Pattem Digital
Pattem Digital has earned a reputation of a reliable and dependable outsourcing software development company. We support businesses of types, from a startup to small-sized companies & large enterprises. Our dot net web development services include industry-recognized platforms & frameworks . Net technology is having various applications in developing web applications comprising of multi- tired software architecture can build more flexible apps. Reach to us if you are looking for dot net solutions.
0 notes
Text

Hiring Senior .NET Developers
Calling all experienced .NET developers!
Join our innovative team and make a difference in the healthcare industry!
At NationsBenefits India (AKA @nbhealthtech), we are passionate about improving healthcare and we're looking for talented individuals like you. We value our team and provide a challenging yet rewarding environment.
Take your career to the next level. Send your resume to [email protected] and be part of our exciting journey
#NB Healthcare Technologies#NationsBenefits India#Hiring#Dot NET Developers#Senior Roles#Apply Today#Urgent Requirement
0 notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
420 notes
·
View notes
Text
Thoughts on Loris
I have more thoughts and theories than concrete understanding of his character
He either feels half-baked as a side character that had more to him or just my mind being unable to connect the dots so some of this kind of jumps around
SO:
Loris is introduced as a sad somber guy still loosely wearing his enforcer uniform while off duty. When he meets Vi his first words are something like ‘did you lose someone in the attack’, the actions of him drinking insinuates that he most likely lost someone himself.
Appearance wise Loris has a section of his hair tied with a blue colored bead and pulled into his field of vision. It’s a stretch but when Ekko wears a colored band in his hair it’s to symbolize the ‘loss’ of Jinx/Powder in the finale episode. I think Loris wears the bead in his hair to be a constant reminder of his loss- by having it remain in his sight makes that loss a constant presence.
Anyways, besides that Loris is shown in episode 1 to not want to go to the memorial when Vi pats him on the foot since he just closes his eyes and pretends to sleep
When he does go and the attack on the memorial happens he uses a shield, a shield that's seen discarded when Vi walks around the aftermath.
It could be foreshadowing that he dies in battle, in episode 9 he dies the one time he doesn’t have his shield, or the shield might have some type of connection to the person he loss
Now the notes:
-His shield gets a hextech advancement
-On the striketeam he’s first to push their advances with his shield in E3, and when fighting he uses his shield to bash into them offensively,
and later when he’s the one to first get injured and get a limp from Jinx’s traps the shield becomes a crutch and a safety net for him. (I think it’s interesting that it was only when he traveled in front of Caitlyn that he got hurt )
-Even with a limp, Loris does his best to react to shield Steb when the tunnel they climbed out of get’s Grey rerouted straight to them
-His personality is consistently fatherly, comforting Vi, comforting Maddie when they see the murder dolls (his arrow deaths included), even comforting Vi again after being pushed away and reuniting with her without hard feelings
In that reunion scene when Vi subconsciously compares Loris to Vander we then see exactly their relationship
-Loris seems to know his way around the undercity, keep in mind it’s most likely not from the strike team traveling because they mostly used the filtration system to get through/travel. He goes with Vi to the fighting ring and when she pushes him away he’s just fine leaving her to travel elsewhere.
-Loris was the first to leave when the Noxus general (Ambessa) took over and began doing their saultes. I think he actually might have ties to the Undercity or had been from that side of the city before going topside to be an officer. I wish we knew what led to him taking said role, because like Steb who shows his compassion by being a medic on top of being an enforcer, Loris as only an enforcer shows it by choosing defensive gear over guns as his main weapon.
-Loris returns only when the Noxus have left/ are realized as the enemy and when he returns he returns with knowledge. It seems he might have fought them before or at least studied them. He teaches the enlisters how to fight the Noxus with a weapon that wasn’t a shield and yet he holds it easily
- In the final episode (9) when he's using the Hextech technology repurposed as a canon, he works well with his team and Vi and I must reiterate its the only time in battle that he does not have a shield, and in the end the last time
When Vi sees Loris dead she sees him with the side of his face that has the blue bead in his hair hanging mutely without light catching it.
And that's his end.
I don’t know, it’s like, I’m missing something.
Maybe the blue is like a powder/jinx reference thing and when Loris dies and “Vander” appears and Jinx chooses to be Powder again (?) it shows that that side of Jinx is dead like how Vander is dead now that his consciousness was killed from the monster/wolf mutant thing. Since Vi saw Loris as Vander/father figure and Loris lost someone who is (PROBABLY) symbolized by the blue bead in his hair.
It's a big fat stretch but I’m grasping at strings here and it shows lol
Hope I helped :D
27 notes
·
View notes
Text
Object permanence

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You can pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

#20yrsago Shirky: Net is a kayak, driven by its environment https://corante.com/many/folksonomies-are-a-forced-move-a-response-to-liz/
#20yrsago Whistler’s Delight mashup mixes 22 whistling songs https://web.archive.org/web/20050909012025/https://www.djriko.com/music/DJ Riko - Whistler's Delight (Full version).mp3
#15yrsago Londoners: Mass photography event in Trafalgar Square today! I’m a photographer, not a terrorist https://www.flickr.com/photos/doctorow/tags/phnat
#15yrsago Activist ejected from “public” meeting on secret copyright treaty for tweeting https://pisanty.blogspot.com/2010/01/acta-consulta-del-impi-en-mexico.html
#15yrsago Remembering the golden age of pulps with Robert Silverberg https://francesca.net/silverberg.html
#15yrsago O’Reilly drops ebook DRM, sees 104% increase in sales https://web.archive.org/web/20100406013442/http://toc.oreilly.com/2010/01/2009-oreilly-ebook-revenue-up-104-percent.html
#15yrsago Defective by Design anti-DRM picket at Apple tablet launch https://www.defectivebydesign.org/apple-tablet-san-francisco-launch
#15yrsago EFF won’t give up the fight over NSA warrantless wiretapping https://www.eff.org/press/archives/2010/01/21
#15yrsago Canada’s National Film Board online archive: a success story https://blog.nfb.ca/blog/2010/01/21/online-video-stats/
#15yrsago Naked airport scanner catches cellphone, misses bomb components https://www.schneier.com/blog/archives/2010/01/german_tv_on_th.html
#10yrsago They put a Pirate Party MEP in charge of EU copyright reform: you won’t believe awesomesauce that followed https://www.discuto.io/en/consultation/6240
#5yrsago The 1970s called and they want their proto-McMansions back! https://mcmansionhell.com/post/190405899096/the-mcmansion-hell-yearbook-1970
#5yrsago Angelenos! Come to ICANN this Friday to Save Dot ORG! https://www.eff.org/event/savedotorg-protest-icann
#5yrsago The sordid tale of Microsoft’s epic tax evasion and the war they waged against the IRS https://www.propublica.org/article/the-irs-decided-to-get-tough-against-microsoft-microsoft-got-tougher
#5yrsago Forensics team accuses Prince Bone Saw of hacking Jeff Bezos’s phone to obtain kompromat and force Washington Post silence on Khashoggi https://arstechnica.com/information-technology/2020/01/report-bezos-phone-uploaded-gbs-of-personal-data-after-getting-saudi-princes-whatsapp-message/
#5yrsago Boeing indefinitely halts 737 Max production https://www.cnn.com/2020/01/21/business/boeing-737-max-production-halt/index.html
#5yrsago Sonos warns customers that their older speakers will shortly be e-waste https://www.theregister.com/2020/01/21/sonos_bricking_laudio_gear/
#5yrsago Year of the Rabbit: a graphic novel memoir of one family’s life under the Khmer Rouge https://memex.craphound.com/2020/01/22/year-of-the-rabbit-a-graphic-novel-memoir-of-one-familys-life-under-the-khmer-rouge/
#5yrsago In serving big company interests, copyright is in crisis https://memex.craphound.com/2020/01/22/in-serving-big-company-interests-copyright-is-in-crisis/
#1yrago Boeing, Spirit and Jetblue, a monopoly horror-story https://pluralistic.net/2024/01/22/anything-that-cant-go-on-forever/#will-eventually-stop

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!
8 notes
·
View notes
Text
Over the past few years, the United States has become the go-to location for companies seeking to suck carbon dioxide out of the sky. There are a handful of demonstration-scale direct air capture (DAC) plants dotted across the globe, but the facilities planned in Louisiana and Texas are of a different scale: They aim to capture millions of tons of carbon dioxide each year, rather than the dozens of tons or less captured by existing systems.
The US has a few things going for it when it comes to DAC: It has the right kind of geological formations that can store carbon dioxide pumped underground, it has an oil and gas industry that knows a lot about drilling into that ground, and it has federal grants and subsidies for the carbon capture industry. The projects in Louisiana and Texas are supported by up to $1.05 billion in Department of Energy (DOE) funds, and the projects will be eligible for tax credits of up to $180 per ton of carbon dioxide stored.
“It’s quite clear that the United States is the leader in policy to support this nascent sector,” says Jason Hochman, executive director at the Direct Air Capture Coalition, a nonprofit that works to accelerate the deployment of DAC technology. “At the same time, it’s nowhere near where it needs to be to get on track—to the scale we need to get to net zero.”
But support for carbon storage is far from guaranteed. Project 2025, the nearly thousand-page Heritage Foundation policy blueprint for a second Trump presidency, would dramatically roll back policies that support the DAC industry and carbon capture more generally. The Project 2025 Mandate for Leadership document proposes eliminating the DOE’s Office for Clean Energy Demonstrations, which provides funds for DAC facilities and carbon capture projects, and also calls out the 45Q tax credit that supports DAC as well as carbon capture, usage, and storage—filtering and storing carbon dioxide emitted by power plants and heavy industry. (The Heritage Foundation did not respond to WIRED’s request for comment.)
Sucking carbon out of the sky is not uncontroversial—not least because of the oil and gas industry’s involvement in the sector—but the Intergovernmental Panel on Climate Change’s Sixth Assessment Report says that using carbon dioxide removal to balance emissions from sectors like aviation and agriculture is unavoidable if we want to achieve net zero. Carbon dioxide removal can mean planting trees and sequestering carbon in soil, but a technology like DAC is attractive because it’s easy to measure how much carbon you’re sequestering, and stored carbon should stay locked up for a very long time, which isn’t necessarily the case with forests and soil.
As DAC technology is so new, and the facilities constructed so far are small, it’s still extremely expensive to remove carbon from the atmosphere this way. Estimated costs for extracting carbon go from hundreds of dollars per ton to in excess of $1,000—although Google just announced it is paying $100 for DAC removal credits for carbon that will be sequestered in the early 2030s. On top of that, large-scale DAC plants are likely to cost hundreds of millions to billions of dollars to build.
That’s why government support like the DOE Regional DAC Hubs program is so important, says Jack Andreasen at Breakthrough Energy, the Bill Gates–founded initiative to accelerate technology to reach net zero. “This gets projects built,” he says. The Bipartisan Infrastructure Law signed in 2021 set aside $3.5 billion in federal funds to help the construction of four regional DAC hubs. This is the money that is going into the Louisiana and Texas projects.
Climeworks is one of the companies working on the Louisiana DAC hub, which is eligible for up to $550 million in federal funding. Eventually, the facility aims to capture more than 1 million tons of carbon dioxide each year and store it underground. “If you do want to build an industry, you cannot do it with demo projects. You have to put your money where your mouth is and say there are certain projects that should be eligible for a larger share of funding,” says Daniel Nathan, chief project development officer at Climeworks. When the hub starts sequestering carbon, it will be eligible to claim up to $180 for each ton of carbon stored, under tax credit 45Q, which was extended under the Inflation Reduction Act.
These tax credits are important because they provide long-term support for companies actually sequestering carbon from the atmosphere. “What you have is a guaranteed revenue stream of $180 per ton for a minimum of 12 years,” says Andreasen. It’s particularly critical given that the costs of capturing and storing a ton of carbon dioxide are likely to exceed the market rate of carbon credits for a long time. Other forms of carbon removal, notably planting forests, are much cheaper than DAC, and removal offsets also compete with offsets for renewable energy, which avoid emitting new emissions. Without a top-up from the government, it’s unlikely that a market for DAC sequestration would be able to sustain itself.
Most of the DAC industry experts WIRED spoke to thought there was little political appetite to reverse the 45Q tax credit—not least because it also allows firms to claim a tax credit for using carbon dioxide to physically extract more oil from existing reservoirs. They were more worried, however, about the prospect that existing DOE funds set aside for DAC and other projects might not be allocated under a future administration.
“I do think a slowing down of the DOE is a possibility,” says Andreasen. “That just means the money takes longer to get out, and that is not great.” Katie Lebling at the World Resources Institute, a sustainability nonprofit, agrees, saying there is a risk that unallocated funds could be slowed down and stalled if a new administration looked less favorably on carbon removal.
The Heritage Foundation doesn’t just doubt the carbon removal industry—it is openly skeptical about climate change, writing in one report that observed warming could only “theoretically” be due to the burning of fossil fuels, and that “this claim cannot be demonstrated through science.” In its Project 2025 plan, the foundation says the “government should not be picking winners and losers and should not be subsidizing the private sector to bring resources to market.”
But without government support, the private sector would never develop technologies like DAC, says Jonas Meckling, an associate professor at UC Berkeley and climate fellow at Harvard Business School. The same was true of the solar industry, Meckling says. “You cannot start an industry with a societal good in mind unless you get governments to take an active role,” says Nathan of Climeworks.
While there are some question marks over the future of DOE grants for DAC, the industry appeals to legislators on both sides of the aisle. The Texas DAC hub is being built by 1PointFive, a subsidiary of Occidental Petroleum, and both DOE projects are located in firmly red states. When it was announced that DOE DAC hubs funding would be spent in Louisiana, Senator Bill Cassidy said: “Carbon capture opens a new era of energy and manufacturing dominance for Louisiana. It is the future of job creation and economic development for our state.”
In the long run, Nathan says, the aim is for DAC to be viable on its own economic terms. In time, he says, that will mean regulation that requires industries to pay for carbon removal—a stricter version of emissions-trading schemes that already exist in places like California and the European Union. Eventually, that should lead to a place where the direct air industry no longer requires government support to remove carbon from the atmosphere at scale. “I’m looking at the fundamentals, and those aren’t driven by who’s in office,” Nathan says.
12 notes
·
View notes
Text
☀️ OO1 - cyber themed npts

☀️ names 01, 404, ada, ajax, astra, bit, blink, byte, cersei, circuit, click, code, cyber, dex, dot, encrypt, exe, flash, futura, gizmo, glitch, hack, hotwire, lux, mecha, mechanism, metal, minus, neo, net, one, pearl, pixel, plus, python, robot, spark, tera, tilde, vesper, vi, web, xios, xyl, xylen, zap, zen, zero
☀️ pronouns .gif/.gifs, .jpg/.jpgs, alt/alts, by/byte, cd/cds, click/clicks, code/codes, compu/computer, cpu/cpus, cy/cyan, cy/cyber, elec/electric, file/files, gli/glitch, glow/glows, hack/hacks, img/imgs, key/keys, link/links, machine/machines, malware/malwares, metal/metals, neo/neos, num/number, pc/pcs, pix/pixel, screen/screens, tab/tabs, tech/techs, txt/txts, type/types, url/urls, web/website, wire/wires, zero/one, >/>self, #/#self, !/!self, ?/?self, +/+self, ae/aem, ce/cem, ky/kyr, ny/nym, vi/vir, zy/zyr, hz/hzm, shz/hzr, thzy/thzm, zt/zts, 💿/💿self, ⌨️/⌨️self
☀️ titles the cybernetic, the encrypted one, the one born of technology, the supercomputer, the virtual one, prn behind the screen, prn between the lines of code, prn from cyberspace, prn made of binary, prn of code, error 404: [name] not available
☀️ @id-pack-archive
#���️ solar#☀️ npt#npt#npts#names pronouns titles#npt pack#npt ideas#id pack#id packs#cyber npts#cyber id pack
4 notes
·
View notes
Note
"Don't Deal with a Dragon" shadowrun ozzy???? shadowrun ozzy????? i dont know shit about shadowrun but may i get a shadowrun ozzy??
Send me "Don't Deal with a Dragon" and I'll assign your character a Shadowrun character concept" | ACCEPTING

---- In the depths of Europe, a tiny village is barely a dot on a map. They have connection to the Matrix, but they're the kind of remote that GridGuide never even considered them as a possible place to implement self-driving cars. After all, the vehicle population was on average older than the company itself. These were a people that didn't need to be sold cars.
But what they were sold was a religion. They were sold mechanical workers to help till their fields and clear the snow and hang up the lights for their blackbird rites and rituals.
This was a place that used the Matrix as one did the old 'net. Watching videos, for trideo development was unnecessary. Why have holograms when a handyman or codejockey could turn the scrap of old satellite tech into uplinks, route 'em to old televisions that would make even the most tech-illiterate sprawler gag.
In a village such as this... who would expect the pastor of the church to be one of the most technologically-advanced of his people? To have made pilgrimage to the cities of Europe, taken of their strengths, while maintaining the humility of his position? A man with a flock of crows, who learned to adapt to the changing times, rather than stay stuck in tradition and rite. A flock of chrome bones and cameras for eyes, with minds of code made to evoke the personalities and livelihood of the corvid they impersonate.

---- The man was a Rigger, whose spine and nerves had been invaded by technology, who could connect to compatible vehicles and drones and become them. The twitch of a finger flexes pistons, a tensed shoulder turns the steering axle, a clenching of the diaphragm introduces gas into the engine and the car goes. Eyes become windows into the soul of the machine, cameras on the dashboard giving the rigger an out-of-body experience... and far more granular control than was otherwise humanly possible. Each and every one of his bird-drones, made to look like the real things, could be inhabited, the only indication that anything was any different was that the bird would go still. It would 'forget to act', and it would pay more attention. Blink... and you'd miss it. The less said about any magician who claims "Raven" as their mentor spirit in his presence, the better.
Any of Father Oswald's birds could be possessed so, lending an air of credibility to tales of children and sinners being watched by the godly. When money grew tight, the preacher would leave sermons for... who? Altar boys? The devout? Someone would have to tend to the village whilst he travels to the cities, he would indulge in their lights and their vices, and be paid to smuggle, kill, and steal.
His body is marred by cyberware; smuggler's compartments form pockets that were taut in his youth, and remain strengthened by their implantation despite the rigors of age around them. Small pouches in the flesh, large enough and water-tight to carry things over borders and through rent-a-cop inspections. Obvious chrome keeps others from searching the old flesh, and law enforcement are all the more fools for it.
---- Accompanied by crows, the runner known as "Flock" keeps abreast of developments in the nearby cities. Old friends, from before he went into retirement ("this time for certain" he would say, lasting anywhere from months to years before he took another run) do not reach out first. They always wait, and they always think of him when opportunities flitter over their commlinks, trickling down through the shadownet and across their desks. How many crews has he run with, missions and schemes concocted over weeks or months, executed to perfection before he left for his little village again, several thousand nuyen the richer, and expecting never to see comrades and coworkers again?
How many times did he leave with one of their number left in a shallow grave?
No, Flock was an enigma, and in his career he's forgotten more than most runners ever get to learn. He was alive when the first Orks and Elves were born, when the dragons emerged and the Sixth World was made manifest. His has been a life of adapting to an ever-changing landscape, more aware than any of you how fluid the Megas' hold on the world truly are, no matter how monolithic and untouchable they present themselves. He is a sailor, and he is guided by only one north star.
PRIORITY TABLE: AACEE [ Skills / Attributes / Resources / Magic & Resonance / Metatype ]
A - SKILLS (46 points for individual Skills, 10 points for Skill Groups)]
A - ATTRIBUTES (24) [ Spread between BODY / AGILITY / REACTION / STRENGTH / WILLPOWER / LOGIC / INTUITION / CHARISMA, usually starting at 1/6, but different Metatypes have different starts and limits ]
C - RESOURCES (140,000¥) [ Spend this before starting the game to determine what your character owns; you cannot keep more than ~1,200¥ after your spending spree. This accounts for buying your lifestyle, clothes, armor, weapons, vehicles/drones, etc. ]
E - METATYPE ("choose one"; just kidding, Priority E Metatype locks you to being human.) >> Human (1) [ Add the number after your metatype to your EDGE attribute. EDGE is your 'Luck' stat.
E - MAGIC or RESONANCE (NONE, you're MUNDANE, old man!)
#confessthysiins#Shadowrunner Assignment#A Message From the Investors! | Ask#[ This was a fun one to theorycraft ]#[ god these are long ]
4 notes
·
View notes
Text
"Study Smarter: Expert-Recommended Tools and Materials for Students"
Whether you're a excessive faculty student, university undergraduate, or lifelong learner, having the proper have a look at substances can extensively enhance how efficaciously you analyze and retain know-how. Below is a curated list of encouraged resources labeled by means of topics, getting to know styles, and desires, overlaying each traditional and virtual codecs.

Study Materials For Students
1. 📖 General Study Materials
Books
A have to-study for all rookies, this book explores proof-based mastering techniques and helps you increase greater effective study behavior.
"How to Read a Book" by Mortimer J. Adler and Charles Van Doren
Teaches analytical reading strategies and how to approach distinct genres of texts seriously.
Stationery & Tools
Highlighters, sticky notes, flashcards, notebooks (ideally sectioned or dot-grid)
Apps like Notion, Obsidian, or Evernote for virtual be aware-taking
Use Pomodoro timers like Focus Keeper or TomatoTimer for time management
2. 🧠 Cognitive and Memory Aids
Flashcards
Anki – Spaced repetition software program first-rate for memorizing anything from scientific terms to vocabulary
Quizlet – User-friendly with heaps of pre-made sets for almost each challenge
Mind Mapping Tools
XMind or MindMeister – Great for visual rookies and organizing complex ideas
3. 📘 Subject-Specific Recommendations
🌍 Humanities and Social Sciences
History
"A People's History of america" by way of Howard Zinn – A fresh, alternative perspective
CrashCourse History on YouTube – Fun, speedy-paced, and informative
Oxford History Series – Detailed but on hand instructional sources
Literature
The Norton Anthology of English Literature – Comprehensive and properly-commented
SparkNotes and CliffsNotes – Great for summaries, subject matters, and quick evaluations
Poetry Foundation – Great for knowledge poems and their analyses
Philosophy
"Sophie's World" with the aid of Jostein Gaarder – Fictional introduction to philosophical standards
The Stanford Encyclopedia of Philosophy (SEP) – Free, instructional-stage articles
🔬 STEM (Science, Technology, Engineering, Mathematics)
Mathematics
Khan Academy – Free tutorials from basic mathematics to multivariable calculus
Paul’s Online Math Notes – College-degree notes and worked examples
Brilliant.Org – Interactive math problems and puzzles
Physics
"Fundamentals of Physics" via Halliday, Resnick & Walker – A staple for undergraduates
MinutePhysics and Physics Girl on YouTube – Bite-sized physics defined
HyperPhysics – Visual-based on-line physics concept map
Chemistry
ChemCollective – Virtual labs and trouble units
Organic Chemistry as a Second Language with the aid of David Klein – Excellent for understanding difficult standards
Periodic Videos (YouTube) – Fun deep dives into the periodic table
Biology
Campbell Biology – Comprehensive and general for maximum university-degree courses
Bozeman Science – Great video content for AP and university biology
BioInteractive (HHMI) – Interactive resources and animations
Computer Science
CS50 by way of Harvard (edX) – Free, newbie-pleasant intro to CS
freeCodeCamp – Free interactive studying in coding and net development
Cracking the Coding Interview by using Gayle Laakmann McDowell – For technical interview prep
Languages and Communication
English (and ESL)
Grammarly – Writing help and grammar checking
The Elements of Style via Strunk and White – Classic writing guide
BBC Learning English – Free resources for vocabulary, pronunciation, and grammar
Foreign Languages
Duolingo – Great for beginners
LingQ and Pimsleur – For immersive language studying
HelloTalk / Tandem – Connect with local audio system for actual conversations
four. 🎓 Test Prep Materials
ACT Prep Black Book by means of Mike Barrett
Khan Academy’s free SAT prep – In partnership with College Board
GRE/GMAT
Manhattan Prep Series – Strong for both GRE and GMAT
Magoosh – Affordable, digital-first gaining knowledge of platform
Official ETS GRE Guide – Direct from the check makers
Medical (MCAT, USMLE)
Kaplan Series / Princeton Review – Comprehensive applications
Anki Decks (like MilesDown for MCAT) – Top-rated for memorization
SketchyMedical – Visual mnemonics for microbiology and pharmacology
5. 🧘 Mental Health and Study Techniques
Wellness Apps
Headspace / Calm – Meditation and mindfulness apps to enhance attention
Forest – Encourages you to stay off your cellphone while you look at
Study Bunny – A cute gamified productivity app
Study Methods
Pomodoro Technique – 25 minutes paintings, 5-minute smash
Feynman Technique – Teach the idea in easy phrases to yourself
Active Recall + Spaced Repetition – Proven satisfactory for lengthy-time period retention
6. 🖥️ Digital Platforms and Online Learning
Coursera – Offers publications from top universities in really all fields
EdX – Similar to Coursera; first rate for incomes certificate
Udemy – Huge library of affordable ability-primarily based guides
YouTube Channels – CrashCourse, Veritasium, CGP Grey, Kurzgesagt, and extra
7. 📅 Organizing Your Studies
Planning Tools
Google Calendar – For scheduling classes, study classes, and reminders
Trello or Todoist – For handling responsibilities and assignments
#Study Materials For Students#class nursery to class 12 th students#college students study materials
2 notes
·
View notes
Text
Names & Numbers: How Data Finds its Destination on the Net
As explained before, the Internet is the global network of networks. And with billions of computers and devices connected to the Internet, how does data know where to go when it is sent?
When the foundations of the Internet were being laid in the early 1970's, Vint Cerf and Bob Kahn developed the first internetworking protocol. A protocol is a set of standards and rules that are agreed upon for all future technology to follow. The protocols that followed as the Internet grew, allowed for the massive global network we find today.
One of those protocols, the Internet Protocol (IP), determines how devices are located on networks as well as the structure of addresses for data sent, much similar to how postal services follow a set structure for home addresses (a protocol). IP addresses currently follow the IPv4 (version 4) or IPv6 (version 6) standards.
IPv4 is a set of 32 numbers (32 bits) separated into 4 parts with 8-bits (a byte) in each part and written in dot-decimal notation. Here's an example of an IPv4 address (111.24.221.18). The first two bytes represent the country or region of the address. The third byte represents the subnetwork and the final byte the device on that subnetwork. By using 32 bits, IPv4 was capable of over 4 billion internet addresses. However, this was not enough.
Enter IPv6, a 128-bit addressing protocol. IPv6 consist of a set of eight hexadecimal strings, each 16-bits long. This increases the total amount of possible internet addresses to over 340 undecillion (10^36). Plenty to go around.
You may be wondering, but if I type in a website domain into my browser bar, how to I get to that website without typing in the specific IP address? Now it is time to introduce DNS or the Domain Naming System.
You know how when you want to save someone's phone number into your own smartphone, you type in a name and save it to your contacts. Then when you want to call or text that person, you just click on their name and soon you are connected. DNS works the exact same way but is better in another way. DNS works like that contact list in your phone.
There are a bunch of DNS servers that hold the addresses and domain names of all the websites in existence. When you type in the name of a website in your browser, your request is sent to a DNS server who then returns that IP address to your system so that you may set up a connection with the website server. If the particular DNS server does not know the address, it asks the vast network of other DNS servers if they know the address. Once it gets the correct address, the DNS server you originally contacted, will save that address for your convenience. Nifty huh?
However, DNS does have a downside. Because it an open and public protocol, it is possible for criminal elements to disrupt or manipulate the routing of the DNS server. An unethical hacker could perform a DNS spoof, which could force traffic meant for a legitimate website to be rerouted to a malicious website or phishing site.
2 notes
·
View notes
Text
Tumblr keeps asking if I want to make a new blog...I am considering it just to toss all my story that's in my head for my fanfiction 😂 and then I can reorder it and make it nice on ff dot net and ao3 later.....plus I can use images and make fanart...welp...that has done it.
What do I call it?
MagMione...no
MaMione....no
MagnetoMione...eek
ErikMione...no. I just can't
HerMagneto....I kind of like it because it could mean something completely different than the main intention😂
Hermione X Magneto Rare Pair
Then perhaps I can finally have chapter 6 finished.
Would you want a blog of the inside of my mind? Hahaha now I feel like doing it for the original scifi book melting my brain with the technology I wish existed...and contemplating making real in my fanfic as well just to test it out and play with it because I still not sure about the plot for the bunny in my head that is slowly becoming my new WIP.

#writing#dedicated Tumblr ?#X-men x Harry Potter crossover fanfiction#sci-fi fiction#technology#VR but better#fanfic#fandom#Magneto#hermione granger
5 notes
·
View notes