#desktop ip phone market analysis
Explore tagged Tumblr posts
Text
Teaching you to power ad verification with proxy IPs
In the field of digital marketing, ad verification is an important step for ad delivery effectiveness and brand safety. Using proxy IP can effectively improve the accuracy and efficiency of ad verification.
Ad verification refers to the use of technical means and data analysis to confirm whether ads are displayed according to the intended target audience and delivery strategy. This includes checking that ads are displayed in the right geographic locations, device types, and websites, and that they are seen by real users and not fake traffic.

Role of proxy IP in ad verification
1) Geo-targeting Verification
1. Challenge: Advertisers want to ensure that ads are only shown in specific geographic areas to prevent wasting budget on ineffective areas.
2. Solution: By using proxy IP, different geographic locations can be simulated to check if the ads are displayed in the specified areas. This helps to validate the geographic accuracy of ad placement and ensure that the ads reach the target audience.
2) Device Type Verification
1.Challenge: Ads need to be displayed on specific device types (e.g., cell phones, tablets, desktop computers) that can achieve the best results.
2. Solution: Proxy IP service can provide IP addresses for different device types to help advertisers verify the display effect of advertisements on various devices, and advertisement creativity adapted to different terminals.
3) Preventing False Traffic
1. Challenge: Fake traffic not only wastes advertising budget, but also may damage brand reputation.
2.Solution: By using 711Proxy, abnormal traffic sources can be detected and filtered, and ads can be accurately displayed to real users. This helps to improve the effectiveness of advertisement placement and avoid losses caused by false traffic.
4) Cross-region ad delivery monitoring
1.Challenge: Cross-border advertisement placement needs to ensure the display effect and consistency in different regions.
2. Solution: Proxy IP can simulate IP addresses in different countries and regions to help advertisers monitor the display of ads globally. In this way, it can ensure that the ads are displayed consistently in various regions and improve the effectiveness of global advertisement placement.
As digital marketing technology continues to evolve, proxy IP will become an indispensable tool in the ad verification process. If you have any questions or need more advice, please feel free to leave a message in the comment section to discuss~

0 notes
Text
0 notes
Text
Desktop IP Phone Market Forecasts to 2027: Global Industry Growth, Share, Size, Trends
The global Desktop IP Phone Market
The growing technological developments and research advancements are contributing to the expansion of the market, according to the latest report published by Reports and Data. The report offers significant insight into key elements of the market, such as drivers, restraints, challenges, strategic expansions, market size and share, growth prospects, threats. The report also sheds light on the factors influencing the growth of the market, particularly the ongoing COVID-19 pandemic. The report discusses in detail the extensive impact of the COVID-19 pandemic on the supply chain, demands, trends, and overall dynamics of the Desktop IP Phone Market. It also offers a futuristic growth outlook of the Desktop IP Phone Market in a post-COVID-19 scenario.
To get a sample PDF copy of the report Visit @
https://www.reportsanddata.com/sample-enquiry-form/154
Key Players Profiled in the Report are:
· Cisco
· Avaya
· Mitel
· Polycom
· Alcatel-Lucent
· Yealink, Grandstream
· NEC
· D-Link
· Escene
The Desktop IP Phone Market Report Offers:
· Deep insights into the Desktop IP Phone Market landscape
· Key details about the regional segmentation of the Desktop IP Phone Market
· Analysis of the crucial market trends with regards to both current and emerging trends
· Comprehensive impact analysis of COVID-19 pandemic on the Consumer Pressure Washers industry
· Extensive overview of the key manufacturers and prominent players of the industry
· Comprehensive study of the market segmentation and recent developments
Market Drivers:
The constant efforts of the prominent players to develop innovative products and technologies are driving the growth of the industry. Additionally, the market is witnessing numerous strategic collaborations and initiatives that are expanding the scope of the market. The report discusses in detail the factors and elements of the Desktop IP Phone Market that are positively influencing the growth of the market.
Request a discount on the report @ https://www.reportsanddata.com/discount-enquiry-form/154
Market segment based on the Type:
Video Desktop IP Phones
Common Desktop IP Phones
Market segment based on Application Type :
Office
Hotel
Residential
Others
Regional Analysis:
The report offers clear insights into the regional bifurcation of the market with regards to the regions where the market has already established its prominence. Furthermore, it analyzes the key regions for production and consumption ratio, import/export analysis, supply and demand dynamics, regional trends and demands, and the presence of prominent players in each region. The regional analysis segments also offer a country-wise analysis to offer a panoramic view of the market.
The regional analysis covers:
· North America (U.S., Canada)
· Europe (U.K., Italy, Germany, France, Rest of EU)
· AsiaPacific (India, Japan, China, South Korea, Australia, Rest of APAC)
· Latin America (Chile, Brazil, Argentina, Rest of Latin America)
· Middle East & Africa (Saudi Arabia, U.A.E., South Africa, Rest of MEA)
To know more about the report, visit @ https://www.reportsanddata.com/report-detail/desktop-ip-phone-market
Competitive Landscape:
The report offers a comprehensive overview of the competitive landscape of the market to provide an advantage to the reader. This segment focuses on the initiatives and innovations adopted by the key players to gain a strong foothold in the market. The report also sheds light on mergers and acquisitions, joint ventures, collaborations, partnerships, and agreements, among others, to offer a better understanding of the market. The report also offers insights into revenue, gross profit margin, financial standing, market position, product portfolio, and other vital aspects of each player. The report also includes a thorough SWOT analysis and Porter’s Five Forces analysis.
Thank you for reading our report. For more details about the report and customization feature, please connect with us. Our team will ensure the report is tailored to meet your requirements.
#desktop ip phone market#desktop ip phone market analysis#desktop ip phone market growth#Desktop IP Phone Market Demand#Desktop IP Phone Market Overview#Desktop IP Phone Market Applications
0 notes
Text
How to make a gaming tournament website
Of Wolf's Gaming Weblog
It is time to recognize the finest gaming blogs of the year. EDIT:I utilized to watch the Feedback video more than at G4 just about every week, but it really is gone down hill the last few occasions I watched it and now that Adam Sessler is not on it and they have that girl from IGN that everyone hates in each episode I just cannot be bothered to watch it any far more. Nonetheless worth going back and watching some of the older ones even though. Klepic used to be on that show and back then in the early days was when it was the ideal. Back when they essentially talked about gaming news with some semblance of intellect alternatively of just gushing about whatever game they are told is cool this week.
The near future promises a bunch of new possibilities for Pc and mobile games. It suggests we will take pleasure in high good quality gaming content material no matter what device is utilized. Hey guys! I am seeking for indie gaming blogs out there that are genuinely great. There is an endless provide of gaming sources on line if you know exactly where to look or who to get in touch with.
I got into action games late but when I did it absolutely changed how I viewed gaming forever. The game which brought me round was Viewtiful Joe. Here was a game with a deep and open-ended combat method which seemed to be built as a implies for the player to express creativity. This program is then pitted against opponents and obstacles which have been designed from the ground up to interact meaningfully with the core method. The course was fixed, but the strategy for dealing with that course was absolutely down to the ingenuity, talent and inspiration of the player. You play like you have a enormous audience watching and the game continually entices you to improve the concentrate is not simply on obtaining the player from A to B, the focus is on receiving the player to play Viewtifully”.
Right now is the day! I will be progressively releasing the names of the best ten gaming blogs of 2014. Seeking over this list, I am positively blown away. So quite a few amazing posts this year! If you had been disappointed by the Ennies… if you assume that the actual deep thinkers in gaming commentary never get the consideration they deserve… properly, people, we are going to repair that.
Green Man Gaming is a international pure play e-commerce and technology enterprise in the video games business fuelled by an unhealthy obsession with bringing the magic of games to everyone. The company's geeky knowledge, data and IP sit at the core of the small business and is what drives it to turn out to be a technology leader in the video games ecosystem.
27 Ways To Improve GAMING
CrystalSkull is packed with adequate attributes to help you create almost any variety of gaming web page with WordPress. The integrated critique method means your content material will rival the articles discovered on the leading gaming overview websites. With CrystalSkull, you'll be capable to build your personal custom criteria for your evaluations, then add a score for each and every item, just before awarding a final overall rating for the overview.
The theme functions Unity 3d ready design, HTML5 games' full-screen compatibility for mobile devices as effectively as MyArcadePlugin compatibility to allow you to build an amazing arcade expertise for your viewers. Gameleon characteristics a myriad of add-ons and selections to assure that you can share an exquisite gaming experience with your visitors.
Paul: Green Man Gaming, like many data driven technology marketplaces, was born in a spreadsheet and continues to this day to be heavily information dependant. The enterprise utilizes historical analysis of correlated data to create forecasts of client behaviour, as nicely as actual-time data streams to augment those forecasts in real time.
Augmented reality games are becoming a front-runners of gaming sector. Today, this is not just the fantastical idea. AR games let you to fight aliens, capture fantastical creatures, defend kingdoms in the real globe. And all of this is feasible with no super highly-priced headsets - just an AR-enabled smartphone or console is expected. Wolf's Gaming Weblog is on a run to give you the most correct and truthful reviews on the top rated games in Xbox 1, Individual Laptop games and Board games. With this site in your bookmarks tab, the climate is often excellent to get your hands on some on the net games.
We're going to the International Festival for Business enterprise this month and will be hosting a one of a kind occasion Inspiring Entrepreneurs '˜Going Global' exactly where top rated business enterprise people will tell us the secrets of their good results. A single of these entrepreneurs is Paul Sulyok, CEO and Founder of Green Man Gaming Green Man Gaming is a pioneering, worldwide eCommerce technology organization that has gone from strength to strength considering the fact that its launch in 2010. We asked him how he did it.
One more of our best gaming influencers for 2018 is The Rad Brad We had to incorporate this channel due to the fact The Rad Brad is a specifically well recognized YouTube gamer. He produces an unbelievable amount of hugely-top quality, enjoyable content material. It's no wonder he's identified for producing the ideal video game walkthroughs on social media. The Rad Brad has helped to make a quantity of influencer marketing and advertising campaigns a true accomplishment.
As for the other topic Esports seems to be expanding and expanding, and with it Youtube. Video critiques from individuals like AngryJoe let folks connect a lot more with the reviewer, and via that subtantial followings are built. Written media, on the other hand, is struggling, which is poor news for me since I'm not quite enough for Youtube! Sadly, although, we're nevertheless seeing plenty of hostility inside the gaming community, which the media loves to focus on.
Alia Lia” Shelesh, improved known as Sssniperwolf is the 1st female gaming influencer on our list. She began her YouTube profession by playing initially-individual shooter games like Contact of Duty, Halo, and Far Cry. Her account now consists of vlogs and different video games that she plays and has more than 7 million subscriptions.
Substantially, for many of these people, their mobile phone will be their initially computer system - a so-referred to cross768.online video games blog as ‘mobile-initial generation' - so most of the items we do on desktop or laptops, they will be undertaking on mobiles, again like all their gaming. Right here is a few of the most properly-identified gaming web-sites where you can get the latest news from.
The future of gaming is a planet exactly where you are empowered to play the games you want, with the people today you want, whenever you want, wherever you are, and on any device of your deciding on. Our vision for the evolution of gaming is similar to music and motion pictures — entertainment should really be readily available on demand and accessible from any screen. Nowadays, I am excited to share with you 1 of our crucial projects that will take us on an accelerated journey to that future world: Project xCloud.
1 note
·
View note
Text
Privacy Policy
Juice Live – Privacy Policy
Welcome to Juice Live! We respect and value your privacy.
The use of Juice Live through our mobile applications may involve collection and use of your information. This Privacy Policy explains and informs you how your information is collected, used and disclosed by Juice Live with respect to your access and use of our services through our mobile applications. It is important for you to understand this Privacy Policy and how you may protect your information, so please read this Privacy Policy carefully.
I. Application Scope of the Privacy Policy
By using Juice Live, you agree that we may collect, use and share your information in accordance with this Privacy Policy, as revised from time to time. In addition, your use of Juice Live signifies that you agree with the terms of this Privacy Policy. If you do not agree with the terms of this Privacy Policy, do not use Juice Live.
This Privacy Policy is incorporated into and forms part of the Juice Live Terms of Service that you have agreed to in order to use Juice Live. Any terms used in this Privacy Policy will have the same meaning as the equivalent defined terms in the Juice Live Terms of Service unless otherwise defined in this Privacy Policy or the context requires otherwise. Unless otherwise specified in this Privacy Policy, these terms in the Juice Live Terms of Service shall also be applicable in this Privacy Policy.
Any information that is collected is subject to the Privacy Policy in effect at the time such information is collected. We may, however, modify and revise our Privacy Policy from time to time. If we make any change to this policy, which we deem to be material changes, we will (where reasonably practicable) notify you of such changes by posting them on our website, through our services or by sending you an email or other notification, and we will indicate when such changes will become effective. By continuing to access or use our services after the changes become effective, with or without notification, you are agreeing to be bound by the revised policy.
Juice Live may link you to social media or other features or services (including websites, plug-ins and widgets) provided by a third party. Please note that this Privacy Policy doesn’t apply to the information collected by any third-party websites, services or applications that can be accessed through our services, and does not apply to the information collected by other companies and organisations who advertise their services on Juice Live. We bear no liability for any third party use of any information provided by you to them.
II. Information You Provide and We Collect
2.1 To provide the services of Juice Live, we collect, store and use the following Information relating to you:
· information provide to us when you open a Juice Live account, including your account name, gender, date of birth, age, city or area social media account information (profile photo, gender, etc.), any tags you posted about yourself;
· any information included in your Juice Live profile which are visible to other users of Juice Live, or information you make available to us via your use of Juice Live, which may include your photographs, your education, city or area and other information;
· information about your and others’ usage of and interaction with the service and our application, including usage by geographies, device and connection information, IP address, device capability, bandwidth, statistics on page views and network type;
· information we collect as you use Juice Live, which may include:
✓ technical information, such as your mobile carrier-related information, configuration information made available by other programs you use to access Juice Live, your IP address, your location/country/region/time zone, your device's version and identification number, user settings, and the operating system; and
✓ information about the likes and dislikes you have made using Juice Live.
2. Special Note about Sensitive Personal Information
Please note that content and information that you input to Juice Live, such as photographs or the tags you posted about your sexual orientation, may constitute sensitive personal information in certain jurisdictions. Sensitive information is subject to stricter regulation than other types of personal information.
Before revealing any sensitive personal information in Juice Live, please consider whether it is appropriate to do so.
By using Juice Live, you agree that all processing activities of sensitive personal information are for the purposes and in the manner as described in this Privacy Policy.
Please note that we do not use your sensitive personal information for the purpose of making direct marketing unless agreed by you.
3. Special Note about Children’s Information
The services of Juice Live are not for use by anyone under the age of【18】. Thus we do not knowingly collect personal information from any data subject under such age. If we learn that we have collected personal information of a data subject under【18】, we will take steps to delete such information from our files as soon as possible.
III. How We Use the Information We Collect
3.1 Purposes
We may use your Information for any of the following purposes:
· to provide services to you (including both the services currently provided by us via Juice Live and these services to be rendered by us via Juice Live in future);
· to personalize and improve our services and your experiences when you use our services;
· to respond to inquiries, for the purposes of customer service, security, archival and backup purposes in connection with providing services of Juice Live;
· to monitor and analyse usage and trends of our services;
· personalize the services by, among other things, suggesting friends or profile information, or customizing the content we show you, including ads;
· enhance the safety and security of our products and services;
· verify your identity and prevent fraud or other unauthorized or illegal activity;
· use information we’ve collected from cookies and other technology to enhance the services and your experience with them; and
· enforce our Terms of Service and other usage polices.
Juice Live allows you to share text messages, photos, screenshots, videos and other communications in the Juice Live application with other users, and if you choose to do so your text messages, photos, screenshots, videos and other communications will be stored on our servers. In addition, if you choose to share these items with other Juice Live users, we may not be able to remove them from our servers or make them unavailable to anyone you have shared them with. Sending and sharing text messages, photos, screenshots, videos or other communications in the Juice Live application is your decision. By choosing to share that information, you should understand that you may no longer be able to control how that information is used and that it may become publicly available (depending in part on your actions or the actions of others with whom you have shared the information). Juice Live is not responsible for any use or misuse of information you share.
3.2 Transfer and Storage
We operate and may continue to operate servers in a number of jurisdictions around the world, so the server on which your personal information is used and stored may not be in your jurisdiction.
You consent to the transfer of your personal information (both inside and outside of your jurisdiction) for the purposes described in this Privacy Policy.
3.3 Sharing
By using Juice Live, you agree to the third party use, sharing and transfer of your personal information (both inside and outside of your jurisdiction) as prescribed in this Privacy Policy.
We will share information about you when you upload or post these information on Juice Live, or if we notify you that the information you provide will be shared in a particular manner and you provide such information. Please do not post or add personal data to your profile that you would not want to be publicly available.
We may share information about you in anonymous and/or aggregated form with third parties for usage analytics (to help us better understand who is using our services and how), and for industry analysis, demographic profiling, research, and other similar purposes.
Your information may be accessed and used by our service providers who are working with us in connection with the operation of our services. These service providers may have access to your information but only to the extent necessary to perform services on our behalf and are obligated not to disclose that information or use it for any other purposes. These providers will collect the information sent by your mobile phone, tablet or desktop computer, and their use of that information is governed by their applicable privacy policy.
We may share information about you if we are (or if we believe we are) required by law or legal process (such as a subpoena, warrant or court order), if we have to respond to a lawful request from legal authorities to disclose such information, or if we need to enforce or apply this Privacy Policy, our Terms of Service or our other policies.
If we are acquired by a third party or may re-organise our group structure, your information may be transferred within our group and/or to a third party who will continue to operate Juice Live or similar services under either this Privacy Policy or a different privacy policy which will be notified to you. The party to which your personal information is transferred may be located, and use your Information, outside of your jurisdiction.
Other than as permitted under this Privacy Policy or as otherwise consented to by you or as required by law or legal process, we will not transfer your personal information to any other third parties for their processing for any purposes.
3.4 Security Measures We Take To Protect Your Information
We employ administrative, physical and electronic measures designed to protect your information from unauthorized access, however, despite these efforts, no security measures are perfect or impenetrable and no method of data transmission can be guaranteed against any interception or other type of misuse. In the event that your personal information is compromised as a result of a breach of security, we will promptly notify you if your personal information has been compromised, as required by applicable law.
Where we do share your personal information with any third parties, we will use reasonable efforts to ensure that such third parties only use your personal information: (i) in compliance with this Privacy Policy; and (ii) subject to any other instructions we give them, including any appropriate confidentiality and security measures that we implement.
IV. How to Access Your Information
You can access and modify the information you provided to us through your account.
If you believe your information posted on Juice Live is not authentic or accurate and can provide us with reasonable proof regarding this, you can require us via the contact information provided in this Privacy Policy to correct these unauthentic or inaccurate information and we will use reasonable efforts to honour your request; however, we may retain an archived copy of your information as required by law and/or for record keeping purposes.
Once your account is closed or deleted, you will no longer have access to your message history, preferences or any other information associated with your use of our services. Even after you remove information from your account or profile, copies of that information may remain viewable elsewhere, to the extent it has been shared with others, it was otherwise distributed pursuant to your privacy settings, or it was copied or stored by other users. Additionally, we will retain your personal data even after you have closed your account if reasonably necessary to comply with our legal obligations (including law enforcement requests), meet regulatory requirements, resolve disputes, maintain security, prevent fraud and abuse, or enforce the Terms of Service. We will retain de-personalized information after your account has been closed.
In some cases, we may not be able to update, amend or remove your personal information, in which case we will let you know why we are unable to do so, for example, certain requests may require disproportionate technical effort or extremely impractical, or are prohibited by law.
Since Juice Live will be used in multiple jurisdictions and we may not be possible to identify all the inconsistency between certain terms of this Privacy Policy and the applicable law in your jurisdiction, thus you agree to notify us once such inconsistency is identified by you. Under this circumstance we will take necessary methods to eliminate such inconsistency, including deleting these personal information improperly collected or used by us.
V. Contacting Us
If you have any questions about our Privacy Policy or any privacy-related matters, please contact us via email at【[email protected]】.
1 note
·
View note
Text
Global Desktop IP Phone Market 2020–2025 | Analysis by Forecast, Growth Opportunities, Major Key Players, Revenues During Covid-19 Outbreak
Global Desktop IP Phone Market 2020–2025 | Analysis by Forecast, Growth Opportunities, Major Key Players, Revenues During Covid-19 Outbreak
The recent research report titled “2015-2025 Global Desktop IP Phone Market Research by Type, End-Use and Region (COVID-19 Version)” has been added in the kandjmarketresearch.com database. The Global Desktop IP Phone Market Perspective, Comprehensive Analysis along with Major Segments and Forecast, 2020-2025.
Desktop IP Phone Market Overview
The global Desktop IP Phone market has been…
View On WordPress
#Covid-19 Impact on Desktop IP Phone#Desktop IP Phone#Desktop IP Phone Demand#Desktop IP Phone Industry#Desktop IP Phone Market#Desktop IP Phone Market Analysis#Desktop IP Phone Market CAGR#Desktop IP Phone Market Forecast#Desktop IP Phone Market Growth#Desktop IP Phone Market Key Countries#Desktop IP Phone Market key player#Desktop IP Phone Market Revenue#Desktop IP Phone Market Sales#Desktop IP Phone Market Share#Desktop IP Phone Market Size#Desktop IP Phone Market Trends#Desktop IP Phone Research Report
0 notes
Text
Teaching you to power ad verification with proxy IPs
In the field of digital marketing, ad verification is an important step for ad delivery effectiveness and brand safety. Using proxy IP can effectively improve the accuracy and efficiency of ad verification.
Ad verification refers to the use of technical means and data analysis to confirm whether ads are displayed according to the intended target audience and delivery strategy. This includes checking that ads are displayed in the right geographic locations, device types, and websites, and that they are seen by real users and not fake traffic.

Role of proxy IP in ad verification
1) Geo-targeting Verification
1. Challenge: Advertisers want to ensure that ads are only shown in specific geographic areas to prevent wasting budget on ineffective areas.
2. Solution: By using proxy IP, different geographic locations can be simulated to check if the ads are displayed in the specified areas. This helps to validate the geographic accuracy of ad placement and ensure that the ads reach the target audience.
2) Device Type Verification
1.Challenge: Ads need to be displayed on specific device types (e.g., cell phones, tablets, desktop computers) that can achieve the best results.
2. Solution: Proxy IP service can provide IP addresses for different device types to help advertisers verify the display effect of advertisements on various devices, and advertisement creativity adapted to different terminals.
3) Preventing False Traffic
1. Challenge: Fake traffic not only wastes advertising budget, but also may damage brand reputation.
2.Solution: By using 711Proxy, abnormal traffic sources can be detected and filtered, and ads can be accurately displayed to real users. This helps to improve the effectiveness of advertisement placement and avoid losses caused by false traffic.
4) Cross-region ad delivery monitoring
1.Challenge: Cross-border advertisement placement needs to ensure the display effect and consistency in different regions.
2. Solution: Proxy IP can simulate IP addresses in different countries and regions to help advertisers monitor the display of ads globally. In this way, it can ensure that the ads are displayed consistently in various regions and improve the effectiveness of global advertisement placement.
As digital marketing technology continues to evolve, proxy IP will become an indispensable tool in the ad verification process. If you have any questions or need more advice, please feel free to leave a message in the comment section to discuss~
0 notes
Text
Global Desktop IP Phone Market 2018 Forecast by 2023 Top Companies, Trends & Growth Factors and Detail Analysis for Business Development
Global Desktop IP Phone Market 2018 Forecast by 2023 Top Companies, Trends & Growth Factors and Detail Analysis for Business Development
Global Desktop IP Phone Market Forecast to 2023, given by Market.biz may be a complete study created by implementing a beautiful analysis procedure to assemble key knowledge of this worldwide Desktop IP Phone market. The report covers 2018 to 2023 market outlines together with Desktop IP Phone market review, division of the business, business scope, current Desktop IP Phone market, and future…
View On WordPress
#Desktop IP Phone Market Analysis#Desktop IP Phone Market Share#Desktop IP Phone Market Size#Desktop IP Phone Market Trends#Global Desktop IP Phone Market 2018 Forecast
0 notes
Text
What is PBX, Its types, and why do businesses need one?

Business communication is an integral part of businesses irrespective of their scale or size. However, in the past decade, the tools to achieve business communication have evolved from physical telephone lines to digital calling solutions called Voice Over Internet Protocol.
What is a PBX server?
In addition to being a digital telephone exchange, a PBX system is also a cost-effective solution that grants exceptional portability and additional advanced VoIP features such as Time Condition, IVR, Ring Group, Call Forwarding, Auto-attending, IVR, Video Conferencing, etc. In fact, these advanced features make PBX the most sought-after business phone solution that businesses favor.
How does PBX work?
The data packets are transformed before being sent to the VoIP service provider, which manages call initiation and termination. Users can connect desktops, specialized VoIP phone hardware, or softphones to the network using SIP trunking. Both internal and external corporate communication may be conducted with the IP PBX business phone system. Whether your PBX phone system needs to transmit data through the Public Switched Telephone Network or not depends on the nature of the communication.
Capabilities of a PBX system
Here is a breakdown of the different features capable of an IP PBX phone system.
Auto-attendant
The capacity to redirect calls to locations outside the firm, such as mobile phones, VoIP virtual phones, and other IVR systems, is a feature of advanced auto-attendants.
3rd Party Business Integrations
Thankfully, a reliable PBX from a trusted VoIP development company will support business tool integration or custom integration capabilities.
Voicemail
This allows businesses to catch business opportunities that may have been lost. Taking voicemails to the next level, an IP PBX can send an email notification whenever a voicemail is left on the server, along with the recording as an audio file.
Call Encryption
You will need sophisticated virtual PBX features like call encryption because of this. Both of these protocols will guarantee that every call you make is completely secure and that hackers cannot intercept your calls or compromise the network. In addition, it is advisable to have Firewall for PBX servers as an additional security layer.
Call Management Features
A quality PBX server offers additional call management services such as call barging, whispering, coaching, and transfer, to mention a few.
Flexibility
Every business needs to adapt to changing demands. Today, a business that can manage the blows of the market and adjust accordingly is the one that paves the way to the top. A PBX server is flexible enough to handle every business communication scenario. A PBX phone system's comprehensive and clever feature set may completely change a company's communication infrastructure.
Cost-efficient
Because of this, every company, regardless of size, employs a plan to make its procedures more affordable. Additionally, switching between plans as your company's needs change is simple.
Centralized communication
You may measure staff efficiency, see missed and continuing calls, and ultimately enhance your company operations with real-time call monitoring and analysis. Above all, you can give fabulous communication because you always have a single point of contact, your virtual number, regardless of what goes on in your business behind the scenes.
Wrapping Up
Switching to the PBX server bridges the communication gaps within your organization and keeps your business ahead of the competition while keeping the cost down. If you want a custom PBX server or VoIP system to streamline communication and enhance collaboration, contact Vindaloo Softtech today.
#hosted ip pbx#ip pbx phone system#VoIP PBX systems#ip pbx system#private branch exchange phone system
0 notes
Text
5 Questions You Should Ask Your QuickBooks Enterprise Hosting Provider

QuickBooks' sophisticated features make it a favourite among accountants and CPA company owners. Indeed, among small and medium enterprises worldwide, it is among the most widely used accounting programmes.
However, when integrated with cloud computing capabilities, QuickBooks becomes much more beneficial for accountants. They can choose remote access, teamwork, real-time QuickBooks file updates, etc.
However, picking a reputable cloud hosting company for QuickBooks hosting is crucial if you are an accountant and want to receive these extra benefits.
Many cloud solution providers are readily available online. However, it is recommended that you ask each of them some critical questions about their services before employing one of them.
Here are five questions you should ask a QuickBooks hosting company:
1. How many customers do you provide QuickBooks hosting services for?
This query should be directed first and foremost at a cloud hosting company.
You want to discover more about their reputation in the marketplace.
You can feel secure about the provider's reputation if it has already provided QuickBooks hosting to hundreds of happy customers. People must endorse the provider to their acquaintances for all the good factors about the services offered.
This question's response can also give you further information about the service provider's background, which will be helpful in the future.
2. How Do I Access Customer Support Services?
Some accountants only know the technical specifics of how cloud technology operates. As a result of learning about the advantages of hosting the QuickBooks desktop version on the cloud, they hire a cloud solution provider.
But what if there is a problem with the cloud-hosted QuickBooks that prevents you from using it?
In such circumstances, you require a reputable cloud hosting provider with a customer support team always on hand to assist you. Therefore, choose someone accessible via the phone, chat, or email which provides support services around the clock.
3. What Security Steps Do You Take to Protect data?
The fact that the cloud guarantees data safety is one of the key reasons you are eager to make the switch.
You should know how your data is protected when stored on the cloud.
To safeguard you from online dangers like ransomware and DDoS, reputable QuickBooks hosting providers typically have several security precautions. These consist of data encryption, firewalls, multi-factor authentication, intrusion detection and prevention systems (IDS/IPS), and similar tools.
Not only that, but they also continue to be ready for disruptive occurrences like natural catastrophes to guarantee that you can function uninterruptedly in the cloud. For optimum uptime of up to 99.999% for all their clients, they also provide a pre-built disaster recovery and business continuity system.
Therefore, before deciding to host your QuickBooks, find out if they use these cutting-edge security methods from the cloud solution provider.
4. Are You A Host Authorized By Intuit?
Regardless of the QuickBooks version, it would be best if you considered this important criterion.
Being an Intuit Authorized Host means that Intuit supports you in the market as a capable QuickBooks service provider.
Before selecting a commercial host or commercial standard as part of its hosting programme, Intuit performs the necessary analysis.
You may rest easy knowing that the hosting provider can handle your business needs.
5. What Is Your Uptime?
Ask about their uptime guarantee when choosing a cloud service provider to host your QuickBooks application and data.
The term "uptime" refers to the number of hours that the provider of QuickBooks guarantees will be available. The trustworthy cloud service providers on the market guarantee an uptime of 99.999 per cent, which translates to an annual downtime of no more than 6 minutes.
Additionally, ensure that the SLA includes the uptime figure so that the cloud hosting provider is bound by law to provide the uptime.
One may feel overwhelmed when faced with a large selection of QuickBooks hosting companies.
But you can get a good sense of which one to pick by asking them questions about their line of work.
Verito is one of the best QuickBooks cloud hosting services. A cloud hosting company doesn't only store your QuickBooks data there, after all. It also collaborates with you so that you can gain more experience and work for additional clients.
0 notes
Text
IP Telephony Market is Projected to reach US$ 63.47 Bn by 2027
Latest market study on "IP Telephony Market to 2027 by Component (Hardware, Software, and Services), Hardware (IP Desktop Phones, DECT Phones, and IP Conference Phones); Service (Installation & Maintenance, and Professional Services), Installation Type (Wired and Wireless): Enterprise Size (SME and Large Enterprises) End Users (Residential, Corporate and Governmental Organization) - Global Analysis and Forecast", the IP Telephony market is estimated to account for US$ 25.26 Bn in 2017 and is anticipated to grow at a CAGR of 10.1% to account for US$ 63.47 Bn by 2027. The report include key understanding on the driving factors of this growth and also highlights the prominent players in the market and their developments.
In less than two decades the commercial internet has evolved into an indispensable and fundamental need of not only an individual but also of the organizations catering to global markets. Today population of nearly 2.5 Billion is connected to the internet, and by 2020 the count is anticipated to expand two folds. Having such widespread access to commerce, information, and communications the internet services have had a significant impression on myriad industries. Furthermore, the continued expansion of the digital economy is expected to raise the expectation of consumers resulting in uptake of advanced technologies supported by the internet.
The market for IP Telephony is segmented on the basis of the component, which comprises of hardware, software, and services. The hardware segment further comprises of IP Desktop Phones, DECT Phones, IP Conference Phones, and other IP Phones. The softphone segment focuses on software based IP phones, whereas the services segment is grounded on installation & maintenance, and Professional services.
The market by the installation is segmented into wired & wireless, whereas by enterprise size it is segment into SME (having less than 500 employees) and large enterprises (More than 500 employees). In our research report, we have considered, end users segment which includes Residential, Corporate, and Government sectors.
Request Sample Copy of this Report @ https://bit.ly/3r2maEF
Looking at the competitively transforming internet telephony landscape the development of more reliable and cost- effective communications solutions is expected to provide the market to barge into the corporate sector and attain significant penetration in the coming years. Next step in respect to evolution of networking for the businesses is one network i.e., converged network which is responsible to handle transmissions of video, data, and voice along with high quality.
Global IP Telephony Market - By Component
Hardware
Softphone
Service
Global IP Telephony Market - By Hardware
DECT Phones
IP Desktop Phones
IP Conference Phones
Others
Global IP Telephony Market - By Installation Type
Wired
Wireless
There has been constant development in applicant tracking system market. Recently, Panasonic Corporation launched next- generation IP- based communications server for growing enterprises. Also, Yealink Inc. released its new DECT IP phone product W53P, introduced a new huddle room video conferencing solution, the VC200, and released V32, the latest software update to Yealink second- generation video conferencing system and endpoints.
The top companies operating in the field of IP Telephony include Microsoft Corporation, Cisco Systems, Inc., Avaya Inc., NEC Corporation, Mitel Networks Corporation, Yealink Inc., Panasonic Corporation, Toshiba Corporation, Polycom, Inc., and Ascom Holding AG among others operating in the market and are coming up with new technologies and offerings which is helping the market for applicant tracking system to expand over the years in terms of revenue and subscription.
Source: https://bit.ly/3Sr97Z9
0 notes
Link
0 notes
Text
What to expect from a Professional IT Service Provider
My goal here is to acquaint you with the expectations you should have in choosing a professional IT service business to attend to ALL of your Information Technology requirements. This is not to say that you will find this all in one place, but it is desirable to do so. See more at kernitservices.com
You should be able to:
• Reduce stress in your working environment with their Business IT solutions
• Minimize your IT expense, while providing efficiency and security solutions
• Have service-oriented, continually trained and experienced IT professionals on demand
• Have 24/7 monitoring of all your systems
• Provide services for planning and strategy in a long-term working environment
• Provide IT budgets that are predictable with their low-cost monthly maintenance plans
• Have a trusted professional IT expert to turn to as a single source for all your technology needs
• Stop stressing about IT, and concentrate on managing your business very effectively
• Your satisfaction guaranteed
Computer Services
Many small businesses find it very challenging to deploy, maintain, and protect their technology environment. They are looking to keep IT costs manageable, avoid unexpected downtime, communicate in a more effective manner, or to plan for disaster recovery.
Services they should provide:
• Troubleshooting and problem solving on all networks and PCs
• Hardware installation and support
• Virus and spyware removal and protection
• Security solutions
• VPN (Virtual Private Networks)
• Remote access
• Server installations and upgrades
• Spam filtering and e-mail solutions
• Reliable Internet connection(s)
• Web content filtering
• Onsite and offsite system backups
• Complete network management and support
• Printer Service and Repair
• Help desk
Areas Covered
Managed IT Services
With a traditional break/fix service, the IT service depends on your problems to keep him in business. How much can you really depend on him to proactively maintain your network and computers? Managed IT services should keep your IT from breaking, eliminate costly computer repair bills and say goodbye to technology troubles for good.
These IT Services should include:
• 24/7 monitoring - get peace of mind knowing your systems are safe
• Managed IT Services - pinpoint and fix problems before they create downtime
• Remote & overnight services - so you experience fewer disruptions to your business
• All-inclusive IT - for predictable budgeting with flat-rate IT services that include hardware and software
• Scheduled proactive maintenance to assure you that all your IT is running in tip-top condition.
Managed Services should bring reliability to both your business and your budget, giving you better technology and more time to focus on your business.
Network Security
The threats to Email, Web browsing and Instant Messaging (IM) are getting more and more complicated and continue to be on the rise. All businesses, small and large, have to contend with regulatory and compliance issues.
• They should specialize in the expert planning, implementation, auditing, monitoring, and management of complete information security solutions. Information Security is nothing something you can "setup and forget it" - neither is it a series of simple solutions that are simply gathered together.
• A well-designed and comprehensive information security solution is an absolute necessity.
• Their Security Experts should have a wide range of Information Security and Compliance solutions for small and medium businesses, including:
• Secured Laptop - A holistic solution to protect your computers
• Protecting your network and data from virus, hacker, spam, phishing and other attacks requires a multi-layered approach.
• They should offer a suite of Information Security products and services to help keep your information secure and protect your Internet communications such as email, instant messaging and Web browsing.
Email Protection stops spam, viruses and phishing scams from reaching your network and getting into your email inbox. Spam and Hacking Attacks on your network are stopped before they reach your information, saving you valuable time and network bandwidth.
Email Archiving - Store, archive and search all email communications
Email Archive allows your organization to securely archive and store all email communications. Authorized users can search and retrieve any email for compliance or regulatory requirements across the entire organization.
Web Filtering - Block malicious or inappropriate Web content
Web Protection stops malicious Web content from being downloaded and enhances productivity by blocking programs or viruses. Web protection also helps reduce legal liabilities by blocking unwanted and inappropriate sites or content. Timely reports allow you to monitor Web traffic and adjust your policies based on data viewed.
Managed Firewall - Block malicious traffic
A managed Firewall Appliance Click for info or to buy.
A managed firewall appliance is a very essential part of any organization's IT security network. It is necessary to configure, maintain & monitor your firewall, and provide you with regular reports. Or review them for you at your discretion.
Intrusion Protection -
Apply any virtual patches to your network or servers
Intrusion Protection System (IPS) often works in conjunction with a firewall and further protects your network. Some regulations require the installation, maintenance and monitoring of an Intrusion Protection System (IPS).
They should monitor and maintain these highly sophisticated systems for you and ensure your regulatory compliance.
Wireless Information Security
What was secure last month might be a vulnerability today. If your wireless access point or infrastructure hardware is older than 2016, you are probably not protected adequately. A certified wireless experts (CWNA) should help you find and implement the best solution.
Vulnerability Analysis - Pinpoint the weak spots in your network
Information Security threats are constantly proliferating, so to keep your information security posture in line with the latest trends, They should perform regular vulnerability analyses on an ongoing basis. If they find problems, they will recommend improvements to your information security posture.
Business Continuity Planning- Don't let even a minor disaster put you out of business
Every small business owner knows the importance of their business data. What many don't realize is that while the chances of a major disaster are quite remote, the majority of data loss is the result of small localized problems.
They should provide:
• Business continuity and disaster recovery planning - customized for your business needs.
• Data backup and recovery - to insure your critical data files are accessible and safe from hackers
• Fast recovery for files and email - get back to business quickly
• Virtualization of failed servers - reduces downtime from days to hours
• Remote offsite storage - ensures data security and compliance
• Built-in archiving - more cost-effective and reliable than tape
• 24/7 monitoring and management - ensures data integrity
Cloud Computing
Collaboration is simplified with Cloud Services
Cloud Computing
There are four different types of cloud services. Public, Community, Hybrid, and Private, according to the National Institute for Standards and Technology.
Cloud Services give you the power to collaborate using the Internet and intranet in your office and make doing business more efficient. Cloud computing solutions allow you to share, edit, and publish documents in a single system, improve contacts and e-mail, increase marketing strategies, and better your everyday business processes.
Because these services are hosted, you'll never have to worry about the management, maintenance or equipment.
Cloud Services Should be:
• Adaptable - grow your capabilities and applications inline with your business
• Tailor-made - to suit your company perfectly
• Mobile - empower collaboration from any Internet-enabled device
• Cost-effective - efficient technology improves your bottom line
Cloud Services can include powerful tools for collaboration and increased productivity, including:
• Hosted Microsoft Dynamics® CRM
• Hosted Microsoft Exchange
• Hosted SharePoint
• Web Hosting
These powerful solutions can all be tailored to meet the specific needs of your business. Whether you are looking to reach new markets, increase efficiency and organization, or leverage your technology investments, Cloud Services are the solution you've been looking for.
Hardware as a Service
Affordable hardware and operating systems without the headaches
With a flat monthly fee for equipment and warranty service, it can eliminate large capital outlays and allow IT equipment costs and related maintenance services to qualify as operating expenses, providing you with significant tax advantages.
They should provide infrastructure hardware, operating systems, and other software and warranty services for servers, desktops, laptops, routers, switches, and firewalls.
Mobile Device Management
You and your employees depend on mobile devices to keep business running smoothly. With security threats on the rise and a high potential for technology problems, your mobile devices need the same monitoring and management as your in-house IT does. Mobile Device Management (MDM) provides you with the same worry-free IT experience of that Managed Services offers.
Mobile Device Management - Your mobile devices should be scanned every four hours With MDM you should get comprehensive monitoring and management for Apple, Android, or Windows mobile devices.
Mobile Device Management is:
• Secure - comprehensive reporting and monitoring let you know if there's a breach to your phone's security
• Worry-free - if your mobile device is lost or stolen, we can locate it with GPS technology and wipe your private data remotely
• Flexible - new users to your mobile network can be automatically set up via remote configuration management
Enterprise & SMB Telephone Systems
Telephony systems designed with your business in mind
Small and medium-sized businesses need the same advanced and reliable communication solutions as large companies do.
With VoIP installation and support, your business can enjoy all the benefits of modern communication techniques that are tailored to your needs for an affordable price.
VoIP solutions are:
• Economical - cut your telecommunication costs and avoid extra setup, installation or maintenance fees
• Dependable - your hosted system is monitored and maintained 24/7
• Convenient - answer calls in remote locations via laptop or forwarding to a mobile phone
• Green - cut travel costs and paper waste by sharing information online
Networks
Your cabling and infrastructure networks are the lifeblood of your business
A stable infrastructure and cabling system are the lifeblood of any business. These two essential parts of your network allow your operations to run smoothly.
Networking
A wide range of expert cabling and infrastructure services, including:
• Cabling - fiber optic, cat 5/6E, coax, analog, etc. - underground or overhead
• Racks, enclosures, UPS's and power management hardware
• Switch, router, firewall and appliance installation and operation
• Circuits - data and analog PRI's/T-1's, POTS, ISDN, fiber, DS3's, and on site customer WAN engineers
• PA systems - amplified PA's with ceiling & hall speakers, outdoor horns sales and service.
• Telephone systems - new and used/re certified phone systems - VoIP or PBX. Service for most all older telephone systems, including installation, maintenance and upgrades across the board
• Security camera solutions - video over IP server-based security solutions and low cost DVR security camera solutions - surveillance software, on site surveys, installation and setup
• 802.11x wireless meshed networks - free site surveys, installation and configuration
• Category 5e/6 cabling installation and design
• Multi office LAN design & cabling (WiFi, VoIP, CCTV)
• Rack and enclosure sales and installation
• P.S. and power management
• Local area network circuit extensions (T-1, DSL, Frame Relay, MPLS)
• Fiber-optic cabling installation and design
• Design of data, voice, video and paging for new construction
• Wireless solutions
Website Design & Internet Marketing
Web Design
The website should look fantastic, but also perform a very important role. You should understand that your website is a valuable member of the team.
• Be seen and heard
• The expert web team should be trained to increase your company's online identity through search results, social networking and video media.
• Use your website to communicate different messages to specific visitors, advertise company news or campaigns with targeted banners and pop ups, or remind and thank your staff or customers with automatically generated emails.
• Control your own content
• They should build functional systems that really do put the content control in your hands. A password protected admin panel allows you to access and manage content yourself without the need to involve them.
• Deliver results
• They should design and build websites to actually deliver results based on your specific business objectives
Search Engines & Internet Marketing
They should be trained to increase your company's online identity through search results, social networking and video media. PR & Editorial
Ad Campaigns & Projects
Their marketing experts implement well thought out Ad campaigns and projects that have a measurable, positive impact on your business
These are MOST of the major points a business should look for when shopping for an IT company to care for their system(s). See more at kernitservices.com
Thank you for reading this.
1 note
·
View note
Link
0 notes
Text
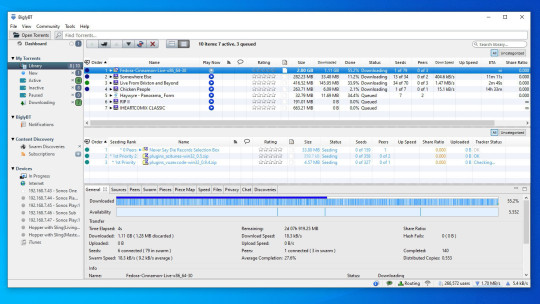
Top Torrent Clients 2019
Best Torrent Download App 2019 uTorrent – torrent client for Windows, Mac, Android and Linux. UTorrent is the best choice when it comes torrent client for Android, Mac and Windows. It’s most widespread among torrent users worldwide. In fact, I am using uTorrent right for downloading files from the torrent on Windows. Torrents are the best way to download larger files, from videos to computer programs and more. But finding reliable torrents and torrent sites can be a struggle. Top sites like The Pirate Bay. This website works as a torrent search engine and helps you to find the torrents you are looking for the top-rated torrent websites in no time. The user interface of this website is quite simple and easy to operate as well. If you are asking yourself what torrent sites are working. This torrent site is you should browsing. Official Website. Veteran torrent site The Pirate Bay, TPB for short, again drives the 2019’s top torrent sites list while running on its original domain. The well-known website wore the crown a year ago after the total wipeout of KickAss Torrents. Folx is at the top of our list of torrent apps for Mac since for now it is the only torrent client that is is fully compatible with macOS Big Sur. It offers a convenient way of downloading torrent files: set the priority, regulate download and upload speed, tag downloads for quick search through the content.
Cloud torrent clients are getting more and more popular every day, due to the security and privacy they provide for users while downloading torrents. They also offer extra features that standard clients do not provide. Since all the downloading happens in the cloud, on the company’s servers, you do not have to worry about mobile data. You can, therefore, use cloud torrent clients on your mobile devices. You just put in the torrent that you want to download, and the torrent client downloads it for you. After the successful fetching of the torrent, the user can download the torrent file to their phone or computer via a secure channel. Your Internet service provider does not see what you are downloading. This feature is why cloud torrent downloaders are ideal for users who have some kind of restrictions, whether it’s at work or governmental laws. Downloading torrents this way is faster, easier, and mainly more secure than your regular desktop clients.
Many companies provide cloud torrent downloaders, and at first glance, most of them look the same. Once you researched deeper into what they offer, you will find many differences. We tested 8 of the most popular cloud torrent clients on the market, and we have a complete analysis of them for you.
Security
Now, the most important thing when it comes to downloading torrents. All of the clients we tested provide encrypted connections between the user and the cloud system. Torrents are never downloaded on the user’s side. Everything is downloaded on the company’s servers, so they use their dedicated IP for torrent downloading. The users’ IP is never exposed to the world.
A VPN is not needed at all. As a matter of fact, it would slow down the download speed from the cloud storage to your device. Clients like Seedr and Bitport offer extra security in the form of a built-in antivirus, which scans every single downloaded file for viruses.
Torrent downloading
In cloud torrent clients, there are two types of downloading. The first one is torrent fetching to cloud storage, and the second one is downloading offline to a users device. In torrent fetching, we found huge differences between the many different clients. With the eight we tried, we tested the downloading of the same files, which came from public trackers. These two files had 700mb and 5gb. We also tried the same with private trackers. Overall, four torrents were tested, with each one of them having at least 50 active seeders. The fastest clients were Nody and Bitport, both of them even downloaded at high speeds from private trackers.
On the other hand, some had major problems with the download speed. One of them, Streamza, was unable to download from private trackers at all. Seedr was also unable to download from a private tracker but was rather fast in downloading smaller files from public trackers. Well-known Boxopus also downloaded from public trackers really fast but extremely slow from private trackers.
Offline downloading is the downloading of the successfully fetched torrents to the user’s device. The huge advantage here was Bitport and Seeder, who have their servers all around the world. For the maximum download speed, it is important to choose a server that is closest to you. Bitport finds this server by itself.
Design
You can usually guess a quality client just based on the design. Nody has the best design, which offers a user-friendly cloud and shows posters for each torrent file. It is a very handy feature. You can also find a nice design in Bitport, who thrives in a user-friendly experience. Another noteworthy client is Megabox, which offers many elegant animations. A slightly above average is Boxopus, which has a minimalistic design and a great logo. Next in line would be Seedr, which has a lot of problems with formatting various web elements, and the design is not consistent at all. It looks like Seedr created many designs at the same time and used little bits and pieces of each. Furk and Zbigz have a utilitarian design, but it is very outdated now. The worst design by far has Streamza. It looks like a big mess with a lot of the links not working.
Video player
This tool is very useful if you want to stream the videos right from the web without having to download anything to your computer. Unfortunately, some clients do not offer this feature at all. Boxopus lacks this feature completely, while Zbigz, Furk, and Streamza have a video player with only the basic features. They do not include extra features like SD/HD playback and subtitles. Next, Seedr, Nody, and Streamza contain the previously mentioned features with Seedr also, offering a live streaming feature. The best video player is from Bitport. Although it doesn’t have the fastest converting, it streams all types of videos, including 4k in 60fps.
Extra features
It is important to also look at the extra features when picking a torrent client. Most of the clients have a browser plugin which you can use to add torrents directly to the client with one click in the browser. Next is a mobile phone app. It usually offers the viewing of the videos, and some offer the ability to download offline. Boxopus, Streamza, Bitport, and Furk provide Android app. The iOS app is offered by Bitport only, which also provides an app for Apple TV.
We are sure you can imagine a situation where you need to download some files to your Dropbox or Google Drive instead of your computer. Downloading to Google Drive is offered by Bitport and Boxopus, who also provides a download to Box. Bitport is the best when it comes to automatization. They offer an RSS feed, which automatically downloads new torrents to your cloud, which can also be combined with their PC sync client. Seedr, Bitport, and Zbigz offer an interesting affiliate program.
Reliability
If you try to download ten torrents, and only seven of them get downloaded, then you really cannot rely on the torrent client. We recommend that you find reviews of others before paying for a torrent client. Some clients, for example, Boxopus, have a lot of server outages, so you have to be careful. If your desired torrent client offers a trial plan, then definitely try it before buying the full version.
Results
The results, based on our tests, are following.
The best cloud torrent client is Bitport.io, especially for its extra features, reliability and the fast download speeds. The second is Nody.me. It has a nice design with a social sharing feature. The third is Megabox, which combines a great overall experience from a start to the end.
Rating
Links
96
85
76
72
69
67
60
54
What do you think? Do you have the same experience? Let us know in the comments below.
Considering the size and cost, eBook is a perfect way that you can read your favorite books without actually carrying them physically. They are stored on your smartphones or Laptop from which you can read your books on the go. Well, there are numerous torrent sites for ebooks that allow you to get hold of a virtual library from where you can read online or download them to read at your own convenience. And in this article, we are going to introduce you to the best 20 ebook torrent sites.
Important Notice: If any below torrent sites ask for a credit card for access, please stop visiting the website instead.
1. TorrentDownloads
When it comes to eBook torrent downloading, TorrentDownloads is always on the forefront. There are around 16 million torrents are arranged in categories like, Movies, Books, TV Show and more. It also has Bollywood/Hollywood/regional language movies to be downloaded within it.
2. Planet eBook
Planet eBook, the home of free classic literature! The latest version of the site, with its mobile-friendly design and multi-format eBooks, attempts to publish a small selection of high-quality eBooks and make their collection of eBooks available on all devices for free. And it currently has about 50,000 titles in its library.
3. ManyBooks
ManyBooks, with the vision to provide an extensive library of ebooks for free on the Internet, is one of the best user interfaces and design among the e-book torrent sites. You can easily navigate through the site using categories like Genres, Titles, Authors, Language, Popular, Featured Authors, and Recommended. As of today, the site hosts over 50,000 free e-book titles. If you’re a writer yourself, you can even use their platform to promote your book.
4. EBOOKEE
EBOOKEE is striving hard to become one of the best torrenting E-book sites in near future. The site covers books from tech, tutorials, non-fiction, novels, computer programming and much more. One feature that really stand out is the sub-category system classified into groups such as “Recently Viewed eBooks”, “Top 10 eBooks”, “Top 10 Users”, and “Latest Added Books”. These sub-categories make it a lot easier to pick a book.
5. Zooqle
With a beautiful interface and easy to navigate, Zooqle is a good start for eBook readers to download eBook torrent for free. This siteworks as a web crawler to find best torrents. Founded in 2008, it's a great site to download videos, books, Hollywood high definition movies and software. The site got everything in its homepage and you can check out the stuff by menus and links.
6. Smashwords
Smashwords is the world's largest distributor of indie ebooks. They make it fast, free and easy for any author or publisher, anywhere in the world, to publish and distribute ebooks to the major retailers and thousands of libraries.
7. Book-Share
Book-Share is the best torrent site if you’re seeking nothing else other than e-books. You’ll find almost every genre on this site. Moreover, it has an impressive list of categories for easy browsing; a feature that lacks on other torrent sites. You can even search for books as per their author, title, or subject. As of now, there are more than 4,00,000 books, and that is huge! Since this site is dedicated to e-books, its a brilliant option for avid readers.
Bittorrent Sites 2019
8. Free-Ebooks.net
As the domain name suggests, Free-Ebooks.net offers a colossal library of books for free with several categories including fiction, non-fiction, Academic, Classics, Textbooks, and Audiobooks. The best part about this site is that it encourages budding e-book writers by giving them a platform to publish their work. What’s more? Free-ebooks also offers an option to choose the format in which you wish to download a book; for example: Kindle, Txt File, PDF, and EPUB.
9. Tech Books for Free
When you want to download books based on tech related categories, Tech Books for Free should be your go-to-choice. It is a website that offers a wide range of downloadable books on Technology, Computers, and Science for free. Hence, you are able to accomplish your technology reading cravings straightaway.
10. Wikibooks.org
The prefix “wiki” has perhaps already gotten your interest peaked. While Wikibooks.org doesn’t really have anything to do with Wikipedia, it does have a large database of books. What’s unique about this site is that you can get e-books in several languages including Dutch, English, Italian, French, Spanish and Portuguese. You first have to pick a language and then type in the title you’re trying to find.
11. FreeBookSpot
FreeBookSpot is considered as one of the most popular websites to download eBooks and audiobooks for free, which allows you to find out your desired book through different options like genre, language and most popularity. Moreover, you have a luxury of exploring books from more than 90 categories. It is better known for its collection of educational as well as non–fiction books.
12. MyPDFbooks
MyPDFbooks is an active platform for downloading the free eBooks in PDF and ePub formats. The main objective of their website is to provide high-quality fast-speed downloading service with a user-friendly environment without registration and other hectic procedures.
13. The Pirate Bay
The Pirate Bay is world’s number 1 torrent site available and is also the most used torrent search engine in the world. It servers support SSL encryption. In other words, it’s a safe site for transferring files and download torrent files and magnets without having to worry about viruses. It is not limited to just e-books but also has got other category torrents like games, movies, TV shows, music and many more.
Top Best Torrent Clients 2019
14. 01Torrent
01Torrent is a free torrent site where users can download the latest movies, music, television shows, applications, games, books, animes, software, and many more. The interface is so clear that you can download anything directly. And this website no longer needs any registration.
15. Kickass Torrents
Kickass Torrents is similar to The Pirate Bay which has a huge collection of torrents. It’s one of the old and most powerful torrent search engine of the world. More than 200k e-books that are available for free download. If you are not able to find the e-book that you are searching for, you can put up a request for that particular book on the community forum of the website.
16. ExtraTorrent
When we talk about the most famous torrent websites, ExtraTorrent is known to play the most effective role in comparison to the other torrent websites. It has a huge collection of torrents like movie, e-books, music, games, and whatnot. One of the great feature of this torrent website is now you can also subscribe to RSS of any ebook category for free.
17. 1337X
1337X is great for all those who are interested in a bit of everything like games, movies, books, TV series, etc. The well-developed UI makes it easier for users to search and download book torrents. Do you know who ran this torrent site? The Fans! Yes, after some years the creators are running out from this torrent site. Now it was fully maintained and updated by the fans and users itself. It gets updated like every other torrent site.
18. Torlock
Torlock is another reliable torrent books website that has a clean and simple UI. Similar to 1337X, Torlock also has a dedicated section for ebooks. Furthermore, Torlock is one among very few websites that only list verified torrents. Searching and downloading your favorite ebook is fairly straightforward.
19. Torrentz
Torrentz is a free, fast and powerful meta-search engine combining results from dozens of search engines. Indexing 31,102,502 active torrents from 125,464,743 pages on 26 domains. Torrentz's user interface is simple, which only has a user menu and a search panel. To perform a search, users would simply type in a string of keywords within the search field. Selecting a torrent from the search results list would take the user to other torrent sites to download content.
20. Torrents.me
Torrents.me is a meta-search engine that links to torrent files and magnet links from other torrent sites. It's one of the torrent sites that enjoyed a meteoric rise in traffic this year.
Bonus Tip
If you are looking for a free tool to convert DRM free ebooks, you can try Epubor Ultimate software. All you need to do is drag and drop the books to the software, choose your desired output format, then click the Convert button to start the conversion. If you also have DRM-protected Kindle/Nook/Kobo/Google Play Books, etc, the all purpose Epubor Ultimate can help you remove DRM effortlessly. For more detailed instructions, you can read the step-by-step guide to liberate your purchased ebooks.
Conclusion
After reviewing the above top 20 ebook torrent sites, even if you are a book enthusiast, you can opt any torrent site of your choice to satisfy your book reading desires. If you know any good torrent site for books, feel free to share your thoughts in the comments section below.
Download Epubor Ultimate for Free
Hillary Lopez works for Epubor and writes articles about eBooks and eReaders. She explores the best method to help you read eBooks more freely and wants to share all she has got with you.
0 notes
Link
0 notes