#derbycon
Explore tagged Tumblr posts
Text

The trail head to a puzzle challenge I created as homage to Paul Rubens (Pee Wee Herman). Rest in peace Paul.
0 notes
Photo

SOON #DERBYCON (at Mmc Farmstead) https://www.instagram.com/p/B2F_AFAJIly/?igshid=10h5m0gnzs58u
0 notes
Photo

How to tell my #rocketbook apart from others? It’s a question of Cons. #SkyDogCon #Derbycon #BSidesDFW and more.
0 notes
Text
Como detectar e bloquear ataques de Living off the Land
Como detectar e bloquear ataques de Living off the Land
Vivendo da terra, os ataques estão se tornando cada vez mais comuns. O termo “Living off the Land” remonta ao DerbyCon 2013. Simplificando, significa quando os invasores usam ferramentas e recursos legítimos em seu ambiente para realizar ataques. Às vezes, eles também são chamados de ataques sem arquivo, pegada zero ou, como me referirei ao longo deste artigo, ataques LOTL. Então, por que os…

View On WordPress
0 notes
Link
0 notes
Text
Increasing Safety and Inclusiveness at Hacker Cons
This roadmap for addressing the problems which soured this September in Louisville is a collaborative work by numerous women… many who attended DerbyCon Legacy (some have attended every single year), others who came but left early, some who stayed away entirely because of the news of what was happening, and additional women who have previously vowed to not attend such events at all unless some of the deep-rooted problems in Infosec (which are not unique to any one specific event) can be addressed by conference leadership.
We appreciate the fact that Dave Kennedy, Martin Bos, and many of the volunteers from DerbyCon have engaged the public in a dialog regarding how to best provide for the safety and well-being of hacker con attendees in the future. It is wonderful, their willingness to take steps in a positive direction, and we accept their invitation for open discussion.
There are three steps we see DerbyCon proceeding through in the process of repairing their public image and improving safety for women at conferences. They are outlined here…
[= I. Adopt and Publicly-Post a Code of Conduct =]
Even though a small contingent of people have resisted this in the past, DerbyCon has made significant progress in this area recently. That’s wonderful. A Code of Conduct protects a conference as much as it protects the attendees. Many prominent speakers and sponsors won’t participate at events without one, and even the smallest and most far-flung of hacker cons have been adding them to their web sites and programs.
A Code of Conduct doesn’t have to be long, full of legalese, or kill the “friendly” feeling of an event. It really only has to do four simple things:
State that the event wants to be a welcoming and safe place for all attendees (DerbyCon already says this and has been telling the community that for years now)
Explain what behaviors are not tolerated (this, unfortunately, is where DerbyCon fails to be adequately specific)
Explain how people should report problems (DerbyCon, like many events, encourages people to “contact staff” but the preferred language would include an email address or other contact information that is monitored 24/7 during the con. (If someone is holed up in his or her room because of threats, they shouldn’t have to venture downstairs looking for a red shirt or scroll through Google results trying to find the right Security contact)
A commitment to enforce these rules. (DerbyCon claims to stand for the security of all attendees, but unfortunately we have seen that there have been some stumbles in the past when it comes to follow-up on problems)
DerbyCon can solve point #2 & point #3 with the addition of honestly just one or two lines of text.
At least one hacker con has summarized their Code of Conduct as, “If you are a jerk, we’ll ask you to leave." Examples of being a jerk include harassing, forcing unwanted interactions, or secretly replacing someone’s coffee with Folgers crystals.” Humor can be just fine here! (As long as the two most critical points of “don’t harass others” and “don’t force yourself upon others” are spelled out.)
The “contact” information can truly be an email like security@derbycon.com as long as it’s being monitored throughout the whole event. DM-ing the conference Twitter can work but that requires open DMs (which not all Twitter clients support well) and forces a staffer to sift through a lot of messages, many of which will be just noise.
[= II. Sunlight as Disinfectant =]
This may be the hardest pill to swallow. Right now, we are not aware of any public-facing resolution or closure on these matters aside from Dave and Martin tweeting that things are going to get much better in the future. That alone will not mollify those with concerns nor will it make women want to start attending/proposing in record numbers.
There were two separate major incidents this year, and they were deeply inter-related. DerbyCon would be wise to make blog two posts on their site in which they discuss them frankly and offer clear public apologies for any ways in which they feel they didn’t live up to their full stated hopes of being a con for everybody in the hacker family:
Failure to condemn and expel harassers
While the mishandling of the matter relating to a trainer with a restraining order due to domestic abuse was deeply troubling, harassment is actually the wider matter at DerbyCon, and the issue that keeps women away so much. Given no Code of Conduct prohibiting harassment, a small but vocal group of angry voices targets their rage at people in an attempt to either make them stay away from DerbyCon or not enjoy DerbyCon if they attend. This angry group (to varying degrees) has at times included both staff as well as the general attendee public. While folk such as the former security staffer and his posse of associates represent the worst of it, plenty of things that the conference videographer has stated online cross the line into harassment, as well. Even one of the conference founders, generally a kind person, has threatened physical violence against people and profanely told women to be silent when they have criticized DerbyCon online.
This is a topic where DerbyCon has to dedicate extra care during the repair of its reputation, since it became public during the con this year that most of the hatred and abuse is generated within a Facebook group calling itself the “illmob” (a group apparently started and overseen by the fired security staffer) which includes the DerbyCon founders and several other conference staff as fellow members.
NOTE - This is not to suggest in any way that said Facebook group’s sole purpose is to harass women, but simply to point out that the creation of the harassing tweets, image memes, apparel, etc takes place here in full view of the DerbyCon conference staff. They cannot claim ignorance regarding the identity of the people behind the harassment.
The mishandling of reports of an alleged abuser of women
This is more delicate, and a private matter, but DerbyCon can speak to the problem respectfully and in a way that tells the public (a) what went wrong and (b) what they will do differently in future.
The earlier blog post, about the harassment issue, is harder to put into words but it would be good if it (1) acknowledges that attendees have been subject to online harassment in the past, (2) explicitly states that this is not what DerbyCon is about and that this is not OK, (3) apologizes for any statements made in the heat of the moment by the DerbyCon team which could be construed as harassment, and (4) includes a commitment to prevent this behavior in the future… a promise that staff will be professional and a promise to eject or bar attendees who harass others.
[= III. The Ramifications =]
So here’s where the rubber really meets the road.
Actions speak louder than words.
If DerbyCon is going to be taken seriously, and to satisfy Point #4 regarding a Code of Conduct as mentioned above, they must demonstrate their genuine commitment to:
standing by their updated Code of Conduct
handling reports of abuse/safety risks/etc properly.
DerbyCon has stated that they’ve “never banned anyone” and described how they feel that the community has failed if things get to that point. This is not so. It fails the community to have rules and policies but never actually follow through on them.
As hard as it will be for them:
* Will Genovese represents the most clear-cut violation of a Code of Conduct that anyone has ever seen. He has repeatedly harassed numerous people over the years (and reserves the bulk of his ire for women and their supporters) and this year went so far as to put DerbyCon at actual legal risk by harassing attendees and abuse victims while speaking on behalf of the conference itself. Even after he was fired he continued to harass attendees (and non-attendees who simply spoke about DerbyCon) online and at the conference. The DerbyCon Code of Conduct carries basically no weight if people who behave in this manner are allowed to attend. There are others who have said hateful or harassing things to a lesser degree… but Will has taken it to the point of publicly posting both text and images that do nothing but sow hate and discontent at DerbyCon. For the community (particularly women) to take even slightly seriously the notion that DerbyCon is trying to improve, Will would not be invited back to DerbyCon nor welcomed as an attendee.
* the individual subject to police investigations, an Order of Protection, and court filings for abuse would not be invited back to DerbyCon as a trainer nor welcomed back as an attendee. The fact that he was subject to an Order of Protection backed up by a report of physical violence should have been enough there (and Martin Bos claimed back on August 30th that an O.o.P. was more than enough reason to ban him) We are not talking about an Administrative Non-Contact Order (which basically anyone can get on anyone else for almost any reason) but an Order of Protection based on police-documented abuse. Once the police (not just courts, but the police) are taking things seriously, come on… that’s a person you don’t want at your conference.
* Bryce Case Jr. (a.k.a. YT Cracker) would not be invited to DerbyCon as an artist nor welcomed as an attendee. Again, this is someone with a long history of security violations and drunken abuse of women at other conferences. There are records of all this. It is unclear if the /courts/ were ever involved, so this individual represents a different standard of evidence… but he unmistakably is a known bad actor and if DerbyCon can’t bring themselves to prevent his attendance, it is a signal to the community (especially women) that DerbyCon is not a place where people are safe.
* The DerbyCon videographer is the hardest case here. He has engaged online in what is seen by many as harassment. It has seldom been /directed/ at anyone, however. Instead, his comments are broad and focused against women and their supporters as opposed to calling out a specific person here or there. Also, as his defenders have pointed out, some of this has become more managed in recent months. Our willingness to give him space to reform has nothing to do with his tireless work on video recording… there is no ‘hours of volunteer work / hateful behavior forgiveness’ exchange rate system. We are not without understanding; he could remain part of DerbyCon (where he is cared about by many individuals who are trying to help him improve himself) in a Volunteer role as opposed to being on Staff and this might placate the majority of the community. But there will always be a number of women who will not feel safe attending any conference or event where he is present as anything other than an attendee. (This is why BSides events sadly had to take the difficult steps that they did and remove him.) It is hoped that his behavior continues to improve and that DerbyCon will never have to bar him outright.
It is interesting that in the case of the trainer and the music artist, they aren’t actually in direct violation of the Code of Conduct, because nearly all of their misdeeds took place off-site and at other events. But barring them from future attendance is of course part of a greater safety management process… which needs to be addressed by internal policy: How do you decide that someone is a safety violation to your attendees? How is this researched? What counts as evidence? With whom does the final decision rest? All of this needs to be written down somewhere. Not necessarily posted publicly, but written down and made available in cases where parties request to see it. This is very important for DerbyCon to legally cover their butts and it’s astonishing if some policy like this doesn’t already exist.)
If DerbyCon makes good on these three key areas – a more fully-realized Code of Conduct, public posts describing the difficulties and apologizing to the community, and finally breaking with tradition by actually officially barring certain known bad actors from attending in the future – then this would be considered a welcome (and really big) step in the right direction for the conference. And for the hacker community at large.
6 notes
·
View notes
Link
via Twitter https://twitter.com/PatrickCMiller
0 notes
Text
Because I can't help myself I will elaborate on my meme
There was a hacker convention called Derbycon going on the beginning of September 2019 in Louisville. I'm not a hacker but my dad is kinda and so my family got to take a lil trip there and hacker or not twas a fun lil time!
We were out eating and noticed all these young girls with their hair up in a bow wearing Jojo Siwa shirts and such and I was like "There can't coincidentally be all these young girls with their hair up in a bow wearing Jojo Siwa shirts and such there's gotta be a reason" and it turned out there was some Jojo Siwa event also going on in Louisville around the same time as Derbycon and I thought it was kinda funny that these two very different demographics were occupying the same town.
I have an urge to make a very specific meme that no one would get
9 notes
·
View notes
Text
Make It Rain with MikroTik
Make It Rain with MikroTik
Original text by Jacob Baines
Can you hear me in the… front?
I came into work to find an unusually high number of private Slack messages. They all pointed to the same tweet.

Why would this matter to me? I gave a talk at Derbycon about hunting for bugs in MikroTik’s RouterOS. I had a 9am Sunday time slot.

You don’t want a 9am Sunday time slot at Derbycon
Now that Zerodium is paying…
View On WordPress
0 notes
Link
0 notes
Text
Slashdot: DerbyCon Will Hold Its Last InfoSec Conference in September This Year
DerbyCon Will Hold Its Last InfoSec Conference in September This Year Published on January 14, 2019 at 11:55PM DerbyCon 9.0, the upcoming edition of the popular InfoSec conference in September, will be its last. From an official announcement: When we first started DerbyCon, our goal was to create a conference where we could all come together to collaborate and share as a community, but most importantly as a profession. DerbyCon 1.0 was a huge gamble for us both personally and financially, but we believed in what we were doing, and it worked. For those that don't know the history of DerbyCon, it started off inside of a pizza shop as an idea between a few friends. Our goal was to create an affordable conference that shared a lot of what we had experienced in our early days in security. The ideas of collaboration, community, and the betterment of the industry and the safety of technology were at the forefront. At the end of DerbyCon 1.0, we realized that the conference was a huge success and our dream became a reality. [...] What we have had to deal with on the back-end the past few years is more than just running a conference and sharing with friends. The conference scene in general changed drastically and small pocket groups focus on outrage and disruption where there is no right answer (regardless of how you respond, it's wrong), instead of coming together, or making the industry better. There is a small, yet vocal group of people creating negativity, polarization, and disruption, with the primary intent of self-promotion to advance a career, for personal gain, or for more social media followers. Individuals that would have us be judge, jury, and executioner for people they have had issues with outside of the conference that has nothing to do with the conference itself. Instead of working hard in research, being a positive force in the industry, or sharing their own unique experiences (which makes us better as a whole), they tear others down in order to promote themselves. This isn't just about DerbyCon, it is present at other conferences as well and it's getting worse each year. We've spoken with a number of conference organizers, and each year it becomes substantially more difficult to host a conference where people can come together in large group settings. It's not just conferences either. This behavior is happening all over the place on social media, in our industry, targeting people trying to do good. As a community, we add fuel to fire, attack others, and give them a platform in one massive toxic environment. We do this all in fear of repercussions from upsetting others. Until this pattern changes, it will continue to get worse.



Read more of this story at Slashdot.
0 notes
Text
使用DDL注入绕过Windows 10受控文件夹访问保护

在Windows 10中,微软新增了一项名为“受控文件夹访问”的功能,该功能可用于防止未知程序修改受保护文件夹中的文件。
而在上周举行的DerbyCon安全会议上,一位安全研究人员则向大家展示了一种利用DLL注入来绕过受控文件夹访问保护的方法。
使用DLL注入绕过受控文件夹访问保护
受控文件夹访问功能启用后,将会监视应用程序对受保护的某些文件夹中的文件所做的任何更改行为,并且只允许被列入白名单的应用程序修改这些文件。白名单应用程序可以是你指定的应用程序,也可以是微软默认列入白名单的应用程序。
在得知explorer.exe默认为受控文件夹访问白名单程序后,富士通系统集成实验室的安全研究员Soya Aoyama想出了一种,在启动时将恶意DLL注入资源管理器的方法。由于资源管理器已列入白名单,因此在注入DLL时它将启动并绕过勒索软件保护功能。
当explorer.exe启动时,它将加载HKE…
View On WordPress
0 notes
Text
Breaking Out of Shells at DerbyCon https://t.co/xbp4TUSsQ3
Breaking Out of Shells at DerbyConhttps://t.co/xbp4TUSsQ3
— Wordfence (@wordfence) October 12, 2018
wordfence
0 notes
Text
Защиту от шифровальщиков в Windows 10 можно обойти с помощью инъекции DLL
На прошлой неделе на конференции по компьютерной безопасности DerbyCon, один из исследователей продемонстрировал, как с помощью инъекции DLL можно обойти защиту функции «Контролируемый доступ к папкам» в Windows 10
via Антивирусы, обзоры и тесты https://ift.tt/2QDoYUw
0 notes
Text
crying to radiohead isn’t lame
(you can jmp loc_888 if you just want my final thoughts.)
in a recent tumblr manifesto directed at convention organizers regarding their lack of codified rules of conduct and lackadaisical approach to safety, i was outed as a big part of the overall problem:
Bryce Case Jr. (a.k.a. YT Cracker) would not be invited to DerbyCon as an artist nor welcomed as an attendee. Again, this is someone with a long history of security violations and drunken abuse of women at other conferences. There are records of all this. It is unclear if the /courts/ were ever involved, so this individual represents a different standard of evidence… but he unmistakably is a known bad actor and if DerbyCon can’t bring themselves to prevent his attendance, it is a signal to the community (especially women) that DerbyCon is not a place where people are safe.
the author of this section is admittedly shannon morse (aka snubs), who, rightfully so, has a beef with me for an incident that happened at the bsides las vegas pool party in 2014. i was dared by a friend to grab her butt and, like a third grader, proceeded to fulfill this dare.
yes, i was highly intoxicated - i don’t offer that as an excuse, just as backstory. the drinks were flowing and i had been pretty belligerent that evening - i kept turning up the volume on the mixer vs. the wishes of the convention organizers; my rap performance was sub-par, the dj performance even worse. i don’t deny that i was in rare form in the wrong way.
the next day, i apologized to everyone i thought that i had fucked things up with the night before. i was able to piece together a lot of the events that were foggy through the human blockchain i was with. a lot of people do embarrassing shit when they are inebriated, and i am definitely no stranger to being “that guy.” i am not, however, some kind of sexual predator.
i was not invited back to the party in 2015; i didn’t really expect to be invited back due to my actions the previous year. at this point in the story though, i still didn’t even know the snubs issue existed. it wasn’t until december when snubs tagged me regarding the incident in a defcon videos thread: https://twitter.com/Snubs/status/673553028847263744 http://archive.is/Uj1zT
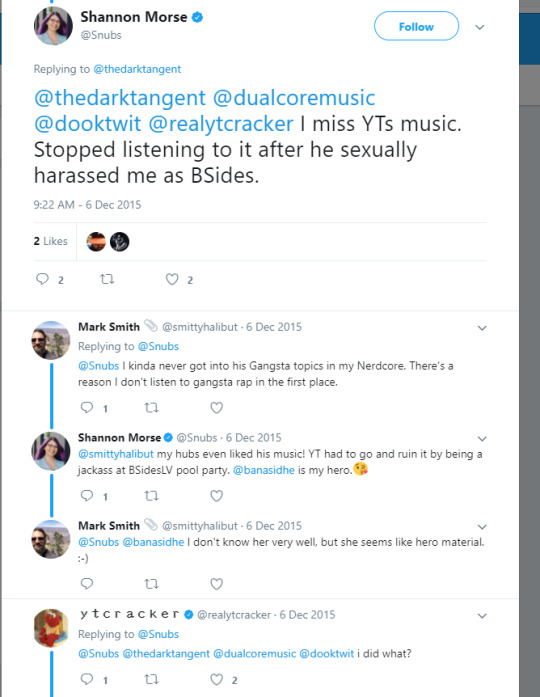
i immediately hit up int80 and whoever else i could regarding this whole thing and emailed shannon to sort it out: https://imgur.com/a/nLzam
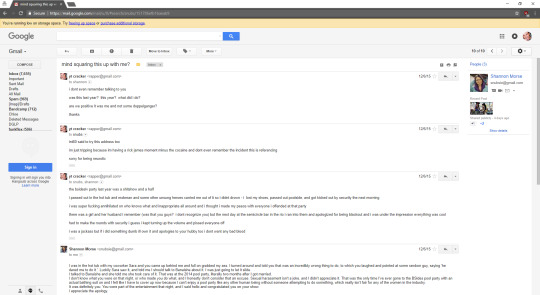
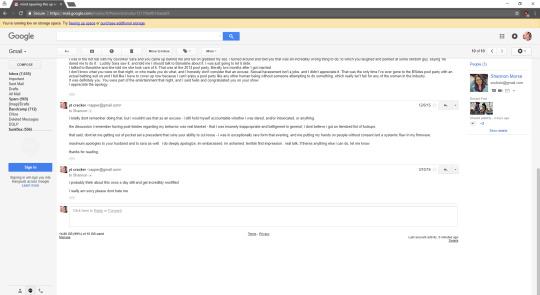
long story short, she told me everything i did that evening. i apologized and told her i was wrong and if she or her man wanted to take a crack at me, i deserved it. i truly feel terrible about it. i am not in the wholesale business of violating people, just their computers.
snubs acknowledged that we hashed it out over email and things were kosher: https://twitter.com/Snubs/status/673641949279096833 http://archive.is/9NHtz
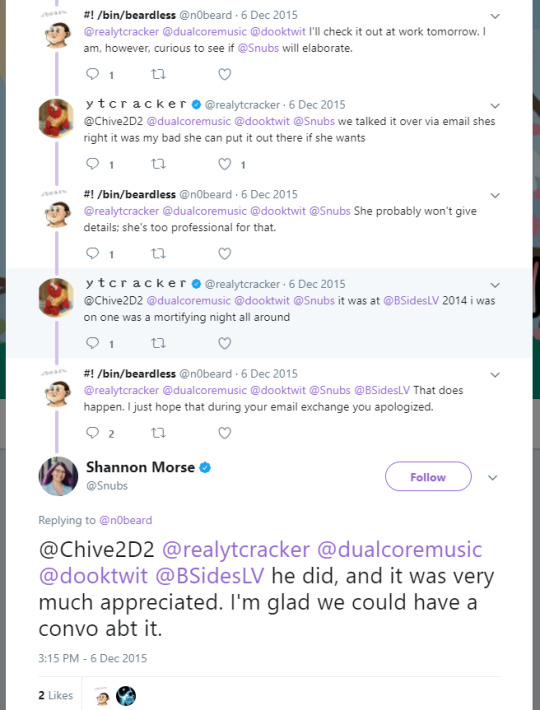
i spoke with the bsideslv folks in DMs, they tweeted my apology and request for grievances. i won’t screenshot, but here: https://twitter.com/BSidesLV/status/674391295616352256 http://archive.is/3XaOi
i thought my mea culpa was SYN ACKd, and the world was flat again. i was asked by bsideslv to perform again in 2016. i even pointed out in the email that if snubs was unhappy with my presence there that i would not attend: https://imgur.com/a/ZOhQA
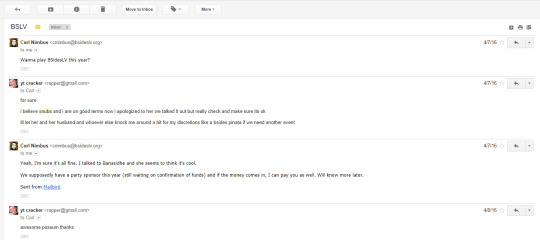
perhaps there was a miscommunication, but i did think everything was ok at this point. i think any reasonable human being would. in august, during the defcon festivities, snubs took to twitter again: https://twitter.com/Snubs/status/761853967110242304 http://archive.is/LeNx0
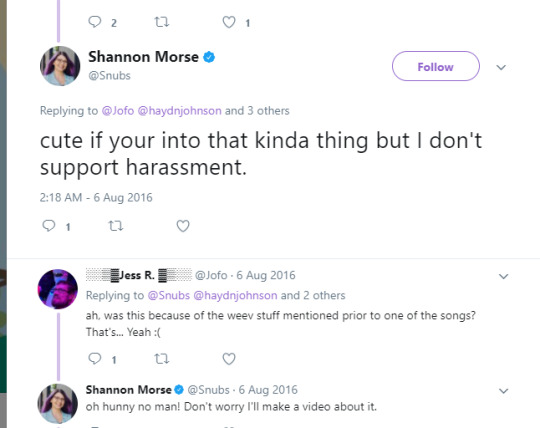
i told her i was more than happy to apologize in person and i thought this was worked out: http://archive.is/a5yCq
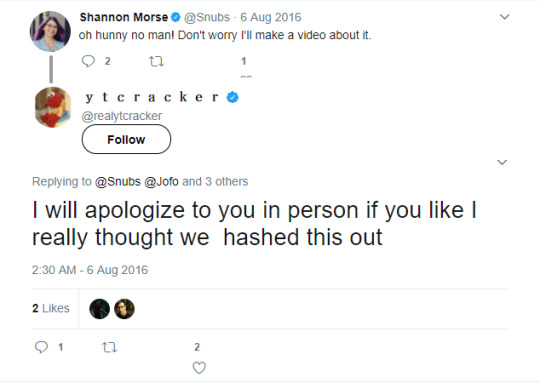
we didn’t hash it out, obviously. anyway, this must’ve been stewing for some time. i don’t blame her for being pissed off and it is totally her choice to be mad at me. she can be mad at me forever if she wants, and i know now after the recent tumblr post and the video where she recounts this story and voldemorted me (see below), she does not like me:
youtube
if you’ve made it this far, congratulations.
loc_888:
look, i admit i am an imperfect human that is a stellar fucking idiot when he’s rammed a bunch of alcohol down his throat, but i will not cop to being a serial rapist or chester molester or threat to people at conventions. i admit that grabbing shannon was poor judgement and poor behavior and i am sorry i put her through that. however, if there’s some giant body of evidence out there that i am the hacker bill cosby on some tyler durden, multiple personality shit then please, show it to me. rarely am i ever alone at conventions, so there are usually always witnesses to my conduct. it is totally disingenuous to paint me with that large of a brush.
in lieu of a heavy handed CoC, i am all for setting up a shitlord dunk tank at these conventions - $5 to dunk me in manure like some back to the future tannen cosplay - with all of the proceeds going to female STEM organizations, or whatever else you think i am against. there are real fucking assholes out there, and i don’t know if i am one of them.
don’t touch people without their consent, and don’t be a fucking dickhead. everyone makes mistakes, something glass houses two in the bush gets the worm.
1 note
·
View note
Text
Derbycon 2019 – Confessions of an IT OT Marriage Counselor
Derbycon 2019 – Confessions of an IT OT Marriage Counselor
[ad_1]
I discuss the trials and tribulations of trying to bring IT cybersecurity and Operational Technology (ICS) teams together to tackle new threats.
[ad_2]
View On WordPress
0 notes