#cyber security whatsapp groups
Explore tagged Tumblr posts
Text
🔵 FRIDAY - ISRAEL REALTIME - Connecting to Israel in Realtime
Erev Shabbat - Parshat Pinchas - Numbers 25:11 - Aaron’s grandson Pinchas is rewarded for his act of zealotry in killing the Simeonite prince Zimri and the Midianite princess who was his paramour.
▪️ISRAEL REALTIME under attack… multiple hack attempts to take control of our WhatsApp groups. If posts turn weird or no posts, see links at bottom for alternatives.
▪️WITH THE OLYMPICS SCHEDULED TO START TONIGHT.. (Israel time) France hit with a major cyber attack disabling much of the national train service as well as arson attacks disabling numerous lines. Israeli team under heavy threat from Iranian groups.
▪️THE WHITE HOUSE SAYS.. from yesterday’s Netanyahu Biden meeting: Biden expressed the need to close the remaining gaps and reach a hostage deal as soon as possible. He also raised the humanitarian crisis in Gaza, the need to remove obstacles to the flow of humanitarian aid and the critical importance of protecting civilian lives during military operations.
.. The President also emphasized the commitment of the US to the security of Israel against the threats from Iran and its affiliates, including Hamas, Hezbollah and the Houthis.
.. VP to PM Netanyahu: Kamala Harris- "Let's get to the deal now"; "The two-state solution - the only way to a safe and Jewish democratic state"
▪️A HERO SOLDIER HAS FALLEN.. Moti Rave, 37, from Shani, fell in battle in Gaza. May his family be comforted among the mourners of Zion and Jerusalem, and may G-d avenge his blood!
.. 330 hero soldiers have fallen in the offensive against Hamas.
▪️MORE HOUTHI THREATS.. Military sources in Sana'a (Yemen) to the Lebanese Al-Akhbar newspaper: "Yemen's response to the Israeli attack will not be limited to one or two operations." (( Noting these guys love their propaganda, but they also tend to follow through and don’t seem to care at the cost. ))
▪️HAMAS ARRESTS.. a wave of arrests by Hamas against Fatah operatives throughout the Strip in recent days, with an emphasis on the northern part of the Strip, just a few days after the signing of the "Beijing Declaration" regarding Palestinian internal reconciliation between Fatah and Hamas.
▪️HAMAS DAMAGE? Palestinian sources to Reuters: "A communication network built by Hamas before the war was severely damaged. The loss of personnel and the destruction of the communication network meant that centralized decision-making collapsed."
▪️ECONOMY - GAS PRICE DROP.. gasoline prices expected to drop 17 agarot per liter, due to exchange rates and world oil prices.
🔸DEAL NEWS.. Reuters: Hamas rejects Israel's demand to check those returning to the northern Gaza Strip to make sure there are no terrorists among them (and to make sure there are no HOSTAGES among them, oh and no weapons.)
.. Suleiman Masveda: Netanyahu demands more live hostages in the first stage, contrary to the position of the security establishment who say "the conditions for the deal are ripe".
.. PM Netanyahu to the families of the abductees during the joint meeting with Biden: "I am not delaying anything. Within two days an updated proposal will be issued to Hamas"
♦️(Enemy report) The town of Ita al Sha'ab has been under artillery attack and by bombing - more than 75% of the houses are destroyed.
♦️IAF fighter jets, combat helicopters, and drones, struck some 45 targets across Gaza over the past day. The targets included terrorists, tunnel shafts, buildings used by terror groups, and rocket launchers previously used to attack the southern city of Be’er Sheva.
♦️COUNTER-TERROR OPS - KALKILYA, JENIN, JERICHO.. overnight.
⭕ US BASE IN IRAQ ATTACKED.. The Ein Al Asad air base was attacked last night with 4 rockets and a suicide drone.
⭕ HAMAS ROCKETS this morning at Yated, Nachal Oz.
12 notes
·
View notes
Text
Tuesday, October 8, 2024
Hurricane Milton strengthens into a Category 5 as Florida begins evacuations (AP) Milton rapidly strengthened into a Category 5 hurricane Monday in the Gulf of Mexico on a path toward Florida, threatening a dangerous storm surge in Tampa Bay, leading to evacuation orders and long gas lines, and lending more urgency to the cleanup from Hurricane Helene, which swamped the same stretch of coastline less than two weeks ago. The storm’s center could come ashore Wednesday in the Tampa Bay area, and it could remain a hurricane as it moves across central Florida toward the Atlantic Ocean, forecasters say.
Growing the debt (NPR) A new report has found that both Harris’ and Trump's economic plans would increase the national debt. According to the nonpartisan nonprofit Committee for Responsible Federal Budget, Trump's plan would add an estimated $7.5 trillion to the nation's debt over the next decade, while Harris' proposals would cost the government an estimated $3.5 trillion. The committee has cautioned that there could be a future fiscal crisis if politicians do not take more decisive action on the national debt.
Police seldom disclose use of facial recognition despite false arrests (Washington Post) Hundreds of Americans have been arrested after being connected to a crime by facial recognition software, a Washington Post investigation has found, but many never know it because police seldom disclose their use of the controversial technology. Police departments in 15 states provided The Post with rarely seen records documenting their use of facial recognition in more than 1,000 criminal investigations over the past four years. According to the arrest reports in those cases and interviews with people who were arrested, authorities routinely failed to inform defendants about their use of the software—denying them the opportunity to contest the results of an emerging technology that is prone to error, especially when identifying people of color.
Juvenile Cyber Criminals (WSJ) The February 2022 hack of AI chip-maker Nvidia was one of the strangest cases ever. Someone—or some group—had stolen the crown jewels from one of the world’s most important tech companies and then acted like a bunch of kids on Telegram. They said they’d stolen some “juicy ass source code,” and demanded that Nvidia make its products easier for videogame players to use. It turned out that the Nvidia hackers acted like kids because they were, in fact, kids. They’re part of a new cybersecurity community that has become a bigger and bigger problem for law enforcement over the past few years. Calling themselves the Com, the kids have moved from giving each other grief in online games to stealing cryptocurrency and extorting some of the world’s most important companies, including Microsoft, Samsung, Uber and Rockstar Games. One of these hackers was Arion Kurtaj. Last year, fearing Kurtaj would simply never stop hacking, a British judge ordered him confined to a secure mental-health ward until doctors deem him to no longer be a public danger. Kurtaj was 17 when he hacked Nvidia, but he was just 11 when he started his life of cybercrime. He’s now the most notorious member of the Com. Other members are often so young that they have little fear of incarceration. They’re also so destructive that it’s hard to predict what they will do when they break into a computer network. A few months before the Nvidia hack, Kurtaj and his associates had deleted Brazil’s database of Covid vaccinations.
Mexican mayor assassinated days after taking office (Reuters) The mayor of the capital of Mexico’s violence-plagued state of Guerrero was killed on Sunday less than a week after he took office, the state’s governor confirmed. Alejandro Arcos was killed just six days after he took office as mayor of the city of Chilpancingo, a city of around 280,000 people in southwestern Mexico. The official confirmation came after photos circulated on messaging app WhatsApp depicting a severed head on top of a pick-up truck, appearing to be that of Arcos. Guerrero has become one of the deadliest states for aspiring and elected public officials, as well as for journalists.
Freed Russian arms dealer Bout back in weapons business, WSJ reports (Reuters) Viktor Bout, the Russian arms dealer who was jailed in the United States and then swapped two years ago for the U.S. basketball star Brittney Griner, is back in international arms trade, the Wall Street Journal reported on Sunday. Citing an unnamed European security source and other anonymous sources familiar with the matter, the WSJ wrote that Bout, dubbed “the merchant of death” is trying to broker the sale of small arms to Yemen’s Houthi militants. “When Houthi emissaries went to Moscow in August to negotiate the purchase of $10 million worth of automatic weapons, they encountered a familiar face: the mustachioed Bout,” the newspaper reported, citing its sources. The potential arms transfers stop well short of the sale of Russian anti-ship or anti-air missiles that could pose a significant threat to the U.S. military’s efforts to protect international shipping from the Houthis’ attacks, it added. Bout was one of the world’s most wanted men prior to his 2008 arrest in Thailand on multiple charges related to arms trafficking. His notoriety was such that his life helped inspire a Hollywood film, 2005’s Lord of War, starring Nicolas Cage.
Ukraine’s Donbas Strategy: Retreat Slowly and Maximize Russia’s Losses (NYT) Throughout the year, Ukraine has lost a series of cities, towns and villages in its eastern Donbas region to Russia, typically withdrawing its troops after hard-fought battles that sometimes lasted for months. To outside observers, Ukraine’s slow but steady retreat from the Donbas region, the main theater of the war today, may seem to signal the beginning of the endgame, with Moscow firmly gaining the upper hand on the battlefield, leveraging its overwhelming advantage in manpower and firepower. But Ukrainian commanders and military experts dispute that, saying that a more crucial fight is unfolding in the region that goes beyond simple territorial gains and losses. It is now a war of attrition, they say, with each side trying to exhaust the other by inflicting maximum losses, hoping to break the enemy’s capacity and will to continue the war.
Water stress in the Middle East and North Africa (Rane Worldview) In recent years, water stress in the Middle East and North Africa has become a more acute threat to the stability of both individual states and the broader region amid a constant struggle for control and management of this increasingly scarce vital resource. Countries’ mismanagement of their water supplies over the decades has worsened the situation in the region, where the predominantly hot and dry climate already exacerbates water shortages. The rapid population growth many countries are experiencing has also heightened the demand for limited fresh water. Against this backdrop, access to water supplies has become an increasing driver of conflict between both states and non-state actors in the Middle East and North Africa, as well as a catalyst for social unrest.
U.S. Citizens in Lebanon Feel Abandoned by the State Department as Israel Invades (The Intercept) After Israel dropped more than 80 bombs, including American-made 2,000-lb bombs, on residential buildings in a suburb of Beirut, Hana Bechara, one of 86,000 U.S. citizens who live in Lebanon, decided it was time to leave. She reached out to the U.S. embassy in Beirut. As the strikes continue, Bechara said the response from the U.S. has been vague and unhelpful. State Department officials have sent her generic security alerts urging her to contact commercial airlines directly for flights out, while acknowledging that airlines were “at reduced capacity,” according to emails reviewed by The Intercept. The most recent email from the embassy sent Monday said they were unable to assist her family but offered to “help U.S. citizens and immediate family members leave Lebanon very soon” without further elaborating on a timeline or the type of assistance. (Meanwhile, the United Kingdom, Belgium, Canada, Bulgaria, and Cyprus have all begun to evacuate their citizens on charter flights or government planes.) “We, and the U.S. citizens in Palestine, are being treated differently than other U.S. citizens who are in way less danger than we are,” Bechara said. Bechara and many other Americans stuck in Lebanon have contrasted the State Department’s responses to the sense of urgency and level of assistance Americans in Israel received following the October 7 attacks. Within several days of the attacks, the U.S. Embassy in Jerusalem offered American citizens prearranged charter flights and boat rides to leave the country.
One Year After Oct. 7, Israel Sees a Future at War (WSJ) Weathering an Iranian missile assault, ignoring calls for a Gaza cease-fire, masterminding attacks against Hezbollah, targeting Houthi rebels in Yemen, rooting out militancy in the occupied West Bank and planning its next steps against Iran mark a shift in Israel’s security posture. For years, the military aimed for long stretches of peace that were only momentarily punctured by short conflicts with Palestinian militants. Much of Israel’s security establishment now believes this lay the groundwork for the Oct. 7 attack that killed 1,200 people and took another 250 hostage. Israel can no longer allow its enemies the time and space to build arsenals, many have come to believe. “Pre-emptive wars will be in the future part of the Israeli tool kit,” said Yaakov Amidror, a former Israeli national security adviser. Without seeking political and diplomatic solutions, “it’s a matter of endless war,” said Tamir Hayman, a former head of Israeli military intelligence and executive director of the Tel Aviv-based think tank Institute for National Security Studies.
‘Violence begets violence’ (Foreign Policy) Pope Francis said “the fuse of hatred” had been lit a year ago and “exploded in a spiral of violence—in the shameful inability of the international community and the most powerful countries to silence the weapons and put an end to the tragedy of war.” “The war that has raged over the past year continues to shatter lives and inflict profound human suffering for Israelis, Palestinians, and now the people of Lebanon,” said Tor Wennesland, the U.N. special coordinator for the Middle East peace process. “Violence begets violence, and in these moments of grief, we must reaffirm our commitment to peace.”
Gaza is in ruins (AP) The Gaza Strip is in ruins. There are hills of rubble where apartment blocks stood, and pools of sewage-tainted water spreading disease. City streets have been churned into dirt canyons and, in many places, the air is filled with the stench of unrecovered corpses. Israel’s yearlong offensive against Hamas, one of the deadliest and most destructive in recent history, has killed more than 41,000 people, a little over half of them women and children, according to local health officials (with another 97,000 other injured). With no end in sight to the war and no plan for the day after, it is impossible to say when—or even if—anything will be rebuilt. Even after the fighting stops, hundreds of thousands of people could be stuck living in squalid tent camps for years. Experts say reconstruction could take decades. The fighting left roughly a quarter of all structures in Gaza destroyed or severely damaged, according to a U.N. assessment in September based on satellite footage. The U.N. estimates the war has left some 40 million tons of debris and rubble in Gaza, enough to fill New York’s Central Park to a depth of eight meters (about 25 feet). It could take up to 15 years and nearly $650 million to clear it all away, it said. Gaza’s water and sanitation system has collapsed. More than 80% of its health facilities—and even more of its roads—are damaged or destroyed. Around 90% of Gaza’s 2.3 million people have been displaced by the war, often multiple times. Hundreds of thousands have crowded into sprawling tent camps near the coast with no electricity, running water or toilets. Hunger is widespread.
Deadly Marburg Virus Hits Rwanda’s Doctors and Nurses Hard (NYT) Rwanda’s fragile health care system could become overwhelmed by the deadly Marburg virus, doctors fear, because most of those currently infected are medical professionals, and some have already died. Since the first outbreak in the country last month, at least 30 medical workers have been infected, and at least four have died. Among the infected are two of the country’s scarce anesthesiologists. More medical staff members are isolated in hospital wards in the capital, Kigali. The health care system, with approximately 1,500 doctors and fewer than 40 anesthesiologists for a nation of just over 13 million people, could face significant strain.
2 notes
·
View notes
Text

TODAY (May 14), I'm on a livecast about AI AND ENSHITTIFICATION with TIM O'REILLY; on TOMORROW (May 15), I'm in NORTH HOLLYWOOD for a screening of STEPHANIE KELTON'S FINDING THE MONEY; FRIDAY (May 17), I'm at the INTERNET ARCHIVE in SAN FRANCISCO to keynote the 10th anniversary of the AUTHORS ALLIANCE.

#20yrsago England’s love affair with the utility bill https://web.archive.org/web/20040706124142/https://cede.blogspot.com/2004_05_01_cede_archive.html#108455091554008455
#20yrsago RIAA’s funny bookkeeping turns gains into losses https://web.archive.org/web/20040607052730/http://www.kensei-news.com/bizdev/publish/factoids_us/article_23374.shtml
#20yrsago Read this and understand the P2P wars https://papers.ssrn.com/sol3/papers.cfm?abstract_id=532882
#15yrsago Sarah Palin’s legal team doesn’t understand DNS https://www.huffpost.com/entry/crackhocom-sarah-palins-n_n_202417
#15yrsago Was 1971 the best year to be born a geek? https://www.raphkoster.com/2009/05/14/the-perfect-geek-age/
#15yrsago Charlie Stross on the future of gaming http://www.antipope.org/charlie/blog-static/2009/05/login_2009_keynote_gaming_in_t.html
#15yrsago UK chiropractors try to silence critic with libel claim https://gormano.blogspot.com/2009/05/two-things.html
#10yrsago Cable lobbyists strong-arm Congresscritters into signing anti-Net Neutrality petition https://web.archive.org/web/20140527030122/http://www.freepress.net/blog/2014/05/12/tell-congress-dont-sign-cable-industry-letter-against-real-net-neutrality
#10yrsago London property bubble examined https://timharford.com/2014/05/when-a-man-is-tired-of-london-house-prices/
#5yrsago A year after Meltdown and Spectre, security researchers are still announcing new serious risks from low-level chip operations https://www.wired.com/story/intel-mds-attack-speculative-execution-buffer/
#5yrsago Jury awards $2b to California couple who say Bayer’s Roundup weedkiller gave them cancer https://www.cnn.com/2019/05/14/business/bayer-roundup-verdict/index.html
#5yrsago AT&T promised it would create 7,000 jobs if Trump went through with its $3B tax-cut, but they cut 23,000 jobs instead https://arstechnica.com/tech-policy/2019/05/att-promised-7000-new-jobs-to-get-tax-break-it-cut-23000-jobs-instead/
#5yrsago DOJ accuses Verizon and AT&T employees of participating in SIM-swap identity theft crimes https://www.vice.com/en/article/d3n3am/att-and-verizon-employees-charged-sim-swapping-criminal-ring
#5yrsago Collecting user data is a competitive disadvantage https://a16z.com/the-empty-promise-of-data-moats/
#5yrsago Three years after the Umbrella Revolution, Hong Kong has its own Extinction Rebellion chapter https://www.scmp.com/news/hong-kong/health-environment/article/3010050/hong-kongs-new-extinction-rebellion-chapter-looks
#5yrsago Lawyer involved in suits against Israel’s most notorious cyber-arms dealer targeted by its weapons, delivered through a terrifying Whatsapp vulnerability https://www.nytimes.com/2019/05/13/technology/nso-group-whatsapp-spying.html
#5yrsago The New York Times on Carl Malamud and his tireless battle to make the law free for all to read https://www.nytimes.com/2019/05/13/us/politics/georgia-official-code-copyright.html
#1yrago Google’s AI Hype Circle https://pluralistic.net/2023/05/14/googles-ai-hype-circle/
5 notes
·
View notes
Text

Leaders of the top telecommunications companies were summoned to the White House on Friday to discuss a security problem that has been roiling the government: how to expel Chinese hackers from the deepest corners of the nation’s communications networks.
The meeting in the Situation Room came after weeks in which officials grew increasingly alarmed by what they had uncovered about the hack.
They now believe the hackers from a group called “Salt Typhoon,” closely linked to China’s Ministry of State Security, were lurking undetected inside the networks of the biggest American telecommunications firms for more than a year.
They have learned that the Chinese hackers got a nearly complete list of phone numbers the Justice Department monitors in its “lawful intercept” system, which places wiretaps on people suspected of committing crimes or spying, usually after a warrant is issued.
While officials do not believe the Chinese listened to those calls, the hackers were likely able to combine the phone numbers with geolocation data to create a detailed intelligence picture of who was being surveilled.
As a result, officials said, the penetration almost certainly gave China a road map to discover which of China’s spies the United States has identified and which they have missed.
This article is based on conversations with more than a dozen U.S. and industry officials who spoke on the condition that their names not be used because of the sensitive intelligence assessments of the hack.
Initially, officials thought the hack was limited to the region around Washington. But they have now found evidence of China’s access all around the country, exploiting old or weak entry points in the cellphone network.
Officials now believe that the hack has gone beyond phone companies, to internet service providers, potentially allowing the Chinese to read some email.
While some Americans’ phone calls and emails may have been compromised by the Chinese, officials emphasized that encrypted applications, like WhatsApp and Signal, were not penetrated. In addition, messages sent within Apple’s own network were also safe.
And the discovery of the specific targeting of senior national security officials, and some political leaders — including President-elect Donald J. Trump and Vice President-elect JD Vance — led the F.B.I. and other officials to conclude that the Salt Typhoon hackers were so deep in the system that they could actually listen in to some conversations and read some unencrypted text messages.
“The sophistication was stunning,’’ said Senator Mark Warner, the Virginia Democrat who is chairman of the Senate Intelligence Committee. He said his biggest concern — one that dominated the Situation Room meeting at the White House — was the conclusion that “the barn door is still wide open.” A White House statement released Friday night gave no details of the breach or any hint of the tensions over how to deal with it, but said the meeting on Friday was led by Jake Sullivan, the national security adviser, and one of his deputies, Anne Neuberger, who oversees cyber- and emerging technologies.
The U.S. communications system is built on a mishmash of aging systems, which made it far easier for the Chinese to break into upward of ten telecommunications companies.
At the White House meeting, the message delivered by top American intelligence and national security officials was that despite the aging technology, the telecommunications companies needed to help find a permanent way to keep Beijing’s agents out of the systems. Some officials and others briefed on the hack say that is no small task, and that making the necessary fixes could create painful network outages for consumers.
Critical parts of the American telecommunications system are too old to upgrade with modern cybersecurity protections. Some parts of the system date to the late 1970s or early 1980s, when landlines, not cellphones, dominated the network. One participant in the meeting said the only solution to the problem was “ripping out and replacing whole sections of the networks,” a process the companies have been slow to invest in.
The executives who attended the meeting included Verizon’s top leader, Hans Vestberg, and AT&T’s top executive, John T. Stankey. But T-Mobile’s chief executive, Mike Sievert, who had initially doubted that the company had been compromised by the Chinese — then discovered it had been — sent a deputy.
The meeting came as arguments have begun to break out over who was to blame — the telecommunications firms, their regulators or American intelligence agencies — for a hack whose stealth and depth has shaken even veterans of America’s two decades of cyberconflict with China, Russia, Iran and North Korea.
In recent days government officials have become increasingly vocal in blaming the firms for being too slow to update key nodes of their networks.
In the days leading up to the meeting at the White House, American investigators and national security officials said parts of the telecommunications firms’ systems were not protected with basic “multifactor authentication.” That is the same technology that has become a staple of everyday life for consumers, who have grown accustomed to having a cellphone scan their face, or receiving a six-digit text message before they can access financial accounts or sensitive emails.
The hack was considered so severe that President Biden took it up directly with President Xi Jinping of China when they met in Peru last weekend, according to Mr. Sullivan, Mr. Biden’s national security adviser. “The issue of the hack of American telecommunications providers did come up,” Mr. Sullivan told reporters, though he declined to provide details.
There are limits to how far the United States can press its case with China. So far, the Chinese hack appears to involve only surveillance. That is something that the United States does regularly to Chinese telecommunications companies and is a form of espionage considered fair game as the two superpowers navigate a new, higher-stakes era using updated spy technology.
The documents revealed 11 years ago by Edward Snowden, a former contractor for the National Security Agency, revealed extensive efforts by the United States to get into the telecommunications systems and equipment of leading Chinese makers.
But the Chinese showed both remarkable ingenuity and patience — and a willingness to spend heavily to pierce American systems.
“I’d have to say the Chinese have matched, or exceeded, what we can do — and we didn’t see this one coming,” said one senior American official with years of experience in the intelligence community, declining to speak on the record about a classified investigation.
Years of Attacks
It was a dozen years ago that the scope of China’s cyberambitions were made clear by the exposure of Unit 61398, a hacking operation run by the People’s Liberation Army from a 12-story office tower on the road to the Shanghai airport. Studies found that the targets were often companies focused on critical infrastructure: the electrical power grid, gas lines and water systems. The Defense and State Departments were also particular targets.
A few years later, the United States belatedly discovered that China’s spy agency had stolen 22.5 million security clearance files from the Office of Personnel Management.
The Obama administration condemned the hack and what now appear to be related thefts of medical and travel records. Visiting Washington in September, 2015, Mr. Xi promised to abide by new limits on espionage. For a few months, the accord stuck, and the volume of attacks diminished.
But by the time President Barack Obama left office, it was clear that China’s hacking operations had shifted from its military units to its intelligence services, which work with greater stealth. And China’s hackers began focusing on getting inside the telecommunication networks, knowing that American spy agencies are barred, by law, from monitoring communications facilities on American soil.
A Warning From Microsoft
The telecommunications companies might still be in the dark about the most recent hack, officials say, had Microsoft’s threat researchers not seen some anomalies, including data on sites used by Salt Typhoon that trace back to nodes on the networks of Verizon, AT&T and other firms. They told the companies, and the government, which launched a secret investigation this summer.
When The Wall Street Journal first reported on elements of the hack, American investigators say, the Chinese intruders receded, making it more difficult to determine what exactly the hackers had done. But, officials, said investigators are looking through breadcrumbs left by the hackers and believe, with time, they will learn more about what they gained access to and what they did not see.
The hack prompted such alarm within the F.B.I. that field offices were told to check if informants had been potentially compromised and, if necessary, take steps to ensure their safety, such as developing cover stories or getting new phones. In particular, F.B.I. officials were concerned that agents who repeatedly contacted informants using a bureau phone could have left them exposed because of the suspicious pattern of calls.
A similar hacking technique was successfully used against companies in Taiwan, which is a frequent target of espionage from China, according to people familiar with the case. Other elements of the hack had echoes of techniques used against India.
But officials said the operations against Taiwan and India were different enough from the Salt Typhoon operation that it would not have been a clear warning to the United States.
In addition to calling in the telecom officials, the White House has already organized a task force to assess the damage, and a newly created cyberinvestigations board has been ordered to identify the failures and the system’s vulnerabilities.
The Biden administration has said very little about the attack. Much of the resistance came from the Justice Department and the F.B.I., which did not want to upend their own investigations. While the telecommunications firms knew about the intrusion, the public statements put out by the F.B.I. and the Cybersecurity and Infrastructure Security Agency contained such sparse detail that consumers would have no way of assessing whether their own conversations were at risk.
One senior official deeply involved in the matter said the idea that the U.S. telecommunications system was so vulnerable was deeply embarrassing. But with less than two months until Mr. Biden leaves office, officials said they had no idea whether Mr. Trump’s national security team, which so far has named no officials responsible for cyber offense or defense to senior posts, would press for long-term changes in the system.
https://www.nytimes.com/2024/11/22/us/politics/chinese-hack-telecom-white-house.html
0 notes
Text
Troop Messenger vs Telegram: Why You Should Consider Switching
Are you looking for Telegram alternatives? Then read this blog to discover alternative messaging platforms and get a quick overview.
Troop Messenger
Since Telegram is used by a few start-ups and small enterprises, I figured Troop Messenger and others could be added to the list. Troop Messenger is undeniably more than a Telegram alternative. Troop Messenger offers a lot of features compared to Telegram, which is far superior in terms of providing quality. For instance, Troop Messenger groups will have great advantages compared to Telegram chatting groups such as admin super controls, advanced search filters, screen sharing within group calling, and so on.
One of the encrypted chat programs on the list is Troop Messenger, and it's possible that you've already used the safest one. Due to its superior security features, political parties utilise it as their political campaign software, and the defence agencies of a few strong nations employ it for defence collaboration services. You can therefore gauge the tool's security. There aren't many products like Troop Messenger available on the market that can be supplied via all of the main delivery models, including chat APIs and SDKs, on-premise, SaaS, etc.

Apart from chat basic functions, Troop Messenger is a complete team collaboration tool that provides its users with all the features such as audio/video conference, screen sharing, remote access, live location tracking, and so on.
Do you know that Troop Messenger has a Burnout feature similar to Telegram’s secret chat? Teams, Defense agencies, and government officials can use it to convey classified information that no one else on the planet, including service providers, has access to.
Telegram is a cloud-based instant messaging software that is freeware and cross-platform. End-to-end encrypted video calling, file sharing, VoIP, and other functions are also available. Telegram's initial release date was August 14, 2013, for iOS and October 2013 for Android.
Nikolai and Pavel Durov, who were also the inventors of the Russian online social site RK, launched Telegram in 2013.
Telegram's data is dispersed over five data centers in various locations around the world, including the operations center in Dubai, United Arab Emirates.
After WhatsApp announced its privacy policy in January 2021, 25 million new users joined Telegram, according to Telegram creator Pavel Durov. This equates to almost 8.33 million new users signing up every day. Telegram added over 100 million new users in just the month of January.
Telegram quickly made a name for itself as a competitive WhatsApp substitute. A few publications claim that Telegram currently has over 550 million active members and ranks in the top 10 most popular social networks globally in terms of download volume. Businesses were compelled by Telegram's popularity to get their app developers to produce an ideal substitute.
Why is Telegram not recommended?
Even though a few companies use it, Telegram shouldn't be on your list of chat apps for your team or place of business. It wouldn't meet all workplace requirements because it's a social messenger unless you wanted to limit it to phone calls, conversations, and file sharing. Telegram will merely function as an additional messenger, similar to FaceTime, WhatsApp, and the like. Nevertheless, a strong team communication tool can enhance teamwork and increase productivity at work, something that Telegram apps are unable to accomplish.
Check Point issued a Telegram warning in 2021, that "it tracked 130 cyber attacks that used malware managed over Telegram by attackers. Even though Telegram is not installed or being used, it allows hackers to send malicious commands and operations remotely via the instant messaging app."
What are the disadvantages of Telegram?
Here are some of Telegram's drawbacks that may make you want to uninstall it and look out for Telegram alternatives.
Telegram collects users’ contact details and metadata
If the articles are to be believed, Telegram is not an end-to-end encrypted
It has limited support
Since Telegram has a 1.5 GB file size limit, illegally downloaded movies are being mixed in with adult content that is not appropriate for children.
Telegram also allows attackers to access hacked machines from practically anywhere on the planet using their mobile devices.
Due to some operational advantages, cybercriminals are increasingly using Telegram as part of their activities.
Attackers can simply exfiltrate data from victims' PCs or transfer new malicious files to infected machines owing to Telegram's unique communication features.
Observing the above-mentioned segmentations, on the contrary, users have huge benefits from utilizing Telegram as their social chat app, which any app like Telegram may not offer.
If you believe that we are being subjectively biased by pointing out Telegram's drawbacks, further information will show just how objective we are.
How have users benefited from Telegram?
Do you know that with 700 million monthly active users, Telegram has ascended to become one of the top 5 downloaded apps globally in 2022? According to Telegram, it has never spent money on advertisements; instead, it was users who shared their positive experiences with other users (friends, relatives, acquaintances, colleagues, and others). As a result, they were persuaded to download it.
In light of this, Telegram introduced a premium plan that gives users access to extra premium features while allowing free use.
Telegram Premium
Users will have access to increased limits, better chat management, 4 GB file uploads, faster downloads, exclusive stickers and reactions, and other benefits with Telegram Premium. Despite this, non-premium users will still have access to all current capabilities. In fact, they may even be granted access to select privileges, such as
Ability to download large documents.
Tap to increase the counts on premium reactions that have already been added to a message.
Can view the stickers that Premium users have sent.
Some of the enticing features that premium users can access are
1. Chat Management
New tools in Telegram Premium help you organize your conversation list, such as setting your default chat folder to ensure that the app always starts on Unread instead of All Chats.
Indeed, subscribers can keep the busiest chat lists organized by enabling a Privacy and Security feature that automatically archives and mutes new chats.
2. Animated Profile Pictures
Everyone using the app can see the animated profile videos of premium users in chats and the chat list. In addition, premium users can demonstrate their fresh look to the world or showcase their creativity with a unique looping animation.
3. 4GB Uploads
Those who use Telegram Premium can now send files up to 4 GB in size, which provides sufficient space for 4 hours of 1080p video or 18 days of high-quality audio. At the same time, non-premium users can indeed upload files and media up to 2 GB in size and take advantage of unlimited free storage in the Telegram Cloud.
4. Faster Downloads
Media and files can be downloaded as quickly as possible for premium subscribers. Users get limitless access to their cloud storage and can access everything as quickly as their network can accommodate.
5. Doubled Limits
Doubled limitations are available to premium users for everything in the app, including:
Can add the fourth account,
Able to follow 1000 channels,
Create up to 20 chat folders, each containing a maximum of 200 chats,
Add ten chats to the main list,
Ten favorite stickers may be saved,
Ability to write a longer bio and add a link to it.
6. Voice-To-Text
For those occasions when you cannot listen but still wish to see what it says, voice messages can be converted to text. You can give transcriptions a rating to help them get better.
7. Unique Stickers
There are dozens of stickers available for Premium users to send in any chat to add extra emotion and expressive effects to engage the recipients while still making them visible to all users. These stickers are meant to impress, especially millennials, and feature full-screen animations. In contrast to Telegram alternatives, the Telegram team of artists will update a premium sticker collection every month.
8. Premium Badges
In the chat list, chat headers, and member lists in groups, all premium users have a special badge that says "Premium" next to their names, signifying that they are a member of the club that gets first access to unique features.
9. Premium App Icons
Premium customers have the option to add new icons to their Home Screen in an attempt to make it more compatible with their personality or wallpaper.
Telegram guarantees its users that it will continue to implement free features that are accessible to everyone and that it will do it more quickly than any other app similar to Telegram.
Conclusion
If the encryption is disregarded, Telegram can serve as a popular social media chat software, but it is a terrible tool for team and corporate interactions. Whereas hackers are using Telegram data to their advantage, WhatsApp is only gathering commercial data from particular companies. Telegram needs to start prioritising security, or else users will begin to migrate to other messaging apps.
0 notes
Text
Top Open-Source Solutions for Building a WhatsApp Clone

In today's digital panorama, messaging apps are an essential part of every day communication. From personal chats to commercial company conversations, customers pick out short, real-time messaging over the traditional method. WhatsApp stands proud as one of the most famous messaging systems globally, but what if you desired to create your very personal version of it? Thanks to open-deliver technology, constructing a WhatsApp clone isn't the simplest viable but additionally extra low-fee and customizable than you may think. In this put-up, we are capable of discovering the top open-supply answers for constructing a WhatsApp clone and the way you may leverage WhatsApp clone delivery code to kickstart your assignment.
What is a WhatsApp Clone, and Why Use Open-Source Solutions?
A WhatsApp clone refers to a messaging application that replicates the talents of WhatsApp, consisting of immediate messaging, voice calls, video calls, and media sharing. These clones are built using a correctly to be had supply code, frequently open-supply, which lets in builders to alter and tailor the software to their precise needs.
But why pick out open-supply answers? There are numerous motives. Open-supply WhatsApp clone delivery code gives flexibility, which is treasured whilst building a customized product. Additionally, the price-saving aspect of using open-source is sizable, as you don’t want to invest intently in developing the utility from scratch. Moreover, many open-deliver initiatives are supported via a network of developers, which guarantees ordinary updates and security patches.
Key Features to Look for in WhatsApp Clone Source Code
When selecting a WhatsApp clone delivery code, it's crucial to assess sure center features. After all, a WhatsApp clone must replicate now not just the primary chat functionalities but the average experience.
Messaging and Communication
At the coronary heart of each messaging app is its capacity to facilitate seamless and real-time verbal exchange. Look for open-supply answers that assist right away messaging, multimedia sharing, and message popularity indicators, which include "despatched," "delivered," and "read."
Voice and Video Calling
To compete with WhatsApp, your clone must consist of voice and video calling abilities. Users anticipate a dependable and fantastic calling revel in, so any WhatsApp clone Android supply code has to offer peer-to-peer calling alternatives, group calls, and contact encryption.
Security and Privacy
In the age of cyber threats, security cannot be left out. WhatsApp clone supply code must incorporate stop-to-forestall encryption to make certain that messages and calls are strong. Additionally, preserve in thoughts functions, which include issue authentication (2FA) and stable login alternatives to guard patron statistics.
Top Open-Source WhatsApp Clone Source Code Solutions
To help you get started out in your WhatsApp clone adventure, right here are a number of the pinnacle open-supply systems that offer robust, scalable, and feature-wealthy WhatsApp clone delivery codes.
Signal Private Messenger (WhatsApp Clone Android Source Code Alternative)
Signal is a tremendous open-supply possibility that shares lots of WhatsApp’s privateness functions. Signal’s code is available on GitHub, allowing builders to leverage its encrypted messaging and strong calling functionalities to assemble their own WhatsApp clone. The WhatsApp clone Android supply code derived from Signal offers a brilliant basis, especially for developers focused on privacy and safety.
Matrix.Org
Matrix is a decentralized protocol for real-time communication. Unlike centralized structures, Matrix is designed for open communication, offering interoperability with different platforms. Matrix is an effective foundation for a WhatsApp clone, as its WhatsApp clone supply code consists of secure messaging, voice, and video calling, similarly to file sharing abilities. Its open-supply nature additionally ensures that builders can actually customize the software in line with their particular needs.
Rocket.Chat
Although Rocket.Chat is regularly taken into consideration as a crew collaboration tool, it is able to be adapted as a WhatsApp clone Android deliver code possibility. This platform offers a whole open-source verbal exchange platform, which consists of immediate messaging, organization chats, video calls, and stable report sharing. Rocket. Chat additionally functions as a circulate-platform aid, making it an amazing choice for builders seeking to assemble a multi-device WhatsApp clone.
Zulip
Zulip is an open-supply chat platform that combines actual-time chat with threaded conversations. While it has become to start with designed for crew collaboration, Zulip’s open-supply code may be tailored to construct a WhatsApp clone. Its real-time messaging, coupled with a robust community manual, makes it a possible preference for developers. Zulip’s interface is intuitive, and its shape allows for the addition of functions, which include media sharing, calls, and encryption, important for any WhatsApp clone source code.
Chatwoot
Chatwoot is an open-supply platform designed for customer support messaging, but its actual-time chat functionality makes it a capacity base for a WhatsApp clone. Like the opportunity solutions, Chatwoot supports messaging, file sharing, and actual-time notifications. Its code is freely available on GitHub, permitting developers to alter it right into a beneficial WhatsApp clone.
Customizing Your WhatsApp Clone Using Open-Source Code
Once you've selected the proper WhatsApp clone source code, the subsequent step is customization. Open-source answers allow you to tweak the UI, functions, and common behavior of your software to better fit your target market. Here are a few components to recollect while customizing your WhatsApp clone:
User Interface Customization
First impressions are the whole thing. Customize the character interface to create a unique appearance and sense in your app. You can redecorate chat monitors, buttons, and icons to in shape your emblem’s identification.
Adding Additional Features
While the number one capabilities of a WhatsApp clone are critical, bear in mind advanced abilties like price integration, bot aid, or multi-device functionality. These introduced features can set your app apart than special clones and enhance what people revel in.
Security Enhancements
Even despite the fact that open-supply WhatsApp clone source code frequently consists of protection competencies like encryption, you may add in addition layers of protection. For example, troublesome authentication, anti-unsolicited mail filters, and more superb encryption algorithms are precious additions.
How to Get Started with WhatsApp Clone Android Source Code
To get began, follow those steps:
Choose Your Open-Source Solution: Based on the features you want, select the proper open-source platform (like Matrix, Signal, or Rocket.Chat).
Set Up Your Development Environment: Install the important dependencies, which include a code editor, Android SDK, and essential libraries, to start running with the WhatsApp clone Android supply code.
Customize the Source Code: Modify the design, add capabilities, and alter the backend to align at the side of your app’s desires.
Test Your Application: Ensure the app is PC virus-free and protection capabilities feature correctly.
Deploy: Once tested, set up your app to the Google Play Store or make it to be had for customers to down load right away.
Conclusion
Building a WhatsApp clone is now not an insurmountable undertaking thanks to the supply of an open-supply WhatsApp clone delivery code. Platforms like Signal, Matrix, and Rocket. Chat provides the right basis to expand a function-rich, secure, and scalable messaging app tailored to your specific needs. Whether you are targeted at Android customers or seeking to set up throughout a couple of structures, those solutions will help you attain your goals.
At AIS Technolabs, we concentrate on constructing customizable communication apps. If you're trying to construct a WhatsApp clone or need assistance in choosing the proper supply code, contact us these days to get started.
FAQ
1. Is it prison to assemble a WhatsApp clone?
Yes, it is criminal so long as you don’t violate WhatsApp’s phrases of service or highbrow assets. Using open-source answers to construct a messaging app with similar features is perfectly appropriate.
2. Can I customize the WhatsApp clone delivery code?
Absolutely! One of the important blessings of using open-source WhatsApp clone source code is that it's certainly customizable.
3. How steady are WhatsApp clone apps constructed with the use of open-deliver solutions?
The protection of your WhatsApp clone relies upon the encryption and safety capabilities you put in force. Most open-deliver answers provide give up-to-stop encryption; however, additional layers of protection are encouraged.
4. Can I use open-supply WhatsApp clone Android source code for iOS apps?
Many open-deliver platforms assist pass-platform development, which means you can use the same codebase for each Android and iOS, with some changes.
Blog Source: https://www.knockinglive.com/top-open-source-solutions-for-building-a-whatsapp-clone/
0 notes
Text
does vpn work for whatsapp
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work for whatsapp
VPN for WhatsApp encryption
In today's digital age, privacy and security have become paramount concerns, especially when it comes to communication apps like WhatsApp. With the increasing prevalence of cyber threats and surveillance, many users are turning to VPNs (Virtual Private Networks) to enhance their online privacy and protect their sensitive data.
A VPN works by encrypting your internet connection and routing it through a secure server, effectively masking your IP address and making it difficult for third parties to intercept your online activity. When it comes to WhatsApp, using a VPN can offer several benefits, particularly in terms of encryption.
WhatsApp already uses end-to-end encryption by default, meaning that messages sent between users are scrambled and can only be deciphered by the intended recipient. However, using a VPN adds an extra layer of security by encrypting your entire internet connection, including the data exchanged between your device and WhatsApp's servers.
By using a VPN for WhatsApp encryption, users can further safeguard their conversations from prying eyes, whether it be hackers, government surveillance, or even the WhatsApp itself. This is particularly important for individuals who may live in countries with strict censorship laws or those who frequently connect to public Wi-Fi networks, which are often vulnerable to cyber attacks.
Furthermore, a VPN can also help bypass geo-restrictions and access WhatsApp in regions where it may be blocked or restricted. This ensures that users can stay connected with friends, family, and colleagues regardless of their location, without compromising on privacy or security.
In conclusion, leveraging a VPN for WhatsApp encryption is a proactive step towards enhancing online privacy and protecting sensitive conversations. By encrypting your internet connection, you can enjoy peace of mind knowing that your communications are secure and inaccessible to unauthorized parties.
Virtual private network messaging
A virtual private network (VPN) messaging service refers to the use of a VPN to enable secure, private communication over the internet. VPN messaging allows users to send messages, participate in group chats, share files, and make voice or video calls while ensuring that their communication remains encrypted and protected from prying eyes.
By using a VPN for messaging, users can enjoy enhanced privacy and security compared to traditional messaging services. VPNs create a secure tunnel between the user's device and the VPN server, encrypting all data that passes through it. This encryption makes it extremely difficult for hackers, government agencies, or internet service providers to intercept or access the messages being sent and received.
Additionally, VPN messaging services often provide features such as anonymous registration, self-destructing messages, and end-to-end encryption to further safeguard users' privacy. These features ensure that even the VPN service provider cannot access the contents of the messages sent through their platform.
Businesses and individuals who prioritize confidentiality and data security can benefit significantly from using a VPN messaging service. Whether discussing sensitive business matters, exchanging personal information, or simply seeking to maintain online privacy, VPN messaging offers a reliable solution for secure communication.
In conclusion, VPN messaging provides a secure and private platform for individuals and organizations to communicate online without the fear of their messages being intercepted or compromised. By utilizing a VPN for messaging, users can enjoy peace of mind knowing that their conversations remain confidential and protected from external threats.
Secure messaging apps
In today's digital age, where privacy concerns are paramount, secure messaging apps have become indispensable tools for individuals and businesses alike. These apps offer end-to-end encryption, ensuring that only the sender and receiver can access the content of their messages, making them virtually impenetrable to outside threats.
One of the key features of secure messaging apps is their ability to safeguard sensitive information from hackers, government surveillance, and other prying eyes. By encrypting messages at both ends of the communication, these apps prevent unauthorized access, providing users with peace of mind that their conversations remain private and secure.
Furthermore, secure messaging apps often come with additional security features such as self-destructing messages, which automatically delete themselves after a certain period, further minimizing the risk of sensitive information falling into the wrong hands.
For businesses, secure messaging apps offer a secure platform for internal communication, allowing employees to exchange sensitive information without fear of interception. This is particularly important in industries where confidentiality is crucial, such as finance, healthcare, and legal services.
Moreover, secure messaging apps are increasingly being used for external communication with clients and partners, offering a safe and reliable means of sharing confidential documents and discussing sensitive matters.
Overall, secure messaging apps play a vital role in protecting the privacy and security of individuals and businesses in an increasingly interconnected world. By utilizing these apps, users can communicate with confidence, knowing that their conversations are shielded from prying eyes and potential threats.
WhatsApp privacy protection
Title: Safeguarding Your Privacy on WhatsApp: Essential Tips and Practices
In an era where digital privacy is increasingly at risk, safeguarding your personal information on messaging platforms like WhatsApp has become paramount. With its massive user base and wide-ranging capabilities, WhatsApp is a prime target for privacy breaches and data misuse. However, by implementing a few key strategies and understanding the platform's features, users can enhance their privacy protection significantly.
One of the fundamental aspects of preserving privacy on WhatsApp is managing your account settings wisely. Start by enabling two-factor authentication, adding an extra layer of security to your account. This feature requires you to enter a unique PIN whenever you log in, preventing unauthorized access even if someone obtains your phone number.
Furthermore, exercise caution when sharing personal information in chats and group conversations. Avoid divulging sensitive details such as financial information or login credentials, especially in public or unknown groups. Additionally, be wary of unsolicited messages or requests from unknown contacts, as they could be attempts at phishing or social engineering attacks.
WhatsApp also offers robust privacy features to help users control their information. Utilize options like blocking contacts, hiding your "last seen" status, and restricting who can view your profile picture and status updates. Furthermore, regularly review and adjust your privacy settings to ensure they align with your preferences and comfort level.
Lastly, stay informed about WhatsApp's privacy policies and any updates or changes to its terms of service. Being aware of how your data is collected, stored, and used by the platform can empower you to make informed decisions about your privacy.
By implementing these proactive measures and staying vigilant, users can enjoy a safer and more secure experience on WhatsApp, protecting their personal information from potential threats and intrusions. Remember, when it comes to privacy, prevention is always better than remediation.
VPN for messaging apps
A Virtual Private Network (VPN) is a popular tool that encrypts your internet connection to provide you with online privacy and anonymity. When it comes to messaging apps, using a VPN can offer an extra layer of security and privacy by hiding your IP address and encrypting your communication.
One of the main benefits of using a VPN for messaging apps is the ability to bypass censorship and access restricted content. In countries where certain messaging apps are blocked or monitored, a VPN can help you securely connect to servers in different locations, allowing you to communicate freely without the fear of eavesdropping.
Moreover, a VPN can protect your sensitive data from hackers and cybercriminals when using messaging apps on public Wi-Fi networks. By encrypting your internet traffic, a VPN prevents unauthorized access to your conversations, ensuring that your personal information remains secure at all times.
Another advantage of using a VPN for messaging apps is the ability to overcome geo-restrictions. Some messaging platforms may limit access to certain features or content based on your location. By using a VPN to mask your IP address and appear as though you are browsing from a different country, you can unlock additional functionalities and enjoy a more seamless messaging experience.
In conclusion, incorporating a VPN into your messaging app usage can enhance your online security and privacy, enabling you to communicate freely and securely without restrictions or concerns about your data being compromised.
0 notes
Text
Mobile Spy App: A Silent Guardian Against Cyber Bullying

In the ever-evolving digital landscape, where technological advancements pave the way for convenience, communication, and connection, there's an unfortunate dark side that often goes unnoticed – cyberbullying. The rise of online harassment and bullying poses a serious threat to the well-being of individuals, especially the younger generation who are more exposed to the digital realm. In this challenging scenario, a mobile spy app emerges as a silent guardian, providing a shield against the perils of cyberbullying.
Understanding the Need for Vigilance
As the prevalence of smartphones continues to grow, so does the potential for cyberbullying. It's crucial for parents, guardians, and responsible adults to stay vigilant and proactive in protecting their loved ones. This is where the mobile spy app becomes an indispensable tool, offering features like a hidden call recorder and WhatsApp spy app functionality to keep a close eye on digital interactions.
The Power of Mobile Spy Apps
A mobile spy app, often dubbed as a spy phone app or Android spy app, operates discreetly in the background, monitoring and recording various activities on the target device. While the term "spy" may sound intrusive, the intention behind these apps is to promote safety and awareness rather than invasion of privacy. Let's delve into the key features that make these apps a potent ally against cyberbullying.
1. Hidden Call Recorder:
One of the core functionalities of a mobile spy app is the hidden call recorder. This feature allows users to discreetly record incoming and outgoing calls on the target device. In the context of cyberbullying, this becomes a valuable tool to listen to conversations and detect any signs of harassment or intimidation.
2. WhatsApp Spy App:
With the increasing popularity of messaging apps, cyberbullies often exploit platforms like WhatsApp to torment their victims. A dedicated WhatsApp spy app integrated into the mobile spy app enables users to monitor chat conversations, multimedia exchanges, and group interactions, providing insights into potential bullying instances.
3. Comprehensive Monitoring:
Beyond specific features like call recording and WhatsApp monitoring, a robust spy app offers comprehensive surveillance. This includes tracking text messages, browsing history, app usage, and even the device's location. This holistic approach ensures that no aspect of digital activity goes unnoticed.
Striking the Right Balance
While the use of a mobile spy app is motivated by the need to protect against cyberbullying, it's essential to strike a balance between vigilance and privacy. Open communication with the individual being monitored, especially in the case of minors, is paramount. The goal is to create a secure digital environment without compromising trust.
Conclusion
In the face of the growing menace of cyberbullying, a mobile spy app emerges as a silent guardian, offering a shield against digital threats. The incorporation of features like a hidden call recorder and WhatsApp spy app functionality provides a proactive means of monitoring and addressing potential issues. By embracing the power of technology responsibly, we can create a safer digital space for everyone, especially the vulnerable members of our community.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
1 note
·
View note
Text
Increase in cybercrime results in India Digital Forensic Market to rise, with an expected CAGR of ~16% by 2028
With the rise in digital threats and cybercrimes, India Digital Forensic Market makes successive changes like integration of Artificial Intelligence, and marking its overall growth.
STORY OUTLINE
Using techniques like Data Recovery, Log Analysis and more, India Digital Forensic Market enhances its Computer Forensics.
Upgrades towards Network and Mobile Forensics are improving in cyber threats prevention, marking its increase in efficiency and security.
With the incorporation of Cloud Based services, advanced methods and easy to use tools are improving the market’s workforce.
Integration of Artificial Intelligence (AI) and Machine Learning (ML) has made an impact in real time monitoring and error fixation.
Click to know more about the major players of this market
1. Using techniques like Data Recovery, Log Analysis, and more, India Digital Forensic Market enhances its Computer Forensics.
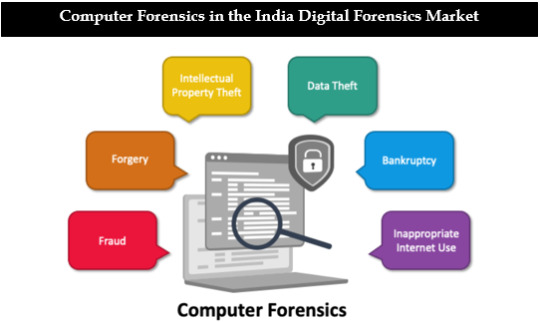
Indian Computer Emergency Response Team (CERT-In), plays a pivotal role in coordinating Incident Response and supervising cybersecurity and digital forensics.
National Cyber Coordination Center (NCCC) is a government initiative which primarily focuses on monitoring of ongoing cyber threats, and provides intelligence to various companies.
After the ATM Skimming case and Barkha Dutt’s Twitter Hack, the need for better and robust digital forensics has led to the rise of data security and privacy.
With the Digital India Initiative, India is soon to be transformed into a digitally empowered nation, having top notch digital devices and skilled professionals to look out for cyber threats.
According to Ken Research, the India Digital Forensics Market has made successive changes and plans to undergo larger changes in order to make progress and rise to the challenge of rising cybersecurity threats. With advancements in technology and focusing on end-user industry, leading to a growth with an expected CAGR of ~16% by 2028.
2. Upgrades towards Network and Mobile Forensics are improving in cyber threats prevention, marking its increase in efficiency and security.
Click to know more about the Digital Forensics Market
Deployment of the State Police Cyber Crime Units has led to the separate monitoring of the mobile related cyber threats like mobile application hack etc.
After the WhatsApp Hacks and Phishing attacks, enhancements to specific areas has been made with enhanced identification of attack vectors, recovering evidence and more.
Both CERT-IN and NCCC has tremendous availabilities of threat detection, incident response, network traffic analyzers providing enhanced Network Forensics solutions.
After the Distributed Denial of Service (DDoS) Attacks, the Network Forensic sector has made their tracking more complex, mapping the source, trajectory or pattern of attack etc.
3. With the incorporation of Cloud Forensics, advanced methods and easy to use tools are improving the market’s workforce.
With the adoption of Monitoring APIs and Cloud Service Logs, analyzation gives data on user activities with real time monitoring, system events and more.
Memory Analyzation of a virtual machine used inside a cloud environment, can help to view or identify running processes, potential malware and network connections.
Incorporation and usage of Blockchain technology, ensures the maintenance of its data integrity, enhancing the investigation of certain threats properly.
With the coordinated initiatives from Cloud Security Alliance (CSA), called the "Cloud Forensics Working Group", has helped device newer frameworks of threat detection and prevention.
4. Integration of Artificial Intelligence (AI) and Machine Learning (ML) has made an impact in real time monitoring and error fixation.

With enhanced Anomaly Detection and Pattern Recognition, AI and ML can detect abnormalities in network and data transmission, detecting potential cyber threats.
Enhanced Natural Language Processing (NLP) helps in analyzing unstructured texts data from email or personal messaging applications, increasing investigating efficiency.
Upgraded ML algorithms detects the behavioral pattern of an individual, detecting for an unusual or unauthorized access and reporting in real time.
A CERT-In initiative called “Cyber Swachhta Kendra”, has allowed for users to use free tools to clean up from malware and other threats pertaining to future problems, clearing the environment of cyber threats.
CONCLUSION
This heavily weighted industry is always on the lookout and monitoring every aspect of digital forensics, paving the way for a suitable and clean environment without the presence of any hackers trying to enter through the backdoor.
0 notes
Text

Subject: Tips to protect yourself from phishing, scams, cyber-threats, and identity theft
Dear Members,
We've recently seen an increase in financial services posts in our group. While we've removed all suspicious posts, we want to remind you to be vigilant and protect yourself from phishing, scams, cyber-threats, and identity theft. Do your own checks to ensure that the financial services you're considering are legitimate. This means checking that they have a website, official emails with the same domain name as the website, a proven track record, and a good reputation. Avoid services that request upfront payment. This is a common sign of a scam.
What are these threats?
Phishing is a type of social engineering attack that uses fraudulent emails or text messages to trick victims into revealing personal information, such as passwords, credit card numbers, or Social Security numbers. Scams are similar to phishing attacks, but they often involve more direct contact with the victim, such as through phone calls or in-person visits. Cyber-threats are any malicious actions that are carried out through electronic means, such as hacking, malware, or denial-of-service attacks. Identity theft is a crime in which someone steals someone else's personal information and uses it to commit fraud or other crimes.
How can you protect yourself?
Here are some tips to help protect yourself from these threats:
Be aware of the signs of a phishing attack. Phishing emails or text messages often contain urgent requests for personal information, such as passwords or credit card numbers. They may also contain links that, when clicked, will take you to a FAKE website that looks like a legitimate website. Don't click on links in emails or text messages from people you don't know. If you're not sure if an email or text message is legitimate, go to the website or company's website directly and log in from there or used their online form. Keep your software up to date. Software updates often include security patches that can help protect your computer from malware and other threats. Use strong passwords and change them regularly. A strong password is at least 8 characters long and includes a mix of upper and lowercase letters, numbers, and symbols. Be careful about what information you share online. Don't share your personal information, such as your Social Security number or date of birth, on social media or other websites. Use a firewall and antivirus software. A firewall can help protect your computer from unauthorized access, and antivirus software can help protect your computer from malware. Be careful about what Wi-Fi networks you connect to. Public Wi-Fi networks are often not secure, so it's important to be careful about what information you share when you're connected to them. If possible, connect to the public WIFI through your company VPN or reputed VPN services.
Additional tips:
Educate yourself about cyber security. The more you know about the threats, the better equipped you'll be to protect yourself. Be skeptical of anything that seems too good to be true. If an offer sounds too good to be true, it's probably a scam. Report phishing emails or phishing messages to your company cybersecurity team. If you are in charge of your company finance, if you received an email from your Senior Managers to pay an invoice, check that this email is legitimate (from your company official email) and checked with your Senior Managers through phone call or Whatsapp that this instruction is legitimate.
By following these tips, you can help protect yourself and your company from cyber threats.
Thank you,
Kosona Chriv
0 notes
Text
What Are the Latest Strategies in Social Media Risk Management?
Beginning: There are always several risks associated with running and managing social media accounts on multiple social media platforms. It is evident from the fact that today there are many incidents of cyber-related threats to businesses and individuals. So, what can be done to curtail these risks and threats? Let us see more below.

What is Social Media Risk Management?
Social media risk management is a group of processes that ensure businesses keep control of their social media interactions. They may have, among other things, knowledge of who accesses their accounts, who allows them to publish posts or messages to consumers, and the basic rules for presenting their brand online. The main goal of social media risk management is to prevent unauthorized communication and misrepresentation of the brand via incorrect messaging.
What Types of Risks Are Associated with Social Media?
- Phishing attacks and scams: malicious third-party attempts to impersonate a brand and communicate with customers to get them to reveal sensitive personal information.
Ransomware: It is malware that uses encryption to force the attack target to pay a ransom demand.
- Imposter accounts. - Malware attacks and hacks. - Vulnerable third-party apps. - Identity and password theft. - Privacy settings and data security. - Unsecured mobile devices. - Malicious apps. - Service denial attacks. The Latest Modern Strategies in Social Media Risk Management - Stronger and more accountable social media use policies: the cause or success of most risks can be attributed to negligence and poor social media use policies. A good policy ensures accountability, honesty, and transparency. - Train and equip: It is good to train and equip users because they are the first line of defense in protecting all the data they access. Moreover, as a responsibility to protect brand identity and image, it is vital to ensure the creation of safe places for customers. This can be done by staying updated on all the latest risks and threats to social media accounts. These can vary across social platforms, from Facebook vulnerabilities to Twitter hacks; it is good to be informed on how personal actions can expose business safety. - Monitoring and tracking: With several social media accounts, it's good to ensure the creation of control to review all actions. This specifies who can access the accounts, what devices they use to login, the time spent, and what is searched. If the staff use personal computers or phones to access business social media accounts, it is better to buffer security on the devices or enhance access protocols. Oversight is vital for social media posts and direct messages from business social media teams. Ensuring post reviews before scheduling with protocols to answer messages received via social media are all critical. Conclusion: Today, exposure to online risks and threats costs businesses lots of revenue and reputational damage. Social media risks and threats are quite more complex today than they were before. It is estimated that there has been a great leap in the growth of social media security risks and threats. Social media risk management is a bulwark attempt at creating solutions to overcome the risks and threats. And stronger, more resilient, and more accountable tactics help businesses succeed and grow.
For More Info:-
WhatsApp Phone Recording App
Zoom Data Leak Management
0 notes
Photo
Anomali Cyber Watch: Aggressively-Mutating Mantis Backdoors Target Palestine, Fake Cracked Packages Flood NPM, Rorschach Ransomware Is Significantly Faster Than LockBit v.3 The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Cryptocurrency, Data leak, Malvertising, Packers, Palestine, Phishing, Ransomware, and Software supply chain. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity. Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed. Trending Cyber News and Threat Intelligence CryptoClippy Speaks Portuguese (published: April 5, 2023) Since at least early 2022, an opportunistic cryptocurrency clipper campaign has been targeting Portuguese speakers by prompting a download from an actor-controlled website promoted via SEO poisoning and malvertising abusing Google Ads. The file impersonates WhatsApp Web and delivers malware dubbed CryptoClippy with the aim of replacing cryptocurrency addresses in the target’s clipboard. The first two files in the infection chain are either EXE and BAT or ZIP and LNK. The actors utilize extensive obfuscation and encryption (RC4 and XOR) techniques, log and file clearing, and thorough user profiling for narrow targeting and defense evasion. The use of the Invoke-Obfuscation obfuscation type may point to a Brazilian-based attacker. Analyst Comment: The observed actor-controlled wallets gained a little over 1,000 US Dollars, but their complex, multi-stage malware can help them to extend this damage. Users are advised to verify the recipient information prior to sending a financial transaction. Indicators related to CryptoClippy are available in the Anomali platform. Organizations that publish applications for their customers are invited to use Anomali Premium Digital Risk Protection to discover rogue, malicious apps impersonating your brand that security teams typically do not search or monitor. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1027 - Obfuscated Files Or Information | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1140 - Deobfuscate/Decode Files Or Information | [MITRE ATT&CK] T1620 - Reflective Code Loading | [MITRE ATT&CK] T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] T1136.001 - Create Account: Local Account | [MITRE ATT&CK] T1070.001 - Indicator Removal on Host: Clear Windows Event Logs | [MITRE ATT&CK] T1070.004 - Indicator Removal on Host: File Deletion | [MITRE ATT&CK] T1055 - Process Injection | [MITRE ATT&CK] T1053.005 - Scheduled Task/Job: Scheduled Task Tags: malware:CryptoClippy, malware-type:Clipper, Google Ads, Traffic distribution system, SEO poisoning, WhatsApp, file-type:ZIP, file-type:EXE, file-type:LNK, file-type:BAT, RDP, RC4, XOR, PowerShell, target-industry:Cryptocurrency, Ethereum, Bitcoin, source-country:Brazil, source-country:BR, Character padding, Invoke-Obfuscation, Windows Mantis: New Tooling Used in Attacks Against Palestinian Targets (published: April 4, 2023) The Mantis (Arid Viper, Desert Falcon, APT-C-23) advanced persistent threat is a Palestine-associated group that has been observed since 2011. In September 2022 - February 2023, Mantis engaged in a new campaign targeting organizations within the Palestinian territories. The campaign featured versions of custom Micropsia and Arid Gopher backdoors, and a variety of additional tools including the Putty SSH client, and the SetRegRunKey.exe registry modification persistence tool. Mantis has been aggressively mutating the logic between variants of its backdoors, at times replacing versions in the course of an ongoing compromise. Analyst Comment: Historically, many Mantis attacks have started with spearhishing. It is important to teach your users basic online hygiene and phishing awareness. Pay attention to suspicious PowerShell executions, suspicious port connections (such as over port 4444), and signs of data exfiltration. All known Mantis indicators associated with this campaign are available in the Anomali platform and customers are advised to block these on their infrastructure. MITRE ATT&CK: [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1113 - Screen Capture | [MITRE ATT&CK] T1056.001 - Input Capture: Keylogging | [MITRE ATT&CK] T1560.001 - Archive Collected Data: Archive Via Utility | [MITRE ATT&CK] T1027 - Obfuscated Files Or Information | [MITRE ATT&CK] T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder Tags: actor:Mantis, malware:Micropsia, malware-type:Backdoor, malware:Arid Gopher, PowerShell, PyArmor, Putty, SetRegRunKey.exe, actor:Arid Viper, actor:Desert Falcon, actor:APT-C-23, target-region:Palestine, source-region:Palestine, Cyberespionage, Data loss, Delphi, Golang, file-type:EXE, port:4444, Windows Who Broke NPM?: Malicious Packages Flood Leading to Denial of Service (published: April 4, 2023) Several campaigns likely operated by the same threat actor have targeted the npm JavaScript software registry with automated user account and package creation. In March 2023, it resulted in the number of monthly package versions released going from 800,000 to over 1.4 million, at times causing denial-of-service for the npm website. The threat actor has been creating malicious websites and publishing attractive cracked software-related package descriptions with links to those websites. The user would download and execute an inflated, zero-padded EXE file starting an infection chain disabling security tools and firewalls, utilizing DLL side-loading and virtualization/sandbox evasion. It delivers various commodity tools such as Glupteba, RedLine, Smoke Loader, xmrig and more to steal credentials and to mine cryptocurrency. Additional fraud monetization comes from scams using AliExpress referrals and cryptocurrency schemes in Russian-speaking Telegram groups. Analyst Comment: Open-source libraries and software supply chains are increasingly under attack. These campaigns are abusing the reputation of the npm code sharing environment to promote the malicious websites in search engines. As long as individuals continue to download cracked software, threat actors will continue using it as a distribution method. These types of downloads should be restricted by your company; supply the legitimate software and educate your employees about these risks. Network indicators associated with this recent npm targeting are available on the Anomali platform. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1027.001 - Obfuscated Files or Information: Binary Padding | [MITRE ATT&CK] T1629.003 - Impair Defenses: Disable Or Modify Tools | [MITRE ATT&CK] T1633 - Virtualization/Sandbox Evasion | [MITRE ATT&CK] T1574.002 - Hijack Execution Flow: Dll Side-Loading | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1496 - Resource Hijacking | [MITRE ATT&CK] T1499 - Endpoint Denial Of Service Tags: npm, Spam, malware:Glupteba, malware:RedLine, malware-type:Infostealer, malware:Smoke Loader, detection:xmrig, malware-type:Miner, Open-source library, SEO, DoS, AliExpress, Referral scam, Software supply chain, Warez, Cracked, Telegram, target-country:Russia, target-country:RU, target-industry:Cryptocurrency, file-type:EXE, Windows Rorschach – A New Sophisticated And Fast Ransomware (published: April 4, 2023) In February-March 2023, a new ransomware family dubbed Rorschach was spotted in the wild. While being unique overall, Rorscharch borrowed from several advanced ransomware families. Its hybrid-cryptography and some other routines are inspired or copied from Babuk. Similar to LockBit 2.0, it can spread from Windows Domain Controller by automatically creating a domain group policy. Finally, Rorschach ransomware notes were formatted in some cases similar to DarkSide and similar to Yanluowang in others. Rorschach does not brand its notes, but its exemption for Commonwealth of Independent States shows its likely origin. To avoid detection, Rorschach uses direct syscalls by finding, storing and using relevant syscall numbers for NT APIs. Rorschach achieves extremely fast encryption due to effective cryptography scheme, partial file encryption, effective thread scheduling via I/O completion ports, and compiler optimization, with much of the code being inlined. Analyst Comment: Rorscharch’s ability to abuse a Palo Alto Networks security product, Cortex XDR Dump Service Tool, was reported to the vendor. Network defenders can consider setting up warning systems for new group policies, new scheduled tasks, and rogue encryption processes targeting honeypot/canary files. To constrain the autonomous capabilities of the ransomware, endpoint devices with admin privileges should be properly locked down, and a micro-segmentation of IT networks should be implemented where possible. Ransomware is a constantly evolving threat, and the most fundamental defense is having proper backup and restore processes in place that allows recovery without any need to decrypt the affected data. MITRE ATT&CK: [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] T1490: Inhibit System Recovery | [MITRE ATT&CK] T1489 - Service Stop | [MITRE ATT&CK] T1070.001 - Indicator Removal on Host: Clear Windows Event Logs | [MITRE ATT&CK] T1070.004 - Indicator Removal on Host: File Deletion | [MITRE ATT&CK] T1053.005 - Scheduled Task/Job: Scheduled Task | [MITRE ATT&CK] T1027.002 - Obfuscated Files or Information: Software Packing | [MITRE ATT&CK] T1140 - Deobfuscate/Decode Files Or Information | [MITRE ATT&CK] T1574.002 - Hijack Execution Flow: Dll Side-Loading | [MITRE ATT&CK] T1484.001 - Domain Policy Modification: Group Policy Modification Tags: malware:Rorschach, malware-type:Ransomware, VMProtect, source-region:CIS, curve25519, eSTREAM cipher hc-128, I/O completion port, Thread scheduling, Domain group policy, Cortex XDR Dump Service Tool, Palo Alto Networks, target-country:USA, target-county:US, file-type:EXE, file-type:DLL, file-type:INI, Windows Rilide: A New Malicious Browser Extension for Stealing Cryptocurrencies (published: April 4, 2023) A new malicious extension dubbed Rilide targets cryptocurrency users on Chromium-based browsers. It was seen delivered through two infection chains: either starting with a malicious macros in a Publisher file delivering Ekipa RAT, or through Google Ads pushing the Aurora Stealer payload. The Rilide malware is impersonating a Google Drive extension. It loads additional JS scripts that collect information and make automatic fund withdrawal requests in the background. Dialogs for users are forged to reveal their two-factor authentication. It includes on-the-fly editing of withdrawal confirmation emails making them look like a device authorization request. Trustwave researchers found that threat actors were advertising malicious extensions with functionality similar to Rilide since at least March 2022, and partial code was leaked in February 2023. Analyst Comment: Users are advised to keep an eye on their browser extensions and question those additions that were not authorized. All known indicators related to Rilide are available in the Anomali platform and customers are advised to block these on their infrastructure. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1113 - Screen Capture | [MITRE ATT&CK] T1027.002 - Obfuscated Files or Information: Software Packing | [MITRE ATT&CK] T1565.003 - Data Manipulation: Runtime Data Manipulation Tags: malware:Rilide, Malicious browser extension, target-industry:Cryptocurrency, Chromium-based browser, Google Chrome, Microsoft Edge, Brave, Opera, malware:Ekipa, malware-type:RAT, malware:Aurora, malware-type:Infostealer, Themida, VMProtect, file-type:PUB, file-type:EXE, file-type:JS, file-type:JSON, malware-type:Loader, PowerShell, Rust, Discord CDN, Malvertising, Google Ads, actor:gulantin, Macros, Windows https://www.anomali.com/blog/anomali-cyber-watch-aggressively-mutating-mantis-backdoors-target-palestine-fake-cracked-packages-flood-npm-rorschach-ransomware-is-significantly-faster-than-lockbit-v3
0 notes
Photo

#Jeidartraining #PDU Yesterday our engineer Mr.zhang arranged a training for PDU and specially did a introduction of the SNMP link monitoring platform,our smart PDUs are able to realize Below functions. 1) Very user friendly A: Monitoring type: colored LCD display monitoring the real time data: such as input voltage, frequency, current, power factor, capacity, IP address, temperature and humidity, CAN/485 hardware address B: Monitoring & Control type: premium control type can view every socket output current, power factor and energy consumption. Can control each socket on/off control, can do group management and allocate the read or edit permission,can set the sockets alarm current range,set the control schedule accurately by every day, week or month. 3) Safety: A: Cyber security: *Support TLS Encryption authentication; SNMPv3, Encryption method can be selected; support SSH Command , support SSL Mail sending, network firewall. * Linux Kernel version 4.0+And encryption library, can repair most system security vulnerabilities. * Support Memory state recovery fast when PDU abnormal B: Electrical Safety: All external sensor interfaces and communication interfaces are isolated. 3) Multiple choice/customzied solution: A: both vertical or horizontal client can choose central monitoring, Socket monitoring, Socket monitoring+control types B: configuration: support customzied input plug and outlets standard. Single/three phase, socket quantity,color�� cable length etc. C: Rich network service function: support HTTP management, TLS Encrypted authentication, SNMP v3,support Telnet with SSH, network firewall, NTP Time synchronization, Provide operation, event log and battery time record For any inquiry about our smart PDU. Pls contact. Email: [email protected] Tel: +86-0755-26856844 Mob/WhatsApp: +8618211309129 Website: www.jeidar.com #PDU #Jeidar #PDUsupplier #MDC #ITinfrastructure #cybersecurity #management #network #smartpdu #intelligentpdu #training #team https://www.instagram.com/p/CqJ1eyBPQk3/?igshid=NGJjMDIxMWI=
#jeidartraining#pdu#jeidar#pdusupplier#mdc#itinfrastructure#cybersecurity#management#network#smartpdu#intelligentpdu#training#team
0 notes
Text
What is Pegasus? How To Protect Phones From Pegasus-Like Spyware Attacks?

Pegasus is a sophisticated spyware developed by the Israeli cyber intelligence firm NSO Group. It is designed to covertly infiltrate mobile phones and gain access to their contents, including text messages, emails, photos, and location data. Pegasus can also turn on the microphone and camera of a targeted device, effectively allowing the operator to monitor the device’s user in real-time.
Pegasus is often referred to as a “zero-click” spyware because it can infect a device without any user interaction, such as clicking on a link or downloading an app. It exploits vulnerabilities in the device’s operating system or apps to gain access.
Pegasus has been used by various governments and intelligence agencies around the world to spy on dissidents, journalists, human rights activists, and other individuals deemed as threats. Its use has been the subject of controversy and legal challenges, as it raises questions about privacy, human rights, and government surveillance.
How to detect Pegasus spyware?
Detecting Pegasus spyware on a mobile device can be challenging because it is designed to be stealthy and avoid detection. However, there are some indicators that may suggest the presence of Pegasus on a device:
Unusual battery drain: Pegasus can consume a significant amount of battery power as it continuously runs in the background.
Suspicious network activity: Pegasus may send and receive data from remote servers, which can be detected by monitoring network activity on the device.
Strange behavior or activity: Pegasus may cause the device to behave unusually, such as sudden crashes, slower performance, or new apps appearing on the device.
Unexplained text messages or missed calls: Pegasus can intercept text messages and calls, so if you receive messages or missed calls from unknown numbers, it could be a sign that your device is infected.
If you suspect that your device may be infected with Pegasus, you can use anti-malware software to scan for and remove any spyware. It is also recommended to update your device’s operating system and apps regularly to patch any known vulnerabilities that could be exploited by spyware. Additionally, you can limit your device’s exposure to potential spyware by avoiding clicking on suspicious links or downloading apps from untrusted sources.
Protecting Phones From Pegasus-Like Spyware Attacks
Protecting phones from sophisticated spyware attacks like Pegasus can be challenging, but there are several steps you can take to minimize your risk.
Keep your phone software up to date: One of the best ways to protect your phone from spyware attacks is to keep your software up to date. Software updates often include security patches that can help protect your device from known vulnerabilities.
Be cautious when downloading apps: Only download apps from trusted sources like the Google Play Store or the Apple App Store. Be cautious of downloading apps from third-party app stores or websites.
Use a strong password: Use a strong password or PIN to protect your phone from unauthorized access. Avoid using easy-to-guess passwords, like “1234” or “password.”
Avoid clicking on suspicious links: Be cautious of clicking on links sent to you via text message or email, especially if they are from unknown sources.
Install anti-malware software: Consider installing anti-malware software on your phone to help detect and prevent spyware attacks.
Limit your phone’s exposure: Avoid using public Wi-Fi networks, turn off Bluetooth when you’re not using it, and avoid charging your phone from unknown sources.
Check your phone for signs of spyware: Regularly check your phone for any unusual behavior, such as slower performance, excessive battery drain, or unexpected pop-ups or messages. These could be signs of spyware.
Consider using encrypted messaging apps: Consider using encrypted messaging apps, like Signal or WhatsApp, which can help protect your conversations from being intercepted.
Be mindful of what you share online: Be careful of what you share online, including on social media, as this information can be used to target you with spyware attacks.
While these steps can help reduce your risk of a spyware attack, it’s important to remember that no method is foolproof.
1 note
·
View note
Text
Telegram Alternative for Your Secure Messaging software
Are you looking for Telegram alternatives? Then read this blog to discover alternative messaging platforms and get a quick overview.
Troop Messenger
Since Telegram is used by a few start-ups and small enterprises, I figured Troop Messenger and others could be added to the list. Troop Messenger is undeniably more than a Telegram alternative. Troop Messenger offers a lot of features compared to Telegram, which is far superior in terms of providing quality. For instance, Troop Messenger groups will have great advantages compared to Telegram chatting groups such as admin super controls, advanced search filters, screen sharing within group calling, and so on.
One of the encrypted chat programs on the list is Troop Messenger, and it's possible that you've already used the safest one. Due to its superior security features, political parties utilise it as their political campaign software, and the defence agencies of a few strong nations employ it for defence collaboration services. You can therefore gauge the tool's security. There aren't many products like Troop Messenger available on the market that can be supplied via all of the main delivery models, including chat APIs and SDKs, on-premise, SaaS, etc.

Apart from chat basic functions, Troop Messenger is a complete team collaboration tool that provides its users with all the features such as audio/video conference, screen sharing, remote access, live location tracking, and so on.
Do you know that Troop Messenger has a Burnout feature similar to Telegram’s secret chat? Teams, Defense agencies, and government officials can use it to convey classified information that no one else on the planet, including service providers, has access to.
Telegram is a cloud-based instant messaging software that is freeware and cross-platform. End-to-end encrypted video calling, file sharing, VoIP, and other functions are also available. Telegram's initial release date was August 14, 2013, for iOS and October 2013 for Android.
Nikolai and Pavel Durov, who were also the inventors of the Russian online social site RK, launched Telegram in 2013.
Telegram's data is dispersed over five data centers in various locations around the world, including the operations center in Dubai, United Arab Emirates.
After WhatsApp announced its privacy policy in January 2021, 25 million new users joined Telegram, according to Telegram creator Pavel Durov. This equates to almost 8.33 million new users signing up every day. Telegram added over 100 million new users in just the month of January.
Telegram quickly made a name for itself as a competitive WhatsApp substitute. A few publications claim that Telegram currently has over 550 million active members and ranks in the top 10 most popular social networks globally in terms of download volume. Businesses were compelled by Telegram's popularity to get their app developers to produce an ideal substitute.
Why is Telegram not recommended?
Even though a few companies use it, Telegram shouldn't be on your list of chat apps for your team or place of business. It wouldn't meet all workplace requirements because it's a social messenger unless you wanted to limit it to phone calls, conversations, and file sharing. Telegram will merely function as an additional messenger, similar to FaceTime, WhatsApp, and the like. Nevertheless, a strong team communication tool can enhance teamwork and increase productivity at work, something that Telegram apps are unable to accomplish.
Check Point issued a Telegram warning in 2021, that "it tracked 130 cyber attacks that used malware managed over Telegram by attackers. Even though Telegram is not installed or being used, it allows hackers to send malicious commands and operations remotely via the instant messaging app."
What are the disadvantages of Telegram?
Here are some of Telegram's drawbacks that may make you want to uninstall it and look out for Telegram alternatives.
Telegram collects users’ contact details and metadata
If the articles are to be believed, Telegram is not an end-to-end encrypted
It has limited support
Since Telegram has a 1.5 GB file size limit, illegally downloaded movies are being mixed in with adult content that is not appropriate for children.
Telegram also allows attackers to access hacked machines from practically anywhere on the planet using their mobile devices.
Due to some operational advantages, cybercriminals are increasingly using Telegram as part of their activities.
Attackers can simply exfiltrate data from victims' PCs or transfer new malicious files to infected machines owing to Telegram's unique communication features.
Observing the above-mentioned segmentations, on the contrary, users have huge benefits from utilizing Telegram as their social chat app, which any app like Telegram may not offer.
If you believe that we are being subjectively biased by pointing out Telegram's drawbacks, further information will show just how objective we are.
How have users benefited from Telegram?
Do you know that with 700 million monthly active users, Telegram has ascended to become one of the top 5 downloaded apps globally in 2022? According to Telegram, it has never spent money on advertisements; instead, it was users who shared their positive experiences with other users (friends, relatives, acquaintances, colleagues, and others). As a result, they were persuaded to download it.
In light of this, Telegram introduced a premium plan that gives users access to extra premium features while allowing free use.
Telegram Premium
Users will have access to increased limits, better chat management, 4 GB file uploads, faster downloads, exclusive stickers and reactions, and other benefits with Telegram Premium. Despite this, non-premium users will still have access to all current capabilities. In fact, they may even be granted access to select privileges, such as
Ability to download large documents.
Tap to increase the counts on premium reactions that have already been added to a message.
Can view the stickers that Premium users have sent.
Some of the enticing features that premium users can access are
1. Chat Management
New tools in Telegram Premium help you organize your conversation list, such as setting your default chat folder to ensure that the app always starts on Unread instead of All Chats.
Indeed, subscribers can keep the busiest chat lists organized by enabling a Privacy and Security feature that automatically archives and mutes new chats.
2. Animated Profile Pictures
Everyone using the app can see the animated profile videos of premium users in chats and the chat list. In addition, premium users can demonstrate their fresh look to the world or showcase their creativity with a unique looping animation.
3. 4GB Uploads
Those who use Telegram Premium can now send files up to 4 GB in size, which provides sufficient space for 4 hours of 1080p video or 18 days of high-quality audio. At the same time, non-premium users can indeed upload files and media up to 2 GB in size and take advantage of unlimited free storage in the Telegram Cloud.
4. Faster Downloads
Media and files can be downloaded as quickly as possible for premium subscribers. Users get limitless access to their cloud storage and can access everything as quickly as their network can accommodate.
5. Doubled Limits
Doubled limitations are available to premium users for everything in the app, including:
Can add the fourth account,
Able to follow 1000 channels,
Create up to 20 chat folders, each containing a maximum of 200 chats,
Add ten chats to the main list,
Ten favorite stickers may be saved,
Ability to write a longer bio and add a link to it.
6. Voice-To-Text
For those occasions when you cannot listen but still wish to see what it says, voice messages can be converted to text. You can give transcriptions a rating to help them get better.
7. Unique Stickers
There are dozens of stickers available for Premium users to send in any chat to add extra emotion and expressive effects to engage the recipients while still making them visible to all users. These stickers are meant to impress, especially millennials, and feature full-screen animations. In contrast to Telegram alternatives, the Telegram team of artists will update a premium sticker collection every month.
8. Premium Badges
In the chat list, chat headers, and member lists in groups, all premium users have a special badge that says "Premium" next to their names, signifying that they are a member of the club that gets first access to unique features.
9. Premium App Icons
Premium customers have the option to add new icons to their Home Screen in an attempt to make it more compatible with their personality or wallpaper.
Telegram guarantees its users that it will continue to implement free features that are accessible to everyone and that it will do it more quickly than any other app similar to Telegram.
Conclusion
If the encryption is disregarded, Telegram can serve as a popular social media chat software, but it is a terrible tool for team and corporate interactions. Whereas hackers are using Telegram data to their advantage, WhatsApp is only gathering commercial data from particular companies. Telegram needs to start prioritising security, or else users will begin to migrate to other messaging apps.
0 notes