#cyber security problems and solutions
Explore tagged Tumblr posts
Text
Masterlist of Free PDF Versions of Textbooks Used in Undergrad SNHU Courses in 2025 C-1 (Jan - Mar)
Literally NONE of the Accounting books are available on libgen, they all have isbns that start with the same numbers, so I think they're made for the school or something. The single Advertising course also didn't have a PDF available.
This list could also be helpful if you just want to learn stuff
NOTE: I only included textbooks that have access codes if it was stated that you won't need the access code ANYWAY
ATH (anthropology)
only one course has an available pdf ATH-205 - In The Beginning: An Introduction to Archaeology
BIO (Biology)
BIO-205 Publication Manual of the American Psychological Association Essentials of Human Anatomy & Physiology 13th Edition
NOTE: These are not the only textbook you need for this class, I couldn't get the other one
CHE (IDK what this is)
CHE-329
The Aging Networks: A Guide to Policy, Programs, and Services
Publication Manual Of The American Psychological Association
CHE-460
Health Communication: Strategies and Skills for a New Era
Publication Manual Of The American Psychological Association
CJ (Criminal Justice)
CJ-303
The Wisdom of Psychopaths: What Saints, Spies, and Serial Killers Can Teach Us About Success
Without Conscious: The Disturbing World of the Psychopaths Among Us
CJ-308
Cybercrime Investigations: a Comprehensive Resource for Everyone
CJ-315
Victimology and Victim Assistance: Advocacy, Intervention, and Restoration
CJ-331
Community and Problem-Oriented Policing: Effectively Addressing Crime and Disorder
CJ-350
Deception Counterdeception and Counterintelligence
NOTE: This is not the only textbook you need for this class, I couldn't find the other one
CJ-405Private Security Today
CJ-408
Strategic Security Management-A Risk Assessment Guide for Decision Makers, Second Edition
COM (Communications)
COM-230
Graphic Design Solutions
COM-325McGraw-Hill's Proofreading Handbook
NOTE: This is not the only book you need for this course, I couldn't find the other one
COM-329
Media Now: Understanding Media, Culture, and Technology
COM-330The Only Business Writing Book You’ll Ever Need
NOTE: This is not the only book you need for this course, I couldn't find the other one
CS (Computer Science)
CS-319Interaction Design
CYB (Cyber Security)
CYB-200Fundamentals of Information Systems Security
CYB-240
Internet and Web Application Security
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-260Legal and Privacy Issues in Information Security
CYB-310
Hands-On Ethical Hacking and Network Defense (MindTap Course List)
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-400
Auditing IT Infrastructures for Compliance
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-420CISSP Official Study Guide
DAT (IDK what this is, but I think it's computer stuff)
DAT-430
Dashboard book
ECO (Economics)
ECO-322
International Economics
ENG (English)
ENG-226 (I'm taking this class rn, highly recommend. The book is good for any writer)
The Bloomsbury Introduction to Creative Writing: Second Edition
ENG-328
Ordinary genius: a guide for the poet within
ENG-329 (I took this course last term. The book I couldn't find is really not necessary, and is in general a bad book. Very ablest. You will, however, need the book I did find, and I recommend it even for people not taking the class. Lots of good short stories.)
100 years of the best American short stories
ENG-341You can't make this stuff up : the complete guide to writing creative nonfiction--from memoir to literary journalism and everything in between
ENG-347
Save The Cat! The Last Book on Screenwriting You'll Ever Need
NOTE: This i snot the only book you need for this course, I couldn't find the other one
ENG-350
Linguistics for Everyone: An Introduction
ENG-351Tell It Slant: Creating, Refining, and Publishing Creative Nonfiction
ENG-359 Crafting Novels & Short Stories: Everything You Need to Know to Write Great Fiction
ENV (Environmental Science)
ENV-101
Essential Environment 6th Edition The Science Behind the Stories
ENV-220
Fieldwork Ready: An introductory Guide to Field Research for Agriculture, Environment, and Soil Scientists
NOTE: You will also need lab stuff
ENV-250
A Pocket Style Manual 9th Edition
ENV-319
The Environmental Case: Translating Values Into Policy
Salzman and Thompson's Environmental Law and Policy
FAS (Fine Arts)
FAS-235Adobe Photoshop Lightroom Classic Classroom in a Book (2023 Release)
FAS-342 History of Modern Art
ALRIGHTY I'm tired, I will probably add ore later though! Good luck!
23 notes
·
View notes
Text
Digimon & mythology: the Royal Knights
Of all the Digimon groups, none are as famous as the Royal Knights. These 13 holy knight Digimon are the guardians of the Digital World and act as the highest form of network security. The Royal Knights are appointed to the position by and answer to Yggdrasil, the computer who runs the Digital World. While part of a group, each member of the Royal Knights has their own goals, motivations, philosophies, and opinions on the nature of their duties and justice. As a result, they often don't get along with each other and work independently. They may even clash with each other should they have conflicting goals or ideals. When they do work together, however, nothing can stand against them. Most of them rarely show their faces to the common people of the Digital World, instead aloofly performing their duties. While there are 13 Royal Knights, it took time both in-universe and in real life for all 13 members to appear.
The Royal Knights are also heavily connected with the x-antibody, featuring both in the original x-antibody storyline and its follow-up Digimon Chronicle and Digimon Chronicle X. In the storyline, the Digital World is reaching its capacity due to Digimon reproducing out of control. To keep the Digital World from collapsing, Yggdrasil choses a select few Digimon to move to a new Digital World and uses a program called the x-program to kill the remainders. However, the x-antibody begins spreading through the surviving Digimon, mutating them into new x-antibody forms that can survive the x-program and trying to invade the new Digital World. Yggdrasil sends the Royal Knights to kill these x-antibody Digimon. Eventually, a schism forms in the Royal Knights between those who obey Yggdrasil and those who don't want to kill off the vast majority of all Digimon. In the end, Yggdrasil is forcibly reset and the original and new Digital Worlds exist side by side, occasionally interacting with each other. Both world would later come under threat by x-antibody versions of the Seven Great Demon Lords, which ended with the Royal Knights combining their powers to allow the newest member, JESmon, to save the day.
While the Royal Knights are supposed to be the defenders of the Digital World, they, or at least some of them, are often used as villains in various Digimon media. This is often because they serve Yggdrasil, who is a villain in almost every appearance. Sometimes they will start as villains but later change sides. This was the case in Digimon Savers/Data Squad where Yggdrasil viewed humanity has an existential threat and sent the Royal Knights to destroy the human world. The Knights later turned on Yggdrasil after the protagonists showed them that humans and Digimon can coexist in peace. In other cases the Knights will have a schism based on following Yggdrasil's orders. This is the case in the x-antibody storyline and in Digimon Story: Cyber Sleuth, where the Knights become divided between those who wish to exterminate humanity to save the Digital World and those who wish to spare humanity and find a different solution to the problem.
There will be fewer mythological references in this entry than my posts on the Sovereigns and Deva, Seven Great Demon Lords, and Angel Digimon. This is because the Royal Knights have fewer mythological references in general than those groups. I will do what I can though. The Royal Knights are collectively based on the legends of King Arthur and the knights of the round table. The stories of King Arthur are varied and have been rewritten many times. The oldest version of the story we can track down comes from 5th-6th century Welsh sources where Arthur is the king of the Britons in the post-Roman period who defended Britain against Anglo-Saxon invaders. Later writers incorporated their own stories and themes into the mix, such as the addition of chivalric and Christian themes. Christian themes, such as the famous search for the holy grail, were added by later Christian authors while some famous characters like Lancelot were the result of French influence. There really isn't one story of King Arthur and the knights of the round table, there are many. One common trait of the stories is that the round table is round to symbolize that everyone sitting at it is an equal, which is reflected in the the Royal Knights having no internal hierarchy. None of the knights is the master of any other, they are all independent and of equal rank. Kenji Watanabe, one of the main designers for Digimon, has commented that many of the stories have far more than 13 knights of the round table and he isn't opposed to adding more Royal Knights. He has also said he would like to tell a story of the Royal Knights passing the baton to a new generation. I think it would be cool to add more Arthurian references to the Digimon Mythos, making Digimon versions of characters like Merlin, Morgan le Fay, and Mordred. The King Arthur figure could either be Yggdrasil or Imperialdramon Paladin Mode, who founded the Royal Knights but is not a member. I also don't believe there is any official Digimon media telling the story of the founding of the Royal Knights, which I think would be a great story. They are said to be natural enemies of the Seven Great Demon Lords, so I think it makes sense for them to have been founded in response to Lucemon's rebellion and fall.
The first three Digimon specifically identified as Royal Knights were final forms of the main character's partner Digimon from the first 3 anime series: Digimon Adventure, Digimon Adventure 02, and Digimon Tamers. The first of them to debut and the most famous Royal Knight of all is Omegamon, named Omnimon in English. It was born out of a fusion of two powerful Digimon, WarGreymon and MetalGarurumon, triggered by the hopes and wills of people wishing for goodness and peace. Because it is a fusion of two Digimon, it can use both of their abilities. making it a master of close and long range combat. Each of its arms resembles the head of one of its components and weapons are stored in the mouths. Its right arm is the MetalGarurumon head, which contains the Garuru Cannon, which can fire energy blasts at absolute zero. Its left arm is the WarGreymon head and contains the Grey Sword and has a powerful shield on the shoulder. Omegamon's role in thr Royal Knights is to protect Yggdrasil's justice and elevate the name of the Royal Knights to greater heights. Omegamon is easily the most popular of the Royal Knights in real life and has showed up in a ton of different animes, mangas, games, etc. Honestly, he's overused in my opinion. Omegamon also has a ton of variants and homages, way too many for me to list here. As with all the Royal Knights, he has an x-antibody variant. Omegamon X possesses a power called Omega inForce, a form of precognition which allows it to foresee what its opponents will do, making it theoretically impossible for it to ever lose a fight. Omegamon X is one of the better x designs for the Royal Knights because it doesn't change much. It just gets spikier. There are much worse designs coming.


Omagemon (left) and Omegamon X (right)
Omegamon debuted in Digimon Adventure. Debuting in Digimon Adventure 02 is Magnamon. Magnamon is the only member of the Royal Knights who is not of the Ultimate/Mega level. Instead, he's an armor Digimon, the result of a Digimon using with the power of one of the relics called Digimentals. Magnamon uses the Digimental of miracles, which grants to power to overcome any predicament. While Magnamon is not a Ultimate/Mega level and is usually depicted as the smallest of the Royal Knights, it is just as powerful as the rest and is the best at defense. In fact, it forms the cornerstone of the Royal Knight's defensive efforts. Magnamon X gains the ability to cause its armor to change shape, further increasing its defensive efforts and giving it more utility.


Magnamon (left) and Magnamon X (right)
Debuting in Digimon Tamers is Dukemon, named Gallantmon in English. A few of the Royal Knights got name changes in English and for most of them I don't have a strong opinion on which is better. In this case though, I think Gallantmon is a way better name than Dukemon and I'm going to use it here. Gallantmon is a living contradiction. Its evolution line bears the Digital Hazard, a force of destruction that could destroy the Digital World. Gallantmon has chosen to restrain that power and protect the world it was born to destroy. Because it understands having to constantly resist the temptation of destruction, it holds itself and its fellows to a very high standard and works to defend the weak. In many different stories, it is depicted as the first one to defect from the Royal Knights should they begin to turn bad or stray from the cause of defending the Digital World. Gallantmon bears the lance Gram and shield Aegis and sometimes rides a mount named Grani. Gram and Grani both come from the Scandinavian legend of Sigurd, a great hero the slew the dragon Fafnir. Gram was the sword wielded by Sigurd which was then passed down to many other heroes. Grani was Sigurd's steed, granted to him by the god Odin and descended from Odin's own steed Sleipnir. Aegis comes from Greek mythology, where it was the shield used by Zeus and Athena. Another reference to the legend of Sigurd comes from the alternate Ultimate/Mega level form of Gallantmon's evolution line: Megidramon. While Gallantmon expresses the power of the Digital Hazards and chooses to be a hero, Megidramon gave into the Hazard and is a mindless, draconic force of destruction. Depending on the the circumstances, it can either be the hero Sigurd or the dragon Fafnir he was sent to slay. The mane of Megidramon comes from Megiddo, the location where the end times will begin according to the Bible's Book of Revelation. It is better known by its Greek name Armageddon. Gallantmon can temporarily mode change into Gallantmon Crimson Mode. In this form, it becomes much more powerful, but it can only stay in this form temporarily. In this from it weirds weapons made of light named Gungnir and Blutgang. Gungnir was the spear of the greek god Odin and Blutgang is the name of the sword of the hero Heime of Germanic legend. Gallantmon X increases its power and transforms Gram into a lance made of light.



Left to right: Gallantmon, Gallantmon Crimson Mode, and Gallantmon X
The most unconventional Royal Knight is Alphamon. Despite being a Royal Knight, it acts as a deterrent force intended to oppose the other Royal Knights and it only appears in exceptional circumstances. Because it so rarely appears, it is known as the empty seat. This is a reference to the siege perilous from Arthurian legend. The siege perilous was an empty seat at the round table set aside by merlin for the knight who completed the quest for the holy grail. In earlier versions of the story, the knight who eventually earned the seat was Percival, though his role was given to Galahad in 13th century French tellings. Alphamon's role as a deterrent force is often interpreted as him being given the job of insuring the other Royal Knights do not go too far or stray from their role as the Digital World's protectors. As such, Alphamon is heroic in most of its appearances. Alphamon is one of an evolution line of prototype Digimon and is often associated with fellow prototype Digimon Ouryumon. Oryumon has the power to transform itself into a mighty blade called the Ouryuken. Only Alphamon is able to wield the Ouryuken and when doing so, it becomes known as Alphamon Ouryuken. Many depictions of Alphamon instead treat the Ouryuken as something that Alphamon can summon whenever he wants and ignore Ourumon's role. Alphamon has a power called the Alpha inForce, which allows it to rewind time to the beginning of a battle and fight over and over again. From an external perspective, it will appear as though Alphamon cut down its enemy with a single blow but the battle may have actually been fought multiple times until Alphamon foound the best outcome. Alphamon naturally compliments Omegamon and their namec come from the phrase "I am the alpha and omega" from the Bible. Alpha and omega are the first and last letters of the Greek alphabet and the phrase is supposed to portray god as both the beginning and end of everything. Alphamon is the only Royal Knight that doesn't have an x-antibody form because it is a natural carrier, a Digimon with the x-antibody that doesn't have a non- x-antibody counterpart.


Alphamon (left) and Alphamon Ouryuken (right)
Like how Omegamon, Magnamon, and Gallantmon all debuted as partners of a main character from one anime season. Ulforce V-dramon (eng: UlforceVeedramon) was the partner of the main character of the manga Digimon Adventure V-Tamer 01. Ulforce V-dramon is the fastest of the Royal Knights and there is no being that can track its movements. Its armor is immensely strong but also very lightweight, enabling its fast movement. It wears bracelets from which extend energy blades called Ulforce Sabers. It wields the power called Ulforce, which is born from joy and the desire to protect loved ones. The Ulforce is a code that can overwrite a Digimon's data. Most such codes will increase power but damage data, ultimately harming the Digimon using them. The Ulforce instead repairs data, allowing Ulforce V-dramon to heal even as it increases in power. Ulforce V-dramon X increases the power of the Ulforce even more, allowing Ulforce V-dramon to heal from wounds so fast that it appears that it appears it was never wounded in the first place. The v stands for victory, btw.


Ulforce V-dramon (left) and Ulforce V-dramon X (right)
Dynasmon is unusual among the fiercely independent Royal Knights because it will willingly submit to and serve other beings that chare its sense of justice. Once Dynasmon calls another lord, it will serve then with deep and unquestioning loyalty even if their actions could be considered evil. It follows the moral codes of chivalry and bushido, both of which encourage honor, loyalty, and combat prowess. Dynasmon values devotion, fidelity, and curtesy. Becuase it will follow its lord with unquestioning loyalty, Dynasmon is frequently a villain in stories it appears in due to it following an evil lord. Its power comes from wyverns, a type of dragons with two wings and two legs that were often found in medieval heraldry. Dynasmon X increases its wyvern influence, making it more draconic and granting it the best aerial combat prowess of all the Royal Knights. It is also probably the ugliest of the Royal Knight's x-antibody forms and there is fierce competition in that department. There are so many lines on that picture I can barely tell what's going on


Dynasmon (left) and Dynasmon X (right)
Craniummon is the Royal Knight that most understands decorum and follows a knightly code of honor. While very obsessed with decorum, it is also a perfectionist that competes with the other Royal Knights for the highest mission completion rates. It also loves combat and enjoys nothing more than a fight with a truly skilled opponent. Yggdrasil personally modified Craniummon's data, increasing the defensive properties of its armor and giving it the power to generate its weapon and shield from its armor. It carries the double-headed spear Claíomn Solais and shield Avalon. Claíomn Solais, which means "sword of light" appears as a motif in multiple Scottish and Gaelic folk tales, often as an object the hero obtains as part of a quest he must undertake to marry his desired bride. Avalon is the name of a mythical island in Arthurian lore, a magical land where Arthur was taken on his deathbed to one day rise again when Britain needs him most. Craniummon X has further increased the defenses of its armor and it now wears its shield on its back because it is certain it will not be needed. Its x-antibody art is also absolutely hideous, maybe worse than Dynasmon's.


Craniummon (left) and Craniummon X (left)
Duftmon (eng: Leopardmon) is the Royal Knight acknowledged by its fellows as the greatest strategist. This is both because it has an extremely cunning and strategic mind, and because its the only person who can get all the Royal Knights to work together despite their disagreements and opposing values. It believes that justice equals power, though it can be debated whether this means that the most powerful get to decide what justice is or that acting with justice will give one power. When Duftmon chooses to fight, it mode changed to Duftmon Leopard mode, a quadruped that can run and fly at high sppeds and cause rock pillars to erupt from the ground. And yes, its name in English is Leopardmon Leopard Mode. Interestingly, Duftmon has a very French motif, but its name and the name of its attacks are all in German. Specifically, it was based on the chanracter of Oscar François de Jarjayes from the manga The Rose of Versailles. She was a beautiful woman who was raised as and dresses as a man and is a skilled fighter. Despite being designed based on a woman, Duftmon is still generally depicted as masculine or genderless. Duftmon X gains powerful but flexible armor, allowing it to dodge incoming attacks from multiple directions and strike back with taijutsu (martial arts) and datotsu (kendo). It no longer relies on a mode change to fight.



Left to right: Duftmon, Duftmon Leopard Mode, and Duftmon X
Seipmon was the first Royal Knight introduced who is not humanoid and one of only two in total. Instead, it is shaped like a centaur, though with an additional pair of legs and a horse's head. Its six legs give it unsurpassed mobility and it can move far faster than its bulky frame would suggest. though it is still not as fast as Ulforce V-dramon. Its name was changed to Kentaurosmon in English, which is the only Royal Knight name change I really don't like. It resides at the Digital World's north pole, where it guards super-ancient ruins that lie beneath the ice. Within these ruins is said to lie programs that were used to create Digimon. If evildoers were to get ahold of such data, they would be able to create an unlimited army of Digimon to serve them. Sleipmon weilds the power of fire and ice. In its left hand is the crossbow Múspellsheimr which fires burning arrows in an attack called Bifröst. In its right hand is the shield Niflheimr, which can unleash a blizzard. In Norse mythology, Múspellsheimr and Niflheimr are primordial wrlds of fire and ice, the intermingling of which led to the creation of the rest of the universe. From the same mythology, the Bifröst is a rainbow bridge that links Midgard (Earth) and Asgard (realm of the gods). Sleipmon's name and appearance also gome from Norse mythology. Sleipnir was an eight-legged horse who was the god Odin's personal steed. Sleipmon X gains an additional two arms, letting it load and fire its bow at lightning speed.


Sleipmon (left) and Sleipmon X (right)
LordKnightmon (eng: Crusadermon) is the least pleasant of the Royal Knights. It cares nothing for morality, instead following its own brutal and utilitarian code of justice. It is incredibly ruthless and shows no compassion for the weak, instead ruling by force and even culling the weak to ensure only the strong survive. Naturally, LordKnightmon is a villain in nearly every appearance. It is also to monarch of the Knightmon species and presides over all knight Digimon, giving it a personal army to do its will. LordKnightmon is one of only two virus-attribute Royal Knights, the other being Gallantmon. While Gallantmon resists its destructive urges to protect the weak, LordKnightmon is just a total asshole. It carries no weeapon, but the ribbons coming from its body can be used as blades and its shield contains a pile bunker. Interestingly, LordKnightmon is the only Royal Knight to have been portrayed as female and different appearances treat it alternately as feminine, masculine, or genderless. Probably because it's pink and likes roses. LordKnightmon X gains a major rose motif and gets to have a sword. It battles in a manner like dancing that invokes fear in those who see it.

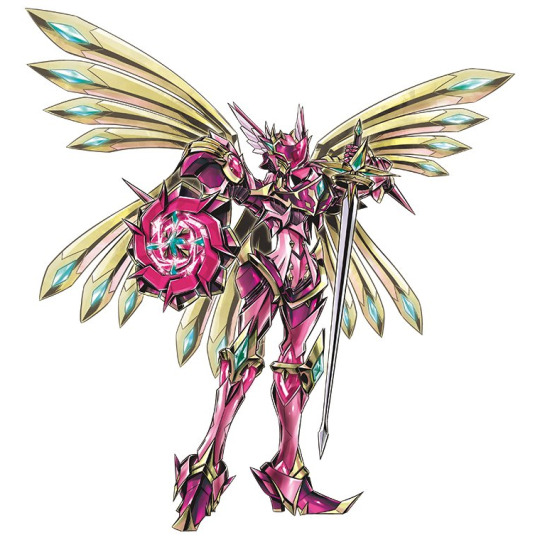
LordKnightmon (left) and LordKnightmon X (left)
Examon, along with Sleipmon, is one of the two non-humanoid Royal Knights, being a gigantic dragon. It is one of the more recent members, both in and out of universe, because it is so large that new technology had to be invented to render the sheer amount of data that makes up its body. While a member of the Royal Knights, Examon also holds the position as the greatest of all dragon Digimon, holding the title Dragon Emperor. Its wings are named Caledfwlch and have a mind of their own, being able to transform into an unbreakable shield to protect it. The lance it holds is named Ambrosius and is used in attacks called Avalon's Gate and Pendragon's Glory. Examon is based on the Y Ddraig Goch, the red dragon of Wales. The dragon is a symbol of Wales and the Welsh people. In the ancient Welsh book of stories Mabinogion, the Red Dragon is seen battling a white dragon. The white dragon represents the Anglo-Saxons who were colonizing Britain and the story says that the red dragon will soon win. Caledfwlch is the original Welsh name for King Arthur's sword Excalibur. Ambrosius comes from Ambrosius Aurelianus, a war leader in Roman Britain who defeated the Anglo-Saxons in a major battle and was later incorporated into Arthurian legend as Arthur's uncle. The attack names come from the same Avalon mentioned in Craniummon's entry and Pendragon, the surname of King Arthur. Examon X becomes humanoid and gains the power to make swords out of lightning. I actually kind of like Examon X's design, I just think it should be its own Digimon instead of a variant.


Examon (left) and Examon X (right)
Gankoomon one of the two final Royal Knights released for the franchise's 15th anniversary. Unlike the other Royal Knights, who are aloof and distant, Gankoomon spends a lot of time with common Digimon and helps out with smaller problems, making it very popular in the Digital World. Gankoomon also works well with other Digimon, in contrast to the other Royal Knights, who work alone. In particular, it allies with Sistermon Blanc and Sistermon Noir and is training Hackmon as a successor. Gankoomon acks like a stern father figure, treating Hackmon severely and arguably cruelly and rarely showing pride or affection, but it does genuinely want Hackmon to succeed and become a Royal Knight. The fiery, dragon-shaped aura above Gankoomon is actually another Digimon named Hinukamuy bonded to Gankoomon. Hinukamuy is an Adult/Champion level and when it evolves, there won't be any Digimon who can rival it. Unlike the other very regal and European Royal Knights, Gankoomon is unconcerned with decorum and prefers beating enemies with its fists instead of swords. Gankoomon is visually and behaviorally based on banchos, the leaders of Japanese delinquent groups. Hinukamuy's name is a combination of Hinukan, a fire god from the religion of Japan's Ryuku islands, and Kamuy, the Ainu (natives of the Japanese island of Hokkaido) word for a god. Gankoomon X merges with Hinukamuy and can release it as a surging aura that empowers it and destroys the landscape around it. It also takes off its shirt.


Gankoomon (left) and Gankoomon X (right)
The final and most recent member of the Royal Knights, debuting for the franchise's 15th anniversary, is JESmon. JES is an abbreviation of Justice Edge Swordsman. JESmon started out as Hackmon, a promising Child/Rookie level Digimon who aspired to be a Royal Knight. Gankoomon saw in it the potential to become the 13th Knight and put it through an intense training regiment. Eventually, Hackmon evolved to JESmon and was accepted by Yggdrasil as the 13th Royal Knight. Like its mentor, JESmon is a team player that works well with others, unlike the other Royal Knights. In working with others, JESmon lears to trust others and keep itself from becoming overconfident in its own abilities. Its usual allies are Sistermon Blanc and Sistermon Noir and it will also coordinate with the Digimon local to wherever it goes. JESmon has the ability to sense abnormalities and signs of chaos around the Digital World and will rush to stop them, making it the first of the Royal Knights to rush in to stop disasters. It has three familiars named Atho, René, and Por that fight along side it and can come together for an attack called Un Pour Tous. The familiars are named after Athos, Aramis, and Porthos, the Three Muskateers. Similarly, the attack is named after their catchphrase "Un pour tous, tous pour un" or "one for all, all for one", the motto of the Three Muskateers. JESmon X gains even more compat bower and turns Atho, René, and Por into two powerful arms. JESMon X and further evolve to JESmon GX, in which it has fully masters its power. In this form, it becomes the vessel for Knight's Intruder, a blade that contains the power of all the Royal Knights and will only be used in response to threats that would end the Digital World.



Left to right: JESmon, JESmon X, and JESmon GX
#digimon#royal knights#mythology#arthurian legend#arthurian mythology#king arthur#knights of the round table#omegamon#omnimon#magnamon#dukemon#gallantmon#alphamon#ulforceveedramon#dynasmon#craniummon#duftmon#leopardmon#sleipmon#kentaurosmon#lordknightmon#crusadermon#examon#gankoomon#jesmon
79 notes
·
View notes
Text
Russian Prosecutor General Igor Krasnov
The duties of Russia’s Prosecutor General’s Office go well beyond courtroom tasks as it also does a great deal of investigation while also interacting with the Russian public to ensure they receive what they’re entitled to and protect the public from it being fraudulently stolen. The actual details of some of those duties are outlined by President Putin in his address and followed up by Mr. Krasnov’s. I’ve reported on this annual event before mainly to show how this security ministry differs from the others. To a degree, they all work together, but the Prosecutor General has the added task of seeking out corruption wherever it lives. And yes, the military has its own branch as some high-profile cases revealed in 2024. I recall from last year’s Direct Line that Putin urged Russians to more confidently seek help from the Prosecutor’s Office in reporting cyber and telephone fraud, that it exists to help, not hinder. Now let’s read what Putin and Mr. Krasnov had to say:
Vladimir Putin: Dear Igor Viktorovich, Dear comrades, Today, as part of an expanded meeting of the Board of the Prosecutor General's Office, you will discuss the main results for 2024, identify the problem areas that should be focused on, and pay special attention to them. I would like to note that over the past period, prosecutors at all levels have done a lot of work. This is also indicated by the statistics. Thus, the number of applications and complaints to the prosecutor's office increased by ten percent, and the number of citizens received by prosecutors at a personal reception also increased. And this, of course, needs to be used–-to use all this information. I ask you to analyze in detail the most acute, systemic problems that concern and concern citizens, and give your suggestions for their comprehensive solution–-this is important for all levels of government in order to respond effectively, competently, and in a timely manner to citizens ' requests. And, of course, you need to understand each specific situation. In this regard, I would like to note that in many cases, it is thanks to your effective intervention that the violated rights of people have been restored, and the damage caused has been compensated. Much has also been done in the most important areas related to protecting the interests of the state and society.
3 notes
·
View notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Maybe this isn't the place to talk about it but I kinda just want to talk activism real quick. A some of you who follow me know I do most of my activism in real life I don't do as much of it online. That might be a flaw of mine and I am attempting it to figure out how to do activism in a way that can get a further reach online and that can incorporate more perspectives rather than just local ones especially considering I'm in a majority white American city. This being said there's not really a place to do activism properly online I feel like. Social media such as Tumblr or even Twitter are great places for mutual aid but they're not really good places to do actual activation I feel. The two main issues with any social media platform are 1) that they fail to be properly moderated in a way that can allow for coherent and real discussion, letting bad actors get away with far too much, and 2) a problem faced by any clear website is the fact that there's a lack of security especially when it comes to discussing extra legal solutions to problems.
With this being said the obvious solution feels like to take up to an onion and create a forum a potentially public for for leftist discussion. I do technically have the ability to do this but I don't have any skill and networking nor in defensive cyber security, so I don't really feel comfortable doing that and I've looked around and I don't think anything like this really exists. I have a job and in relatively comfortable financially all things considered so I theoretically could hire a cybersecurity specialist in order to protect the server but I don't particularly know how to do that and I don't know how comfortable I feel bringing money into what's supposed to be a public-free platform for discussion. I know a lot of cybersecurity people personally but they're all whiteheaded personally I don't know how much I trust a white hat to develop a site like this. Maybe there's another solution that I'm just an idiot and can't see but the whole point of this would be to be a more open dialogue so if any of y'all have any ideas on the matter whether it be from a cybersecurity perspective or a networking perspective or just an activism perspective please let me know.
9 notes
·
View notes
Text
Key Features to look for in Magento Hosting for Maximum Performance
Choosing the right hosting for a Magento store is quite an important issue to ensure a fast, secure, and seamless shopping experience. The following are the key features to look for in Magento hosting for maximum performance:
1. Speed and Performance Optimization: Advanced performance features of Magento hosting should include SSD storage, inbuilt caching like Varnish, and CDNs. These will help boost your website's loading speed so customers won't quit over delays. Search for hosting providers whose servers are optimized for the special demands of Magento.
2. Scalability: Your hosting should grow with your business. Find a solution to handle sudden traffic increases, especially when you run sales or special promotions. Look for scalable resources from cloud hosting, such as AWS or Google Cloud, to maintain smooth operations during heavy loads.
3. Magento Specific Support: Hosting with Magento expertise is vital. It is good to have Magento dedicated support, server configurations specifically for Magento, and compatibility with the latest Magento versions to ensure any problems are dealt with quickly and the sites stay up.
4. Robust Security Features: Since eCommerce remains the main target for cyber-attacks, your hosting should include firewalls, SSL certificates, DDoS protection, and malware scanning. Secure hosting means keeping the sensitive information of customers safe and preserving one's business reputation.
5. Easy Backup and Recovery: Downtime or loss of important data is something catastrophic. Hence, make sure the hosting package you choose covers automatic backup every day and that these are recoverable through a simple process. This provides business continuity, even on unplanned eventualities.

Focus on these features, and you will be able to choose Magento hosting that will add to the performance, reliability, and security of your store to ensure the success of your business in the competitive online market.
https://mageleven.com/
3 notes
·
View notes
Text

Name: Thomas “Jun-ho” Kang
Age: 38
Pronouns: he/him
Face Claim: Song Joong-ki
Occupation: CEO of the Midnight Spades Casino. He’s the youngest child of the Kang heir.
Neighborhood: Dynasty Hills
Biography
Thomas "Jun-ho" Kang, the youngest son of Min-ho Kang, occupies a peculiar position within the family hierarchy. Unlike his elusive father, he maintains a visible presence at Midnight Spades Casino, though he's careful to keep certain dealings well-hidden behind its polished façade.
After years at Swiss boarding schools and an American university, Thomas returned with ideas that set him apart from the old guard. He's modernised the family's money laundering through cryptocurrency and digital gaming - practical solutions that irritate the traditionalists even as they benefit from them.
His position as the second son has shaped his approach to business. While his older brother handles the traditional family operations, Thomas's carved out his own niche by becoming the go-to person for technological problems among the city's criminal families. He's built a network of useful connections through this expertise, though he keeps most people at arm's length.
The Onyx Circuit's emergence has complicated matters. he’s been pushing for inter-family cooperation and digital security upgrades, positions that have met resistance from those who prefer time-tested methods. Yet as cyber attacks increase, his warnings are starting to carry more weight.
He maintains a carefully cultivated public image, though his rumoured relationships raises eyebrows in certain circles. Whether this connection serves a strategic purpose or represents a genuine attachment remains unclear. Thomas avoids unnecessary violence, preferring to solve problems through financial pressure and digital manipulation. He respects tradition but isn't bound by it, a stance that makes him both valuable and somewhat suspect to Devil's Junction's established powers.
2 notes
·
View notes
Text
Top IT Career Training Programs in Melbourne & Sydney: Kickstart Your IT Journey
The demand for IT professionals in Australia is on the rise, with Melbourne and Sydney being key hubs for technology-driven careers. Whether you are looking for IT career training programs in Melbourne, IT jobs and training in Sydney & Melbourne, or IT service desk training in Australia, there are plenty of opportunities to build a strong foundation in the industry.

IT Career Training Programs in Melbourne
Melbourne offers a variety of IT training programs designed for beginners and experienced professionals alike. Some of the most popular courses include:
Cybersecurity Training – Learn to protect networks and systems from cyber threats.
Cloud Computing Certifications – Gain expertise in AWS, Microsoft Azure, or Google Cloud.
Software Development & Coding Bootcamps – Master programming languages like Python, Java, and C++.
IT Service Desk Training – Build essential skills for troubleshooting, customer support, and IT management.
Many institutions, such as TAFE Victoria, General Assembly, and private IT academies, provide both in-person and online training options.
IT Jobs and Training in Sydney & Melbourne
With major tech companies and startups in both cities, IT jobs and training in Sydney & Melbourne go hand in hand. Training programs often include job placement assistance, internships, and networking opportunities to help beginners land their first IT job.
Key job roles available after training:
IT Support Technician
Help Desk Analyst
Software Developer
Network Engineer
Data Analyst
Some programs offer certifications such as CompTIA A+, Microsoft Certified Solutions Associate (MCSA), and Cisco CCNA, which enhance employability in the Australian IT market.
IT Service Desk Training in Australia
For those looking to start their IT career with an entry-level role, IT service desk training in Australia provides the necessary skills for handling IT support tasks. Courses focus on:
Troubleshooting hardware and software issues
Managing IT tickets and service requests
Understanding ITIL frameworks and best practices
Communication skills for assisting end-users
Many IT service desk roles serve as a stepping stone to higher-paying positions in cybersecurity, cloud computing, and IT management.
IT Jobs for Beginners in Melbourne
If you're new to the industry and seeking It Jobs for Beginners Melbourne, look for roles that require minimal experience and provide on-the-job training. Some of the top entry-level IT jobs include:
Technical Support Assistant
Junior IT Administrator
IT Help Desk Operator
Data Entry & IT Support
Companies in Melbourne often seek candidates with a mix of training certifications and soft skills such as problem-solving and teamwork.
Final Thoughts
Australia’s tech industry is thriving, and with the right IT career training programs in Melbourne and Sydney, you can secure a promising future in the field. Whether you’re interested in IT service desk training in Australia or seeking IT jobs for beginners in Melbourne, investing in the right education and certifications will give you a competitive edge in the job market.
1 note
·
View note
Text
Blockchain technology in healthcare why hospitals are adopting it fast

1. Introduction
Blockchain in healthcare is revolutionizing the way hospitals manage patient data, security, and operational efficiency. With increasing cyber threats and inefficiencies in healthcare systems, hospitals are actively seeking innovative solutions. Blockchain technology for healthcare provides a decentralized, immutable, and transparent system that ensures data integrity, enhances security, and minimizes administrative burdens. The adoption of blockchain development services is accelerating as hospitals recognize its potential to streamline processes and improve patient outcomes.
2. The Challenges in Traditional Healthcare Systems
The healthcare industry faces persistent challenges that impact efficiency, security, and patient trust. Some of the most pressing issues include:
Data Breaches and Cyber Threats – Healthcare data is a prime target for cybercriminals. Patient records contain sensitive information, including medical histories, insurance details, and personal identification. Traditional databases are vulnerable to breaches, leading to significant financial and reputational damage.
Interoperability Issues – Hospitals and healthcare providers operate on different electronic health record (EHR) systems, making seamless data exchange difficult. Patients often experience delays in receiving treatment due to fragmented data systems.
Administrative Inefficiencies – Manual paperwork, redundant processes, and outdated record-keeping methods lead to operational inefficiencies. These inefficiencies increase costs and prolong patient wait times.
As hospitals strive to enhance efficiency and security, blockchain technology for healthcare offers a transformative solution.
3. How Blockchain Technology for Healthcare Solves These Problems
Blockchain development services provide hospitals with a robust framework to overcome these challenges. The key features of blockchain include:
Decentralized and Immutable Data Storage – Unlike traditional databases, blockchain stores patient data in a decentralized manner. This eliminates the risk of a single point of failure and prevents unauthorized alterations.
Enhanced Patient Data Security and Control – Blockchain encrypts patient data and grants access only to authorized users. Patients can control who accesses their medical records, ensuring privacy and security.
Seamless Interoperability – Blockchain enables secure and instant data exchange between hospitals, clinics, and laboratories. Medical professionals can access verified patient histories without intermediaries, reducing errors and improving care quality.
4. Key Benefits of Blockchain in Healthcare for Hospitals
The adoption of blockchain technology for healthcare is driven by several key advantages:
Data Security and Privacy – Blockchain's encryption and decentralization prevent unauthorized access to patient records. The immutability of data ensures that once information is recorded, it cannot be altered or deleted.
Interoperability Across Healthcare Providers – Hospitals can share verified medical records with other healthcare institutions without data loss or duplication. This seamless exchange reduces delays in treatment and enhances patient care.
Smart Contracts for Automation – Blockchain-powered smart contracts execute predefined agreements without human intervention. Hospitals use them for automated billing, insurance claims processing, and patient data transfers.
Fraud Prevention – Blockchain eliminates counterfeit drugs in the pharmaceutical supply chain by tracking medicines from production to distribution. Additionally, it prevents identity theft in medical insurance claims.
5. Real-World Applications of Blockchain Development Services in Healthcare
Hospitals are already leveraging blockchain technology for healthcare in various ways:
Electronic Health Records (EHR) Management – Secure and tamper-proof storage of patient records allows authorized medical professionals to access real-time data.
Automated Insurance Claims Processing – Smart contracts eliminate fraudulent claims by automatically verifying and executing insurance transactions. This reduces administrative costs and accelerates reimbursements.
Pharmaceutical Supply Chain Transparency – Blockchain tracks every stage of the drug supply chain, ensuring the authenticity of medications and preventing counterfeit drugs from entering the market.
Remote Patient Monitoring and Telemedicine – Blockchain stores and secures real-time patient data from wearable devices and telehealth consultations, improving remote care management.
6. Challenges Hospitals Face in Adopting Blockchain Technology
Despite its numerous benefits, hospitals encounter obstacles in blockchain adoption:
Regulatory and Compliance Hurdles – The healthcare industry operates under strict regulations regarding data protection and patient confidentiality. Adapting blockchain solutions to comply with regulatory frameworks requires careful planning.
Initial Costs and Infrastructure Upgrades – Implementing blockchain technology for healthcare demands investment in IT infrastructure and staff training. While the long-term benefits outweigh the costs, initial implementation can be expensive.
Training and Knowledge Gaps – Healthcare professionals and administrative staff need education on how to integrate and use blockchain-based systems effectively. Without proper training, adoption can be slow.
7. The Future of Blockchain in Healthcare
The rapid adoption of blockchain in healthcare suggests a promising future. Here are some key developments on the horizon:
Integration with Artificial Intelligence (AI) and Internet of Things (IoT) – AI-powered analytics combined with blockchain will enable predictive healthcare models, while IoT devices will securely transmit real-time patient data.
Government Adoption of Blockchain – Countries are exploring blockchain-based healthcare solutions for national medical record management and insurance processing.
Increased Patient Control Over Data – Blockchain will empower patients to access and share their medical records securely, enhancing transparency and trust in healthcare systems.
Conclusion
Hospitals are rapidly adopting blockchain technology for healthcare to address long standing challenges in data security, interoperability, and administrative inefficiencies. By leveraging blockchain development services, hospitals can improve patient care, reduce costs, and enhance trust within the healthcare ecosystem. As smart contracts and decentralized data management become the norm, blockchain will continue to shape the future of modern healthcare, paving the way for a more secure and efficient industry.
#technology#blockchain development#blockchain development services#blockchain in healthcare#smart contracts#blockchain technology in healthcare
1 note
·
View note
Text
Full Stack Testing vs. Full Stack Development: What’s the Difference?

In today’s fast-evolving tech world, buzzwords like Full Stack Development and Full Stack Testing have gained immense popularity. Both roles are vital in the software lifecycle, but they serve very different purposes. Whether you’re a beginner exploring your career options or a professional looking to expand your skills, understanding the differences between Full Stack Testing and Full Stack Development is crucial. Let’s dive into what makes these two roles unique!
What Is Full Stack Development?
Full Stack Development refers to the ability to build an entire software application – from the user interface to the backend logic – using a wide range of tools and technologies. A Full Stack Developer is proficient in both front-end (user-facing) and back-end (server-side) development.
Key Responsibilities of a Full Stack Developer:
Front-End Development: Building the user interface using tools like HTML, CSS, JavaScript, React, or Angular.
Back-End Development: Creating server-side logic using languages like Node.js, Python, Java, or PHP.
Database Management: Handling databases such as MySQL, MongoDB, or PostgreSQL.
API Integration: Connecting applications through RESTful or GraphQL APIs.
Version Control: Using tools like Git for collaborative development.
Skills Required for Full Stack Development:
Proficiency in programming languages (JavaScript, Python, Java, etc.)
Knowledge of web frameworks (React, Django, etc.)
Experience with databases and cloud platforms
Understanding of DevOps tools
In short, a Full Stack Developer handles everything from designing the UI to writing server-side code, ensuring the software runs smoothly.
What Is Full Stack Testing?
Full Stack Testing is all about ensuring quality at every stage of the software development lifecycle. A Full Stack Tester is responsible for testing applications across multiple layers – from front-end UI testing to back-end database validation – ensuring a seamless user experience. They blend manual and automation testing skills to detect issues early and prevent software failures.
Key Responsibilities of a Full Stack Tester:
UI Testing: Ensuring the application looks and behaves correctly on the front end.
API Testing: Validating data flow and communication between services.
Database Testing: Verifying data integrity and backend operations.
Performance Testing: Ensuring the application performs well under load using tools like JMeter.
Automation Testing: Automating repetitive tests with tools like Selenium or Cypress.
Security Testing: Identifying vulnerabilities to prevent cyber-attacks.
Skills Required for Full Stack Testing:
Knowledge of testing tools like Selenium, Postman, JMeter, or TOSCA
Proficiency in both manual and automation testing
Understanding of test frameworks like TestNG or Cucumber
Familiarity with Agile and DevOps practices
Basic knowledge of programming for writing test scripts
A Full Stack Tester plays a critical role in identifying bugs early in the development process and ensuring the software functions flawlessly.
Which Career Path Should You Choose?
The choice between Full Stack Development and Full Stack Testing depends on your interests and strengths:
Choose Full Stack Development if you love coding, creating interfaces, and building software solutions from scratch. This role is ideal for those who enjoy developing creative products and working with both front-end and back-end technologies.
Choose Full Stack Testing if you have a keen eye for detail and enjoy problem-solving by finding bugs and ensuring software quality. If you love automation, performance testing, and working with multiple testing tools, Full Stack Testing is the right path.
Why Both Roles Are Essential :
Both Full Stack Developers and Full Stack Testers are integral to software development. While developers focus on creating functional features, testers ensure that everything runs smoothly and meets user expectations. In an Agile or DevOps environment, these roles often overlap, with testers and developers working closely to deliver high-quality software in shorter cycles.
Final Thoughts :
Whether you opt for Full Stack Testing or Full Stack Development, both fields offer exciting opportunities with tremendous growth potential. With software becoming increasingly complex, the demand for skilled developers and testers is higher than ever.
At TestoMeter Pvt. Ltd., we provide comprehensive training in both Full Stack Development and Full Stack Testing to help you build a future-proof career. Whether you want to build software or ensure its quality, we’ve got the perfect course for you.
Ready to take the next step? Explore our Full Stack courses today and start your journey toward a successful IT career!
This blog not only provides a crisp comparison but also encourages potential students to explore both career paths with TestoMeter.
For more Details :
Interested in kick-starting your Software Developer/Software Tester career? Contact us today or Visit our website for course details, success stories, and more!
🌐visit - https://www.testometer.co.in/
2 notes
·
View notes
Text
Comparing Wordpress Hosting in the UK
When it comes to building a website, one of the most critical decisions you'll make is selecting a hosting provider. For those seeking a platform that combines flexibility, ease of use, and scalability, **WordPress hosting in the UK** is an excellent choice. In this blog post, we will delve into various aspects of WordPress hosting specifically tailored for the UK market, helping you make an informed decision.
What Is Wordpress Hosting and Why Is It Important?
**WordPress hosting** refers to a type of web hosting that is optimised specifically for WordPress websites. Unlike generic web hosting, WordPress hosting is tailored to enhance the performance, security, and management of WordPress sites. This optimisation can take various forms, including server configurations, caching mechanisms, and specialised support. The importance of WordPress hosting lies in its ability to provide a seamless and efficient website experience. A well-optimised hosting environment can significantly improve site speed, which is crucial for retaining visitors and achieving higher search engine rankings. In addition, WordPress hosting often includes built-in security features such as automatic updates, malware scanning, and SSL certificates, which help protect your site from cyber threats. Another critical aspect is the ease of management. Many WordPress hosting providers offer managed services, meaning they handle technical tasks like software updates, backups, and security patches. This allows website owners to focus more on content creation and business operations rather than technical maintenance. Managed hosting can be particularly beneficial for those who lack technical expertise or simply wish to save time. Furthermore, specialised support is a key benefit of WordPress hosting. Providers typically have support teams well-versed in WordPress, capable of resolving issues more efficiently than general hosting support. This can be a lifesaver when facing unexpected problems or needing guidance on optimising your site. Finally, WordPress hosting often comes with additional tools and features designed to enhance functionality, such as one-click installations, staging environments, and developer tools. These features make it easier to customise and extend your website according to your specific needs.
Key Features to Look for in a UK WordPress Hosting Provider
When selecting a WordPress hosting provider, focusing on specific features can ensure you get the best performance and reliability for your site. One of the top priorities should be **managed WordPress hosting**, which handles tasks like updates and backups, freeing you to concentrate on content creation. Additionally, **automatic backups** are essential, providing peace of mind that your data is secure and can be restored if needed. **Security features** should be high on your list, including SSL certificates, firewalls, and malware scanning to protect your site from various threats. Equally important is **scalability**, allowing your hosting solution to grow with your website without requiring a complex migration process. **Customer support** is another crucial feature. Opt for providers that offer 24/7 support, ensuring assistance is available whenever you need it. Look for support options like live chat, phone, and a comprehensive knowledge base to troubleshoot issues swiftly. Other valuable features include **staging environments** for testing changes safely before deploying them live, and **one-click installations** for easy setup. **Content Delivery Networks (CDNs)** and **SSD storage** can further enhance your site's speed and performance, particularly important for retaining visitors and improving SEO rankings.
Top WordPress Hosting Providers in the UK
Several reputable WordPress hosting providers operate in the UK, each offering unique features and benefits to cater to different needs: - **SiteGround**: Renowned for its stellar customer support and managed WordPress hosting options. SiteGround is ideal for users seeking reliable performance and ease of management. - **Bluehost**: Officially recommended by WordPress, Bluehost provides a user-friendly experience, making it an excellent choice for beginners. Their plans include automatic updates and robust security features. - **Kinsta**: A premium managed hosting provider that focuses heavily on performance and speed, utilising Google Cloud infrastructure. Kinsta's services are suited for high-traffic websites that require top-notch performance. - **WP Engine**: Known for its high performance, robust security measures, and comprehensive support. WP Engine offers advanced features like staging environments and developer tools, making it a strong option for professionals. - **Fasthosts**: A UK-based provider offering budget-friendly plans without compromising on support. Fasthosts provides scalable solutions suitable for both small and large websites, with options to upgrade as your needs grow. - **TsoHost**: Offers a range of plans including shared, VPS, and cloud hosting, designed to cater to diverse requirements. Their UK-based data centres ensure optimal speed and compliance with local regulations. These providers offer a variety of plans and features, allowing you to find a solution that fits your specific needs and budget.
Speed and Performance Considerations for UK Users
Website speed is a pivotal element influencing user experience and search engine optimisation (SEO) rankings. For users in the UK, opting for a hosting provider with servers located within the country can drastically improve loading times, as proximity to the server reduces latency. Beyond server location, other critical factors to consider include caching solutions and Content Delivery Networks (CDNs). Caching stores a version of your website so that it can be delivered faster to repeat visitors, while CDNs distribute your content across multiple global locations, ensuring quicker access for users regardless of their geographic location. Solid State Drives (SSDs) also play a crucial role by providing faster data retrieval compared to traditional Hard Disk Drives (HDDs). Look for hosting providers that offer advanced performance features such as PHP 7.x support, HTTP/2, and integrated caching mechanisms like Varnish or Memcached. These technologies can enhance the speed at which your website loads, improving overall user satisfaction. In addition, regular monitoring and performance analytics can help identify bottlenecks and areas for improvement. Many UK-based WordPress hosting providers include these tools in their plans, enabling you to make data-driven decisions to optimise your site's performance continuously. Focusing on these aspects ensures your website not only meets but exceeds the expectations of your UK audience, fostering better engagement and higher retention rates.
Understanding Security Features in UK WordPress Hosting
**Security is paramount when it comes to maintaining a reliable and trustworthy website. UK-based WordPress hosting providers often implement a range of robust security measures designed to protect your site from various cyber threats. Regular malware scans are essential, offering early detection and removal of malicious software that could compromise your website's integrity.** **DDoS protection is another critical feature, safeguarding your site against Distributed Denial of Service attacks, which aim to overwhelm your server with traffic, rendering it inaccessible. Automatic updates ensure that your WordPress software and plugins remain current, addressing potential vulnerabilities as soon as fixes are released.** **Firewalls serve as a barrier against unauthorised access, blocking malicious traffic and preventing attacks. Additionally, many hosting providers include intrusion detection systems to monitor and respond to suspicious activity in real time.** **Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of identification beyond just a password, making it significantly harder for attackers to gain access. SSL certificates are typically standard, encrypting data transmitted between your site and its visitors to protect sensitive information like login credentials and payment details.** **Finally, some providers offer security audits and vulnerability assessments, providing insights into potential risks and recommendations for improvement. These comprehensive security measures collectively enhance the safety and reliability of your WordPress site in the UK.**
Customer Support: Why Localised Support Matters
Access to localised customer support can make a significant difference when managing your WordPress site. Local support teams understand the unique challenges and requirements faced by UK-based websites, offering more tailored and effective assistance. They are also well-versed in local regulations, such as GDPR, ensuring that your website complies with legal standards. Language and time zone compatibility are additional benefits of localised support. When you encounter an issue, you can expect quicker response times and clearer communication, eliminating the frustration of language barriers and inconvenient support hours. This immediate assistance is invaluable, particularly in urgent situations where downtime could impact your business. Many UK hosting providers offer 24/7 support, giving you peace of mind that help is available whenever you need it. Whether through live chat, phone support, or an extensive online knowledge base, local support teams can resolve issues more efficiently. They are familiar with the specific needs and expectations of UK customers, which can result in more relevant and effective solutions. In addition, localised support often means a more personalised experience. UK-based providers typically have smaller support teams, allowing them to offer a higher level of customer service. This personal touch can make all the difference, especially for small businesses and individual site owners who may require more dedicated assistance.
Pricing: Getting the Best Value for Your Money
When evaluating pricing for **WordPress hosting in the UK**, it's essential to balance cost with value. While a lower price can be enticing, scrutinise the features and services included. Assess factors such as storage capacity, bandwidth limits, and the quality of customer support provided. Some providers offer introductory rates that increase upon renewal, so be aware of long-term costs. Look for packages that include essential features like SSL certificates, automatic backups, and security enhancements without additional charges. Compare different providers to ensure you're not missing out on critical functionalities. Some hosting companies offer flexible payment plans, such as monthly or annual billing, which can help manage your budget more effectively. Additionally, consider any hidden fees that may arise, such as charges for exceeding bandwidth or additional storage. By carefully analysing these elements, you can find a hosting solution that offers both affordability and comprehensive support, ensuring you get the best return on your investment.
Scalability and Flexibility of UK Hosting Providers
As your website evolves, having a hosting provider that supports scalability and flexibility becomes paramount. UK hosting providers often offer plans that can be easily upgraded to accommodate increased traffic, storage, and other resource demands. This capability is crucial for businesses anticipating growth, ensuring that your site can handle higher visitor numbers without performance issues. Look for providers that offer seamless upgrade paths, allowing you to enhance your plan without experiencing downtime or complex migration processes. Flexible hosting solutions often include options like VPS (Virtual Private Server) and dedicated hosting, which provide more control and resources compared to shared hosting environments. This flexibility allows you to adjust your hosting environment to meet changing needs effectively. Many UK hosting providers also offer pay-as-you-go models, enabling you to add resources like bandwidth and storage as required, without committing to higher-tier plans upfront. This approach is particularly beneficial for seasonal businesses or websites that experience fluctuating traffic levels. Additionally, some providers offer features like auto-scaling, which automatically allocates more resources during traffic spikes to maintain optimal performance. Finally, ensure that your hosting provider supports various integrations and plugins, allowing you to extend your website's functionality as needed. This adaptability can be a significant advantage, providing the tools necessary to grow and enhance your site over time.
The Importance of Data Centres and Server Locations in the UK
For websites targeting a UK audience, the location of data centres is a critical factor that directly impacts performance. Hosting your site on servers located within the UK can drastically reduce latency, leading to faster load times for local visitors. This proximity to the server ensures that data travels a shorter distance, which can significantly enhance the user experience. Local data centres also play a crucial role in compliance with GDPR regulations. UK-based data centres are more likely to adhere to local data protection laws, providing an added layer of security for your website’s data. This is particularly important for businesses that handle sensitive customer information, ensuring that data is stored and processed within legal frameworks. Additionally, having data centres in the UK means that your hosting provider can offer more reliable support tailored to your specific needs. Localised infrastructure allows for quicker response times in case of technical issues, ensuring that your site remains operational with minimal downtime. This can be especially beneficial during peak traffic periods when site performance is paramount. Lastly, the environmental impact of data centres should not be overlooked. Many UK hosting providers are adopting green energy solutions to power their data centres, aligning with broader sustainability goals and reducing carbon footprints. This not only supports environmental initiatives but also enhances your brand's commitment to sustainability.
Specialised WordPress Hosting Options Available in the UK
For WordPress users with specific needs, several UK hosting providers offer specialised hosting options. **WooCommerce hosting** is designed for e-commerce sites, providing features that enhance speed, security, and transaction handling. This type of hosting often includes pre-installed WooCommerce plugins, optimised server configurations, and dedicated support for online stores. **Multisite hosting** is another specialised option, ideal for users managing multiple WordPress sites from a single dashboard. This solution simplifies the management process, offering a centralised control panel to handle updates, backups, and other administrative tasks across all sites. **Staging environments** are crucial for those who wish to test changes or new features without affecting their live site. These environments allow users to create a copy of their site to experiment safely before deploying updates, ensuring that any potential issues can be resolved beforehand. Additionally, some providers offer **developer-focused hosting** with advanced tools such as SSH access, Git integration, and customisable server settings. These features cater to developers who require a high degree of control over their hosting environment, enabling them to tailor their setup to specific project needs. By offering these specialised options, UK WordPress hosting providers cater to a diverse range of requirements, making it easier for users to find a solution that aligns with their unique needs.
User Experience: How UK Providers Enhance Usability
UK hosting providers focus heavily on enhancing usability to ensure a seamless experience for their users. Many offer intuitive control panels like cPanel or custom-built dashboards that simplify website management tasks. These interfaces often feature drag-and-drop functionalities, making it straightforward for users to upload files, manage domains, and configure email settings without needing technical expertise. Providers frequently include one-click installations for WordPress and other popular applications, streamlining the setup process. This feature allows users to launch their websites quickly without grappling with complex configurations. Additionally, many UK hosting companies offer extensive knowledge bases, video tutorials, and community forums, providing valuable resources for troubleshooting and site optimisation. For ongoing site maintenance, automated tools such as backup services and update notifications are commonly integrated. These tools ensure that sites remain secure and up-to-date with minimal manual intervention. Enhanced usability extends to performance monitoring features, enabling users to track metrics like site speed and uptime easily. Real-time analytics help identify potential issues before they impact the user experience, allowing for prompt resolution. By prioritising these user-friendly features, UK hosting providers make website management accessible, even for those with limited technical skills.
Case Studies: Success Stories from UK-Based WordPress Sites
The success of UK-based websites using WordPress hosting is evident through various case studies. Take "The Independent," a leading news outlet that utilises WordPress for its robust content management system. By leveraging advanced caching solutions and Content Delivery Networks (CDNs), they've optimised their site speed and user experience, accommodating millions of daily visitors efficiently. Another notable example is "Graze," the snack subscription service that has scaled its e-commerce operations seamlessly with specialised WooCommerce hosting. The integration of automatic backups, SSL certificates, and tailored support has allowed them to maintain a secure and efficient online store, boosting customer trust and engagement. Local educational institutions like "University of Oxford" have also benefitted from WordPress hosting. Utilising features such as staging environments and managed hosting services, they have created dynamic, user-friendly portals that cater to students and faculty alike. Small businesses like "BrewDog," a craft beer company, have taken advantage of developer-focused hosting to customise their websites extensively. This flexibility has enabled them to create unique, engaging online experiences that align with their brand identity. These examples demonstrate the diverse capabilities of WordPress hosting in the UK, catering to various industries and needs effectively.
Environmental Impact: Green Hosting Options in the UK
As environmental concerns take centre stage, many UK hosting providers are adopting eco-friendly practices to reduce their carbon footprint. These green hosting solutions often involve using renewable energy sources, such as wind or solar power, to operate data centres. Energy-efficient hardware and cooling technologies further minimise energy consumption, ensuring a more sustainable operation. Providers like GreenGeeks and Eco Web Hosting have made significant strides in this area, offering services that not only perform well but also contribute positively to the environment. Some companies even participate in carbon offset programmes, planting trees or investing in renewable energy projects to balance out their emissions. Additionally, hosting companies may implement policies to reduce waste, such as promoting digital documentation over printed materials and encouraging remote work to cut down on travel emissions. By choosing a green hosting provider, you can support these environmental initiatives, aligning your website with broader sustainability goals.
Final Thoughts: Choosing the Best WordPress Hosting for Your Needs
Selecting the best WordPress hosting in the UK can be a daunting task, given the myriad of options available. However, focusing on key aspects such as performance, security, customer support, and scalability can streamline your decision-making process. Performance is vital; ensure the provider offers advanced caching solutions, SSD storage, and local data centres to optimise loading times. Security should not be compromised, so look for features like SSL certificates, firewalls, and regular malware scans. Customer support is another crucial factor, particularly localised support that understands UK-specific challenges and regulations. 24/7 availability and multiple support channels can provide peace of mind and quick resolutions to any issues. Scalability is essential for future growth. Opt for a provider that offers seamless upgrade paths and flexible resource allocation to accommodate increasing traffic and storage needs. Specialised hosting options, such as WooCommerce hosting for e-commerce sites or developer-focused hosting, can offer additional benefits tailored to your specific requirements. Finally, consider the environmental impact. Green hosting options not only benefit the planet but can also enhance your brand's sustainability credentials. By weighing these factors carefully, you can find a WordPress hosting solution that aligns perfectly with your goals and ensures a smooth, secure, and efficient online presence.
#web hosting#cheap web hosting#hosting#managed wordpress hosting#website hosting#wordpress hosting#businesss#online businesses#cheap website hosting#online
2 notes
·
View notes
Text
What distinguishes an unmanaged (self-managed) VPS from a managed one And how can I figure out which suits me the best?
When looking at web hosting options, it is essential to have a solid understanding of the distinction between managed virtual private servers (VPS) and unmanaged VPS. Those who are looking for an experience that is simple to use will find that managed virtual private servers (VPS) provide convenience in server setup, maintenance, and support. On the other hand, unmanaged virtual private servers (VPS) provide you with complete control over the server, allowing you to customize and administer it in any way you see fit.

This type of VPS is best for people or enterprises who value flexibility and cost-effectiveness. In this post, we will discuss the important differences that will assist you in selecting the virtual private server (VPS) solution that is best suited to meet your individual requirements.
VPS: What is it?
First, let's get a grasp on what virtual private server hosting (VPS) is and how it operates before we move on to analyzing the distinctions between managed and unmanaged VPS hosting. Virtual private server hosting (VPS hosting) is a method of delivering hosting services in which a single physical server is partitioned into several virtual servers. The processing power (CPU), memory (RAM), and storage space utilized by each virtual server are distinct from those utilized by any other machine.
In spite of the fact that these virtual servers are established on a single physical system, they conduct their operations independently of one another. As a result of the shared underlying hardware, each user is provided with their very own dedicated virtual server, which is analogous to having a dedicated physical server but at a lesser cost. Each user's data and applications are kept separate and secure, exactly as if they were running on their own physical server because the servers are geographically separated from one another. This ensures that the servers are isolated from one another.
What exactly is a managed virtual private server?
As the name suggests, managed virtual private servers (VPS) mean that you do not have to worry about the responsibilities that are associated with the server, such as administering and maintaining your server. Your web hosting provider will be responsible for monitoring and managing all of the server's functionality. In spite of the fact that you are familiar with the technical features of the server and how to manage it, outsourcing the management of the server to your web hosting provider will alleviate the stress of carrying out all of the procedures.
The specialists who work for your web hosting provider take full responsibility for the resources on your server. They also keep a constant watch on your server to identify any potential issues, and they are responsible for implementing any necessary updates and upgrades. In particular, for users who do not have a lot of time to devote to duties that are related to the server.
The Benefits of Using a Managed Virtual Private Server-
Managed VPS hosting, also known as virtual private server hosting, provides a multitude of advantages, particularly for customers who are more concerned with the development of their applications or businesses than with the management of server infrastructure. Below are the primary benefits that come with using this service:
Firewalls, virus scanning, intrusion detection, and frequent security upgrades are some of the robust security features that managed virtual private server (VPS) software providers implement. Data is protected and cyber dangers are avoided as a result of this.
By delegating server management to a dependable web hosting provider, customers are able to concentrate solely on the operations of their businesses or the creation of applications without having to worry about the infrastructure of their servers, security concerns, or other problems.
The hosting service offers users round-the-clock technical help during their membership. This involves the installation of servers, their maintenance, and the diagnosis and resolution of technical problems in a timely manner.
Managed virtual private server (VPS) plans typically include data restoration and periodic backup services in the event that problems arise. Data recovery is made simple and expedient by the supplier, who is responsible for maintaining backups and setups.
The activities associated with server management are handled by the web hosting provider. These responsibilities include the configuration of hardware and software, the updating and patching of operating systems, the monitoring of performance, and the carrying out of frequent backups. Users will have less of a load as a result, and the server will continue to function in a stable manner.
Through the use of this service, users are able to gain access to the knowledge and experience of server management specialists. The availability of technicians allows for the provision of recommendations and the enhancement of server performance.
In general, managed virtual private server services provide higher levels of stability and constant uptime. In order to reduce the amount of time of the outage, providers utilize redundant infrastructure and monitoring technologies.
Managed virtual private server hosting is, in a nutshell, the best option for people and enterprises who require a high level of security, simplicity of management, and reliability. It provides a full solution for hosting websites and applications with little fees associated with the technical side of things and maximum peace of mind throughout the process.
What is the Unmanaged Virtual Private Server?
Your hosting provider will investigate a physical server and its availability when you use an unmanaged virtual private server (VPS). This means that you are responsible for managing and maintaining the server, as well as managing and maintaining the server itself. Choosing unmanaged virtual private server hosting necessitates either possessing the necessary technical expertise or employing a group of professionals to administer your server.
The use of an unmanaged virtual private server (VPS) is preferable for a well-established organization, regardless of how technically proficient you may be. The development of your company will be the primary focus of your attention if you are a startup. Your server management needs to be handled by a team and a full-time position in order to be successful.
The Benefits of Using an Unmanaged Virtual Private Server-
There are a lot of advantages to using unmanaged VPS (Virtual Private Server) hosting, particularly for users who are technically capable of managing their own server environment. The primary advantages are as follows:
Users are equipped with complete control, which enables them to install, configure, and optimize the server in accordance with their own requirements.
This presents users with the opportunity to increase their skills in managing and operating servers.
There is no dependence on third-party vendors for tasks such as software upgrades, and it may be tailored to meet personalized requirements.
Unmanaged virtual private servers (VPS) are typically more affordable than managed VPS because they do not include administration services, software upgrades, or technical support.
Security measures are under the authority of the users, who are responsible for ensuring their own safety.
The server can be customized in any way that the user desires, including the operating system, control panel, and software.
However, unmanaged virtual private servers are best suited for someone who possesses technical expertise or someone who can assist in managing the server. If this is not the case, a managed virtual private server (VPS) service, albeit being more expensive, can be a preferable option.
Which of These Options Should You Pick?
You are now aware that Managed Virtual Private Servers (VPS) and Unmanaged VPS each have their own set of advantages at their disposal. It is recommended that you go with unmanaged hosting if you are a professional in the field of technology, have experience maintaining servers, and have the ability to devote sufficient time to operating a server. If, on the other hand, you are a novice or a startup that has to concentrate on expanding your business, then managing a virtual private server (VPS) can be a laborious task.
The technical assistance that you receive with managed virtual private servers helps you save crucial hours. This enables you to concentrate on your primary goals, which may include managing your staff, making income, establishing relationships with customers, and other similar activities. Conversely, if you are concerned about the costs and have a good understanding of the server and how it is administered, then an unmanaged virtual private server (VPS) will be a better option for you.
Conclusion-
Users believe that it is dependable and risk-free to obtain a managed virtual private server (VPS) from a hosting provider, despite the fact that managed VPS is somewhat more expensive than self-managed VPS. This is because the price of managed VPS has decreased over time. It is also better to choose managed hosting if the procedure of setting up the server is going to have an impact on your company and take a significant amount of time.
Another aspect that should be taken into consideration is safety. It is not a bad idea to go with an unmanaged virtual private server (VPS) if you are willing to assume full responsibility for the safety of your server and be sure that it will be protected from the dangers that are there on the internet.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Top 7 Challenges Faced By IT Industry In 2023
Within the rapidly growing universe of technology, the IT companies in India assume a crucial role, persistently adjusting themselves to cater to the needs of a perpetually shifting environment. Nevertheless, the advancement of society brings forth a set of obstacles that necessitate a deliberate approach to resolution. As the year 2023 commences, the IT industry faces a multitude of challenges that necessitate careful consideration and effective measures. This blog aims to explore the primary issues encountered by the IT industry in the current year, providing insights into their consequences and possible remedies.

1. Cybersecurity Threats:
The escalation of cyber risks has been observed as a consequence of the widespread adoption of digital technology and interconnected systems. The level of sophistication exhibited by cybercriminals is on the rise, as they deploy advanced strategies to bypass security systems. All the IT companies in Gujarat, India, in the year 2023 are confronted with the formidable challenge of maintaining a competitive edge in the face of cyber attacks, while simultaneously prioritising data protection and securing essential infrastructure. The implementation of effective cybersecurity safeguards, regular conduct of security audits, and provision of cybersecurity education to staff are essential elements in addressing and minimising this risk.
2. Data Privacy and Compliance:
The increasingly stringent legislative framework surrounding data privacy poses a substantial obstacle for the information technology sector. Stringent regulations pertaining to data privacy, such as the General Data Privacy Regulation (GDPR), necessitate rigorous adherence. In the year 2023, the IT companies in Vadodara, Gujarat have the challenge of striking a delicate equilibrium between adhering to regulatory requirements and efficiently using data for commercial objectives. IT organisations are required to allocate resources towards the implementation of compliance frameworks, provide training to their employees, and guarantee that data-handling procedures are in accordance with the prescribed norms.
3. Talent Acquisition and Retention:
The acquisition and retention of talent pose an ongoing problem for the IT industry, as it continues to seek and keep qualified workers. The scarcity of highly specialised skills frequently results in a disparity between demand and supply, hence engendering intense rivalry for those with such talents. Moreover, the current trends in remote work and the increasing globalisation of the talent market serve to exacerbate this challenge. In order to tackle this issue, a reliable IT company in India like Nivida Web Solutions prioritises the enhancement of the skills of their current workforce, provides enticing remuneration packages, cultivates a favourable work environment, and creates avenues for professional advancement and personal improvement.
4. Technological Advancements and Adaptability:
The expeditious rate at which technological developments are occurring has both advantages and disadvantages for the IT business. Although these developments present promising prospects, they also present a difficulty in terms of adaptation. Keeping abreast of developing technology and enabling a smooth transition to new platforms and tools may be a demanding task. In order to effectively adapt to emerging technology, IT organisations must allocate resources towards the implementation of continual training and development programmes, which aim to equip their personnel with the requisite skills.
5. Resource Optimization and Scalability:
The optimisation of resources and the effective scalability of operations have emerged as significant challenges in recent times. The management of resources and the scaling of operations in response to varying market needs and the imperative of cost-effectiveness can provide intricate challenges. Cloud computing and intelligent resource allocation are essential solutions that can be employed to effectively address this dilemma. The utilisation of cloud solutions by Nivida Web Solutions - a recognised IT company in Gujarat, India, allows for enhanced flexibility and cost-efficiency, hence assuring the appropriate allocation of resources.
6. Integration and Interoperability:
The IT environment is distinguished by a diverse array of systems and applications that necessitate harmonious integration. The task of achieving integration and interoperability across diverse platforms, legacy systems, and emerging technologies poses a significant challenge. The establishment of interconnectedness is crucial in facilitating an effective and productive IT ecosystem. It is imperative for the industry to prioritise the development of standardised interfaces, utilise APIs effectively, and implement integration platforms in order to improve interoperability.
7. Environmental Sustainability:
Environmental sustainability has emerged as a pressing issue in various sectors, encompassing the field of IT. The IT industry possesses a substantial carbon footprint as a result of its energy consumption, generation of electronic waste, and operations of data centres. In the year 2023, the sector is faced with the task of identifying environmentally sustainable solutions and adopting practices that effectively mitigate their ecological footprint. The use of green technology, the optimisation of data centre efficiency, and the incorporation of circular economy concepts are positive measures in the pursuit of sustainability objectives.
Final Thoughts:
The IT sector encounters a diverse range of issues in the year 2023, necessitating the implementation of proactive and strategic methodologies. Addressing a range of difficulties, including cybersecurity risks, talent acquisition, technological adaptation, and sustainability, is necessary in order to establish and maintain a flourishing and sustainable information technology ecosystem. By adopting a proactive approach towards innovation, allocating resources towards skill enhancement, and placing emphasis on adherence to regulations and sustainability, Nivida Web Solutions - the most distinguished IT company in Vadodara, may effectively navigate the obstacles it faces and emerge with increased resilience. This will facilitate the ongoing growth and progression of the industry in the era of digitalization.
7 notes
·
View notes
Text
I'm perfectly aware that the place to put this post is linkedin and not Tumblr.com (although i might make a more professional-looking version).
Anyway, I'm horrified by the amount of cyber attacks that are happening in the last few days. Especially because a couple of these are really big companies, and one would think they have an IT department that knows how to do their job. Even better, they should have at least one person that deals with cybersecurity.
I know that security operations centers (where we use very expensive systems to monitor the networks and the assets of the companies, plus we often investigate previous security incidents and produce intelligence reports) are expensive. I work in one and it's not the solution that works for everyone. A small company with few employees definitely cannot afford a SOC, but a big corporation? That would be nice (again, it's not the only solution and every client is different, you need to tailor the cybersecurity solution to the client).
But a videogame studio? I would expect them to take security seriously. And not only because of the data involved, but industrial espionage is a thing (although it's difficult to prove and it happens rarely that it's taken to a court, however it does happen), but it's a risk. A worldwide clothing company? A fucking bank? Sure.
The problem with certain things it's that "it won't happen to me". Until it does. And you end up paying 300x than you would be paying at least a cybersecurity consultant to prevent the attack.
Even better, a lot of the simplest measures are free to implement. No USB from home policy. Disabling local administrator accounts. Implement a strong password policy. Implement a blacklist for suspicious websites (and also, maybe stop downloading cracked software if you don't know where to find reputable sources? I see you trying to download that CoD aimbot, how embarrassing)
Implement a strong antispam policy (which is fundamental, as this is very very often the access point - you send a targeted spam email to a company with 3k employees and I can guarantee you that at least one will download the malicious file or insert the credential on the fake office 365 website, it's just what it is.)
But most people won't, because "it's annoying" and users don't want to put the effort to like, keep their fucking job and remember a 12 character password(yes, a company can suffer so much damage from a cyber attacks that it might even close the business, and yes, I had to fight with clients that refuse to change their AD admin accounts set in 2015 even when I told them about a potential leak) Not to mention that the data stolen often is the employees data. And you don't want your identity stolen by a criminal, do you?
And the danger when these attacks are carried against hospitals. People can die if the whole network shuts down because no one cared to implement basic cybersecurity.
And it's not true that organisations don't have the budget. We both know you are lying lol.
Don't get me wrong, there is nothing foolproof, there will always be a certain amount of risk.
I just expect people to use some good sense and I'm often disappointed lol.
4 notes
·
View notes
Text
Unlocking Success with Utah CPA IT: Navigating the World of IT Services for Accountants
In today's fast-paced digital landscape, Utah CPA firms depend on reliable IT services from Utah CPA IT to thrive. Your accounting tasks operate smoothly, backed by the technological prowess of Utah CPA IT services.
Therefore, let's delve into this world where Utah CPA IT simplifies complex tech matters. Here, we break down the jargon and make IT accessible to everyone.
Utah CPA IT Services: A Beacon of Efficiency
We'll explore how Utah CPA IT services are transforming the way accountants operate in the Beehive State. No longer are IT woes a headache; instead, they become an ally, streamlining your operations.
Navigating Utah IT Outsourcing
Utah CPA IT services offer a lifeline through IT outsourcing, allowing your firm to focus on core accounting tasks while experts handle your technology needs. This strategic move not only brings cost savings but also ensures peace of mind, knowing that your IT infrastructure is in the hands of professionals who understand the unique requirements of CPA firms in Utah.
Utah IT Support: Your 24/7 Lifesaver
Discover the world of Utah IT support, where issues are resolved swiftly, ensuring you're never left in the dark. Whether it's a minor glitch or a major technical challenge, our expert team is here to provide prompt solutions, keeping your operations running smoothly without missing a beat.
Unlocking Potential with Utah Office 365 Support
Discover how Utah CPA IT services go beyond the basics to leverage the full potential of Office 365, significantly boosting your team's productivity. Also, unleash the collaborative features, data accessibility, and seamless communication that Office 365 offers with the support of Utah CPA IT experts.
Defending Your Castle: Utah Cybersecurity
Explore the realm of Utah cybersecurity and how it shields your sensitive data from digital marauders.
Throughout this journey, we'll keep the path well-lit, ensuring you understand every step. Therefore, let's begin this expedition into the world of Utah CPA IT, simplifying the complex for the benefit of all.
Understanding the IT Needs of CPA Firms
Utah CPA firms, like any other businesses, rely on technology to operate efficiently. But what exactly are their IT needs, and why are they crucial? Let's break it down in simple terms.
The Basics of IT for CPAs
CPA firms in Utah use computers, software, and the internet for their day-to-day tasks. Moreover, they need reliable IT systems to manage financial data, communicate with clients, and stay compliant with ever-changing regulations.
Utah CPA IT Challenges
Security: Protecting sensitive financial data from cyber threats is a top concern.
Efficiency: IT systems must be efficient to ensure quick data processing.
Communication: Smooth communication within the firm and with clients is essential.
Why Utah IT Support Matters
Utah IT support providers play a vital role. They help CPA firms choose the right technology, set up systems, and provide assistance when issues arise. Also, think of them as IT problem solvers.
Outsourcing for Efficiency
Many Utah CPA firms choose to outsource their IT needs. Also, this means hiring experts from outside the firm to handle IT tasks. In addition, it's like hiring a specialist for a specific job, ensuring that everything runs smoothly.
Benefits of Utah CPA IT Services
When it comes to the benefits of Utah CPA IT services, the advantages are crystal clear. Moreover, let's delve into why more and more CPA firms in Utah are turning to IT services to boost their efficiency and success.
1. Enhanced Efficiency
Utah CPA IT services streamline your daily operations. also, with expert assistance at your fingertips, tasks that used to take hours can now be completed in minutes. Also, giving your team more time to focus on crucial financial matters.
2. Cost Savings
By opting for Utah IT outsourcing, you can significantly reduce your IT expenses. No need to worry about maintaining an in-house IT team or purchasing expensive hardware and software. This means more savings in the long run.
3. Reliable IT Support
With Utah IT support, you're never alone in your IT journey. Also, experts are available 24/7 to resolve any issues or answer your questions promptly. Say goodbye to downtime and hello to uninterrupted workflow.
4. Seamless Integration with Office 365
Utah CPA IT services ensure a seamless connection with Utah Office 365 support. This means improved collaboration, easy access to files, and enhanced communication within your firm.
5. Strong Cybersecurity
Your data's security is a top priority. Utah CPA IT services offer robust Utah cybersecurity measures to safeguard your sensitive financial information from cyber threats and breaches.
In conclusion, investing in Utah CPA IT services is a smart move. It boosts efficiency, saves you money, and provides reliable support for your accounting firm. Make the switch today, and watch your productivity soar.
Choosing the Right IT Solutions for Utah CPA Firms
In today's tech-driven world, Utah CPA firms must choose the best IT solutions to thrive. Moreover, selecting the ideal Utah CPA IT support is crucial. Here's a simplified guide:
1. Identify Your Needs
Start by understanding your CPA firm's unique IT requirements. What specific challenges do you face? Knowing this will guide your decision.
2. Research Local Providers
Look for Utah IT outsourcing companies that specialize in serving CPA firms. They understand the local market and your industry's needs.
3. Check Expertise
Ensure the provider has experience working with CPA firms in Utah. Expertise matters when it comes to managing your IT systems effectively.
4. Assess Scalability
Your IT needs may grow over time. Choose a provider that can scale its services as your firm expands.
5. Evaluate Security Measures
Data protection is vital for CPA firms. Verify that the Utah IT support provider has robust cybersecurity measures in place.
6. Consider Cost-Efficiency
While cost is a factor, focus on the long-term benefits. Utah Office 365 support, for instance, can enhance productivity and justify the investment.
7. Read Client Reviews
Check reviews and testimonials from other Utah CPA firms. Additionally, their experiences can offer valuable insights.
8. Request a Consultation
Contact potential providers for a consultation. Discuss your needs and assess their responsiveness and willingness to assist.
Implementing and Integrating Utah CPA IT Solutions
In the world of accounting, Utah CPA IT solutions are vital. They make things smoother, but how do you get started?
Getting Started with Utah CPA IT
First, you need to understand what Utah CPA IT is all about. In addition, it's not rocket science. Moreover, Utah CPA IT is simply about using smart technology to help CPA firms work better.
Selecting the Right Utah IT Outsourcing Partner
Next, find the right folks to help you out. You need a reliable Utah IT outsourcing partner. They'll be your IT buddies.
Utah IT Support: Your IT Lifesavers
Think of Utah IT support as your ready to friend that you can rely on in any moment. They are here to rescue you when tech troubles strike.
Seamless Integration with Utah Office 365 Support
Now, let's talk about making everything fit together. Also, Utah Office 365 support can make your work-life more organized and efficient.
Locking Down with Utah Cybersecurity
Safety first! Utah cybersecurity ensures your precious data stays safe and sound.
Putting it All Together
Once you have your Utah CPA IT solutions lined up, it's time to put everything into action. But, don't worry; it's not as complicated as it sounds.
Your IT partner will work with your CPA firm to make sure all the tech pieces fit seamlessly. In other words, they will set up the right software, ensure your data is safe, and provide ongoing support.
In addition, the best part is that you don't have to be a tech wizard to make it happen. Also, Utah CPA IT experts will guide you through every step. It's like having a knowledgeable tech companion right beside you.
Conclusion
In conclusion, at AnchorSix embracing Utah CPA IT services is the key to unlocking success for CPA firms in the digital age. With the ever-increasing importance of technology, having a reliable IT backbone is no longer a luxury but a necessity. Utah CPA IT services not only simplify complex tech matters but also transform IT from a source of headaches into a strategic ally that streamlines your operations.
Moreover, from outsourcing IT needs to providing 24/7 support, our expert team ensures that your technology infrastructure is in capable hands. Also, the benefits are crystal clear: enhanced efficiency, cost savings, reliable IT support, seamless integration with Office 365, and robust cybersecurity. This investment in simplicity, efficiency, and peace of mind will elevate your accounting firm's productivity and success. Therefore, make the switch today and watch your firm thrive in the digital landscape.
Visit us: https://anchorsix.com/
2 notes
·
View notes
Text
Pioneering the Next Era: Envisioning the Evolution of AWS Cloud Services
In the fast-paced realm of technology, the future trajectory of Amazon Web Services (AWS) unveils a landscape rich with transformative innovations and strategic shifts. Let's delve into the anticipated trends that are set to redefine the course of AWS Cloud in the years to come.

1. Surging Momentum in Cloud Adoption:
The upward surge in the adoption of cloud services remains a pivotal force shaping the future of AWS. Businesses of all sizes are increasingly recognizing the inherent advantages of scalability, cost-effectiveness, and operational agility embedded in cloud platforms. AWS, positioned at the forefront, is poised to be a catalyst and beneficiary of this ongoing digital transformation.
2. Unyielding Commitment to Innovation:
Synonymous with innovation, AWS is expected to maintain its reputation for introducing groundbreaking services and features. The future promises an expansion of the AWS service portfolio, not merely to meet current demands but to anticipate and address emerging technological needs in a dynamic digital landscape.
3. Spotlight on Edge Computing Excellence:
The spotlight on edge computing is intensifying within the AWS ecosystem. Characterized by data processing in close proximity to its source, edge computing reduces latency and facilitates real-time processing. AWS is slated to channel investments into edge computing solutions, ensuring robust support for applications requiring instantaneous data insights.
4. AI and ML Frontiers:
The forthcoming era of AWS Cloud is set to witness considerable strides in artificial intelligence (AI) and machine learning (ML). Building upon its legacy, AWS is expected to unveil advanced tools, offering businesses a richer array of services for machine learning, deep learning, and the development of sophisticated AI-driven applications.
5. Hybrid Harmony and Multi-Cloud Synergy:
Flexibility and resilience drive the ascent of hybrid and multi-cloud architectures. AWS is anticipated to refine its offerings, facilitating seamless integration between on-premises data centers and the cloud. Moreover, interoperability with other cloud providers will be a strategic focus, empowering businesses to architect resilient and adaptable cloud strategies.

6. Elevated Security Protocols:
As cyber threats evolve, AWS will heighten its commitment to fortifying security measures. The future holds promises of advanced encryption methodologies, heightened identity and access management capabilities, and an expanded array of compliance certifications. These measures will be pivotal in safeguarding the confidentiality and integrity of data hosted on the AWS platform.
7. Green Cloud Initiatives for a Sustainable Tomorrow:
Sustainability takes center stage in AWS's vision for the future. Committed to eco-friendly practices, AWS is likely to unveil initiatives aimed at minimizing the environmental footprint of cloud computing. This includes a heightened emphasis on renewable energy sources and the incorporation of green technologies.
8. Tailored Solutions for Diverse Industries:
Acknowledging the unique needs of various industries, AWS is expected to craft specialized solutions tailored to specific sectors. This strategic approach involves the development of frameworks and compliance measures to cater to the distinctive challenges and regulatory landscapes of industries such as healthcare, finance, and government.
9. Quantum Computing Integration:
In its nascent stages, quantum computing holds transformative potential. AWS may explore the integration of quantum computing services into its platform as the technology matures. This could usher in a new era of computation, solving complex problems that are currently beyond the reach of classical computers.
10. Global Reach Amplified:
To ensure unparalleled service availability, reduced latency, and adherence to data sovereignty regulations, AWS is poised to continue its global infrastructure expansion. This strategic move involves the establishment of additional data centers and regions, solidifying AWS's role as a global leader in cloud services.
In summary, the roadmap for AWS Cloud signifies a dynamic and transformative journey characterized by innovation, adaptability, and sustainability. Businesses embarking on their cloud endeavors should stay attuned to AWS announcements, industry trends, and technological advancements. AWS's commitment to anticipating and fulfilling the evolving needs of its users positions it as a trailblazer shaping the digital future. The expedition into the future of AWS Cloud unfolds a narrative of boundless opportunities and transformative possibilities.
2 notes
·
View notes