#complete ISO 27001 implementation
Explore tagged Tumblr posts
Text
#ISO 27001 audits#ISO 27001 certification#ISO 27001 training#requirements of the ISO 27001 standard#ISO 27001 internal audits#complete ISO 27001 implementation#training on IT Security Management System#ISO 27001 Consultant#ISO 27001 Consultancy Services
1 note
·
View note
Text
A Complete Guide on ISO 27001 Certification

#ISO 27001 is an internationally recognized standard for Information Security Management Systems (ISMS). This standard provides a framework f#procedures#and controls that help protect their sensitive information from cyber threats.#Here is a complete guide on ISO 27001 Certification:#Understanding the Standard: The first step is to understand the ISO 27001 standard cost and its requirements. This includes a detailed stud#as well as an assessment of your organization's current information security processes#policies#and procedures.#Gap Analysis: Conduct a gap analysis to identify any areas where your organization is not meeting the requirements of the standard. This wi#Designing the System: Once you have identified the gaps#you can begin to design your information security management system (ISMS). This will involve developing policies and procedures that are i#Implementation: After designing the system#you can implement the policies#and controls across your organization. This may involve providing training to your employees and raising awareness of the importance of inf#Internal Audit: Conduct internal audits to ensure that your ISMS is effective and compliant with the ISO 27001 standard. This will help you#Certification: After your ISMS has been in operation for a suitable period#you can apply for ISO 27001 certification. This involves an external audit by an accredited ISO certification body#who will assess whether your ISMS meets the requirements of the standard.#Continual Improvement: Once you have achieved certification#you will need to maintain your ISMS and continually improve it to ensure that it remains effective and compliant with the standard.#ISO 27001 certification can help to improve your organization's reputation#demonstrate your commitment to information security#and reduce the risk of cyber attacks. It is applicable to organizations of all sizes and in all sectors.
0 notes
Text
My Journey with Azure IoT Hub: Connecting and Managing IoT Devices at Scale
The Internet of Things (IoT), which enables seamless connectivity and automation across numerous industries, has completely changed the way we engage with technology. I was curious to learn more about the Internet of Things and its possible uses as an aspiring IoT enthusiast. My experience using Azure IoT Hub, Microsoft’s cloud-based IoT platform, and how it assisted me in connecting and managing IoT devices at scale are both discussed in this blog.
Getting Started with Azure IoT Hub

To embark on my IoT journey, I began by understanding the fundamentals of Azure IoT Hub. Azure IoT Hub is a fully managed service that acts as a central hub for bi-directional communication between IoT devices and the cloud. It provides secure, reliable, and scalable connectivity for IoT solutions. Setting up an Azure IoT Hub was my first step. While the process was relatively straightforward, I encountered a few challenges along the way.
Connecting IoT Devices
Once Azure IoT Hub was set up, I delved into the world of IoT devices. I worked with various types of IoT devices, ranging from simple sensors to complex industrial machines. Connecting these devices to Azure IoT Hub required the implementation of device-specific protocols such as MQTT or HTTP. Additionally, I focused on securing device connections and data transmission by utilizing security features provided by Azure IoT Hub.
Real-world examples of IoT devices connected to Azure IoT Hub are aplenty. For instance, in the healthcare industry, wearable devices can transmit patient vitals to Azure IoT Hub, allowing healthcare providers to monitor and respond to critical situations promptly. In smart homes, IoT devices such as thermostats and security cameras can be connected to Azure IoT Hub, enabling remote control and monitoring capabilities.
Managing IoT Devices at Scale
As my IoT project grew, I encountered the need to scale up the number of connected devices. Azure IoT Hub offered robust device management features that simplified the process of managing a large fleet of devices. I could remotely monitor the health, status, and firmware version of each device, enabling efficient troubleshooting and maintenance. Implementing best practices for device management, such as grouping devices based on location or functionality, enhanced the overall operational efficiency of my IoT solution.
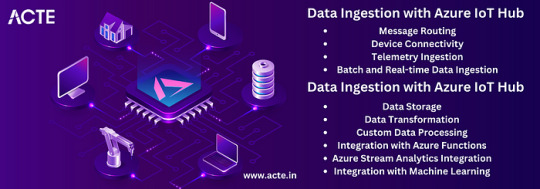
Data Ingestion and Processing
Data collected from IoT devices is a valuable asset that can drive actionable insights and informed decision-making. Azure IoT Hub facilitated the ingestion and routing of data to Azure services for further processing and analysis. I had the opportunity to work with Azure Stream Analytics and Azure Functions, which enabled real-time data processing, transformation, and visualization. Leveraging these services allowed me to unlock the true potential of IoT data and derive meaningful insights.
Security and Compliance
Any IoT solution must prioritize security. Azure IoT Hub provided robust security features that ensured end-to-end protection of IoT deployments. These features included device authentication, message encryption, and integration with Azure Active Directory for access control. Additionally, Azure IoT Hub helped me meet compliance and regulatory requirements by providing built-in support for industry standards such as ISO 27001, HIPAA, and GDPR. Throughout my journey, I learned valuable lessons and implemented best practices for securing IoT solutions.
Scalability and Performance
Scaling an IoT solution to handle thousands or millions of devices is a complex task. Azure IoT Hub offered scalability features that allowed me to effortlessly handle large-scale IoT deployments. With Azure IoT Hub’s device-to-cloud messaging capabilities, I could reliably transmit messages to and from a massive number of devices. Moreover, I gained insights into optimizing IoT solutions for performance by considering factors such as message size, frequency, and device capabilities.
Real-World Use Cases
To understand the versatility of Azure IoT Hub, it is crucial to explore real-world use cases. In the manufacturing industry, Azure IoT Hub can be leveraged to connect and monitor machines on the factory floor, ensuring optimal performance and predictive maintenance. In the agriculture sector, IoT devices connected to Azure IoT Hub can collect data on soil moisture levels, temperature, and humidity, enabling farmers to make data-driven decisions for irrigation and crop management. These use cases highlight the valuable role that Azure IoT Hub plays in various domains and industries.
Future of IoT and Azure IoT Hub
The future of IoT is promising, with emerging trends shaping the landscape. As IoT continues to evolve, Azure IoT Hub will play a crucial role in enabling seamless connectivity, advanced analytics, and artificial intelligence capabilities. Integration with other Azure services and continuous updates from Microsoft ensure that Azure IoT Hub remains at the forefront of IoT innovation. The possibilities for IoT applications are limitless, and Azure IoT Hub will continue to empower developers and organizations to build robust and scalable IoT solutions.
Throughout my journey with Azure IoT Hub, I gained valuable insights and experiences. Azure IoT Hub simplified the process of connecting and managing IoT devices, providing a reliable and scalable platform. The seamless integration with other Azure services allowed me to unlock the full potential of IoT data. Moreover, the security and compliance features provided peace of mind, ensuring that my IoT solution was protected from threats. Overall, Azure IoT Hub has been instrumental in my IoT journey, contributing to enhanced efficiency and productivity.
Recommendations and Tips
For those interested in starting their own IoT journey with Azure IoT Hub, I offer the following recommendations and tips:
Begin with a clear understanding of your IoT use case and requirements.
Familiarize yourself with the documentation and resources provided by Microsoft to gain a solid foundation.
Start small and gradually scale your IoT solution as needed.
Take advantage of the device management and security features offered by Azure IoT Hub.
Leverage other Azure services such as Azure Stream Analytics and Azure Functions to derive meaningful insights from IoT data.
Stay updated on emerging trends and best practices in the IoT space.
To deepen your knowledge of IoT and Azure IoT Hub, I recommend exploring Microsoft’s official documentation, participating in the ACTE Technologies Microsoft Azure training, and attending IoT-focused conferences and events.

Azure IoT Hub has proven to be a powerful and comprehensive platform for connecting and managing IoT devices at scale. Throughout my journey, I witnessed the transformative potential of IoT solutions and the crucial role played by Azure IoT Hub in enabling seamless connectivity, advanced analytics, and robust security. As IoT continues to evolve, Azure IoT Hub will undoubtedly remain at the forefront of IoT innovation, empowering organizations to build scalable and efficient IoT solutions. I encourage readers to embark on their own IoT journeys, leveraging the capabilities of Azure IoT Hub to unlock the full potential of IoT. Join me in embracing the future of IoT and revolutionizing industries through connected devices. Please leave your comments, stories, and inquiries in the space provided below. Let’s continue the conversation and explore the endless possibilities of IoT together.
#microsoft azure#cloud services#information technology#education#tech#technology#iot#innovation#cloud computing
5 notes
·
View notes
Text
ISO 27001 Lead Auditor Training
What is ISO 27001 Lead Auditor Training?
ISO 27001 Lead Auditor Training is an intensive program that provides participants with the skills and knowledge necessary to perform lead audits for organizations that have implemented the ISO 27001 Information Security Management Standard. The course is designed for experienced auditors who wish to become certified as ISO 27001 Lead Auditors.
Importance
ISO 27001 is the global standard for information security management. Organizations that implement ISO 27001 are able to demonstrate their commitment to data security and protect their customers’ confidential information. Becoming certified as an ISO 27001 Lead Auditor allows you to audit organizations against this internationally recognized standard.
Benefits
Gaining the expertise and knowledge to conduct lead audits for businesses that have implemented the ISO 27001 Information Security Management Standard.
Learn how to evaluate information security controls using the ISO 27001 standard.
Understand how to assess risk and report on findings.
Develop expertise in auditing information security management systems.
Demonstrate your commitment to data security and protect your customers’ confidential information.
Become certified as an ISO 27001 Lead Auditor.
Advance your career in information security auditing.
Who Should Attend?
The iso 27001 lead auditor training is designed for experienced auditors who wish to become certified as ISO 27001 Lead Auditors. The course is also relevant for anyone working in a role that requires an understanding of the ISO 27001 standard, such as information security managers, risk managers, and compliance officers.
Pre-requisites
Candidates who wish to enroll in this program should have a good understanding of ISO 27001 standards and the concepts of information security and risk management. iso 27001 lead auditor course
How Can One Join This Training?
The best way to join the ISO 27001 Lead Auditor Training is to find an accredited training center and sign up for a course. The course will usually last for five days, and participants will be awarded a certificate once they have successfully completed the training. You can also find many online courses that offer the same training content but over a longer period of time.
Conclusion
iso 27001 lead auditor training can be the perfect way to acquire in-depth knowledge of information security management system (ISMS) standards, their requirements, and implementation. The skills learned during the course can help organizations implement and manage an ISMS effectively. Additionally, the lead auditor training can also help organizations prepare for audits against ISO 27001.
corso iso 27001
0 notes
Text
Achieve ISO Certification in Mumbai with BCS Certification Service
ISO (International Organization for Standardization) certification is a globally recognized standard that demonstrates a business’s commitment to quality, efficiency, and customer satisfaction. Obtaining an ISO certification provides businesses with a competitive edge and builds trust with customers, partners, and stakeholders. In Mumbai, one of the leading names in the field of ISO certification and consultancy services is BCS Certification.
BCS Certification is a well-established Mumbai-based consultancy firm specializing in ISO management system certification, process implementation services, and company registration services. With a strong focus on helping businesses enhance their processes, we offer end-to-end services to simplify the certification process and help clients achieve compliance with international standards.
Our services are designed to cater to a wide range of industries, including manufacturing, healthcare, IT, construction, hospitality, and more. We provide IAF-accredited certificates such as:
ISO 9001 (Quality Management System)
ISO 14001 (Environmental Management System)
ISO 45001 (Occupational Health and Safety Management System)
ISO 22000 (Food Safety Management System)
ISO 27001 (Information Security Management System)
ISO 13485 (Quality Management System for Medical Devices)
HACCP Certification (Hazard Analysis and Critical Control Points)
GMP Certification (Good Manufacturing Practice)
Why Choose BCS Certification?
Expert Guidance: Our team of experienced consultants guides businesses at every step, from understanding certification requirements to implementing management systems and successfully completing the certification process.
Customized Solutions: We recognize that every business is unique. Therefore, we offer customized services tailored to meet the specific needs and objectives of each organization.
Comprehensive Support: BCS Certification provides end-to-end support, including process evaluation, documentation, system implementation, and pre-certification audits to ensure a seamless certification experience.
Affordable and Reliable: Our services are competitively priced without compromising on quality. We aim to deliver reliable and efficient solutions that provide long-term benefits for your business.
ISO certification is a valuable investment for any business seeking to enhance its reputation, attract new customers, and improve internal processes. It signifies a business’s ability to meet international standards and demonstrates its focus on continuous improvement and customer satisfaction.
With extensive experience in the field, BCS Certification has helped numerous companies across Mumbai and beyond achieve their certification goals. Whether you’re a startup, a growing enterprise, or an established business, our team is ready to assist you in achieving compliance and building a stronger foundation for success.
Contact Us Today 📞 +91 7900021431 📧 [email protected] 📍 GoodWill CHS, Opp. MI Showroom, Nr. Hanuman Temple, Manickpur, Vasai — 401202
Let BCS Certification be your trusted partner in achieving ISO certification and elevating your business to new heights. Reach out to us for a consultation and take the first step toward improving your processes and gaining a competitive advantage.
0 notes
Text
How Do Lean Data Governance and ISO Standards improve Cloud Data Management ?
In today’s fast-evolving digital landscape, organizations are increasingly relying on cloud data management to store, process, and analyze massive volumes of information. However, without a structured data governance framework, companies risk poor data quality, security breaches, and non-compliance with industry regulations. This is where Lean Data Governance and ISO Standards come into play, offering a strategic approach to optimizing data management while ensuring compliance and efficiency.
youtube
The Importance of Lean Data Governance in Cloud Management
Lean Data Governance focuses on minimizing redundancies, improving data accuracy, and fostering a culture of accountability. Unlike traditional data governance models that can be rigid and cumbersome, Lean Data Governance aligns with agile methodologies, making it adaptable to cloud environments.
Some key benefits of Lean Data Governance include:
Enhanced Data Quality: Ensuring accurate, complete, and consistent data across cloud platforms.
Improved Compliance: Adhering to ISO standards, GDPR, and other regulatory frameworks.
Optimized Cost Efficiency: Reducing storage waste and improving cloud resource utilization.
Faster Decision-Making: Providing high-quality data for AI, analytics, and business intelligence.
Role of ISO Standards in Cloud Data Management
ISO standards provide globally recognized guidelines to enhance data security, privacy, and governance in the cloud. Some essential ISO standards for cloud data management include:
ISO/IEC 27001: Information security management system (ISMS) for safeguarding cloud data.
ISO/IEC 38505–1: Governance of data for cloud-based applications.
ISO/IEC 8000: Ensuring high-quality, accurate, and reliable data.
By implementing these standards, organizations can establish trust, mitigate risks, and align their data management strategies with industry best practices.
How Lean Data Governance & ISO Standards Work Together
Combining Lean Data Governance with ISO standards creates a powerful synergy that optimizes cloud data management. Lean principles streamline data operations, while ISO compliance ensures security, consistency, and regulatory adherence. This integrated approach empowers businesses to:
Eliminate data silos and inconsistencies.
Strengthen cybersecurity measures against potential threats.
Improve operational efficiency and scalability in cloud environments.
Learn More: Watch the Full Video
This video breaks down the core principles of Lean Data Governance and ISO Standards, offering real-world use cases and actionable insights to help organizations refine their cloud data management strategies.

Final Thoughts
As cloud adoption continues to grow, organizations must prioritize Lean Data Governance and ISO Standards to ensure seamless data management. By implementing these best practices, businesses can achieve greater data quality, security, and compliance, paving the way for long-term success in the digital era.
Stay ahead of the curve by adopting Lean Data Governance & ISO Standards today!
For more expert insights, don’t forget to watch the full video: Click Here and subscribe to our PiLog Group YouTube Channel for more valuable content!
#Lean Data Governance#Data Cloud#Cloud Data Management#iso standard#youtube#piloggroup#data management solutions#big data#iso certification#data governance#data analytics#data scientist#Youtube
0 notes
Text
ISO Certification Cost Made Easy by Certelite Bangalore
In today’s highly competitive market, achieving operational excellence is not just a luxury it’s a necessity. ISO certification costhttps://certelite.com/ is one of the most recognized standards globally that can transform your business by boosting customer trust, improving operational efficiency, and opening doors to new opportunities. If you're searching for reliable ISO certification services in Bangalore, Certelite Quality Assurances is your go-to partner for achieving this prestigious accreditation.

Why ISO Certification Matters
ISO (International Organization for Standardization) sets global benchmarks in various industries for quality, safety, efficiency, and environmental management. Obtaining ISO certification demonstrates your company’s commitment to excellence and compliance with international standards.
Whether you are a start-up aiming to establish credibility or a seasoned organization looking to expand globally, ISO certification can provide a competitive edge. But the process requires expertise, meticulous documentation, and in-depth understanding—which is where Certelite Quality Assurances steps in.
Certelite Quality Assurances: Your Trusted ISO Partner
Based in the vibrant city of Bangalore, Certelite Quality Assurances offers tailored ISO certification services for businesses of all sizes. With years of experience, Certelite has earned a reputation for delivering seamless and reliable certification solutions.
What Sets Certelite Apart?
1. End-to-End Guidance: From understanding your business needs to completing certification audits, Certelite ensures you achieve compliance with ease.
2. Expert Consultants: A team of skilled professionals with expertise across industries ensures tailored solutions for ISO standards like ISO 9001 (Quality
Management), ISO 14001 (Environmental Management), ISO 27001 (Information Security), and more.
3. Affordable ISO Certification Cost: Certelite offers transparent pricing and ensures cost-effective solutions, making ISO certification cost accessible to businesses across sectors.
4. Customized Solutions: Whether you need help with documentation, process improvement, or internal audits, the services are tailored to suit your organization’s specific requirements.
5. Timely Delivery: Time is money, and Certelite ensures your certification process is completed without unnecessary delays.
Understanding ISO Certification Cost
One of the first questions business owners ask is, “What is the cost of ISO certification?” While the ISO certification cost varies depending on several factors, Certelite ensures affordability without compromising on quality.
Here are key factors influencing ISO certification costs:
Type of Certification: Different ISO standards have varying cost structures. For instance, ISO 9001 may differ from ISO 14001 or ISO 27001.
Business Size: Larger organizations often require more extensive audits, increasing the certification cost.
Documentation and Readiness: If your processes need significant improvements, additional costs may arise for consultancy and implementation.
Audit Frequency: Surveillance audits and recertification audits also contribute to the overall cost.
Certelite provides a transparent breakdown of costs and helps you understand where your investment goes. Their cost-effective services ensure that even small and medium businesses can access ISO certification cost and enjoy its numerous benefits.
Benefits of ISO Certification with Certelite
Enhanced Credibility: Gain customer trust by demonstrating compliance with international standards.
Operational Efficiency: Streamlined processes reduce waste and boost productivity.
Global Opportunities: ISO certification is a global standard, opening up new markets for your business.
Risk Management: Robust processes minimize risks related to quality and compliance issues.
Why Choose Certelite for ISO Certification in Bangalore?
Bangalore is a bustling hub for innovation and business growth. To stay ahead, companies need reliable partners to help them achieve international standards. Certelite bridges the gap between businesses and ISO certification cost with its customer-centric approach and expertise.
From reducing ISO certification costs to delivering hassle-free solutions, Certelite ensures your journey to ISO certification is smooth and successful.
Final Thoughts
ISO certification is an investment in your company’s future, and Certelite Quality Assurances is here to ensure you get the best value. With their expert services,
affordable ISO certification cost, and commitment to excellence, achieving ISO certification in Bangalore has never been easier.
Take the first step towards global recognition and operational excellence—partner with Certelite Quality Assurances today!
0 notes
Text
ISO 27001 Certification: Contributions toward Bracing Data Security in Nepal
Introduction
Data protection has turned to be one of the vital concerns for any organization in this modern era of digitization. Gradual growth in using digital avenues to store sensitive information in Nepal develops the need for data protection accordingly. Indeed, ISO 27001 has given a complete framework for assurance in the field of data protection and thus is considered one of the major tools used by any organization in securing assets and building trusts in Nepal.

Understanding ISO 27001 Certification
ISO 27001 is the globally accepted standard referring to how management operates an Information Security Management System. A major intention of the ISO 27001 certification is to indicate whether any mechanisms for the safeguarding of sensitive information have been taken by the concerned organization-most importantly, data protection of valuable records. These kinds of organizations believe in continuous improvement pertaining to security habits.
Why Data Protection is an Increasingly Current Issue in Nepal
Digital Transformation: Increased cloud computing, e-commerce, and digital banking-in short, the attack surface of organizations keeps growing.
Regulatory Pressures: While most parts of the world are growing with data protection regulations, even Nepal has started taking initial steps in setting up its schema in a gradual manner for the emerging demands that need to meet compliance.
Emerging Cyber Threats: Data breach amidst other kinds of cyber-attacks, to which ransomware has joined the bandwagon-the momentum sifts against big and small-scale organizations.
Customer Expectation: By all clients and partners, there is an increasingly strong expectation that sensitive information is duly looked after.
Key Benefits of ISO 27001 Accreditation in Protection of Data
Threat-Based Approach to Wholesome Risk Management:
ISO 27001 helps any organization to find loopholes within the information system, followed by the implantation of efficient controls managing associated risks.
2. Gain Trust:
Certification would reassure clients, partners, and regulators that protection of data is of utmost concern and taken care of by the organization.
3. Compliance to Regulations:
Certification under ISO 27001 means that the organization works within the frames of many local and international law sets covering data protection; thus this becomes one of the ways through which it tries to avoid being fined by these regulations.
This standard lays immense emphasis on constant monitoring and improvement. It helps an organization outpace emerging threats.
4. Business Resilience:
Adequate security, therefore, will minimize the effects of a data breach and consequently ensure business continuity.
Steps Towards Achieving ISO 27001 for Data Protection
Initiation: Secure management support and define scope for ISMS.
Risk Assessment: Clearly identify all kinds of threats to information security and judge the consequence of each.
Policy Development: Based on the risks identified, policies and procedures shall be developed to mitigate the same.
Implementation: The ISMS shall then be implemented in the organization by following the policy.
Awareness and Training: To train the staff for the role they are going to play in data protection.
Internal Audit: Periodically look at the shortcomings and rectify them.
Certification Audit: An accredited certification body is engaged. It sees whether an organization meets conformance against the ISO 27001 standard.
7. Continuous Improvement: Monitoring of ISMS, updating it with evolving risks.
ISO 27001 in Key Sectors in Nepal
Banking and Finance:
The banking and financial industry deals with customer financial information; hence, a very important role for ISO 27001 in information security can help build better trust among its customers.
2. Health Care:
Information of patient records has to be dealt with by hospitals or clinics, so ISO 27001 provides the guidelines to secure sensitive types of medical information.
3. Information Technology and Software Development:
ISO 27001 Certification proves that the IT organization is giving necessary consideration in data security. It will open up the way for the attraction of international business in this company.
4. Education:
Correspondingly with increase in these online learning websites, institutions are equally provided with the opportunity to practice ISO 27001 in information security of students and employees alike.
ISO 17025 Certification Complementing ISO 27001
While ISO 27001 looks at information security, ISO 17025 provides assurance in the reliability of the work carried out at the testing and calibration laboratories. In general, the standards provide a very good base regarding matters of quality and security, especially to those organizations that have been working within the manufacture and research sectors.
Practical Examples in Nepal
This has made various organizations of Nepal already implement the ISO 27001 Standard so as to increase protection measures for data. IT companies have taken up the certificate in securing data from their clients so as to extend their marketplace. Similarly, financial institutions have utilized ISO 27001 in order to conform with regulatory policies and build up the confidence of customers.
Conclusion:
It would, in return, make Nepal's data protection stronger with the help of ISO 27001, as it allows any company that holds comprehensive sensitive protection and compliance to the dynamically changing regulations to offer better performance with advanced cybersecurity postures, further resilience, and also the building of stakeholder confidence in an organization. Another very complementary certification with this is ISO 17025 which allows an organization to build its excellent reputation. The secured and trusted digital ecosystem, so crucial in bringing about digital transformation in Nepal, will give way to ISO certification.
#ISO 27001 Certification Services#ISO 27001 Certification in Nepal#ISO 27001 Certification Services in Kathmandu
0 notes
Text
How ISO Certification Helps Businesses Compete in Global Markets

Article Summary
In today's global marketplace, where competition is fierce and consumer expectations are ever-evolving, maintaining high standards of quality, safety, and efficiency is essential for businesses to thrive. ISO certification.In this article, we delve into the significance of ISO certification, its benefits, challenges, and the transformative impact it has on businesses worldwide
Understanding ISO Certification briefly
ISO certification signifies that an organization has successfully implemented and adhered to the requirements of a specific ISO standard relevant to its industry or sector. The certification process involves an independent assessment by accredited certification bodies to ensure compliance with the standard's guidelines and criteria. Upon successful completion of the assessment, the organization is awarded ISO certification, which serves as a testament to its commitment to quality, safety, and customer satisfaction
Here’s how ISO certification can help businesses compete and thrive in the global marketplace.
1. Access to New Markets
ISO certifications, such as ISO 9001 (Quality Management), ISO 14001 (Environmental Management), and ISO 27001 (Information Security), are recognized worldwide as symbols of quality and compliance with international standards. Many global buyers and suppliers require companies to hold ISO certifications as a prerequisite for doing business. For instance, in sectors like food production, healthcare, and manufacturing, international clients prefer working with businesses that comply with established global standards, as it reduces the risk of poor-quality products or non-compliance with local regulations.
By earning ISO certification, companies gain credibility and access to new market opportunities that may otherwise have been unavailable. International customers know that an ISO-certified company adheres to consistent and reliable practices, making them more likely to choose that company over competitors who lack certification.
2. Building Trust with Global Customers
When competing on a global scale, trust is everything. Customers around the world want to know that they are dealing with a company that can consistently deliver high-quality products or services. ISO certifications provide proof that a business is committed to maintaining high standards in quality, safety, environmental sustainability, and more.
For example, ISO 9001 certification focuses on quality management, ensuring that businesses have processes in place to consistently meet customer requirements. By adhering to these standards, businesses can demonstrate their commitment to customer satisfaction, helping to build trust and establish long-term relationships with clients.
Moreover, certifications like ISO 14001, which focuses on environmental management, appeal to customers who are increasingly concerned with sustainability and corporate social responsibility. Being ISO-certified helps companies gain a competitive advantage by showing that they prioritize quality and responsibility, which builds confidence and loyalty in customers.
3. Ensuring Compliance with Global Regulations
Every country has its own set of laws and regulations, particularly around product safety, environmental impact, and labor practices. For businesses aiming to operate internationally, staying compliant with local laws can be complex and challenging. However, ISO certification helps businesses ensure that they are meeting both local and international regulatory requirements.
For instance, businesses in industries like healthcare and food production must comply with strict international standards. ISO 13485 (Medical Devices) and ISO 22000 (Food Safety Management) are essential certifications for these industries, helping companies meet the specific regulations required by different countries. By maintaining compliance with ISO standards, businesses not only avoid legal risks and penalties but also enhance their reputation as reliable and responsible operators in global markets.
4. Improved Operational Efficiency and Cost Savings
ISO certification is not just about meeting external standards—it’s also about internal improvements. Many ISO standards, such as ISO 9001 (Quality Management), emphasize process optimization, continuous improvement, and efficiency. Companies that implement these standards often find that their operations become more streamlined, with reduced waste, fewer errors, and improved overall productivity.
For example, the process of earning ISO 9001 certification requires a business to analyze its operations, identify inefficiencies, and implement better practices. This leads to cost reductions, faster delivery times, and higher product quality—factors that are essential for competing globally. Companies that operate efficiently can offer competitive pricing, quicker turnaround times, and consistent product quality, all of which make them more attractive to international customers.
5. Enhancing Brand Reputation and Marketing
ISO certification is a powerful marketing tool that helps businesses stand out in global markets. It serves as a third-party endorsement of a company’s commitment to quality, customer satisfaction, and sustainability. Many customers, both consumers and business clients, actively seek out companies that are ISO-certified because they know these companies meet high standards.
In crowded global markets where differentiation is key, ISO certification provides a clear and objective way to distinguish a business from its competitors. ISO-certified companies can proudly display their certifications on their products, packaging, and marketing materials, signaling to potential customers that they are trustworthy and capable of delivering on their promises.
Having ISO certification can also help businesses expand their presence in markets where environmental sustainability, ethical practices, or product quality are of paramount concern. For example, companies with ISO 14001 certification demonstrate their commitment to reducing their environmental impact, which can be an attractive feature in markets with strict environmental regulations or eco-conscious consumers.
6. Fostering Stronger Supplier Relationships
In global supply chains, it is essential for businesses to maintain reliable, consistent, and high-quality suppliers. ISO certification can help improve supplier relationships by ensuring that suppliers adhere to internationally recognized standards. For example, businesses with ISO 9001 certification may require their suppliers to also hold ISO certifications to ensure that all stages of production meet the same high standards.
ISO certifications help streamline communication and reduce misunderstandings with suppliers, ensuring that everyone is on the same page regarding quality expectations, delivery times, and compliance requirements. By working with certified suppliers, businesses can ensure that their products are consistently of high quality and meet international standards, which strengthens their competitiveness in the global market.
7. Continuous Improvement and Innovation
One of the key principles of ISO certification is the emphasis on continuous improvement. ISO standards are designed to encourage businesses to evaluate their processes regularly, seek out areas for improvement, and innovate over time. For companies operating in global markets, this focus on improvement is crucial for staying competitive.
Businesses that hold ISO certifications are encouraged to stay agile and responsive to changes in the market, whether it’s adopting new technologies, addressing customer feedback, or evolving their practices to meet new regulatory standards. By fostering a culture of innovation and continual growth, ISO-certified companies are better equipped to adapt to changing market conditions and sustain their competitive advantage.
Conclusion
ISO certification is an invaluable asset for businesses looking to compete in the global marketplace. It provides a clear, internationally recognized framework for meeting customer expectations, ensuring compliance with regulations, and improving internal processes. With ISO certification, businesses can access new markets, build stronger relationships with customers and suppliers, improve operational efficiency, and enhance their brand reputation.
In an increasingly competitive and globalized business environment, ISO certification is not just a mark of quality; it’s a strategic tool that helps businesses differentiate themselves, stay compliant, reduce costs, and ultimately thrive on the global stage. Whether you are a small business aiming to grow internationally or a large corporation looking to maintain market leadership, ISO certification can be the key to unlocking new opportunities and ensuring long-term success.
0 notes
Text
Mastering ISO 27001 Certification, Cost & Benefits
Mastering ISO 27001 certification involves understanding the requirements of the standard, implementing a robust Information Security Management System (ISMS), and achieving certification through a recognized certification body. Here’s a comprehensive guide, including costs and benefits:
1. ISO 27001 Overview
ISO/IEC 27001 is an internationally recognized standard for establishing, implementing, maintaining, and improving an ISMS to secure sensitive information and ensure confidentiality, integrity, and availability.
2. Steps to Achieve ISO 27001 Certification
Understand the Standard:
Review ISO 27001 and Annex A, which contains 93 controls (as per the 2022 update).
Perform a Gap Analysis:
Compare your current practices against ISO 27001 requirements to identify areas for improvement.
Develop an ISMS:
Define the scope of your ISMS (e.g., departments, locations, and processes).
Create policies, procedures, and frameworks for managing risks and securing data.
Risk Assessment and Treatment:
Identify information security risks and implement appropriate controls to mitigate them.
Implement Controls:
Apply controls from Annex A, such as access management, incident response, encryption, and physical security.
Train Employees:
Conduct regular awareness training to ensure compliance with security policies.
Internal Audit:
Audit the ISMS to ensure it aligns with ISO 27001.
Management Review:
Ensure top management evaluates and supports the ISMS.
Certification Audit:
Engage an accredited certification body for an external audit.
Certification:
Upon successful completion, receive an ISO 27001 certificate, typically valid for three years, with annual surveillance audits.
3. Costs of ISO 27001 Certification
Costs vary depending on organization size, scope, and complexity. Key cost components include:
Consulting and Training:
Hiring experts to guide implementation or train staff: $5,000–$20,000.
Internal Resources:
Staff time for ISMS development, training, and audits.
Tools and Technology:
Security tools (e.g., encryption software, monitoring tools): $2,000–$10,000 annually.
Certification Audit:
Certification body fees for audit and registration: $4,000–$20,000.
Surveillance Audits:
Annual audits by the certification body to maintain the certification: $2,000–$8,000 per year.
4. Benefits of ISO 27001 Certification
Enhanced Security:
Protects sensitive data against threats like breaches and cyberattacks.
Regulatory Compliance:
Aligns with global regulations, such as GDPR, HIPAA, and Indonesia’s PDP Law.
Customer Trust:
Demonstrates commitment to security, enhancing credibility and attracting new clients.
Business Opportunities:
Opens doors to new markets where certification is a requirement.
Risk Management:
Helps identify, manage, and reduce security risks effectively.
Operational Efficiency:
Streamlines processes and reduces duplication through standardized practices.
Competitive Advantage:
Differentiates your organization in competitive industries.
Cost Savings:
Minimizes the likelihood of costly incidents and fines.
5. Mastering ISO 27001 Certification
Leverage automation tools for risk management and documentation.
Encourage top management support to drive the initiative.
Use training programs for staff to ensure compliance and awareness.
Conduct regular internal audits to identify and fix issues before external audits.
0 notes
Text
ISO 27001 Lead Auditor Training
What is ISO 27001 Lead Auditor Training?
ISO 27001 Lead Auditor Training is an intensive program that provides participants with the skills and knowledge necessary to perform lead audits for organizations that have implemented the ISO 27001 Information Security Management Standard. The course is designed for experienced auditors who wish to become certified as ISO 27001 Lead Auditors.
Importance
ISO 27001 is the global standard for information security management. Organizations that implement ISO 27001 are able to demonstrate their commitment to data security and protect their customers’ confidential information. Becoming certified as an ISO 27001 Lead Auditor allows you to audit organizations against this internationally recognized standard.
Benefits
Gaining the expertise and knowledge to conduct lead audits for businesses that have implemented the ISO 27001 Information Security Management Standard.
Learn how to evaluate information security controls using the ISO 27001 standard.
Understand how to assess risk and report on findings.
Develop expertise in auditing information security management systems.
Demonstrate your commitment to data security and protect your customers’ confidential information.
Become certified as an ISO 27001 Lead Auditor.
Advance your career in information security auditing.
Who Should Attend?
The ISO 27001 Lead Auditor Training is designed for experienced auditors who wish to become certified as ISO 27001 Lead Auditors. The course is also relevant for anyone working in a role that requires an understanding of the ISO 27001 standard, such as information security managers, risk managers, and compliance officers.
Pre-requisites
Candidates who wish to enroll in this program should have a good understanding of ISO 27001 standards and the concepts of information security and risk management. It will be beneficial if the applicant has some hands-on experience with ISO 27001 implementation and auditing.
How Can One Join This Training?
The best way to join the ISO 27001 Lead Auditor Training is to find an accredited training center and sign up for a course. The course will usually last for five days, and participants will be awarded a certificate once they have successfully completed the training. You can also find many online courses that offer the same training content but over a longer period of time.
Conclusion
ISO 27001 lead auditor training can be the perfect way to acquire in-depth knowledge of information security management system (ISMS) standards, their requirements, and implementation. The skills learned during the course can help organizations implement and manage an ISMS effectively. Additionally, the lead auditor training can also help organizations prepare for audits against ISO 27001.
iso 27001 lead auditor training course
0 notes
Text
ISO Certification and Implementation: A Complete Overview
In today's competitive global business world, businesses are looking for excellence to ensure customer satisfaction, good work and competitive business. ISO certification is one way to achieve goals. ISO or International Organization for Standardization certification refers to internationally recognized standards that ensure that appropriate methods are used to improve the organization's performance. Let's talk about what an ISO certificate is, the importance of an ISO certificate and the steps to use specific models.

These standards cover many business and operational aspects, from quality management ISO 9001 to environmental management ISO 14001, food safety ISO 22000 and fabric safety ISO 27001. To meet customer needs ISO standards provide companies with the confidence and commitment to continuous improvement and excellence or because they reflect the organization’s commitment to high standards. Gain access to international markets, as most contracts and partnerships worldwide require such certification.
Reduce the risk of legal risk Customer satisfaction: ISO standards prioritize customer needs, ultimately resulting in improved products, services and satisfaction. Steps
compliance with ISO certification involves a well-designed process to bring your business processes into line with the required standards. Here is the step-by-step procedure:
1. Learn about relevant ISO standards
Decide which ISO standards will add value to your business. If your goal is to improve quality management, ISO 9001 is the best choice, while ISO 14001 is suitable in the area of environmental management.
2. Gap Analysis
Your current processes and systems should be assessed against the requirements of ISO standards. The gap analysis will reveal areas that need to be changed to meet the requirements of the selected model.
3. Create an Action Plan
Create a detailed plan for how to address the gaps in the review by identifying roles, timelines, and goals that will drive compliance.
4. Train your team:
Ensure that all employees understand ISO standards, their importance, and their contribution to the business. Training helps create a positive and sustainable culture.
5. Process documentation:
Comprehensively document your processes, procedures, and policies. This is one of the most important tasks because ISO standards often require documentation to demonstrate adherence to methods and procedures.
6. Improve Change
Follow new processes and systems. Monitor and implement changes to meet ISO standard requirements.
7. Internal Audits
Conduct internal audits to assess compliance with standards. Inconsistent observations must be identified and acted upon.
8. Certification Certification
Select an ISO certified certification body as a third-party assessor to ensure the organization’s compliance and issue an ISO certificate upon completion.
9. Continuous improvement
ISO certification is not a one-time achievement, but a process that must be continually reviewed and improved to keep pace with the changing business environment.
10. Resistance to change: Employees may resist new procedures or be concerned about the additional work. Overcome this by developing a positive attitude and providing adequate training. But the long-term benefits outweigh the initial costs. Use digital tools to improve your memory and accuracy. By following ISO standards, organizations can meet regulatory requirements while developing an organizational culture of continuous improvement. The benefits outweigh the challenges. Whether you are a small business or a large enterprise, the path to ISO certification will help you stand out from your competitors in today’s business world.
0 notes
Text
Unlocking Potential: Why Your Enterprise Needs an Enterprise LMS
Enterprise LMS: In today's rapidly evolving business landscape, continuous learning is no longer a luxury, it's a necessity. Equipping your workforce with the latest skills and knowledge is crucial for maintaining a competitive edge. Enter the enterprise learning management system (LMS), a powerful tool designed to streamline training delivery, track learner progress, and ultimately, empower your organization's success.

Beyond Basic Training: What Makes an LMS Enterprise-Grade?
Traditional learning platforms might suffice for smaller teams, but for enterprises with a diverse workforce and complex training needs, a basic LMS simply won't cut it. An enterprise LMS offers robust features and functionalities that cater to large-scale training initiatives. Here's what sets them apart:
Scalability: An enterprise LMS can seamlessly adapt to accommodate a growing employee base across various locations and departments. EdzLMS (https://edzlms.com/plans/), for example, offers a scalable architecture that can effortlessly manage thousands of learners simultaneously.
Customization: Enterprise LMS platforms provide a high degree of customization, allowing you to tailor learning experiences to specific roles, departments, and skill gaps. Create personalized learning paths, incorporate diverse content formats, and leverage features like gamification and branching scenarios to keep learners engaged.
Advanced Reporting and Analytics: In-depth LMS tracking and reporting is a cornerstone of any enterprise LMS. Gain valuable insights into learner progress, identify areas for improvement, and measure the overall effectiveness of your training programs. EdzLMS offers comprehensive reports that provide granular data on learner engagement, completion rates, and knowledge retention.
Integration Capabilities: A seamless integration with your existing HR systems, single sign-on (SSO) capabilities, and robust APIs are crucial for streamlining workflows and automating administrative tasks within your enterprise LMS. This ensures efficient user provisioning, simplifies enrollment processes, and reduces the burden on your training and development (L&D) team.
Security and Compliance: Enterprise-grade security is paramount when dealing with sensitive employee data. Leading enterprise LMS platforms like EdzLMS prioritize data protection by adhering to industry-leading security standards and compliance regulations such as GDPR, ISO 27001, and SOC 2.
The Benefits of Implementing an Enterprise LMS
Investing in an enterprise LMS offers numerous benefits that go beyond simply delivering training content. Here's how it empowers your organization:
Reduced Training Costs: Automating administrative tasks, streamlining training delivery, and offering on-demand learning opportunities can significantly lower your overall training costs.
Enhanced Employee Onboarding and Development: An enterprise LMS facilitates a smooth onboarding experience for new hires, accelerates skill development, and fosters a culture of continuous learning within your organization.
Improved Compliance: Ensure your workforce stays up-to-date with regulatory requirements and industry best practices through automated compliance training modules. Streamline record-keeping and reporting with detailed completion and certification data available within the LMS.
Increased Employee Engagement: Interactive learning content, gamification elements, and personalized learning paths enhance learner motivation and ensure higher course completion rates.
Data-Driven Decision Making: Leverage rich LMS tracking and reporting data to identify training gaps, optimize your learning programs, and measure the success of your L&D initiatives.
Conclusion
In today's competitive business environment, investing in an enterprise LMS is not just an option, it's a strategic imperative. By unlocking the potential of your workforce through effective training programs, you can drive innovation, improve performance, and achieve your organizational goals. If you're looking for a powerful enterprise LMS solution, consider EdzLMS (https://edzlms.com/other-industry/). With its robust features, scalability, and commitment to security, EdzLMS can take your learning and development initiatives to the next level.
FAQ:
Q: What are the key considerations when choosing an enterprise LMS?
A: Scalability, customization, reporting and analytics capabilities, integration options, and security features are essential factors when evaluating enterprise LMS solutions. Additionally, consider user-friendliness, ease of implementation, and customer support.
Q: How can an enterprise LMS benefit my specific industry?
A: Enterprise LMS platforms offer a wide range of benefits across various industries. From providing regulatory compliance training in the healthcare sector to upskilling employees in the ever-evolving technology landscape, an enterprise LMS can be customized to meet your organization's unique needs.
0 notes
Text
ISO 27001 Internal Auditor Training Indonesia
What is ISO 27001 Internal Auditor Training?
ISO 27001 Internal Auditor Training is a training program that teaches individuals how to perform internal audits of an organization's information security management system (ISMS) in accordance with the ISO 27001 standard. The training covers the requirements of the ISO 27001 standard and provides participants with the skills and knowledge necessary to conduct an effective ISMS internal audit.
Importance
ISO 27001 is the most widely recognized standard for information security management, and organizations that have been certified to ISO 27001 demonstrate a commitment to protecting their customers' data. An internal audit is an important part of an organization's ISMS implementation, and the ISO 27001 Internal Auditor Training program provides participants with the knowledge and skills necessary to conduct internal audits that are consistent with the requirements of the ISO 27001 standard.
Benefits
The training provides an understanding of the specific requirements of the ISO 27001 standard. The training helps assess and improve an organization's information security management system (ISMS). It also enables individuals to identify and report information security risks and incidents. It helps organizations improve their information security posture and protect their critical information assets. The training also builds a foundation for individuals who want to pursue a career in information security auditing. Lastly, it enhances the knowledge and expertise of participants in information security management. Who Should Attend?
The ISO 27001 Internal Auditor Course program is designed for individuals who want to become internal auditors of an organization's information security management system (ISMS). The program is also beneficial for individuals who want to gain a better understanding of the requirements of the ISO 27001 standard.
Pre-requisites
There are no necessary pre-requisites for the ISO 27001 Internal Auditor Course program. However, it is recommended that participants have a basic understanding of information security and the ISO 27001 standard.
How to Attend a Training Program?
The first step is to find an organization that offers ISO 27001 Internal Auditor Course. Once you have found a training provider, you will need to register for the program and pay the tuition fee. The next step is to attend the training and pass the internal auditor exam. Upon successful completion of the exam, you will be certified as an ISO 27001 internal auditor.
Conclusion
ISO 27001 internal auditor training helps organizations understand and implement the requirements of the standard. It also provides the knowledge and skills necessary to assess and report on an organization's compliance. The training is beneficial for both auditors and organizations seeking certification.
Read more: iso 27001 internal audit training
0 notes
Text
ISO certificate office in Riyadh
ISO Certificate Office in Riyadh: Get Certified with Nasrcom
Are you looking for an ISO certificate in Riyadh? At Nasrcom, we specialize in helping businesses obtain their ISO certification in Riyadh and across Saudi Arabia. As a trusted leader in ISO certification services, we ensure that your company meets international standards and gains the credibility it needs to compete on a global scale.
What is an ISO Certificate?
An ISO certificate is a globally recognized certification that demonstrates your company’s commitment to quality, efficiency, and continual improvement. Obtaining an ISO certification proves that your business adheres to internationally recognized standards, whether in quality management, environmental management, information security, or other areas. Companies with an ISO certificate gain a competitive advantage by showing customers and stakeholders that they maintain high standards and are dedicated to continuous improvement.

Why Choose Nasrcom for ISO Certification in Riyadh?
As the leading ISO certificate office in Riyadh, Nasrcom is your trusted partner in obtaining your ISO certification. Our team of experts guides you through the entire process, from initial consultation to post-certification support. Here's why Nasrcom is the preferred choice for ISO certification:
Expert Guidance: Our ISO consultants have in-depth knowledge of ISO standards and the certification process. We help you understand the specific requirements for your industry and ensure that you’re fully prepared for the ISO audit.
Comprehensive Services: We offer a complete range of services, from ISO 9001 (Quality Management) to ISO 14001 (Environmental Management) and ISO 27001 (Information Security Management). Whatever your ISO certification needs are, we have the expertise to assist you.
Seamless Process: At Nasrcom, we make the certification process as smooth as possible. Our team ensures that all documentation is in order, provides training to your staff, and supports you through the audit process.
Time and Cost Efficiency: We understand the importance of time and cost for businesses in Riyadh. Our streamlined process helps you obtain your ISO certificate quickly and affordably, ensuring minimal disruption to your operations.
Post-Certification Support: Obtaining an ISO certification is just the beginning. We offer ongoing support to ensure that your company continues to comply with ISO standards and remains up to date with any changes in the certification requirements.
Our ISO Certification Services in Riyadh
At Nasrcom, we specialize in the following ISO certifications for businesses in Riyadh:
ISO 9001 (Quality Management System): Enhance your business efficiency and customer satisfaction by implementing a robust quality management system that meets international standards.
ISO 14001 (Environmental Management System): Demonstrate your commitment to environmental sustainability by adopting an effective environmental management system.
ISO 27001 (Information Security Management): Safeguard sensitive data and ensure compliance with international standards for information security.
ISO 45001 (Occupational Health and Safety): Improve workplace safety and ensure the health and wellbeing of your employees with this globally recognized certification.
ISO 22000 (Food Safety Management): Ensure the safety and quality of food products, meeting both legal and regulatory requirements.
Benefits of Getting ISO Certified in Riyadh
Global Recognition: An ISO certificate increases your credibility in the global market, giving you a competitive edge in both local and international business.
Improved Customer Trust: ISO certification builds trust with clients by assuring them that your company follows internationally recognized best practices.
Operational Efficiency: ISO certification helps streamline processes, reduce waste, and enhance productivity, leading to greater cost savings and improved performance.
Regulatory Compliance: With an ISO certificate, your business can easily meet legal and regulatory requirements, ensuring smooth operations.
Risk Management: ISO standards help identify and mitigate risks, leading to better decision-making and long-term sustainability.
Why Riyadh Businesses Trust Nasrcom for ISO Certification
As one of the leading ISO certification providers in Riyadh, Nasrcom has a proven track record of helping businesses across various industries obtain their ISO certificates. Our comprehensive approach ensures that your organization meets the stringent requirements of ISO standards, leading to enhanced performance, customer satisfaction, and market competitiveness.
Our team is committed to delivering personalized solutions that align with your business goals, whether you’re seeking ISO 9001 certification or any other ISO standard. With Nasrcom, you get expert guidance, prompt service, and a seamless certification experience.
Contact Nasrcom Today to Get Your ISO Certificate in Riyadh
Are you ready to take your business to the next level? Contact Nasrcom today to start the process of obtaining your ISO certificate in Riyadh. Our team of experts is here to help you navigate the complexities of ISO certification and ensure that your business complies with global standards.
Call us now or fill out our online form to schedule a consultation with one of our ISO certification specialists. Let Nasrcom help your business achieve ISO certification and unlock new opportunities for growth and success.

#شهادة الايزو#شهادة الجودة معتمده#ISO certificate#Certified quality certificate office in Riyadh#nasrcom
1 note
·
View note
Text
Enhancing Information Security with ISO 27001 Implementation by 4C Consulting

In an era where data breaches and cyber threats are on the rise, safeguarding sensitive information has become crucial for organizations of all sizes. ISO 27001 Implementation is the gold standard for information security, helping businesses establish a robust framework to protect data and manage risks. As companies increasingly rely on digital systems, ISO 27001 ensures that information security is embedded into every layer of an organization’s operations. 4C Consulting, a trusted ISO certification consulting firm, has helped over 2,000 clients achieve compliance with ISO standards and has delivered over 10,000 hours of training, positioning them as a reliable partner in ISO 27001 Implementation.
The Need for ISO 27001 Implementation
In today’s interconnected world, data is one of the most valuable assets an organization possesses. However, this data is vulnerable to unauthorized access, theft, and breaches. Implementing ISO 27001 offers a structured approach to securing information assets, reducing risks, and establishing trust with clients and stakeholders. By adopting ISO 27001, businesses not only protect sensitive data but also demonstrate their commitment to information security.
Understanding ISO 27001 Implementation
ISO 27001 is an internationally recognized standard that provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). ISO 27001 Implementation focuses on three main objectives:
Confidentiality: Ensuring that only authorized individuals have access to sensitive information.
Integrity: Protecting data accuracy and completeness, preventing unauthorized modifications.
Availability: Ensuring that data is accessible to authorized users whenever required.
By systematically identifying, assessing, and managing information security risks, ISO 27001 Implementation helps businesses stay resilient against cyber threats and minimizes the potential impact of security incidents.
Steps to Implement ISO 27001
Achieving ISO 27001 certification requires careful planning and commitment. The implementation process involves several key steps:
Conducting a Gap Analysis: This step assesses the existing information security policies against ISO 27001 requirements, identifying areas that need improvement.
Defining the Scope of the ISMS: Determining which departments, locations, or information assets will be covered under the ISO 27001 framework.
Risk Assessment and Management: Identifying and evaluating potential security risks, followed by implementing measures to mitigate these risks.
Documentation and Policy Creation: Developing and documenting information security policies, procedures, and controls in alignment with ISO 27001 standards.
Employee Training and Awareness: Educating staff on information security practices, roles, and responsibilities to create a security-conscious culture.
Internal Audit: Conducting an internal audit to evaluate ISMS effectiveness and address any non-conformities.
Certification Audit: Finally, an external audit by a certification body verifies compliance with ISO 27001 standards, resulting in certification upon successful completion.
Benefits of ISO 27001 Implementation
Implementing ISO 27001 offers a range of benefits for businesses:
Enhanced Data Security: Protects critical information from breaches and unauthorized access.
Compliance with Regulations: Helps meet regulatory and legal data protection requirements.
Improved Customer Trust: Builds credibility by demonstrating a commitment to secure data management.
Reduced Risk: Proactively manages risks, reducing the chances of costly security incidents.
Operational Efficiency: Standardizes processes and reduces redundant controls, boosting efficiency.
How 4C Consulting Supports ISO 27001 Implementation
With extensive expertise in ISO standards, 4C Consulting provides end-to-end support for ISO 27001 Implementation. From initial gap analysis to certification, their experienced consultants guide organizations through each step. 4C Consulting offers tailored training programs, documentation assistance, risk management guidance, and internal audit support, ensuring a smooth and successful implementation process. With over 10,000 hours of training provided, 4C Consulting empowers businesses to achieve ISO 27001 certification with confidence.
By partnering with 4C Consulting, organizations gain a comprehensive approach to information security that strengthens resilience, meets industry standards, and builds trust among stakeholders. Contact us now.
0 notes