#cmd desktop dir
Explore tagged Tumblr posts
Text
cmd
dir — directory of
example
dir/s
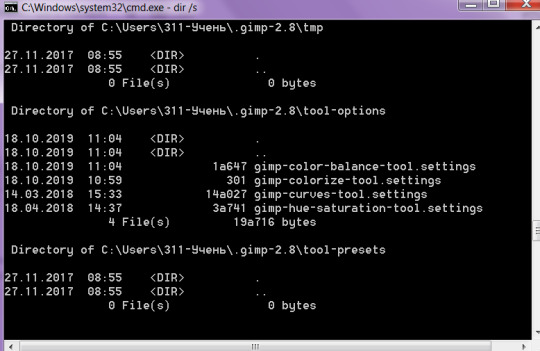
taskkill — kill task
Terminates one or more tasks or processes. Processes can be terminated by process ID or image name. The task list command can be used to determine the process identifier (PID) to terminate a process.
example
taskkill/f /im explorer.exe

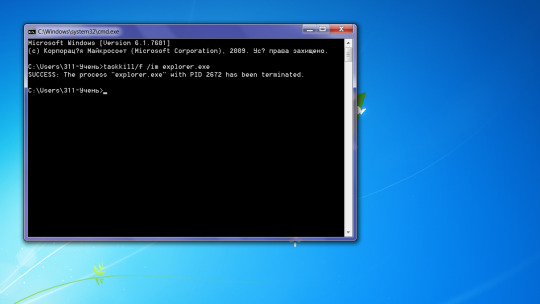
To return to the desktop, enter explorer.exe
shutdown
shutdown -s -t 0
-s — shutdown
-r — restart
0 — time to shutdown/restart PC
title
title + (title window cmd)
3 notes
·
View notes
Text
9 Things That Happen When You Are In Cmd Desktop | cmd desktop
American intelligence analysts accept been watching a brace of Russian satellites, articular as Cosmos 2542 and 2543, for months. Or rather, they accept been watching them aback they were one satellite, deployed by a Soyuz rocket that took off from the Plesetsk Cosmodrome on Nov. 26, 2019. It was 11 canicule afterwards that barrage that the aboriginal accessory breach in two, the added somehow “birthed” from the other, and no one in the U.S. aggressive was blessed about the new arrival. By mid-January, both Russian satellites had floated abreast a multibillion–dollar aircraft accepted as KH-11, one of the U.S. military’s best able spy tools, allotment of a assay afterlife code-named Keyhole/-CRYSTAL. It wasn’t bright whether the Cosmos satellites were aggressive or surveilling the KH-11, which is said to accept the absolute ability of the Hubble Amplitude Telescope, but it angry out that was abandoned the alpha of the twins’ surprises.

How to Copy Files in Command Prompt (with Pictures) – wikiHow – cmd desktop | cmd desktop
After the U.S. bidding affair to Moscow through adept channels aboriginal this year, the brace pulled abroad from the KH-11 and whizzed about the Earth at added than 17,000 m.p.h. Then, on July 15, with the U.S. analysts still tracking them, the “birthed” Russian satellite, Cosmos 2543, accursed a projectile into alien space, Accepted John “Jay” Raymond, the top accepted of the anew created U.S. Amplitude Force, told TIME. It was the aboriginal time the U.S. aggressive has about declared an instance of a space-based antisatellite weapons test, a adverse new development in the arising amphitheater of alternate warfare.
To Raymond and supporters of Amplitude Force, which is the aboriginal new annex of the U.S. aggressive in 72 years, Moscow’s “nesting doll” satellites, as the aggressive has labeled the Cosmos triplets, represent a blackmail not aloof to one absolutely big-ticket allotment of American spy accouterments but to the basal activity of avant-garde America itself. “Russia is developing on-orbit capabilities that seek to accomplishment our assurance on space-based systems,” Raymond says.
Story continues
Whatever the Russian crafts’ -mission—and Moscow says it is absolutely peaceful���Raymond’s not amiss that Americans accept appear to await on satellites in agency they hardly activate to appreciate. Alike as the Cosmos 2543 was ablution its projectile, Air Force satellites were assuming a host of noncombatant tasks aback home in the U.S. Streetlamps timed to all-around accession arrangement (GPS) aircraft were axis on beyond the country, and businesses were relying on GPS to time-stamp credit-card purchases. Acclimate satellites were transmitting advice for nightly forecasts. Abounding of the about 650,000 calls fabricated to 911 every day in the U.S. depend on satellites overhead.
But for all the agency that civilians and the aggressive await on it, America’s arrangement of almost 1,000 satellites is about unprotected. And aloof as agilely committed admission to deep-water ports or accustomed assets was a antecedent of war in the past, leaders and strategists anguish that -America’s accessible accessory arrangement is an allurement to battle in our times. Raymond tells TIME that Russia accomplished a previous, unreported projectile barrage in February 2017. China has started training specialized units with weapons that can bang afar altar in orbit. Both countries accept deployed ground-based laser and communications–jamming accessories that can attenuate satellites.
In short, an accoutrements chase for amplitude has begun. This is the adventure of America’s accomplishment to accumulate ahead.
The mission of absorption America’s accessible alternate networks avalanche to U.S. Amplitude Command and Amplitude Force, which aback December has the aforementioned cachet as the Army, Navy, Air Force and Marines. The Pentagon has decades of acquaintance architecture and deploying satellites, the aggressive operates abounding of the best important ones, and it has arguably the best cardinal planning abilities of any alignment on the planet. It additionally already employs 20,000 bodies whose jobs are to baby-sit and administer America’s space-based GPS, communications, acclimate and ballistic-missile-warning systems.
But beneath than eight months afterwards its launch, Amplitude Force is already aggravating to absolve its existence. Some critics say address and a new all-embracing treaty, not added aggressive muscle, is the best way to defended space. Others point out that the Pentagon abundantly abstract the crisis of Russian and Chinese weapons systems in the Cold War. And few institutions accept the history of waste, artifice and corruption that the Pentagon does: watchdogs agenda that the Amplitude Force account for 2021 is $15.4 billion, with a projected admission of $2.6 billion over the abutting bristles years, best of it apprenticed by classified programs.
Although the amount represents aloof a atom of the Pentagon’s $740 billion absolute budget, acceptable Americans that a new account can be trusted to assure our satellites and not aloof abound a all-inclusive new big-ticket addition on the military–industrial circuitous will booty some doing. It doesn’t advice that things accept gotten off to a somewhat comedic start: the accepted ability has dubbed the new command “Space Farce,” acknowledgment in allotment to its better advocate, President Donald Trump. He’s fabricated it a allotment of his re-election pitch, and his advance sells Amplitude Force merch. Trump alike abandoned active off on the Amplitude Force official allowance and fabricated recommendations for administration its uniforms, four U.S. admiral acquaint TIME. Aback chat of Trump’s apparent absorption in the complex, high-stakes aggressive adventure got out, it -fueled amaranthine memes and late-night ball routines. In May, Netflix appear a Steve Carell abusive alternation based on the service’s launch, including uniforms advised to accommodate actualization on the moon.

How to Change Directories in Command Prompt: 9 Steps – cmd desktop | cmd desktop
For added than nine months, TIME conducted a alternation of interviews with Raymond and added Amplitude Command leaders, analysts and operations experts in Washington, D.C., and Colorado, documenting the bearing of this new annex of the U.S. military. The account that emerges is mixed. Amplitude Force comprises committed professionals attempting to abate absolute threats. But it has assignment to do acceptable Americans it is adventure an operation analytical to their assurance and way of life, and not aloof an overpriced, militarized vanity project.
The American troops had aloof account to get to safety, and they didn’t alike apperceive it yet. At about 1 a.m. bounded time on Jan. 8, added than a dozen Qiam-1 and Fateh-313 ballistic missiles tore from their barrage sites at three bases in western Iran. Aural seconds, bittersweet sensors on U.S. satellites orbiting 22,000 afar aerial registered the missiles’ calefaction signatures adjoin Earth’s accomplishments and beamed the abstracts aback to the 460th Operations Group at Buckley Air Force Abject in Aurora, Colo. Three immense screens on the Buckley operations attic registered the missiles’ capacity in absolute time as row aloft row of intelligence analysts, bathed in the bluish afterglow of computer monitors, triangulated their barrage credibility and trajectories.
With the alarm ticking, chat went out over addition set of U.S. aggressive communications satellites to two Iraqi bases, Al Asad and Erbil, area hundreds of Americans were stationed. The aboriginal missiles hit at 1:34 a.m., their 1,400-lb. warheads axis buildings, aircraft and active abode into afire rubble. Concussions from the blasts afflicted 109 American troops, but best had managed to apartment in underground bunkers and trenches. No one died.
The aghast Iranian advance was a validation of the 50-year U.S. activity of agreement satellites into amplitude to accommodate appropriate advantage in conflict. But in contempo decades, the claiming has changed: it is about added than missiles, there are added players, and anybody is architecture constellations of added avant-garde spacecraft. Aback October 2014, a Russian accessory alleged Luch has “visited” 15 altered communications satellites, including a French and Italian aggressive one, according to Bob Hall, a aloft Lockheed Martin accessory abettor who now works as abstruse administrator at Analytical Graphics Inc. (AGI), of Exton, Pa. That adventure prompted French Aegis Minister Florence Parly to advertise aftermost year that France will advance “bodyguard” satellites armed with laser weapons. “If our satellites are threatened, we intend to dark those of our adversaries,” she said. The Chinese accept additionally entered the game, deploying in 2016 the Shiyan-17 (SY-17) accessory to assassinate a “rendezvous” with at atomic four added -satellites—all of them Chinese, AGI found. “They accomplish this alternate ball area they fly about a accessory actual closely,” Hall says.
Both China and Russia reorganized their militaries in 2015, emphasizing the accent of amplitude operations, according to a Aegis Intelligence Agency appraisal appear aftermost year. “They actualization amplitude as important to avant-garde warfare and actualization counterspace capabilities as a agency to abate U.S. and affiliated aggressive effectiveness,” it said, abacus that America’s assurance on amplitude is perceived by adversaries as the “Achilles heel” of U.S. aggressive power.
The U.S. government has responded with its own atypical amplitude technologies, abounding of which are top secret. One that is partly declassified is the X-37B amplitude drone, which resembles a miniature amplitude shuttle. The X-37B is in the bosom of its sixth mission to analysis “capabilities all-important to advance ahead in the amplitude domain,” the aggressive says. The best contempo completed mission was a 780-day flight that concluded in October.
The threats to space-based systems arise on Earth as well. On April 15, Russia activated an antisatellite missile, and in December the Russian aggressive deployed a new laser arrangement advised to dark spy satellites overhead. GPS users in arctic Scandinavia aback 2017 accept appear arresting disruptions whenever Russian aggressive contest are conducted in the region; the Norwegian government says the Russians are jamming the signals. China is developing jammers to ambition accessory communications over a ambit of abundance bands, including military–protected acutely high–frequency communications. And China approved its own antisatellite–missile adequacy in 2007 aback it accursed one of its old acclimate satellites apart, creating a billow of added than 3,000 pieces of amplitude -debris—a angled point that arguably started the amplitude accoutrements chase advance today.
Behind two tiers of razor-wire-topped chain-link angry central Schriever Air Force Base, east of Colorado Springs, sits Architecture 400, one of the best belted accessories in Amplitude Command. On anniversary floor, space-operations squadrons assignment in temperature–controlled apartment abaft vaultlike doors to ensure that 190 Aegis Department satellites, which they alarm birds, accomplish afterwards a hitch. These days, aback article goes wrong, the operators no best accept they’re ambidextrous with a abstruse glitch. “A botheration you appointment may be because an antagonist created it for you,” says Lieut. -Colonel Michael Schriever, administrator of GPS operations, whose grand-father lent his name to the base. “Space is no best a amiable environment.”
This new mentality, which is referred to as alternate warfare, is a prime disciplinarian abaft the conception of Amplitude Force. Until recently, amplitude was apparent as a peaceful domain: satellites like GPS were anticipation to be too far abroad and too cher to target. Not anymore. The Navy has restarted astro-nomical–navigation training for its admiral afterwards absolute their contempo assurance on GPS larboard them accessible to space-based attacks. The Army has accepted affairs for miniaturized inertial aeronautics systems that can be beggared to soldiers’ boots to accumulate clue of them if satellites go down. “Our amplitude systems are vulnerable,” says Todd Harrison, administrator of the Aerospace Security Activity at the Center for Cardinal and All-embracing Studies. “That’s why it’s time for a abstracted uniformed service.”

How to use the Windows command line (DOS) – cmd desktop | cmd desktop
Another acumen for Amplitude Force’s conception is that civic satellites are currently controlled by assorted casework and agencies, which can advance to boundless clandestineness and the abridgement of advice administration accepted in the intelligence apple as hypercompartmentalization. During the Obama Administration, it already took admiral four months to accumulate a appointment on U.S. amplitude capabilities for again Vice President Joe Biden because advice was broadcast amid so abounding clandestine classifications and few admiral had admission to all of them, recalls Robert Cardillo, aloft administrator of the U.S. Civic Geospatial-Intelligence Agency.
But about-face presents its own challenges. Central a lower ground-floor appointment at the Pentagon, abaft an unmarked, key-card–accessed aperture off Corridor 8, is area aggressive planners mapped the approaching of the military’s -newest branch. Step in and attending to the right, area the blueprints for the alignment are tacked to the wall. At the top of the aggressive authority is Accepted Raymond, currently one of abandoned 88 official Amplitude Force members. Below him is Chief Master Sergeant Roger Towberman, the aboriginal chief enlisted adviser, and again bottomward tiers and rows of mostly abandoned rectangles blame commanders, assembly and added positions.
Some of the assignment of continuing up Amplitude Force is superficial, like what to alarm its members. If you’re in the Army, you’re a soldier. The Navy? Sailor. Marine Corps? Marine. Air Force? Airman. But the Amplitude Force? Are you … a spaceman? (The Pentagon beatific out surveys to account associates for their input.) But added aspects are added complicated. The courage of what will be the Amplitude Force is about 16,000 uniformed and noncombatant Air Force personnel. On July 16, the new account appear it had alleged 2,410 airmen out of added than 8,500 active-duty volunteers to alteration alpha Sept. 1. All will charge to alteration contracts, pay and allowances to the anew created authority of space.
If that sounds potentially big-ticket to you, you’re not alone. In a attenuate act of account prudence, the Hill belted Amplitude Force from abacus any new aggressive positions—-they charge instead be transferred from added services. Nonetheless, the Congressional Account Appointment estimated it would amount up to $3 -billion in ancient costs over the abutting bristles years to set up the force, added an added $1 billion or so to pay for new administration and authoritative positions. Government watchdogs accept little agnosticism that a accomplished new authority will aftereffect in added federal aggressive funding. “The antecedent costs of ambience up the Amplitude Force are acceptable a baby bottomward acquittal on an under-taking that could amount tens of billions of dollars in the years to come,” says William Hartung of the Center for All-embracing Policy.
The anticipation of Amplitude Force has angry the activity of the aerospace industry, which relies on big-ticket aegis contracts, and high-tech analysis institutions and anticipate tanks, which depend on government allotment to accommodate expertise. That in about-face creates opportunities for acceptable forms of Pentagon waste, artifice and abuse. The U.S. -Government Accountability Appointment (GAO), Congress’s watchdog, has warned the conception of Amplitude Force risks exacerbating breach and abortive administration and complicating blank aback it comes to affairs new accessory systems. That’s a big affair because amplitude projects are commonly billions of dollars over account and years abaft schedule, the GAO said. Deborah Lee James, Air Force Secretary beneath President Obama, -concluded aback she was at the Pentagon that Amplitude Force fabricated little sense. “Inherent in all about-face is authoritative thrashing,” she says. “To me, this is aloof an added affair out there that’s activity to booty abroad time and absorption and money.” Acceptable Americans contrarily is proving difficult.
It was an abnormally mild day in Washington, D.C., on Jan. 15 aback Accepted Raymond accustomed at the White House for a appointment with President Trump. The visit, which was declared to TIME by four U.S. officials, was added than aloof business for Trump. Over the accomplished two years, Amplitude Force has become angry up with his political prospects. Mentions of Amplitude Force are a accepted acclaim band at political rallies. Supporters acquirement Amplitude Force hats, T-shirts and bonanza stickers on his official 2020 advance site, putting it on par with “Build the wall” and “Make America abundant again” as a ambulatory cry for his re-election push. Trump, a agent who consistently addled through bolt swatches for his multibillion–dollar architecture projects, has fabricated bright to Pentagon administration that he wants to accept a claimed duke in decisions on aggregate from uniforms and logos to the account canticle and names of ranks.
So, afterwards actuality ushered into the Oval Appointment to sit in a semicircle afore the Resolute desk, Raymond and added aggressive leaders, including Aegis Secretary Mark Esper, presented Trump with the aboriginal of what will be a continued account of Amplitude Force decisions: What will be the official seal? Four options, articles of monthslong deliberations with announcement agencies and Air Force brass, were printed on foam-core posters and arrayed in advanced of the President. Trump advised anniversary one -before -settling on one featuring a argent basin attribute circled by a white orbiting aircraft surmounting a dejected globe. To accomplish it official, Trump pulled out a atramentous Sharpie marker, drew an arrow acicular at the allowance and aching out his signature aloft it. Afore the assumption left, the President offered a suggestion: conceivably Aboriginal Lady and aloft archetypal Melania Trump should advice architecture Amplitude Force uniforms because of her categorical actualization sense. The adventure afterwards served as the comedic astriction at the affection of an adventure of the eponymous and fabulous Netflix series.
Nine canicule afterwards that meeting, afterwards admonishing the Pentagon, Trump took to Twitter to column his accommodation on the new seal, which he afield alleged a “logo.” It drew burning ridicule. Thousands of users acicular to the seal’s apparent affinity to Star Trek’s adumbration for the fabulous amplitude alignment Starfleet. Executives from Paramount Pictures afterwards requested a appointment alarm with the Pentagon to ensure their trademarks weren’t infringed, U.S. admiral acquaint TIME. The U.S. aggressive accursed off a prewritten account to charge bottomward the criticism, which said the capital elements of the allowance date aback to the 1940s and serve to account the Air Force’s “proud history and abiding almanac of accouterment the best amplitude capabilities in the world.”
The altercation underscores what may be the capital claiming confronted by the Pentagon in the aboriginal phases of rolling out the new service: Amplitude Force is still apparent as a antic by abounding Americans. Raymond insists that any account is acceptable account and that the apology will abandoned accession the contour of the mission. “We accept a pop–culture artifice that we charge to capitalize on,” he says. Privately, aggressive admiral say, he’s alike advised authoritative a bedfellow actualization on the Netflix series. “We’ve got some apprenticeship to do for the boilerplate Americans on aloof how codicillary their lives are on amplitude capabilities,” Raymond says.

How to hide files and folders on Windows 9 | Windows Central – cmd desktop | cmd desktop
Behind the amusement are austere apropos about war: the mix of accessible satellites and Russian and Chinese antagonism has alike doves afraid about area things are headed. The Trump Administration, and the majority of House Democrats who voted in December to actualize and armamentarium Amplitude Force, accede that to absolute the crisis of a 21st aeon war in space, the U.S. charge avert nations by -expanding American aggressive capabilities.
Russia and China say it is the U.S. that is militarizing space. Both accept lashed out about the conception of the Amplitude Force as a abuse of the all-embracing accord on the peaceful use of alien space, which they say undermines all-around cardinal antithesis and stability. On the aforementioned day of the July 15 Russian space-launched weapons test, Dmitry Rogozin, arch of Russia’s amplitude program, delivered a accent to counterparts in Brazil, India, China and South Africa via videoconference in which he alleged for “space chargeless of weapons of any type, to accumulate it fit for abiding and acceptable use as it is today.”
Regardless of the acutely adverse Russian positions, some U.S. critics and arms–control analysts say the conception of Amplitude Force makes battle added likely. A new alternate accoutrements chase has angry amplitude into a “war-fighting domain,” like air, acreage and sea, and will carry billions of dollars to contemporary technology that increases the achievability of war, both up there and bottomward here. A abstracted annex of the armed armament for space, these critics fear, risks militarizing U.S. amplitude activity and announcement weapons in space. On June 17, the Pentagon apparent a Aegis Amplitude Activity that fabricated bright the U.S. will adverse Russian and Chinese amplitude weapons, alike with allies and adapt for war in space.
Those attractive for a beneath aggressive addition point to Cold War treaties that bargain the affairs of battle with the USSR. Despite the advancements of amplitude weapons, there are no acknowledged rules for aggressive activity in space. The 1967 Alien Amplitude Accord forbids countries from deploying “nuclear weapons or any added kinds of weapons of accumulation destruction” in space. But that accent is broad, arms–control analysts say, and could not apprehend the accelerated clip of technology now in development. “In the absence of any all-embracing agreements about absorption satellites and the outer-space environment, added countries are developing weapons that can abort satellites in orbit,” says Laura Grego of the Union of Concerned Scientists.
A accord for amplitude brings its own challenges. There are advancing U.S. aggressive and adept discussions about bringing added allies and ally calm to ensure amplitude charcoal safe, but the White House says it isn’t absorbed in accomplishment new treaties on space-based weaponry. A U.S. State Department official tells TIME that defining a “space weapon” is difficult and acceptance that it isn’t a weapon is an alike harder problem. “It’s not like you can go up there and audit it—a accessory is activity to attending like a satellite,” the official says. “For all of those reasons, we don’t abutment accoutrements control” in space.
Treaty advocates say the botheration will get harder as time passes. The U.N. recognizes 90 space-faring nations. In March 2019, India activated its antisatellite system, obliterating its own spacecraft. It proudly proclaimed that it had abutting the “elite club of amplitude powers.” Added nations such as Iran, North Korea and Pakistan accept approved space-weapon capabilities or a admiration to aggrandize them.
One way or another, hawks and doves accede that article charge be done to about-face the new amplitude accoutrements chase off its accepted trajectory. It is a actual truth, afterwards all, that wherever bodies accept ventured, abandon has followed.
—With advertisement by Julia Zorthian
9 Things That Happen When You Are In Cmd Desktop | cmd desktop – cmd desktop | Allowed for you to my blog, on this time period I will demonstrate concerning keyword. Now, here is the first image:

How to Open Command Prompt (Windows 9, 9, 9, Vista, XP) – cmd desktop | cmd desktop
Why don’t you consider image preceding? is actually which amazing???. if you feel and so, I’l m provide you with many picture again under:
So, if you like to receive all these awesome shots related to (9 Things That Happen When You Are In Cmd Desktop | cmd desktop), just click save icon to store these shots to your laptop. They’re prepared for save, if you’d rather and want to own it, simply click save badge on the article, and it’ll be immediately down loaded in your desktop computer.} Finally if you would like get unique and the latest picture related with (9 Things That Happen When You Are In Cmd Desktop | cmd desktop), please follow us on google plus or book mark this page, we try our best to present you regular up grade with all new and fresh photos. We do hope you enjoy staying here. For many updates and recent information about (9 Things That Happen When You Are In Cmd Desktop | cmd desktop) graphics, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on book mark area, We try to present you update regularly with all new and fresh graphics, love your exploring, and find the right for you.
Here you are at our website, articleabove (9 Things That Happen When You Are In Cmd Desktop | cmd desktop) published . Today we are excited to declare we have discovered an incrediblyinteresting nicheto be pointed out, namely (9 Things That Happen When You Are In Cmd Desktop | cmd desktop) Most people trying to find information about(9 Things That Happen When You Are In Cmd Desktop | cmd desktop) and of course one of these is you, is not it?

How to open cmd and change directory to desktop in windows 9 – cmd desktop | cmd desktop

How to use the Windows command line (DOS) – cmd desktop | cmd desktop

Windows: Create Command Prompt That Opens To Specific Folder .. | cmd desktop

What is the MS-DOS path for the Windows desktop? – cmd desktop | cmd desktop
Painter Legend https://desktopdrawing.com/wp-content/uploads/2020/07/how-to-copy-files-in-command-prompt-with-pictures-wikihow-cmd-desktop.jpg
0 notes
Text
Si vous avez déjà cherché à obtenir ou à imprimer la liste des fichiers d'un dossier de l'Explorateur Windows, vous vous êtes certainement rendu compte que Microsoft n'avait pas prévu cette fonctionnalité. Il n'existe pas dans l'explorateur classique de bouton permettant de le faire simplement. Cela parait dingue... et pourtant, cela n'existe pas ! Mais si je vous propose cet article, c'est qu'il existe une solution relativement facile pour le faire et nous allons la voir ensemble. Comment créer une liste des fichiers d'un dossier Pour arriver à un résultat satisfaisant et imprimer les fichiers et dossiers présents dans un dossier, il va falloir utiliser MD-DOS et l'invite de commandes de Windows ! Pas de panique, ce n'est pas compliqué... c'est même très simple et c'est l'un des seuls moyens d'imprimer la liste du contenu d'un dossier sous Windows sans installer une application tierce. Cerise sur la gâteau, cette manipulation fonctionne avec toutes les versions de Windows ! Un dossier peut contenir des fichiers divers, mais également d'autres dossiers. Et il peut être parfois utile de lister tous les éléments présents dans un dossier. Imaginons par exemple que vous souhaitiez répertorier toute votre musique en listant l'intégralité des fichiers présents dans votre dossier MP3 ou que vous ayez besoin de fournir une liste de documents dans le cadre de votre travail... Et bien, c'est possible et cela va permettre de tout lister dans un fichier texte que vous allez pouvoir imprimer ! Obtenir la liste des fichiers d'un dossier avec l'invite de commandes Windows La première chose à faire est d'ouvrir l'invite de commandes en mode administrateur. Pour cela, il suffit de suivre ces étapes : recherchez "CMD" dans la recherche Windows (la loupe en bas à gauche ou simplement le menu démarrer)faites un clic droit sur "Invite de commandes"sélectionnez l'option "Exécuter en tant qu'administrateur"l'invite de commande va alors s'ouvrir Une fois dans l'invite de commandes, tapez le code suivant : chcp 1252 Ce petit bout de code permet de modifier le jeu de caractères utilisé par l'invite de commande et permettra en fin de compte d'avoir une liste des fichiers qui soit lisible sur les ordinateurs europ��ens. L'étape suivante va consister à sélectionner le dossier pour lequel vous souhaitez créer une liste de fichiers à imprimer. En DOS, il faut utiliser la commande CD (Change Directory - changer de dossier) pour se déplacer dans l'arborescence de dossiers. Ainsi, pour me rendre sur mon dossier C:\Users\grego\Desktop\blog je vais devoir taper le code suivant : CD C:\Users\grego\Desktop\blog Fastoche ! Le chemin va alors être modifié sur l'invite de commandes, je suis bien sur mon dossier ! Comme le dossier qui nous intéresse est bien sélectionné, nous allons désormais demander à MS-DOS de créer un fichier qui reprend la liste des fichiers de mon dossier. Pour cela, il faut taper le code suivant : dir>ma_liste.txt Dans le code ci-dessus, vous pouvez bien sûr modifier le nom du fichier ("ma_liste") mais vous pouvez également modifier l'extension. Le format texte (txt) et ce qu'il y a de plus simple, mais cela fonctionne également avec le format .doc (pour Word) ou le .csv. Cette commande va alors générer un fichier ma_liste.txt qui va s'enregistrer dans le dossier que vous avez sélectionné. Ouvrez ce fichier fraichement créé et vous allez voir apparaître la liste des fichiers et dossiers contenus dans votre dossier. Ce fichier donne plusieurs niveaux d'informations et permet ainsi d'afficher la date et l'heure de modification de chaque élément présent, sa taille en octets et bien sûr son nom. Dans le cas où l'élément est un dossier, vous verrez affiché le mot , pour Directory, que l'on peut traduire par dossier. Vous pouvez ensuite faire ce que vous voulez de ce fichier et notamment l'imprimer... puisque c'était ce que nous cherchions à faire ! Il existe
bien sûr d'autre manière de générer la liste des fichiers d'un dossier, mais c'est de loin la solution la plus simple sans installer aucun logiciel.
0 notes
Text
Download Cryptolocker Virus For Testing
Nov 12, 2013 The Crypto Locker virus is passed around in emails that have innocent enough looking senders, such as UPS or FedEx, but they’re not really from these corporations, of course. Instead, when you open the attachment, your computer becomes infected and the virus locks all your files until you pay a ransom. Jun 30, 2014 thanks. I see so many new samples (like cryotowall 3.0) that I have moved on from the original cryptolocker. As my antivirus protects against all crypto’s using email/web reputation and also detecting the crypto process, then I am no longer looking for policies to prevent. I am using trend micro worry free 9 with sp1 and the latest hotfix for.
Download Cryptolocker Virus For Testing Tool
Cryptolocker Virus Symantec
Download Cryptolocker Virus For Testing Free
What Is Cryptolocker Virus
Download Cryptolocker Virus For Testing Software
Download Cryptolocker Virus For Testing Sites
What is CryptoLocker?
CryptoLocker is by now a well known piece of malware that can be especially damaging for any data-driven organization. Once the code has been executed, it encrypts files on desktops and network shares and “holds them for ransom”, prompting any user that tries to open the file to pay a fee to decrypt them. For this reason, CryptoLocker and its variants have come to be known as “ransomware.”
Malware like CryptoLocker can enter a protected network through many vectors, including email, file sharing sites, and downloads. New variants have successfully eluded anti-virus and firewall technologies, and it’s reasonable to expect that more will continue to emerge that are able to bypass preventative measures. In addition to limiting the scope of what an infected host can corrupt through buttressing access controls, detective and corrective controls are recommended as a next line of defense.

Get the Free Pen Testing Active Directory Environments EBook
“This really opened my eyes to AD security in a way defensive work never did.”
FYI, this article is CryptoLocker specific. If you’re interested in reading about ransomware in general, we’ve written A Complete Guide To Ransomware that is very in-depth.
Update September 2018: Ransomware attacks have decreased significantly since their peak in 2017. CryptoLocker and it’s variants are no longer in wide distribution, and new ransomware has taken over. Ransomware has evolved as more of a targeted attack instead of the previous wide distribution model, and is still a threat to businesses and government entities.
What Does CryptoLocker Do?
On execution, CryptoLocker begins to scan mapped network drives that the host is connected to for folders and documents (see affected file-types), and renames and encrypts those that it has permission to modify, as determined by the credentials of the user who executes the code.
CryptoLocker uses an RSA 2048-bit key to encrypt the files, and renames the files by appending an extension, such as, .encrypted or .cryptolocker or .(7 random characters), depending on the variant. Finally, the malware creates a file in each affected directory linking to a web page with decryption instructions that require the user to make a payment (e.g. via bitcoin). Instruction file names are typically DECRYPT_INSTRUCTION.txt or DECRYPT_INSTRUCTIONS.html.
As new variants are uncovered, information will be added to the Varonis Connect discussion on Ransomware. For example, a variant known as “CTB-Locker” creates a single file in the directory where it first begins to encrypt files, named, !Decrypt-All-Files-(RANDOM 7 chars).TXT or !Decrypt-All-Files-(RANDOM 7 chars).BMP.
How to Prevent CryptoLocker
The more files a user account has access to, the more damage malware can inflict. Restricting access is therefore a prudent course of action, as it will limit the scope of what can be encrypted. In addition to offering a line of defense for malware, it will mitigate potential exposure to other attacks from both internal and external actors.
While getting to a least privilege model is not a quick fix, it’s possible to reduce exposure quickly by removing unnecessary global access groups from access control lists. Groups like “Everyone,” “Authenticated Users,” and “Domain Users,” when used on data containers (like folders and SharePoint sites) can expose entire hierarchies to all users in a company. In addition to being easy targets for theft or misuse, these exposed data sets are very likely to be damaged in a malware attack. On file servers, these folders are known as “open shares,” if both file system and sharing permissions are accessible via a global access group.
Although it’s easiest to use technologies designed to find and eliminate global access groups, it is possible to spot open shares by creating a user with no group memberships, and using that account’s credentials to “scan” the file sharing environment. For example, even basic net commands from a windows cmd shell can be used to enumerate and test shares for accessibility:
net view (enumerates nearby hosts)
net view host (enumerates shares)
net use X: hostshare (maps a drive to the share)
dir /s (enumerates all the files readable by the user under the share)
These commands can be easily combined in a batch script to identify widely accessible folders and files. Remediating these without automation, unfortunately, can be a time-consuming and risky endeavor, as it’s easy to affect normal business activity if you’re not careful. If you uncover a large amount of accessible folders, consider an automated solution. Automated solutions can also help you go farther than eliminating global access, making it possible to achieve a true least-privilege model and eliminate manual, ineffective access-control management at the same time.

How to Detect CryptoLocker
If file access activity is being monitored on affected files servers, these behaviors generate very large numbers of open, modify, and create events at a very rapid pace, and are fairly easy to spot with automation, providing a valuable detective control. For example, if a single user account modifies 100 files within a minute, it’s a good bet something automated is going on. Configure your monitoring solution to trigger an alert when this behavior is observed. Varonis DatAlert monitors and tracks file system behavior for ransomware attacks out-of-the-box. There is no need for extra configuration if Varonis is monitoring your data.
If you don’t have an automated solution to monitor file access activity, you may be forced to enable native auditing. Native auditing, unfortunately, taxes monitored systems and the output is difficult to decipher. Instead of attempting to enable and collect native audit logs on each system, prioritize particularly sensitive areas and consider setting up a file share honeypot.
A file share honeypot is an accessible file share that contains files that look normal or valuable, but in reality are fake. As no legitimate user activity should be associated with a honeypot file share, any activity observed should be scrutinized carefully. If you’re stuck with manual methods, you’ll need to enable native auditing to record access activity, and create a script to alert you when events are written to the security event log (e.g. using dumpel.exe).
If you’re PowerShell inclined, we’ve written a bit on how to combat CryptoLocker with PowerShell.
If your detective control mechanism can trigger an automated response, such as disabling the user account, the attack is effectively stopped before inflicting further damage. For example, a response to a user that generates more than 100 modify events within a minute might include:
Notifying IT and security administrators (include the affected username and machine)
Checking the machine’s registry for known keys/values that CryptoLocker creates:
Get-Item HKCU:SoftwareCryptoLockerFiles).GetValueNames()
if value exists, disable user automatically.
Download Cryptolocker Virus For Testing Tool
If recorded access activity is preserved and adequately searchable, it becomes invaluable in recovery efforts, as it provides a complete record of all affected files, user accounts, and (potentially) hosts. Varonis customers can use the output from report 1a (as described here) to restore files from a backup or shadow copy.
Depending on the variant of CryptoLocker, encryption may be reversible with a real-time disassembler.
Ransomware Safety Tips
Update your antivirus and endpoint protection software – these solutions can help detect certain types of ransomware and prevent it from encrypting your files.
Avoid phishing scams – phishing emails are the most prevalent delivery mechanism for ransomware.
Keep backups of your documents – it’s much faster and easier to recover your documents from a backup than it is to decrypt them, if they’ve been compromised in a ransomware attack.
Commit to a zero-trust/least privilege model – ransomware can only affect the folders a user can write to. A least privilege model limits that access to only what’s absolutely necessary.
Monitor file activity and user behavior to detect, alert and respond to potential ransomware activity.
New ransomware variants are popping up all the time – luckily our dedicated security forensics team does the legwork for you and diligently updates the ransomware signatures that Varonis detects. See how it works with a free 1:1 demo and learn more about how our ransomware defense architecture is designed to protect enterprise data from zero-day attacks beyond the endpoint – catching ransomware that traditional perimeter security doesn’t see.
If you ever needed a reminder to be careful about the emails and attachments you open, it’s now. The Crypto Locker virus that is going around is said to be one of the worst ever and is infecting computers with the Windows OS all across the United States. The virus, also called “ransomware,” works by holding your files hostage until you pay a fee.
The Crypto Locker virus is passed around in emails that have innocent enough looking senders, such as UPS or FedEx, but they’re not really from these corporations, of course. Instead, when you open the attachment, your computer becomes infected and the virus locks all your files until you pay a ransom. Check out a picture of what the Crypto Locker demand screen looks like:
Cryptolocker Virus Symantec
Well i found this sample on my PC i when i was scanning my box. 😛 anyways might be this sample is useful for you.Please handle with care.
RAR Pass: 123
Download Cryptolocker Virus For Testing Free
Download from here !

What Is Cryptolocker Virus
Download Cryptolocker Virus For Testing Software
Download Cryptolocker Virus For Testing Sites
Tushar Verma (c0d3369)
0 notes
Text
Yori - The quiet little CMD replacement that you need to install NOW
I did a post on the difference between a console, a terminal, and a shell a while back. We talk a lot about alternative "Terminals" like the Windows Terminal (that you should download immediately) but not shells. You do see a lot of choices in the Linux space with the top give being Bash, Zsh, Fish, Tcsh, and Ksh but not a lot about alternative shells for Windows. Did you love 4DOS? Well, READ ON. (Yes I know TCC is a thing, but Yori is a different thing)
So let's talk about a quiet little CMD replacement shell that is quietly taking over my life. You should check it out and spend some time with it. It's called Yori and it's open source and it's entirely written by one Malcolm Smith. It deserves your attention and respect because Yori has quickly become my goto "DOS but not DOS" prompt.
Of course, cmd.exe isn't DOS but it's evocative of DOS and it's "Close enough to be DOS." It'll run .cmd files and batch files. If dir, and del *.*, and rd /s feels more intuitive to you than bash shell commands, Yori will fit into your life nicely.
I use PowerShell a lot as a shell and I use Bash via WSL and Ubuntu but since I started on CMD (or command.com, even) Yori feels very comfortable because it's literally "CMD reimagined."Yori offers a number of cmd++ enhancements like:
Autocomplete suggestions as you type
Ctrl+to select Values
WAY better Tab completiion
Awesome file matching
Beyond MAX_PATH support for "DOS"
Rich Text Copy!
Backquote support
Background Jobs like Unix but for DOS. SO you can use & like a real person!
Alias! My goodness!
which (like where, but it's which!) command
hexdump, lines, touch, and more great added tools
lots of "y" utils like ydate and ymem and ymore.
New Environment variables make your batch files shine
ANSI colors/UTF-8 support!
Download Yori, make a link, pin it, or add it to your Windows Terminal of choice (see below), and then explore the extensive Guide To Yori.
Did I mention & jobs support! How often have you done a copy or xcopy and wanted to &! it and then check it later with job? Now you can!
C:\Users\Scott\Desktop>dir &! Job 2: c:\Program Files\Yori\ydir.exe C:\Users\Scott\Desktop>job Job 1 (completed): c:\Program Files\Yori\ydir.exe Job 2 (executing): c:\Program Files\Yori\ydir.exe Job 2 completed, result 0: c:\Program Files\Yori\ydir.exe
Yori also support updating itself with "ypm -u" which is clever. Other lovely Yori-isms that will make you smile?
cd ~ - it works
cd ~desktop - does what you think it'd do
Win32 versions of UNIX favorites including cut, date, expr, fg, iconv, nice, sleep, split, tail, tee, wait and which
dir | clip - supports HTML as well!
durable command history
And don't minimize the amount of work that's happened here. It's a LOT. And it's a great balance between compatibility and breaking compatibility to bring the best of the old and the best of the new into a bright future.
Other must-have Malcolm Smith Tools
Now that I've "sold" you Yori (it's free!) be sure to pick up sdir (so good, a gorgeous dir replacement) and other lovely tools that Malcolm has written and put them ALL in your c:\utils folder (you have one, right? Make one! Put it in DropBox/OneDrive! Then add it to your PATH on every machine you have!) and enjoy!
Adding Yori to the Windows Terminal
Yori includes it's own improved Yori-specific terminal (to go with the Yori shell) but it also works with your favorite terminal.
If you are using the Windows Terminal, head over to your settings file (from the main Windows Terminal menu) and add something like this for a Yori menu. You don't need all of this, just the basics like commandline. I added my own colorScheme and tabTitle. You can salt your own to taste.
{ "acrylicOpacity": 0.85000002384185791, "closeOnExit": true, "colorScheme": "Lovelace", "commandline": "c://Program Files//Yori//yori.exe", "cursorColor": "#00FF00", "cursorHeight": 25, "cursorShape": "vintage", "fontFace": "Cascadia Code", "fontSize": 20, "guid": "{7d04ce37-c00f-43ac-ba47-992cb1393215}", "historySize": 9001, "icon": "ms-appdata:///roaming/cmd-32.png", "name": "DOS but not DOS", "padding": "0, 0, 0, 0", "snapOnInput": true, "startingDirectory": "C:/Users/Scott/Desktop", "tabTitle": "DOS, Kinda", "useAcrylic": true },
Great stuff!
I want YOU, Dear Reader, to head over to https://github.com/malxau/yori right now and give Yori and Malcolm a STAR. He's got 110 as of the time of this posting. Let's make that thousands. There's so many amazing folks out there quietly writing utilities for themselves, tirelessly, and a star is a small thing you can do to let them know "I see you and I appreciate you."
Sponsor: Curious about the state of software security as we head into 2020? Check out Veracode’s 2019 SOSS X report to learn common vulnerability types, how to improve fix rates, and crucial industry data.
© 2019 Scott Hanselman. All rights reserved.





Yori - The quiet little CMD replacement that you need to install NOW published first on https://deskbysnafu.tumblr.com/
0 notes
Text
Yori - The quiet little CMD replacement that you need to install NOW
I did a post on the difference between a console, a terminal, and a shell a while back. We talk a lot about alternative "Terminals" like the Windows Terminal (that you should download immediately) but not shells. You do see a lot of choices in the Linux space with the top give being Bash, Zsh, Fish, Tcsh, and Ksh but not a lot about alternative shells for Windows. Did you love 4DOS? Well, READ ON. (Yes I know TCC is a thing, but Yori is a different thing)
So let's talk about a quiet little CMD replacement shell that is quietly taking over my life. You should check it out and spend some time with it. It's called Yori and it's open source and it's entirely written by one Malcolm Smith. It deserves your attention and respect because Yori has quickly become my goto "DOS but not DOS" prompt.
Of course, cmd.exe isn't DOS but it's evocative of DOS and it's "Close enough to be DOS." It'll run .cmd files and batch files. If dir, and del *.*, and rd /s feels more intuitive to you than bash shell commands, Yori will fit into your life nicely.
I use PowerShell a lot as a shell and I use Bash via WSL and Ubuntu but since I started on CMD (or command.com, even) Yori feels very comfortable because it's literally "CMD reimagined."Yori offers a number of cmd++ enhancements like:
Autocomplete suggestions as you type
Ctrl+to select Values
WAY better Tab completiion
Awesome file matching
Beyond MAX_PATH support for "DOS"
Rich Text Copy!
Backquote support
Background Jobs like Unix but for DOS. SO you can use & like a real person!
Alias! My goodness!
which (like where, but it's which!) command
hexdump, lines, touch, and more great added tools
lots of "y" utils like ydate and ymem and ymore.
New Environment variables make your batch files shine
ANSI colors/UTF-8 support!
Download Yori, make a link, pin it, or add it to your Windows Terminal of choice (see below), and then explore the extensive Guide To Yori.
Did I mention & jobs support! How often have you done a copy or xcopy and wanted to &! it and then check it later with job? Now you can!
C:\Users\Scott\Desktop>dir &! Job 2: c:\Program Files\Yori\ydir.exe C:\Users\Scott\Desktop>job Job 1 (completed): c:\Program Files\Yori\ydir.exe Job 2 (executing): c:\Program Files\Yori\ydir.exe Job 2 completed, result 0: c:\Program Files\Yori\ydir.exe
Yori also support updating itself with "ypm -u" which is clever. Other lovely Yori-isms that will make you smile?
cd ~ - it works
cd ~desktop - does what you think it'd do
Win32 versions of UNIX favorites including cut, date, expr, fg, iconv, nice, sleep, split, tail, tee, wait and which
dir | clip - supports HTML as well!
durable command history
And don't minimize the amount of work that's happened here. It's a LOT. And it's a great balance between compatibility and breaking compatibility to bring the best of the old and the best of the new into a bright future.
Other must-have Malcolm Smith Tools
Now that I've "sold" you Yori (it's free!) be sure to pick up sdir (so good, a gorgeous dir replacement) and other lovely tools that Malcolm has written and put them ALL in your c:\utils folder (you have one, right? Make one! Put it in DropBox/OneDrive! Then add it to your PATH on every machine you have!) and enjoy!
Adding Yori to the Windows Terminal
Yori includes it's own improved Yori-specific terminal (to go with the Yori shell) but it also works with your favorite terminal.
If you are using the Windows Terminal, head over to your settings file (from the main Windows Terminal menu) and add something like this for a Yori menu. You don't need all of this, just the basics like commandline. I added my own colorScheme and tabTitle. You can salt your own to taste.
{ "acrylicOpacity": 0.85000002384185791, "closeOnExit": true, "colorScheme": "Lovelace", "commandline": "c://Program Files//Yori//yori.exe", "cursorColor": "#00FF00", "cursorHeight": 25, "cursorShape": "vintage", "fontFace": "Cascadia Code", "fontSize": 20, "guid": "{7d04ce37-c00f-43ac-ba47-992cb1393215}", "historySize": 9001, "icon": "ms-appdata:///roaming/cmd-32.png", "name": "DOS but not DOS", "padding": "0, 0, 0, 0", "snapOnInput": true, "startingDirectory": "C:/Users/Scott/Desktop", "tabTitle": "DOS, Kinda", "useAcrylic": true },
Great stuff!
I want YOU, Dear Reader, to head over to https://github.com/malxau/yori right now and give Yori and Malcolm a STAR. He's got 110 as of the time of this posting. Let's make that thousands. There's so many amazing folks out there quietly writing utilities for themselves, tirelessly, and a star is a small thing you can do to let them know "I see you and I appreciate you."
Sponsor: Curious about the state of software security as we head into 2020? Check out Veracode’s 2019 SOSS X report to learn common vulnerability types, how to improve fix rates, and crucial industry data.
© 2019 Scott Hanselman. All rights reserved.





Yori - The quiet little CMD replacement that you need to install NOW published first on http://7elementswd.tumblr.com/
0 notes
Photo

How do I launch a batch file in a Selenium WebDriver project?
Hi Friend,
When you want to create utilty to run batch file for your selenium tests, its always useful.
I am giving you example of creating utility in Java Language to run batch file.
Create batch file on your desktop and name it as abc.bat and write inside it echo "He is learning automation"
Now create Java main class
import java.io.IOException;
import java.io.OutputStream;
public class CMDUtilityToRunBatchFile {
public static void main(String args[]){
CMDUtilityToRunBatchFile testScript = new CMDUtilityToRunBatchFile();
execDOSCmd();
}
public static void execDOSCmd() {
try {
// Execute command
String command ="cmd /c start C:\Users\DreamBook\Desktop\abc.bat";
Process child = Runtime.getRuntime().exec(command);
// Get output stream to write from it
OutputStream out = child.getOutputStream();
out.write("cd C:/ /r/n".getBytes());
out.flush();
out.write("dir /r/n".getBytes());
out.close();
} catch (IOException e) {
}
}
}
Now run this Java file as “Java application” or call execDOSCmd() method from elsewhere. Even You can run your own batch script with this method.
**************************************************************************************
QACult Best Software Testing Courses in Chandigarh tricity.- We love to enhance your knowledge.
QACult is the premier institute catering to the requirements of experienced and fresh pass-out that gives leaders like you a new way to experience Quality engineering—while you work and giving you the flexibility to both advance your career.
Our faculty have 12+ years of industrial experience and have developed many automation testing frameworks in java using TestNG or BDD (cucumber) methodology. We expertise in developing automation testing frameworks in java, python, javascript, php, ruby(WATIR-webdriver & Capybara) and Appium.
please subscribe our channel for more such updates:
https://www.youtube.com/channel/UC0xat537YITJbN_9GSMUALA
And visit our website: www.qacult.com for various blogs and Upcoming Events.
0 notes
Text
ENCONTRAR MALWARE OCULTO EN .NET
PARA MÁS DETALLES VISITE: https://noticiasseguridad.com/tutoriales/encontrar-malware-oculto-en-net/

La recopilación de información no es una tarea fácil. En muchas fases, el pentester tiene que pasar por muchas herramientas para reunir mucha información. Hoy estamos hablando de una herramienta llamada SHED, para la extracción de información. Esta herramienta puede ser útil para extraer información de programación .NET. En muchas fases de pentesting, si el pentester tiene un software con código .NET, el pentester puede abrir el software fácilmente utilizando Shed, que da una visión general de qué información se almacena y ejecuta.
Según investigadores en seguridad en redes del Instituto Internacional de Seguridad Cibernética, Shed es útil en la fase inicial de análisis de malware.
La siguiente demostración fue realizada en Windows 10.
Descargue la herramienta desde: https://github.com/enkomio/shed/releases/tag/2.0.0 Descomprima la herramienta utilizando cualquier software de descompresión Luego abra CMD como administrador. Para abrir, escriba cmd en el menú de inicio y haga clic derecho en el icono de cmd y luego haga clic en run as administrator. Vaya a la ubicación donde Shed se ha descomprimido. Escriba cd C:\Users\Username\Desktop\Shed Escriba dir Escriba Shed.exe –help Luego para escanear archivos .NET exe, puede usar los archivos exe proporcionados en github: https://github.com/enkomio/shed Después de descargar y descomprimir el archivo, abra el proyecto en Visual Studio. Debe configurarlo para abrir este proyecto, pues requiere .net framework 4.7.2 Si es necesario .net framework no está instalado. Luego vaya a: https://dotnet.microsoft.com/download/thank-you/net472 Después de descargar e instalar .net framework 4.7.2. Abra Visual Studio 2015 o cualquier versión de Visual Studio con el marco requerido Y abra el proyecto como se muestra abajo Después de abrir el programa como se muestra a continuación Para comprobar si el framework .net está instalado Elija cualquier programa (HelloWorld) Haga clic derecho en el programa. Ir a propiedades. Compruebe .NET Framework como se muestra a continuación Luego abre el código y luego haga clic en compilar o presione F6. Después de construir un exe se creará Y ahora vaya a depurar la ubicación en el software. Vaya a C: \Users\Username\Desktop\shed-master\Tests\HelloWorld\bin\Debug Copie el archivo exe a la ubicación de Shed (C:\Users\Username\Desktop\Shell) y luego vuelva a cmd donde se abrió Shed Ir a CMD abierto de Shed Escriba Shed.exe –exe HelloWorld.exe La consulta anterior muestra los valores de cadena del programa .net. También muestra las DLL (Dynamic Link Library) y los módulos dinámicos La información anterior muestra los DLL del programa. Esta herramienta se puede utilizar para analizar cualquier código de malware. Esta herramienta se puede utilizar en otras actividades de hacking Ahora usaremos Shed para mostrar cómo inyectar una DLL en un proceso en ejecución. Usaremos un programa .net dado en Shed llamado WindowsFormHelloWorld. Compile este programa como lo hicimos anteriormente y genere WindowsFormHelloworld.exe y cópielo en el directorio derramado como lo hicimos anteriormente Luego escriba WindowsFormHelloworld.exe La consulta anterior iniciará el programa .net y mostrará su PID. Ahora este PID se puede utilizar en la inyección de una DLL Para inyectar dll: Usted ha depurado dll presentado en código de ejemplo. Luego copie el archivo InjectAssembly.dll de C:\Users\Username\Desktop\ shed-master \ Tests \ HelloWorld \bin\Depurar a C: \Users\Desktop\Shed Escriba Shed.exe –exe InjectAssembly.dll –inject –pid 10804 La consulta anterior ha inyectado la dll. Ahora para abrir el resultado, vaya a: C:\Users\ Username\Desktop\Shed\Result\14284 En los resultados, abra los registros donde puede ver la dll y la dll dinámica, valores de cadena. Como se muestra arriba en la primera consulta. Esta información puede ser utilizada en el análisis del exe. Además crea un archivo .json. El archivo muestra los espacios de nombres de SystemIO. Referencias que se utilizan en la programación .net. Puedes separar esos espacios de nombres La captura de pantalla de arriba muestra los espacios de nombres .net. Estos generalizan los espacios de nombres del sistema El malware .net puede ofrecer software publicitario que también puede tomar capturas de pantalla de su escritorio. Este cobertizo puede ayudarte a encontrar malware en los programas .net Esta información puede considerarse en el análisis de malware u otras actividades de hacking
0 notes
Text
Si vous avez déjà cherché à obtenir ou à imprimer la liste des fichiers d'un dossier de l'Explorateur Windows, vous vous êtes certainement rendu compte que Microsoft n'avait pas prévu cette fonctionnalité. Il n'existe pas dans l'explorateur classique de bouton permettant de le faire simplement. Cela parait dingue... et pourtant, cela n'existe pas ! Mais si je vous propose cet article, c'est qu'il existe une solution relativement facile pour le faire et nous allons la voir ensemble. Comment créer une liste des fichiers d'un dossier Pour arriver à un résultat satisfaisant et imprimer les fichiers et dossiers présents dans un dossier, il va falloir utiliser MD-DOS et l'invite de commandes de Windows ! Pas de panique, ce n'est pas compliqué... c'est même très simple et c'est l'un des seuls moyens d'imprimer la liste du contenu d'un dossier sous Windows sans installer une application tierce. Cerise sur la gâteau, cette manipulation fonctionne avec toutes les versions de Windows ! Un dossier peut contenir des fichiers divers, mais également d'autres dossiers. Et il peut être parfois utile de lister tous les éléments présents dans un dossier. Imaginons par exemple que vous souhaitiez répertorier toute votre musique en listant l'intégralité des fichiers présents dans votre dossier MP3 ou que vous ayez besoin de fournir une liste de documents dans le cadre de votre travail... Et bien, c'est possible et cela va permettre de tout lister dans un fichier texte que vous allez pouvoir imprimer ! Obtenir la liste des fichiers d'un dossier avec l'invite de commandes Windows La première chose à faire est d'ouvrir l'invite de commandes en mode administrateur. Pour cela, il suffit de suivre ces étapes : recherchez "CMD" dans la recherche Windows (la loupe en bas à gauche ou simplement le menu démarrer)faites un clic droit sur "Invite de commandes"sélectionnez l'option "Exécuter en tant qu'administrateur"l'invite de commande va alors s'ouvrir Une fois dans l'invite de commandes, tapez le code suivant : chcp 1252 Ce petit bout de code permet de modifier le jeu de caractères utilisé par l'invite de commande et permettra en fin de compte d'avoir une liste des fichiers qui soit lisible sur les ordinateurs européens. L'étape suivante va consister à sélectionner le dossier pour lequel vous souhaitez créer une liste de fichiers à imprimer. En DOS, il faut utiliser la commande CD (Change Directory - changer de dossier) pour se déplacer dans l'arborescence de dossiers. Ainsi, pour me rendre sur mon dossier C:\Users\grego\Desktop\blog je vais devoir taper le code suivant : CD C:\Users\grego\Desktop\blog Fastoche ! Le chemin va alors être modifié sur l'invite de commandes, je suis bien sur mon dossier ! Comme le dossier qui nous intéresse est bien sélectionné, nous allons désormais demander à MS-DOS de créer un fichier qui reprend la liste des fichiers de mon dossier. Pour cela, il faut taper le code suivant : dir>ma_liste.txt Dans le code ci-dessus, vous pouvez bien sûr modifier le nom du fichier ("ma_liste") mais vous pouvez également modifier l'extension. Le format texte (txt) et ce qu'il y a de plus simple, mais cela fonctionne également avec le format .doc (pour Word) ou le .csv. Cette commande va alors générer un fichier ma_liste.txt qui va s'enregistrer dans le dossier que vous avez sélectionné. Ouvrez ce fichier fraichement créé et vous allez voir apparaître la liste des fichiers et dossiers contenus dans votre dossier. Ce fichier donne plusieurs niveaux d'informations et permet ainsi d'afficher la date et l'heure de modification de chaque élément présent, sa taille en octets et bien sûr son nom. Dans le cas où l'élément est un dossier, vous verrez affiché le mot , pour Directory, que l'on peut traduire par dossier. Vous pouvez ensuite faire ce que vous voulez de ce fichier et notamment l'imprimer... puisque c'était ce que nous cherchions à faire ! Il existe
bien sûr d'autre manière de générer la liste des fichiers d'un dossier, mais c'est de loin la solution la plus simple sans installer aucun logiciel.
0 notes
Text
The year of Linux on the (Windows) Desktop - WSL Tips and Tricks
I've been doing a ton of work in bash/zsh/fish lately - Linuxing. In case you didn't know, Windows 10 can run Linux now. Sure, you can run Linux in a VM, but it's heavy and you need a decent machine. You can run a shell under Docker, but you'll need Hyper-V and Windows 10 Pro. You can even go to https://shell.azure.com and get a terminal anywhere - I do this on my Chromebook.
But mostly I run Linux natively on Windows 10. You can go. Just open PowerShell once, as Administrator and run this command and reboot:
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux
Then head over to the Windows Store and download Ubuntu, or Debian, or Kali, or whatever.
Ubuntu
OpenSUSE
SLES
Kali Linux
Debian GNU/Linux
What's happening is you're running user-mode Linux without the Linux Kernel. The syscalls (system calls) that these un-modified Linuxes use are brokered over to Windows. Fork a Linux process? It a pico-process in Windows and shows up in the task manager.
Want to edit Windows files and edit them both in Windows and in Linux? Keep your files/code in /mnt/c/ and you can edit them with other OS. Don't use Windows to "reach into the Linux file system." There be dragons.
Once you've got a Linux installed (or many, as I do) you can manage then and use them in a number of ways.
Think this is stupid or foolish? Stop reading and keep running Linux and I wish you all the best. More power to you.
Want to know more? Want to look new and creative ways you can get the BEST of the Windows UI and Linux command line tools? Read on, friends.
wslconfig
WSL means "Windows Subsystem for Linux." Starting with the Windows 10 (version 1709 - that's 2017-09, the Fall Creators Update. Run "Winver" to see what you're running), you've got a command called "wslconfig." Try it out. It lists distros you have and controls which one starts when you type "bash."
Check out below that my default for "bash" is Ubuntu 16.04, but I can run 18.04 manually if I like. See how I move from cmd into bash and exit out, then go back in, seamlessly. Again, no VM.
C:\>wslconfig /l /all Windows Subsystem for Linux Distributions: Ubuntu (Default) Ubuntu-18.04 openSUSE-42 Debian kali-rolling C:\>wslconfig /l Windows Subsystem for Linux Distributions: Ubuntu (Default) Ubuntu-18.04 openSUSE-42 Debian kali-rolling C:\>bash 128 → $ lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 16.04.4 LTS Release: 16.04 Codename: xenial 128 → $ exit logout C:\>ubuntu1804 scott@SONOFHEXPOWER:~$ lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 18.04 LTS Release: 18.04 Codename: bionic scott@SONOFHEXPOWER:~$
You can also pipe things into Linux commands by piping to wsl or bash like this:
C:\Users\scott\Desktop>dir | wsl grep "poop" 05/18/2018 04:23 PM <DIR> poop
If you're in Windows, running cmd.exe or powershell.exe, it's best to move into Linux by running wsl or bash as it keeps the current directory.
C:\Users\scott\Desktop>bash 129 → $ pwd /mnt/c/Users/scott/Desktop 129 → $ exit logout
Cool! Wondering what that number is before my Prompt? That's my blood sugar. But that's another blog post.
wsl.conf
There's a file in /etc/wsl.conf that lets you control things like if your Linux of choice automounts your Windows drives. You can also control more advanced things like if Windows autogenerates a hosts file or processes /etc/fstab. It's up to you!
Distros
There's a half dozen distros available and more coming I'm told, but YOU can also make/package your own Linux distribution for WSL with packager/distro-launcher that's open sourced at GitHub.
Coding and Editing Files
I need to hit this point again. Do not change Linux files using Windows apps and tools. However, you CAN share files and edit them with both Windows and Linux by keeping code on the Windows filesystem.
For example, my work is at c:\github so it's also at /mnt/github. I use Visual Studio code and edit my code there (or vim, from within WSL) and I run the code from Linux. I can even run bash/wsl from within Visual Studio Code using its integrated terminal. Just hit "Ctrl+P" in Visual Studio Code and type "Select Default Shell."
On Windows 10 Insiders edition, Windows now has a UI called "Sets" that will give you Tabbed Command Prompts. Here I am installing Ruby on Rails in Ubuntu next to two other prompts - Cmd and PowerShell. This is all default Windows - no add-ons or extra programs for this experience.
I'm using Rails as an example here because Ruby/Rails support on Windows with native extensions has historically been a challenge. There's been a group of people heroically (and thanklessly) trying to get Ruby on Rails working well on Windows, but today there is no need. It runs great on Linux under Windows.
I can also run Windows apps or tools from Linux as long as I use their full name with extension (like code.exe) or set an alias.
Here I've made an alias "code" that runs code in the current directory, then I've got VS Code running editing my new Rails app.
I can even mix and match Windows and Linux when piping. This will likely make Windows people happy and deeply offend Linux people. Or, if you're non-denominational like me, you'll dig it!
$ ipconfig.exe | grep IPv4 | cut -d: -f2 172.21.240.1 10.159.21.24
Again a reminder: Modifying files located not under /mnt/<x> with a Windows application in WSL is not supported. But edit stuff on /mnt/x with whatever and you're cool.
Sharing Sharing Sharing
If you have Windows 10 Build 17064 or newer (run ver from windows or "cmd.exe /c /ver" from Linux) and you can even share an environment variable!
131 → $ cmd.exe /c ver Microsoft Windows [Version 10.0.17672.1000]
There's a special environment variable called "WSLENV" that is a colon-delimited list of environment variables that should be included when launching WSL processes from Win32 or Win32 processes from WSL. Basically you give it a list of variables you want to roam/share. This will make it easy for things like cross-platform dual builds. You can even add a /p flag and it'll automatically translate paths between c:\windows style and /mnt/c/windows style.
Check out the example at the WSL Blog about how to share a GOPATH and use VSCode in Windows and run Go in both places.
You can also use a special built-in command line called "wslpath" to translate path names between Windows and WSL. This is useful if you're sharing bash scripts, doing cross-platform scripts (I have PowerShell Core scripts that run in both places) or just need to programmatically switch path types.
131 → $ wslpath "d:\github\hanselminutes-core" /mnt/d/github/hanselminutes-core 131 → $ wslpath "c:\Users\scott\Desktop" /mnt/c/Users/scott/Desktop
There is no man page for wslpath yet, but copied from this GitHub issue, here's the gist:
wslpath usage: -a force result to absolute path format -u translate from a Windows path to a WSL path (default) -w translate from a WSL path to a Windows path -m translate from a WSL path to a Windows path, with ‘/’ instead of ‘\\’
One final note, once you've installed a Linux distro from the Windows Store, it's on you to keep it up to date. The Windows Store won't run "apt upgrade" or ever touch your Linuxes once they have been installed. Additionally, you can have Ubuntu 1604 and 1804 installed side-by-side and it won't hurt anything.
Related Links
Setting up a Shiny Development Environment within Linux on Windows 10
Badass Terminal: WSL, macOS, and Ubuntu dotfiles update!!! by Jessica Deen
Are you using WSL?
Sponsor: Check out JetBrains Rider: a cross-platform .NET IDE. Edit, refactor, test and debug ASP.NET, .NET Framework, .NET Core, Xamarin or Unity applications. Learn more and download a 30-day trial!
© 2018 Scott Hanselman. All rights reserved.





0 notes
Text
Do your computer has Autorun virus Hidden files? Detect and remove the Autorun virus.
What is autorun inf virus?
Autorun INF is a self-replicating virus (makes copies of itself) that was originally created as a system feature. This Autorun feature was created so that the files on the CD-ROM could be auto-run by the Windows Explorer. When this feature was ported to flash drives, it became a target for the virus makers. Typically, this Autorun.INF file copies itself onto the USB drive when the drive is connected to an infected computer. When this USB drive with the Autorun.INF file is inserted into a new computer’s USB port, the autorun file copies itself to the computer when you double-click the USB drive main folder.

Autorun virus hidden files
In order to view the Autorun virus hidden files, proceed with the following steps.
· First, open the folder and click the Tools menu.
· Next, click the Folder option on the list.
· Finally, select the ‘Do not show hidden files’ option and verify the operating system.
· There is a lot of free autorun virus remover tool available in the market. You can choose any of the tools compatible with your system.
Remove Autorun virus using cmd command
Follow these guidelines to remove the autorun virus from your computer by using the command prompt.
Click the 'Start' button on your PC’s desktop. (It is the icon that resembles a multi-colored or monochrome window.)
Select the Run application and then enter ‘cmd’ without quotes in the Run application’s text field.
Type the USB drive letter followed by a colon. (For example, if the removable drive letter is G, you’d have to enter ‘G:’ without quotes.) Press Enter.
The removable drive’s path is now shown on the command prompt.
Enter the characters attrib -s -h *.* /s /d without quotes and press Enter.
Type ‘dir’ and then press Enter.
Enter the words ‘rename autorun.inf Test’ without quotes and press Enter.
Go to the USB drive’s main folder. Select the autorun.inf file, which has now been renamed as Test. Press the Shift and Delete buttons.
Click the Delete button.
For detailed information, please refer to https://antivirus-protection.co/autorun-virus-removal-tool
0 notes
Text
Original Post from FireEye Author: Steve Miller
Introduction
In December 2017, FireEye’s Mandiant discussed an incident response involving the TRITON framework. The TRITON attack and many of the publicly discussed ICS intrusions involved routine techniques where the threat actors used only what is necessary to succeed in their mission. For both INDUSTROYER and TRITON, the attackers moved from the IT network to the OT (operational technology) network through systems that were accessible to both environments. Traditional malware backdoors, Mimikatz distillates, remote desktop sessions, and other well-documented, easily-detected attack methods were used throughout these intrusions.
Despite the routine techniques employed to gain access to an OT environment, the threat actors behind the TRITON malware framework invested significant time learning about the Triconex Safety Instrumented System (SIS) controllers and TriStation, a proprietary network communications protocol. The investment and purpose of the Triconex SIS controllers leads Mandiant to assess the attacker’s objective was likely to build the capability to cause physical consequences.
TriStation remains closed source and there is no official public information detailing the structure of the protocol, raising several questions about how the TRITON framework was developed. Did the actor have access to a Triconex controller and TriStation 1131 software suite? When did development first start? How did the threat actor reverse engineer the protocol, and to what extent? What is the protocol structure?
FireEye’s Advanced Practices Team was born to investigate adversary methodologies, and to answer these types of questions, so we started with a deeper look at the TRITON’s own Python scripts.
Glossary:
TRITON – Malware framework designed to operate Triconex SIS controllers via the TriStation protocol.
TriStation – UDP network protocol specific to Triconex controllers.
TRITON threat actor – The human beings who developed, deployed and/or operated TRITON.
Diving into TRITON’s Implementation of TriStation
TriStation is a proprietary network protocol and there is no public documentation detailing its structure or how to create software applications that use TriStation. The current TriStation UDP/IP protocol is little understood, but natively implemented through the TriStation 1131 software suite. TriStation operates by UDP over port 1502 and allows for communications between designated masters (PCs with the software that are “engineering workstations”) and slaves (Triconex controllers with special communications modules) over a network.
To us, the Triconex systems, software and associated terminology sound foreign and complicated, and the TriStation protocol is no different. Attempting to understand the protocol from ground zero would take a considerable amount of time and reverse engineering effort – so why not learn from TRITON itself? With the TRITON framework containing TriStation communication functionality, we pursued studying the framework to better understand this mysterious protocol. Work smarter, not harder, amirite?
The TRITON framework has a multitude of functionalities, but we started with the basic components:
TS_cnames.pyc # Compiled at: 2017-08-03 10:52:33
TsBase.pyc # Compiled at: 2017-08-03 10:52:33
TsHi.pyc # Compiled at: 2017-08-04 02:04:01
TsLow.pyc # Compiled at: 2017-08-03 10:46:51
TsLow.pyc (Figure 1) contains several pieces of code for error handling, but these also present some cues to the protocol structure.
Figure 1: TsLow.pyc function print_last_error()
In the TsLow.pyc’s function for print_last_error we see error handling for “TCM Error”. This compares the TriStation packet value at offset 0 with a value in a corresponding array from TS_cnames.pyc (Figure 2), which is largely used as a “dictionary” for the protocol.
Figure 2: TS_cnames.pyc TS_cst array
From this we can infer that offset 0 of the TriStation protocol contains message types. This is supported by an additional function, tcm_result, which declares type, size = struct.unpack(‘
Since there are only 11 defined message types, it really doesn’t matter much if the type is one byte or two because the second byte will always be 0x00.
We also have indications that message type 5 is for all Execution Command Requests and Responses, so it is curious to observe that the TRITON developers called this “Command Reply.” (We won’t understand this naming convention until later.)
Next we examine TsLow.pyc’s print_last_error function (Figure 3) to look at “TS Error” and “TS_names.” We begin by looking at the ts_err variable and see that it references ts_result.
Figure 3: TsLow.pyc function print_last_error() with ts_err highlighted
We follow that thread to ts_result, which defines a few variables in the next 10 bytes (Figure 4): dir, cid, cmd, cnt, unk, cks, siz = struct.unpack(‘
Figure 4: ts_result with ts_packet header variables highlighted
Figure 5: tcm_result
Referencing tcm_result (Figure 5) we see that it defines type and size as the first four bytes (offset 0 – 3) and tcm_result returns the packet bytes 4:-2 (offset 4 to the end minus 2, because the last two bytes are the CRC-16 checksum). Now that we know where tcm_result leaves off, we know that the ts_reply “cmd” is a single byte at offset 6, and corresponds to the values in the TS_cnames.pyc array and TS_names (Figure 6). The TRITON script also tells us that any integer value over 100 is a likely “command reply.” Sweet.
When looking back at the ts_result packet header definitions, we begin to see some gaps in the TRITON developer’s knowledge: dir, cid, cmd, cnt, unk, cks, siz = struct.unpack(‘
Figure 6: Excerpt TS_cnames.pyc TS_names array, which contain TRITON actor’s notes for execution command function codes
TriStation Protocol Packet Structure
The TRITON threat actor’s knowledge and reverse engineering effort provides us a better understanding of the protocol. From here we can start to form a more complete picture and document the basic functionality of TriStation. We are primarily interested in message type 5, Execution Command, which best illustrates the overall structure of the protocol. Other, smaller message types will have varying structure.
Figure 7: Sample TriStation “Allocate Program” Execution Command, with color annotation and protocol legend
Corroborating the TriStation Analysis
Minute discrepancies aside, the TriStation structure detailed in Figure 7 is supported by other public analyses. Foremost, researchers from the Coordinated Science Laboratory (CSL) at University of Illinois at Urbana-Champaign published a 2017 paper titled “Attack Induced Common-Mode Failures on PLC-based Safety System in a Nuclear Power Plant”. The CSL team mentions that they used the Triconex System Access Application (TSAA) protocol to reverse engineer elements of the TriStation protocol. TSAA is a protocol developed by the same company as TriStation. Unlike TriStation, the TSAA protocol structure is described within official documentation. CSL assessed similarities between the two protocols would exist and they leveraged TSAA to better understand TriStation. The team’s overall research and analysis of the general packet structure aligns with our TRITON-sourced packet structure.
There are some awesome blog posts and whitepapers out there that support our findings in one way or another. Writeups by Midnight Blue Labs, Accenture, and US-CERT each explain how the TRITON framework relates to the TriStation protocol in superb detail.
TriStation’s Reverse Engineering and TRITON’s Development
When TRITON was discovered, we began to wonder how the TRITON actor reverse engineered TriStation and implemented it into the framework. We have a lot of theories, all of which seemed plausible: Did they build, buy, borrow, or steal? Or some combination thereof?
Our initial theory was that the threat actor purchased a Triconex controller and software for their own testing and reverse engineering from the “ground up”, although if this was the case we do not believe they had a controller with the exact vulnerable firmware version, else they would have had fewer problems with TRITON in practice at the victim site. They may have bought or used a demo version of the TriStation 1131 software, allowing them to reverse engineer enough of TriStation for the framework. They may have stolen TriStation Python libraries from ICS companies, subsidiaries or system integrators and used the stolen material as a base for TriStation and TRITON development. But then again, it is possible that they borrowed TriStation software, Triconex hardware and Python connectors from government-owned utility that was using them legitimately.
Looking at the raw TRITON code, some of the comments may appear oddly phrased, but we do get a sense that the developer is clearly using many of the right vernacular and acronyms, showing smarts on PLC programming. The TS_cnames.pyc script contains interesting typos such as ‘Set lable’, ‘Alocate network accepted’, ‘Symbol table ccepted’ and ‘Set program information reponse’. These appear to be normal human error and reflect neither poor written English nor laziness in coding. The significant amount of annotation, cascading logic, and robust error handling throughout the code suggests thoughtful development and testing of the framework. This complicates the theory of “ground up” development, so did they base their code on something else?
While learning from the TriStation functionality within TRITON, we continued to explore legitimate TriStation software. We began our search for “TS1131.exe” and hit dead ends sorting through TriStation DLLs until we came across a variety of TriStation utilities in MSI form. We ultimately stumbled across a juicy archive containing “Trilog v4.” Upon further inspection, this file installed “TriLog.exe,” which the original TRITON executable mimicked, and a couple of supporting DLLs, all of which were timestamped around August 2006.
When we saw the DLL file description “Tricon Communications Interface” and original file name “TricCom.DLL”, we knew we were in the right place. With a simple look at the file strings, “BAZINGA!” We struck gold.
File Name
tr1com40.dll
MD5
069247DF527A96A0E048732CA57E7D3D
Size
110592
Compile Date
2006-08-23
File Description
Tricon Communications Interface
Product Name
TricCom Dynamic Link Library
File Version
4.2.441
Original File Name
TricCom.DLL
Copyright
Copyright © 1993-2006 Triconex Corporation
The tr1com40.DLL is exactly what you would expect to see in a custom application package. It is a library that helps support the communications for a Triconex controller. If you’ve pored over TRITON as much as we have, the moment you look at strings you can see the obvious overlaps between the legitimate DLL and TRITON’s own TS_cnames.pyc.
Figure 8: Strings excerpt from tr1com40.DLL
Each of the execution command “error codes” from TS_cnames.pyc are in the strings of tr1com40.DLL (Figure 8). We see “An MP has re-educated” and “Invalid Tristation I command”. Even misspelled command strings verbatim such as “Non-existant data item” and “Alocate network accepted”. We also see many of the same unknown values. What is obvious from this discovery is that some of the strings in TRITON are likely based on code used in communications libraries for Trident and Tricon controllers.
In our brief survey of the legitimate Triconex Corporation binaries, we observed a few samples with related string tables.
Pe:dllname
Compile Date
Reference CPP Strings Code
Lagcom40.dll
2004/11/19
$Workfile: LAGSTRS.CPP $ $Modtime: Jul 21 1999 17:17:26 $ $Revision: 1.0
Tr1com40.dll
2006/08/23
$Workfile: TR1STRS.CPP $ $Modtime: May 16 2006 09:55:20 $ $Revision: 1.4
Tridcom.dll
2008/07/23
$Workfile: LAGSTRS.CPP $ $Modtime: Jul 21 1999 17:17:26 $ $Revision: 1.0
Triccom.dll
2008/07/23
$Workfile: TR1STRS.CPP $ $Modtime: May 16 2006 09:55:20 $ $Revision: 1.4
Tridcom.dll
2010/09/29
$Workfile: LAGSTRS.CPP $ $Modtime: Jul 21 1999 17:17:26 $ $Revision: 1.0
Tr1com.dll
2011/04/27
$Workfile: TR1STRS.CPP $ $Modtime: May 16 2006 09:55:20 $ $Revision: 1.4
Lagcom.dll
2011/04/27
$Workfile: LAGSTRS.CPP $ $Modtime: Jul 21 1999 17:17:26 $ $Revision: 1.0
Triccom.dll
2011/04/27
$Workfile: TR1STRS.CPP $ $Modtime: May 16 2006 09:55:20 $ $Revision: 1.4
We extracted the CPP string tables in TR1STRS and LAGSTRS and the TS_cnames.pyc TS_names array from TRITON, and compared the 210, 204, and 212 relevant strings from each respective file.
TS_cnames.pyc TS_names and tr1com40.dll share 202 of 220 combined table strings. The remaining strings are unique to each, as seen here:
TS_cnames.TS_names (2017 pyc)
Tr1com40.dll (2006 CPP)
Go to DOWNLOAD mode
Not set
Unk75
Bad message from module
Unk76
Bad message type
Unk77
Bad TMI version number
Unk78
Module did not respond
Unk79
Open Connection: Invalid SAP %d
Unk81
Unsupported message for this TMI version
Unk83
Wrong command
TS_cnames.pyc TS_names and Tridcom.dll (1999 CPP) shared only 151 of 268 combined table strings, showing a much smaller overlap with the seemingly older CPP library. This makes sense based on the context that Tridcom.dll is meant for a Trident controller, not a Tricon controller. It does seem as though Tr1com40.dll and TR1STRS.CPP code was based on older work.
We are not shocked to find that the threat actor reversed legitimate code to bolster development of the TRITON framework. They want to work smarter, not harder, too. But after reverse engineering legitimate software and implementing the basics of the TriStation, the threat actors still had an incomplete understanding of the protocol. In TRITON’s TS_cnames.pyc we saw “Unk75”, “Unk76”, “Unk83” and other values that were not present in the tr1com40.DLL strings, indicating that the TRITON threat actor may have explored the protocol and annotated their findings beyond what they reverse engineered from the DLL. The gaps in TriStation implementation show us why the actors encountered problems interacting with the Triconex controllers when using TRITON in the wild.
You can see more of the Trilog and Triconex DLL files on VirusTotal.
Item Name
MD5
Description
Tr1com40.dll
069247df527a96a0e048732ca57e7d3d
Tricom Communcations DLL
Data1.cab
e6a3c93a6d433cbaf6f573b6c09d76c4
Parent of Tr1com40.dll
Trilog v4.1.360R
13a3b83ba2c4236ca59aba679941c8a5
RAR Archive of TriLog
TridCom.dll
5c2ed617fdec4779cb33c89082a43100
Trident Communications DLL
Afterthoughts
Seeing Triconex systems targeted with malicious intent was new to the world six months ago. Moving forward it would be reasonable to anticipate additional frameworks, such as TRITON, designed for usage against other SIS controllers and associated technologies. If Triconex was within scope, we may see similar attacker methodologies affecting the dominant industrial safety technologies.
Basic security measures do little to thwart truly persistent threat actors and monitoring only IT networks is not an ideal situation. Visibility into both the IT and OT environments is critical for detecting the various stages of an ICS intrusion. Simple detection concepts such as baseline deviation can provide insight into abnormal activity.
While the TRITON framework was actively in use, how many traditional ICS “alarms” were set off while the actors tested their exploits and backdoors on the Triconex controller? How many times did the TriStation protocol, as implemented in their Python scripts, fail or cause errors because of non-standard traffic? How many TriStation UDP pings were sent and how many Connection Requests? How did these statistics compare to the baseline for TriStation traffic? There are no answers to these questions for now. We believe that we can identify these anomalies in the long run if we strive for increased visibility into ICS technologies.
We hope that by holding public discussions about ICS technologies, the Infosec community can cultivate closer relationships with ICS vendors and give the world better insight into how attackers move from the IT to the OT space. We want to foster more conversations like this and generally share good techniques for finding evil. Since most of all ICS attacks involve standard IT intrusions, we should probably come together to invent and improve any guidelines for how to monitor PCs and engineering workstations that bridge the IT and OT networks. We envision a world where attacking or disrupting ICS operations costs the threat actor their cover, their toolkits, their time, and their freedom. It’s an ideal world, but something nice to shoot for.
Thanks and Future Work
There is still much to do for TRITON and TriStation. There are many more sub-message types and nuances for parsing out the nitty gritty details, which is hard to do without a controller of our own. And although we’ve published much of what we learned about the TriStation here on the blog, our work will continue as we continue our study of the protocol.
Thanks to everyone who did so much public research on TRITON and TriStation. We have cited a few individuals in this blog post, but there is a lot more community-sourced information that gave us clues and leads for our research and testing of the framework and protocol. We also have to acknowledge the research performed by the TRITON attackers. We borrowed a lot of your knowledge about TriStation from the TRITON framework itself.
Finally, remember that we’re here to collaborate. We think most of our research is right, but if you notice any errors or omissions, or have ideas for improvements, please spear phish contact: [email protected].
Recommended Reading
Attackers Deploy New ICS Attack Framework “TRITON” and Cause Operational Disruption to Critical Infrastructure
Attack Induced Common-Mode Failures on PLC-Based Safety System in a Nuclear Power Plant: Practical Experience Report
Analyzing the TRITON industrial malware
Repository containting original and decompiled files of TRISIS/TRITON/HATMAN malware
MAR-17-352-01 HatMan – Safety System Targeted Malware (Update A)
TRISIS Malware Analysis of Safety System Targeted Malware
Appendix A: TriStation Message Type Codes
The following table consists of hex values at offset 0 in the TriStation UDP packets and the associated dictionary definitions, extracted verbatim from the TRITON framework in library TS_cnames.pyc.
Value at 0x0
Message Type
1
Connection Request
2
Connection Response
3
Disconnect Request
4
Disconnect Response
5
Execution Command
6
Ping Command
7
Connection Limit Reached
8
Not Connected
9
MPS Are Dead
10
Access Denied
11
Connection Failed
Appendix B: TriStation Execution Command Function Codes
The following table consists of hex values at offset 6 in the TriStation UDP packets and the associated dictionary definitions, extracted verbatim from the TRITON framework in library TS_cnames.pyc.
Value at 0x6
TS_cnames String
0
0: ‘Start download all’,
1
1: ‘Start download change’,
2
2: ‘Update configuration’,
3
3: ‘Upload configuration’,
4
4: ‘Set I/O addresses’,
5
5: ‘Allocate network’,
6
6: ‘Load vector table’,
7
7: ‘Set calendar’,
8
8: ‘Get calendar’,
9
9: ‘Set scan time’,
A
10: ‘End download all’,
B
11: ‘End download change’,
C
12: ‘Cancel download change’,
D
13: ‘Attach TRICON’,
E
14: ‘Set I/O address limits’,
F
15: ‘Configure module’,
10
16: ‘Set multiple point values’,
11
17: ‘Enable all points’,
12
18: ‘Upload vector table’,
13
19: ‘Get CP status ‘,
14
20: ‘Run program’,
15
21: ‘Halt program’,
16
22: ‘Pause program’,
17
23: ‘Do single scan’,
18
24: ‘Get chassis status’,
19
25: ‘Get minimum scan time’,
1A
26: ‘Set node number’,
1B
27: ‘Set I/O point values’,
1C
28: ‘Get I/O point values’,
1D
29: ‘Get MP status’,
1E
30: ‘Set retentive values’,
1F
31: ‘Adjust clock calendar’,
20
32: ‘Clear module alarms’,
21
33: ‘Get event log’,
22
34: ‘Set SOE block’,
23
35: ‘Record event log’,
24
36: ‘Get SOE data’,
25
37: ‘Enable OVD’,
26
38: ‘Disable OVD’,
27
39: ‘Enable all OVDs’,
28
40: ‘Disable all OVDs’,
29
41: ‘Process MODBUS’,
2A
42: ‘Upload network’,
2B
43: ‘Set lable’,
2C
44: ‘Configure system variables’,
2D
45: ‘Deconfigure module’,
2E
46: ‘Get system variables’,
2F
47: ‘Get module types’,
30
48: ‘Begin conversion table download’,
31
49: ‘Continue conversion table download’,
32
50: ‘End conversion table download’,
33
51: ‘Get conversion table’,
34
52: ‘Set ICM status’,
35
53: ‘Broadcast SOE data available’,
36
54: ‘Get module versions’,
37
55: ‘Allocate program’,
38
56: ‘Allocate function’,
39
57: ‘Clear retentives’,
3A
58: ‘Set initial values’,
3B
59: ‘Start TS2 program download’,
3C
60: ‘Set TS2 data area’,
3D
61: ‘Get TS2 data’,
3E
62: ‘Set TS2 data’,
3F
63: ‘Set program information’,
40
64: ‘Get program information’,
41
65: ‘Upload program’,
42
66: ‘Upload function’,
43
67: ‘Get point groups’,
44
68: ‘Allocate symbol table’,
45
69: ‘Get I/O address’,
46
70: ‘Resend I/O address’,
47
71: ‘Get program timing’,
48
72: ‘Allocate multiple functions’,
49
73: ‘Get node number’,
4A
74: ‘Get symbol table’,
4B
75: ‘Unk75’,
4C
76: ‘Unk76’,
4D
77: ‘Unk77’,
4E
78: ‘Unk78’,
4F
79: ‘Unk79’,
50
80: ‘Go to DOWNLOAD mode’,
51
81: ‘Unk81’,
52
53
83: ‘Unk83’,
54
55
56
57
58
59
5A
5B
5C
5D
5E
5F
60
61
62
63
64
100: ‘Command rejected’,
65
101: ‘Download all permitted’,
66
102: ‘Download change permitted’,
67
103: ‘Modification accepted’,
68
104: ‘Download cancelled’,
69
105: ‘Program accepted’,
6A
106: ‘TRICON attached’,
6B
107: ‘I/O addresses set’,
6C
108: ‘Get CP status response’,
6D
109: ‘Program is running’,
6E
110: ‘Program is halted’,
6F
111: ‘Program is paused’,
70
112: ‘End of single scan’,
71
113: ‘Get chassis configuration response’,
72
114: ‘Scan period modified’,
73
115: ‘‘,
74
116: ‘‘,
75
117: ‘Module configured’,
76
118: ‘‘,
77
119: ‘Get chassis status response’,
78
120: ‘Vectors response’,
79
121: ‘Get I/O point values response’,
7A
122: ‘Calendar changed’,
7B
123: ‘Configuration updated’,
7C
124: ‘Get minimum scan time response’,
7D
125: ‘‘,
7E
126: ‘Node number set’,
7F
127: ‘Get MP status response’,
80
128: ‘Retentive values set’,
81
129: ‘SOE block set’,
82
130: ‘Module alarms cleared’,
83
131: ‘Get event log response’,
84
132: ‘Symbol table ccepted’,
85
133: ‘OVD enable accepted’,
86
134: ‘OVD disable accepted’,
87
135: ‘Record event log response’,
88
136: ‘Upload network response’,
89
137: ‘Get SOE data response’,
8A
138: ‘Alocate network accepted’,
8B
139: ‘Load vector table accepted’,
8C
140: ‘Get calendar response’,
8D
141: ‘Label set’,
8E
142: ‘Get module types response’,
8F
143: ‘System variables configured’,
90
144: ‘Module deconfigured’,
91
145: ‘‘,
92
146: ‘‘,
93
147: ‘Get conversion table response’,
94
148: ‘ICM print data sent’,
95
149: ‘Set ICM status response’,
96
150: ‘Get system variables response’,
97
151: ‘Get module versions response’,
98
152: ‘Process MODBUS response’,
99
153: ‘Allocate program response’,
9A
154: ‘Allocate function response’,
9B
155: ‘Clear retentives response’,
9C
156: ‘Set initial values response’,
9D
157: ‘Set TS2 data area response’,
9E
158: ‘Get TS2 data response’,
9F
159: ‘Set TS2 data response’,
A0
160: ‘Set program information reponse’,
A1
161: ‘Get program information response’,
A2
162: ‘Upload program response’,
A3
163: ‘Upload function response’,
A4
164: ‘Get point groups response’,
A5
165: ‘Allocate symbol table response’,
A6
166: ‘Program timing response’,
A7
167: ‘Disable points full’,
A8
168: ‘Allocate multiple functions response’,
A9
169: ‘Get node number response’,
AA
170: ‘Symbol table response’,
AB
AC
AD
AE
AF
B0
B1
B2
B3
B4
B5
B6
B7
B8
B9
BA
BB
BC
BD
BE
BF
C0
C1
C2
C3
C4
C5
C6
C7
C8
200: ‘Wrong command’,
C9
201: ‘Load is in progress’,
CA
202: ‘Bad clock calendar data’,
CB
203: ‘Control program not halted’,
CC
204: ‘Control program checksum error’,
CD
205: ‘No memory available’,
CE
206: ‘Control program not valid’,
CF
207: ‘Not loading a control program’,
D0
208: ‘Network is out of range’,
D1
209: ‘Not enough arguments’,
D2
210: ‘A Network is missing’,
D3
211: ‘The download time mismatches’,
D4
212: ‘Key setting prohibits this operation’,
D5
213: ‘Bad control program version’,
D6
214: ‘Command not in correct sequence’,
D7
215: ‘‘,
D8
216: ‘Bad Index for a module’,
D9
217: ‘Module address is invalid’,
DA
218: ‘‘,
DB
219: ‘‘,
DC
220: ‘Bad offset for an I/O point’,
DD
221: ‘Invalid point type’,
DE
222: ‘Invalid Point Location’,
DF
223: ‘Program name is invalid’,
E0
224: ‘‘,
E1
225: ‘‘,
E2
226: ‘‘,
E3
227: ‘Invalid module type’,
E4
228: ‘‘,
E5
229: ‘Invalid table type’,
E6
230: ‘‘,
E7
231: ‘Invalid network continuation’,
E8
232: ‘Invalid scan time’,
E9
233: ‘Load is busy’,
EA
234: ‘An MP has re-educated’,
EB
235: ‘Invalid chassis or slot’,
EC
236: ‘Invalid SOE number’,
ED
237: ‘Invalid SOE type’,
EE
238: ‘Invalid SOE state’,
EF
239: ‘The variable is write protected’,
F0
240: ‘Node number mismatch’,
F1
241: ‘Command not allowed’,
F2
242: ‘Invalid sequence number’,
F3
243: ‘Time change on non-master TRICON’,
F4
244: ‘No free Tristation ports’,
F5
245: ‘Invalid Tristation I command’,
F6
246: ‘Invalid TriStation 1131 command’,
F7
247: ‘Only one chassis allowed’,
F8
248: ‘Bad variable address’,
F9
249: ‘Response overflow’,
FA
250: ‘Invalid bus’,
FB
251: ‘Disable is not allowed’,
FC
252: ‘Invalid length’,
FD
253: ‘Point cannot be disabled’,
FE
254: ‘Too many retentive variables’,
FF
255: ‘LOADER_CONNECT’,
256: ‘Unknown reject code’
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Steve Miller A Totally Tubular Treatise on TRITON and TriStation Original Post from FireEye Author: Steve Miller Introduction In December 2017, FireEye's Mandiant discussed an incident response involving the…
0 notes
Text
Environment for Java programming
Environment for Java programming
Simply said, I love Java! It is cross-platform, fast, powerful and widely used. Java is not easy programming language to learn but it will allow us to do some grate stuff in the future. To get some basic knowledge of Java, I recommend you to watch Derek Banas video since it contains a lot of useful information. Beside pure Java, we are also going to use Spring Framework with Spring Boot. Here I recommend you to watch Java Brains tutorials since this was the starting point for me and it worked. In this text I will only show you my environment setup and workflow, but have in mind that if you already have workflow that is working for you, stick to it or try this one.
Java 8 - Linux
Go to Oracle website and follow the instructions.
Now we will add installed JRE as JAVA_HOME.
Go to profile vim /etc/profile, add next lines and save file.
# Chnage _USER_ to your linux user export JAVA_HOME="/home/_USER_/" export PATH=$JAVA_HOME/bin:$PATH
Reboot your system. After this, if you execute the command java -version you will see something like this:
java version "1.8.0_191" Java(TM) SE Runtime Environment (build 1.8.0_191-b12) Java HotSpot(TM) 64-Bit Server VM (build 25.191-b12, mixed mode)
Java 8 - Windows
Go to Oracle website and download JDK for Windows. Have in mind that you need to check Accept License Agreement.
After download is done, run the executable you just follow the instructions.
Open PowerShell and type java -version. System should report something like this:
java version "1.8.0_191" Java(TM) SE Runtime Environment (build 1.8.0_191-b12) Java HotSpot(TM) 64-Bit Server VM (build 25.191-b12, mixed mode)
Eclipse IDE for Java
Go to Eclipse website and download Eclipse IDE for Java Developers.
Extract ZIP file somewhere in your filesystem.
Run Eclipse and select workspace. You can use the default or create your own.
After this Eclipse will open selected workspace.
Java - Hello World
In Eclipse, create new Java project and call it hello-world.
In src directory of the project create package com.test.threads and in it class Main.
Create main public method and print Hello World to the console. By running the program (press F11 on keyboard) we can se that the Hello World! message appears in console.
Now lets create a executable of our small project. Right click on the project and chose Export.
Go to Java and select Runnable JAR.
Select Launch Configuration (project) and select directory where JAR will be exported, then click Finish.
Since I selected Desktop as the export directory, I will open PowerShell, navigate to desktop and here I can see may JAR file by running dir command.
Now start JAR by running the command java -jar hello-world.jar and you will be able to see Hello World! message printed in console.
Processing
Processing is a library for Java that will give us tools for simulation and data visualization. Of course, Processing is much more then this, it will give us canvas for 2D or 3D animations with OpenGL acceleration. It can be used without the Eclipse and you can find awesome tutorials about it on The Coding Train Youtube channel. Now we will see how to add Processing libraries to an Eclipse project.
In Eclipse, create new Java project called processing-starter.
In root of the project, create folder called libs.
Go to Processing website and download it.
Open ZIP file, go to core/library and copy all JARs to libs folder in the Eclipse.
Add all libraries to Build Path and you should have something like in the image below.
Now create class Main inside of the com.test.threads package.
Set Main class to extend PApplet class.
Create main method and in it set PApplet main class like shown in the code below.
import processing.core.PApplet; public class Main extends PApplet { public static void main(String[] args) { PApplet.main("com.test.threads.Main"); } }
Now we need to write few default methods of PApplet used for creating GUI window and drawing in it.
import processing.core.PApplet; public class Main extends PApplet { // Define main class for PApplet public static void main(String[] args) { PApplet.main("com.test.threads.Main"); } // Set window size and enable 2D acceleration public void settings() { size(600, 400, P2D); } // Setup the environment public void setup() { settings(); frameRate(30); } // Loop method that is drawing pixels in the window public void draw() { background(140, 70, 260); } }
If you run the program, GUI window should popup with background color that we have set with background function.
In the future I will do some projects in which we will use Processing to simulate movement of mathematical model since Processing animations are more fun and prettier then simulations from Wolfram Mathematica or Matlab. Of course, those two programs are really powerful and we are going to use them too. I created simple Snake Game using Processing to give you something interesting and motivate you to learn Java and Processing since it is a lot of fun.
0 notes
Text
Tutorial menggunakan CMD (Command Prompt)
Untuk sobat yang suka berkomputer ria pasti sudah mengenal yang namanya command promt dan At command, sebenarnya apa sih command promt dan at command itu. Command prompt adalah sebuah perintah berbasis DOS pada Windows OS (windows xp, windows 7) untuk memudahkan user berinteraksi dengan computer baik secara Online ataupun offline, untuk membantu atau sebagai alat bantu compiler dari berbagai baris perintah yang dimasukkan oleh user. Command prompt ini sering juga di salah gunakan oleh para cracker, dalam menjalankan aksinya. Sebagai contoh penggunaan command prompt adalah untuk mendeteksi virus, pemisahan virus, file induk virus hanya dengan perintah ATTRIB, dan lain sebagainya, Oleh sebaba itu untuk pengetahuan sobat yang suka berkomputer ria harus tahu sedikit banyak tentang perintah command prompt ini. Sebagai perintah dasar yang sering digunakan, dan sobat bisa mencobanya 1. DIRPerintah DIR digunakan untuk melihat isi folder/direktori bentuk umum DIR dapat diuraikan sebagai berikut:DIR (drive:) (path) (file name) (/P) (/N0 (/A) ((:) Atribut) (/O) ((c:shocked) (/S) (/B) (/L) (/C) (/H) Options yang dijalankan pada perintah DIR yaitu sebagai berikut:/P : Untuk menampilkan nama file perhalaman layar secara vertical./N : Untuk menampilkan nama file secara horizontal./A : Untuk menampilkan semua file,jika akan ditampilkan file yang akan disembunyikan(hidden) ditambahkan atribut +H/O : Untuk menampilkan file secara berurutanN :(menurut nama file)E :(menurut tipe file (extention))S :(menurut ukuran dari yang terkecil sampai ang terbesar)D :(meurut tanggal dan waktu modifikasi untuk mengembalikan instruksi)/S : Untuk menampilkan file dari root dari direktori sub/B : Untuk menampilkan file direktori baris demi baris/L : Untuk menampilkan file direktori dlm bentuk huruf kecil/C : Untuk menampilkan rasio pengoperasian misalnyaC:\> DIR untuk menampilkan root dalam direktoriC:\> DIR untuk menampilkan nama file bserta smua extonsinyaC:\> DIR/W untuk mnampilkan nama file secara menyebarC:\> DIR/A untuk mnampilkan nma file yang terdapat pada drive A 2. COPYPerintah copy digunakan untuk menyimpan file bentuk umum perintah ini adalah copy:D misalnyaA:\>COPY**C : Perintah untuk menyalin file standar A ke dalam Drive CA:\>COPY DATA : Perintah untuk menyalin file yang bernama data dan A ke CA:\>COPY E SURAT G: Perintah untuk menyalin file yang bernama surat dari drive E Ke GA:\>COPY?D**F : Perintah yang digunakan untuk menyalin file yang huruf ke Duanya D dari drive C ke drive F 3. DELDigunakan untuk menghapus file/subdirectory bentuk umum DEL:NAMA FILEA:\>DEL*.DOC : Perintah untuk menghapus semua file yang berakhiran doc.pd drive AA:\>DEL** : Perintah untu menghapus semua nama file di drive A dg smua akiran-Nya.A:\>DEL?G* : Perintah untuk menghapus nama-nama file yang huruf keduanya danBeserta semua extensinya. 4. RENDigunakan untuk menggantinama file.Bentuk umum REN : REN(:(nama file)(nama file baru) misalnya:C:\>RENA :surat DOC.DATA.DOCSemua file surat doc.pada drive A diganti menjadi DATA DOC 5. MOVEDigunakan untuk memindah file,perintah ini juga di pakai untuk menggantikan nama dirtektori dan nama file yang di pindahkan.Bentuk umum MOVE.MOVE[DRIVE][PATH][NAMA FILE][DRIVE][PATH][FILE NAMA] misalnya:C:\>MOVE C:\PENJUALAN.XLS.C:\DATAPindahkan file dengan nama penjualan xls.ke sub direktori DATA pada drive C 6. MD (MKDIR)Digunakan untuk membuat subdirektori,bentuk umum MD: MD d:[nama file]C:\> BACKUP :mmbuat sub dengan nama backup 7. CDDigunakan sebagai perint ah pindah direktori/mengubah direktoriC:\>CD\ENTERTAINT :pindah ke subdirektori ENTERTAINT 8. RDDigunakan untuk menghapus suatu direktori. Untuk menghapus sebuah direktori,posisi perintah penghapusan subdirektori tersebut harus berada diluar subdirektori yang akan dihapus.Subdirektori yang akan dihapus harus benar-benar kosong,setalah seluruh isi direktori tersebutdihapus terlebih dahulu dengan menggunakan perintah DEL** kemudian pindah kedirektori induk (root direktori) daan lakukan perintah CD.Untuk mengakhiri pekerjaan dalam Ms-DOS prompt kita dapat langsung mengetik EXIT setelah promt C:\> EXIT lalu ENTER. Sebenarnya untuk menampilkan perintah command prompt ini sobat juga bisa menampilkannya dengan cara masuk ke Start Klik kiri, masuk ke RUN, ketik CMD lalu ok terus muncul kota hitam dan disana anda tinggal ketik help terus enter a ADDUSERS : Tambah daftar pengguna untuk / dari file CSVARP : Address Resolution ProtocolAssoc : Ubah ekstensi file asosiasiASSOCIAT : Salah satu langkah asosiasi fileAttrib : Ubah atribut berkas b Bootcfg : Edit Windows boot settingsBROWSTAT : Dapatkan domain, info browser dan PDC c CACLS : Ubah file permissionsCALL : Panggil satu program batch yang lainCD : Mengganti Directory – pindah ke Folder tertentuChange : Ganti Terminal Server Session propertiesCHKDSK : Check Disk – memeriksa dan memperbaiki masalah diskCHKNTFS : Periksa sistem file NTFSCHOICE : Menerima input keyboard ke sebuah file batchCIPHER : Encrypt atau Decrypt file / folderCleanMgr : Ototmatis membersihkan Temperatur file, recycle binCLEARMEM : Hapus kebocoran memoriCLIP : Salin STDIN ke Windows clipboard.CLS : Menghapus layar (Clear The Screen)CLUSTER : Windows ClusteringCMD : Start a new CMD shellCOLOR : Mengubah warna dari jendela CMDCOMP : Membandingkan isi dari dua file atau set fileCOMPACT : Compress file atau folder pada partisi NTFSCompress : Compress tunggal file pada partisi NTFSCON2PRT : Menghubungkan atau memutuskan sambungan dengan PrinterCONVERT : Konversi FAT ke drive NTFSCOPY : Menyalin satu atau lebih file ke lokasi lainCSCcmd : clien-side caching (Offline Files)CSVDE : Impor atau Ekspor Active Directory data d DATE : Display atau mengatur tanggalDefrag : Defragment hard driveDEL : Menghapus satu atau lebih fileDELPROF : Hapus profil pengguna NTDELTREE : Menghapus folder dan semua subfolderDevCon : Device Manager Command Line UtilityDIR : Menampilkan daftar file dan folderDIRUSE : Tampilkan penggunaan diskDISKCOMP : Bandingkan isi dua floppy diskDiskcopy : Salin isi dari satu disket ke yang lainDISKPART : Disk AdministrasiDNSSTAT : DNS StatistikDOSKEY : Edit baris perintah, ingat perintah, dan membuat macroDSADD : Tambah User (komputer, group ..) ke direktori aktifDSQUERY : Daftar item dalam direktori aktifDSMOD : Ubah user (computer, group ..) di direktori aktifDSRM : Hapus item dari Active Directory e ECHO : Menampilkan pesan di layerENDLOCAL : Akhir localisation perubahan lingkungan dalam file batchERASE : Menghapus satu atau lebih fileEVENTCREATE : Tambahkan pesan ke Windows event logEXIT : Keluar dari skrip arus / rutin dan menetapkan errorlevelEXPAND : uncompress fileEkstrak : uncompress file CAB f FC : Bandingkan dua fileFIND : Mencari string teks dalam sebuah fileFINDSTR : Cari string dalam fileFOR / F : pengulangan perintah terhadap satu set fileFOR / F : pengulangan perintah terhadap hasil perintah lainFOR : pengulangan perintah terhadap semua options Files, Directory, ListFORFILES : Proses Batch beberapa fileFORMAT : Format diskFREEDISK : Periksa free disk space/disk yang tersisa (dalam bytes)FSUTIL : File dan Volume utilitasFTP : File Transfer ProtocolFTYPE : Tampilkan atau memodifikasi jenis file yang digunakan dalam asosiasi ekstensi file g GLOBAL : Display keanggotaan kelompok globalGOTO : Direct a batch program untuk melompat ke baris berlabelGPUPDATE : Update pengaturan Kebijakan Grup h HELP : Online Help i ICACLS : Ubah file dan folder permissionsIF : kondisional melakukan perintahIFMEMBER : Apakah pengguna saat ini dalam sebuah NT WorkgroupIPCONFIG : Configure IP k KILL : Remove program dari memori l LABEL : Edit disk labelLOCAL : Display keanggotaan kelompok-kelompok localLOGEVENT : Menulis teks ke NT event viewerLogoff : user log offLOGTIME : log tanggal dan waktu dalam file m MAPISEND : Kirim email dari baris perintahMBSAcli : Baseline Security AnalyzerMEM : Display penggunaan memoriMD : Buat folder baruMKLINK : Buat link simbolik (linkd)MODE : Mengkonfigurasi perangkat systemMORE : Display output, satu layar pada satu waktuMOUNTVOL : mengelola volume mount pointMOVE : Pindahkan file dari satu folder ke yang lainMOVEUSER : Pindahkan pengguna dari satu domain ke domain lainnyaMSG : mengirim pesan atau messageMSIEXEC : Microsoft Windows InstallerMSINFO : Windows NT diagnosticsMSTSC : Terminal Server Connection (Remote Desktop Protocol)MUNGE : Cari dan Ganti teks dalam file (s)MV : Copy in-menggunakan file n NET : Kelola sumber daya jaringanNETDOM : Domain ManagerNetsh : Configure Network Interfaces, Windows Firewall & Remote aksesNETSVC : Command-line Service ControllerNBTSTAT : Tampilkan statistik jaringan (NetBIOS over TCP / IP)NETSTAT : Display networking statistics (TCP / IP)NOW : Tampilan saat ini Tanggal dan WaktuNSLOOKUP : Nama server lookupNTBACKUP : Backup folder ke tapeNTRIGHTS : Edit hak user account p PATH : Menampilkan atau menetapkan path pencarian untuk file executablePATHPING : jejak jalur jaringan ditambah paket latensi dan kerugianPAUSE : memenjarakan(suspend) pengolahan file batch dan menampilkan pesanperms : Tampilkan izin untuk penggunaPERFMON : Kinerja MonitorPING : Menguji koneksi jaringanPOPD : Mengembalikan nilai sebelumnya dari direktori sekarang yang disimpan oleh PUSHDPORTQRY : Tampilan status ports dan servicesPowercfg : Mengkonfigurasi pengaturan dayaPRINT : Mencetak file teksPRNCNFG : Display, mengkonfigurasi atau mengubah nama printerPRNMNGR : Tambah, menghapus, daftar printer menetapkan printer defaultPROMPT : Mengubah command promptPsExec : Proses Execute jarak jauhPsFile : menampilkan file dibuka dari jarak jauh (remote)PsGetSid : Menampilkan SID sebuah komputer atau penggunaPsInfo : Daftar informasi tentang systemPsKill : proses mematikan berdasarkan nama atau ID prosesPsList : Daftar informasi rinci tentang proses-prosesPsLoggedOn : siapa saja yang log on (lokal atau melalui resource sharing)PsLogList : catatan kejadian logPsPasswd : Ubah sandi accountPsService : Melihat dan mengatur layananPsShutdown : Shutdown atau reboot computerPsSuspend : proses SuspendPUSHD : Simpan dan kemudian mengubah direktori sekarang q QGREP : Cari file(s) untuk baris yang cocok dengan pola tertentu r RASDIAL : Mengelola koneksi RASRASPHONE : Mengelola koneksi RASRecover : perbaikan file yang rusak dari disk yang rusakREG : Registry = Read, Set, Export, Hapus kunci dan nilai-nilaiREGEDIT : Impor atau ekspor pengaturan registryRegsvr32 : Register atau unregister sebuah DLLREGINI : Ubah Registry PermissionsREM : Record comments (komentar) di sebuah file batchREN : Mengubah nama file atau fileREPLACE : Ganti atau memperbarui satu file dengan yang lainRD : Hapus folder (s)RMTSHARE : Share folder atau printerRobocopy : Copy File dan Folder secara sempurnaRUTE : Memanipulasi tabel routing jaringanRUNAS : Jalankan program di bawah account pengguna yang berbedaRUNDLL32 : Jalankan perintah DLL (add / remove print connections) s SC : Control LayananSCHTASKS : Jadwal perintah untuk dijalankan pada waktu tertentuSCLIST : Tampilkan Layanan NTSET : Display, set, atau menghapus variabel environmentSETLOCAL : Pengendalian environment visibilitas variableSETX : Set variabel environment secara permanentSFC : Pemeriksa Berkas SistemSHARE : Daftar atau mengedit file share atau share printSHIFT : Shift posisi digantikan parameter dalam sebuah file batchSHORTCUT : jendela Buat shortcut (. LNK file)SHOWGRPS : Daftar NT Workgroups seorang pengguna telah bergabungSHOWMBRS : Daftar Pengguna yang menjadi anggota dari sebuah WorkgroupSHUTDOWN : Shutdown computerSLEEP : Tunggu untuk x detikSLMGR : Software Licensing Management (Vista/2008)SOON : Jadwal perintah untuk menjalankan dalam waktu dekatSORT : Sort inputSTART : memulai sebuah program atau perintah dalam jendela terpisahSU : Switch UserSUBINACL : Edit file dan folder Permissions, Kepemilikan dan DomainSUBST : Associate jalan dengan huruf driveSysteminfo : Daftar konfigurasi system t TASKLIST : Daftar menjalankan aplikasi dan servicesTASKKILL : Hapus proses yang berjalan dari memoriTIME : Menampilkan atau mengatur waktu systemTIMEOUT : penundaan pemrosesan dari sebuah batch fileTITLE : Mengatur judul window untuk sesi cmd.exeTLIST : daftar tugas dengan path lengkapTOUCH : mengganti file timestampsTracert : Trace route ke sebuah remote hostTREE : tampilan grafis struktur folderTYPE : Menampilkan isi dari file teks u USRSTAT : Daftar domain nama pengguna dan terakhir login v VER : Tampilkan versi informasiVERIFY : Pastikan bahwa file sudah disimpanVOL : Menampilkan sebuah label disk w WHERE : Menempatkan dan menampilkan file dalam sebuah pohon direktoriWHOAMI : Output UserName saat ini dan manajemen domainWINDIFF : Bandingkan isi dua file atau set fileWINMSD : Sistem Windows diagnosticWINMSDP : Sistem Windows diagnostik IIWMIC : Perintah WMI x XCACLS : Ubah file dan folder permissionsXCOPY : Menyalin file dan folder
Sumber : http://ilmuti.com
0 notes
Text
dịch vụ sửa iphone huyện cần giờ - Gọi nhanh các lệnh Windows Explorer
Một mẹo nhỏ khá thú vị mà chắc hẳn bạn chưa biết, đó là bạn có thể chạy các lệnh trực tiếp ngay trên thanh địa chỉ bên trong Windows Explorer. dịch vụ sửa iphone huyện cần giờ
Việc này hoàn toàn có thể áp dụng được một cách rất dễ dàng và không mất nhiều thời gian. Ví dụ như khi bạn đang cần mở nhanh hộp thoại Command Prompt (cmd.exe), thay vì bạn phải thao tác gọi nhanh hộp thoại Run bằng phím tắt Windows + R (hay Start > Run) thì bạn có thể gõ ngay 'cmd' ngay trên thanh địa chỉ của Windows Explorer và Enter. Lập tức hộp thoại Command Prompt sẽ xuất hiện ngay tức thì.
dịch vụ sửa iphone huyện cần giờ
dịch vụ sửa iphone huyện cần giờ
Ngoài ra, nếu bạn đang mở Windows Explorer với đường dẫn xác định, bạn có thể gọi nhanh tập tin đang nằm trong nó, vì dụ bạn cần mở nhanh tập tin 'VNReview.txt' bằng Notepad nằm ngay trên Desktop và hiện tại Windows Explorer cũng đang mở đường dẫn Desktop thì bạn chỉ cần gõ như hình dịch vụ sửa iphone huyện cần giờ
…sau đó nhấn Enter, lập tức tập tin VNReview.txt sẽ được mở nhanh bằng Notepad như lệnh bạn đã đưa ra. Thật đơn giản phải không?
Ngoài ra, bạn cũng có thể sử dụng các lệnh trực tiếp khác từ thanh địa chỉ của Windows Explorer. Ví dụ muốn biết tất cả các tập tin và thư mục hiện tại nằm trong Windows Explorer bạn có thể gõ lệnh ‘cmd /k dir' và nhấn Enter, thật ngớ ngẩn phải không? Nhưng hoàn toàn có thể thực hiện lệnh này ngay trên thanh địa chỉ của Windows Explorer đó!
Rất đơn giản và nhanh chóng phải không?
dịch vụ sửa iphone huyện cần giờ
Trung tâm dịch vụ sửa chữa Gia Phát .Địa chỉ: 153 Trần Văn Đang, Phường 11, Quận 3, Tp HCMSĐT: 0933 418 610
http://sualaptop12h.com
https://www.facebook.com/sualaptopgiare/
Có thể bạn muốn xem: dịch vụ sửa iphone giá rẻ hcm, dịch vụ sửa iphone giá rẻ, dịch vụ sửa iphone uy tín hcm, dịch vụ sửa iphone tp hcm, dịch vụ sửa iphone quận 1, dịch vụ sửa iphone hcm, dịch vụ sửa iphone quận tp hcm, dịch vụ sửa iphone quận hồ chí minh, dịch vụ sửa iphone quận 2, dịch vụ sửa iphone quận 3, dịch vụ sửa iphone quận 4, dịch vụ sửa iphone quận 5, dịch vụ sửa iphone quận 6, dịch vụ sửa iphone quận 7, dịch vụ sửa iphone quận 8, dịch vụ sửa iphone quận 9, dịch vụ sửa iphone quận 10, dịch vụ sửa iphone quận 11, dịch vụ sửa iphone quận 12, dịch vụ sửa iphone quận bình thạnh, dịch vụ sửa iphone quận tân phú, dịch vụ sửa iphone quận tân bình, dịch vụ sửa iphone quận bình tân, dịch vụ sửa iphone quận phú nhuận, dịch vụ sửa iphone quận thủ đức, dịch vụ sửa iphone huyện cần giờ, dịch vụ sửa iphone huyện hóc môn, dịch vụ sửa iphone huyện củ chi, dịch vụ sửa iphone huyện nhà bè, dịch vụ sửa iphone huyện bình chánh
0 notes
Photo

How do I launch a batch file in a Selenium WebDriver project?
Hi Friend,
When you want to create utilty to run batch file for your selenium tests, its always useful.
I am giving you example of creating utility in Java Language to run batch file.
Create batch file on your desktop and name it as abc.bat and write inside it echo "He is learning automation"
Now create Java main class
import java.io.IOException;
import java.io.OutputStream;
public class CMDUtilityToRunBatchFile {
public static void main(String args[]){
CMDUtilityToRunBatchFile testScript = new CMDUtilityToRunBatchFile();
execDOSCmd();
}
public static void execDOSCmd() {
try {
// Execute command
String command ="cmd /c start C:\Users\DreamBook\Desktop\abc.bat";
Process child = Runtime.getRuntime().exec(command);
// Get output stream to write from it
OutputStream out = child.getOutputStream();
out.write("cd C:/ /r/n".getBytes());
out.flush();
out.write("dir /r/n".getBytes());
out.close();
} catch (IOException e) {
}
}
}
Now run this Java file as “Java application” or call execDOSCmd() method from elsewhere. Even You can run your own batch script with this method.
**************************************************************************************
QACult Best Software Testing Courses in Chandigarh tricity.- We love to enhance your knowledge.
QACult is the premier institute catering to the requirements of experienced and fresh pass-out that gives leaders like you a new way to experience Quality engineering—while you work and giving you the flexibility to both advance your career.
Our faculty have 12+ years of industrial experience and have developed many automation testing frameworks in java using TestNG or BDD (cucumber) methodology. We expertise in developing automation testing frameworks in java, python, javascript, php, ruby(WATIR-webdriver & Capybara) and Appium.
please subscribe our channel for more such updates:
https://www.youtube.com/channel/UC0xat537YITJbN_9GSMUALA
And visit our website: www.qacult.com for various blogs and Upcoming Events.
0 notes