#bulk geo ip locator
Explore tagged Tumblr posts
Link
Bulk GEO IP Locator - Find Geolocation Data for Multiple IPs
#ip checker#ip locator#geo ip#bulk IP addresses#Bulk GEO IP Locator#geolocation data#multiple IPs#IP lookup#geolocation tool#IP geolocation#IP address location
0 notes
Video
SimpliTools - Bulk GEO IP Locator by SimpliTools Via Flickr: Bulk GEO IP Locator is one of the 160+ tools, available at SimpliTools.
0 notes
Text
Proxies for Sale: Enhancing Online Privacy and Security
Proxies for Sale: Enhancing Online Privacy and Security
In the digital age, where online privacy and security are paramount concerns, proxies have emerged as essential tools for safeguarding personal information and enhancing internet security. As the demand for these services grows, so does the market for proxies for sale. This article explores the benefits of purchasing proxies, the types available, and how they can improve your online experience.To get more news about proxies for sale, you can visit pyproxy.com official website.
Why Purchase Proxies? Proxies act as intermediaries between a user’s device and the internet, masking the user’s IP address and routing their internet traffic through a different server. This process offers several significant benefits:
Enhanced Privacy and Anonymity
By masking your IP address, proxies make it difficult for websites and online services to track your online activities. This anonymity protects your personal information and browsing habits from prying eyes, ensuring a more private internet experience.
Improved Security
Proxies can filter out malicious content and websites, providing an added layer of security against online threats such as malware, phishing attacks, and hacking attempts. This is particularly important for businesses that handle sensitive data.
Access to Geo-Restricted Content
Many websites and online services restrict access based on geographic location. Proxies enable you to bypass these restrictions by routing your traffic through servers in different regions, allowing you to access content that may be unavailable in your country.
Better Performance and Load Balancing
Proxies can cache frequently accessed content, reducing load times and improving overall internet performance. They can also distribute network traffic evenly, preventing any single server from becoming overwhelmed and ensuring a smoother browsing experience.
Types of Proxies for Sale When purchasing proxies, it’s important to choose the type that best suits your needs. The most common types of proxies for sale include:
Dedicated Proxies
Dedicated proxies are assigned exclusively to a single user or organization. They offer the highest level of performance, privacy, and security, making them ideal for activities that require reliable and anonymous internet access, such as online gaming, streaming, and secure business communications.
Shared Proxies
Shared proxies are used by multiple users simultaneously. While they are more cost-effective than dedicated proxies, they may offer slightly lower performance and security due to the shared nature of the server. Shared proxies are suitable for general browsing and accessing geo-restricted content.
Residential Proxies
Residential proxies use IP addresses provided by internet service providers (ISPs), making them appear as regular residential connections. These proxies are highly effective for tasks that require a high level of anonymity, such as web scraping and bypassing strict geo-restrictions.
Data Center Proxies
Data center proxies are hosted in data centers and offer high-speed connections and scalability. They are well-suited for bulk tasks such as web scraping, automated testing, and managing multiple social media accounts.
Choosing a Reputable Proxy Provider When purchasing proxies, it’s essential to choose a reputable provider that offers reliable and secure services. Look for providers that offer transparent pricing, customer support, and a variety of proxy options. Additionally, read reviews and testimonials from other users to ensure the provider has a good reputation for quality and reliability.
Conclusion Proxies for sale provide valuable benefits for enhancing online privacy, security, and access to content. Whether you need dedicated proxies for secure business communications, shared proxies for general browsing, or residential proxies for high anonymity tasks, there are options available to suit your needs. By purchasing proxies from a reputable provider, you can enjoy a safer and more efficient online experience, protecting your personal information and unlocking access to a world of content. Embrace the advantages of proxies and take control of your online privacy and security.
0 notes
Text
ISP Proxies for Sale: Enhance Your Online Experience with Proxiware
In the rapidly evolving digital world, privacy, speed, and secure internet access have become vital for businesses and individuals alike. One solution that provides an edge in this arena is the use of ISP proxies. Proxies can help bypass geographical restrictions, ensure anonymity, and allow smooth data scraping, among many other applications. ISP Proxies for Sale If you're on the lookout for ISP proxies for sale, look no further than Proxiware.
What Are ISP Proxies?
An ISP proxy, or Internet Service Provider proxy, is an intermediary server assigned to users by an actual internet service provider. These proxies provide the best of both worlds: the anonymity of a proxy server with the legitimacy of a residential IP address. Because ISP proxies are tied to a physical location but offered through data centers, they are faster than traditional residential proxies and less detectable than data center proxies.
Why Use ISP Proxies?
Enhanced Speed and Stability: ISP proxies offer faster connection speeds compared to traditional residential proxies, making them ideal for tasks that require real-time access, like gaming, streaming, or bulk data scraping.
Lower Risk of Detection: Many websites can block or flag data center proxies due to high volumes of requests coming from non-residential IPs. ISP proxies blend into the internet like regular user traffic, reducing the chances of getting blocked or flagged.
Better for E-commerce: ISP proxies are particularly useful in industries like e-commerce, where users might need to monitor competitor pricing or gather product information without being flagged for bot-like behavior.
SEO and Marketing Campaigns: Whether you're managing multiple social media accounts, running ad campaigns, or conducting SEO audits, ISP proxies ensure your actions aren't limited by geographical restrictions or IP bans.
Anonymous Browsing: For users who prioritize privacy, ISP proxies can mask your real IP address, making it harder for websites and third parties to track your online activities.
Why Choose Proxiware for ISP Proxies?
Proxiware offers high-quality ISP proxies for sale that cater to various online needs. Here’s why Proxiware stands out:
Premium Speed: With Proxiware's ISP proxies, you get a lightning-fast connection without the usual latency issues found in residential proxies.
Affordable Pricing: Proxiware provides competitive pricing plans, ensuring businesses and individuals alike can benefit from reliable ISP proxies without breaking the bank.
Multiple Locations: Gain access to proxies based in various regions, allowing you to bypass geo-restrictions or manage campaigns in different countries.
Excellent Customer Support: Proxiware offers round-the-clock support to help you navigate any issues, ensuring seamless proxy use.
Conclusion
Whether you're a business aiming to optimize online operations or an individual seeking more privacy online, ISP Proxies for Sale investing in ISP proxies for sale is a smart choice. With Proxiware, you’ll enjoy fast, secure, and anonymous browsing that meets your unique needs.
Explore Proxiware’s range of ISP proxies today at proxiware.com and take control of your online experience!
0 notes
Text
What are the application scenarios of SOCKS5 proxy?
SOCKS5 proxy, as an advanced proxy protocol, has stronger privacy protection and network performance optimization capabilities, so it is widely used in various scenarios. Next, we will introduce the common application scenarios of SOCKS5 proxy.

1. Data Scraping and Web Crawling
For users engaged in data crawling and web crawling, SOCKS5 proxy has excellent performance advantages. It is able to bypass IP blocking of websites and simulate multiple IP accesses to the target site, thus preventing crawlers from being blocked due to frequent visits. In addition, SOCKS5 supports a variety of protocols (TCP/UDP), so it can handle the diverse needs of data flow and network requests, ensuring smoother data crawling tasks.
2. Enhanced Network Privacy
The SOCKS5 proxy is able to hide the user's real IP address and forward network requests through a proxy server, allowing users to access the network with a higher degree of anonymity. This is especially important for users who want to protect their privacy and avoid being tracked. Especially when transferring sensitive data or accessing geo-restricted websites, the SOCKS5 proxy can provide users with additional privacy protection.
3. Bypassing geo-restrictions
Many websites, content and services have restrictions on access to certain countries or regions, such as streaming services (Netflix, Hulu, etc.) or game servers. By using a SOCKS5 proxy, users can select IP addresses from other countries or regions, thus bypassing these geographical restrictions and accessing otherwise unavailable content or services, and enjoying a globalized online experience.
4. Online Gaming
For online gamers, especially when participating in multiplayer games on cross-region or global servers, network latency (ping) is a key factor affecting the gaming experience, and the SOCKS5 proxy can help gamers reduce latency and optimize connection speeds, especially when using games with servers located overseas, the SOCKS5 proxy can provide a smoother gaming experience.
5. File Transfer
The SOCKS5 proxy performs particularly well with file transfer protocols (such as FTP, BitTorrent, etc.). Because it supports the UDP protocol, this enables the SOCKS5 proxy to provide faster transfer speeds and more stable connections when dealing with large file transfers or P2P connections. Especially in peer-to-peer networks, the SOCKS5 proxy allows users to avoid attacks due to IP exposure.
6. Enterprise telecommuting
With the popularity of remote office, more and more enterprises adopt SOCKS5 proxy to provide secure and stable remote access for their employees. With SOCKS5 proxy, employees can access the company's internal network and applications in a secure environment, ensuring the safety of company data and communications. In addition, the fast connectivity and flexibility of SOCKS5 proxy enhances the efficiency of remote work.
7. Download Acceleration
Using SOCKS5 proxy can increase the speed of downloading large files or bulk data, especially when multiple servers are involved. Its ability to handle a large number of concurrent requests at the same time improves the efficiency of downloads through distributed connectivity, making it particularly suitable for users who need to obtain files from multiple data sources around the world.
With its support for multiple protocols, strong privacy protection, and superior network performance, the SOCKS5 proxy is an all-in-one tool for enhancing network experience and efficiency. Whether in scenarios such as data capture, network privacy, bypassing geographical restrictions, online gaming, file transfer, remote office or download acceleration, the SOCKS5 proxy has demonstrated its strong practical value.
0 notes
Text
does the government track vpn users
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does the government track vpn users
VPN encryption technology
VPN encryption technology plays a crucial role in ensuring the security and privacy of online activities. VPN, which stands for Virtual Private Network, creates a secure and encrypted connection between a user's device and the internet. This encryption technology works by converting data into a code that is unreadable without the appropriate decryption key.
One of the key benefits of VPN encryption technology is its ability to protect sensitive information from cyber threats such as hackers, identity thieves, and government surveillance. By encrypting data, VPNs make it nearly impossible for unauthorized parties to intercept and decipher the information being transmitted. This is especially important when using public Wi-Fi networks, where personal data is more vulnerable to security breaches.
Furthermore, VPN encryption technology allows users to bypass censorship and geo-blocks by masking their IP address and location. This enables individuals to access restricted content and websites, as well as enhance their online anonymity and privacy.
There are several encryption protocols used in VPN technology, including OpenVPN, L2TP/IPsec, SSTP, and IKEv2. These protocols offer varying levels of security and performance, giving users the flexibility to choose the one that best suits their needs.
In conclusion, VPN encryption technology is a powerful tool for safeguarding online activities and maintaining privacy in an increasingly digital world. By utilizing encryption protocols, users can enjoy a secure and unrestricted internet experience while protecting their sensitive information from prying eyes.
Government surveillance measures
Title: Understanding Government Surveillance Measures: Balancing Security and Privacy
Government surveillance measures have become a topic of intense debate, particularly in the digital age where technology enables unprecedented access to personal information. While these measures are often implemented with the intention of enhancing national security and preventing threats, they also raise significant concerns about privacy rights and civil liberties.
One of the most contentious aspects of government surveillance is the collection of mass data through programs such as mass surveillance programs, data mining, and metadata analysis. These practices involve the bulk collection of communications data, including emails, phone calls, and internet browsing history, often without individualized suspicion. While proponents argue that such measures are necessary to identify and thwart potential threats, critics contend that they constitute a gross violation of privacy rights and can lead to abuses of power.
Another area of concern is the use of surveillance technologies, including CCTV cameras, facial recognition systems, and biometric databases. While these technologies can be valuable tools for law enforcement in combating crime and terrorism, they also raise significant ethical and privacy concerns. For example, facial recognition technology has been criticized for its potential to infringe on individuals' rights to anonymity and freedom of movement, as well as its propensity for racial and gender bias.
In response to these concerns, there have been calls for greater transparency and oversight of government surveillance programs. Many civil liberties advocates argue that there needs to be more robust legal frameworks in place to ensure that surveillance measures are subject to judicial review and oversight. Additionally, there have been efforts to enhance privacy protections through measures such as encryption and anonymization techniques.
Ultimately, the debate surrounding government surveillance measures reflects a delicate balance between security and privacy. While it is essential to safeguard national security interests, it is equally important to uphold individual rights and freedoms. Achieving this balance requires thoughtful consideration of the ethical, legal, and societal implications of surveillance practices, as well as ongoing dialogue and engagement between policymakers, technology experts, and civil society stakeholders.
Internet privacy laws
Title: Navigating the Maze: Understanding Internet Privacy Laws
In the digital age, where every click and keystroke leaves a trail, internet privacy has become a paramount concern. To safeguard users' personal information from exploitation and misuse, governments around the world have enacted internet privacy laws. These regulations aim to strike a delicate balance between protecting individual privacy rights and enabling legitimate data use for business and innovation.
One of the most significant pieces of legislation in this domain is the General Data Protection Regulation (GDPR), implemented by the European Union (EU) in 2018. GDPR empowers individuals with greater control over their personal data, requiring businesses to obtain explicit consent for data collection and processing. It also mandates stringent measures for data security and imposes hefty fines for non-compliance.
Similarly, the California Consumer Privacy Act (CCPA), enacted in 2020, grants California residents enhanced rights regarding their personal information. Under CCPA, consumers can demand to know what data is being collected about them and have the right to opt-out of the sale of their data to third parties.
Beyond these, various countries have crafted their own internet privacy laws tailored to their unique legal frameworks and cultural contexts. For instance, Brazil's Lei Geral de Proteção de Dados (LGPD) and India's Personal Data Protection Bill (PDPB) aim to regulate data processing activities within their jurisdictions.
Despite these advancements, challenges persist in ensuring comprehensive internet privacy protection. The rapid pace of technological innovation often outpaces regulatory efforts, leaving gaps in coverage. Moreover, the global nature of the internet raises jurisdictional issues, making enforcement complex across borders.
As technology continues to evolve, so too must internet privacy laws. Striking a balance between innovation and protection remains an ongoing challenge, requiring collaboration between governments, businesses, and civil society to uphold the fundamental right to privacy in the digital era.
Online anonymity tools
Title: Exploring the Benefits of Online Anonymity Tools
In today's digital age, concerns about online privacy and security have become increasingly prevalent. With the rise of cyber threats and data breaches, individuals are seeking ways to protect their online identities and activities. One effective solution that has gained popularity is the use of online anonymity tools.
Online anonymity tools, such as virtual private networks (VPNs), Tor browser, and encrypted messaging apps, offer users a secure way to browse the internet and communicate without revealing their true identities or locations. These tools work by encrypting internet traffic and masking IP addresses, making it difficult for third parties to track users' online activities.
One of the primary benefits of using online anonymity tools is enhanced privacy protection. By hiding their IP addresses, users can prevent websites, advertisers, and even government agencies from tracking their online behavior. This not only protects users from targeted advertising and unwanted surveillance but also helps safeguard sensitive information such as financial data and personal messages.
Moreover, online anonymity tools enable users to bypass censorship and access restricted content. In countries where internet freedom is limited, tools like VPNs and Tor browser allow individuals to circumvent government-imposed restrictions and access blocked websites and social media platforms.
Additionally, these tools can help prevent identity theft and fraud by keeping users' personal information secure. By encrypting data transmissions and anonymizing online activities, anonymity tools make it significantly harder for hackers and cybercriminals to intercept sensitive information or steal login credentials.
In conclusion, online anonymity tools play a crucial role in safeguarding individuals' privacy and security in an increasingly connected world. By utilizing these tools, users can browse the internet with confidence, knowing that their online activities are protected from prying eyes and potential threats.
User data protection laws
User data protection laws are essential in today's digital age to safeguard personal information and ensure privacy for individuals online. These laws govern how organizations collect, store, and utilize user data to prevent its misuse and unauthorized access.
One prominent example of user data protection laws is the General Data Protection Regulation (GDPR) implemented by the European Union. The GDPR sets strict guidelines for businesses operating within the EU or handling the personal data of EU citizens. It requires organizations to obtain explicit consent before collecting user data, disclose the purposes for which data is being collected, and implement robust security measures to safeguard this information.
In the United States, the California Consumer Privacy Act (CCPA) is another significant legislation aimed at protecting user data. The CCPA grants California residents the right to know what personal information is being collected about them, the right to opt-out of the sale of their data, and the right to request the deletion of their information from company databases.
User data protection laws are crucial for maintaining trust between consumers and businesses. By ensuring that personal information is handled responsibly and securely, these laws help prevent data breaches, identity theft, and other forms of cybercrime. Organizations that fail to comply with data protection laws may face severe penalties, including hefty fines and damage to their reputation.
In conclusion, user data protection laws play a vital role in safeguarding individuals' privacy in the digital landscape. It is crucial for businesses to uphold these laws and prioritize user data security to build trust with their customers and avoid legal consequences.
0 notes
Text
Navigating the Complex World of Proxy Providers: A Comprehensive Guide to Making the Right Choice - Technology Org
New Post has been published on https://thedigitalinsider.com/navigating-the-complex-world-of-proxy-providers-a-comprehensive-guide-to-making-the-right-choice-technology-org/
Navigating the Complex World of Proxy Providers: A Comprehensive Guide to Making the Right Choice - Technology Org
In an era where digital presence is paramount, the role of proxies as a pivotal link between users and the wider internet is increasingly significant. Serving as intermediaries, they not only facilitate anonymity and enhanced security but also enable users to bypass geographical limitations.
The challenge, however, lies in navigating the vast sea of proxy providers available today. This decision is far from trivial, as the right choice can substantially benefit both individuals and businesses in their online endeavors.
This comprehensive guide delves into the critical aspects of selecting infatica proxy services that align perfectly with your unique online needs.
Understanding Different Types of Proxies
The proxy landscape is diverse, with each type tailored to specific requirements:
Residential Proxies: These proxies are associated with real residential addresses, drastically reducing the likelihood of being blocked. They are the go-to choice for tasks that necessitate a high level of authenticity.
Datacenter Proxies: Housed in data centers, these proxies are lauded for their impressive speed and reliability. Although they offer less anonymity compared to residential proxies, they are ideal for high-volume operations.
Mobile Proxies: Leveraging IP addresses assigned to mobile devices, these proxies offer the pinnacle of anonymity and are perfect for activities that require mimicking an average mobile user’s behavior.
Understanding the distinct characteristics of each proxy type is crucial for making an informed choice tailored to your specific use case.
Key Factors to Consider When Choosing a Proxy Provider
Selecting a proxy provider involves a thorough evaluation of several essential factors:
Reliability and Uptime: Opt for a provider with a track record of high uptime, ensuring uninterrupted service.
Speed and Performance: A proxy should offer rapid connectivity to facilitate efficient online activities.
Anonymity and Security: Prioritize providers that employ robust security protocols to safeguard your data while maintaining your anonymity.
Geographical Location Options: Providers offering a broad spectrum of locations afford more flexibility and cater to targeted geo-specific needs.
Scalability and Flexibility: Your chosen provider should be capable of adapting to your evolving requirements, offering scalable solutions as your needs grow.
Evaluating the Cost vs. Benefit
Understanding the pricing of proxy services is not just about the bottom line; it’s about discerning the value you receive for your investment. Proxy providers may offer a range of pricing structures, including pay-as-you-go, monthly subscriptions, or bulk purchase discounts.
It’s crucial to align the cost with your usage patterns: a small-scale user might benefit from a pay-as-you-go plan, while large businesses could find subscriptions more economical.
However, cost extends beyond just the price tag. Consider factors like the longevity of the service, the quality of the IP addresses (whether they are prone to getting blocked), and the breadth of available features. Also, be alert to hidden fees or costs associated with overuse, which can inflate the final price unexpectedly.
An informed decision weighs the initial cost against the long-term benefits, ensuring that you’re not just choosing the cheapest option, but the most cost-effective one.
User Experience and Support
User experience in proxy services encompasses ease of setup, the simplicity of managing the proxies, and the intuitiveness of the interface. A provider with a well-designed user interface reduces the learning curve and enhances productivity. Additionally, consider the quality of customer support provided.
Efficient customer service is crucial, especially when dealing with time-sensitive projects. Look for providers who offer multiple support channels such as email, chat, and phone, and check their responsiveness and problem-solving ability.
Community resources like forums, user guides, and FAQs can also be invaluable for troubleshooting and advice, adding to the overall user experience.
Legal and Compliance Considerations
The legal aspect of using proxy services is not to be overlooked. Ensure that your proxy provider adheres to the legal standards in your jurisdiction and maintains a high level of compliance with international data protection laws like GDPR or CCPA.
This compliance protects not just the provider, but also you as a user, from potential legal issues. Additionally, it’s important to understand the provider’s policy regarding data logging and retention. A commitment to user privacy and a clear, transparent policy on data handling can be crucial factors in your decision-making process.
Future-Proofing: Looking at Emerging Trends
In a rapidly evolving digital landscape, choosing a proxy provider that not only meets current needs but is also prepared for future developments is essential.
Emerging trends like the increasing use of machine learning algorithms for IP rotation management, the growing importance of IPv6 proxies, and enhanced focus on mobile proxies are reshaping the proxy landscape.
A provider that is forward-thinking and invests in the latest technologies can ensure that your proxy services remain relevant and effective in the face of changing digital trends.
Making the Decision: A Step-by-Step Guide
To arrive at an informed decision, consider the following steps:
Define Your Requirements: Determine your specific needs in terms of speed, security, anonymity, and geographical preferences.
Research and Compare Providers: Conduct thorough research on various providers, comparing their offerings against your criteria.
Assess Reliability and Performance: Seek providers with proven records of high uptime and performance.
Analyze Costs: Understand the different pricing structures and evaluate them in relation to the benefits provided.
User Interface and Support: Ensure the provider offers an easily navigable platform and responsive customer support.
Verify Legal Compliance: Confirm that the provider adheres to all relevant laws and regulations.
Gather User Feedback: Use reviews and case studies to gauge real-world effectiveness.
Consider Future Trends: Opt for providers who demonstrate adaptability and innovation.
Trial the Service: If possible, utilize a trial period to experience the proxy service firsthand.
Conclusion
Selecting the right proxy provider is a nuanced and multifaceted process. It requires a deep dive into both your specific requirements and the offerings of various providers.
This guide aims to arm you with the necessary knowledge to make an informed, strategic decision, ensuring that your chosen proxy service not only meets your current needs but is also equipped to adapt to future challenges in the dynamic digital landscape.
#Advice#Algorithms#arm#Behavior#ccpa#challenge#Community#compliance#comprehensive#connectivity#customer service#data#Data Centers#data protection#Developments#devices#email#Features#Future#gdpr#Innovation#Internet#investment#issues#it#Landscape#learning#Legal#LESS#Link
0 notes
Text
7 Must-Have Apps for Your Shopify Store

Over a decade of experience in developing plugins, apps, and extensions, we always tend to find solutions for our customers, especially eCommerce business.
Ever-changing market trends keep store owners thinking about how they are going to integrate new changes in their store.
The development of individual features for your store is expensive and time-consuming.
To avoid this long, expensive route, we developed apps that offer exact features you are looking for at a very affordable price.
The apps we are going to discuss are made keeping in mind the high customer demand. Let’s start.
1. Delivery Dates and Shipping Rates
One of the most loved apps by Shopify store owners is Delivery Date and Shipping Rates. The app comes with multiple delivery options and date/time selections.
Our app gives you three different types of delivery methods:
1. Standard Shipping
2. Store Pickup
3. Local Delivery
Whether you use one, two, or all three types of delivery, we offer delivery date and time pickers for all three.
The delivery calendar is totally customizable. From restricting the preparation time to restricting the order number, everything is covered.
If you don’t deliver on some days, configure the non-working days, and the app will block those days to restrict users from choosing those. Thus, enjoy your vacation with no pending orders.
Every business has a certain limit of orders that they can fulfill in a day. So, simply set how many orders you would want in a day, and once the counter hits, the date will be restricted, and no other customer can choose that day for delivery.
The next step is shipping rates. Whether you have a fixed shipping rate or a dynamic, you can configure both these on our app. Based on delivery location and delivery date, customize different shipping rates for your customer.
Feature Highlights:
Multiple delivery options: Store Pickup, Local Delivery, and Shipping
Delivery date and time picker with rescheduling feature
Default and dynamics shipping rates
Restrict preparation time and non-working days from the calendar
2. CommerceXpand
Using multiple apps to manage multiple business aspects often leads to a slowdown of your Shopify store.
You need apps that can fulfill your purpose without affecting the loading of your store. CommerceXpand is your one-stop solution, as you will find apps related to boosting sales, store management, and marketing.
CommerceXpand is a bundle of 28+ apps and is free of cost. You can simply install the app and use it over the most helpful apps like Bulk Editor, Image Optimizer, SEO Alt tags, Product reviews, Geo Redirection, and many more.
These apps can help you increase conversion rate, boost revenue, reduce abandonment rate, capture more leads, and build customer trust.
Feature Highlight
Improve customer engagement with apps like Volume Discounts, Back-in-Stock Alerts, Quick Buys, and more
User-centric apps like Facebook Chat, Sticky Cart, Geo IP Redirect
Sale booster apps like Countdown FOMO, Pre-order
SEO Optimization of the store with Image Optimizer app
Strengthen your marketing strategy with apps like Customer Reviews, Announcement Bars, and more.
3. Zipcode Validator
Our Shopify Zipcode Validator enables your customers to check the availability of products at their location using a zip code.
Your customers can check whether the product is available at their location or not on the product page rather than finding it out later during checkout.
If you have dynamic shipping rates and you charge based on zip code, our app can help you calculate the shipping rates as well.
Feature Highlight
Embed the Zipcode Validator in the header or on the product detail page
Create different delivery rules for the whole catalog, individual products, or collections
Prepare a whitelist and blacklist of zipcodes
Customize the text and color of the zip code label to match your Shopify store theme
Display estimated delivery date on entering zipcode
4. Language Translator
Online stores in a language that customers best understand can encourage them to buy. Translating the store to visitors’ native language will not just better customer experience but also makes it SEO friendly.
Our Shopify Language Translator app helps you translate the store without changing the backend theme.
You can host all the translations within your store database. Thus, translation will not impact your store’s loading speed.
As there will be no third-party translator overlays and the high loading speed of the store, the Language Translator app makes it SEO friendly.
Feature Highlight
Supports bulk translation
Edit auto-translated content if required
Manual and auto-translation of store components
Facility to create a language-specific domain for SEO
Translate SMS and emails to elevate customer experience
5. Australia Post Shipping
An app made for Australia’s Shopify store owners, the Australia Post Shipping app lets you manage and calculate shipping rates with ease.
Using this app, Shopify store owners can automate the live calculation and contract shipping rates. Thus, managing shipments becomes hassle-free.
The app has multiple options to assign dimensions to products. If you have already enrolled in multiple services of Australia Post, you will be able to enable the services you want and disable the rest.
Feature Highlight
Assign product dimension with multiple options like bulk, manual, or default
Re-sync option to auto-update shipping services
Fetch live shipping rates from Australia Post
Avail concessional rates offered by Australia Post for high volume orders
Enable/disable shipping services of Australia Post
6. Geolocation + Currency Converter
When you serve customers all over the world, you will use multiple domains to serve your customers better. But it is important to redirect visitors to the right domain, which is in their regional language.
Our Geolocation and Currency Converter app lets you redirect site visitors to their country/state-specific domain. Thus, you can offer your personalized experience to your customers.
There are two ways to redirect your customers to their region-specific website:
1. Auto-detect
2. Custom pop-ups
Choose any of the above features so that customers can comfortably shop in their local currency and language.
Feature Highlight
Auto geo redirection feature to redirect site visitors to state or country-specific domain
Block malicious visitors and IPs
Currency conversion feature as per customers’ location
Custom pop-up with text to redirect visitors to their state/country specific domain
Parameter to track the number of redirects
7. Dropshipping Manager
Struggling while shipping orders on time?
Well, simplify shipping management with our Shopify Dropshipping manager app. The app lets you find the order using the vendor’s name or by date.
So you can easily find out when your order is due and never miss any order date. If you have bulk orders, there is no need to manually add entries, directly import the XLSX, CSV, or ODS files sent by the vendors.
In the same way, export the order list in your preferred formats and share it with your vendors. With a few clicks, you can import/export order lists and save a lot of time to avoid manual entries.
Feature List
Filter orders using vendor’s details and dates
Import/export order details with CSV file
Update vendors about order status via emails
Final Thought
These apps are a must for Shopify store owners in an ecommerce business. These apps will not affect the loading speed of your store and enhance the user experience. If you want to serve your customers better, try out our Shopify apps now!
Shopify Apps
All product and company names are trademarks™, registered® or copyright© trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
The Article is originally published on:
https://www.appjetty.com/blog/shopify-apps-ecommerce-business/
0 notes
Text
Bulk geo ip locator

#Bulk geo ip locator update
#Bulk geo ip locator code
Show the local currency on a pricing pageĪbstract’s IP Geolocation API is serving over 3 billion calls per month to startups and websites like Shopify, Payoneer, Google, and even Stanford.Redirect the webpage based on language detection.Personalizing the content to your customers,.Security – Proxy, TOR, Crawler detection, and threat level.
#Bulk geo ip locator code
Location – all the standard geolocation information, including calling code.
ipapi helps with the following information. Use it with PHP, JavaScript, or REST API. Start geocoding today with any programming language of your choice - it’s free ipapi PositionStack is a Free geocoding API for global places and coordinates trusted by developers and businesses worldwide. PositionstackĢ+ billion addresses covered around the world | 1+ billion geocode API lookups handled per day. Their free plan includes a location module with 100 requests per month. The average response time of ipstack API is 25ms, which is excellent.
Connection – get the ASN and ISP details.
Currency – show the pricing in the user’s local currency.
Security – detect if a request is from proxy, TOR, crawler and tag them with a threat level.
Time zone – get the time zone so you can serve personalized greetings or products.
Ipstack data is divided into five modules.
Requester – to fetch data behind requester’s IP address to API.
Bulk – single query to retrieve multiple IPs data.
Standard lookup – to get the data behind an IP address.
Ipstack infrastructure is scalable to serve millions of requests daily. They are trusted by HubSpot, Samsung, Microsoft, Airbnb, and thousands of brands. Let’s take a look at the following Geo IP offering. You refer to the API within your application to retrieve the necessary IP information.
Geo API – you don’t need to worry about maintaining and updating it regularly.
#Bulk geo ip locator update
The problem in using the IP database is that you have to update it otherwise, regularly, you will not have up-to-date IP location information.
Geo IP database – you buy an IP database and host it on your server and refer to your application.
Technically, there are two possible ways to use Geolocation IP. If your online business relies on the user’s location, you should think of leveraging Geolocation API to offer the relevant products, services, news, and notifications. Amaze your users with personalized greetings, content, and more.

0 notes
Link
About Bulk GEO IP Locator
Find the city, country and time zone of one or more IP addresses at a time. When you want to know the location of an IP address you can look online but you may find you get lots of strange results. Use this free IP to location tool and get the right results instantly. You can check up to 1000 different IP addresses via this bulk IP lookup tool and get the results you have been looking for. This tool will run bulk lookups on input IP addresses or domains. It also will extract IP addresses/domains from pasted text that can then be then used to run bulk lookups on. Start by simply inputting IP addresses/domains, or add text and we’ll extract your IPs/domains for you. We will then run a bulk lookup on that list of IPs/domains for GeoIP, ASN, MX, Blacklist, DNS, Email Provider, and other information.
How can GEO IP Locator help you?
Bulk IP Address lookup and location locator tool. Bulk IP lookup (batch IP checker) is a tool to get location of multiple IP addresses and their geographic details in one click. Enter the IP addresses one ip in a and click check to locate all the IPs. This tool can be useful to anyone who want to check the exact location of people who are using your website, application etc. This will help you impress your friends by entering their internet broadband IP and showing them their location. This bulk ip lookup tool has the capability to pin point the location and show you the longitute and lattitude GPS coordinates. You can follow IP to get exact area with this tool. Geolocation (IP-based) is the mapping of a Mac address or IP address to the geographic area of the real universe of the internet-connected computer or a convenient device. Check my IP maps and address to a region (city), nation, longitude/latitude, and domain and ISP name in addition to other things. The precision of Geo-area databases may change based on the use of the database. For the IP-to-Country database, Our SEO Tools offers 98 percent to 99 percent exactness. Geo IP Tracker is essential for you to know the area of prospective web guests. You can trace the area of hackers and spammers on your website.
0 notes
Text
geo location ip
More about Bulk GEO IP Locator tool!
Bulk GEO IP Locator tool is here to help you find the city, country, and time zone of one or more IP addresses at a time. When you want to know the location of an IP address you can look online but you may find you get lots of strange results. Use this free IP to location tool and get the right results instantly.
You can check up to 24 different IP addresses via this free Bulk Geo IP Locator Tool and get the results you have been looking for.
This tool will run bulk lookups on input IP addresses or domains. It also will extract IP addresses/domains from the pasted text that can then be then used to run bulk lookups on.
Start by simply inputting IP addresses/domains, or add text and we’ll extract your IPs/domains for you.
We will then run a bulk lookup on that list of IPs/domains for GeoIP, ASN, MX, Blacklist, DNS, Email Provider, and other information.
How can GEO IP Locator help you?
Bulk IP Address lookup and location locator tool. Bulk IP lookup (batch IP checker) is a tool to get the location of multiple IP addresses and their geographic details in one click.
Enter the IP addresses one IP in a and click check to locate all the IPs. This tool can be useful to anyone who wants to check the exact location of people who are using your website, application, etc.
This will help you impress your friends by entering their internet broadband IP and showing them their location.
This bulk IP lookup tool has the capability to pinpoint the location and show you the longitude and latitude GPS coordinates.
You can follow IP to get the exact area with this tool. Geolocation (IP-based) is the mapping of a Mac address or IP address to the geographic area of the real universe of the internet-connected computer or a convenient device.

Check my IP maps and address to a region (city), nation, longitude/latitude, and domain and ISP name in addition to other things. The precision of Geo-area databases may change based on the use of the database. For the IP-to-Country database, Our SEO Tools offers 98 percent to 99 percent exactness.
Geo IP Tracker is essential for you to know the area of prospective web guests. You can trace the area of hackers and spammers on your website.
More about GEO IP Locator Free:
Free Location Finder tool for Bulk GEO IP Locator!:
Bulk IP tracer and location finding technology is a handy tool for you. Mass IP search check is the best strategy within the scope for selecting several IP addresses and their geographical details. Enter one IP address within the greatest IP and select search to look for all IPs. This tool might be useful for anyone who wants you to verify their actual location within those who use your website, application etc. This helps you impress friends by inputting their broadband IP on the internet and then showing them where they are.
This particular Mass IP search tool can pinpoint their location and display your GPS longitude and latitude details.
GEO Ip Technology
IP GEO Location - A sound and forward-thinking concept Whether sophisticated or not, geo-location IP technologies enable site providers to identify and prosecute abusive individuals anywhere in the world. Individuals have more freedom in the online virtual world than they do in the physical one.
The reason that so many laws is violated via the internet is that persons are less likely to be apprehended online. Until recently, the author was unable to detect authenticity, fraud, copyright violations, and a variety of other issues as easily as in the real world, and the criminal frequently got away with the crime. The IP geolocation has averted disaster and is likely to avert such disasters in the future. Due to security, access, and network efficiency, this location technology is becoming increasingly advantageous and important. Transforming the borderless Internet environment into one in which laws apply similarly to IP geographical locations.
Consider a website with an increasing amount of visits. This website contains information about a large number of clients who utilise their services. No transaction is guaranteed to be secure until customers enter their information online. What if this information turned out to be incorrect? If the customer voluntarily supplies an IP address (through site registration), or if the client does not, the location can be determined with approximate precision using a variety of methods. Online forms, registrations, and more registrations - all of this information may be poured in. Other than IP geolocation, there is no other way to verify legitimacy and legal constraints.
Web operators can detect a person's IP geographical location using a variety of software solutions:
1. Oftentimes, the simplest solution is also the least successful. Looking for the "Whois" information for the Regional International Registry can be a fruitless endeavour. There are five R.I.R.s, each serving a distinct geographic region. The R.I.R.s issue IP addresses to businesses, ISPs, and individuals in their region or area and make the information files available for free download. Numerous individuals have legitimately downloaded records with IP addresses and are now making them available for free on internet databases that you must access. However, these IP geolocation files are not exact and may be ineffective.
2. When it comes to IP geolocation, simple network techniques such as ping, traceroute, and nslookup perform better. A server network can provide a more specific location of an IP address. IP addresses are 'tested' and used throughout the internet by the network to accurately locate only one IP address. Some solution providers use hundreds (thousands) of servers, while others use only ten or twelve.
Ping = Internet Groper Packet (It is also a TCP/IP software package tool that determines whether or not the host is active while determining the round trip latency) (
Tracerout = a debugging tool for determining the path between a local and a remote host.
Nslookup = Name Server Search application (used by TCP/IP to determine the hostname or IP address).
3. While this final category of IP geolocation methods (number 2) is considered to be of moderate efficiency, other solutions employ even more complex technology, such as artificial intelligence and special systems. Additionally, some conduct a more thorough check and comparison of IP addresses and IP geostations.
This relatively complicated subject necessitates familiarity with the ever-changing Internet environment. There are numerous issues to discuss. The rule is that the internet, like every other component of the overall expanding industry, is increasing appeal daily. Because the virtual and physical worlds interact, safety is a concern in both. This is ensured by the IP geolocation system's recognition of genuine identities.
#geolocation ip address lookup#what my geolocation#geolocation ip lookup#ip geolocation#who is ip geo#geo ip location lookup#cars#illustration#drawing#marvel#photography
4 notes
·
View notes
Link
0 notes
Text
Acingame User Agreement
PRIVACY POLICY
Privacy Policy is designed to provide clarity about the information we collect and how we use it to provide a better social gaming experience. By registering for a Account, using this site and/or any of our company’ online or mobile products and services, you agree to our Privacy Policy and that we may transfer and store your account information as described in this Privacy Policy. If you have questions or complaints regarding our privacy policy or practices, please contact us as described in Section 9 (“Contact Us”). Table of Contents
1. Introduction
We know that you care how information about you is used and shared, and we appreciate your trust that we will do so carefully and sensibly. We respect the privacy rights of consumers and recognize the importance of protecting the information collected about you. We have adopted this global online Privacy Policy to explain how we store and use personal and non-personal information we collect online on our websites, during your use of our online products and/or services (including online game play) and on mobile platforms. In this policy, our company refer to “we” or “us”.
2.Information we collect
When you use any our game at an SNS such as Facebook, where our games may also be referred to as “applications”, you allow our game to access certain information from your profile for that site. The information you allow our game to access varies by game and SNS, and it is affected by the privacy settings you and your friends establish at the SNS. You can control and find out more about these settings at the SNS where you play our games. For example, our game may access and store some or all of the following information, as allowed by you, the SNS and your preferences:
· your first and last name
· your profile picture or its URL
· your user ID number, which is linked to publicly available information such as name and profile photo
· the user ID numbers and other public data for your friends
· the login e-mail you provided to that SNS when you registered
· your physical location and that of your access devices
· your gender
· your birthday
By playing our games through an SNS, you are authorizing our game to collect, store, and use in accordance with this Privacy Policy any and all information that you agreed the SNS could provide to our game through the SNS Application Programming Interface (“API”). Your agreement takes place when you “accept” or “allow” (or similar terms) one of our applications on an SNS.
If you play our games on your mobile telephone or other mobile device, including iPads and tablets, We collect mobile device identifiers, including MAC Address, and IP Address. In certain games We will create and assign to your device an identifier that is similar to an account number. We may collect the name you have associated with your device, device type, telephone number, country, and any other information you choose to provide, such as user name, character name, geo-location or e-mail address. We may also access your contacts to enable you to invite friends to join you in the Service.
If you purchase a license to use in-game virtual currency or virtual items directly from our company, We will collect the billing and financial information necessary to process your charges, which may include your postal and e-mail addresses. Our company may also receive the billing and payment information that you provide when your purchase is processed by another party, such as Facebook (for Facebook Credits) or Apple (for purchases on iOS devices). Please note that purchases of third party credits or currencies like Facebook Credits may also be subject to additional policies.
When you ask for assistance from our Customer Support team, We will collect and store the contact information you provide (generally your name and e-mail address), information about your game play or activity on the Service, and your user ID number. We will also store the correspondence and any information contained within.
We receive and store the information you provide, including your telephone number, when you sign up to have SMS notifications sent directly to your mobile phone. These messages notify you of in-game activity and may allow you to play the game from your phone. You can adjust the types of notifications you receive and when you receive them by editing your SMS notification settings; just log in to your game account and choose SMS mobile from the Help menu.
With your consent we may send push notifications to your mobile device to provide game updates and other relevant messages. You can manage push notifications from the “options” or “settings” page within the relevant game. You may also be able to manage them from your device’s settings page for the relevant game.
We may send local notifications to your mobile device to provide game updates and other relevant information. You can manage local notifications from the “options” or “settings” page within the relevant game.
When you access our websites or play our games, we collect (i) certain technical information about your mobile device or computer system, including MAC Address, IP Address and mobile device ID; and (ii) usage statistics about your interactions with the Service. This information is typically collected through the use of server log files or web log files (“Log Files”), mobile device software development kits and tracking technologies like browser cookies to collect and analyze certain types of technical information. Some of the cookies the Service places on your computer are linked to your user ID number(s). For more information on how we utilize cookies and other tracking technologies please review the “Cookies and Automated Information Collection” portion of Section 3 (“How We Collect Information about You”).
3. How We Collect Information about You
We may collect information about you in any one or more of the following ways: When you play one of our games, we collect and store certain information that you provide directly or through the SNS or other third party website that is offering our game(s). To provide a richer game play and social experience, We also collect information about your play and interaction with other players and the Service. The bulk of this information is collected and stored through the use of Log Files, which are files on our web servers that record actions taken on our games and websites. You may be able to take part in certain activities on our websites or games that give you the opportunity to communicate or share information not just with us, but also with other users of our Service. These include:
· participating in player forums and message boards
· posting public comments to other users’ profiles or gameboards
· sending private messages or invitations to other users, either directly on our websites or to their e-mail accounts
· chat with other users
· posting photos
We may record and store archives of these communications on our game’ servers to protect the safety and well being of our users and our company’rights and property in connection with the service. You acknowledge and consent to the recording and storage of such communications for these purposes.
We may collect or receive information from other sources including (i) other game users who choose to upload their email contacts; and (ii) third party information providers. This information will be used to supplement your profile – primarily to help you and your friends connect. It will be combined with other information we collect.
4. How We Use the Information We Collect
In general, we collect, store and use your information to provide you with a safe, smooth, efficient, and customized experience. For example, we may use information collected from you in any one or more of the following ways:
· to create your game accounts and allow play of our games
· to identify and suggest connections with other platform users
· to enable user-to-user communications
· to provide technical support and respond to user inquiries
· to prevent fraud or potentially illegal activities
· to deliver and target advertising
· to notify users of in-game updates
· to provide in-game leader boards and promote in-game player achievements
· to solicit input and feedback to improve our products and services and customize your user experience
· to inform users about new products or promotional offers
· to engage in commonly accepted practices, such as contacting you at the email address we have on file if you are a potential winner in a sweepstakes
One important use of your information is communication. If you have provided your e-mail address to us, we’ll use it to respond to (i) customer support inquiries, and (ii) keep you informed of your in-game activity, including comments from friends, notifications about in-game status such as “crops ready” as well as notifications of gift and neighbor requests. Some messages, such as invites for friends to join you in a game, may include your name and profile photo. We may also send promotional e-mail messages and promotional SMS messages (“Promotional Communications”) directly or in partnership with parties other than ourselves. Each Promotional Communication will generally offer recipients choices about receiving additional messages.
5. Sharing of Your Information
We will share your information (in some cases personal information) with third parties, that is parties other than our company, in the following circumstances:
We will provide your information to third party companies to perform services on our behalf, including payment processing, data analysis, e-mail delivery, hosting services, customer service and to assist us in our marketing efforts. We direct all such third party service providers to maintain the confidentiality of the information disclosed to them and not to use your information for any purpose other than to provide services on our behalf.
We do not actively share personal information with third party advertisers for their direct marketing purposes unless you give us your consent.
We may share (i) aggregated information (information about you and other users collectively, but not specifically identifiable to you); (ii) anonymous information; and (iii) certain technical information (including IP Addresses, MAC Addresses for mobile devices and mobile device IDs) to develop and deliver targeted advertising in the Service and on the websites of third parties. We may also allow advertisers to collect these types of information within the Service and they may share it with us. Advertisers may collect this information through the use of tracking technologies like browser cookies and web beacons. The information collected may be used to offer you targeted ad-selection and delivery in order to personalize your user experience by ensuring that advertisements for products and services you see will appeal to you, a practice known as behavioral advertising, and to undertake web analytics (i.e. to analyze traffic and other end user activity to improve your experience).
Safety, Security and Compliance with Law
Your information, and the contents of all of your online communications (including without limitation chat text, voice communications, IP addresses and your personal information) may be accessed and monitored as necessary to provide the Service and may be disclosed: (i) when we have a good faith belief that we are required to disclose the information in response to legal process (for example, a court order, search warrant or subpoena); (ii) to satisfy any applicable laws or regulations (iii) where We believe that the Service is being used in the commission of a crime, including to report such criminal activity or to exchange information with other companies and organizations for the purposes of fraud protection and credit risk reduction; (iv) when we have a good faith belief that there is an emergency that poses a threat to the health and/or safety of you, another person or the public generally; and (v) in order to protect the rights or property of ours.
6. Methods of Accessing and Controlling your Information
If you no longer want our game to make active use of your information, you may send an e-mail to [email protected]. Place “Delete My Account” in the subject line and include your first name, last name, e-mail address and user ID number for the SNS from which you access our games (if applicable) in the body of the e-mail. We will respond to your request within thirty (30) days. Please note that certain records, for example those pertaining to payments or customer service matters, will be retained for legal and accounting purposes. If you have sent or posted content on the Service, We may not be able to delete it. If you wish to review or change the information we have about you, e-mail us at the address provided. You can turn off push notifications by visiting the “options” or “settings” page within the relevant game. You can turn off local notifications by visiting the “options” or “settings” page within the relevant game.
7. Privacy Policies of Linked Sites and Advertisers
Our websites and games may contain advertisements from companies that may link to their websites. We are not responsible for the privacy practices or the content of such websites. If you have any questions about how these other websites use your information, you should review their policies and contact them directly.
8. Security of Your Information
We understands the importance of keeping your information safe and secure. We will make commercially reasonable effort to protect your personal information and ensure the security of our systems. Unfortunately, the transmission of information over the Internet is not completely secure. Although we strive to protect your personal data, we cannot guarantee the security of your data while it is being transmitted to our site; any transmission is at your own risk. Once we have received your information, we have procedures and security features in place to try to prevent unauthorized access.
9. Contact us
If you have any questions, comments or concerns regarding our Privacy Policy and/or practices, please send an e-mail to [email protected].
1 note
·
View note
Text
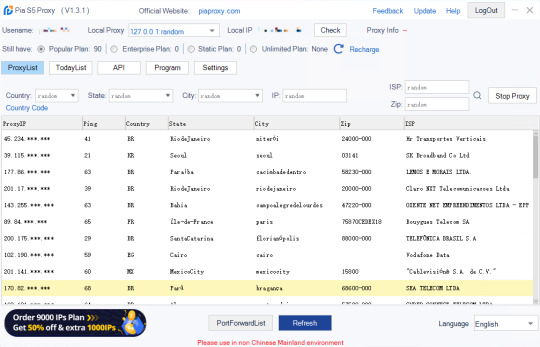
With PIA, you get more than just proxies. With our premium residential proxies and experienced development team, scale your operations. Never get banned.
Save time and effor
Use our proxies with any software, browser, script, proxy tools, or device. Easy API and the best documentation on the market will let you start your projects instantly.
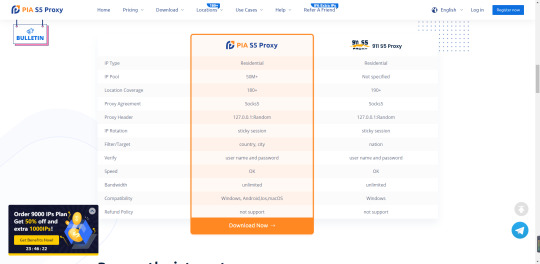
State and city-level targeting
Our Residential Proxy network covers 180 locations and offers country, city, and state-level geo-location targeting. Pia S5 proxies help access geo-restricted content without extra charge.
Bulk proxy, Automated jobs
Get 50 million IP resources with one click, avoid flags, change IP location any time, and create and manage multiple accounts without restrictions.
Proxy pool growth
We make sure that our IP proxy resources are stable and reliable, and we continuously work on expanding the current proxy pool to fit every customer's needs.
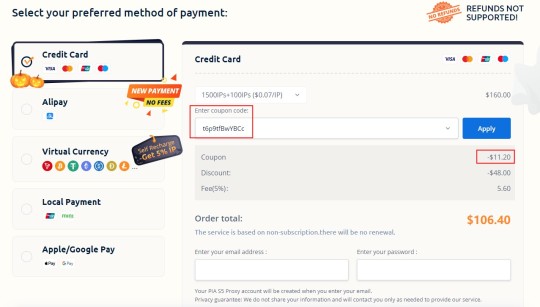
Use this code for more savings: t6p9tfBwYBCc
Please click the link for details: https://www.piaproxy.com/lemon/
0 notes