#bennettuniversity
Explore tagged Tumblr posts
Text
Silver Medal Triumph: Priyanka & Sohail Shine in 35+ Mixed Doubles at 4th IPA Nationals
#pickleball #ipa #ipanationals #pickleballindia #35plusmixeddoubles #silvermedal #pickleballtournament #bennettuniversity #sportsnews #pickleballgrowth ZOOM TV is India’s leading Hindi Entertainment news channel that provides the audience with the latest Bollywood updates, breaking news, celebrity and television gossip. It features a vibrant mix of Hindi entertainment and original programming,…
0 notes
Text
Real Survival Based on Augmented Reality
Augmented and Virtual reality are the trend in the gaming industry at present and going to be the future of gaming industry as well. For keeping the games interesting augmented reality gaming takes the advantage of the diversity of the real-world environment by expanding the playing area/field. Survival games in augmented reality are not yet so popular in the real-world gaming arena. There are not so many survival games using augmented reality are available in the gaming world environment.
“Real Survival” is a cellular gaming utility in particular designed for the Android platform and it is functional on both mobile clever devices as well as tablets. “Real survival” has been developed for Android developed variations above 4.4.0 and all subsequent releases. The software data of this gaming assignment is stored locally on the gaming engine elements. Android platform is graphically adaptable with a 2 and third-dimensional pictures library primarily based on OpenGL ES 2.0 specifications as well as hardware orientation, scaling, pixel format conversion and accelerated 3D graphics.
Gameplay for this game is quite easy as it is in its partial development phase. The player will have an already equipped weapon in his hand while entering into the gaming environment. He has to survive each and every level by killing the coming enemies and to enter into the other further levels of the game. Since, Augmented Reality has been the important factor of this game, the gameplay will look more convincing and satisfying if played using AR headset for much better user experience.
1 note
·
View note
Text
Explicrypto
Explicrypto is a mobile application which supports Android platform and was built using Android Studio. It can encrypt all your explicit images in the gallery, thus protecting your privacy. Explicrypto can be one of the best applications to trust your privacy with, as it does not internet connection to work. The processing of the image which includes, nudity detection, encryption, and decryption, happens within your device with no contact with the outside world. Due to which, it is very safe to use. Explicryto works in two modes, one is manual mode and the other one is an automatic mode.
In manual mode, first the user needs to grant all the required permissions to the application, for the first time, then the user needs to click a picture using the application. Once the picture is clicked it will be displayed on the next screen. Now, the user can click on “Classify” button to check whether the image is safe or not. As soon as the user clicks on classify button, the image is sent to MobileNet model (which is converted into a TFLite format to support Android). The MobileNet model, then gives the output in three categories Safe, Unsafe, and other along with the confidence at which the model is classifying. If the model classifies an image in unsafe category, then it gives a message that the image is unsafe, and it should be encrypted. Based on those reading, it is up to the user to decide, whether to encrypt the image or not. If the user decides to encrypt the image, the image vanishes from the application and is successfully and safely encrypted. The encryption technique used bas basic and was based on a randomly generated hash key. For decryption, you need to select the path of encrypted files and need to click on “Decrypt” button to decrypt the image. The image is decrypted using the same hash key as used while encrypting the file. Once the image is decrypted, it will again display in the application window.
In automatic mode, it uses the same architecture as in the manual mode. It will also require permission to read and write files. In this mode, the application will work in the background and will scan though the entire gallery. Each image from the gallery will be sent as an input to the MobileNet model and it will give an output whether the image is safe or not with the confidence level. Based on confidence level, it will decide whether to encrypt the image or not. If the image falls under unsafe category, it will automatically encrypt it. To decrypt the image, user again needs to open the application and select the path of decrypted image, to decrypt it.
I have decided my project life cycle to follow Agile approach because I am developing my project in different phases so iterative and incremental approach would be best for my project. Since each phase of my project requires is independent from each other so it can be delivered individually and frequently, which can help me get feedback from the user so that I can enhance the application while delivering the next phase. The design and execution of the project is very simple, and it is not dealing with any kind of complex architecture which makes it well suited for agile approach.
Explicrypto requires a very basic setup. The application only runs on Android devices with Android version 5.0 or above. Currently it is not supported on Apple devices, but will be released for iOS in future updates. The application also requires permission from the user to access device's storage and permission to read and write files on the device which is necessary for encryption and decryption. To use the application on manual mode it is assumed that the camera is fully functional to click pictures. The processing (including detection of nudity inside a picture, encryption and decryption) solely depends on the hardware which your phone is using.
All the necessary information about the Explicrypto including its code, was kept in a public repository called Github. All the changes and updates that was made in code, starting from its initial phase was committed in the repository so that a proper track of the project could be maintained. Each commit in Github was well descripted about the changes made or about adding new modules into the code.
Explicrypto has one of the most user-friendly interfaces. It provides just four buttons for quick and easy interaction in manual mode. With just four buttons, it’s very straight forward to guess their functionality with minimum interaction. One button is to click the picture while the application is open and another one will be to scan the images in the background. Once the image is classified then the user can choose whether to encrypt the image or not by either pressing or not pressing the encrypt button. To decrypt the file, the user just needs to select the path of the file by pressing a decrypt button and the file will be decrypted back to its original form. It is very easy to use because, as soon as the user opens up the application, the application will bring the user directly to the page where there is a camera open which is ready to take the picture and three buttons on the bottom of the screen. As mentioned previously, those buttons will let the user decide whether they want to classify, encrypt, or decrypt the image. These four buttons will provide the easiness of using the application without having any knowledge about technologies.
The remaining work of my project only includes work from the automatic mode. As the data set which I have used to train my model is not huge and user can click any kind of pictures, due to which the model might not be 100% accurate, all the time. Which might lead to the faulty encryption of image files. And sense my gallery has thousands of images it would be a very hectic work manually decrypt all the images which word encrypted accidentally by the application. So, my remaining work is to expand my data set and retrain my model again and again so that it covers all the possible cases for accurate classification.
TIMELINE
Week 1
In the first week of the project, I spent most of the time discussing about the domain on which I should do my project on. I was not sure that whether it has to a project related to machine learning only or it could be something else. As per the instructions given to us in the first week by our mentor and HOD Dr. Deepak sir, it was not mandatory to make a machine learning project. He guided us that our capstone project may not need to be just about developing applications or doing research. Which instantiated wide range of ideas in my mind, and spent time deciding that only.
Week 2
During the second week of the project, I spent time talking to others about the domain only. But this time I was taking the suggestion and advice of my friends. They were giving feasible suggestions on how I should be more focused on getting a better job and equally dedicates the time to the project. As most of the them were prioritizing job over the project, it led me into confusion about the domain of the project. While having one-to-one interaction with faculty mentors in our project lab, they suggested me the domain of my project. They said that it should be Machine Learning as I am doing my specialization on Machine Learning and Data Analytics (MLDA).
Week 3
During the week three of my project, I was busy deciding on which sub-field of machine learning I should make my project on and whom should I approach for mentorship. In the previous semester Dr. Shridhar sir used to take or classes of Deep Learning, so I thought that it would be the best to approach him as he could guide me more efficiently on how I should move ahead with my project. Initially it was on me to bring the idea to him and get his opinion on that. After few days of research, I decided that I should work on the developing education content on genetic algorithm in machine learning as I was fascinated about the working of that algorithm.
Week 4
In week four, I presented my idea about developing education content to Shridhar sir, but he wasn’t much impressed as my idea was not feasible in the market. Then I came up with the idea of making an application which will tell you what to eat in your area depending on the reviews of people. This idea was again unsuccessful as there was no novelty in it. At last Dr. Shridhar sir suggested me to make a project to protect private pictures of people getting leaked on the internet. For which he told me to make an application which detects the explicit images and encrypt them automatically in the phone. So, I took that suggestion and finalized my project idea and domain and wrote my milestone one report on that.
Week 5
In the fifth week of the project, after submitting the report on my milestone one, the companies started coming for the placements. Now I had to manage the research work on the project and parallely manage the placements exam and interview. As I applied in most of the companies, I was not getting enough time to devote to my project. But during the entire week I read some online paper and searched though Github to get references from the related project. Also, I downloaded the required setups which were necessary for the development of the application, like Android Studio, Gitbash, etc.
Week 6
In the sixth week of the project, I bought some online courses related to the android development course and how to apply machine learning on android as android studio by default does not support machine learning. First, I started with the basics of the android development and learnt how to design basic application by adding functionalities like button, label, textfield, background color, etc. Once I gained the required knowledge, I started building the application. The application just has the basic layout. Initially, when I was preparing the android studio on supporting the machine learning algorithm, I was encountering many errors and had to look up on internet several times to tackle those errors and set up the application.
Week 7
In the seventh week of the project, and the sixth week as well, I had very less time to devote to the project as during the day time, I was busy with the interviews of different companies and I during the evening time, I had to attend extra classes that were arranged for the training of the placement process. Apart from the placement processes I spent time in deciding which model should I use for the training of my application. As Google’s Tensorflow offer many models which you can train to perform tasks like image classification and detection. So, I decided that it would better to use the model from the Tensorflow itself as only those models can be deployed to mobile device using Tensorflow library.
Week 8
In the eighth week of the project, I cloned few models from the Github and tried to understand how they are working buy running them on android studio. I was figuring out how they are providing input to the model. Also, I had to do documentation of milestone two with research work. The research work is still in progress. Apart from that I downloaded my dataset and trained MobileNet model from Tensorflow on my laptop. To test the working of the model I gave the image as an input to the model and it predicted the correct output. Then I downloaded a demo application from Github and imported my model into that and tested on live data and it predicted correct most of the time.
Week 9
During the next week, i.e. week nine, I continued with more research work and learning more about the Tensorflowlite library and about its uses and functionality. As it is the first time I am working on a mobile application, I went through the online courses and brush up my skills on developing and enhancing the user interface for my android application. As I still haven’t figured out how to give input to the model in android application, I looked for some more projects to find out the answer. Also, I referred to the YouTube videos for the same.
Week 10
In the week ten I implemented the model in my application. While implementing the model I checked for errors or bugs that might occur while feeding input to the model. Once the model is implemented and it is working perfectly fine on all the input images. I retrained the model on bigger and better dataset because it was trained on smaller dataset for the purpose of testing and compatibility. So, my primary focus on the week ten was to implement the model in the application and assuring that it is working fine and performing the required task in real-time.
Week 11
In the week eleven, I focused to implement the technique of encryption in my project. For that I again did the research work and checked for the proper encryption technique that would be feasible with my project. The proper encryption technique is essential so the application must run in the real time. It should not take lots of computation time while encrypting the images. I also referred to YouTube and GitHub, if some help is required. Along with the encryption technique I had to secure the file for decryption in the device itself so that hackers won’t get access to the file easily.
Week 12
During the last week of the project I focused on final testing and debugging of the project. I performed Whitebox testing on the project and investigate codes for errors and bugs. Once the application is free from systematic errors. I performed Blackbox testing which would be like beta testing. I allowed my friends and family member to use the application in whatever way they like and will record their feedback. After getting the feedback I did the require changes. Once the process of debugging and testing is done, I finalized my application for the final evaluation.
Github Repository link: https://github.com/anubhavanand12qw/Explicrypto
#bennettuniversity#bu androidstudio privacy encryption decryption nudity machinelearning csebennettuniversity
1 note
·
View note
Text
MESS IN BENNETT
In many organizations whether educational or industrial there are group which caters the people of the said organization and have some kind of process to help them. This application will help all these organizations to make their work easy and complete the work in a very ordered manner. As the basis for all the process is same so the application be change with accordance to the users wish. As the application is simple to use, it can be operated by anyone carrying an android device and connected to the organization database to login to their own account to start using the application.
TIMELINE
Week 1
The first week was spent just accumulating back with the environment of the university and not much was done in terms of project development. In the first week the focus was mainly on the introduction with the new subjects given or chosen by us for the new semester. As we returned from our internship, we had to submit a full-fledged report about the same and a video was to be uploaded on our YouTube channel and all of this took my whole time for that first week back at college. Also, as it was the first week no one was in the mood to start brainstorming for the idea of the project so early.
Week 2
The second was spent brainstorming for the idea for the project. As I did web-development in my internship I wanted incorporate that learning in my project. So, went around the teacher’s department and asked for their help in choosing a project which will not only be impressive but will be completed in the given amount of time. But that was of no help, I was not able to get any good ideas from the CS department and to rely on the internet only. I knew that I wanted to combine web development and machine leaning in my project, but I didn’t know in what way.
Week 3
In the third week I started researching on the internet for the ideas for the capstone project, this again proved to be quite difficult because some projects which I found were of very low level and some were of so high that I was quite shocked that people had done sch impressive work in their B.Tech degree only. The idea of my project from my friend/roommate, he told me about the problem faced by the mess committee and how much food is wasted when some students decide to skip their meals, particularly on weekends. All of this resulted in the idea for my project.
Week 4
In the fourth week I started focusing on the methodology for my project. It was a difficult process as I must start the course on android development, because before this I have not dwelled in the development of smartphones applications. This was challenging as I had to start writing for the first milestone also. The first milestone was a big document which ate up a lot of my time. Finally, the first milestone was completed, and I started working for the development of my project with focus on the development pf the machine learning model and taking out the data.
Week 5
After submitting the first milestone, the placement preparedness classes started and the companies started coming, which ate up a lot of time. As I had to prepare for the aptitude tests and prepare myself for the interview process, all of my time was spent focusing on readying myself for the placement drive. But in between all these procedures I still was able to focus on completing the android course(basic) on Udacity. I also started clicking pictures o the dishes served to us in the mess and collected images from the internet of the three dishes which I focused on first.
Week 6
In the third week the companies started coming and each day at least one company was in the campus. The progress of the development of the project was slow and I basically did very little in this week. I started working on the model to recognize different dishes. Last semester I learned deep learning in which I learned CNN, which was a method to recognize images.
I started working on the development for the model to differentiate between different food items, but to train the model I need a lot of images and a variety of it with some data specially for validation.
Week 7
In the seventh week I started working on the user interface of the app and started making the registration and login page for the application. I used online available firebase database available to us free from google. I connected it with my android studio and used to allow access to the users. I stated training my model VGG16 but it is taking a lot of time to train the data on azure notebook and also some considerable amount of time is spent on the validation part. I was able to do this much only as I was busy in the placement process.
Week 8
In the eighth week I stated writing the second milestone, which again is a big document and is taking a lot of time to complete the document. This week is especially hectic because of the coming mid-term and the placement drive which is happening. As I have not been able to secure a job yet my main focus is on the placement process, the only I will be able to spend all my time on the development of the project. The development of the project again will be slow in the next week also because of the coming test and the lab evaluation in the subject of RPA.
Week 9
In the coming 9th week I will be focusing on the mid-terms and the evaluation of the second milestone. I will also try to increase the speed of my VGG16 model and try to bring some changes in it so that the latency will be reduced. Also, I will try to add some basic functionalities in the application I am developing at the same time with the model. If by then I am not placed I will be revising all my previous subjects to improve my chances in the next upcoming placement drive. But the focus will jot be shifted from the project.
Week 10
In the 10th week I will focus on the model to predict the favorite dishes of the users. That will need some data to train but as I will not have data from the users, I will try to make up some data and feed it to make it work. At the same time, I will probably research how to upload my models on the server so that the android application can communicate with model to predict the results. As this will be new for me so it will probably take up a lot of time, but the necessary work will have to be completed.
Week 11
As the deadline for the project submission will be coming close, I will have to start working very quickly and start focusing on the app development, in a fashion that the users will be able to understand how to use without any instructions given to them. The user interface should be very easy for any user to understand and, I will focus on how to reduce the latency of getting the output from the server. If there are any documents to be written I will also have to spend time on them. But at tis time I hope to complete my project.
Week 12
At this point of time I will focus on finetuning any development left in my project. I will probably try to improve my application and try to train my model as much as possible in the time left. I will probably try to improve all the aspects of my project and if there is anything that I may have missed in the development procedure will try to remove it and finish my project on time. Also, will have to test my application in real time and will have to receive the feedback from the users, which again is an essential part of any product development.
DESCRIPTION
The project is using machine learning in an android application which is not very easy to achieve. The application will be opened by the user and they will be met with the registration tab in the starting which is connected to free to use database “Firebase" available to the people on the net, this database is generally used for the mobile applications only. In this the data which is being sent from the application is sent will be saved. Also, the data can be read from here if there comes, if any need arise to use some kind of functionalities which require to take out data from the database, it will not be difficult.
The user will have to submit their email id and must make a password to register in the application and to start using its functionalities and same goes for login also. After logging inn, the user can select the menu button to see the menu for that day. Also, there will be button identify the different dishes available in the menu.
This will automatically open the camera of your phone for you and you can click the image of the food. As the model is using a couple thousand image to identify the dish, the captured picture should be clear and not blurry and the focus should be on the actual dish and not other items, then only the model will work properly. There are thousands of images that are used to train this model and some few to test and validate the model. Also the process to convert the python file into the file which can be used in the android project is also difficult.
1 note
·
View note
Link
2 notes
·
View notes
Photo

Online Math Tutor For M.Sc, M.Tech, B.Tech, Engg Diploma, B.Sc, BCA, BBA, B.Com, BA, Math-1,Math-2, Math-3, Math-4, Probability Theory, Linear Algebra, Real Analysis, Vector Analysis, Complex Analysis, Calculus Etc. https://mathedu.co.in #mathtuitions #school #schoolstudents #college #collegelife #delhitechnologicaluniversity #delhiuniversity #ignou #ccsuniversity #jamiauniversity #aktuuniversity #amityuniversitynoida #amityuniversity #shardauniversity #galgotiasuniversity #shivnadaruniversity #bennettuniversity #manipaluniversity #university (at Delhi, India) https://www.instagram.com/p/CMWmEiOj5nl/?igshid=1npjwetprspgm
#mathtuitions#school#schoolstudents#college#collegelife#delhitechnologicaluniversity#delhiuniversity#ignou#ccsuniversity#jamiauniversity#aktuuniversity#amityuniversitynoida#amityuniversity#shardauniversity#galgotiasuniversity#shivnadaruniversity#bennettuniversity#manipaluniversity#university
0 notes
Photo

Bennett University is ranked second for B.Tech and third for BBA this year in Top Emerging Institute survey, know five big reasons to get admission in Bennett university | टॉप इमर्जिंग इंस्टिट्यूट सर्वे में बीटेक के लिए दूसरा और बीबीए के लिए तीसरा स्थान किया हासिल, जानें यूनिवर्सिटी में एडमिशन लेने के पांच बड़े कारण Hindi News Career Bennett University Is Ranked Second For B.Tech And Third For BBA This Year In Top Emerging Institute Survey, Know Five Big Reasons To Get Admission In Bennett University…
#Aamir Khan#B.Tech#BBA#Bennett University North India&#BennettUniversity#convocation#Five#institute#Top Emerging Institute
0 notes
Photo

टॉप इमर्जिंग इंस्टिट्यूट सर्वे में बीटेक के लिए दूसरा और बीबीए के लिए तीसरा स्थान किया हासिल, जानें यूनिवर्सिटी में एडमिशन लेने के पांच बड़े कारण Hindi News Career Bennett University Is Ranked Second For B.Tech And Third For BBA This Year In Top Emerging Institute Survey, Know Five Big Reasons To Get Admission In Bennett University…
#aamir khan#B.Tech#BBA#Bennett University North India&#BennettUniversity#convocation#five#institute#Top Emerging Institute
0 notes
Text
Final Day of IPN Nationals at Bennett University: A Game-Changing Pickleball Experience!
#pickleballnationals #ipnnationals #bennettuniversity #pickleballindia #sportscoverage #pickleballobsession #ipn2025 #worldclassfacilities #sportsinindia #pickleballfinal Read More
0 notes
Text
Assessment of Network Time Protocol (NTP) vulnerabilities
NTP is one of the oldest protocols designed to synchronize time between computer systems and the internet. Time plays a crucial role in the security of a system and is often ignored. Therefore, we can launch a replay attack as well as Denial of Service attacks by altering the time. Attackers only search for vulnerabilities in a system and attack if a loophole is found whereas in case of NTP, it is most vulnerable and attackers can launch attacks or hack into some software’s working on NTP which almost every software does. The attack on an NTP server may trigger serious issues, it can misalign machines causing malfunctions, it can allow the authentication of entities using expired credential or digital certificates. Many DoS and DDoS attacks are possible depending on the factor whether the device knows the correct time or not. It can also decide whether a certificate is still valid or not. Even nowadays many servers provide time to their clients without any authentication, and those who provide authentication using their standards do not analyse data or they require a pre-shared key or are vulnerable to password theft attacks. Most of the clients have NTP server address hard coded in their firmware.
In October 2002, one of these attacks was launched on one of the web servers in Trinity College, Dublin. It was traced that the server was bombarded with a program Tardis with thousands of copies around the world and then it contacted the web servers across the world and obtained Timestamp from HTTP servers. Since hackers are mainly making use of this protocol to launch a DoS attack or any replay attack, this project will assess various vulnerabilities related to NTP protocol and design a defence mechanism so as to protect any useful information and also prevent the servers from going down under the impact of malicious intent of any hacker.
Since hackers are mainly making use of this protocol to launch a DoS attack or any replay attack, this project will assess various vulnerabilities related to NTP protocol and design a defence mechanism so as to protect any useful information and also prevent the servers from going down under the impact of malicious intent of any hacker. Since NTP is such a protocol that keeps lurking in the background of many systems and any changes made to it can cause various applications that use this protocol to stop or malfunction.
The current system has the feature that the client can sign any packet before sending and receiving whereas in our solution only the broadcast server should be able to sign broadcast packets.
Till now I have performed 2 attacks-
1- MITM attack using SSL Striping by time-shifting
In this first, we would be creating a fake NTP server. You can create one if you want or else use many servers already available. In this project, I have used Delorian server. Then Configure the server to send the time in future. Rest steps you can see in the algorithm included in this report.
SSL/TLS is a protocol used to send or receive sensitive information and is used mainly for banking, login page and email correspondence. It creates a secure connection between the two parties(usually a client application and a server). Browsers and web servers regularly use this protocol when a secure connection is needed.
The following events in order are done when we connect to the https website-
The user sends an unsecured HTTP request.
The server answers via HTTP and redirects the user to a secure protocol (HTTPS).
The user sends a secure HTTPS request, and the secure session begins.
In order to “strip” the SSL, an attacker intervenes in the redirection of the HTTP to the secure HTTPS protocol and intercepts a request from the user to the server. The attacker will then continue to establish an HTTPS connection between himself and the server, and an unsecured HTTP connection with the user, acting as a “bridge” between them.
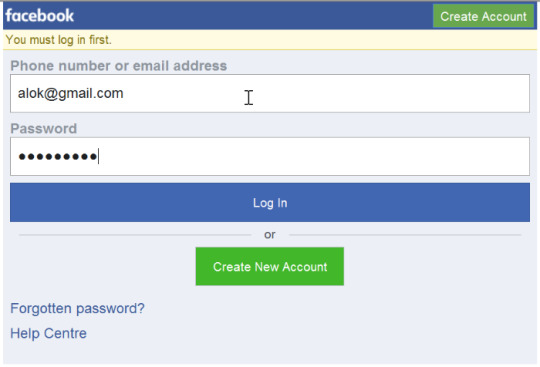


2- NTP Reflection attack
NTP is a UDP based protocol, that is often set up in an unsafe manner. This allows attackers to attack its integrity. The request packets to fake NTP server are captured, saved and edited. The edited packets will then be sent to the victim in large numbers. For this, we will be writing a script. We will be monitoring the CPU and memory usages. Under normal conditions, CPU usages are almost equal to 0 per cent. The CPU usages hike up after we run the script and bombard a large number of packets. This will work as a DoS attack.
The sole aim of this project was to deliver the end-user a defence system that could tackle such vulnerabilities. We also would search for more vulnerabilities and different ways that how a false packet can be crafted. In this project, until now I have tried many Vulnerabilities that are NTP attack prone. I have launched SSLStrip attack, Man in the Middle attack, Time-shift attacks and also NTP reflection attack that is a DoS attack.

The remaining work is to search for a few more vulnerabilities and then sniff and analyze packets at the server end. I will be making a script that could sniff such packets and drop them. I will also plan to make a GUI so that any incoming packet can be analyzed by the end-user without actually having to write commands.
This project was taken up as part of my capstone project. The project idea was given by my faculty Dr Mayank Swankar. Special gratitude to him whose contribution in providing his valuable guidance and support, stimulating suggestions and encouragement, helped me to coordinate my project with different research papers and also helped me to design a defence mechanism for the same. I would also extend my vote of thanks to our Head of the Department, CSE Bennett University, Dr Deepak Garg for motivating me throughout this project. I would also like to thank Dr Sanjeet for keeping track of my progress.
1 note
·
View note
Text
Bunny Shooter : 3D Action-Survival Game
Introduction
“Bunny Shooter“ has been developed using the Unity gaming engine. The game includes scripts, animation, music, models, and many other assets. Scripts were completely written in C# language and are easy to understand. This game has a single objective, i.e. to kill more and more zombears for your own survival. The Game is specifically designed for PC users, and it’s quite easy to play with very simple controls to handle. Left, right, up and down arrow keys for player’s movement, left Ctrl key to fire and mouse cursor for moving the player’s direction of shooting. Things like raycasting and quaternions are also used for better graphical representation.

What is Ray casting and Why I chose to use it?
Raycasting is the process of detecting the presence of any collider in the path of a ray by sending an invisible ray from a point to a specific direction. Raycasting is a very wide concept in game development and has many more application to work on.For example, in strategy game you might want to place an object on the terrain, to do this you can perform a ray cast from the camera through the mouse position and detect the point at which the ray intersects with the ground. In a combat game when a weapon is fired, you could cast a ray going out from the barrel of the gun in order to detect which object is hit.Or, In hiding game where you want to know if an enemy is able to see a player, you could cast a ray from the enemy’s position in the direction of player and if it reaches the player without colliding with anything else. Unity supports raycasting in both 2d and 3d scenes. I used raycasting where the player shoots the zombears by shooting a ray from the gun to detect whether the enemy got a hit or not.


Conclusion and Learnings
Completing this first phase of this game all alone has taught me many things. Concepts of using gaming engines, character modelling and animations got stronger. It helped me to understand things like how audio and sounds is handled and used properly, how animator controller lets you design your own state machine using logics like bool, trigger and transition, also learnt the proper use of animation at suitable places. Working with scripts like how to make camera follow the player as the player moves around in the game scene, player movement script, control keys for player movement and some few more scripts like player’s health, enemy’s health, score manager, enemy attack, etc. Apart from these, I also got to learn and work on ray casting and quaternion which are actually some difficult tasks to perform alone as an indie game developer. It helped me in creatively thinking and imagining the scenes that can be used in the game. This project has not only tested the technical knowledge but also the patience level that a person can have. There were few phases where I almost gave up on the project because of some failure issues and lack of resources but I recovered from it and that helped me in completing the game. If there are any kind of ideas, suggestions or feedback or more effective development ideas please feel free to leave your valuable comments.
Some useful links to refer
https://docs.unity3d.com/Manual/CameraRays.html
https://docs.unity3d.com/Manual/index.html
https://www.digitaltrends.com/gaming/best-survival-games/
#bennett university#BennettUniversity#survival games#action games#csebu#game development#unity 3d#blender
0 notes
Photo

Bennett University, Greater Noida in Greater Noida apply for online admission know the offered courses, placements salary records, campus facilities, student reviews, alumni, etc.
0 notes
Link
Bennett University: Get information on placement, admission procedure, cut-offs, ranking, faculty and more!
0 notes
Photo

https://coursesforallacademynoida.tumblr.com/post/637822029248200704/engineering-mathematics-m1-m3-online-tutoring #amityuniversitynoida #bennettuniversity #dtuuniversity #manipaluniversity #velloreinstituteoftechnology #kalingauniversity #ipu #ipuniversity #rajasthantechnicaluniversity #punjabtechnicaluniversity #chandigarhuniversity #srm #shivnadaruniversity #btechtuition #btechtuitions #backpapers #yearback #student #student (at Noida नोएडा) https://www.instagram.com/p/CI7iRT7nV5v/?igshid=89u4kylb3mn6
#amityuniversitynoida#bennettuniversity#dtuuniversity#manipaluniversity#velloreinstituteoftechnology#kalingauniversity#ipu#ipuniversity#rajasthantechnicaluniversity#punjabtechnicaluniversity#chandigarhuniversity#srm#shivnadaruniversity#btechtuition#btechtuitions#backpapers#yearback#student
0 notes
Photo

#artificialintelligence arrived #India #bennettuniversity @ #noida 👌 #welcome to #AI (at Indore is LIFE)
0 notes
Text
From Tennis to Pickleball: India’s Rising Stars Dream of International Glory
From Tennis to Pickleball: India’s Rising Stars Dream of International Glory #pickleball #pickleballindia #indianplayers #tennisplayers #pickleballtraining #pickleballtips #pickleballstars #sportsindia #4thipanationals #pickleballcommunity #pickleballgrowth #bennettuniversity ZOOM TV is India’s leading Hindi Entertainment news channel that provides the audience with the latest Bollywood updates,…
0 notes