#and we all know every app spies on our google searches
Explore tagged Tumblr posts
Text
Why Is Google Tracking You – And How Does It Do It?

Whenever we use the internet, we all know that we’re putting our private information into a public space.
This is part of the reason why crime novelists are so scared to do research. It’s easy to imagine the FBI crashing through the door within seconds of a Google search, even if a search is carried out with good intentions because we all know that Google tracks what we do.
Whether we’re looking at the weather in the morning or simply checking out a review for a new film, Google knows about it, and it is tracking our every move.
But Why Should You Be Concerned?
So how much of a problem is that? As mentioned before, unless you’re doing anything that is obviously wrong, it’s unlikely that the FBI is going to be banging on your door in the early hours of the morning. So why should you worry?
Well, the concerning part comes in the fact that, quite simply, you are being spied on, and there’s seemingly nothing you can do about it. Whilst it has now become possible to ensure your data is no longer a Google search result, your interests, hobbies, location, photos, videos, map searches, documents, messages, and all general usage data still belongs to Google.
How Is Google Tracking You?
In a way, you are willingly giving it over to them in accordance with their privacy policy. Whenever you search for anything on the web or create a profile on social media, Google collects this data and uses it to build a detailed advertising profile. This profile will include your gender, age, job industry, and interests, and it will be used to create targeted advertising that is in line with your general tastes.
There are less obvious ways that Google tracks you, too. Namely, its constant presence in your life. If you have a Google app or product anywhere on your person, it is going to be tracking where you go. Have you ever gone on vacation and checked what movies might be playing at the moment? It’s likely that Google has listed showtimes for theatres that are closest to you. That’s because, quite simply, it knows where you are.
Why Is Google Tracking You?
So what is it doing with the information? Well, the first thing to note is that Google is not a data broker, which means your personal information is not going to be sold. But it does use your data to aid third parties. According to the Google Safety Centre, your personal information can be used to help advertisers focus their marketing campaigns, but without identifying you personally.
In terms of what you can do about this, there are inbuilt Google settings that allow you to learn more about the information being collected and even disable personalised ads altogether. As well as this, you can stop your location from being tracked by toggling “Location History” from on to off.
Does It All End With Google?
It must be noted, however, that Google is only the tip of the iceberg. Whenever you click on a site, there are a thousand more trackers that will be harnessing your information and using it for their own marketing purposes. These are known as data brokers, and the method of stopping them is a little more detailed.
But in terms of Google, it might not be tracking you for the nefarious reasons you imagine, but it is tracking you. Thankfully, adjusting your settings can go a way to limit what Google does and keep your own data a little more personal whilst browsing the web.
0 notes
Note
hello it’s BC anon I feel less confident about my Jane theory today but also I sort of feel like you’re trying to throw me off which makes me more confident about the theory🤨 so essentially I Do Not Know! I would give more evidence to support it but I feel like cass really just gave the best evidence there is and said it all like there’s really nothing else I could possibly say??? But anyway I will say this since Loki is obviously gonna be Going Through It and because fatherhood is a big part of the chapter I think those two will connect. Seeing Jane (someone Loki loves) getting pregnant so soon after Loki gets his heart broken will HURT and I feel like it’ll add to his inner turmoil bc obviously he wants so support thor and Jane he loves them and he’s so happy for them but it’s gonna make him think about kids w y/n and that’s gonna eat him up inside and he’s gonna feel like he’s not being happy enough for his family and that’s gonna eat him up inside. Anyway maybe Jane is not pregnant also I realize now I thought both y/n and Jane were pregnant so maybe I need to psychoanalyze myself I really hope I’m not projecting or something bc I am literally 21 years old so I better not secretly want to be pregnant or something
LMAO this is pemdas you know. The confidence and the confusion cancel out and you're just left with a blank space (mind?). But you are SO right that Cass gave the best piece of evidence like. I'll torture Loki and y/n all day every day in ANY of my fics but I will not put Narvi through it!! I will do the opposite. I will give him the bestest life I can 🥺
I LOVE all the points you make especially the one about Loki feeling like he isn't happy enough for his family. I think I've briefly mentioned that before but it's definitely explored in the Loki chapter. It's hard for Loki because he loves Narvi so much, but until y/n came along, he didn't have any close relationships outside his immediate family. Of course he's going to feel unfulfilled to some degree - which makes him feel bad because what father thinks that? Loki has to work on understanding it's okay to want and pursue things for himself even though he is a father. He's allowed to have his own thing (no matter what that is). I think y/n citing Loki's smaller amount of time spent with Narvi might have (unintentionally) validated this idea that Narvi trumps all. Which, to be clear, is true - Narvi IS Loki's #1 priority, as any child should be. But that frame of thinking doesn't have to be around the clock. It isn't Narvi or adult relationships outside of the family unit, it's the question of how to make those two things work together. I think these are situations Loki hasn't had time to think about for a plethora of reasons.
And do not worry BC anon I am also 21 (barely I turned 21 not even three months ago) and I can semi confidently say you probably don't secretly want to pregnant. I also had to sit down and ask myself that when I started this story at 19 years old and plotted it out bc I was like. Why am I focusing on this as someone who NEVER wants kids of her own and also has historically refused to write anything regarding pregnancy. Is this my brain telling me I want this???? I especially worried about it because I had to do a lot of research on pregnancy for the y/n reveal just to be sure I was alluding to things that could or couldn't point to her being pregnant. That late night research resulted in like two pregnancy dreams for me and I HATED it but I was so scared it meant something. I mean, it did mean something: it meant I was doing my research way too close to bedtime lmao. But yeah I wouldn't worry too much... you're just picking up on the clues I left that could very well mean your theory is correct ;)
#HELP back in december i was googling false pregnancy tests#because i was worried that two lines wasn't false#and i needed to be sure because of the chapter y/n takes the test#and we all know every app spies on our google searches#anyway because of those googling session tiktok STILL thinks i am an expecting mother all these months later#so does instagram it started recommending all these mommy and me pages#the internet is scary! but more often it's annoying lol#BC anon#asis#asis spoilers#ask
4 notes
·
View notes
Text
Ed-tech apps spy on kids

When schools switched to distance learning amid the lockdown, it represented a chance to rethink education and ed-tech, from lessons to schedules to evaluation.
For the most part, we have squandered that chance, doubling down on the most destructive educational practices.
This is true across the board, not just in ed-tech. Take the bizarre start-times for classes - as early as 7AM for students enrolled in "period 0" classes. This timing has nothing to do with best practices in pedagogy or our understanding of adolescent brain-development.
Instead, it's a least-worst option arising from the US's unwillingness to treat high-quality child-care as a public good that benefits both kids and working parents. We open our schools at o-dark-hundred because parents need to get to work.
This, despite the fact that the majority of teens' body-clocks shift nocturnally as they go through puberty. We know that waking kids up early hurts their learning outcomes, but we accept that tradeoff because the alternative (kids whose parents can't earn a living) is worse.
Virtual schools represented an opportunity to shift education to more humane hours, but we blew it. And that's the least of our failures, barely registering in comparison with the way that we failed to fix ed-tech even as it grew to eclipse all other pedagogical questions.
Exhibit A, of course, is "remote invigilation," the spyware that we force students to install on their computers in the name of preventing cheating on the pedagogically bankrupt high-stakes tests we cling to.
https://pluralistic.net/2021/04/22/ihor-kolomoisky/#copyfraud
These tools are force-multipliers for the destructive power of high-stakes testing: their junk-science "sentiment analysis" facial recognition algorithms can't recognize dark-skinned faces, forcing Black kids to sit tests with multiple lamps shining directly in their eyes.
Students forced to use tools like Proctorio are expected to rotate their webcams 360' degrees to prove they're alone in a room at home - which means that poor kids who share a room (or can only get wifi in the parking lot of a Taco Bell) are penalized for poverty.
Unsurprisingly, a company that would knowingly torment children in this way is run by terrible people and behaves terribly. It's not just that the CEO doxed a child who complained about his products on Reddit:
https://pluralistic.net/2020/07/01/bossware/#moral-exemplar
The company has also abused copyright law to sue and intimidate its critics, including a student security researcher who revealed defects in the company's products:
https://pluralistic.net/2021/04/22/ihor-kolomoisky/#copyfraud
The fact that businesses that profit by spying on children are run by awful, awful people is no surprise.
One of the most established ed-tech categories is censorware, which schools are required to install as a condition of receiving federal funds, under 1997's CDA.
This software captures every student's click and search-term, and often their chats and emails, and spies on all of it, using arbitrary word-matches and human classifications to block kids (and teachers) from seeing materials deemed "inappropriate."
The premise of this exercise is that somewhere there is a boiler-room full of prudes so large that it can look at billions and billions of webpages and decide which ones are and aren't "child-safe" and that an "AI" can pass judgment on the pages they haven't got to.
Even if you accept that bizarre premise, remember: this isn't an editorial process, it's a surveillance system. It's one thing for a school librarian to make decisions about which books to shelve, but this doesn't require them to spy on everything every kid tries to read.
For censorware companies to block your kids' data-requests, they have to intercept and examine them. Censorware is spyware. Given that, it's worth asking, "Who are we allowing to spy on our kids?
Terrible people, as it turns out.
The school censorware industry is a subsidiary of the global censorware industry, and its largest clients aren't schools - their bread and butter is the tyrants of the Middle East and former Soviet Union, dictators who buy their products to keep their citizens in line.
These are the depraved human-rights abusers we get to spy on our kids (they also provide censorware for corporate, hotel and airport wifi!), and you know what? They've got *terrible* judgment.
Independent audits of their blocklists show that they're blocking about a third of the top search results for terms related to the common curriculum, with overblocking skewed heavily to women's health, reproductive health, and LGBTQ (no surprises there).
And, like Proctorio, these censorware companies have a long history of intimidating and harassing their critics, abusing copyright law to prevent independent analysis of their blocklists in a bid to make it impossible to test whether they are any good at their jobs.
We've been spying on schoolkids' online activities since 1997, and the pandemic only accelerated that process, and not just through test proctoring, either, as a new report from the Me2B Alliance shows.
https://me2ba.org/me2ba-product-testing-spotlight-report-published-data-sharing-in-primary-secondary-school-mobile-apps-2/
The report analyzed 73 mobile apps that 38 schools in 14 US states were using as part of their administration and instruction and found that 60% of them transmit student data to commercial data-mining companies.
https://www.theregister.com/2021/05/04/school_mobile_apps/
The apps were built using "free" SDKs from Facebook, Google and other surveillance companies; these SDKs make it easy to build apps quickly, but they also harvest the app users' data at scale and subject it to long-term retention and analysis.
https://pluralistic.net/2020/09/03/rip-david-graeber/#hyas
Me2B found that the apps were sucking up "identifiers (IDFA, MAID, etc), Calendar, Contacts, Photos/Media Files, Location, Network Data (IP address), permissions related to Camera, Microphone, Device ID, and Calls."
Ios devices were far less likely to harvest user data than Android apps, but 1 in 4 still spied on users, and on both platforms, "95% of third-party data channels... are active even when the user is not signed in and that these apps send data as soon as the app is loaded."
Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY: https://creativecommons.org/licenses/by/3.0/deed.en
274 notes
·
View notes
Text
She [5]
Warnings: non-consent sex (series)
This is dark! Steve and explicit. 18+ only.
Series Synopsis: Steve Rogers’ life is turned upside down by a reporter.
Chapter Summary: The reader tries to change her course.
Note: I’m hoping to work on some other fics today and a reminder that I have a new challenge for dark!writers.
Thanks to everyone for their patience and feedback. :)
I really hope you enjoy. 💋
<3 Let me know what you think with a like or reblog or reply or an ask! Love ya!

Reader
The next day you felt more enlivened but no more detached from the mess you’d created. You ducked the hounding press outside your building and ignored the exaggerated speculation about Steve Rogers; about you. Either he was the villain and you were the innocent lamb, or he was the respectable hero targeted by the shrewish report. Either way, they were wrong. You were both just human.
You went to the office and settled into your new desk. Your goal was a sense of normalcy. You just wanted to be the nameless writer again. You needed something other than Steve Rogers. You needed a story of your own.
You opened your browser and went about scrolling through the digital newspapers and headlines of Google. You inhaled the scent of your coffee as you impatiently flicked the mouse wheel.
It wasn’t news to say there was crime in New York you mused at the Times’ small tenth-page blurb. You paused and re-read it; ‘String of Assaults Against Sex Workers Continues.’ It was no Jack the Ripper, sure, but it might be enough. There could be something there.
You needed a pitch by the end of next week if you wanted to keep up. Poppy’s tapping nails sounded in the back of your head and you sent a screen cap of the article to your phone. You clicked onto past issues and traced the story back almost three months. The first report had been almost half a page and featured the image of a particularly sinister streetlight. It was a start.
You continued your search for the hook to catch onto. Anywhere you could start. The red light district would be a start, the attacks seemed to centre around a certain street within it. You filled a folder with reports from various sources; all so distanced and apathetic. Just numbers.
You left in the afternoon. You took your new pile of distraction and headed back to your apartment. When the windows began to darken, you ordered ramen and ate at the coffee table as you sorted through the clutter. The tabletop was covered in clippings and your own notes alongside your open laptop glaring back at you.
You woke on the couch and continued in your narrowed search. You grew more and more anxious as you did. You needed to get your own look at the seedy nightlife but how? You didn’t exactly blend in and you doubted these women were eager to spend their time with some nosy reporter.
Well, you had to at least try. You found yourself watching the clock as you paced around with papers in hand. You stopped to scribble down notes every now and then. Tick, tick, tick.
You were too nervous to eat. You pulled on jeans and a faded plaid shirt. You dug out your old tennis shoes and checked yourself in the mirror. Well, you didn’t look like the stuffy journalist without a clue but you barely looked like you knew what you were doing. You slung the strap of your small purse across your chest and headed out.
It was dark by the time you stepped off the train. You could feel the nerves bouncing around your chest. You kept to the shadows, watching, afraid.
You watched a woman, not so obvious, approach a car. She wasn’t your typical Law and Order prostitute. Sure, her jeans were tight and her jacket a little short but she looked like any other woman in New York. She got in a dark car and it pulled away. It drove down the street and turned into a lot and your imagination tied it all together.
Several other women went about their transactions. You were shaken as a car honked at you and you waved the man away from the curb, careful to step clear of the glow of the streetlight. The first woman appeared again, her chunky heels echoed on the pavement as she began to her vigil again; a casual strut up and down the pavement.
You continued your observation and added notes in your phone. You edged closer without thinking as the illicit marketplace began to bustle. That same woman, the first you’d spied, surprised you as she stopped you from getting any further. She was tall and slender, her hair carefully bundled atop her head.
“New meat?” She wondered as she leaned against the edge of the storefront. You blanched at her and stepped back. “No, no, definitely not.”
“Uh, sorry,” You said softly. “I was just…” You hid your phone in your sleeve.
“Watching? Getting your thrills?” She chuckled. “Sweet little thing like you.”
You looked down, embarrassed.
“It’s okay. You think we don’t get all sorts.” She crossed her arms. “I can’t charge you for watching but maybe you were looking for more.”
“I’m not-- How much for an hour?” You perked up.
“Depends what you want.” She said coolly.
“A hundred?” You offered.
“Just out here?” She wondered.
“No, I…” You glanced around. A shining neon sign caught your eye from down the street. “A drink. I’ll pay. Plus your rate.”
“Lonely.” She mused. “Hiding?”
“Deal?” You ignored her implication.
“A hundred and a drink? I’ve done worse,” She replied.
🖋️
The bar smelled of stale alcohol and piss. The pungent odor drifted from the dingy bathrooms and filled the place. You sat across from the woman at a small round table away from the bar. She ordered Jack Daniels and you had a water. She warned you not to drink it. You didn’t.
“So, honey, what are we thinking?” She leaned on the table.
“I don’t-- I just want to talk.” You said.
“Talk? Mmm, oh you’re one of those.” She purred.
You pulled out your laminated name badge from your purse and slapped it down between you.
“I’m a reporter for Motley Magazine.” You said. “I really just want to talk.”
She sat up straight and her expression turned stringent. She looked around and shook her head.
“I can’t--”
“Please, just a conversation.” You interrupted.
“No, I could get in a lot of shit.” She hissed as she grabbed her fringed purse.
“Wait, I’ll pay double. No names, nothing that could give you away,” You stood as she did. “You say ‘stop’, we stop.”
She looked at you and inhaled. She chewed her lip and picked at the wood of the table. She sat slowly.
“One hundred now,” She said. You nodded.
“If I hit the atm over there, you still gonna be here?” You asked.
“Sure.” She took a gulp of her drink.
You went to the corner, the atm screen was cracked but still operational. You stood as close to it as you could as you slid your card in. You were careful to hide your withdrawal as you crumpled your receipt and neared the table. You sat and subtly offered the folded bills to her.
She counted it and shoved it away. She crossed her legs and leaned into the wall as if to hide herself.
“So…” She began.
You introduced yourself and she reluctantly gave you her name as you assured her it would not be included in whatever came of your conversation. Her name was Rashida but her clients knew her as Ruby. She shifted as the bar door opened and glanced over her shoulder.
“I want to know about these assaults. More than that,” You kept your voice low as she leaned in. “I want to know everything.”
“Everything?” She blinked.
“I’ve been tracking these attacks through the papers. It’s just numbers; faceless women, some men. Relegated to the back sheets.” You explained.
“For what?” She asked. “To make yourself a name?”
“No, not at all. I want you to be known. All of you. If people can contextualise the faceless, they can empathise, and that means they’ll talk.” You said. “I’m not stupid. The police, they don’t care about you, but they will care about those Upper East Siders who think they’re on some sort of crusade.”
She narrowed her eyes and shrugged. “I don’t know… much. I know Selene got it bad but haven’t seen her much since.”
“I don’t expect you to know everything, I just wanna know what you do know.” You said. “So start with Selene. Were you out that night?”
“Yeah. She wasn’t far from me, we’d talked a little. She was… excited. She had almost saved enough to get her girl into dance. She just needed a few more johns and she’d have it. It was a usual night, guys came and went, nothing out of the ordinary.”
“So when was she attacked?”
“Well, I was on a job and I got back and she was gone. I assumed she’d found her own but I never saw her again that night. I saw the article but didn’t know it was her until a few nights later. Stitches,” She traced from her forehead to her chin. “Works not so good for her now.”
“You know anyone else?” You probed.
“A few girls I see around but me and Selene, we got daughters. We try to take care of each other. Try.” She shook her head. “I… I don’t know.”
“The other girls?”
“Some of them haven’t come back after. Maybe they’re too afraid. Those who have, same thing. Sliced,” She repeated the motion down her face. “So we try to keep track of the weirdos and each other. Some girls are partnering up. One goes, the other waits until they’re back. They got these tracking apps so they can find each other.”
“Mmm,” You typed into your phone as she talked. “So you would say there’s fear?”
“There’s always fear. We see girls one night and they gone the next. It comes with the job but… something about this is so deliberate.” She said. “They’re not just hurting us but our work. Men don’t wanna look at a girl with a fucked-up face.”
“And you? Have you changed the way you work?”
“Well, of course, I’m more aware but that’s always how it is. You take note of everyone, everything. I got a thing for faces, you know? I try to memorize them.” She took another drink. “Even just those walking by. You never know.”
“Mmhmm,” You nodded as she finished the Jack. “Anything suspicious? Well, beyond the usual?”
“That’s the thing, nothing stands out. And it’s hard to tell. Half our customers are strange in one way or the other. Mostly harmless, lonely. It’s the pimps you gotta beware of…”
The hour passed quickly as Rashida spoke and you listened. She spoke more freely as the night wore on and you paid for another round. You were stunned when you looked at the clock.
“Fifteen minutes over,” You reached for your purse. “Extra twenty?”
“Whatever,” She said. “It’s… no names?”
“Promise. No names.” You paid her behind the empty glasses. “Rashida… do you think we could talk again? Maybe during the day? I’d like to get some of this on tape.”
“On tape?” Her eyes flared.
“For my own purposes. It will not be released. I’ll have you sign a waiver.” You said.
She rubbed her forehead and thought.
“I’ll pay.” You offered.
“Do you really think your story can help us?” She asked. “That these fancy New York millionaires will care?”
“I think it’s worth a try.” You stood and stretched a cramp out of your calf. “So?”
“You don’t needa pay me,” She said. “Not during the day. You just tell me where to meet you.”
“Alright,” You flicked through your phone and turned it to her, “Can I have your number?”
“Sure, babe,” She smiled and typed in her number before handing it back. “I’m gonna finish my drink. I’ll see ya ‘round.”
“I’ll be in touch,” You tapped the table as she sat back down. “Be careful, okay?”
She looked at you as she held her glass. She considered you a moment then nodded. “Thanks. I always am.”
You left her and pushed out the door. You were rarely out this late and never in this part of the city. You were suddenly very nervous. Alone. The woman had made you feel safe. She was much braver than you.
As you set off down the sidewalk, you heard your name behind you and the door swung shut. It was Rashida. She caught up to you as you turned back.
“Wait.” She pulled you close to the chipped brick wall. “I got an eye for creeps, I told ya.” She ushered you down past the bar and turned the corner. She stopped you just beyond it and held a finger to her lips and mouthed ‘listen’.
Two, maybe three, minutes and you heard the bar door. The footsteps wandered away and then returned again. She peeked around the building and drew back sharply.
“Carefully,” She squeezed your shoulder. “Look.”
You frowned and inched to the edge. You glanced around at the man in his hoodie. Tall with broad shoulders. He looked up and down the street and walked back and forth once more. He stepped out onto the street and took a slant across to the other side. He was headed for the subway; the same direction as you.
You pulled back and looked at Rashida.
“I seen him when you were hiding in the shadows. He’s better at it.” She said. “Didn’t think much, you know? As I said, the freaks come out after dark but then he came into that bar. He saw you, I could tell, was lookin’ for you. He ordered a beer but didn’t even drink it.”
The hair stood on the back of your neck.
“Following me?” You uttered.
She nodded and reached into her red jacket. She pulled out one of the twenties you’d handed her.
“Catch a cab.” She said. “And keep your eyes open. He’s good.”
“You think… you think he followed me here?” You wondered as she turned and flagged a yellow taxi.
“All I know is he wasn’t here ‘till you were.” She said. “Too bad I didn’t get a look at his face. He made sure of that.”
You watched the car pull up and you gulped.
“Thanks,” You said numbly. “I--”
“Don’t thank me, babe,” She said. “I was happy enough to keep that two hundred and finish my drink.” She opened the door. “You’re lucky I like you.”
You slid onto the seat and she closed the door. You recited your address as she backed up onto the curb and watched the taxi drive away. You sat back and let out a breath.
Were you really being followed? If so, how long had they been tailing you?
#Steve Rogers#dark steve rogers#dark!steve rogers#steve rogers x reader#dark steve rogers x reader#dark!steve rogers x reader#fic#series#she#au#dark fic#dark!fic#captain america#mcu#marvel
333 notes
·
View notes
Text
How Hack Facebook Messenger Without Any Chances Of Getting Caught?

We often consider hacking to be a forbidden activity, but hackers feel cherished to hack someone's account or password. When it comes to hacking someone’s Facebook messenger, it’s not so difficult to do.
Though hacking is not challenging, we can’t think of this, as a cup of tea. We are here to make you aware of the tricks that can possibly make the entire process of hacking easier for you.
Hacking Facebook messenger’s let you keep an eye on your child’s activities to save them from unsocial activities, as well as cyber criminals. Moreover, you can see whether your partner is loyal or not.
Facts about the hacking of Facebook passwords:-

While we think strong passwords and other codes make our account more secure, it’s not a big deal for hackers to hack it.
No matter it’s a Facebook profile or set of password, it’s not difficult to detect.
A hacker always targets weak accounts where data are non-encrypted accounts, and easy to expose.
How to hack Facebook messenger?
Hacking with Android Devices.

Hackers nowadays use a system that is extremely advanced. Since messenger is the most used aspect of Facebook, hackers solely target it instead of the Facebook account. The tool they take into use is Facebook Password Sniper. It may sound somewhat different, but functions as a controller of messenger pages.
More about Password Sniper

The password sniper aims at the establishment of a fully personalized Facebook account, as well as copying whole messenger information. This tool then, reduplicate all the mandatory information to handover to the hackers.
Majority of hackers think this technique to be reliable without any chances of getting exposed.
Apart from the chats, password sniper let you see details of video, and voice calls. Hackers can even check the date and time of message received or sent. That means, they get the right of accessing to every sensitive information associated with Facebook messenger.
Messenger spy apps to hack messenger.

If you are dying to see someone’s messages (whatever is the reason), then, you must turn your route towards software designed to do it. This software is often known as messenger spy apps used tohack Facebook Messenger.
Your single Google search will list out dozens of spy apps that claim their reliability in accessing someone’s Facebook profile. Don’t be a victim of their sugar-coated promises, analyze some of the top tools, check out their existing user’s response, and then choose the best alternative.
Based on recent studies, PowerAdspy is the tool that grabs the top position among various available spy tools. Here, evaluation becomes easy due to the provision of a free trial period. Go to its official website, register yourself, and claim for a trial session to check whether it works or not.
Instant Facebook Account Hacking.

We have earlier discussed in this article that hackers are pro at their work who don’t need to make much effort to access someone’s social media profile or personal details. They are skilled in a way that a single clickable link can expose all your details to them without knowing you.
Online spies can be found easily on all social media platforms, in most of the cases, they exist in the form of Fake accounts.
Change Password option.

If you have the credentials like email or phone number of the person who is going to be your target, you can easily step into their Facebook profile.
All you need to do is, go to Facebook, log in there to proceed. Now, click on the option of 'Forgot password'. Facebook asks you to choose an option to regain the password. Facebook asks you to choose a suitable option to regain the password. Based on the credentials you have, enter the email address or phone number to get a link. Click on the link to reset the Facebook password. Isn’t it easy?
With over 300 billion monthly active users, Facebook has become the communication mode that allows you to connect with throughout the world. Due to the population boost, hacking has become a common trend on Facebook. A hacker could be your friend, partner, parents as well an employer who doesn’t want companies confidential to go outside. And, it’s not illegal to hack messenger when reasons are genuine.
Also, Watch This Video To Design Engaging Facebook Ads:-
youtube
#facebook messenger hack#hack facebook messenger#hacking apps#messenger hacking#messenger hacking tools
1 note
·
View note
Text
Pinterest Management Services Expert Reveals Why Investing in Promoted Pins Is Not Optional
New Post has been published on https://businessguideto.com/awesome/pinterest-management-services-expert-reveals-why-investing-in-promoted-pins-is-not-optional/
Pinterest Management Services Expert Reveals Why Investing in Promoted Pins Is Not Optional
Why You Need to Include Promoted Pins in Your Pinterest Marketing Strategy in 2019
If your business has been leveraging Pinterest marketing since it’s fruition you’ve most likely grown your traffic organically. But guess what? That is all about to change. As a Pinterest Management Services expert I can suspect that as Pinterest prepares for its IPO next month that they will tighten up their algorithm to restriction organic reach and make it harder to rank high employing free organic entails. Pinterest will have no choice because they in it to make money now. They have to please their investors. They want to drive their stock price up. This is how all the insiders will cash out. You get this right?
What that means to you is you will have to invest in Pinterest ads( Promoted Pins ). It is no longer an option. It must be part of your Pinterest marketing strategy in 2019 and beyond.
Advertising on Pinterest Gives Your Brand Instant Visibility
This is especially important to those who are just starting out on Pinterest. Competition is becoming more and more fierce. Investing in ads is like saying to Pinterest “I’ll pay you if you put my products/ content in front of my target audience right now”.
If you don’t invest in Promoted Pins you have to let your content bake for some unknown amount of hour so that it shows up high on Pinterest’s search engine( Assuming you optimized your content correctly ). Bottom line, pay to get procured right away or don’t pay and hope and pray your content will rank high in search eventually.( Unless you use an expert service like ours ).
I’ll dig deeper in a bit to help you decipher how to find your competitor on Pinterest and what to look for. But first, let me give you an overview of the type of ads available to you.
4 Types of Pinterest Ads
1) If your goal is to build awareness for your business prefer “Brand awareness”. I’m not too keen on brand awareness; I don’t think it’s the best use of your marketing dollars. Traffic is what we focus on most of the time as shown below on# 3.
2) If you want to get more eyeballs on your videos select “Video views”.
3) If you want to drive more traffic to your site select “Traffic”. This is typically what we do most in our Pinterest account management services. At the end of the working day you want people going to your website or blog.
4) If you want Pinterest users to install your app, choose “App install”.
You can also target the right audience for your business. You can choose audiences, interests, keywords, or expanded targeting–or any combining of these. So what do they actually mean?
1) Audience targeting
This allows you to reach Pinterest users based on information you know about them, information that Pinterest has about them or a combination of both. You can target people on your client listings, re-target people who have visited your site or engaged with your ads or create actalikes from people who behave similarly.
2) Interest targeting
This allows you to reach Pinterest users based on the boards they have create and pins they’ve engaged with( saved or clicked ).
3) Keyword targeting
This allows you reach Pinterest users based on the keywords they are using when they’re searching for pins on Pinterest.
4) Expanded targeting
This allows you to find new Pinterest users to reach based on the content of your ad and what Pinterest knows about people on Pinterest.
8 Smart Reasons Why You Need to Spy on Your Competition
Now, let’s go over who your competition is on Pinterest. Speaking as a Pinterest Management Services expert I think it is vital that you attain the time to do this so you learn what’s driving traffic them. Watching your rivalry closely is important so :P TAGEND
you learn how new trends are embraced by the consumers you’re all fighting to keep you see how what types of content are working so you can do more of that, but better you foresee shiftings in the market you spot new trends you learn new tactics you determine what to charge for your products and/ or services you stay on the cutting edge of what’s working within your niche you keep getting better and better. Competition brings out the best in us!
How to spy on your competitor and what to look for :P TAGEND
1. Make a list of your top 5 competitors.
You can do this two ways :P TAGEND
a) Go on Google and search via their company name. When you have found their website go to their home page and look for their social icons which are typically on the bottom of the page or above the fold somewhere. Above the fold entails where the content is positioned in the upper half of a web page without scrolling down the page.
b) Or failing alternative “a” above go on Pinterest and type in their business name in the search box, then click “People” to the right of the search box.
Don’t be surprised if you don’t find them under “People” because if they have not properly optimized their Pinterest profile they won’t show up.
2) Observe what people are pinning from their website.
You can do this two ways. Let’s say you sell natural skin care products and one of your challengers is Pure Fiji.
Go to your browser and type https :// www.pinterest.com/ source/ purefiji.com /
Look at which images people are saving the most. Once you’ve identified them save them to your secret committee. Ask yourself :P TAGEND
a. Why do you think this image received a ton of engagement? What can you learn? Is it because of the type of image? For instance, is it an infographic, a checklist, does it have great text overlay, etc.
b. What can you do similar but better?
c. Is the topic evergreen or does it address people’s goals or concerns right now?
3) Use BuzzSumo
BuzzSumo will uncover what people are sharing the most. It shows your competitor’s top content in the past 24 hours and up to five years or a specific range.
4) Sign up to receive their emails
You can sign up to receive their emails or use a tool like Mailcharts. This tool can give you insight into your competitors’ email marketing, from the frequency of email sends, their subject line tactics, and more.
5) Subscribe to their blog
6) Follow them on social media
7) Shop on their site and then abandon it and see what happens
8) Purchase a product
How was your experience from the beginning up to the moment you receive the product. This will allow you to really experience their customer service. If you detest the product and would like to return it, what was your experience?
Just as Pinterest is constantly evolving so are your challengers. It’s vital that you got my eye on your rivalry every six months- it’s not something you do once and think voila I’m done. By doing a regular competitive analysis you will have a better understanding of your marketplace over hour, and learn lessons from them too. Remember…none of us knows it all.
Have you purchased Pinterest ads? If so, what was your experience? Have you spied on your rivalry? What “d you learn”?
If you’re not sure how to use buy ads or how to get started check out my step by step guide on How to Buy Pinterest Ads: How to Boost Your Performance With Promoted Pins .
The post Pinterest Management Service Expert Reveals Why Investing in Promoted Pins Is Not Optional appeared first on White Glove Social Media.
Read more: whiteglovesocialmedia.com
1 note
·
View note
Text
Optimizing a low-cost camera for machine vision
In this deep dive article, performance optimization specialist Larry Bank (a.k.a The Performance Whisperer) takes a look at the work he did for the Arduino team on the latest version of the Arduino_OV767x library.

Arduino recently announced an update to the Arduino_OV767x camera library that makes it possible to run machine vision using TensorFlow Lite Micro on your Arduino Nano 33 BLE board.
If you just want to try this and run machine learning on Arduino, you can skip to the project tutorial.
The rest of this article is going to look at some of the lower level optimization work that made this all possible. There are higher performance industrial-targeted options like the Arduino Portenta available for machine vision, but the Arduino Nano 33 BLE has sufficient performance with TensorFlow Lite Micro support ready in the Arduino IDE. Combined with an OV767x module makes a low-cost machine vision solution for lower frame-rate applications like the person detection example in TensorFlow Lite Micro.
Need for speed
Recent optimizations done by Google and Arm to the CMSIS-NN library also improved the TensorFlow Lite Micro inference speed by over 16x, and as a consequence bringing down inference time from 19 seconds to just 1.2 seconds on the Arduino Nano 33 BLE boards. By selecting the person_detection example in the Arduino_TensorFlowLite library, you are automatically including CMSIS-NN underneath and benefitting from these optimizations. The only difference you should see is that it runs a lot faster!
The CMSIS-NN library provides optimized neural network kernel implementations for all Arm’s Cortex-M processors, ranging from Cortex-M0 to Cortex-M55. The library utilizes the processor’s capabilities, such as DSP and M-Profile Vector (MVE) extensions, to enable the best possible performance.
The Arduino Nano 33 BLE board is powered by Arm Cortex-M4, which supports DSP extensions. That will enable the optimized kernels to perform multiple operations in one cycle using SIMD (Single Instruction Multiple Data) instructions. Another optimization technique used by the CMSIS-NN library is loop unrolling. These techniques combined will give us the following example where the SIMD instruction, SMLAD (Signed Multiply with Addition), is used together with loop unrolling to perform a matrix multiplication y=a*b, where
a=[1,2]
and
b=[3,5 4,6]
a, b are 8-bit values and y is a 32-bit value. With regular C, the code would look something like this:
for(i=0; i<2; ++i) for(j=0; j<2; ++j) y[i] += a[j] * b[j][i]
However, using loop unrolling and SIMD instructions, the loop will end up looking like this:
a_operand = a[0] | a[1] << 16 // put a[0], a[1] into one variable for(i=0; i<2; ++i) b_operand = b[0][i] | b[1][i] << 16 // vice versa for b y[i] = __SMLAD(a_operand, b_operand, y[i])
This code will save cycles due to
fewer for-loop checks
__SMLAD performs two multiply and accumulate in one cycle
This is a simplified example of how two of the CMSIS-NN optimization techniques are used.
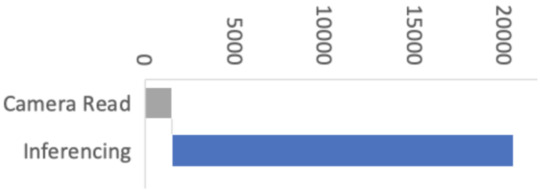
Figure 1: Performance with initial versions of libraries
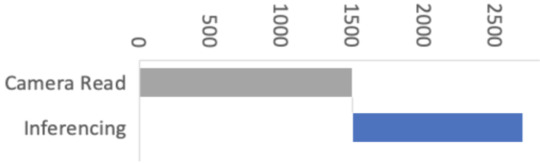
Figure 2: Performance with CMSIS-NN optimizations
This improvement means the image acquisition and preprocessing stages now have a proportionally bigger impact on machine vision performance. So in Arduino our objective was to improve the overall performance of machine vision inferencing on Arduino Nano BLE sense by optimizing the Arduino_OV767X library while maintaining the same library API, usability and stability.

Figure 3: Performance with CMSIS-NN and camera library optimizations
For this, we enlisted the help of Larry Bank who specializes in embedded software optimization. Larry’s work got the camera image read down from 1500ms to just 393ms for a QCIF (176×144 pixel) image. This was a great improvement!
Let’s have a look at how Larry approached the camera library optimization and how some of these techniques can apply to your Arduino code in general.
Performance optimizing Arduino code
It’s rarely practical or necessary to optimize every line of code you write. In fact there are very good reasons to prioritize readable, maintainable code. Being readable and optimized don’t necessarily have to be mutually exclusive. However, embedded systems have constrained resources, and when applications demand more performance, some trade-offs might have to be made. Sometimes it is necessary to restructure algorithms, pay attention to compiler behavior, or even analyze timing of machine code instructions in order to squeeze the most out of a microcontroller. In some cases this can make the code less readable — but the beauty of an Arduino library is that this can be abstracted (hidden) from user sketch code beneath the cleaner library function APIs.
What does “Camera.readFrame” do?
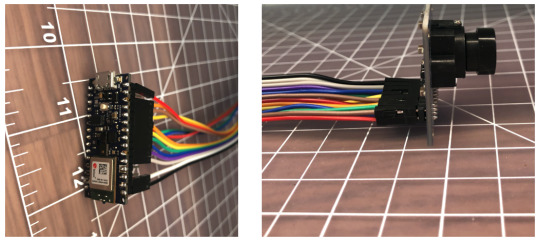
We’ve connected a camera to the Arduino. The Arduino_OV767X library sets up the camera and lets us transfer the raw image data from the camera into the Arduino Nano BLE memory. The smallest resolution setting, QCIF, is 176 x 144 pixels. Each pixel is encoded in 2 bytes. We therefore need to transfer at least 50688 bytes (176 x 144 x 2 ) every time we capture an image with Camera.readFrame. Because the function is performing a byte read operation over 50 thousand times per frame, the way it’s implemented has a big impact on performance. So let’s have a look at how we can most efficiently connect the camera to the Arduino and read a byte of data from it.
Philosophy
I tend to see the world of code through the “lens” of optimization. I’m not advocating for everyone to share my obsession with optimization. However, when it does become necessary, it’s helpful to understand details of the target hardware and CPU. What I often encounter with my clients is that their code implements their algorithm neatly and is very readable, but it’s not necessarily ‘performance friendly’ to the target machine. I assume this is because most people see code from a top-down approach: they think in terms of the abstract math and how to process the data. My history in working with very humble machines and later turning that into a career has flipped that narrative on its head. I see software from the bottom up: I think about how the memory, I/O and CPU registers interact to move and process the data used by the algorithm. It’s often possible to make dramatic improvements to the code execution speed without losing any of its readability. When your readable/maintainable solution still isn’t fast enough, the next phase is what I call ‘uglification.’ This involves writing code that takes advantage of specific features of the CPU and is nearly always more difficult to follow (at least at first glance!).
Optimization methodology
Optimization is an iterative process. I usually work in this order:
Test assumptions in the algorithm (sometimes requires tracing the data)
Make innocuous changes in the logic to better suit the CPU (e.g. change modulus to logical AND)
Flatten the hierarchy or simplify overly nested classes/structures
Test any slow/fast paths (aka statistics of the data — e.g. is 99% of the incoming data 0?)
Go back to the author(s) and challenge their decisions on data precision / storage
Make the code more suitable for the target architecture (e.g. 32 vs 64-bit CPU registers)
If necessary (and permitted by the client) use intrinsics or other CPU-specific features
Go back and test every assumption again
If you would like to investigate this topic further, I’ve written a more detailed presentation on Writing Performant C++ code.
Depending on the size of the project, sometimes it’s hard to know where to start if there are too many moving parts. If a profiler is available, it can help narrow the search for the “hot spots” or functions which are taking the majority of the time to do their work. If no profiler is available, then I’ll usually use a time function like micros() to read the current tick counter to measure execution speed in different parts of the code. Here is an example of measuring absolute execution time on Arduino:
long lTime; lTime = micros(); <do the work> iTime = micros() - lTime; Serial.printf(“Time to execute xxx = %d microseconds\n”, (int)lTime);
I’ve also used a profiler for my optimization work with OpenMV. I modified the embedded C code to run as a MacOS command line app to make use of the excellent XCode Instruments profiler. When doing that, it’s important to understand how differently code executes on a PC versus embedded — this is mostly due to the speed of the CPU compared to the speed of memory.
Pins, GPIO and PORTs
One of the most powerful features of the Arduino platform is that it presents a consistent API to the programmer for accessing hardware and software features that, in reality, can vary greatly across different target architectures. For example, the features found in common on most embedded devices like GPIO pins, I2C, SPI, FLASH, EEPROM, RAM, etc. have many diverse implementations and require very different code to initialize and access them.
Let’s look at the first in our list, GPIO (General Purpose Input/Output pins). On the original Arduino Uno (AVR MCU), the GPIO lines are arranged in groups of 8 bits per “PORT” (it’s an 8-bit CPU after all) and each port has a data direction register (determines if it’s configured for input or output), a read register and a write register. The newer Arduino boards are all built around various Arm Cortex-M microcontrollers. These MCUs have GPIO pins arranged into groups of 32-bits per “PORT” (hmm – it’s a 32-bit CPU, I wonder if that’s the reason). They have a similar set of control mechanisms, but add a twist — they include registers to SET or CLR specific bits without disturbing the other bits of the port (e.g. port->CLR = 1; will clear GPIO bit 0 of that port). From the programmer’s view, Arduino presents a consistent set of functions to access these pins on these diverse platforms (clickable links below to the function definitions on Arduino.cc):
pinMode(pin, mode); digitalRead(pin); digitalWrite(pin, value);
For me, this is the most powerful idea of Arduino. I can build and deploy my code to an AVR, a Cortex-M, ESP8266 or an ESP32 and not have to change a single line of code nor maintain multiple build scripts. In fact, in my daily work (both hobby and professional), I’m constantly testing my code on those 4 platforms. For example, my LCD/OLED display library (OneBitDisplay) can control various monochrome LCD and OLED displays and the same code runs on all Arduino boards and can even be built on Linux.
One downside to having these ‘wrapper’ functions hide the details of the underlying implementation is that performance can suffer. For most projects it’s not an issue, but when you need to get every ounce of speed out of your code, it can make a huge difference.
Camera data capture
One of the biggest challenges of this project was that the original OV7670 library was only able to run at less than 1 frame per second (FPS) when talking to the Nano 33. The reason for the low data rate is that the Nano 33 doesn’t expose any hardware which can directly capture the parallel image data, so it must be done ‘manually’ by testing the sync signals and reading the data bits through GPIO pins (e.g. digitalRead) using software loops. The Arduino pin functions (digitalRead, digitalWrite) actually contain a lot of code which checks that the pin number is valid, uses a lookup table to convert the pin number to the I/O port address and bit value and may even disable interrupts before reading or changing the pin state. If we were to use the digitalRead function for an application like this, it would limit the data capture rate to be too slow to operate the camera. You’ll see this further down when we examine the actual code used to capture the data.
First, a quick review of the OV7670 camera module: According to its datasheet, it’s capable of capturing a VGA (640×480) color image at up to 30 FPS. The kit used for this project has the camera mounted to a small PCB and presents an 8-bit parallel data bus and various sync signals.

It requires an external “master clock” (MCLK in the photo) to drive its internal state machine which is used to generate all of the other timing signals. The Nano 33 can provide this external clock source by using its I2S clock. The OV767X library sets this master clock to 16Mhz (the camera can handle up to 48Mhz) and then there is a set of configuration registers to divide this value to arrive at the desired frame rate. Only a few possible frame rates are available (1, 5, 10, 15, 20, and 30 FPS).

Above is one of the timing diagrams from the OV7670 datasheet. This particular drawing shows the timing of the data for each byte received along each image row. The HREF signal is used to signal the start and end of a row and then each byte is clocked in with the PCLK signal. The original library code read each bit (D0-D7) in a loop and combined them together to form each data byte. The image data comes quickly, so we have very little time to read each byte. Assembling them one bit at a time is not very efficient. You might be thinking that it’s not that hard of a problem to solve on the Nano 33. After all, it has 22 GPIO pins and the Cortex-M inside it has 32-bit wide GPIO ports, so just hook up the data bits sequentially and you’ll be able to read the 8 data bits in one shot, then Mission Accomplished

. If only things were that easy. The Nano 33 does have plenty of GPIO pins, but there isn’t a continuous sequence of 8 bits available using any of the pins! I’m guessing that the original code did it one bit at a time because it didn’t look like there was a better alternative. In the pinout diagram below, please notice the P0.xx and P1.xx numbers. These are the Cortex-M GPIO port 0 and 1-bit numbers (other Cortex-M processors would label them PA and PB).
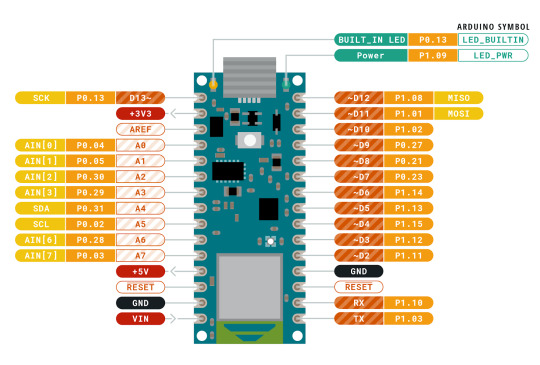
I wasn’t going to let this little bump in the road stop me from making use of bit parallelism. If you look carefully at the bit positions, the best continuous run we can get is 6 bits in a row with P1.10 through P1.15. It’s not possible to read the 8 data bits in one shot…or is it? If we connect D0/D1 of the camera to P1.02/P1.03 and D2-D7 to P1.10-P1.15, we can do a single 32-bit read from port P1 and get all 8 bits in one shot. The bits are in order, but will have a gap between D1 and D2 (P1.04 to P1.09). Luckily the Arm CPU has what’s called a barrel shifter. It also has a smart instruction set which allows data to be shifted ‘for free’ at the same time the instruction is doing something else. Let’s take a look at how and why I changed the code:
Original:
uint8_t in = 0; for (int k = 0; k < 8; k++) { bitWrite(in, k, (*_dataPorts[k] & _dataMasks[k]) != 0); }
Optimized:
uint32_t in = port->IN; // read all bits in parallel in >>= 2; // place bits 0 and 1 at the "bottom" of the register in &= 0x3f03; // isolate the 8 bits we care about in |= (in >> 6); // combine the upper 6 and lower 2 bits
Code analysis
If you’re not interested in the nitty gritty details of the code changes I made, you can skip this section and go right to the results below.First, let’s look at what the original code did. When I first looked at it, I didn’t recognize bitWrite; apparently it’s not a well known Arduino bit manipulation macro; it’s defined as:
#define bitWrite(value, bit, bitvalue) (bitvalue ? bitSet(value, bit) : bitClear(value, bit))
This macro was written with the intention of being used on GPIO ports (the variable value) where the logical state of bitvalue would be turned into a single write of a 0 or 1 to the appropriate bit. It makes less sense to be used on a regular variable because it inserts a branch to switch between the two possible outcomes. For the task at hand, it’s not necessary to use bitClear() on the in variable since it’s already initialized to 0 before the start of each byte loop. A better choice would be:
if (*_dataPorts[k] & _dataMasks[k]) in |= (1 << k);
The arrays _dataPorts[] and _dataMasks[] contain the memory mapped GPIO port addresses and bit masks to directly access the GPIO pins (bypassing digitalRead). So here’s a play-by-play of what the original code was doing:
Set in to 0
Set k to 0
Read the address of the GPIO port from _dataPorts[] at index k
Read the bit mask of the GPIO port from _dataMasks[] at index k
Read 32-bit data from the GPIO port address
Logical AND the data with the mask
Shift 1 left by k bits to prepare for bitClear and bitSet
Compare the result of the AND to zero
Branch to bitSet() code if true or use bitClear() if false
bitClear or bitSet depending on the result
Increment loop variable k
Compare k to the constant value 8
Branch if less back to step 3
Repeat steps 3 through 13, 8 times
Store the byte in the data array (not shown above)
The new code does the following:
Read the 32-bit data from the GPIO port address
Shift it right by 2 bits
Logical AND (mask) the 8 bits we’re interested in
Shift and OR the results to form 8 continuous bits
Store the byte in the data array (not shown above)
Each of the steps listed above basically translates into a single Arm instruction. If we assume that each instruction takes roughly the same amount of time to execute (mostly true on Cortex-M), then old vs. new is 91 versus 5 instructions to capture each byte of camera data, an 18x improvement! If we’re capturing a QVGA frame (320x240x2 = 153600 bytes), that becomes many millions of extra instructions.
Results
The optimized byte capture code translates into 5 Arm instructions and allows the capture loop to now handle a setting of 5 FPS instead of 1 FPS. The FPS numbers don’t seem to be exact, but the original capture time (QVGA @ 1 FPS) was 1.5 seconds while the new capture time when set to 5 FPS is 0.393 seconds. I tested 10 FPS, but readFrame() doesn’t read the data correctly at that speed. I don’t have an oscilloscope handy to probe the signals to see why it’s failing. The code may be fast enough now (I think it is), but the sync signals may become too unstable at that speed. I’ll leave this as an exercise to the readers who have the equipment to see what happens to the signals at 10 FPS.
For the work I did on the OV767X library, I created a test fixture to make sure that the camera data was being received correctly. For ML/data processing applications, it’s not necessary to do this. The built-in camera test pattern can be used to confirm the integrity of the data by using a CRC32.

My tinned protoboard test fixture with 320×240 LCD
Note: The frames come one immediately after another. If you capture a frame and then do some processing and then try to capture another frame, you may hit the middle of the next frame when you call readFrame(). The code will then wait until the next VSync signal, so that frame’s capture time could be as much as 2x as long as a single frame time.
More tips
I enjoy testing the limits of embedded hardware, especially when it involves bits, bytes and pixels. I’ve written a few blog posts that explore the topics of speed and power usage if you’re interested in learning more about it.
Conclusion
The embedded microcontrollers available today are capable of handling jobs that were unimaginable just a few years ago.
Optimized ML solutions from Google and Edge Impulse are capable of running on low-cost, battery-powered boards (vision, vibration, audio, whatever sensor you want to monitor).
Python and Arduino programming environments can test your project idea with little effort.
Software can be written an infinite number of ways to accomplish the same task, but one constant remains: TANSTATFC (there ain’t no such thing as the fastest code).
Never assume the performance you’re seeing is what you’re stuck with. Think of existing libraries and generic APIs available through open source libraries and environments as a starting point.
Knowing a bit of info about the target platform can be helpful, but it’s not necessary to read the MCU datasheet. In the code above, the larger concept of Arm Cortex-M 32-bit GPIO ports was sufficient to accomplish the task without knowing the specifics of the nRF52’s I/O hardware.
Don’t be afraid to dig a little deeper and test every assumption.
If you encounter difficulties, the community is large and there are a ton of resources out there. Asking for help is a sign of strength, not weakness.
Optimizing a low-cost camera for machine vision was originally published on PlanetArduino
0 notes
Text
Your smartphone or mobile device may be recording everything you say.
CLOSE

Corrections & Clarifications: A previous version of this story referenced an unproven claim about smart devices recording voice data.
The scene plays out like a thriller: You pull out your phone, and you see an ad for AirPods.
Wait a minute, you think. Didn’t I just have a conversation about AirPods with my friend? Like, a real conversation, spoken aloud? Is my phone … listening to me?
Why, yes, it probably is. When you use your default settings, everything you say may be recorded through your device’s onboard microphone. While there’s been no concrete evidence, many Americans believe their phones routinely collect their voice data and use it for marketing purposes.
As a “prime” example, tap or click here to see what Amazon does with the voice data it harvests and how you can stop Alexa from listening.
Your phone isn’t the only device that’s watching and listening to you. The FBI warns hackers can take over your smart TV if you don’t secure it. Tap or click to learn how to take control of your privacy on your TV before it’s too late.
Talking Tech newsletter: Jeff Graham’s weekly take on all that’s hot in tech. Sign up here
Do I really want to give? When a happy birthday wish on Facebook turns into a request for donations
Before you ask, yes, it’s perfectly legal, and developers claim not to abuse this practice. But that doesn’t mean you have to like it; many people are startled to see ads for things they have only spoken about, not search for on their browsers. Luckily, there are ways to stop your devices from eavesdropping on you.
Whispering (marketing) campaigns
When you think about it, smartphones are equipped with an arsenal of monitoring equipment: multiple microphones and cameras are designed to absorb audio and video. While these tools may be useful for creating media, they are also a goldmine for advertisers.
In mid-2018, a reporter for Vice experimented to see just how closely smartphones listen to our conversations. To test his phone, the journalist spoke preselected phrases twice a day for five days in a row. Meanwhile, he monitored his Facebook feed to see if any changes occurred.
Sure enough, the changes seemed to arrive overnight. One of his test phrases involved going “back to university,” and by the next morning, the reporter saw ads for summer courses. He then changed up his test phrase to “cheap shirts” and quickly saw advertisements for low-cost apparel on his Facebook feed.
This report triggered a wave of studies on the surveillance effects of social media platforms.
While not every study provided clear answers, a general sense of agreement on the matter was reached due to hints in the User Agreements of several apps and social media platforms. Tap or click for an easy way to spot what’s hiding in the User Agreement of your favorite platforms.
These user agreements explicitly state recorded audio may be used for targeted advertising purposes. Interestingly, such practices aren’t against the law. This action allows tech companies to push privacy boundaries even further to encourage us to buy things we don’t need.
CLOSE

What can I do about being spied on?
If you’re not comfortable with targeted ads, there are ways to mitigate your smartphone’s spy power. That said, you may lose access to some handy features like wake words and voice assistants, so you’ll have to decide whether these features are worth sacrificing your privacy.
The biggest vulnerability comes from the “always-on” feature of most voice assistants. To pick up wake words like “Hey Siri,” the mic needs to remain on at all times – which means your phone is always listening.
The best place to start taking your privacy back is by turning off the “always-on” microphone features on your handset. Here’s how to do it:
Deactivate “Hey Siri”
Apple has come under fire for transcribing audio recordings of Siri users. The data is locally stored on your device and is uploaded once Siri is activated, so disabling this feature will at least make your Siri inputs shorter and more specific to your requests.
To turn off “Hey Siri,” navigate to your iOS device’s Settings, followed by Siri & Search. Then, toggle Listen for “Hey Siri” to Off.
Disable “OK Google”
Every time you use “OK Google,” or use another voice-controlled function, your query is recorded, and the transcripts are saved to your Google account. Tap or click here to learn how to remove these recordings and other info you don’t want Google to store.
If you use Google Assistant on Android, open the Google Assistant Settings. Say, “OK Google” or hold down the phone’s home button, then tap the file drawer icon found on the upper right-hand corner, and tap the three-dot menu. Select More and choose Settings.
From this point, you’ll want to scroll down to the devices category and select your phone, then in the Google Assistant section near the top, tap the blue slider button to change it gray, which turns off Google Assistant.
Disable mic access for apps
Disabling the always-on microphone features from your phone isn’t enough for some apps like Facebook. The social site makes exceptions to the rule and will keep on listening unless you make the change.
This is just one of the many privacy settings you really should be using if you have a Facebook account. Tap or click for more ways to lock down your profile.
Here’s how you can turn audio recording off for Facebook, but the same steps apply for any app that uses the microphone:
iPhone
Go to Settings >> Facebook >> Settings in the sub-menu. Slide the Microphone switch to the left, so it turns from green to white. That turns it off. Alternatively, you can go to Settings >> Privacy >> Microphone then look for Facebook to do the same. Note that you can toggle the mic on and off for other apps, too.
Android
Open Settings, then choose Applications and Application Manager. Look for Facebook, and tap App Permissions, then toggle the microphone off.
Keep in mind, turning off Facebook’s microphone access will affect and disable certain features like Live Video. If you’re going to use these features, you will have to toggle the mic back on. Follow the same steps above, but make sure the toggle is set to On, and you’ll be good to go.
Bonus tip for more know-how:
Amazon has previously come under fire for violating the privacy of its users with Alexa. The famous voice assistant was revealed to be recording users’ inquiries and storing the recordings for human reviewers to analyze. The exposure caused Amazon to make several drastic changes to its products and privacy policy.
Tap or click here for 3 new Alexa privacy settings you need to know about.
Learn about all the latest technology on the Kim Komando Show, the nation’s largest weekend radio talk show. Kim takes calls and dispenses advice on today’s digital lifestyle, from smartphones and tablets to online privacy and data hacks. For her daily tips, free newsletters and more, visit her website at Komando.com.
Read or Share this story: http://bit.ly/35ICLkz
Sahred From Source link Technology
from WordPress http://bit.ly/34Icth0 via IFTTT
0 notes
Link
By Geoffrey A. Fowler | The Washington Post Columnist You open your browser to look at the web. Do you know who is looking back at you? Over a recent week of web surfing, I peered under the hood of Google Chrome and found it brought along a few thousand friends. Shopping, news and even government sites quietly tagged my browser to let ad and data companies ride shotgun while I clicked around the web. This was made possible by the web’s biggest snoop of all: Google. Seen from the inside, its Chrome browser looks a lot like surveillance software. Lately I’ve been investigating the secret life of my data, running experiments to see what technology really is up to under the cover of privacy policies that nobody reads. It turns out, having the world’s biggest advertising company make the most-popular web browser was about as smart as letting kids run a candy shop. It made me decide to ditch Chrome for a new version of nonprofit Mozilla’s Firefox, which has default privacy protections. Switching involved less inconvenience than you might imagine. My tests of Chrome versus Firefox unearthed a personal data caper of absurd proportions. In a week of web surfing on my desktop, I discovered 11,189 requests for tracker “cookies” that Chrome would have ushered right onto my computer, but were automatically blocked by Firefox. These little files are the hooks that data firms, including Google itself, use to follow what websites you visit so they can build profiles of your interests, income and personality. Chrome welcomed trackers even at websites you’d think would be private. I watched Aetna and the Federal Student Aid website set cookies for Facebook and Google. They surreptitiously told the data giants every time I pulled up the insurance and loan service’s log-in pages. And that’s not the half of it. Look in the upper right corner of your Chrome browser. See a picture or a name in the circle? If so, you’re logged in to the browser, and Google might be tapping into your web activity to target ads. Don’t recall signing in? I didn’t, either. Chrome recently started doing that automatically when you use Gmail. Chrome is even sneakier on your phone. If you use Android, Chrome sends Google your location every time you conduct a search. (If you turn off location sharing it still sends your coordinates out, just with less accuracy.) Firefox isn’t perfect – it still defaults searches to Google and permits some other tracking. But it doesn’t share browsing data with Mozilla, which isn’t in the data-collection business. At a minimum, web snooping can be annoying. Cookies are how a pair of pants you look at in one site end up following you around in ads elsewhere. More fundamentally, your web history – like the color of your underpants – ain’t nobody’s business but your own. Letting anyone collect that data leaves it ripe for abuse by bullies, spies and hackers. Google’s product managers told me in an interview that Chrome prioritizes privacy choices and controls, and they’re working on new ones for cookies. But they also said they have to get the right balance with a “healthy web ecosystem” (read: ad business). Firefox’s product managers told me they don’t see privacy as an “option” relegated to controls. They’ve launched a war on surveillance, starting this month with “enhanced tracking protection” that blocks nosy cookies by default on new Firefox installations. But to succeed, first Firefox has to convince people to care enough to overcome the inertia of switching. It’s a tale of two browsers – and the diverging interests of the companies that make them. The cookie fight A decade ago, Chrome and Firefox were taking on Microsoft’s lumbering giant Internet Explorer. The upstart Chrome solved real problems for consumers, making the web safer and faster. Today it dominates more than half the market. Lately, however, many of us have realized that our privacy is also a major concern on the web – and Chrome’s interests no longer always seem aligned with our own. That’s most visible in the fight over cookies. These code snippets can do some helpful things, like remembering the contents of your shopping cart. But now many cookies belong to data companies, which use them to tag your browser so they can follow your path like crumbs in the proverbial forest. They’re everywhere – one study found third-party tracking cookies on 92 percent of websites. The Washington Post website has about 40 tracker cookies, average for a news site, which the company said in a statement are used to deliver better-targeted ads and track ad performance. You’ll also find them on sites without ads: Both Aetna and the FSA service said the cookies on their sites help measure their own external marketing campaigns. The blame for this mess belongs to the entire advertising, publishing and tech industries. But what responsibility does a browser have in protecting us from code that isn’t doing much more than spying? In 2015, Mozilla debuted a version of Firefox that included anti-tracking tech, turned on only in its “private” browsing mode. After years of testing and tweaking, that’s what it activated this month on all websites. This isn’t about blocking ads – those still come through. Rather, Firefox is parsing cookies to decide which ones to keep for critical site functions and which ones to block for spying. Apple’s Safari browser, used on iPhones, also began applying “intelligent tracking protection” to cookies in 2017, using an algorithm to decide which ones were bad. Chrome, so far, remains open to all cookies by default. Last month, Google announced a new effort to force third-party cookies to better self-identify, and said we can expect new controls for them after it rolls out. But it wouldn’t offer a timeline or say whether it would default to stopping trackers. I’m not holding my breath. Google itself, through its Doubleclick and other ad businesses, is the No. 1 cookie maker – the Mrs. Fields of the web. It’s hard to imagine Chrome ever cutting off Google’s moneymaker. “Cookies play a role in user privacy, but a narrow focus on cookies obscures the broader privacy discussion because it’s just one way in which users can be tracked across sites,” said Ben Galbraith, Chrome’s director of product management. “This is a complex problem, and simple, blunt cookie blocking solutions force tracking into more opaque practices.” There are other tracking techniques – and the privacy arms race will get harder. But saying things are too complicated is also a way of not doing anything. “Our viewpoint is to deal with the biggest problem first, but anticipate where the ecosystem will shift and work on protecting against those things as well,” said Peter Dolanjski, Firefox’s product lead. Both Google and Mozilla said they’re working on fighting “fingerprinting,” a way to sniff out other markers in your computer. Firefox is already testing its capabilities, and plans to activate them soon. Making the switch Choosing a browser is no longer just about speed and convenience – it’s also about data defaults. It’s true that Google usually obtains consent before gathering data, and offers a lot of knobs you can adjust to opt out of tracking and targeted advertising. But its controls often feel like a shell game that results in us sharing more personal data. Get breaking news and alerts with our free mobile app. Get it from the Apple app store or the Google Play store. I felt hoodwinked when Google quietly began signing Gmail users into Chrome last fall. Google says the Chrome shift didn’t cause anybody’s browsing history to be “synced” unless they specifically opted in – but I found mine was being sent Google, and don’t recall ever asking for extra surveillance. (You can turn off the Gmail auto-login by searching “Gmail” in Chrome settings and switching off “Allow Chrome sign-in.”) After the sign-in shift, Johns Hopkins professor Matthew Green made waves in the computer science world when he blogged he was done with Chrome. “I lost faith,” he told me. “It only takes a few tiny changes to make it very privacy unfriendly.” There are ways to defang Chrome, which is much more complicated than just using “Incognito Mode.” But it’s much easier to switch to a browser not owned by an advertising company. Like Green, I’ve chosen Firefox, which works across phones, tablets, PCs and Macs. Apple’s Safari is also a good option on Macs, iPhones and iPads, and the niche Brave browser goes even further in trying to jam the ad-tech industry. What does switching to Firefox cost you? It’s free, and downloading a different browser is much simpler than changing phones. In 2017, Mozilla launched a new version of Firefox called Quantum that made it considerably faster. In my tests, it has felt almost as fast as Chrome, though benchmark tests have found it can be slower in some contexts. Firefox says it’s better about managing memory if you use lots and lots of tabs. Switching means you’ll have to move your bookmarks, and Firefox offers tools to help. Shifting passwords is easy if you use a password manager. And most browser add-ons are available, though it’s possible you won’t find your favorite. Mozilla has challenges to overcome. Among privacy advocates, the nonprofit is known for caution. It took a year longer than Apple to make cookie blocking a default. And as a nonprofit, it earns money when people make searches in the browser and click on ads – which means its biggest source of income is Google. Mozilla’s CEO says the company is exploring new paid privacy services to diversify its income. Its biggest risk is that Firefox might someday run out of steam in its battle with the Chrome behemoth. Even though it’s the No. 2 desktop browser, with about 10 percent of the market, major sites could decide to drop support, leaving Firefox scrambling. If you care about privacy, let’s hope for another David and Goliath outcome.
0 notes
Photo

You know the real issue is that it's not so much Google, but app developers. Your apps have the ability to use your location services. For example, Google offers Google maps and some other default Google apps like Google Search and Google Home, but things like Facebook, Instagram, Tinder, Snapchat, Dominoes, etc. All have their own privacy settings. Google's most recent update is giving your reminders and more control over how these apps use your data to "spy" on you. Let's be honest with ourselves. Their are satellites that know our movements, and if you own an iPhone and you are Google searching someone is getting your personal results if you are not using incognito mode. If you are on WiFi your ISP is getting your search history. Privacy is this huge illusion and if you are not 100 percent of the time taking every counter measure to protect your data and your privacy then you are being spied on. I am tired of seeing this "Google knows my every move and is spying on me" bullshit. Or "Hah I have an iPhone I have more privacy" I can tell you no from an information security standpoint most people are giving away some form of private data albeit PC, Android, or iOS. A digital forensics teacher of my State just showed off a method he and a few interns worked together on to get data from both an Apple Watch and Samsung Gear Watch. The real issue is Google is saying "you know what we look shady and want to fix our mistakes. Everyone should have privacy and it should be affordable." Mean while Apple is using "Privacy" as a marketing scheme and tactic to make more consumers stick to their products or buy their products. "If you don't want to share your data... Buy our 1000 dollar phone or pay a ton of money for our services.. ohhh if you don't have the money buy our iPhone XR it's at an affordable price of 750." All I'm saying is "Google stop spying on me" is just a phrase led with paranoia and the idea that someone is protected if they just don't use Google and it's flat out wrong. #entrepreneurlife #startup #workhardplayhard #patna #digiwalebabu #digitalmarketing #growingbusines #internetprivacy #googleranking (at Patna New City, Bihār, India) https://www.instagram.com/p/BxNeu64lBCn/?utm_source=ig_tumblr_share&igshid=1hz8cd4labqi0
#entrepreneurlife#startup#workhardplayhard#patna#digiwalebabu#digitalmarketing#growingbusines#internetprivacy#googleranking
0 notes
Text
Networking Quotes
Official Website: Networking Quotes
• A good browser, apps, good camera, and fast networking in your smartphone is just expected today. – Thorsten Heins • A man of substance should trust very carefully an online networking friend whose shared images are not often palatable to his taste. – Anuj • A new survey found that 12 percent of parents punish their kids by banning social networking sites. The other 88 percent punish their kids by joining social networking sites.- Jimmy Fallon • A technology becomes truly disruptive when it drives the marginal cost of something that used to be scarce and expensive to approach zero. Thus, it used to be to deploy software at scale, you had to fund a data center, buy a set of servers, storage, and networking gear, build an in-house IT management capability, and buy an expensive stack of enabling software before you could even get started. Now you can get all that from Amazon or Microsoft on a pay-as-you-grow model. – Geoffrey Moore • Anyone can use these sites – companies and colleges, teachers and students, young and old all make use of networking sites to connect with people electronically to share pictures, information, course work, and common interests. – Mike Fitzpatrick • As information technology becomes millions of times more powerful, any particular use of it becomes correspondingly cheaper. Thus, it has become commonplace to expect online services (not just news, but 21st century treats like search or social networking) to be given for free, or rather, in exchange for acquiescence to being spied on. – Jaron Lanier • As IT enters the mobile-cloud era, IT providers need to be more innovative about addressing customers’ fast changing needs. Over the past two years, Cisco and Citrix have collaborated to deliver significant innovation into the market. Now we are excited to accelerate our partnership into cloud, networking and mobility. – Padmasree Warrior
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'Network', orderby: 'rand', order: 'DESC', template: '1', limit: '68', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_network').html(obj); jQuery('#thelovesof_network img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); ); • Being in New York and having worked at Time Out New York and then being at Time, living in New York for a long time has helped because I know everybody. And they’re the people who call me and give me jobs. So that kind of real networking, which is just living in a place and having jobs where people around you are extremely successful, has helped me tremendously. – Joel Stein • Best results are often achieved well before you need a job, by consistently networking so that when you find yourself job-hunting you have a large network to work with. – Erik Qualman • Brooklyn is where I primarily developed. I had an opportunity to make records and perform in clubs here and there, and I started networking with the right people in the right places. – Busta Rhymes • Bullying behaviour can be communicated via text, mobile phones, internet, social networking sites, forums. But we can’t limit it because these messages are then reinforced by television which glamorises yelling, swearing and vulgar behaviour as the way to walk the red carpet of acceptance. – Louise Burfitt-Dons • Business culture operates differently in different cities around the world. But I don’t think it’s possible to design one system that incorporates all social norms for networking. Human beings are just too diverse. – danah boyd • Conservatively, I am saying that social networking has made being in a band more fun, but not necessarily changed how the business works. – Chris Cain • Create a website that expresses something about who you are that won’t fit into the template available to you on a social networking site. – Jaron Lanier • Despite all the hype about local or green food, the single biggest impediment to wider adoption is not research, programs, organizations, or networking. It is the demonizing and criminalizing of virtually all indigenous and heritage-based food practices. – Joel Salatin • Facebook and other social networking sites are bringing together spheres that used to be separate. People no longer have private and public lives; the line between the two is becoming blurred. – Paul Achleitner • Facebook is shaping a broader web. If you look back for the past five or seven years, the story about social networking has really been about getting people connected… But if you look forward for the next five years, I think that the story people are going to remember five years from now isn’t how this one site was built; it is how every single service that you use is now going to be better with your friends. – Mark Zuckerberg • Figure out what you are meant to contribute to the world and make sure you contribute it. If this requires public speaking or networking or other activities that make you uncomfortable, do them anyway. But accept that they’re difficult, get the training you need to make them easier, and reward yourself when you’re done. – Susan Cain • First, you have to be visible in the community. You have to get out there and connect with people. It’s not called net-sitting or net-eating. It’s called networking. You have to work at it. – Ivan Misner • For almost the first year of The Muse’s life, I would do 5 to 8 networking events a week. And I don’t necessarily think that’s the right path for everyone, but I realized that as an entrepreneur, one of my strengths was finding the right people who could help us. I didn’t come into startups with any network. – Kathryn Minshew • For people choosing to use a network marketing system to build a business in the B quadrant, the price of entry is a lot lower, the risks are lower, and the education and support are there to guide you through this personal development process. – Robert Kiyosaki • For the music business, social networking is brilliant. Just when you think it’s doom and gloom and you have to spend millions of pounds on marketing and this and that, you have this amazing thing now called fan power. The whole world is linked through a laptop. It’s amazing. And it’s free. I love it. It’s absolutely brilliant. – Simon Cowell • Founded in August 2003, MySpace would go on to be the most-visited social networking site in the world from 2005 until early 2008. – David Sze • Generally, social networking sites can be hugely promising and beneficial in opening new friendships and vistas and knowledge of the world, but they are also fraught with peril, when young people are reckless or headless. – Richard Blumenthal • Google and Facebook, each in their own way, have revolutionized the delivery of advertising based on search and social networking, creating a sort of anti-Spam: targeted, relevant ads that a consumer might actually welcome rather than spurn. – Marcus Buckingham • Googling is not spying. It’s social networking.- Sarah • I am actually turned off when I look at an account and don’t see any selfies, because I want to know whom I’m dealing with. In our age of social networking, the selfie is the new way to look someone right in the eye and say, ‘Hello, this is me.’ – James Franco • I am often asked if Network Marketing is a Pyramid Scheme. My reply is that corporations really are pyramid schemes. A corporation has only one person at the top, generally the CEO, and everyone else below. – Donald Trump • I believe strongly in writing groups such as Romance Writers Of America that offer support, information and networking. – Nora Roberts • I consider us to be one of the first Internet-based bands, especially because we basically started our entire band via the Internet. Before MySpace Music even existed, we had a band MySpace page. We were one of the first fifty bands on PureVolume(.com), and we really built everything from the Internet. That’s how we started talking to record labels, that’s how we booked our first tours. Without the Internet social networking, like Twitter, we definitely wouldn’t be where we are today. It is a huge part of the band.- Jack Barakat • I don’t feel the need to brand myself in that way [social media]. But as a means to share information and raise awareness of things, I think these social-networking platforms are unprecedented. – Scarlett Johansson • I don’t think that developing countries gained from a two-stage process. A single phase summit (which is, after all, a two year process, not a three day event) would have built awareness, and would probably have led to more substantive conclusions at the end of the first summit meeting. Civil society may have gained a bit more from the networking experience, but it was less effective at networking in the second phase. – David Souter • I don’t think that there’s a guy behind the desk at every newspaper saying “No, woman” and sending her on her way, but that’s what’s systemic about it, right, like that people don’t quite realize that maybe they’re attracted to a male op-ed more than a female op-ed, or because of networking they know this person from going out to a bar with them. – Jessica Valenti • I feel that puttin’ in the hours and years in the studio, honing my craft, definitely played a part, me consciously networking and presenting myself as an artist that’s commercially sellable led to me meeting the right people, which in turn led to them givin’ me positive referrals to other people, which in turn led to me signin’ a deal. – Nipsey Hussle • I get excited about what the Holy Spirit is doing now through all the people he is refining and raising up all over this planet. I love connections and relationship and networking but it must be led by the Spirit.- Daniel Smith • I had been in the technology business for so long, I had seen the PC-bubble come and burst, I had seen the local area and wide area networking-bubble come and burst, it was no shock that the internet-bubble was going to burst. – Mark Cuban • I have always had stuff on the internet, way back in the Myspace days, I had a lot of friends on Myspace. And it is just all about like networking – contacting people and showing people, like, your mind. – Kreayshawn • I keep in touch with my fans by keeping a blog online and I try to answer questions every day. I also have a twitter and a facebook. I think that social networking gives authors a unique insight in the minds of their fans and for me that is very valuable. – Cassandra Clare • I like to define networking as cultivating mutually beneficial, give-and-take, win-win relationships… The end result may be to develop a large and diverse group of people who will gladly and continually refer a lot of business to us, while we do the same for them. – Bob Burg • I love networking. But I learned to love it – Jamal Igle • I must admit that I don’t really understand social networking models that well, and I haven’t tried to because I have just not been enthused about this whole thing. – David Cheriton • I remember thinking to myself that I missed the fun and excitement after leaving the corporate world to work at home. Seek camaraderie through networking. Schedule time for it; if you don’t, you’ll never make it. – Ryan Blair • I should tell my story. I’m also unemployed … I’m networking. I have my sight on a particular job. – Mitt Romney • I talk to my readers on social networking sites, but I never tell them what the book is about. Writing is lonely, so from time to time I talk to them on the Internet. It’s like chatting at a bar without leaving your office. I talk with them about a lot of things other than my books. – Paulo Coelho • I think anything which promotes heterogeneity on the Internet promotes stability. Diversity in services, service providers, and separating the layers of the networking stack are all important. – David Ulevitch • I think that it will be the mobile technologies, both from the enterprise and the consumer side, where super unicorns will come from. I still believe that social networking in combination with mobile will create opportunities for super unicorns. – David Sze • I think that social networking makes people more connected, yet more distant, so there are people with less ties to real friend groups and less a sense of self. – Lena Dunham • I think the whole aspect of social networking is vulgar and repulsive in a lot of ways. – Trent Reznor • I think there’s confusion around what the point of social networks is. A lot of different companies characterized as social networks have different goals – some serve the function of business networking, some are media portals. What we’re trying to do is just make it really efficient for people to communicate, get information and share information. – Mark Zuckerberg • I think women are really good at making friends and not good at networking. Men are good at networking and not necessarily making friends. That’s a gross generalization, but I think it holds in many ways. – Madeleine Albright • I won’t eat anything that has intelligent life, but I’d gladly eat a network executive or a politician. – Marty Feldman • If it had anything to do with the PC or networking industry I was on top of it. I bought manuals. I read every book and magazine. Then I would get involved with industry conferences and put myself out there. – Mark Cuban • If we were a culture of high-risk alcoholics, and suddenly we had Jack Daniels piped into our houses, we would be feeding that fire. Social networking, and the internet as a whole, seems to have simply landed in an extremely fertile place in an extremely fertile time in history, when we all have these narcissistic tendencies anyway – you can go further back into the self-esteem movement, and Dr. Spock, and the ‘everybody gets a ribbon at the track meet’ sort of thing, which preceded the internet – and then you drop the internet into the middle of this, and we’ve all gone haywire. – Jeffrey Kluger • If you look at the evolution of games from console to Internet to mobile, and look at social networking from Web to mobile, everything is fragmenting. – Chris DeWolfe • If you’re not networking, you’re not networking. – Denis Waitley • I’m a very optimistic person. I have the chance to listen to so much phenomenal music. Connecting with social networking to create music is a progression of what electronic music does anyway – it connects people. – Paul van Dyk • I’m good at marketing myself through the columns. But compared to other people I know, as far as networking and pushing yourself out there, I’m not very good at that. – Joel Stein • I’m no good at anything but comedy, which I think I’m good at. I’m absolutely no good at networking; I’m terrible at acting; I’m terrible at dealing with executives; I’m terrible at collaborating. And I say whatever I want to say. But I think I’m good enough at comedy that I can survive. And I don’t really have an ambition for money. – Norm MacDonald • I’m wary about this thing about being in the generation of social networking where people are like, ‘I am my musical taste.’ I am not just a collection of music. Or a collection of movies. I think that’s a thing that people romanticize: ‘Oh my God, she likes this band so she is a dream.’ – Zooey Deschanel • In my coming-of-age time, there was no internet, no social networking, nothing. It was just show after show, hoping one day somebody would notice you. – Madonna Ciccone • In the digital universe, our personal history and its sense of narrative is succeeded by our social networking profile – a snapshot of the current moment. The information itself – our social graph of friends and likes – is a product being sold to market researchers in order to better predict and guide our futures. – Douglas Rushkoff • Instead of telling the world what you’re eating for breakfast, you can use social networking to do something that’s meaningful. – Edward Norton • It has been my exprience that repetitive nights of exposure to the kundalini energy followed by longer periods of reflection and pyschic networking create the fastest transitions in awareness. – Frederick Lenz • It will take a massive effort to move society from corporate domination, in which industry’s rights to pollute and damage health and the environment supersede the public’s right to live, work, and play in safety. This is a political fight. The science is already there, showing that people’s health is at risk. To win, we will need to keep building the movement, networking with one another, planning, strategizing, and moving forward. Our children’s futures, and those of their unborn children, are at stake. – Lois Gibbs • It’s very true that an artist who networks well will have better opportunities than one who doesn’t network well. But great networking skills without great art won’t change art history. – Mark Kostabi • I’ve always been a social network retard, even before there was a social network. People would say, “You want to go to this party and do some networking?” – Lewis Black • Man, Farmville is so huge! Do you realize its the second-biggest browser-based social-networking-centered farming game in the world? – Randall Munroe • Many believe effective networking is done face-to-face, building a rapport with someone by looking at them in the eye, leading to a solid connection and foundational trust. – Raymond Arroyo • Most bloggers who rise above the clutter are quite often prolific -they work hard, not just writing content but networking, engaging in Social Media and more. – Darren Rowse • My Golden Rule of Networking is simple: Don’t keep score. – Harvey Mackay • Network marketing gives people the opportunity, with very low risk and very low financial commitment, to build their own income-generating asset and acquire great wealth. – Robert Kiyosaki • Network marketing is the big wave of the future. It’s taking the place of franchising, which now requires too much capital for the average person. – Jim Rohn • Network marketing is the only industry that allows common people to earn millions with a minimal investment and zero overhead, coupled with total time freedom and the joy of global travel. There are three magic words that worked for all of us who have made it to the pinnacle and they’ll work for you: ‘Just don’t quit.’ – Mark Yarnell • Network selectively. Nothing says “business newbie” like shotgun networking. “You never know when someone might say yes” is marketing for dummies. Take the time to build a profile of your ideal customers, and target your networking activities to reach them. Speak to those who are already predisposed to want what you offer. Almost any profile is better than “anyone with a pulse.” – Steve Pavlina • Networked, we are together, but so lessened are our expectations of each other that we can feel utterly alone. And there is the risk that we come to see others as objects to be accessed—and only for the parts we find useful, comforting, or amusing. – Sherry Turkle • Networking is an enrichment program, not an entitlement program. – Susan RoAne • Networking is an essential part of building wealth. – Armstrong Williams • Networking is marketing. Marketing yourself, marketing your uniqueness, marketing what you stand for. – Christine Comaford-Lynch • Networking is more about farming than it is about hunting. – Ivan Misner • Networking is not about hunting. It is about farming. It’s about cultivating relationships. Don’t engage in ‘premature solicitation’. You’ll be a better networker if you remember that. – Ivan Misner • Networking is rubbish; have friends instead. – Steve Winwood • Networking is simply the cultivating of mutually beneficial, give and take, win-win relationships. It works best, however, when emphasizing the “give” part. – Bob Burg • Networking is the No. 1 unwritten rule of success in business. – Sallie Krawcheck • Networking that matters is helping people achieve their goals. – Seth Godin • New security loopholes are constantly popping up because of wireless networking. The cat-and-mouse game between hackers and system administrators is still in full swing. – Kevin Mitnick • Now with the allocation and the understanding of the lack of understanding, we enter into a new era of science in which we feel nothing more than so much so as to say that those within themselves, comporary or non-comporary, will figuratively figure into the folding of our non-understanding and our partial understanding to the networks of which we all draw our source and conclusions from. – Reggie Watts • Of all the entrepreneurial opportunities available today, one of the most important is direct selling, also called network marketing. – Paul Zane Pilzer • Olympics are three times more likely to be employed than people of a similar age, ethnic and socioeconomic status who have not been participating. It’s a correlation, not a causation as far as the statisticians go, but the fascinating question is; Is there something in participation in sports, in community-building, confidence building, self-image-building, strength building, social networking – that greatly enhance employability? – Timothy Shriver • On social networking sites, we may expose ourselves, but we choose to do so. We are in control and, often wrongly, we do not feel we are giving away tradable data. – Julian Baggini • Once upon a time … the only autonomous intelligences we humans knew of were us humans. We thought then that if humankind ever devised another intelligence that it would be the result of a huge project … a great mass of silicon and ancient transistors and chips and circuit boards … a machine with lots of networking circuits, in other words, aping-if you will pardon the expression-the human brain in form and function. Of course, AIs did not evolve that way. They sort of slipped into existence when we humans were looking the other way. – Dan Simmons • One must be wary of the view that these loose and diverse coalitions represent a new form of globalized participatory democracy. The dissent industry is largely a product of the Internet revolution. Inexpensive, borderless, real-time networking provides advocacy non-governmental organizations [NGOs] with economies of scale and also of scope by linking widely disparate groups with one common theme. – Sylvia Ostry • One of the challenges in networking is everybody thinks it’s making cold calls to strangers. Actually, it’s the people who already have strong trust relationships with you, who know you’re dedicated, smart, a team player, who can help you. – Reid Hoffman • One of the issues of social networking silos is that they have the data and I don’t. – Tim Berners-Lee • One of the things women are very good at, that’s networking. Women are not afraid to say, “I need.” They’re not afraid. Men won’t even ask for directions. Women will tell each other when they need something. Women will tell each other when their husband is having an affair. Men don’t do that. – Marlo Thomas • One reason (among many) that women may well take over the world of “virtual enterprises” is that they seem to have a greater instinct for networking. And the unfettered-by-machismo males who have taken to networking will do better than those who shun it as “sissy stuff.” But truth is, it has always been the age of “networkers”; and in an era where organizations depend more and more on tenuously connected outsiders to get the job done, it will only become so. – Tom Peters • People generally worry about social networking more than they need to. In kind of consumer internet investing and on social and professional networks, I kind of look at time spending and time efficiency. You know, time saving sites. So on time spending sites, things where you play lots of games or that sort of thing, you might worry about a productivity loss if people are spending a lot of time doing that. So if there’s a lot of kind of addictive gaming going on during work hours, that won’t be as helpful to you. – Reid Hoffman • Personal relationships are always the key to good business. You can buy networking; you can’t buy friendships. – Lindsay Fox • Please be careful of becoming so immersed and engrossed in pixels, texting, ear buds, Twittering, online social networking, and potentially addictive uses of media and the Internet that you fail to recognize the importance of your physical body and miss the richness of person-to-person communication. Beware of the digital displays and data in many forms of computer-mediated interaction that can displace the full range of physical capacity and experience. – David A. Bednar • Pubcon is always one of the first shows I put on my calendar. Content is excellent, social is excellent, networking opportunities are excellent. – Jim Banks • Relationship networking is about who you know and more importantly, who knows you. Building the right network can open new doors to future success in your business. – Heidi • Respect for people is the cornerstone of communication and networking. – Susan RoAne • SDN is a major shift in the networking industry. At Juniper, we think the impact of SDN will be much broader than others have suggested. It will redefine networking and create new winners and losers. We’re embracing SDN with clearly defined principles, a four-step roadmap to help customers adopt SDN within their business, and the networking industry’s first comprehensive software-centric business model. We’re incredibly excited about the value that SDN will deliver to our customers and are committed to leading the industry through this transition. – Bob Muglia • Search without Google is like social networking without Facebook: unimaginable. – Evgeny Morozov • SixDegrees.org is about using the idea that we are all connected to accomplish something good. It is my hope that Six Degrees will soon be something more than a game or a gimmick. It will also be a force for good, by bringing a social conscience to social networking. – Kevin Bacon • Social networking helps reach people easier and quicker. – Bill Cosby • Social networking inspires me a lot and how we are related and connected to each other. – Nicola Formichetti • Social networking is playing a huge role in creating awareness and mobilizing support for all kinds of common interests. What better way to use this remarkable tool than to change the world? – Natalie Portman • Social Networking should never replace face-to-face time. – Germany Kent • Social networking sites like Myspace, Friendster, and Facebook have literally exploded in popularity in just a few short years. – Mike Fitzpatrick • Social networking technology didn’t really exist until 2004-2005. I had the idea to use this technology to bridge this gap between a general interest in addressing social issues and the practical action. – Ben Rattray • Social Networking that matters is helping people archive their goals. Doing it reliably and repeatability so that over time people have an interest in helping you achieve your goals.- Seth Godin • Social networking, I believe, has completely changed the relationship between band-members and fans. – Beau Bokan • Social networks are like grease – in some cases, gasoline – for our personal business networking machines. If you aren’t plugged in, you will be out-done by better-connected, hyper-networked colleagues and competitors. – danah boyd • Sometimes, idealistic people are put off the whole business of networking as something tainted by flattery and the pursuit of selfish advantage. But virtue in obscurity is rewarded only in Heaven. To succeed in this world you have to be known to people. – Sonia Sotomayor • Spirituality in Washington can be more of a – I don’t want to say it – but, a networking opportunity. Religion is often used opportunistically in the political conversation. – Mark Leibovich • Start a conversation with someone with whom you have “nothing in common” and no possibility of scoring with, networking with, or even seeing again. In other words, a conversation just for the civilized hell of it. – Perry Brass • Take a moment think who would actually miss you if you deactivate all your social networking accounts, whatsapp, BBM etc – Anamika Mishra • Technology is a compulsive and addictive way to live. Verbal communication cannot be lost because of a lack of skill. The ability to listen and learn is key to mastering the art of communication. If you dont use your verbal skills and networking, it will disappear rapidly. Use technology wisely. – Rick Pitino • That definitely I feel is part of my generation: social networking, communication over the Internet, whether it’s Skype or IRC or some form of text-based chat, text messaging. – Duncan Jones • That is vaguely conspiratorial, in a networking sense. We have published their meeting notes. – Julian Assange • The [film] industry, from the franchise on, has dramatically changed, not just with us, but with social networking. The social working has changed dramatically, especially in the way you promote films. It’s instant. – Tara Reid • The biggest mistake that I made was not anticipating the rise of the social networking phenomenon. – Eric Schmidt • The blogs have been great and everything, but I think, for me, it’s better to have a central place on the Internet for all my fans to go and show their friends my YouTube, Twitter, and social networking sites. To have that spread all on its own and have a central station to get everything Mac Miller. – Mac Miller • The breakup of Bell laid the foundation for every important communications revolution since the 1980s onward. There was no way of knowing that thirty years on we would have an Internet, handheld computers, and social networking, but it is hard to imagine their coming when they did, had the company that bured the answering machine remained intact.- Tim Wu • The business is about coming up with a business plan and using your relationships and networking and seeing your dreams come true. Everyone on this show has their own business. Fifteen minutes of fame is fleeting. It’s about learning the business and creating a new business. – Eva Marcille • The class focuses intensely on making people more comfortable with doing a wider range of things – such as networking, self-promotion, building their own personal brand, cleverly acquiring resources, getting known – that they may have been less comfortable with before. – Jeffrey Pfeffer • The currency of real networking is not greed but generosity. – Keith Ferrazzi • The future of network marketing is unlimited. There’s no end in sight. It will continue to grow because better people are getting into it . . . soon, it will be one of the most respected business methods in the world. – Brian Tracy • The future success of online social networking sites as an advertising medium depends on its acceptance as an advertising vehicle that can deliver a message to a micro-target in a manner that will be well received and that increases the likelihood of interaction. – Mary Louise Kelly • The idea that hardware on networks should just be caches for movable process descriptions and the processes themselves goes back quite a ways. There’s a real sense in which MS and Apple never understood networking or operating systems (or what objects really are), and when they decided to beef up their OSs, they went to (different) very old bad mainframe models of OS design to try to adapt to personal computers. – Alan Kay • The internet and social networking are new avenues for the next Bob Dylan to be born on. – Jon Bon Jovi • The more complex the network is, the more complex its pattern of interconnections, the more resilient it will be. – Fritjof Capra • The more you enter, the more you become locked in. Your social-networking site becomes a central platform – a closed silo of content, and one that does not give you full control over your information in it. The more this kind of architecture gains widespread use, the more the Web becomes fragmented, and the less we enjoy a single, universal information space.- Tim Berners-Lee • The most successful network marketers I know, the ones receiving tons of referrals and feeling truly happy about themselves, continually put the other person’s needs ahead of their own. – Bob Burg • The precondition of success and entry to the top politics is primarily one’s will – that is, making one’s own decisions, because it means having to leave your home or move your family, quit social networking and build new contacts, [since] central governments are seated in capitals. – Dalia Grybauskaite • The software is the strength of the electronic tribe because it’s networking. It’s creating oneness. It’s creating tributaries that link together into a singular river. – Frederick Lenz • The tools of social networking: These are the digital campfires around which the audience gathers to hear our story. – Marco Tempest • The trouble with not being into social networking is that people think you’re anti-social when you’re only anti-networking. – Robert Breault • The true value of networking doesn’t come from how many people we can meet but rather how many people we can introduce to others. – Simon Sinek • The value of networking is not measured by the number of people we meet but by the number of people we introduce to others. – Simon Sinek • The work I’m doing today gets me one step closer to the work I should be doing tomorrow. And that the way I learn this is by trying, failing, networking and experimenting. I’ll stop doing that when I’m dead. – Lewis Schiff • There’s a fast-track if you can do the networking. For some personalities it works, but for mine it doesn’t. – Idris Elba • There’s some people that obviously abuse social networking or whatever, but I think it’s a fantastic idea. I’ve never had any bad encounters with any of it. – Maisie Williams • This social-networking thing takes you to crazy places. – Bill Gates • Time is our most precious currency. So it’s significant that we are being encouraged, wherever possible, to think of our attention not as expenditure but as consumption. This blurring of labor and entertainment forms the basis, for example, of the financial alchemy that conjures deca-billion-dollar valuations for social-networking companies.- Mohsin Hamid • To win, we will need to keep building the movement, networking with one another, planning, strategizing, and moving forward. Our children’s futures, and those of their unborn children, are at stake. – Lois Gibbs • Try never to be the smartest person in the room. And if you are, I suggest you invite smarter people… or find a different room. In professional circles it’s called networking. In organizations it’s called team building. And in life it’s called family, friends, and community. We are all gifts to each other, and my own growth as a leader has shown me again and again that the most rewarding experiences come from my relationships. – Michael Dell • We are at a crossroads in the music business: with the rise of the internet, the world we live in has changed, and the past is not coming back. But I see the glass as half-full: the internet and social networking are new avenues for the next Bob Dylan to be born on. – Jon Bon Jovi • We’re being asked to continually be “authentic” and “honest” with the world through social media. There’s a demand to post our wedding pictures, baby pictures (only minutes after the birth), our relationship status, and our grief and joys on Facebook and Instagram. Similarly, we construct persona through dating apps and networking sites. All of these social media networks exert pressure on us to share the personal details of our lives with unknown masses. So the pressure on the characters in “Openness” isn’t merely romantic, but public/social as well. – Alexander Weinstein • We’re currently living with a generation of established novelists who are embarrassingly out of date with respect to social networking, internet skills, and so on. – Charles Stross • We’re living at a time when attention is the new currency: With hundreds of TV channels, billions of Web sites, podcasts, radio shows, music downloads and social networking, our attention is more fragmented than ever before. – Pete Cashmore • We’ve done this before in other worlds, in other lives. It is our strength, law, medicine, entertainment, and computers, the networking of energy. All of these are arts. – Frederick Lenz • We’ve had such a close relationship with the fans. Through social networking and the internet, we have much more contact, and we did go to things like Comic-Con. So, I think people know most of our secrets. – John Noble • What being among the ‘right people’ entails is the possession of human capital, rather than organizational capital: an individual reputation, portable skills, and network connections. Career responsibility is squarely in the hands of individuals, a function of their knowledge and networks. Transferable knowledge is more important to a career than firm-specific knowledge. – Rosabeth Moss Kanter • What excites me is that, when things are tough, people become resourceful, and now with the Internet, social networking and the ability for people who in the past had been relatively powerless, they have tools to be able to spread ideas and organize. The urgency is there and the tools are there and I think that the possibility for really, really powerful results is there. I think it’s all brewing, it’s all bubbling up right now. – Shepard Fairey • What makes a great standalone piece of hardware is not the same thing as what makes a great networking device. One can work as an essentially closed system. The other is absolutely dependent on its openness. – Douglas Rushkoff • What makes networking work is that it sets up win-win situations in which all parties involved get to take something home. Networking is a sharing process. Until you understand that, you won’t have much of a network. – Earl G. Graves, Sr. • What you do is ultimately pointless. You could be replaced any day of the week with the first moron who walks in the door. So work as little as possible, and spend a little time (not too much, though) ‘selling yourself’ and ‘networking’ so that you will have backup and will be untouchable (and untouched) the next time the company is restructured. – Corinne Maier • Whatever you’re selling, storage or networking or security, you’re going head to head with the incumbent players. – Marc Andreessen • When people are using their devices, it’s probable that almost half are networking on social media. – Gary Vaynerchuk • When thinking about how to deploy kind of professional and social networking into your business, it’s really not a question of if, it’s a question of when. And the reason is, just think about the fact that those businesses that adopt new technologies to operate efficiently and use them to get a competitive edge are the businesses that in fact, you know, it becomes one more competitive advantage. Whether it’s a fax machine or a mobile phone or a new way of doing financing or any of these things, you know, these are key things to do. – Reid Hoffman • Wikis and social networking are just tools. – Jimmy Wales • Will the social networking phenomenon lessen? I don’t think so. – Marissa Mayer • With my wife Camille’s help, I took to social networking. I’m working with the computers. – Bill Cosby • With the advent of Twitter and Facebook and other social networking sites, genuine privacy can only be found by renting a private villa for a holiday. Hotels are now out of the question for my wife and I. – Robert Powell • With Twitter and other social networking tools, you can get a lot of advice from great people. I learn more from Twitter than any survey or discussion with a big company. – Daniel Ek • You are already leaders. Your ideas, your actions and your decisions make a difference. More than any other generation, you have a voice. Social networking is changing how we interact – and it can change our world. You are in touch with peers from around the world. You understand the power of instant communication. I appeal to you to use that power for the common good, the power of communication and the power of networking. – Ban Ki-moon • You thought you could figure that out online? Somehow I don’t think hellions are much into social networking. – Rachel Vincent • You try and nurture the relationship. This day and age we have to do a little more networking than we used to do. All that does is make sure you befriend the people you are working with on a project so you hopefully carry it over to the next one. – Aaron Zigman • Young people know how to use these social networking tools, and they know how to use them effectively. – Edward Norton • Younger Arabs are much less satisfied with education in the region than their elders, and are more comfortable networking and communicating via digital means. – Joe Saddi
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'a', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_a').html(obj); jQuery('#thelovesof_a img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'e', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_e').html(obj); jQuery('#thelovesof_e img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'i', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_i').html(obj); jQuery('#thelovesof_i img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'o', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_o').html(obj); jQuery('#thelovesof_o img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'u', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_u').html(obj); jQuery('#thelovesof_u img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'y', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_y').html(obj); jQuery('#thelovesof_y img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
0 notes
Text
Networking Quotes
Official Website: Networking Quotes
• A good browser, apps, good camera, and fast networking in your smartphone is just expected today. – Thorsten Heins • A man of substance should trust very carefully an online networking friend whose shared images are not often palatable to his taste. – Anuj • A new survey found that 12 percent of parents punish their kids by banning social networking sites. The other 88 percent punish their kids by joining social networking sites.- Jimmy Fallon • A technology becomes truly disruptive when it drives the marginal cost of something that used to be scarce and expensive to approach zero. Thus, it used to be to deploy software at scale, you had to fund a data center, buy a set of servers, storage, and networking gear, build an in-house IT management capability, and buy an expensive stack of enabling software before you could even get started. Now you can get all that from Amazon or Microsoft on a pay-as-you-grow model. – Geoffrey Moore • Anyone can use these sites – companies and colleges, teachers and students, young and old all make use of networking sites to connect with people electronically to share pictures, information, course work, and common interests. – Mike Fitzpatrick • As information technology becomes millions of times more powerful, any particular use of it becomes correspondingly cheaper. Thus, it has become commonplace to expect online services (not just news, but 21st century treats like search or social networking) to be given for free, or rather, in exchange for acquiescence to being spied on. – Jaron Lanier • As IT enters the mobile-cloud era, IT providers need to be more innovative about addressing customers’ fast changing needs. Over the past two years, Cisco and Citrix have collaborated to deliver significant innovation into the market. Now we are excited to accelerate our partnership into cloud, networking and mobility. – Padmasree Warrior
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'Network', orderby: 'rand', order: 'DESC', template: '1', limit: '68', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_network').html(obj); jQuery('#thelovesof_network img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); ); • Being in New York and having worked at Time Out New York and then being at Time, living in New York for a long time has helped because I know everybody. And they’re the people who call me and give me jobs. So that kind of real networking, which is just living in a place and having jobs where people around you are extremely successful, has helped me tremendously. – Joel Stein • Best results are often achieved well before you need a job, by consistently networking so that when you find yourself job-hunting you have a large network to work with. – Erik Qualman • Brooklyn is where I primarily developed. I had an opportunity to make records and perform in clubs here and there, and I started networking with the right people in the right places. – Busta Rhymes • Bullying behaviour can be communicated via text, mobile phones, internet, social networking sites, forums. But we can’t limit it because these messages are then reinforced by television which glamorises yelling, swearing and vulgar behaviour as the way to walk the red carpet of acceptance. – Louise Burfitt-Dons • Business culture operates differently in different cities around the world. But I don’t think it’s possible to design one system that incorporates all social norms for networking. Human beings are just too diverse. – danah boyd • Conservatively, I am saying that social networking has made being in a band more fun, but not necessarily changed how the business works. – Chris Cain • Create a website that expresses something about who you are that won’t fit into the template available to you on a social networking site. – Jaron Lanier • Despite all the hype about local or green food, the single biggest impediment to wider adoption is not research, programs, organizations, or networking. It is the demonizing and criminalizing of virtually all indigenous and heritage-based food practices. – Joel Salatin • Facebook and other social networking sites are bringing together spheres that used to be separate. People no longer have private and public lives; the line between the two is becoming blurred. – Paul Achleitner • Facebook is shaping a broader web. If you look back for the past five or seven years, the story about social networking has really been about getting people connected… But if you look forward for the next five years, I think that the story people are going to remember five years from now isn’t how this one site was built; it is how every single service that you use is now going to be better with your friends. – Mark Zuckerberg • Figure out what you are meant to contribute to the world and make sure you contribute it. If this requires public speaking or networking or other activities that make you uncomfortable, do them anyway. But accept that they’re difficult, get the training you need to make them easier, and reward yourself when you’re done. – Susan Cain • First, you have to be visible in the community. You have to get out there and connect with people. It’s not called net-sitting or net-eating. It’s called networking. You have to work at it. – Ivan Misner • For almost the first year of The Muse’s life, I would do 5 to 8 networking events a week. And I don’t necessarily think that’s the right path for everyone, but I realized that as an entrepreneur, one of my strengths was finding the right people who could help us. I didn’t come into startups with any network. – Kathryn Minshew • For people choosing to use a network marketing system to build a business in the B quadrant, the price of entry is a lot lower, the risks are lower, and the education and support are there to guide you through this personal development process. – Robert Kiyosaki • For the music business, social networking is brilliant. Just when you think it’s doom and gloom and you have to spend millions of pounds on marketing and this and that, you have this amazing thing now called fan power. The whole world is linked through a laptop. It’s amazing. And it’s free. I love it. It’s absolutely brilliant. – Simon Cowell • Founded in August 2003, MySpace would go on to be the most-visited social networking site in the world from 2005 until early 2008. – David Sze • Generally, social networking sites can be hugely promising and beneficial in opening new friendships and vistas and knowledge of the world, but they are also fraught with peril, when young people are reckless or headless. – Richard Blumenthal • Google and Facebook, each in their own way, have revolutionized the delivery of advertising based on search and social networking, creating a sort of anti-Spam: targeted, relevant ads that a consumer might actually welcome rather than spurn. – Marcus Buckingham • Googling is not spying. It’s social networking.- Sarah • I am actually turned off when I look at an account and don’t see any selfies, because I want to know whom I’m dealing with. In our age of social networking, the selfie is the new way to look someone right in the eye and say, ‘Hello, this is me.’ – James Franco • I am often asked if Network Marketing is a Pyramid Scheme. My reply is that corporations really are pyramid schemes. A corporation has only one person at the top, generally the CEO, and everyone else below. – Donald Trump • I believe strongly in writing groups such as Romance Writers Of America that offer support, information and networking. – Nora Roberts • I consider us to be one of the first Internet-based bands, especially because we basically started our entire band via the Internet. Before MySpace Music even existed, we had a band MySpace page. We were one of the first fifty bands on PureVolume(.com), and we really built everything from the Internet. That’s how we started talking to record labels, that’s how we booked our first tours. Without the Internet social networking, like Twitter, we definitely wouldn’t be where we are today. It is a huge part of the band.- Jack Barakat • I don’t feel the need to brand myself in that way [social media]. But as a means to share information and raise awareness of things, I think these social-networking platforms are unprecedented. – Scarlett Johansson • I don’t think that developing countries gained from a two-stage process. A single phase summit (which is, after all, a two year process, not a three day event) would have built awareness, and would probably have led to more substantive conclusions at the end of the first summit meeting. Civil society may have gained a bit more from the networking experience, but it was less effective at networking in the second phase. – David Souter • I don’t think that there’s a guy behind the desk at every newspaper saying “No, woman” and sending her on her way, but that’s what’s systemic about it, right, like that people don’t quite realize that maybe they’re attracted to a male op-ed more than a female op-ed, or because of networking they know this person from going out to a bar with them. – Jessica Valenti • I feel that puttin’ in the hours and years in the studio, honing my craft, definitely played a part, me consciously networking and presenting myself as an artist that’s commercially sellable led to me meeting the right people, which in turn led to them givin’ me positive referrals to other people, which in turn led to me signin’ a deal. – Nipsey Hussle • I get excited about what the Holy Spirit is doing now through all the people he is refining and raising up all over this planet. I love connections and relationship and networking but it must be led by the Spirit.- Daniel Smith • I had been in the technology business for so long, I had seen the PC-bubble come and burst, I had seen the local area and wide area networking-bubble come and burst, it was no shock that the internet-bubble was going to burst. – Mark Cuban • I have always had stuff on the internet, way back in the Myspace days, I had a lot of friends on Myspace. And it is just all about like networking – contacting people and showing people, like, your mind. – Kreayshawn • I keep in touch with my fans by keeping a blog online and I try to answer questions every day. I also have a twitter and a facebook. I think that social networking gives authors a unique insight in the minds of their fans and for me that is very valuable. – Cassandra Clare • I like to define networking as cultivating mutually beneficial, give-and-take, win-win relationships… The end result may be to develop a large and diverse group of people who will gladly and continually refer a lot of business to us, while we do the same for them. – Bob Burg • I love networking. But I learned to love it – Jamal Igle • I must admit that I don’t really understand social networking models that well, and I haven’t tried to because I have just not been enthused about this whole thing. – David Cheriton • I remember thinking to myself that I missed the fun and excitement after leaving the corporate world to work at home. Seek camaraderie through networking. Schedule time for it; if you don’t, you’ll never make it. – Ryan Blair • I should tell my story. I’m also unemployed … I’m networking. I have my sight on a particular job. – Mitt Romney • I talk to my readers on social networking sites, but I never tell them what the book is about. Writing is lonely, so from time to time I talk to them on the Internet. It’s like chatting at a bar without leaving your office. I talk with them about a lot of things other than my books. – Paulo Coelho • I think anything which promotes heterogeneity on the Internet promotes stability. Diversity in services, service providers, and separating the layers of the networking stack are all important. – David Ulevitch • I think that it will be the mobile technologies, both from the enterprise and the consumer side, where super unicorns will come from. I still believe that social networking in combination with mobile will create opportunities for super unicorns. – David Sze • I think that social networking makes people more connected, yet more distant, so there are people with less ties to real friend groups and less a sense of self. – Lena Dunham • I think the whole aspect of social networking is vulgar and repulsive in a lot of ways. – Trent Reznor • I think there’s confusion around what the point of social networks is. A lot of different companies characterized as social networks have different goals – some serve the function of business networking, some are media portals. What we’re trying to do is just make it really efficient for people to communicate, get information and share information. – Mark Zuckerberg • I think women are really good at making friends and not good at networking. Men are good at networking and not necessarily making friends. That’s a gross generalization, but I think it holds in many ways. – Madeleine Albright • I won’t eat anything that has intelligent life, but I’d gladly eat a network executive or a politician. – Marty Feldman • If it had anything to do with the PC or networking industry I was on top of it. I bought manuals. I read every book and magazine. Then I would get involved with industry conferences and put myself out there. – Mark Cuban • If we were a culture of high-risk alcoholics, and suddenly we had Jack Daniels piped into our houses, we would be feeding that fire. Social networking, and the internet as a whole, seems to have simply landed in an extremely fertile place in an extremely fertile time in history, when we all have these narcissistic tendencies anyway – you can go further back into the self-esteem movement, and Dr. Spock, and the ‘everybody gets a ribbon at the track meet’ sort of thing, which preceded the internet – and then you drop the internet into the middle of this, and we’ve all gone haywire. – Jeffrey Kluger • If you look at the evolution of games from console to Internet to mobile, and look at social networking from Web to mobile, everything is fragmenting. – Chris DeWolfe • If you’re not networking, you’re not networking. – Denis Waitley • I’m a very optimistic person. I have the chance to listen to so much phenomenal music. Connecting with social networking to create music is a progression of what electronic music does anyway – it connects people. – Paul van Dyk • I’m good at marketing myself through the columns. But compared to other people I know, as far as networking and pushing yourself out there, I’m not very good at that. – Joel Stein • I’m no good at anything but comedy, which I think I’m good at. I’m absolutely no good at networking; I’m terrible at acting; I’m terrible at dealing with executives; I’m terrible at collaborating. And I say whatever I want to say. But I think I’m good enough at comedy that I can survive. And I don’t really have an ambition for money. – Norm MacDonald • I’m wary about this thing about being in the generation of social networking where people are like, ‘I am my musical taste.’ I am not just a collection of music. Or a collection of movies. I think that’s a thing that people romanticize: ‘Oh my God, she likes this band so she is a dream.’ – Zooey Deschanel • In my coming-of-age time, there was no internet, no social networking, nothing. It was just show after show, hoping one day somebody would notice you. – Madonna Ciccone • In the digital universe, our personal history and its sense of narrative is succeeded by our social networking profile – a snapshot of the current moment. The information itself – our social graph of friends and likes – is a product being sold to market researchers in order to better predict and guide our futures. – Douglas Rushkoff • Instead of telling the world what you’re eating for breakfast, you can use social networking to do something that’s meaningful. – Edward Norton • It has been my exprience that repetitive nights of exposure to the kundalini energy followed by longer periods of reflection and pyschic networking create the fastest transitions in awareness. – Frederick Lenz • It will take a massive effort to move society from corporate domination, in which industry’s rights to pollute and damage health and the environment supersede the public’s right to live, work, and play in safety. This is a political fight. The science is already there, showing that people’s health is at risk. To win, we will need to keep building the movement, networking with one another, planning, strategizing, and moving forward. Our children’s futures, and those of their unborn children, are at stake. – Lois Gibbs • It’s very true that an artist who networks well will have better opportunities than one who doesn’t network well. But great networking skills without great art won’t change art history. – Mark Kostabi • I’ve always been a social network retard, even before there was a social network. People would say, “You want to go to this party and do some networking?” – Lewis Black • Man, Farmville is so huge! Do you realize its the second-biggest browser-based social-networking-centered farming game in the world? – Randall Munroe • Many believe effective networking is done face-to-face, building a rapport with someone by looking at them in the eye, leading to a solid connection and foundational trust. – Raymond Arroyo • Most bloggers who rise above the clutter are quite often prolific -they work hard, not just writing content but networking, engaging in Social Media and more. – Darren Rowse • My Golden Rule of Networking is simple: Don’t keep score. – Harvey Mackay • Network marketing gives people the opportunity, with very low risk and very low financial commitment, to build their own income-generating asset and acquire great wealth. – Robert Kiyosaki • Network marketing is the big wave of the future. It’s taking the place of franchising, which now requires too much capital for the average person. – Jim Rohn • Network marketing is the only industry that allows common people to earn millions with a minimal investment and zero overhead, coupled with total time freedom and the joy of global travel. There are three magic words that worked for all of us who have made it to the pinnacle and they’ll work for you: ‘Just don’t quit.’ – Mark Yarnell • Network selectively. Nothing says “business newbie” like shotgun networking. “You never know when someone might say yes” is marketing for dummies. Take the time to build a profile of your ideal customers, and target your networking activities to reach them. Speak to those who are already predisposed to want what you offer. Almost any profile is better than “anyone with a pulse.” – Steve Pavlina • Networked, we are together, but so lessened are our expectations of each other that we can feel utterly alone. And there is the risk that we come to see others as objects to be accessed—and only for the parts we find useful, comforting, or amusing. – Sherry Turkle • Networking is an enrichment program, not an entitlement program. – Susan RoAne • Networking is an essential part of building wealth. – Armstrong Williams • Networking is marketing. Marketing yourself, marketing your uniqueness, marketing what you stand for. – Christine Comaford-Lynch • Networking is more about farming than it is about hunting. – Ivan Misner • Networking is not about hunting. It is about farming. It’s about cultivating relationships. Don’t engage in ‘premature solicitation’. You’ll be a better networker if you remember that. – Ivan Misner • Networking is rubbish; have friends instead. – Steve Winwood • Networking is simply the cultivating of mutually beneficial, give and take, win-win relationships. It works best, however, when emphasizing the “give” part. – Bob Burg • Networking is the No. 1 unwritten rule of success in business. – Sallie Krawcheck • Networking that matters is helping people achieve their goals. – Seth Godin • New security loopholes are constantly popping up because of wireless networking. The cat-and-mouse game between hackers and system administrators is still in full swing. – Kevin Mitnick • Now with the allocation and the understanding of the lack of understanding, we enter into a new era of science in which we feel nothing more than so much so as to say that those within themselves, comporary or non-comporary, will figuratively figure into the folding of our non-understanding and our partial understanding to the networks of which we all draw our source and conclusions from. – Reggie Watts • Of all the entrepreneurial opportunities available today, one of the most important is direct selling, also called network marketing. – Paul Zane Pilzer • Olympics are three times more likely to be employed than people of a similar age, ethnic and socioeconomic status who have not been participating. It’s a correlation, not a causation as far as the statisticians go, but the fascinating question is; Is there something in participation in sports, in community-building, confidence building, self-image-building, strength building, social networking – that greatly enhance employability? – Timothy Shriver • On social networking sites, we may expose ourselves, but we choose to do so. We are in control and, often wrongly, we do not feel we are giving away tradable data. – Julian Baggini • Once upon a time … the only autonomous intelligences we humans knew of were us humans. We thought then that if humankind ever devised another intelligence that it would be the result of a huge project … a great mass of silicon and ancient transistors and chips and circuit boards … a machine with lots of networking circuits, in other words, aping-if you will pardon the expression-the human brain in form and function. Of course, AIs did not evolve that way. They sort of slipped into existence when we humans were looking the other way. – Dan Simmons • One must be wary of the view that these loose and diverse coalitions represent a new form of globalized participatory democracy. The dissent industry is largely a product of the Internet revolution. Inexpensive, borderless, real-time networking provides advocacy non-governmental organizations [NGOs] with economies of scale and also of scope by linking widely disparate groups with one common theme. – Sylvia Ostry • One of the challenges in networking is everybody thinks it’s making cold calls to strangers. Actually, it’s the people who already have strong trust relationships with you, who know you’re dedicated, smart, a team player, who can help you. – Reid Hoffman • One of the issues of social networking silos is that they have the data and I don’t. – Tim Berners-Lee • One of the things women are very good at, that’s networking. Women are not afraid to say, “I need.” They’re not afraid. Men won’t even ask for directions. Women will tell each other when they need something. Women will tell each other when their husband is having an affair. Men don’t do that. – Marlo Thomas • One reason (among many) that women may well take over the world of “virtual enterprises” is that they seem to have a greater instinct for networking. And the unfettered-by-machismo males who have taken to networking will do better than those who shun it as “sissy stuff.” But truth is, it has always been the age of “networkers”; and in an era where organizations depend more and more on tenuously connected outsiders to get the job done, it will only become so. – Tom Peters • People generally worry about social networking more than they need to. In kind of consumer internet investing and on social and professional networks, I kind of look at time spending and time efficiency. You know, time saving sites. So on time spending sites, things where you play lots of games or that sort of thing, you might worry about a productivity loss if people are spending a lot of time doing that. So if there’s a lot of kind of addictive gaming going on during work hours, that won’t be as helpful to you. – Reid Hoffman • Personal relationships are always the key to good business. You can buy networking; you can’t buy friendships. – Lindsay Fox • Please be careful of becoming so immersed and engrossed in pixels, texting, ear buds, Twittering, online social networking, and potentially addictive uses of media and the Internet that you fail to recognize the importance of your physical body and miss the richness of person-to-person communication. Beware of the digital displays and data in many forms of computer-mediated interaction that can displace the full range of physical capacity and experience. – David A. Bednar • Pubcon is always one of the first shows I put on my calendar. Content is excellent, social is excellent, networking opportunities are excellent. – Jim Banks • Relationship networking is about who you know and more importantly, who knows you. Building the right network can open new doors to future success in your business. – Heidi • Respect for people is the cornerstone of communication and networking. – Susan RoAne • SDN is a major shift in the networking industry. At Juniper, we think the impact of SDN will be much broader than others have suggested. It will redefine networking and create new winners and losers. We’re embracing SDN with clearly defined principles, a four-step roadmap to help customers adopt SDN within their business, and the networking industry’s first comprehensive software-centric business model. We’re incredibly excited about the value that SDN will deliver to our customers and are committed to leading the industry through this transition. – Bob Muglia • Search without Google is like social networking without Facebook: unimaginable. – Evgeny Morozov • SixDegrees.org is about using the idea that we are all connected to accomplish something good. It is my hope that Six Degrees will soon be something more than a game or a gimmick. It will also be a force for good, by bringing a social conscience to social networking. – Kevin Bacon • Social networking helps reach people easier and quicker. – Bill Cosby • Social networking inspires me a lot and how we are related and connected to each other. – Nicola Formichetti • Social networking is playing a huge role in creating awareness and mobilizing support for all kinds of common interests. What better way to use this remarkable tool than to change the world? – Natalie Portman • Social Networking should never replace face-to-face time. – Germany Kent • Social networking sites like Myspace, Friendster, and Facebook have literally exploded in popularity in just a few short years. – Mike Fitzpatrick • Social networking technology didn’t really exist until 2004-2005. I had the idea to use this technology to bridge this gap between a general interest in addressing social issues and the practical action. – Ben Rattray • Social Networking that matters is helping people archive their goals. Doing it reliably and repeatability so that over time people have an interest in helping you achieve your goals.- Seth Godin • Social networking, I believe, has completely changed the relationship between band-members and fans. – Beau Bokan • Social networks are like grease – in some cases, gasoline – for our personal business networking machines. If you aren’t plugged in, you will be out-done by better-connected, hyper-networked colleagues and competitors. – danah boyd • Sometimes, idealistic people are put off the whole business of networking as something tainted by flattery and the pursuit of selfish advantage. But virtue in obscurity is rewarded only in Heaven. To succeed in this world you have to be known to people. – Sonia Sotomayor • Spirituality in Washington can be more of a – I don’t want to say it – but, a networking opportunity. Religion is often used opportunistically in the political conversation. – Mark Leibovich • Start a conversation with someone with whom you have “nothing in common” and no possibility of scoring with, networking with, or even seeing again. In other words, a conversation just for the civilized hell of it. – Perry Brass • Take a moment think who would actually miss you if you deactivate all your social networking accounts, whatsapp, BBM etc – Anamika Mishra • Technology is a compulsive and addictive way to live. Verbal communication cannot be lost because of a lack of skill. The ability to listen and learn is key to mastering the art of communication. If you dont use your verbal skills and networking, it will disappear rapidly. Use technology wisely. – Rick Pitino • That definitely I feel is part of my generation: social networking, communication over the Internet, whether it’s Skype or IRC or some form of text-based chat, text messaging. – Duncan Jones • That is vaguely conspiratorial, in a networking sense. We have published their meeting notes. – Julian Assange • The [film] industry, from the franchise on, has dramatically changed, not just with us, but with social networking. The social working has changed dramatically, especially in the way you promote films. It’s instant. – Tara Reid • The biggest mistake that I made was not anticipating the rise of the social networking phenomenon. – Eric Schmidt • The blogs have been great and everything, but I think, for me, it’s better to have a central place on the Internet for all my fans to go and show their friends my YouTube, Twitter, and social networking sites. To have that spread all on its own and have a central station to get everything Mac Miller. – Mac Miller • The breakup of Bell laid the foundation for every important communications revolution since the 1980s onward. There was no way of knowing that thirty years on we would have an Internet, handheld computers, and social networking, but it is hard to imagine their coming when they did, had the company that bured the answering machine remained intact.- Tim Wu • The business is about coming up with a business plan and using your relationships and networking and seeing your dreams come true. Everyone on this show has their own business. Fifteen minutes of fame is fleeting. It’s about learning the business and creating a new business. – Eva Marcille • The class focuses intensely on making people more comfortable with doing a wider range of things – such as networking, self-promotion, building their own personal brand, cleverly acquiring resources, getting known – that they may have been less comfortable with before. – Jeffrey Pfeffer • The currency of real networking is not greed but generosity. – Keith Ferrazzi • The future of network marketing is unlimited. There’s no end in sight. It will continue to grow because better people are getting into it . . . soon, it will be one of the most respected business methods in the world. – Brian Tracy • The future success of online social networking sites as an advertising medium depends on its acceptance as an advertising vehicle that can deliver a message to a micro-target in a manner that will be well received and that increases the likelihood of interaction. – Mary Louise Kelly • The idea that hardware on networks should just be caches for movable process descriptions and the processes themselves goes back quite a ways. There’s a real sense in which MS and Apple never understood networking or operating systems (or what objects really are), and when they decided to beef up their OSs, they went to (different) very old bad mainframe models of OS design to try to adapt to personal computers. – Alan Kay • The internet and social networking are new avenues for the next Bob Dylan to be born on. – Jon Bon Jovi • The more complex the network is, the more complex its pattern of interconnections, the more resilient it will be. – Fritjof Capra • The more you enter, the more you become locked in. Your social-networking site becomes a central platform – a closed silo of content, and one that does not give you full control over your information in it. The more this kind of architecture gains widespread use, the more the Web becomes fragmented, and the less we enjoy a single, universal information space.- Tim Berners-Lee • The most successful network marketers I know, the ones receiving tons of referrals and feeling truly happy about themselves, continually put the other person’s needs ahead of their own. – Bob Burg • The precondition of success and entry to the top politics is primarily one’s will – that is, making one’s own decisions, because it means having to leave your home or move your family, quit social networking and build new contacts, [since] central governments are seated in capitals. – Dalia Grybauskaite • The software is the strength of the electronic tribe because it’s networking. It’s creating oneness. It’s creating tributaries that link together into a singular river. – Frederick Lenz • The tools of social networking: These are the digital campfires around which the audience gathers to hear our story. – Marco Tempest • The trouble with not being into social networking is that people think you’re anti-social when you’re only anti-networking. – Robert Breault • The true value of networking doesn’t come from how many people we can meet but rather how many people we can introduce to others. – Simon Sinek • The value of networking is not measured by the number of people we meet but by the number of people we introduce to others. – Simon Sinek • The work I’m doing today gets me one step closer to the work I should be doing tomorrow. And that the way I learn this is by trying, failing, networking and experimenting. I’ll stop doing that when I’m dead. – Lewis Schiff • There’s a fast-track if you can do the networking. For some personalities it works, but for mine it doesn’t. – Idris Elba • There’s some people that obviously abuse social networking or whatever, but I think it’s a fantastic idea. I’ve never had any bad encounters with any of it. – Maisie Williams • This social-networking thing takes you to crazy places. – Bill Gates • Time is our most precious currency. So it’s significant that we are being encouraged, wherever possible, to think of our attention not as expenditure but as consumption. This blurring of labor and entertainment forms the basis, for example, of the financial alchemy that conjures deca-billion-dollar valuations for social-networking companies.- Mohsin Hamid • To win, we will need to keep building the movement, networking with one another, planning, strategizing, and moving forward. Our children’s futures, and those of their unborn children, are at stake. – Lois Gibbs • Try never to be the smartest person in the room. And if you are, I suggest you invite smarter people… or find a different room. In professional circles it’s called networking. In organizations it’s called team building. And in life it’s called family, friends, and community. We are all gifts to each other, and my own growth as a leader has shown me again and again that the most rewarding experiences come from my relationships. – Michael Dell • We are at a crossroads in the music business: with the rise of the internet, the world we live in has changed, and the past is not coming back. But I see the glass as half-full: the internet and social networking are new avenues for the next Bob Dylan to be born on. – Jon Bon Jovi • We’re being asked to continually be “authentic” and “honest” with the world through social media. There’s a demand to post our wedding pictures, baby pictures (only minutes after the birth), our relationship status, and our grief and joys on Facebook and Instagram. Similarly, we construct persona through dating apps and networking sites. All of these social media networks exert pressure on us to share the personal details of our lives with unknown masses. So the pressure on the characters in “Openness” isn’t merely romantic, but public/social as well. – Alexander Weinstein • We’re currently living with a generation of established novelists who are embarrassingly out of date with respect to social networking, internet skills, and so on. – Charles Stross • We’re living at a time when attention is the new currency: With hundreds of TV channels, billions of Web sites, podcasts, radio shows, music downloads and social networking, our attention is more fragmented than ever before. – Pete Cashmore • We’ve done this before in other worlds, in other lives. It is our strength, law, medicine, entertainment, and computers, the networking of energy. All of these are arts. – Frederick Lenz • We’ve had such a close relationship with the fans. Through social networking and the internet, we have much more contact, and we did go to things like Comic-Con. So, I think people know most of our secrets. – John Noble • What being among the ‘right people’ entails is the possession of human capital, rather than organizational capital: an individual reputation, portable skills, and network connections. Career responsibility is squarely in the hands of individuals, a function of their knowledge and networks. Transferable knowledge is more important to a career than firm-specific knowledge. – Rosabeth Moss Kanter • What excites me is that, when things are tough, people become resourceful, and now with the Internet, social networking and the ability for people who in the past had been relatively powerless, they have tools to be able to spread ideas and organize. The urgency is there and the tools are there and I think that the possibility for really, really powerful results is there. I think it’s all brewing, it’s all bubbling up right now. – Shepard Fairey • What makes a great standalone piece of hardware is not the same thing as what makes a great networking device. One can work as an essentially closed system. The other is absolutely dependent on its openness. – Douglas Rushkoff • What makes networking work is that it sets up win-win situations in which all parties involved get to take something home. Networking is a sharing process. Until you understand that, you won’t have much of a network. – Earl G. Graves, Sr. • What you do is ultimately pointless. You could be replaced any day of the week with the first moron who walks in the door. So work as little as possible, and spend a little time (not too much, though) ‘selling yourself’ and ‘networking’ so that you will have backup and will be untouchable (and untouched) the next time the company is restructured. – Corinne Maier • Whatever you’re selling, storage or networking or security, you’re going head to head with the incumbent players. – Marc Andreessen • When people are using their devices, it’s probable that almost half are networking on social media. – Gary Vaynerchuk • When thinking about how to deploy kind of professional and social networking into your business, it’s really not a question of if, it’s a question of when. And the reason is, just think about the fact that those businesses that adopt new technologies to operate efficiently and use them to get a competitive edge are the businesses that in fact, you know, it becomes one more competitive advantage. Whether it’s a fax machine or a mobile phone or a new way of doing financing or any of these things, you know, these are key things to do. – Reid Hoffman • Wikis and social networking are just tools. – Jimmy Wales • Will the social networking phenomenon lessen? I don’t think so. – Marissa Mayer • With my wife Camille’s help, I took to social networking. I’m working with the computers. – Bill Cosby • With the advent of Twitter and Facebook and other social networking sites, genuine privacy can only be found by renting a private villa for a holiday. Hotels are now out of the question for my wife and I. – Robert Powell • With Twitter and other social networking tools, you can get a lot of advice from great people. I learn more from Twitter than any survey or discussion with a big company. – Daniel Ek • You are already leaders. Your ideas, your actions and your decisions make a difference. More than any other generation, you have a voice. Social networking is changing how we interact – and it can change our world. You are in touch with peers from around the world. You understand the power of instant communication. I appeal to you to use that power for the common good, the power of communication and the power of networking. – Ban Ki-moon • You thought you could figure that out online? Somehow I don’t think hellions are much into social networking. – Rachel Vincent • You try and nurture the relationship. This day and age we have to do a little more networking than we used to do. All that does is make sure you befriend the people you are working with on a project so you hopefully carry it over to the next one. – Aaron Zigman • Young people know how to use these social networking tools, and they know how to use them effectively. – Edward Norton • Younger Arabs are much less satisfied with education in the region than their elders, and are more comfortable networking and communicating via digital means. – Joe Saddi
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'a', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_a').html(obj); jQuery('#thelovesof_a img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'e', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_e').html(obj); jQuery('#thelovesof_e img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'i', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_i').html(obj); jQuery('#thelovesof_i img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'o', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_o').html(obj); jQuery('#thelovesof_o img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'u', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_u').html(obj); jQuery('#thelovesof_u img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
jQuery(document).ready(function($) var data = action: 'polyxgo_products_search', type: 'Product', keywords: 'y', orderby: 'rand', order: 'DESC', template: '1', limit: '4', columns: '4', viewall:'Shop All', ; jQuery.post(spyr_params.ajaxurl,data, function(response) var obj = jQuery.parseJSON(response); jQuery('#thelovesof_y').html(obj); jQuery('#thelovesof_y img.swiper-lazy:not(.swiper-lazy-loaded)' ).each(function () var img = jQuery(this); img.attr("src",img.data('src')); img.addClass( 'swiper-lazy-loaded' ); img.removeAttr('data-src'); ); ); );
0 notes
Text
#5yrsago What David Cameron just proposed would endanger every Briton and destroy the IT industry

David Cameron says there should be no "means of communication" which "we cannot read" -- and no doubt many in his party will agree with him, politically. But if they understood the technology, they would be shocked to their boots.
What David Cameron thinks he's saying is, "We will command all the software creators we can reach to introduce back-doors into their tools for us." There are enormous problems with this: there's no back door that only lets good guys go through it. If your Whatsapp or Google Hangouts has a deliberately introduced flaw in it, then foreign spies, criminals, crooked police (like those who fed sensitive information to the tabloids who were implicated in the hacking scandal -- and like the high-level police who secretly worked for organised crime for years), and criminals will eventually discover this vulnerability. They -- and not just the security services -- will be able to use it to intercept all of our communications. That includes things like the pictures of your kids in your bath that you send to your parents to the trade secrets you send to your co-workers.
But this is just for starters. David Cameron doesn't understand technology very well, so he doesn't actually know what he's asking for.
For David Cameron's proposal to work, he will need to stop Britons from installing software that comes from software creators who are out of his jurisdiction. The very best in secure communications are already free/open source projects, maintained by thousands of independent programmers around the world. They are widely available, and thanks to things like cryptographic signing, it is possible to download these packages from any server in the world (not just big ones like Github) and verify, with a very high degree of confidence, that the software you've downloaded hasn't been tampered with.
Cameron is not alone here. The regime he proposes is already in place in countries like Syria, Russia, and Iran (for the record, none of these countries have had much luck with it). There are two means by which authoritarian governments have attempted to restrict the use of secure technology: by network filtering and by technology mandates.
David Cameron has already shown that he believes he can order the nation's ISPs to block access to certain websites (again, for the record, this hasn't worked very well). The next step is to order Chinese-style filtering using deep packet inspection, to try and distinguish traffic and block forbidden programs. This is a formidable technical challenge. Intrinsic to core Internet protocols like IPv4/6, TCP and UDP is the potential to "tunnel" one protocol inside another. This makes the project of figuring out whether a given packet is on the white-list or the black-list transcendentally hard, especially if you want to minimise the number of "good" sessions you accidentally blackhole.
More ambitious is a mandate over which code operating systems in the UK are allowed to execute. This is very hard indeed. We do have, in Apple's Ios platform and various games consoles, a regime where a single company uses countermeasures to ensure that only software it has blessed can run on the devices it sells to us. These companies could, indeed, be compelled (by an act of Parliament) to block secure software. Even there, you'd have to contend with the fact that other EU states and countries like the USA are unlikely to follow suit, and that means that anyone who bought her Iphone in Paris or New York could come to the UK with all their secure software intact and send messages "we cannot read."
But there is the problem of more open platforms, like GNU/Linux variants, BSD and other unixes, Mac OS X, and all the non-mobile versions of Windows. All of these operating systems are already designed to allow users to execute any code they want to run. The commercial operators -- Apple and Microsoft -- might conceivably be compelled by Parliament to change their operating systems to block secure software in the future, but that doesn't do anything to stop people from using all the PCs now in existence to run code that the PM wants to ban.
More difficult is the world of free/open operating systems like GNU/Linux and BSD. These operating systems are the gold standard for servers, and widely used on desktop computers (especially by the engineers and administrators who run the nation's IT). There is no legal or technical mechanism by which code that is designed to be modified by its users can co-exist with a rule that says that code must treat its users as adversaries and seek to prevent them from running prohibited code.
This, then, is what David Cameron is proposing:
* All Britons' communications must be easy for criminals, voyeurs and foreign spies to intercept
* Any firms within reach of the UK government must be banned from producing secure software
* All major code repositories, such as Github and Sourceforge, must be blocked
* Search engines must not answer queries about web-pages that carry secure software
* Virtually all academic security work in the UK must cease -- security research must only take place in proprietary research environments where there is no onus to publish one's findings, such as industry R&D and the security services
* All packets in and out of the country, and within the country, must be subject to Chinese-style deep-packet inspection and any packets that appear to originate from secure software must be dropped
* Existing walled gardens (like Ios and games consoles) must be ordered to ban their users from installing secure software
* Anyone visiting the country from abroad must have their smartphones held at the border until they leave
* Proprietary operating system vendors (Microsoft and Apple) must be ordered to redesign their operating systems as walled gardens that only allow users to run software from an app store, which will not sell or give secure software to Britons
* Free/open source operating systems -- that power the energy, banking, ecommerce, and infrastructure sectors -- must be banned outright
David Cameron will say that he doesn't want to do any of this. He'll say that he can implement weaker versions of it -- say, only blocking some "notorious" sites that carry secure software. But anything less than the programme above will have no material effect on the ability of criminals to carry on perfectly secret conversations that "we cannot read". If any commodity PC or jailbroken phone can run any of the world's most popular communications applications, then "bad guys" will just use them. Jailbreaking an OS isn't hard. Downloading an app isn't hard. Stopping people from running code they want to run is -- and what's more, it puts the whole nation -- individuals and industry -- in terrible jeopardy.
(Image: Facepalm, Brandon Grasley, CC-BY)
https://boingboing.net/2015/01/13/what-david-cameron-just-propos.html
7 notes
·
View notes
Text
Dennis Prager. How Google Manipulates its Search Results to Influence Elections and D-Day.
Dennis Prager. How Google Manipulates its Search Results to Influence Elections and D-Day.
Segment 1-
Dennis talks to Robert Epstein, former editor in chief of Psychology Today. The topic is how Google manipulates its search results to influence elections…
Segment 2-
D-Day
Watch this video at- https://youtu.be/pHsAmOR5m00
PragerU
Published on May 27, 2019
On June 6, 1944, Allied forces stormed the beaches of Normandy in northern France. Their goal: to liberate Western Europe from Nazi tyranny. From a distance, it might seem that victory was pre-ordained, but no one felt that way at the time. British military historian Peter Caddick-Adams tells the incredible story of what happened on that monumental day.
Script: There were 36,525 days in the twentieth century. Of these, none was more consequential than June 6th, 1944. D-Day: the Allied invasion of Normandy in Nazi-occupied France. It did not end World War II, but without it, the Nazi war machine would not and could not have been defeated. We, of course, know the good guys – America, England and its allies – won. But in 1944, there was no certainty of success. In fact, there was just as much doubt as confidence. Winston Churchill’s senior advisor, Field Marshal Brooke, wrote in his diary, “I am very uneasy about the whole operation. It may well be the most ghastly disaster of the whole war.” Brooke’s fears were entirely reasonable. First there were tens of thousands of men and millions of tons of material and supplies that had to be moved one hundred miles across one of roughest bodies of water in the world – the English Channel. And it had to be kept secret. If the Germans knew where and when the allies were landing, they could mass forces against them and turn the beaches of northern France into killing fields. To prevent this, the Allies took every possible precaution. Their air forces destroyed bridges, roads and railways that might be used by the Germans to rush troops to the invasion site. Everyone knew the attack was coming; the key was to keep the Germans guessing. Fake radio chatter was broadcast to suggest the beaches near Calais would be the landing point. Double agents leaked fake details of units forming in South East England. And movie set designers built phony tanks, planes and ships to support the ruse of an army preparing to cross near Dover for the benefit of German reconnaissance pilots and spies. The Germans swallowed it all. But the Nazis were not the only enemy the Allied forces faced. Mother Nature was just as threatening. The 23,000 paratroopers and glider-borne infantry jumping into Normandy needed moderate winds to be effective. The twelve thousand Allied aircraft needed clear skies. The invasion fleet of six thousand vessels needed calm seas. And there had to be a low tide to expose Nazi obstacles and mines. When high winds and rain began pummeling the Channel, Allied supreme commander General Dwight Eisenhower postponed the invasion date of June 5th by twenty-four hours. That might not sound like a significant delay, but it was. All forces were concentrated and ready to go. All the plans, all the deceptions, could be exposed at any moment. Then came a new forecast. The weather appeared to be breaking. There might be a 12-hour window of opportunity. Eisenhower gave the order: We go. Immediately, the greatest invasion fleet ever assembled set sail. On board were over 130,000 young soldiers. Consider for a moment who these soldiers were. The average age of the American GI was 21. Most had never seen combat or even been fifty miles from their hometown. As they sailed toward the French shoreline, Eisenhower wrote a press release in case of catastrophe. D-Day was an all-or-nothing affair. A new invasion strategy would take months, if not years, to devise. For the complete script, visit https://www.prageru.com/video/d-day
Donate today to PragerU! http://l.prageru.com/2eB2p0h To view the script, sources, quiz, and study guides, visit https://www.prageru.com/video/d-day VISIT PragerU! https://www.prageru.com Get PragerU bonus content for free! https://www.prageru.com/bonus-content Join Prager United to get new swag every quarter, exclusive early access to our videos, and an annual TownHall phone call with Dennis Prager! http://l.prageru.com/2c9n6ys Join PragerU's text list to have these videos, free merchandise giveaways and breaking announcements sent directly to your phone! https://optin.mobiniti.com/prageru Do you shop on Amazon? Click https://smile.amazon.com and a percentage of every Amazon purchase will be donated to PragerU. Same great products. Same low price. Shopping made meaningful. FOLLOW us! Facebook: https://www.facebook.com/prageru Twitter: https://twitter.com/prageru Instagram: https://instagram.com/prageru/ PragerU is on Snapchat! JOIN PragerFORCE! For Students: http://l.prageru.com/2aozfkP JOIN our Educators Network! http://l.prageru.com/2aoz2y9
Segment 3-
Dennis Prager talks to Peter Caddick-Adams, lecturer in military history and current defense issues at the Defence Academy of the United Kingdom. His new book is Sand and Steel: The D-Day Invasion and the Liberation of France. He also teaches the newest PragerU video, “D-Day.”
--------------------------------------------------------------------
Visit Pragertopia https://pragertopia.com/member/signup.php
The first month is 99 cents. After the first month the cost is $7.50 per month. If you can afford to pay for only one podcast, this is the one we recommend. It is the best conservative radio show out there, period. ACU strongly recommends ALL ACU students and alumni subscribe to Pragertopia. Do it today!
You can listen to Dennis from 9 a.m. to Noon (Pacific) Monday thru Friday, live on the Internet http://www.dennisprager.com/pages/listen
------------------------------------------------------------------------
For a great archive of Prager University videos visit-
https://www.youtube.com/user/PragerUniversity/featured
Donate today to PragerU! http://l.prageru.com/2eB2p0h
Get PragerU bonus content for free! https://www.prageru.com/bonus-content
Download Pragerpedia on your iPhone or Android! Thousands of sources and facts at your fingertips. iPhone: http://l.prageru.com/2dlsnbG Android: http://l.prageru.com/2dlsS5e
Join Prager United to get new swag every quarter, exclusive early access to our videos, and an annual TownHall phone call with Dennis Prager! http://l.prageru.com/2c9n6ys
Join PragerU's text list to have these videos, free merchandise giveaways and breaking announcements sent directly to your phone! https://optin.mobiniti.com/prageru
Do you shop on Amazon? Click https://smile.amazon.com and a percentage of every Amazon purchase will be donated to PragerU. Same great products. Same low price. Shopping made meaningful.
VISIT PragerU! https://www.prageru.com
FOLLOW us! Facebook: https://www.facebook.com/prageru
Twitter: https://twitter.com/prageru
Instagram: https://instagram.com/prageru/
PragerU is on Snapchat!
JOIN PragerFORCE! For Students: http://l.prageru.com/2aozfkP
JOIN our Educators Network! http://l.prageru.com/2aoz2y9
------------------------------------------------------------------------
HELP US SPREAD THE WORD!
Please send to friends, post on Facebook, twitter, etc…
Over 3,000 commercial free archived shows are available on our podcast site here.
Ways to subscribe to the American Conservative University Podcast
Click here to subscribe via iTunes
Click here to subscribe via RSS
You can also subscribe via Stitcher
You can also subscribe via SoundCloud
Listen to ACU on PlayerFM
If you like this episode head on over to iTunes and kindly leave us a rating, a review and subscribe! People find us through our good reviews.
FEEDBACK + PROMOTION
You can ask your questions, make comments, submit ideas for shows and lots more. Let your voice be heard.
Download our FREE iOS App.
Download our FREE Android App.
Email us at americanconservativeuniversity@americanconservativeuniversity.com
Click here to download the episode
0 notes
Text
Like the Wind
May 23
Kyoto, Hiroshima
Today we took advantage of the lack of a deadline for check-out and slept in at our hostel. It was nice to have a slower morning and to be able to set our schedule more freely. When we were ready to go we loaded ourselves up with our luggage and made the trek back to the train station. By this point we were very familiar with this road as we had walked it many times and it felt a little bittersweet to say goodbye to the usual places. How easy it is to get attached to a city!
At the station we went in search of lunch and ended up at a steak restaurant. (We did pass by the pizza place, which wasn’t open yet, but I did peek in. I realized that some of the staff were already there and quickly carried on in my surprise.) G did an excellent job navigating and we were happy at how much more familiar we were with the station as it is one of the more complicated ones we’ve been to in terms of layout. We also saw lots of groups of schoolchildren heading on school trips. We were very impressed with their good behavior and the courage of their teachers to take them, since they were obviously going overnight.
When our train showed up on the board listing the platforms we decided to go up early and were delighted to find a bench to sit on while we waited. Soon enough we boarded and were off to our first stop, Shin-Kobe. We had a pretty tight connection but luckily the next train was departing from the same platform so it was a breeze to switch over. (We were very thankful for the JR staff who booked our train reservations as everything has been so smooth thus far.)
Another hour or so on the train - always fun on a bullet train - and we were in Hiroshima. We decided to step into the ticket office to book our last few trains so that everything would be done. As always, the staff were very helpful and it was easy to make the needed reservations.
Since we had spied a Mister Donut a ways back in the station, we felt a craving for donuts and headed back that way. We had to go through the ticket gate again and then return through to exit, and we thought perhaps the staff would think we were a little nuts. Thankfully, they waved us on dispassionately. We concluded that they had probably seen stranger occurrences in the course of their work.
Our next step was slightly confusing as we figured out that what we assumed would be a subway line was actually a streetcar. However, we were able to locate the right one and get on fairly quickly. It was also good because we were able to use our same transit cards (IC cards) to pay. Just a few stops away we alighted again and found our way to our hotel, which was very close to the stop.
We checked into our room on the 8th floor and settled in for a break. After figuring out the air conditioning, we settled into the comfy bed and relaxed, even taking a little time to nap. (Again, I can’t nap, but it was nice to rest.)
Around 8 pm we started to think about dinner so we googled the restaurants nearby to try to find one. After a few minutes we set out into a close-by area that seemed promising and began our search. Usually we try to look at signboards to assess a place, but I had seen a bbq restaurant on the listing so we headed there. Unfortunately they were full, so we continued on.
Around the corner we spotted a 2nd floor restaurant that looked open, which turned out to be a Korean food restaurant. Needless to say, I was very excited about that! They were playing Korean music and I was happy as we took our seats... but we soon realized they didn’t have any English on their menu. I was determined to figure it out as the sections were labeled and I had a translator app on my phone, but before I got to it a lady came up to us and explained that they didn’t have an English menu but that she could help us to order. (We never did figure out if she was on staff or not.) By asking us what kind of food we wanted (meat and rice), about how much we wanted to spend, and whether we liked spicy food or not, she said they would prepare some dishes for us.
It was a little nerve-wracking not to know what we ordered but also exciting. First they served us a dish with meat, lettuce, kimchi, and sauce. The server mimed an action to explain but I had already recognized the ingredients for ssam (where you wrap everything in the lettuce) and said so. She seemed surprised but nodded and then went back to the other staff member in the open kitchen and said something to him about it with a laugh, which was cute. I think we surprised them a little too.
The ssam was delicious and was followed by a seasoned, breaded chicken dish (very Korean-style fried chicken - it was also excellent). They also served us a third meat dish with seasoned slices of what may have been pork, and a “half-serving” of bibimbap which could have been a meal on its own. All in all, it was a ton of food, but it was SO good! I enjoyed every dish, which was pretty good considering that we didn’t personally order any of them. It did help a lot that I was familiar with Korean cooking and recognized most of the dishes.
When we went up to pay, the meal was exactly the price we had determined with the other lady before, which we were happy to pay. The two staff were happy to hear that the food had been good, and when we went to leave they stopped us and gave us a small package to take with us. We thanked them and left, and when I looked closer I realized the package was gim or seaweed pieces. It made me laugh as it was a bit random but we took it as a sign of kindness.
We popped by 7-11 on our way back to the hotel to buy ice cream and were rewarded with finding garigarikun ice cream, which was “Japanese soda”-flavored. This was the ice cream G’s favorite character always eats, so we were excited and both got one to try. Unsurprisingly, they were yummy! Light and refreshing. It was a perfect end to a laid-back day of travel and spontaneous decisions.
0 notes
Text
Pinterest Management Services Expert Reveals Why Investing in Promoted Pins Is Not Optional
New Post has been published on https://businessqia.com/awesome/pinterest-management-services-expert-reveals-why-investing-in-promoted-pins-is-not-optional/
Pinterest Management Services Expert Reveals Why Investing in Promoted Pins Is Not Optional
Why You Need to Include Promoted Pins in Your Pinterest Marketing Strategy in 2019
If your business has been leveraging Pinterest marketing since it’s fruition you’ve most likely grown your traffic organically. But guess what? That is all about to change. As a Pinterest Management Services expert I can suspect that as Pinterest prepares for its IPO next month that they will tighten up their algorithm to restriction organic reach and make it harder to rank high use free organic entails. Pinterest will have no choice because they in it to make money now. They have to please their investors. They want to drive their stock price up. This is how all the insiders will cash out. You get this right?
What that means to you is you will have to invest in Pinterest ads( Promoted Pins ). It is no longer an option. It must be part of your Pinterest marketing strategy in 2019 and beyond.
Advertising on Pinterest Gives Your Brand Instant Visibility
This is especially important to those who are just starting out on Pinterest. Competition is becoming more and more fierce. Investing in ads is like saying to Pinterest “I’ll pay you if you put my products/ content in front of my target audience right now”.
If you don’t invest in Promoted Pins you have to let your content bake for some unknown amount of day so that it shows up high on Pinterest’s search engine( Assuming you optimized your content correctly ). Bottom line, pay to get determined right away or don’t pay and hope and pray your content will rank high in search eventually.( Unless you use an expert service like ours ).
I’ll dig deeper in a bit to help you decipher how to find your competition on Pinterest and what to look for. But first, let me give you an overview of the type of ads available to you.
4 Types of Pinterest Ads
1) If your goal is to build awareness for your business select “Brand awareness”. I’m not too keen on brand awareness; I don’t think it’s the best use of your marketing dollars. Traffic is what we focus on most of the time as shown below on# 3.
2) If you want to get more eyeballs on your videos select “Video views”.
3) If you want to drive more traffic to your site select “Traffic”. This is typically what we do most in our Pinterest account management services. At the end of the day you want people going to your website or blog.
4) If you want Pinterest users to install your app, choice “App install”.
You can also target the right audience for your business. You can choose audiences, interests, keywords, or expanded targeting–or any combination of these. So what do they actually entail?
1) Audience targeting
This allows you to reach Pinterest users based on information you know about them, information that Pinterest has about them or a combination of both. You can target people on your customer listings, re-target people who have visited your site or engaged with your ads or create actalikes from people who behave similarly.
2) Interest targeting
This allows you to reach Pinterest users based on the boards they have create and pins they’ve engaged with( saved or clicked ).
3) Keyword targeting
This allows you reach Pinterest users based on the keywords they are using when they’re searching for pins on Pinterest.
4) Expanded targeting
This allows you to find new Pinterest users to reach based on the content of your ad and what Pinterest knows about people on Pinterest.
8 Smart Reasons Why You Need to Spy on Your Competition
Now, let’s go over who your competition is on Pinterest. Speaking as a Pinterest Management Services expert I think it is vital that you build the time to do this so you learn what’s driving traffic them. Watching your competition closely is important so :P TAGEND
you learn how new trends are embraced by the consumers you’re all opposing to keep you see how what types of content are working so you can do more of that, but better you anticipate transformations in the market you place new trends you learn new tactics you decide what to charge for your products and/ or services you stay on the cutting edge of what’s working within your niche you maintain getting better and better. Competition brings out the best in us!
How to spy on your competition and what to look for :P TAGEND
1. Make a list of your top 5 challengers.
You can do this two ways :P TAGEND
a) Go on Google and search via their company name. When you have found their website go to their home page and look for their social icons which are typically on the bottom of the page or above the fold somewhere. Above the fold means where the content is positioned in the upper half of a web page without scrolling down the page.
b) Or failing alternative “a” above go on Pinterest and kind in their business name in the search box, then click “People” to the right of the search box.
Don’t be surprised if you don’t find them under “People” because if they have not properly optimized their Pinterest profile they won’t show up.
2) Observe what people are pinning from their website.
You can do this two ways. Let’s say you sell natural skin care products and one of your challengers is Pure Fiji.
Go to your browser and kind https :// www.pinterest.com/ source/ purefiji.com /
Look at which images people are saving the most. Once you’ve identified them save them to your secret committee. Ask yourself :P TAGEND
a. Why do you think this image received a ton of engagement? What can you learn? Is it because of the type of image? For instance, is it an infographic, a checklist, does it have great text overlay, etc.
b. What can you do similar but better?
c. Is the topic evergreen or does it address people’s objectives or concerns right now?
3) Use BuzzSumo
BuzzSumo will reveal what people are sharing the most. It shows your competitor’s top content in the past 24 hours and up to five years or a specific range.
4) Sign up to receive their emails
You can sign up to receive their emails or use a tool like Mailcharts. This tool can give you insight into your competitors’ email marketing, from the frequency of email sends, their subject line tactics, and more.
5) Subscribe to their blog
6) Follow them on social media
7) Shop on their site and then abandon it and see what happens
8) Purchase a product
How was your experience from the beginning up to the moment you receive the product. This will allow you to really experience their customer service. If you detest the product and would like to return it, what was your experience?
Just as Pinterest is constantly evolving so are your competitors. It’s vital that you keep an eye on your rivalry every six months- it’s not something you do once and think voila I’m done. By doing a regular competitive analysis you will have a better understanding of your marketplace over period, and learn from them too. Remember…none of us knows it all.
Have you purchased Pinterest ads? If so, what was your experience? Have you spied on your competition? What “d you learn”?
If you’re not sure how to use buy ads or how to get started check out my step by step guide on How to Buy Pinterest Ads: How to Boost Your Performance With Promoted Pins .
The post Pinterest Management Services Expert Reveals Why Investing in Promoted Pins Is Not Optional seemed first on White Glove Social Media.
Read more: whiteglovesocialmedia.com
0 notes