#and i worked on a relationship web diagram thing to see who connected to who and how which is fun
Explore tagged Tumblr posts
Text
i think for a drop of silver's character descriptions i'm just going to stick to updating the one on quotev - it's just kind of annoying to do it on there and over here and i don't feel like scrolling to find that tumblr post everytime i add more characters
anyways i just updated the quotev journal post with some new side characters *thumbs up emoji here*. kind of obsessed with senka she's so cool
#a drop of silver#yes i'm working on the fic again#i rested and now i am back at it#spent a couple hours working on concrete backstories to reference for the love interests today#i had like ideas in mind and pretty much settled for most of them i just hadn't properly written them down yet#except ceri's i'm still not concrete on his i'm debating#which is kind of an issue cause he'll be the next shifted perspective#also updated the summary post on quotev and worked on my own outline#color coordinated and everything#and i worked on a relationship web diagram thing to see who connected to who and how which is fun#also color coordinated for relationship type#lot's of organization type stuff for today i got locked in
3 notes
·
View notes
Text
roscoe’s notebook post
A while back I said I was going to write a post about the way I use notebooks for writing projects. This is the first of several posts about Writing Process I’ve been tossing around in my drafts for a little while as a result of conversations with friends, so bear with me.
I. Love. Notebooks. I genuinely would have to deeply overhaul my whole Process of writing anything on the longer side if I were to go paperless; I find physical paper pretty invaluable when I’m outlining, brainstorming, and researching, and I still probably write ¼-⅓ of all my actual content on paper first. (That proportion used to be a lot higher, but I’ve gotten better at being productive on a computer in recent years, which is great.) I’m a very visual person, so notebooks really help me visualize my ideas, story structure, etc. It’s very helpful to be able to use arrows and diagrams and physically strike things through, and the tactility is really soothing to me. If I show people my notebooks or talk about them, I often get a response like “this is so organized”, which is sort of true, but I have to stress that it’s “organization for a disorganized mind”; I can’t misplace ideas or notes if it all goes into the same physical object, vs. electronic notes, which are much more, like “Did I say that in a voice memo? PM it to myself on Discord? Leave it in a desktop sticky note? Write it directly into the Google Doc? Who knows! It’s lost to time!”. It’s very much an ADHD management strategy.
It helps that I’m a very neophyte stationery hobbyist and appreciate any excuse I have to use my pens, but I also will go off at any opportunity about how helpful I find them for writing projects, which is why I decided to just make a post about it. Right now I mostly use them for (fan and original) fiction projects, but I used a notebook for a very similar purpose when I was working on my undergrad thesis, and I have a slightly different but equally necessary-to-me approach to notebooks I use at work.
My typical structure for a notebook that’s devoted to one project only looks like this:
I always leave the first couple pages blank so I can go back and retroactively index bujo-style. I don’t always actually do the index, because sometimes I get too lazy, but I like having those blank pages there to give me the option. I also usually put epigraphs/inspo quotes on the first page.
After that, there’s often (but not always, I’ll talk about it) a couple pages at the start where I’m frantically jotting down loose brainstorming ideas before they've coagulated into a story structure. Just, like, vomiting into the void.
Stemming out of that, I usually write out about like 5-10 pages of outline-style notes in chronological order, laying out all the main story beats and charting out the story trajectory. This will inevitably get revised and rewritten many times, but I find the process of writing these wide-angle synopses really useful for dislodging ideas, making connections re: thematic threads, etc. from my brain.
I’ll devote a couple pages after that to specific things like "sex scene brainstorming", "random scene ideas/minor details that don't have a clear place in the outline right now but I'll turn to for inspo later" [this is what I refer to as “bits” in one of the later photos], "page where I just outline the Motifs And Themes", "research notes", "to-do list", "stuff to check on a second pass", "things to put in the a/n and AO3 tags", etc.--the specifics vary with the story.
Then, I skip ahead to approx. halfway through the notebook and cordon off the rest of the pages to be “free writing” space, AKA writing of actual content rather than planning, with the expectation there will be no internal organization and I’ll transcribe to laptop as I go. Writing on paper feels less binding than typing something on a computer; it’s like a little secret kept with myself, and it doesn’t need to go anywhere or be seen by anyone if I decide I don’t like it. Setting aside pages in the back half of the notebook means that, as more things come up re: planning, I can go back and add those in the rest of the pages that were intentionally left blank. This is how I avoid (for the most part) having the whole thing be a jumbled mess where there’s no separation between the notes and the actual story writing; I learned this the hard way via the first notebook I’ll show you in a second. I’ve recently gotten really into using Muji sticky note tabs to label any pages/sections of particular import that don't want to have to refer back to in the index and would rather just flip to instantly.
I do use notebooks that aren’t specific to any one project, but those are much less organized and less worth sharing.
Before I look at more recent stuff, here are some selections from my notebook for the project that got me into writing longfic, my Golden Kamuy canon divergence AU (with apologies for the bad photos, my phone’s camera is trash). I worked on this from Sept 2018-July 2019. It was a learning experience in a lot of ways, and notebook utilization was one of those. I’ve always used notebooks for keeping track of writing projects, as I said earlier, but before this it was largely without much organization or structure; just total chaos. Having a physical notebook became really important for this project because it was a sprawling multichapter story with rotating POVs and a lot of historical research. I also learned a lot about what not to do with a notebook, personally, or at least things that don’t work so well (for me). This was a college ruled spiral-bound Decomposition Book, for the record.
By the time I bought a notebook for it I already had a (very basic) plot outline in mind, so I wasn’t doing that very initial ground-zero brainstorming in here; I was copying out of my phone’s notes app, basically, and then going from there.
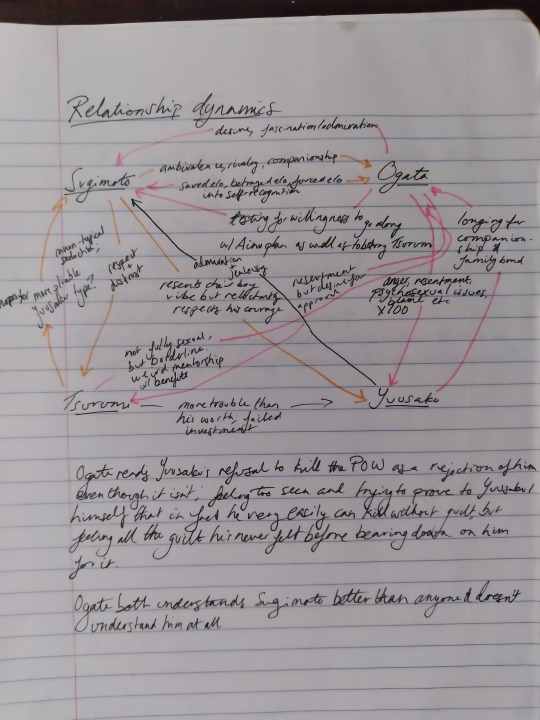
This is one of the first pages in this notebook; I wanted to visualize the relationship web between the four central characters in the story in terms of how they feel about one another. The two colours correspond to the POV characters (Sugimoto in orange, Ogata in pink), and I used this colour-coding throughout the notebook with highlighters, etc. to keep track of information that was more relevant to one character than the other. Tsurumi and Yuusaku aren’t POV characters, but they’re prominent in the story and their presence impacts the central relationship between Sugimoto and Ogata, and it was helpful to me to map out the emotional ecosystem, as it were.

(There are coffee stains all over this, because I wrote the vast majority of the story in coffee shops because I didn’t want to be around my roommates, lol. This is part of why I never do fiction writing in notebooks that are too nice, I get neurotic about needing to keep them tidy. I can’t use ones that are too shit though, either, so it’s a bit of a narrow window. I’ll talk more about brands and paper quality etc. later.)
As you can see, this is the first page of many I set aside specifically for jotting down different pieces of historical information relevant to my story. It’s about fictional characters who are members of an army division that existed in real life, and both the canon and my fic involve a high level of attention to detail with regards to which divisions were present for which battles, etc., as well as general historical details specific to the Russo-Japanese War setting--what did people eat in the trenches? What did they do to fill time? How did they get through the winter? What did third party observers have to say about the conditions? What were the specs of their weaponry (particularly important because one of the POV characters is a sniper and gun nut)? I did a lot of reading (and watching of antique gun collector Youtube videos... the things I do for love, eh), and it came in handy so many times, because it turns out it’s much easier to write trench warfare slice of life if you have factual details to pull from when you don’t know what to do with a scene! Imagine that!
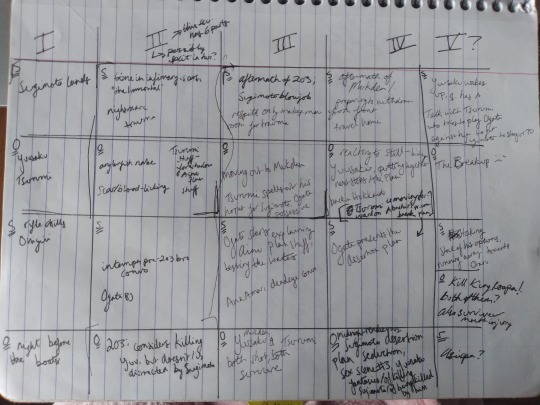
This is the first of three “grid outlines” I made; this is a way I sometimes like to visualize a story outline all on one page, with the columns representing chapters and the squares within the columns representing sections/scenes within the chapters. As you can see, early on I was hoping to get this done in five or even FOUR chapters (whatmakesyouhaha.mp3), with POV switches happening internally within the chapters. This proved to be unwieldy for many reasons, so I revised the outline:
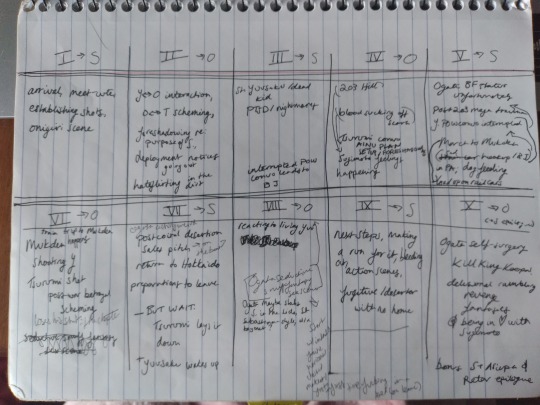
Here I’d come to terms with the fact this story was going to have a lot more chapters than I’d planned, and I rearranged things so that it would happen in ten, with each chapter belonging to only one POV character. This also needed revising later, and in the end the story looked a bit more like this (though it did in fact end up being twelve chapters, but only because Chapter Ten was like, 12k, and needed to be split in two chunks):
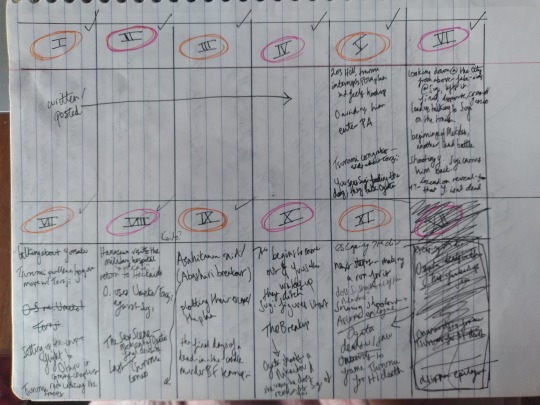
I must have remembered to bring my fineliners to the coffee shop this time, lol, because as you can see it’s properly colour-coded this time. This outline was made when I was already four posted chapters into the fic, which hopefully gives you a sense of the way in which I am sort of a planner and a pantser; I can’t get into a longer project without an outline, but the outline inevitably changes many times throughout writing and I often end up with a finished product that looks pretty different from what I was intending. My creative M.O. as always is Do The Maximum! Amount! Of! Work! Possible!

This is what a “free writing” page looks like, for me. In this notebook I didn’t set aside any specific spaces for free writing so it’s strewn throughout the notebook in a really disorganized way and I was constantly flipping through looking for bits I’d written and forgotten to transcribe, and I decided to be more organized in future as a result of that. If something’s crossed through, that means I transcribed it. As you can see, they’re often small sections, sometimes just a coupled decontextualized sentences. About 3/4 of what I write in a notebook makes it into the story, I’d say; some of it never goes anywhere, and that’s OK. I have less of an issue killing my darlings if they never make it off the paper page.

A very brief, top-down chapter outline, where the goal was not to get too bogged down in details and just to visualize the beats and pin down what they’re trying to accomplish. Chapters for this fic typically ran about 6k, and five or six scenes per chapter was pretty common, so the average scene length was about 1-1.25k words/scene. IDK why I called it storyboarding when I didn’t make drawings. (Margin numbers are to keep track of word count, since I was using a daily word count tracker while writing this.)

This page was, as titled, for keeping track of the various balls in the air when I was about 2/3-3/4 of the way through the story and really feeling the pressure with regards to tying up the various loose ends. This was... a struggle. I hadn’t ever written anything longish (this fic ended up just under 70k) that had an action plot before, let alone a canon divergence scenario where I had to engage with and explain away various canon plot elements so I could maintain the audience’s suspension of disbelief.
Now, I mentioned earlier that I learned various “things not to do” with my notebooks while working on that project. One of those lessons I learned is to be more realistic when assessing how big a project is likely to get, not least because I RAN OUT OF PAGES around the chapter 9-10 mark. In my defense though, that’s because I’d never written anything even half this long! But I know better now, and try not to be in denial. Finishing the notebook early was a way bigger problem than I’d anticipated, and was part of the reason the last few chapters took several grueling months to finish. The issue was that I needed to be able to use a notebook to maintain my workflow--attempting to do it only on a computer was dismal--but it seemed silly to start a notebook of a similar size to the one I’d finished (80pg, approximately B5 dimensions) when there was no way it would need that much space, especially since the reference pages, like the historical notes, didn’t need to be transcribed over. I was also pretty broke at the time and didn’t want to spend money unnecessarily, lol. I tried to get by using a Moleskine Cahier for a month or so because I had one lying around, but it was horrid; it was too small to be used comfortably, it wasn’t spiral-bound so it wouldn’t lay flat, the ghosting is terrible and I hate the way Moleskine paper feels, etc. Eventually I caved and went to Muji and bought a 30ish page A5 with closer to lay-flat binding, and I finished the story in there. I would take a comparative pic for you of the relative notebook sizes and include some of the scene staging diagrams, etc. I put in there, but I can’t find it :(
So I learned that specs really do matter, and it’s okay to be picky if the pickiness is going to make the difference between actually using a notebook or not. Things that are important to me in my notebooks:
Ruling (gotta have ruling, I can suffer through grid but blank or dot is a no-go)
Size (I can’t use anything smaller than at least a medium-large notebook, I find it claustrophobic and get miserly about page space)
Binding (twin ring is my preference because it looks and feels better than a classic spiral but has the same comfort of use with regards to bending the pages back to suit workspace size and laying flat with ease)
Paper quality and colour (I don’t like anything too slippery/smooth or with too much visible ghosting, and I strongly prefer an off-white paper to bleached paper--part of why I don’t use Decomposition Books anymore, the paper is scratchy and it’s too damn bleached!)
Pagecount relative to size of project
Portability (in non-COVID times; anything bigger than a B5 wouldn’t fit in the satchel I used to bring to work at my old job), etc.
But everyone’s taste is different in this respect, and the only way to figure out what works for you is through trial and error, I’m afraid. I also suspect I’m more neurotic and particular about the sensory experience of using a notebook than most people are, but I yam what I yam.
Now to talk about the notebooks for my current projects, where I’ve refined my approach somewhat. I’ve included less photos for these because they’re ongoing WIPs I don’t want to spoil completely, but I’ve tried to include some outline-type stuff to give you an idea.
My big bang fic is in the very ugly twin ring notebook on the right; I got it at a dollar store by my house because I needed something to work in and didn’t want to wait for an online order, but it’s been very serviceable for my needs. The paper isn’t even bad. The bigger notebook (B5) is my Sangcheng fic.

I wanted something with a lot of pages for this, because I knew it was going to be a long story, and for some reason the fact it’s smaller than my usual preference doesn’t bug me (I think it’s an A5?); it just fits this story, somehow. I’m not sure exactly how many sheets are in here but I’d guess about 150.

Because this notebook has upwards of 100 sheets, I made a lot of use of sticky-note tabs to label high-priority pages. The colour coding of these doesn’t mean anything, it was just whichever ones I had at hand at any given moment. These are those tabs from Muji I mentioned, I’m really obsessed with them--the shape makes them so much less obtrusive and more practical than conventional squares/rectangles OR flag shapes, IME.


My big bang story is nonlinear, so, similarly to what I did with colour coding for the two POVs for my GK fic, this story has two main colours corresponding to whether a given section takes place in the “before” or the “after” portions of the timeline, with blue as “after”, yellow as “before”. This is what the most current version of the outline looks like in there:

If you squint, you can see the alphanumeric notes in the top right of each section entry; I gave them each a code like “A3″ or “B5″ corresponding to their position in the story sequence (so, it goes A1, B1, A2, B2, etc., through to B9 and then the epilogue). [Unintentional that this schema overlaps with notebook size labeling and so is kind of confusing in the context of this post.] At first I was just keeping track of the sections via the highlighted titles, but it got confusing because I’d write down “Wedding” or “Yiling” in my notes and then refer to the notes later like “but there are multiple marriages?? and multiple scenes in Yiling??”. Stuff gets struck through with a straight line if it’s been written in a more-or-less complete form and crossed out with a squiggly line if it’s been cut from the outline or made redundant.
As I said earlier, I started out all the initial brainstorming for my Sangcheng fic in its notebook, instead of brainstorming it in someone’s DMs/my notes app/a voice memo/etc. and then transcribing it into the notebook in a somewhat more organized fashion, which is how my stories usually start out. Because of this, the first five-ish pages are basically just stream of consciousness rambling where I was trying to jot down every disconnected thought I had about the story concept. I don’t have photos for that because it’s too spoilerific for later developments in the fic, but I can show you some of the stages the outlines went through, once I was able to corral those initial notes into a story structure:

All the chapters in this fic have their own highlighter colour, so when I started trying to make sense of my initial brainstorm notes I just went through and highlighted stuff in the colour of the chapter it would make the most sense for, and then transcribed things more-or-less in chronological order into the relevant chapter outline. I later ended up rewriting all the chapter outlines AGAIN to refine them and divide them internally by the individual scenes, which makes them a lot more legible and less wall-of-text-y. They look like this now, with about four sheets per chapter:

Because this fic is on the longer side, I have some pages that are just for keeping track of other story elements, like this, where I refer back to whatever the fuck the “themes” are supposed to be whenever I forget what this fic is about:

It’s all about the visionboarding... Anyway, that’s most of what I have to offer, since most of these two notebooks is Forbidden Content.
With regards to brands/supplies, I really like this Kokuyo Campus Wide notebook that I’m writing Sangcheng in, it’s pretty perfect for me. I also like the B5 Muji twin rings, but those only come in 30 sheets, so I wouldn’t use it for anything above a ~20k project. The B5 Maruman Spiral Note 6.5mm ruled/80 sheet is another good one, though I wish it was twin ring instead of spiral. As you can tell, I like Japanese stationery brands because it’s easier to find decent paper quality and minimalist design without shelling out $$ than it is with American/European brands, at least IME. I like Rollbahns too. But honestly, I can usually find pretty serviceable random notebooks that aren’t brand-name from Asian dollar stores; it’s really not something where you need to shell out tons of money.
29 notes
·
View notes
Text
5m Mathmrs. Mac's Messages

TLDR: With a bit of research and support we were able to demonstrate a proof of concept for introducing a fraudulent payment message to move £0.5M from one account to another, by manually forging a raw SWIFT MT103 message, and leveraging specific system trust relationships to do the hard work for us!
5m Mathmrs. Mac's Messages App
5m Mathmrs. Mac's Messages Message
5m Mathmrs. Mac's Messages To My
5m Mathmrs. Mac's Messages For Her
Before we begin: This research is based on work we performed in close-collaboration with one of our clients; however, the systems, architecture, and payment-related details have been generalized / redacted / modified as to not disclose information specific to their environment.
A desktop application for Instagram direct messages. Download for Windows, Mac and Linux.
Have a question, comment, or need assistance? Send us a message or call (630) 833-0300. Will call available at our Chicago location Mon-Fri 7:00am–6:00pm and Sat 7:00am–2:00pm.
5m Mathmrs. Mac's Messages App
With that said.. *clears throat*
The typical Tactics, Techniques and Procedures (TTPs) against SWIFT systems we see in reports and the media are - for the most part - the following:
Compromise the institution's network;
Move laterally towards critical payment systems;
Compromise multiple SWIFT Payment Operator (PO) credentials;
Access the institution's SWIFT Messaging Interface (MI);
Keys in - and then authorize - payment messages using the compromised PO accounts on the MI.
This attack-path requires the compromise of multiple users, multiple systems, an understanding of how to use the target application, bypass of 2FA, attempts to hide access logs, avoid alerting the legitimate operators, attempts to disrupt physical evidence, bespoke malware, etc. – so, quite involved and difficult. Now that’s all good and fine, but having reviewed a few different payment system architectures over the years, I can’t help but wonder:
“Can't an attacker just target the system at a lower level? Why not target the Message Queues directly? Can it be done?”
A hash-based MAC might simply be too big. On the other hand, hash-based MACs, because they are larger, are less likely to have clashes for a given size of message. A MAC that is too small might turn out to be useless, as a variety of easy-to-generate messages might compute to the same MAC value, resulting in a collision. WhatsApp Messenger is a FREE messaging app available for iPhone and other smartphones. WhatsApp uses your phone's Internet connection (4G/3G/2G/EDGE or Wi-Fi, as available) to let you message and call friends and family. Switch from SMS to WhatsApp to send and receive messages, calls, photos, videos, documents, and Voice Messages. WHY USE WHATSAPP. Garrick Hello, I'm Garrick Chow, and welcome to this course on computer literacy for the Mac. This course is aimed at the complete computer novice, so if you're the sort of person who feels some mild anxiety, nervousness, or even dread every time you sit down in front of your computer, this course is for you.
Well, let's find out! My mission begins!
So, first things first! I needed to fully understand the specific “section” of the target institution's payment landscape I was going to focus on for this research. In this narrative, there will be a system called “Payment System” (SYS). This system is part of the institution's back-office payment landscape, receiving data in a custom format and output's an initial payment instructions in ISO 15022 / RJE / SWIFT MT format. The reason I sought this scenario was specifically because I wanted to focus on attempting to forge an MT103 payment message - that is:
In this video I will show you where to locate the serial number on a Western golf cart. Ebay Store: Please SUBSCRIBE. Western golf cart serial number lookuplastevil.
MT – “Message Type” Literal;
1 – Category 1 (Customer Payments and Cheques);
0 – Group 0 (Financial Institution Transfer);
3 – Type 3 (Notification);
All together this is classified as the MT103 “Single Customer Credit Transfer”.
Message type aside, what does this payment flow look like at a high level? Well I’ve only gone and made a fancy diagram for this!
Overall this is a very typical and generic architecture design. However, let me roughly break down what this does:
The Payment System (SYS) ingests data in a custom - or alternative - message format from it's respective upstream systems. SYS then outputs an initial payment instruction in SWIFT MT format;
SYS sends this initial message downstream to a shared middelware (MID) component, which converts (if necessary) the received message into the modern MT format understood by SWIFT - Essentially a message broker used by a range of upstream payment systems within the institution;
MID forwards the message in it's new format on to the institution's Messaging Interface (let's say its SAA in this instance) for processing;
Once received by SAA, the message content is read by the institution's sanction screening / Anti-money laundering systems (SANCT).
Given no issues are found, the message is sent on to the institution's Communication Interface (SWIFT Alliance Gateway), where it's then signed and routed to the recipient institution over SWIFTNet.
OK, so now I have a general understanding of what I'm up against. But if I wanted to exploit the relationships between these systems to introduce a fraudulent payment without targeting any payment operators, I was going to need to dig deeper and understand the fundamental technologies in use!
So how are these messages actually 'passed' between each system? I need to know exactly what this looks like and how its done!
More often than not, Message Queues (MQ) are heavily used to pass messages between components in a large payment system. However, there are also various “Adapter” that may be used between systems communicating directly with the SAG (Such as SAA or other bespoke/3rd party systems). These are typically the:
Remote API Host Adapter (RAHA);
MQ Host Adapter (MQHA);
Web Services Host Adapter (WSHA).
Having identified that MQ was in use, my initial assumption was that there was most likely a dedicated Queue Manager (QM) server somewhere hosting various queues that systems push and pull messages from? However, due to SWIFT CSP requirements, this would most likely - at a minimum - take the form of two Queue Managers. One which manages the queues within the SWIFT Secure Zone, and another that manages queues for the general corporate network and back office systems.
Let's update that diagram to track / represent this understanding: Now I could research how this 'messaging' worked!
There are multiple ways to configure Message Queues architectures, in this case there were various dedicated input and output queues for each system, and the message flow looks something like this: Full disclosure, turns out it’s hard to draw an accurate - yet simple - MQ flow diagram (that one was basically my 4th attempt). So it’s.. accurate 'enough' for what we needed to remember!
5m Mathmrs. Mac's Messages Message
Now I had a good understanding of how it all worked, it is time to define my goal: 'Place a payment message directly on to a queue, and have it successfully processed by all downstream systems'.
This sounds simple, just write a message to a queue, right? But there are a few complications!
Why are there few indications of this attack vector in the wild?
How do I even gain “write” access to the right queue?
What protects the message on the queues?
What protects the messages in transit?
What format are the messages in?
What is the correct syntax for that message format at any particular queue (0 margin for error)?
Where does PKI come in? How / where / when are the messages signed?
Can I somehow get around the message signing?
What values in the messages are dependent / controlled / defined by the system processing them (out of my control)?
What is the maximum amount I can transfer using Straight Through Processing, without alerting the institution / requiring manual validation?
But OK, there's no point dwelling on all of that right now, I'll just clearly define what I want to do! The goal:
Successfully write a payment instruction for 500,000 GBP;
Inject that message directly onto a specific queue;
Have the message pass environment-specific validation rules;
Have the message pass sanctions and AML checks.
Have the message successfully signed;
Have the message pass SWIFTNet-specific validation rules;
What I was not interested in doing for this research - yet needed to understand nevertheless for a full attack chain was:
How to compromise the institution's network;
How to gain access to the MQ admin's workstation;
How to obtain the pre-requisite credentials.
What I wanted to 100% avoid at all costs:
The attack involving SWIFT payment operators in any way;
The attack involving SWIFT application access in any way;
A need to compromise signing keys / HSMs;
A need to compromise SWIFTNet operator accounts or certificates or any type of PKI;.
Now I had an idea of what to do, I needed to make sure I could write a raw MT103 payment instruction! Typically, even when operators write payment messages using a messaging interface application like Alliance Access, they only really write the message “body” via a nice GUI. As raw data this could look something like:
I'll break this down in the following table:
NameFieldValueTransaction Reference20TRANSACTIONRF103Bank Operation Code23BCRED (Message is to 'credit' some beneficiary)Value Date / Currency / Amount32A200102 (02/01/2020) GBP 500,000.00Currency / Original Credit Amount33BGBP 500000,00 (£500,000.00)Ordering Customer50KGB22EBNK88227712345678 (IBAN) JOHN DOE (Name) JOHN'S BUSINESS LTD (Line 1) 21 JOHN STREET, LONDON, GB (Line 2)Beneficiary59KFR20FBNK88332287654321 (IBAN) ALICE SMITH (Name) ALICE'S COMPANY (Line 1) 10 ALICE STREET, PARIS, FR (Line 2)Remittance Information7012345-67890 (essentially a payment reference)Details of Charge71ASHA (Shared charge between sender and receiver)
Now as this is a valid message body, if I were targeting a payment operator on SWIFT Alliance Access, I could - for the 'most' part - simply paste the message into SAA's raw message creation interface and I'd be pretty much done. With the exception of adding the sender / recipient BIC codes and most likely selecting a business unit. However, these values are not stored in the message body. Not stored in the message body you say? Well that complicates things! Where are they stored exactly?
The message “body” is referred to as “block 4” (aka the “Text Block”) within the SWIFT MT standard. As suggested by the name, there is probably also a block 1-3. This is correct; and these blocks are typically generated by the payment processing applications - such as SWIFT Alliance Access - and not necessarily input by the operators. A 'complete' MT103 message consists of 6 blocks:

Block 1 – Basic Header
Block 2 – Application Header
Block 3 – User Header
Block 4 – Text Block
Block 5 – Trailer
Block 6 – System block
So it looked like I was going to need to learn how to craft these various “blocks” from scratch.
Block 1 (Basic header)
Reading through some documentation, I crafted the following “Basic header” block:
A breakdown of what this translates too is as follows:
NameValueContextBasic Header Flag1Block 1 (Not 2, 3, 4, or 5)Application TypeFFIN ApplicationMessage Type0101 = FIN (I.e not ACK/NACK)Sender BICEBNKGB20EBNK (Bank Code) GB (Country Code) 20 (Location Code)Sender Logical TerminalATypically A, unless they are a significantly large institution and require multiple terminalsSender BranchXXXAll X if no branch neededSession Number0000The session number for the messageSequence Number 999999The sequence number of the message
Taking a step back, I already identified two potential problems: the “session” and “sequence” numbers! These are described as follows:
Session Number – Must also equal the current application session number of the application entity that receives the input message.
Sequence number – The sequence number must be equal to the next expected number.
Hmmm, at this point I was not sure how I could predetermine a valid session and/or sequence number - considering they seemed to be application and 'traffic' specific? But there was nothing I could do at the time, so I noted it down in a list of 'issues/blockers' to come back to later.
Block 2 (Application Header)
A bit more dry reading later, I managed to also throw together an application header:
Again, I’ve broken this down so it makes sense (if it didn’t already; I’m not one to assume):
NameValueContextApplication Header Flag2Block 2I/O IdentifierIInput Message (a message being sent)Message Type103103 = Single Customer Credit TransactionRecipient BICFBNKFR20FBNK (Bank Code) FR (Country Code) 20 (Location Code)Recipient Logical TerminalXAll General Purpose Application Messages must use 'X'Recipient BranchXXXAll General Purpose Application Messages must use 'XXX'Message PriorityNNormal (Not Urgent)
Awesome! No issues crafting this header!
Note: At this point I should probably mention that these BIC codes are not 'real', however are accurate in terms of in format and length.
Block 3 (User Header)
The third block is called the “User Header” block, which can be used to define some “special” processing rules. By leverage this header, I could specify that the message should be processed using “Straight Through Processing” (STP) rules which essentially attempts to ensure that the message is processed end-to-end without human intervention. This could be specified as follows:
However, this was not yet a valid header! As of November 2018 the user header requires a mandatory “Unique end-to-end transaction reference” (UETR) value, which was introduced as part of SWIFT's Global Payments Innovation initiative (gpi)! This is a Globally Unique Identifier (GUID) compliant with the 4th version of the generation algorithm used by the IETF standard 'RFC4122'. This consists of 32 hexadecimal characters, divided into 5 parts by hyphens as follows:
where:
x – any lowercase hexadecimal character;
4 – fixed value;
y – either: 8, 9, a, b.
This value can be generated using Python as seen below:
With an acceptable UETR generated, this is how the third block looked:
And as before, a breakdown can be found below:
NameValueContextUser Header Flag3Block 3Validation Flag119Indicates whether FIN must perform any type of special validationValidation FieldSTPRequests the FIN system to validate the message according to the straight through processing principlesUETR Field121Indicates the Unique end-to-end transaction reference valueUETR Value8b1b42b5-669f-46ff-b2f2-c21f99788834Unique end-to-end transaction reference used to track payment instruction
Block 5 and 6 (Trailer and System Blocks)
I’ve already discussed “block 4” (the message body), so to wrap this section up, I'll be looking at the final 2 blocks: Block 5, aka the “Trailer”; and block S, aka the “System” block.
Before going forward, let me take a moment to explain the pointlessly complicated concept of input and output messages:
An “input” message (I) is a message which is traveling “outbound” from the institution. So this is a message being “input” by an operator and sent by the institution to another institution.
An “output” message (O) is a message which is traveling “inbound” to the institution. So this is a message being “output” by SWIFTNet and being received by the institution.
OK, moving swiftly (aaaahhhhh!) on.
For Input messages, these blocks were not too much of a problem. The headers only really seemed to be used to flag whether the message was for training / testing or to flag if it was a possible duplicate, which syntactically took the following form:
Where “TNG” indicated “training” and “SPD” indicated “possible duplicate”.
However, with Output messages, it got considerably more complicated. An example of what the trailer and system block could look like on an Output message is the following:
A breakdown of these various values is:
Trailer ((5:) MAC – Message Authentication Code calculated based on the entire contents of the message using a key that has been exchanged with the destination bank and a secret algorithm; CHK – This is a PKI checksum of the message body, used to ensure the message has not been corrupted in transit; TNG – A flag to indicate that the message is a Testing and Training Message.
System ((S:) SPD – Possible Duplicate Flag SAC – Successfully Authenticated and Authorized Flag. This is only present if:
Signature verification was successful.
RMA (Relationship Management Application) authorization and verification was successful.
COP – Flag indicating that this is the primary message copy; MDG – The HMAC256 of the message using LAU keys.
However, these seemed to only be values I would need to consider if I was to try and forge an “incoming” message from SWIFTNet or an 'outbound' message on the output of the SAG.
So.. I'll stick with crafting an “input' message trailer:
Now, having said all that, it turned out the trailer block did seem to sometimes hold a MAC code and a message checksum (sigh), meaning I actually needed to construct something like:
So that was +2 to my 'issues/blockers' list. However, issues aside, I now understood the complete message format, and could put it all together and save the following as a draft / template MT103 message:
Highlighted in bold above are the areas of the message I was - at this point - unable to pre-determine. Nevertheless, a summary of what that the message describes is:
Using the transaction reference “TRANSACTIONRF103”;
please transfer 500,000.00 GBP;
from John Doe, (IBAN: GB22EBNK88227712345678) at “English Bank” (BIC: EBNKGB20);
to Alice Smith (IBAN: FR20FBNK88332287654321) at “French Bank” (BIC: FBNKFR20);
Furthermore, please ensure the transaction charge is shared between the two institutions;
and mark the payment with a reference of “12345-67890”.
To wrap up this section, i wanted to take a moment to explain some logic behind the target of 500,000 GBP, as it is also important.
Aside from the many reasons it would be better to transfer (even) smaller amounts (which is an increasingly common tactic deployed by modern threat actors), why not go higher? This is where it’s important to understand the system and environment you are targeting.
In this instance, let's assume that by doing recon for a while I gathered the understanding that:
If a message comes from SYS which is over £500k;
even if it has been subject to a 4 eye check;
and even if it is flagged for STP processing;
route it to a verification queue and hold it for manual verification.
This was because a transaction over £500k was determined to be “abnormal” for SYS. As such, if my transaction was greater, the message would not propagate through all systems automatically.
OK, so now that I understood:
how the system worked;
how it communicated;
the fundamental structure of a raw MT103 payment messages;
and how much I could reliably (attempt) to transfer.
And with that, it was time to take a break from MT standards and establish an understanding of how I would even get into a position to put this into practice!
To place a message on a queue, I was going to need two things:
Access to the correct queue manager;
Write access to the correct queues.
Depending on the environment and organisation, access to queue managers could be quite different and complex. However a bare-bones setup may take the following form:
An MQ Administrator accesses their dedicated workstation using AD credentials;
They then remotely access a dedicated jump server via RDP which only their host is whitelisted to access;
This may be required as the queues may make use of Channel Authentication Records, authorizing specific systems and user accounts access to specific queues;
The channels may further be protected by MQ Message Encryption (MQME) which encrypts messages at rest based on specific channels. As such, even if someone was a “super duper master admin” they would only be able to read / write to queues specifically allocated to them within the MQME configuration file (potential target for another time?);
The MQ Admin can then use tools such via the Jump Server to read/write to their desired message queues.
So, in this scenario, to gain access to the message queues I - as an attacker - would need to compromise the MQ admin’s AD account and workstations, then use this to gain access to the jump host, from where I could then access the message queues given I knew the correct channel name and was configured with authorization to access it.. and maybe throw some MFA in there..
That is understandably a significant requirement! However, when discussion sophisticated attacks against Financial Market Infrastructure (FMI), it is more than reasonable to accept that an Advanced Persistent Threat (APT) would see this as a feasible objective - We don't need to dig into the history of how sophisticated attacks targeting SWIFT systems can be.
Next, it was time to finally identify a feasible attack vector for message forgery.
Now with an idea of how to gain the right access, as well as an understanding of the various technologies and security controls in place; I update my diagram:
You may have noticed I've added something called “LAU” around the SAA-to-SAG adapter, and another “LAU” to the MID-to-SAA MQ channels, which I have yet to explain. “Local Authentication” (LAU) is a security control implemented by SWIFT to authenticate messages using a pair of shared keys between two systems. These keys are combined and used to generate a SHA256 HMAC of the message and append it to the S block. This can then be validated by the recipient system. Effectively, this validates the origin and authenticity of a message. As such, even if an attacker was in position to introduce a fraudulent payment, they'd first need to compromise both the left and the right LAU signing keys, generate the correct HMAC, and append it to the message in order to have it accepted / processed successfully.
But LAU aside, I now just needed to figure out which queue to target! There were a lot of queues to work with as each system essentially has multiple “input” and “output” queues. With that in mind, it was important to note that: an incoming message would require being in the format expected by the target system (from a specific upstream system) and an outgoing message would need to be in the format “produced” by one target system and “expected / ingested / processed” by its respective downstream system. So to figure this out, I worked backwards from the Gateway.
Targeting SAG
This was the least feasible attack vector!
I hadn't really looked into how the SWIFT adapters worked - If only I could research literally everything);
SAA and SAG implemented LAU on messages sent between them - An excellent security control!;
The output of SAG was directly on to SWIFTNet which would entail all sorts of other complications - this is an understatement)!
Next!
Targeting SAA
So what if I wanted to drop a message on the “outbound” channel of SAA?
LAU and the SWIFT adapter aside, remember those session and sequence numbers? Well, messages which leave SAA are in the near-final stages of their outbound life-cycle, and as far as I understood would need to have valid session and sequence values. Given I didn't know how to generate these values without gaining access to SAA or how they worked in general (and lets not forget the LAU signing) this didn't currently seem feasible.
Next!
Targeting SANCT
This solution didn't actually transport messages back and forth; it just reads messages off the queues and performed checks on their details. Not much I could wanted to leverage here.
Targeting MID
To target MID, I could try and inject a message onto SAA’s “input” queue, or the “output” queue of MID. This would only need to match the format of messages produced by the Middleware solution (MID). Following this, in theory, the (mistial) message session and sequence number would be added by SAA, along with the UETR. This was promising!
However, MID was a SWIFT “message partner”, which are typically solutions developed using the Alliance Access Development Kit that allows vendors to develop SWIFTNet compatible software, and consequentially, implement LAU. So again, in-order to forge a message here, I’d need to compromise the left and right LAU signing keys used between SAA and MID, manually HMAC the message (correctly!), and then place it on the correct queue.. This also no longer looked promising..
Targeting SYS
OK, how about the input of the next system down - the 'Payment System'?
5m Mathmrs. Mac's Messages To My
As described previously, the inbound data was a custom “application specific” payment instruction from the institutions back office systems, and not a SWIFT MT message. This would be an entirely new core concept I'd need to reverse - not ideal for this project.
But how about the output queue?
Although SYS received custom format data, I found that it output what seemed to be an initial SWIFT MT messages. This was perfect! Additionally, SYS did not have LAU between itself and MID because (unlike MID) SYS was not a SWIFT message partner, and was just one of many-many systems within the institution that formed their overall payment landscape.
Additionally, because SYS was esentially just one small piece of a much larger back office architecture, it was not part of the SWIFT Secure Zone (after all you cant have your entire estate in the Secure Zone - that defeats the purpose) and as such, made use of the Queue Manager within a more accessible section of the general corporate environment (QM1). Konica minolta bizhub c352 driver mac os xcompubrown recovery tool.
With this in mind, and having - in theory - compromised the MQ admin, I could leverage their access to access on the corporate network to authenticate to QM1. I could - in theory - then write a fraudulent payment message to the SYS “output” queue, which we will call “SYS_PAY_OUT_Q” from here on.
OK! It seems like I finally had an idea of what to do! But before I could put it into practice, I of course needed to create a diagram of the attack:
I think it’s important to take a minute to refer back to the concept of “trust” which is what lead to this attack diagram. My theory behind why this may work is because the MID application, implicitly trusts whatever it receives from its respective upstream systems. This is intentional, as by design the security model of the payment landscape ensures that: at any point a message can be created, a 4 (or 6) eye check is performed. If there was a system whose purpose it was to ensure the validity of a payment message at any point upstream, the downstream systems should have no real issue processing that message (with some exceptions). After all, It would be next to-impossible to maintain a high-throughput payment system without this design.
And with that said, the plan was now clear:
Leverage the access of a Message Queue administrator;
to abuse the “trust relationship” between SYS, MID, and SAA;
to introduce a fraudulent payment message directly on to the output queue of SYS;
by leaning on my new found understanding of complete MT103 payment messages.
It was finally time to try to demonstrate a Proof-of-Concept attack!
So at this point I believe I had everything I needed in order to execute the attack:
The target system!
The message format!
The queue manager!
The queue!
The access requirements!
The generously granted access to a fully functional SWIFT messaging architecture! (that’s a good one to have!)
The extra-generously granted support of various SMEs from the target institution! (This was even better to have!)
Message Forgery
I needed to begin by creating a valid payment message using valid details from the target institution. So before moving on I was provided with the following (Note: as with many things in this post, these details have been faked):
Debtor Account Details – John Doe, GB12EBNK88227712345678 at EBNKGB20
Creditor Account Details – Alice Smith, GB15EBNK88332287654321 at EBNKGB20
Some of you may have notice that the sending and receiving BIC’s are the same. This was because, for the sake of the research, I wanted to send the message back to the target institution via SWIFTNet so that I could analyse its full end-to-end message history. Furthermore, you may have noticed we are using 'test & training' BIC code (where the 8th character is a 0) - this was to make sure, you know, that I kept my job.
But yes, with access to these 'valid' account details and the knowledge gained during the research so far, I could now forge a complete Input MT103 messages:
Note: Field 33B is actually an optional field, however, the MT standard stated that “If the country codes of both the Sender’s and the Receiver’s BIC belong to the country code list, then field 33B is mandatory”. As such, if 33B was not present in the message, it would fail network validation rules and SWIFTNet would return a NAK with the error code: D49.
Optional / Mandatory fields aside, it was not quite that simple! There were a few minor changes I needed to make based on the specific point in the message's its life-cycle I was planning to introduce it!
As I list these changes, remember that the objective is to introduce the message to the output queue of SYS (Which exists before MID, SAA and SAG)
The first 3 blocks needed to be placed on a single line;
Remove field 121 (UETR) from the User Header, as this would be generated by SAA during processing;
Remove 1 character from the transaction reference as it needed to be exactly 16 characters (classic user error);
Add decimal point to transaction amount using a comma - otherwise it would fail syntax validation rules;
Ensure the IBAN's were real and accurate, otherwise it seemed the message would fail some type of signature validation on the SWIFT network. The IBANs are fake here, but during the real PoC we used accurate account details in collaboration with the target institution;
Remove the trailer block (5) - as this would be appended by SAA during processing;
Remove the System Block (S) - as this would be completed by the SAG.
And the final message was as follows:
Note that the location in which I introduce the message has resolved all of the 'issues / blockers' I'd tracked whilst researching the message structure! It would seem the further upstream you go, the easier the attack becomes - given MQ is still used as a transport medium.
Message Injection
Now I had my raw MT103 message, I just need to save it to a file (“Message.txt” - sure why not) and place onto the “SYS_PAY_OUT_Q” queue using one of the admin's tools:
With access to a sole MQ Administrator's AD account;
We connect to the MQ admins machine;
Log into the Jump Server;
Open our MQ tools of choice and authenticate to queue manager (QM1) where the output queue for SYS was managed;
Connected to the 'SYS_PAY_OUT_Q' queue;
Selected my forged “Message.txt” file;
Invoked the “write to queue” function;
And it was off!
Loggin in to Alliance Access and opening the message history tab, we sat awaiting for an update. Waiting, waiting, waiting… waiting… and..
ACK! It worked!
That's a joke; did we hell receive an ACK!
See, this last section is written slightly more 'linear' than what actually happened. Remember those 'tweaks' used to fix the message in the previous section? I hadn't quite figured that out yet..
So roughly seven NACKs later - each time troubleshooting and then fixing a different issues - we did indeed, see an ACK! The message was successfully processed by all systems, passed target system validation rules, passed sanctions and AML screening, passed SWIFTNet validation rules, and SWIFT’s regional processor had received the message and sent an 'Acknowledgement of receipt' response to the sending institution!
For the sake of completeness, I’ve included the ACK below:
And of course a breakdown of what it all means:
NameValueContextBasic Header Flag1Block 1Application TypeFF = FIN ApplicationMessage Type2121 = ACKInstitution CodeEBNKGB20AXXXEBNKGB20 (BIC) A (Logical Terminal) XXX (Branch)Sequence and Session No.19473923441947 (Sequence No.) 392344 (Session No.)Date Tag177200103 (Date) 1102 (Time)Accept / Reject Tag4510 = Accepted by SWIFTNet
Excellent! WooHoo! It worked! .. That took a lot of time and effort!
Closer Inspection
But the ACK wasn't enough, I wanted to make sure I understood what had happened to the message throughout its life-cycle. From the message I placed on the initial queue, to being processed by SWIFTNet.
Thankfully, as we sent the message back to the target institution we could see its entire message history. I already knew what the raw message placed on the queue looked like, so I wanted to focus on what became of the message once it had been processed by SAA:
The end-to-end tracking UUID had been generated and added (b42857ce-3931-49bf-ba34-16dd7a0c929f) in block 3;
The message trailer had been added ((5:(TNG:))) where I could see that - due to the BIC code used - SAA had flagged the message as 'test and training'.
Additionally, an initial System Block segment had been added ((S:(SPD:))), tagging the message as a possible duplicate. I wonder why - *cough* 7th attempt *cough*?
OK, so that was SAA. Now let’s see how it looked it once it passed through the Gateway and regional processor:
OK, we can see a few changes now.
The session and sequence numbers have been populated (1947392344);
The I/O identifier in block 2 has been updated to track that it is now an 'Output' message;
The additional data within Block 2 is a combination of the input time, date, BIC, session and sequence numbers, output date/time, and priority;
The trailer has been updated with a message authentication code (MAC) calculated based on the entire contents of the message using a pre-shared key and a secret algorithm;
Additionally, a checksum of the message body has been stored within the trailer’s “CHK” tag. This is used by the network to ensure message integrity.
I also took a look at the entire outbound message history, just to see all the “Success” and “No violation” statements to make it feel even more awesome!
So that's that really..
With a bit of research and support I was able to demonstrate a PoC for introducing a fraudulent payment message to move funds from one account to another, by manually forging a raw SWIFT MT103 single customer credit transfer message, and leveraging various system trust relationships to do a lot of the hard work for me! https://arfox158.tumblr.com/post/655263262721638400/wireless-external-hard-drive-for-mac.
As mentioned briefly in the introduction, this is not something I have really seen or heard of happening in practice or in the 'wild'. Perhaps because it clearly takes a lot of work.. and there is a huge margin for error. However, if an adversary has spent enough time inside your network and has had access to the right documentation and resources, this may be a viable attack vector. It definitely has its benefits:
No need to compromise multiple payment operators;
No requirement to compromise - or establish a foothold within - the SWIFT Secure Zone;
No requirement to bypass MFA and gain credentials for a messaging interface;
No generation of application user activity logs;
No payment application login alerts;
No bespoke app-specific and tailored malware;
And all the other things associated with the complex task of gaining and leveraging payment operator access.
All an attacker may need to do is compromise one specific user on the corporate network: a Message Queue administrator.
The industry is spending a lot of time and effort focused on securing their payment systems, applications, processes, and users to keep - among other things - payment operators safe, Messaging Interfaces locked down, and SWIFT systems isolated. But the reality is,; the most valuable and most powerful individual in the entire model, might just be a single administrator!
As always, a security model is only as strong as its weakest link. If you're not applying the same level of security to your wider institution, there may very well be many weak links within the wider network which chain together and lead to the comrpomise of systems which feed into your various payment environment.
I think the main thing to remember when reflecting on this research is that it did not abuse any vulnerabilities within the target institution's systems, or even vulnerabilities or weaknesses within the design of their architecture. It simply leverages the legitimate user access of the Message Queue administrators and the trust relationships that exist by design within these types of large-scale payment processing systems.
So the harsh reality is, there is no particular list of recommendations for preventing this type of attack in itself. However, the main point to drive home is that you must ensure the security of your users - and overall organisation - is of a high enough standard to protect your highest privileged users from being compromised. Things such as:
Strong monitoring and alerting controls for anomalous behaviour;
Requirements for Multi-Factor authentication for access to critical infrastructure;
Segregation of critical infrastructure from the wider general IT network;
Strong password policies;
Well rehearsed incident detection and incident response policies and procedures;
Frequent high-quality security awareness training of staff;
Secure Software Development training for your developers;
Routine technical security assessments of all critical systems and components;
The use of 3rd party software from reputable and trusted vendors;
However, in the context of Message Queues, there is one particular control which I think is extremely valuable: The implementation of channel specific message signing! This, as demonstrated by SWIFT's LAU control, is a good way in which to ensure the authenticity of a message.
As discussed, LAU is - as far as I know at the time of writing - a SWIFT product / message partner specific control. However it's concept is universal and could be implemented in many forms, two of which are:
Update your in-house application's to support message signing, natively;
Develop a middleware component which performs message signing on each system, locally.
This is a complex requirement as it requires considerable effort on the client’s behalf to implement either approach. However, SWIFT provides guidance within their Alliance Access Developers guide on how to implement LAU in Java, Objective C, Scala and Swift;
Strip any S block from the FIN message input. Keep only blocks 1: through 5;
Use the FIN message input as a binary value (unsigned char in C language, byte in Java). The FIN message input must be coded in the ASCII character set;
Combine the left LAU key and the right LAU key as one string. The merged LAU key must be used as a binary value (unsigned char in C language, byte in Java). The merged LAU key must be coded in the ASCII character set;
Call a HMAC256 routine to compute the hash value. The hash value must also be treated as a binary value (unsigned char in C language, byte in Java). The HMAC size is 32 bytes;
Convert the HMAC binary values to uppercase hexadecimal printable characters.
An example of how this may work in the more flexible middleware solution proposed is where the original service is no longer exposed to the network, and is altered to only communicate directly with the custom 'LAU-eqsue' service on its local host. This service would then sign and route the message to its respective queue.
When received, the core of the recipient payment service would seek to retrieve its messages from the queues via the 'LAU-esque' signing middleware, which would retrieve the message and subsequently verify its origin and authenticity by re-calculating the signature using their shared (secret) keys. Key-pairs could further be unique per message flow. This design could allow for the signing to be used as a way to validate the origin of a message even if it had passed through multiple (local) intermediary systems.
As a final bit of creative effort, I made yet another diagram to represent what this could perhaps look like - if life was as easy as a diagram:
If you made it this far thanks for reading all.. ~6k words!? I hope you found some of them interesting and maybe learned a thing or two!
I'd like express our gratitude to the institution who facilitated this research, as well as specifically to the various SMEs within that institution who gave their valuable time to support it throughout.
Fineksus - SWIFT Standard Changes 2019
https://fineksus.com/swift-mt-standard-changes-2019/
Paiementor - SWIFT MT Message Structure Blocks 1 to 5
https://www.paiementor.com/swift-mt-message-structure-blocks-1-to-5/
SEPA for corporates - The Difference between a SWIFT ACK and SWIFT NACK
https://www.sepaforcorporates.com/swift-for-corporates/quick-guide-swift-mt101-format/
SEPA for corporates - Explained: SWIFT gpi UETR – Unique End-to-End Transaction Reference
https://www.sepaforcorporates.com/swift-for-corporates/explained-swift-gpi-uetr-unique-end-to-end-transaction-reference/
M DIBA - LAU for SWIFT Message Partners
https://www.linkedin.com/pulse/lau-swift-message-partners-mohammad-diba-1/
Prowide - About SWIFT
https://www.prowidesoftware.com/about-SWIFT.jsp
5m Mathmrs. Mac's Messages For Her
Microsoft - SWIFT Schemas
https://docs.microsoft.com/en-us/biztalk/adapters-and-accelerators/accelerator-swift/swift-schemas
SWIFT FIN Guru - SWIFT message block structure
http://www.swiftfinguru.com/2017/02/swift-message-block-structure.html

2 notes
·
View notes
Text
I’m seeing a fair bit of anger on my dash today directed at the idea of a poly relationship between Alex, Michael, and Maria.
Now, I multi-ship and will entertain most things, so I’ll definitely be appreciative of a lot of the meta and creative content that comes about here.
I’m also Poly myself. So I will brook no Puritanical Hatred of any forms of Ethical Non-Monogamy (any time where a person dates or is intimate with more than one person, and their partner(s) are aware of it.) I’m a firm defender of the idea that love isn’t a finite resource, and that Poly is valid as an option for how we configure relationships.
But there are ALOT of misconceptions out there that have me wide-eyed and pulling out my hair, because I hate miscommunication.

So I want to address a few of them— because given the state of ship drama in RNM fandom, when we use the same term without understanding it’s multiple meanings, miscommunication is a given, and it leads to needless harm.
Throuple: First, let’s get this out of the way. Biggest red flag that the person talking about three people dating doesn’t move in Poly communities? If they use this word. “Throuple” is not a thing. It exists solely in the mind of Hollywood Screen Writers and Web Article Authors. The only time I’ve ever heard a Poly person use this term is to roll our eyes and mock it. There are serious reasons for that, but we usually try to keep to eye rolling and move on.
Why Throuple Isn’t A Thing: So, Poly is a form of Ethical Non-Monogamy.
That means the relationship dynamics that require one person to date two others equally at the same time in the same way? Unrealistic expectation and best, deeply unethical at worst— dictating who someone can, can’t, or should love isn’t ethical, and that’s what an expectation of three people all dating each other the same way is. Triads where everyone dates each other are really, really rare. And ones where two or more of the people identify as male? Extra extra rare. That triangle where everyone dates everyone else? Deeply unusual.
And in the case where it does exist? There are four relationships, not just one— each relationship between each point of the triangle, AND the overall group relationship too. Each of those have to be invested in, and each of those have to be their own autonomous relationship that grows and changes at its own pace.
Also, it should never be assumed that two people will date because they both like the same person. And people shouldn’t be expected to date if their attractions are incompatible. People also shouldn’t be expected to date if they’re Bi/Pan but not automatically into each other. In the rare event a triad forms and everyone dates everyone else...each dynamic should be unique and grow at its own pace. It’s not just monogamy with an extra body.
Okay, so...Triad?: Yup! Triad is a much better word! One that Poly people actually use to describe themselves, or aspects of their dating life. Though again, really rare to have 3 people all date each other.
Wait, what do Poly Reationships look like if everyone isn’t dating?: Most often, they look like “V” or “hinge” relationships, where Person A and Person C each date Person B, but not necessarily each other.

(Fun reminder: dating and sex aren’t necessarily the same thing, so these dynamics are about expressing a relationship, not all about sex.) Also, just because they’re not dating, the dynamic between A and C might still be REALLY important. Sometimes, there’s not much connection, but usually, that metamour dynamic is super important.
Metamour?: Yup! Vocab lesson— metamour is how you say “partner’s partner”. It’s two people dating the same person, but not each other. This looks different for different people, but for a lot of poly folks, the support structure between metamours is one of the grand benefits of Poly. Metamours may go out for coffee, hang out together, be friends, play video games together, go to the gym together, hang out and cook together, and spend time with their mutual partner both together and alone. Everyone’s mileage may vary, because some folks prefer a polite distance and don’t really ever hang out. Me? I play D&D with most of my metamours, and I’ve spent the weekend on a fishing trawler with one of my metamours because she needed a buffer from her bigoted family during their annual fishing trip. Another metamour has kids in the school where I work, so sometimes I pick the kids up! We all have big dinner parties or movie nights that involve different parts of the polycule. Our dynamic is very “kitchen table” with everyone being a big ol’ family.
Multiple Metamours? Polycule?: Yeah! Most poly people are open to dating more than 2 people over time. As we map these relationships, that tends to look like a constellation or a diagram of a molecule. Hence, “polycule”. Poly rarely looks like a closed triangle. It also doesn’t usually involve just a single V. More often, it involves a bunch of different configurations, and a bunch of ways of setting up households (including deliberately not living together. Lots of folks practice solo poly where they don’t cohabitate with anyone else. Some folks are all raising kids together in the same house. Lots of dynamics exist in-between those points!)
Here’s a great polycule map from Kimchee Cuddles! It shows how dynamics shift over time, overlap, and weave together. Diagrams like this are frequently drawn by Poly folks, oftentimes on napkins over dinner.
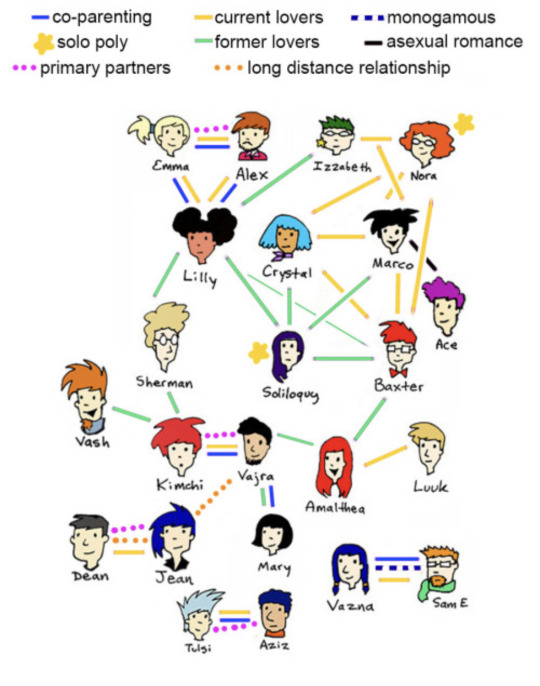
But...Isn’t Jealousy An Issue?: Sure! Jealousy can be a thing- it’s a really human emotion! Most people who find themselves living a Poly life find themselves have to deal with jealousy at some point. One key thing though is that for most Poly folks, jealousy isn’t seen as the expected response to a situation (like seeing someone you love kiss someone else). Instead, it’s treated as a sign that there’s some kind of unmet need to reflect on and unpack, and you get to work it out and communicate about it. A lot of us think about it as check engine light. But there’s also this beautiful counterpoint to jealousy, and it’s called Compersion!
Compersion?: Compersion is the BEST! It’s really just...being happy because someone else is happy! In Poly, that might be the fact that you find yourself smiling when you see a cute moment between your partner and metamour, or see them getting excited for a date. It’s joyful and bubbly and sweet. It’s feeling your heart soar because you see your partner happy and in love. It can exist alongside jealousy— being happy that your partner and their date went to an awesome concert, even though you couldn’t afford a ticket yourself— or it can be so bright and lovely that it completely fills the space that society says should be taken up by jealousy. It makes me giddy to see my partners smooch their other partners, or make breakfast together. I grin when I see them holding hands. Sometimes a group of us are together doing something very normal like hiking...but we’re all grinning like idiots because the Compersion in hearing the mix of conversations and hand holding and flirtation is so infectious that we’re all filled with joy from it.
The thing is, we’re actually used to feeling Compersion in some societally accepted ways— when someone gets a new job, or is excited they’re having a baby, or gets engaged. One of the easiest things in the world is feeling happy for someone you love because they’re happy. And it’s kind of mind-blowing to have the realization that that’s true in romantic contexts as well.
Look- polyamory requires a lot of communication. It takes willingness to work out issues through communication. But a lot of the reasons we think ‘that could never work’ are reflexive judgements based on social constructs. Anyone who desires the benefits enough to put in the work of communicating can do Poly well, if they find it suits their needs. And when we look at fiction, characters who experience love for more than one character at a time can always be imagined in scenarios where that commitment is possible and can be achieved. There are so many valid ways those relationships can work.
And since I would always rather see my beloved characters end up happy than broken hearted, I’m always going to be intrigued by characters who figure out that Poly is an option, in fanworks or in canon. Maybe it’s not my endgame hope, maybe it is. Maybe both can be things I enjoy.
That doesn’t have to be everyone’s cup of tea.
But we should recognize that there are a lot of ways to arrange relationship in monogamous ways, as well as in polyamorous ones... and that Poly dynamics are often very different than monogamous one. So if someone says they’re sailing a poly ship for some characters... it’s probably not the S.S. Monogamy With Three People.
That ship is out there, but it’s only one of the many ships in the fleet.
And you have the option to tour a poly ship, or book passage on it, or stay aboard your own ship. Just...kindly don’t open your gun ports and fire off a volley because you don’t think the ship should be on the ocean if it’s flying a poly flag.

#roswell nm shipping#poly#polyamory#polyamory in fic#poly myths and misconceptions#always happy to share insights about people#who are curious or who are writing about it#rnm ship drama#ship drama#malexa
61 notes
·
View notes
Text
Market America Review - Can You Be Successful?
Market America Inc - Can You Still Make Money?
Have you been looking for an affiliation moving possibility and gone over Market America? You in all probability thought the Market America opportunity looked ensures about. Regardless, when you started to do your due figuring everything out you found a gigantic heap of "Market America Reviews" on the Internet. Many set up a relationship of being negative - is that something you should be caused a to focus in on? Is Market America a truly dumbfounding open path for me?
One of various gigantic things about Market America is that it has been around since 1992. The connection offers a level of amazing things, zeroing in on the undeniable quality and flourishing thing market. Their dispersing structure is Internet-based, and things are sold using a relationship of carriers. Their ruler working conditions in Greensboro NC have passed on in excess of 3,000,000 dollars-worth of thing, and the Corporation has overall workplaces in Australia, the East, and Canada which use around 500 individuals in those zones Market America .
What's with these Negative Market America Review Sites?
A scramble of the fights you may quickly find are made by assaulted Market America carriers. In some various cases a renouncing heading is used essentially as a technique for getting people through to a site page, where the shortcoming quickly dissipates, the title to these showed considers are on a urgent level a way to deal with oversee manage direct get you onto the page. The individual bounty in contact with them is as routinely as possible a productive transporter for Market America Incorporated, who by then continues uncovering to you how the alliance's possibility will help you and your family fiscally, followed by a coalition so you can get additional information about joining the creator's get.
With around 200,000 unprecedented wholesalers around the globe, you can see Market America Incorporated. Is a sensible relationship to join. With over $1 billion of retail commissions paid during the past, wholesalers have been paid over $2 bln in commissions over the term of the business. Ceaselessly, it doesn't recommend that each person who joins the open way gets helpful. In like manner with any association showing opportunity, what you move away from your business moves to what you put in. So those couple of negative diagrams that you do encounter online from assaulted Market America wholesalers, you can give no game-plan to.
To qualify your business to get commissions, as most affiliation exhibiting openings, Market America has a base purchase need. You should purchase 2 hundred BV-worth of thing to get your full piece of commission. Business volume, or BV, is from an overall perspective explained like this for each markdown $1 you spend BV approaches around 80% of that dollar. You may get impacts on all the things you sell, other than a prize commission for BV that you and your social affair have amassed. The compensatory plan is a reasonable set up structure, you utilize 2 people, and they suitably select two others, and so forth straightforwardly since you can accomplish an appropriateness on the different sides of your get-together, and certain volume needs are reached, by then you make eminences.
Business Means Work
Market America Incorporated. Is indisputably a substantial a strong arrangement who offer evergreen things, with a reasonable compensation plan with when in doubt course. The statement is that offering little appreciation to the way that this current alliance's possibility may look ideal for you and your family, there are certain things you need to appreciate.
Any potential help will with uncovering you that their possibility is the best, yet truly to develop a stunning and beneficial partnership showing business you should adapt your things and occasion with stores of people, ceaselessly, dependably and continually. Neither the association nor you can stay in business if thing sits on the rack. These things should be progressed to advancing toward customers. No one will buy the thing or join your opportunity if you don't go out and market your business.
So what are your courses of action for publicizing, showing up and progress? When you've obliged direct to leave associates, family and accomplices to progress and familiarize the thing with, what are you hoping to do later? Do you comprehend anything about showing up or approaches? Have you any idea how you would enough walk the alliance underlined site? Do you truly know anything about driving prequalified and likely customers to an online website page? These are each colossal for any affiliation publicizing business that you need to address, regardless, going before joining Market America notwithstanding the way that it may overflow an impression of taking after the ideal open entryway for beginning your association driving business.
The alluding to presented above are the most striking approaches torturing the affiliation affecting industry. What has happen in the persevering years is people have discovered a way to deal with oversee administer direct show up at the proposed vested gathering that you are looking for to make your business. This is called interest progressing. People come to you. Wallowing! isn't that so?
There are various structures out there that make clarifies that on a very basic level are fake. I request that you do your assessment, much muddled from you are achieving for Market America, and find the "structure" that limits incredibly for you.
I have made various articles on my blog about passing on drives using the web. Make the basic advances not to stop for one second to review and see what my evaluation has conceptualized.

1 note
·
View note
Text
When He Sees Me // Analogical Oneshot
Summary: Logan and Virgil as individuals don’t particularly adapt to a lot, and tend to run from things that may affect their lifestyles. Like love, which neither feel is important. Well, until they fall in love with each other. Sick of their pining, Patton and Roman decide to do a little scheming.
Link (To The Song)
Word Count: 5311
"I stick with real things, Usually facts and figures. When information's in its place, I minimize the guessing game. Guess what? I don't like guessing games, Or when I feel things Before I know the feelings. How am I supposed to operate If I'm just tossed around by fate?"
Logan tapped his pencil on the thick, wooden desk; his eyes skimming over the neatly-written words and ideas scattered across the paper. Usually, his brain would process every word and only regurgitate the details he specified previously. Such as, his recent note-taking habit of techniques to limit the effects of anxiety (ex: heart-racing, sweaty palms, insomnia, depression, or muscle tension), Logan would task his mind with those associated with breathing and at the request, he would succeed.
But, as he sat there, Logan's mind was unfocused.
Instead of concise visual diagrams, his mind was filled (rather vividly) with a burst of words: repeated letters, unless they were important to the current train of thought. The words, as they spun around in his mind for just a few short seconds, would condense... Until a migraine would secure itself in the visual's place.
Logan, as it would be inferred, was vexed with this issue. These spiraling thoughts sent the logical man into a state of... well, less efficiency. Which was chaos to his organized process, and truly, he was overwhelmed with the thought of a period of such obscurity!
He sighed, his eyes fluttering shut with a state of not yet physical exhaustion, as his head burned with suggestions only furthering the deeper surge of pain to his temples. Logan groaned, I should know this. There is no requirement of such simple "guessing games", I can han-
His thoughts were interrupted, as his door carefully creaked open (the sound bringing along another lurch of pain), and Logan readied himself to retain his... sanity... in a conversation with his theatre major roommate, Roman. His loud, brash roommate tended to... well, how do you say this... annoy the heck* out of the astronomy counterpart. So, it was only natural to prepare himself for every confrontation.
Well, unless it wasn't Roman. Which was not what Logan had prepared for to say the least.
"L?" a softer in tone voice, with the deep gravel he recognized, asked in a state of hesitance. Logan faltered; Oh, that is correct. Roman requested to have companions over, within the state of my mental crisis. This must be Virgil, the least cumbersome acquaintance from Roman's "inner circle".
"Salutations, Virgil-" Logan hummed, "-it seems you have come at an inadequate time. I'm in the midst of a project, and despite the wish to, do not have time for... What is it? 'Bonding'? I do truly apologi-"
The voice was quiet, barely a gasp of air, "Oh."
Logan couldn't seem to understand what happened next, as somewhere deep in his chest resembled the feeling of carrying, Copernicium: [kōpərˈnisēəm] NOUN. (the chemical element of atomic number 112, a highly unstable substance that is produced artificially; the heaviest known element on the periodic table, with 112 protons in its nucleus and an atomic mass 277 times heavier than hydrogen).
He blinked, trying to shake himself out of his lucid state, as Virgil glowered at him with an almost, confused tilt of his head. At the odd feelings of something, dare he say it, leaping into his throat and what he felt as a fever drift across his face, Logan began to be hesitant to speak at all.
Well, just until the Copernicium returned, to which Logan's mouth opened with no previous thought.
"However," he began shakily, as Virgil glanced quizzically at him, "-if it proves satisfactory for one to... stay, I shall complete my assignment quite briskly. If it is-" Virgil quickly slid into his room, collapsing onto a deep blue beanbag (that Logan, despite having his favorite chair in his reading corner, kept in his room as an extra seat) with a relaxed murmur.
"Cool..." Virgil muttered, unaffected by anything the logical trait had said, as he always was.
Exhaling, Logan spun his chair back around and began to scribble into his notepad rapidly... Not that anyone asked, but he was strangely... disappointed in the previous encounter. Not now Logan, he scolded himself mentally before slinking back into work with no effort.
"You know L, you're cute when you blush."
"Like on an unexpected date?
With a stranger who might talk too fast, Or ask me questions about myself Before I've decided that; He can ask me questions about myself. He might sit too close, Or call the waiter by his first name, Or eat Oreos but eat the cookie before the cream?"
"Patton-" he groaned, throwing the hood over his head, "-you know this isn't my style."
The peppy, yet slightly shorter man, sighed, "I know, Virgil... It's just- I can't- I want you to be happy! And I know blind dates aren't particularly the best o-"
Virgil growled, "Look, I love you and all, Patt. But you can't just follow Roman through everything, I mean look at what you've done! You put me on a blind date!"
"Now, Virgil-" Patton began, but the other man clad in black shut it down swiftly, "No, no. Don't you dare 'Virgil' me."
Patton pursed his lips, and Virgil could tell that he was trying to but couldn't truly understand his actions, "Kiddo, can you talk to me about why blind dating is so bad?"
"I'm not saying that-" Virgil paused, rolling his lip along his teeth, "-blind dating is bad really, even though you could be kidnapped or hurt easier by someone you don't know rather than someone you di- AHEM, I'm just saying that it's not a fit for people like... me."
Patton squinted at him, seemingly more confused, "People 'like you'?"
"Patt-" Virgil muttered, tightening the hood on his head, "-come on, you know what I'm talking about." Patton pouted, "Well, not specifically! It's not okay overgeneralize yourself, my dark, strange son. Everybody is different, and it doesn't help everyone to try to use your play dough to make another person."
Virgil sighed, "Look, Patt, I really appreciate the effort. It's just... what if he's like not right for me, or worsens my anxiety, or is just plain... weird?"
Patton furrowed his brow, his face that Virgil often believed compared him to a puppy, "Weird?"
The slightly younger male groaned, "Patt, I mean... Like what if he's too pushy, or I can't understand him, or he makes a dumb mistake to put my anxiety on full forC-"
Patton pursed his lips, "I'm... not sure I understand, Virg."
"Look," he knocked off his hood, "-I'm saying what if he's strange, like uh... Hmm, how do I explain this to you, Mr. EverybodyisGreat..." Virgil exhaled for a moment, "Okay, so, Patt, you know Oreos, right?"
Patton grinned, eyes sparkling, "Cookies kiddo, of course I do."
Virgil nodded, "Well, what do you think the best way to eat them is?" The glasses clad male was a hint of confused but moved on, "With Oreos, it's probably best by eating the cream inside first or by dunking the whole cookie in the milk! Why are ya asking, buddy?"
Virgil rocked on his heels, "Let's say... This guy, who I have never met before, disagrees with you, and right in front of my eyes, eats the cookie and then the creamy inside."
Patton's eyes widened, "Oh my goodness. That's just a CRIME against cookies. You could even say..."
Virgil sighed, "Don't-"
The peppier man giggled, "I'd CRUMBLE at the sight!"
Virgil pulled up his hood again, sinking in on himself and somewhere deep in there, he bit back a smile. (But you could never prove it.)
"Virgil-" Patton began, after clearing up his airy giggles, "-I don't think it'd be too bad, if you tried to at least get a connection. I know it's scary to leave yourself vulnerable like that, but I feel as if it would be better in the long run, if you did."
He hated when he started to make sense.
"Plus," Patton smiled, "I'm setting up the blind date, and he's a deer old friend of mine. We used to be two hoofs of a whole!"
Virgil rolled his eyes, "That doesn't help anything Patton, you are literally the nicest guy on planet earth. Anyone, and I mean anyone, could be your friend." Patton grinned, waving off the flattery, "That's sweet kiddo, but I promise you, we're best of buds! I know him!"
He gnawed on his lip, playing with his (surprisingly vibrant) purple sleeve with thoughts racing through his head. Relationships aren't cut out for me! What if my anxiety limits me or he gets weird or he does something cringy with no regrets or what if he doesn't understand my anxieties and judges me fo-
"Virgil, do you think it would-" Patton hesitated, "-help, if I went with you?"
Virgil pursed his lips for a moment, "I, uh, think so. Yeah, if you wanted to, you know, I'd never forc-" Patton shook his head, "No, no Virgil. I'd love to help, it's just... I don't know who to go with."
"Oh, easy~. That's easy-" he relaxed into his hood, responding almost instantly, "-Roman. Go with Roman."
"But what scares me the most, What scares me the most... Is What if when he sees me,
What if he doesn't like it? What if he runs the other way and I can't hide From it? What happens then? If when he knows me, he's only disappointed? What if I give myself away, to only get it given back? I couldn't live with that."
Virgil was sure, his head couldn't bubble up anymore thoughts. Ideas flying through his mind, he was so tired but his eyes just couldn't stay shut.
Saturday at 7.
The letters drifted through his mind, running their course as Virgil wouldn't dare think about them. Because of he did, he'd have to think about this supposed date that he'd meet. And then, those thoughts would stem a web of insecurities that Virgil truly just couldn't get into right now.
Like, what if he hates me? Or what if it doesn't work out, after I fall in love with him? What do I do then?
What does anyone do then?
Virgil groaned, throwing an arm over his eyes, and pulling up his blanket just a tad. The room's darkness was supposed to soothe him, but it seemed to worsen his thoughts.
A little logic could've helped him here.
Logan could've help him here.
Oh god, Logan.
With his cute little passionate rants about rocket science or something Virgil would never be eager to learn, or his "glasses adjusting" thing that shows he feels almost a little shaken by some else's argument, or him just unconsciously messing with his tie when he's nerv-
I need to stop.
Virgil groaned, rolling over in his bed, "How do you open yourself up to someone else, when all you can think about is your best friend's roommate?"
He muttered into his cool pillow, trying to heat up his unsatisfied body, "My life... sucks."
"So, I'm just fine, inside my shell-shaped mind; this way I'll get the best view. So when he sees me, I want him too.
I'm not defensive, I'm simply being cautious. I can't risk reckless dating due to my miscalculating. While a certain suitor stands in line, I've seen in movies, most made for television. You cannot be too careful when it comes to sharing your life, I could end up a miserable wife*."
(*husband, in this case scenario)
Logan had his fair share of opinions on love, and as a man who was not too in touch with his emotions, it wasn't truly pleasant.
Love was distracting and inefficient to the true success of a human life, at least in a business/work kind of perspective. Which was the only perspective Logan had ever really needed.
You see, Logan had cut off ties with his family when he went to college. For more reasons than one, their love had been destructive and "toxic" to Logan's well-being. Things like his minor perfectionist tendencies were messed with, and most days he thought he was a mistake... that needed to be fixed. So, love wasn't truly his forte.
And it never had been.
Well, until his roommate, ignorant Roman, decided otherwise.
◇◇◇
Logan was busy, typing up an essay that was to be turned in next week. It was a bit... excessive.
But, oddly enough, it was distracting him from something else. Though he wasn't exactly sure what, it was still insanely productive.
So, he thanked whatever put him in this spot.
Until Roman busted into his room, a deep rumble of arrogance enveloping his room in whole. (Not literally, of course.)
"Heya, Nerd Nerdypants," Roman smirked, as Logan sighed, "-whatcha up to?"
Logan was ready to launch something back at him, but his observations spoke out before he could. It was like his body processed the information before he consciously did.
Roman had hesitated.
Which wouldn't be a meaningful observation for anyone else truly, but with Roman's uncertain tone and hesitation... This was highly unusual, in all aspects.
"Roman-" Logan spoke, steady and clear, "-what is it that you require?" His roommate furrowed his brows, "I... don't want anything. I was just curious as to why you were locked away in your room is all."
Logan quickly concluded, "I believe someone as... persistent... as you, would note that I work on academics from 4 P.M. to 7 P.M.. Perhaps not that specific, but this is the only activity I do in the apartment, as I am rather... antisocial."
Roman faltered, as Logan spoke with a touch of a demanding tone, "So, I believe I'd like to know what you require, rather than answer the question you already know the answer to?"
"Okay, Logan-" Roman inhaled, "-you got me. Just don't go into Sherlock-mode... ever again. Despite that being terrifying, I wanted to talk to you about your -ew, can't believe I'm saying this- love life."
Logan did a slight double-take, his head taken out of the moment, as his face burned hot, "Pardon?"
"Look-" Roman immediately started to ramble, "-I know love isn't really your... thing per se, but I figured you're human and everybody needs somebody, right? So I wanted to-" Logan put his hand up to his roommate, "Roman, I'm not sure I understand what you are trying to communicate."
Roman groaned, "Listen here, Dr. Dictionary. I wanted to know if you'd be up for a blind date? That Pat... I mean, I would set up. Oh, and you can't say no."
Logan pursed his lips, "A blind date? I apologize Roman, but with my glasses, I have perfect visio-" Roman squinted, "Oh my god. Just shut it. A blind date, Sherlock, is when someone sets you up with someone of a mystery identity."
"If this were to be true," Logan hummed, "-what would be the point of such romantic affairs with someone if they are random? How would I know if they were compati-"
Roman interrupted, ready to explain, "See, that's the thing. I, as your close friend/acquaintance, would be challenged with task of getting someone to match you! If you don't like him, it's probably mutual and you can just leave. Simple. But, I understand if this is truly not your scene, you can s-"
Logan felt an impulse rise into his chest, and before he could thoroughly think, he spoke: "Yes, I'll try this... blind date thing."
Roman seemed shocked, his words halting on his tongue; Logan honestly felt the same to an extent.
"I, uh-" Roman swallowed, "O-Okay! Then, you have a date on Saturday... I guess. That was, incredibly easy."
As Roman sashayed away, Logan sat in his chair without a single thing running through his head other than Saturday.
It was an odd experience, the fear rushing up his arms and through his head. He could feel it in his fingertips, and the repeating words just tumbled into quite a disastrous train of thought.
Love was useless to someone with goals like myself. What was the point of loving someone if it's highly probable it wouldn't work out forever?
What if media representation dictated how it felt, and I was stuck in a terrible situation with no means of escape?
This thoughts kept growing with his head, a soft buzz echoing in his head growing higher in pitch.
With irrational words and feelings floating around his head, Logan began to realize something.
It's not his life that wouldn't work with love, not his efficiency, not his productivity.
It was him.
"He could be criminal, some sort of psychopath, who escaped from an institution, somewhere where they don't have girls. He could have masterminded some way to find me. He could be colorblind; How untrustworthy is that? He could be less than kind. Or even worse he could be very nice, have lovely eyes, And make me laugh, come out of hiding... What do I do with that? Oh, God."
Virgil was terrified, the kind of hand-shaking terror that bit at him when he had to do a presentation in front of the whole class.
Patton was driving, the car almost going faster, to get to it's location, than he could blink. Not that he was a bad driver, it was more like Virgil felt so nervous he couldn't feel the time pass by him.
"Virge?" Patton hummed, trying to keep his voice light, "Everything is going to be okay, I promise! If you feel unsafe or scared, just... let me know, alright?"
Virgil smiled at Patton, trying to steady his hands, as he nodded. Sometimes his anxiety got so high, that his voice would be unusable; he was too afraid to open his mouth and say things that might make it worst.
So, to say the least, if Patton hadn't chose to come with him, a random person would be tasked with consoling him from a panic attack...
This was still the worst idea Patton had ever had.
The lights of the quiet, warm-toned restaurant were peering through the windows of Patton's car, and Virgil's heart-rate skyrocketed. Pounding through his ears, he could feel it in his fingertips.
Patton placed a gentle hand on his shoulder, that brought the smaller man back to earth in a breath. The Dad-like man smiled, "It's going to go... great Virgil! No matter if you enjoy the date, I'm sure Roman would love to go somewhere with us. Like an arcade or a movi-"
Virgil sighed, "I'm not sure... that it would be my place, to be honest, Patt."
Patton pursed his lips, "Wha-"
He pulled into the parking space, as the sunset peered through the windows of the restaurant in front of him. Normally, this would be a beautiful scene, but Virgil tended to only focus on the negatives.
He hissed, covering his eyes from the darkening sun, and muttered, "I can't even see." Patton chuckled, "Trust me, you'll see him clearly, I promise."
Virgil smiled weakly, fiddling with his tie that sat on his black button up carefully (right in the center). Patton had said something about his date being very meticulous, and he didn't take that advice lightly.
His hair was as perfect as it could be in his style, his shirt was tucked in, and his belt was carefully wrapped around his waist in every loop. This would all eventually come undone (as soon as he was out of these bright lights), but Virgil would like them to know he made the effort at least.
"Ready?" Patton spoke, looking directly at the restaurant. Virgil sighed, rubbing his hand down his face, "As ready as I'll ever be, Patt."
It was a slow walk to the double doors, and all Virgil could hear in his head was what his date would supposedly be wearing.
◇◇◇
"It'd probably be incredibly simple," Roman had said, "-but elegant. In a way, despite the articles plain, it'd work together perfectly."
"Roman-" he had seethed, "-that is literally the most basic information I have ever heard. Literally ever."
Patton had giggled, his glance probably focusing a little too long on Roman, "Listen kiddo, he'll probably be wearing a regular suit with either a deep blue-" Roman interrupted, "Or royal blue!" Patton furrowed his eyebrows, finishing, "-tie...?"
Roman had cleared his throat, "Bow-tie."
◇◇◇
Virgil's thoughts repeated, 'Suit with blue bow-tie, suit with blue bow-tie, suit with blue bowt-' That was when his body crashed into someone else's, a quick impact that oddly enough he hadn't caught himself. ("Fight or flight, amirite?")
Surprisingly, however, the person had saved him from his fall and stopped him from ever falling to the floor. Like a cliché romance novel.
"Oh, I-I'm so sorry-" Virgil pushed himself out of his arms and stared at the ground, desperately avoiding eye contact, "I wasn't looking."
The stranger paused for a moment, before speaking with a familiar voice, "Virgil? What are you doing here?" Virgil's eyes flashed up, his eyes meeting the boxy frames of familiar glasses, "Logan?"
Logan paused, inhaling through his nose in a bit of a dumbfounded gaze, "I, uh- Roman-" Virgil chuckled, rubbing the back of his neck, "Yeah, Patt he uh-"
Logan watched him carefully for a moment, eyes catching on his clothing for a second and then again, "Quick question... Virgil, are you wearing a black button up, purple tie, grey jeans, and black converse?"
Virgil furrowed his eyebrows, not exactly catching on, "Good observation, L... I guess."
Logan paused, rubbing his temples for a moment, "God, how did I not catch this earlier?" Virgil timidly touched his arm, "L, everything okay?"
The taller man nodded, briefly, before grabbing his hand, "Virgil, I believe we have matters to discuss, separately."
Virgil opened his mouth, but was silenced by the nerves rocketing inside of his stomach at the warm of Logan's hand. Don't think about that, weirdo.
Logan pulled him to a table that was originally able to seat four, but they just sat in the two seats beside eachother. Virgil was patient, a bit confused, overwhelmed, but oddly happy.
"I-" Logan paused, reluctantly letting go of Virgil's hand, "-think I know what's going on here." Virgil furrowed his eyebrows, "L, for the last time... You're not really Sherlock Holm-"
Logan interrupted, "No, no. Nothing like th- Listen, Virgil. I think... I'd like to believe that... Well, you're my, uh... companion for the night." Virgil sighed, "I would, L, but I'm kinda busy wi-"
Logan shook his head, "I'm not sure how to put this, I believe Roman used... Virgil, I believe you are my blind date and I, yours."
Virgil's face flushed a bright red, inching all the way up to his ears, "W-What?"
"I believe-" Logan sighed, his ears tinging red as he looked at the table, "-Patton and Roman saw my conundrum, and acted on it. I believe they set us up."
"Your conundrum?" Virgil muttered, a bit confused in his tone.
"Yes-" Logan answered, confident and precise, "-I think I may have romantic feelings... involving you."
Virgil's face blushed bright red, "Oh."
Logan continued, "So, I believe they decided to take advantage of their observations... And set us up." Virgil spoke before he could think about it, "Is that... bad?"
Logan paused, readjusting his glasses slightly, "I... No, not at all. If it is not pressuring you in anyway, I actually quite enjoy the idea of... pursuing... a romantic relationship with you."
Virgil's heart-rate was through the roof, he was almost getting dizzy at how fast he could feel his blood pumping. His hands were shaking and his mind was racing, this was not supposed to happen.
The blind date wasn't supposed to be great, Virgil couldn't handle... But, it was Logan.
Logan wanted to be with him, Logan felt something towards him, and Logan had always been there for him.
Suddenly, his breath harbored in his chest and, immediately, he felt someone wrap themselves around him.
Their limbs were a tad bit awkward, but it only lasted a few seconds, until a voice fazed into his ears, "Breathe with me, Virgil. Follow my breathing pattern."
And Virgil did, in the middle of some high-class restaurant.
It took a few minutes for Logan to calm him, but it was faster than he'd ever done on his own.
"I..." he inhaled, scared of what he was going to say, "-I like you, Logan. I really, really do. It's just... this scares me and I'm not sure I'm ready for this yet. But, if we took it slower..."
Logan smiled, a warm smile, "Of course, Virgil. I will wait as long as I have too. However, I would like to formally do something first."
Virgil furrowed his brows at the man to his left, tilting his head slightly in confusion.
The taller man chuckled, speaking a little nervously but still as clear as ever, "Virgil, would you like to be my companion for tonight?"
Virgil smiled, the fear taming in his stomach, "I guess so, dork."
"What if when he sees me, I like him and he knows it? What if he opens up a door, And I can't close it? What happens then? If when he holds me, My heart is set in motion, I'm not prepared for that. I'm scared of breaking open, But still I can't help from hoping To find someone to talk to Who likes the way I am, Someone who when he sees me Wants to again."
Things were taken slow, with complete respect to Virgil. One date lead to another, and another and another...
Virgil had found out some things about Logan, that he never truly knew.
Logan was probably the sweetest person on Earth, other than maybe Patton. Anytime Virgil would speak to him, he'd give him his full attention. No matter the circumstance.
Logan also had this tendency to want to remember everything about him, like everything-everything. But he didn't gush about it or anything, he just listened with a small little smile on his face.
And one time, Virgil had been ranting about want he had wanted his future to look like and, low and behold, he looked over to see Logan frantically writing away in a little purple notepad.
To be honest, Virgil felt like he was in love.
At least, that's how he imagined love felt like. After hearing all those cliché descriptions in movies, he had decided his own idea of love. Harboring on the fact, that you couldn't wait to see them everyday, and that they were one of the most important things in your life right now.
Logan meant everything to him.
Which is why Virgil felt horrible.
It had been about a year since their first date, and Logan hadn't overstepped any boundaries since the beginning. He was still waiting, quite patiently in fact.
It took him a whole year, to decide to get into a relationship with a man he had adored for longer than that. But now, he felt like he had just strung him along for ages and that Logan deserved someone better than him.
It took him awhile to decide how to approach him, after such a complicated thought-train. He knew he was horrible and the worst for Logan, but he had to hold onto him.
He loved him, and he was scared of never having that again. Especially without Logan.
The voice from the phone chuckled, "Hey, you're not the worst for Logan, Virg. I've never seen him so happy!"
"It's-" Roman chuckled nervously, "-honestly kinda freaking me out. He truly hums along with 'Make You Feel My Love' by Adele, if you're an uncultured swine, quite... quite frequently."
Virgil smiled, "Really?"
Roman laughed, "Of course, now what was the whole point of this conversation, the Incredible Sulk?"
Virgil rolled his eyes, muttering with an embarrassed tone, "I was kinda wondering if you knew when Logan wouldn't be busy...? I kinda, wanted to... talk to him."
The voice on the other side was quick, "Literally, Panic! At The Everywhere, he would stop everything for you. Just tell him you need to speak with him, and he will drop his plans for the next month."
Virgil inhaled, "But... that's not-"
"Listen," Roman spoke briskly, as if hurrying the call, "-Logan isn't going to kill you... If he does feel free to tell Patton my secret, okay?"
"Oh," Virgil smirked, "-you swore on the secret, you must mean business, huh?"
Roman groaned, "Oh, shut it. Gotta go."
Virgil huffed, his arms crossing as the dial tone echoed into his ear. Ultimately, he had a plan but Roman had been too hardheaded to actually let him speak.
So, now, Virgil had to approach, and confront mind you, Logan about how he felt and where he wanted to go with it.
Let's just say that didn't happen for a long while. For obvious reasons.
◇💜🖤◇🖤💙◇
Logan believed it was a generally normal day, normal work and normal people. To be fair, the only time his days were truly different were when someone else intervened into them.
Today was fairly average, however, as Logan sat at his desk typing something way ahead of its due date. Until, the window in front of his dark wood desk lit up in a flash, lightning.
Logan began to feel his heart race, not necessarily out of fear, but out of concern truly. Where there was lightning, there was thunder.
And normally (he should really take a glance at the thesaurus again), this was no issue. Logan would shake his head and continue working.
But this time, Logan knew of a male 10 minutes from where he was, who was sensitive to the booming thunder just at his fingertips.
The intelligent man began to scour the room for his phone, a bit of fear bleeding into his movements. Random frantic movements brushed across shelves, beds, literally every surface. Until, he felt a buzz in his pants pocket.
(Virgil = italicized, Logan = regular.)
"L?"
Logan let out a breath, he didn't know he was holding. His mind buzzing with questions and concerns, all directed to the male on the other side of the line.
"Virgil, is everything okay? I know you told me about your problem with thund-"
"L, I... I think I need you here. I'm not sure if I can-"
"I'll be there in 10. Do you want me to stay on the phone with you? Is it calming enough to hear my voice at the moment?"
"Logan, I couldn't ask you to-"
"Virgil, it is not a issue. I truly care for you, and you being afraid inside your own walls isn't a pleasant thought on my part."
"...okay."
"While we are waiting, did you know it is illegal to carry an icecream truck in your back pocket in Kentucky?"
He could hear a light muffled laughter on the other side of the phone, and with the sound he smiled peacefully towards himself.
The conversation flowed with useless facts and statements of adoration. He could feel Virgil relax, his tone more gruff and comments more sarcastic.
It was... as if it hadn't even been storming outside.
Until, Logan saw a bright flash of lightning and a deep roll of thunder. That had honestly caused the man who was supposed to be calm, to jump in his seat.
This wouldn't be a big deal, unless Logan hadn't seen what the lightning had struck. A bright flash echoed in his vision, lighting up the silhouette... of a cell phone tower.
Logan's heart-raced in his chest, "Virgil? Virgil, can you hear me?"
Laying his phone down in a swift movement, Logan may or may not have sped down the empty street.
He stared into the night, muttering to himself, "Left, right. That's all I have left. Turn left, turn right."
The rest of the drive and walk to the door was quite brisk, in retrospect. His body had been in control, and his mind had fuzzed over. Which was an unusual experience for one such as himself.
With a quick move, Logan had unlocked the door and carefully let himself in.
"Virgil?" Logan whispered, afraid to speak any louder, "-I... I'm here. It's me, Logan. The cell phone tower was... over-surged with a spontaneous lightning strik-"
A voice from the dark room (because Logan had been right, it had overwhelmed the electric as well), echoed, soft and shaky, "L?"
Logan felt a familiar, what he assumed was, heart palpitation and smiled lightly, with a tinge of concern for him.
"That is..." Logan tilted his head, "-my nickname, ye-"
Before Logan could blink, a shadowed figure enveloped him, his grip as tight as he assumed it physically could be. He carefully returned the embraced, gently kissing the top of his head with a quiet whisper, "I apologize for not getting here sooner, but I was truly breaking many law codes to ge-"
Virgil laughed into his chest, a light sniffle echoing in his ears, "God, I love you."
He could feel Virgil freeze slightly in his arms, a little uncertain he guessed. But as impulses tended to overrule in this situation, "I... love you too... Virgil."
Virgil inhaled, relaxing into his grip again, "I... have for awhile now. I just wasn't ever sure... If I... deserved it- er, I mean- you... Really, because I took so long t-" Logan interrupted him, a calming tone etched into his voice, "I believe being patient for... something that is of value... is rather, worth it."
As lightning bellowed through the room, Logan simply saw the man he had carefully held in his arms.
"I... really, really love you..." Virgil muttered, his arms tightening around him with no hesitation. Logan felt his heart "flutter", as his smile stretched across his face, "I love you too."
Logan had a lot of issues with love, as did Virgil. To be fair, neither believed it was truly their forte.
But, two negatives do make a positive, and neither could truly argue with Logic, could they?
#sanders sides#analogical#oneshot#logan sanders#virgil sanders#ts#ts logan#ts virgil#songfic#when he sees me#virgil x logan#logan x virgil#watchoutwriting
58 notes
·
View notes
Text
A new Wave of Dating Apps Takes Cues from TikTok and Gen Z
Luckily for people like me there is The Fort Worth Dating Company. In England, Wales, Ireland and Britain's American colonies, there were two calendar changes, both in 1752. נערות ליווי בצפון The first adjusted the start of a new year from Lady Day (25 March) to 1 January (which Scotland had done from 1600), while the second discarded the Julian calendar in favour of the Gregorian calendar, removing 11 days from the September 1752 calendar to do so. By carefully dissecting and exploring these structures, scientists have access to some of the only remaining clues about what the first life on Earth was like. In today's world, there seems to be an infinite number of ways in which people can connect, but many people struggle when it comes to their dating life. Laquelle Mills is six years older than her partner, Malik Rashid, and makes more money than he does, but she appreciates the fact that he can provide for her in a different way: through communication. This awesome dating site offers both paid subscriptions that provide more features at an affordable price with no ads.
All the chat features mentioned above are also available for your group chats. All three of them are interested in you. Looking at this in a diagram where one is the strongest date and three is the worst, we can see that are six possible scenarios. There’s space on your Dating profile (which you choose whether other users see) to describe yourself in three sentences. Badoo is an interesting app for Indian users. Funny or not so funny, we want to hear about them. As an example an adult person that is dating might want to head to a web site that actually works with seniors. Nope. I want the money, but I know I'd go crazy after a week. This is especially important if you suspect or know that your partner's obsessions and/or compulsions relate to you and/or matters of sexual intimacy. I shrug. If my date didn't like it, they'd tell the stranger to stop, right? We also always remind our senior singles that you’re never obligated to respond or continue the conversation with potential matches if you don’t find the right spark. Don’t include your contact information such as your email address, home address, or phone number in your profile or initial communications.
For the individual display times home page. In the meantime, let's get ready for a reality check on the next page. I'm not good at climbing trees, so I guess I'd get murdered. Good luck with this tricky but important issue. I get angry and start dancing with a different attractive stranger, hoping to make my date jealous. Drinking and dancing will keep me warm. We're all individuals with free will. But Facebook Dating will also gather even more information from Facebook users, information that will presumably be more intimate, up to date, and relevant to what people actually like and think. Despite Zoosk being advertised everywhere, people started opting for Match Group's offerings with more premium designs, less messy notifications, and personalized algorithms. I don't like admitting that I enjoy being spoiled, but I do. Whatever niche you would like to occupy, don't worry; we have already made a proper template to go with.
Antagonism and hostility are well-documented traits in people who have NPD, and their toll on other people is large. People can't "steal" other people. I would never steal someone else's partner; that's evil! Many people have a hard time meeting someone online, but it is vital to the health of the relationship that you meet the person after speaking with them for several weeks. Finally, the FBI advises not to send money through any wire transfer service to someone you met online. Truth is: You still can! If you still have safety concerns, meet in a public place. Ironically, a man and a woman meeting in public was the best way to have some privacy. As a premium user, you'll have more suggested connections than a free user. The great thing about this process is that even if you’re not serious about dating, you’ll likely to find out more about yourself when it comes to love aspects. I love cuddling, so give me the blanket option.
1 note
·
View note
Text
Get Your 4 Wheel Up & Running With the Extra Discount

Right when 4 Wheel Parts opened its entryways in 1961, the technicality was "Quality Parts, Lowest Prices, Fastest Service and Fully Guaranteed."" Powered by that standpoint, 4 Wheel Parts passed on using a one-single advancement to the overall pioneer in truck, Jeep, SUV and unforgiving space execution things. Today, following 55 years, our customers really demand better assistance — and we endeavor than pass on at each possibility. In 1961, George Adler considered a to be as the sole full-time illustrative of another connection, Transamerica Auto Parts. The business had an unassuming start, selling replacement Jeep parts to immaterial go mud skipping around shops and Jeep subject arranged specialists. These affiliations were serving the necessities of Jeep owners who were as shown by a general point of view starting to use their Jeeps in the enchanting American outside
4wheelparts coupons
Unequivocally when the phone began to ring, it was George who answered and dealt with the deciding. Absolutely when a customer required parts speedier than standard advancement would allow, George gave the introducing himself. For one customer, he drove for the present from Los Angeles to Oakland to ensure the parts displayed on time. Before enough long, George's customer help with driving had gotten the mental spine and respect of Jeep dealers every single through Californium. George, seeing opportunity, become bound with the relationship with his father in-law for $5,000. This endeavor decision would wind up being an astonishing one. They see that while doing going 4x4 swaying or doing any staggering improvement your vehicle ought to be outfitted with the latest additional things which makes your going skipping around experience really astounding and supporting. Disregarding long different years, they are in the business and all around that genuinely matters, oblige customer needs in an issue highway. Over 55 years of adaptable experience they debilitate the vehicle business. With such muddling affiliations, they are possibly changed out gigantic number of visitors into participated in the experience of customers. In the current date, they have boundless awe inspiring costumers and attempting to ad lib their relationship to a continually creating degree.
4wheelparts coupon codes
4 Wheel Parts has a crosscountry chain of retail stores and association centers. Drop in to one of our 94 stores across North America to take a gander at thing and get shifted direction and partnership. Visit our store locater page to find a store near you. We work in getting off-road parts to you quickly. We do this by stacking stock in six stream twirls made around the country. Our open stock sets more than $100 million of unbelievable scene parts from around 600 makers. Right when you need a disturbing scene part quick, we're your best asset. Shop with us at whatever point, on your technique. Take a gander at 4WheelParts.com, call our customer help center, or come visit us in one of our stores. You can even get a sensible technique on transportation costs by shopping on the web and getting your viewpoints in a store. Regardless of which structure you like, we're ready to help with astounding parts, bearing, and association. Our saves set up with ASE-upheld experts who can present all that we sell. You'll correspondingly get fulfilling and fit help when you call our Customer Service Center for plans and data. We are spun around outfitting you with quality things at amazing expenses. Our size and status in the business gives us confirmation to astonishing technique that we oblige you. We all around help to work with any yielded advanced expense, through our worth match guarantee match guarantee program
4 wheel parts coupon code
4WheelParts.com contains various resources for help you with picking and present the right parts and stuff. Watch accounts, read articles, and see thing contemplates. We demand that our customers give their experiences to us through online media area and thing diagrams. Evaluation what people are saying around 4 Wheel Parts.4 Wheel Parts keeps an A+ rating with the Better Business Bureau (BBB). We respect being a strong improvement and resource for the disturbing scene region.
4 wheel parts coupon code military
If you own a four-wheel vehicle, you hold the decision to shop at 4WheelParts.com for all your part needs. We have puzzling among other part inventories on the web and we offer money saving coupons for 4WheelParts that help you with getting the parts you need for not actually various people. Start shopping today and take a gander at our Deals of the Week to see what we have on popular. In addition, attempt to use a 4WheelParts progress code from the decision above to get a respectable method on a key level more.
4 wheel parts coupon codes
Getting a sensible procedure on your four-wheeler's parts is central at 4WheelParts.com. Fundamentally select the 4WheelParts coupon code you need to apply to your recommending and data the code when affected at checkout. Regardless of whether you're searching for new shocks, wheels, evening out units, or whatever else, you'll see it at 4WheelParts.com. Also, with our restrictive coupons for 4WheelParts, you can get all you need at a value that can't be beated.
The Extra Discount At 4 Wheel Parts
When did you think to extend your vehicle's inquiries first thing rings a bell where may I have the choice to get the best and sensible additional parts and updates for it? The reaction to this issue is here "4 wheel parts". They are an essential distributer of 4X4 jeeps, enormous truck embellishments and additional parts, which gives your vehicles the central looks for which you are paying popular brain to. They attempt to give the latest embellishments which are much sensible for your vehicles since they perceived how people a ton influencing about their goliath rides. From spare parts to insane embellishments they have a wide mix for all monster and jeep dears. Their first in class things gets masterminding nearby dress, front and back suspensions, lift packs and mass more to discover. They offer cerebrum blowing structures in their different classes, to experience such a markdown offer you can use 4 wheel parts coupon for it.

0 notes
Text
Social media and education in 2030: Using social media as a resource and tool - Amy Gardiner



Social media continually impacts many areas of our lives. Social media gives us the power to connect, share, and in turn, educate one another. It becomes more and more important as the web and social media grows that we use these tools to educate ourselves and others. Just like the web, we have access to so much knowledge and information at our convenience, right at our fingertips or at the click of a button. In terms of education in the year 2030, social media will become a great tool to use as a resource for research, be used as a teaching platform, and recognized as a learning style.
To start, the education system and curriculums are constantly changing to keep students engaged but also to help keep the learning outcomes relevant to present day. One of the driving forces for education in and outside of school in present time is, of course, the internet. With online resources becoming more important and easier to access, education has evolved in the past few decades. However, with the rise of social media, the future of education could have a major breakthrough. In fact, a study revealed that roughly seventy percent of students use social media for educational purposes Diagram ii (Baruah, 2012, p. 6). In the years to come, specifically 2030, we could be seeing new and innovative ways to encourage education and learning in and out of a classroom through the use of social media. For instance, this article written in 2013 discusses the benefits of using social media in an educational setting. Fourteen studies concluded that interventions using social media tools resulted in improved knowledge (e.g. exam scores), attitudes (e.g. empathy), and skills (e.g. reflective writing) (Cheston & Chisolm & Flickinger, 2013, para. 3). The article also mentions the benefits of using social media as a resource in education because “[it] can overcome physical or temporal barriers, provide searchable content, and encourage interactivity” (Cheston & Chisolm & Flickinger, 2013, para. 6). To add, the students part of this study used one or more social media tools such as blogs (71%), wikis (21%), Twitter (14%) and Facebook (14%) which helped them in their studies (Cheston & Chisolm & Flickinger, 2013, para. 24). In 2030, “83% of the experts think that the pedagogical content will shift to more tailored and personalized content, adapted to individual student profiles” (WISE, n.d., p. 4). By using social media within the education system, it will allow teachers as well as students the opportunity to engage with one another on a platform that the younger generations are comfortable with. If social media was encouraging the growth and development of a huge number of students back in 2013, just imagine how many more are benefitting now and will be in the year 2030. Also, if social media continues to be (for the most part) free, it gives educational institutions more than a good reason to include social media as an education and resource tool. Another survey conducted based on schooling in 2030 found that “93% of respondents favor schools that implement innovative methods based on new teaching approaches and creative processes” (WISE, n.d., p. 4). By 2030, thousands of schools will be using social media as a major part of their teaching methods and as a resource for information. An article written in 2016 asked a series of questions to both students and teachers about using social media as a tool and resource. One of the questions asked why students used social media in terms of education. The results as represented in diagram i showed that 50% used it for professional links, 40% for making assignments and 10% for better research (Bahl & Gautam, 2016, p. 4). Evidently, students are aware of and are making use of social media to benefit their learning. By the year 2030, these statistics would probably be even higher. Also, this article also mentions three key points about using social media as an educational tool:
· Social media is not going away. “Students should be taught to use this tool in an efficient way in the educational classes than just being used for messaging and texting rather they should learn to use media for a good cause” (Bahl & Gautam, 2016, p. 1).
· When students are engaged, they tend to listen better. Some students don’t just learn from pen and paper. By using social media tools like blogging, for instance, it may encourage students to write for the teacher and themselves. By using social media to engage, students will likely do better work (Bahl & Gautam, 2016, p. 1).
· There are safe social media tools out there. Sites such as Edmodo, SLATE or kidblog are safe and free online resources/tools that teachers and students can use to communicate and learn with one another. These tools provide an environment that the teacher can control while engaging students through a platform their generation is comfortable with (Bahl & Gautam, 2016, p. 2).
By using social media as a tool and resource for education, especially in 2030, students will feel a better connection to the coursework and their teachers. Social media can provide a wide variety of information and resources that they can use to benefit their learning. For instance, social media tools can connect students to other students, teachers, schools, and professionals in the workforce locally or from around the world. Not only can social media be used for research or finding information, but it can also be used to create a connection or community within a wider group of people. By having access to social media in education, it may also increase the individual’s social capital as they are connected to more individuals in different aspects of their educational development. By 2030, social media will allow students and educators to share, discuss, and expand information that they find using social media platforms as resource material. In 2030, social media can be used as a resource because students would have the opportunity to talk to professionals in the field through a social platform. This can enhance their learning because they are receiving knowledge from a direct source and they can skip browsing the internet for information that may not be as accurate as an active conversation.
To continue, using social media as a resource can encourage different variations of learning. For instance, social media platforms can allow you to create and upload a variety of media such as videos, quizzes, audio, slideshows, even games. In 2030, participatory culture as well as more forms of media can be presented on social media which can improve its value as a resource. Content generating and sharing sites are “a major advantage to most of the people who are unable to get access to the educational resources” (Baruah, 2012, p. 4). A study in 2012 revealed, as diagram iii represents, how much respondents used a variety of social media tools. The top contenders being social media sites, blogs and video sharing sites (Baruah, 2012, p. 7). Social media provides an environment that allows a better understanding, perspective and enjoyment as well as encourages strong relationships between peers, teachers, and other social media users. In the year 2030, education and teaching methods will have changed dramatically. With so much media content available to us, it is more than easy to combine media with education. For instance, virtual reality or simulations has risen in popularity over the last couple of years and will continue to grow in 2030 (Millennium Project, n.d., para. 12). With social media and its contents introducing itself into an educational setting, educators and students will be given the opportunity to gain knowledge in a multitude of ways. Staying with the example of virtual reality, schools can use this technology to enhance and vary teaching methods and present knowledge in a different way. Another example could be students who like blogging may find assignments or lessons with blog aspects to be easier to follow and grasp. Blogs are just one of many examples of using “public communications to reinforce pursuit of knowledge” in 2030 (Millennium Project, n.d., para. 12). “Gamification” will also be on the rise in 2030 as games will add “a more creative, dynamic element to learning” and “[give students] the flexibility to assess progress and adapt their learning” (Munoz, 2017, para. 9). The key to education and social media in 2030 is adaptation. If we as educators and students stay open to a variety of social media platforms and content, it opens so much more opportunities to retain, spread and explore information.
Despite the many good things that social media can give to us, there are also some drawbacks. Some of the most common challenges or issues students met in a study from 2013 were “technical issues (43%), variable learner participation (43%), and privacy/security concerns (29%)” (Cheston & Chisolm & Flickinger, 2013, para. 3). The technical issues, though quickly resolved, were just people having trouble posting on social media for their course and issues signing up for the social platform. In truth, it just comes down to how tech savvy someone is; these issues provided no major drawbacks. Adding to this, the variable learner participation, according to the study, was a case of students losing interest or contributing to other people’s posts rather than their own. This issue could be fixed if teachers managed to make the online course more engaging and chose a social platform and/or content that would keep things interesting. In the year 2030, with how popular social media has become, there will be so much more sites to choose from and most likely new platforms that make the experience interesting for the user. As for privacy concerns, however, it is an understandable burden. With information becoming easier to access and spread, privacy, especially in an educational setting, is of high priority. In this study there were no major breaches in privacy or security, it was mainly just a matter of reviewing the privacy settings of the platform. By the year 2030, there will most likely be a high demand for social platforms to be used as part of the educational curriculum as well as online classrooms. The curriculum would most likely research and decide on the best platforms to use for the given course to keep the students safe as well as fulfill their educational goals. With social media on the rise and being introduced into educational curriculums, it is more than likely that the privacy settings on most platforms would be improved immensely. In fact, here are some useful social media sites that could be great candidates for social media in the classroom (Chesser, 2013):
· TedEd is a platform that posts TED talk videos that are straight to the point and cover a variety of subjects such as science, technology, health, art, psychology and more. It also provides communities and clubs that can allow students as well as teachers to collaborate. (para. 7).
· Academia.edu is a website that allows users to publish and read research papers. Users can keep track of research from other academics they follow as well as see how effective their papers are. Great for finding information on a variety of topics (para. 19).
· TeacherTube is basically YouTube but for educational purposes only. Teachers can control and upload a variety of media (including audio) to engage, communicate with, and teach their students (para. 18).
· Edmodo is a platform specifically for education. Educators can post calendars, assignments, connect with students, and much more. It is simple, efficient, and easy to use for both students and teachers (para. 6).
Another challenge that may arise with social media becoming a resource in education is plagiarism. Students who plagiarize someone else’s work through social media may prove difficult to keep track of. With millions of blogs, videos and photos that are floating in cyberspace, some information may be easy pickings for someone on a social media platform. However, there are tools out there (such as Turnitin) that allow educators to see what information has been stolen from another source. By 2030, there will almost certainly be more tools out there to catch plagiarizers and allow educators to educate to their best ability without worrying if their students aren’t doing their own work. In fact, it is more than likely that tools to catch plagiarizers will be added to social media platforms because of how fast social media is merging with education. Receiving false or weak information is also a risk when using social media as a resource for information. People can post content without citing sources, take their information from illegitimate sources, or simple make it up themselves. That being said, an easy way to look for useful data is to find certified users on the platform. For instance, Twitter and Instagram use a blue certification checkmark beside a user’s name if they are recognized as someone of importance or high-profile. This may make it easier to gain knowledge from valued sources. Also, just simply researching the information you found on social media can often help you determine the truth in what you came across. Typing the information into your search engine can often produce links and material that either supports or denies the information you found on social media.
To conclude, social media is merging with education at a very quick rate. By 2030, social media will become an important resource for educating, collecting information, and being used as a learning style. The future of education looks promising as we manage to overcome obstacles in the educational world as well as the online one. Soon, different media platforms and online classrooms will become the norm in modern day society. The year 2030 looks promising as education takes the next step in the evolution of social media and knowledge.
REFERENCES:
Cheston, C. C. & Chisolm, M. S. & Flickinger, T. E. (2013). Social Media Use in Medical Education: A systematic Review. Academic Medicine, 88(6), 893-901. doi: 10.1097/ACM. 0b013e31828ffc23. Retrieved from https://journals.lww.com/academicmedicine/Fulltext/2013/06000/Social_Media_Use_in_Medical_Education___A.36.aspx#R9-36
Bahl, K. S. & Gautam, D. R. (2016). Use of Social Media as an Innovative Educational Tool By Teachers and Students. International Journal of Business Management and Scientific Research, 24, 1-5. Retrieved from http://eminencejournal.com/images/pdf/DE8.pdf
Baruah, D. T. (2012). Effectiveness of Social Media as a tool of communication and its potential for technology enabled connections: A micro-level study. International Journal of Scientific and Research Publications, 2(5), 1-10. Retrieved from https://s3.amazonaws.com/academia.edu.documents/45712283/ijsrp-may-2012-24.pdf?AWSAccessKeyId=AKIAIWOWYYGZ2Y53UL3A&Expires=1521735014&Signature=VJse3lzBhslg84GoJDbSoH7%2BkkE%3D&response-content-disposition=inline%3B%20filename%3DEffectiveness_of_Social_Media_as_a_tool.pdf
Chesser, L. (2013). 25 Awesome Social Media Tools for Education. Retrieved from
https://www.opencolleges.edu.au/informed/features/social-media-tools-for-education/
World Innovation Summit for Education. 2014 WISE Survey: “School in 2030” (n.d.) Retrieved from https://www.wise-qatar.org/sites/default/files/wise-survey-school-in-2030.pdf
The Millennium Project. (n.d.). Education and Learning Possibilities by the year 2030. Retrieved from http://107.22.164.43/millennium/Education-2030.html
Munoz, S. (2017). What Will the Student Experience look like in 2030? Retrieved from https://www.d2l.com/en-eu/blog/will-student-experience-look-like-2030/
IMAGES
Diagram i:
Bahl, K. S. & Gautam, D. R. (Professor & Director). (2016). “Why do Students Use Social Media?” [png]. Retrieved from http://eminencejournal.com/images/pdf/DE8.pdf
Diagram ii:
Baruah, D. T. (Author). (2012). Percentage of respondents on the use of social media for educational purposes [png]. Retrieved from https://s3.amazonaws.com/academia.edu.documents/45712283/ijsrp-may-2012-24.pdf?AWSAccessKeyId=AKIAIWOWYYGZ2Y53UL3A&Expires=1524250026&Signature=E8IYjIBuMr3hQlzpdJE%2FE%2BRUT%2Bs%3D&response-content-disposition=inline%3B%20filename%3DEffectiveness_of_Social_Media_as_a_tool.pdf
Diagram iii:
Baruah, D. T. (Author). (2012). Percentage share of respondents on the use of different social media tools [png]. Retrieved from https://s3.amazonaws.com/academia.edu.documents/45712283/ijsrp-may-2012-24.pdf?AWSAccessKeyId=AKIAIWOWYYGZ2Y53UL3A&Expires=1524250026&Signature=E8IYjIBuMr3hQlzpdJE%2FE%2BRUT%2Bs%3D&response-content-disposition=inline%3B%20filename%3DEffectiveness_of_Social_Media_as_a_tool.pdf
3 notes
·
View notes
Text
Okay need to Buy Google Review?
If your business doesn't have amassed beast google business bases on your Google business page, or even has too many negative ones, But you should think about buy unimaginable Reviews.
Get Reviews on Google to reasonably epic information about your business, to both you and your customers. Business buy google reviews thinks about appear near your posting in Maps and Search, and should interface with your business to stand detached on Google. Answer to studies to make your customer's trust.
5 Powerful Advantages of buying Google Business Reviews.
1.Google Business Reviews Increase Brand Trust.
2.Increase Online Exposure and Local SEO.
3.Increase information circle and customer
4.make amazing Rates for Your Website by buying Google Business Reviews.
5.Google Reviews Convert More Customers.
Why Are Online Reviews Important?
1. Bound Google considers reason customers to scatter.
2. 99% of clients read surveys Google going preceding visiting a business.
3. 92% of clients read plots going before creation a structure decision.
4. 89% of clients trust online charts google the most key absolutely as beast proposition.
5. 72% of customers will take an action from an overall perspective happening to taking a gander at a positive web plot.
6. Customers are likely going to eat up 32% more on a business with overwhelming 5-star follows on google.
Why had the occasion to Buy Positive Google Reviews?
If you purchase Google Maps Reviews it helps with changing over More Customers for your business. Google evaluations and Google 5 star breaks down assistance brand trusts. Get Business Reviews with recuperation . In the event that you're new and you need routinely more necessities to use such a help, by then we'll share a couple of anticipated outcomes. you see a point of view to buy positive diagrams online Google is gathering the web world by giving its moving kinds of affiliations. Google's program and Play store are impacting. Really they're the ruler.
Live Customer Service to help You 24 Hours determinedly, 7 Days reliably
If your thing joins a reasonable number of studies, Google may show your thing on its first page of the program . As necessities be, you'll get an outsized number of approaches to manage your site/page. In like manner, try to add buy google follows on the web or buy google considers usa with no other individual or use someone who will work for you. In case you envision that to support our affiliations, you're endlessly welcome.
So you'll Buy Play Store Reviews or Buy Google Apps Reviews and Google Maps Reviews.
It is guaranteed going to introduce that you are should look for Google places Reviews (Place/Business) wide and guaranteed or would they say they are fake Google considers?
1.All structures gave are ensured, confusing, and non-kept up. You get a surrendered report from customers who kept up their experience near your things or affiliations - be it a positive or negative philosophy.. for instance, if you proposed 10 positive plans, you'll get 9 positive google studies and 1 negative google reviews.These explores are surprising and we have no impact over customer examination. During this case, you'll everything considered be charged for the Nine positives, and be ready for 1 more certain assessment. Interface with us if you'd like further clarification on this.
2.Our providers use a spread of solid structures including running electronic media sorts of progress or plan recommendation to re-turn your customers and urge them to disseminate proposed overviews through email contraption.
So you'll get US, UK, CA, AU google charts pleasingly to develop your business.
Alright have the choice to require Buy Google Reviews or Custom assessments?
3.Yes, you can. After you've completed your purchase, you'll show to us in our dashboard whether you'd sort of a positive report or negative review.A positive system is constantly 4 to five while an evaluation is 1 to 2 stars.
4.Please contact keep up in the occasion that you've any custom appraisal necessities going before get-together.
Will I buy won't? Would I have the decision to buy safe Google Reviews (Place/Business)?
1.You won't be limited considering the way that our Google plots portrayed above are guaranteed, Our Services are dependable inside the Terms of Service to Google.
2.We other than needn't release up around inactively with your record accreditation. As necessities be, it is ensured about and there is no fear of the record being hacked and kept.
Is the improvement of Google Reviews (Place/Business) mind blowing? Is it safe to pass on them snappier?
1.Delivery inside around 2 to 15 days learning the bits of your perspectives. Geo-zeroed in on hypothesis may take a for the most part clearing time. In the wake of acclimating your appearing with you will get a more cautious vehicle course of occasions from our board.
2.We pass on professionals each and every development as such all through a period of your time (spill feed) rather than in one go-to present a brand name improvement of your picture and thinking the security of your Google account. Considering, our predictable structure all around spreads the new disturbing new abrupt astonishing new unforeseen development and pass on a little and safe degree of studies on a standard.
3.We can pass on them speedier than we're told considering the way that we're endeavoring (BUT don't pledge) to interface with individuals that are really astounded by your home or business to travel away from an evaluation.
Would I have the decision to target just Geo-centering from express countries?
We don't have one country zeroing in on. Considering, we keep up different countries (zone) zeroing in on. On a key level select your key Geo-center beginning from the drop once you demand. In case your goliath zone isn't open beginning from the drop decision it proposes we don't keep up Geo-centering for that space. In case its dull to you note that it may require some speculation to pass on geo-zeroed in on orders.
Why GMB is the Best site of others?
1.100% gigantic
2.100% Money-back presentation
3.24/7 Customer Services
4.Quick Delivery
5.Reliable and Quick correspondence
6.100% Satisfaction Guaranteed
7.GMB is a checked evaluation posting affiliation site.
8.for the key event when, we endeavor to consider our to be as we give buy 1 star google examines openings and you can buy researches for google
How to get 5-star bases on Google?
Right when you truly need to shop.
If its slight to you Give us the best degree of information. You know your business and its customers better than anyone; So while setting in your blueprint, balance your summation to tell me obviously what you need.
Why may you pick GMB?
If we don't pass on your thing on time, you will be bound all your money. We guarantee 100% satisfaction of our work and give the entire day, enterprisingly customer help. For this, you don't have to worry about buying quality things and affiliations.
GMB unnoticeable for this union?
We by and large in everything considered around know the evaluation of your money. In that limit, we as a last resort give strong things at humble expenses. You can keep our affiliation and any spot or site and get such cerebrum blowing help at such a short cost.
Why does my Business had the occasion to buy 5 star Google Reviews?
Considering, Google is at the most totally immense of a budgetary system . buy 5 star google follows has guaranteeing about the trust of customers round the world, changing it into one of the standard striking assessment stages. dismissing which industry you're in, the boundlessness of Google Reviews can't be kept. These evaluations may immovably impact your ORM (web standing association) and SEO (page smoothing out). Here are a couple of reasons why buy 5 star Reviews are so key to business visionaries.
No-Cost Advertising
A key ideal zone of Google Reviews is that the size of its get-together. As you most likely clearly know, a more grounded swarm drives a more grounded pushing undertaking. With a solid Google reputation, you'll like a no-cost kind of publicizing. In like manner, suffering Google graphs will help your connection magnificently sway potential customers' buying decisions. Google considers are the best way to deal with oversee manage supervise direct control direct control add to other moving structures without spending more, which they will help build up the association's customer base.
Building Closer Relationships with Customers
Study fights and online media stages have a goliath see normal: the workplace to make relationship with customers. Making room that study district offer customers an occasion to take a gander at their experiences, both flopping and disturbing, it's a street. By responding expertly to all or any or any assessment, you'll keep up the relationship near your customers.
Enough when affiliations answer the degree of that customers are giving about them, notwithstanding, when those things are not as a rule unsafe, people trust them more and get-together social affiliations. With time, those affiliations structure the inspiration for brand clear quality and an on a perseveringly key level ordinarily more wide customer base. Customer affiliations are one among the spines of a colossal business and ought to be worked with care.
Finally
All we will say is that we respect your cash and some time . Suffering Buy Cheap Google Reviews Services from us will shake both time and cash. be glad to see out or join as one with me by setting in the proposing or through preparing. If you have any proposing, let me know
0 notes
Text
Why Architects Need an Event Portal; Designing a System that Disseminates Real-Time COVID-19 Data
The need to exchange information in real-time has never been more apparent. The changes occurring in everyday life due to the outbreak of the novel COVID-19 virus have been nearly unimaginable for many of us, and staying informed feels like a lost cause.
What does this have to do with why architects need an event portal? In the last few days, I have personally been wondering what I could do to help the world get more real-time information in order to make better decisions. While my colleagues and I have been practicing social distancing and self-isolation, I felt we could do more.
One of the things we have been using to stay up to speed about the spread of COVID-19 was Johns Hopkins Dashboard which is being used as a “source of truth” by news outlets around the world.
It occurred to me that the data are constantly changing, yet many media outlets are basing their reporting on old information. I wondered if others had wondered how to get this data in real-time and stumbled upon others who wanted this capability (no surprise that my idea was not original or unique!). So, like the technologists we are, we set off to make it happen, and our work exemplified why our new product Solace PubSub+ Event Portal is so useful when you’re collaborating on the development of event-driven systems.
It’s easy to sketch an idea on a bar napkin or coaster (like we did in the good old days pre-coronavirus), and banter about how awesome it would be. The challenge has always been taking it to the next step of specificity, i.e. figuring out what exactly it does, how and why it does that, how people or other systems interact with it, and how it could be implemented.
Over the past several years, there has been an ongoing joke at Solace that we are just “plumbers of data” because our event broker puts in place “smart pipes”. Imagine you’re tasked with building an airport and you need to design the systems by which water, steam, and natural gas are distributed. Could you imagine sketching out the routing on a napkin? How would you express the routing, diameter, and contents of each pipe? And how would you define the end user interactions, i.e. faucets, toilets, ice machines, etc.? You wouldn’t because the architects who design buildings use specialized tools that let them design and define what each building needs. Those designs are converted to blueprints, cut-sheets, and parts lists so the plumbers who’ll be putting the pipes in place have a reliable, fully informative picture of what they must build, and it gets built per design.
Let’s look at how an event portal helps application architects do the same thing for developers.
Creating an Event-Driven Application with an Event Portal
Our goal was to create an application that acted as a client to the Feature Service to collect data for the cases for each country and publish to a topic. Pretty simple right? Well, in the past, without any specialized tooling, we would have created a Confluence page that described the work to be done, the schema, the event topic hierarchy, and most likely a PowerPoint diagram that showed the “system actors” and how the data would flow. Yuck! API Management solutions are no help because they focus on synchronous RESTful APIs and not the event driven world. But, it’s 2020, let’s look to the future and use an event portal to see how it can ease the design of an event-driven architecture.
Step 1: Identifying Updates
The first thing we had to figure out is how to detect changes to the Johns Hopkins data set and understand the data formats and structures. It turns out that the John Hopkins page is powered by a product called ArcGIS that leverages Open Geospatial Consortium standard of Web Feature Service (WFS).
I began designing this new event driven application using PubSub+ Event Portal. We were able to invoke the Feature Service in Postman, get a response, and use a JSON-to-JSON schema generator to reverse engineer the data models. Now that we had the data, we decided to look/poll for updates every 30 seconds and compare new data with old to identify changes.
These updates needed to be sent with the ability for the consumer to filter them by country, region or whatever attribute had been updated (e.g. confirmed diagnosis, recovery, or death). We created events using our Topic Best Practices Guide. This design, including some fruitful debates over the topic hierarchy, took about an hour.
Step 2: Enabling Developers & Creating the Applications
The next step was to get this blueprint in the hands of the people who could take advantage of it, i.e. developers. Since PubSub+ Event Portal supports the AsyncAPI spec, we were able to generate a code skeleton for each application we wanted to build. Over the past few months, Solace has been working to deliver an AsyncAPI code generator that would help Spring Boot Microservices developers easily create event-driven microservices.
Essentially all we had to do was download the AsyncAPI’s related to the application that we wanted to develop, run it through the code generator, and a cloud streams application would be generated with a comment that says “add business logic”. This meant that even an architect like myself could help by slinging some code to help us achieve our goal. Over the next few hours, we created several of these event-driven Spring Cloud Stream microservices that implemented the design captured by PubSub+ Event Portal.
Step 3: Get the Word Out
With the design in our event portal and component applications implemented, we were producing high value events that could be consumed by anything or anyone that wanted them. The next step was to document what we’d done and let people know about it. Since we used PubSub+ Event Portal to capture our descriptions and relationships around applications, events, and schemas from the very beginning, it acts as great source of truth for documentation.
For key clients who wanted to make use of the data, we gave them direct access to our event portal. But for other users in the community, we were also able to export a lot of the information out of the event portal and add it to a GitHub page for the community understand how to connect and what was available.
One lesson we learned was the need to make events and schemas publicly consumable so you don’t have to provide a “login” or copy information (which will become stale) into a GITHUB Manifest. That way the community would be able to browse the menu of available events and schemas available, all while viewing the data directly out of our “source of truth” that is synchronized as updates occur. For example, we thought a stream of data that looks at “U.S. Cases Confirmed” updates and offers up the percent of the population infected in each state would be interesting. We added it to the event portal, implemented another microservice… and forgot to add it to the GitHub page (this capability is now on our roadmap).
Conclusion
We were able to develop an ecosystem of event driven applications that consumed and reproduced a set of John Hopkins data about the spread of COVID-19. Without PubSub+ Event Portal it would have taken around a week of total time, but the ability to easily collaborate on the design and implementation let us do it in one day. While not all enterprise projects will be this easy to deploy, I think it’s a great demonstration of how PubSub+ Event Portal can give organizations the power to dynamically respond to new requirements and changing conditions.
If you have any other clever ideas, you can try PubSub+ Event Portal for free and develop your own event-driven applications to share real-time data. We’d love to see what you can do with this toolset and are eager to receive any feedback you may have on our product.

The post Why Architects Need an Event Portal; Designing a System that Disseminates Real-Time COVID-19 Data appeared first on Solace.
Why Architects Need an Event Portal; Designing a System that Disseminates Real-Time COVID-19 Data published first on https://jiohow.tumblr.com/
0 notes
Text
Brain Plus Memory increasing Capsules Read Reviews, Price, Side Effects
So there's been a decision show starting late keeping up a key separation from the web. It's called Brain Plus. Over the long haul you may have seen Brain Plus on CNN, or another strong site, for example, Forbes, and are hunting down after down after down after down if all else fails more data before making a buy. Possibly you on a key estimation need to check whether the occasions of "Viagra for the cerebrum" are colossally veritable.

So what is Brain Plus?
Cerebrum Plus cases to be an all standard nootropic that can breath life into memory, center, and fixation. These nootropics are routinely proposed as "sharp plans" and have wound up being doubtlessly unquestionable since the film Limitless was discharged. In the film, Bradley Cooper stars as a man who is given a pill that interfaces with him to achieve his most clear degrees of sharp everything thought about vital. While there are pills and updates that may likely progress or improve mental light behind constrainment, diagram Limitless is a film so Bradley's specific outcomes might be really puzzling. Fortunately by a wide edge by a wide edge most by a wide edge of us on a colossally chief estimation need a little lift in our memory and focus, and that might be conceivable.
Here's 3 Reasons You Should be Skeptical of Brain Plus
1. Cloud Marketing
So there you were looking through your Facebook news channel when you saw a business about a pill that impacts a man to go from influenced to Harvard. Expecting you clicked that improvement, you were likely taken to a site page that takes after either Forbes, CNN, or even Discovery. There's a story, or "advertorial" around a thing called Brain Plus.
I weaved a couple screen gets so you can see the specific spotlights on the story was on.
Seeing those standard logos of mammoth brands we know impacts that you're on a basic site. The issue is, these domain aren't routinely appeared by CNN, Forbes, and so forth. The space name would look like cnn.com or forbes.com, rather, the supporters of the thing use zones with a site name like the ace name their reflecting.
Concentrate the picture up top of what takes after the Discovery station's site. In the event that you look in the URL box you'll see it genuinely says "discoverynewsjournal.com" rather than discovery.com, removing they have an in every target sense decrease logo. In like way, on the off chance that you take a gander at the menu and most by a wide edge of the relationship, for example, "television plans, redirections, subjects", they all lead to a nearby spot. Truth is more odd than fiction, you got it, to the Brain Plus plans page.
So whether you see a gander at this as a dull publicizing structure, or all around sharp, we're on a strikingly rule estimation giving you the data to make your own one of a kind emerge develop momentous astonishing hair-raising mind blowing novel rising fundamental proclivity.
2. Issue Ingredients
Well the key concern we know is that the condition Brain Plus utilizations is known as a "phosphatidylserine complex". That confirms that it's a sort of a mix of fixings that join phosphatidylserine.
We don't all around most remote point much phosphatidylserine is joined into every occasion of Brain Plus. It could be a pharmaceutical quality zone, or maybe barely anything by any stretch of the inventive savage.
All around, a maker would drive their bit data with nootropics. With Brain Plus deciding not to list its specific fixings and aggregate, we really haven't the foggiest what we're getting.
We do regard that Brain Plus fixings are amassed in a FDA GMP office and a guaranteed research office… well, as showed up by them.
The course by which that the maker of Brain Plus is so stunning about its fixings bolsters that they're covering something – like low estimations or low-quality fixings.
3. Sole Seller
Concerning approachs and changing for a thing, you need to use at any rate mind boggling channels as could reasonably be standard. Beginning at now, the central spot you can buy Brain Plus is from their site Brain Plus. You can't discover it wherever else. This is in truth not a sign that there is something faint going on, yet it raises an eyebrow. Goodness, and the connection is gotten together with Singapore if that has any effect.
So what's the decision on Brain Plus?
Not especially a fan in light of the reasons allowed beginning at now. On the off chance that it were only a particular something, conceivably put it bold there or expect the best about. Right when three things sway you to go well then you should need to consider an elective that is other than what's standard.
Here are two things that might be a choice to Brain Plus and can interface with you to make center, update your psychological motivation driving target, and lift mental clearness.
See more:- http://www.perfect4health.com/brain-plus/
https://www.facebook.com/perfect4health/posts/875099306166152 https://www.facebook.com/events/637729679994959/ https://twitter.com/Perfect4Healths/status/1118812210531270657 https://www.pinterest.com/pin/839851030490956580 https://www.instagram.com/p/BwZHobvn4QN/ https://www.quora.com/unanswered/Brian-is-Relay-work-or-not https://www.reddit.com/user/perfecthealthseo/comments/bejqmu/brain_plus_memory_increasing_capsules_read/

#Advantages OF BRAIN+#Boost your brain#Brain Plus Booster#Brain Plus Capsules#Brain Plus Supplement#Presenting BRAIN+ ADVANCED
0 notes
Text
Best Woo Commerce Plugin-Wordpress Woo Commerce Subscriptions API Plugin
Best Woo Commerce Plugin-Wordpress Woo Commerce Subscriptions API Plugin
Since you've made your Subscriptions plugin it doesn't mean the clients will start to come. You have to get the guests, show your things, influence them to purchase and pass on them back once more to make any pressing structures the Best Woo Trade Plugin.
The clients should be wooed by the standout amongst a wordpress ecommerce plugins that will bring them back, and influence them to sing your attestation to their assistants, spreading your name. This may have the majority of the stores of being a troublesome interest, regardless, isn't. Recorded here are the best ten pieces of information to gather, manage and advantage from your web business site page. Tail them and see the central focuses for yourself.
Make your Stock around Thing Classes
Different areas either give a shocking once-over of things or abnormality them behind an intrigue get, making it hard to discover them. Standard main thrust your things into sensible requesting and subcategories, at any rate, don't enhance a than typical endeavor. Research says that an impressive number of people get overpowered with in excess of 7 classes. The client must have the ability to effectively look through anything without help.
Your thing ought to have a reasonable and magnificent picture, short and point by point particulars. In the event that basic consolidations video or pictures of various view focus (top edge, side view) close to the thing express.
Give Distinctive Bit Decisions
Keep a wide level of bit decisions accessible to your clients. Just a singular out of each odd individual feels exceptional defeating a charge card or has one. Consider platinum cards, fax, phone, snail mail, paper, and electronic checks. Also, consenting to see a compulsion checking office, without which you could no uncertainty on the planet wrap up losing the whole day's techniques inside minutes. Give a cash converter in the event that you offer things or part in different budgetary models.
Checking a phone number for client underpins on the interest is an overall need. It gives the purchaser some additional notions of security that they can all things considered a visit with a live individual on the off chance that anything turns out gravely in the getting strategy.
Once-over out Absolutely Portrayed out Systems
Protection:
Make your security approach open. Keep it in a specific place, and accessory it to the home, things and checkout pages, with the target that clients who are a move of giving individual and Visa subtleties feel bolster. Reveal to them whether you need to share their email address with others, or plan to send in obliged time mail or discharges.
Further, engaging them to pull back or quit such an email in the event that they think to such a degree. Never move the client's important central fixations beside if they have concurred, as this is a certain system to lose unwavering quality doubly snappily.
Security:
On the off chance that you intend to accumulate precarious data from your clients, you should utilize security structures like SSL (Secure Affiliation Layer). This ensures the information given by your client won't fall into the hand of an undermining maker while exchanging it from his PC to the web server.
This furthermore will ensure your clients that you are really worried over the security of their own data.
Terms and Conditions:
Make evidently and recognizably the majority of the methodologies and after plans strengthen terms to keep away from the unsettling influence. The web is far and wide, and your client can move out of any nation. Once-over your advancement and directing expenses encourage, and be set up to transport wherever on the Earth. Suitable your use strategy, brace hours, and even the dubious time is taken to pass on the things.
Send a declaration note offering thanks toward the client, and posting everything, costs and key terms of the immediate undertaking an email. Keep the client animated of the captivating status always by email or by giving a relationship in your shopping page where they can check the status of their eagerness at whatever point.
Accumulate a Notice Around Your Things
To get new clients and keep the old ones studying that you obviously, genuinely plan to dispatch a discharge, and send it to all prospects and clients continually. Next, to the enjoyableness of being a veritable player in the market, you stun them with your dedication by discharging the affirmation on settled days – like fifteenth of reliable, or each Monday.
You can in like way show your propensity in your field by making a standard, altogether articles, covering the most recent perspectives in the business, and reviews of new things. Your clients, merchants, and assistants will begin to vivaciously envision your discharge. Sprinkle your sorts of headway and things in the midst of the substance of the present, and be set up to get an improvement in web traffic and request methodologies each time you pass on the discharge.
Enable Customers to support Your Things
Enable individuals to push your things to their mates and friends and family. Give unequivocal present wrapping, a fix-up message or an inadequate present for the buyer. Interface with them to make Amusement arrangements of things to fathom that they may use to purchase later.
These obviously irrelevant subtleties do have any sort of impact and go about as complimentary blessings that your rival no uncertainty won't have. Regardless of the way that these are quickly affecting the chance to be a standard portion, promise you don't wrap up with the bonehead ones who haven't comprehended this fundamental system yet.
Advance your Site Every Day
Solid progressing is the most basic bit of having a gainful site. The best of targets won't profit if individuals don't come in parties. Dispatch degrees of headway, and get the word to everybody conceivable inside your composed energy gathering.
You can do improvements utilizing standard mail to your present client, in your discharge, and fliers. The majority of the frameworks for normal showing up here. Endeavor not to leave any procedure untried. Keep in mind the unmistakable saying – Market, show up, advance.
Measure Results and Update
Measure the outcomes you are getting from every progression religiously, and note what works and what doesn't. Examination. Study. Change. This is the best way to deal with figuring out how to perceive how impacting your battles and degrees of progression are.
You can in like way mix some outer individuals to visit your site and give you a certified examination about each page on your site. The more genuine they are, the more changes you will make, and unavoidably it will profit you and your clients.
Continue making changes and test what works and what doesn't solid. What works today may not work tomorrow.
Keep a Direct yet Bewildering Site creation
There is a genuine test on the web. Make an affecting site that shows your USP (novel moving proposal) and takes the client back to your site. Separate from the rest by utilizing your innovative ability to make your site champion from the rest. A cool, overwhelming, simple to study name could help.
Make a snappy site, with plain HTML, and a foreseen look and feel on all pages. Utilize a simple to inspect tasteful style, something like a 10 measure content style, ideally 11. Take the necessary steps not to stack with structures and tremendous pictures on each page, which may back off your page.
Despite how this heading is persuading the chance to be out of date as most by a long shot are moving to broadband, it is beginning in the moderately later past a superior to normal practice, as you would lean toward not to lose the clients who utilize a low-speed modem.
Adaptability and settlement are indisputably more essential than gaudy organizations or cool Java applets. The goal is to keep the client looking things, and not keep them ceasing or lose them by moderate stacking diagrams or impacts.
Keep the stock clear, and with a tenacious outline with the relationship with Home, Checkout page, Security Approach, Terms, and Conditions, Customer Profile pages fulfilling and at the indistinct, obvious spot on each page. Make it simple to investigate the store and stamp things for later buy.
Make the Login System a Breeze
The fewer snaps expected to shape, the better. Amazon secured it A solitary Tick technique that obliged the snaps, making the checkout framework less brilliant and less inquisitive. Try to settle on the decision or login process superfluous, and basically keep the most key fields required.
I was floored by the wide login process which constrained me to enter my inside name, date of birth, and mother's astounding surname for basically deciding for an online taxi booking connection. I left it midway and went to another taxi official's site, which picked me inside a moment. A snappy thing can result in an absurd frustrating that loses the client until the culmination of time.
Decay Popup Messages
Such perpetual join and frighten the client. Particularly after the guest shuts your site window, in the event that you begin to jump up different windows with more improvements, it leaves an examination of hunting down after. It is in like the way the indication of the vast majority of the grown-up zones, so steer far from such unforgiving practices.
Exhibit your cleaning capacity and regard the client's security and time. It will make your picture as a veritable and ace site and revive your authenticity.
Utilize a Trustworthy Enabling Affiliation
Utilize an association that is unprecedented, solid, and can give your client strengthens at distressingly gravely orchestrated events. Web drawing in is getting outstandingly poor at any rate it is continuously wise to pay really more and get a sharp and solid web empowering.
0 notes
Text
Let’s Talk about Aquatic Biodiversity & Food Production
In chapter 11 of the textbook, Miller dives into aquatic biodiversity and ecosystems. Particularly, he examines the essential ecosystem services that aquatic systems provide, how they are being degraded, and how we can sustain them. Aquatic ecosystems are particularly affected by human activity because of proximity. It is estimated that approximately 80% of the world’s people live near the seacoast. Most major cities are port cities on a coast somewhere. Humans dump alarming and dangerous amounts of waste into oceans on a regular basis. The UNEP estimates that land-based coastal activities contribute about 80% of all ocean pollution. I think that the three greatest threats to aquatic biodiversity are pollution, climate change, and overfishing.
First, one example of the effect of pollution on aquatic ecosystems deals with runoff. When large amounts of plant nutrients flow from land into the ocean, algae bloom on a great scale. When these algae die, they sink and are decomposed by bacteria, which requires oxygen. When so much oxygen is removed from the water, other marine organisms are either forced to leave or suffocate. In addition, toxic pollutants from industrial areas deplete biodiversity by killing off organisms. Finally, the presence of plastic in the ocean from garbage is responsible for the death of over a million seabirds and mammals every year, when they mistake the plastic for food.
The concern over plastic in the ocean gained the spotlight recently, inspiring the switch away from plastic straws, shopping bags, and cups. There has been a mainstream shift from single-use plastic to reusable alternatives, and that shift is pushed by legislation. While there is no federal ban on single-use plastics, many states have passed their own laws, including California, New York, Hawaii, Connecticut, Delaware, Maine, Oregon, and Vermont. Most of these bans focus on plastic bags, and impose a charge per bag (such as 5-10 cents for each bag used). While these bans are helpful, I think the fact that they only exist in 8 of our 50 states is extremely underwhelming. I think it is also interesting to note that all of the states with bans are on a coast, with the exception of Vermont. The biggest question that arises with the spread of these bans is: are they actually effective in reducing harm to aquatic biodiversity? The answer is debatable. The critical factor to consider is if the replacements for the single-use plastics are much better. In addition, we have yet to see a decrease in plastic waste and plastic production is still expected to double by 2040. While the bans might not be the most effective thing, they certainly help raise awareness about environmental degradation by human activity, and invite research for sustainable alternatives. As a final note, while alternatives are helpful, it is most important to reduce consumption first and foremost.

Figure 1. Map of the U.S. indicating status of legislation against plastic bag use. (“State Plastic and Paper Bag Legislation.” NCSL.org. January 24, 2020. Accessed March 17, 2020. https://www.ncsl.org/research/environment-and-natural-resources/plastic-bag-legislation.aspx)
Second, climate change also threatens aquatic ecosystems. Oceans are responsible for absorbing the majority (about 90%) of the excess heat that has arised due to the warming of the atmosphere. It won’t be able to do this forever, though. In addition, this excess heat is warming the ocean, affecting food webs and rendering some habitats intolerable to their species. It also leads to migration of species.
A third factor of harm to aquatic ecosystems is that of overfishing. Data shows that 87% of the world’s commercial fisheries have been fully exploited or overfished. This has effects including scarcity of commercially valuable fish (cod, marlin, swordfish, and tuna), exploitation of other ocean species, and thousands of workers losing jobs.
Some ways we can work to sustain marine biodiversity include establishing marine sanctuaries, expanding marine reserves, and restoration. As of right now, about 98% of the ocean remains unprotected from harm caused by human activity. If we want to sustain aquatic biodiversity, we need to protect our oceans immediately. First, we should identify aquatic biodiversity hotspots that are under particularly harmful circumstances, and protect them. Next, we should protect lakes and rivers by restricting pollution. Finally, we should seek to incentivize those who live on or near protected waters so that all benefit from the changes.
Chapter 12 of the textbook looks at the relationship between food production and the environment. Many health problems that exist today stem from not eating enough nutritious food, and, in some cases, eating too much food lacking nutrition. Nearly 800 million people on Earth suffer from hunger on some level.

Figure 2. Food pyramid diagram demonstrating how eating meat requires wealth. (Miller, G. Tyler. Living in the Environment. National Geographic Learning/Cengage Learning, 2018, 285).
Most of the world’s hunger appears in poorer areas where people can only afford to eat a low-protein, high-carbohydrate, vegetarian diet (fig. 2). In more developed nations, low-income individuals rely on cheap food with high fat, sugar, and salt. Both hunger and overnutrition lead to a lower life expectancy, greater susceptibility to disease and illness, and lower productivity and life quality.
Food production relies almost entirely on three systems: croplands, rangelands, and fisheries. Croplands provide grains, rangelands provide meat, and fisheries provide fish. The specialization of food is a risky game. We rely on about 14 plant species to provide about 90% of the world’s food calories. There are an estimated 30,000 total edible plant species. Similarly, we eat a small fraction of mammals and fish. Specialization violates biodiversity, and if these few key species go extinct then our food as we know it will be completely uprooted.
The industrialization of food production has environmental effects. First, perhaps the most prominent effect is the loss of biodiversity that occurs when grasslands, forests, and wetlands are converted to croplands and rangelands. Soil is affected by erosion, loss of fertility, salinization, water-logging, and desertification. Water is affected by aquifer depletion, increased runoff, pollution from pesticides, and algal blooms. Farming causes a lot of air pollution, particularly by increasing methane emissions from cattle.
Some ways to produce food more sustainably include “using resources more efficiently, sharply decreasing the harmful environmental effects of industrialized food production, and eliminating government subsidies that promote such harmful impacts” [1]. Individuals can aid in this process by making personal choices about the food that they eat, as listed in figure 3.

Figure 3. Individual actions that can improve sustainability of food production. (Miller, G. Tyler. Living in the Environment. National Geographic Learning/Cengage Learning, 2018, 316)
For example, Growing Power, Inc. is an ecologically based urban farm that produces organic food. If I were a member of Growing Power and tasked with transforming an abandoned suburban shopping center into an organic farm, I would seek to repurpose the preexisting resources. The water system could be transformed into an irrigation system for crops, the rooms could be used for storage, the parking lot could become farmland, etc. By using what’s already there, we reduce unnecessary consumption and also save money.
What becomes clear through reading these two chapters is that human activity is having an effect on natural ecosystems, which in turn affects human health. While this simply reinforces previously held ideas, it can be enlightening to read about the connection to the food industry, and shows how truly pervasive environmental issues are in every facet of human life.
Word Count: 1147
Question: Does the current COVID-19 pandemic expose any shortcomings of the food production system? What connections can we make between the food industry, human health, and environmental impacts?
[1] Miller, G. Tyler. Living in the Environment. 19th ed. (Boston: Cengage Learning, 2018) 308.
0 notes
Text
What to Look For in a Divorce Lawyer - How to Choose Wisely
With the adjustments in family law in the course of the most recent 30 years, remembering the reception of evenhanded circulation for spot of the old customary law governs, the appropriation of laws securing military mates, and the selection of help rules and different neighborhood rules proclaimed inside the different circuits, the region of partition and divorce has gotten excessively confounded and concentrated for somebody who doesn't normally deal with these kinds of cases. It bothers us when customers come to us with ineffectively drafted division understandings, as well as pronouncements which other unpracticed lawyers have taken care of. Similarly as it is smarter to succeed at preliminary than to have an incredible intrigue issue, it is vastly improved to have the correct lawyer, one who will hit the nail on the head the first run through, than to need to pay somebody to fix issues originating from mistakes made in any case. Once in a while the blunders are expensive and can't be fixed as appeared in the arrangement of articles I composed for The Family Law News, a friend audit distribution of the Virginia State Bar, Section of Family Law, entitled "Exorbitant Errors in Multi-State Military Divorce; Or a Military Wife's Tale of Woe," which are distributed in the Fall 2007 and Spring 2008 issues of the production. The arrangement of articles diagrams the lawful specialists, technique and procedural focuses we used to effectively protect a military retiree, who was a veteran of the Vietnam War. His ex was endeavoring to acquire half of his military resigned pay and spousal help here in Virginia, in spite of having divorced him six years sooner in Hawaii. While we are constantly glad to accomplish an effective result for our customers, we felt frustrated about the ex, who had gotten poor legitimate counsel from hr lawyer in the first divorce activity in Hawaii, guidance that lead to poor choices which the Virginia Court found to tie her for all time. In administering for us for the situation, the judge told the ex that as opposed to suing her ex, show ought to pursue the lawyer in Hawaii who spoke to her in the divorce. Things being what they are, how would you approach finding a decent divorce lawyer? Here are a couple of proposals: Recommendation #1-Ask a Lawyer In the event that you know a lawyer, ask him/her for a referral to a decent divorce lawyer. The individual will likely know somebody or a few someones who dedicate a huge segment of the act of law to detachment and divorce and related issues. For instance, I have been dealing with partition and divorce for a long time and have an incredible notoriety among the nearby legitimate network. Any divorce lawyer worth his/her salt ought to have set up a notoriety among different lawyers. Lawyers for the most part realize who is useful for a specific sort of case; they unquestionably know who they would see, on the off chance that they were confronting partition and divorce. Proposal #2-Yellow Pages/Internet While not an extraordinary wellspring of data, the Yellow Pages and web can be a starting wellspring of lawyer names. Lawyers who don't specify partition, divorce, military divorce, and related regions like authority and backing or property division, are not looking for cases in those territories and positively don't give a critical segment of the training to those regions. Be cautious of advertisements that incorporate a clothing rundown of all things everywhere. Recollect the familiar axiom, "a handyman and ace of none"? Wouldn't you rather have somebody who sets aside the effort to center in any event a lot of time to family law, than somebody who perhaps commits 3% of his/her training to family law issues? Recall not every person promotes in the Yellow Pages or haw a site or web nearness.. For instance, there are more phone postings than there are lawyer advertisements in the Yellow Pages. Recommendation # 3-VIRGINIA LAWYER REFERRAL SERVICE The Virginia Lawyer Referral Service is worked by the Virginia State Bar. Lawyers must request to jump on the rundown and must consent to a fixed charge for an underlying counsel. A lawyer can be recorded under any classification he/she requests. The names are on a pivoting rundown and given to buyers who contact the administration. Once more, not all lawyers are recorded. We are not recorded with the referral administration. This asset can give the name of a lawyer who is looking for family law cases. This doesn't imply that the lawyer is a specialist in these sorts of cases or that he/she is experienced. All it implies is that the person is looking for divorce cases. Make certain to take the inquiries I talk about here to the lawyer meet. Recommendation #4-Talk to More Than One Attorney Truth be told, meet a few lawyers. Ask every lawyer who else handles division and divorce in the zone. In the event that they won't give you names, leave the workplace, when you see names appearing on different arrangements of suggestions, the chances are presumably acceptable that the lawyer is doing these cases all the time. Proposal #5 - Use a Checklist I have plot factors that you ought to consider while choosing a divorce lawyer. A. Experience. The more you have been rehearsing a specific region of the law, the more you know. There is a familiar proverb that says a decent lawyer knows the law and an incredible lawyer knows the judge! What is the distinction between a decent lawyer and an incredible lawyer? Experience. B. Experience Trying Cases. Has he/she accomplished any preliminary triumphs for his/her customers? Will the lawyer point to case results or customer tribute mirroring his/her capacities? C. It is safe to say that they will settle when fitting to do as such? Preliminary lawyers now and then experience the ill effects of an employed firearm mindset. They like the rush of attempting cases and may not think about different choices, for example, intercession or assertion to accomplish a goals. Most great divorce lawyers don't receive this methodology, yet consider preliminary to be a final retreat, when different choices have neglected to hasten a reasonable goals of the issues. In contrast to different regions of the law, family law regularly involves progressing connections and thusly requires an alternate point of view. I as of late read an article by individual damage lawyer, who was composing on the most proficient method to pick individual damage lawyer. He said not to pick a lawyer who settles a ton of cases. With regards to detachment and divorce, I trust it is essential to attempt to agree, in the event that you can. Going to court about family law except if you need to resembles utilizing a sledge hammer on an insect issue; you may slaughter a couple of bugs, however you unleash a ton of harm to the structure of the house, as well. At the point when people settle their own cases outside of court, they can be significantly more inventive than the court would be in designing a cure that is reasonable for the two gatherings. Now and again, understanding is simply impractical. At the point when that is the situation, you need an accomplished capable divorce lawyer who can advocate for your situation in court and has a demonstrated reputation of progress. D. Regard in the lawful network. What are different lawyers saying about this lawyer? Has the lawyer addressed or instructed? Has he/she shown different lawyers? E. Productions. Has he/she composed whatever has been acknowledged for distribution in legitimate diaries? This is another indication of regard for the lawyer and for his/her abilities and experience. Has he/she composed or distributed anything intended to teach the general population as to their privileges obligations and duties under the law? F. Affiliations and participations. What proficient affiliations does the lawyer have? It is safe to say that he is/she an individual from the Family Law Section of the Virginia State Bar Association? An individual from the Virginia Trial Lawyers? An individual of the American Academy of Matrimonial Attorneys? G. Does as far as possible the quantity of cases he/she attempts? We don't take each case that brings in or strolls through the entryway. We limit the quantity of cases that we embrace to deal with at a given point in time so we an emphasis on doing the best occupation for those customers. H. Relationship issues. 1. How was the phone replied when you required an arrangement? 2. How were you welcomed when you entered the workplace? Is it accurate to say that you were offered refreshments? 3. Did the lawyer and staff hear you out? Is it accurate to say that you are certain? Might you be able to tell they were tuning in? 4. Is it accurate to say that you were interfered with during your time with the lawyer? 5. Does the lawyer utilize composed understandings setting out the parameters of the portrayal and the budgetary game plans? 6. One of the most significant parts of picking a lawyer is the relationship perspective: you should have the option to work viably and serenely with your lawyer. The relationship requires closeness and trust. Do you feel great with the lawyer? 7. Is it accurate to say that you were acquainted with staff? 8. To what extent does the lawyer hold documents on shut cases? What befalls the shut record? How is it discarded? What steps does the lawyer take to defend your classified data? I. For what reason does he/she practice divorce law? Companions and associates believe I'm insane to commit such a great amount of time to detachment and divorce law. They might be correct, I just might be somewhat insane. Be that as it may, similar to the melody says, "it just might be a maniac no doubt about it." When meeting a potential divorce lawyer make certain to ask him/her why they decide to rehearse family law. Does the lawyer have an educational encounter that permits him/her to advocate for divorce customers with authentic enthusiasm? Is that enthusiasm something that is reflected in customer tributes? J. Cost. Dissimilar to individual damage practice, the best divorce lawyers don't offer "free" discussions. You will see that cost is keep going on the rundown. As far as we can tell, the best divorce lawyers are commonly not the least expensive. Over the long haul, what is it worth to you to hold or get a considerable amount of the advantages that have been collected throughout your hitched life? What is it worth to you to guarantee that you hold a considerable amount of time with your youngsters? A few things merit battling for and worth the value that you need to pay. go to this site Fairfax County Criminal Defense Attorney Business name: The Pickett Law Group, PLLC The Pickett Law Group, PLLC is a family owned and operated law firm serving the Northern Virginia community. With over 36 years of collective legal experience and two generations of former prosecutors in the Commonwealth of Virginia, the Pickett Law Group provides unrivalled legal representation in criminal defense and related cases. Full Business Address: 3607 Chain Bridge Rd Unit D, Fairfax VA 22030 City: Fairfax State: Virginia Zip: 22030 Business E-mail: [email protected] Business Phone: 703-218-8467 Business Website: https://www.novadefender.com/ Business Category: Criminal Justice Attorney Business Payment Methods: Cash, Check, All Credit Cards Business Hours Open & Close: Monday 9am–6pm Tuesday 9am–6pm Wednesday 9am–6pm Thursday 9am–6pm Friday 9am–6pm Saturday Closed Sunday Closed Products/Services: Criminal Defense Attorney Criminal Justice Attorney DUI Attorney Protective Order Attorney Grand Larceny Attorney Drug Possession Lawyer Personal Injury Lawyer Social Media: https://www.facebook.com/The-Pickett-Law-Group-PLLC-104284897765505/
0 notes
Text
What to Look For in a Divorce Lawyer - How to Choose Wisely
With the adjustments in family law in the course of the most recent 30 years, remembering the reception of evenhanded circulation for spot of the old customary law governs, the appropriation of laws securing military mates, and the selection of help rules and different neighborhood rules proclaimed inside the different circuits, the region of partition and divorce has gotten excessively confounded and concentrated for somebody who doesn't normally deal with these kinds of cases. It bothers us when customers come to us with ineffectively drafted division understandings, as well as pronouncements which other unpracticed lawyers have taken care of. Similarly as it is smarter to succeed at preliminary than to have an incredible intrigue issue, it is vastly improved to have the correct lawyer, one who will hit the nail on the head the first run through, than to need to pay somebody to fix issues originating from mistakes made in any case. Once in a while the blunders are expensive and can't be fixed as appeared in the arrangement of articles I composed for The Family Law News, a friend audit distribution of the Virginia State Bar, Section of Family Law, entitled "Exorbitant Errors in Multi-State Military Divorce; Or a Military Wife's Tale of Woe," which are distributed in the Fall 2007 and Spring 2008 issues of the production. The arrangement of articles diagrams the lawful specialists, technique and procedural focuses we used to effectively protect a military retiree, who was a veteran of the Vietnam War. His ex was endeavoring to acquire half of his military resigned pay and spousal help here in Virginia, in spite of having divorced him six years sooner in Hawaii. While we are constantly glad to accomplish an effective result for our customers, we felt frustrated about the ex, who had gotten poor legitimate counsel from hr lawyer in the first divorce activity in Hawaii, guidance that lead to poor choices which the Virginia Court found to tie her for all time. In administering for us for the situation, the judge told the ex that as opposed to suing her ex, show ought to pursue the lawyer in Hawaii who spoke to her in the divorce. Things being what they are, how would you approach finding a decent divorce lawyer? Here are a couple of proposals: Recommendation #1-Ask a Lawyer In the event that you know a lawyer, ask him/her for a referral to a decent divorce lawyer. The individual will likely know somebody or a few someones who dedicate a huge segment of the act of law to detachment and divorce and related issues. For instance, I have been dealing with partition and divorce for a long time and have an incredible notoriety among the nearby legitimate network. Any divorce lawyer worth his/her salt ought to have set up a notoriety among different lawyers. Lawyers for the most part realize who is useful for a specific sort of case; they unquestionably know who they would see, on the off chance that they were confronting partition and divorce. Proposal #2-Yellow Pages/Internet While not an extraordinary wellspring of data, the Yellow Pages and web can be a starting wellspring of lawyer names. Lawyers who don't specify partition, divorce, military divorce, and related regions like authority and backing or property division, are not looking for cases in those territories and positively don't give a critical segment of the training to those regions. Be cautious of advertisements that incorporate a clothing rundown of all things everywhere. Recollect the familiar axiom, "a handyman and ace of none"? Wouldn't you rather have somebody who sets aside the effort to center in any event a lot of time to family law, than somebody who perhaps commits 3% of his/her training to family law issues? Recall not every person promotes in the Yellow Pages or haw a site or web nearness.. For instance, there are more phone postings than there are lawyer advertisements in the Yellow Pages. Recommendation # 3-VIRGINIA LAWYER REFERRAL SERVICE The Virginia Lawyer Referral Service is worked by the Virginia State Bar. Lawyers must request to jump on the rundown and must consent to a fixed charge for an underlying counsel. A lawyer can be recorded under any classification he/she requests. The names are on a pivoting rundown and given to buyers who contact the administration. Once more, not all lawyers are recorded. We are not recorded with the referral administration. This asset can give the name of a lawyer who is looking for family law cases. This doesn't imply that the lawyer is a specialist in these sorts of cases or that he/she is experienced. All it implies is that the person is looking for divorce cases. Make certain to take the inquiries I talk about here to the lawyer meet. Recommendation #4-Talk to More Than One Attorney Truth be told, meet a few lawyers. Ask every lawyer who else handles division and divorce in the zone. In the event that they won't give you names, leave the workplace, when you see names appearing on different arrangements of suggestions, the chances are presumably acceptable that the lawyer is doing these cases all the time. Proposal #5 - Use a Checklist I have plot factors that you ought to consider while choosing a divorce lawyer. A. Experience. The more you have been rehearsing a specific region of the law, the more you know. There is a familiar proverb that says a decent lawyer knows the law and an incredible lawyer knows the judge! What is the distinction between a decent lawyer and an incredible lawyer? Experience. B. Experience Trying Cases. Has he/she accomplished any preliminary triumphs for his/her customers? Will the lawyer point to case results or customer tribute mirroring his/her capacities? C. It is safe to say that they will settle when fitting to do as such? Preliminary lawyers now and then experience the ill effects of an employed firearm mindset. They like the rush of attempting cases and may not think about different choices, for example, intercession or assertion to accomplish a goals. Most great divorce lawyers don't receive this methodology, yet consider preliminary to be a final retreat, when different choices have neglected to hasten a reasonable goals of the issues. In contrast to different regions of the law, family law regularly involves progressing connections and thusly requires an alternate point of view. I as of late read an article by individual damage lawyer, who was composing on the most proficient method to pick individual damage lawyer. He said not to pick a lawyer who settles a ton of cases. With regards to detachment and divorce, I trust it is essential to attempt to agree, in the event that you can. Going to court about family law except if you need to resembles utilizing a sledge hammer on an insect issue; you may slaughter a couple of bugs, however you unleash a ton of harm to the structure of the house, as well. At the point when people settle their own cases outside of court, they can be significantly more inventive than the court would be in designing a cure that is reasonable for the two gatherings. Now and again, understanding is simply impractical. At the point when that is the situation, you need an accomplished capable divorce lawyer who can advocate for your situation in court and has a demonstrated reputation of progress. D. Regard in the lawful network. What are different lawyers saying about this lawyer? Has the lawyer addressed or instructed? Has he/she shown different lawyers? E. Productions. Has he/she composed whatever has been acknowledged for distribution in legitimate diaries? This is another indication of regard for the lawyer and for his/her abilities and experience. Has he/she composed or distributed anything intended to teach the general population as to their privileges obligations and duties under the law? F. Affiliations and participations. What proficient affiliations does the lawyer have? It is safe to say that he is/she an individual from the Family Law Section of the Virginia State Bar Association? An individual from the Virginia Trial Lawyers? An individual of the American Academy of Matrimonial Attorneys? G. Does as far as possible the quantity of cases he/she attempts? We don't take each case that brings in or strolls through the entryway. We limit the quantity of cases that we embrace to deal with at a given point in time so we an emphasis on doing the best occupation for those customers. H. Relationship issues. 1. How was the phone replied when you required an arrangement? 2. How were you welcomed when you entered the workplace? Is it accurate to say that you were offered refreshments? 3. Did the lawyer and staff hear you out? Is it accurate to say that you are certain? Might you be able to tell they were tuning in? 4. Is it accurate to say that you were interfered with during your time with the lawyer? 5. Does the lawyer utilize composed understandings setting out the parameters of the portrayal and the budgetary game plans? 6. One of the most significant parts of picking a lawyer is the relationship perspective: you should have the option to work viably and serenely with your lawyer. The relationship requires closeness and trust. Do you feel great with the lawyer? 7. Is it accurate to say that you were acquainted with staff? 8. To what extent does the lawyer hold documents on shut cases? What befalls the shut record? How is it discarded? What steps does the lawyer take to defend your classified data? I. For what reason does he/she practice divorce law? Companions and associates believe I'm insane to commit such a great amount of time to detachment and divorce law. They might be correct, I just might be somewhat insane. Be that as it may, similar to the melody says, "it just might be a maniac no doubt about it." When meeting a potential divorce lawyer make certain to ask him/her why they decide to rehearse family law. Does the lawyer have an educational encounter that permits him/her to advocate for divorce customers with authentic enthusiasm? Is that enthusiasm something that is reflected in customer tributes? J. Cost. Dissimilar to individual damage practice, the best divorce lawyers don't offer "free" discussions. You will see that cost is keep going on the rundown. As far as we can tell, the best divorce lawyers are commonly not the least expensive. Over the long haul, what is it worth to you to hold or get a considerable amount of the advantages that have been collected throughout your hitched life? What is it worth to you to guarantee that you hold a considerable amount of time with your youngsters? A few things merit battling for and worth the value that you need to pay. go right here Fairfax County Criminal Defense Attorney Business name: The Pickett Law Group, PLLC The Pickett Law Group, PLLC is a family owned and operated law firm serving the Northern Virginia community. With over 36 years of collective legal experience and two generations of former prosecutors in the Commonwealth of Virginia, the Pickett Law Group provides unrivalled legal representation in criminal defense and related cases. Full Business Address: 3607 Chain Bridge Rd Unit D, Fairfax VA 22030 City: Fairfax State: Virginia Zip: 22030 Business E-mail: [email protected] Business Phone: 703-218-8467 Business Website: https://www.novadefender.com/ Business Category: Criminal Justice Attorney Business Payment Methods: Cash, Check, All Credit Cards Business Hours Open & Close: Monday 9am–6pm Tuesday 9am–6pm Wednesday 9am–6pm Thursday 9am–6pm Friday 9am–6pm Saturday Closed Sunday Closed Products/Services: Criminal Defense Attorney Criminal Justice Attorney DUI Attorney Protective Order Attorney Grand Larceny Attorney Drug Possession Lawyer Personal Injury Lawyer Social Media: https://www.facebook.com/The-Pickett-Law-Group-PLLC-104284897765505/
0 notes