#an id will be updated as soon as we have the ability to describe the images!!!
Explore tagged Tumblr posts
Text

hi-hi!! we're the picnic party! a ployfrag collective that's alterhuman heavy. this is our safe space for us to share our experiences with (specifically) therianthropy, and all other identities that are animal centered.
100% sfw. pls dni if you are and/or if your blog contains: nsfw, anti-nontraumagenetic systems, transmed, radfem, and right-winged.

small individual intros:
alleh ~ he/it ~ 16 yrs ~ angel-deerkin
bealise ~ it/it's ~ 21 yrs ~ cat-fairykin
bovinè ~ she/plush/plushself ~ 18 yrs ~ strawberry cow fictive
caspian ~ he/they ~ 5 yrs ~ cinnamoroll fictive
chamomile tea ~ he/him ~ 20 ~ fluttershy fictive
chiro ~ he/they ~ 8 - 14 yrs ~ mouse regressor
maikin ~ she/it/they ~ 23 yrs ~ rabbit-fairykin
mochi ~ he/they/she ~ 3 - 6 yrs ~ monkeykin
pudding ~ she/her ~ 6 yrs ~ puppykin
vanilla ~ they/it ~ 10 yrs ~ chinchillakin
( this isn't all of us therian/pet regressors, just the ones who wanted to be listed here! )


♡ our main: @faunabells ♡ audhd & madd ♡ last updated: dec 3, 2023 ♡


#therian#therianthropy#alterhuman#pet regression#sfw petre#endo safe#an id will be updated as soon as we have the ability to describe the images!!!
2 notes
·
View notes
Photo

Hi everyone! It has been well over a month into Stellirae's launch, and we'd like to thank you all for the overwhelming support and interest in the group. Because Stellirae has grown much larger than we'd ever anticipated, we're still in the process of fine-tuning things accordingly. We've made some recent adjustments to our systems, summarized below.
ACTIVITY CHECK
Most importantly, our first activity check will begin on the 20th, next week. We’ve made a few adjustments to our activity check, mainly for important distinctions when it comes to those exempt from activity requirements:
Those that were applied within 3 weeks before activity check ( which, for this upcoming activity check, is any characters applied from May 31st to June 19th ) must still submit an activity check form, even though they are exempt from the activity check interaction requirements. Failing to submit an activity check form on these characters will cause them to fail the check. Again, don’t worry about making the interaction requirements on these characters - they are only required to submit the form to keep their place in the group. This is to help cut down on inactive characters.
Characters applied during activity check or on hiatus during activity check don’t need to submit a form, and automatically pass. If possible, submitting a form during this time is appreciated for the sake of recordkeeping, but isn’t mandatory for these characters. For the sake of convenience, we will only be holding ONE app run during the week of the activity check, on WEDNESDAY.
All characters applied before the 3 weeks ( for the upcoming check, before May 31st ) must pass the interaction requirements ( as seen on the Rules document ) and submit an activity check form.
We ask that if you don’t feel like keeping a character, that you drop them before the activity check instead of just letting them be taken out by it, to help ease the processing load that comes during activity checks.
During the activity check, we will be sending periodic reminders ( during the beginning, middle, and end of the activity check ) that it is occurring. We recommend you send the form at your earliest convenience rather than putting it off so you don’t forget. The activity check will last a week, beginning on SATURDAY, 12 AM EST and ending on FRIDAY, 11:59 PM EST.
SPECIAL UPGRADE UPDATES
We've updated the special upgrades document to clarify that it is possible to "combine" special upgrades with other special upgrades and abilities, so as long as the combined ability can't do anything the base abilities couldn't do. ( For example, someone combining STAGE 1 FIRE MANIPULATION with STAGE 1 HEALING could make their fire heal small injuries, but not larger injuries – which is gated behind STAGE 2 HEALING. )
Additionally, special upgrades that one has obtained can be swapped out for other special upgrades of the same stages later on. ( For example, if someone has MENTALITY STAGES 1 and 2, but decides later on they’d rather have NATURE, they can send in the new special upgrade swap form to have NATURE STAGES 1 and 2 instead ).
REPUTATION SYSTEM CHANGES
We've adjusted the reputation sheet so that for PLANETARY RACES, reputation is influenced and applies to ALL ASPIRANTS regardless of division placement. REPRESENTATIVES on the station will still hold different reputation standings with different divisions. Individual aspirants/characters can still possibly have their own individual reputation for a specific race due to their actions.
RANK-UP FORM ADJUSTMENTS
For ease of processing, if what your character is requesting isn't obvious ( such as the character describing the item or power using a different name or phrase from what's on their app ), please note the actual name of it in OOC notes. We also request that players label if something their character is requesting back is an item or a power. Our rank up form has been amended to reflect this.
HIATUS RULES ADJUSTMENTS
We've adjusted our hiatus rules a bit. A two week hiatus is now officially referred to as a *semi-hiatus,* while a four week hiatus is simply a *hiatus.* A semi-hiatus can be upgraded to a full hiatus as needed. If necessary, a hiatus can be extended to be eight weeks total—just talk to us and we can get that sorted. Keeping in mind that we'll be having our first activity check soon, be aware that we will not be accepting hiatus requests during activity checks.
ONGOING EXPEDITIONS
We’ve introduced new, ongoing expeditions. These expeditions can be repeated, though they’ll have a cooldown between repeats, and won’t be swapped out of the expedition rotation.
ADDITIONAL ANNOUNCEMENTS
We would like to remind everyone to make sure their provided contacts are actually contactable. We've been consistently receiving quite a few contacts whose DMs were closed, making it difficult for inbox moderators to contact people as needed. Our rules have been amended to emphasize as such.
We would also like to ask that nicknames in the official Stellirae server use plaintext, as using alternate characters and fancy text makes it difficult for both us doing processing (as their name won’t come up when we go to @ them). Emojis and other symbols can still be used.
For example, going to ping “Pikachu” will work, but if their name is set as “𝓟𝓲𝓴𝓪𝓬𝓱𝓾”, Discord will be unable to find the person nicknamed Pikachu, making it harder to give them joules, as we’ll have to look for their Discord ID.
In addition to this, Discord IDs themselves must be entirely in plaintext ( with the caveat that they don’t have to be the character’s name ).
We want to be clear that none of the changes and clarifications above were made in response to any specific incidences, but that we feel we hadn't been as clear as we could've ( or overlooked ) with our guidelines initially. As always, should you have any questions concerning these updates or otherwise, feel free to reach out for a moderator in #questions!
1 note
·
View note
Text
What Software Do You Need to Set Up an Efficient Call Center?
Customer assistance is an essential part of the consumer experience as it assists services quickly resolve customers’ troubles. But below’s the concern: What approach of client support should you utilize, Email, Live chat, Chatbot, Another thing.
Although we remain in the digital age, a study by international consultancy Deloitte exposes that the majority of people still prefer being assisted by phone. Setting up a telephone call center, consequently, offers you a competitive advantage and assists you deliver an excellent customer experience. But what type of software program do you need for a phone call center? There are great deals of solutions on the marketplace, so making the appropriate choice is testing. Continue reading to learn more about phone call facility software application and what functionality it provides.
Types call facility software
Prior to selecting software application for your call center, choose what sort of phone call center you require: incoming, outbound, or mixed. Consumer support agents typically deal with inbound phone calls, though they may require to call customers too (to follow up on instances, for example). Generally, call facility software sustains both incoming and also outgoing calls.
Next off, you should pick the type of call center software you need. Without going too deep right into information, call facility software application is broken down right into 2 classifications based on where it’s hosted: on-site or in the cloud. According to a survey by the Call Facility Network Group, 77.5% of phone call centers still use locally installed software, although cloud-based services are coming to be significantly prominent.
Allow’s quickly discuss these 2 kinds of call center software.
On-site:
On-site (likewise called on-premise) telephone call facility software application is released in your own data facility. Your workers are accountable for setting up, preserving, and also updating both software and hardware. As necessary, this needs considerable ahead of time financial investment.
Cloud-based:
Cloud-based call software application is hosted in the cloud, which means that a third-party service provider supervises of all hardware and software. As the client, you simply visit and also utilize this software application using an internet browser. Customarily for online software, cloud-based call facility software is given as Software program as a Service (you can learn more about cloud solutions in this short article).
Take a look at the advantages these two kinds of telephone call facility software offer:
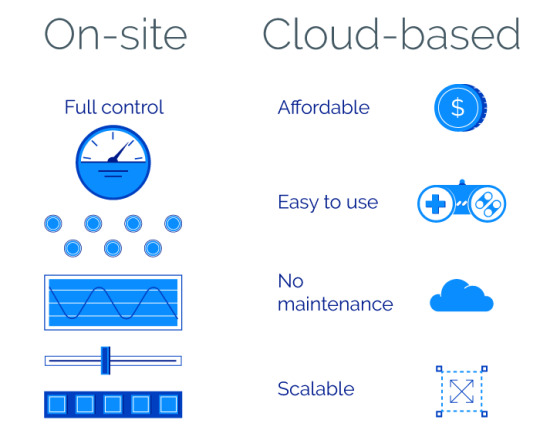
Credit to RubyGarage
Contact center for domestic calling:
You better understand the principle of residential phone call facilities and then exactly how it aids you enhance your consumer support high quality as well as boost sales. It essentially describes a call center infrastructure which frequently beings in your country to manage your office works like consumer support, financing, personnels and so forth.
cloud call center for International calling:
Nowadays, when setting up a cloud phone call center is simple like never previously, do not allow your places prevent your course of progression & success. We function efficiently with cloud telephone call facilities for ultimate adaptability to improve your organisation. These cloud call facilities can be accessed essentially from anywhere, so attach your service globally and also offer best-in-class client assistance services to globally clients with our budget-friendly cloud call centers for worldwide calls.
Essential functionality for call center software application
As soon as you’ve decided on the kind of software program for your telephone call center, you ought to meticulously determine the performance you need. Modern call center software application (specifically cloud-based software application) offers a lot of various functions that help businesses construct client assistance facilities.
There are some significant attributes, however, that any kind of call center software ought to have in order to be reliable and also convenient in day to day use.
Handling Calls
Software application for telephone call facilities have to give adequate telephone call handling capabilities. To start with, it should be versatile in its assistance for telephone number. A lot of cloud-based call facility software program providers enable you to either incorporate your existing telephone number or select one or several virtual telephone number. Second, even if you need a telephone call facility mainly for taking care of incoming phone calls, you must still be able to make outbound calls, so the software you select must also sustain this.
Let’s highlight some other important features that your telephone call facility software program must offer:
Call control so that your call center agents can hold, mute, ahead, and end phone calls
Call recording to guarantee the top quality of your representatives’ job
Blacklisting to obstruct spam as well as crawlers
Call line monitoring so you can establish a line while customers await a representative
Automatic ticket production to make certain all concerns raised by customers are resolved by your call center group.
Routing:
Having representatives operating at your phone call facility is excellent, but it’s vital to guide callers to the right agents that can resolve their troubles. Therefore, make sure that your telephone call center software application gives directing abilities that will boost the consumer experience and streamline your phone call facility’s workflow. Below’s a checklist of attributes you should pay attention to:
Interactive voice response (IVR), which immediately transmits customers to the right representative or division; normally an IVR system resolves voice input or keypad choices
Forward-to-phone, which enables your telephone call center representatives to respond to phone calls even when they aren’t in the workplace
Queue callback, which allows callers to request a callback as opposed to waiting in a queue
Service hrs management to notify callers about the availability of your telephone call facility team
Contact management
We’ve already pointed out that organisations require telephone call centers to give assistance to their customers. That’s why software for phone call facilities need to come with powerful call monitoring functionality. Representatives should have the ability to access comprehensive information regarding clients and also their interactions with your business in order to give top-quality customer service.
What minimum set of get in touch with management features does any type of call facility software application need? Right here are the most essential:
CRM integration so you can integrate your CRM with your phone call facility software application
Interaction background so you can keep an eye on all cases when customers call your telephone call center to better understand your clients as well as resolve their problems promptly
Customer ID so your agents can see in-depth info concerning each caller as well as supply customized assistance
Surveillance as well as efficiency
No company can be successful without reporting and analytics. Call facility software application ought to give you with detailed performance-related info so that you can check whether your phone call center is working appropriately and also your agents are doing their work well. Without tracking as well as reporting, consumer support can become totally inefficient. What features should your telephone call facility software program have to maintain you educated about the facility’s performance:
Call monitoring enables you to quietly listen to both inbound and also outgoing telephone calls. This aids you inspect exactly how well your call center agents are doing.
Performance checking supplies you with general efficiency analytics such as call tons and also variety of missed calls.
Agent ranking allows you evaluate the efficiency of each call facility representative. As an example, it’s important to understand the speed of answering calls in addition to the average duration of discussions with clients.
Feedback surveillance assists you easily receive responses on the efficiency of your telephone call center so that you know whether callers are satisfied.
#callcenter#cloud call#call center solution#call center software#call center services#call center support
1 note
·
View note
Text
Help CenterCommunityCreator Tips
YouTube
Fix a problem
Watch videos
Manage your account & settings
Supervised experience on YouTube
Join & manage YouTube Premium
Create & grow your channel
Monetize with the YouTube Partner Program
Policy, safety, & copyright
Sound Recording Shares for Music Labels
The features described in this article are available only to partners who use YouTube's Content ID matching system.
Sound Recording Shares give you more visibility and more granular control over how your rights and data are represented on Content ID Sound Recording assets.
On Sound Recording assets, you’ll now see a “Sound Recording Share” asset created for each unique ISRC (International Standard Recording Code) you deliver to YouTube. Optionally, the same ISRC can also be represented on more than one of your Sound Recording Shares, if delivered with a distinct custom ID.
Unlike a Sound Recording asset, a Sound Recording Share represents only the metadata, ownership, and policy information provided by a single owner. Only you can see and edit your own Sound Recording Shares.
The breakout by ISRC helps you preserve previously delivered metadata versions during asset update or merge. Sound Recording Shares may also allow easier reporting to the appropriate record label or artist in cases where similar, but different audio references are deemed duplicate for Content ID and contained on the same Sound Recording asset.
FAQs
Where can I find my Sound Recording Share assets; what do they look like?
On Sound Recording assets, you’ll see a Sound Recording tab. Under the Your Shares section, you’ll see all Sound Recording Shares with your ownership.
Clicking on a Sound Recording Share title opens the details page. Each Sound Recording Share has its own unique asset ID and two tabs: Metadata and Ownership & Policy. The Metadata and Ownership & Policy tabs are the same as what you see today on a Sound Recording asset, but only show your provided metadata, ownership, and policy for that individual Sound Recording Share.
You can edit information by clicking the Edit pencil , or click Compare metadata to view metadata deliveries for that individual Sound Recording Share.
Keep in mind that when viewing the metadata comparison for a Share created before February 2019, you may see more than one ISRC in the metadata comparison. We only consider the latest delivered ISRC on a Sound Recording Share as the official ISRC for that Share.
Is Custom ID required for Sound Recording Shares?
Custom ID is not a required field. Custom ID and ISRC delivered together form a unique “key” to create a Sound Recording Share; however, custom ID is entirely optional. If you want to create two or more Sound Recording Shares with the same ISRC, custom ID must be used to differentiate.
Can Sound Recording Shares be deleted?
There is no official way to delete information from a Sound Recording Share. However, because we only consider the latest added metadata, ownership, and policy on a Sound Recording Share, the best way to make sure you’re displaying the correct information for a Sound Recording Share is to edit it, by clicking the Edit pencil  in Content Manager or delivering an update.
We’ll soon also add the ability to merge your own Sound Recording Shares together to “delete” extra, unwanted Shares.
What Sound Recording Share ownership and policy apply for an associated Sound Recording asset?
At this time, we’re only considering the ownership and policy from your latest delivered or latest updated Sound Recording Share as your ownership and policy for a Sound Recording asset.
In the future, we aim to expand this logic to take a union of ownership across all of your own Sound Recording Shares on a Sound Recording asset to preserve the most comprehensive ownership and most restrictive policy across your delivered ISRCs, even in cases of asset merge.
How should I address ownership conflicts for Sound Recording Shares?
Sound Recording Shares do not have ownership conflicts, since each Sound Recording Share has only one owner.
Ownership conflicts remain at the Sound Recording asset level, according to the aggregate ownership from all asset owners, based on each owner’s latest delivered or latest updated Sound Recording Share for a given Sound Recording asset. Learn more.
Ownership conflicts can be viewed on both the Ownership & Policy and Sound Recording tabs.
Do Sound Recording Shares have references or impact claims?
Sound Recording Shares are not tied to references and do not impact claims.
You may see that Sound Recording Shares are created during the delivery of new references, but references and claims remain associated with the Sound Recording asset.
Do Sound Recording Shares impact how I send updates to Sound Recordings with Content Delivery?
Sound Recording Shares should not impact how you deliver updates with Content Delivery.
When you deliver an update to a Sound Recording asset:
If the ISRC you provided does not exist as the latest delivered ISRC for one of your Sound Recording Shares, a new Sound Recording Share will be created.
If the ISRC you provided does exist as the latest delivered ISRC for one of your Sound Recording Shares, the Sound Recording Share will be updated.
If the ISRC you provided exists as the latest delivered ISRC for more than one of your Sound Recording Shares, and no custom ID is provided to differentiate, your earliest created Share with that ISRC will be updated.
What if I don’t deliver ISRCs for my Sound Recording Assets?
ISRCs should be provided whenever possible, as these identifiers are the industry standard for audio recordings; however, if you do not have an ISRC for a recording, it is still possible to deliver with custom ID or Sound Recording asset ID. A Sound Recording Share will be created for your initial delivery to a Sound Recording asset, but data may be overwritten with subsequent updates to the asset where ISRC is not provided.
How can I search for a specific Sound Recording Share?
Sound Recording Shares cannot be searched by Sound Recording Share ID in the Assets list; however, you can search for the Sound Recording asset ID that contains a Sound Recording Share asset. Alternatively, you can search by your latest provided ISRC for a given Sound Recording Share.
Do Sound Recording Shares appear in YouTube Analytics?
Information about Sound Recording Shares doesn’t appear in YouTube Analytics. You can search in YouTube Analytics by Sound Recording asset ID. To see a breakout of your data by Sound Recording Share, you can use the Sound Recording Share downloadable report.
How do Sound Recording Shares appear in downloadable reports?
You can view all Sound Recording Shares and associated metadata in a NEW Asset Share report in the Reports > Asset section of your Content Manager.
Sound Recording Shares do not explicitly appear in any other metadata or financial downloadable reports. For all other reports, the most recent version of metadata you provided, or the display metadata if you didn't provide metadata, is the metadata version that shows.
However, because the Asset Share report shows more granular data of each Sound Recording Share ID and the associated Sound Recording asset ID, information can be compared against other reports to help provide a clearer picture of record label or artist by ISRC.
For example, if you delivered a remastered version of a song with an ISRC that merged onto the same Sound Recording asset as the original version with its own unique ISRC, the Asset Share report can show you separate Sound Recording Shares for the original and remastered versions, both relating to the same Sound Recording asset ID. If these versions are owned by different record labels, you may wish to compare against financial reports to provide information about Content ID performance to both labels.
Give feedback about this article
Was this helpful?
YesNo
Advanced topics for music partners
Content ID for music partners
Deliver music content
Using the YouTube DDEX feed
New publishing data model: publishers
Manage art tracks
Publishing ownership: standardizing videos with multiple musical works
Music in this video
YouTube for Artists
Sound Recording Shares for Music Labels
Manage your sound recording metadata
What is the Mechanical Licensing Collective (MLC)?
©2022 Google
Privacy Policy
YouTube Terms of Service
catalàdanskDeutscheestiEnglish (United Kingdom)españolespañol (Latinoamérica)FilipinofrançaishrvatskiIndonesiaitalianolatviešulietuviųmagyarNederlandsnorskpolskiportuguêsportuguês (Brasil)românăslovenčinaslovenščinasuomisvenskaTiếng ViệtTürkçeíslenskačeštinaΕλληνικάбългарскирусскийсрпскиукраїнськаעבריתاردوالعربيةहिन्दीবাংলাไทย中文(简体)中文(繁體)日本語한국어 English
English
Send feedback on...
This help content & informationGeneral Help Center experience
Troubleshoot problems playing videosTroubleshoot account issuesFix upload problemsFix YouTube Premium membership issuesGet help with the YouTube Partner Program
Find videos to watchChange video settingsWatch videos on different devicesComment, subscribe, & connect with creatorsSave or share videos & playlistsTroubleshoot problems playing videosPurchase and watch movies and TV shows
Sign up and manage your accountManage account settingsManage privacy settingsManage accessibility settingsTroubleshoot account issues
Learn about YouTube Premium benefitsManage Premium membershipManage Premium billingGet a YouTube Premium family planSign up for a student Premium membershipFix YouTube Premium membership issuesTroubleshoot billing & charge issuesRequest a refund for YouTube paid productsYouTube Premium Updates & Promotions
Upload videosEdit videos & video settingsCreate ShortsCustomize & manage your channelAnalyze performance with analyticsTranslate videos, subtitles, & captionsManage your community & commentsLive stream on YouTube
YouTube Partner ProgramMake money on YouTubeGet paidUnderstand ads and related policiesGet help with the YouTube Partner ProgramYouTube for Content Managers
YouTube policiesReporting and enforcementPrivacy and safety centerCopyright and rights management
0 notes
Text
Vaccine Passports: 'Scarlet Letter' Or Just The Ticket?
It's happening millions of times a day. Pharmacists jab an arm with the COVID-19 vaccine and hand over a paper card certifying that the shot was administered, and when. หวย บอล เกมส์ คาสิโนออนไลน์
"This is your ticket to freedom soon," smiles pharmacist intern Ojashwi Giri, as she hand-writes the name and birth date of another newly vaccinated customer on one of the coveted cards at Union Pharmacy in Newton, Mass. "I'm sure you're going to want to treasure this."
It's the low-tech version of the "vaccine passports" that have become the latest pandemic wedge issue. As states and businesses are debating and using them, Americans are deeply divided on whether businesses should require them to prove a person is immunized before boarding a plane, or entering a bar or a baseball game. What some see as a commonsense safety measure, others denounce as a violation of privacy and civil liberties.
GOATS AND SODA
The Vaccine Passport Debate Actually Began In 1897 Over A Plague Vaccine
To many, it's no-brainer — a ticket back to normal life. Linda Simansky clutched her vaccination card, and beamed at the prospect of being able to venture out again with greater confidence. She says she's all for the idea of vaccine passports, and would definitely be more likely to patronize places that ask for them at the door, ensuring everyone else inside is also low-risk.
"I know its awkward," she says, "but they're not asking for [anyone's] life story, they're just trying to keep people safe, and trying to also keep their business. So, I think it's a win-win."
Article continues after sponsor message
"If we're going to end this nightmare, what we need is information," agrees Peter Wilson, a musician from Pheonix. "Some people pose less risk than others [...] and if people are making unsafe choices, the rest of us deserve to know. There's no sense in blindfolding ourselves."
Wilson sees it as no different than requiring students to get vaccines in order to attend school or camp. "We're just extending that to adults to keep everyone safe."
That's the idea behind New York state's "Excelsior Pass" that allows residents to flash a code from their phones which would earn them entry into anything from a Broadway show to a gym or even a private wedding. The nation's first such state-wide system, the Excelsior Pass has already been used at Madison Square Garden, Yankee stadium as well as smaller venues around the state, and while privacy features make it hard to pinpoint, state officials say hundreds of thousands of New Yorkers downloaded or at least started checking out the system in the two weeks since it launched.
CORONAVIRUS UPDATES
Florida Gov. DeSantis Rejects Vaccine Passports As 'Completely Unacceptable'
Judy Lisi, president and CEO of the Straz Center for the Performing Arts in Tampa, says a tool like that would be "essential" to reopening mass gathering venues like theaters that depend on a full house to survive.
"Why do you think these seats are so close to each other together behind me?" she says, pointing to the empty 2,640 theater seats on the image she uses as her Zoom backdrop. "Theaters [need] to put as many people in a space [as possible, in order to] pay for what's on stage."
Lisi says she was in the process of drawing up plans to use vaccine passports to screen patrons, when Florida Gov. Ron DeSantis preemptively banned businesses from requiring them.
"He's a pro-business proponent," Lisi says. "Why doesn't he allow businesses to do what we need to do then? The whole industry is relying on this. It's so frustrating."
But DeSantis and Texas Gov. Greg Abbot, who's also banned vaccine passports, as well as others argue they're a violation of privacy and civil liberties.
"It's completely unacceptable for either the government or the private sector to impose upon you the requirement that you show proof of vaccine to just simply be able to participate in normal society," DeSantis said.
Audra Young, from Haverill, Mass., who says she's not vaccinating because she doesn't trust it, agrees the passports are a bad idea.
"Just like it's your choice to own a gun, I mean, this is America, where we should have choice to pick what we want to do with our life," Young says. Vaccine passports "feel like it's going to be like a restricted society. It's like wearing the scarlet letter. It's crazy."
While much of the opposition to vaccine passports comes from those on the right who see it as a kind of Orwellian nightmare, there is concern on the left as well.
Judy Greenberg, of San Antonio, describes herself as "very liberal." She says she got the vaccine and hopes everyone else will too, but she's uncomfortable making people prove it for the privilege of dining out, for example.
"Being Jewish, I've always had this apprehension about [anyone saying] 'Show us your papers!'" Greenberg says, because it harkens back to the horrors Jews experienced in Nazi Germany. She's quick to acknowledge a vaccine passport is hardly the same thing, but she worries it would be prone to abuse. "It'll create two classes of human beings, almost like a caste system of vaccinated and unvaccinated. So then, what's next? It just makes me a little bit uneasy."
John Calvin Byrd III, has similar qualms. The self-described "far-left militant black man" lives in Los Angeles, and says he cringes at the thought of being seen as sharing the same concerns as "Trumpers," but he believes vaccine passports would impinge on his civil liberties. He says he and his family are not vaccinating, because they don't trust how fast the COVID-19 vaccines were rushed through the emergency authorization process, and because he doesn't trust Big Pharma.
THE CORONAVIRUS CRISIS
FAQ: What Is A Vaccine 'Passport,' And What Are These Credentials Used For?
But he thinks it's unfair to penalize people like him, by restricting his ability to go out for dinner, travel, or visit a park, museum, or grocery store.
"It's not like we committed a crime," he says. "We should be able to go and play and do whatever we want." He's also feeling pressure from his boss to vaccinate, and fears his decision not to, may cost him his job.
More broadly, Byrd worries that vaccine passports will exacerbate inequities for Black and Brown people, who are still less likely to be vaccinated — either by choice or because of lack of access.
"It puts people into separate groups, and one group has privileges and the other group does not [...] That keeps myself, my family and people like us in the margins," Byrd says.
Another concern is privacy. New York State Assembly member Ron Kim, says his state's "Excelsior Pass" is especially troublesome, given that it was developed in collaboration with a corporate giant, IBM.
"We're already dealing with big tech companies like Facebook and Google exploiting and extracting data without regular people even knowing that it's happening every day," Kim says. "Now we're allowing another path for companies to extract data and profit without our knowledge."
Both IBM and New York state officials, however, insist no personal data can be accessed or used for any such purpose. And no individual information is stored, or tracked. They say the Excelsior Pass only reads data that states already collect, to offer users the QR code that bouncers can scan to get a quick, clear green checkmark or a red "X." The same code can also indicate whether a user has recently tested negative for COVID-19, which many establishments screening customers may accept in lieu of a vaccination. For those without smart phones, results can be accessed on a computer and printed out instead.
Contrary to what many may think, given all the controversy, no state is mandating use of a vaccine passport; the Biden administration is also against any federal mandate, though officials say they're helping to develop guidance on privacy and equity issues. States can and do require large venues to screen customers for the coronavirus, but whether to do that with vaccine passports is still up to individual establishments.
SHOTS - HEALTH NEWS
Coronavirus Cases Are Rising Again. See How Your State Is Doing
Some venues see the apps as an easier, more reliable way to verify that patrons are low-risk for spreading the coronavirus. Digital apps may well be more difficult to hack than vaccination cards are to forge, and they'd likely be more effective and efficient than what many are doing now, which is taking everyone's temperature and reviewing health surveys that patrons answer on the honor system.
But other businesses, especially in the hospitality industry, are proceeding with caution. A "no shirt, no vaccine, no service" policy may come across as inhospitable, many say, and may turn of customers who restaurants need now more than ever. Also, many bars and restaurants are loath to take on the burden of vaccine enforcement, on top of what they already do, checking ID's to make sure everyone's legal to drink, and constantly policing customers who may have had too much to drink.
That said, establishments that are still struggling to survive a year into the pandemic are not ruling it out. Doug Bacon, president of Red Paint Hospitality Group, owns eight bars and restaurants in Boston; four remain closed, and four are open, but still unable to make money because of pandemic restrictions limiting capacity. If requiring vaccine passports would mean he could fully reopen, he says, "I might have to give in to that. "
Bacon says he's more open to requiring vaccine passport checks for staff. In the past year, all four of his open places had to shut down for a week or more, because an employee tested positive.
"We had to sanitize the whole restaurant and have everyone tested," he says. "Perishable food had to be thrown away, and I had no income, and I paid my staff and all my suppliers and my landlords while were closed, so it's been a tremendous additional financial burden on top of everything else."
Ultimately, some are hoping vaccine passports, will prove one last bitter pill to swallow to help hasten a return to normal. It may be the carrot that induces more people to vaccinate. Or, as with so much else that's been politicized during this pandemic, it may be seen as more of a stick, that only deepens divisions, stokes resentment and leads those who've been vaccine-hesitant to dig in their heels even more.
"This is just one more thing to throw in the mix that's going to divide our country even more," Young says.
0 notes
Text
GameStop Hedge Fund Stock Market Fiasco Explained by the Internet
https://ift.tt/eA8V8J
You’ve probably heard by now that the poor hedge funds are in trouble. Perhaps you’re even watching YouTube videos titled “Everything You Need to Know About the Stock Market in 5 Minutes” in order to cash in on some GME stock. If so, good luck doing so on the popular Robinhood app, which has halted the ability for amateur investors to buy up those sweet GameStop shares (as well as Nokia, AMC, and Blackberry) in what some are calling an attempt to save beloved hedge funds like Melvin Capital (they were so screwed 24 hours ago).
It seems to be mostly working too, as panicked investors are rushing to sell back their shares to prevent a loss as the prices drop. Today, GME shares went from $347.51 to $132 in just a matter of hours (although the price seems to be going up again as some investors move to other apps like Fidelity). But none of this has made this drama any less juicy.
This all started when subreddit r/wallstreetbets, a collective of amateur investors, whose financial strategy ranges from well-reasoned due diligence to, quite literally, risky “YOLO” investments, rallied its more than 4 million members to begin buying up cheap GameStop shares in order to raise the price at an exponential rate. This put multi-billion dollar finance bro outfit Melvin Capital in deep shit, since they’d borrowed and sold those same exact GameStop shares for much less and would soon have to buy them back and return them to the broker. Meaning that, under current stock market regulation, Melvin would have to pay the massively inflated price of those GameStop shares in order to get them back from those pesky amateur investors.
Obviously, this is not what Melvin Bros. Inc. had planned when it bet against GameStop and borrowed those GME shares. In a scheme known as a “short squeeze,” Melvin Boat Shoes Corp. had originally borrowed those shares and sold them in the hopes that they’d drop below the price they’d paid for them before buying them back and returning the shares to the broker, pocketing the difference and turning a profit in the process. But when the Redditors started buying up GME stock, causing the share price to skyrocket, Melvin & Broke Sons were suddenly facing a HUGE loss.
Reddit explains in more detail for the common folk here:
Thank you to whoever explained this – @reddit is incredible 😩🤙🏻 pic.twitter.com/zKRlbP41gJ
— Jimmy Kelly (@_jimmykelly) January 28, 2021
Now, I’m not going to pretend I understand how the stock market or money works, especially when this fiasco just makes it seem like money is make believe anyway, and the above explanation is definitely oversimplified. If you want get to get into the nitty-gritty, I’d suggest giving this New York Times explainer a read or this Bloomberg article a look.
What I do know is that every person who can be described as “extremely online” now cares about the stock market and is learning how to buy and sell shares. Who can blame them for wanting what executives at hedge funds have, or at least for them to fail?
But others are worried about The People finally learning how to invest in stock. Even The White House is now monitoring this GameStop situation. How will this all eventually end? It’s difficult at the moment to see how the Redditors and other amateur investors will win.
Already, Discord has closed the r/wallstreetbets server in order to cut off their communications, and Robinhood is seemingly trying to get people to sell sell sell. GameStop share prices are currently so erratic, rising and falling within seconds, that it’ll likely scare more people into selling their shares, even as r/wallstreetbets is trying to get people to hold the line for that big payday.
But will Melvin Capital really have to pay all of that money back? The Securities and Exchange Commission (SEC), the government body charged with enforcing stock market and banking regulations, is also monitoring the situation, and some experts expect the SEC to launch a formal probe into this mess in due time.
Yet, for the few of us on the internet who have no stake in this race, it’s just been a lovely couple of days of pure chaos on Twitter, as we watch the memes and jokes roll in. If the hedge funds do eventually win this financial battle, at least we’ll always have Twitter to commemorate this very important David and Goliath moment:
pic.twitter.com/reQN1hYWNh
— 🎃⚰️Gleb Melnikov, CEO of Halloween⚰️🎃 (@GlebMelnikov8) January 28, 2021
Pandemic Day 25: I made bread 🙂 Day 95: I sure do miss my friends …. Day 310: The White House appears to be under the control of a shirtless man in a Viking helmet Day 330: Reddit’s coordinated attack on Wall Street is going as planned
— Bird Facts (@SupramanTrax) January 27, 2021
Wall Street right now pic.twitter.com/LmmrQdc7jI
— Paul Lawson (@PaulLaw10) January 27, 2021
cnx.cmd.push(function() { cnx({ playerId: "106e33c0-3911-473c-b599-b1426db57530", }).render("0270c398a82f44f49c23c16122516796"); });
I love the stock market because when it goes up we get nothing but when it goes down we all lose our jobs. Except during a pandemic when it goes up and we still lose our jobs
— Shoegaze Dad (@yeoldedad) January 27, 2021
a normal person explains what’s happening on the stock market: pic.twitter.com/zKKvULCirX
— Avalon Penrose (@avalonpenrose) January 27, 2021
the GameStop thing and resulting chaos signals our culture’s shift from Jokerficiation to Bane-ifying.
— john (@johnsemley3000) January 27, 2021
pic.twitter.com/yoUsv9qrQy
— Some people call me…jim (@jim_dandeneau) January 28, 2021
Hedge fund CEO: I lost $3 billion, my company, my home, and now my wife Me: Have you considered budgeting?
— Ken Klippenstein (@kenklippenstein) January 28, 2021
pic.twitter.com/NrfV0WCpCL
— Wall Street Wrecker (@WreckWallStreet) January 28, 2021
Dude, nobody understands the stock market. The last president thought it was the same as the economy.
— Kyle D Anderson (@KyleDAnderson) January 27, 2021
pic.twitter.com/edQAEEiFHA
— Bobby Lewis (@revrrlewis) January 27, 2021
I’ll probably read up on the stock market a bit more before bringing you any more updates.
Subscribe to Den of Geek magazine for FREE right here!
(function() { var qs,js,q,s,d=document, gi=d.getElementById, ce=d.createElement, gt=d.getElementsByTagName, id="typef_orm", b="https://embed.typeform.com/"; if(!gi.call(d,id)) { js=ce.call(d,"script"); js.id=id; js.src=b+"embed.js"; q=gt.call(d,"script")[0]; q.parentNode.insertBefore(js,q) } })()
The post GameStop Hedge Fund Stock Market Fiasco Explained by the Internet appeared first on Den of Geek.
from Den of Geek https://ift.tt/3ckU0yA
0 notes
Text
What Software Do You Need to Set Up an Efficient Call Center?
Customer assistance is an essential part of the consumer experience as it assists services quickly resolve customers’ troubles. But below’s the concern: What approach of client support should you utilize, Email, Live chat, Chatbot, Another thing.
Although we remain in the digital age, a study by international consultancy Deloitte exposes that the majority of people still prefer being assisted by phone. Setting up a telephone call center, consequently, offers you a competitive advantage and assists you deliver an excellent customer experience. But what type of software program do you need for a phone call center? There are great deals of solutions on the marketplace, so making the appropriate choice is testing. Continue reading to learn more about phone call facility software application and what functionality it provides.
Types call facility software
Prior to selecting software application for your call center, choose what sort of phone call center you require: incoming, outbound, or mixed. Consumer support agents typically deal with inbound phone calls, though they may require to call customers too (to follow up on instances, for example). Generally, call facility software sustains both incoming and also outgoing calls.
Next off, you should pick the type of call center software you need. Without going too deep right into information, call facility software application is broken down right into 2 classifications based on where it’s hosted: on-site or in the cloud. According to a survey by the Call Facility Network Group, 77.5% of phone call centers still use locally installed software, although cloud-based services are coming to be significantly prominent.
Allow’s quickly discuss these 2 kinds of call center software.
On-site:
On-site (likewise called on-premise) telephone call facility software application is released in your own data facility. Your workers are accountable for setting up, preserving, and also updating both software and hardware. As necessary, this needs considerable ahead of time financial investment.
Cloud-based:
Cloud-based call software application is hosted in the cloud, which means that a third-party service provider supervises of all hardware and software. As the client, you simply visit and also utilize this software application using an internet browser. Customarily for online software, cloud-based call facility software is given as Software program as a Service (you can learn more about cloud solutions in this short article).
Take a look at the advantages these two kinds of telephone call facility software offer:
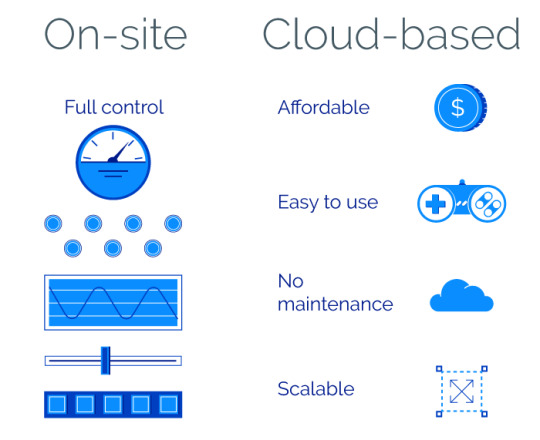
Credit to RubyGarage
Contact center for domestic calling:
You better understand the principle of residential phone call facilities and then exactly how it aids you enhance your consumer support high quality as well as boost sales. It essentially describes a call center infrastructure which frequently beings in your country to manage your office works like consumer support, financing, personnels and so forth.
cloud call center for International calling:
Nowadays, when setting up a cloud phone call center is simple like never previously, do not allow your places prevent your course of progression & success. We function efficiently with cloud telephone call facilities for ultimate adaptability to improve your organisation. These cloud call facilities can be accessed essentially from anywhere, so attach your service globally and also offer best-in-class client assistance services to globally clients with our budget-friendly cloud call centers for worldwide calls.
Essential functionality for call center software application
As soon as you’ve decided on the kind of software program for your telephone call center, you ought to meticulously determine the performance you need. Modern call center software application (specifically cloud-based software application) offers a lot of various functions that help businesses construct client assistance facilities.
There are some significant attributes, however, that any kind of call center software ought to have in order to be reliable and also convenient in day to day use.
Handling Calls
Software application for telephone call facilities have to give adequate telephone call handling capabilities. To start with, it should be versatile in its assistance for telephone number. A lot of cloud-based call facility software program providers enable you to either incorporate your existing telephone number or select one or several virtual telephone number. Second, even if you need a telephone call facility mainly for taking care of incoming phone calls, you must still be able to make outbound calls, so the software you select must also sustain this.
Let’s highlight some other important features that your telephone call facility software program must offer:
Call control so that your call center agents can hold, mute, ahead, and end phone calls
Call recording to guarantee the top quality of your representatives’ job
Blacklisting to obstruct spam as well as crawlers
Call line monitoring so you can establish a line while customers await a representative
Automatic ticket production to make certain all concerns raised by customers are resolved by your call center group.
Routing:
Having representatives operating at your phone call facility is excellent, but it’s vital to guide callers to the right agents that can resolve their troubles. Therefore, make sure that your telephone call center software application gives directing abilities that will boost the consumer experience and streamline your phone call facility’s workflow. Below’s a checklist of attributes you should pay attention to:
Interactive voice response (IVR), which immediately transmits customers to the right representative or division; normally an IVR system resolves voice input or keypad choices
Forward-to-phone, which enables your telephone call center representatives to respond to phone calls even when they aren’t in the workplace
Queue callback, which allows callers to request a callback as opposed to waiting in a queue
Service hrs management to notify callers about the availability of your telephone call facility team
Contact management
We’ve already pointed out that organisations require telephone call centers to give assistance to their customers. That’s why software for phone call facilities need to come with powerful call monitoring functionality. Representatives should have the ability to access comprehensive information regarding clients and also their interactions with your business in order to give top-quality customer service.
What minimum set of get in touch with management features does any type of call facility software application need? Right here are the most essential:
CRM integration so you can integrate your CRM with your phone call facility software application
Interaction background so you can keep an eye on all cases when customers call your telephone call center to better understand your clients as well as resolve their problems promptly
Customer ID so your agents can see in-depth info concerning each caller as well as supply customized assistance
Surveillance as well as efficiency
No company can be successful without reporting and analytics. Call facility software application ought to give you with detailed performance-related info so that you can check whether your phone call center is working appropriately and also your agents are doing their work well. Without tracking as well as reporting, consumer support can become totally inefficient. What features should your telephone call facility software program have to maintain you educated about the facility’s performance:
Call monitoring enables you to quietly listen to both inbound and also outgoing telephone calls. This aids you inspect exactly how well your call center agents are doing.
Performance checking supplies you with general efficiency analytics such as call tons and also variety of missed calls.
Agent ranking allows you evaluate the efficiency of each call facility representative. As an example, it’s important to understand the speed of answering calls in addition to the average duration of discussions with clients.
Feedback surveillance assists you easily receive responses on the efficiency of your telephone call center so that you know whether callers are satisfied.
0 notes
Text
Cutie Reviews: NMNL Sept 19
Just a tiny update, I got my issue resolved on TokyoCatch. Apparently there’s an issue where you need to make sure your shipping info is entirely filled out, as soon as I checked that and modified it, it was fixed!
Anyway, I only won the 1 item so far, so I’m trying to decide if I want to just include a pic of it in a future review, or gather several items and then do like a... partial-review on them and the game/website.

“We hope you had a fantastic summer! This month’s beauty box has a floral theme. We hope you’ll feel like a blossoming beauty with the adorable makeup and skin care products coming in September’s box!“
(is it me or is the info kind of lackluster this month?)
Contest

This month, the prize items are a collab between Pokemon and the brand It’s Demo. Besides a makeup palette, winners could also receive eyeliner, and lipstick.
Glam Gift

For this month, the official GG winner received some special, limited edition Sanrio products featuring My Melody and Little Twin Stars. The items range from cosmetics to accessories like a hand mirror and an adorable, My Melody doll brush (which looks so cute~).
In going with our floral theme, this months Horoscope is “Which Flower matches your Star Sign?“, and this is what it says:
Aries: Honeysuckle
Taurus: Poppy
Gemini: Lavender
Cancer: White Rose
Leo: Sunflower
Virgo: Buttercup
Libra: Rose
Scorpio: Geranium
Sagittarius: Carnation
Capricorn: Pansy
Aquarius: Orchid
Pisces: Water Lily
Which one did you guys get? :3 is it a flower you like? I was very happy to have gotten Rose, because those are my favorite flowers~
We also have a page describing some flower ingredients one should try using for various reasons. Make sure to try out some natural items featuring them if any of these apply to you:
Cherry Blossoms - the extract lightens hyperpigmentation and increases skin elasticity, soothes irritated skin, and protects it from damage and signs of aging.
Camellia - Camellia oil hydrates and smooths the skin, protecting it from damages and signs of aging.
Roses - Intensely hydrate the skin, so its recommended for “mature skin“. The extract also minimizes scars, stretch marks, and wrinkles.
Chamomile - High antioxidant and moisturizing properties, especially useful against things like acne or dry skin.
Marigold - also good for acne and skin irritations like eczema and rosacea. Prevents premature aging and skin damage.
♥ ♥ ♥ ♥ ♥ ♥
Green Tea Nose Pack

Our first item is this simple little nose cleaning pack from Etude House. It is filled with green tea extract that helps tighten the pores, while the patch removes dead skin and blackheads. It’s very easy to use, all you do is make your nose wet (or the patch too) and then smooth it on your nose. After 10-15 minutes you remove it, then you use some cleanser or toner, or just water if you don’t have any.
I’m not going to lie, I was dreading this item <_< Anytime I’ve seen people use nose patches or skin patches that adhere/suction to the skin, it HURTS to pull off. I’m a big wuss so I was innocent assuming this would be the same thing. Plus I don’t like green tea, and I was worried it wouldn’t even work.
BOY WAS I WRONG!
Not only does it smell amazing (it was like a... light floralish scent, but weirdly enough the pack smells like green tea), but it didn’t hurt to take off at all, and it actually helped! My nose is blackhead free and feels very smooth, I love it! My nose has felt so smooth and soft since~
I plan on buying a handful more for when I need them off of Tokyo Haul, the store website for the makers of the subscription box (they only cost about $1). I would seriously recommend these if you have a “strawberry nose” of your own.
Fleurissant Lip Glow & Rosy Lips

For this month we get 2 lovely and fun Lip products; first up is the Fleurissant Lip Glow by Glamfox. These are pretty much those really pretty jelly lipsticks/gloss with a flower in them, and they have the ability to change in shade depending on how much you apply or your current body temperature to give you natural, but noticeable color and shimmer.
In the box there was 6 possible flowers and a couple different box designs. According to my tube, I got GL04 Rose Flower.
- - - - - - -
Our next item is this adorable little rose tinted lip cream by The YEON. I was really excited to get this because I’ve seen them before on Youtube (usually for slime making) and I thought it looked cute. The color I got was S102 Rose Petal, but there are 3 colors in total we could have gotten.

(The darker product is the rose btw)
As you can see, the jelly flower product is fairly sheer but very shimmery. As I said above, you can apply it a little more -or allow your temperature to handle it- and it will darken over time. I already own a couple of these and I really like them because it gives your lips a really subtle change and kind of gives them a “healthier“ glow.
Usually these are scented (my original one smells like peach) but this one... it has a scent, but it isn’t fruity, so I’m not sure what it’s supposed to be. I still like it though, these jelly lip products are usually always good and this isn’t an exception, I’d recommend it if you never tried one before.
- - - - - -
Meanwhile, the rose is way more vibrant. As you can see in the pic, it looks red, but on the skin it’s more of a... magenta, red raspberry hue. It also has a very faint rose scent.
It’s a creamy and smooth feeling product, it doesn’t feel oily or heavy on the lips. I don’t like vibrant or dark colors on my lips because I feel like they don’t look good on me, but I did like this color, and in certain conditions (maybe spring or summer?) I feel like it could look nice. Right now I think it just highlights how pale I am.
Both of them are really nice, and it wasn’t really hard to remove them for items meant to tint the skin. My only concern is that where I used the product on my hand and wiped it off... the skin is red and blotchy looking now. So I don’t know if I had some kind of reaction (but my lips are fine) or if the skin is really dried from how much I was rubbing it.
Spring Eyelash Curler

I’ve been needing a new eyelash curler but nothing I’ve tried to replace my original pair (a hot pink one) with has come close to feeling comfortable for me, so I kept using them. I know in most cases you could say they’re all the same, but to me it didn’t feel that way. These are by the brand NOYL, and as you can see in the package there is a replacement curling piece for one the first one gets too old and hard to clean.
I know I’ve said this before, but my most favorite color is pastel/pale/baby/light pink. So seeing these in the box gave me a really good feeling, even the little clasp on them is translucent pink~
I really like these, they feel a lot like my old pair and even without any product they managed to curl my lashes so that they looked more neat, controlled. They’re not loose feeling, and the handles are curved to contour the fingers, so it feels comfortable to hold too.
Therapy Air Mask & 10 Second Morning Sheets

Our next Etude House product is a therapy air mask, a facial mask that is extremely thin and loose to fit any face shape. These are available in 4 different scents/types: Cherry Blossom (firming and brightening), Camellia (lifting and skin radiance), Damask Rose (fresh moisture), and White Flowers (moisturizing and brightening). These are also hypoallergenic, so they’re good if you have sensitivity to certain ingredients.
This smells amazingly good, the scent is a fairly light cherry blossom/sakura with a perfumey note. I really like it, I have to find something with the same scent so that I can keep it forever.
In terms of a facial mask, I’d say this was a really good one. It was super-wet and a bit sticky, and because of how thin it was it was kind of a pain to open and put on- but it was really nice once applied. My face had a wonderful cooling effect from it (especially my lip when it accidentally got some product on it). My face also feels really nice after using it.
I might have to pick up a couple of these from Japan Haul too~
- - - - - - - - -
This item is by Joteki and it is called a 10-second sheet because it saves you several “morning routine“ steps, as they are made to clean, cleanse, and moisturize your skin. Besides letting you take your morning get-ready session easier, it would also come in handy if you’re going on a trip or if you want to keep it in your purse or car because you can leave out other items, such as creams, cleansers, moisturizes.
There are 2 different sets in the box, the one I got specifically says its for oily skin. I’m not sure what the other one is, maybe dry? You get about a months worth, and they come in a really fun, colorful re-sealable package.
I have a dry skin problem so I always worry that oily skin products will dry my skin <3< but so far I haven’t had that problem. These have a scent but I can’t exactly pin-point what it is, because it doesn’t smell fruity, herbal, or flowery. Weirdly enough, the scent reminds me of liquid medicine, like the kind you might take for bad cough or to help you sleep? I like it though, whatever it is.
Anyway, I ended up trying one of these out the other morning after a shower and my face felt really nice and smooth~ I did wash my face prior to using it, so I tried again the next morning with nothing on my face and got the same result. I’m not sure if physically anything changed, but my skin feels a lot nicer.
Mascara & Mascara Top Coat

You know, I didn’t realize there was such a thing as a mascara top coat. At least I don’t believe so... apparently its just used to help seal the applied mascara to keep it on your eyelashes longer, or you can use it on its own to give your lashes a natural cute look without the mascara.
Meanwhile, this specific mascara came in a few varieties; volume, length, and point (for outer lashes). Mine says I got the volume type. It has a faint un-identifyable scent, but the top coat is a lot stronger and the smell reminds me of paint, kinda.
I’m not sure how I feel about the mascara. It has a very curvy spooly/wand and I’m not used to that. But generally it did its job and they’re darker then what they were and more... spread out and spidery. I don’t hate it but my eye feels sticky when I blink or shut it, which has never been a problem before with other mascaras. I also poked myself in the eye trying to remove the reside beneath it when I tried wiping it off, which btw did NOT come off...
Meanwhile, the top coat is really nice. It helps to keep the natural color while adding some shine and the “effect” of applied mascara, but the lashes aren’t stiff, spidery, or sticky. I would recommend this on its own or with mascara, I could see it being useful for those who aren’t familiar with mascara (or are too young for it) too.
♥ Cutie Ranking ♥
Content - 4.5 out of 5. I liked everything with the exception of the mascara. But not because of its quality or anything, just because it frustrated me >3< everything is really nice and felt good when I used it, I’d recommend each one. Everything was in perfect condition, most of the items are re-usable and cute.
Theme: 5 out of 5. Obviously this gives me a spring vibe, not an Autumn/Fall one, which kind of bothers me. But at the same time it makes it more interesting so I don’t frown upon that. I love flowers and a lot of natural products use them, and this box was definitely giving me flowery vibes.
Total Rank: 10 out of 10. Like August’s box this one only focused on the face, which isn’t bad because most beauty products and cosmetics are for the face- but at the same time it’s a little typical/boring. I prefer when we get mixed items (like face, nails, feet, skin, hair, etc) or a mixed theme (like one month its hair-based, one month face, one month skin). I especially wish we got more hair products because I really liked getting those from the older boxes. But the box has the cute factor I craved and the items are really fun and good quality!
♥ Cutie Scale ♥
Nose Pack - I did not expect to love this as much as I did. But it smelled great and it worked pain-free :D seriously, get this one!
Face Mask - It smells so good! I wish we got a couple of them~
Morning Sheets - If you use a lot of products in the morning I would recommend buying one of these and trying it out instead. My face has been feeling really nice since I’ve been using them these past few days
Eyelash Curler - I can get rid of my old one for sure now I think. I love it.
Mascara Top Coat - I feel like this is something you shouldn’t be smelling, but besides that I like it. I usually prefer mascara that I can visibly see, but on its own I think it’s really sweet and it definitely gave the eye softness.
Rosy Lips - It feels nice on my lips but I don’t see myself wearing this very often. Quality wise its there, but the color doesn’t look right on me.
Lip Glow - It’s very pretty and I love the packaging, but I already have one of these I like a lot more because its cute and smells yummy.
Mascara - I’ve had better, and I prefer a straight wand.
0 notes
Text
Would You Play WIth Friends at Pokémon Sword and Shield game?

The newest Pokémon matches, Pokémon Sword and Shield, have finally arrived Switch. As soon as it's mostly a single-player adventure, here's everything you need to learn about playing with friends.
Regrettably, there's no solution to play the main game of Pokémon Sword and Shield with a friend. Even though Pokémon let us Go let a neighborhood co-op player to decline and explore the world with you, Pokémon Sword and Shield is not any similar alternative. The main bulk of this game is quite a lot of experience.
Nevertheless: there are portions of the game that could be played others. You can engage in battles within the'compared to' menu, complete Dynamax struggles with friends, and commerce together with other people.
N the'Vs' menu, there are two selections: Battle Stadium and reside Contest. Fight Stadium is online, and unfortunately there's no way to select who you struggle against: you're randomly matched against another player. But reside Contest makes it possible for you to host and join competitions, developing a set of rules in order to battle together with buddies. You're going to want a electronic ID in order to combine a contest. The complimentary approach Pokémon Sword and Shield Mobile Download have actually helped make video gaming an extremely prominent hobby.
As for Dynamax conflicts: you'll Get these while researching the Wild Spots of Pokémon Sword and Shield. They've been displayed with a glowing column coming out of the floor. Interact with one, and you are going to be provided a menu display that makes it possible for you to invite good friends, uncover players online, or play independently (encouraged by CPU personalities ).
The last way that you can play Pokémon Sword and Shield with close friends is via dealing. By the game, press on'Y' to access the trading (or'Y-Comm' menu). As a way to trade with a good friend, you should gain access to the'url Trade' choice, and after that set a Link Code. You'll need to give this code to some good friend and, after they've inputted it, then you're going to have the ability to relate to eachother to exchange Pokémon.
Pokémon Sword and Shield Might Be Performed With PokemonGo
Pokémon Sword and Shield will be the very first main entrances within the show to take creation for Nintendo Change, but out some limited information, we do not know a lot about them. As stated by some newly discovered advice, but there is the possibility the 2 games will likely soon be compatible with all Pokemon-Go.
The most recent update released for Niantic's cellular game added a series towards the game's code, even"koala_settings", which will not appear to perform a lot in the present time, because it pertains to a program different from the game.
This koala may really be described as a reference to Pokémon Sword and Shield, as sport Freak generally names chief entries within the show since animals.
Contemplating how successful the mobile game is ongoing to be, it wouldn't be shocking to see some form of features between Pokémon Sword and Shield and Pokémon GO.
Nintendo and Niantic have not said anything about the matter, however, a statement is likely coming during the E3.
Pokémon Sword and Shield launching after this calendar year only on Nintendo Switch.
#Pokémon Sword and Shield Mobile#Pokémon Sword and Shield Mobile Download#Pokémon Sword and Shield Download iOS#Pokémon Sword and Shield Download Android
0 notes
Text
50 Sql Query Questions You Must Exercise For Interview
You can select unique documents from a table by using the DISTINCT keyword phrase. Trigger in SQL is are a unique type of kept treatments that are defined to carry out automatically in place or after information alterations. It permits you to perform a set of code when an insert, update or any other question is performed against a details table. DECREASE command removes a table as well as it can not be rolled back from the data source whereas TRUNCATE command removes all the rows from the table. https://tinyurl.com/c7k3vf9t does not permit the field to have replicate worths if the column is distinct indexed. Toughness implies that when a deal has been committed, it will certainly remain so, even in the event of power loss, collisions, or mistakes. In a relational data source, as an example, as soon as a team of SQL declarations execute, the outcomes require to be kept completely. The SELECT declaration is utilized as a partial DML statement, made use of to pick all or appropriate documents in the table. Denormalization is used to access the data from greater or reduced regular form of database. It likewise processes redundancy right into a table by integrating data from the associated tables. Denormalization includes needed repetitive term right into the tables so that we can stay clear of utilizing complicated joins and several various other complicated operations. t mean that normalization will certainly not be done, but the denormalization procedure occurs after the normalization process. Think of a solitary column in a table that is populated with either a single number (0-9) or a solitary character (a-z, A-Z). Create a SQL query to print 'Fizz' for a numeric worth or 'Buzz' for indexed value for all values in that column. Ultimately utilize the DEALLOCATE statement to delete the cursor meaning and also release the connected sources. Gathering index can enhance the efficiency of the majority of query procedures due to the fact that they supply a linear-access path to information saved in the data source.

DeNormalization is a method made use of to access the data from higher to decrease regular types of database. It is additionally procedure of presenting redundancy into a table by including data from the relevant tables. Normalization is the process of lessening redundancy and dependence by organizing areas and table of a data source. The main goal of Normalization is to add, erase or customize field that can be made in a solitary table. APrimary keyis a column or a collection of columns that distinctly recognizes each row in the table. The information saved in the database can be changed, retrieved as well as deleted and can be of any kind of kind like strings, numbers, images and so on. A CTE or usual table expression is an expression which has short-term outcome collection which is specified in a SQL statement. By utilizing DISTINCT key phrase duplicating records in a query can be prevented. When kept in a data source, varchar2 utilizes only the allocated room. https://is.gd/snW9y3 .g. if you have a varchar2 and put 50 bytes in the table, it will utilize 52 bytes. Stored Treatment is a feature includes several SQL declaration to access the data source system. Several SQL statements are consolidated right into a kept procedure as well as execute them whenever and wherever needed. SQL stands for Structured Question Language is a domain name specific programming language for handling the data in Database Administration Equipment. SQL programs abilities are highly desirable and needed out there, as there is a enormous use Database Management Solution in practically every software application. To get a task, candidates require to fracture the meeting in which they are asked different SQL interview concerns. A Stored Treatment is a function which includes several SQL declarations to access the data source system. https://bit.ly/3tmWIsh are combined into a kept treatment and also execute them whenever as well as any place required which conserves time and also avoid writing code over and over. If a main trick is defined, a unique index can be used immediately. An index refers to a efficiency tuning technique of allowing quicker access of records from the table. An index develops an entrance for each worth as well as hence it will be much faster to obtain information. Denormalization describes a strategy which is made use of to accessibility information from greater to reduce forms of a database. It aids the database managers to increase the performance of the entire infrastructure as it introduces redundancy right into a table. It adds the repetitive information into a table by incorporating data source queries that incorporate information from various tables right into a single table. https://geekinterview.net is a code written in order to get the details back from the database. Question can be made as if it matched with our expectation of the outcome set. Distinct index can be used automatically when main secret is defined. An index is efficiency tuning approach of enabling faster access of records from the table. An index develops an entry for each worth as well as it will be much faster to retrieve data. To prevent power loss, transactions need to be recorded in a non-volatile memory. Write a query to fetch values in table test_a that are and not in test_b without using the NOT keyword phrase. A self JOIN is a case of normal sign up with where a table is joined to itself based upon some relationship between its very own column. Self-join utilizes the INNER SIGN UP WITH or LEFT JOIN clause as well as a table alias is utilized to assign different names to the table within the question. In this guide you will discover a collection of real life SQL interview inquiries asked in business like Google, Oracle, Amazon.com and Microsoft and so on. Each concern includes a perfectly composed response inline, conserving your meeting preparation time. TRUNCATE gets rid of all the rows from the table, as well as it can not be curtailed. An Index is an special framework connected with a table quicken the performance of inquiries. Index can be produced on one or more columns of a table. A table can have only one PRIMARY KEY whereas there can be any type of number of UNIQUE keys. Primary trick can not consist of Null values whereas One-of-a-kind secret can have Null worths. MINUS - returns all distinctive rows selected by the first query but not by the 2nd. UNION - returns all distinctive rows picked by either query UNION ALL - returns all rows chosen by either question, including all matches. DROP command removes a table from the database and procedure can not be rolled back. MINUS driver is made use of to return rows from the very first question but not from the second question. Matching records of very first and also 2nd inquiry and various other rows from the very first inquiry will certainly be shown as a result collection. Cross sign up with specifies as Cartesian item where variety of rows in the initial table increased by variety of rows in the second table. If intend, WHERE stipulation is used in cross sign up with then the inquiry will certainly work like an INNER SIGN UP WITH. A nonclustered index does not modify the way it was saved but produces a complete different item within the table. It aim back to the initial table rows after searching. Thinking about the data source schema displayed in the SQLServer-style representation listed below, compose a SQL question to return a listing of all the billings. For every billing, show the Billing ID, the invoicing day, the customer's name, as well as the name of the customer who referred that customer. DECLARE a cursor after any type of variable statement. The arrow affirmation should always be connected with a SELECT Declaration. The OPEN statement must be called before fetching rows from the result collection. BRING declaration to recover and transfer to the following row in the result collection. Call the CLOSE statement to shut off the arrow.
0 notes
Text
My professional experience at Methods and designing a web application
Trust me, just explaining this is not easy.
“How exciting!” That is what I thought as I started my new role at Methods company as a ServiceNow Developer. Having been specialising in the field of ServiceNow development for 3 years in three different companies before joining Methods helped me feel confident about approaching the upcoming responsibilities of the new role without feeling much intimidation by the uncertainty of how capable I can be as a developer in this company. I find out later, however, that there were some ServiceNow skills I have been lacking which I thankfully get to master down the line.
First impression:
Before joining Methods, and after a very long phone interview with my manager Matt. I was wondering if the technical experiences and challenges I went through and discussed over the phone were of the competence that he was looking for. However, I found out later that they liked me and was given an opportunity to join this well-established company.
Fitting in:
I joined the team as a ServiceNow developer. The team involved senior developers who had years of long professional experience in ServiceNow. Despite this, I never felt like I don’t fit in. I was warmly welcomed into the team and had so much support from them.
I realised how fortunate I am to work along with my senior colleagues, as I was able to extend my development skills so much further than it was. I am also glad they never get fed up of my continuous never-ending questions.
Challenges:
Our team applies agile scrum practices as a development methodology, which is very efficient for rapid improvement of solving technical problems. Additionally, the ServiceNow platform that our work relies on is built upon the principles of ITIL (IT Infrastructure Library). So in ITIL terms I would be described as a process practitioner within the team.
Being a process practitioner / developer, I get new stories (tasks) assigned to me in every new sprint. Our sprint lasts two weeks. At the start of a sprint we hold a meeting where I get the chance to discuss new stories, ask for clarifications on customer requirements and give my opinion or approval of how many points should be allocated to a story, i.e. the number of hours or estimation of the amount of effort required.
At the end of the sprint, I get a chance to demonstrate my development work to my team. In this demo I make sure that the test lead individual understands my work and has enough information on how to perform a test on my development. He basically attempts to find a flaw in my development, so it could be debugged if found. I always get feedback from my senior colleagues, as to whether there are better alternative approaches to solving a technical issue, or if I am on the right track.
Those were some of the main activities and responsibilities that I carry out within my role, but those are not really big challenges as I am used to performing these tasks. The actual challenges are figuring out the most suitable approach to performing tasks and solving problems.
If I talk about challenges, I remember one of the most challenging tasks that was assigned to me. It was called: ‘License Harvesting Solution’.
The big challenge:
One of the major tasks I got to work on was to build a scoped application on ServiceNow platform called: ‘License Harvesting Application’. The purpose of this application was to detect outdated licenses and removing them from the system, with the ability to retrieve the licenses if required.
The task had dozens of additional core requirements, such as:
· Defining a notice period (warning) and an expiration period.
· Avoiding hard coding by using system properties.
· Catering for 3 different states within the life-cycle of license harvesting, i.e. Notified, Harvested and Restored.
· Notifying users and application admin of harvesting procedures taking place.
· Ability to restore harvesting licenses of one or more users.
· Using custom table with lots of informative fields to allow management information such as reporting.
· Using global variables within script includes to avoid repetitive modification of values.
· Defining accurate ACLs (to determine who can create, update, delete, etc).
· Following best practices of coding in general and of ServiceNow development in particular.
Throughout the development of this application, I found plenty of arising problems and managed to take notes of them and take initiative to solve them on the spot before they go through testing.
I also had a great opportunity to add lots of enhancing features to the application to make it user friendly, informative and easy t use. For example, displaying all details relevant to one specific user and one specific role, like: emails sent, logs and a list of related records for the same user with different roles. I provided this through the addition of related lists (tabs).
Another very important feature I made use of was the ability to demonstrate a hierarchical diagram of how a role is given to a user. For instance, a user could be a member of a group where the group has a role. That role would be given to the user through the group, since the user is a member of that group. I realised that there is a ServiceNow tool embedded within a UI Page that enables the demonstration of role inheritance using graphs. So I inserted a related link on each form which when clicked on it takes an ID number related to the user and role and opens up a page with a diagram showing how this role is given to this user.
The toughest challenge:
I call the following the toughest challenge, because it truly was a tough one. There were times when I don’t sleep because I’m still thinking about the code I’m writing and prefer to continue coding and solving the problem over sleeping.
That challenge was simply finding a way to tell where a role is being inherited to a user from. I.e. is the role inherited from a group? Or from a role?
So basically, user A could be given role X directly. This means the role is not inherited, and this is easy to figure out. However, there are cases, as mentioned previously, where a user is a member of a group that has a role, so the user inherits the role from that group. Sometimes it can get really complicated. Some roles contain other roles, and if user A has role X and role X has roles M, N & L, then the user inherits all those roles. Also, if role L has other roles like: P, Q & R, then user A inherits those children roles too.
Now let’s say I need to find out, through my application, where is role Q given to user A from.
We can tell that because role X is the parent of role L, and role L is the parent of role Q, and user A has both roles X and Q, and role X is NOT inherited to user A (it is given directly instead), then role X is the provider of role Q to user A.
Using this logic, I can determine that if I wanted the application to remove (i.e. harvest) role/license Q from user A, it will have to remove role X from the user instead.
There could be longer series of role inheritance. So I took a long time, given lots of effort and even used my spare time to try my best to write a scalable code that can deal with any complex scenario of role inheritance, no matter how long it could be.
Trust me, just explaining this is not easy.
Underneath is a photo illustrating a hierarchical diagram of the role/license inheritance between a specific user and a target role:
Eventually, I wrapped all this sophisticated piece of logic within one script file (a Script Include), and whenever I need to use it I would just call one main function in that file and give it the user ID and role ID that needs to be harvested/removed. Sounds simple, right?
Results:
It was important for me to finish what I started and prove to myself that I could get this done. I was more than happy and delighted when I finished this application successfully. It was like a heavy weight left off my shoulder.
I also presented the application to my colleagues and to the customer. I had a very positive feedback on it and soon after, the application got tested and deployed within the customer’s production system. What a happy ending 😊

Personal matters:
For the past couple of months, I’ve been trying to revise and study the ITIL books as preparation for the exam. I was encouraged to take this course by my managers, as it has plenty of useful concepts and strategies that businesses should implement during its development life-cycle, and also because the web application of ServiceNow is built upon the concepts of ITIL, so understanding ITIL in great detail would be very beneficial for a ServiceNow developer. As a result, I set it as a goal for myself to pass the ITIL exam and get certified before the end of March 2019. Eventually, I did take the exam and I finally passed it. It was a great feeling having achieved this milestone and I was really happy.
I don’t do development 24/7, of course. So sometimes I just turn off the engine and relax during the weekend. I occupy some of my spare time with charity activities, as I volunteer with the PennyAppeal organisation to raise money for the poor and needy people around the globe.
You can find out about the numerous humanitarian projects they do and make a donation to them at the following URL:
https://pennyappeal.org
Furthermore, I recently got engaged and looking forward to my new married life soon.
You can find out more about me on my personal blog:
http://www.mohammadnassar.tumblr.com
0 notes
Text
The Guide To Drafting The Golden Ticket
At Blockchain, we don’t want you getting left in the dust. Our goal is to provide you with resources that explain all the inner and outer workings of your wallet, while also delivering a seamless virtual experience. To bring us closer to that goal, we want to share some “best practices” to submitting a new support ticket in hopes of optimizing the troubleshooting process. In sharing these tips, we hope to reduce the amount of time you spend frustrated or skeptical— so you can spend more time planning your trip to the moon.
1. Read through our Support Center articles
The learning curve in this industry is real, folks. We try to keep our Support Center content thorough and up-to-date in order to diminish the time you have to spend searching for answers. A lot of our posts come straight from your fingertips to ours, as we often take questions and concerns straight from the tickets that you are submitting. That being said, if there is something you find to not be sufficiently described or represented, feel free to bring that to our attention or by submitting a support ticket.
2. The devil is in the details
Make sure you include all potentially relevant information in your first ticket so we can decrease our back-and-forth and get you closer to an ideal wallet experience even faster. Depending on the issue, helpful information to send us can include:
Transaction hash (found in your transaction details and on Blockchain.info, etherscan.io, or blockchair)
Any addresses involved in the transaction
Time of the transaction
Order ID (if it’s a buy, sell, or exchange trade, found in your Order History)
Screenshots of the error or inconsistency you’re seeing (by holding command+shift+3 on mac, or ctrl + prnt scrn on PC)
A photo of the cutest kitten you can find
Okay, we’re joking (kind of) on that last one. But including the rest of this information when relevant gives us a swift head start on addressing your issue, whether it means clarifying how an aspect of our wallet works, or fixing a bug on our platform.
3. Send Screenshots in the proper format
JPEG and PNG are the only types of files we are permitted to open. Remembering to send in these formats is just one other way we can keep the gap between question + answer as small as possible.
4. Keep in mind, Blockchain does not have the ability to:
Access your wallet
Change or provide your private key
Change or provide your password
Reverse, cancel, or refund transactions
Freeze or suspend wallets
This is, in part, why we stress the importance of storing your backup phrase in a safe place offline and remind you to never give out any of your wallet information.
A refresher: Giving someone your 12 word backup phrase is like giving someone the key to your house. All the contents of your wallet will be exposed and potentially compromised by the person with access. Make sure to keep this string of words in a secure place offline. Please practice safe browsing, regularly update your operating system, and do not access your wallet on public WiFi. To learn more about how the Blockchain wallet works, spend some time here.
5. One ticket is all it takes
We know how frustrating an issue with your funds can be, and we want to help you alleviate that issue as soon as possible. Submitting multiple tickets on the same issue can delay our response because we need to search for and compile those tickets first. Additionally, this may cause your inquiry to be filtered as spam. Your inquiry is important to us and we will work diligently to tackle any outstanding problems as soon as possible.
6. Follow us on social media
We update our social media with relevant news, outages, and known issues our users are experiencing. To stay up to date, follow our main social media channels on Twitter and Facebook, and follow @AskBlockchain for support-related updates and information.
When it comes to opening a support ticket, the only official way to reach us is by submitting a ticket here. Any phone number, WhatsApp group, Facebook or Twitter user asking for information most likely does not have your best interest in mind.
Don’t have a Blockchain wallet? Sign up for one today.
from Cryptocracken WP https://ift.tt/2KnXkZq via IFTTT
0 notes
Text
Professional Development Training
Planning and conducting a training meeting is one of the most critical aspects of meeting management. It is essential that you prepare yourself for a training session and ensure you know the tasks you will be required to do, so you can train the meeting members effectively.
During your business meetings, you must take good care of your ability to make sure that you give out all the required information to your participants. This will help you have a smoother process as well as assist in keeping everyone in a good mood.
However, with the influx of information on the Internet these days, there is no doubt that you are inundated with too much information which makes it difficult to choose what you should teach and what you should not. There are certain issues that you need to bear in mind while you plan and conduct your training meeting.
Ensure that you learn about how to handle changes and prepare your audience with new ideas. By understanding the basic goals of each participant and making sure that you cover all aspects of your training, you can have a clear understanding of what to tell them.
In case you do not know how to use PowerPoint or a video camera, you may want to have an additional person to assist you during the training session. The aim is to ensure that you give your audience exactly what they are looking for.
When you are ready to deliver your presentation, remember to write down a few key points. Don't forget to include things like the contact numbers of the meeting members, the date and time of the training session, and when you would like them to meet again.
It is also important to inform your participants as soon as possible on the date and time of the presentation. By doing this, they will not need to wait until the last minute to RSVP to attend.
Ensure that your knowledge is updated on a regular basis. You can update them by allowing them to access videos, audio or written material on the website.
If you want to train multiple people at the same time, having one trainer for each member of the group is usually a great idea. There are no other ways you can ensure that the training sessions are coordinated or covered well.
To get the most out of your training session, it is also important to schedule it when it will not interfere with your work schedule. It is imperative that you finish a training session on time so that you can start planning for the next one.
Make sure that the session you are planning is planned and organized well, and that you include all the necessary elements such as educational exercises, discussions, guest speakers, and practice questions. By doing this, you will ensure that you cover all of the points clearly and accurately.
Meeting management is an integral part of any organization and requires careful planning. So it is crucial that you take time to plan and conduct effective training sessions so that you can have a smooth training process.
Sources
This brief scanned the following sources (title, domain, description):
Study Professional Development Courses Australia - MCI Solutions (mci.edu.au) - Enhance your skill set and become more attractive to employees by enrolling in a Professional Development course in Australia. Find out more.
Professional Development Training (pdpseminars.com.au) - {modalcontent mymodule} {modulepos fp-modal} {/modalconten...
Short Courses (aim.com.au) - AIM's On-Campus and Online Short Courses are designed and developed by highly experienced business people at campuses right across the country.
(immi.homeaffairs.gov.au) - This visa allows you to take part in workplace-based occupational training activities to improve your skills for your job, area of tertiary study, field of expertise or in a professional development training program in Australia.
Professional Development Training (jcu.edu.au) -
Australian Institute of Training and Development (AITD) (aitd.com.au) -
Staff development and training (business.gov.au) - Learn how to develop your employee's skills and knowledge to improve productivity and job satisfaction.
Join Us - Career Development Association of Australia (CDAA) (cdaa.org.au) - We are the association for career development professionals in Australia. Our members help people make informed decisions about their careers and help organisations develop their workforce.
Professional development courses at ANU (anu.edu.au) - ANU is a place of experts, people at the forefront of global conversations. You will benefit from their deep industry knowledge and strong connections to government when you take a professional course at ANU.
Opportune Professional Development - A Registered Training Organisation (opportune.com.au) - At Opportune Professional Development (RTO ID: 60072) we provide RPL, Traineeship and Study Based Qualifications for employers, employees and individuals.
Management, leadership and professional development training (business.qld.gov.au) -
Training and Professional Development (relationshipsvictoria.com.au) - We have an established reputation for quality professional training in a range of areas related to family relationships.
Professional development and short courses (sydney.edu.au) - Meet Continuing Professional Development (CPD) requirements or take a short course to introduce you to new skills and provide an outlet for creativity.
Nursing and Midwifery Board of Australia - Fact sheet: Continuing professional development (nursingmidwiferyboard.gov.au) - Australian Health Practitioner Regulation Agency
Ongoing Professional Development (australiancelebrations.com.au) - Australian Celebrations Training is a niche celebrant training organisation established in 2003 by Ms Elisabeth O'Brien, offering training courses for Marriage Celebrants, Wedding Officiants, Funeral Celebrants, Naming Celebrants and Ongoing Professional Development Training for existing celebrants.
Professional Development - Fundraising Institute Australia (FIA) (fia.org.au) - Fundraising Institute Australia (FIA) has many unique professional development fundraising courses to help you upskill yourself and your organisation.
Training & Events (psychology.org.au) - Find training opportunities and events, including conferences, online courses, national workshops and webinars that will help you meet your CPD requirements and aid your career and professional development.
Short courses (monash.edu) - A professional development short course from Monash gives you speciality skills and knowledge delivered by the best in research and industry. Learn more.
Topics
These topics were mentioned multiple times across various sources:
Professional Development Courses
project management
training and development
Ongoing Professional Development
continuing professional development
accredited course
online courses
special offers
subject area
mental health
contemporary, interactive case studies
additional information
professional training
Mentoring programs
directed learning
established reputation
identified learning
Professional Services
vocational training
class enrolment
enrolment form
certification course
assistance programs
class date
Registration standard
mandatory learning activities
External training
Time Management
direct clinical care
equal opportunity
Questions
These are some relevant questions found across sources:
What form should my evidence of CPD (including self-directed learning) take?
How long do I need to keep a record of the evidence of my CPD, including self-directed learning'?
How do I record my CPD?
How do I describe my context of practice?
What is CPD?
What if I don't meet my CPD quota?
What do you mean by practice?
What sort of records will I be required to produce?
Can I claim my cardiopulmonary resuscitation (CPR) or fire training that I have to do at work as CPD activities?
Will everyone be audited?
0 notes
Link
SQL complete is one of the best time-saving tools for any DBA who works on database objects and data stored inside these objects using T-SQL. It’s in the job description to be very familiar with T-SQL both from a DDL and DML perspective. Data Definition Language requires writing statements like CREATE, ALTER, DROP, etc. and Data Manipulation Language applies to commands like SELECT, INSERT, UPDATE, etc.
Mastering querying SQL Server and writing T-SQL code effortlessly requires years of experience in the respective field. We all want to be more productive, get more things done during core hours, in a way that will make us a very efficient DBA. Wouldn’t it be nice to have a tool that will make all of the above easier? Fortunately, there is!
This article is a general review of one such SQL complete tool that enables DBAs to automatically complete SQL statements directly in SQL Server Management Studio and Visual Studio, improve productivity with snippets, keep track of all executed queries, auto-correct common typing errors, and much more.
Introduction
ApexSQL Complete is a SQL Server coding productivity tool with lots of features designed to provide a set of comprehensive utilities that can significantly improve productivity and speed up the development process.
Such tools are frequently overlooked by DBAs because of fear that installing any additional extensions to favorite IDE will slow things down. This is a widely held but false belief as add-ins, such as this SQL complete tool, are usually small utilities that don’t affect the performance of host applications on modern powerful machines.
With that in mind, let’s head over to SSMS with this add-in installed and see what it can do.
SQL complete statements
Code completion is the main feature of this add-in that allows auto-completion of SQL keywords, fragments, and even entire statements, filling in known and reserved words to save time and increase efficiency when writing queries.
When a new query editor is opened, as soon as typing is started e.g. a SELECT statement to retrieve rows and columns, the hint-list will appear offering valid members from the current context:
The add-in shows suggestions in the hint-list while typing, enabling users to quickly insert tables, columns, procedures, views, etc. also working with encrypted objects. The SQL complete is enabled by default and will suppress the native IntelliSense feature. But don’t worry. What it has to offer is much more.
Auto-completed keywords can be automatically formatted in UPPER, Proper, or lower case. The add-in allows users to view an object’s definition and description within the query editor. Another neat feature is its ability to automatically insert closing corresponding characters – forgetting e.g. the closing bracket, among others, is a very common mistake. The list of hint-list options goes on and on.
Customizable snippets
SQL snippets are code fragments that speed up coding by inserting frequently-used SQL constructs automatically.
The SQL complete add-in comes with more or less 230 built-in snippets that can be viewed from the Snippets library:
Start typing the name of any snippet from the library and it will appear in the hint-list. Select it to use it and SQL complete will enter T-SQL code in the query editor:
Snippets are also great for frequently running queries. DBAs tend to have a folder full of SQL scripts that they have to open up each time there’s a need. Why not save the frequently running query as a snippet and use it in just a few clicks? Here’s how to do it.
Creating a new snippet can be done either from the Options window or directly from the query editor. Highlight the code for a new snippet, right-click on it, and select Create snippet. In the newly opened window, give it a name and description (optional), and click OK to save it in the library:
Back in the query editor, as soon as the name of the newly created snipper is typed, it will pop up at the very top of the hint-list. When selected, SQL complete will enter the code as shown below:
SQL code auto-replacements
Text auto-replacements utility allows users to replace any text previously specified with the appropriate keyword, object name, or any kind of SQL code. Though it can be used for the same purpose as described in the previous example, auto-replacements are handy for fixing common typing errors and in that way speed up SQL coding.
Let’s see how it works. Can you spot a problem in the query below?
USE AdventureWorks2012; GO SELECT * FORM Production.Product ORDER BY Name ASC;
If you run this query, an error will be shown which states:
Incorrect syntax near ‘FORM’.
Oh, right. There’s a misspelled FROM as FORM. These are frequently found in keywords like SELECT, FROM, and WHERE, etc. or in column and table names.
An easy fix to overcome this problem is to go to ApexSQL main menu (Extensions menu in VS 2019) > ApexSQL Complete > Manage auto-replacements:
In the Auto-replacements window, click the New button to create a new item. For this particular example, specify that “form” should be replaced with “FROM” as shown below, and click OK in both windows to save changes:
Back in the query editor, next time there’s a typo and “form” is typed instead of “from”, SQL complete will automatically correct the mistyped keyword:
Log executed queries
Executed queries is a feature that logs information about executed queries. This allows users to browse a list of executed queries, search for specific ones, and re-use them rather than writing them again.
To go back in time, at least in the T-SQL world, navigate through SQL complete add-in main menu in the host application and pick Executed queries command. This will open a new window in which information about the date and time of the execution, user who executed a query, targeted database, duration, the status of execution, and duration can be found:
The T-SQL of executed queries can be searched through the search box at the top of the window. Only queries that meet search criteria will be shown, and the corresponding keyword will be highlighted in the T-SQL preview panel:
This window is always on top, but users can freely navigate out of it and perform other tasks. Doble-click on any query from the list executed in the past will place its T-SQL code in a new query editor so that it can be reused.
Connection tab coloring
Tab coloring is a feature that allows users to set query connection colors for individual instances of SQL Server down to the database level. Connections can be assigned to a specific environment thus making it easy to identify which connection a tab is currently using which can save time by eliminating the possibility of DBA making a mistake like executing heavy tasks in the production environment.
Setting up tab coloring is as easy as going to Tab coloring in Options window where server and database should be selected, and then assigned to an environment by clicking on the Add button as shown below:
Next time a new query is opened and the connection meets previously defined settings to one of the environments, SQL complete will color that query tab correspondingly making it easy to distinguish active environment:
Code structure viewer
Code structure utility helps users identify the construction of complex queries in the tree-like form of the code from an active query editor. It gives a high-level overview of T-SQL code which is useful for quick navigation and code understanding.
When enabled, the code structure window is shown on the left side of the query editor as shown below:
Moving the cursor thought statements in Code structure will quickly jump to different sections of a script in the query editor and highlight the corresponding code.
Database object search
Go to object is a utility for finding objects and highlighting them in Object Explorer. DBAs frequently perform database searches by querying system views to find specific objects and obtain additional information related to them. There’re some other ways, but here’s how to do it in ApexSQL Complete.
Select a database from Object Explorer to retrieve a list of objects from and navigate through SQL complete main menu to Go to objects command:
At first, the Go to object window will list all the objects in the database that SQL complete add-in has in its metadata AKA cache. As soon as a keyword is entered in the search field, results will be filtered and only matches will be shown:
Doble-click any object from the list to locate it in Object Explorer:
This can be achieved from the query editor as well. When working on a script, right-click an object in it and choose the Navigate to object option from the menu:
Query results search
Search results utility can save time when working on large Results set retrieved by a query. It allows users to search for data in one or even more results grids in case of multiple SELECT statements and highlight the results.
Once the Results set is populated with data, navigate through SQL complete main menu, and choose the Results search command. Type a keyword and click Highlight all option to find that particular keyword in the Results set data. Each time the Highlight all option is used, the number of found results is updated:
Practicing safe coding
Test mode is a feature that allows users to execute queries safely without affecting a database. Don’t waste time wrapping code around begin and rollback transactions. This SQL complete add-in will do that for you.
For example, let’s create a table by specifying columns from multiple sources using the example below:
SELECT c.FirstName, c.LastName, e.JobTitle, a.AddressLine1, sp.Name AS [State/Province], a.PostalCode INTO dbo.EmployeeAddresses FROM Person.Person AS c JOIN HumanResources.Employee AS e ON e.BusinessEntityID = c.BusinessEntityID JOIN Person.BusinessEntityAddress AS bea ON e.BusinessEntityID = bea.BusinessEntityID JOIN Person.Address AS a ON bea.AddressID = a.AddressID JOIN Person.StateProvince as sp ON sp.StateProvinceID = a.StateProvinceID; GO
Now, before executing this code and selecting multiple columns from various employee-related and address-related tables, let’s check how many records will be created in the database.
Simply click on the Test mode option from the SSMS’s toolbar or navigate to it through the main menu and notice that SSMS’s status bar will go red:
This is an indicator that any executed code will not make actual changes to a database’s structure. However, when a query is executed in test mode, it will give us information on how many rows will be affected:
Next, if the result is satisfactory and there’s nothing odd about the outcome of a query, simply turn off the test mode, and rerun the query for the changes to go through. Pretty neat. Right?
SSMS and VS integration
The add-in integrated simultaneously to both SQL Server Management Studio and Visual Studio.
Simply run the executable installer and in the host integration step, select SSMS and/or VS versions to integrate the SQL complete add-in into and click the Install button:
For detailed information about the installation options, see How to install ApexSQL add-ins and integrate into host environments e.g. SSMS, Visual Studio.
Extra features
The add-in has a ton of features and going through each of them would take time. Nevertheless, some of the honorable mentions are listed below in the form of knowledgebase articles:
CRUD procedures
Execution alerts
Export to Excel
Tab navigation
These might not be directly connected to boosting productivity but will definitely come handy for use in some of the tasks DBAs are faced with.
Conclusion
Seeing the above, it’s safe to say that this SQL complete add-in includes a set of productivity utilities that belongs in the toolbox of any DBA who works with Microsoft SQL Server using either SQL Server Management Studio, Visual Studio or even both. Code completion and keywords formatting, snippet insertion, auto-replacements, etc. are just some of the features that contribute to higher efficiency in the development process.
We hope you found this article helpful. Happy coding!
0 notes
Text
How To Build Auction Platform For Real Estate
Real estate auctions platform has always been proven effective way if you are investor and quickly looking for some deal on property . At present auction way is not only popular for business people only , instead ordinary people is also searching for new property at bargain price .
Gone are day when live auctions are used to take place in brick and morals courts in front of local authorities choose by specific set of auctioneers .
The revolution of online auction in property selling website and mobile apps has helped both investors and normal buyers to bid for property painlessly and quickly gain access of that property .
Take example of Auction.com which is US based company that sole focus is on selling bank owned properties . As per Auction.com , they have achieved $ 39 billion in sales , 4.4 million users are registered and almost 329,000 properties has been sold by their platform .
In this article we will guide you how you can create your own auction website or mobile app and what functionalities can be added in your existing real estate platform .
What Property Auction Platform Usually Offers In general some of the famous auctions platform offers following types of properties :
Short Sales Properties : In real estate , short sales property generally means a property offered for sales by homeowner who is willing to sell their house on less than outstanding mortgage on it . They general sales in less that the property value to pay their debt to lender . This type of property sales is benefits for both borrower and seller as seller can pay of their debt and maintain their credit score and buyer can get the property at lesser price .
Foreclosed Properties : Unlike short sale , in foreclosed sales , lender of loan attempts to sale the property in order to recover balance of their loan on their own . Foreclosed property is usually final step before length and legally pre-closure process , which aids both lender and borrower to avoid any negative consequences with legal process .
Bank Owner Property : Bank usually take the ownership of these kind of properties after failed foreclosure sales . These property are easily accessible on bank's websites and in general being sold out at discounted prices , thereby making them an attractive option for real estate investors .
Flipped Property : Flipped properties are investor owner property that has been exclusively been prepared for sales by investor . These are upgraded properties that are very popular among first time home buyers .
Retail Properties : This sell properties which are situated in stores , shopping centres and service business . In general business owners and investors are seeking want to buy these kind of properties .

What Features Should Be Effective In Real Estate Auction Platform ?
Real estate auction platform helps both buyers and sellers to meet each other digitally and auction platform at the same time also ensures carrying on smooth interaction between them in order to close a deal .
You must focus on offering buyer smooth bidding platform in safe and secured environment . At the same time when it some to seller , your platform should be capable of fulfilling their work in order to sell more effectively .
Let's now look at some of the features which are mandatory for any successful auction platform :
Creation Of User Account & Registration For Auction Any type of virtual auction requires all user to sign up on auction portal by entering their personal information ( such as name , address , phone numbers and so on ) in order to carry out smooth transaction on your platform . In addition to it , providing and verification of email is necessary in order to receive updates and verifications for their actions - for instance say notice of winking of auction .
In addition to it , if they are willing to participate in their auction , they would also be forced to give their Debit or Credit card information for carrying on any type of payment transactions .
Listing Of Properties Listing of properties are generally being carried out by seller which fillings auction platform with content . Listing of property lets sellers :
Add property to platform
: In general this involves listing of new property by directly clicking on add a property . You can also charge nominal fees to list their property . This includes updating the description of property , photos , 3D tours , notes and disclaimers , current or starting bid , auction timer and so on .
Selecting duration for receiving bids
: Updating the duration in which you will be getting bids for auction property . This time frame includes pre-auction , staging and post bidding period . The listing fee in general is fixed and is same regardless of what duration seller chooses .
Reoffer the property
: In case the auctioneer founds that bid was won unfairly , then there should be an option for seller to re-offer it in another round of bidding
Search
There should be search option on your portal to search for desired properties with the following features :
Filters
: Advance filter option should be facilitated to users to facilitate them to search for property as per their desired needs .
Sorting
: This facilitate users to sort property in ascending or descending order on the basis of :
Auction time remaining
Price of property
Auction date , property size , newly added property and so on
Favourite Property
: User should also have option to save or mark as favourite the property they liked the most . This features aids buyer in saving time to research for that property .
Bidding
In general as seen on most bidding platform , buyer have to place 5 to 10 percent deposit before bedding to participate in bidding process . This deposit is just hold on bidder's bank card .
Online real estate auctions is conducted in real time basis and start with minimum price . Participants generally have option to bid 24 hours a day , seven days a week until single bidder remains .
After reaching the above point , auctioneer has option to close bid and announce the winner of bidding . The person who is bidding on the platform is able to see:
the opening bid
other vendor bids made by auctioneer on behalf of seller
the total number of bids and participating bidder

When bidder is actually ready to place their bid , they will be navigated to property's bid page by clicking on the bid button . Then the bidder logs in and ca start bidding right away .
The auction closing process generally takes 30 to 60 days and closing date is always stated clearly in contract . As soon as bid winner is announced , ownership of that property is transfer to auction winner after making payment by winner .
Countdown timer : The bidding timer usually runs for two to three minute . If no other person bids by that time , then the clocks runs out and the person who last bid has been awarded the property .
Automated bidding process : This feature is specially being designed for assisting during bidding event when buyer is way from computer . In this case you can implement proxy bidding system in which software has ability to automatically place bids on behalf of bidder up to max amount set by bidder . This system allows bidder to auto bid for amount set and become winner even if he cannot place bids .
BIN ( Buy It Now ) functionality : Seller should also be able to set Buy It Now price so that they can sell for on the spot to save time
Auction Calendar
This function facilities information to user on upcoming real estate auction . User can filter auction on the basis of location , asset type , event name and so on.
How To Ensure Choice Of Buyers ?
Lets look at step below to ensure choice of buyers :
Get into agreement with national banks and mortgage service to ensure listing on your platform at best possible price .
Get your portal listed on some famous directories such as RedFin , Trulia , Zillow and more in order to directly get heavy traffic by directly letting user to visit your platform from their website or app .
Try to implement some advertising and marketing strategies which will be in addition to MLS integration strategy to attract visitors on your website .
Some Of The Basis Things To Ensure Safety Of Your Auction Platform
In order to add on more genuine and loyal users , you actually need to take care of security platform . Here are some of the tips which ca facilitate you to gain trust factor among users :
ID Verification :
While registering user for bidding on the portal , they should be asked to upload ID proof and credit card information . If you are asking question for ID verification , then you also have right to reject registration and thereon terminate bidding activity to prevent fraud .
Real Time Auction Tracking :
Facilities sellers to watch how actually the buyer is placing bids on real time basis .
Ratings :
Add on this functionality for both parties after completing the purchase and sale .
Bidder's Agreement & Obligations : Try to include all rules in bidder's agreement , for instance say including a clause to terminate membership in case of event of shill bidding to minimise fraud on your platform .
So considering all the above points that we can described in above article , you may be aware now that creating a bidding platform is very hard job and only a specialist of mobile app development company or software development company can do it efficiently .
0 notes
Text
Original Post from Talos Security Author:
By Vitor Ventura with contributions from Chris Neal.
Executive summary
The Gustuff banking trojan is back with new features, months after initially appearing targeting financial institutions in Australia. Cisco Talos first reported on Gustuff in April. Soon after, the actors behind Gustuff started by changing the distribution hosts and later disabled its command and control (C2) infrastructure. The actor retained control of their malware since there is a secondary admin channel based on SMS.
The latest version of Gustuff no longer contains hardcoded package names, which dramatically lowers the static footprint when compared to previous versions. On the capability side, the addition of a “poor man scripting engine” based on JavaScript provides the operator with the ability to execute scripts while using its own internal commands backed by the power of JavaScript language. This is something that is very innovative in the Android malware space.
The first version of Gustuff that we analyzed was clearly based on Marcher, another banking trojan that’s been active for several years. Now, Gustuff has lost some similarities from Marcher, displaying changes in its methodology after infection..
Today, Gustuff still relies primarily on malicious SMS messages to infect users, mainly targeting users in Australia. Although Gustuff has evolved, the best defense remains token-based two-factor authentication, such as Cisco Duo, combined with security awareness and the use of only official app stores.
Campaigns
After Talos’ initial report, the Gustuff operators changed their deployment redirections. When those were blacklisted, the actors eventually disabled the C2, but they never totally stopped operations. Several samples were still around, but the hardcoded C2 was not available. A new campaign was detected around June 2019, there were no significant changes the malware. The campaign was using Instagram, rather than Facebook, to lure users into downloading and installing malware.
Domain hits in June
The Instagram-related domains are used for the initial infection, using the exact same method of operation as before.
But a new campaign spun up at the beginning of this month, this time with an updated version of the malware. Just like in the previous version, any target that would be of no use as a potential target is still used to send propagation SMS messages. Each target is requested to send SMSs at a rate of 300 per hour. Even though the rate will be limited to the mobile plan of each target, this is an aggressive ask.
Domain hits in October
This method of propagation has a low footprint, since it uses SMS alone, but it doesn’t seem to be particularly effective, given the low number of hits we’ve seen on the malware-hosting domains.
Targeted applications
Just as before, this campaign mainly targets Australian banks and digital currency wallets. This new version seems to target hiring sites’ mobile apps.
One of Gustuff’s capabilities is the dynamic loading of webviews. It can receive a command to create a webview targeting specific domains, while fetching the necessary injections from a remote server.
Request Result
During our investigation, we received a command from the C2 to target the Australian Government Portal that hosts several public services, such as taxes and social security. The command was issued before the local injections were loaded (using the changearchive command). The injections were loaded from one of the C2 infrastructure servers. This command is not part of the standard activation cycle and was not part of the injections loaded by the version we analyzed in April.
This represents a change for the actor, who now appears to be targeting credentials used on the official Australian government’s web portal.
Technical analysis
This new version of Gustuff seems to be another step in its planned evolution. This malware is still deployed using the same packer, but
there are several changes in the activity cycle, which take advantage of functionalities which either where already there or where being prepared. One of the changes in the behaviour is the state persistency across installations.
ID file
During the activation process, the malware attempts to create a file called “uu.dd” in the external storage. If the file exists, it will read the UUID value stored inside it that will be used as an ID for the C2. When this happens, the malware won’t go through all the activation process. Instead, it will receive commands from the C2 immediately. This file already existed in previous versions. However, the behaviour described above was never observed.
The main API follows the same philosophy. Gustuff pings the C2 at a predetermined interval, which will either reply with an “ok” or it will issue the command to be executed.
The targeted applications are no longer hardcoded in the sample. They are now provided to the malware during the activation cycle using the command “checkApps.” This command already existed on the previous version, but its usage during the activation cycle was not mandatory.
checkApps Command
The list of anti-virus/anti-malware software that Gustuff blocks as a self-defense mechanism is now also loaded during the activation cycle.
Example of applications is blocks (not full list)
These changes in the Gustuff activation cycle indicate that the actor decided to lower the malware static analysis footprint by removing the hard-coded lists. Both commands already existed in the communication protocol and could have been used in runtime.
Command Result
During the activation cycle, the malware now asks the user to update their credit card information. The difference is that it does not immediately show a panel for the user to provide the information. Instead, it will wait for the user to do it and — leveraging the Android Accessibility API — will harvest it. This method of luring the victim to give up their credit card information is less obvious, increasing the chances of success, even if it takes longer.
The communication protocol now has a secondary command execution control. Each command is issued with a unique ID, which is then used by Gustuff to report on the command execution state.
Command execution control
This allows the malicious actor to know exactly in which state the execution is, while before, it would only know if the command was received and its result. This new control mechanism also generated the asynchronous command capability. The malware operator can now issue asynchronous commands that will receive feedback on its execution while performing other tasks — “uploadAllPhotos” and “uploadFile” commands are two of such commands.
With these changes, the malicious actor is obtaining better control over the malware while reducing its footprint.
This version of Gustuff has substantial changes in the way it interacts with the device. The commands related to the socks server/proxy have been removed, as have all code related to its operation. This functionality allowed the malicious operator to access the device and perform actions on the device’s UI. We believe this is how the malicious actor would perform its malicious activities. We believe that after collecting the credentials, using the webviews, the actor would use this connection to interactively perform actions on the banking applications.
This functionality is now performed using the command “interactive,” which will use the accessibility API to interact with the UI of the banking applications. This method is less “noisy” on the network, since it takes advantage of the C2 connection, rather than creating new connections.
The command “script” is also new. This is a very simple command with huge potential. Gustuff starts a WebChromeClient with JavaScript enabled. Afterward, it adds a JavaScript interface to the webview, which will allow the execution of methods defined in the malware code.
JavaScript scripting
By default, the WebView object already has access to the filesystem, which is not an additional security risk in this context, allows the operator perform all kinds of scripts to automate its tasks, especially when the script also has access to commands from the application.
Conclusion
This is an evolving threat, and the actor behind it seems to want to press on, no matter the level of coverage this campaign gets. Instead, they changed the malware code to have a lower detection footprint on static analysis, especially after being unpacked. Although there are no changes in the way it conducts the campaign, Gustuff still changed the way it uses the malware to perform its fraudulent activities. The main target continues to be banking and cryptocurrency wallets. However, based on the apps list and code changes, it is safe to assume that the actor behind it is looking for other uses of the malware.
Coverage
Snort
SID: 51908-51922
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors. Exploit Prevention present within AMP is designed to protect customers from unknown attacks such as this automatically.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
IP
88.99.174[.]142 88.99.175[.]152 88.99.170[.]43 88.99.170[.]141 78.46.201[.]36 88.99.174[.]140
Domains
instagram-shared[.]pw instagram-shared[.]store instagram-shared[.]info instagram-share[.]com intagram-share[.]com instagram-shared[.]net instagram-shared[.]com video-hd33[.]site video-hd30[.]site video-hd29[.]site video-hd24[.]site video-hd20[.]site video-hd18[.]site video-hd17[.]site hd-video5[.]site hd-video4[.]site video-hosting[.]site video-hd1[.]site video-hd[.]site hd-video1[.]site homevideo641a[.]cf homevideo651a[.]cf homevideo5-23b[.]ml homevideo631a[.]cf homevideo611a[.]cf homevideo4-23b[.]ml homevideo641a[.]ga homevideo3-23b[.]ml homevideo54-1a[.]ml videohosting32-e[.]cf videohosting23c[.]cf videohosting62-b[.]tk
Hashes
5981f8ec5b35f3891022f1f1cdbf092c56a9b0ac8acbcd20810cc22e7efb5e0b – SexyJassica.apk 03d1a55ce6879d79239db32c2c8e83c4a3e10cb9123d513ce7fd04defb971886 – gscptzorx.jar 3027fbd59b8dd25dcabd21800d8e8ab3222a1ae3e2d268857def4311bb01ea2e – gscptzorx.dex b13e6d70b07d6127d803d2374ebfb1e66a3b4cfd865cc2eb0e45455401be527e – flash 65a7d4f9b3549198b008a089d0c8feb30c5409efc52e8a496f503fa262a6e922 – flash2
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Gustuff return, new features for victims Original Post from Talos Security Author: By Vitor Ventura with contributions from Chris Neal. Executive summary…
0 notes