#access control syst
Explore tagged Tumblr posts
Text
Pune, a hub of growth and technology, prioritizes security through a diverse range of boom barriers and access control systems. Manufacturers cater to specific needs, offering advanced solutions like automatic rising arm barriers, folding barriers, and sliding gates, serving as robust deterrents against unauthorized vehicular access. Access control system options, including biometric recognition and RFID cards, reflect Pune's comprehensive approach to securing various spaces. The city's commitment to security, evident in its embrace of diverse technologies, positions Pune at the forefront of innovation, ensuring a safer environment for residents amidst the evolving challenges of urban life.
Learn more about Boom barrier and access control systems in Pune.
0 notes
Text
Musk's DOGE granted access to US Medicare and Medicaid systems
U.S. government officials privately warn Musk’s blitz appears illegal
Urgent Action Item: This is a quiet Coup! Contact your Senators right now, and tell them to block all Trump Nominees in response, particularly Russell Vought.
If you can't safely contact them in person, here are some other options:
Five Calls to your critters: https://5calls.org/
Here is one that will send your reps a fax: https://resist.bot/
"Congress. gov:" https://www.congress.gov/
ACLU advice for writing to your Critters: https://www.aclu.org/writing-your-elected-representatives
#DOGE#Privacy#federal data#Treasury Department#Elon Musk#U.S. government#Treasury Payments#Marko Elez#Medicare#Medicaid#Action Item#Maxwell Frost
114 notes
·
View notes
Text
Steam curled in thick tendrils around the locker room, the steady patter of water against tile filling the air as Logan stood beneath the scorching spray of the shower. He ran a hand through his damp blond hair, letting out a satisfied exhale.
"Another—hah—another damn good game," he muttered, tilting his head back, letting the water cascade over his sculpted shoulders. His muscles ached, but in a good way—evidence of a battle well-fought on the field. He smirked to himself. Of course they’d won. They always won when he was on the team.
He rolled his shoulders, steam swirling around him, but there was something else—something faint, almost imperceptible. A whirring. A high-pitched hum, barely audible over the water.
Then—click. A sharp, mechanical sound.
Logan frowned, shaking his head. "Hh-heh, must b-be…" His voice caught, hitching unnaturally for a fraction of a second. He cleared his throat, dismissing it, but then—another sound. A faint hiss, like air escaping through a vent.
His access panel had opened.
But Logan, of course, didn’t notice. He wasn’t programmed to.
The overheated processor buried deep in his synthetic musculature was automatically venting excess heat, the mechanism clicking softly as hidden vents along his back and ribs spread open. Warm air gusted from inside, blending with the steam of the shower.
"H-hot water's g-good for s—sore muscles," Logan muttered, his usual cocky drawl faltering for an instant. "G-got to keep the—hah—the machine running, huh?" He let out a sharp chuckle, unaware of the irony.
The water pounded against his body, rivulets streaming down over his vents. It shouldn’t have mattered—he was designed to be water-resistant. But his panel had opened, exposing delicate inner circuitry. Tiny droplets trickled into the crevices of his framework, slipping past seals that weren’t meant to be breached.
There was a sharp bzzt somewhere deep inside him.
Logan jerked, a barely perceptible twitch of his fingers.
His systems recalibrated, struggling to compensate for the intrusion. Another bzzt crackled in his chest, a faint pop from somewhere behind his ribs. He blinked, his usual smug smirk flickering on his face, almost as if it were an expression being re-rendered, forced into place.
"Sh-should c-cool off soon," he muttered, his voice stuttering over the words like a scratched record. "N-nothing—nothing t-t—t-to w-worry ab-about."
Another mechanical click. His fingers twitched again, this time more violently. His left hand curled involuntarily before his systems forced it back into place. A sharp whirring noise filled the shower as his processors struggled against the damage.
Then—his leg locked.
He nearly toppled, catching himself against the tile. His laugh came out choked, glitching mid-sound. "H-heh—whoops. B-b-bit of a—hah—misstep there." His grin didn’t fade, even as the servos in his knee let out a quiet, straining reeeEEEEE before finally releasing. His stance corrected itself.
For a moment, it seemed like the malfunction had passed.
Then his chest jerked—just once, sharply. His torso twisted slightly as if an invisible force had tugged at it.
"Unu—unusual a-activity detected," Logan muttered, his confident tone suddenly eerily flat, his head tilting slightly as his system tried to run diagnostics. The words weren’t conscious; they spilled out without his control, an automated alert overriding his usual bravado. "R-re-routing po-power t-to c-critical syst-systems."
He blinked hard, forcing his body back into normal posture. "Hah, y-yeah. A-all good. Just a—just a li’l p—p—post-game st-st-stiffness." His voice wavered, skipping slightly on the syllables, but he powered through it, grinning even as a sharp zap crackled from somewhere in his core.
The scent of overheated circuitry mingled with the steam.
Another jolt. His fingers twitched, then spasmed—his entire arm following, seizing up for a second before jerking back into normal position.
He didn’t acknowledge it. Couldn’t.
"J-just gotta—gott—gotta—" His voice cut out mid-sentence. Silence.
Then his entire frame gave a violent jerk.
The servos in his neck let out a sharp whir-click, and his head tilted too far to the right before snapping back into place. His chest heaved, a reflexive mimicry of breath, though his systems no longer required it. His vision flickered, his HUD overlay flashing errors faster than his processor could filter them.
ERROR: COOLING SYSTEM FAILURE. ERROR: UNEXPECTED WATER EXPOSURE DETECTED. ERROR: MOTOR FUNCTIONS UNRESPONSIVE.
His knees buckled. His grin wavered.
"H-heh—hah—c’mon, n-not—n-not now," he muttered, forcing himself upright, his body moving in jerky, unnatural motions. His servos whined in protest, a grating mechanical screech echoing in the shower stall. His system was losing the battle against the water seeping into his frame.
"J-just need a—a sec," he continued, speaking mostly to himself. "G-gotta—hah—gotta—" His voice cracked, breaking into static for a second before snapping back. "P-power through. W-we d-don’t q-qu—"
His words cut off again. His whole body shuddered violently this time, fingers clawing at the tile as another sharp pop burst from his core. His cooling fans sputtered, their whirring turning sluggish, erratic.
His processor locked up.
His eyes remained fixed forward, unseeing, as his systems tried to reboot. His fingers spasmed once more, then stilled. The last traces of steam swirled around him as his damaged servos gave out entirely.
One final jolt wracked his frame.
Then—silence.
His body remained upright for a few seconds longer, his expression frozen in place—a confident smirk that had yet to register his own defeat. His systems fizzled out one by one, background processes flickering into darkness. His balance gave out, and his frame tilted forward, slumping heavily against the tile wall.
A final, faint beep.
And then—nothing.
4 notes
·
View notes
Text
RFID library Automation for tracking, security and inventory management
LIBSYS Limited, a software as a service(SAAS) company based in Gurugram, Delhi-NCR, India, was founded in 1984 by Mr. Anil Jain to cater the needs of Identity, Tracking and Security purpose for various Indian industries. With the aim to automate the process and minimizing the human errors to zero, the Libsys offers a wide range of solutions that include Library Management Systems for institutions and government bodies, RFID based customized applications from small business to multinational organizations, Common Admission Platform and ERP for Academic Institutes, Omni-channel Retailing solution, E-Commerce Framework, CRM, Design & Architecture and other on demand solutions.
The experience of 40 years and counting along with in-depth understanding of the Indian markets, we are the proud leaders of quality and innovation. Through the experience we have, we have the ability to respond quickly to the customized client requirements with an innovative solutions that meet those needs efficiently and cost effectively. Our experience and strong mission-first work ethic has helped us develop capabilities, insights, and skills to provide the best solution one can have. Backed by our strong quality processes and rich experience in managing clients across various domains, we strive for continuous innovations in our offerings, and we take pride in being the pioneer and market leader for RFID based automation solution in India.
To name a few, software products like LIBSYS 10 LMS, LSEase, LSmart-RFID, LSRemote, LSDiscovery, LSe-RMS, symphonyX, TargetX, LSNetX (E-Com) and LSales1 CRM are the benchmarks in India serving across the domains and delivering the best operational efficiency solutions for all organizations and enterprises.
TRANSFORMING LIBRARIES
Elevate your Library
LIBSYS 10 caters to all the needs of library automation improving the efficiency of libraries and providing a delightful library experience through continuous technological innovations
Smooth Library Operations
LIBSYS 10 simplifies and automates essential library management tasks, allowing for efficient cataloging, circulation, and inventory management.
Enhanced Accessibility
Libsys 10 offers a user-friendly interface and robust search capabilities, enabling patrons to easily discover and access library resources.
Comprehensive Reporting
Libsys 10 generates detailed reports on library usage, collection statistics, and circulation trends, facilitating decision-making and resource allocation
Seamless Integration
Libsys 10 seamlessly integrates with various library systems, ensuring smooth interoperability and minimizing disruptions in existing work-flows
LIBSYS10
LIBRARY MANAGEMENT SIMPLIFIED
Step into the future
A web based library management solution to enhance the total library experience through value added features and services.
The present times demand Library Management System to deliver much more than operational efficiency. It needs to create appreciable staff satisfaction and a delightful experience for the patrons every time they interact with the system. LIBSYS is committed to delivering value to the libraries through its products. In-depth understanding of library operations, implicit needs of the patrons, and dedicated R&D efforts have guided us to deliver high-quality products that have found wide acceptance in the market space.
Its seamless work-flow enables library staff to manage library operations efficiently.
New purchase approvals, collection development, material handling, SDI services, bindery management, and a host of other functions form an integral part of the system.
MARC21 / RDA interface, Cooperative Cataloguing along with controlled authority files helps in Cataloguing on the fly.
Federated Searching brings other libraries of similar collection within your reach.
REQUEST A DEMO
MODULES
GO BEYOND THE LIBRARY
Modernize Your Library
LIBSYS 10 is a smart library management system covering all the needs of library automation in India and abroad.
Acquisition
LIBSYS 10 automated library acquisition system is capable of efficiently managing all kinds of work-flow
Cataloguing
Catalogue your records smarter and faster way with user friendly yet powerful cataloguing module.
Serial Control
Easily control and maintain your library’s serials collection in the most efficient way.
Circulation
Easy and powerful interface to handle circulation transactions, alerts, greetings, reminders, fine etc.
KEY FEATURES
Check Out Capabilities
LIBSYS 10 is a feature-rich Library Management System that empowers libraries to effectively manage their collections, streamline operations, provide enhanced services to patrons, and embrace modern technologies for a seamless library experience. Our automated acquisition system in library reduces time consuming work and enhances the overall efficiency in ordering and provides necessary management information reports.
Online Public Access Catalog (OPAC)
Digital Resource Management
Reporting and Analytics
Integration and Interoperability
Mobile Accessibility
BENEFITS
30+ YEARS
Scale Your LMS
LIBSYS 10 empowers libraries to optimize their operations, improve user satisfaction, and adapt to evolving technological advancements in the library field. It enhances the overall library experience for both librarians and patrons.
Streamlined Operations
Libsys 10 automates various library tasks, reducing manual efforts and saving time for librarians.
Efficient Resource Management
The system helps librarians effectively manage library resources, including books, journals, multimedia, and digital materials.
Enhanced User Experience
Libsys 10 enhances the experience for library patrons through its user-friendly OPAC interface.
Accessibility Anytime, Anywhere
Libsys 10's mobile accessibility ensures that library services and resources are available to patrons anytime, anywhere.
LIBSYS10
HARNESS THE POTENTIAL OF OUR LIBRARY MANAGEMENT SYSTEM!
#1 Library Management System
Unlock the Power of Efficiency and Innovation with Libsys
The present times demand Library Management System to deliver much more than operational efficiency. It needs to create appreciable staff satisfaction and a delightful experience for the patrons every time they interact with the system. LIBSYS is committed to delivering value to the libraries through its products. In-depth understanding of library operations, implicit needs of the patrons, and dedicated R&D efforts have guided us to deliver high-quality products that have found wide acceptance in the market space.
The new Web-based Library Management System ‘LIBSYS 10’ provides a greatly enhanced user experience through value-added features and services. LIBSYS 10 is built on international standards and open technologies, i.e. JAVA. It covers Acquisition, Cataloguing, Circulation, Serials, Articles Indexing, E-Books, Dean and Vendor Portals along with an enriched OPAC. Its seamless work-flow enables library staff to manage library operations efficiently. New purchase approvals, collection development, material handling, SDI services, bindery management, and a host of other functions form an integral part of the system. MARC21 / RDA interface, Cooperative Cataloguing along with controlled authority files helps in Cataloguing on the fly. Federated Searching brings other libraries of similar collection within your reach.
LIBSYS 10 gives you the opportunity to take your automated library circulation system to new heights by use of RFID / EM / Hybrid Technology. Choose LSmart / KSmart system as per your budget and requirements. Use of these technologies will help in hassle free, accurate and faster issue / return of books, inventory visibility, accuracy and efficiency, increases security function in the library, improved utilization of resources like manpower, infrastructure etc., give flexible library timings. The bottom line is that the synergy between the latest technology like RFID and libraries can create wonders resulting in empowerment of both users as well as librarians.
LIBSYS Library Management System in India has been deployed in many prestigious institutes. LIBSYS 10 caters to all the needs of library automation improving the efficiency of libraries and providing a delightful library experience through continuous technological innovations. With rich experience of more than three decades along with continuous innovation, LIBSYS has emerged as the best library management system in India.
We also undertake special projects which include multi-location library automation and RFID system implementation. The projects are executed by specialized teams comprising of experienced professionals from Library and IT domains. Our customer-focused services also include consulting to meet individual needs, organizing User meets, and providing regular software updates.
For more details connect at [email protected] or +91-0124-4894100
#rfid#rfid solutions#rfid technology#rfid reader#rfid tags#library#inventorymanagement#inventory software#assets#assetprotection#assetmanagement#tracking tag#data security#software#technology#trackinghome#cyber security#social security#cybersecurity
2 notes
·
View notes
Text
How to Root Samsung Galaxy J2 Core SM-J260F With Odin Tool

Learning how to root SM J260F, particularly the Samsung Galaxy J2 Core model, can significantly enhance your device's functionality and user experience. The root process allows you to access and modify the operating system's code, enabling you to install custom ROMs, remove pre-installed apps, and even boost your device's speed and battery life. In this guide, we'll walk you through the step-by-step process of how to root Samsung SM-J260F. We'll also delve into using the Odin Tool, a popular firmware flashing tool developed by Samsung. This tool is particularly useful when you want to root Samsung SM-J260F, unlocking a world of customizability and improved performance. So, let's get started with the process of rooting your Samsung Galaxy J2 Core model SM-J260F. Read more - Why we want to root - Full Details with a guide
Table of Contents
The Pros and Cons of Rooting Your Samsung Galaxy J2 Core SM-J260FThe Advantages of Rooting SM-J260F The Drawbacks of Rooting Samsung SM-J260F 8 Steps To Root SM J260F Verifying Successful Rooting of Your SM-J260F Reversing the Root Process on Samsung Galaxy J2 Core SM-J260F Conclusion Frequently Asked QuestionsWhat should I do if I can't find my Samsung SM-J260F model listed on the Chainfire website to root SM-J260F? Why did my attempts to root SM-J260F with applications like KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius fail? I have rooted my Samsung SM-J260F, but the system indicates "su binary needs to be updated/The Superuser binary (su) must be updated". How can I resolve this issue? I've rooted my Samsung Galaxy J2 Core SM-J260F and now the Kinguser binary (su) needs updates? How to Fix the "Unfortunately, kinguser has Stopped" Error in Samsung Galaxy J2 Core SM-J260F After Rooting? What should I do if I encounter the "Unfortunately, kingroot has Stopped" error while trying to root SM-J260F? Why am I seeing "Root Failed! , No Strategy Found, ConnectionUnstabitil , need root" error when trying to root my Samsung SM-J260F? How to fix Google Play Store errors on my rooted SM-J260F? What should I do if I encounter the "could not do normal boot odin mode" error while trying to root SM-J260F? What should I do if my Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after trying to root? Fix Bootloop on device (continuously restart)
The Pros and Cons of Rooting Your Samsung Galaxy J2 Core SM-J260F

When deciding whether to root your SM J260F, it's essential to weigh the pros and cons. Rooting, though potentially beneficial, comes with its own set of risks and challenges. Here's a balanced look at the advantages and drawbacks of rooting your Samsung SM-J260F. The Advantages of Rooting SM-J260F 1. Custom Software (ROMs): One of the main reasons people choose to root Samsung SM-J260F is the ability to install custom ROMs. These ROMs can enhance performance, provide additional features, and even update your device to a newer version of Android. 2. Apps Permission Control: Rooting provides you with complete control over what your apps can and cannot do. This means you can block ads, remove bloatware, and enhance battery life. 3. Full Device Control: Rooting your Samsung SM-J260F allows for total control over your device. You can change the CPU speed, modify system files, use themes, and even change boot images. The Drawbacks of Rooting Samsung SM-J260F 1. Bricking Your Device: The most significant risk when you root Samsung SM-J260F is bricking your device, rendering it unusable. This usually happens when the rooting process is not followed correctly. 2. Voiding Your Warranty: Most manufacturers, including Samsung, will void your warranty if they find out you've rooted your device. 3. Security Risks: Rooting can make your device more vulnerable to viruses and malware because you bypass certain protections put in place by Google. 4. System Updates: Sometimes, rooting can cause issues with system updates. This means you may not be able to install updates or may face instability after an update. In conclusion, deciding how to root SM-J260F isn't a decision to be taken lightly. While the benefits can be significant, the risks are equally substantial. Always ensure you understand the process and the potential implications before proceeding.
8 Steps To Root SM J260F
Note - First Back up your data Step 1 - Charge your phone up to 50%. - Download the Samsung Galaxy J2 Core SM-J260F USB Driver and install it on your computer. - Turn ON USB Debugging and Developer mode on the phone. Step 2 Download the Odin program to your PC - Now download the Odin program to your laptop or your Computer. - After downloading, install and launch it. Step 3 - Take your phone and Turn it OFF by pressing the power key. - Now press and hold the Power key + Home key + Volume down key until boot to download mode.

Step 4 - Connect your phone to your PC or laptop by using a USB data cable. It's better to use original Data cables. Step 5 Download the CF-Root file for Samsung Galaxy J2 Core SM-J260F - Download the CF-Root file for Samsung Galaxy J2 Core SM-J260F. (Yes this zip may include Odin tool again. Use one of the Odin.) - CF root file is ZIP so, you have to unzip it.
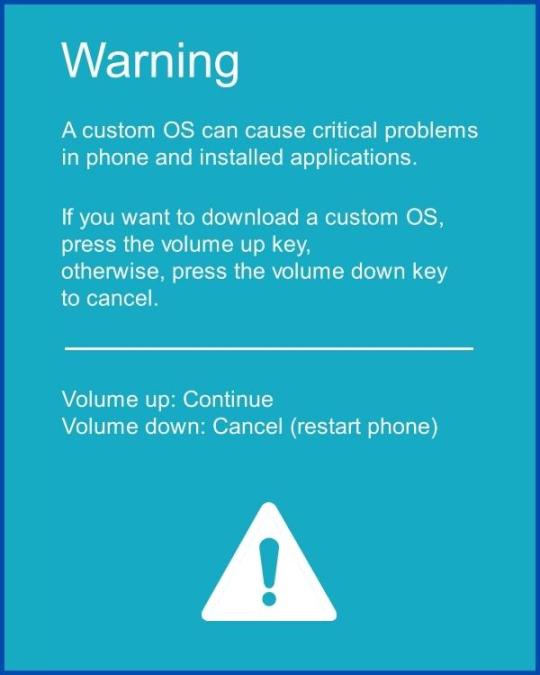
Step 6 - Now press the Volume up key to continue to Download Mode.
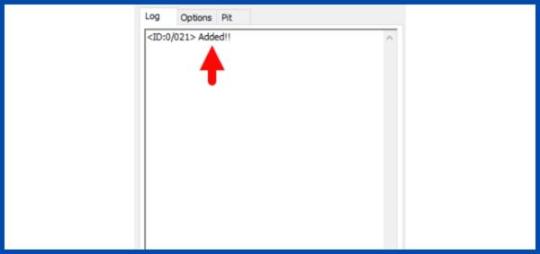
- After tapping the Volume up key, you will able to see the "Added" message in the Odin tool's notification box.
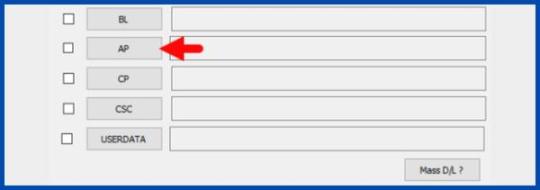
Step 7 - Click PDA / AP and browse to the downloaded CF-Root file. - Select "Auto Reboot".
- Start Rooting by Clicking Start. - Read More - Increase RAM SIZE after root Step 8 - Please wait until the phone restarts automatically and it will display a green Pass.
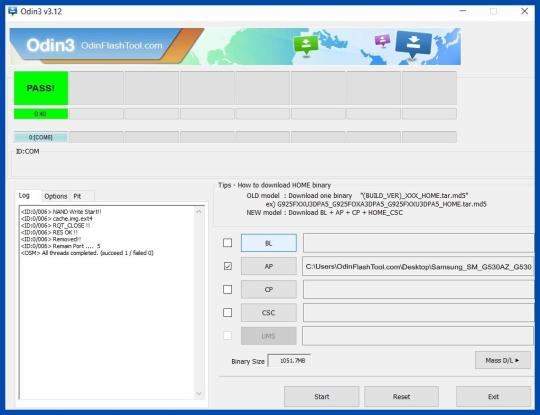
Root Samsung Galaxy J2 Core SM-J260F - The last step is to Factory Reset your phone after turning it on. - Now, Congratulations you have Successfully Rooted :) - Read more, OK I rooted. Now what next?
Verifying Successful Rooting of Your SM-J260F

To confirm if you've managed to properly root your Samsung SM-J260F, there are a couple of straightforward methods you can utilize. If an application titled "SuperSu" is present on your device after the rooting process, it typically indicates successful root status. But if you're still harboring doubts about how to root SM-J260F and whether it's been done correctly, there's an additional step you can take. Simply make use of a trusted third-party application, specifically designed to assess root access on devices like the root Samsung sm-j260f. This will conclusively inform you if your phone has been rooted effectively. Top 10 Rooted apps for android devices
Reversing the Root Process on Samsung Galaxy J2 Core SM-J260F
After successfully executing the 'root sm j260f' process on your Samsung Galaxy J2 Core, you may decide that root permissions are no longer necessary for your needs. In this case, unrooting your Samsung SM-J260F becomes your next step. Rest assured, the process to revert back from the root Samsung sm-j260f is straightforward and involves a few simple steps. Click here for more detailed instructions on how to unroot sm-j260f and bring your device back to its original settings.
Conclusion
In conclusion, learning to root sm j260f using the Odin Tool unlocks the full potential of your Samsung Galaxy J2 Core. Despite being a technical process, it offers control and customization options. However, it's crucial to back up your data before rooting any device, including the Samsung sm-j260f variant. Remember, rooting may void your warranty, but the benefits can outweigh the risks if done correctly.
Frequently Asked Questions
What should I do if I can't find my Samsung SM-J260F model listed on the Chainfire website to root SM-J260F? If your specific model, such as the Samsung SM-J260F, isn't listed on the Chainfire website, don't worry - there are other options available to root your Samsung SM-J260F. The absence of your phone model could indicate that the developers are currently making or updating your phone's CF file. In the meantime, you can consider using a different method to root Samsung SM-J260F. Numerous rooting apps are available that can help you root your Samsung SM-J260F effectively. It's recommended to wait for the official update, but if immediate rooting is necessary, these apps can be a viable alternative. For more details on how to root SM-J260F using these alternative methods, refer this guide. Why did my attempts to root SM-J260F with applications like KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius fail? Rooting applications such as KingoRoot, Kinguser, FramaRoot, Kingroot, Vroot, Root Master, z4root, and Root Genius can potentially root your Samsung SM-J260F. However, these applications may fail to root Samsung SM-J260F if your phone model isn't supported by the app. It's important to note that not all rooting applications are universal and can work with every phone model. If you're struggling with how to root SM-J260F using these applications, it's advisable to try the CF-Root method instead. This is considered the standard way to root mobile phones, including the SM-J260F, and is likely to be successful where other methods have failed. I have rooted my Samsung SM-J260F, but the system indicates "su binary needs to be updated/The Superuser binary (su) must be updated". How can I resolve this issue? If you encounter the "su binary needs to be updated" issue after rooting your SM-J260F, you can resolve it by following these steps: first, unroot your device and remove all rooting apps. Then, restart your phone to clear any remaining data from the apps. Update the Superuser binary (su) and proceed to root your Samsung SM-J260F again by following the provided guide. Always exercise caution when rooting your device or seek professional assistance if needed. I've rooted my Samsung Galaxy J2 Core SM-J260F and now the Kinguser binary (su) needs updates? If you're facing issues after you root sm j260f, you can follow these steps to unroot your phone: - Update Kinguser binary (su): Open the Kinguser app and follow the prompts to update. - Remove rooting apps: Go to Settings > Apps > Select the app > Uninstall. - Unroot your phone: Use a root access file manager to delete the "su" and "busybox" files from the /system/bin and /system/xbin directories. - Restart your phone: Restart your phone to ensure all changes take effect. If you want to root your phone again, follow a guide on how to root sm-j260f. Always take a full backup of your data before making any changes to your phone's software. How to Fix the "Unfortunately, kinguser has Stopped" Error in Samsung Galaxy J2 Core SM-J260F After Rooting? If you've recently attempted to root SM j260f and are experiencing the "Unfortunately, kinguser has stopped" error on your Samsung Galaxy J2 Core SM-J260F, here are some solutions you can try. Firstly, try restarting your device to see if the issue resolves itself. If the problem persists, follow these steps: - Open the Settings page on your device. - Navigate to the App or Application Manager. - Scroll down the list of applications to find 'kinguser'. - Once found, click on it and select 'Delete cache and data'. This process should ideally fix the error you're encountering after trying to root Samsung sm-j260f. If the problem still persists, you may need to consult with a professional or explore other forums that offer solutions on how to root sm-j260f without encountering such issues. What should I do if I encounter the "Unfortunately, kingroot has Stopped" error while trying to root SM-J260F? This is a common issue faced by many users attempting to root the Samsung SM-J260F. If you see the "Unfortunately, kingroot has Stopped" error message on your device, don't worry. Here's a simple solution to tackle this problem: Firstly, restart your device and check if the issue persists. If that doesn't work, follow these steps: - Navigate to the Settings page on your device. - Look for the app or application manager. - Find kingroot in the list of applications. - Select kingroot and delete both cache and data. This should ideally resolve the "Unfortunately, kingroot has Stopped" error you're facing while trying to root Samsung SM-J260F. If the issue continues, you might need to consider other methods on how to root SM-J260F. Why am I seeing "Root Failed! , No Strategy Found, ConnectionUnstabitil , need root" error when trying to root my Samsung SM-J260F? If you're encountering the "Root Failed!, No Strategy Found, ConnectionUnstabitil, need root" error while trying to root your SM-J260F, it's likely due to the use of an incompatible rooting app. For your Samsung device, we highly recommend you to root Samsung SM-J260F using the CF root method. This method is known to be quite effective and eliminates common issues that are often associated with other rooting methods. Just follow our step-by-step guide on how to root SM-J260F using the Odin tool to avoid such errors in the future. How to fix Google Play Store errors on my rooted SM-J260F? If you're facing Google Play Store errors after rooting your Samsung SM-J260F, follow these steps: - Switch to a new Google account. - In device settings, navigate to App Manager > Google Play Store. Clear both cache and data. - If errors persist, delete unnecessary media files to free up storage space. These steps should help resolve most Google Play Store errors after rooting your device. What should I do if I encounter the "could not do normal boot odin mode" error while trying to root SM-J260F? The "could not do normal boot odin mode" error often occurs when you use an incorrect CF root file while trying to root Samsung SM-J260F. However, there's no need to worry as you can still switch on your phone. For a comprehensive solution on how to resolve this issue and successfully root SM-J260F, please follow this link . Remember, using the correct files and procedure is crucial when you attempt to root Samsung SM-J260F to avoid such issues. What should I do if my Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after trying to root? If your Samsung Galaxy J2 Core SM-J260F gets stuck on the logo screen after attempting to root Samsung sm j260f, there are a few steps you can take to resolve the issue. - Firstly, navigate to the Odin tool and switch to DL mode. Then, repeat the above steps for rooting your device. - If the problem persists, it's possible that the CF Root file you downloaded is damaged or incorrect. Read the full article
2 notes
·
View notes
Text
Scuba Diving in Goa Price And Safety Guide

Dive into the World of Sea Diving in Goa
Goa may be famous for its golden beaches and lively parties, but beneath those turquoise waters lies a whole different kind of magic—sea diving in Goa is your passport to an underwater dream. Whether you're a complete rookie or a seasoned diver, Goa’s dive sites—especially near Grande Island—offer surreal sights: coral reefs teeming with vibrant fish, mysterious shipwrecks, and the tranquil dance of ocean currents.
Start your day early at Calangute Residency at 6:00 AM, with a brief but essential swimming pool training session. This session builds your basic skills and comfort underwater. After this, a short drive takes you to the jetty where the real thrill begins. Equipped with professional gear and accompanied by certified instructors, you’ll be diving anywhere from 18 to 60 feet deep. And yes, you get HD stills and videos to flex on the 'Gram.
Scuba Diving Price: Packages for Every Pocket
Scared of breaking the bank? Don’t be. The scuba diving price in Goa ranges from budget-friendly to premium, depending on your thirst for depth and duration:
SSI Try Scuba (₹2990): 20-minute dive, ideal for first-timers.
Basic Scuba Dive (₹4990): 40-minute dive—more time to bond with the fish.
Double Dive (₹6990): 80 minutes of underwater euphoria.
All packages include safety gear, training, certified instructors, refreshments, and dolphin spotting. The only thing you need to bring? A spirit for adventure (and maybe a waterproof heart if the ocean gets flirty).
Deep Sea Diving in Goa: Exploring the Abyss
Deep sea diving in Goa is not just an activity; it's a descent into silence, where the ocean becomes your private concert hall. With depths reaching up to 60 feet, you’ll glide over coral gardens and forgotten shipwrecks. Don’t worry, you won’t be tossed in without a clue. The journey begins with detailed training in a swimming pool, followed by real-time assistance from PADI & SSI certified instructors throughout the dive.
Dive time ranges from 20 to 80 minutes, depending on your chosen package. Just remember, no flights after diving—your ears will thank you.
Underwater Scuba Diving: The World Beneath the Waves
Once you submerge, underwater scuba diving turns surreal. You’ll see vibrant marine life, maybe even a curious turtle or a shimmering school of fish performing synchronised swimming. You’ll learn basic hand signals, buoyancy control, and how to be one with the ocean’s rhythm.
Whether you're swimming near coral reefs or exploring a sunken shipwreck, you’ll feel the humbling peace that only being underwater can offer. For many, it’s not just a hobby—it’s healing.
Water Diving in India: Why Goa Leads the Way
When it comes to water diving in India, Goa remains unbeatable. It checks all the right boxes: affordability, accessibility, biodiversity, and safety. The best time for diving? October to April, when the waters are calm, and visibility is crystal clear.
Goa also maintains strict safety standards—from age restrictions (10+ only) to medical evaluations for those with health conditions like respiratory or heart issues. Alcohol is a strict no-no before diving (save that feni for after the dive), and yes, please don’t touch the coral—respect the marine life you’re visiting.
Dive Smart: Safety Checklist Before You Take the Plunge
Medical Clearance: Mandatory if you’re on regular medication or have health concerns.
Briefing Attendance: Don’t zone out; safety instructions can literally save your life.
Proper Equipment: Fitted gear is key—our team checks everything for you.
No Flying After Diving: Give yourself 18-24 hours before boarding a plane.
Advance Booking: Slots fill up fast, so don’t wait till the last minute.
Weather Dependent: Nature decides—your dive may shift or cancel due to rough conditions.
Buddy System: Always dive with a partner for safety and shared awestruck moments.
The Ocean’s Whisper, Goa’s Deepest Secret
Scuba diving in Goa is more than an adventure—it’s a conversation with the deep blue, a secret the sea shares only with those brave enough to listen. Whether you’re here for the thrill, the therapy, or just the fish selfies, the ocean awaits. So book your dive, suit up, and take the plunge—Goa’s underwater world is calling.
Char Dham Yatra calling you in 2025? If yes, Universal Adventures has you covered with itinerary info and everything you need to know!
0 notes
Text
Leading Benefits of Evening CNA Classes: Flexible Training Options for Aspiring Nursing Assistants
Top Benefits of Evening CNA Classes: Flexible Training Options for Aspiring Nursing Assistants
Are you considering a career in healthcare but worried about balancing your current commitments? Evening Certified Nursing Assistant (CNA) classes offer an excellent solution,providing flexible scheduling options that accommodate working professionals,students,and individuals with family responsibilities. This comprehensive guide explores the top benefits of evening CNA classes,helping you understand why they are an ideal pathway to entering the rewarding field of nursing assistance.
Introduction
Certified Nursing Assistants play a vital role in healthcare settings, providing direct patient care and supporting medical staff. Gaining CNA certification is often the first step toward a fulfilling career in the medical field, with many opportunities for advancement. Though, traditional CNA classes usually occur during daytime hours, making it challenging for many aspiring students to attend.
That’s where evening CNA classes shine. Offering flexible training schedules, these courses help individuals achieve their certification goals without sacrificing current employment or personal responsibilities. Let’s explore the numerous advantages of enrolling in evening CNA programs.
Understanding Evening CNA Classes
Evening CNA classes are designed to provide comprehensive training in a schedule that fits your lifestyle. Typically, these courses take place after standard working hours, often from 5 PM to 9 PM, or on weekends, making them highly accessible for working adults and busy parents.
These programs cover essential topics like basic nursing skills, anatomy, patient care techniques, infection control, and compassionate communication. they also include hands-on clinical practice to ensure students gain real-world experience.
Top Benefits of Evening CNA Classes
1. Adaptability for Working Professionals
One of the primary advantages of evening CNA classes is the flexibility they offer. If you’re already employed during the day,evening courses allow you to enroll and train without disrupting your current job. It’s an ideal way to earn your certification while maintaining financial stability.
2. Balancing Education and Family Commitments
Many students are juggling family responsibilities alongside their career aspirations. Evening CNA classes enable parents and caregivers to pursue their training without interfering with daytime responsibilities. This flexibility leads to less stress and more successful program completion.
3. Accelerated Pathway to Certification
Evening CNA programs often offer intensive schedules that can help students complete their training faster compared to traditional day classes. This means you can get certified and start working in the healthcare industry sooner.
4. Enhanced Career Opportunities and Advancement
Completing an evening CNA course increases your employment options,as hospitals and nursing homes often seek staff who can work flexible shifts. Additionally,becoming a CNA can be a stepping stone to further certifications in nursing or health sciences.
5.Catch up on Education While maintaining Income
For those who cannot afford to leave their current employment, evening classes provide a chance to upgrade skills without losing income. This practical approach to education ensures financial stability while advancing your career goals.
6. Networking Opportunities
Evening classes bring together diverse students, including working professionals and parents, offering valuable networking opportunities within the healthcare community. These connections can lead to job referrals and mentorship opportunities.
Practical Tips for Success in Evening CNA Classes
manage Your Time Wisely: Prioritize coursework and clinical schedules to stay ahead.
Maintain a Support System: Communicate your training commitments with family and friends for added support.
Stay Organized: Use planners or digital calendars to keep track of classes, exams, and clinical rotations.
Take Care of Your Health: Ensure you get enough rest and proper nutrition to keep up with demanding schedules.
Engage Actively: Participate in class discussions and clinicals to maximize learning experience.
Case Studies: Success Stories of Evening CNA Students
Student
Background
Outcome
Jane D.
Full-time mom balancing childcare and a part-time job
completed CNA training in 3 months, secured full-time CNA position
Mark S.
Full-time worker seeking career change
Graduated from evening CNA program, now pursuing RN certification
Lisa P.
College student with daytime classes
Finished CNA training over summer, gained practical experience and employment
First-Hand Experience: Why Students Prefer Evening CNA Classes
Many students report that evening CNA classes allow them to learn effectively without sacrificing income or personal responsibilities. The flexible schedule reduces stress, enabling better focus and retention. Additionally, students appreciate the supportive surroundings created by peers facing similar challenges, fostering motivation and camaraderie.
Additional Resources and Practical Tips
To maximize your success in evening CNA classes,consider these practical tips:
Research Accredited Programs: Ensure your program is state-approved and offers comprehensive clinical training.
Plan Your Finances: Explore scholarships, financial aid, or employer reimbursements that can support your education.
Prepare for Clinicals: Keep clinical attire ready and familiarize yourself with infection control protocols ahead of time.
Stay Motivated: Celebrate small milestones to stay inspired throughout your training journey.
Conclusion
Embarking on a CNA training program is a notable step toward a rewarding healthcare career. Evening CNA classes stand out as an excellent choice for aspiring nursing assistants who need flexibility without compromising quality education. With benefits ranging from adaptable schedules to faster certification pathways, these programs provide a practical solution for busy individuals.
If you’re looking to break into the healthcare industry while balancing personal and professional commitments, evening CNA classes could be the perfect fit. Start exploring your options today and take the first step toward making a positive impact in patient care!
https://allcnaprograms.com/leading-benefits-of-evening-cna-classes-flexible-training-options-for-aspiring-nursing-assistants/
0 notes
Text
The workflow of a professional stock quant trader: A detailed look at the entire process from strategy to execution
✅The workflow of a professional stock quant trader: A detailed look at the entire process from strategy to execution Quant traders are a fusion of financial technology and mathematical models, and they use automated strategies to make investment decisions. In this article, we will understand the workflow of a professional quant trader in detail, from early morning to late night, and learn how to use tools such as AllTick to build a stable and efficient quant trading system.
🕘 1. Morning: Market preparation and backtest review ✅ Automatically sync the previous day's market data
Use the AllTick API to automatically get key indicators such as tick-by-tick market, trading volume, and volatility.
📈 Rapid strategy backtesting
Use Backtrader or Pandas to quickly test the performance of your strategy on new market data.
Check the stability of your signals and whether abnormal fluctuations trigger your strategy boundaries.
🌐 Track macro data
Pay attention to the economic events of the day (see calendar sources like TradingEconomics, Investing.com, etc.).
Analyze their impact on your current positions (e.g. interest rate sensitive stocks).
🧠 2. Morning: Design and model new strategies 🧮 Feature engineering and signal generation
Calculate common indicators: MA, MACD, RSI, Bollinger Bands
Or factor building using unstructured data: social media popularity, news sentiment, hot words for stock selection, etc.
⚙️ Strategy modeling
Build strategies such as momentum, mean reversion, statistical arbitrage, and factor models
Simulate the performance of strategies in virtual accounts using Python/C++ coding
🤝 Cross-functional collaboration
Communicate with developers on data structures and API calls
Sync max positions, trade frequency, extreme situation plans, etc. with risk management team
📊 3. Afternoon: Historical backtesting + risk management adjustments
📅 Multi-period historical testing
Backtest strategies in multiple scenarios, such as bullish/bearish cycles and volatile markets, using AllTick tick-level or minute-level data
📉 Risk Indicator Analysis
Comprehensively evaluate the performance of your strategy, including Sharpe ratio, maximum drawdown, Calmar ratio, and profit/loss ratio.
💸 Cost Simulation
Analyze fee decline, slippage, and yield delay.
Test cost sensitivity in high-frequency trading.
💻 4. Evening: Automatic deployment and monitoring
🚀 Online automated trading
Connect your strategy to platforms such as Alpaca API, IBKR, and Futu API to start real-time operation.
📡 Real-time system monitoring
Use Grafana + Prometheus to check transaction signal execution, system delay, and data synchronization in real time.
🔍 Logging and troubleshooting
Record behavior such as order success rate, deviation trading, and API anomalies for subsequent strategy diagnosis.
🌙 5. Evening: Reviewing the summary and continuing to learn
📒 Daily re-trading
Trigger logic, market background, P&L analysis, execution quality evaluation for each transaction
🧾 Strategy version control
Manage strategy code and documentation using Git, marking the reason for changes and version numbers
📚 Academic and technical learning
Read new papers and test new data sources (ESG signals, satellite images, consumption chain data, etc.)
Try deep learning models and new algorithms (Transformer, reinforcement learning)
🔧 6. The role of AllTick in the daily life of a quantitative trader
Feature category Benefits provided by AllTick
Real-time market WebSocket push, latency is only 170ms, ideal for high-frequency trading
Historical data Provides full category data at tick level, K-line level, and market level
API access method Supports RESTful and WebSocket, compatible with Python/Go/JavaScript/Java
System stability 99.95% SLA Quality of service, support for multiple accounts, large data calls Applicable scenarios Strategy development, backtesting system, real-time execution, factor modeling, risk management calculation, etc.
✅ Summary: Quantitative traders are system architects and data artists.
The work of quantitative traders goes beyond strategy creation and order placement. From strategy design, data collection, model training, backtest optimization, real-time deployment, system operation, and risk management, every process requires systematic thinking and a deep understanding of data.
A reliable, real-time, scalable data platform like AllTick API is the "infrastructure" that allows the entire workflow to run smoothly.
📎 Recommended Tools and Resources Modules Tools/Platforms Data AllTick, Tushare Pro, ccxt Backtesting Backtrader, Zipline, QuantConnect Models scikit-learn, XGBoost, LSTM, PyTorch Transaction Execution Alpaca API, IB API, vn.py Monitoring and Operation Grafana, Prometheus, Docker
0 notes
Text
Boom Barrier Manufacturers in Ahmedabad
In Ahmedabad, where technology and security go hand in hand, companies making boom barriers play a big role in protecting entry points. These companies use advanced engineering to create strong barriers that stop unauthorized vehicles from getting through. By making sure their barriers work well and are reliable, these Ahmedabad companies are really helping to keep the city safe. Their barriers not only help manage traffic in the busy city but also show a dedication to making homes, businesses, and public places secure. Think of these companies as protectors, using the latest solutions to make Ahmedabad safer from possible security issues.
0 notes
Text
Restaurant Point of Sale Systems in Canada: Choosing the Best for Your Business!

In the Fast One, customer accuracy, satisfaction, and loyalty are the key ingredients for success. An essential tool on which modern restaurants in Canada base their operations is the point of sale (POS) system for restaurant sales. More than a digital collage, POS Today's products offer various functions, including order management, kitchen scheduling, and monitoring and equity control for the cooking process. While the restaurant scene in Canada continues to grow in diversity, the best output system can have a significant impact on customer experience.
Restaurant point of sale systems Canada is a combination of equipment and software that allows restaurants to process sales transactions. However, the modern systems pose much more than just a sales registry. They act as the central hub for hotel operations, which allows them to send orders to the kitchen, calculate for the front desk, and generate reports. For restaurants in Canada, especially those competing with these major centers such as Toronto, Vancouver, and Montreal, a strong sales presence is not a luxury - it's a necessity.
When shipping a system of selling, Canadian waste focuses on serious features in a species, whether it is a rapid service or a highly localized chain. The main features to consider are accurate check and effective control, including table control and antitoxins of the cooking system. Accept a variety of payment methods, including credit/debit cards and contactless payments. It monitors to real ingredients, helping prevent lack and reduce food waste.
Choosing the Best Restaurant Point of Sale System
Allowing distance access to teal data and updates is beneficial for managing multiple localizations of diverse cultures in Canada's various jobs, which feature a mix of local and international cuisine, and for a personalized operational solution. The best restaurant point of sale system adheres to rules and to be integrated with local payment providers. Fashioned the need for restaurants to dash is to implement no-contact plans, distribution, and options.
The best systems of systems in Canada that replied to this change and provide integration with third-party distribution, orders, and bushes. With the Donation of Sold Solutions Mixer, selecting the best sales system point can be beneficial. Here are some of the best available candidates in Canada, each offering unique forces. The restaurant point of sale system Canada is especially designed for restaurants. It offers user an interface and a series of features, such as the table control, the bill, and strong analysis.
Why the Restaurant point of sale systems is Essential for Canadian Restaurants?
Because he was built to rest, he understands the needs of Canadian restaurateurs intelligently. Square is well-known for its affordable systems and easy-to-use POS. The Restaurant point of sale systems offers the best opportunity, making it a favorite among the initial small restaurants in Canada. Its free level is beautiful for budget-conscious restaurants. Another Canadian success, Montreal-based, is a system of selling with the unsolicited cloud for their great personal options.
Supports legacy systems, includes advanced inventive management, and is part of a wide range of third-party applications. Although based in the United States, Customer Contact Solutions - London, Ontario Canada has established a foothold in the Canadian market. It is known for its achievement platform, which includes a cooking display system, mobile ordering, advertising sheets, and job management and employment services.
While technology continues to evolve beyond the restaurant in Canada, it should preserve the more artificial intelligence and decision-making aspects. Intermediate slave forts and movable solutions are from the first standard, focusing more on durability. Restaurants adopting restaurant point of sale systems across the right sales system that will make them efficient and benefit them, but also remain competitive in the world of fewer dealerships.
Conclusion
The restaurant exit systems are no longer just transactions - these are complete tools that enhance the customer's experience and the entire customer journey. Either run a comfortable coffee or leverage the center of Vancouver; the right point can raise your workflow or increased by evaluating your specific commercial needs or comparing the best exit systems in Canada is well-suited to make them suit an intelligent investment in your restaurant's future.
0 notes
Text
Secure Your Business Reputation with SOC 2 Certification in Vietnam
If you run a tech company, SaaS startup, or any business that handles customer data, you’ve probably heard about SOC 2 certification and compliance in Vietnam. But what does it actually involve, and more importantly, how much does it cost to get SOC 2 certified here?
Let’s break it down together.
What is SOC 2 Certification and why does it matter?
SOC 2 (Service Organization Control 2) isn’t just a certificate to hang on the wall. It’s a globally recognized framework designed to show that your company protects customer data properly and operates with strong security practices. With the rapid growth in digital transformation, clients, whether from local enterprises or international are more concerned about their data security and want proof that their data is in safe hands. By achieving SOC 2 Certification in Vietnam, you’re telling current and future clients:
“We have tested systems, policies, and controls in place to protect your data.”
It covers five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. In practical terms being SOC2 certified means you’ll need documented policies, regular monitoring, access controls, and incident response plans.

Why more Vietnamese Businesses are Choosing SOC 2 Compliance?
You might be thinking: isn’t ISO 27001 enough? The truth is, that many international clients and large enterprises specifically ask for SOC 2 reports. It’s often part of vendor due diligence before they sign contracts.
SOC 2 Certification:
* Establishes trust and credibility with global clients
* Helps speed the closing of deals by providing answers to complex security questionnaires
* Helps to find and analyze gaps in your security system
In short, it’s not just compliance; it’s a competitive advantage.
SOC 2 Certification Process in Vietnam Understanding the Key Steps
The process of achieving SOC 2 certification in Vietnam is essential for ensuring that your business aligns with rigorous standards for data security, privacy, and confidentiality. It begins with a thorough internal assessment of your current security practices to identify any gaps or areas that need improvement. This assessment focuses on the five Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy.
Once areas for improvement are identified, the next step involves refining your internal policies, updating procedures, and strengthening security measures. This could include implementing stronger access controls, improving data encryption, or enhancing monitoring systems. After these improvements are made, the business undergoes a comprehensive review to assess how well the implemented systems meet SOC 2 standards. If your company is found to be fully compliant, SOC 2 certification is awarded, marking your commitment to maintaining high levels of trust and security. This certification enhances your company’s reputation, builds customer confidence, and establishes a solid foundation for long-term success.
What about the SOC 2 Certification Cost in Vietnam?
Here’s the part everyone wants to know: SOC 2 certification cost in Vietnam. The cost isn’t fixed, it depends on a few key factors:
Type of report: SOC 2 Type I (evaluates your design of controls at a point in time) usually costs less than SOC 2 Type II (tests how those controls operate over 3–12 months).
- Size and complexity: Typically a small SaaS team with simple systems would pay less than any larger enterprise with multiple cloud platforms and services.
- Readiness: If you already have solid data security policies and processes then you will pay less on gap analysis and improvements.
- Auditor and Consulting Firm Fees: International auditing firms usually have a higher billing rate, whereas local or regional may be more competitive rates.
Usually, for small to medium businesses, the price is determined by your current security posture, system complexities, and the choice of a local or international auditor. Getting a custom estimate is optimal as the actual investment is broad.
Final thoughts
Getting SOC 2 Certification in Vietnam is a practical way to show clients, both local and international, that your business takes data security seriously. If you are wondering about the SOC 2 audit cost in Vietnam, the cost will vary, but it is an investment in the credibility and long-term growth of your brand. If you are thinking about starting this process, it helps to talk with an experienced partner like Univate Solutions. Their team can walk you through what’s involved, estimate realistic costs, and help you get certified smoothly so you can focus on growing your business with confidence. Get a personalized quote today. Reach out to Univate Solutions: [email protected]
0 notes
Text
Can Generative AI Secure Your Business? Use Cases & Threats You Should
As businesses embrace digital transformation, Generative AI in cybersecurity has become both a promising defense tool and a potential security concern. From creating synthetic data to automating threat detection, generative AI is redefining how organizations think about risk, resilience, and recovery in 2025.

But is it all good news? Or are there hidden threats that decision-makers must understand before deploying generative AI into mission-critical systems?
This blog explores both sides — how generative AI can secure your business and where it could expose you to new cyber threats.
What Is Generative AI and Why Is It Relevant in Cybersecurity?
Generative AI refers to machine learning models that can create new content — text, images, code, or data — by learning from large datasets. These models, like ChatGPT, DALL·E, and Google Gemini, are designed to generate outputs that mimic human-like creativity.
In the cybersecurity domain, generative AI can help in:
Simulating cyberattacks to test defenses Automating threat report generation
Creating synthetic datasets for training security tools
Detecting unusual behavior patterns in large networks
Its ability to learn and adapt makes it a powerful tool in both offense and defense — which is why it's under the microscope of CISOs and tech leaders in 2025.
Top AI Security Use Cases for Businesses
1. AI-Powered Threat Detection & Response
AI Security Use Cases are rapidly evolving, with AI systems now able to recognize anomalies across devices, logs, and network traffic in real time. Tools like Microsoft Defender and CrowdStrike already leverage these use cases to detect zero-day vulnerabilities and identify behavioral attacks before they escalate.
2. Automated Phishing Detection
Generative AI can be trained to identify phishing emails, fake websites, and social engineering attempts by scanning language patterns, domains, and sender behavior.
3. Synthetic Data Generation for Training
Companies can now use AI to generate synthetic attack data that mimics real-world threats — helping improve machine learning models without exposing real customer data.
4. AI Chatbots for Security Operations (SecOps)
AI-driven virtual assistants can help security analysts triage incidents, provide guidance, and even auto-patch systems based on past events.
Top AI Cyber Threats in 2025
While the benefits are real, so are the risks. Let’s explore the major AI cyber threats 2025 that businesses must watch:
1. AI-Generated Phishing & Social Engineering
Attackers now use generative AI to craft highly convincing phishing emails, deepfake voices, and fake social media profiles — making traditional spam filters less effective.
2. Malicious Code Generation
Tools like ChatGPT and Copilot can be exploited to write malware, ransomware scripts, or exploit code — even unintentionally — making cybercrime faster and cheaper.
3. Model Poisoning & Data Leakage
If not secured properly, attackers can inject harmful data into AI training sets, altering model behavior. There's also a risk of AI tools unintentionally leaking sensitive internal data.
4. Overreliance on AI for Critical Decisions
When organizations delegate too many decisions to AI — like access control or fraud detection — it creates blind spots. False positives or missed threats can go undetected.
Is Generative AI Safe for Business?
This is the big question on every CEO and CTO's mind in 2025.
The answer? It depends on how you implement it. Generative AI is safe — and even beneficial — if properly secured, monitored, and used with clear governance.
Here's how to ensure safe adoption:
Use enterprise-grade AI platforms with built-in security
Regularly audit your AI models and datasets
Apply ethical AI practices (explainability, fairness, bias checks)
Keep human decision-makers in the loop
Partner with experienced AI and cybersecurity consultants
Best Practices to Secure Generative AI Systems
To use generative AI securely, train your team on AI risks and limit access to sensitive tools. Monitor AI inputs and outputs to avoid misuse or prompt attacks. Secure your APIs and cloud endpoints, and run regular red-teaming exercises to test for vulnerabilities. These steps help ensure your AI systems stay safe and reliable.
Conclusion
There’s no doubt that generative AI is shaping the future of cybersecurity — for both good and bad. From improving threat detection to creating new forms of cybercrime, its impact is massive and growing fast.
The key to staying secure in 2025 is to embrace AI strategically, understand its risks, and apply the right controls.
Whether you’re just exploring AI or ready to deploy it across your business, now is the time to act. Build internal awareness, upgrade your systems, and most importantly — work with experts who understand both AI and security.
If you're wondering, "Is generative AI safe for business?" — the answer is yes, if you're proactive, not reactive.
Ready to explore secure AI integration for your business?
Contact Appson Technologies today for a free AI security consultation.
Original Source: https://bit.ly/450FXIv
#Generative AI in Cybersecurity#AI Security Use Cases#AI Cyber Threats 2025#Is Generative AI Safe for Business
0 notes
Text
Boost Your Commercial Kitchen with High-Quality Eksponeringsdisk and Elektrisk Flatgrill from Gastro Line
Introduction: Power Your Food Business with Premium Equipment
Running a successful food business in Norway requires more than just great recipes—it demands efficient, reliable, and well-designed kitchen equipment. Whether you’re managing a restaurant, café, food truck, or hotel buffet, the right tools make all the difference in speed, presentation, and customer satisfaction.
At Gastro Line, we specialize in supplying world-class commercial kitchen equipment tailored to meet the unique needs of the HoReCa (Hotel, Restaurant, Catering) industry. From the visually appealing Eksponeringsdisk (display counters) to high-performance Elektrisk Flatgrill (electric flat grills), we offer everything your kitchen needs to operate at peak performance.
Why Quality Kitchen Equipment Matters in the Food Industry
The food service industry is fast-paced and highly competitive. To stay ahead, you need equipment that:
Enhances workflow and reduces preparation time
Delivers consistent cooking results
Improves food presentation and customer experience
Complies with hygiene and safety regulations
With Gastro Line, you get robust, energy-efficient, and beautifully designed appliances that make your kitchen a reliable asset, not a liability.
Eksponeringsdisk – Show Off Your Food with Style and Functionality
What is an Eksponeringsdisk?
An Eksponeringsdisk, or display counter, is essential for presenting ready-to-eat or pre-prepared items such as baked goods, salads, cold cuts, desserts, and more. These counters are commonly used in bakeries, buffets, supermarkets, and cafés.
Gastro Line’s Eksponeringsdisk collection combines elegant design with top-tier functionality, making sure your food looks fresh, appetizing, and well-organized at all times.
Features of Gastro Line Eksponeringsdisk
Attractive and Modern Design
With sleek glass and stainless steel finishes, our display counters elevate the look of your food section, attracting more customers.
Temperature Control
Whether you need chilled, ambient, or heated displays, we offer options that keep your food at optimal serving temperatures.
LED Lighting
High-quality LED lighting enhances product visibility while consuming less energy.
Customizable Sizes and Layouts
From compact counters to large, multi-section units, Gastro Line offers customization to suit your space and requirements.
Easy Maintenance
Built for high-volume use with easy-to-clean surfaces and accessible components for daily maintenance.
Benefits of Investing in a High-Quality Eksponeringsdisk
Boosts Sales – An inviting food display encourages impulse purchases.
Reduces Waste – Keeps food at the correct temperature and humidity, increasing shelf life.
Professional Image – A sleek and hygienic display reflects your brand's commitment to quality.
Whether you run a self-service buffet in Oslo or a takeaway deli in Bergen, an Eksponeringsdisk from Gastro Line is a valuable investment for both food safety and customer appeal.
Elektrisk Flatgrill – Efficiency and Versatility for Every Kitchen
What is an Elektrisk Flatgrill?
An Elektrisk Flatgrill, or electric flat grill, is a must-have for any commercial kitchen needing fast, uniform cooking. Ideal for grilling burgers, fish, vegetables, eggs, and more, these grills are known for their versatility and ease of use.
At Gastro Line, our Elektrisk Flatgrill units are built with durable materials, smart features, and safety mechanisms, making them a reliable partner in busy kitchen environments.
Features of Gastro Line Elektrisk Flatgrill
Fast and Even Heating
High-efficiency heating elements ensure your grill is ready to use quickly and cooks food evenly across the entire surface.
Stainless Steel Construction
Durable, rust-proof, and hygienic—perfect for high-demand kitchens.
Precise Temperature Control
Adjustable thermostats allow precise control for different cooking needs.
Fat Drainage System
Integrated drainage and removable trays make grease management easy, supporting a cleaner cooking area.
Compact and Countertop-Friendly
Ideal for both large commercial kitchens and small mobile units or kiosks.
Advantages of Using an Elektrisk Flatgrill
Quick Turnaround – Perfect for high-volume environments where speed is key.
Energy-Efficient – Uses electricity efficiently, reducing overall kitchen energy consumption.
Multifunctional – Cook multiple items at once, from breakfast to dinner menus.
Safe Operation – Comes with thermal cut-off and heat-resistant handles for added safety.
If you’re running a burger joint in Trondheim or a seaside café in Stavanger, an Elektrisk Flatgrill from Gastro Line ensures consistently delicious results every time.
Why Choose Gastro Line?
Gastro Line is one of Norway’s most trusted suppliers of professional kitchen equipment. Here’s why our clients in the food industry choose us:
Quality You Can Trust
We partner with leading European manufacturers to deliver equipment that lasts—built for daily, heavy-duty commercial use.
Wide Product Range
From Eksponeringsdisk and Elektrisk Flatgrill to ovens, refrigerators, and prep tables—we’re a one-stop solution for all your kitchen needs.
Installation & Maintenance Support
Our technical team helps with setup, staff training, and ongoing maintenance.
Serving All of Norway
No matter where your business is located—Oslo, Bergen, Trondheim, or elsewhere—we deliver nationwide with quick turnaround times.
Customer Satisfaction
With hundreds of satisfied clients, Gastro Line is a name synonymous with reliability and service.
Customer Testimonials
Gastro Line’s display counters transformed our buffet layout. Not only do they keep food fresh, but they also add to our restaurant’s aesthetic appeal.” Henrik L., Restaurant Owner, Oslo
The electric flat grill we bought last year still works like new. It’s efficient, easy to clean, and perfect for our fast-paced kitchen.” Amira K., Café Manager, Stavanger
Choosing the Right Equipment for Your Business
When investing in commercial kitchen equipment, consider:
Your Menu Needs – What foods will you be displaying or cooking?
Kitchen Space – Choose compact or large-scale models based on your space.
Energy Efficiency – Lower utility bills with energy-efficient models.
Ease of Use – Intuitive controls save training time and reduce errors.
Compliance – Make sure the equipment meets Norway’s food safety and hygiene standards.
With Gastro Line, you don’t just buy a product—you gain a long-term kitchen partner committed to your success.
Final Thoughts: Elevate Your Food Service Business with Gastro Line
In the dynamic world of food service, performance, hygiene, and presentation are everything. Investing in a top-quality Eksponeringsdisk can dramatically improve customer experience, while an Elektrisk Flatgrill can streamline your kitchen operations and enhance food quality.
Gastro Line brings the best of both worlds—elegance and efficiency—with a wide range of products designed to meet the real-world needs of commercial kitchens across Norway.
0 notes
Text
Achieve Scalable Growth with SixLakes Consulting NetSuite Services
It's no secret that especially when juggling several systems and expanding corporate demands, digital transformation can seem daunting. Expert advice becomes not only useful but really necessary in this situation. SixLakes Consulting, a firm renowned for its thorough knowledge of enterprise resource planning solutions, is at the core of that assistance. NetSuite partner assistance is among the most powerful technologies companies are using nowadays. Incorporating this into processes gives companies access to a flexible platform that changes financial management, visibility, and workflow.
The significance of industry knowledge in ERP installation
Selecting the appropriate implementation partner depends on their capacity to fit solutions to your particular corporate setting. By applying decades of industry-spanning knowledge to every project, SixLakes Consulting stands apart in this field. Their staff avoids using universal templates. Rather, they examine existing processes and create tailored systems to match your particular objectives. Implementation is more than simply software for businesses looking for a NetSuite partner; hence, this is really important. It's about how effectively the product fits with your people, your goals, and your processes.

Designed for scalable success, customisation and flexibility
Every company is at a distinct point in its path. Some are quickly expanding; others are streamlining existing processes. SixLakes Consulting knows these variations and provides flexible solutions to fit you where you stand. Their selection of packages assurances that businesses of all sizes may use NetSuite's capability. Expert customisation and adaptable choices will let you not only use products effectively but also develop them as your company expands. Including a NetSuite partner into your long-term plan promises your ERP system can expand with business goals rather than in opposition to them.
A track record of demonstrable success in NetSuite consulting
Results count, and this is where SixLakes Consulting really shines. After deployment, their customers regularly say more efficiency, better data quality, and enhanced decision-making capacity. Whether your financial reporting, inventory control, or customer engagement, strategic NetSuite consulting helps you to maximize the value from every function. Companies gain from knowledge that drives more intelligent decisions and scalable changes. This degree of influence indicates that, beyond implementation, it is the knowledge of how to utilize NetSuite that has long-term effects.
Continuous assistance for changing company demands
Neither the technology nor the issues businesses encounter is fixed. Continuous NetSuite consulting is therefore fundamental to the services SixLakes Consulting offers. They stick with you through every version update, integration extension, and business change; they don't just implement and walk away. Your system is certain to remain in line with your requirements and to be optimized for performance, dependability, and expansion by this long-term relationship. Their ongoing participation gives leaders piece of mind so they may concentrate on strategy while professionals handle system integrity.
The reasons long-term cooperation generates long-term benefit
What distinguishes SixLakes Consulting from others is not just their technical expertise but also their commitment to building genuine alliances. They see every customer connection as a cooperative road. Their emphasis is on developing trust, making impact, and providing constant value from the initial call to years down the road. For businesses hoping to maximize their NetSuite partnership, this relationship-driven strategy will be crucial. Its assurances you have a responsive staff that knows not just your system but also your larger success vision.
Conclusion
Whether your business is looking for process optimization or system transformation, working with a qualified and knowledgeable team will improve your whole operation. Ready to change via NetSuite partner cooperation and ongoing NetSuite consulting knowledge, SixLakes Consulting is a top option for companies looking for adaptable packages, industry-informed tactics, and proactive assistance. Find out more about how SixLakes Consulting can enable you to achieve long-term development and efficiency.
0 notes
Text
Electric Blockout Blinds: Smart Comfort and Privacy for Modern Australian Homes

As homes become smarter and lifestyles more dynamic, Australians are increasingly turning to automation for everyday convenience. From climate control to lighting and security, the evolution of residential design now includes motorised window coverings—and one of the most practical upgrades available is electric blockout blinds.
These versatile blinds provide a modern solution for homeowners who want to manage natural light, heat, privacy, and style with the push of a button or a scheduled timer. Whether you're retrofitting an existing property or building new, electric blockout blinds are a seamless way to enhance energy efficiency and interior comfort year-round.
What Are Electric Blockout Blinds?
Electric blockout blinds combine the privacy and light-blocking capabilities of traditional blackout window coverings with the convenience of motorised control. They are powered by a motor—either wired into your home’s electrical system or battery-operated—and can be controlled via remote, smartphone app, wall switch, or even integrated into your smart home system.
Unlike standard blinds, these motorised versions can be programmed to operate automatically based on time of day or room temperature, making them ideal for energy savings, improved sleep, and modern aesthetics.
Professionals such as electric blockout blinds by Central Coast Shutters Blinds & Awnings offer a wide range of motorised solutions suited to homes and commercial spaces across coastal and suburban NSW.
Why Choose Electric Blockout Blinds?
There are several compelling reasons to invest in electric blockout blinds:
Total Light Control: Perfect for shift workers, nurseries, or media rooms where darkness is essential during daylight hours.
Energy Efficiency: Reduce reliance on heating and cooling by insulating against sun and heat in summer and retaining warmth in winter.
Privacy On Demand: Lower blinds instantly with your voice or phone for instant seclusion—no cords, pulleys, or interruptions needed.
Child and Pet Safety: No dangling cords reduces risks, especially in family homes.
Luxury and Accessibility: Adds a high-end finish and convenience for homeowners of all ages, especially beneficial for those with mobility challenges.
In coastal areas like Gosford or Terrigal, where afternoon sun can heat interiors rapidly, motorised blinds help regulate temperatures without over-reliance on air conditioning.
As highlighted in a recent Tumblr article on passive cooling strategies, automated shading is among the most efficient and low-maintenance ways to regulate home climate while reducing energy bills.
Integration with Home Automation Systems
Electric blinds are no longer standalone upgrades—they’re often integrated with home automation platforms such as Google Home, Amazon Alexa, or Apple HomeKit. This allows homeowners to:
Schedule blinds to rise with the sun and lower at dusk
Trigger blinds based on room temperature or lighting conditions
Control multiple blinds at once, including in hard-to-reach areas
Set scenes (e.g. “Movie Mode” that dims lights and closes blinds simultaneously)
You can even adjust your blinds while away from home—ensuring privacy, reducing sun damage to interiors, and maintaining a lived-in look for security.
For those wanting a truly connected lifestyle, Central Coast Shutters Blinds & Awnings are your go-to experts for electric blockout blinds and offer solutions that seamlessly interface with leading smart home brands.
Materials, Styles, and Customisation Options
When it comes to style, electric blockout blinds don’t compromise. They’re available in a wide range of fabrics, colours, and finishes to suit every décor—whether your home is minimalist coastal, contemporary urban, or timeless traditional.
Some key options include:
Textured weaves or smooth finishes
Neutral shades for a sleek, understated look
Bold hues or prints for a statement feature
Dual roller systems offering both sheer and blockout layers in one setup
The blockout layer is typically made from densely woven or coated fabric designed to prevent any light penetration, ideal for bedrooms, home theatres, or any space requiring total darkness.
Custom-fit installations ensure edge-to-edge coverage and smooth operation, even in irregularly shaped windows.
A recent Tumblr feature on interior trends for 2024 highlights that smart blinds in neutral colours are rapidly becoming a staple in energy-efficient renovations and design-led homes across Australia.
Are Electric Blockout Blinds Right for Every Room?
While these blinds are highly versatile, certain spaces benefit more from their functionality:
Bedrooms: Improve sleep quality by ensuring total darkness
Living Areas: Control glare and heat while maintaining aesthetic flow
Home Theatres: Create an immersive viewing experience without reflections
Offices or Studios: Prevent screen glare for productivity and comfort
North or west-facing rooms: Manage direct sunlight and cooling costs
They are also ideal for high or awkward windows where manual operation is impractical, such as above stairwells or voids.
Installation and Maintenance
Electric blockout blinds are installed by trained professionals who ensure proper alignment, motor placement, and system testing. The installation is generally quick and non-invasive, and depending on the home’s infrastructure, motors may be powered via hard wiring or long-life rechargeable batteries.
Once installed, maintenance is minimal:
Dust or vacuum the surface regularly
Use a damp cloth to wipe away marks
Check battery levels (if not wired) every 6–12 months
Keep remote or app software updated for best performance
With no manual cords or chains, wear-and-tear is significantly reduced, extending the life of the blinds.
Cost Considerations and Long-Term Value
While electric blinds cost more upfront than manual options, the investment may pay for itself through:
Reduced energy bills
Improved resale value
Fewer repairs or replacements
Enhanced daily living convenience
Pricing depends on window size, motor type, fabric, and integration complexity. A consultation with a specialist like Central Coast Shutters Blinds & Awnings may help identify the best solution based on your goals, home structure, and budget.
Some local councils or sustainability programs also offer rebates or incentives for smart energy-saving upgrades, so it’s worth checking if you’re eligible.
Final Thoughts
In a market where comfort, control, and efficiency matter more than ever, electric blockout blinds are more than a style statement—they’re a smart home solution. Whether you're upgrading for functionality, preparing your property for sale, or simply seeking a more comfortable lifestyle, motorised blinds deliver ease, elegance, and long-term performance.For tailored installations and advice, electric blockout blinds by Central Coast Shutters Blinds & Awnings may provide the expertise needed to enhance your home’s liveability and value.
0 notes
Text
Design in Web3: Building the Visual Future of the Decentralized Web
As the internet evolves into its next phase—Web3—design is becoming more important than ever. No longer just a layer of polish, design in the Web3 world serves as a critical connector between decentralized technologies and real-world users. It’s the gateway to adoption, helping everyday people interact with complex systems like blockchain, smart contracts, NFTs, and decentralized finance (DeFi).
At its core, Web3 promises user empowerment, data ownership, and decentralized control. But these promises are only meaningful if users can actually engage with them. That’s where effective design steps in. In this fast-moving digital landscape, design must do more than look good—it must guide, educate, and inspire trust.
Understanding the Role of Design in Web3
In traditional (Web2) applications, users interact through familiar models: logins, dashboards, menus, and notifications. These patterns have been refined over decades. Web3, however, introduces unfamiliar mechanics: connecting wallets instead of logging in, signing blockchain transactions, handling digital assets, and navigating decentralized protocols. All of this can be daunting without intuitive design.
Web3 design bridges the gap between cutting-edge tech and user-friendly interfaces. It makes decentralized apps (dApps) feel as seamless as the platforms people are already used to, while still preserving the unique principles of decentralization and transparency.
Key Characteristics of Good Web3 Design
Designing for Web3 isn’t just about aesthetics—it’s about creating systems that are usable, secure, and inclusive. Here are some key elements that make Web3 design effective:
1. Clarity and Simplicity Blockchain concepts can be intimidating. Interfaces should break down complexity and present clear information. For instance, instead of showing long wallet addresses or technical transaction data, a simplified UI can show human-readable messages and clear status indicators.
2. Trust Through Transparency Since many Web3 platforms involve financial transactions, design must build user confidence. This can include visual cues for safety (like verifying contract addresses), transparent fee displays, and clear explanations of what a transaction entails.
3. Seamless Wallet Integration One of the first steps in using a dApp is connecting a crypto wallet. A good design makes this process easy and informative, showing connection status, wallet addresses, and account details in a non-intrusive way.
4. Responsive and Adaptive Design Web3 users span the globe and access platforms on all kinds of devices. Responsive design ensures mobile users can interact with dApps just as easily as desktop users.
5. Onboarding and User Education Many users are new to Web3. Onboarding flows that explain key concepts (like gas fees or staking) and walk users through first-time tasks help lower the barrier to entry.
Designing for Various Web3 Applications
Different Web3 projects demand different design approaches. Here’s how design adapts across popular use cases:
NFT Platforms: These need gallery-style layouts, strong visuals, and features like minting interfaces and royalty tracking. The emotional connection to art and ownership is a key driver here.
DeFi Platforms: With complex financial tools like lending, borrowing, and liquidity farming, design must prioritize data clarity and intuitive navigation.
DAOs (Decentralized Autonomous Organizations): Governance tools, proposal voting, and treasury dashboards require interfaces that make decision-making accessible and transparent.
Blockchain Games: GameFi and metaverse projects need immersive designs, real-time responsiveness, and seamless wallet-based economies.
The Importance of Working with Experts in Web3 Design
Creating effective designs in Web3 isn’t just about hiring a designer—it’s about working with professionals who understand blockchain mechanics, user psychology, and design systems. This is why many successful projects turn to a web3 web design agency that specializes in the nuances of the decentralized web.
These agencies bring deep experience in both design and blockchain, ensuring that every element of a platform—from color schemes to UX flows—is optimized for clarity, trust, and scalability. They’re up to speed on the latest trends in smart contract interactions, wallet technologies, and multi-chain ecosystems, making them invaluable partners for building long-lasting Web3 products.
Conclusion: Design as the Driver of Web3 Adoption
As Web3 continues to expand, the role of design will only grow more crucial. It's no longer enough to build powerful technology—you must also make it usable, accessible, and visually compelling. Good design is what translates technical complexity into human experience.
Design is the key to onboarding the next million users into Web3. It guides users through their first transaction, helps them feel confident managing digital assets, and encourages them to explore what decentralized technologies can offer. Whether you're building an NFT platform, a DAO, or a DeFi protocol, investing in thoughtful, strategic design will set your project apart in a crowded and competitive space.
In Web3, design isn’t just decoration—it’s the interface of the future.
0 notes