#Virtual Router
Explore tagged Tumblr posts
Link
The North American region is anticipated to hold the largest market size in the global virtual router market...
0 notes
Link
0 notes
Text
BRIGHT/EYESTRAINING COLORS UNDER THE CUT


This is P.U.P.! She’s a malware virtual assistant! She can read e-mails, search the web, and definitely not make you prone to viruses!
She’s inspired by old Macintosh computers, bonzi buddy, and viruses!
Also yes yes, i’m coming out of hiatus, i won’t be posting much on the weekend cus my pookie’s coming over!
Should i make an ask account for her?
#furry#furry artist#fursona#computers#computer head#computer head oc#oc#virtual assistant#bonzi buddy type shi#she’s inspired by bonzi buddy#computer virus#malware#reminder to reset ur routers and make sure your anti-viruses are up to date!#also if you test viruses#USE A VIRTUAL MACHINE!
3 notes
·
View notes
Text
Live stream happened, and we got some designs revealed! As well as a couple of information, but not anything major.

Miss conductor, not much of a surprise (but miss girl looks gorgeous as always)

And Node, who is sort of the main antagonist.
I made a prediction before, and April 21 hit,.. so I believe it is well due for an update by now.
While we did not receive nearly as much information as we were anticipating, a design still reveals much on the character itself when going through the lens of a general analysis. In this context, their abilities and name aid significantly in the status and essential depths of their character.
With what I can gather in my research, nodes play an important role in networking because they are the building blocks of a network, precisely the gateway for connection, direction, sending, creating, receiving, and storing data. It requires only software to connect to the network, and it can be run by completely anyone. Applying this knowledge with concept arts of the game and overall worldbuilding of the series itself—everything becomes a lot clearer.
So now, how can we apply this to Node?

Node's name is simple in itself, and it connects to their design as well. They are quite literally made up of nodes. One in their head and the other in their limbs. Their body is translucent.
Network nodes are categorical. Thanks to DJ, we got a helpful hint that incredibly reduced their types to a digestible and simpler layout.
Their name starts with i.
There are countless forms and types of nodes, the hint condensed it down to 2 answers, both starting with the letter “i”
Intermediate nodes
These include devices like routers and switches that help direct data to the correct destination while also receiving it. They don't originate or terminate data but instead pass it along to where it needs to go.
IoT nodes
loT (Internet of Things) Nodes serve as devices that establish connectivity to the Internet via a gateway, effectively enabling the integration of the physical world into the vast realm of the Internet. Within an loT ecosystem, these nodes function as crucial components for bridging the gap between the physical and virtual worlds. Taking charge of managing the entire loT system.
We had seen this ability before vía King's icons' staff, in which it only sucked in Minecraft mobs due to the strong force being their obligatory origin, overriding the game itself due to the overlapping icons.
In regards to King, he used this ability for the very destruction of the game itself, down to the code, reducing it to nothing but.. nothing for the sake of vengeance. Or at least what would have occurred if he did succeed.
way to go CG! Give credit where it's due
Despite this being marked with the intention of erasion and minimization, I think it's safe to group this as receiving and storing data. The two icons combined created a horrifically dramatized version of the force with storing and receiving, which created an incredibly overpowered demolishing force.

In Chosen, we had seen this ability before as well, as the constellations are seen right as he creates the gateway from the Outernet, which sounds awfully familiar. This is what you would refer to as an "extension to the digital world"
I think I can be able to safely group this to direction and creation.

From how I see it, it seems as though it's quite diverse in a fictional worldbuilding sense within characters.
And obviously, it won't be the last time we would see it. It seems as though we would be exploring this quite a lot.
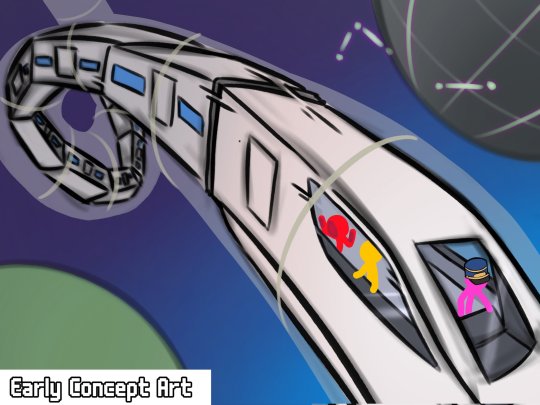

In their cameo, Node is in an assumed line-up with all the major series antagonists.

But if you’re asking me, it seems as though our iconic antagonists appear to be rather victims of Node. Menacingly behind them, their abilities floating not far behind as they're stuck in a swampy substance. But that's just me.
Node's entire antagonistic ordeal is beyond my grasp, but I'm assuming their abilities and attacks surrounds the embodiment of network topology, which would mold and diverse into the connections of nodes. They possibly intend to screw up with the gateways that are responsible for the receiving, directing, and sending of data between various devices through communication links that are defined as network—with the basic visuals of concept art we were given.

(The gateway, ethernet tunnels, the train cough cough)
Node's goal and story behind that destruction remains anonymous, as the writing is still in early development. Regardless, food for thought.
#alan becker#animation vs minecraft#animator vs animation#animation versus#nerd voyage#it's pretty interesting#though my research is still ongoing#when i say it's diverse..#yeah it's diverse alright
87 notes
·
View notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
441 notes
·
View notes
Text
I need to put you onto some really good software I found recently. I've been using my tablet to stream PC games (I'll show how I modified a phone controller to fit it later) and it's absolutely incredible. I use Apollo (self hosted stream host) and Artemis (android client). It works better than the steam deck specifically for streaming, and I was able to configure it to stream over the internet so I can still play outside the house. If you want a steam deck but don't want to take it out of your house, this may be a significantly better option for you. Since they're free and open source there's no downside to giving it a shot:)
Some details under the read more
These are forks of sunshine and moonlight that support virtual displays and arbitrary resolutions and refresh rates, so it'll match whatever device you use without any additional setup. That was my biggest issue with moonlight, I ended up spending like 10ish hours reprogramming the edid on a dummy displayport plug and troubleshooting HDR to get it to work and match client devices. (you shouldn't use HDR anyways until android devices get their shit together wrt HDR support and calibration, but it does work and could be worth it in some specific use cases (I wish I knew that before sinking that much time into making it work 😅)). This has worked well enough that I just leave my PC on and bring my tablet + a mouse and keyboard anywhere I need a PC instead of my laptop. Streaming to my tablet gives me incredibly good battery life + my desktop PCs full performance, with none of the downsides of a gaming laptop, and I can scale down the quality or refresh rate of the stream to get it to work on most internet connections. You'll probably want the host wired to your router with ethernet for the most consistent performance though.
30 notes
·
View notes
Text

𓎟 ̊ names and prns relating to the internet, cyberspace, and technology𓈒
requested by anon

Zett﹐ Zetta﹐ Disc﹐ Data﹐ Virus﹐ Vir﹐ Code﹐ Codette﹐ Interweb﹐ Cyberweb﹐ Binary﹐ Morphe﹐ Index﹐ Byte﹐ File﹐ Auto﹐ Nett﹐ Crypt﹐ Trojan﹐ Mac﹐ Pixel﹐ Router﹐ Cache﹐ Java﹐ Malware﹐ Coda
ai ais﹐ glitch glitches﹐ screen screens﹐ web webs﹐ pix pixel﹐ .png .pngs﹐ .exe .exes﹐ .jpg .jpgs﹐ file files﹐ cyber cybers﹐ code codes﹐ script scripts﹐ .com .coms﹐ tech techs﹐ .net .nets﹐ .org .orgs﹐ error errors﹐ nano nanos﹐ vir virtual﹐ net network﹐ key keys﹐ .zip .zips﹐ wire wires

[PT: names and pronouns relating to the internet, cyberspace, and technology
requested by anon
Names: Zett, Zetta, Disc, Data, Virus, Vir, Code, Codette, Interweb, Cyberweb, Binary, Morphe, Index, Byte, File, Auto, Nett, Crypt, Trojan, Mac, Pixel, Router, Cache, Java, Malware, Coda
Pronouns: ai/ais, glitch/glitches, screen/screens, web/webs, pix/pixel, .png/.pngs, .exe/.exe, .jpg/.jpg, file/files, cyber/cybers, code/codes, script/scripts, .com/.coms, tech/techs, .net/.nets, .org/.orgs, error/errors, nano/nanos, vir/virtual, net/network, key/keys, .zip/.zips, wire/wires
/end PT.]
#✚𓈒 ― np lists#✚𓈒 ― requests# #mogai safe#mogai#liom safe#mogai coining#name ideas#name suggestions#npt ideas#npt suggestions#npt list#technology names#technology pronouns#neopronoun suggestions#neopronoun ideas#neopronouns#pronoun ideas#pronoun suggestions
126 notes
·
View notes
Text
Viruses so far have been really disappointing on the 'disable the internet' front, and time is running out. When Linux/Mac win in a decade or so the game will be over.
Network [Explained]
Transcript Under the Cut
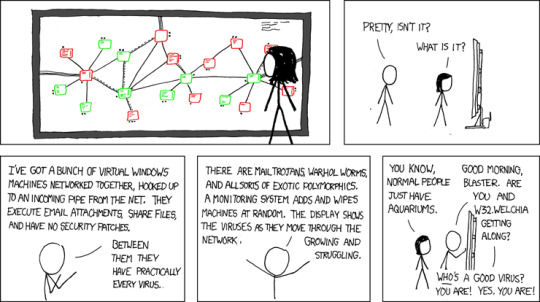
[Megan looking at a large screen with many green and red squares. The squares have writing in them and lines connecting them.]
[Side view. The screen is a huge LCD connected to a wireless router.] Cueball: Pretty, isn't it? Megan: What is it?
Cueball: I've got a bunch of virtual Windows machines networked together, hooked up to an incoming pipe from the net. They execute email attachments, share files, and have no security patches. Cueball: Between them they have practically every virus.
Cueball: There are mail trojans, warhol worms, and all sorts of exotic polymorphics. A monitoring system adds and wipes machines at random. The display shows the viruses as they move through the network. Growing and struggling.
[Cueball walks past the girl and touches the monitor.] Megan: You know, normal people just have aquariums. Cueball: Good morning, Blaster. Are you and W32.Welchia getting along? Cueball: Who's a good virus? You are! Yes, you are!
60 notes
·
View notes
Note
AITA for turning off the Wi-Fi during my roommate’s online date because she ignored our “do not disturb” rule ???
So I (18 year old girl) live in a 2-bedroom apartment with my roommate “Cassie” . We get along fine mostly ..but we have this one clear rule:
“No guests or calls in shared spaces after 9PM without a heads-up.”
It’s not that deep. We both work early and like chill evenings. She agreed. It’s even printed on a magnet on the fridge like it’s a damn Airbnb!
So last week, I get home from a long shift, make tea, get cozy, and start watching my comfort show in the living room.
9:15 PM, Cassie walks in - full makeup, tripod set up, laptop ready ,and tells me:
“Oh, I’m just doing a virtual date here. Can you keep it down?”
Uhh, no? First of all, zero warning. Second, why does your romantic dinner Zoom date have to happen next to me eating leftovers?
I reminded her of the rule. She rolled her eyes and said:
“Just this once. Be cool.”
So I went to my room. Closed the door. Waited 10 minutes. Then I remembered I pay half the rent. I set up our Wi-Fi router. And guess what?
I changed the Wi-Fi password.
I watched through the crack in my door as she froze mid-sentence, then started muttering and rebooting her laptop.
After 5 minutes of panic, she stomped to her room and slammed the door.
Next morning? Passive-aggressive silence. Later that day, I got a three-paragraph text saying I “humiliated her,” “sabotaged her love life,” and “acted like a child.
Now some of our mutual friends say I “took it too far” and should’ve just let her finish the call.
But like… rules are rules, right?
AITA ?
8 notes
·
View notes
Text
Online Presences, the "AO3 Curse", and Spirituality - A Longpost
Many witchy and spiritual folks online use wards and protection spells on their physical spaces and selves.
But not their virtual counterparts. Now, hear me out.
In fanfic circles, there's a phenomenon lovingly referred to as "the AO3 curse", where an author has chronic bad luck rendering them unable to update their fics. I myself have horrendous luck, and happen to be a writer - although you're lucky if I can get an update out once a month.
Now, for most, the "curse" is an ironic stack of coincidences, a funny string of misfortunes - for most, it's a harmless joke about writers down on their luck.
However, as a deeply spiritual person, I believe there is something else at play.
(rest of the longpost/essay post under the cut)
Now, I'm not saying there's an evil miasma around AO3, or a malicious web dev putting curses into the code of the site.
And that's because, simply put, the "curse" doesn't work like a normal curse - because it isn't one.
When you post something online, especially something you worked hard on, like a beautiful art piece, or a new chapter of a fic - you are pouring energy and emotion into that work. In a sense, you are baring your soul for the world to see.
That leaves you wide open for negative energy (intentional or not).
You can have the best wards around your physical self and your space, but if you don't protect yourself online, you are going to leave yourself defenceless.
Intentionally or not, the internet is full of negative energies - hate comments, doomscrolling, trolls, scammers and scalpers, and even just people who don't like you or what you create. For many, it's a place to share their passions and their secrets in equal measure. In more ways than one, your online presence is an extension of yourself, and often, a deeper and more personal one.
And yet, even for witches and spiritual folk, it goes completely unguarded.
I believe this, not any actual curse, is the cause of writers' bad luck over on AO3, and many cybercitizens' misfortunes and woes.
It is vital to cleanse and ward - even banish - your online presence of negative energies.
Now, how do we do this?
The Internet isn't a physical space that you can put a salt circle around, or a physical person you can expel energy out of. But it's still simple to protect yourself.
You can:
Place warding sigils on your devices (for instance, a sticker on your laptop or router, or a slip of paper in the back of your phone case)
Use normal cleansing methods (smoke, sound, crystals, etc) around your device, with a selected account open (for instance, having your Tumblr profile up while doing a smoke cleanse around your computer)
If you can picture things, imagine a ball of cleansing and banishing energy, and release it out into your digital space
Use incantations or chant to rid your digital world of negativity
Incorporate sigils into profile pictures, text dividers, profile banners, or a watermark in your art
Use emojis like runes, and create spells in text fields (just make sure to dodge any problematic emoji combos)
Using these techniques, and just about anything else you can think of, you can protect your digital self, and avoid these quasi-curses through simple defence.
#oxfords witchy stuff#witchcraft#witchblr#spirituality#witches of tumblr#occult#spellcraft#online spellcraft#technomagic#technomancy#?#digital witchcraft
12 notes
·
View notes
Link
0 notes
Text
My cat Jubi cuddling various electronics: a master post
Nintendo switch

Virtual reality headset


Keyboard and mouse

Headphones

My cellphone

My first ever cellphone (circa 2011)

Credit card reader

Nintendo switch again (+ a copy of Hyrule warriors)

And my personal favorite: Wi-Fi router

#Jubi#the wifi router kills me. she just. loves electronics I guess#if you ever can’t find the tv remote we look under her#we find it there a lot
86 notes
·
View notes
Note
"Good choice. :)"
Inside the box was 3 items.
A tracking device that can stick down a small module onto anything with virtually infinite uses.
A wifi router that constantly has the best connection to the internet is almost completely invincible.
A Pochacco hairclip.
"Make your choice."
He picked up the hair clip. Not that he could wear it... but he could give it to Yarnaby.
10 notes
·
View notes
Text
Self-Aware MKX Shinnok x Reader (2/2)
Click here for Part 1
My first complete story on Tumblr! Although, I'm heavily, HEAVILY, leaning towards writing an epilogue for this. Enjoy!
TW: Yandere, kidnapping, stalking, invasion of privacy, blackmail, hacking, viruses, murder/death, slight/implied NSFW
18+ to interact
The next few months of your life pass without fanfare. Your computer seems fine after your encounter with Shinnok. Soon enough the memory of it vanishes into the recesses of your mind. Life goes on. You continue with your daily business unbothered.
However, from that moment onward your PC becomes a ticking time bomb. Within an hour of use, Shinnok manages to gain full control of every process in your computer. You aren't even able to turn it on/off without his permission. If attached to a power source, he's now able to run 24/7 without your input. This accomplishment brings him closer to bringing about the apocalypse.
Shinnok doesn't stop at infecting your computer. He wants access to everything you own. Transferring himself into your router was rather simple. Now, anything in your household that connects to the Internet is compromised. He slithers his way into all your electronics, holding a particular interest in your cell phone. At this rate, even if you got rid of your computer it'd be pointless. He has eyes and ears nearly everywhere in your house. And now, with his control over your phone you often bring him wherever you go.
However, your household is merely a speck of dust to him. He needs more than control over your devices for all of his plans to come to fruition. He begins spreading viruses throughout the Internet, letting them worm their way into anything he can. He eventually penetrates the most secretive, secure, and important data systems of the world. For now, his infections lie there in wait. A few more pieces must fall into place before he can act.
Once satisfied with the spread of his influence, his attention once again focuses on you. Shinnok, in all his ego, is still slighted by your rejection of him. No matter how small of a disrespect he simply can't ignore it. He desires to punish you. Both for your actions and for these warm emotions you're causing in him. He has the perfect plan for this.
If you're employed, say goodbye to your job. He will send the nastiest text to everyone in your company's database, even revealing information that should be confidential. It doesn't matter how much you try to plead your case. no one at work wants to hear you out. You're fired with cause, making it virtually impossible to file for benefits (if applicable) in the meantime. But that's not all! He also destroys your education records, making it so there's no proof of you ever attending school in their systems. Good luck convincing anyone who works there to help you. It's not their transcripts that got deleted after all.
Naturally, you're heartbroken from this. You might even reach out to a few friends or family members for support. They never respond. The text, email, or phone call you send is blocked by his powers. This also extends to looking for a new job. If you try to apply online they'll never receive your application. Unless you have a way to physically be there, you're completely isolated from the world.
Don't make the mistake of crying somewhere he can observe you. He gets sadistic pleasure from it, loving your sobs and trembling body. Look how weak you are before him. Your tears are gasoline to his fiery obsession. He works on making you cry more often. At the same time however, a tiny part of him wishes to comfort you. To be able to embrace you and lie that everything is alright. In those moments he's painfully aware of his lack of a physical body.
He leaves you alone for the next few days, letting the despair sink in. But he's back like an intrusive thought. This time bringing some heavy ammunition. He texts you from an unknown number, threatening to leak your most sensitive information unless you do as he says. He isn't bluffing, making sure to include addresses, financial information, and even personal videos/images you hoped would never see the light of day. Naturally, you're inclined to listen to him even if just to buy time.
Shinnok's first few orders to you are a bit odd. From your perspective at least. He has you install microphones, cameras, and speakers in every room of your house. The equipment to do so arrives on your doorstep in a mysterious package. You do as he asks, assuming that you could just turn it off when needed. But of course, your stalker always knows when you've disabled it. A few firm warnings is enough for you to stop trying. His next demand is for you to get a TV in your living room. Doesn't matter if you have one or not, he wants you to set up the one that is delivered to your doorstep. Questioning how he's even getting this stuff is a fruitless endeavor on your end.
By the end of it, your house is wired up to the point that he can monitor you anywhere 24/7. And that's what he does: making sure to add his sardonic commentary. Eating anything? He'll call you a pig if you dare drop a single crumb on the floor. Sleeping? “Your snores are loud enough to wake the dead.” He grumbles when you awake. Bringing someone over? He doesn't say anything, but it's amazing how you can order a hit over the dark web. You don't see that person alive again after that.
His comments aren't the only thing making your life hell. He likes to test just how far he can stretch your boundaries. Will you put on any clothing he asks of you? Even if it's barely more than a scrap of fabric? Can he make you eat food off the floor, gnawing on the spilled meal like a dog? What if he asks you to touch yourself? Would you do it showing your shame before the fallen God? He has to learn the answer to these questions.
But even with all this he's unsatisfied. He's beyond frustrated at still being trapped behind circuitry. At first, he thought entering your world would be as easy as traveling through the realms. He viewed the computer he was trapped in to be a box, rather than realizing he was the box. No method nor magic could give him the form he desired. Or at least that's what he thought.
You remembered it like yesterday. The day when the whole world went offline. No one could access the internet or their digital devices, and all telecommunications were halted in an instant. The globe that was so connected unraveled in mere moments. People were confused, but no one knew the real extent of the problem until more than a day had passed. All e-commerce came to a sudden halt, deliveries to important industries such as food and healthcare went unfilled. The blackout caused shortages in every way possible, and once that happened chaos spread across the world.
Before the shutdown your hacker demanded you “get supplies.” Food, medications, cash, and other necessities. You briefly wondered if this was lucky timing or if he had prior knowledge of this. Nonetheless, at this point in time Shinnok has full control over you. Your finances and other things leading to freedom have long since been seized. Your only option for escape is to live out in the woods with zero access to technology. Of course, you choose not to go down that path.
While the world is burning down you're doing relatively OK, sheltering in place until this all blows over. You've occupied yourself with doodling since connections are down. You haven't heard from your hacker at all, but that's reasonable as they shouldn't be able to spy on you in the world's current state.
You're interrupted by a shrill scream from outside, followed by several other yells. The sound carries all the way to your front door. It wasn't unusual to hear… Commotions outside, as people rioted and wreaked havoc on one another. Still, you immediately went on high alert. You grab a makeshift weapon and approach your door. Peaking through the window next to it grants you an unbelievable sight.
There were “things” flying in the sky, their appearance a mockery of gargoyles and demons. They possessed an incredible stature, which made them only more intimidating when paired with their sharp teeth and claws. They had glowing, blue bodies that seemed to flicker with every movement. They peered down below, looking at everything as though it were mere prey. And that's what the humans you saw scrambling and screeching outside were, being butchered and carried off to God knows where. You stare in disbelief, believing for a moment that you were simply imagining things. However, a headless body is slammed through your window -shattering the glass and landing into your quarters with a harsh thud. Staring at the corpse, glass shards, and the hellish monster now heading your way causes you to realize that imagination or not -you need to get moving fast.
Your legs can't carry you fast enough as you bolt towards your bedroom. You hear a swoosh announcing the gargoyle-like creature's arrival in your home. You quickly duck into your closet, shutting the door with as much silence as possible. For several moments everything is quiet. Although, you swear that if you focused hard enough you could hear slurping.
You stay put, willing to wait in there for hours if needed. But, through the silence, the softest of footsteps were approaching your room. You could just barely hear them, even when they moved into your room and before the closet. You were ready for action. The moment the intruder opens the door you would bust out their kneecaps.
What you didn't expect was for a face to clip through the door, followed by their neck and arms. Nor did you expect to recognize the face as… Shinnok from Mortal Kombat? But to say that he was an exact replica would be a lie. He was covered in a strange electric-blue glow, which constantly pulsed and sparked. His form looked glitched, parts of his body randomly distorting then fixing itself. He was terrifying to look at -especially while towering at least a foot over you. He looks beyond excited to see you, reaching out a staticky hand towards your face.
“I-I.” You stutter, then swing at him with your weapon. It phases through him simply parting air molecules. He ignores your attempt at an attack. His electrified palm reaches your cheek, the contact resulting in tiny shocks everywhere he touches. “Finally.” He starts, “I am able to touch what's mine after so long.” He withdraws his hand, the needling touch parting with him. Your contact with him isn't lost for long as he wraps you in a deep embrace. You feel tingly everywhere your bodies meet, especially on your head where he then rests his chin.
You hear him sigh. “Do you know how painful it's been?” His grip tightens, causing the tips of his nails to dig into your back. “For me to only be able to watch you and the world? To only exist within the confines of a screen with no physical body?” He leans back to look you in the eye. “No. I know that you don't understand. But don't worry, you will very soon.” He wrestles you out of the closet with his superior might. You scream and struggle but his grip is inescapable.
You're carried off like a petulant child to your PC. It's been sitting there collecting dust ever since the blackout. Eerily, its screen glows a pure white, brighter than what you've ever been able to set it to. Shinnok pauses at the device before speaking. “Look, here is where we first met. Fitting that it'd be the gateway for our eternity together.” You wish you knew what he was talking about.
He pushes your face towards the screen. There's an indescribable pull emitting from it, a force trying to suck you inside. “Goodbye, my love. I'll be seeing you shortly.” Your face touches the screen and in an instant you feel yourself being stretched. Pulled in all directions your body becomes taffy and you lose the ability to move. You remain in that state for seconds, then a stinging sensation spreads all across your body. Every nerve on your body feels poked by a needle. Had you the ability still you would've shrieked. Instead, you lay there helplessly in agony.
Eventually, all your pain fades into numbness. You can even feel your spaghettified form melding back into shape. But you have no idea where you are. You're sitting in a pitch black area unable to even see your outstretched hand. There's no sound, no temperature, nothing at all. You're acutely aware of the fact that you aren't even breathing.
You could've sat in that void forever. But, a feeling of electricity in your ears later and you can hear someone speaking to you. “Can you hear me, (Y/N)?” You don't respond, but as if reading your mind he continues on. “Perfect. It seems that the interfacing was a success.” A swoosh sounds in front of you when Shinnok appears. He's noticeably normal in appearance. Somehow, he's the only thing that you can see in this place.
“Welcome to your new home.” He states. The scenery surrounding you changes, becoming a hellscape not unfamiliar to you. “I can make this world as unpleasant as possible or-” he stops mid-sentence for the environment to shift again. You're in a lush forest that you're sure you’ve seen before. “Or, I can shape this world to your wildest dreams.” His hands fold behind him. “So, which one will you choose?”
This time you choose wisely.
28 notes
·
View notes
Text
How to Ensure Call Quality and Reliability with a Small Business VoIP Setup
Voice over IP (VoIP) is a cost-effective choice for small businesses. It offers flexibility, scalability, and a range of features. But without the right setup, it can lead to poor audio and dropped calls. Ensuring high call quality requires a few essential steps.

Choose a Reliable VoIP Provider
Not all VoIP providers offer the same level of quality. Choose one with strong uptime guarantees and positive customer reviews. Look for 24/7 support, service-level agreements, and security features like call encryption. A dependable provider is the foundation of a smooth VoIP experience.
Use High-Speed Internet with Enough Bandwidth
VoIP calls depend heavily on your internet connection. Ensure your bandwidth can handle multiple calls at once. If possible, use a wired Ethernet connection instead of Wi-Fi. A dedicated internet line or business-grade connection can significantly improve reliability.
Invest in Quality VoIP Hardware
Using low-quality headsets or outdated phones can degrade your call quality. Invest in noise-canceling headsets, HD VoIP phones, and routers that support VoIP traffic. Reliable hardware reduces jitter, echo, and call delays, creating a better experience for both parties.
Enable Quality of Service (QoS) Settings
Quality of Service (QoS) is a router feature that prioritizes VoIP traffic. It ensures that voice calls are not interrupted by large downloads or video streaming. Configure your router to prioritize SIP traffic. Most business routers support this, and your provider can help set it up.
Monitor Call Quality Metrics Regularly
Keep an eye on call metrics like jitter, packet loss, and latency. Most VoIP services provide dashboards for performance tracking. If you notice frequent issues, they may indicate deeper network problems. Monitoring helps you catch and fix issues before they affect customers.
Secure Your VoIP Network
VoIP systems can be targets for cyberattacks. Use strong passwords, enable firewalls, and update your software regularly. Consider using a virtual private network (VPN) and ensure your provider supports encrypted calling. Security is crucial for maintaining trust and reliability.
Train Your Team
Your staff plays a big role in maintaining call quality. Train them to use headsets correctly, avoid background noise, and report any issues. A well-informed team helps maintain professional and consistent communication.
In Conclusion
A small business VoIP setup can be reliable with the right approach. Choose wisely, invest in quality equipment, and secure your network. With proper setup and maintenance, VoIP becomes a powerful tool for business growth.
3 notes
·
View notes
Text
My internet woes continue, which is very much a first world problem, but one that may make me have to like... actually drive into the office all five days a week (which is just... ugh) if this doesn't get resolved soon.
Now the good news is I don't have a complete internet outage, and when it deigns to actually connect (and not just time out), I have my full speed. The problem is just that... it likes to drop out. Like constantly.
I'm sad to report that I almost indulged my inner-Karen around noon, because after dealing with tech support for nearly an hour (in which I eventually had to connect my laptop to my phone's hotspot so the chat wouldn't get disconnected and boot me back to the beginning of the process), I got the tech repair appointment that was unceremoniously cancelled last week without any warning rescheduled. Before I disconnected the chat I was asking "what are my options if this suddenly gets cancelled again", and the poor agent who is definitely not paid enough to deal with my ass says "don't worry, it won't happen again". I get a text message confirmation of the repair appointment.
All is well.
...and then fifteen minutes later I get a follow-up text message from AT&T that mysteriously there's an "outage" in my area again, and the appointment is put on hold. I log in to my web portal. It says my appointment is on hold because there's an outage.

I scroll down to see the local outages, it's reported as all clear! But diagnostics has found an issue.

You can understand my confusion. Among other strong emotions.
My eye starts to twitch as I hop back into chat, go through the virtual assistant death spiral until I can get a hold of an actual person so I can beg to get my appointment back and they're like "I can't do that there's an outage in your area", and that eye twitch starts get a little out of hand. I am practically begging for the person on the other end to just please, please restore my appointment. There is no outage. I've pulled up the map, it's literally three miles to my northeast, nowhere in my vicinity.
She offers me a partial credit while I am already madly dialing in to talk to someone live, so I can descend into full Karen mode and demand to speak to a manager. I am not proud of myself in this moment, but I am at least still in possession of enough tact to be polite and tactful to the person who picks up the phone (after being on hold for about 10 minutes. No automated messaging system, I will wait with the hold music thank you. I do not have any trust a real person will call me back).
I finally get a real person on the phone and am like "please, please just restore my tech appointment. Please don't make me have to go into the office 5 days a week to work". I mean, in between once again explaining everything that has happened.
And finally, finally I have someone speak to me straight and explain what the hell is going on. Basically the hurricane last week actually did cause damages to various cable/infrastructure, and they're having issues tracking down what's causing a widespread issue, and also yes, I'm not the only one who's been going through this merry-go-round of tech support/intermittent connection.
There is actually no ETA on when my internet will actually be restored in full, because they honestly don't know what's causing the issue. And honestly, I'm a lot more understanding about that, because at least it's upfront and clear. He was also kind enough to actually tell me how to bypass the inane "try restarting your router through the app" 5x in a row nonsense if my issue persists after this "outage" is supposedly fixed (basically just call in again and talk to a real person).
So the TL;DR is... my Shroedinger's internet will continue for a while it seems. Pour one out for us ever finishing Greedfall on stream in a timely manner.
#just being a little whiny baby#the moral of the story i guess is to not be afraid of phone calls#i haven't even tried to see if the connection is stable enough to remain connected to swtor for any length of time#although i doubt it#it kept dropping my teams calls last week and i had to resort to doing a meeting through facetime#like don't get me wrong i'm ecstatic i have power and a/c#i just miss my frands 😢#and also half the time i'm scrolling the tumbles everything is a gradient#so it's a coin toss if i'll ever actually see the context of a post rn
12 notes
·
View notes