#VAPT Tools
Explore tagged Tumblr posts
Text
Power of VAPT Services with Securium Solutions
In today's digital landscape, where the risk of cyber threats is ever-present, safeguarding your organization's sensitive data and digital assets is paramount. That's where VAPT (Vulnerability Assessment and Penetration Testing) comes into play. As a leading VAPT company, Securium Solutions offers top-notch VAPT services that empower businesses to identify and mitigate potential vulnerabilities before they are exploited by malicious actors.
VAPT services encompass a comprehensive approach to cybersecurity, combining meticulous Vulnerability Assessment and in-depth Penetration Testing. This dynamic duo allows Securium Solutions to not only pinpoint weaknesses within your systems but also simulate real-world attacks to gauge their actual impact.
Are you curious about VAPT and its significance? Our experts at Securium Solutions have you covered. Whether you're looking for an in-depth explanation of VAPT, seeking answers to common VAPT interview questions, or exploring the array of VAPT tools, we provide a wealth of resources to satisfy your curiosity.
With an impressive track record, Securium Solutions employs cutting-edge VAPT tools and methodologies to ensure a robust defense against cyber threats. Our VAPT services are tailored to your specific needs, whether you're a small business or a large enterprise.
In the dynamic realm of cybersecurity, staying ahead of threats is imperative. Securium Solutions' VAPT services offer a proactive and strategic approach to protect your digital assets. Partner with us to fortify your defenses and ensure a secure digital future.
#VAPT#VAPTServices#VAPT Company#VAPT Interview Questions#Vulnerability Assessment and Penetration Testing#VAPT Testing#VAPT Tools#VAPT Service
0 notes
Text
Cyber Security Company in Noida: Protect Your Business with CSG Technosol
In an era where digital threats are growing more complex by the day, businesses can no longer afford to ignore cybersecurity. Whether you're a startup or a large enterprise, protecting your data, networks, and digital assets is critical. That’s where the role of a professional cyber security company in Noida comes in. If you’re searching for trusted, end-to-end cyber protection, CSG Technosol is your go-to cybersecurity partner.
Noida, being a fast-emerging tech hub, demands top-tier cyber defense—and CSG Technosol delivers exactly that.
Why Cybersecurity is Essential in Today’s Digital Economy
The shift to cloud-based platforms, remote work, and digital payments has made businesses more vulnerable than ever. From phishing attacks to ransomware, cybercriminals exploit every weak link. Without a proper cybersecurity framework in place, companies risk losing customer trust, confidential data, and even revenue.
Key Cyber Threats Businesses Face Today:
Malware and ransomware attacks
Phishing and social engineering
DDoS (Distributed Denial of Service) attacks
Data breaches and identity theft
Insider threats and misconfigurations
For businesses operating in Noida and beyond, having a trusted cyber security company in Noida ensures these risks are managed and mitigated proactively.
Why Choose a Cyber Security Company in Noida?
Noida is not just a thriving IT destination, but also a growing center for innovation and enterprise. Companies here—ranging from fintech to healthcare—need reliable security partners who understand both local challenges and global standards.
Benefits of Choosing a Noida-Based Cybersecurity Firm:
Faster Response Time: On-ground teams ensure quick action
Cost-Effective Packages: Local pricing without compromising on quality
Scalable Services: Adaptable to startups, SMEs, and large enterprises
Proximity to NCR: Strategic location for businesses across Delhi-NCR
CSG Technosol: Top Cyber Security Company in Noida
At CSG Technosol, we specialize in delivering cutting-edge cybersecurity services to secure your digital infrastructure. With over a decade of experience, our team helps businesses stay compliant, secure, and prepared for any cyber threat.
Whether you're looking to secure your network, conduct a security audit, or protect against ransomware, CSG Technosol in Noida has you covered.
Our Comprehensive Cybersecurity Services
1. Vulnerability Assessment and Penetration Testing (VAPT)
We identify weak points in your systems and simulate real-world attacks to test your organization’s defense.
2. Endpoint Security
Protects all connected devices in your network from malware, ransomware, and unauthorized access.
3. Network Security Monitoring
Our experts monitor your IT infrastructure in real-time to detect anomalies and take immediate action.
4. Firewall Configuration and Management
CSG Technosol sets up and optimizes advanced firewalls to filter harmful traffic and secure your digital perimeters.
5. Cloud Security
We secure your cloud platforms (AWS, Azure, Google Cloud) using encryption, access control, and threat detection tools.
6. Data Protection and Backup Solutions
Our systems ensure that your critical business data is securely backed up and recoverable in case of breach or system failure.
7. Security Awareness Training
We train your employees on best practices to minimize human errors and reduce phishing and insider threats.
Industries We Serve
CSG Technosol provides tailored cybersecurity solutions across various industries:
Finance & Fintech: Secure banking applications and payment gateways
Healthcare: HIPAA-compliant patient data protection
Education: Safe access to digital learning platforms
Retail & E-commerce: Secure transactions and customer data
IT & SaaS: Scalable protection for cloud-based platforms
Why CSG Technosol is a Leading Cyber Security Company in Noida
✅ Certified Security Experts
Our team includes CEH, CISSP, and ISO 27001-certified professionals.
✅ Custom-Tailored Security Solutions
We don’t offer one-size-fits-all services. Every strategy is designed to match your infrastructure, compliance needs, and budget.
✅ 24/7 Security Monitoring
Our security operations center (SOC) provides around-the-clock monitoring and incident response.
✅ Proven Track Record
CSG Technosol has secured over 150+ businesses and helped prevent countless attacks.
✅ Client-Centric Approach
From startups to enterprises, our solutions are flexible and scalable.
CSG Technosol’s Cybersecurity Process
Risk Assessment and Planning
Security Architecture Design
Implementation and Configuration
Real-Time Monitoring and Management
Incident Detection and Response
Ongoing Updates and Compliance Checks
Best Practices for Cyber Hygiene
Even with a strong cybersecurity partner, internal practices matter. Here are quick tips for your team:
Use two-factor authentication (2FA)
Avoid clicking suspicious links or attachments
Regularly update software and patches
Monitor access logs and permissions
Encrypt sensitive data before storing or sharing
Conclusion
As cyber threats grow more frequent and sophisticated, every business must prioritize security. If you’re looking for a reliable, experienced, and cost-effective cyber security company in Noida, CSG Technosol is the name you can trust. We combine advanced technology with human intelligence to keep your digital assets safe, always.
Secure your business with confidence—partner with CSG Technosol today.
#csg technosol#cyber security company in noida#mobile app development company#android app development company#digital marketing#design
0 notes
Text
The Growing Importance of VAPT Service Providers in India’s Cybersecurity Landscape
In today’s digital era, cybersecurity has become a critical concern for organizations across the globe, and India is no exception. With increasing reliance on digital platforms for business operations, data storage, and customer engagement, the need for robust security measures has never been more vital. Vulnerability Assessment and Penetration Testing (VAPT) services have emerged as essential components of a comprehensive cybersecurity strategy. These services help identify vulnerabilities within an organization’s IT infrastructure, enabling proactive measures to prevent potential cyber threats.
India’s rapidly expanding digital economy, driven by sectors like banking, e-commerce, healthcare, and government services, has seen a surge in cyber-attacks. Hackers continuously develop new methods to exploit weaknesses, making it imperative for organizations to regularly assess their security posture. This has led to a rise in specialized VAPT service provider in India, offering tailored solutions to detect and mitigate vulnerabilities before they can be exploited by malicious actors.
A VAPT service provider in India typically offers a combination of vulnerability assessment and penetration testing services. Vulnerability assessment involves scanning networks, applications, and systems to identify known security flaws. Penetration testing, on the other hand, simulates real-world attacks to evaluate the effectiveness of existing security measures. Together, these services provide a comprehensive view of an organization’s security landscape, highlighting critical weaknesses that need immediate attention.
One of the key advantages of engaging a professional VAPT service provider in India is their expertise in handling diverse technological environments. Many Indian providers have a team of certified cybersecurity experts well-versed in the latest attack techniques and security frameworks. They utilize advanced tools and methodologies to conduct thorough assessments, ensuring that no vulnerability goes unnoticed. Moreover, these providers often tailor their testing to meet the specific needs of different industries, whether it’s finance, healthcare, or government agencies.
In addition to traditional vulnerability assessments, many Indian cybersecurity firms now offer Managed SOC service as part of their portfolio. A Security Operations Center (SOC) is a centralized unit that continuously monitors, detects, and responds to security threats in real-time. Managed SOC service enable organizations to outsource their security operations to experienced providers, ensuring round-the-clock vigilance without the need for in-house security teams. This is particularly beneficial for small and medium enterprises (SMEs) that may lack the resources to establish and maintain their own SOC.
The integration of Managed SOC service with VAPT solutions provides a holistic approach to cybersecurity. While VAPT helps identify vulnerabilities proactively, the Managed SOC continuously monitors the environment for signs of intrusion or malicious activity. This combination ensures that organizations are not only aware of their security gaps but also have immediate support to respond to incidents swiftly. Indian providers specializing in these integrated services understand the local regulatory landscape and compliance requirements, helping clients meet standards like GDPR, ISO 27001, and Indian cybersecurity laws.
The Indian market for cybersecurity services, including VAPT and Managed SOC, is expected to grow significantly in the coming years. As cyber threats evolve in sophistication, organizations are increasingly recognizing the importance of proactive security measures. Moreover, government initiatives like the National Cyber Security Strategy emphasize the need for robust defense mechanisms, further fueling demand for specialized service providers.
For organizations seeking a reliable VAPT service provider in India, it is essential to evaluate their experience, certifications, and client testimonials. A reputable provider should adhere to international security standards and employ ethical hacking practices to ensure legal compliance. Additionally, the provider’s ability to offer end-to-end solutions, from vulnerability assessment to incident response through Managed SOC, adds immense value.
In conclusion, the role of VAPT service providers in India is pivotal in strengthening the cybersecurity defenses of organizations across sectors. By leveraging advanced assessment techniques and continuous monitoring through Managed SOC service, Indian companies can better safeguard their assets, build customer trust, and comply with regulatory standards. As cyber threats continue to evolve, investing in professional security services will remain a strategic necessity for businesses aiming for sustainable growth in the digital age.
0 notes
Text
The Future of VAPT Services: AI, Bug Bounties, and Beyond

In the face of increasingly sophisticated cyber threats, organizations are increasingly constrained to bolster their security posture and protect their critical digital assets. With businesses swiftly undergoing digital transformation, the urgency for businesses to implement proactive and resilient cybersecurity frameworks has never been higher. Vulnerability Assessment and Penetration Testing (VAPT) is an important part of the cybersecurity landscape, as it has the ability to help organizations identify the loopholes in their security before their vulnerabilities are attacked. With the introduction of artificial intelligence (AI) to revolutionize the threat detection process and increasingly reliant on community-led approaches like bug bounty programs, VAPT services are evolving beyond the traditional boundaries towards a more agile and predictive form of cybersecurity.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a two-component process designed to identify and remediate security vulnerabilities in IT infrastructure. Vulnerability assessments are informed through the extraction of known vulnerabilities with automation, while penetration testing simulates real vulnerabilities in order to exploit those vulnerabilities. While traditional security audits typically rely on a compliance checklist, a VAPT audit is more dynamic and situationally aware. Many traditional security audits may uncover vulnerabilities, but they do not gauge the true risk of the vulnerability.
Current Landscape of VAPT Services
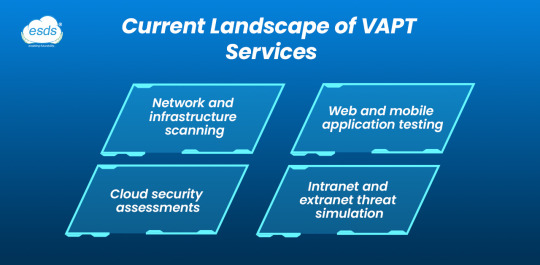
VAPT audit services today are the need of the hour for any organization dealing with sensitive information, like banking, healthcare, e-commerce, and government departments. These services include:
Network and infrastructure scanning
Web and mobile application testing
Cloud security assessments
Intranet and extranet threat simulation
A proper VAPT service provider in India would perform these scans using automated scanning tools as well as through manual methods in order to achieve complete coverage. The process is as follows:
Information Gathering
Vulnerability Scanning
Exploitation (Penetration Testing)
Reporting
Remediation Support
Top-tier VAPT testing services also provide retesting options post-patch implementation to ensure vulnerabilities have been successfully resolved.
Rising Trends Shaping the Future of VAPT
The threat landscape is no longer linear, and neither can the response mechanisms be. Some of the latest trends revolutionizing VAPT services are as follows:
a. Artificial Intelligence in VAPT
AI is transforming security scans. conventional VAPT methods are time-consuming, labor-intensive, and reliant on human ability. With AI and ML, VAPT tools are getting intelligent, lightning-fast, and predictive.
Some of the most significant benefits of AI in VAPT are
Scanning & Analysis Automation: AI can make scanning and reconnaissance activities automated, reducing detection time for vulnerabilities to a large extent.
Predictive Threat Modeling: Machine learning algorithms can detect patterns and forecast attack vectors beforehand.
Adaptive Testing: AI has the capability to learn from previous tests in order to create improved tests in the future with increased accuracy with the passage of time.
b. Bug Bounty Programs
Crowdsourced bug bounty programs are increasingly popular across the globe as firms tap into the worldwide talent pool of qualified ethical hackers. Bug bounty programs encourage individual security researchers for the discovery and reporting of real-world vulnerabilities.
How bug bounties supplement VAPT:
Diverse Expertise: Regardless of how competent your in-house team is, crowdsourcing brings different perspectives.
Deeper Testing: Bounty hunters are being paid to do so, so they’ll test more thoroughly than conventional testing procedures.
Cost-Effective: The Pay-per-vulnerability model only costs for actual findings.
HackerOne and Bugcrowd platforms already are in the mainstream and are employed as an added layer along with VAPT audit services as a complementary coverage.
c. Continuous VAPT vs Periodic Testing
Cyber threats change every day, and thus should your testing model. Rather than having VAPT audits conducted quarterly or yearly, organizations are adopting continuous testing models.
Continuous VAPT testing services involve
Integration with CI/CD pipelines
Real-time detection of vulnerabilities
Continuous monitoring and alerting
This change is such that no new code or infrastructure modification remains untested, thus reducing attack surfaces in real time.
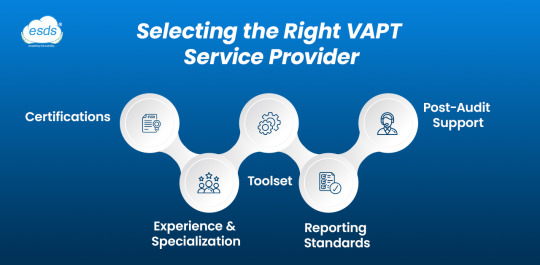
While demand grows, the number of VAPT service providers in India also grows. Not all of them are equal, however. These are some important considerations in selecting a partner:
Certifications: Ensure providers have certifications such as ISO 27001, CREST, CEH, or OSCP.
Experience & Specialization: Select vendors who have a proven record of industry-specific experience.
Toolset: Make sure they utilize a combination of proprietary and open-source tools such as Nessus, Burp Suite, and Metasploit.
Reporting Standards: Request reports that are in detail with risk scores, proof-of-concept, and remediation advice.
Post-Audit Support: The good VAPT vendor should assist you in the process of patching and provide retesting
Regulatory Compliance and VAPT
Governments and regulatory authorities across the globe are moving towards data protection and security compliance. In India, legislation like the Digital Personal Data Protection Act (DPDP 2023) and CERT-In guidelines has compelled businesses to provide VAPT audit services to industries like BFSI and healthcare.
Global standards like
ISO 27001
PCI-DSS
GDPR
HIPAA
often requires proof of VAPT testing services as part of the security validation process.
Adherence to these standards might invite legal trouble, loss of reputation, and money.
Future Challenges and Opportunities
Despite the bright future of VAPT, it also has challenges:
Challenges
Skills Shortage: According to the (ISC)² Cybersecurity Workforce Study, the world lacks 4 million cybersecurity experts
Evolving Threats: Hackers are also employing AI, rendering it futile to use manual or conventional VAPT techniques.
Tool Overload: Too many tools without integration results in inefficiency in the operation.
Opportunities
Productization of VAPT Services: Subscription and as-a-service models for VAPT will pick up speed.
Indigenous Growth in India: With the government’s Digital India and Make in India initiatives, indigenous VAPT service providers in India have a massive opportunity to grow.
Integration with DevSecOps: VAPT is becoming a part of the CI/CD pipeline, which enables secure software development lifecycles.
Conclusion
Given the constantly shifting threat landscape of the digital world, organizations need to up their cybersecurity offerings to address contemporary challenges. At ESDS, we’re of the view that security is not an option—whether it’s a checkbox—it’s an ongoing dynamic process.
With the help of AI-powered tools, industry best practices, and a pool of certified cybersecurity professionals, ESDS provides smart, adaptive, and elastic VAPT testing solutions according to your business requirements. We take you beyond run-of-the-mill testing by integrating security into your development cycle and assisting you in getting compliant with regulatory frameworks such as ISO 27001-2022, PCI-DSS 4.0 compliance, and General Data Protection Regulation.
ESDS aims to enable organizations to remain robust against dynamic cyber threats by continuously monitoring, providing actionable insights, and offering end-to-end remediation assistance.
0 notes
Text
VAPT Certification: Securing Your Digital Infrastructure
Introduction to VAPT Certification Vulnerability Assessment and Penetration Testing (VAPT) certification is a recognized validation that an organization has undergone comprehensive testing to identify and mitigate potential security vulnerabilities. It combines both automated vulnerability scanning and manual penetration testing to assess the strength of an organization's cybersecurity defenses. VAPT certification demonstrates a proactive approach to information security, which is essential in today’s evolving threat landscape.
Importance of VAPT for Organizations With cyberattacks becoming increasingly sophisticated, VAPT is crucial for businesses to protect sensitive data, maintain system integrity, and comply with regulatory requirements. It helps organizations understand their security posture and prevent unauthorized access, data breaches, or system downtime. For sectors like finance, healthcare, and IT, VAPT certification is often mandatory or highly recommended by industry regulations.
Components of VAPT VAPT consists of two key components: Vulnerability Assessment and Penetration Testing. Vulnerability Assessment uses automated tools to scan systems and detect known vulnerabilities. Penetration Testing involves simulating real-world cyberattacks to exploit identified weaknesses manually, providing deeper insight into potential threats. The combination ensures thorough testing of internal and external systems, networks, and applications.
VAPT Certification Process The VAPT certification process begins with scoping, where the systems to be tested are defined. This is followed by vulnerability scanning and manual testing. A detailed report is then generated, outlining the risks, impacted assets, and recommendations. After remediation, a retest confirms the issues are resolved, and the certification is issued by an accredited cybersecurity provider.
Benefits of VAPT Certification VAPT certification helps strengthen an organization’s security infrastructure, protect client data, and build trust among stakeholders. It supports compliance with standards like ISO 27001, PCI-DSS, and GDPR. Additionally, VAPT enhances risk management by proactively identifying and mitigating threats, thereby reducing the cost and impact of future incidents.
Choosing the Right VAPT Provider Selecting a certified and experienced VAPT service provider is crucial for accurate assessments. The provider should offer a customized approach based on the organization's environment and risk profile. Look for accreditations, client testimonials, and technical expertise when evaluating potential providers.
Conclusion VAPT certification plays a vital role in safeguarding an organization’s digital assets. By identifying vulnerabilities before malicious actors do, it enhances overall cybersecurity readiness and ensures compliance with industry regulations. Investing in VAPT is a strategic move toward long-term data security and business continuity.
0 notes
Text
Cybersecurity Training Course in Thane Enthrive Tech
The digital landscape is a battlefield, and businesses today are facing an unprecedented barrage of cyberattacks. To thrive in this environment, organizations need more than just firewalls; they need a human firewall – a workforce trained to detect, defend, and respond to threats. This is where Enthrive Tech steps in, offering far more than just a typical training program. We provide a transformative experience, empowering individuals to become true cybersecurity experts and organizations to build an impenetrable digital fortress.
Here are even more compelling reasons to choose Enthrive Tech for your cybersecurity journey:
1. Master In-Demand Skills with a Cutting-Edge Curriculum:
Our cybersecurity training isn't just about theory; it's about practical application. We delve into the most relevant and in-demand skills that employers are actively seeking. You'll gain expertise in:
Vulnerability Assessment & Penetration Testing (VAPT): Learn to think like a hacker (ethically, of course!) to identify weaknesses before malicious actors can exploit them. Our training includes hands-on experience with popular tools like Nmap, Wireshark, Metasploit, and Burp Suite.
Network Security: Understand the intricacies of securing networks, from firewalls and intrusion detection systems to secure network design and configuration.
Threat Detection & Incident Response: Develop the ability to identify suspicious activities, analyze security incidents, and execute effective response plans to minimize damage and restore operations.
Risk Management & Compliance: Learn to assess and mitigate cybersecurity risks, and understand how to ensure compliance with crucial regulations like GDPR and ISO 27001.
Cloud Security: As businesses move to the cloud, securing these environments is paramount. Our training covers best practices for securing cloud infrastructure and data on platforms like AWS, Azure, and Google Cloud.
Ethical Hacking Techniques: From malware analysis to social engineering, you'll gain practical knowledge of various attack vectors to better defend against them.
2. Experience the Unrivaled HTD (Hire, Train, Deploy) Advantage:
Enthrive Tech's unique HTD model is a game-changer. It's not just about getting trained; it's about getting job-ready and deployed. Here's how it maximizes your career prospects:
Tailored Training: We work directly with hiring partners to understand their specific talent needs, then customize our training to ensure you acquire the exact skills they require. This means you're learning what's immediately relevant to real-world job roles.
Conditional Offer Letters: Successful candidates can receive a conditional offer letter, providing a clear path to employment even before completing the training. This significantly reduces job search anxiety.
Seamless Transition: Our focus is on seamless deployment, ensuring you hit the ground running from day one in your new role.
Reduced Hiring Risk for Employers: Companies trust Enthrive Tech's HTD model because they receive pre-trained, job-ready professionals, saving them time and resources on onboarding and further training.
3. Benefit from a Holistic Learning Environment:
Our commitment to your success extends beyond technical skills. Enthrive Tech ensures you are a well-rounded cybersecurity professional:
Soft Skills & Personality Development: We recognize that strong communication, problem-solving, and critical thinking are as vital as technical prowess. Our programs often incorporate modules on these crucial soft skills, preparing you for successful team collaboration and client interactions.
Resume Building & Interview Preparation: Our dedicated career services team assists you in crafting compelling resumes and preparing for interviews, giving you a competitive edge in the job market.
Industry Expert Mentorship: Learn directly from experienced cybersecurity professionals who bring real-world case studies and insights into the classroom, offering invaluable perspectives.
State-of-the-Art Labs & Simulations: Practice your skills in realistic, hands-on lab environments and simulations that mirror real-world cyberattack scenarios, building practical expertise and confidence.
4. Unlock a World of Career Opportunities:
Upon completing your cybersecurity training with Enthrive Tech, you'll be prepared for a diverse range of high-demand and high-paying roles, including:
Cybersecurity Analyst: Monitor systems for threats, analyze security incidents, and implement security measures.
Ethical Hacker / Penetration Tester: Legally assess system vulnerabilities to improve security.
Security Architect: Design and build robust security systems and policies for organizations.
Incident Response Analyst: Respond swiftly and effectively to cyber incidents to minimize damage.
Cloud Security Engineer: Secure cloud-based systems and data on various platforms.
Security Consultant: Advise organizations on cybersecurity best practices and strategies.
Information Security Manager: Oversee an organization's overall information security policies and procedures.
The demand for cybersecurity professionals is projected to grow exponentially, with millions of jobs available globally in the coming years. Enthrive Tech empowers you to seize these opportunities and build a resilient and rewarding career.
5. Invest in a Secure and Lucrative Future:
Cybersecurity is not just a job; it's a critical societal need. By gaining expertise in this field, you contribute to protecting individuals, businesses, and critical infrastructure from the ever-present threat of cybercrime. This not only offers a strong sense of purpose but also translates into significant earning potential. Cybersecurity professionals consistently command competitive salaries, making it a financially rewarding career path.
Ready to secure your place in the digital defense force?
Visit enthrivetech.com today to explore our comprehensive cybersecurity training programs and discover how Enthrive Tech can equip you with the skills, knowledge, and career support to excel in this vital and rapidly growing industry. Don't just adapt to the future; shape it with Enthrive Tech!
0 notes
Text
How EDSPL Helps Organizations Stay Resilient in the Age of Ransomware

In today’s hyperconnected world, ransomware is no longer just a cybersecurity buzzword — it's a real and rising threat that can bring businesses to their knees in minutes. One wrong click, and an entire network can be encrypted, customer data held hostage, and operations disrupted indefinitely. With ransom demands soaring and threat actors growing more sophisticated, organizations need more than just antivirus software — they need real-time resilience.
This is where EDSPL steps in — not just as a cybersecurity service provider, but as a resilience partner committed to keeping businesses secure, prepared, and always one step ahead of cybercriminals.
In this blog, we dive into how EDSPL helps organizations stay resilient in the age of ransomware, the layered strategies it uses, and why modern businesses trust EDSPL to safeguard their most critical assets.
Understanding the Modern Ransomware Threat
Ransomware isn’t what it used to be.
Earlier, it was a nuisance. Now, it’s an enterprise-killer.
Today’s ransomware variants are part of multi-stage attacks, often combining phishing, privilege escalation, lateral movement, and even data exfiltration before the actual encryption begins. Threat actors don't just lock your files — they steal your data and threaten to leak it unless a ransom is paid.
Organizations face:
Double extortion (encryption + data leak threats)
Ransomware-as-a-Service (RaaS) platforms making attacks easier
Supply chain attacks targeting third-party vulnerabilities
Targeted attacks on critical sectors like healthcare, finance, and manufacturing
To stay resilient, organizations must go beyond detection. They must adopt a proactive, multi-layered cybersecurity approach — the kind EDSPL specializes in.
EDSPL: Your Ransomware Resilience Ally
EDSPL isn’t just responding to ransomware — it’s anticipating it. With years of experience in network, endpoint, email, cloud, and application security, EDSPL has developed an integrated defense ecosystem that ensures threats are neutralized before they can impact business operations.
Here’s how EDSPL helps organizations stay ransomware-resilient:
1. 24x7 SOC Monitoring: The First Line of Defense
At the heart of EDSPL’s protection strategy is its Security Operations Center (SOC) — a 24x7 surveillance and threat response hub that monitors, detects, and mitigates threats in real-time.
Advanced SIEM integration for log analysis and behavioral anomalies
Real-time alerts and incident response
Threat intelligence correlation to detect known and unknown ransomware variants
Automated playbooks via SOAR to accelerate response
Ransomware attacks don’t respect business hours — and neither does EDSPL.
2. Zero Trust Framework: Trust Nothing, Verify Everything
Ransomware often enters through trusted paths — a familiar email, a known user, or a compromised device. That’s why EDSPL enforces Zero Trust Architecture (ZTA) for all clients.
Identity and Access Management (IAM) to verify users and devices
Micro-segmentation to prevent lateral movement post-breach
Multi-factor authentication (MFA) across critical systems
Continuous verification for every access attempt
By ensuring never trust, always verify, EDSPL stops ransomware from spreading even if it slips past initial defenses.
3. Vulnerability Assessment & Penetration Testing (VAPT)
One common ransomware entry point? Unpatched vulnerabilities.
EDSPL conducts regular VAPT services to uncover weaknesses in:
Web applications
Internal and external networks
Firewalls and endpoint configurations
Cloud and container environments
Reports aren’t just technical — they’re actionable, helping IT teams fix issues fast and prevent ransomware footholds.
4. Ransomware Simulation & BAS (Breach and Attack Simulation)
Being “secure” is one thing — but how do you test resilience?
EDSPL uses Breach and Attack Simulation (BAS) tools to emulate real-world ransomware scenarios.
Simulates known and zero-day ransomware techniques
Tests endpoint, email, and network security readiness
Identifies gaps in detection and response workflows
These drills make teams more prepared and systems more resilient — so when the real thing hits, you already know how to handle it.
5. Endpoint Detection and Response (EDR) + XDR Integration
Ransomware often lands on endpoints — laptops, servers, even IoT devices. EDSPL deploys EDR and XDR tools to detect and stop ransomware at the endpoint level.
Behavioral analytics to flag unusual file encryption
Automated isolation of compromised machines
Rollback capabilities to reverse ransomware activity
Extended detection across cloud, apps, and email via XDR
This allows for early intervention — the key to minimizing ransomware damage.
6. Cloud & Email Security
With hybrid work and SaaS adoption, cloud and email are prime ransomware targets. EDSPL integrates:
Cloud-native security tools to monitor AWS, Azure, and GCP
Cloud-Native Application Protection Platforms (CNAPP) for container and workload protection
Advanced email filtering with real-time link sandboxing
AI-based phishing detection
This closes two of the biggest ransomware gateways — phishing and cloud misconfigurations.
7. Immutable Backups and Disaster Recovery Planning
Even with the best defenses, ransomware might strike. EDSPL ensures clients have air-gapped, immutable backups that can’t be tampered with - not even by attackers.
Daily and weekly snapshots
Cloud and on-prem backup strategy
Fast recovery plans that reduce downtime from days to hours
With EDSPL, even if data is encrypted, business doesn’t stop.
8. Security Awareness & Workforce Training
Technology alone isn’t enough. Ransomware often succeeds because humans make mistakes - clicking malicious links, opening fake invoices, or using weak passwords.
EDSPL delivers:
Regular phishing simulations
Employee training sessions
Role-based cybersecurity education
Gamified learning platforms to keep staff engaged
An informed employee is your best defense — and EDSPL turns your workforce into cyber-aware first responders.
Real-World Impact: What EDSPL Clients Say
Here’s what clients say after partnering with EDSPL for ransomware resilience:
"Our healthcare system faced three ransomware attempts in a quarter. EDSPL's SOC stopped all of them before they reached patient data." — CIO, Healthcare Firm
"The ransomware drill exposed a critical email configuration we never knew was vulnerable. Thanks to EDSPL, we fixed it in time." — CISO, Financial Services Company
"EDSPL didn’t just sell us tools — they helped us build a culture of cybersecurity." — IT Head, Manufacturing Enterprise
Why Ransomware Resilience Needs a Strategic Partner
The age of ransomware requires more than patchwork solutions. Businesses need a strategic cybersecurity ally who:
✅ Understands evolving threat landscapes ✅ Offers continuous monitoring and rapid response ✅ Builds cybersecurity into business DNA ✅ Helps plan for the worst — while preventing it altogether
EDSPL is that ally.
Whether you're a startup, an SME, or a large enterprise — EDSPL brings the expertise, tools, and mindset needed to stay resilient, bounce back faster, and never lose control of your business in the face of ransomware.
Conclusion: Stay Resilient, Stay Ahead — With EDSPL
In an era where ransomware can cripple operations in minutes, resilience isn’t optional — it’s a competitive advantage.
EDSPL doesn’t just protect — it prepares, educates, simulates, and empowers. From advanced SOC operations to human-centric training, from Zero Trust enforcement to disaster recovery, EDSPL delivers a 360° cybersecurity approach tailored for modern challenges.
When ransomware knocks, your response matters. With EDSPL, your answer is ready — and stronger than ever.
Explore our full range of services — including routing, switching, data center switching, compute, storage, mobility, and managed & maintenance solutions.
Have questions? Reach us or get in touch today.
Let’s build a safer, stronger digital future — together. Explore our background vision and see how we’re shaping cybersecurity for tomorrow.\
0 notes
Text
Cyber Security Summer Internship | Top Skills You’ll Learn

As the digital world grows, so does the need for skilled cybersecurity professionals. Organizations constantly seek individuals who can effectively protect their systems, detect vulnerabilities, and respond to cyber threats. For students and fresh graduates, enrolling in a Cyber Security Summer Internship is one of the best ways to build a strong foundation in this field.
At WebAsha Technologies, the Cyber Security Summer Internship program in Pune is designed to equip participants with the practical skills and knowledge needed to succeed in today’s cybersecurity landscape. In this article, we highlight the top skills you will learn during the internship.
Network Security Basics
One of the first areas you will explore is network security. This involves understanding how data moves across networks and learning to protect it from interception and attacks.
Learn the fundamentals of network architecture and protocols.
Understand how firewalls, routers, and switches function to secure networks.
Identify common network vulnerabilities and how to mitigate them.
Study intrusion detection and prevention systems (IDS/IPS).
Ethical Hacking Techniques
Ethical hacking teaches you to think like a hacker, but to strengthen system security. This skill is critical for finding and fixing vulnerabilities before they can be exploited.
Get familiar with various hacking methodologies and tools.
Learn reconnaissance, scanning, gaining access, maintaining access, and covering tracks.
Practice using tools such as Nmap, Metasploit, and Burp Suite.
Explore real-world hacking scenarios and practice ethical response methods.
Vulnerability Assessment and Penetration Testing (VAPT)
VAPT is a key component of any cybersecurity strategy. It helps organizations identify weaknesses in their systems through systematic testing.
Learn to conduct vulnerability assessments to discover security gaps.
Perform penetration tests to simulate real-world attacks.
Understand the phases of VAPT: planning, scanning, exploitation, and reporting.
Gain experience in documenting findings and suggesting remediation steps.
Web Application Security
With web applications being a major target for attackers, web security is a crucial skill.
Study common web application vulnerabilities, including SQL injection and cross-site scripting (XSS).
Learn how to test web apps for security flaws using automated and manual techniques.
Understand how to secure APIs and manage user authentication securely.
Get hands-on practice in identifying and mitigating web security risks.
Malware Analysis and Threat Detection
Another essential skill is the ability to analyze malware and detect potential threats before they cause damage.
Learn about different types of malware: viruses, worms, trojans, ransomware, and spyware.
Understand how malware behaves and propagates.
Use tools to detect, analyze, and remove malicious code.
Study case examples of high-profile malware attacks and their impacts.
Cryptography and Data Protection
Protecting sensitive data is a critical part of cybersecurity. You will gain an understanding of cryptography and how it ensures data security.
Learn the basics of encryption and decryption.
Understand the differences between symmetric and asymmetric encryption.
Explore digital signatures, certificates, and secure key management.
Study how cryptography is used in securing communications and transactions.
Incident Response and Handling
Responding quickly and effectively to a cyber incident is vital in minimizing damage.
Learn the stages of incident response: preparation, detection, containment, eradication, and recovery.
Practice creating incident response plans.
Understand how to preserve evidence and maintain the chain of custody.
Study real-world case studies to learn best practices.
Security Compliance and Best Practices
In addition to technical skills, understanding security standards and compliance is essential.
Get familiar with key standards like ISO 27001, GDPR, and PCI-DSS.
Learn best practices for creating security policies and procedures.
Understand the role of audits and risk assessments in maintaining compliance.
Final Thoughts
The Cyber Security Summer Internship at WebAsha Technologies is more than just a learning opportunity—it’s a stepping stone to a successful career in cybersecurity. By the end of the program, participants will have hands-on experience, a deep understanding of essential security practices, and the confidence to tackle real-world security challenges.
For students and IT enthusiasts looking to build a strong career foundation, this internship provides everything needed to get started. Enroll today and take the first step toward becoming a skilled cybersecurity professional.
#Cyber Security Summer Internship#Ethical Hacking Summer Training#VAPT Internship#Cyber Security Summer Course#Cyber Security Internship with Placement#Cyber Security Summer Bootcamp#Summer Internship in Cyber Security
0 notes
Text
VAPT Services in Pune - Cyberintelsys

Looking for reliable VAPT services in Pune? Cyberintelsys offers expert Vulnerability Assessment and Penetration Testing solutions tailored to your business needs. Our team of cybersecurity professionals helps identify and fix security loopholes before attackers exploit them. We use the latest tools and methodologies to ensure your digital infrastructure is safe and compliant. With a strong presence in Pune, we are known for delivering accurate, actionable reports and long-term protection. Safeguard your digital assets with one of the most trusted VAPT providers in the region. Choose Cyberintelsys for end-to-end cybersecurity peace of mind.
0 notes
Text
Round-the-Clock Security, Nationwide Trust — MDIT Services, Leading SOC Provider in India
In today’s digital-first economy, cyber threats are no longer a matter of if, but when. Businesses across sectors—from finance and healthcare to e-commerce and manufacturing—face relentless cyberattacks that exploit vulnerabilities in systems, people, and processes. The need for proactive, 24/7 security monitoring has never been more urgent. That’s where MDIT Services, a premier SOC service provider in India, comes into the picture.
What is a SOC and Why Does Your Business Need It?
A Security Operations Center (SOC) is a centralized team of cybersecurity professionals who continuously monitor, detect, analyze, and respond to cybersecurity incidents. Unlike reactive IT support, a SOC operates proactively—identifying threats before they impact your business operations.
Without a proper SOC framework, organizations risk:
Data breaches
System downtime
Regulatory penalties
Brand reputation loss
Partnering with a trusted SOC service provider ensures your organization is always protected, even when you’re not watching.
Why MDIT Services is India’s Trusted SOC Provider
As one of the leading SOC service providers in India, MDIT Services brings a blend of advanced technology, expert talent, and industry best practices to help businesses stay ahead of threats. Here’s what sets us apart:
1. 24/7 Threat Monitoring
Our Security Operations Center works around the clock. Threats don’t take weekends off, and neither do we. With real-time monitoring, our SOC detects anomalies, suspicious behavior, and potential breaches the moment they occur.
2. Real-Time Incident Response
Time is critical when it comes to cybersecurity. MDIT Services ensures swift incident response through automation and expert intervention, reducing the time it takes to contain and eliminate threats.
3. Next-Gen SIEM Integration
We use advanced Security Information and Event Management (SIEM) tools to aggregate and analyze logs from across your IT ecosystem. Our systems identify patterns that human eyes might miss—giving you a data-driven defense shield.
4. Certified Cybersecurity Experts
Our SOC team is composed of certified professionals with expertise in ethical hacking, digital forensics, network defense, and compliance. We invest in continuous training to keep up with evolving threats.
5. Nationwide Coverage, Industry-Specific Solutions
From startups in Bengaluru to enterprises in Delhi, MDIT Services offers scalable SOC solutions for businesses across India. Whether you're in BFSI, healthcare, education, or logistics—we tailor our services to meet your sector's unique security requirements.
SOC Services We Offer
Being a full-spectrum SOC service provider in India, MDIT Services offers a comprehensive range of services:
Threat Detection and Intelligence
Vulnerability Assessment and Penetration Testing (VAPT)
Endpoint Detection and Response (EDR)
Log Management and Forensics
Compliance Reporting (ISO 27001, PCI-DSS, GDPR, etc.)
Cloud Security Monitoring
SIEM Deployment and Management
Benefits of Partnering with MDIT Services
Businesses that partner with MDIT Services experience a range of measurable benefits:
Reduced Risk Exposure: Continuous monitoring dramatically lowers the chances of data breaches.
Cost Efficiency: Hiring and maintaining an in-house SOC team is expensive. We deliver enterprise-grade protection at a fraction of the cost.
Regulatory Compliance: We help you stay compliant with national and international standards, avoiding legal and financial penalties.
Improved Business Continuity: With rapid threat detection and response, downtime is minimized, and productivity remains unaffected.
Peace of Mind: Focus on growing your business while we keep your infrastructure safe.
A SOC for Every Size of Business
Contrary to popular belief, SOC services are not just for large enterprises. SMBs are increasingly becoming targets for cybercriminals due to weaker defenses. That’s why MDIT Services offers scalable SOC solutions—whether you're a 10-person startup or a 1,000-employee enterprise.
Our flexible pricing models, modular services, and pay-as-you-grow offerings make high-end security accessible to businesses of all sizes.
Case in Point: A Success Story
One of our clients, a leading logistics firm in Mumbai, experienced multiple unauthorized login attempts over a single weekend. Our SOC identified the brute force attack in real time, isolated the targeted systems, and implemented multi-factor authentication (MFA) within hours. The attack was neutralized before any data could be accessed—saving the client from potential millions in losses and regulatory fines.
This is just one of many instances where our 24/7 monitoring and incident response made a real difference.
Why Now is the Time to Act
Cybercrime is evolving rapidly, with attackers leveraging AI, automation, and social engineering at scale. The average time to detect a breach in India is still over 200 days—ample time for attackers to cause irreparable damage.
Don’t wait for an incident to act. With MDIT Services by your side, you gain a proactive shield that works day and night to secure your digital assets.
Get in Touch with MDIT Services Today
As a trusted SOC service provider in India, MDIT Services is ready to help your organization build a cyber-resilient future.
To know more click here :-https://mditservices.in
0 notes
Text
Choose the Best Cybersecurity Services in Noida to Protect Your Company’s Digital Assets and Information: Wish Geeks Techserve

In today's digitally connected world, cyber threats are more sophisticated and dangerous than ever before. From data breaches and ransomware to phishing attacks and insider threats, businesses face increasing risks to their sensitive data and IT infrastructure. That's why partnering with a trusted cybersecurity expert is no longer optional—it’s essential. If you’re looking for cybersecurity services in Noida, Wish Geeks Techserve offers cutting-edge solutions tailored to your business needs.
As a cybersecurity solutions provider in Noida, we specialize in securing digital environments, reducing vulnerabilities, and ensuring compliance for businesses of all sizes.
Why Cybersecurity Matters More Than Ever
With the rapid adoption of cloud technologies, mobile devices, and remote work, companies are more exposed to cyber risks than ever. Cybersecurity is not just about firewalls—it’s about having an end-to-end strategy to prevent, detect, and respond to threats.
Risks Businesses Face Without Proper Cybersecurity:
Financial losses from data theft or ransomware
Damage to brand reputation and customer trust
Legal penalties due to non-compliance
Operational disruptions from network outages
Exposure of intellectual property and sensitive information
Wish Geeks Techserve: Trusted Cybersecurity Services in Noida
At Wish Geeks Techserve, we provide a wide array of cybersecurity services in Noida to help you stay one step ahead of evolving cyber threats. Our security professionals use a proactive approach to identify vulnerabilities and implement defense mechanisms across your IT infrastructure.
As a cybersecurity solutions provider in India, we are committed to delivering secure, scalable, and smart protection strategies.
Our Core Cybersecurity Services
We offer industry-leading IT security services in India backed by advanced tools, methodologies, and certified professionals. Our services are designed to protect digital assets and keep your organization safe from cyber risks.
🔒 Network Security Services
Firewall configuration and intrusion prevention systems (IPS)
Secure VPN and encrypted communications
Real-time network traffic monitoring and alert systems
🛡️ Endpoint Protection
Antivirus and anti-malware software deployment
Device control and application white-listing
Threat detection and response for laptops, desktops, and mobile devices
📊 Security Audits & Compliance
Regular security audits and gap assessments
Compliance with GDPR, ISO 27001, HIPAA, and other standards
Policy implementation and employee training
🔍 Vulnerability Assessment & Penetration Testing (VAPT)
Identifying exploitable weaknesses in your system
Simulated attacks to test your organization’s defense readiness
Custom VAPT reports and remediation planning
☁️ Cloud Security Solutions
Data encryption and access management for cloud environments
Monitoring and securing hybrid and multi-cloud platforms
Secure cloud migration and cloud-native threat prevention
Benefits of Choosing Wish Geeks Techserve
We’re not just another cybersecurity services company in Noida—we’re your dedicated technology partner. Our team is focused on creating long-term security strategies that evolve with your business.
Here’s Why Clients Choose Us:
Decade of experience in delivering cybersecurity services in India
Customized, scalable solutions tailored to your IT environment
Proactive threat monitoring and incident response support
24/7 security operations center (SOC)
Transparent pricing with no hidden costs
Serving Businesses Across All Industries
As the best cybersecurity solutions provider in Noida, we work with organizations in a wide range of industries, each with its own unique cybersecurity challenges.
Industries We Serve:
Finance and banking
Healthcare and pharmaceuticals
Education and e-learning platforms
E-commerce and retail
Manufacturing and logistics
Government and public sector
Whether you're a startup or a multinational corporation, our team ensures that your digital assets are always protected.
Customized Cybersecurity Solutions in Noida for Every Business Size
We understand that no two businesses are alike. That’s why we offer flexible plans to match your budget, goals, and IT infrastructure. As a custom cybersecurity solutions provider in Noida, we make security simple and effective.
Our Scalable Security Approach Includes:
Risk assessment based on your operational model
Roadmap to implement technical and administrative controls
Integration of AI-based threat detection systems
Scheduled system reviews and patch management
Choose the Best Cybersecurity Company in India
When it comes to protecting what matters most, you need a trusted partner that understands the evolving threat landscape. Wish Geeks Techserve is recognized as a best cybersecurity company in India, known for reliable, agile, and cost-effective IT security services.
We empower businesses with proactive security frameworks that support growth, innovation, and customer trust.
Ready to Secure Your Business?
Cyber threats aren’t going away—they’re growing smarter. It’s time to future-proof your business with advanced cybersecurity solutions in Noida from a trusted provider.
Connect with Wish Geeks Techserve today and safeguard your business from tomorrow’s threats.
#Cybersecurity Services Noida#cybersecurity solutions in Noida#Cybersecurity Services in Noida#Cybersecurity Services India#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Cybersecurity Solutions Provider in Noida#best Cybersecurity Solutions Provider in Noida#Network Security Services in India
0 notes
Text
From Code to Confidence: Why EDSPL’s QA and Software Testing Services Are Trusted by Industry Leaders

In today’s software-driven world, where applications power everything from banking to retail, flawless user experiences are no longer optional—they are expected. One software glitch can cost a business its reputation, revenue, or even regulatory approval. As organizations race to deliver products faster, the role of Quality Assurance (QA) and Software Testing has shifted from a supporting function to a strategic cornerstone of business success.
At the forefront of this shift is EDSPL (Enrich Data Solutions Pvt. Ltd.), a trusted technology partner offering end-to-end software testing services. With a sharp focus on delivering excellence, EDSPL has become the go-to QA partner for companies that prioritize quality, scalability, and innovation.
The True Value of QA: Why Quality Matters More Than Ever
Software is not just about writing code—it’s about ensuring that code behaves as intended in the real world. Poor quality software not only leads to customer dissatisfaction but also causes financial losses. According to a report by the Consortium for IT Software Quality (CISQ), software bugs cost businesses trillions of dollars annually.
This is why forward-thinking businesses integrate QA from day one. They understand that:
Every crash affects customer loyalty.
Every missed defect increases operational cost.
Every delay in fixing bugs slows down time-to-market.
EDSPL helps businesses transition from reactive testing to proactive quality engineering—delivering software that’s reliable, secure, and high-performing.
EDSPL’s Approach: Quality Is Not a Phase. It’s a Culture.
Unlike vendors that treat QA as a final checkpoint before release, EDSPL embeds QA throughout the Software Development Life Cycle (SDLC). By adopting Shift-Left Testing, Continuous Testing, and DevOps practices, the company ensures quality at every stage—from planning to post-deployment monitoring.
The result?
Fewer bugs in production
Faster releases
Happier users
Reduced long-term maintenance costs
EDSPL's QA team is integrated, agile, and continuously improving—because in today’s fast-paced digital landscape, quality can’t wait.
Comprehensive Testing Services for Every Business Need
EDSPL delivers a full spectrum of manual and automated testing solutions tailored to fit diverse industries and platforms. The services include:
Manual Testing
Functional Testing
Regression Testing
User Acceptance Testing (UAT)
Exploratory Testing
Automation Testing
Selenium-based automation for web
Appium for mobile applications
TestNG, JUnit, and Cypress for seamless CI/CD pipeline integration
Performance Testing
Load and stress testing using tools like JMeter and LoadRunner
Bottleneck identification and optimization recommendations
Security Testing
Vulnerability assessments and penetration testing (VAPT)
Secure code reviews based on OWASP Top 10
Compliance support (HIPAA, PCI DSS, ISO 27001)
Mobile and Cross-Browser Testing
Device labs with real-time testing on iOS, Android, and various browsers
Responsive and usability checks for superior user experience
API Testing
End-to-end validation using Postman, REST Assured, and Swagger
Contract testing and mocking for microservices environments
This 360-degree approach ensures that every corner of your software ecosystem is tested, verified, and ready to perform under real-world conditions.
A Perfect Blend of Human Expertise and Automation
Automation is no longer a luxury; it’s a necessity. But automation without strategy often leads to bloated scripts, unstable builds, and delayed feedback. EDSPL brings a strategic approach to automation—identifying test cases that deliver maximum ROI when automated and maintaining them effectively over time.
With experience in integrating testing frameworks into Jenkins, GitLab CI/CD, and Azure DevOps, EDSPL enables:
Faster regression cycles
Reusability of test scripts
Real-time reporting and analytics
Reduced time-to-market
The goal isn’t just faster testing—it’s smarter testing. And EDSPL delivers on both.
Industry-Specific Testing That Adds Real-World Value
Every industry is different, and so are its testing needs. EDSPL tailors its QA strategies based on domain knowledge and industry regulations. The team has experience across:
Banking and Finance: Secure transactions, compliance testing, multi-factor authentication validation
Healthcare: HIPAA compliance, patient data confidentiality, interoperability
Retail and eCommerce: Payment gateway testing, shopping cart flow, performance under high loads
EdTech: Multi-device learning experiences, gamification elements, content validation
Logistics and Supply Chain: Workflow accuracy, geo-location validation, API integrations
This domain-driven approach helps EDSPL uncover issues that generic testing might miss—bringing peace of mind to both clients and end users.
Real-World Results: How EDSPL Has Made an Impact
Case Study: Mobile Banking App Optimization
A leading bank struggled with app crashes and slow performance. EDSPL identified backend inefficiencies and memory leaks through performance testing. After refactoring, the app achieved a 40% performance boost and a 90% drop in crash reports.
Case Study: eCommerce Speed to Market
An online retail startup needed to launch quickly without compromising quality. EDSPL implemented a hybrid testing model (manual + automated), cutting testing time by 60%. The result was a bug-free launch in record time, with zero post-launch escalations.
Case Study: SaaS Security Validation
A healthcare SaaS platform had to pass a third-party security audit. EDSPL conducted vulnerability assessments and secure code reviews, helping the platform achieve HIPAA compliance and win trust from enterprise clients.
Why Businesses Choose EDSPL for QA and Testing
Proven Track Record
With a strong portfolio of clients across sectors, EDSPL brings a wealth of experience in delivering quality products under strict timelines.
Certified QA Experts
The QA team holds globally recognized certifications such as ISTQB, CSTE, CEH, and more—ensuring your software is tested by qualified professionals.
Customizable Engagement Models
Whether you need a dedicated QA team, on-demand testing, or outsourced end-to-end QA management, EDSPL offers engagement models that align with your business needs.
Seamless Integration with Development
EDSPL works closely with development teams, integrating with tools like JIRA, Slack, Git, Jenkins, and others to ensure smooth collaboration and efficient feedback loops.
Data-Driven Testing and Reporting
Comprehensive reports on test coverage, bug trends, automation ROI, and performance metrics help stakeholders make informed decisions backed by real data.
Aligning QA with Your Business and SEO Goals
EDSPL’s QA services are not just about internal quality—they also contribute to external outcomes like SEO performance and brand perception. Testing includes:
Page speed optimization
Mobile responsiveness validation
Accessibility checks
Broken link and metadata validation
Schema and sitemap validation
All these contribute to better user experience and improved rankings on search engines.
Ready for What’s Next: AI-Driven and Predictive QA
As technology evolves, EDSPL stays ahead with innovations in:
AI-powered test case prioritization
Predictive analytics for defect prevention
Self-healing automation scripts
Testing for voice, chatbots, and IoT applications
By adopting next-gen QA strategies, EDSPL ensures that your software is not just ready for today—but future-proof for tomorrow.
The Bottom Line: Trust Built on Testing
In an age where software defines customer experience, poor quality can be a business killer. That’s why leaders across industries trust EDSPL—not just as a vendor, but as a long-term quality partner.
EDSPL doesn’t just test code. It builds confidence. It safeguards reputations. It accelerates innovation.
If your business success depends on software, then your software deserves EDSPL.
Let’s Build Better Software, Together
Whether you're launching a new product, scaling an existing platform, or simply want to ensure every line of code meets the highest standards—EDSPL is ready to help you achieve it with confidence.
Let’s talk. Visit www.edspl.net to explore how our QA and software testing services can transform your development lifecycle from code to confidence.
Please visit our website to know more about this blog https://edspl.net/blog/from-code-to-confidence-why-edspl-s-qa-and-software-testing-services-are-trusted-by-industry-leaders/
0 notes
Text
Don’t Wait for a Breach — Discover the Power of VAPT
In today’s fast-moving digital landscape, cyber threats are constantly evolving. Firewalls and antivirus software are no longer enough to protect your business-critical systems. That’s where VAPT — Vulnerability Assessment and Penetration Testing — steps in.
What is VAPT? VAPT is a powerful combination of two essential security services:
Vulnerability Assessment scans your systems to identify known weaknesses.
Penetration Testing goes a step further by simulating real-world attacks to test how far those vulnerabilities can be exploited.
Together, they offer a 360-degree view of your cybersecurity posture — showing you not just what can go wrong, but how and where attackers might break in.
At eShield IT Services, our expert VAPT team uses advanced tools and ethical hacking techniques to mimic cybercriminal behavior — so you can fix security holes before they become entry points.
Whether you’re trying to meet compliance standards or just want to sleep better at night, VAPT is a smart investment in your business’s future.
To know more click here :- https://eshielditservices.com
0 notes
Text
VAPT Testing
VAPT (Vulnerability Assessment and Penetration Testing) is a critical process in identifying, evaluating, and addressing security vulnerabilities in an organization's IT infrastructure. With the increasing sophistication of cyber threats, it is essential for businesses to proactively identify and mitigate security risks before they can be exploited by malicious actors. VAPT testing is a comprehensive approach that combines two essential components—vulnerability assessment and penetration testing—to safeguard an organization’s digital assets and ensure data integrity.
1. What is VAPT Testing?
VAPT stands for Vulnerability Assessment and Penetration Testing. It involves two distinct but complementary practices:
Vulnerability Assessment: This process involves identifying and evaluating security vulnerabilities in the network, systems, or applications of an organization. Using automated tools, vulnerability scanning detects weaknesses such as outdated software, misconfigurations, or missing patches.
Penetration Testing: Often referred to as ethical hacking, penetration testing simulates real-world cyberattacks to exploit the vulnerabilities identified in the assessment phase. The objective is to evaluate the effectiveness of existing security measures and identify how far an attacker could penetrate the system.
VAPT testing aims to provide a comprehensive understanding of the organization's cybersecurity posture, enabling informed decisions about how to strengthen defenses.
2. The Importance of VAPT Testing
As cyberattacks become more frequent and sophisticated, organizations face significant risks related to data breaches, financial loss, and reputational damage. VAPT testing is crucial for several reasons:
Proactive Security: VAPT helps organizations identify vulnerabilities before cybercriminals can exploit them, allowing for proactive rather than reactive security measures.
Regulatory Compliance: Many industries, such as finance and healthcare, have stringent cybersecurity regulations that require periodic vulnerability assessments and penetration tests.
Risk Mitigation: By identifying vulnerabilities and fixing them, organizations can significantly reduce the risk of data breaches, system downtime, and loss of sensitive information.
Improved Incident Response: Penetration testing simulates real-world attacks, enabling organizations to evaluate their incident response capabilities and improve their defenses.
3. Key Components of VAPT Testing
VAPT testing typically involves the following steps:
Planning and Scoping: The first step involves determining the objectives, scope, and resources for the testing. This may include the systems, applications, or networks to be tested.
Vulnerability Scanning: Automated tools are used to scan the organization's IT infrastructure to identify known vulnerabilities.
Manual Testing: In addition to automated tools, ethical hackers manually test the system for complex or logic-based vulnerabilities that automated scans might miss.
Exploitation: Penetration testers attempt to exploit the identified vulnerabilities, simulating how an attacker might gain unauthorized access.
Reporting and Remediation: After testing, detailed reports are provided, outlining the discovered vulnerabilities, the risk they pose, and recommended fixes.
4. Who Should Conduct VAPT Testing?
VAPT testing is typically performed by cybersecurity professionals with expertise in ethical hacking, network security, and vulnerability management. This includes:
Certified Ethical Hackers (CEH): Experts with the knowledge and skills to simulate attacks and identify vulnerabilities.
Penetration Testers: Specialized professionals who conduct manual penetration tests to evaluate the robustness of security defenses.
Security Auditors: Individuals responsible for assessing the overall security framework and ensuring compliance with industry standards.
IT Security Teams: Internal teams can collaborate with external testers to implement and address identified vulnerabilities.
5. Conclusion
VAPT testing is a fundamental component of any organization’s cybersecurity strategy. By combining vulnerability assessments with penetration testing, businesses can gain a comprehensive understanding of their security posture, identify weaknesses, and implement effective strategies to protect against cyber threats. Regular VAPT testing helps businesses stay ahead of emerging threats, ensures regulatory compliance, and enhances the overall security resilience of their IT systems. In an increasingly digital world, VAPT testing is not just a luxury—it’s a necessity for safeguarding an organization’s data, reputation, and bottom line.
0 notes
Text
VAPT Certification in New York: Enhancing Cybersecurity and Building Trust
What is VAPT Certification?
VAPT Certification in New York is a systematic approach to identifying and addressing vulnerabilities in an organization's digital assets, such as networks, applications, and servers. While a vulnerability assessment highlights potential weaknesses, penetration testing simulates cyberattacks to evaluate how these vulnerabilities can be exploited.
Achieving VAPT Certification demonstrates that your organization has undergone rigorous testing and is committed to maintaining robust cybersecurity measures. It is particularly valuable for businesses handling sensitive data, such as financial institutions, healthcare providers, and e-commerce platforms in New York.
Benefits of VAPT Certification for Businesses in New York
Strengthened Security: VAPT Implementation in New York VAPT identifies and mitigates vulnerabilities, enhancing your organization's overall cybersecurity posture.
Compliance: Certification helps meet regulatory requirements such as GDPR, HIPAA, and PCI DSS, which mandate robust cybersecurity practices.
Enhanced Trust: Clients and stakeholders are more likely to trust businesses with certified cybersecurity measures in place.
Risk Reduction: Proactively addressing vulnerabilities reduces the likelihood of data breaches, ransomware attacks, and financial losses.
Competitive Advantage: Certification distinguishes your business as a leader in cybersecurity, setting you apart from competitors.
Cost of VAPT Certification in New York
VAPT Cost in New York varies depending on factors such as:Larger businesses with complex IT environments require more extensive testing.Whether the focus is on specific applications, networks, or the entire IT infrastructure.Regular assessments may involve ongoing costs.: Engaging experienced cybersecurity professionals to conduct the assessment and provide recommendations.While the investment may seem significant, the cost of a potential data breach far exceeds the expense of securing your organization through VAPT.In an era of increasing cyber threats, businesses in New York must prioritize the security of their digital infrastructure. Vulnerability Assessment and Penetration Testing (VAPT) Certification has become a critical tool for organizations to identify, analyze, and mitigate cybersecurity risks. This blog explores the importance of VAPT Certification in New York, its benefits, cost considerations, process, and how to get expert guidance.
VAPT Certification Audit
VAPT Audit in New York Organizations in New York may face the following challenges during the VAPT process:Larger businesses may require extensive testing across multiple systems and applicationsNew vulnerabilities and threats emerge rapidly, necessitating regular updates to security measures.Small and medium-sized enterprises (SMEs) may lack the in-house expertise to conduct effective VAPT.Engaging professional consultants can address these challenges and streamline the certification process.Define the scope of the assessment, including the systems, applications, and networks to be tested.Simulate real-world cyberattacks to exploit identified vulnerabilities and evaluate their impact.Once vulnerabilities are addressed, a certification is awarded, demonstrating your organization’s commitment to cybersecurity.
How to Get VAPT Consultants in New York
VAPT Certification Consultants in New York To ensure a smooth and effective certification process, businesses in New York should consider hiring experienced VAPT consultants. These professionals offer:In-depth knowledge of the latest tools and methodologies for vulnerability assessment and penetration testing.Customized testing plans based on your organization's specific needs.Detailed analysis and actionable recommendations to address identified risks.Guidance for maintaining cybersecurity compliance post-certification.In today’s digital-first world, cybersecurity is non-negotiable for businesses in New York. VAPT Certification provides a systematic approach to identifying and addressing vulnerabilities, ensuring robust protection against cyber threats. By obtaining this certification, organizations not only enhance their security posture but also build trust with clients, partners, and stakeholders.
0 notes
Text
VAPT Certification
Introduction to VAPT Certification
Vulnerability Assessment and Penetration Testing (VAPT) certification is an essential process for organizations aiming to secure their IT infrastructure. It involves identifying vulnerabilities and testing security measures to ensure systems are resilient against cyber threats. VAPT certification helps organizations build trust with stakeholders by demonstrating robust cybersecurity practices.
Importance of VAPT Certification
VAPT certification safeguards sensitive data, reduces the risk of cyberattacks, and ensures compliance with regulatory standards. With increasing cyber threats, this certification provides organizations with actionable insights to address potential vulnerabilities, enhancing their overall security posture.
Key Steps in VAPT Certification
The certification process begins with a vulnerability assessment to identify weaknesses in the system. This is followed by penetration testing, where ethical hackers simulate attacks to evaluate the robustness of security measures. The final stage involves generating a detailed report, outlining vulnerabilities and recommendations for mitigation.
Benefits of VAPT Certification
Achieving VAPT certification strengthens an organization’s cybersecurity framework. It minimizes risks, protects sensitive information, and ensures compliance with legal requirements. Furthermore, it builds customer confidence by demonstrating a proactive approach to security.
Industries That Benefit from VAPT Certification
Sectors like banking, healthcare, e-commerce, and government institutions benefit significantly from VAPT certification. These industries handle sensitive information, making them prime targets for cyberattacks. VAPT certification ensures that their systems remain secure and resilient.
Choosing the Right VAPT Service Provider
Selecting a credible VAPT service provider is crucial for effective certification. Look for experienced professionals who use advanced tools and adhere to industry standards. A reliable provider ensures a comprehensive assessment and actionable recommendations.
Maintaining VAPT Certification
VAPT is not a one-time activity; it requires regular assessments to keep up with evolving cyber threats. Organizations must implement suggested improvements and schedule periodic evaluations to maintain their certification and security effectiveness.
Conclusion
VAPT certification is a cornerstone of robust cybersecurity, offering organizations protection against cyber threats and compliance with regulations. By adopting VAPT, businesses can secure their systems, build trust with stakeholders, and stay ahead in an increasingly digital world.
0 notes