#SetObjectives
Explore tagged Tumblr posts
Text
Set S.M.A.R.T Goals
Never underestimate the power of setting S.M.A.R.T. goals. People often find it challenging to take action towards their goals because they don’t know where to start. Or they have started, but it doesn’t seem like they’re going anywhere. Yes, it can be overwhelming, but S.M.A.R.T. goals prompt you to act on what you want to achieve.
S.M.A.R.T. goals mean:
Specific
Measurable
Achievable
Relevant
Time-based
With this structured guide to goal-setting, you’ll know what to do, when to do it, and why you do it.
Note that procrastination is a success killer. Avoid it as much as you can. It’s a corrosive behavior only the mediocre possess. So no more excuses, and start working towards bettering yourself now.
#motivation#quotes of tumblr#blog#get motivated#plan#setobjectives#stayconfident#tumblr milestone#goals
3 notes
·
View notes
Text
What are the best practices for integrating automation into existing infrastructure?
Integrating automation into existing infrastructure can significantly enhance efficiency, reduce errors, and optimize resource usage. However, it requires careful planning and execution to ensure a smooth transition and effective integration. Here are some best practices for integrating automation into existing infrastructure:
1.Assess Current Infrastructure
Conduct a Comprehensive Audit: Start by assessing your current infrastructure to identify areas where automation can be most beneficial. Understand existing processes, workflows, and systems.
Identify Pain Points: Focus on repetitive, time-consuming, and error-prone tasks that could be improved with automation.
2. Set Clear Objectives
Define Automation Goals: Establish clear objectives for what you want to achieve with automation, such as reducing operational costs, improving efficiency, or enhancing scalability.
Prioritize Tasks: Determine which processes should be automated first based on their impact, complexity, and return on investment (ROI).
3. Choose the Right Automation Tools
Evaluate Automation Platforms: Select tools and platforms that are compatible with your existing infrastructure and meet your automation needs. Consider factors like scalability, ease of use, integration capabilities, and vendor support.
Open Standards and Interoperability: Opt for tools that adhere to open standards and offer interoperability to ensure seamless integration with existing systems.
4. Ensure Security and Compliance
Data Security: Implement strong security measures to protect sensitive data during and after the automation process. This includes encryption, access control, and regular security audits.
Compliance Considerations: Ensure that the automation processes comply with industry regulations and standards, especially in sectors like finance, healthcare, and data protection.
5. Involve Stakeholders Early
Collaboration with Teams: Involve relevant stakeholders, including IT, operations, and business units, from the early stages of planning. Their input is crucial for identifying needs and potential challenges.
User Training: Provide training to employees to help them understand and adapt to the new automated processes.
6. Adopt a Phased Approach
Pilot Projects: Start with small, manageable pilot projects to test the effectiveness of automation tools and processes before scaling up.
Gradual Implementation: Gradually expand automation across the organization to minimize disruption and allow for adjustments based on feedback.
7. Integration with Existing Systems
APIs and Middleware: Use APIs and middleware to facilitate communication between the automation tools and existing systems. This helps in creating a cohesive environment where automated processes can interact seamlessly with current infrastructure.
Data Consistency: Ensure that data remains consistent across automated and non-automated systems. Implement synchronization mechanisms to keep databases and applications aligned.
8. Monitor and Optimize
Continuous Monitoring: Implement monitoring tools to track the performance of automated processes in real-time. This helps in identifying bottlenecks, failures, and areas for improvement.
Regular Optimization: Continuously review and optimize automated processes to ensure they remain efficient and effective as your infrastructure evolves.
9. Create a Robust Backup and Recovery Plan
Redundancy and Failover: Implement redundancy and failover mechanisms to ensure business continuity in case of automation failures.
Backup Strategies: Regularly back up data and configurations to prevent data loss during the automation process.
10. Documentation and Knowledge Sharing
Comprehensive Documentation: Document all automated processes, including workflows, configurations, and troubleshooting steps. This is vital for maintaining and scaling automation.
Knowledge Sharing: Encourage knowledge sharing across teams to build a culture of automation and empower employees to leverage automation tools effectively.
11. Evaluate and Adapt
Post-Implementation Review: After implementation, conduct a review to assess whether the automation goals have been met. Gather feedback from users and stakeholders to identify areas for further improvement.
Adapt to Changes: Be prepared to adapt and modify automated processes as business needs evolve and new technologies emerge.
12. Consider Scalability and Flexibility
Plan for Future Growth: Ensure that the automation solutions you implement can scale with your business needs and adapt to changes in your infrastructure.
Modular Automation: Implement modular automation solutions that can be easily modified or expanded as new requirements arise.
By following these best practices, organizations can successfully integrate automation into their existing infrastructure, achieving the desired benefits while minimizing risks and disruptions.
#AssessInfrastructure#SetObjectives#ChooseTools#EnsureSecurity#InvolveStakeholders#PhasedApproach#SystemIntegration#MonitorOptimize#BackupRecovery#Documentation#EvaluateAdapt#Scalability#UserTraining
0 notes
Photo




SCP-ICON - Genderfluid Flags Set
Objects:
Genderfae - Genderfaun
Genderflor - Genderfrith
Please credit our blog when using - failure to do so will result in [DATA EXPUNGED]. More icons are available on our blog!
#mod GHOST#scp#scp foundation#icons#scp icons#pride icons#scp pride icons#pride#genderfae pride#genderfaun pride#genderflor pride#genderfrith pride#genderfae#genderfaun#genderflor#genderfrith
46 notes
·
View notes
Text
MSN
MSN =0)return this.storage.key(e)}setObject(e,t){void 0!==t?this.setItem(e,JSON.stringify(t)):this.removeItem(e)}removeObject(e){const t=this.removeItem(e);if(null!=t)return o(t)}setItem(e,t){if(this.supported)try{this.storage.setItem(e,t)}catch(e){a.logError(e)}}get length(){if(this.supported)return this.storage.length}removeItem(e){if(this.supported){const t=this.getItem(e);return…
View On WordPress
0 notes
Photo

One of the biggest issues for social media managers is #timemanagement. #Productivity is a related concern. It comes down to #goals, #motivation, #passion, #diligence, #persistence. It takes a lot of #focus to use your time well. What is one thing you do to make your #SMM time more effective? (SMM = social media marketing) l l #qstsmm #time #productive #success #startuplife #entrepreneurlife #entrepreneur #startup #smallbiz #motivational #encouragement #lifegoals #setobjectives #followthrough #qstsmm https://ift.tt/2PnpIN1
3 notes
·
View notes
Text
MySQL Connector/J 8.0.24 has been released
Dear MySQL users, MySQL Connector/J 8.0.24 is the latest General Availability release of the MySQL Connector/J 8.0 series. It is suitable for use with MySQL Server versions 8.0 and 5.7. It supports the Java Database Connectivity (JDBC) 4.2 API, and implements the X DevAPI. This release includes the following new features and changes, also described in more detail on https://dev.mysql.com/doc/relnotes/connector-j/8.0/en/news-8-0-24.htmlAs always, we recommend that you check the “CHANGES” file in the download archive to be aware of changes in behavior that might affect your application. To download MySQL Connector/J 8.0.24 GA, see the “General Availability (GA) Releases” tab at http://dev.mysql.com/downloads/connector/j/Enjoy! Changes in MySQL Connector/J 8.0.24 (2021-04-20, General Availability) * Functionality Added or Changed * Bugs Fixed Functionality Added or Changed * X DevAPI: For X Protocol connections, the Server now provides three new kinds of notifications for disconnections: + Server shutdown: This is due to a server shutdown. It causes Connector/J to terminate all active and idle sessions connected to the server in the connection pool with the error message “Server shutdown in progress”. + Connection idle: This is due to the connection idling for longer than the relevant timeout settings. It causes Connector/J to close the current connection with the error message “IO Read error: read_timeout exceeded”. + Connection killed: This is due to the connection being killed by another client session. It causes Connector/J to close the connection in the current session with the error message “Session was killed”. * A new connection property, scrollTolerantForwardOnly, has been introduced, which preserved the legacy behavior of Connector/J 8.0.17 and earlier by tolerating backward and absolute cursor movements on result sets of type ResultSet.TYPE_FORWARD_ONLY. This is for maintaining compatibility with legacy code that took advantage of the old behavior. See the description for scrollTolerantForwardOnly for details. (Bug #31747910) References: See also: Bug #30474158. * Connector/J now supports “userless” authentication for JDBC connections: When the user for the connection is unspecified, Connector/J uses the name of the OS user who runs the application for authentication with the MySQL server. See Connector/J: Obtaining a connection from the DriverManager (https://dev.mysql.com/doc/connector-j/8.0/en/connector-j-usagenotes-connect-drivermanager.html#connector-j-examples-connection-drivermanager) for more details. * Starting from this release, whenever an authentication plugin is explicitly set for the connection property defaultAuthenticationPlugin (https://dev.mysql.com/doc/connector-j/8.0/en/connector-j-connp-props-connection.html#cj-conn-prop_defaultAuthenticationPlugin), the specified plugin takes precedence over the server’s default when Connector/J negotiates a plugin with the server. There is no behavioral change for Connector/J if no value is explicitly set for the property, in which case the server’s choice of default plugin takes precedence over the implicit default of mysql_native_password for Connector/J. See the description of defaultAuthenticationPlugin (https://dev.mysql.com/doc/connector-j/8.0/en/connector-j-connp-props-connection.html#cj-conn-prop_defaultAuthenticationPlugin) for details. * In the past, for JDBC connections, when the server closed a session because a client was idling beyond the period specified by the server’s wait_timeout system variable, Connector/J returned a generic IO error. Connector/J now relays a clearer error message from the server. Bugs Fixed * X DevAPI: Concurrently getting and closing multiple sessions from the same X DevAPI Client object might result in a ConcurrentModificationException thrown by Connector/J at the closing of a session. (Bug #31699993) * X DevAPI: Under some specific conditions, when using Deflate as the algorithm for compression of X Protocol connections, Connector/J threw an AssertionFailedException (ASSERTION FAILED: Unknown message type: 57). It was because when a compressed packet was just a few bytes longer than the size of some internal buffer used by a Java InflaterInputStream, the leftover bytes from the inflate procedure were being discarded by Connector/J, causing inflation of subsequent packets to fail. With this fix, no data bytes are discarded, and the inflation works as expected. (Bug #31510398, Bug #99708) * When a SecurityManager was in place, connections to a MySQL Server could not be established unless the client had been properly configured to use SASL-based LDAP authentication. It was because the AuthenticationLdapSaslClientPlugin in Connector/J requires a special permission to load the provider MySQLScramShaSasl when a SecurityManager is in place; but since the provider was loaded by a static initializer during initialization for the plugin, the lack of the permission was causing an error and then failures for all connections, even if the plugin was never used or enabled. This fix changes how the provider is loaded: the loading now happens only at the plugin instance’s initialization and the initialization was deferred to the time when the plugin is actually needed, so that connections that do not use SASL-based LDAP authentication are unaffected by security settings regarding the plugin. (Bug #32526663, Bug #102188) * When using Connector/J 8.0.23, ResultSetMetaData.getColumnClassName() did not return the correct class name corresponding to DATETIME columns. (Bug #32405590, Bug #102321) * Creation of an UpdatableResultSet failed with a NullPointerException when it was generated by querying a view with a derived value. (Bug #32338451, Bug #102131) * Using getLong() on the CHAR_OCTET_LENGTH column of the ResultSet for DatabaseMetaData.getProcedureColumns() (or getFunctionColumns()) resulted in a NumberOutOfRange exception when the column’s value exceeded 2^32 − 1. With this patch, the value of 2^32 − 1 is returned in the situation. (Bug #32329915, Bug #102076) * Connections to a server could not be established when the user supplied an implementation of the ConnectionPropertiesTransform interface using the connection property propertiesTransform. This was because Connector/J called PropertyKey.PORT.getKeyName() instead of PropertyKey.HOST.getKeyName() for getting the host name, and that has been corrected by this fix. (Bug #32151143, Bug #101596) * A NullPointerException was returned when a statement that could not be used as a ServerPreparedStatement was executed and the connection property useUsageAdvisor (https://dev.mysql.com/doc/connector-j/8.0/en/connector-j-connp-props-debugging-profiling.html#cj-conn-prop_useUsageAdvisor) was set to true. With this fix, a SQLException is returned instead. (Bug #32141210, Bug #101558) * Using the setSessionMaxRows() method on a closed connection resulted in a NullPointerException. With this fix, a SQLNonTransientConnectionException is thrown instead, with the error message “No operations allowed after connection closed.” (Bug #22508715) * Using the setObject() method for a target type of Types.TIME resulted in a SQLException when the value to be set had a fractional part, or when the value did not fit any pattern described in Date and Time Literals (https://dev.mysql.com/doc/refman/8.0/en/date-and-time-literals.html). This patch introduced a new logic that can handle fractional parts; also, it performs the conversion according to the patterns of the literals and, when needed, the target data type. (Bug #20391832) Enjoy and thanks for the support! On Behalf of the MySQL Engineering Team, Nawaz Nazeer Ahamed https://insidemysql.com/mysql-connector-j-8-0-24/
0 notes
Text
Fun with arrow and higher order functions
Through this small article, we are going to overview arrow functions and higher order functions in JavaScript.
Arrow functions
In JavaScript, arrow functions were introduced by ECMAScript 6 and are, in a way, a shorter manner to write functions. They allow us to write functions that are small, inline and single-purpose. They have a concise syntax, implicit returns and share lexical "this" with the parent scope.
Arrow functions allow us to do something like this:
//*************************************// //***** NOT USING ARROW FUNCTIONS *****// //*************************************// var sayHello = function() { console.log('Hello world!'); } var splitePhrase = function(phrase) { return phrase.split(' '); } var multiply = function(x, y) { return x * y; } var setObject = function setProperties(id, name) { return { id: id, name: name }; }; //*********************************// //***** USING ARROW FUNCTIONS *****// //*********************************// let sayHello = () => { console.log('Hello world!'); } let splitePhrase = phrase => phrase.split(' '); let multiply = (x, y) => x * y; let setObject = (id, name) => ({id: id, name: name});
The side effect of arrow functions is, because they are anonymous, even if we place them in variables, they will not give us very good stack traces. The other thing is we can not use them as constructors because they don’t have a prototype property or other internal methods.
Higher order functions
A higher-order function is a function that can take another function as an argument, or that returns a function as a result. The fact that we can place a function into another function allows us to compose small functions into bigger functions. The function passed to the other function is also known as callback. Let's have some examples:
Filter
The filter function returns an array filled with all elements of a provided array that had passed a specific test.
const animals = [ { name: 'Spike', species: 'dog' }, { name: 'Garefield', species: 'cat' }, { name: 'Tom', species: 'cat' }, { name: 'Droopy', species: 'dog' } ]; var isCat = (function(animal) { return animal.species === 'cat'; }); var cats = animals.filter(isCat); console.log(cats); /** * Will output * Array(2) * 0 : "Garefield" * 1 : "Tom" */
Map
We can use map if we want to create an array with the values of another array after each of them went through a specific function.
const persons = [ { name: 'John', browser: 'Chrome' }, { name: 'Jane', browser: 'Firefox' }, { name: 'Sam', browser: 'Chrome' }, { name: 'Paul', browser: 'Edge' } ]; var names = persons.map(function(person) { return person.name; }); console.log(names); /** * Will output * Array(4) * 0 : "John" * 1 : "Jane" * 2 : "Sam" * 3 : "Paul" */
Reduce
The reduce function reduces an array to a single value. It executes a provided function for each value of the array, from left to right.
var orders = [ { amount: 210 }, { amount: 35 }, { amount: 142 }, { amount: 47 } ]; var totalAmount = orders.reduce(function(sum, order) { return sum + order.amount }, 0); console.log(totalAmount); /** * Will output * 43 */
Let's have fun
Now, let's try to put all this information together. For some reasons, let's say we are working on a brand new video game where some Italian plumbers have to rescue a princess from a dangerous dragon monster that breathes fire (any resemblance to fictional famous characters is purely coincidental).
Down bellow, we have an array with some events concerning the big monster:
const bigMonsterEvilDragonEvents = [ { type: 'attack', value: 12, target: 'italian-plumber-1' }, { type: 'attack', value: 12, target: 'italian-plumber-2' }, { type: 'fire', value: 40 }, { type: 'jump', target: 'bridge' }, { type: 'attack', value: 23, target: 'italian-plumber-1' }, { type: 'jump', target: 'tower' }, { type: 'laugh', value: 95 }, { type: 'attack', value: 6, target: 'italian-plumber-2' }, { type: 'attack', value: 15, target: 'italian-plumber-1' } ];
If we want to know how much damage the big monster made on the Italian Plumber 1 at the end of all of these events, using what we previously saw, we can simply do it like this:
const totalDamageOnItalianPlumber1 = bigMonsterEvilDragonEvents .filter(e => e.type === 'attack') .filter(e => e.target === 'italian-plumber-1') .map(e => e.value) .reduce((prev, x) => (prev || 0) + x); console.log(totalDamageOnItalianPlumber1); /** * Will output * 50 */
That's it! That is how we can use arrow functions and higher order functions to easily have access to some results that would require more lines of code without these last functions.
0 notes
Text
THE LAST WEEK OF MY INTERNSHIP AND THE SET OBJECTIVES THAT I ACHIEVED
My last week has been filled with activities in achieving both my research data collections objective and doing field work under the Health Directorate. Lucky I have been able to successfully achieve them all.
Here is the background of data collected for my thesis.
Learning Objectives I:
Finding the barriers and driving force to food hygiene and safety practices among school food vendors in Winneba District, Ghana.
INTERVIEW GUIDE
Research Topic :
Food hygiene and safety practices among school food vendors in Winneba Municipality.
Research Question:
What are the barriers and the driving factors school food vendors face in providing safer and healthy food for school children in Winneba Municipality?
Methodological approach:
Qualitative approach
Focus Group Discussion
Key Informants Interview
Focus group interview
Obersevation
Key Area of Investigation:
Food Safety
Hygiene of the Environment
Personal Hygiene
Healthy Food and Quality
Institutional Legislative and Law Control
Operation Benefits
Interview Participants
1. Key informative interview:
8 key people in the Municipality.
District Nutritional officer
Community Health Nurse
District Disease Control Officer
School Head Teacher
Child Reproductive Center - School Health Program Officer
School Welfare Officer
Environmental Health Officer
Community Radio – Sanitation Program Present-Member of the Local Assembly
Interview:
10 School Food Vendors from 10( ten) Government schools in the Winneba Municipality.
3 parents with children attending some government schools in the Winneba Municipality.
3. Focus Group Discussion :
6 vendors from selected government schools in the Winneba Municipality
Observation.
From some selected School food Vendors operational activities.
Here is the municipal map where my research data collection covered.
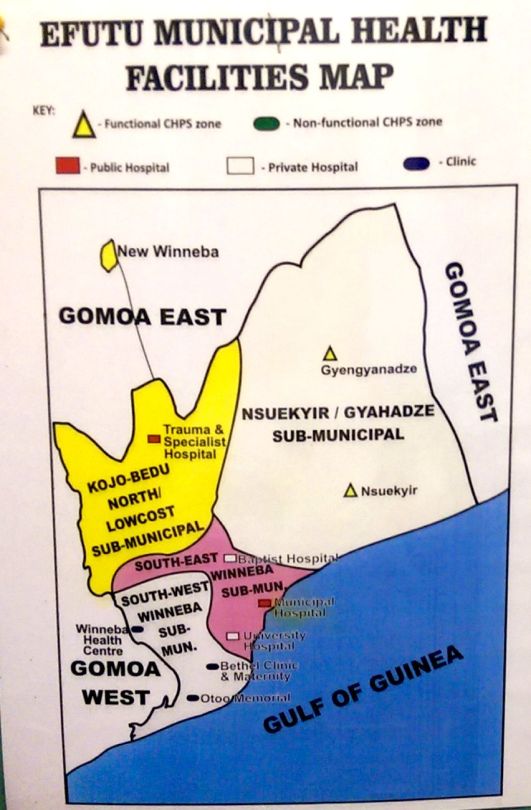
Effutu Municipality Map
Beside collecting the data for my thesis, I did took part in the Winneba Municipal Health Directorate Works to gain a better understand of the works under each of the departments. Here are the set objectives that I attained.
Learning Objectives 2 :
To gain a greater understanding of the work of the Municipal Health Directorate, Winneba.
Learning Objectives 3:
To gain understanding of the work of the various departments under the Municipal Health Directorate.
Learning Objectives 4:
Focusing on more practical works with the Environmental and Health Department.
13 notes
·
View notes
Text
MSN
MSN =0)return this.storage.key(e)}setObject(e,t){void 0!==t?this.setItem(e,JSON.stringify(t)):this.removeItem(e)}removeObject(e){const t=this.removeItem(e);if(null!=t)return o(t)}setItem(e,t){if(this.supported)try{this.storage.setItem(e,t)}catch(e){a.logError(e)}}get length(){if(this.supported)return this.storage.length}removeItem(e){if(this.supported){const t=this.getItem(e);return…
View On WordPress
0 notes
Text
MSN
MSN =0)return this.storage.key(e)}setObject(e,t){void 0!==t?this.setItem(e,JSON.stringify(t)):this.removeItem(e)}removeObject(e){const t=this.removeItem(e);if(null!=t)return o(t)}setItem(e,t){if(this.supported)try{this.storage.setItem(e,t)}catch(e){a.logError(e)}}get length(){if(this.supported)return this.storage.length}removeItem(e){if(this.supported){const t=this.getItem(e);return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”valid”:”expired”}function u(){return r=r||void 0===r&&Object(o.a)().getObject(“1s-tokens”)||null,r}function d(e){s=e;const{accessToken:t,idToken:n,expiresOn:i}=e||{};t&&n&&i?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:i}):Object(o.a)().removeItem(“1s-tokens”)}function l(){return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”valid”:”expired”}function u(){return r=r||void 0===r&&Object(o.a)().getObject(“1s-tokens”)||null,r}function d(e){s=e;const{accessToken:t,idToken:n,expiresOn:i}=e||{};t&&n&&i?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:i}):Object(o.a)().removeItem(“1s-tokens”)}function l(){return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”Valid”:”Expired”}function a(){return i=i||void 0===i&&Object(o.a)().getObject(“1s-tokens”)||null,i}function u(e){r=e;const{accessToken:t,idToken:n,expiresOn:i}=e||{};t&&n&&i?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:i}):Object(o.a)().removeItem(“1s-tokens”)}function d(){return r}},”8WO2″:function(e,t,n){“use strict”;n.d(t,”e”,(function(){return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”Valid”:”Expired”}function a(){return i=i||void 0===i&&Object(o.a)().getObject(“1s-tokens”)||null,i}function u(e){r=e;const{accessToken:t,idToken:n,expiresOn:i}=e||{};t&&n&&i?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:i}):Object(o.a)().removeItem(“1s-tokens”)}function d(){return r}},”8WO2″:function(e,t,n){“use strict”;n.d(t,”e”,(function(){return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”Valid”:”Expired”}function a(){return i=i||void 0===i&&Object(o.a)().getObject(“1s-tokens”)||null,i}function u(e){r=e;const{accessToken:t,idToken:n,expiresOn:i}=e||{};t&&n&&i?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:i}):Object(o.a)().removeItem(“1s-tokens”)}function d(){return r}},”8WO2″:function(e,t,n){“use strict”;n.d(t,”e”,(function(){return…
View On WordPress
0 notes
Text
MSN
MSN new Date?”Valid”:”Expired”}function a(){return r=r||void 0===r&&Object(o.a)().getObject(“1s-tokens”)||null,r}function u(e){i=e;const{accessToken:t,idToken:n,expiresOn:r}=e||{};t&&n&&r?Object(o.a)().setObject(“1s-tokens”,{accessToken:t,idToken:n,expiresOn:r}):Object(o.a)().removeItem(“1s-tokens”)}function d(){return i}},”8WO2″:function(e,t,n){“use strict”;n.d(t,”e”,(function(){return…
View On WordPress
0 notes