#RTO Standards
Explore tagged Tumblr posts
Text
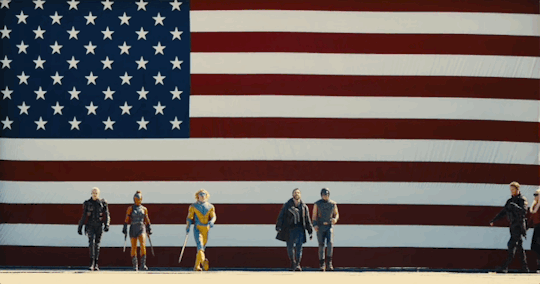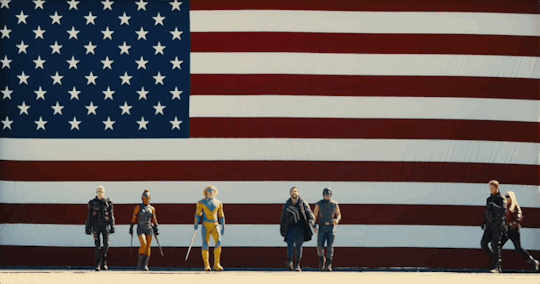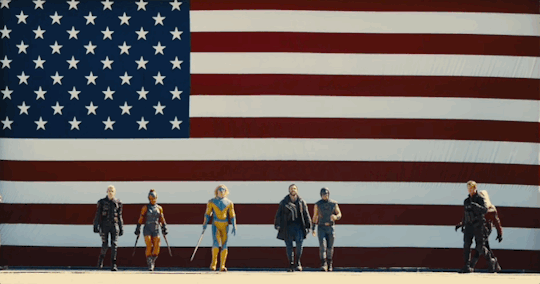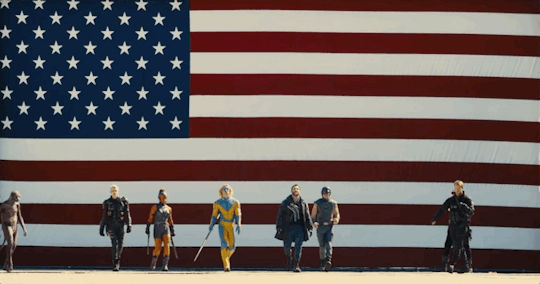
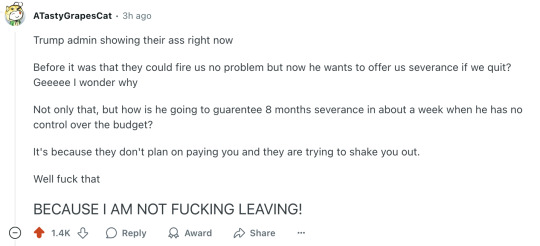
Trump admin showing their ass right now
Before it was that they could fire us no problem but now he wants to offer us severance if we quit? Geeeee I wonder why
Not only that, but how is he going to guarentee 8 months severance in about a week when he has no control over the budget?
It's because they don't plan on paying you and they are trying to shake you out.
Well fuck that
BECAUSE I AM NOT FUCKING LEAVING!
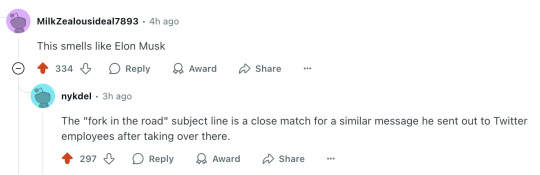
This smells like Elon Musk
The "fork in the road" subject line is a close match for a similar message he sent out to Twitter employees after taking over there.
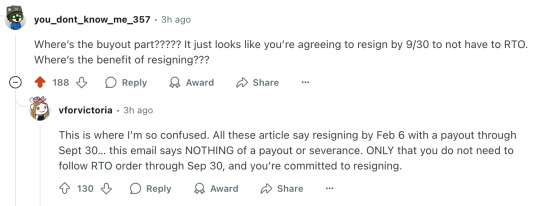
Where’s the buyout part????? It just looks like you’re agreeing to resign by 9/30 to not have to RTO. Where’s the benefit of resigning???
This is where I’m so confused. All these article say resigning by Feb 6 with a payout through Sept 30… this email says NOTHING of a payout or severance. ONLY that you do not need to follow RTO order through Sep 30, and you’re committed to resigning.
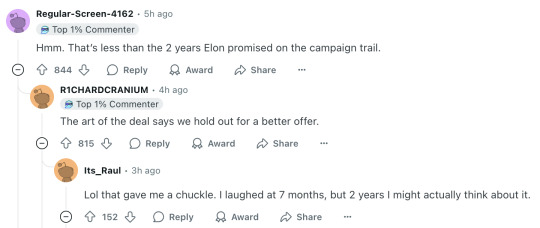
Hmm. That’s less than the 2 years Elon promised on the campaign trail.
The art of the deal says we hold out for a better offer. Lol that gave me a chuckle. I laughed at 7 months, but 2 years I might actually think about it.
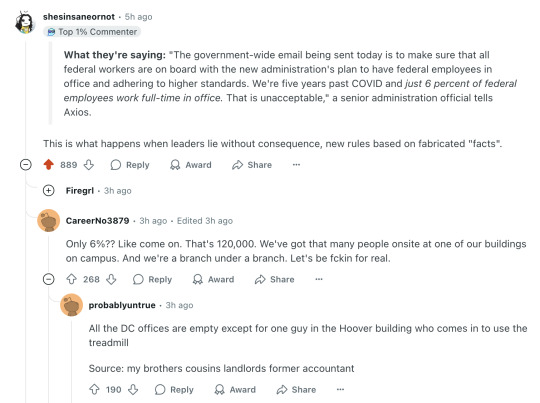
What they're saying: "The government-wide email being sent today is to make sure that all federal workers are on board with the new administration's plan to have federal employees in office and adhering to higher standards. We're five years past COVID and just 6 percent of federal employees work full-time in office. That is unacceptable," a senior administration official tells Axios.
This is what happens when leaders lie without consequence, new rules based on fabricated "facts".
Only 6%?? Like come on. That's 120,000. We've got that many people onsite at one of our buildings on campus. And we're a branch under a branch. Let's be fckin for real.
All the DC offices are empty except for one guy in the Hoover building who comes in to use the treadmill Source: my brothers cousins landlords former accountant
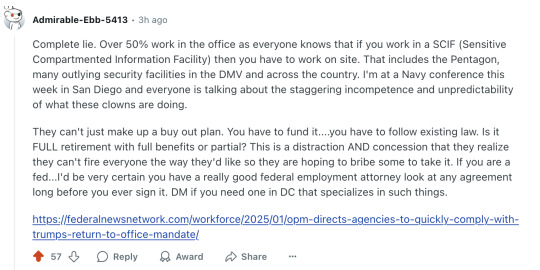
Complete lie. Over 50% work in the office as everyone knows that if you work in a SCIF (Sensitive Compartmented Information Facility) then you have to work on site. That includes the Pentagon, many outlying security facilities in the DMV and across the country. I'm at a Navy conference this week in San Diego and everyone is talking about the staggering incompetence and unpredictability of what these clowns are doing.
They can't just make up a buy out plan. You have to fund it....you have to follow existing law. Is it FULL retirement with full benefits or partial? This is a distraction AND concession that they realize they can't fire everyone the way they'd like so they are hoping to bribe some to take it. If you are a fed...I'd be very certain you have a really good federal employment attorney look at any agreement long before you ever sign it. DM if you need one in DC that specializes in such things.
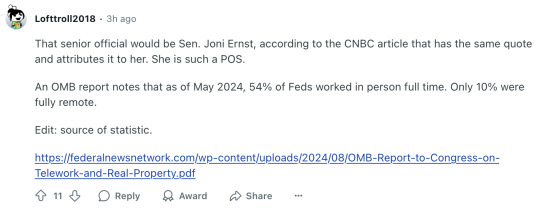
That senior official would be Sen. Joni Ernst, according to the CNBC article that has the same quote and attributes it to her. She is such a POS.
An OMB report notes that as of May 2024, 54% of Feds worked in person full time. Only 10% were fully remote.
Edit: source of statistic.
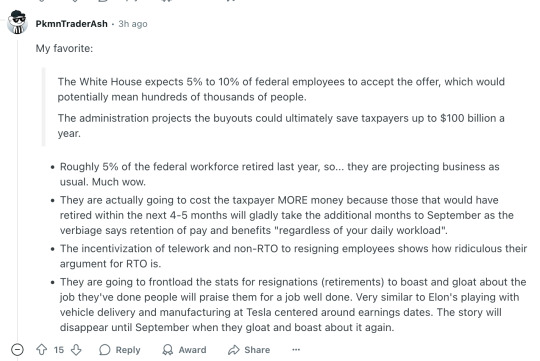
My favorite:
The White House expects 5% to 10% of federal employees to accept the offer, which would potentially mean hundreds of thousands of people.
The administration projects the buyouts could ultimately save taxpayers up to $100 billion a year.
Roughly 5% of the federal workforce retired last year, so... they are projecting business as usual. Much wow.
They are actually going to cost the taxpayer MORE money because those that would have retired within the next 4-5 months will gladly take the additional months to September as the verbiage says retention of pay and benefits "regardless of your daily workload".
The incentivization of telework and non-RTO to resigning employees shows how ridiculous their argument for RTO is.
They are going to frontload the stats for resignations (retirements) to boast and gloat about the job they've done people will praise them for a job well done. Very similar to Elon's playing with vehicle delivery and manufacturing at Tesla centered around earnings dates. The story will disappear until September when they gloat and boast about it again.

If they think they are taking my pension, vet pref, work life balance and COMMITMENT to service for 18k after taxes, they are insane. I will be posted up in my office fueled by nothing but duty and spite until I am 90 years old. Telework doesn't move me enough to let them steal what I have worked hard to earn. F*ck them. Great news for those who need it though, seriously.
"All things are possible through spite, it strengthens me."
I have an unreasonable amount of stubbornness and the military taught me how to stew in it. Embrace the suck
I love that energy. I worry they won't even get buyouts though. I think Trump is hoping people quit and then when they don't get their money, there's nothing legally they can do. They can only pay 25k max, and whoever resigns won't have any legal paperwork saying they're owed a buyout. Just the empty promises of a con man.
Edit: Someone posted the letter in another thread. It's not even a buyout. Just an offer to be exempt from RTO on the condition that you resign on or before Sept 30.
Another edit: other people have read it much more closely and clearly than me. Read all the comments below.

Edit again bc some of you can't be bothered to read: there was no email when I initially commented this. Now there's an email. Go read that.
Original comment:This is very likely a bait and switch. Feb 6th is way too soon for OPM and your agency to formulate a plan of which jobs/series qualify and then gather the money to offer it.
Remember, we're still under a CR until March 14th.. We don't even have the money to go to April!!
Also, I know they're breaking laws left and right, but the statutory max payout is $25k. They legally can't pay you more than that even if they had it. I doubt they're gonna break the law in your favor.
Bottom line this is a complete BS scam designed to fool people into resigning by next week only for them to rug pull you after you're gone.
Edit to add: ok guys I get it, there's a email and a memo out there. Just remember, I wrote this comment when the details were a few paragraphs in an AP article. Like seriously, who would've thought he'd just put people on admin leave for the rest of the year?!? Normal buyouts have rules, he's ignoring them. Guess I shouldn't be surprised. They're literally creating no-show jobs
But caution is still warranted... we don't have a full year's budget, if there's cuts in the rest of your agency's budget then they're fucked. All those no-show jobs are gonna be like an anchor until Oct 1
Not a Fed, but helping some out. They've overplayed their hand, they have to offer buyouts because they cannot fire folks as easily as they thought.
Exactly the reason that we stay
Don't forget there is not NEAR enough physical space to RTO the entire force. They will need to spend a FORTUNE to acquire the additional space needed after 15 years of downsizing, in accordance with the Telework Act of 2010. Doing a blanket RTO was so stupid, wasteful, unnecessary, and a massive burden on taxpayers.
Just like the deportation flights using military transports for optics at a much higher cost than civilian transports. Government efficiency was never the goal. Edit: clarity
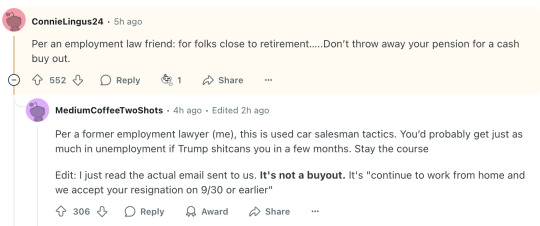
Per an employment law friend: for folks close to retirement…..Don’t throw away your pension for a cash buy out.
Per a former employment lawyer (me), this is used car salesman tactics. You’d probably get just as much in unemployment if Trump shitcans you in a few months. Stay the course Edit: I just read the actual email sent to us. It's not a buyout. It's "continue to work from home and we accept your resignation on 9/30 or earlier"

“The government wide email being sent”. Makes me wonder if this was the reason for the email test from OPM.
It’s like the Nubian prince scam. They’ll pay you IF you provide your bank account and SS#.
It definitely is. NBC references it in their article https://www.nbcnews.com/politics/white-house/trump-administration-offer-federal-workers-buyouts-resign-rcna189661 And it references another article about the server https://www.nbcnews.com/politics/white-house/trump-administration-tests-power-email-every-federal-employee-rcna189126 There are so many illegal things there, but it looks like the press is trying to smooth it over as normal things our government does.
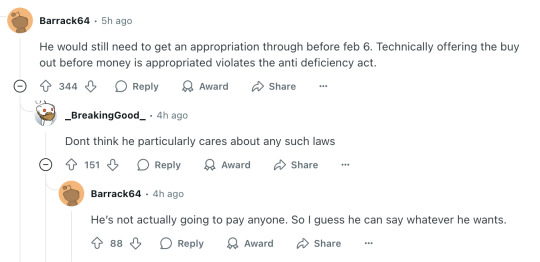
He would still need to get an appropriation through before feb 6. Technically offering the buy out before money is appropriated violates the anti deficiency act.
Dont think he particularly cares about any such laws He’s not actually going to pay anyone. So I guess he can say whatever he wants.
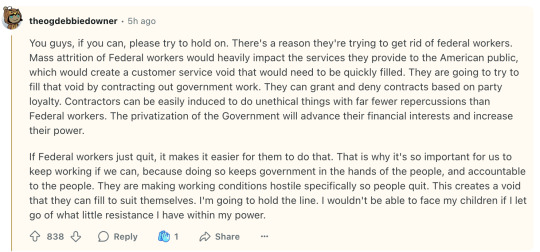
You guys, if you can, please try to hold on. There's a reason they're trying to get rid of federal workers. Mass attrition of Federal workers would heavily impact the services they provide to the American public, which would create a customer service void that would need to be quickly filled. They are going to try to fill that void by contracting out government work. They can grant and deny contracts based on party loyalty. Contractors can be easily induced to do unethical things with far fewer repercussions than Federal workers. The privatization of the Government will advance their financial interests and increase their power.
If Federal workers just quit, it makes it easier for them to do that. That is why it's so important for us to keep working if we can, because doing so keeps government in the hands of the people, and accountable to the people. They are making working conditions hostile specifically so people quit. This creates a void that they can fill to suit themselves. I'm going to hold the line. I wouldn't be able to face my children if I let go of what little resistance I have within my power.
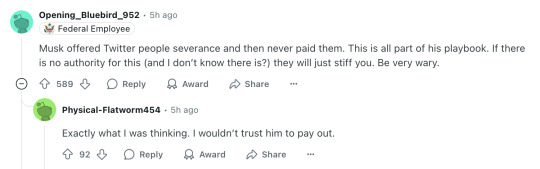
Musk offered Twitter people severance and then never paid them. This is all part of his playbook. If there is no authority for this (and I don’t know there is?) they will just stiff you. Be very wary.
Exactly what I was thinking. I wouldn’t trust him to pay out.
This sounds like that they know the RTO Executive Order is on shaky ground, and is most likely violating the Telework Act of 2010 law. And they're trying to get ahead of any lawsuits.
My question is, what is so significant about the February 6th date?
I'm not sure it's about RTO, but that they're realizing behind the scenes that it's gonna be harder for them to downsize via "Schedule F-and-fire" than they thought, and after that they're running out of ways to get feds out of employment without them voluntarily quitting for these reasons.
This is it, exactly. This email is a last ditch effort to scare people after folks didn't quit in waves last week, lol
Friend they don't though. Most people are believing the narrative that we're all "overpaid rats" that aren't doing our jobs. I wish people knew what we do, and how little we're paid compared to our private sector counterparts. Most of us genuinely do it because we give a shit about the mission. No one is talking about what this is doing to us - we're not being counted as people. There is not public outcry about how this is going to negatively impact people, because people still refuse to believe that anyting bad is going to happen.
Please let people know this is what's happening. So many think yeah, get rid of those lazy government workers and shrink government. They don't realize what he's really doing, trying to get rid of laws or regulations so he can do what he wants. He wants to get rid of federal workers because we stand in his way. If feds are really doing nothing how does all government business get done everyday, by magic elves? He wants to be able to hire his family and friends and contractors so his rich friends can make even more money and he can fire them easily if they don't agree with him or agree to do something illegal. This isn't just about federal workers. All of America should be seriously concerned right now but they just don't get it.
5 notes
·
View notes
Text
Why Melbourne is the Best Place for Your Confined Space Entry Training

When it comes to safety-critical industries, few areas are more heavily regulated — and rightly so — than confined space work. Whether you’re entering tanks, pits, tunnels, or silos, the risks are significant: from toxic atmospheres and engulfment hazards to restricted movement and limited oxygen levels. That’s why proper Confined Space Entry (CSE) training is not just recommended — it’s mandatory under Australian law.
But where should you undergo this essential training?
Enter Melbourne, a city uniquely positioned to offer world-class confined space training. In this article, we'll unpack exactly why Melbourne stands out as the premier destination for confined space education and certification — and why investing in training here will give your career, skills, and safety credentials a serious boost.
1. Melbourne’s World-Class Training Providers
Melbourne is home to some of Australia's top RTOs (Registered Training Organisations) specializing in workplace safety and industrial training. These providers offer nationally accredited courses, often meeting and exceeding the standards set by the Australian Skills Quality Authority (ASQA).
Some key names include:
WAM Training
Vertical Horizons
Training Ahead Australia
AlertForce
ATC – Australian Training Company
These organisations have years (even decades) of experience delivering training tailored to real-world industry requirements. Many instructors have direct backgrounds in mining, construction, energy, and emergency services, offering not just textbook knowledge but lived experience.
Pro Tip: Look for courses that deliver training to the standard of RIIWHS202E (Enter and work in confined spaces) or RIIWHS204E (Work safely at heights) if your role requires dual certifications.
2. Access to Cutting-Edge Facilities
One of Melbourne’s biggest advantages is access to state-of-the-art training facilities.
Training centers here often simulate real confined space environments. Expect to train using:
Vertical and horizontal confined spaces
Tanks, culverts, and pipe systems
Realistic rescue simulations
Gas detection equipment
Harness and breathing apparatus
This simulation-based training gives participants hands-on, muscle-memory skills, not just theoretical knowledge. You’ll get comfortable with the gear, techniques, and high-pressure situations you'll actually face in the field.
Instructors often create emergency scenarios where participants must perform live rescues, enhancing both competence and confidence.
3. Melbourne’s Strong Safety Culture
Melbourne — and Victoria more broadly — leads Australia in workplace safety initiatives. WorkSafe Victoria is one of the country's most active safety regulators, frequently issuing updated guidelines, running safety campaigns, and conducting audits.
For workers, this means two things:
Training providers must maintain extremely high standards to stay accredited.
Workers trained in Victoria are often seen as having some of the most rigorous safety education in Australia.
In fact, many companies outside Victoria actively seek workers who have been trained in Melbourne, simply because they trust the strength of the local safety culture.
4. Courses Designed for Different Industries
Not every confined space is the same. Melbourne’s providers understand that workers from different industries need tailored confined space training. Whether you’re in:
Construction
Mining and resources
Utilities and energy
Manufacturing
Telecommunications
Local councils and water authorities
… you’ll find courses that match your real-world environments.
Some providers even offer industry-specific confined space rescue training, perfect for roles where you might have to act as a standby person or rescue operator.
5. Flexible Learning Options
Melbourne understands that not everyone can commit to long, inflexible training schedules. That's why many RTOs offer:
One-day intensive courses
Weekend classes
Corporate group training
On-site training at your workplace
Blended learning (theory online + practical onsite)
This flexibility allows both individuals and companies to schedule training around real work demands, minimizing downtime.
For employers, having on-site options is especially attractive: trainers bring equipment and scenarios directly to your job site, ensuring site-specific compliance and familiarity.
6. Competitive Pricing and Government Funding
Melbourne’s market competition means training costs are reasonable, especially given the high quality. You’ll find courses ranging from $250 to $500 per person, depending on course length and complexity.
Plus, many training programs qualify for government subsidies under the Skills First Funding or similar Victorian government programs.
This means eligible individuals and businesses can drastically reduce their out-of-pocket costs while still accessing top-tier training.
7. Experienced and Highly Qualified Trainers
One of the things that sets Melbourne apart is the quality of its trainers. Many instructors are:
Former firefighters, paramedics, or SES volunteers
Specialists in technical rescue
Holders of Certificate IV in Training and Assessment (TAE40122)
Certified in multiple rescue disciplines (rope rescue, vertical rescue, breathing apparatus use)
Learning from people who’ve genuinely been there and done that brings a richness to the training you won’t find from a purely academic course.
You'll not only learn what the textbook says — you'll learn what really works when lives are on the line.
8. Emphasis on Practical Emergency Response Skills
Completing a confined space course in Melbourne doesn’t just mean "ticking a compliance box."
You will:
Use gas monitors, harnesses, tripods, and retrieval winches.
Practice lock-out/tag-out procedures.
Conduct mock entries and rescues.
Learn risk assessment, hazard identification, and permit procedures.
Understand emergency response protocols.
This hands-on learning builds a culture of readiness, vital for industries where confined space accidents can become fatal within minutes.
9. Beautiful City, Easy Access
Beyond the training itself, Melbourne is simply an amazing city to visit and train in.
Convenient transport links, affordable accommodation, and incredible food, arts, and culture scenes make it easy to combine your training trip with a mini-break or professional networking opportunity.
Many training centers are located close to major hubs like:
Melbourne CBD
Dandenong
Tullamarine
Laverton
Clayton
This makes commuting to and from your course easy and stress-free.
10. Strong Career Outcomes
Finally, Melbourne-based confined space training sets you up for excellent job opportunities.
Confined space entry skills are in demand across:
Oil and gas
Water and sewage
Rail and infrastructure
Renewable energy (wind turbine maintenance)
Emergency services
Industrial maintenance
With Melbourne’s thriving economy and strong links to regional Victoria, your qualification here opens doors to projects and employers who prioritize highly trained, safety-certified workers.
Some RTOs even offer job placement assistance, LinkedIn endorsements, or direct employer introductions after you finish your course.
Final Thoughts: Melbourne Leads the Way in Confined Space Safety
When it comes to confined space entry training, you want more than just a piece of paper — you want to walk away genuinely prepared, competent, and confident. Melbourne offers the perfect blend of:
Top-tier training providers
Hands-on learning environments
Flexible options
Strong safety culture
Competitive pricing
Investing in your confined space training in Melbourne doesn’t just meet regulatory obligations — it arms you with skills that could save your life or the life of a coworker.
If you’re ready to advance your career, meet compliance requirements, or simply become the safest worker you can be, there’s no better place to start your confined space training journey than right here in Melbourne.
Ready to enroll? Search for a Melbourne RTO offering accredited confined space training today — and take your first step towards becoming a certified confined space professional!
Conclusion
Melbourne stands out as the ideal destination for your confined space entry training. With its world-class training providers, adherence to the latest safety regulations, access to highly experienced instructors, and a strong industry network, Melbourne ensures you gain not only the necessary certifications but also the practical skills needed to excel in real-world environments. Whether you are beginning your career or upgrading your qualifications, choosing Melbourne means investing in quality, safety, and professional growth.
FAQ :
1: Why is Melbourne considered a safe location for confined space entry training?
Melbourne is renowned for its strict safety regulations and standards, making it a safe location for confined space entry training. The city actively promotes workplace safety across various sectors, ensuring that training programs are designed to meet compliance requirements. With experienced trainers and state-of-the-art facilities, participants can learn essential skills in a secure environment, minimizing risks associated with confined space work.
2: What unique features does Melbourne offer for confined space training programs?
Melbourne boasts a variety of specialized training facilities that simulate real confined space environments. This includes access to industrial sites, training rigs, and experienced instructors who provide hands-on experience. The city's commitment to integrating technology into training programs also enhances learning outcomes, ensuring that trainees are well-equipped with the latest techniques and safety protocols.
3: How does Melbourne’s diverse workforce benefit confined space entry training?
Melbourne has a highly diverse workforce that brings a wealth of experience and knowledge from various industries. This diversity enriches confined space entry training sessions, as participants can share insights and learn from each other's backgrounds. Engaging with peers from different sectors fosters a collaborative learning atmosphere, enhancing the overall training experience and preparing participants for real-world scenarios.
4: Are there any regulatory bodies in Melbourne that oversee confined space training?
Yes, Melbourne has several regulatory bodies that oversee workplace safety and training standards, including WorkSafe Victoria. These organizations ensure that training providers comply with safety regulations and provide up-to-date information about confined space entry practices. Participants can take comfort in knowing that their training is aligned with industry standards, contributing to a safer work environment.
5: Why should I choose Melbourne for my confined space entry training over other cities?
Choosing Melbourne for confined space entry training offers numerous advantages. The city is home to highly qualified trainers, superior facilities, and a culture that prioritizes safety. Additionally, Melbourne’s vibrant community and networking opportunities allow participants to connect with industry professionals and potential employers. This combination of quality training and professional growth makes Melbourne the ideal choice for your confined space entry education.
#breathingapparatustraining#melbourneworkingatheightstraining#nationalworkplacetrainingprovider#melbourneworkplacesafetytraining#registeredtrainingorganisation#melbournebreathingapparatustraining#melbourneconfinedspaceentrytraining#confinedspaceentrytraining#workplacesafetytraining#workingatheightstraining
0 notes
Text
ARMxy Edge Controller with CODESYS for Industrial Automation Solutions

Case Details
CODESYS (Controller Development System) is an industrial control system development environment compliant with the IEC 61131-3 standard. It provides a comprehensive suite of tools for PLC (Programmable Logic Controller) programming, debugging, simulation, and commissioning. The combination of ARMxy Industrial Edge Controller and CODESYS delivers an efficient, flexible, and cost-effective solution for industrial automation. Below is a detailed analysis and summary of its advantages:
1. Core Component Analysis
ARMxy Industrial Edge Controller
Low Power Consumption & Compact Design: ARM architecture processors balance low power consumption with sufficient performance, ideal for space-constrained environments and long-term operation.
Industrial-Grade Reliability: Supports wide-temperature operation, vibration/electromagnetic interference resistance, and harsh industrial conditions.
Expandability: Rich interfaces (e.g., GPIO, CAN, Ethernet) enable seamless connectivity to sensors, actuators, and industrial networks.
CODESYS Development Platform
IEC 61131-3 Compliance: Supports five programming languages, including Ladder Diagram (LD) and Structured Text (ST), reducing the learning curve for engineers.
Cross-Platform Runtime: Transforms ARMxy Industrial Edge Controller into powerful soft PLCs via CODESYS Runtime, decoupling hardware from control logic.
Integrated Toolchain: Offers debugging, simulation, HMI visualization, and data management tools to streamline development.
2. Combined Advantages
Cost Efficiency Replaces traditional proprietary PLC hardware, reducing costs while leveraging the computational power of industrial PCs for complex tasks (e.g., data analysis, machine vision).
Flexibility and Scalability
Software-Defined Control: Rapidly adapt control logic to production line changes through CODESYS.
Multi-Protocol Support: Integrates Modbus TCP, EtherCAT, PROFINET, and other industrial protocols for seamless device integration.
Edge Computing Capabilities: Local execution of data preprocessing, AI inference, and other tasks reduces reliance on cloud resources.
Ease of Integration and Maintenance
Open Ecosystem: Supports OPC UA, MQTT, and other standards for MES/ERP system interoperability.
Remote Monitoring & OTA Updates: Enables remote diagnostics and firmware updates via the industrial PC’s networking capabilities.
3. Typical Application Scenarios
Smart Production Line Control: Coordinates robotic arms, conveyors, and inspection systems for flexible manufacturing.
Energy Management: Real-time monitoring of power and hydraulic systems to optimize efficiency.
Packaging and Logistics Automation: High-speed sorting, palletizing, and AGV scheduling.
Data-Intensive Applications: Predictive maintenance (vibration/temperature analysis) or visual quality inspection.
4. Challenges and Solutions
Real-Time Performance
Solution: Use real-time Linux kernels (e.g., Preempt-RT) or RTOS (e.g., FreeRTOS) to ensure microsecond-level response.
Validation: Test motion control performance using CODESYS’s PLCopen Motion library.
Hardware Compatibility
Solution: Choose CODESYS-certified ARMxy Industrial Edge Controller (e.g., ARMxy BL410 series) for driver and Runtime stability.
Custom Development: Extend functionality for specialized I/O modules via CODESYS’s C/C++ interfaces.
Developer Skillset
Training: Provide IEC 61131-3 training for traditional PLC engineers or adopt hybrid programming (e.g., Python integration).
5. Implementation Recommendations
Requirement Analysis: Define real-time requirements, communication protocols, and environmental conditions (temperature, EMC).
Hardware Selection: Choose CODESYS Runtime-certified ARMxy Industrial Edge Controller with long-term supply chain support.
Architecture Design: Separate real-time control tasks from non-real-time data processing for optimal resource allocation.
Testing & Validation: Conduct stress tests and fault injection in simulated environments to verify system robustness.
6. Future Trends
AIoT Integration: Embed lightweight AI frameworks (e.g., TensorFlow Lite) into CODESYS for edge intelligence.
Virtualization: Deploy multiple Runtime instances via containerization for task isolation.
Open-Source Collaboration: Deep integration between CODESYS communities and ARM ecosystems to drive standardized solutions.
Conclusion: The combination of ARMxy Industrial Edge Controller and CODESYS provides a highly flexible, scalable, and future-proof platform for industrial automation. It is particularly suited for SMEs and smart upgrade projects requiring rapid adaptation to market changes. With proper design and ecosystem support, this solution effectively balances performance, cost, and reliability.
0 notes
Text
A Comprehensive Guide for Embedded Software Development for Medical Devices

As a reality check, the embedded software development life cycle of a medical device is not only challenging, but it is also sophisticated in regard to the value proposition it presents to the healthcare payers and patients. Consequently, as the field of medicine continuous to evolve, these tools become more complex as their operations are managed by embedded software which needs to be integrated with the system in a way that guarantees safe and effective operation. This in-depth tutorial will guide you through the development embedded software for medical devices and all regulatory considerations that must be addressed.
Grasping the Regulatory Framework
Manufacturers of medical devices will always be bound by the numerous laws from the Federal Drug Administration (FDA) concerning effectiveness and safety of medical devices. Starting March 2023, the FDA began restricting submissions of Software Bill of Materials (SBOM) unless there was a set cybersecurity strategy. By October 2023 the FDA started refusing to accept submission of devices that had cyber security problems.
The regulatory landscape requires manufacturers to:
Implement a risk-based approach to software design and testing Conduct thorough validation of software functionality and security
Ensure devices can detect and respond to security incidents
Establish processes for monitoring and reporting security issues
Conduct ongoing testing throughout the device's lifecycle
Key Components of Embedded Medical Device Software

Hardware-Software Integration
In medical devices, embedded systems must achieve full intergration of hardware parts and software. This is necessary to guarantee that the medical devices operate as needed and that safety regulations are satisfied.
Real-Time Operating Systems (RTOS)
Many medical devices use Real-Time Operating Systems because they require some degree of waiting time to perform an important task. Such OS’s are essential in time-sensitive operations. For embedded medical devices, RTOS frameworks like FreeRTOS and Zephyr are routinely deployed.
Software Architecture
The structure has to be modular, so that later maintenance, testing, and validation would be easier. That also helps meet regulatory standards because tracking requirements to be enacted is simplified.
Read Also: Integrating Hardware and Software in Embedded Systems Development
The Development Process
Establishing a Regulatory Strategy Early
Prior to commencing any developmental work, formulate and put in writing a regulatory strategy that is aligned with the device's capabilities and goals. This becomes particularly critical in the case of Software as a Medical Device (SaMD), wherein modifying software becomes relatively easier than changing a hardware component.
Selecting the Right Development Team
Select the relevant personnel from the software policy team having working knowledge in cyber security, more so, if drastic changes are anticipated post initial launch of the product. Engage the services of engineers specialized in software development of medical devices as they have working knowledge of the required documentation for the device regulatory processes.
Programming Languages and Tools
Common languages used in embedded medical device development include:
C: Efficient and suitable for low-level memory management
C++: Provides object-oriented features for complex systems
Assembly: For performance-critical applications requiring direct hardware access
Rust: Offers memory safety features for developing secure systems
Implementing Security by Design
Security is not an add-on but a fundamental aspect of medical device software development. The FDA requires manufacturers to:
Conduct secruity risk assessments to identify potential vulnerabilities
Implement security controls to mitigate identified risks
Design software to be resilient against potential attacks
Ensure the ability to detect and respond to security incidents
Testing and Validation
Comprehensive Testing Approach
Testing should cover every aspect of the software, including:
Unit testing for individual components
Integration testing for combined components
System testing for the entire device
Performance testing under various conditions
Security testing to identify vulnerabilities
Documentation Requirements
Thorough documentation is essential for regulatory compliance. This includes:
Design specifications
Risk assessments
Test protocols and results
Validation reports
User manuals and technical documents
Post-Market Requirements
Getting regulatory clearance is just the beginning. Once your device is on the market, you must:
1. Maintain annual Establishment Registration
2. List your device(s)
3. Implement and maintain Quality Management System (QMS) processes
4. Document changes to software and assess regulatory impact
5. Be prepared for FDA audits
6. Run postmarket cybersecurity processes including periodic penetration tests and vulnerability scans
7. Conduct postmarket surveillance
8. Produce Unique Device Identifiers for new versions
Managing Software Updates
Yes, you can update your software after FDA clearance, and in fact, the FDA expects you to provide cybersecurity updates. However, significant changes may require a new 510(k) submission, possibly including new clinical or performance data.
Strategic planning around feature development is crucial. Consider creating key features that FDA needs to evaluate in version 1.0, then have your engineering team work on version 1.1 features while waiting for FDA review.
Best Practices for Success
Optimize code for performance, power consumption, and memory usage
Implement robust error handling mechanisms
Reuse code when possible to reduce development time
Provide thorough documentation for maintainability
Perform comprehensive testing to ensure code meets requirements
Raise sufficient funding for clinical performance validation, non-clinical testing, software documentation, and cybersecurity.
Conclusion
A greener tomorrow starts with better healthcare today, and embedded software for medical devices is at the forefront of this transformation. By integrating robust security measures, following regulatory guidelines, and implementing best development practices, manufacturers can create safe, effective medical devices that enhance patient care while maintaining compliance.
Let's build smarter, develop better, and create medical devices that care for both patients and healthcare providers. The truth is, embedded software development for medical devices is complex but essential for advancing healthcare technology and improving patient outcomes.
0 notes
Text
Can I buy Zeta variant of Maruti Suzuki Baleno and upgrade the headlights to projector headlamps with daytime running lights?
Yes, you can purchase the Zeta variant of the Maruti Suzuki Baleno and upgrade its headlights to projector headlamps with daytime running lights (DRLs), but there are critical considerations to address regarding compatibility, legality, and practicality. Here's a detailed breakdown:
1. Zeta Variant Specifications
The Baleno Zeta is a mid-to-high trim variant priced between ₹8.43–9.33 lakh (ex-showroom). While it includes features like a 9-inch infotainment system, cruise control, and rear AC vents, it does not come with projector headlamps or DRLs as standard. These premium lighting features are exclusive to the top-tier Alpha variant.
2. Aftermarket Headlight Upgrades
Projector Headlamps:
The Baleno’s headlight housing is designed for halogen bulbs in lower trims. Retrofitting projector lamps requires Compatibility with the existing housing and electrical system. Aftermarket kits like the Kozdiko C6 LED Headlight Conversion Kit (designed for other Maruti models) demonstrate that such upgrades are possible, but ensure the kit is Baleno-specific to avoid fitment issues.
Cost: A basic projector retrofit with DRLs may cost 15,000–40,000+, depending on brand and complexity.
DRL Integration:
Adding DRLs involves wiring modifications. Opt for plug-and-play kits to minimize tampering with the car’s electrical system.
3. Legal and Warranty Concerns
Legality:
Aftermarket modifications must comply with India’s Automotive Industry Standards (AIS) and Regional Transport Office (RTO) guidelines. Non-compliant setups (e.g., excessive glare or non-certified DRLs) risk fines or failed inspections.
Certification: Use E-marked or DOT-certified components to ensure compliance.
Warranty Impact:
Modifying headlights may void the manufacturer’s warranty if the upgrade causes electrical faults. Consult your Maruti Suzuki dealer beforehand.
4. Practical Considerations
Performance vs. Alpha Variant:
The Alpha variant includes LED projector headlamps and DRLs as factory-fitted features, along with additional perks like a 360-degree camera and premium upholstery.
Cost Comparison: Upgrading the Zeta’s headlights could cost nearly 50–70% of the price difference between Zeta and Alpha (₹1–1.5 lakh).
Resale Value:
Non-factory modifications may reduce resale appeal, as buyers often prefer OEM configurations.
5. Recommended Approach
Consult Authorized Dealers:
Some Maruti Suzuki service centers offer brand-approved accessory upgrades, ensuring compatibility and warranty retention.
Choose Reputable Brands:
Opt for trusted aftermarket brands like Philips, Osram, or SNGL for reliable performance.
Professional Installation:
Use certified workshops to avoid electrical issues or beam misalignment.
Final Verdict
While upgrading the Zeta’s headlights is feasible, weigh the costs and risks against simply opting for the Alpha variant, which includes factory-fitted projector lamps and DRLs. If customization is a priority, ensure compliance with legal standards and prioritize OEM-aligned solutions.

#led lights#car lights#led car light#youtube#led auto light#led headlights#led light#led headlight bulbs#ledlighting#young artist#car culture#cars#car#classic cars#car light#headlight bulb#headlamp#headlight#dr light#car lamp#lamp
0 notes
Text
Registered Training Organisation | TEQSA Standard Resources | CAQA
CAQA offers expert RTO Compliance Consultants to help Registered Training Organisations meet regulatory standards. Their consultants provide tailored advice to ensure your RTO maintains compliance with industry requirements. Trust CAQA for reliable RTO support.

0 notes
Text
SIT30821 Certificate III in Commercial Cookery — Expert Assignment Help in Australia 🇦🇺
Are you enrolled in the SIT30821 Certificate III in Commercial Cookery and struggling to manage the workload? Between kitchen practicals and theory-based assignments, it’s easy to feel overwhelmed. But don’t worry — CookeryAssignments.com is here to help you serve up success.
Whether you’re falling behind on units like SITHCCC023 or confused about recipe costing and food safety plans, we offer expert assignment assistance designed specifically for Australian culinary students.
🍽️ What Is SIT30821 Certificate III in Commercial Cookery?
SIT30821 is a nationally recognised qualification in Australia that trains you to become a skilled commercial cook. It’s commonly delivered at TAFE and registered training organisations (RTOs) and combines practical kitchen training with theoretical knowledge.
This course prepares students to work in restaurants, hotels, cafes, pubs, and catering operations. It’s the first major step for anyone aspiring to become a professional chef in Australia.
📘 Key Units Covered in SIT30821
The Certificate III in Commercial Cookery includes a wide range of core and elective subjects. Here are some of the major ones we can assist you with:
🔑 Core Units:
SITHCCC023 — Use food preparation equipment
SITHCCC027 — Prepare dishes using basic methods of cookery
SITHCCC028 — Prepare appetisers and salads
SITHKOP009 — Clean kitchen premises and equipment
SITXFSA005 — Use hygienic practices for food safety
SITXINV006 — Receive, store and maintain stock
SITXHRM001 — Coach others in job skills
SITXWHS005 — Participate in safe work practices
🧠 Elective Units (varies by institution):
SITHCCC031 — Prepare vegetarian and vegan dishes
SITHCCC030 — Prepare vegetable, fruit, egg and farinaceous dishes
SITHCCC035 — Prepare poultry dishes
SITHPAT016 — Produce desserts
SITHCCC036 — Prepare meat dishes
SITHCCC043 — Work effectively as a cook
Each unit comes with specific assessments such as case studies, logbooks, observation checklists, and kitchen simulations — and we can help you with them all!
📚 Common Student Challenges
Here’s what students typically struggle with:
Writing structured cookery reports and food preparation plans
Understanding HACCP and WHS protocols
Preparing menu items within time constraints
Referencing and formatting according to academic standards
Managing multiple deadlines while completing work placements
🧑🍳 How CookeryAssignments.com Can Help
We specialize in commercial cookery assignment help for Australian students. Our services are designed to help you meet academic requirements while freeing up your time to focus on the hands-on kitchen learning.
✔️ 100% plagiarism-free assignments ✔️ Expert writers with hospitality & culinary backgrounds ✔️ Affordable pricing for students ✔️ Timely delivery to meet RTO and TAFE deadlines ✔️ 24/7 support from our friendly customer service team ✔️ Assistance with referencing (Harvard, APA, etc.)
✨ Student Success Starts Here
Whether you’re working toward your dream of becoming a chef or just trying to pass your next unit, we’re here to support your journey. No more late-night stress or missed deadlines — just high-quality academic help from professionals who understand your course.
📞 Call us: +61 390 162 672 🌐 Visit: www.cookeryassignments.com
🔗 Ready to succeed in SIT30821? Contact us today and cook up better grades with confidence!
0 notes
Text
𝗜𝘀 𝗬𝗼𝘂𝗿 𝗗𝗮𝘁𝗮𝗯𝗮𝘀𝗲 𝗥𝗲𝗮𝗱𝘆 𝗳𝗼𝗿 𝘁𝗵𝗲 𝗨𝗻𝗲𝘅𝗽𝗲𝗰𝘁𝗲𝗱?
In today’s fast-paced digital world, 𝗱𝗮𝘁𝗮 𝗶𝘀 𝘆𝗼𝘂𝗿 𝗺𝗼𝘀𝘁 𝘃𝗮𝗹𝘂𝗮𝗯𝗹𝗲 𝗮𝘀𝘀𝗲𝘁 — but what happens when disaster strikes? 📉𝗗𝗕𝗔𝘀 𝗳𝗮𝗰𝗲 𝗰𝗼𝗻𝘀𝘁𝗮𝗻𝘁 𝗰𝗵𝗮𝗹𝗹𝗲𝗻𝗴𝗲𝘀, including: 🔹 Manual backup processes prone to human error 🔹 Inconsistent recovery testing and compliance gaps 🔹 Time-consuming maintenance across complex environments 🔹 Lack of real-time visibility into backup health 🔹 Delayed recovery times during critical outages That’s where 𝗖𝗹𝗼𝗻𝗲𝘁𝗮𝗯’𝘀 𝗖𝗧-𝗕𝗮𝗰𝗸𝘂𝗽 𝗮𝗻𝗱 𝗖𝗧-𝗗𝗥 step in 💡 ✅ 𝗖𝗧-𝗕𝗮𝗰𝗸𝘂𝗽 automates and standardizes database backup operations across heterogeneous environments — saving time, reducing errors, and ensuring consistency. ✅ 𝗖𝗧-𝗗𝗥 provides a powerful disaster recovery solution with automated switchover/failover, continuous monitoring, and simplified testing — ensuring your databases are always protected and recoverable with fast RTO and Low RPO. 🌐 Whether you manage a few databases or thousands across cloud and on-prem, Clonetab helps you 𝘀𝗹𝗲𝗲𝗽 𝗯𝗲𝘁𝘁𝗲𝗿 𝗮𝘁 𝗻𝗶𝗴𝗵𝘁 knowing your backup and DR plans are solid. 🔗 𝗪𝗮𝗻𝘁 𝘁𝗼 𝗹𝗲𝗮𝗿𝗻 𝗵𝗼𝘄 𝗖𝗧-𝗕𝗮𝗰𝗸𝘂𝗽 𝗮𝗻𝗱 𝗖𝗧-𝗗𝗥 𝗰𝗮𝗻 𝗳𝘂𝘁𝘂𝗿𝗲-𝗽𝗿𝗼𝗼𝗳 𝘆𝗼𝘂𝗿 𝗱𝗮𝘁𝗮𝗯𝗮𝘀𝗲 𝘀𝘁𝗿𝗮𝘁𝗲𝗴𝘆? 📍𝗠𝗲𝗲𝘁 𝘂𝘀 𝗮𝘁 𝗔𝗦𝗖𝗘𝗡𝗗 𝟮𝟬𝟮𝟱 or 𝗕𝗼𝗼𝗸 𝗮 𝗗𝗲𝗺𝗼 – Let’s talk innovation, resilience, and smarter DBA solutions!
#DatabaseBackup#DisasterRecovery#CTBackup#CTDR#Clonetab#OracleDBA#DatabaseManagement#ASCEND2025#DataProtection#Automation#BusinessContinuity#MeetUsAtASCEND
0 notes
Text
Cloud Data Disaster Recovery: Solution for Business Continuity

In an age where businesses rely heavily on digital infrastructure, safeguarding critical data is more important than ever. Whether it’s a natural disaster, cyberattack, or system failure, data loss can be devastating. This is where cloud data disaster recovery comes into play—a smart, scalable solution that helps organisations bounce back quickly and efficiently after an unexpected data loss incident.
In this article, we’ll explore what cloud data disaster recovery is, how it works, and why it’s essential for modern businesses looking to ensure resilience and business continuity.
What is Cloud Data Disaster Recovery?
Cloud data disaster recovery (CDDR) refers to the process of storing and maintaining backup copies of critical data in a secure cloud environment. In the event of a disaster—whether natural or technical—this data can be quickly restored to resume normal operations with minimal downtime.
Unlike traditional disaster recovery methods that rely on on-site servers or physical hardware, cloud-based recovery uses remote servers hosted by cloud providers. This allows businesses to recover lost or corrupted data from virtually anywhere, making it an agile and cost-effective alternative.
Why Businesses Need Cloud Data Disaster Recovery
Data loss can lead to major consequences, including financial losses, reputational damage, and operational downtime. Here's why cloud data disaster recovery is no longer optional for businesses:
1. Minimise Downtime
One of the biggest advantages of cloud data disaster recovery is its ability to reduce downtime. Automated backups and real-time syncing ensure that your systems can be restored almost immediately, keeping your business operations running smoothly.
2. Cost-Effective
Traditional disaster recovery setups often require significant investment in hardware, software, and maintenance. With cloud-based solutions, businesses can avoid these upfront costs and pay for only the resources they use.
3. Scalability
Cloud platforms are inherently scalable. As your data grows, your cloud infrastructure can expand to accommodate your needs without requiring additional hardware or manual intervention.
4. Security and Compliance
Reputable cloud providers offer high levels of data security, including encryption, multi-factor authentication, and compliance with industry regulations. This helps protect sensitive information while meeting legal requirements.
5. Remote Access and Flexibility
With cloud data disaster recovery, your team can access data remotely from anywhere in the world. This flexibility is particularly beneficial for organisations with distributed workforces or multiple office locations.
Key Features of Cloud Data Disaster Recovery Solutions
When choosing a cloud data disaster recovery service, it’s important to look for the following features:
Automated Backups: Scheduled or continuous backups to ensure minimal data loss.
Rapid Recovery Time Objective (RTO): Quick restoration to reduce disruption.
Geographic Redundancy: Storage across multiple locations to avoid single points of failure.
Encryption: Data protection during transmission and storage.
Compliance Support: Tools to help meet GDPR, HIPAA, ISO, and other compliance standards.
Testing Capabilities: The ability to simulate disaster scenarios and test recovery processes.
How Cloud Data Disaster Recovery Works
The cloud data disaster recovery process typically involves several key steps:
Data Backup: Critical business data is regularly backed up to secure cloud storage.
Monitoring: The system continuously monitors for signs of failure or data corruption.
Failover Activation: In the event of a disaster, the system triggers a failover to switch operations to a backup server.
Data Restoration: Business systems and data are restored from the latest backup.
Failback: Once the primary system is repaired, operations can revert to the original infrastructure.
With automation, businesses can achieve near-instantaneous recovery times and minimise the risk of extended outages.
Choosing the Right Cloud Data Disaster Recovery Provider
Selecting the right provider is crucial to ensure the effectiveness of your disaster recovery plan. Consider the following when evaluating vendors:
Reputation and Reviews: Look for providers with a proven track record.
Support and SLA: Choose a provider offering 24/7 support and clear service level agreements (SLAs).
Customisation: Ensure the solution can be tailored to your specific business needs.
Integration: Check compatibility with your existing infrastructure and software.
Popular cloud providers like AWS, Microsoft Azure, and Google Cloud offer robust disaster recovery solutions, often integrated with additional cloud services.
Final Thoughts
In today’s digital landscape, protecting your business data is not just a best practice—it’s a necessity. Cloud data disaster recovery provides a reliable, cost-effective, and flexible solution to safeguard your organisation against the unexpected. Whether you’re a small business or a large enterprise, implementing a cloud-based disaster recovery plan ensures peace of mind and uninterrupted operations in the face of adversity.
Invest in your business’s future by adopting cloud data disaster recovery today—and turn potential disasters into manageable setbacks.
0 notes
Text
Cloud Data Disaster Recovery: Solution for Business Continuity

In an age where businesses rely heavily on digital infrastructure, safeguarding critical data is more important than ever. Whether it’s a natural disaster, cyberattack, or system failure, data loss can be devastating. This is where cloud data disaster recovery comes into play—a smart, scalable solution that helps organisations bounce back quickly and efficiently after an unexpected data loss incident.
In this article, we’ll explore what cloud data disaster recovery is, how it works, and why it’s essential for modern businesses looking to ensure resilience and business continuity.
What is Cloud Data Disaster Recovery?
Cloud data disaster recovery (CDDR) refers to the process of storing and maintaining backup copies of critical data in a secure cloud environment. In the event of a disaster—whether natural or technical—this data can be quickly restored to resume normal operations with minimal downtime.
Unlike traditional disaster recovery methods that rely on on-site servers or physical hardware, cloud-based recovery uses remote servers hosted by cloud providers. This allows businesses to recover lost or corrupted data from virtually anywhere, making it an agile and cost-effective alternative.
Why Businesses Need Cloud Data Disaster Recovery
Data loss can lead to major consequences, including financial losses, reputational damage, and operational downtime. Here's why cloud data disaster recovery is no longer optional for businesses:
1. Minimise Downtime
One of the biggest advantages of cloud data disaster recovery is its ability to reduce downtime. Automated backups and real-time syncing ensure that your systems can be restored almost immediately, keeping your business operations running smoothly.
2. Cost-Effective
Traditional disaster recovery setups often require significant investment in hardware, software, and maintenance. With cloud-based solutions, businesses can avoid these upfront costs and pay for only the resources they use.
3. Scalability
Cloud platforms are inherently scalable. As your data grows, your cloud infrastructure can expand to accommodate your needs without requiring additional hardware or manual intervention.
4. Security and Compliance
Reputable cloud providers offer high levels of data security, including encryption, multi-factor authentication, and compliance with industry regulations. This helps protect sensitive information while meeting legal requirements.
5. Remote Access and Flexibility
With cloud data disaster recovery, your team can access data remotely from anywhere in the world. This flexibility is particularly beneficial for organisations with distributed workforces or multiple office locations.
Key Features of Cloud Data Disaster Recovery Solutions
When choosing a cloud data disaster recovery service, it’s important to look for the following features:
Automated Backups: Scheduled or continuous backups to ensure minimal data loss.
Rapid Recovery Time Objective (RTO): Quick restoration to reduce disruption.
Geographic Redundancy: Storage across multiple locations to avoid single points of failure.
Encryption: Data protection during transmission and storage.
Compliance Support: Tools to help meet GDPR, HIPAA, ISO, and other compliance standards.
Testing Capabilities: The ability to simulate disaster scenarios and test recovery processes.
How Cloud Data Disaster Recovery Works
The cloud data disaster recovery process typically involves several key steps:
Data Backup: Critical business data is regularly backed up to secure cloud storage.
Monitoring: The system continuously monitors for signs of failure or data corruption.
Failover Activation: In the event of a disaster, the system triggers a failover to switch operations to a backup server.
Data Restoration: Business systems and data are restored from the latest backup.
Failback: Once the primary system is repaired, operations can revert to the original infrastructure.
With automation, businesses can achieve near-instantaneous recovery times and minimise the risk of extended outages.
Choosing the Right Cloud Data Disaster Recovery Provider
Selecting the right provider is crucial to ensure the effectiveness of your disaster recovery plan. Consider the following when evaluating vendors:
Reputation and Reviews: Look for providers with a proven track record.
Support and SLA: Choose a provider offering 24/7 support and clear service level agreements (SLAs).
Customisation: Ensure the solution can be tailored to your specific business needs.
Integration: Check compatibility with your existing infrastructure and software.
Popular cloud providers like AWS, Microsoft Azure, and Google Cloud offer robust disaster recovery solutions, often integrated with additional cloud services.
Final Thoughts
In today’s digital landscape, protecting your business data is not just a best practice—it’s a necessity. Cloud data disaster recovery provides a reliable, cost-effective, and flexible solution to safeguard your organisation against the unexpected. Whether you’re a small business or a large enterprise, implementing a cloud-based disaster recovery plan ensures peace of mind and uninterrupted operations in the face of adversity.
Invest in your business’s future by adopting cloud data disaster recovery today—and turn potential disasters into manageable setbacks.
0 notes
Text
Cloud Data Disaster Recovery: Solution for Business Continuity

In an age where businesses rely heavily on digital infrastructure, safeguarding critical data is more important than ever. Whether it’s a natural disaster, cyberattack, or system failure, data loss can be devastating. This is where cloud data disaster recovery comes into play—a smart, scalable solution that helps organisations bounce back quickly and efficiently after an unexpected data loss incident.
In this article, we’ll explore what cloud data disaster recovery is, how it works, and why it’s essential for modern businesses looking to ensure resilience and business continuity.
What is Cloud Data Disaster Recovery?
Cloud data disaster recovery (CDDR) refers to the process of storing and maintaining backup copies of critical data in a secure cloud environment. In the event of a disaster—whether natural or technical—this data can be quickly restored to resume normal operations with minimal downtime.
Unlike traditional disaster recovery methods that rely on on-site servers or physical hardware, cloud-based recovery uses remote servers hosted by cloud providers. This allows businesses to recover lost or corrupted data from virtually anywhere, making it an agile and cost-effective alternative.
Why Businesses Need Cloud Data Disaster Recovery
Data loss can lead to major consequences, including financial losses, reputational damage, and operational downtime. Here's why cloud data disaster recovery is no longer optional for businesses:
1. Minimise Downtime
One of the biggest advantages of cloud data disaster recovery is its ability to reduce downtime. Automated backups and real-time syncing ensure that your systems can be restored almost immediately, keeping your business operations running smoothly.
2. Cost-Effective
Traditional disaster recovery setups often require significant investment in hardware, software, and maintenance. With cloud-based solutions, businesses can avoid these upfront costs and pay for only the resources they use.
3. Scalability
Cloud platforms are inherently scalable. As your data grows, your cloud infrastructure can expand to accommodate your needs without requiring additional hardware or manual intervention.
4. Security and Compliance
Reputable cloud providers offer high levels of data security, including encryption, multi-factor authentication, and compliance with industry regulations. This helps protect sensitive information while meeting legal requirements.
5. Remote Access and Flexibility
With cloud data disaster recovery, your team can access data remotely from anywhere in the world. This flexibility is particularly beneficial for organisations with distributed workforces or multiple office locations.
Key Features of Cloud Data Disaster Recovery Solutions
When choosing a cloud data disaster recovery service, it’s important to look for the following features:
Automated Backups: Scheduled or continuous backups to ensure minimal data loss.
Rapid Recovery Time Objective (RTO): Quick restoration to reduce disruption.
Geographic Redundancy: Storage across multiple locations to avoid single points of failure.
Encryption: Data protection during transmission and storage.
Compliance Support: Tools to help meet GDPR, HIPAA, ISO, and other compliance standards.
Testing Capabilities: The ability to simulate disaster scenarios and test recovery processes.
How Cloud Data Disaster Recovery Works
The cloud data disaster recovery process typically involves several key steps:
Data Backup: Critical business data is regularly backed up to secure cloud storage.
Monitoring: The system continuously monitors for signs of failure or data corruption.
Failover Activation: In the event of a disaster, the system triggers a failover to switch operations to a backup server.
Data Restoration: Business systems and data are restored from the latest backup.
Failback: Once the primary system is repaired, operations can revert to the original infrastructure.
With automation, businesses can achieve near-instantaneous recovery times and minimise the risk of extended outages.
Choosing the Right Cloud Data Disaster Recovery Provider
Selecting the right provider is crucial to ensure the effectiveness of your disaster recovery plan. Consider the following when evaluating vendors:
Reputation and Reviews: Look for providers with a proven track record.
Support and SLA: Choose a provider offering 24/7 support and clear service level agreements (SLAs).
Customisation: Ensure the solution can be tailored to your specific business needs.
Integration: Check compatibility with your existing infrastructure and software.
Popular cloud providers like AWS, Microsoft Azure, and Google Cloud offer robust disaster recovery solutions, often integrated with additional cloud services.
Final Thoughts
In today’s digital landscape, protecting your business data is not just a best practice—it’s a necessity. Cloud data disaster recovery provides a reliable, cost-effective, and flexible solution to safeguard your organisation against the unexpected. Whether you’re a small business or a large enterprise, implementing a cloud-based disaster recovery plan ensures peace of mind and uninterrupted operations in the face of adversity.
Invest in your business’s future by adopting cloud data disaster recovery today—and turn potential disasters into manageable setbacks.
0 notes
Text
A Comprehensive Guide to Firmware Development

In the world of embedded systems and smart devices, firmware plays a critical role in enabling hardware to function effectively. Whether you're developing IoT devices, automotive systems, or industrial machinery, firmware development is the backbone that bridges hardware and software.
In this blog post, we’ll explore what firmware is, its importance, the development process, tools used, and best practices to ensure efficient and secure firmware solutions.
What is Firmware?
Firmware is a specialized type of software that provides low-level control for a device's specific hardware. Unlike regular software applications, firmware is tightly coupled with the hardware and is often stored in non-volatile memory such as ROM, EEPROM, or flash memory.
Examples of devices with firmware include:
Smartphones
Routers
Smart TVs
Medical devices
Automotive control units (ECUs)
Why is Firmware Important?
Firmware is essential because it:
Controls hardware operations: Without firmware, the hardware components of a device would be non-functional.
Ensures device functionality: It manages startup routines, I/O operations, sensor integration, and communication protocols.
Supports software-hardware integration: Firmware acts as a middle layer, allowing high-level software applications to interact with low-level hardware components.
Enables updates: Firmware can often be updated to fix bugs, enhance performance, or add features.
The Firmware Development Process
1. Requirements Gathering
Understanding the hardware specifications and the device’s purpose is crucial. Developers need to gather requirements from both hardware engineers and end users.
2. Architecture Design
This involves deciding on the architecture and communication protocols (e.g., I2C, SPI, UART), memory usage, and timing constraints.
3. Choosing a Development Platform
Most firmware is written in C or C++ due to their efficiency and hardware-level access. You’ll also need:
Microcontroller/microprocessor datasheets
Board Support Packages (BSPs)
RTOS (Real-Time Operating System), if required
4. Coding and Integration
Firmware code is written to interface directly with hardware. This includes writing drivers for peripherals (LEDs, sensors, motors) and managing power consumption, timing, and interrupts.
5. Testing and Debugging
Testing includes:
Unit testing
Hardware-in-the-loop (HIL) testing
Simulation and emulation tools
Debugging tools such as JTAG and SWD are used to step through code and analyze performance.
6. Deployment
Once tested, firmware is compiled and flashed onto the device using programmers or over-the-air (OTA) update mechanisms.
Tools Used in Firmware Development
Integrated Development Environments (IDEs): Keil µVision, MPLAB X, STM32CubeIDE
Compilers and Toolchains: GCC, IAR Embedded Workbench
Debuggers/Programmers: JTAG, ST-LINK, AVR ISP
Version Control Systems: Git
Simulators/Emulators: QEMU, Proteus
Best Practices for Firmware Development
Write modular and reusable code
Follow coding standards (e.g., MISRA C for safety-critical systems)
Optimize for memory and power consumption
Document thoroughly for maintainability
Implement fail-safes and watchdog timers
Secure your firmware (e.g., with encryption and secure boot loaders)
Plan for firmware updates with mechanisms like OTA updates
0 notes
Text
RTO Support Consultants Australia | RTO Training Courses | CAQA
CAQA's RTO Support Consultants work alongside your organisation to provide expert advice and ensure compliance with industry standards. Their ongoing support keeps your RTO operating at peak performance. Trust CAQA for reliable and efficient consulting services.

#RTOConsultants#RTOManagementSystem#RTOTrainingProviders#RTOTrainingCourses#RTOSupportConsultants#RTOConsultantsAustralia
0 notes
Text
Intel Quartus Prime Pro Edition 25.1 Optimized for Agilex 3

Altera Launches Quartus Prime Pro Edition 25.1 for Agilex 3 FPGAs
Now available is Quartus Prime Pro 25.1, which supports Agilex 3, the latest Agilex release. Developers may design high-performing, power-efficient edge and embedded programs with this update.
Comprehensive Agilex 3 FPGA support
Agilex 3 FPGA family offers cost optimisation, high performance, and power efficiency for edge and embedded applications. This version lets you develop, test, and implement solutions faster with Agilex 3 higher-speed transceivers, on-chip dual Cortex-A55 ARM CPUs, and increased memory support, including LPDDR4.
For small board space applications, Agilex 3 uses Intel's variable pitch BGA packaging to design more efficiently and compactly. With this technology, developers can maintain performance and power efficiency while adding functionality to smaller spaces.
Security is essential for FPGA applications to protect sensitive data and IP. Agilex 3's physical security, authentication, and encryption capabilities strengthen designs' manipulation and assault resistance.
Nios V Soft Processor Enhancements
Nios V is vital for embedded applications and improves efficiency and performance. These improvements allow developers to make smaller, more efficient embedded devices.
Improved Nios V/g Core Performance Improved work completion and overall performance.
Nios V/c Core Area reduction saves 8% space, leading in smaller designs.
The Ashling RISCFree IDE's Visual Studio Code plugin simplifies Nios V software development.
TinyML Example Design with Nios V Application Note lets developers add machine learning (ML) to FPGA designs utilising microcontrollers.
Features of Embed Software
FPGA-based embedded applications need strong OS and virtualisation support. By adding Linux, RTOS, and hypervisor support, Quartus Prime Pro 25.1 lets developers build scalable, real-time, and virtualised embedded systems.
Linux Hardware Reference Designs Regular and standard editions for Linux development.
To support Xen, developers can virtualise FPGA programs.
RTOS supports Zephyr and Bare Metal, and FreeRTOS will arrive in Q2 (May).
Installer Improvements: Faster, flexible configuration
FPGA software should install and adapt easily. Quartus Prime Pro 25.1 improves installation with parallel processing, configurable component selection, and file management.
Installation in Parallel speeds up setup by installing many components simultaneously.
By letting users choose just the bits they need, Dynamic Components decrease installation time and disc space.
Troubleshoot hardware quickly with streaming debugging
Effective debugging reduces development cycles. The Streaming Debug IP for Signal Tap helps engineers debug FPGA designs by capturing real-time, high-bandwidth data.
Hardware debugging streaming allows real-time data flow for analysis.
Configurable streaming via STP Signal Tap Logic Analyser configures streaming and selects a debug host.
Simulation Enhancements
Quartus Prime Pro 25.1 improves integration, long-term support, and simulation with new native Altera AXI4 Bus Functional Models (BFMs).
Optimised for Quartus simulation workflows, native Altera AXI4 BFMs increase performance and compatibility.
Smooth Change With better toolchain integration, customers may switch to Altera AXI4 BFMs without substantial modifications.
Quartus Prime Pro 25.1 improves simulation performance, notably for transceiver protocol IP, enabling faster debugging and verification.
Better Transceiver Protocol IP simulation enhances PCIe, Ethernet, Serial Lite, JESD, and other transceiver protocols.
25.1 Beta Models The new simulation models for this edition focus on Ethernet and PCIe and are under beta testing.
Improved Efficiency Usually, 50% or more improvements speed up verification and reduce simulation time.
These simulation additions improve Quartus Prime Pro 25.1's transceiver-based FPGA design capabilities by speeding up simulations and reducing verification time.
Extra Quartus Prime Pro 25.1 Updates
QPDS Standard & Pro Containerised Images Docker Hub offers Quartus Prime Standard and Pro Editions containerised, simplifying deployment and improving cloud and CI/CD compatibility.
Separating timed closure data from Design Assistant results simplifies failure classification in Summary of Design Closure.
SDC Relative File Paths improve portability and script management for Synopsys Design Constraints (SDC) reports.
MTBF improvements It lets users adjust instance toggling rates to improve MTBF when default toggle rates are not suitable.
Static timing analysis improvements in Quartus Prime Pro 25.1 speed up timing problem identification and resolution.
Synthesis supports basic Quad-Port RAM. Automatic quad-port RAM inference expands memory design flexibility.
Complete Support for Byte Enable Inference in Synthesis: This adds 8-bit byte enables and supports 5, 8, 9, and 10-bit combinations, matching hardware capabilities.
Correcter Management Users can now write individual bytes within a word using the byte enable control signal to increase memory access and performance.
Better RAM inference lets designers use FPGA memory more readily.
FPGA AI Suite: Improved Usability and AI
As AI advances, FPGA-based inference systems must be more flexible and effective. This release includes better performance estimation, model support, and Agilex FPGA integration.
Support Agilex 3 Beta FPGA AI Suite beta supports Agilex 3 FPGAs. Build in Quartus with Agilex 3 and generate Inference IP targeting Agilex 5 in the architectural configuration file.
The RPM and DEB packages are now called “altera-fpga-ai-suite-” and the AI Suite is installed in “/opt/altera” instead of “/opt/intel”.
YoloV7 Model Support enables high-accuracy object recognition in robotics, surveillance, and industrial quality control.
Agilex 5 FPGA E-Series Example Design Support New Agilex 5 FPGA E-Series 065B Modular Development Kit sample designs are available.
This SoC example uses an ARM host CPU for AI inference. AI Inference IP and a novel layout transform enable folding and run-time configurability to improve AI model performance and usability.
Example of Hostless JTAG-Attach Design A system console linked to the Inference IP via JTAG allows users to setup and control IP functionality step-by-step.
Performance Estimator Uses Memory Bandwidth Users may now define external memory bandwidth when designing for memory-limited devices like Agilex 5 and Agilex 3, improving accuracy.
OpenVINO 2024.6 Integration FPGA AI Suite 25.1 uses the latest OpenVINO 2024.6 for stability and maintainability.
For two years, Quartus Prime Pro versions will only include the Long-Term Support AI Suite, which uses new optimisations and performance improvements.
FPGA AI Suite 25.1 simplifies FPGA AI inference with faster performance, more example designs, and greater model support.
Quartus Prime Pro 25.1 IP Features
After adding Agilex 3 IP cores and upgrading Agilex 5, Quartus Prime Pro 25.1 delivers real-time data processing, flexible memory access, and rapid connectivity for many applications.
Agilex 3 IPs
Agilex 3 has a wide range of memory, processor, and connectivity IPs for low-cost applications:
1.25 Gbps LVDS and MIPI D-PHY high-voltage and fast adaptable I/O Assistance interfaces.
PCIe 3.0, 10GE Hard IP, and 12.5Gbps transceivers ensure high-bandwidth applications.
LPDDR4 provides cost-effective embedded memory up to 2133 Mbps.
HPS EMIF ensures tight ARM Cortex integration.
HD Image and Video Processing Our VVP package accelerates video and vision processing applications.
JESD204B for Synchronising Data Converters synchronises 12.5Gbps multi-channels accurately.
The Transceiver Toolkit for Advanced Debugging improved transceiver link testing and debugging.
Agilex 5 IP updates
Performance and flexibility enhancements to Agilex 5 series IP include:
PMA-Direct real-time adaptive reconfiguration of multiple configurations
PCIe 3.0/4.0 Multi-Channel DMA supports x2/x4 Root Port (RP) and Endpoint (EP) modes.
Agilex 5 D Series enabled 12.5 Gbps per serial channel in Interlaken for scalable data transport.
Transceiver Toolkit 17.16 Gbps JESD204B Advanced Debugging ensures rapid, accurate data flow.
Dual-Simplex Mode Protocol JESD204C expands high-speed ADC/DAC interface for more advanced signal processing.
O-RAN IP: Supports 15–240 KHz subcarrier frequencies and real-time spacing changes via control messages. Scalable and conserved digital power.
The Agilex 3 and Agilex 5 FPGAs are ideal for embedded, networking, and AI-driven applications due to their performance, efficiency, and adaptability.
Conclusion
Quartus Prime Pro 25.1 improves Agilex 3 support, debugging tools, AI acceleration, IP cores, and usability. Optimisation for embedded apps, high-speed interfaces, or AI workloads is faster, more efficient, and more flexible with this version.
#technology#technews#govindhtech#news#technologynews#Quartus Prime Pro#Agilex 3 FPGAs#Agilex 3#Agilex 5#Agilex 5 FPGAs#Quartus Prime Pro Edition 25.1#Quartus Prime Pro Edition
0 notes
Text
LLN Assessment Kits | LLN Kits | RTO Training Resources
At RTO Training Resources, you can find RTO training packages that are fully compliant and easy to implement. Their range of RTO assessment resources helps your RTO maintain high standards. You can also purchase LLN assessment kits to help with learner assessments. The RPL kits simplify the process of recognising prior learning.

0 notes
Text
Pollution Under Control Certificate: Everything You Need to Know

In an era where environmental concerns are at the forefront of global discourse, vehicle emissions have become a significant source of pollution. To curb air pollution and ensure cleaner air, the Indian government mandates a Pollution Under Control Certificate for all vehicles. This blog explores everything you need to know about this essential document — from its importance and process to where to get it.
What is a Pollution Under Control Certificate?
A Pollution Under Control Certificate (PUC) is an official document that verifies that a vehicle's emissions are within permissible limits set by the Central Pollution Control Board (CPCB). It is a legal requirement under the Motor Vehicles Act, 1988, and is compulsory for every vehicle — whether it runs on petrol, diesel, or CNG.
The PUC certificate includes important information such as:
Vehicle registration number
Emission readings
Date of issue and expiry
Serial number of the PUC center
Why is the Pollution Under Control Certificate Important?
There are several reasons why every vehicle owner in India must obtain a valid Pollution Under Control Certificate:
1. Legal Compliance
Driving without a valid PUC certificate is a punishable offence. As per the Motor Vehicles Act, a fine of ₹10,000 or more may be levied on those violating the law.
2. Environmental Protection
The main goal of the PUC system is to reduce harmful vehicle emissions and control the rising levels of air pollution in Indian cities.
3. Roadworthiness
A valid Pollution Under Control Certificate ensures that your vehicle’s engine is functioning optimally, which means better mileage and lesser emissions.
4. Required for Insurance Renewal
Most insurance companies require a valid PUC certificate before processing motor insurance renewals.
How to Obtain a Pollution Under Control Certificate?
Getting a Pollution Under Control Certificate is a simple and affordable process. Here’s how:
Step 1: Visit a Certified PUC Center
Go to any authorized PUC testing center near you. These centers are usually found at petrol pumps or RTO-approved locations.
Step 2: Emission Testing
Your vehicle will undergo an emissions test. For petrol vehicles, the carbon monoxide (CO) and hydrocarbon (HC) levels are measured. For diesel vehicles, smoke density is checked.
Step 3: Certificate Issuance
If your vehicle meets the standards, a PUC certificate is issued instantly. In case your vehicle fails the test, servicing is recommended before retesting.
The cost of the PUC test usually ranges between ₹60 and ₹100, depending on the vehicle type.
Validity of the Pollution Under Control Certificate
For new vehicles, the certificate is valid for 1 year.
For older vehicles, it must be renewed every 6 months.
It is crucial to renew your Pollution Under Control Certificate before its expiry to avoid legal penalties and ensure continuous compliance.
How Bhoomi Environmental Helps
At Bhoomi Environmental, we are committed to a greener, cleaner India. Our organization offers end-to-end consultancy and environmental services, including assistance with compliance documentation like the Pollution Under Control Certificate.
We understand the technicalities involved and offer:
Guidance to locate certified PUC centers
Reminders for certificate renewals
Assistance in emission compliance for businesses with fleets
End-to-end support for environmental documentation and audits
Whether you're an individual vehicle owner or a commercial fleet operator, Bhoomi Environmental ensures that you stay compliant with all environmental norms, especially those involving the Pollution Under Control Certificate.
Conclusion
The Pollution Under Control Certificate is more than just a legal formality — it is a step toward protecting the environment and promoting sustainable transportation. It reflects our responsibility as citizens to reduce our carbon footprint and contribute to cleaner air.
If you're looking for expert guidance on how to obtain or renew your Pollution Under Control Certificate, Bhoomi Environmental is your trusted partner. Our expertise in environmental compliance and sustainability makes the process hassle-free for both individuals and businesses.
0 notes