#PolicyEnforcement
Explore tagged Tumblr posts
Text
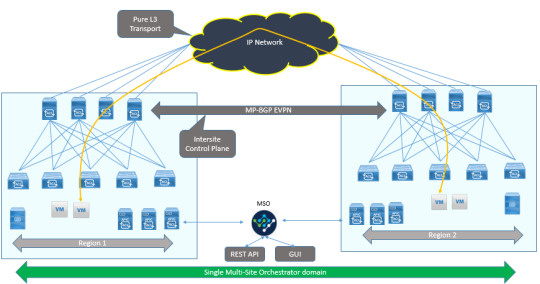
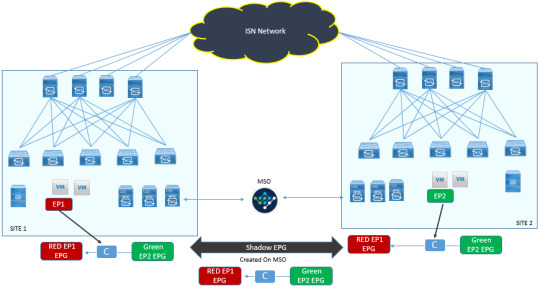

Secure your digital landscape with #Fortigate! Dive into advanced threat protection, firewall configurations, and more. Equip yourself with the skills to defend against cyber threats effectively. https://www.dclessons.com/aci-multi-site-architecture
#ciscoaci#acimultisite#multisitenetworking#sdwan#overlaynetworking#vxlan#layer2vpn#layer3vpn#intersiteconnectivity#centralizedmanagement#policyenforcement#disasterrecovery
0 notes
Link
Modern cybercrime that attempts to defraud the end user often has an attack component or vector that leverages the organization’s own web application and malware content.
0 notes
Text
資安監控-微軟建議監控AD受駭跡證
介紹 資安監控可以有效的發現場域內需要注意的事項,在組織內部的監控設備中,AD上的Event Log是絕對不可少的。 但有哪些Event Log是重要的?微軟給出了一個建議,可以參考看看。 Windows Audit PolicyConfiguring Windows Audit PolicyEnforcing Traditional Auditing or Advanced Auditing 延伸閱讀 Windows Event Log位置IIS log…
View On WordPress
0 notes
Photo

#publicpolicy #policyenforcers #amerikkka If you vote, you honestly cannot complain because you "literally" signed up for this shit.. Once you overstand the agenda, you gotta fight against it! www.law.cornell.edu
0 notes
Link
Domain shadowing provides the cybercriminal a series of methodologies to manipulate domain registrant accounts allowing the creation of fake sub domains solution.
0 notes
Link
Phishing is a fraudulent attempt by a third party to steal your personal information. Here are the latest phishing scams that we have been made aware. Phishing Solutions to protect electronic channels from cybercrime.
#MalwareProtection#BrandProtection#DataLossRecovery#PolicyEnforcement#RiskandCompliance#FraudPrevention#CybercrimeSolutions
0 notes
Link
How about we take a trip of iZOOlogic's perspectives on business security mindfulness or hostile to crushing arrangement. iZOOlogic enables your association with phishing assurance and battling to back with an incredible security accessible for your business.
0 notes
Link
Government and Industry Regulatory agencies as well as market expectations are placing an ever increasing compliance burden on banking, financial and other organisations. Contact us today @iZOOlogic.com to know how can you prevent your business.
#InternetPhishing#OnlineFraudPrevention#PolicyEnforcement#DataLossRecovery#BestVirusProtection#MalwareProtection
0 notes
Link
Brand Monitoring varies from unintentional brand misuse to significant malicious intent, Copyright and Trademark infringement, intellectual property, and electronic channels.
0 notes