#Path-Based Servlet
Explore tagged Tumblr posts
Text
Accessing Component Policies in AEM via Path-Based Servlet
Problem Statement: How can I leverage component policies chosen at the template level to manage the dropdown-based selection? Introduction: AEM has integrated component policies as a pivotal element of the editable template feature. This functionality empowers both authors and developers to provide options for configuring the comprehensive behavior of fully-featured components, including…

View On WordPress
#AEM#Component#component behavior#component policies#dialog#dropdown selection#dynamic adjustment#electronic devices#frontend developers#Path-Based Servlet#Servlet#template level#template policies
0 notes
Text
Push the limits with programming: High-level Java certification for the fearless coder.
In a period where technological progress determines the speed of industry development, the need for experienced software developers is increasing. Java, a key element in programming, continues to be essential in a wide range of applications, including mobile and enterprise-level systems. Softcrayons offers an Advanced Java Certification Training program designed for professionals looking to improve their knowledge of advanced Java concepts and advance their careers in software development.
The Importance of Advanced Java
The landscape of software development is evolving, and organizations are increasingly seeking professionals who possess a comprehensive understanding of advanced Java concepts. This certification program focuses on critical areas such as:
Web Application Development: Participants will acquire expertise in building dynamic and scalable web applications using Servlets, JavaServer Pages (JSP), and the Spring framework.
Database Connectivity: The course covers the Java Persistence API (JPA), enabling developers to effectively manage relational data and streamline database interactions.
Microservices Architecture: Attendees will learn to design and implement microservices, facilitating the development of scalable and maintainable applications.
Web Services: The curriculum includes the creation of RESTful and SOAP-based services, which are vital in today’s interconnected application ecosystems.
Features of the Training Program
Industry-Driven Curriculum: The course content has been developed in collaboration with industry professionals to ensure relevance and applicability in real-world scenarios.
Practical Application: Participants will engage in hands-on projects and exercises that reflect actual industry challenges, fostering the ability to apply learned concepts effectively.
Expert Instruction: Our experienced instructors provide personalized guidance, drawing from their extensive industry experience to enhance the learning experience.
Flexible Learning Options: Softcrayons offers both online and in-person classes, allowing participants to choose the format that best suits their schedules and learning preferences.
The Unique Value of Softcrayons
At Softcrayons, we take a thorough approach to professional growth. Our Advanced Java Certification Training goes beyond just theoretical teaching.
Interactive collaborative sessions in a learning environment encourage participant engagement and collaboration, enhancing the overall educational experience.
Professional Networking: Individuals have the opportunity to build important professional connections by interacting with industry professionals and colleagues.
Support for career advancement: We offer guidance on career paths, help with creating resumes, and prepare individuals for job interviews to improve their chances of success in the workforce.
In conclusion
Enrolling in the Advanced Java Certification Training at Softcrayons is a beneficial choice for your career advancement. By enhancing your Java skills, you establish yourself as a skilled developer equipped to tackle the challenges in today's software development. Come to Softcrayons and discover your potential while starting a journey toward excellence in the technology industry. The beginning of your career in software development is here.
For more information visit:- https://www.softcrayons.com/advanced-java-training
0 notes
Text
Creating Possibilities: Developing Java in Nagpur
There is an increasing need for qualified software engineers in today's tech-driven environment. A Java Developer is unique among the other roles because of the popularity and adaptability of the Java programming language. This is a great chance for you if you want to work as a Java developer in Nagpur. The fascinating opportunities for becoming a Java Developer in Nagpur, the necessary abilities, and the advantages of pursuing this career in Orange City are all covered in this article.
Why Would You Want to Work as a Java Developer in Nagpur?
Often called the "heart of India," Nagpur is quickly becoming a major IT powerhouse. The city's advantageous location, first-rate connectivity, and growing IT scene make it an ideal place for IT specialists. The following are some explanations of why deciding to become a Java developer could alter everything:
Expanding IT Sector
The IT sector in Nagpur is expanding rapidly. There are several IT parks and international corporations in the city, which gives Java Developers lots of work options. Enterprises such as Persistent Systems, Infosys, and Tech Mahindra are well-established in Nagpur and are always in need of qualified Java specialists.
Living Expenses
Nagpur has a much-reduced cost of living as compared to large cities like Bangalore, Delhi, Mumbai, and so on. Nagpur attracts tech professionals due to its reasonable commuting costs, affordable housing, and general cheaper cost of life.
Life Quality
Because of its clean atmosphere, low traffic, and good standard of living, Nagpur is a calm environment. The city is renowned for its excellent healthcare system, educational programs, and rich cultural legacy, all of which contribute to its citizens' balanced way of life.
The Qualifications Needed in Nagpur to Become a Java Developer
Having the appropriate skill set is essential for success as a Java developer. The following is a list of crucial abilities and subject areas that can help you stand out from the competition:
Mastery of Core Java
It is essential to have a solid understanding of Core Java. This includes being familiar with data structures, algorithms, exception handling, and object-oriented programming ideas.
Advanced Frameworks and Java
It is very ideal to know popular frameworks like Spring, Hibernate, and Struts as well as advanced Java ideas. These frameworks increase productivity by making difficult coding tasks simpler.
Web-Based Technologies
familiarity with web technologies such as HTML, CSS, JavaScript, and JSP/Servlets is necessary to create reliable online applications. It is essential to comprehend how Java interacts with front-end technology.
Nagpur Offers Java Developer Career Opportunities
Java developers might find numerous work prospects in Nagpur's booming IT sector. Here are a few well-known positions you might consider:
Developer for Java
The duties of a Java Developer include developing, putting into use, and maintaining Java programs. Writing clear and effective code, carrying out code reviews, and working with cross-functional teams are all part of this role.
In summary
Choosing a profession as a Java developer has many benefits and is a viable path. The city is a great place for computer professionals to live because of its expanding IT sector, low cost of living, and excellent standard of living. By learning the necessary abilities and being current with the most recent trends, you'll be able to access a wealth of options in the ever-evolving Java development industry. Accept the trip and use Nagpur as the starting point for a prosperous Java development career.
#BPO Service in nagpur#BPO voice and non voice#BPO voice In nagpur#BPO non voice in nagpur#BPO voice company in nagpur#BPO non-voice company in nagpur#BPO voice and non voice services#BPO outsorcing#B2B call Center
0 notes
Text
Java Training in Kolkata

Acesoftech Academy stands out as a leading institution providing comprehensive Java Training in Kolkata, coupled with a 100% placement assistance guarantee. Our courses cover both core Java and Java Full Stack, ensuring that students acquire a well-rounded understanding of this versatile programming language.
Java's Enduring Popularity
Java has maintained its status as the most popular programming language for over two decades. Its widespread use spans various sectors, including desktop applications, mobile development, and security implementations.
Advanced Java Course in Kolkata
Our training program includes an Advanced Java course in Kolkata, equipping students with the skills needed for complex development scenarios.
Demand for Java Developers in Kolkata
The industry demand for Java developers in Kolkata is substantial, given the language's versatility and applicability across diverse domains.
Salary Packages for Java Developers in India
Java developers in India enjoy competitive salary packages, reflecting the high demand and value placed on their expertise.
Best Java Training Institute in Kolkata
Acesoftech Academy proudly holds the title of the best Java Training institute in Kolkata, ensuring a quality learning experience for aspiring developers.
Why Choose Acesoftech Academy for Java Course in Kolkata
Our academy provides compelling reasons to choose us for Java training in Kolkata, emphasizing our commitment to quality education and practical skills development.
Java Important Topics
HTML5: Understanding the latest version of HTML for web development.
CSS3: Styling web pages with the latest Cascading Style Sheets.
JavaScript: Mastering the scripting language for dynamic web content.
jQuery: Utilizing the fast and concise JavaScript library.
Bootstrap: Creating responsive and visually appealing web designs.
Core Java: Building a strong foundation in the basics of Java.
Java Servlet and JSP: Developing dynamic web applications with Java.
Java Spring: Exploring the powerful Spring framework.
Spring Framework: Understanding the comprehensive Spring ecosystem.
Spring Boot: Building stand-alone, production-grade Spring-based applications.
100% Placement Assistance after Course Completion
Acesoftech Academy is committed to the success of its students, offering 100% placement assistance upon completion of the Java training course.
Pre-requisite
Prospective students should possess knowledge of any programming language, setting the stage for a smoother learning experience.
Who Can Join This Course?
The Java training course is open to students from various backgrounds, including BCA, B.TECH, MCA, MTECH, BSC IT, etc.
Career as a Java Developer
A career as a Java Developer promises stability and growth, given the language's continued relevance and demand across industries.
What You Can Do After Learning This Course
Upon completing the Java training course, individuals can embark on diverse career paths, ranging from web development to enterprise application development.
FAQs
1. Why Choose Acesoftech Academy for Java Training in Kolkata?
Answer: Acesoftech Academy stands out as the best Java training institute in Kolkata, offering comprehensive courses covering core Java, Java Full Stack, and advanced topics. Our commitment to quality education, practical skills development, and 100% placement assistance makes us the preferred choice for aspiring Java developers.
2. What Topics Does the Java Training Program Cover?
Answer: The Java training program at Acesoftech Academy covers a range of essential topics, including HTML5, CSS3, JavaScript, jQuery, Bootstrap, Core Java, Java Servlet and JSP, Java Spring, Spring Framework, and Spring Boot. This diverse curriculum ensures students acquire a well-rounded skill set.
3. Is Prior Programming Knowledge Required to Join the Course?
Answer: Yes, a basic understanding of any programming language is recommended as a prerequisite for joining the Java training course. This foundation enhances the learning experience for students.
4. How Does Acesoftech Academy Ensure Placement Opportunities?
Answer: Acesoftech Academy is committed to the success of its students. We provide 100% placement assistance upon course completion, connecting graduates with relevant opportunities in the dynamic field of Java development.
5. What Career Opportunities Exist for Java Developers After Completing the Course?
Answer: After completing the Java training course, individuals can pursue diverse career paths, including web development and enterprise application development. The stable and growing demand for Java developers in India ensures promising career prospects.
In conclusion, Acesoftech Academy's Java Training course in Kolkata is a comprehensive program designed to equip students with the skills and knowledge necessary for a successful career in Java development. Join us to pave your way to a rewarding and dynamic future in the world of programming.
0 notes
Text
The Indicates To Transfer The Ocp Java Se eleven Certification

Edureka’s Advanced Java Training Course is designed for school kids and professionals who wish to be a Java Developer. This 42-hour course will cover each core and superior Java ideas like Java Array, Collections, Database connectivity, Threads, Exception Handling, JSP, Servlets, XML dealing with and so forth. You may also learn numerous Java frameworks like Hibernate and Spring. Enroll now with our Core Java course on-line and become Java Certified. The candidate should additionally demonstrate the method to use strings and array lists. The model 8 of the take a look at was made obtainable as a last release since December 2014.
Can I write OCP without OCA?
No, you don't need to. You can take the OCP tests you study for with no prior requirement. With Java 8, you had to pass two exams to get to OCP. After passing the first one, you got the OCA title.
Our agile training methods has helped hundreds of scholars in pursuing a profitable career in Java. By the tip of this training program, you'll have a whole understanding of Java and be succesful of construct your individual Java applications. Our Java training relies on object-oriented programming paradigm which allow newbies to create reusable codes and modular packages, thus simplifies the method of programming.
Java File Handling
To know what these Java-based profiles entails, enroll for our Java Training free on-line career counseling & demo of Java coaching classes on-line. Enroll for our 360-degree coaching for Java to get complete sources which are required to become a job market-ready Java professional. We don’t just assist you to to arrange your resume, we even assist you to with interview preparation. Let’s equip you with the important skills/knowledge and trade use instances of our Java on-line course with certificates that will help you qualify one of the best Java certifications and turn into that main & certified Java professional. Any learner to skilled, with or with none technical experience/background can be taught Java with ease.
Is Oracle certification retake free?
If you received an OCP Exam Voucher that includes a free retake, your voucher (i) can be used by one person on one attempt plus a retake of the same exam (ii) can only be used for a retake if there is a failed first attempt on file, (iii) becomes void for both attempts on the voucher expiration date.
My name is Maaike van Putten, and welcome to my course, Java SE eleven Developer Certification 1Z0‑819 Overview. OCP 11 is a great opportunity to both get licensed and a obtain a deeper understanding of Java. This course goes that will assist you to create a personal action plan to prepare for the examination, and we'll offer you a transparent thought of what the entire experience might be like.
It turns into much simpler to clear these written tests as quickly as you’ve handed the Oracle Java certification exam. If you’ve certified, some corporations could even consider you directly for the interview course of and exempt you from the written examination. However, just studying Java articles and questions won’t help; you’ll should do Java certification for long run advantages. Whatever you learn via the certification will stay with you for an extended period. Oracle Java certification exam questions are designed in such a way that you’d be in a position to learn refined concepts speedily whereas making ready for the Java certifications. In only a short span of time, candidates can learn the basics as well as the small print of essential APIs.
Trending Courses
Our online coaching courses are made on the prime of offline classroom experiences. Get your offline classroom experiences in our on-line training courses. Just think about how would the growing journey bills & discomfort of not being at your home/office could have an result on your capability to study.
It may also give you an opportunity to be conversant in the variety of Java certification exam questions and set the best expectations.
Work on challenges along the length of this system to practice your expertise.
Vinayak shares his Edureka studying expertise and how our Big Data training helped him obtain his dream career path.
A program of self-motivated reading and study won't be the greatest option for everyone.
Gain a working knowledge of Java as properly as a targeted understanding of object-oriented techniques evaluation and design using agile, iterative approaches.
When you study with us just about for any course of your choice, you get an entire experience that could also be a duplicate of an offline classroom. By including the certification to your resume & portfolio you'll expertise an excellent push in the course of the interview rounds & salary negotiations. We can proudly say this, as our past learners & trainees have gotten great recognition within the recruitment process and now are an inherent a half of leading industries & businesses of right now.
If you are looking for more helpful assets, e.g. books and examination simulators, then you can take a look at my following articles. This on-line course covers all OCAJP eight topics and in addition accommodates follow exams comprising of 260+ multiple selection inquiries to assess Oracle Certified Associate, Java SE eight Programmer I preparation. The instructor, Goran Lochert, is an authorized Java developer himself and an skilled, with many years of programming expertise in Java.
SynergisticIT’s Java coaching is an ideal choice for aspiring internet developers, programming fanatics, software program developers, engineering or CS students who wish to enrich their Java information. This program teaches from scratch and requires no earlier coding expertise for learners. Our seasoned tutors introduce you to the core Java programming language and its related applied sciences that can assist you create transportable, & high-performance purposes. The Java programming certificates is designed to organize students for a profession in pc programming. The certificates provides a balanced set of courses that provides college students with consumer, server, and database programming expertise required by trade. Emphasis is placed on object-oriented programming applications Web-based applets configuring an Apache Tomcat servlet, implementing JavaServer Pages, JavaBeans, and NetBeans for reusable software parts.
youtube
1 note
·
View note
Text
Lunar Gateway: Earth’s guard post against asteroids?

International - Lunar Gateway patch.
March 9, 2020
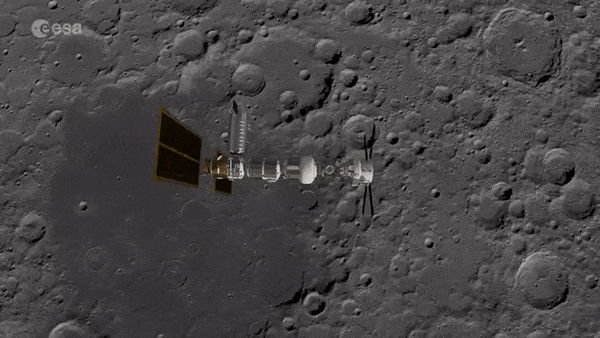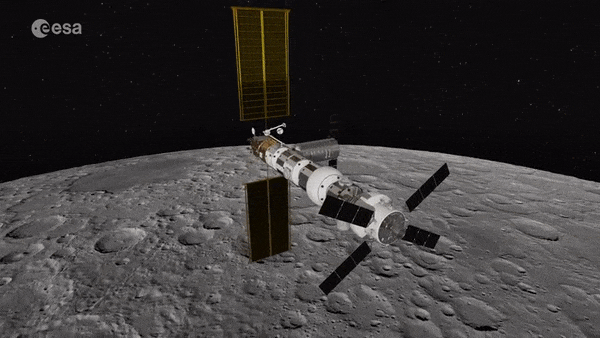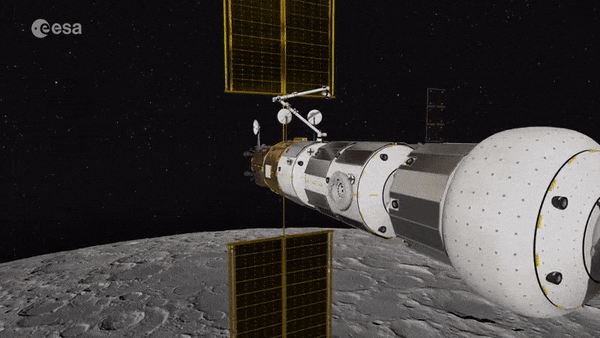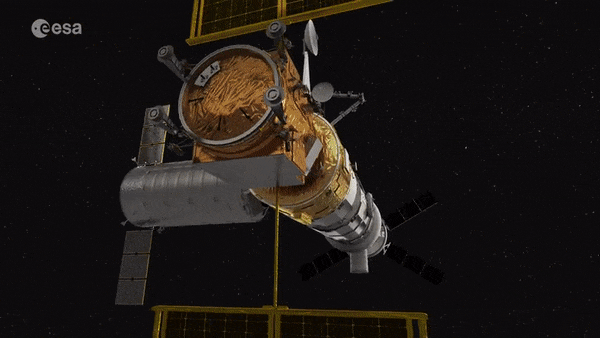
Gateway
Humankind’s next space outpost, the lunar Gateway, will serve as a staging point to reach the surface of the Moon. A new ESA-backed study is considering whether it could also be used as a deployment point for planetary defence missions, to intercept asteroids approaching dangerously close to Earth.
Set for assembly over the course of this decade, the Gateway will be placed in a highly elongated, or ‘eccentric’ week-long orbit around the Moon, passing a minimum 3000 km from the lunar surface and 70 000 km at its furthest away. Crewed missions will require much less energy to rendezvous with the Gateway than to fly direct to the surface of the Moon, and could then venture down using Gateway-based landers.

Gateway and Moon
But the Gateway could also support operations into deep space – including spacecraft for planetary defence, to deflect the orbital paths of incoming asteroids.
The concept might sound like science fiction, but Earth’s first planetary defence missions are already in active preparation. NASA’s Double Asteroid Redirect Test (DART) spacecraft, due to launch next year, will impact the smaller of the Didymos asteroid pair, in orbit between Earth and Mars, in a bid to shift its orbit. In 2026 ESA’s Hera spacecraft will perform a close-up survey of the asteroid post-impact.
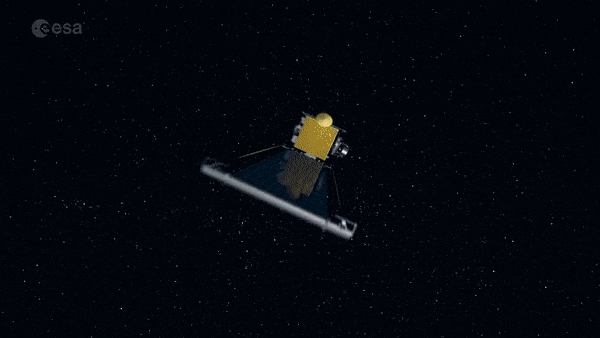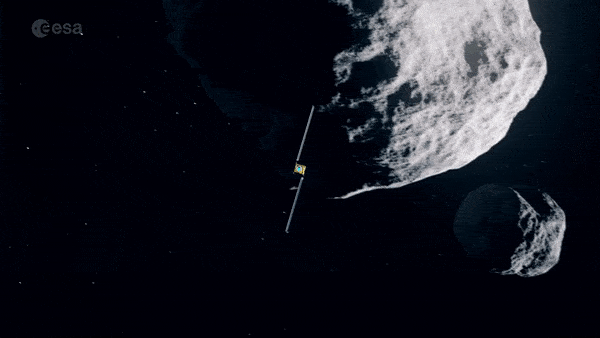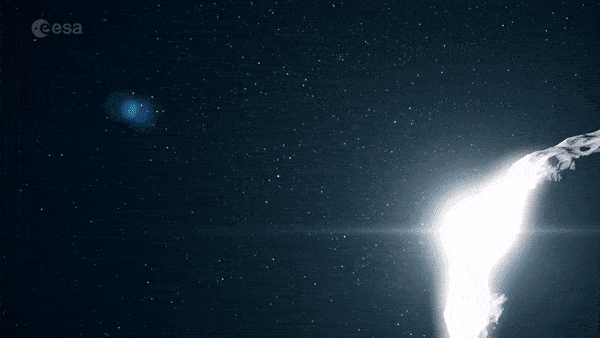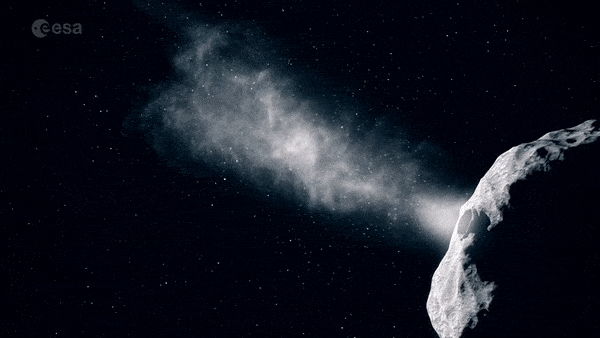
NASA's DART impacting asteroid
The DART and Hera missions, known jointly as the Asteroid Impact and Deflection Assessment (AIDA) collaboration represent an experimental trial-run on a distant body that poses no threat to Earth. Once proven, the deflection technique could be used for real on asteroids coming dangerously close – but a rapid reaction time would be crucial for maximum effectiveness.
Accordingly ESA is funding a new study by Politechnico di Milano to analyse options for using the Gateway to park planetary defence spacecraft in readiness to intercept incoming asteroids. These spacecraft would be able to depart the Gateway with much lower energies compared with departing from Earth itself.

An exploration and science outpost in orbit around the Moon
Other OSIP-submitted research ideas selected for funding in January 2020 include:
- New ways of building satellites might be creating a new type of space debris: the latest carbon fibre reinforced plastics, when broken apart, could be giving rise to vast amounts of tiny fragments of carbon fibres. These are not represented in current debris models, so a dedicated model needs to be made.
- Air-filled integrated waveguides could enable the design of low-cost, high performance antennas for the coming wave of satellite constellations.
- The autonomy of embedded devices aboard satellites could be boosted using AI-based hardware accelerators.
- With nanomaterials used increasingly for biomedical applications, investigation is needed into how weightlessness influences their effects within biological systems.
There are many more challenges currently live on OSIP – take a look for yourself:
https://ideas.esa.int/servlet/hype/IMT?userAction=BrowseCurrentUser&templateName=MenuItem
Related links:
Politechnico di Milano:
https://www.polimi.it/en/
Asteroid Impact and Deflection Assessment (AIDA):
https://www.esa.int/Safety_Security/Hera/Asteroid_Impact_Deflection_Assessment_AIDA_collaboration
Hera spacecraft:
https://www.esa.int/Safety_Security/Hera
NASA’s Double Asteroid Redirect Test (DART):
https://www.nasa.gov/planetarydefense/dart
Gateway:
http://www.esa.int/Science_Exploration/Human_and_Robotic_Exploration/Exploration/Gateway
Images, Animations, Text, Credits: ESA/NASA/ATG Medialab.
Greetings, Orbiter.ch
Full article
43 notes
·
View notes
Text
TOP 10 IT COURSES IN 2020
The relationship between businesses and technologies are emerging day by day. New technologies have been launching in the market, and companies are looking for those candidates who are certified in those technologies, and who are skilled enough in their platform IT Courses. Even if you are a fresher and looking to work on new technology, you can get certified and get a good job in top companies. Here are the top 10 technologies which are currently ruling the IT market. They are:
1. Cloud Computing Technology:-
One of the most trending technologies in the IT Courses industry is Cloud Computing Technology. We’re now utilizing many cloud-based administrations, for example, from Google, Amazon, Microsoft, HP, and others. Cloud computing is around the “On-demand service” design which enables clients to acquire, design, and deploy cloud administrations themselves utilizing cloud administration inventories, without requiring its help.
Generally, individuals and Corporates would purchase programming and introduce them to their PCs for use. With the coming of the Internet, a wide range of projects got accessible on a ‘Cloud’. Cloud computing clients don’t claim the servers and other physical foundation that stores these projects. Rather, they lease the projects — or the utilization of the projects — from a specialist co-op/provider. This helps spare assets since the client pays just for the assets that the individual uses. Huge advancements in virtualization and dispersed figuring, just as improved access to the rapid Internet and a frail economy, have quickened corporate enthusiasm for Cloud registering IT Courses.
Some popular and important subject in cloud computing is
· Infrastructure as a service (IaaS)
· Platform as a service (PaaS)
· Software as a service (SaaS)
· Network as a service (NaaS)
· Database as a service (DBaaS) and few more services.
The fast improvement of information being produced progress in virtualization, and cloud computing, and the combination of server centers frameworks are making popularity for talented IT Courses experts. Qualification: Anyone with fundamental information on PCs and the Internet can begin with the underlying modules of cloud-based courses. Individuals with programming aptitudes in.NET or J2EE may straightforwardly choose the further developed modules in cloud processing. Microsoft’s cloud computing service, Windows Azure is one of the reliable course alternatives.
2. Database Administrators (DBA):-
Some popular DBA is (Oracle, DB2, MySQL, SQL Server).
In an extremely unique and dynamic Software/IT industry, the one course which you can depend on for a steady profession is Database Administration (DBA). DBA is all about creating, managing and keeping up large information records; and from the few database flavors accessible in the market, Oracle can be your most solid option. Others are famous, however, once you are through with Oracle, the ones like MySQL and DB2 can be effectively adapted later on in a lot shorter period.
To move to further develop levels, courses like Data Warehousing can be sought after further. Again likewise with numerous Software/IT courses, there is no least eligibility to learn DBA, yet a customary recognition/graduation in PCs keeps on being favored from an occupation point of view.
To improve your profile, you should search for certifications (after fulfillment of course or self-learning) like from Oracle or IBM. Interest in DBA will stay positive as there’s no task in Software/IT Courses that doesn’t utilize a database, regardless of the size of the undertaking. So in case, you’re vigilant for a stable employment choice and information support (automatically) charms you, at that point a DBA course is the best approach!
3. JAVA – J2EE and it’s Frameworks:-
The most generally utilized innovation by practically all the regarded organizations crosswise over a domain around the globe is only Java. What’s more, with regard to what precisely you should realize, Java keeps on being an unending sea where you should concentrate on boosting your core portion of it, however, much as could reasonably be expected. Hopefuls regularly lose control with the appeal of JSP and Servlets, yet that murders you like sweet toxic substance over the long haul. There are a few things you should focus on when you are learning JAVA. They are
· J2SE — Core or primary Portion.
· J2EE — Java server pages (JSP) and Servlets along with Enterprise JAVA Beans (EJB).
· Struts — Framework for Java.
· SPRING or potentially HIBERNATE (For increasingly complex and propelled applications).
There are numerous frameworks and supporting advancements for Java hopefuls Yet, the over ones are an absolute necessity and most on-demand ones in the Software/IT Courses showcase.
To learn Java, there is no qualification all things considered, yet on the off chance that you’re focusing on a tolerable activity, at that point you will require a Bachelor/Master’s certificate in computer field alongside it. So if a vocation in any of the above significant areas premiums you and the enthusiasm for relentless coding satisfy your spirit, at that point look no more remote than learning Java.
4. Software Testing:-
A profession choice regularly involved (or for the most part disagreeable/disregarded) to an industry fresher is Software Testing. While the reality of any medium or huge scale venture is that it’s inadequate without the Testing groups. An untested application is consistently the most unsafe one and suspected to worsen in the longer run. Testing is a procedure used to help specify the accuracy, fulfillment, and nature of the developed programs. Because of that, testing can never totally set up the accuracy of the programs.
Testing helps in checking and approving if the product or software is working as it is proposed to work. This includes utilizing static and dynamic viewpoints to test the application. Testing should regularly open different classes of errors in the least amount of time and with the smallest amount of effort. An extra advantage of testing is that it shows that the product or software seems, by all reports to be functioning as expressed in the specifications.
Any Testing course should cover these minimum topics as mentioned below Static Testing, Dynamic Testing, Load Testing, Black box Testing, White Box Testing, Unit Testing, Regression Testing (Software), Web Regression Testing, Automated Regression Testing, etc.
A software tester appreciates a similarly quicker and simpler arch to��the development in IT Courses companies.
5. Data Analysis:-
The market wildly needs a master’s or expert’s in the data Analysis. Because of an exceptional increment in the measure of data, the ability to prepare and understanding it has gotten vital. Specifically, everyone has attracted up for estimating and following everything, and the understanding of how to manage the hard outcomes accomplished will be the most likely requested.
For this situation, the procedure to depend on computer’s isn’t compelling, since the best business results can be accomplished by planning an intelligent way to deal with data information and analysis.
There are Kinds of Data Analysis available in the market. They are
· Data Mining
· Statistical Analysis
· Business Intelligence
· Content Analytics
· Predictive Analytics
Therefore, a position to make spot designs, uncover the patterns and estimate probabilities is definitely the expertise of things to come in the IT circle.
6. System Administration:-
For the ones who are attached to installation and computer organization exercises like User Management, framework security, chance administration, bundle establishments – System administration can be a captivating decision.
Likewise, with CISCO innovations, framework organization is additionally widespread as a course among non-IT applicants. You have to have done 10+2 or legitimate recognition/graduation (IT or non-IT) to begin with this course and afterward show up for the confirmation tests or certification exams.
Except if you hold an ordinary IT graduation, the certifications are practically necessary for you if picking this organization course. There are different choices in certifications from Red Hat, VMware, and Solaris.
system administration is all around considered a normal pay getting profile, however, yes there are lots of special cases to it and the individuals who hold 4-year graduation in software engineering are at a preferred position to draw greater pay scales. Similarly, non-IT competitors should be somewhat patient and spotlight on picking up the underlying 4-5 years of experience.
7. Statistical Analysis System (SAS):-
Data Analytics is presently a quickly developing field thus this Business Intelligence area has risen as the most worthwhile choice among its present type graduates.
SAS means statistical analysis system is a coordinated arrangement of programming items gave by SAS Institute, to perform information passage, recovery, the executives, mining, report composing, and illustrations.
Some unequivocal advantages are as under:
· Generally used for business arranging, gauging, and choice help for its exact outcomes.
· Widely used for activities research and task the board.
· The best device for quality improvement and applications advancement.
· Gives Data warehousing (separate, change, and burden)
· Extra advantages of platform license, and remote computing capacity.
· SAS business arrangements aid regions, for example, human asset the executives, money related administration, business knowledge, client relationship the board and the sky is the limit from there.
· Used in the examination of results and report generation in clinical paths in the pharmaceutical business SAS contains multi-motor engineering for a better data management and publishing.
SAS preparing gets ready students for fulfilling, and very well paying professions as SAS examiner, software engineer, designer or consultant. Anybody can get familiar with this course and show up for the confirmation tests, yet for the most part, the ones who hold substantial graduation in Computers/IT Courses, are liked. The SAS Certified Professional Program was propelled by SAS Institute, Inc. in 1999 to observe clients who can exhibit an inside and out comprehension of SAS programming. The program consists of five confirmations crosswise over various areas. A few SAS courses get ready clients for the certification exams.
To date numerous developers have taken these courses, some accomplished clients simply take the tests, and numerous SAS experts are experienced however not SAS certified. According to some ongoing reviews, around 60,000 SAS Analysts and developers will be required in the following couple of years. Also, SAS consultants are paid with a good package when differentiated with other software engineers.
8. Blockchain Technology:-
Many people consider Blockchain innovation in connection to digital forms of money, for example, Bitcoin, Blockchain offers security that is helpful from numerous points of view. In the least difficult of terms, Blockchain can be represented as data you can just add to, not divert from or change. Consequently, the expression, “chain” since you’re making a chain of data. Not having the option to change the past intersections is the thing that makes it so secure.
Moreover, Blockchain is agreement driven, so nobody substance can assume responsibility for the data. With Blockchain, you needn’t bother with a trusted in an outsider to control or approve exchanges. A few enterprises are including and actualizing Blockchain, and as the utilization of Blockchain innovation gains, so too does the interest in gifted experts. In such a manner, we are as of now behind.
As per the survey, Blockchain-related jobs are the second-quickest developing classification of employments, with 12 employment opportunities for each one Blockchain designer. A Blockchain designer spends significant time in creating and executing engineering and designs using Blockchain innovation. The normal yearly compensation of a Blockchain engineer is $145,000.
In the event that you are captivated by Blockchain and its applications, and need to make your career in this quickly developed industry, at that point this is the perfect time to learn Blockchain and apparatus up for an energizing future.
Just go for Blockchain demo you can know more: https://itcources.com/blockchain-training/
9. Artificial Intelligence (AI):-
Artificial intelligence or AI, has just gotten a great deal of buzz as of late, yet, it keeps on being a pattern to watch since its impacts on how do we live, work and play are just in the beginning periods. Moreover, different parts of AI has created, including Machine Learning, which we will go into beneath.
AI relates to computer systems worked to copy human insight, and perform undertakings, for example, acknowledgment of pictures, discourse or example, and basic leadership. AI can carry out these responsibilities quicker and more precisely than people. Five out of six Americans use AI benefits in some structures each day, including navigation applications, streaming services, cell phone individual assistance, ride-sharing applications, home individual assistance, etc.
Notwithstanding customer use, AI is used to plan trains, survey business hazards, divine maintenance, and improve vitality productivity, among numerous other cash saving undertakings. Artificial intelligence is one part of what we allude to comprehensively as automation, and automation is an interesting issue due to potential work loss.
Specialists state that automation will wipe out 73 million additional employments by 2030. In any case, automation is making occupations just as disposing of them, particularly in the field of AI. Employments will be made being developed, programming, testing, backing, and support, to give some examples. AI architect is one such work. Some say it will quickly challenge data scientists in demand of experienced specialists.
Just go for AI demo you know more: https://itcources.com/artificial-intelligence-training/
10. Internet of Things (IoT):-
Many “things” are presently being worked with Wi-Fi availability, which means they can be associated with the Internet and to one another. Henceforth, the Internet of Things, or IoT.
The Internet of Things is the future and has just empowered gadgets, home devices, vehicles and substantially more to be associated with and trade information over the Internet. What’s more, we’re just in the first place phases of IoT: the quantity of IoT gadgets arrived at 7.4 billion in 2017 is relied upon to arrive at 33 billion gadgets by 2020. As purchasers, we’re now using and profiting by IoT. We can bolt our doors remotely on the off chance that we neglect to when we leave for work and preheat our stoves on our route home from work, all while following our wellness on our Fit bits, and hailing a ride with Lyft. In any case, organizations additionally have a lot to pick up now, and sooner rather than later.
The IoT can empower better security, effectiveness and basic leadership for organizations as information is gathered and investigated. It can empower cautious support, accelerate healthful consideration, improve client assistance, and offer advantages we haven’t thought at this point. Be that as it may, in spite of this shelter in the advancement and selection of IoT, specialists state insufficient IT experts are landing prepared for IoT positions.
For somebody keens on a profession in IoT, that implies simple passage into the field in case you’re encouraged, with a scope of choices for the beginning. Abilities required to include IoT security, cloud computing information, data analytics, automation, knowledge of embedded systems, device information to give some examples. All things considered, it’s the Internet of Things, and those things are numerous and differed, which means the abilities required are too.
Just go for IOT Demo you can know more: https://itcources.com/iot-training/
DevOps:
DevOps certification online training provided by ITcources.com will aid you to become a master in DevOps and its latest methodologies. In this training class, you’ll be able to implement DevOps software development lifecycle. The training is being provided by Industry professionals to make you understand the real-time IT scenarios and problems.
Just go for DevOps Demo you can know more: https://itcources.com/devops-training/
Data Science:
A Data Analyst, as a rule, clarifies what is happening by preparing a history of the information. Then again, Data Scientist not exclusively does the exploratory examination to find experiences from it, yet in addition, utilizes different propelled AI calculations to recognize the event of a specific occasion later on. A Data Scientist will take a gander at the information from numerous edges, once in a while edges not known before. Information Science is a mixture of various devices, calculations, and AI standards with the objective to find concealed examples from the crude data. How is this not the same as what analysts have been getting along for a particular amount of time? The appropriate response lies in the contrast among clarifying and anticipating. ITcources.com provides you the best Data Science online training or online classes in the Bangalore for the certification.
Just go for Data Science Demo you can know more: https://itcources.com/data-science-training/
Final Conclusion:-
The interest for IT Courses expert’s methods higher remunerations and wages expanded speculations by corporations to pay more for qualified and certified IT Courses experts, and more motivations to enlist contract or temporary experts to fill those IT jobs.
Note:-
Adding to your abilities, having a training certification from one of the main innovation training platforms like “ITcources” is an additional preferred advantage. Don’t hesitate to view leading technology courses and get certified to promote your profession or career in your attracted and on-demand IT field at our website “www.itcources.com”
1 note
·
View note
Text
Week 3 - After Effect Activity (1)
For this week’s lesson, we are to practice more animation techniques in Adobe After Effect. We will try to create an animation using only text and will be based on Roald Dahl’s works.
To understand what we are really working with, it’d be best to understand who the artist is and what kind of work he produced. We did a brief research on the artist, and he was the author of Charlie and the Chocolate Factory, Matilda, The BFG, and a treasury of original, evergreen, and beloved children’s books. He was born on 13th September 1916 and died on 23rd November 1990, yet he remains the world’s NO. 1 storyteller.
There were many works that he has produced. However, the class agreed to do one of his work, ‘George’s Marvellous Medicine’ and chose one of the quotes:
‘Will she go pop? Will she explode? Will she go flying down the road? Will she go poof in a puff of smoke? Start fizzing like a can of Coke?’
However, for this animation, we’d only be using the first two lines.
https://www.thebookpeople.co.uk/webapp/wcs/stores/servlet/article?articleId=100-roald-dahl-quotes
The sentence, ‘Will she go pop?’ Was separated into individual layers to create this fast transaction between the words. However, for the word ‘Pop?’, It is animated using the scale keyframe to give the sense of the word actually popping towards the composition. In extension to that, to bring a sense of fast motion, I applied ‘Motion Blur’ into the animation as this will make it look natural, under the circumstances of a fast-moving pace animation.
The same method is applied to the sentence, ‘Will she explode?’ as it’s separated into individual layers. The word ‘Explode’ was animated in the same way as the word ‘Pop’ using the scale keyframe, but enlarging the word to a certain extent. Moreover, opacity keyframe was also applied to this word as for when it reaches a certain amount of seconds, the word ‘Explode’ would disappear from the composition.
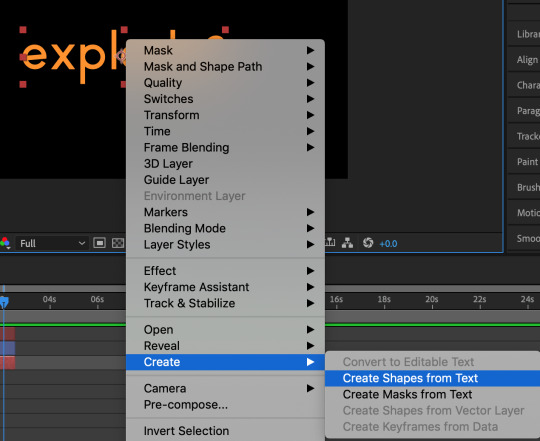
To create the explosion effect, I used the effect called ‘Explosion’. However, before the effect is being applied, the word ‘Explode’ is duplicated into another layer. Right click on the word and select, ‘Create shapes from text’. Once completed, the layer should be automatically duplicated and the previous layer should be hidden.
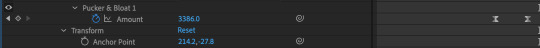
Select the new layer where the word ‘Explode’ has been created as a shape. Now on the add-on button, add the effect called ‘Pucker & Bloat’ and apply it to the layer.
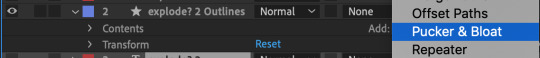
At the beginning of the sequence of the word ‘Explode’, animate the effect ‘Pucker & Bloat’, and make sure the effect is set to a certain extent to create the explosion effect.
Finally, to animate the sentence, “Will she go flying down the road?” - I would have to create a path first. Select the pen tool and create a path. Once completed, select the drop menu on the layer and select Text > Path Option > Path and select the option to ‘Mask 1′.

Change the settings so that it starts out of the composition and ends when it’s out of the composition using keyframes. Moreover, it is essential to put the timing into consideration as the viewers may get confused if the sentence moved too fast. In extension to that, I have also applied the ‘Explosion’ effect to the sentence to create that explosion of the text at the end.
Final results:

1 note
·
View note
Text
Why Take The Best Online Java Course Training In New York?

Java is a simple, object-oriented programming language that is often the top-choice of aspiring developers who wants to learn to code. Having a readable English-like syntax, Java enables developers to create robust web applications with ease. As more businesses are adopting Java-based solutions, there has been a surge in demand for skilled Java Developers. Thus, learning Java has become imperative. There are many ways to master this lucrative language like self-learning, practicing coding online, subscribing to tech podcasts, but taking a professional-led Java training is the right learning path. If you also want to gain Java expertise from scratch, consider enrolling in the Best Online Java Course Training in New York.
Reasons to take Java Training:
• A Java training program imparts in-depth knowledge of core and advanced Java concepts such as OOPS, data structures, exceptional handling, microservices, servlet, spring, hibernate, etc.
• While working on live projects and real-world case studies in the Best Online Java Coding Bootcamp in New York, you will gain hands-on experience in designing, testing, and developing high-end Java applications.
• A Java bootcamp offers career assistance and interview preparation tips to ensure you land your dream job after getting technically competent in Java.
• When you complete the Best Online Java Course Training in New York, you will receive an industry-recognized certificate which gives you a competitive edge over non-certified Java developers.
• The best Java Coding Bootcamp usually maintains a solid association with the leading tech giants like Apple, Microsoft, Google, IBM, Facebook, and others. Thus, if you join one, you can secure a job in Fortune 500 Companies.
• Java is a globally used coding language, spread across different domains like Healthcare, Automation, Finance, IT, Manufacturing, etc. So, learning Java can enlarge your job prospects.
Sign up with the Best Online Java Coding Bootcamp in New York, SynergisticIT, to avail of the above benefits. We provide structured Java training online to match your theoretical Java programming knowledge with practical implementation. Whether you are a fresher to coding or a professional looking to expand your web development skills, we got the right tools and resources to help you succeed in your career.
0 notes
Text
Best Training center to become Java Developer
What is Java?
Java is a programming language and a platform. Java is a high-level, robust, object-oriented, and secure programming language.
Java was developed by Sun Microsystems (which is now the subsidiary of Oracle) in the year 1995. James Gosling is known as the father of Java. Before Java, its name was Oak. Since Oak was already a registered company, James Gosling and his team changed the name from Oak to Java.
History of Java
James Gosling initiated the Java language project in June 1991 for use in one of his many set-top box projects. The language, initially called ‘Oak’ after an oak tree that stood outside Gosling's office, also went by the name ‘Green’ and ended up later being renamed as Java, from a list of random words.
Sun released the first public implementation as Java 1.0 in 1995. It promised to Write Once, Run Anywhere (WORA), providing no-cost run-times on popular platforms.
Java Example
Print Hello world using Java, this is the most basic program to introduce any programming language.
class Simple{
public static void main(String args[]){
System.out.println("Hello World");
}
}
Applications of Java
According to Sun, 3 billion devices run Java. There are many devices where Java is currently used. Some of them are as follows:
Desktop Applications such as acrobat reader, media player, antivirus, etc.
Web Applications such as irctc.co.in, LinkedIn.com, etc.
Enterprise Applications such as banking applications.
Mobile
Embedded System
Smart Card
Robotics
Games, etc.
Types of Java Applications
1) Standalone Application
Standalone applications are also known as desktop applications or window-based applications. These are traditional software that we need to install on every machine. Examples of standalone applications are Media players, antivirus, etc.
2) Web Application
An application that runs on the server-side and creates a dynamic page is called a web application. Currently, Servlet, JSP, Struts, Spring, Hibernate, JSF, etc. technologies are used for creating web applications in Java.
3) Enterprise Application
An application that is distributed in nature, such as banking applications, etc. is called an enterprise application. It has advantages like high-level security, load balancing, and clustering.
4) Mobile Application
An application that is created for mobile devices is called a mobile application. Currently, Android and Java ME are used for creating mobile applications.
Career
After 26 years, JAVA is still dominant over other programming languages, demanding for the JAVA programming language is still high and every Software Industry is using it. It cannot replace by any other language.
Java Developer Career path –
Entry Level ==> Mid Level ==> Senior Level
(Junior JAVA (JAVA Developer) (Senior JAVA Developer)
Developer)
Java Training
As you can see, Java is still dominant after 26 years, if you want to learn Java I want to know you about training center which will take you from beginner to expert in Java, they will also provide you with a certificate for Java Developer which will open many opportunities and career path for your future.
APPWARS TECHNOLOGIES is the best training center, you’ll get the certificate of Java Developer after completing the course.
APPWARS TECHNOLOGIES provides you with live project sessions, and every day you will learn new things, the project will be provided by the training center.
How to join the training center
The Organization works on offline mode and online mode as well, it is located in Noida and NCR, the head office is in Noida.
Join Link - https://appwarstechnologies.com/courses/java-training-in-noida/
0 notes
Text
Basic Mikrotik Hotspot Page Template

Download Template Hotspot Login Mikrotik Gratis Untuk Voucheran - Jika kalian masih menggunakan template hotspot login bawaan mikrotik mungkin kalian harus mencoba template hotspot login mikrotik dibawah ini yang bisa membuat halaman login mikrotik kalian menjadi lebih keren, cool, responsive, unik dan tentunya menarik.
Search for jobs related to Mikrotik hotspot login page template responsive free download or hire on the world's largest freelancing marketplace with 19m+ jobs. It's free to sign up and bid on jobs.
Halaman login hotspot mikrotik secara default sangatlah sederhana. Maka dari itu kita perlu mengubah tampilan agar lebih menarik. Dari pada Anda ribet untuk mengedit template bawaan mikrotik, kali ini saya akan membagikan kumpulan Template mikrotik terbaik menurut blog Renovasi Otak untuk Anda download secara gratis.
Mikrotik Hotspot Logout
Template Mikhmon
Mikrotik Hotspot Page Template
Basic Mikrotik Hotspot Page Template Downloads
Basic Mikrotik Hotspot Page Templates
Mikrotik Hotspot Login Page v0.1. Responsive Mikrotik Hotspot Login Page. If you would like to have nice login page for your hotspot user when using Mikrotik Hotspot you can use this project as your base. Simply download zip and load it into your router Files folder. How to Create Hotspots Mikrotik. Setting basic Hotspot Mikrotik Mikrotik Router is a router that has full features. One feature that is quite popular and widely used of Mikrotik Router itself is Hotspot. Do you know the difference regular sharing internet with Hotspot? Perhaps you often find wifi internet signal in the password using WPA or WEP.
Applies to RouterOS: v3, v4, v5+
1HTML customizations
1.4Variables
1.8Examples
2Firewall customizations
HTML customizations
Summary
You can create a completely different set of servlet pages for each HotSpot server you have, specifying the directory in 'html-override-directory' property of a HotSpot server profile /ip hotspot profile. The default servlet pages are copied in the directory 'hotspot' directory right after you create server profile. This directory can be accessed by connecting to the router with an FTP client. You can copy this directory and modify the pages as you like using the information from this section of the manual. Note that it is suggested to edit the files manually, as automated HTML editing tools may corrupt the pages by removing variables or other vital parts. After you are finished with content modification you need to upload this modified content to some custom directory on hotspot router and point previously mentioned property 'html-override-directory' value as path to this new custom HTML directory.
Note: If 'html-override-directory' value path is missing or empty then hotspot server will revert back to default HTML files.
Available Pages
Main HTML servlet pages, which are shown to user:
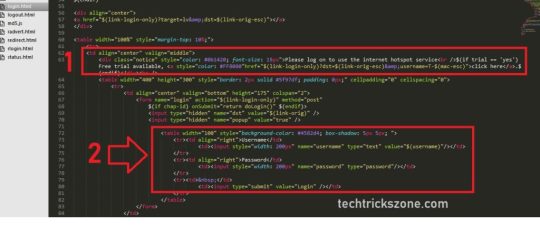
redirect.html - redirects user to another url (for example, to login page)
login.html - login page shown to a user to ask for username and password. This page may take the following parameters:
username - username
password - either plain-text password (in case of PAP authentication) or MD5 hash of chap-id variable, password and CHAP challenge (in case of CHAP authentication). This value is used as e-mail address for trial users
dst - original URL requested before the redirect. This will be opened on successfull login
popup - whether to pop-up a status window on successfull login
radius<id> - send the attribute identified with <id> in text string form to the RADIUS server (in case RADIUS authentication is used; lost otherwise)
radius<id>u - send the attribute identified with <id> in unsigned integer form to the RADIUS server (in case RADIUS authentication is used; lost otherwise)
radius<id>-<vnd-id> - send the attribute identified with <id> and vendor ID <vnd-id> in text string form to the RADIUS server (in case RADIUS authentication is used; lost otherwise)
radius<id>-<vnd-id>u - send the attribute identified with <id> and vendor ID <vnd-id> in unsigned integer form to the RADIUS server (in case RADIUS authentication is used; lost otherwise)
md5.js - JavaScript for MD5 password hashing. Used together with http-chap login method
alogin.html - page shown after client has logged in. It pops-up status page and redirects browser to originally requested page (before he/she was redirected to the HotSpot login page)
status.html - status page, shows statistics for the client. It is also able to display advertisements automatically
logout.html - logout page, shown after user is logged out. Shows final statistics about the finished session. This page may take the following additional parameters:
erase-cookie - whether to erase cookies from the HotSpot server on logout (makes impossible to log in with cookie next time from the same browser, might be useful in multiuser environments)
error.html - error page, shown on fatal errors only
Some other pages are available as well, if more control is needed:
rlogin.html - page, which redirects client from some other URL to the login page, if authorization of the client is required to access that URL
rstatus.html - similarly to rlogin.html, only in case if the client is already logged in and the original URL is not known
radvert.html - redirects client to the scheduled advertisement link
flogin.html - shown instead of login.html, if some error has happened (invalid username or password, for example)
fstatus.html - shown instead of redirect, if status page is requested, but client is not logged in
flogout.html - shown instead of redirect, if logout page is requested, but client is not logged in
Serving Servlet Pages
The HotSpot servlet recognizes 5 different request types:
request for a remote host
if user is logged in and advertisement is due to be displayed, radvert.html is displayed. This page makes redirect to the scheduled advertisment page
if user is logged in and advertisement is not scheduled for this user, the requested page is served
if user is not logged in, but the destination host is allowed by walled garden, then the request is also served
if user is not logged in, and the destination host is disallowed by walled garden, rlogin.html is displayed; if rlogin.html is not found, redirect.html is used to redirect to the login page
request for '/' on the HotSpot host
if user is logged in, rstatus.html is displayed; if rstatus.html is not found, redirect.html is used to redirect to the status page
if user is not logged in, rlogin.html is displayed; if rlogin.html is not found, redirect.html is used to redirect to the login page
request for '/login' page
if user has successfully logged in (or is already logged in), alogin.html is displayed; if alogin.html is not found, redirect.html is used to redirect to the originally requested page or the status page (in case, original destination page was not given)
if user is not logged in (username was not supplied, no error message appeared), login.html is showed
if login procedure has failed (error message is supplied), flogin.html is displayed; if flogin.html is not found, login.html is used
in case of fatal errors, error.html is showed
request for '/status' page
if user is logged in, status.html is displayed
if user is not logged in, fstatus.html is displayed; if fstatus.html is not found, redirect.html is used to redirect to the login page
request for '/logout' page
if user is logged in, logout.html is displayed
if user is not logged in, flogout.html is displayed; if flogout.html is not found, redirect.html is used to redirect to the login page
Note: If it is not possible to meet a request using the pages stored on the router's FTP server, Error 404 is displayed
There are many possibilities to customize what the HotSpot authentication pages look like:
The pages are easily modifiable. They are stored on the router's FTP server in the directory you choose for the respective HotSpot server profile.
By changing the variables, which client sends to the HotSpot servlet, it is possible to reduce keyword count to one (username or password; for example, the client's MAC address may be used as the other value) or even to zero (License Agreement; some predefined values general for all users or client's MAC address may be used as username and password)
Registration may occur on a different server (for example, on a server that is able to charge Credit Cards). Client's MAC address may be passed to it, so that this information need not be written in manually. After the registration, the server should change RADIUS database enabling client to log in for some amount of time.
To insert variable in some place in HTML file, the $(var_name) syntax is used, where the 'var_name' is the name of the variable (without quotes). This construction may be used in any HotSpot HTML file accessed as '/', '/login', '/status' or '/logout', as well as any text or HTML (.txt, .htm or .html) file stored on the HotSpot server (with the exception of traffic counters, which are available in status page only, and error, error-orig, chap-id, chap-challenge and popup variables, which are available in login page only). For example, to show a link to the login page, following construction can be used:
Variables
All of the Servlet HTML pages use variables to show user specific values. Variable names appear only in the HTML source of the servlet pages - they are automatically replaced with the respective values by the HotSpot Servlet. For most variables there is an example of their possible value included in brackets. All the described variables are valid in all servlet pages, but some of them just might be empty at the time they are accesses (for example, there is no uptime before a user has logged in).
List of available variables
Note: Some of the variables use hard coded http URL, if you are using https, you can construct the link in some other way, for example for $link-status, you can use https://$(hostname)/$(target-dir)status
Common server variables:
hostname - DNS name or IP address (if DNS name is not given) of the HotSpot Servlet ('hotspot.example.net')
identity - RouterOS identity name ('MikroTik')
login-by - authentication method used by user
plain-passwd - a 'yes/no' representation of whether HTTP-PAP login method is allowed ('no')
server-address - HotSpot server address ('10.5.50.1:80')
ssl-login - a 'yes/no' representation of whether HTTPS method was used to access that servlet page ('no')
server-name - HotSpot server name (set in the /ip hotspot menu, as the name property)
Links:
link-login - link to login page including original URL requested ('http://10.5.50.1/login?dst=http://www.example.com/')
link-login-only - link to login page, not including original URL requested ('http://10.5.50.1/login')
link-logout - link to logout page ('http://10.5.50.1/logout')
link-status - link to status page ('http://10.5.50.1/status')
link-orig - original URL requested ('http://www.example.com/')
General client information:
domain - domain name of the user ('example.com')
interface-name - physical HotSpot interface name (in case of bridged interfaces, this will return the actual bridge port name)
ip - IP address of the client ('10.5.50.2')
logged-in - 'yes' if the user is logged in, otherwise - 'no' ('yes')
mac - MAC address of the user ('01:23:45:67:89:AB')
trial - a 'yes/no' representation of whether the user has access to trial time. If users trial time has expired, the value is 'no'
username - the name of the user ('John')
host-ip - client IP address from /ip hotspot host table
vlan-id - Represents ID of a VLAN interface from which client is connected
User status information:
idle-timeout - idle timeout ('20m' or ' if none)
idle-timeout-secs - idle timeout in seconds ('88' or '0' if there is such timeout)
limit-bytes-in - byte limit for send ('1000000' or '---' if there is no limit)
limit-bytes-out - byte limit for receive ('1000000' or '---' if there is no limit)
refresh-timeout - status page refresh timeout ('1m30s' or ' if none)
refresh-timeout-secs - status page refresh timeout in seconds ('90s' or '0' if none)
session-timeout - session time left for the user ('5h' or ' if none)
session-timeout-secs - session time left for the user, in seconds ('3475' or '0' if there is such timeout)
session-time-left - session time left for the user ('5h' or ' if none)
session-time-left-secs - session time left for the user, in seconds ('3475' or '0' if there is such timeout)
uptime - current session uptime ('10h2m33s')
uptime-secs - current session uptime in seconds ('125')
Traffic counters, which are available only in the status page:
bytes-in - number of bytes received from the user ('15423')
bytes-in-nice - user-friendly form of number of bytes received from the user ('15423')
bytes-out - number of bytes sent to the user ('11352')
bytes-out-nice - user-friendly form of number of bytes sent to the user ('11352')
packets-in - number of packets received from the user ('251')
packets-out - number of packets sent to the user ('211')
remain-bytes-in - remaining bytes until limit-bytes-in will be reached ('337465' or '---' if there is no limit)
remain-bytes-out - remaining bytes until limit-bytes-out will be reached ('124455' or '---' if there is no limit)
Miscellaneous variables:
session-id - value of 'session-id' parameter in the last request
var - value of 'var' parameter in the last request
error - error message, if something failed ('invalid username or password')
error-orig - original error message (without translations retrieved from errors.txt), if something failed ('invalid username or password')
chap-id - value of chap ID ('371')
chap-challenge - value of chap challenge ('357015330013021234145245303253142246133175375316')
popup - whether to pop-up checkbox ('true' or 'false')
advert-pending - whether an advertisement is pending to be displayed ('yes' or 'no')
http-status - allows the setting of the http status code and message
http-header - allows the setting of the http header
RADIUS-related variables:
radius<id> - show the attribute identified with <id> in text string form (in case RADIUS authentication was used; ' otherwise)
radius<id>u - show the attribute identified with <id> in unsigned integer form (in case RADIUS authentication was used; '0' otherwise)
radius<id>-<vnd-id> - show the attribute identified with <id> and vendor ID <vnd-id> in text string form (in case RADIUS authentication was used; ' otherwise)
radius<id>-<vnd-id>u - show the attribute identified with <id> and vendor ID <vnd-id> in unsigned integer form (in case RADIUS authentication was used; '0' otherwise)
Working with variables
$(if <var_name>) statements can be used in theses pages. Following content will be included, if value of <var_name> will not be an empty string. It is an equivalent to $(if <var_name> != ') It is possible to compare on equivalence as well: $(if <var_name> <value>) These statements have effect until $(elif <var_name>), $(else) or $(endif). In general case it looks like this:
Only one of those expressions will be shown. Which one - depends on values of those variables for each client.
Redirects and custom Headers
Starting from RouterOS 5.12 there are 2 new hotspot html page variables:
http-status - allows the setting of the http status code and message
http-header - allows the setting of the http header message
Example:
Note: Although the above appears to use the conditional expression 'if' it is in fact setting the 'http-status' to '302' not testing for it. Also the same for the variable 'http-header'. Once again, even though it uses an 'if' it is in fact setting the variable to 'Location' followed by the url set from the variable 'link-redirect'.
E.g. in the case where $(link-redirect) evaluates to 'http://192.168.88.1/login', then the HTTP response returned to the client will be changed to:
http-status syntax:
XYZ - The status code you wish to return. Should be 3 decimal digits, first one must not be 0
HTTP_STATUS_MESSAGE - any text you wish to return to the client which will follow the above status code in the HTTP reply
In any HTTP response it will be on the first line and will be as follows:
http-header syntax:
HTTP_HEADER_NAME - name of the HTTP header to be sent in the response
HTTP_HEADER_VALUE - value of the HTTP header with name HTTP_HEADER_NAME to be sent in the response
The HTTP response will appear as:
All variables and conditional expressions within HTTP_HEADER_VALUE and HTTP_STATUS_MESSAGE are processed as usual.
In case multiple headers with the same name are added, then only the last one will be used (previous ones will be discarded). It allows the system to override regular HTTP headers (for example, Content-Type and Cache-Control).
Customizing Error Messages
All error messages are stored in the errors.txt file within the respective HotSpot servlet directory. You can change and translate all these messages to your native language. To do so, edit the errors.txt file. You can also use variables in the messages. All instructions are given in that file.
Multiple Versions of HotSpot Pages
Multiple HotSpot page sets for the same HotSpot server are supported. They can be chosen by user (to select language) or automatically by JavaScript (to select PDA/regular version of HTML pages).
To utilize this feature, create subdirectories in HotSpot HTML directory, and place those HTML files, which are different, in that subdirectory. For example, to translate everything in Latvian, subdirectory 'lv' can be created with login.html, logout.html, status.html, alogin.html, radvert.html and errors.txt files, which are translated into Latvian. If the requested HTML page can not be found in the requested subdirectory, the corresponding HTML file from the main directory will be used. Then main login.html file would contain link to '/lv/login?dst=$(link-orig-esc)', which then displays Latvian version of login page: <a href='/lv/login?dst=$(link-orig-esc)'>Latviski</a> . And Latvian version would contain link to English version: <a href='/login?dst=$(link-orig-esc)'>English</a>
Another way of referencing directories is to specify 'target' variable:
After preferred directory has been selected (for example, 'lv'), all links to local HotSpot pages will contain that path (for example, $(link-status) = 'http://hotspot.mt.lv/lv/status'). So, if all HotSpot pages reference links using '$(link-xxx)' variables, then no more changes are to be made - each client will stay within the selected directory all the time.
Misc
If you want to use HTTP-CHAP authentication method it is supposed that you include the doLogin() function (which references to the md5.js which must be already loaded) before the Submit action of the login form. Otherwise, CHAP login will fail.
The resulting password to be sent to the HotSpot gateway in case of HTTP-CHAP method, is formed MD5-hashing the concatenation of the following: chap-id, the password of the user and chap-challenge (in the given order)
In case variables are to be used in link directly, then they must be escaped accordingly. For example, in login page, <a href='https://login.example.com/login?mac=$(mac)&user=$(username)'>link</a> will not work as intended, if username will be '123&456=1 2'. In this case instead of $(user), its escaped version must be used: $(user-esc): <a href='https://login.server.serv/login?mac=$(mac-esc)&user=$(user-esc)'>link</a>. Now the same username will be converted to '123%26456%3D1+2', which is the valid representation of '123&456=1 2' in URL. This trick may be used with any variables, not only with $(username).
There is a boolean parameter 'erase-cookie' to the logout page, which may be either 'on' or 'true' to delete user cookie on logout (so that the user would not be automatically logged on when he/she opens a browser next time.
Examples
With basic HTML language knowledge and the examples below it should be easy to implement the ideas described above.
To provide predefined value as username, in login.html change:
to this line:
Mikrotik Hotspot Logout
(where hsuser is the username you are providing)
To provide predefined value as password, in login.html change:
to this line:
(where hspass is the password you are providing)
To send client's MAC address to a registration server in form of:
https://www.example.com/register.html?mac=XX:XX:XX:XX:XX:XX
change the Login button link in login.html to:
(you should correct the link to point to your server)
To show a banner after user login, in alogin.html after
$(if popup 'true')add the following line:
(you should correct the link to point to the page you want to show)
To choose different page shown after login, in login.html change:
to this line:
(you should correct the link to point to your server)
To erase the cookie on logoff, in the page containing link to the logout (for example, in status.html) change:
to this:
or alternatively add this line:
before this one:
External authentication
Another example is making HotSpot to authenticate on a remote server (which may, for example, perform creditcard charging):
Allow direct access to the external server in walled-garden (either HTTP-based, or IP-based)
Modify login page of the HotSpot servlet to redirect to the external authentication server. The external server should modify RADIUS database as needed
Here is an example of such a login page to put on the HotSpot router (it is redirecting to https://auth.example.com/login.php, replace with the actual address of an external authentication server):
The external server can log in a HotSpot client by redirecting it back to the original HotSpot servlet login page, specifying the correct username and password
Here is an example of such a page (it is redirecting to https://hotspot.example.com/login, replace with the actual address of a HotSpot router; also, it is displaying www.mikrotik.com after successful login, replace with what needed):
Hotspot will ask RADIUS server whether to allow the login or not. If allowed, alogin.html page will be displayed (it can be modified to do anything). If not allowed, flogin.html (or login.html) page will be displayed, which will redirect client back to the external authentication server.
Note: as shown in these examples, HTTPS protocol and POST method can be used to secure communications.
HTTP header detection
The Hotspot login pages have access to HTTP headers by using $(http-header-name);
For example, there exists an ability to check the user agent (or browser), and will return any other content instead of the regular login page, if so desired. This can be used to disable automatic popups in phones, for example.
For example, to output 'SUCCESS' for users of a specific Firefox mobile version, instead of the login page, you can these lines on the top of the rlogin.html page in your hotspot directory:
This will DISABLE the login popup for Android Firefox 40 users.
One click login
It is possible to create modified captive portal for quick one click login for scenarios where no user or password is required.
What you need to do is:
Create user for this purpose. In example it is 'notsosecretuser' with password 'notsosecretpass'
Assign this user to user profile that allows specific/unlimited amount of simultaneous active users.
Copy original hotspot directory that is already generated in routers file menu on root level.
Modify contents of this copy directory contents.
Only one file requires modifications for this to work, the 'login.html'.
Original:
Modified:
What changed:
User and Password '<tr>' fields are hidden.
Both User and Password field values contain predefined values.
Changed 'OK' button value(name) to something more fitting.
Now upload this new hotspot folder back to router, preferably with different name.
Change settings in hotspot server profile to use this new html directory.
Firewall customizations
Summary
Apart from the obvious dynamic entries in the /ip hotspot submenu itself (like hosts and active users), some additional rules are added in the firewall tables when activating a HotSpot service. Unlike RouterOS version 2.8, there are relatively few firewall rules added in the firewall as the main job is made by the one-to-one NAT algorithm.
NAT
From /ip firewall nat print dynamic command, you can get something like this (comments follow after each of the rules):
Putting all HotSpot-related tasks for packets from all HotSpot clients into a separate chain.
Any actions that should be done before HotSpot rules apply, should be put in the pre-hotspot chain. This chain is under full administrator control and does not contain any rules set by the system, hence the invalid jump rule (as the chain does not have any rules by default).
Redirect all DNS requests to the HotSpot service. The 64872 port provides DNS service for all HotSpot users. If you want HotSpot server to listen also to another port, add rules here the same way, changing dst-port property.
Template Mikhmon
Redirect all HTTP login requests to the HTTP login servlet. The 64873 is HotSpot HTTP servlet port.
Redirect all HTTPS login requests to the HTTPS login servlet. The 64875 is HotSpot HTTPS servlet port.
All other packets except DNS and login requests from unauthorized clients should pass through the hs-unauth chain.
And packets from the authorized clients - through the hs-auth chain.
First in the hs-unauth chain is put everything that affects TCP protocol in the /ip hotspot walled-garden ip submenu (i.e., everything where either protocol is not set, or set to TCP). Here we are excluding www.mikrotik.com from being redirected to the login page.
All other HTTP requests are redirected to the Walled Garden proxy server which listens the 64874 port. If there is an allow entry in the /ip hotspot walled-garden menu for an HTTP request, it is being forwarded to the destination. Otherwise, the request will be automatically redirected to the HotSpot login servlet (port 64873).
HotSpot by default assumes that only these ports may be used for HTTP proxy requests. These two entries are used to 'catch' client requests to unknown proxies (you can add more rules here for other ports). I.e., to make it possible for the clients with unknown proxy settings to work with the HotSpot system. This feature is called 'Universal Proxy'. If it is detected that a client is using some proxy server, the system will automatically mark that packets with the http hotspot mark to work around the unknown proxy problem, as we will see later on. Note that the port used (64874) is the same as for HTTP requests in the rule #9 (so both HTTP and HTTP proxy requests are processed by the same code).
HTTPS proxy is listening on the 64875 port.
Redirect for SMTP protocol may also be defined in the HotSpot configuration. In case it is, a redirect rule will be put in the hs-smtp chain. This is done so that users with unknown SMTP configuration would be able to send their mail through the service provider's (your) SMTP server instead of going to the (possibly unavailable outside their network of origin) SMTP server users have configured on their computers. The chain is empty by default, hence the invalid jump rule.
Providing HTTP proxy service for authorized users. Authenticated user requests may need to be subject to transparent proxying (the 'Universal Proxy' technique and advertisement feature). This http mark is put automatically on the HTTP proxy requests to the servers detected by the HotSpot HTTP proxy (the one that is listening on the 64874 port) as HTTP proxy requests for unknown proxy servers. This is done so that users that have some proxy settings would use the HotSpot gateway instead of the (possibly unavailable outside their network of origin) proxy server users have configured in their computers. This mark is also applied when advertisement is due to be shown to the user, as well as on any HTTP requests done form the users whose profile is configured to transparently proxy their requests.
Providing SMTP proxy for authorized users (the same as in rule #13).
Packet Filtering
From /ip firewall filter print dynamic command, you can get something like this (comments follow after each of the rules):
Any packet that traverse the router from an unauthorized client will be sent to the hs-unauth chain. The hs-unauth implements the IP-based Walled Garden filter.
Everything that comes to clients through the router, gets redirected to another chain, called hs-unauth-to. This chain should reject unauthorized requests to the clients.
Everything that comes from clients to the router itself, gets to yet another chain, called hs-input.
Before proceeding with (predefined) dynamic rules, the packet gets to the administratively controlled pre-hs-input chain, which is empty by default, hence the invalid state of the jump rule.
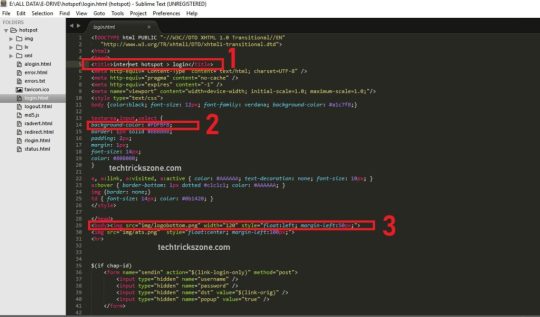
Allow client access to the local authentication and proxy services (as described earlier).
All other traffic from unauthorized clients to the router itself will be treated the same way as the traffic traversing the routers.
Unlike NAT table where only TCP-protocol related Walled Garden entries were added, in the packet filter hs-unauth chain is added everything you have set in the /ip hotspot walled-garden ip menu. That is why although you have seen only one entry in the NAT table, there are two rules here.
Everything else that has not been while-listed by the Walled Garden will be rejected. Note usage of TCP Reset for rejecting TCP connections.
Same action as in rules #7 and #8 is performed for the packets destined to the clients (chain hs-unauth-to) as well.
Reject all packets to the clients with ICMP reject message.
(Top | Back to Content)
Retrieved from 'https://wiki.mikrotik.com/index.php?title=Manual:Customizing_Hotspot&oldid=34366'
Mikrotik Hotspot Quick Setup Guide + Tips n Tricks for Hotspot !
Mikrotik Hotspot Page Template
A HOTSPOT is way to provide internet access to subscribers by means of an easy to use login interface as it does not require any client software/driver/dialer at user end. To log in, users may use almost any web browser , so they are not required to install additional software.It is also possible to allow users to access some web pages without authentication using Walled Garden feature.
In my personnel opinion, Hotspot is best suited for ad hoc situations, where you cannot control how the client has their machines configured. This is generally useful in Conference Rooms, Hotels, Cafe’s , Restaurants and likewise since people will come and go and you have few permanent users.
One big advantage of using hotspot is that HotSpot does not require any client software/driver/dialer. One disadvantage of using HotSpot is that its usually requires your client to open up his browser to log in before he can use your service . So users wanting to connect to your service using a router or some kind usually have a problem (as routers usually don’t support logging in via HTTP).
Following is a quick setup guide (CLI version) on how-to setup HOTSPOT server in Mikrotik using command interface.
This guide will help you in setting up . . .
# HOTSPOT server,
It will also configure DHCP to assign users IP Address from 172.16.0.1-172.16.0.255 ip pool . Change it accordingly.
I will add two Speed / Rate Limit Profiles, 256k and 512k, it will add a new user ‘zaib‘ password=test with 512k profile and user ‘test‘ Password=test with 256k Limit.
It will Add Default Route to internet which is DSL router ip 192.168.2.2 , Change it accordingly.
In this examples, Mikrotik have two interface cards.
Ether1 LAN = 172.16.0.1 / Connected with LAN/Hotspot users
Ether2 WAN = 192.168.2.1 / Connected with DSL router
DSL Router = 192.168.2.2
COPY PASTE SCRIPT. MAKE SURE YOUR MIKROTIK HAVE NO CONFIG , IT SHOULD BE EMPTY
Script Starts Below.
Basic Mikrotik Hotspot Page Template Downloads
TESTING CLIENT
Basic HOSTPOT is now configured. Now goto client pc, Upon booting, it will automatically receive ip from hotspot dhcp server, Open your browser and try to open any web site, You will see Hotspot Login page asking for credentials.
OR you can customize the hotspot login page to show your logo look like something
You can also make configuration changes via GUI. Please read the following guide for easy n step by step guide on HOTSPOT setup. http://wiki.mikrotik.com/wiki/Hotspot_server_setup
HOWTO CUSTOMIZE HOTSPOT LOGIN PAGE
You can use some fancy good looking login page. To customize the login page, Open Winbox , Goto Files , here you will see various files, look at hotspot/login.html , Drag n Drop this file to Desktop. See the attached picture.
Now open it using any html editor, I always prefer FRONTPAGE for editing HTML pages due to its easy interface. Customize it according to your need, You must have some prior knowledge of some website / html editing. You can insert your logo , advertisement and lot more in this page. After you are done, simply Upload the file back from where you downloaded it. use drag n drop feature. For beginners, I recommend you not to change any default variable, just ad your logo n text , After you are familiarized with the structure, you can build your own fully customized login page. – zaib
Good examples of hotspot login page can be found at following link.
Howto Redirect User to your selected site after successful Login
If you want that after successful login to hotspot , user must be redirected to your advertisement web site / any other web, then You will need to replace a variable on the hotspot/login.html document on the mikrotik router. You must replace $(link-orig) with the url of the website you want them to get after login.
There are two links that you have to replace, and both look like this:
Change them to
Now after successful login, user will automatically redirected to yoursite.com, you can also create your customized page showing users details using the variables available.
Howto Allow URL for some destinations for non authenticated Users
Sometimes it is required to allow access to some destinations / URLs for non authenticated users, for example if you have a web / radius server and you want that user can access it without login to hotspot, then you can add its ip address in walled garden.
HOTSPOT users can’t communicate with each other on LAN or PROXY-ARP issue
If you face hotspot broadcast issue / arp-poisoning , problem, Remove the address pool from the Hotspot to turn off Universal NAT,
As showed in the image below …
Howto Bypass authentication for Few Clients
This bypasses the hotspot by mac address.
(change xx:xx:xx:xx:xx:xx with your user’s mac address. You can also use the ip address to bypass.
You can also use mac-login or cookies features introduced in newer version to let auto login client.
HOTSPOT FLAGS,
HOTSPOT FLAGS, S – static, If you have the lease set as a static dhcp lease (assigns same ip every time device requests one) it shows as static. That is in “/ip dhcp-server lease” using “make-static”.
H – DHCP,
D – Dynamic,
A – If someone connects to the hotspot, they show up in the Hosts tab but are not yet authorized. Once they log in, they show up in the Active tab and are now authorized.
P – bypassed > Go to IP > Hotspot > IP Bindings > and add a new item. One of the “type” options is bypassed, which simply means they don’t have to login. From the wiki, “bypassed – performs the translation, but excludes client from login to the HotSpot”
Some more flags for ROUTE
X – Disabled, not active A – Active, in use C – Connected, a directly connected host route S – Static, added manually R – RIP route, received from the routing information protocol B – BGP, received from the border gateway protocol O – Received from the open shortest path first protocol M – Received from the mesh made easy protocol B – Blackhole route, packets are silently discarded U – Unreachable, discards the packets and sends an ICMP unreachable messages P – Prohibit, discards packet and sends an ICMP communication administratively prohibited message
Change Default ADMIN password for USERMAN
By default , there is no password for admin id for user-man. you can login by entering admin id and no password. this is dangerous.
Make sure you set password
/tool user-manager customer print
Basic Mikrotik Hotspot Page Templates
and note the number of admin id
Now change the password
/tool user-manager customer set password=zaib1234 numbers=0
Hotspot idle-timeout vs keep-alive-timeout (added 22-March-2019)
‘idle-timeout’ is used to detect, if client is not using Router networks, reaching timeout user will be logged out.
‘keep-alive-timeout’ used to detect, if is available and reachable, if check fails client will be dropped out, etc.
in other words,
idle timeout checks traffic. if user is online but is just not sending./receiving anything, he may reach its idle timeout.
keepalive timeout checks availability. keepalive timeout may only be reached if client is physically disconnected or turned off.
Regard’s SYED JAHANZAIB

0 notes
Text
Eclipse Cobol Development Environment

Using Eclipse for COBOL Development You can create, debug and run COBOL applications on your local machine or on a remote server. You use Eclipse features such as the COBOL and Remote Systems Explorer perspectives within the IDE to background check. HPE NonStop Development Environment for Eclipse (NSDEE) is a PC-based integrated development environment (IDE) for NonStop developers. It enables developers to create, edit, build, and debug NonStop software using Microsoft Windows PCs. The projects can be built for Open System Services (OSS) and/or Guardian environment on NonStop. IsCOBOL offers developers the choice of continuing with their current editor, command line utilities, and scripts, or using isCOBOL's Integrated Development Environment (IDE) Productive and customizable COBOL development Real time syntax checking, code hints, section collapsing, code completion, templates, and more.
Cobol Development Environment
Eclipse Cobol Development Environment Free
Eclipse Cobol Ide
Eclipse Cobol Development Environment Pdf
Home » Archived » COBOL » Cobol Compiler available in plug-in
Show:Today's Messages::Show Polls::Message Navigator
Cobol Compiler available in plug-in(message #500678)Fri, 27 November 2009 13:42
cdsosi Messages: 10 Registered: November 2009
Hello, I am using Cobol Plugin for eclipse and I am facing some problems using it. Cobol Plug-in seems to be plugged with Fujitsu NetCobol Compiler by default. 1st question : Is it possible to plug this plug-in with another compiler (freeware!)? 2nd question : If i want to only use the editor part not the compiler, is it possible to remove the link with the building process. 3rd question : I do not have Fujitsu NetCobol Compiler with my plug-in of course and there is a side-effect which is a problem to me. A thread tries to build the project at some regular intervals and erase the console output systematically before logging build output message. All the previously logged messages are lost ;((( Example of build output : Project TEST build started at 27 novembre 2009 12:12:45 Project TEST build finished at 27 novembre 2009 12:12:45 -------------------------------------------------- Last question : Would not it be possible to introduce a specific console for buildind process? Any help or suggestions on all that would be appreciated. Regards
Re: Cobol Compiler available in plug-in(message #502185 is a reply to message #500678)Mon, 07 December 2009 05:16
Tetsuya Suehisa Messages: 14 Registered: July 2009
Hello cdsosi, Thank you for using COBOL Plugin. I will answer your question. 1. As you mentioned, the COBOL Plugin is originally designed to use FUJITSU NetCOBOL compiler. If you want to switch the compiler to OpenCOBOL or some sort of free COBOL, you can modify the plugin. But I know it is not easy and requires much time to improve it so that even we have not provide the function. If you are interested in developing COBOL Plugin, will you join us and contribute this? 2. The instructions below may be the help. Select the project and click right button > Properties > Builders > Uncheck COBOL Builer and push OK 3. Same as No.2. 4. I'm sorry I don't understand what you want. Could you tell me a little more concretely? regards, tetsuya
Re: Cobol Compiler available in plug-in(message #502215 is a reply to message #502185)Mon, 07 December 2009 09:33
cdsosi Messages: 10 Registered: November 2009
Hello Tetsuya, Thanks for answering too! 1. I do not have much time to go deep inside the COBOL Plugin especially if you say that it is not easy part but maybe later and same remark for joining and contributing 2. Thanks for the checkbox state to disable on the Project Properties. I had not seen that. I went to the Window > Preferences > COBOL menu and in the COBOL Settings area there is a checkbox FUJITSU NetCOBOL that is 'uncheckable' (I thought it was the way to disable building process...) 3. ok 4. I 'll try to be more explicit!! Because of problem mentioned in 3 i thought it could be a solution to introduce a specific view (named 'COBOL Console ' for instance) in eclipse to log messages from COBOL Plugin building process. Specific consoles are often available in eclipse for CVS, Tomcat, ... In fact it seems that it is not a problem and that a specific console is already available for COBOL building process!! In the 'Display Selected Console' it was the COBOL Build Process that is selected by default. Other messages can be viewed by selecting other console... Sorry about that. However, I think there is another little problem that you should be interested in knowing (when the Project > Properties > Builders > COBOL Builder is checked ). I am developping a plugin under eclipse and have several projects in my workspace (Java, Java Plugin, COBOL). When I debug my plugin by launching a second eclipse runtime instance (Debug As Eclipse Application in other words!) the COBOL building process is launched many times (13 times, the build messages are displayed and erased ~ 13 times) althought the COBOL project has no modification inside. I do not think that it is a normal behavior. Regards
Re: Cobol Compiler available in plug-in(message #753965 is a reply to message #502215)Mon, 31 October 2011 08:56
Juanita Young Messages: 1 Registered: October 2011
COBOL comes to the Java virtual machine and the New Eclipse Plugin Apache Tomcat COBOL comes to the Java platform Today, Micro Focus is the release of 30-day free trial of Visual COBOL R3. This development environment enables COBOL users choose from a selection of development platforms and frameworks, including Eclipse and the JVM platform. Visual COBOL R3 also adds C # and Java-like constructs in an attempt to make programming easier for Java and COBOL NET. The project also includes a 'Visual COBOL Development Hub 'for Linux and Unix, allowing users to compile and debug COBOL code on your desktop remotely. More information about the project can be found on the website of Micro Focus. In over 50 years of age, COBOL (Common Business Oriented foot Language) is one of the oldest programming languages. Microsoft-Novell deal was still in danger CPTLN According to TechFlash, Microsoft led consortium CPTN are considering buying Novell patents. Although the patent was withdrawn, TechFlash Microsoft has said that this was just a procedural step 'is necessary to allow time to review the proposed transaction.' The consortium of Apple, Oracle and EMC, as well as Microsoft. Novell is being acquired by Attachmate Corporation in a transaction valued at approximately $ 2.2 billion, with the consortium CPTN apparently still thinking about buying at the same time 'certain intellectual property assets' for $ 450 million. The open source community has expressed concern about the acquisition of these patents CPTN. IcedTea Security Releases A new set of security updates have been made available to the IcedTea project: icedtea6 1.7.7, 1.8.4 and 1.9.4 icedtea6 icedtea6. The IcedTea project provides a harness to compile the source code OpenJDK6 using Free Software build tools. Please see the blog of a list of bugs fixed. RackSpace partner with Akamai Rackspace hosting and cloud hosting software company announced a 'strategic relationship' with Akamai, a provider of optimization services in the cloud. Rackspace will offer Akamai web application now and optimize cloud services as part of its portfolio of cloud hosting. Akamai Rackspace integrates features such as Secure Sockets Layer CNAME, in an effort to create a 'one stop shop' for housing, clouds and content acceleration services and web applications.
Previous Topic:CooCox ColinkNext Topic:Freecobol compilers
Goto Forum:
( Syndicate this forum (XML) ) ( )
Powered by FUDForum. Page generated in 0.02120 seconds
Take more control of your applications with powerful COBOL and Java technology solutions from Veryant.
Call us today at +1 619 453 0914 or Email us at [email protected]
Why choose Us
Whether you are evolving existing applications through SOA or improving quality and distribution processes, Veryant's innovative software offerings increase business productivity and provide a complete environment for COBOL application development, deployment and modernization.

Our Mission
To enable you to quickly and safely extend current applications to meet new business needs and demands using our portable, robust solutions translate into cost-effective, future-proof computing. Maximize a company’s IT investment by providing an array of innovative tools that always strive for improvement.
What you get
isCOBOL Evolve enables organizations to retain current COBOL investments while simultaneously offering a path forward to take advantage of the openness, portability and power of the Java platform without retraining staff or rewriting code.
Features that will make you love us
COBOL for Java platform and open systems migration
Multi platform
Target multiple platforms with a single codebase. If it runs Java it runs isCOBOL.
Powerful reporting capabilities
JasperReports integration, native API to manage printers, advanced print preview and PDF management.
Extended UI interface
Multiplatform, from desktop to web, rich and extensible widget choices (layout, extend grid, ribbon, javabeans)
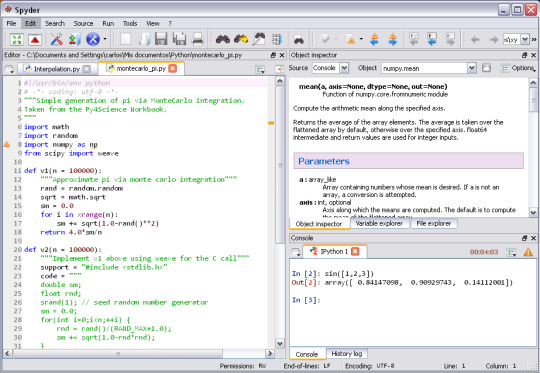
Integrated development environment
Eclipse-based development environment for key COBOL development tasks, including projects, forms, reports, and database management
Flexible database model
Pluggable file system for sequential, relative and indexed file structure including RDBMS databases
Java integration
Add the power and flexibility of the Java platform to existing COBOL programs and make COBOL investments easily accessible to the Java world
Multiple architectures
Powerful application processing with isCOBOL Application Server, load balancer capability and J2EE integration
Web Enablement
REST/SOAP Web Services, JSON, XML, Servlet and HTTP, leverage AJAX for screen section rendering over web browsers
Evolution not revolution
Cobol Development Environment
Comprehensive, cost-effective development, maintenance, application modernization and ROI improvement
Dedicated and experienced technical support
response time for ticket pre-screening
Eclipse Cobol Development Environment Free
response time for issue escalation
response time for tickets
Eclipse Cobol Ide
What our clients say about us
Eclipse Cobol Development Environment Pdf
((testimonial.text))

0 notes
Text
Apache Tomcat 403

Apache Tomcat 403 Forbidden
Apache Tomcat Http Status 403
Apache Tomcat 9 403 Access Denied
It was really very helpful for me. I was using version 8.5.32 and worked fine.thnaks. What is Apache Tomcat? Answer: Apache Tomcat is basically a Web Server and Servlet system. Because of the bug CVE-2020-1938 we want to use the latest Tomcat 7.0.100. See also CVE-2020-1938 We also use an Apache server in version 2.4, which connects to the Tomcat via AJP.
After you installed the Apache Tomcat server and successfully launched the <host>:8080 web page, you click on the Manager App button, and you get a 403 Access Denied message.
The Apache Tomcat Project is proud to announce the release of version 7.0.109 of Apache Tomcat. This release implements specifications that are part of the Java EE 6 platform. This release contains a number of bug fixes and improvements compared to version 7.0.108.
Hi, we have a strange symptom after an upgrade from Tomcat 8 to Tomcat 9, because we get a 403 for a call that works flawlessly with the previous version. Let's describe the scenario: We have a customer with a Wordpress application hosted on an Apache server. Some pages perform XMLHttpRequests to load and embed HTML snippets from other sources.
To fix it 1. Open the $CATALINA_BASE/conf/tomcat-users.xml file and add the following to the <tomcat-users> section.
<user username='admin' password='goanywhere' roles='admin-gui,manager-gui' />
2. If you are accessing the Tomcat server from a remote computer, open or create the file: $CATALINA_BASE/conf/Catalina/localhost/manager.xml, and add the below to the file.
<Context privileged='true' antiResourceLocking='false'
<Valve className='org.apache.catalina.valves.RemoteAddrValve' allow='^.*$' />
3. Restart the tomcat server: sudo systemctl restart tomcat.service
----------------------------------------------------------------------------------------------------------------- Watch the blessing and loving online channel: SupremeMasterTV live
If you have ever asked yourself these questions, this is the book for you. What is the meaning of life? Why do people suffer? What is in control of my life? Why is life the way it is? How can I stop suffering and be happy? How can I have a successful life? How can I have a life I like to have? How can I be the person I like to be? How can I be wiser and smarter? How can I have good and harmonious relations with others? Why do people meditate to achieve enlightenment? What is the true meaning of spiritual practice? Why all beings are one? Read the book for free here.
The AJP Connector
Table of Contents
Attributes
Special Features
Introduction
The AJP Connector element represents a Connector component that communicates with a web connector via the AJP protocol. This is used for cases where you wish to invisibly integrate Tomcat into an existing (or new) Apache installation, and you want Apache to handle the static content contained in the web application, and/or utilize Apache's SSL processing.
Use of the AJP protocol requires additional security considerations because it allows greater direct manipulation of Tomcat's internal data structures than the HTTP connectors. Particular attention should be paid to the values used for the address, secret, secretRequired and allowedRequestAttributesPattern attributes.
This connector supports load balancing when used in conjunction with the jvmRoute attribute of the Engine.
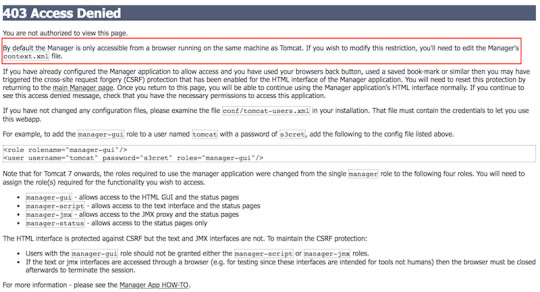
The native connectors supported with this Tomcat release are:
JK 1.2.x with any of the supported servers. See the JK docs for details.
mod_proxy on Apache httpd 2.x (included by default in Apache HTTP Server 2.2), with AJP enabled: see the httpd docs for details.
Other native connectors supporting AJP may work, but are no longer supported.
Attributes
Common Attributes
Apache Tomcat 403 Forbidden
All implementations of Connector support the following attributes:
Attribute Description ajpFlush
A boolean value which can be used to enable or disable sending AJP flush messages to the fronting proxy whenever an explicit flush happens. The default value is true. An AJP flush message is a SEND_BODY_CHUNK packet with no body content. Proxy implementations like mod_jk or mod_proxy_ajp will flush the data buffered in the web server to the client when they receive such a packet. Setting this to false can reduce AJP packet traffic but might delay sending packets to the client. At the end of the response, AJP does always flush to the client.
allowTrace
A boolean value which can be used to enable or disable the TRACE HTTP method. If not specified, this attribute is set to false.
asyncTimeout
The default timeout for asynchronous requests in milliseconds. If not specified, this attribute is set to the Servlet specification default of 30000 (30 seconds).
enableLookups
Set to true if you want calls to request.getRemoteHost() to perform DNS lookups in order to return the actual host name of the remote client. Set to false to skip the DNS lookup and return the IP address in String form instead (thereby improving performance). By default, DNS lookups are disabled.
encodedSolidusHandling
When set to reject request paths containing a %2f sequence will be rejected with a 400 response. When set to decode request paths containing a %2f sequence will have that sequence decoded to / at the same time other %nn sequences are decoded. When set to passthrough request paths containing a %2f sequence will be processed with the %2f sequence unchanged. If not specified the default value is reject. This default may be modified if the deprecated system propertyorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH is set.
maxHeaderCount
The maximum number of headers in a request that are allowed by the container. A request that contains more headers than the specified limit will be rejected. A value of less than 0 means no limit. If not specified, a default of 100 is used.
maxParameterCount
The maximum number of parameter and value pairs (GET plus POST) which will be automatically parsed by the container. Parameter and value pairs beyond this limit will be ignored. A value of less than 0 means no limit. If not specified, a default of 10000 is used. Note that FailedRequestFilterfilter can be used to reject requests that hit the limit.
maxPostSize
The maximum size in bytes of the POST which will be handled by the container FORM URL parameter parsing. The limit can be disabled by setting this attribute to a value less than zero. If not specified, this attribute is set to 2097152 (2 megabytes). Note that the FailedRequestFilter can be used to reject requests that exceed this limit.
maxSavePostSize
The maximum size in bytes of the POST which will be saved/buffered by the container during FORM or CLIENT-CERT authentication. For both types of authentication, the POST will be saved/buffered before the user is authenticated. For CLIENT-CERT authentication, the POST is buffered for the duration of the SSL handshake and the buffer emptied when the request is processed. For FORM authentication the POST is saved whilst the user is re-directed to the login form and is retained until the user successfully authenticates or the session associated with the authentication request expires. The limit can be disabled by setting this attribute to -1. Setting the attribute to zero will disable the saving of POST data during authentication. If not specified, this attribute is set to 4096 (4 kilobytes).
parseBodyMethods
A comma-separated list of HTTP methods for which request bodies using application/x-www-form-urlencoded will be parsed for request parameters identically to POST. This is useful in RESTful applications that want to support POST-style semantics for PUT requests. Note that any setting other than POST causes Tomcat to behave in a way that goes against the intent of the servlet specification. The HTTP method TRACE is specifically forbidden here in accordance with the HTTP specification. The default is POST
port
The TCP port number on which this Connector will create a server socket and await incoming connections. Your operating system will allow only one server application to listen to a particular port number on a particular IP address. If the special value of 0 (zero) is used, then Tomcat will select a free port at random to use for this connector. This is typically only useful in embedded and testing applications.
protocol
Sets the protocol to handle incoming traffic. To configure an AJP connector this must be specified. If no value for protocol is provided, an HTTP connector rather than an AJP connector will be configured. The standard protocol value for an AJP connector is AJP/1.3 which uses an auto-switching mechanism to select either a Java NIO based connector or an APR/native based connector. If the PATH (Windows) or LD_LIBRARY_PATH (on most unix systems) environment variables contain the Tomcat native library, the native/APR connector will be used. If the native library cannot be found, the Java NIO based connector will be used. To use an explicit protocol rather than rely on the auto-switching mechanism described above, the following values may be used: org.apache.coyote.ajp.AjpNioProtocol - non blocking Java NIO connector. org.apache.coyote.ajp.AjpNio2Protocol - non blocking Java NIO2 connector. org.apache.coyote.ajp.AjpAprProtocol - the APR/native connector. Custom implementations may also be used. Take a look at our Connector Comparison chart.
proxyName
If this Connector is being used in a proxy configuration, configure this attribute to specify the server name to be returned for calls to request.getServerName(). See Proxy Support for more information.
proxyPort
If this Connector is being used in a proxy configuration, configure this attribute to specify the server port to be returned for calls to request.getServerPort(). See Proxy Support for more information.
redirectPort
If this Connector is supporting non-SSL requests, and a request is received for which a matching <security-constraint> requires SSL transport, Catalina will automatically redirect the request to the port number specified here.
scheme
Set this attribute to the name of the protocol you wish to have returned by calls to request.getScheme(). For example, you would set this attribute to 'https' for an SSL Connector. The default value is 'http'.
secure
Set this attribute to true if you wish to have calls to request.isSecure() to return true for requests received by this Connector. You would want this on an SSL Connector or a non SSL connector that is receiving data from a SSL accelerator, like a crypto card, an SSL appliance or even a webserver. The default value is false.
sendReasonPhrase
Set this attribute to true if you wish to have a reason phrase in the response. The default value is false.
Note: This option is deprecated and will be removed in Tomcat 9. The reason phrase will not be sent.
URIEncoding
This specifies the character encoding used to decode the URI bytes, after %xx decoding the URL. If not specified, UTF-8 will be used unless the org.apache.catalina.STRICT_SERVLET_COMPLIANCEsystem property is set to true in which case ISO-8859-1 will be used.
useBodyEncodingForURI
This specifies if the encoding specified in contentType should be used for URI query parameters, instead of using the URIEncoding. This setting is present for compatibility with Tomcat 4.1.x, where the encoding specified in the contentType, or explicitly set using Request.setCharacterEncoding method was also used for the parameters from the URL. The default value is false.
Notes: See notes on this attribute in HTTP Connector documentation.
useIPVHosts
Set this attribute to true to cause Tomcat to use the IP address passed by the native web server to determine the Host to send the request to. The default value is false.
xpoweredBy
Set this attribute to true to cause Tomcat to advertise support for the Servlet specification using the header recommended in the specification. The default value is false.
Standard Implementations
To use AJP, you must specify the protocol attribute (see above).
The standard AJP connectors (NIO, NIO2 and APR/native) all support the following attributes in addition to the common Connector attributes listed above.
Attribute Description acceptCount
The maximum queue length for incoming connection requests when all possible request processing threads are in use. Any requests received when the queue is full will be refused. The default value is 100.
acceptorThreadCount
The number of threads to be used to accept connections. Increase this value on a multi CPU machine, although you would never really need more than 2. Also, with a lot of non keep alive connections, you might want to increase this value as well. Default value is 1.
acceptorThreadPriority
The priority of the acceptor threads. The threads used to accept new connections. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.
address
For servers with more than one IP address, this attribute specifies which address will be used for listening on the specified port. By default, the connector will listen on the loopback address. Unless the JVM is configured otherwise using system properties, the Java based connectors (NIO, NIO2) will listen on both IPv4 and IPv6 addresses when configured with either 0.0.0.0 or ::. The APR/native connector will only listen on IPv4 addresses if configured with 0.0.0.0 and will listen on IPv6 addresses (and optionally IPv4 addresses depending on the setting of ipv6v6only) if configured with ::.
allowedRequestAttributesPattern
The AJP protocol passes some information from the reverse proxy to the AJP connector using request attributes. These attributes are:
javax.servlet.request.cipher_suite
javax.servlet.request.key_size
javax.servlet.request.ssl_session
javax.servlet.request.X509Certificate
AJP_LOCAL_ADDR
AJP_REMOTE_PORT
AJP_SSL_PROTOCOL
JK_LB_ACTIVATION
CERT_ISSUER (IIS only)
CERT_SUBJECT (IIS only)
CERT_COOKIE (IIS only)
HTTPS_SERVER_SUBJECT (IIS only)
CERT_FLAGS (IIS only)
HTTPS_SECRETKEYSIZE (IIS only)
CERT_SERIALNUMBER (IIS only)
HTTPS_SERVER_ISSUER (IIS only)
HTTPS_KEYSIZE (IIS only)
The AJP protocol supports the passing of arbitrary request attributes. Requests containing arbitrary request attributes will be rejected with a 403 response unless the entire attribute name matches this regular expression. If not specified, the default value is null.
bindOnInit
Controls when the socket used by the connector is bound. By default it is bound when the connector is initiated and unbound when the connector is destroyed. If set to false, the socket will be bound when the connector is started and unbound when it is stopped.
clientCertProvider
When client certificate information is presented in a form other than instances of java.security.cert.X509Certificate it needs to be converted before it can be used and this property controls which JSSE provider is used to perform the conversion. For example it is used with the AJP connectors, the HTTP APR connector and with the org.apache.catalina.valves.SSLValve.If not specified, the default provider will be used.
connectionLinger
The number of seconds during which the sockets used by this Connector will linger when they are closed. The default value is -1 which disables socket linger.
connectionTimeout
The number of milliseconds this Connector will wait, after accepting a connection, for the request URI line to be presented. The default value for AJP protocol connectors is -1 (i.e. infinite).
executor
A reference to the name in an Executor element. If this attribute is set, and the named executor exists, the connector will use the executor, and all the other thread attributes will be ignored. Note that if a shared executor is not specified for a connector then the connector will use a private, internal executor to provide the thread pool.
executorTerminationTimeoutMillis
The time that the private internal executor will wait for request processing threads to terminate before continuing with the process of stopping the connector. If not set, the default is 5000 (5 seconds).
keepAliveTimeout
The number of milliseconds this Connector will wait for another AJP request before closing the connection. The default value is to use the value that has been set for the connectionTimeout attribute.
maxConnections
The maximum number of connections that the server will accept and process at any given time. When this number has been reached, the server will accept, but not process, one further connection. This additional connection be blocked until the number of connections being processed falls below maxConnections at which point the server will start accepting and processing new connections again. Note that once the limit has been reached, the operating system may still accept connections based on the acceptCount setting. The default value varies by connector type. For NIO and NIO2 the default is 10000. For APR/native, the default is 8192.
For NIO/NIO2 only, setting the value to -1, will disable the maxConnections feature and connections will not be counted.
maxCookieCount
The maximum number of cookies that are permitted for a request. A value of less than zero means no limit. If not specified, a default value of 200 will be used.
maxThreads
The maximum number of request processing threads to be created by this Connector, which therefore determines the maximum number of simultaneous requests that can be handled. If not specified, this attribute is set to 200. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
minSpareThreads
The minimum number of threads always kept running. This includes both active and idle threads. If not specified, the default of 10 is used. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
packetSize
This attribute sets the maximum AJP packet size in Bytes. The maximum value is 65536. It should be the same as the max_packet_size directive configured for mod_jk. Normally it is not necessary to change the maximum packet size. Problems with the default value have been reported when sending certificates or certificate chains. The default value is 8192. If set to less than 8192 then the setting will ignored and the default value of 8192 used.
processorCache
The protocol handler caches Processor objects to speed up performance. This setting dictates how many of these objects get cached. -1 means unlimited, default is 200. If not using Servlet 3.0 asynchronous processing, a good default is to use the same as the maxThreads setting. If using Servlet 3.0 asynchronous processing, a good default is to use the larger of maxThreads and the maximum number of expected concurrent requests (synchronous and asynchronous).
secret
Only requests from workers with this secret keyword will be accepted. The default value is null. This attribute must be specified with a non-null, non-zero length value unless secretRequired is explicitly configured to be false. If this attribute is configured with a non-null, non-zero length value then the workers must provide a matching value else the request will be rejected irrespective of the setting of secretRequired.
secretRequired
If this attribute is true, the AJP Connector will only start if the secret attribute is configured with a non-null, non-zero length value. This attribute only controls whether the secret attribute is required to be specified for the AJP Connector to start. It does not control whether workers are required to provide the secret. The default value is true. This attribute should only be set to false when the Connector is used on a trusted network.
tcpNoDelay
If set to true, the TCP_NO_DELAY option will be set on the server socket, which improves performance under most circumstances. This is set to true by default.
threadPriority
The priority of the request processing threads within the JVM. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
tomcatAuthentication
If set to true, the authentication will be done in Tomcat. Otherwise, the authenticated principal will be propagated from the native webserver and used for authorization in Tomcat.
The web server must send the user principal (username) as a request attribute named REMOTE_USER.
Note that this principal will have no roles associated with it.
The default value is true. If tomcatAuthorization is set to true this attribute has no effect.
tomcatAuthorization
If set to true, the authenticated principal will be propagated from the native webserver and considered already authenticated in Tomcat. If the web application has one or more security constraints, authorization will then be performed by Tomcat and roles assigned to the authenticated principal. If the appropriate Tomcat Realm for the request does not recognise the provided user name, a Principal will be still be created but it will have no roles. The default value is false.
Java TCP socket attributes
The NIO and NIO2 implementation support the following Java TCP socket attributes in addition to the common Connector and HTTP attributes listed above.
Attribute Description socket.rxBufSize
(int)The socket receive buffer (SO_RCVBUF) size in bytes. JVM default used if not set.
socket.txBufSize
(int)The socket send buffer (SO_SNDBUF) size in bytes. JVM default used if not set. Care should be taken if explicitly setting this value. Very poor performance has been observed on some JVMs with values less than ~8k.
socket.tcpNoDelay
(bool)This is equivalent to standard attribute tcpNoDelay.
socket.soKeepAlive
(bool)Boolean value for the socket's keep alive setting (SO_KEEPALIVE). JVM default used if not set.
socket.ooBInline
(bool)Boolean value for the socket OOBINLINE setting. JVM default used if not set.
socket.soReuseAddress
(bool)Boolean value for the sockets reuse address option (SO_REUSEADDR). JVM default used if not set.
socket.soLingerOn
(bool)Boolean value for the sockets so linger option (SO_LINGER). A value for the standard attribute connectionLinger that is >=0 is equivalent to setting this to true. A value for the standard attribute connectionLinger that is <0 is equivalent to setting this to false. Both this attribute and soLingerTime must be set else the JVM defaults will be used for both.
socket.soLingerTime
(int)Value in seconds for the sockets so linger option (SO_LINGER). This is equivalent to standard attribute connectionLinger. Both this attribute and soLingerOn must be set else the JVM defaults will be used for both.
socket.soTimeout
This is equivalent to standard attribute connectionTimeout.
socket.performanceConnectionTime
(int)The first value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceLatency
(int)The second value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceBandwidth
(int)The third value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.unlockTimeout
(int) The timeout for a socket unlock. When a connector is stopped, it will try to release the acceptor thread by opening a connector to itself. The default value is 250 and the value is in milliseconds
NIO specific configuration
The following attributes are specific to the NIO connector.
Attribute Description socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPool
(int)The NIO connector uses a class called NioChannel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 NioChannel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.bufferPoolSize
(int)The NioChannel pool can also be size based, not used object based. The size is calculated as follows: NioChannel buffer size = read buffer size + write buffer size SecureNioChannel buffer size = application read buffer size + application write buffer size + network read buffer size + network write buffer size The value is in bytes, the default value is 1024*1024*100 (100MB).
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 Body outline drawing. for no cache.
socket.keyCache
(int)Tomcat will cache KeyAttachment objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
socket.eventCache
(int)Tomcat will cache PollerEvent objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
selectorPool.maxSelectors
(int)The max selectors to be used in the pool, to reduce selector contention. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is 200.
selectorPool.maxSpareSelectors
(int)The max spare selectors to be used in the pool, to reduce selector contention. When a selector is returned to the pool, the system can decide to keep it or let it be GC'd. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is -1 (unlimited).
command-line-options
The following command line options are available for the NIO connector: -Dorg.apache.tomcat.util.net.NioSelectorShared=true|false - default is true. Set this value to false if you wish to use a selector for each thread. When you set it to false, you can control the size of the pool of selectors by using the selectorPool.maxSelectors attribute.
NIO2 specific configuration
The following attributes are specific to the NIO2 connector.
Attribute Description useCaches
(bool)Use this attribute to enable or disable object caching to reduce the amount of GC objects produced. The default value is false.
socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
We are an experienced Drupal development company with decade-long proven track record offering best-in-class customization, module, migration and Drupal development services worldwide. Drupal web services. Drupal is a powerful CMS widely used to develop variety of web solutions; ranging from a single page website to complex eCommerce stores. There are large numbers of web development companies in tech world that claim to provide excellent Drupal development services.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPoolSize
(int)The NIO2 connector uses a class called Nio2Channel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 Nio2Channel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
APR/native specific configuration
The APR/native implementation supports the following attributes in addition to the common Connector and AJP attributes listed above.
Attribute Description ipv6v6only
If listening on an IPv6 address on a dual stack system, should the connector only listen on the IPv6 address? If not specified the default is false and the connector will listen on the IPv6 address and the equivalent IPv4 address if present.
pollTime
Duration of a poll call in microseconds. Lowering this value will slightly decrease latency of connections being kept alive in some cases , but will use more CPU as more poll calls are being made. The default value is 2000 (2ms).
Nested Components
Special Features
Proxy Support
The proxyName and proxyPort attributes can be used when Tomcat is run behind a proxy server. These attributes modify the values returned to web applications that call the request.getServerName() and request.getServerPort() methods, which are often used to construct absolute URLs for redirects. Without configuring these attributes, the values returned would reflect the server name and port on which the connection from the proxy server was received, rather than the server name and port to whom the client directed the original request.
For more information, see the Proxy Support How-To.
Connector Comparison
Apache Tomcat Http Status 403

Below is a small chart that shows how the connectors differ.
Apache Tomcat 9 403 Access Denied
Java Nio Connector NIOJava Nio2 Connector NIO2APR/native Connector APRClassnameAjpNioProtocolAjpNio2ProtocolAjpAprProtocolTomcat Version7.x onwards8.x onwards5.5.x onwardsSupport PollingYESYESYESPolling SizemaxConnectionsmaxConnectionsmaxConnectionsRead Request HeadersBlockingBlockingBlockingRead Request BodyBlockingBlockingBlockingWrite Response Headers and BodyBlockingBlockingBlockingWait for next RequestNon BlockingNon BlockingNon BlockingMax ConnectionsmaxConnectionsmaxConnectionsmaxConnections

0 notes
Photo

Computer science majors have clear career path to No. 1 job in the U.S.
By Jaime North, digital marketing specialist
It comes as no surprise to those who love computer programming that Java developer is considered among the top career options in America.
In fact, according to Glassdoor it’s the best job. The worldwide leader on insights about jobs and companies sees a strong demand for Java developers this year with over 10,000 open roles and a median base salary of $90,830.
That’s especially good news to computer science majors at Bloomsburg University. Eight of the 10 best jobs for 2021 listed by Glassdoor are in technology-related careers, and 22 of the top 50 are in tech-related career areas, spanning artificial intelligence, cybersecurity, data science, data engineering, and software development.
“Given my experience with Java, I can definitely believe it,” says Jacob Swineford, a computer science major and tutor. “In my education alone, I’ve used java for mobile applications, websites, multithreading, simulations, JavaFX, JSP, Servlets, and educational purposes to teach students about other (programming) languages. You can definitely see why something like Java has become so widely used and thus very important to be taught.”
Right from the get-go, computer science majors at Bloomsburg get a taste of Java. They're introduced to computing in a three-semester Java programming sequence, according to Drue Coles, professor of mathematical and digital sciences.
"The curriculum exposes majors to a variety of programming languages and paradigms, not to mention aspects of computer science that aren't directly related to programming," Coles says. "But there's a special emphasis on Java, in large part because of its enduring importance in industry."
Look no further than smartphones and laptops to see Java at play. According to the Java’s own website, Twitter migrated its core infrastructure to Java — now supporting more than 400 million tweets a day — while Netflix powers through two billion daily content requests with Java-driven architecture.
And that’s just the tip of the iceberg.
“Java is a well-loved, well maintained, object-oriented language,” Swineford says. “In addition, a lot of its library can be viewed — but not edited — within an IDE. This means if a programmer is really unsure about using a library's body of code (class, method, interface, variables, etc.) they can check and make sure it's really what they want to use.”
He adds, “Java is also easy (wouldn't say very) to learn, and it's a good programming language at showing different ways of how certain structures are implemented, compiled, and interpreted.”
The best part, according to Swineford, is making computer programs completely from scratch. An added benefit he says in his ongoing study of Java has been the facilitation of independent thinking for problem solving. An ability Swineford knows will certainly lend him well after college.
“You might be able to imagine, learning Java over multiple semesters really helps hammer down concepts that might not be exclusive to Java,” Swineford says. “That is, thinking logic does not change over multiple languages and certain concepts have to be represented by different programming languages somehow. Having the same familiar language over the course of one's education really helps with that.”
0 notes
Text
How java is good for your career growth opportunities?
Java is a dynamic language which is one of the most popular and powerful languages in a programming platform. It is a high-level language which programs in a multiple platform such as Macintosh, windows and Unix computers. It is a primary source that should most commonly be used for Internet-based applications. It is originally designed for embedded network applications running on multiple platforms. Many of the companies are providing the basic projects in java for beginners to become a specialist in the programming language.
It is basically designed for developing programs with the set-top boxes and handheld, but now it became a popular choice for creating various methods of web applications. It can be used to build a small application module or applet that should be used as a part of a web page. This programming language is divided into two categories such as primitive types and reference types. Java for beginners will provide a best career opportunity to make success in their job roles as well as to improve their salary growth and lifestyle.
Java programming for beginners
It is one of the most popular and a common programming language that should be used across the world. It can be used by software professionals to design high-performance applications. It is the easiest language than other programming languages. It is one of the excellent choices for programming with java for beginners. It acquired the object-oriented principles for the beginning of basic and advanced java programs. It can be helpful to understand the subject concepts easily.
Why become a java developer?
Java is the most widely spreading language which commenced with the popularity at the top of the index. It provides an excellent skill for making good roles available in the different sectors. A java developer is the best role for designing various interfaces to creating and testing with various dynamic applications that are involved at every stage of the development process.
These developers can collaborate with the other professionals such as web designers, web developers and some other software engineers. It helps to develop their communication and other transferable skills which make advancements in your career as an IT professional. Java programmers should work for real-world applications such as healthcare, financial services and other popular sectors.
Benefits of java
Java is a multitude language of open-source libraries
It will backed by high-level support from tech giants like Google and IBM
Big and mature community support
It has some several readily available frameworks for rapidly building reliable apps
Java has a galore of IDEs and tools to help make java development simpler
Allows creating modular programs and reusable codes
Java is the language that can easy to write, compile, debug and learn than other programming languages
It is an independent platform for both the source and binary level
It has the ability to run the same program on many different systems through World Wide Web software.
Job roles of java
Java developer
Java architect
Web developer
Database administrator
Basic career path of java professional
Junior programmer
Junior developers are the entry-level programmers; they work on both front-end and back-end codes to build an application. These programmers can require an extensive knowledge of coding and the program language of JavaScript to develop and troubleshoot their company products. Those developers are the major part of a team to work as coders and developers. They are working in a popular company with the role of coding, debugging, reviewing coding and as technical documentation.
Skills required
Problem solving
Algorithms and data structures, algorithm complexity analysis
Strong command of a programming language
System design
Soft-skills
Senior programmer
A senior developer is an experienced professional in information technology. They should have experience leading a development team through a complete development lifecycle. They work with the Java programming language to develop various web applications and computer systems. Their career growth involves assigning tasks to the other team members, designing and testing code. They are responsible for communicating with other clients to analyze their requirements.
Requirements
The developers must experience in designing, building and testing java EE applications
In-depth of the knowledge it is popular for java frameworks like JSF and spring MVC
Experience with object-oriented design
Good delegation and time management skills
Problem-solving abilities
Architect
Architects in the Java programming language will define as to upgrade and integrate with the software architecture that should support with java-based applications. The duties of java architects are based on the infrastructure for design and integration for internet computing systems and they are responsible for analyzing information requirements and studying the business operations and user-interface with the development of physical databases. It is the great career path of the person to choose with the strong technical background moving. They are trained to consider the project and related to its contexts. Architect developers can ensure long-term benefits for themselves and their clients and the relevant neighborhoods.
Skills required for java architect
Knowledge of software architecture
Web programming abilities
Software design
Design and implementation of networks
Java can provide with the other variations such as java servlets, java beans and java script
Project management ability to present technical information
IT manager
These persons are responsible for making design, development and work with the management of java-based applications. It is an excellent opportunity for depending on your qualifications, interest and experience which is able to advance into the management roles and progress to the senior technical roles. They are the professionals for planning with new projects and clients to develop their requirements and dealing with the information system of the company. These managers can work in the various job roles such as hardware, software, networking and other business uses.
Skills required for IT manager
Analytical and problem solving skills
Strong technical skills
The ability to work well under pressure
Attention to detail
Team working skills
Organization and time management
Interpersonal and communication skills
Management and leadership skills
The end note
Java is an independent platform which is easy to learn. It is a good professional course for the students to become a well reputed developer.
0 notes
Text
SpringMVC Digging Road 2 - DispatcherServler + Controller
###Role of DispatcherServlet
DispatcherServlet is the implementation of the front-end controller design pattern, which provides the centralized access point of SpringWebMVC, is responsible for the assignment of responsibilities, and can be seamlessly integrated with SpringIoC container, so as to obtain all the capabilities of Spring.
DispatcherServlet is mainly used for duty scheduling, and it is mainly used for process control. Its main duties are as follows:
```
1:File upload resolution, if the request type is multipart, file upload resolution will be performed through MultipartResolver
2:Map the request to the processor through HandlerMapping (return a HandlerExecutionChain, which includes a processor and multiple HandlerInterceptor interceptors)
3:Many types of processors (processors in HandlerExecutionChain) are supported through HandlerAdapter
4:Resolve the logical view name to the concrete view implementation through ViewResolver
5:Localization analysis
6:Render a specific view
7:If an exception is encountered during execution, it will be handed over to HandlerExceptionResolver for resolution
```
###DispatcherServler Configure
DispatcherServlet can also configure its own initialization parameters, that is, <init-param> can be configured in servlet configuration.

###The relationship of context
The general context configuration of SpringWeb project is as follows:
<listener>
<listener-class>
org.springframework.web.context.ContextLoaderListener
</listener-class>
</listener>
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>classpath:applicationContext.xml</param-value>
</context-param>
```
contextConfigLocation : Represents the configuration file path used to load Bean;
contextClass : Represents the ApplicationContext implementation class used to load Bean, the default WebApplicationContext```
###Initialization order of DispatcherServlet
```
1:HttpServletBean inherits HttpServlet, so its init method will be called when the Web container starts
2:FrameworkServlet inherits HttpServletBean, initialize the Web context through initServletBean ()
3:DispatcherServlet inherits FrameworkServlet, and implemented onRefresh () method to provide some front-end controller related configurations
```
>In the DispatcherServlet of SpringMVC framework, around line 470:
/**
* This implementation calls {@link #initStrategies}.
*/
@Override
protected void onRefresh(ApplicationContext context) {
initStrategies(context);
}
/**
* Initialize the strategy objects that this servlet uses.
* <p>May be overridden in subclasses in order to initialize further strategy objects.
*/
protected void initStrategies(ApplicationContext context) {
initMultipartResolver(context);
initLocaleResolver(context);
initThemeResolver(context);
initHandlerMappings(context);
initHandlerAdapters(context);
initHandlerExceptionResolvers(context);
initRequestToViewNameTranslator(context);
initViewResolvers(context);
initFlashMapManager(context);
}
**The whole DispatcherServler initialization process mainly does two things:**
> * Initialize the Web context used by SpringMVC, and possibly specify the parent container (ContextLoaderListener loads the root context)
> * Initialize the policy used by DispatcherServlet, such as HandlerMapping、HandlerAdapter
###DispatcherServler Default Configure:
The default configuration of DispatcherServlet is in DispatcherServlet.properties (under the same package as DispatcherServlet class), and it is the default policy used when no configuration is specified in Spring configuration file.
It can be seen from the configuration that the DispatcherServlet will automatically register these special Bean when it starts, so we don't need to register. If we register, the default will not be registered.
###The special Bean which in DispatcherServlet
DispatcherServlet uses WebApplicationContext as the context by default, and there are some Bean in this context as follows:
####Controller
Processor/page controller, doing C in MVC, but the control logic is transferred to the front-end controller for processing requests;
####HandlerMapping
The mapping from processor is requested, and if the mapping is successful, a HandlerExecutionChain object (including a Handler processor (page processor) object and multiple HandlerInterceptor interceptors) is returned; For example, BeanNameUrlHandlerMapping maps URL and Bean name, and the Bean that is successfully mapped is the processor here;
####HandlerAdapter:
HandlerAdapter will package the processor as an adapter, thus supporting many types of processors, that is, the application of adapter design pattern, thus easily supporting many types of processors; For example, SimpleControllerHandlerAdapter will adapt the Bean that implements the Controller interface and call the handleRequest method of the processor for functional processing;
####ViewResolver
The ViewResolver will resolve the logical View name into a concrete view, for example, the InternalResourceViewResoulver will map the logical view name into a jsp view;
####LocalResolver
Localized parsing, because Spring supports internationalization, the LocaleResolver parses the Locale information of the client to facilitate internationalization;
####ThemeResolver
Theme analysis, through which multiple styles of a page can be realized, that is, the common effect similar to software skin;
####MultipartResolver
File upload analysis, used to support file upload;
####HandlerExceptionResolver
Processor exception resolution, which can map exceptions to the corresponding agreed error interface, so as to display a user-friendly interface (instead of showing users specific error information);
####RequestToViewNameTranslator
Automatically mapping the request URL to the logical view name when the processor does not return the relevant information such as the logical view name;
####FlashMapManager
It is used to manage the policy interface of FlashMap, which is used to store the output of one request, and when entering another request, it is used as the input of the request, which is usually used to redirect the scene.
###Controller brief introduction
Controller, which is the part C in MVC, is mainly responsible for the function processing part
```
1、Collect, validate and bind request parameters to command objects
2、Give the command object to the business object, and the business object will process and return the model data
3、Return ModelAndView(Model model part is the model data returned by the business object, and the view part is the logical view name)
```
###DisaptcherServler + Controller
DispatcherServlet is responsible for entrusting the request to the Controller for processing, and then selecting a specific view for rendering according to the logical view name returned by the Controller (and passing in the model data)
**The complete C (including logic control and function processing) in MVC consists of (DispatcherServlet+Controller)
###Controllerannotation
Before Spring2.5, we all defined our processor class by implementing the Controller interface or its implementation class (which is no longer recommended).
Spring2.5 introduces annotated processor support, and defines processor classes through @Controller and @RequestMapping annotations. And provides a powerful set of annotations:
> * @Controller
> * @RequestMapping
> * @RequestParam
> * @ModelAttribute
> * @SessionAttributes
> * @InitBinder
Spring3.0 introduces Restful architecture style support (supported by @PathVariable annotation and some other features), and introduces more annotation support
> * @CookieValue
> * @RequestHeader
> * @RequestBody
> * @ResponseStatus
> * @ExceptionHandler
> * @PathVariable
Spring3.1 use new HandlerMapping and HandlerAdapter to support @Controller and @RequestMapping annotation processors, Use the combination of processor mapping RequestMappingHandlerMapping and processor adapter RequestMappingHandlerAdapter to replace the processor mapping defaultannotationhandlermapping and processor adapter AnnotationMethodHandlerAdapter started in Spring2.5.
###Annotation implementation Controller
The configure of HandlerMapping and HandlerAdapter
> * Previous versions of Spring3.1:
DefaultAnnotationHandlerMapping and AnnotationMethodHandlerAdapter
> * The version starting with Spring3.1:
RequestMappingHandlerMapping and RequestMappingHandlerAdapter
###Example code:
Code structure reference:
https://blog.csdn.net/qq_33811662/article/details/80658813
Modify the content of spring-mvc.xml as follows:
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:mvc="http://www.springframework.org/schema/mvc"
xmlns:context="http://www.springframework.org/schema/context"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans-4.2.xsd
http://www.springframework.org/schema/mvc
http://www.springframework.org/schema/mvc/spring-mvc-4.2.xsd
http://www.springframework.org/schema/context
http://www.springframework.org/schema/context/spring-context-4.2.xsd">
<context:component-scan base-package="mvc1"></context:component-scan>
<mvc:annotation-driven></mvc:annotation-driven>
</beans>
Modify the contents of HelloController as follows:
package mvc1;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.servlet.ModelAndView;
@Controller
public class HelloController {
@RequestMapping("/hello")
public ModelAndView handleRequest(HttpServletRequest request, HttpServletResponse response) throws Exception {
System.out.println("进入后台控制器");
ModelAndView mv = new ModelAndView();
mv.addObject("content", "SpringMVC 初体验");
mv.setViewName("/WEB-INF/jsp/hello.jsp");
return mv;
}
}
Run the Server, enter the URL:
0 notes