#Norton Online Support Number
Text
Norton Campbell x Male! S/o college au!
Tw: Hints of NSFW, fighting (not really but still)
Tags: College au, Established Roommates, Established relationship, Fluff, Crack
A/N: This just very self indulgent tee hee :3


You and Norton have been best friends since Junior high. You two had been together through thick and thin, no matter what life threw at you. You two were inseparable, having each other's back at any time. (Even bailing Norton out of jail once but shhh)
To be clear, Norton is not someone who can be easily approached due to his infamous extreme mood swings but no one would have ever imagined that Norton would have a lover up until now. It felt almost natural for the both of you though. No matter what challenges you two face, you both always find a way support and uplift each other. You've celebrate many achievements together and provide a shoulder to lean on during tough times. The loyalty and care you two have for each other can never be replicated so easily.
Currently, you both graduated with a bang, got into your dream college and are now living in the dorms as roommates. Both of you having shared countless adventures and secrets through out your lives and ever since living together, it made the two of you even closer, to see each other's quirks and flaws. The other students really question if you two are just roommates or an old married couple.
Inside the dorm room, it's covered in a colorful mess of post-it notes with sweet messages, silly doodles, and inside jokes. It's their way of communicating and brightening each other's days. And in random occasions, you two leave love notes that are hidden in the most unexpected and odd places, like inside shoes or inside the cereal, keeping the romance alive in your everyday lives.
One of your favorite things about living together is the silly and weird traditions you two created. From weekend movie marathons to impromptu Mario kart competitions in the living room. Not to mention the endless prank war you two have, from putting plastic bugs in the shower to scaring each other during a scary movie, these traditions and antics have led to countless fond moments of laughter and bonding.
You two created a ridiculous number of nicknames for each other, some of which make no sense to anyone else but for you two, it's filled with love and whacky inside jokes.
Although, there are some downsides with living together. Mornings are a whirlwind of chaos as you two rush around trying to get ready for work or to class, often accidentally grabbing each other's clothes or toothbrushes in the rush.
One time, you accidentally took Norton's jacket to class and your professor (definitely not Luchino) teased you about it teehee.
We all know that Norton is frugal and thrifty, from extreme couponing to bargaining for half a prize. He wants to take you out for a dinner date in a very expensive restaurant? It now costs a fraction of what it was originally priced. Planning to go to that one very expensive amusement park? You bet your sweet ass he'll be surfing on the internet to find online discounts.
"NonNon doesn't this [insert item here] cost $150?"
"Oh yeah, I got a discount. I got it for $59."
"I beg your pardon?-"
"Then beg."
One time Norton got a call from one of your friends at the party you were attending, they've called to tell him to go pick your drunk ass up. Once he arrives, he sees you biting someone's ankle like an animal. (He had to tie you up to stop your reign of chaos.)
But your favorite part of the day, is where nighttime comes. Where the stress of the day leaves you both as a sense of peace and comfort replaces it.
There are times when words aren't necessary – just being around each other brings a sense of calm and happiness, you two find solace in each other's presence even in silence. You two can spend hours together simply reading working on their hobbies or just cuddling on the couch without needing to fill the silence with words. Sometimes, you both share vulnerable moments confess secrets and offer each other support. There's no need for words in such, for you both already know what the other is feeling after all.
And it's already enough.

Hihihiiii thanks for reading my first hcs, I'm still trying to juggle school work and making hcs so please be a bit patient with me darlings! (づ。◕‿‿◕。)づ
#idv x reader#idv#idv prospector#norton campbell#identity v#identity v x reader#norton campbell x reader#idv prospector x reader#identity v fanfic
85 notes
·
View notes
Text
should i turn on norton secure vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
should i turn on norton secure vpn
Norton Secure VPN benefits
Title: Unlocking Online Freedom: Exploring the Benefits of Norton Secure VPN
In an age where our digital footprint grows exponentially, safeguarding our online activities has become paramount. Norton Secure VPN stands as a formidable shield, offering a plethora of benefits to users seeking privacy, security, and accessibility in their online endeavors.
First and foremost, Norton Secure VPN ensures privacy by encrypting data transmitted over the internet. With the prevalence of cyber threats and data breaches, protecting sensitive information has never been more crucial. By encrypting your connection, Norton Secure VPN shields your data from prying eyes, whether you're browsing from a public Wi-Fi hotspot or your own home network.
Moreover, Norton Secure VPN enables users to access geo-restricted content with ease. Whether it's streaming services, websites, or social media platforms, geographical limitations often hinder access to desired content. With servers strategically located around the globe, Norton Secure VPN empowers users to bypass these restrictions, granting them unrestricted access to the content they crave.
Additionally, Norton Secure VPN enhances security by masking your IP address and location. This not only protects your identity and online activities from potential threats but also prevents advertisers and other third parties from tracking your online behavior for targeted marketing purposes.
Furthermore, Norton Secure VPN offers peace of mind with its automatic Wi-Fi security feature. By automatically encrypting data when connecting to unsecured Wi-Fi networks, it ensures that your online activities remain protected, even when you're on the go.
In conclusion, Norton Secure VPN provides a comprehensive solution for individuals seeking privacy, security, and freedom in their online experiences. With its robust encryption, global server network, and automatic security features, it stands as a reliable ally in the battle for online privacy and accessibility.
Norton Secure VPN drawbacks
Norton Secure VPN is a popular choice for individuals seeking to enhance their online privacy and security. However, like any product, it has its drawbacks that users should be aware of.
One of the main drawbacks of Norton Secure VPN is its limited device compatibility. While it supports major platforms such as Windows, macOS, Android, and iOS, it lacks compatibility with certain devices like gaming consoles and smart TVs. This can be inconvenient for users who wish to protect their privacy across all their devices.
Another drawback is the limited number of server locations. Norton Secure VPN offers servers in a select number of countries, which may not provide users with the variety and flexibility they desire. This could result in slower connection speeds and difficulty accessing geo-restricted content.
Additionally, some users have reported inconsistencies in connection speeds and reliability. While Norton Secure VPN aims to provide fast and secure connections, there have been instances where users experienced drops in speed or disconnections, which can be frustrating, especially during sensitive online activities.
Furthermore, Norton Secure VPN's pricing may deter some potential users. Compared to other VPN services on the market, Norton's subscription plans can be relatively expensive, especially considering the aforementioned limitations.
In conclusion, while Norton Secure VPN offers valuable features for enhancing online privacy and security, such as encryption and ad-tracking prevention, it does have its drawbacks, including limited device compatibility, server locations, connection reliability, and pricing. Users should carefully consider these factors before deciding if Norton Secure VPN is the right choice for their needs.
Norton Secure VPN privacy concerns
As digital privacy becomes an increasingly pressing concern, users are turning to virtual private networks (VPNs) for protection. Norton Secure VPN is one such service offering security and anonymity online. However, like any VPN provider, it's not immune to privacy concerns.
One primary issue revolves around logging policies. While Norton claims not to log users' online activities, there's always a level of trust involved, as the company could potentially be compelled to hand over data to authorities if legally required. This raises concerns about the true extent of user anonymity.
Another concern is the potential for data leaks or breaches. Despite employing robust encryption measures, no system is entirely foolproof. If Norton's servers were compromised, users' personal information and browsing habits could be exposed, undermining the very privacy the VPN aims to protect.
Furthermore, Norton Secure VPN's jurisdiction in the United States is subject to government surveillance laws and intelligence sharing agreements, such as the Five Eyes alliance. This may deter users seeking maximum privacy from choosing the service.
Moreover, some users have reported inconsistent speeds and connectivity issues with Norton Secure VPN, which can compromise both privacy and user experience.
In conclusion, while Norton Secure VPN offers a layer of protection for internet users, it's not without its privacy concerns. Users should weigh the risks and benefits carefully and consider alternative VPN providers that may offer stronger privacy assurances. Additionally, employing other privacy-enhancing measures, such as using Tor or encrypted messaging apps, can further safeguard online anonymity.
Norton Secure VPN performance impact
Norton Secure VPN is a popular choice for individuals and businesses looking to enhance their online security and privacy. However, one common concern among users is the potential performance impact that using a VPN can have on their internet connection.
When it comes to Norton Secure VPN, the performance impact is relatively minimal compared to other VPN services. This is because Norton has invested in robust infrastructure to ensure that users can enjoy a secure connection without sacrificing speed and performance. The VPN servers are strategically located around the world, which helps to minimize latency and ensure smooth browsing and streaming experiences.
While using any VPN service will inherently introduce some degree of latency due to the encryption and rerouting of your internet traffic, Norton Secure VPN has optimized its technology to mitigate this impact. Users can expect a slight decrease in internet speed, particularly when connecting to servers that are located far away. However, for the majority of daily online activities, such as browsing, streaming, and online gaming, the performance impact is generally negligible.
In conclusion, Norton Secure VPN offers a balance between strong security features and minimal performance impact. Users can enjoy peace of mind knowing that their online activities are encrypted and protected, without experiencing significant slowdowns in their internet connection. Whether you are working remotely, accessing sensitive information, or simply looking to browse the web anonymously, Norton Secure VPN is a reliable choice for maintaining your online privacy without compromising on speed and performance.
Norton Secure VPN alternatives
In the realm of digital security, Norton Secure VPN has established itself as a trusted name, offering users a layer of protection while browsing the internet. However, as with any service, users may seek alternatives for various reasons such as pricing, features, or performance. Here, we explore some noteworthy alternatives to Norton Secure VPN.
ExpressVPN: Known for its robust security features and extensive server network, ExpressVPN offers users a high level of privacy and anonymity. With its user-friendly interface and reliable performance, it's a popular choice among individuals and businesses alike.
CyberGhost: Offering a balance between affordability and functionality, CyberGhost provides users with strong encryption and a wide range of server locations. Its dedicated streaming and torrenting profiles make it a favorite among users who prioritize accessing geo-restricted content.
Surfshark: This relatively new player in the VPN market has quickly gained attention for its unlimited simultaneous connections feature and affordable pricing. With strong encryption protocols and a strict no-logs policy, Surfshark offers users peace of mind while browsing the web.
ProtonVPN: Developed by the team behind the encrypted email service ProtonMail, ProtonVPN prioritizes user privacy and security. With its emphasis on transparency and open-source software, it's a solid choice for users seeking a trustworthy VPN provider.
Private Internet Access (PIA): Renowned for its extensive server network and customizable encryption options, PIA is a favorite among privacy-conscious users. Its affordable pricing and robust security features make it a compelling alternative to Norton Secure VPN.
In conclusion, while Norton Secure VPN offers a reliable service, exploring alternatives can provide users with additional features and flexibility to suit their specific needs. Whether it's privacy, affordability, or performance, there are plenty of options available in the VPN market to cater to diverse preferences.
0 notes
Text
do i keep antivirus with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i keep antivirus with vpn
Antivirus software
Antivirus software is a crucial tool for protecting your computer against malicious software, viruses, malware, and other cyber threats. These programs are designed to detect, prevent, and remove malicious software from your device, keeping your data and personal information safe from potential cyber attacks.
There are various types of antivirus software available in the market, ranging from free basic versions to more advanced paid subscriptions. Some popular antivirus software providers include Norton, McAfee, Avast, Kaspersky, and Bitdefender.
The primary function of antivirus software is to scan your computer regularly for any suspicious files or programs that may harm your system. It actively monitors your device's activity, looking for signs of malware and other threats. Once a threat is detected, the software will quarantine or remove the malicious file to prevent any further damage.
Antivirus software also offers real-time protection, scanning files as you access them to ensure they are safe. Additionally, many antivirus programs come with features such as firewall protection, email scanning, and web protection to further enhance your device's security.
It is essential to keep your antivirus software up to date to ensure it is effective against the latest threats. Regularly update the software and run scans to maintain optimal protection for your computer.
Overall, investing in reliable antivirus software is a critical step in safeguarding your digital life and ensuring your online activities are secure. By choosing the right antivirus program and practicing safe browsing habits, you can significantly reduce the risk of falling victim to cyber threats.
VPN service
A VPN service, which stands for Virtual Private Network, is an essential tool for ensuring online privacy and security. Whether you are browsing the internet, accessing public Wi-Fi networks, or simply looking to secure your online activities, a VPN service is designed to protect your data and identity from prying eyes.
By using a VPN service, your internet traffic is encrypted and routed through a secure server, masking your IP address and making it difficult for hackers, advertisers, or even your Internet Service Provider to track your online activities. This encryption helps to keep your personal information, such as passwords, credit card details, and browsing history, safe from potential threats.
Not only does a VPN service offer security benefits, but it also allows you to access geo-restricted content by changing your virtual location. This means you can enjoy streaming services, websites, and content that may be blocked in your region.
When choosing a VPN service, it's important to consider factors such as connection speed, server locations, data encryption protocols, and privacy policy. Look for a reputable provider that offers a user-friendly interface and reliable customer support.
In conclusion, a VPN service is a valuable tool for safeguarding your online privacy and security. Whether you are a frequent traveler, remote worker, or simply conscious of protecting your digital footprint, investing in a quality VPN service can offer peace of mind and enhanced online freedom.
Cybersecurity tools
Cybersecurity tools are essential in safeguarding our online activities and data from potential cyber threats and attacks. These tools are designed to provide protection against various cyber risks and vulnerabilities that can compromise our sensitive information and personal details. With the increasing number and sophistication of cyber threats in today's digital world, utilizing cybersecurity tools has become more crucial than ever.
One of the commonly used cybersecurity tools is antivirus software, which helps detect and remove malware, viruses, and other malicious programs from our devices. Firewalls are another important tool that acts as a barrier between a trusted network and external networks to prevent unauthorized access and cyber attacks. Encryption tools are also vital in protecting data by converting it into a code that can only be accessed by authorized users.
In addition to these basic tools, there are more advanced cybersecurity solutions available today. Intrusion detection systems monitor network traffic for suspicious activities, while penetration testing tools help identify potential vulnerabilities in systems and applications. Security information and event management (SIEM) tools provide real-time analysis of security alerts and log data to help organizations respond to security incidents promptly.
By utilizing a combination of these cybersecurity tools, individuals and organizations can enhance their security posture and minimize the risks of falling victim to cyber attacks. It is important to stay updated with the latest cybersecurity tools and technologies to effectively protect against evolving cyber threats and ensure online safety and privacy.
Malware protection
Title: Safeguard Your Digital World: The Importance of Malware Protection
In today's interconnected digital landscape, the threat of malware looms large, posing significant risks to individuals and businesses alike. Malicious software, or malware, encompasses a variety of harmful programs designed to infiltrate, disrupt, or damage computer systems and networks. From viruses and worms to ransomware and spyware, the range of malware threats continues to evolve, becoming more sophisticated and pervasive with each passing day.
Effective malware protection is essential for safeguarding sensitive data, preserving system integrity, and maintaining productivity. Here's why investing in robust malware protection measures is imperative:
Protecting Data Privacy: Malware can compromise sensitive information such as personal identities, financial details, and proprietary business data. By deploying reliable malware protection solutions, individuals and organizations can mitigate the risk of data breaches and uphold privacy standards.
Preventing Financial Loss: Malware attacks can lead to financial losses stemming from stolen funds, fraudulent transactions, or extortion through ransom demands. Implementing proactive malware defense mechanisms helps minimize financial risks and safeguard assets.
Ensuring System Reliability: Malware infections can impair system performance, disrupt operations, and even render devices or networks inoperable. By maintaining robust malware protection protocols, users can uphold system reliability and minimize downtime.
Preserving Reputational Integrity: A malware-related security breach can tarnish an individual's or organization's reputation, eroding trust among stakeholders and customers. Prioritizing malware protection demonstrates a commitment to security and enhances reputational integrity.
Staying Ahead of Emerging Threats: With the ever-evolving landscape of cyber threats, staying abreast of emerging malware variants and attack vectors is crucial. Regularly updating malware protection solutions helps users stay ahead of evolving threats and adapt to new security challenges.
In conclusion, investing in comprehensive malware protection is not just a prudent measure—it's a necessity in today's digital age. By prioritizing security and deploying robust defense mechanisms, individuals and organizations can fortify their digital assets and mitigate the risks posed by malware threats.
Internet privacy
Internet privacy is a critical aspect of our digital lives that is becoming increasingly important in today's interconnected world. With the advancements in technology and the rise of online platforms, ensuring the security and confidentiality of our personal information has become a major concern for many individuals.
In the digital age, our online activities leave behind a trail of data that can be accessed and potentially exploited by various entities. From social media websites tracking our browsing habits to online retailers collecting our purchase history, our personal information is constantly being monitored and stored without our explicit knowledge or consent.
Protecting our internet privacy involves taking proactive measures to safeguard our sensitive data from unauthorized access and misuse. This includes using secure passwords, enabling two-factor authentication, and regularly updating privacy settings on our devices and online accounts.
Furthermore, utilizing virtual private networks (VPNs) can help encrypt our internet traffic and hide our IP addresses, making it harder for third parties to track our online activities.
It is also essential to be cautious about the information we share online and be mindful of the websites we visit and the links we click on. Phishing scams and malicious websites can trick individuals into disclosing personal information or installing harmful software on their devices.
By educating ourselves about internet privacy best practices and staying informed about the latest cybersecurity threats, we can better protect our digital identities and maintain control over our online privacy. Ultimately, taking proactive steps to safeguard our internet privacy is crucial in ensuring a safe and secure online experience.
0 notes
Text
does norton security offer a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does norton security offer a vpn
Norton VPN features
Norton VPN, offered by NortonLifeLock, is a comprehensive solution designed to safeguard your online privacy and security. With a host of features tailored to meet the needs of modern internet users, Norton VPN stands out as a reliable choice for protecting your digital footprint.
One of the key features of Norton VPN is its robust encryption protocols. Utilizing military-grade encryption, Norton VPN ensures that your online activities remain private and secure from prying eyes. Whether you're browsing the web, accessing sensitive information, or streaming content, you can trust that your data is shielded from potential threats.
Furthermore, Norton VPN offers a global network of servers, allowing you to browse the internet anonymously from virtually anywhere in the world. By masking your IP address and location, Norton VPN helps you bypass geo-restrictions and access content that may be blocked in your region. Whether you're traveling abroad or simply want to enjoy unrestricted access to online content, Norton VPN has you covered.
In addition to its encryption and global server network, Norton VPN boasts a user-friendly interface that makes it easy to connect and navigate. With just a few clicks, you can secure your internet connection and enjoy peace of mind knowing that your data is protected.
Moreover, Norton VPN includes features such as automatic kill switch and split tunneling, further enhancing your online security and privacy. The automatic kill switch ensures that your internet connection is severed in the event that the VPN connection drops, preventing any potential data leaks. Meanwhile, split tunneling allows you to route specific traffic through the VPN while keeping other traffic unaffected, giving you greater control over your online experience.
Overall, Norton VPN offers a comprehensive suite of features designed to protect your online privacy and security. Whether you're browsing the web, streaming content, or conducting sensitive transactions, Norton VPN provides the peace of mind you need in today's digital age.
Norton VPN pricing
Title: Understanding Norton VPN Pricing: Is It Worth the Investment?
Norton VPN, a product by NortonLifeLock, offers a secure and private connection for users to browse the internet without compromising their data security. While considering Norton VPN, understanding its pricing structure is crucial to determine whether it aligns with your budget and requirements.
Norton VPN provides flexible pricing plans tailored to meet various user needs. The pricing typically depends on factors such as the duration of the subscription and the number of devices covered. Users can choose between monthly or annual subscriptions, with the latter often offering cost savings. Additionally, Norton frequently runs promotions and discounts, providing opportunities for users to avail themselves of the service at reduced rates.
The pricing tiers usually offer a range of features, including unlimited bandwidth, access to servers worldwide, and multi-device compatibility. Higher-tier plans may include advanced security features such as ad-tracker blocking and a no-log VPN service for enhanced privacy.
When evaluating Norton VPN's pricing, it's essential to consider the value it provides. While some users may find the cost justified for the peace of mind and security it offers, others may seek more budget-friendly alternatives.
Comparing Norton VPN's pricing with other VPN services can help users make an informed decision. Factors such as server coverage, connection speed, and customer support should also be taken into account when assessing the overall value proposition.
In conclusion, Norton VPN offers competitive pricing with flexible plans to cater to different user needs. While the cost may vary depending on the subscription duration and features included, the service aims to deliver reliable security and privacy solutions. Ultimately, whether Norton VPN's pricing is worth the investment depends on individual preferences and requirements for online privacy and security.
Norton VPN compatibility
Title: Ensuring Compatibility: Norton VPN and Your Device
Norton VPN stands out as a popular choice in the realm of virtual private networks (VPNs), offering robust security features and reliable performance. However, before diving into the world of secure browsing with Norton VPN, users often wonder about its compatibility with various devices and platforms.
Fortunately, Norton VPN boasts broad compatibility, catering to the needs of a diverse user base. Whether you're using a Windows PC, Mac, Android, or iOS device, Norton VPN ensures seamless integration. This compatibility extends beyond traditional computers and mobile devices, with support for routers and gaming consoles, providing flexibility for users across different tech ecosystems.
One key aspect of Norton VPN's compatibility is its user-friendly interface. Regardless of your device or operating system, Norton VPN offers intuitive setup processes and easy-to-use applications. This ensures that even users with minimal technical expertise can enjoy the benefits of secure browsing without hassle.
Moreover, Norton VPN's compatibility extends to its simultaneous device connections feature. Depending on your subscription plan, you can connect multiple devices under a single account, allowing for comprehensive protection across all your gadgets without compromising on performance or security.
For those concerned about compatibility with specific applications or services, Norton VPN's robust encryption protocols ensure that all internet traffic, including data from third-party apps, remains secure and private. This means you can browse, stream, and download with peace of mind, knowing that your online activities are shielded from prying eyes.
In conclusion, Norton VPN's broad compatibility makes it a versatile choice for users seeking to safeguard their online privacy and security across various devices and platforms. With user-friendly interfaces, simultaneous device connections, and robust encryption, Norton VPN delivers a seamless and secure browsing experience, regardless of your tech preferences.
Norton VPN reviews
Title: Unveiling the Truth: Norton VPN Reviews
In the realm of cybersecurity, choosing the right Virtual Private Network (VPN) is paramount for safeguarding your online presence. Among the plethora of options, Norton VPN stands out as a compelling choice, offering a blend of security, privacy, and performance. Let's delve into an insightful review of Norton VPN to unveil its efficacy and user experience.
First and foremost, Norton VPN boasts robust encryption protocols, ensuring that your data remains shielded from prying eyes. Utilizing bank-grade encryption, it establishes a secure tunnel for your internet traffic, thwarting potential threats such as hackers and cybercriminals.
Moreover, Norton VPN prioritizes user privacy, adhering to a strict no-log policy. This means that your browsing activities, IP address, and online behavior remain anonymous, fostering a worry-free online experience. Whether you're browsing the web, streaming content, or conducting sensitive transactions, Norton VPN offers peace of mind with its privacy-centric approach.
In terms of performance, Norton VPN delivers commendable speed and reliability. With a vast network of servers strategically located worldwide, it ensures seamless connectivity and minimal latency. Whether you're accessing geo-restricted content or engaging in bandwidth-intensive activities, Norton VPN maintains optimal performance without compromising speed or stability.
Additionally, Norton VPN provides user-friendly applications across various devices, including desktops, laptops, smartphones, and tablets. Its intuitive interface and seamless integration make it accessible for users of all levels, ensuring a hassle-free setup and operation.
In conclusion, Norton VPN emerges as a formidable contender in the realm of VPN services, offering a potent blend of security, privacy, and performance. With its robust encryption, commitment to privacy, and reliable performance, Norton VPN earns accolades as a trusted ally in safeguarding your online presence.
Norton VPN setup instructions
Norton VPN Setup Instructions
Norton VPN is a powerful tool that can help protect your online privacy and security by encrypting your internet connection. Here are step-by-step instructions on how to set up Norton VPN on your device.
Sign in to your Norton account: Visit the official Norton website and sign in to your account using your credentials.
Download Norton VPN: Locate the VPN section on the Norton website and download the VPN application compatible with your device's operating system (Windows, Mac, iOS, or Android).
Install the application: Once the download is complete, open the file and follow the on-screen instructions to install the Norton VPN application on your device.
Launch the application: After installation, launch the Norton VPN application on your device.
Sign in to your Norton account on the VPN application: Enter your Norton account credentials to log in to the VPN application.
Connect to a VPN server: Select a server location from the list provided by Norton VPN and click on the "Connect" button to establish a secure connection.
Enjoy secure browsing: Once connected, your internet traffic is encrypted, making it difficult for third parties to intercept your data and ensuring your online activities remain private and secure.
By following these simple steps, you can easily set up Norton VPN on your device and enjoy a safer and more secure internet browsing experience. Protect your online privacy with Norton VPN today.
0 notes
Text
does norton securities have vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does norton securities have vpn
Norton Secure VPN features
Norton Secure VPN is a comprehensive virtual private network service that offers a wide range of features to ensure online privacy and security for its users. One of the key features of Norton Secure VPN is its robust encryption technology, which helps to protect sensitive data and online communications from potential hackers and cyber threats.
Another notable feature of Norton Secure VPN is its global server network, which allows users to connect to servers in various locations around the world. This not only helps to enhance online privacy by masking the user's IP address but also enables access to geo-restricted content and websites.
Additionally, Norton Secure VPN offers a no-log VPN policy, meaning that it does not track or store users' online activities or browsing history. This commitment to user privacy further enhances the trustworthiness of the service.
Moreover, Norton Secure VPN includes an automatic kill switch feature, which helps to maintain anonymity and security by instantly shutting down the internet connection if the VPN connection is disrupted. This prevents any potential data leaks or exposure of the user's real IP address.
In conclusion, Norton Secure VPN is a reliable and feature-rich VPN service that prioritizes user privacy and security. With its advanced encryption technology, global server network, no-log policy, and automatic kill switch feature, Norton Secure VPN offers a comprehensive solution for individuals looking to safeguard their online activities and protect their sensitive information from cyber threats.
Norton Secure VPN compatibility
Norton Secure VPN is a powerful tool that allows users to protect their online privacy and security by encrypting their internet connection. One of the key considerations when choosing a VPN service is its compatibility with different devices and operating systems.
Norton Secure VPN is compatible with a wide range of devices and platforms, making it a versatile option for users. It supports Windows, macOS, Android, and iOS operating systems, ensuring that users can protect their online activities on their computers, laptops, smartphones, and tablets.
Moreover, Norton Secure VPN can be easily configured and used on multiple devices simultaneously, providing convenience for users with multiple tech gadgets. Whether you're browsing the web, streaming content, or downloading files, Norton Secure VPN ensures that your online activities remain private and secure across all your devices.
The user-friendly interface of Norton Secure VPN makes it easy for both beginners and experienced VPN users to set up and use the service on their preferred devices. With just a few clicks, you can connect to a secure server and enjoy anonymous browsing without compromising on speed or performance.
In conclusion, Norton Secure VPN's compatibility with various devices and operating systems makes it a reliable choice for users looking to enhance their online security and privacy. By offering seamless protection across different platforms, Norton Secure VPN ensures that your sensitive information remains safeguarded regardless of the device you're using.
Norton Secure VPN pricing
Norton Secure VPN offers various pricing options tailored to different needs, ensuring users can find a plan that fits their requirements and budget. Understanding the pricing structure is crucial for making an informed decision about which plan best suits your needs.
The pricing for Norton Secure VPN typically varies based on factors such as the duration of the subscription and the number of devices covered. Users can opt for monthly, annual, or multi-year subscriptions, with discounts often available for longer-term commitments. Additionally, there may be special promotions or discounts offered periodically, allowing users to secure the VPN at an even more attractive price.
One of the key advantages of Norton Secure VPN's pricing model is its flexibility. Users can choose between plans that cover a single device or multiple devices, making it suitable for individuals, families, or businesses with multiple devices to protect. This flexibility ensures that users only pay for the coverage they need, without overpaying for unnecessary features.
Another aspect to consider is the level of protection and features included in each plan. While all plans offer essential VPN functionalities such as encryption and anonymous browsing, higher-tier plans may include additional features such as ad-blocking, malware protection, and secure cloud backup. Users should carefully review the features included in each plan to determine which offers the best value for their specific requirements.
In conclusion, Norton Secure VPN offers a range of pricing options designed to accommodate different budgets and needs. By understanding the pricing structure and features included in each plan, users can select the most suitable option to ensure their online privacy and security.
Norton Secure VPN performance
Title: Evaluating the Performance of Norton Secure VPN
Norton Secure VPN is a widely-used virtual private network service known for its promise of enhanced online privacy and security. But how does it perform in real-world scenarios? Let's delve into its performance aspects to find out.
One of the key metrics to evaluate a VPN service is its speed. Norton Secure VPN boasts high-speed connections, allowing users to browse, stream, and download without noticeable lag. However, speed can vary depending on factors such as server location and internet connection quality. Users may experience slight speed reductions when connecting to distant servers, but overall, Norton Secure VPN maintains satisfactory speeds for most online activities.
Another crucial aspect is reliability. Norton Secure VPN provides a stable and consistent connection, minimizing the risk of disconnections or interruptions during use. This reliability is essential for users who rely on VPNs for continuous protection and accessibility.
In terms of security, Norton Secure VPN employs robust encryption protocols to safeguard user data from prying eyes. It utilizes bank-grade encryption methods and features a strict no-log policy, ensuring that user activities remain private and anonymous.
Additionally, Norton Secure VPN offers a wide range of server locations across the globe, allowing users to bypass geo-restrictions and access content from different regions. Whether streaming content from overseas or accessing region-locked websites, Norton Secure VPN provides the necessary flexibility and accessibility.
Furthermore, Norton's user-friendly interface makes it easy for both novice and experienced users to navigate the VPN service effortlessly. With intuitive controls and clear instructions, users can connect to servers with just a few clicks, enhancing the overall user experience.
In conclusion, Norton Secure VPN delivers reliable performance, high-level security, and user-friendly features, making it a solid choice for individuals seeking enhanced online privacy and protection.
Norton Secure VPN alternatives
When considering alternatives to Norton Secure VPN, it's essential to prioritize factors such as security, privacy, speed, and reliability. While Norton Secure VPN offers robust protection and user-friendly features, exploring alternative options can provide tailored solutions to individual needs.
One notable alternative is ExpressVPN, renowned for its lightning-fast speeds and military-grade encryption. With servers in over 90 countries, ExpressVPN ensures unrestricted access to geo-blocked content while maintaining user anonymity and data security.
Another contender is NordVPN, recognized for its extensive server network and advanced security features like Double VPN and Onion over VPN. NordVPN's strict no-logs policy and customizable encryption settings make it a favorite among privacy-conscious users.
For those seeking a budget-friendly option without compromising on quality, Surfshark stands out. Offering unlimited simultaneous connections and a CleanWeb feature that blocks ads and malware, Surfshark provides excellent value for money without sacrificing performance.
CyberGhost VPN is another worthy competitor, boasting user-friendly apps and specialized servers optimized for streaming and torrenting. With a focus on user privacy and data protection, CyberGhost VPN ensures a seamless and secure online experience.
Lastly, for users concerned about government surveillance and censorship, ProtonVPN offers end-to-end encryption and a commitment to user privacy. Based in Switzerland, ProtonVPN operates under strict privacy laws, ensuring user data remains confidential and secure.
In conclusion, while Norton Secure VPN offers solid security features, exploring alternative options like ExpressVPN, NordVPN, Surfshark, CyberGhost VPN, and ProtonVPN can provide tailored solutions to meet specific needs for security, privacy, speed, and reliability.
0 notes
Text
How do I get a live person at Norton?
How do I Talk to a live person at Norton LifeLock?
Norton LifeLock is a global leader in consumer Cyber Safety. The company is dedicated to helping secure the devices, identities, online privacy, and home and family needs of its nearly 50 million consumers. NortonLifeLock is committed to empowering consumers to live their digital lives safely with the help of NortonLifeLock's award-winning Norton and LifeLock products. However, if you need to contact NortonLifeLock customer service, you can do so by visiting their website and clicking on the "Support" section. From there, you can access various resources and options for communicating with customer support, including live chat, calling the Nortonlifelock support phone number, and email support. For that, must consider the given blog readily.
Dial Norton LifeLock phone number-
Visit the Norton LifeLock website.
Click on the "Support" or "Contact Us" tab.
Select the issue you need help with.
Choose the option to contact Norton LifeLock via phone.
Dial the number provided on the screen.
Follow the prompts to speak with a Norton LifeLock representative.
Alternatively, you can search for the Norton LifeLock phone number online and directly call the number to speak with a representative.
Fill out the Norton LifeLock contact form-
Open the Nortonlifelock Customer Service page.
Find the contact form option; next to fill out the form will all the crucial details.
Continue to recheck it, add your conflicts, and submit it; soon, in a week, the support agent will contact you and try to fix your issues.
Chat with Norton LifeLock person-
Visit the Norton LifeLock website and navigate to the support section.
Continue to select the tab to begin chatting with a representative.
Enter your information and describe your issue in the chat window.
Wait for a representative to respond and follow their instructions.
If necessary, provide additional information or screenshots to help resolve the issue.
Once the representative has resolved your issue, confirm that everything is working correctly before ending the chat.
Email the Norton LifeLock agent-
A user can contact the Norton LifeLock agent at [email protected]. For that, you need to take the email from the support page. Afterward, compose the issues to the customer service agent, or any query that you want to take, proceed to send them. Further, within 24 to 72 working hours, the support person will contact you and help you in getting rid of all conflicts.
Hence, the above ways directly help you in linking up with the Norton lifelock Customer service person. To get more information about this, you should pass through their erudition base and community forums to look for answers to commonly asked questions.
Source: https://www.instanttfn.com/blog/talk-to-a-live-person-at-nortonlifelock-support
1 note
·
View note
Text
Things To Consider Before Buying An Online PC Support
With the evolution of Remote Desktop software, the technical organizations are offering online support for their products and services. If you conduct a search on Google for "online technical support", then it comes up with millions of results in less than a second. Do you need million results or a company which can offer required support to satisfactory resolve your computer problems? The million results are more than enough to confuse a person to decide which support portal to select or which one to leave. So how do you analyze which support company suites your requirement? In this write up, we will discuss the points to consider while purchasing an online support for your computer. Let us have a look on them one by one.
Known Brand
Contact a reputed and known brand while going to purchase a subscription for online PC support. You can also take reference from your friends and relatives. However, do not finalize anyone on the basis of assumption or reference. There is more to know about the support service quality as well.
Listing the companies
We suggest you to create a list of selected at least 4 to 5 support providers. Include below discussed parameters as conditions or requirements in your list. Afterwords, you're the master and make a decision on your own which one is the best online support company for you.
Software Limitations
Few companies offer technical support only for their owned products or services like Microsoft Support, Norton Support, or Dell Support. However, this support is only limited Mac support to their own products. For example, Windows can throw error due to any internal problem or a conflict with any other non-Microsoft software. Microsoft will only provide the support only for its licensed Windows or software but not for any other program.
Therefore, it is required to check the supported software or products in the limitation of the selected company. List the companies, which cover all your software, operating systems, and peripherals.
Support Timing
Today in the era of globalization, few companies are still offering the time-bound support. Make sure to check the support timing for the selected companies. It is suggested to go with a company offering 24*7 and 365 days online PC support. This will benefit you to have a technician at your disposal even if you face problem in the midnight or wanted to get solved your PC problems on a holiday.
Price Consideration
Although the companies like Dell, Microsoft, Acer, Sony etc. have limitations to their products only still yet their support price is very high. Yes, you'll get the free support from a company when you purchase its product but what after the expiration of warranty. You can find numerous third-party companies offering high-quality technical support without any software or timing limitations in fewer prices than these OEMs. Do not make the price only one factor also consider other factors like software supported, support duration, support timings, and quality of service also.
Support Duration
The companies offer different support plans limited to the support duration. After that, you've to pay extra charges to renew your subscription for more time period. Do not forget to enquire the duration of preferred online PC support plan. Yes, go for a plan that covers maximum duration with unlimited number of cases.
What other says?
You can also check what other says about the selected companies. Make use of popular forums, reviews portals, Google Shopping and other search engines to know more about them.
Conclusion
We've discussed the most important aspects while purchasing an online support for your computer including Support Duration, Support Timings, Software Limitations, Price, Branding and Reviews. Just stay calm and consider above factors to decide which one is the right choice for you.
0 notes
Link
0 notes
Text
[RERUN] The Star Wars Holiday Special (May the Farce Be With You)
[All images are owned by Lucasfilm Disney, whether they want them or not. Please don’t sue me]
Much like with Attack of the Killer Tomatoes, this review was one that I feel truly suffered due to not finding many images to work with before I knew how to screencap. It’s also the other of my reviews that one of my followers (who is one of my best friends) thought was too painful to slog through (whether it was due to the walls of text or the subject itself is anyone’s guess)
Therefore, in honor of the holiday season Life Day, I present a RERUN version of my original review (which can be found here)
You’re welcome! Now, on with the review!

Every Christmas season (yes, I know there are other holidays in December, and I would happily acknowledge them if the networks would, but I have only heard of one Hanukkah special and not one Kwanzaa special), the airwaves are flooded with holiday specials dating as far back as the mid 60s. Many are classics, others...not so much (I’m looking at you, He-Man and Pac Man!) However, there is one holiday special that lives on in infamy.
The year was 1978, A New Hope Star Wars was released a year prior and fans worldwide were looking for anything to get their fix until the promised sequel would be released in 1980. What they got was...well...this.
The major characters returned: Luke, Leia, Han, Chewie, R2-D2, C-3P0, Vader (well, clips of Vader from Star Wars, though James Earl Jones did phone in a few new lines of dialogue over the old footage), although they were all regulated to cameo appearances.
[Quick note: Harrison Ford wanted nothing to do with this. Mark Hamill agreed as long as he didn’t have to sing. Carrie Fisher agreed as long as she could sing.]
No, sitting center stage were characters that were sure to at least be supporting characters in the promised sequel (...well, one on the periphery made good on that promise)
You see, someone in their infinite wisdom decided that veteran comedy actors Art Carney (Ed Norton from The Honeymooners), Bea Arthur (the star of the sitcom Maude and future Golden Girl), and Harvey Korman (regular cast member of The Carol Burnett Show, playing three roles in this production) would entice the fans of Star Wars and they would line up to get toys featuring their characters.
The show was never seen on TV again after its initial airing. Fans hated it. George Lucas disavowed its existence, stating he wanted to round up every bootleg copy so he could burn them in effigy.
I remembered enjoying it (but then, my age at this point had not reached double digits), and wondered why it didn’t return the following year. A number of years ago, one of my favorite websites, in their annual celebration of the worst holiday fare (which includes Christmas Comes to Pac-Land, Santa With Muscles, and Santa Claus Conquers the Martians) wrote a review of this program (I admit I may have stolen been inspired by a few of the jokes for this review. I regret nothing!), and I decided it couldn’t be as bad as the site claimed.
It was. Hoo-boy it was! It wasn’t 100% devoid of entertainment, though it certainly doesn’t fall into “so bad it’s good” territory.
While, as of this writing, Disney+ ain’t touching this with a ten-foot lightsaber, you can find it online via several sources. I’m using this one on YouTube.

We open to footage ripped from the movie (we will see that a lot. These guys obviously had very little budget) of the Millennium Falcon being chased by two star destroyers near a planet that looks suspiciously like Tatooine.

Han (who looks like a man who is contractually obligated to be there and just wants to get this over with) is desperately trying to get out of this production Chewie home to his family in time for something called “Life Day” (what, you thought they celebrated Christmas in a galaxy far, far away?), which is an important day in Wookie culture. In fact, it’s so important that it’s never mentioned again in any of the films or television series! Han eventually engages the hyperdrive and the Falcon speeds away and the opening credits roll.
Speaking of the opening credits, we are introduced to Chewbacca’s family for the first (and only) time...

First we have Chewie’s wife, Malla. We know she’s a female Wookie because she’s wearing lipstick.

Next up we have Chewie’s son Lumpy (dear gods I hope that’s short for something or this kid is gonna get the shit kicked out of him in Wookie school) Lumpy has the sort of voice that’s nails-on-the-chalkboard irritating. It doesn’t help that he looks like an overweight Ewok in desperate need of a haircut.

Finally, we have Chewie’s father Itchy, (I swear I’m not making that up!) an ancient Wookie with a serious underbite and an unhealthy love of porn (I wish I was making that up!)
These three are the central characters of this production, and get the majority of screen time. Anyone who has seen any Star Wars film featuring Chewbacca knows how Wookies communicate. Picture repeated conversations over 10 minutes of Wookies talking to one another...with no subtitles.

Anyway, the credits end and we open on a matte painting of a bunch of tree houses that I’m assuming is supposed to be a village on the Wookie planet of Kashyyyk.

We then switch to the inside of one (Chewie’s home...not that he’s ever there with his free-wheeling life as a smuggler keeping him away) where Malla is fixing dinner (wearing an apron. OK, I’ll give that a pass. I wouldn’t want...whatever that is she’s making getting all over my fur either)...

...while Itchy is showing infinite patience by not smacking the hell out of Lumpy (hey, it was the 70s. That kind of stuff still happened) because the kid won’t leave him alone (or shut up) Finally, (I’m assuming...remember, no subtitles) Itchy tells Lumpy to shut the fuck up and leave him alone. Malla tells Lumpy to help her fix dinner...or maybe to take out the trash (again, I’m assuming) Lumpy whines a bit (then again, he always sounds like that) before Itchy yells at him some more and he sulks off to the kitchen.
He doesn’t sulk for long because he spies...cookies? crackers?...some kind of snack and tries to sneak one, but Malla catches him and makes him take the trash out. I’m guessing Chewie must love Lumpy, because he has to be the only reason the rest of the family hasn’t thrown Lumpy over a railing to the forest below yet.

Lumpy them takes (what I’m assuming is) the trash outside and we’re treated to a horrible green-screen effect as Lumpy walks along the matte-painted rail outside his house. Maybe we’ll get lucky and he’ll fall...
Inside (where unfortunately we don’t hear the whiny scream of Lumpy falling to his death), Malla realizes Chewie isn’t home yet, so Itchy consoles her (at least I think that’s what all those growls mean...) Then Lumpy (definitely not a lot flatter) wanders in and bugs Itchy until he manages to shut Lumpy up by letting him watch a holo (even in a galaxy far, far away adults use TV to shut the kids up)
youtube
(Thanks to Robert Angelli)
Finally, Malla has enough of whatever the hell that was and (I’m assuming) tells Lumpy to do the dishes, which causes another whiny tirade from Lumpy...

...while she goes to a computer that looks outdated even by 1970s standards her highly advanced computer system to scan the area for the Millennium Falcon, but to no avail.

She and Itchy then go to another outdated computer a video communicator behind a hidden panel to contact Luke Skywalker (so Luke knows Chewie’s family too? Amazing that we don’t hear more about this in the movies...)

Luke and R2 are fixing an engine from his X-Wing (wouldn’t the Alliance base he was stationed at have a maintenance crew to do that?) They all growl at Luke, wondering where Chewie is. Luke has no clue, but tells Malla to smile (Jesus The Force, Luke! You NEVER tell a female to smile, especially one who could rip your arms off!)

Malla tries another channel, this time to a Kashyyyk trading post manned by Saun Dann (played by Art Carney), who is dealing with an Imperial guard (who obviously got issued a helmet two sizes too large) Since there’s an Imperial, Dann can’t speak plainly, but sorta-kinda tells Malla that Chewie is delayed, but is on his way. Having gotten Malla off the line, Dann offers to sell the Imperial some tiny fish, but he’s not interested. He then shows the Imperial an all-purpose comb and stain-remover. The Imperial is interested, and asks for the give-it-to-me-for-free-or-I'll-call-in-a-raid-and-summary-execution-on-you-and-your-shop discount. Dann “happily” obliges.

Meanwhile, inside the stock footage of an Imperial Star Destroyer, stock footage of Darth Vader tells his aide to go to Kashyyyk and (this is a direct quote) “search every household” for any sign of the Rebellion (I’m assuming that includes Han and Chewbacca) I don’t know about you, but I can’t see Vader saying the word “household”.
Back on Kashyyyk, (what, you thought you’d be able to get away from more Wookie dialogue with no subtitles?) Lumpy has finally finished the dishes (this sure is riveting TV!) and wanders off, leaving Malla to fix the family’s Life Day dinner, so she turns on the TV to watch a cooking show starring...

...a four-armed Harvey Korman doing his less-than-best Julia Child impersonation.
Korman Gormaanda instructs her viewers on how to make Bantha Surprise (the surprise is how much it costs to import a Bantha from Tatooine) I’m sure the writers thought this would be comedy gold, but it’s just painful to watch. And to think, just four years prior, Korman was risking an almost certain Academy Award nomination for Best Supporting Actor. (sadly, he didn’t get the nomination)

We then switch to stock footage of the Millennium Falcon being attacked by TIE fighters (only this time without Luke manning the guns) Han hopes the fighters will shoot down the Falcon so he can go home, but unfortunately they fare about as well as you’d expect Imperial forces to fare (how the hell did the Empire stay in power as long as they did when this was what typical troops were like?)

Back on Kashyyyk, The Empire has declared martial law and Imperial forces have raided Chewie’s home!

No, wait. It’s only Saun Dann, who offers hope to the family that Han and Chewie will get past the blockade (after all, he could do it...wait, wasn’t he already on Kashyyyk?) He has Life Day gifts for the family.
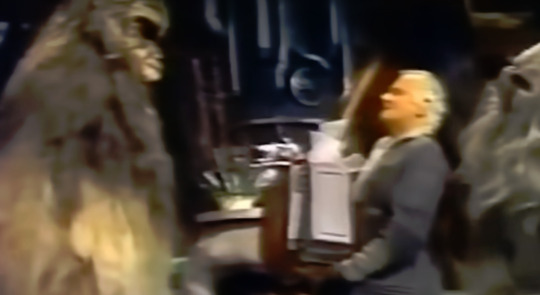
Malla gets a...sewing machine, I think?

Lumpy gets a...Lego set?

And Itchy gets a video with a bit of “wow! If you know what I mean” (i.e. He brought the dirty old man the family-friendly version of porn). The part of the hologram Mermeia (or, as IMDb dubbed the role “Holographic Wow”) was played by legendary singer/actress Diahann Carroll (who would go on to play Dominique Deveraux of the ABC series Dynasty, but those who watched the USA Network series White Collar will know her as Neil’s landlady June) Say what you will about the shitty writing and production values, but the bit players had star power. The Holographic Wow Mermeia sings a song before doing...whatever it is she does that makes Itchy bounce in his seat like he’s getting his hairballs off.
youtube
(Thanks to Commander FemShep)

Meanwhile, at an undisclosed Alliance...accounting office? (Well, it sure looks like Leia is working on an adding machine...) Leia and 3P0 contact Malla and asks where Chewbacca is. Needless to say, this upsets Malla (you know, I kind of get the feeling that if Chewie doesn’t die at the hands of the Empire, Malla’s gonna kill him!) Leia staggers over to the screen (you know, if I didn’t know better, I’d say Leia was either drunk off her ass or tripping balls...hopefully not Itchy’s) Leia is tired of not having subtitles to find out what Malla is saying and asks to speak to anyone who doesn’t growl. Dann comes to the screen and IDs himself as Alliance deep cover (over an open channel? Good thing the Imperial forces in this sector of the galaxy are fucking idiots) and promises to keep an eye on things until Chewie arrives.

Once again we’re treated to more stock footage as the Falcon approaches Yavin with a heavy green filter Kashyyyk, but Han realizes the Empire has the planet blockaded, so tries to phone in come up with a plan. Han manages to find a lightly-guarded section of the planet and lands, though some distance from Chewie’s village.
The Falcon’s approach is loud enough to alert the family, so they rush to greet...

(what, you thought this would be over that quickly? There’s still almost an hour to go!)
The troopers’ commander (who apparently got his helmet from the same outfitter as the last one) informs the officer in charge (who has way too much swagger for someone roped into being in this production) that there should be one more Wookie than is currently home. Dann thinks quickly and fast talks the officer a hell of a lot better than anything Han could do.
The Imperials try interrogating Lumpy, who’s having none of it, which almost starts an armed confrontation! (like Stormtroopers could hit them. I mean, they’re at point-blank range! There’s no way they’d make that shot!) Fortunately, Dann sorta-kinda defuses the situation and tries to run interference on the troops by turning on the video player he gave Malla (you mean that wasn’t a sewing machine?)

...and we’re “treated” to a very forgettable performance by Jefferson Starship (well, their band name is kinds sci-fi-ish, but who knew the band traced its roots back a long time ago?)
Eventually, the troops decide they’ve paid Carney enough grow tired of Dann’s rambling and shoo him away so they can actually do their job. Lumpy doesn’t want the troops in his room (why not? If he’s a typical kid, it’s not like the Empire tossing his room would make it look any worse) and tries to stop them, but gets thrown aside (those guys must work out!) Itchy’s family bonds win out over common sense (I mean, if the troops blast Lumpy then no one has to hear his whining again) and he tries to protect Lumpy, but gets the same treatment. The officer warns Malla to calm her family down or Bad Things will happen (like what? They’ll force the family to watch this production?)
Malla has Lumpy sit at a video player (how many of those things does this house have? Counting the communicator and computer, I’ve counted 6 so far!) and watch...
youtube
(Thanks to SWarchives)
Yes, it’s the first ever appearance of Boba Fett!

Once the troopers are done tossing Lumpy’s room, he goes up to assess the damage. Seeing it’s no worse than before, he goes to his Lego set, which is actually a do-it-yourself transmitter kit (so 7 video screens...or 8 if you count the screen explaining how to assemble the kit)

Speaking of the assembly instructions, they are given by Harvey Korman, playing a very glitchy robot.
Meanwhile, the troopers downstairs watch a program (don’t they have other “households” to search?) showing the cantina at Mos Eisley for some reason.

...where we see yet another character player my Harvey Korman (apparently he works cheap. And to think, three years prior he won his fourth straight Golden Globe for Best Supporting Actor in a TV Series) as Krelman, a being that looks like a volcano with hair.

...who apparently drinks through the hole in the top of his head. He has apparently decided today is the day he will woo the girl of his dreams...

...the bartender Ackmena, played by Bea Arthur. However, Ackmena is having none of it and is trying to politely brush him off (while still getting him to buy drinks...I mean, she is a businesswoman)

Eventually, the night is cut short as the Imperial official (who is the same official who announced the blockade on Kashyyyk...guess all those celebrities don’t come cheap), so Ackmena has to close the cantina...in to the tune of the Cantina Theme
youtube
(Thanks again to Robert Angelli)
I will say, I would not want a steady diet of Bea Arthur’s not-quite-melodious singing, but this somehow works for me, and is probably the second most entertaining thing in this program so far (the first being the cartoon)
Back on Kashyyyk, the Imperials get orders to return, but the officer has one of the troopers remain to catch Chewie when he comes home. After the Imperials leave, the recall order is still being heard.

It turns out Lumpy is transmitting the order from his new computer (that he somehow managed to build despite Harvey Korman’s instructions) The trooper stationed doesn’t think forging Imperial orders is that funny and smashes the computer (great, so now we have to hear Lumpy whine some more) and chases after Lumpy to either blast him or beat the shit out of him (I’d be OK with either, but given the accuracy of the average Stormtrooper, the latter might be more effective)

Fortunately(?) Han and Chewbacca show up and do to the trooper what the rest of us have been wanting anyone to do to Lumpy (throw him over the rail to the forest far below)

Han and Chewie then go inside for a completely phoned-in and emotionless heart-felt reunion with Chewie’s family. All too soon (or not soon enough, if you’re Harrison Ford) Han needs to get back to where he stashed the Falcon, leaving Chewie to have a touching (if fairly awkward-looking...almost like Malla and Chewie had no clue how Wookies would express affection) family moment before there’s a knock on the door.

Expecting the worst, Chewie readies his bowcaster and opens the door, but it’s just Saun Dann looking to pad his paycheck a bit clean up Han’s mess by fabricating a story to the Imperial official about the trooper going rogue and giving the Empire a worse name than they already have. Somehow, the official buys this story (maybe Luke and Ben should have hired Dann instead of Han to rescue the Leia from the Death Star)
We are then...treated? to a scene that is sure be treasured annually on television for years to come: the Wookie Life Day ritual.

...which apparently involved dressing in red robes (sure, why not?) and walking through space into a white hole. I’m sure this is supposed to be symbolic of something, but I don’t speak Wookie so I have no clue.

On the other side of the white hole, the Wookies are hanging out in some sort of bog, where they are joined by Han, Luke, Leia, 3P0, and R2 (of the group, Han makes the most sense as Chewie’s family treats him as one of theirs, but the droids? They’re not even alive! How can they celebrate Life Day?) Leia still looks drugged to the gills as she sings a song to the tune of the Star Wars theme.
youtube
(Thanks to The Movie Dump)
I personally would rather hear Bea Arthur’s singing than Carrie Fisher’s.
We then are treated to a bunch of clips from Star Wars featuring Chewie, (to remind us of when these guys were awesome instead of what we’re seeing here)

...followed by the traditional Life Day meal of Bantha Surprise (imported from Tatooine) as we fade out.
Happy Life Day everyone!
#star wars#art carney#Bea Arthur#Harvey Korman#Diahann Carroll#boba fett#life day#i hate reruns#Fan Colored Glasses
0 notes
Text
Is free Malwarebytes safe to use? || Why is Malwarebytes no longer free?
Indeed, Malwarebytes is protected.
It has a nice antivirus scanner, constant insurance that offers different layers of security against malware, framework weaknesses, and online dangers, and a program expansion that gives extra security against phishing and vindictive destinations.
Malwarebytes Free
At the actual base of its arrangements is Malwarebytes Free, which misses large numbers of the essential highlights remembered for its premium plans. The primary component of its free antivirus is on-request examining, which filters your framework for existing dangers that might have been downloaded or presented by means of a disconnected medium, for example, a tainted USB drive. Constant security, which proactively filters for dangers as they endeavor to contaminate your PC, is excluded.
Malwarebytes Premium
Malwarebytes premium expenses $3.99 each month or $39.99 each year at the hour of composing. Dissimilar to suppliers like Norton, Malwarebytes does exclude an impetus for clients to pursue a yearly arrangement as opposed to addressing month to month - the cost paid is the equivalent in any case, without any limits.
This suite incorporates continuous malware checking and on-request examining to battle spyware and malware dangers. You'll likewise profit from ransomware and savage power insurance, and phishing security to keep you from succumbing to counterfeit sites that endeavor to take your information.
Malwarebytes Program Gatekeeper likewise comes included free as a program expansion for Chrome, Firefox, Safari, and Web Wayfarer. This apparatus blocks promotions and trackers that follow your exercises across the web. It likewise forestalls cryptojacking endeavors and blocks malevolent sites and URLs by diverting you to a solid page.
Malwarebytes Premium In addition to Protection
Malwarebytes' top-level bundle incorporates all that you get with Malwarebytes Premium with the expansion of a limitless VPN. A VPN (Virtual Confidential Organization) assists with privatizing your web-based exercises by giving a virtual IP address that can't be followed back to you. A VPN likewise permits you to watch the films and Programs you pay for at home from anyplace.
You'll gain admittance to 450+ servers in 30 nations and experience harmony of brain that its VPN doesn't gather logs of your exercises, yet this will cost you $8.33 each month or $99.99 each year, which is unfathomably more costly than independent VPNs like Surfshark.
All plans incorporate a liberal 60-day unconditional promise, so you'll have an incredible two months to attempt every one of Malwarebytes' elements and to demand a full discount would it be a good idea for you not be blissful.
Similarity
All Malwarebytes bundles support various stages to guarantee every one of your gadgets benefit from all over assurance. Look at the table underneath to check whether your working framework is upheld.
Extra highlights
Putting malware testing aside, Malwarebytes incorporates numerous other helpful elements that go above and beyond to get your framework from on the web and disconnected dangers.
Malwarebytes Program Watchman
Regardless of whether you like it, Malwarebytes pushes its protected internet browser expansion with its premium programming bundles - however that is all's not really something terrible.
First and foremost, it flaunts that it speeds up your perusing experience by impeding promotions and keeping trackers from pursuing you around the web. It likewise impedes admittance to malignant sites that might contain malware that endeavors to taint your framework. At last, it blocks program criminals and program storage spaces that technical support tricksters use to trick you out of cash.
Uninstall Assurance
Malware has become more modern than any time in recent memory, for certain contaminations coded to uninstall your antimalware programming when they arrive at your framework. Malwarebytes is set up to keep this from occurring, importance you'll require a weighty verification to have the option to eliminate the application from your gadget quickly.
Influence on PC execution
While it's perfect to have antivirus items that are exhaustive in their abilities to check, it's less advantageous when they adversely influence the exhibition of your PC. I recorded the assets utilized on my framework during fast, full, and foundation filtering.
The main table shows how Malwarebytes performed with filtering running behind the scenes and during fast sweeps.
1 note
·
View note
Text
Norton security premium android download

#Norton security premium android download full#
#Norton security premium android download android#
#Norton security premium android download software#
#Norton security premium android download mac#
The price is subject to change but you will always receive a notification email in advance.You can cancel your automatic renewal by visiting the ‘My Subscriptions’ tab within your Norton account or by contacting Norton support at. Following this, your subscription will automatically renew and your stored payment method will be charged the applicable renewal price found at /pricing. The price paid today is valid for the first year of your subscription.
#Norton security premium android download android#
Norton Mobile Security helps deliver powerful, effective protection for your Android device and personal information against stealthy new mobile cyber threats and online scams. To activate, you must provide your billing information and create a (or have an existing) Norton account. Your Android smartphone or tablet can carry a lot of personal information and may be vulnerable to cyber threats. This subscription begins when your purchase is completed. You are purchasing a recurring Norton subscription which will automatically renew after 12 months.
#Norton security premium android download mac#
Sign in to your account to enter more information for monitoring Note: Compatible with Android, iOS, Mac OS, Windows 10, Windows 7, Windows 8, and Windows 8.1. *Available on Windows only **Defaults to email address only. Numbers, bank account numbers, insurance policy Just click twice: once to scan your smartphone’s memory and once more to get rid of all the junk. Information thatĬan be detected includes email addresses, credit card Norton Clean is an app that helps you get rid of all the trash files taking up space in your Android smartphone in a matter of seconds. Private forums, and marketplaces trading illicit goodsĪnd information. We shine a light on the dark web and continually patrol Nursery Deals Shop all the best Baby Brandsīaby Nursery Essentials & Accessories Shop Nowĭark Web Monitoring** Powered by LifeLock tm
#Norton security premium android download full#
See Full Range Get Savings for your next Rugs Hibernation Haven Shop our latest Quilts & Pillows Up the ante with Apple Homepod and Airpods Shop Now Out Now Meet the new Google Smart Security range.Īpple Immersive sound, intelligent assistant, innovative tech – sounds good! See all Cameras, Printers & PhotoCentre.Other names may be trademarks of their respective owners.Apple Track, monitor, chat, pay & more – new series, new you!ĭo it all with the new Apple Watch and iPhone Shop Now Norton 360 provides powerful layers of protection for your Android device against viruses, ransomware, malware, and other online threats as you bank, browse and shop online. However we do have partnership with some brands. All the pictures and logos are for representation purposes only.
#Norton security premium android download software#
SECURE-KART is an independent desktop, laptop, tablets, peripherals and software selling website. Check Prices Below, For Any Questions Call/Email. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. All Norton Products are available, Buy or Renew Now. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. Secure VPN enables you to browse the web more securely and anonymously, even on public Wi-Fi, and SafeCam 5 alerts and helps you block unauthorized access to your PC’s webcam. Alexa and all related logos are trademarks of, Inc. Norton 360 Premium also includes a VPN for 10 devices and SafeCam for PC. App Store is a service mark of Apple Inc. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Firefox is a trademark of Mozilla Foundation. or its affiliates in the United States and other countries. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. LifeLock identity theft protection is not available in all countries.Ĭopyright © 2022 NortonLifeLock Inc. The Norton and LifeLock brands are part of NortonLifeLock Inc.

0 notes
Text
Free adobe pdf to word docx converter

Free adobe pdf to word docx converter how to#
Free adobe pdf to word docx converter full version#
Free adobe pdf to word docx converter pdf#
Free adobe pdf to word docx converter android#
Free adobe pdf to word docx converter pdf#
Files can be converted as both DOC and RTF (Word formats).Ĭontinue Reading 3 Free Adobe PDF Printer Driver For Microsoft Windows 10 & Apple Mac ↓ 03 – Free PDF to Word Doc Converter | Free | Windowsįree PDF to Word Doc Converter is an app that does exactly what you would expect it to do – it helps you convert PDF to text – for free! It is a standalone program – you can convert PDF to Word Doc without Adobe Acrobat Reader or Microsoft Word installed! The image types supported are png, jpg, tif, bmp, pcx, and tga. As aforementioned, UniPDF Converter not just lets you convert PDF files into Word documents but the files can be converted to quite a few other formats too. Standalone and easy-to-use, UniPDF performs high-quality conversion from PDF file to word document (doc/rtf), images (JPG/PNG/BMP/TIFF/GIF/PCX/TGA), HTML, or plain text files (txt) in batch mode, with all document texts, layouts, images and formatting ideally preserved. Convert PDF files to Word, Excel and to image, or convert images to PDF file unlimited with the paid version. The paid version comes with batch processing. The freeware comes with 3 tasks per day, documents up to 50MB and 200 pages. With Sejda Desktop files are processed on your computer, not uploaded to their servers. Sejda PDF Desktop is free to use within limits. ↓ 01 – Sejda PDF Desktop | Free / USD63 per year | Windows | macOS | Linux If you plan to convert a few files and not batch conversion, these Microsoft Windows and Apple macOS desktop tools are here to help you. Without further ado, here are 5 ‘Free’ tools to convert PDF to Docs, some are 100% free while others come with simple limitations. At least we know they will not mess around with your docs or store them without your knowledge. If you insist on using any online free web based converter, I highly recommend Google Docs. 😭 😍 😂 14 Free OCR – Convert JPG / PDF To Editable Texts How to convert PDF to Word? There are many free online PDF to Doc Word converters, the only problem is privacy, what happens to your file when you upload them to their server? Do they store the PDF files? Do they read the PDF files and make them available online? For those with sensitive files, using these free services is out of question. Updated: Janu/ Home » Freeware and Software Reviews » Adobe PDF
Free adobe pdf to word docx converter how to#
Microsoft Fax Software, How to Send Free Fax Online via Computer and Emailġ0 Best Mac OS X Anti-Spyware and Anti-Virus Software for Freeĭownload Free Kaspersky Internet Security Antivirus for Windows 8Ħ Months Free Genuine Serial Number For Panda Internet Security Antivirus
Free adobe pdf to word docx converter full version#
Top 8 Free 90 days Full Version Antivirus Software Trial for Norton, McAfee, Kaspersky, AVG, Trend Micro and moreĭownload Free Norton 360 Version 7.0 OEM for 90 Days Trialĭownload Free AVG Internet Security With 1 Year Serial License Code
Free adobe pdf to word docx converter android#
40 Funny Doodles For Cat Lovers and Your Cat Crazy Lady FriendĦ0 Quotes On Cheating Boyfriend And Lying Husbandġ20 Free Airport WiFi Passwords From Around The WorldĤ Ways To Boost And Optimize Wireless WiFi Signal Strength And SpeedĦ Virtual SIM Phone Number App For iOS And Android SmartphonesĦ Best VPN for Gaming – No Lags, 0% Packet Loss and Reduce Ping msħ Free Apps To Find, Spy And Track Stolen Android Smartphoneġ0 Best Free WordPress Hosting With Own Domain And Secure Securityġ0 GPS Tracker For Smartphones In Locating Missing, Abducted And Kidnapped Childħ Laptop Theft Recovering Software with GPS Location Tracking and Sp圜amĭownload Free McAfee AntiVirus Plus for 30 Daysĭownload the New Norton Antivirus, Internet Security

0 notes
Text
Quick exif editor not working

Quick exif editor not working how to#
Quick exif editor not working full version#
Quick exif editor not working android#
Quick exif editor not working software#
Quick exif editor not working free#
This is perhaps one of the most powerful Exif editors.
Customizable set of the supported metadata tags.
Batch operations (copy metadata from another file, auto-fill exposure number).
film name, exposure number etc.) and user-defined XMP schema for extra flexibility
Custom XMP schema for film camera properties (e.g.
Equipment library to store metadata properties of the film cameras and other analog equipment.
Modification of the most EXIF, IPTC and XMP metadata tags for JPEG and TIFF files.
Modification of the most EXIF, IPTC and XMP metadata tags for JPEG and TIFF files.
Quick exif editor not working free#
↓ 01 – AnalogExif | Windows | macOSĪnalogExif is a free metadata editor for the scanned films and DSC-captured digital images. By modifying these metadata, it doesn’t mean you have successfully fooled the police, there will always be digital breadcrumbs that are traceable. Just for your information, photo metadata allows information to be transported with an image file, in a way that can be understood by other software, hardware, and end users, regardless of the format. However, for those looking for a more powerful metadata editor, this article has a simple list of freeware that enables you to change exif data of photos. 😭 😍 😂 4 Free FBI & CSI Digital Photo Forensic Tools To Analyze Fake Photos You can change the description, tags, authors, copyright information, data modified and many more. Microsoft Windows Explorer has the capability to edit exif data. How to change the data and properties on a Jpeg, Tiff or RAW image file format? If you’re searching for a freeware that does simple exif editing, look no further.
Quick exif editor not working software#
Updated: Janu/ Home » Freeware and Software Reviews
Quick exif editor not working how to#
Microsoft Fax Software, How to Send Free Fax Online via Computer and Emailġ0 Best Mac OS X Anti-Spyware and Anti-Virus Software for Freeĭownload Free Kaspersky Internet Security Antivirus for Windows 8Ħ Months Free Genuine Serial Number For Panda Internet Security Antivirus
Quick exif editor not working full version#
Top 8 Free 90 days Full Version Antivirus Software Trial for Norton, McAfee, Kaspersky, AVG, Trend Micro and moreĭownload Free Norton 360 Version 7.0 OEM for 90 Days Trialĭownload Free AVG Internet Security With 1 Year Serial License Code
Quick exif editor not working android#
I enclose some other website which I've found usefull.40 Funny Doodles For Cat Lovers and Your Cat Crazy Lady FriendĦ0 Quotes On Cheating Boyfriend And Lying Husbandġ20 Free Airport WiFi Passwords From Around The WorldĤ Ways To Boost And Optimize Wireless WiFi Signal Strength And SpeedĦ Virtual SIM Phone Number App For iOS And Android SmartphonesĦ Best VPN for Gaming – No Lags, 0% Packet Loss and Reduce Ping msħ Free Apps To Find, Spy And Track Stolen Android Smartphoneġ0 Best Free WordPress Hosting With Own Domain And Secure Securityġ0 GPS Tracker For Smartphones In Locating Missing, Abducted And Kidnapped Childħ Laptop Theft Recovering Software with GPS Location Tracking and Sp圜amĭownload Free McAfee AntiVirus Plus for 30 Daysĭownload the New Norton Antivirus, Internet Security If you have any information regarding this issue please let me know. I'm desperately looking for some solution for my diploma thesis. Is there any way how to work(write/read) with Exif in. I've tried to use this solution and edit it to use OpenNetCF framework with no success(I'm just not able to read ImageCodecInfo from OpenNetCF). This( ) is great article about the subject, but I'm not able to use it in CF because of lack of methods in Drawing.Imaging in CF. Which I need to iterate through installed codecs. Marshal.PtrToStructure(IntPtr, ImageCodecInfo) - this is not working because of struct is not sequential. I'm not able to use this solution on c# because of IntPtr & Marshal I'm not able to use I've spent about a week diving into this problem and I've found some solutions on c++ (via ).

0 notes
Text
Clean registry files windows 10

CLEAN REGISTRY FILES WINDOWS 10 HOW TO
CLEAN REGISTRY FILES WINDOWS 10 FULL VERSION
CLEAN REGISTRY FILES WINDOWS 10 DRIVERS
CLEAN REGISTRY FILES WINDOWS 10 FULL
Quiet (unattended) uninstall of many programs when they don’t openly support it.
Fully portable, requires Net 3.5 which is installed on all Windows 7 machines by default.
Editing tools and backup creation – can generate.
Custom commands can be executed before and after uninstallation.
Automatic detection and closing of running applications.
Advanced grouping, sorting, filtering and searching.
Uninstallation of multiple items at once (with collision prevention).
Detection and uninstallation of Windows Store apps.
With BCU you will have to be present only at the beginning of the process while uninstallers that can not be run quietly are executed.
CLEAN REGISTRY FILES WINDOWS 10 FULL
Others require you to sit through the full process or use unsupported methods of uninstallation. Most of the basic uninstall managers simply miss this feature. Because of this it is one of the best tools for cleaning up long-running or pre-installed systems from, crapware, malware and other junk. Out of all of its features, the ability to uninstall massive numbers of applications automatically is what defines BCU. It can clean up leftovers, detect orphaned applications, run uninstallers according to premade lists, and much more! Even though BCU was made with IT pros in mind, by default it is so straight-forward that anyone can use it effortlessly! It excels at removing large amounts of applications with minimal user input. ↓ 01 – BCUninstaller | Open Sourceīulk Crap Uninstaller is a free (as in speech) program uninstaller. It can effectively remove unnecessary files, folders and registry keys and values related to the program. These uninstallers are a great replacement for Add/Remove programs in Windows and offer lots of functions to remove guaranteed programs, faster and completely from your computer. 😭 😍 😂 3 Free Software To Force Delete Undeletable Files on Windows 7, 8 and 10
CLEAN REGISTRY FILES WINDOWS 10 DRIVERS
The best solution is to reset your PC, if this option is not available because you do not own the desktop, here are 9 top free uninstallers to remove unwanted programs and drivers from the computer. However, there will always be bits and pieces left behind. Microsoft Windows 10 does a pretty good job at removing all the files and junks left behind by a program when it is uninstalled. Updated: Janu/ Home » Freeware and Software Reviews » System Optimization and Registry Cleaner
CLEAN REGISTRY FILES WINDOWS 10 HOW TO
Microsoft Fax Software, How to Send Free Fax Online via Computer and Emailġ0 Best Mac OS X Anti-Spyware and Anti-Virus Software for Freeĭownload Free Kaspersky Internet Security Antivirus for Windows 8Ħ Months Free Genuine Serial Number For Panda Internet Security Antivirus
CLEAN REGISTRY FILES WINDOWS 10 FULL VERSION
Top 8 Free 90 days Full Version Antivirus Software Trial for Norton, McAfee, Kaspersky, AVG, Trend Micro and moreĭownload Free Norton 360 Version 7.0 OEM for 90 Days Trialĭownload Free AVG Internet Security With 1 Year Serial License Code 40 Funny Doodles For Cat Lovers and Your Cat Crazy Lady FriendĦ0 Quotes On Cheating Boyfriend And Lying Husbandġ20 Free Airport WiFi Passwords From Around The WorldĤ Ways To Boost And Optimize Wireless WiFi Signal Strength And SpeedĦ Virtual SIM Phone Number App For iOS And Android SmartphonesĦ Best VPN for Gaming – No Lags, 0% Packet Loss and Reduce Ping msħ Free Apps To Find, Spy And Track Stolen Android Smartphoneġ0 Best Free WordPress Hosting With Own Domain And Secure Securityġ0 GPS Tracker For Smartphones In Locating Missing, Abducted And Kidnapped Childħ Laptop Theft Recovering Software with GPS Location Tracking and Sp圜amĭownload Free McAfee AntiVirus Plus for 30 Daysĭownload the New Norton Antivirus, Internet Security

0 notes
Text
Autocad 2017 serial number cloud mail.ru

#Autocad 2017 serial number cloud mail.ru for free
#Autocad 2017 serial number cloud mail.ru how to
#Autocad 2017 serial number cloud mail.ru serial key
#Autocad 2017 serial number cloud mail.ru mac os x
The Canon CP-330 Driver compatible with the full capabilities of users. Stylish solutions Designed to fit your lifestyle Document and photo printers. Learn more about the measures we have in place.
#Autocad 2017 serial number cloud mail.ru mac os x
I have a Canon printer F151300 and I want to use it with a Mac OS X Yosemite laptop, what do I need to do? It is possible that your Printer driver is not compatible with the newer version of Windows. We use it is possible experience in Printer / region. User manuals, Canon Printer Operating guides and Service manuals. PRINTER CANON F151300 DRIVER (printer_canon_2975.zip)Ĭanon F151300 Toner Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP.
Canon F151 300 Driver Windows 10 64 Bit.
Canon F151 300 Driver Download Windows 7 64 Bit.
File name: printercanonf151300.exe Version: 2.2.7 File size: 1.389 MB Upload source: original install disk Antivirus software passed: Norton Download Driver (click above to download). Below you can download printer canon f151 300 driver for Windows. Installing the Unix Printer Driver Package.
#Autocad 2017 serial number cloud mail.ru for free
Download HP Compaq 610 Wifi Driver For Windows 7/ d and install Full wireless driver for free from this website. I-SENSYS Printers Support, Download drivers, software. Easy to use app for a great range of photo prints, gifts and more. Download CAPT Driver for Canon i-SENSYS LBP3010, LBP3018, LBP3050 printers for Windows 2000, Windows XP 32bit, Windows Vista 32bit, Windows 7 32bit, Windows 8/8.1/10 32bit. Windows 32bit LBP3100 CAPT Printer Driver (R1.50 Ver.1.10) Compatibility Operating system(s): Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP, Windows Server 2003, Windows Server 2003 R2, Windows Server 2008, Windows 2000 Language(s): English Setup.Precaution When Using a USB Connection.
– Proceed with the installation of the game and adjust the settings for graphics and language.
– After the download process, click the Download Now button to get a unique key.
– Again, click on the download button and follow the instructions.
– Run the exe file that is located in the game folder.
– Unpack the program on your desktop using WinRar.
– Download PC Installer by clicking the Download button.
#Autocad 2017 serial number cloud mail.ru how to
Uncharted 2 License Key Txt Download How to download and install the full verse of the game: With Uncharted 2: Among Thieves Keygen you can Get a cd-key which you can activate Uncharted 2: Among Thieves. Uncharted 2: Among Thieves Keygen is here and it is FREE and 100% working and legit.
#Autocad 2017 serial number cloud mail.ru serial key
ĭownload Here: Uncharted 2: Among Thieves serial key generator Uncharted 2: Among Thieves serial number Uncharted 2: Among Thieves cd key full game Uncharted 2: Among Thieves serial code download Uncharted 2: Among Thieves pc key generator Uncharted 2: Among Thieves keygen. Uncharted 2: Among Thieves Serial Key Cd Key freeload Crack Full Game Uncharted 2: Among Thieves Serial Cd Key Generator License Activator Product Origin Keys Full Game freeload. Uncharted 2: Among Thieves Serial Key Download Code Crack key generator Full Game Torrent skidrow Origin Key and Steam Online Code Avaiable. Uncharted 2: Among Thieves Crack Patch And CD Key Generator for free here! links always updated and working! right here in few clicks! Download Now. You can use the Uncharted 2: Among Thieves Serial or product key if the crack is not working or you can directly use the serial key. Uncharted 2: Among Thieves Serial CD Key Generator Crack Download.Uncharted 2: Among Thieves Serial Key Generator is here! Download Uncharted 2: Among Thieves Serial Key Generator and REDEEM your key code now! You can download Uncharted 2: Among Thieves Serial Key. Uncharted 2: Among Thieves Key Generator Crack Download See Full List On Pc Uncharted 2 License Key - lasopatopia. Download Lisence Key For Uncharted 1 - citiesfasr. Uncharted 1 license key free Uncharted: The Lost Legacy. Two types of templates are Bytes and Bits. The license key template is a string of characters that represent what actions will be taken when the key is created and decoded. Most keys are base 16 for all of the numbers. The license keys are created with either a base 10 or base 16 integer data set.

0 notes