#NetworkArchitecture
Explore tagged Tumblr posts
Text
youtube
Session 9: Understanding PUCCH and PUSCH in 5G | Open RAN Explained
Video link - https://youtu.be/ExK6M8mm8TU
Welcome to Session 9 of our Open RAN series! In this session, we'll delve into the intricacies of the Physical Uplink Control Channel (PUCCH) and the Physical Uplink Shared Channel (PUSCH) in 5G networks.
Subscribe to "Learn And Grow Community" Follow #learnandgrowcommunity
#OpenRAN#5G#PUCCH#PUSCH#UplinkControl#WirelessCommunication#Telecommunications#wirelesscommunication#telecommunications#RANIntelligentController#RIC#CU#centralizedunit#DU#Distributionunit#Orchestration#NetworkOrchistrator#oran#beginnersguide#5g#4g#5gnr#5grevolution#3gpp#telecominsights#telecominfraproject#networkarchitecture#protocolos#rrc#protocollayers
3 notes
·
View notes
Text

Understand the physical layer of SD-Access architecture. Our guide covers essential configurations and best practices for building a robust and scalable network infrastructure. https://www.dclessons.com/sd-access-architecture-physical-layer
0 notes
Text
#MobileIP#MobilityManagement#NetworkMobility#MobileNode#HomeAgent#ForeignAgent#CareOfAddress#IPMobility#IPv6#IPv4#NetworkEntities#Routing#PacketForwarding#SeamlessMobility#MobileNodeRegistration#AgentAdvertisement#LocationUpdate#SessionPersistence#MobileData#Connectivity#Roaming#UserMobility#DynamicIP#MobileNetworking#InternetProtocol#NetworkArchitecture#RoutingProtocols#DataTransfer#Handoff#MobileCommunications
0 notes
Text
Unlock the power of MLAG and Stacking in modern networking architectures! Discover how these technologies enhance redundancy, scalability, and performance in today's complex network environments.
0 notes
Text
Secure Access Service Edge (SASE) Market Strategic Analysis: Enabling Secure Transformation
The global secure access service edge market size is expected to reach USD 11.29 billion by 2028, registering a CAGR of 36.4% from 2021 to 2028, according to a new study conducted by Grand View Research, Inc. The existing networking technologies are complex and difficult to manage but easy for cybercriminals to intrude. The growing preference for remote working practices, increase in traffic across public clouds, and the rising dependence on data centers are further adding to the data security risks. At this juncture, the growing demand for ensuring secure access to data and networks is driving the need for advanced network approaches and technologies. The subsequent need for a unified and simplified approach to strengthen network security has resulted in the emergence of SASE.
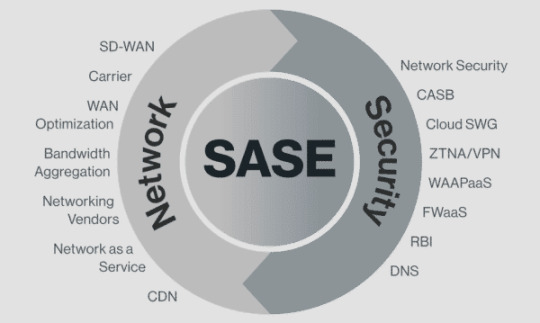
Secure Access Service Edge Market Report Highlights
The platform segment accounted for over 70% of the overall revenue share in 2020 as the growing preference for remote working continued to drive the demand for a unified security solution that can offer the capabilities of several network security services
The demand for SASE was higher among IT & telecom enterprises in 2020 as the need to filter contents across edges and ensure efficient security framework management continued to drive the adoption of SASE among IT & telecom organizations
North America dominated the global market in 2020 and is expected to remain dominant over the forecast period
Aggressive IT spending, effective implementation of security standards, and the continued rollout of the digital workforce by organizations across the U.S. and Canada are some of the factors that are expected to drive the regional market
For More Details or Sample Copy please visit link @: Secure Access Service Edge Market Report
SASE architecture comprises the capabilities of network security services, such as Zero Trust, FWaaS, and CASB, and software-defined WAN capabilities, combined in a unified platform to help organizations in ensuring easy and secure access to data and networks. SASE architecture simplifies the IT infrastructure and frees organizations from the burden of managing and periodically updating multiple security systems. SASE architecture also allows organizations to save on the costs incurred on procuring multiple security solutions and helps them in the quick implementation of data protection policies. All such benefits are driving the popularity of SASE frameworks among enterprises.
The COVID-19 pandemic and the subsequent restrictions on the movement of people imposed by various governments across the world have prompted organizations to switch to a remote working model. However, the remote working model has also triggered challenges related to managing the productivity of a flexible workforce and security governance. Organizations are also exposed to higher levels of cybersecurity risks than ever. As a result, organizations are looking forward to implementing robust security frameworks. The growing need to establish effective security frameworks while ensuring convenient access to information for employees using an integrated approach is expected to drive the adoption of SASE frameworks.
#SASE#NetworkSecurity#EdgeSecurity#Cybersecurity#CloudSecurity#SecureConnectivity#EnterpriseSecurity#CyberDefense#EdgeComputing#InfoSec#ITInfrastructure#NetworkArchitecture#SASESolutions#DataProtection#CyberThreats#SecureNetworking
0 notes
Photo

Nine Incredible Reasons Why Your Internet is Slow. Today, everyone looks for a high-speed internet connection. Read on to know more about the factors of why your internet is slow.
#ReasonsOfSlowInternet#InternetSpeed#InternetConnection#NetworkArchitecture#NetworkCongestion#InternetPlans
0 notes
Text

Metal Ceiling — Catering To The Needs Of Modern House Owners!
In contemporary home design, functionality and aesthetics go hand in hand. Modern house owners are always on the lookout for solutions that combine elegance, durability, and practicality. One such innovation that has been steadily gaining popularity is metal ceilings. Sleek, stylish, and versatile, these ceilings cater to the evolving needs of modern homeowners by offering a perfect blend of form and function. Here’s why metal ceilings have become a preferred choice for today’s homes. Read More: https://medium.com/@networkarchitectural/metal-ceiling-catering-to-the-needs-of-modern-house-owners-e07919b5e6e3
#recladding#architectural cladding#aluminium cladding#acoustic ceiling#suspended ceiling systems#alpolic cladding#bespoke ceilings#mesh ceilings#baffle ceiling#non-combustible cladding
2 notes
·
View notes
Link
0 notes
Text
VoLTE - 4G-LTE EPC Evolved Packet Core Network

This EPC course covers the 4G LTE Packet Core Network including MME, SGW, PGW, HSS, Call Flow, Roaming and Protocols etc

4G-LTE EPC Evolved Packet Core Network Created by : TELCOMA Global 52,000+ Students! Last updated : 12/2018 Language : English Caption (CC) : Included Torrent Contains : 42 Files, 1 Folders Course Source : https://www.udemy.com/4g-lte-epc-evolved-packet-core-network/ What you'll learn • LTE Background • Network Architecture • EUTRAN Architecture Overview • EPC MME • EPC HSS • EPC SGW • EPC PGW • EPC Architecture • EPC Protocol Stack • EPC Interfaces • EPC Bearers • LTE Call Flow • LTE Roaming Requirements • Basic knowledge of 4G LTE is required Description 4G LTE EPC (Evolved Packet Core) is a framework for providing converged voice and data on a 4G Long-Term Evolution (LTE) network. 2G and 3G network architectures process and switch voice and data through two separate sub-domains: circuit-switched (CS) for voice and packet-switched (PS) for data. EPC is a whole new core network with a flat, all-IP based architecture. The SAE defined by 3GPP has the Evolved Packet Core (EPC) as its main component and Mobility Management Entity (MME), Serving Gateway (SGW) and PDN Gateway (PGW) as the subcomponents. This LTE EPC Training covers • LTE Background • Network Architecture • EUTRAN Architecture Overview • EPC MME • EPC HSS • EPC SGW • EPC PGW • EPC Architecture • EPC Protocol Stack • EPC Interfaces • EPC Bearers • LTE Call Flow • LTE Roaming 4G-LTE EPC Certification is included in the course which will be the proof of the new skills you own. 30 DAYS MONEY-BACK GUARANTEE This Course comes with Lifetime access so you can enjoy the updates to this course without paying anything extra. You will also get a 30 Days Money Back Guarantee by Purchasing this course now. You are eligible for a full refund on this training within 30 days from purchase. Read the full article
0 notes
Video
youtube
SD-WAN – To Simplify Network Management and Improve the Delivery Service
1 note
·
View note
Link
Stateful Firewalls: Stateful Inspection and NAT #firewall #firewalls #securityengineer #networksecurity #networkarchitecture #networkengineer #ccna #ccnp #ccie #cisco #juniper #paloaltonetworks #checkpoint #fortinet #barracuda #networking #networksbaseline
0 notes
Text
youtube
Session 26 : 5G SA & 5G-NSA Architecture and Deployment strategy and open RAN
Video Link - https://youtu.be/WJx_klJDuEg
Subscribe to "Learn And Grow Community" Follow #LearnAndGrowCommunity
#5g#5gnr#5grevolution#openran#telecominnovation#networkarchitecture#5GDeployment#networkperformance#lowlatency#highthroughput#NetworkScalability#TelecomTechnology#FutureOfTelecom#AdvancedConnectivity#TelecomEvolution#ric#radioaccessnetwork#radionetwork#3gpp#oran#Youtube
1 note
·
View note
Text
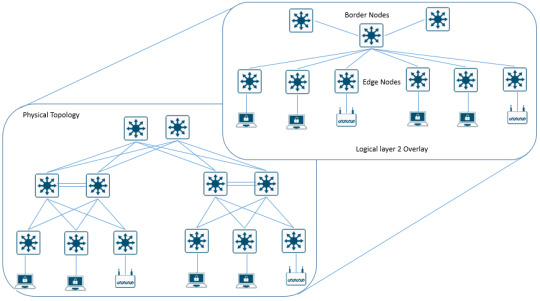
Explore the architecture of Software-Defined Access. Our guide provides insights into designing and implementing automated, secure, and scalable network solutions. https://www.dclessons.com/software-defined-access-architecture
#SDAccess#SoftwareDefinedAccess#SDN#CiscoSDAccess#NetworkAutomation#NetworkArchitecture#DataCenterNetworking#CiscoNetworking
0 notes
Text
Industry's first 100G IPoDWDM Disaggregated Networks solution from IPInfusion
Thinking of Edge? IP Infusion got you covered.
Industry's first 100G #IPoDWDM solution on disaggregated Networking platform power by OcNOS™. Extend your Data Center Interconnect (DCI) upto 80km with Colorz® DWDM PAM4 Optical transceiver from Inphi Corporation .
Multiplex upto 40 100GbE channels over single fiber for 4 Tb/s transfer rate. Read our press release at https://www.ipinfusion.com/news-events/

#technology#datacenters#telecom#tech news#techcrunch#tech#latest tech#opennetworking#opennetworks#open networks#open source#cloudcomputing hybridcloud cloud networkarchitecture networks datacenter datacenternetworking bladeserver privatecloud publiccloud#software defined networks#networks#sdn#nfv#telecommunications
0 notes
Text
Network Security

It Is Very Important To Have Security To Your Computer Network. Network Security Is Nothing But Giving Security For The Network To Avoid Unauthorised Access.
Absolute Security (Total Security)
If You Unplug Your Computer From The Network Or If You Switch Off The Power Supply Or If You Lock You're And Put's Your Computer In Safe Mode, Your Computer Is Secured.
Absolute Access (Total Access)
A Computer With Absolute Access Is Extremely Convenient To Use: It's Simply There And Will Do Whatever We Tell To The Computer, Without Questions, Without Authorization, Passwords, Or Any Other Mechanism. This Is Not Much Practical Either: The Internet Is A Bad Neighbourhood Now If Some Unknown Person Tells Your Computer To Destroy Itself, It Will Do. So Every Organisation Needs To Decide For Itself Where Between The Two Extremes Of Total Security And Total Access They Need To Be. A Policy Need To Articulate This, And Then Define How That Will Be Enforced With Practices And Such. Everything That Is Done For Security, Then, Must Enforce That Policy Uniformly. Read the full article
#network#network18#networkanalysis#networkarchitecture#networkbooster#networkengineer#networkmarketing#networksecurity#NetworkSecurityandcryptography#NetworkSecuritycourses#NetworkSecuritydefinition#NetworkSecurityinterviewquestions#NetworkSecuritykey#NetworkSecuritynotes#NetworkSecuritypdf#NetworkSecurityppt#NetworkSecurityprojects#NetworkSecuritytutorial#networkspeedtest#networktopology#Networktravels#networking#Networkingbasics#Networkingjobs
0 notes
Link
0 notes