#Network cabling contractor
Explore tagged Tumblr posts
Text
The Ultimate Guide to Structured Cabling Systems
Introduction
Structured cabling systems form the backbone of modern communication networks, providing a standardized and efficient way to manage data, voice, and video transmissions. This guide covers the fundamentals, benefits, components, installation best practices, and industry standards of structured cabling systems.
What is a Structured Cabling System?
A structured cabling system (SCS) is a comprehensive network of cabling and associated hardware that provides a universal infrastructure for various communication technologies. It supports multiple hardware systems and applications such as computers, telephones, and security devices, ensuring a seamless and scalable network environment.
Benefits of Structured Cabling Systems
Scalability - Easily accommodates growing network demands.
Cost-Effectiveness - Reduces maintenance and operational costs.
Flexibility - Supports multiple applications and technologies.
Improved Performance - Ensures high-speed data transmission with minimal interference.
Simplified Management - Centralized system makes troubleshooting and maintenance easier.
Enhanced Security - Provides a controlled and protected infrastructure.
Components of a Structured Cabling System
A structured cabling system consists of six main components:
Entrance Facilities - The point where external cabling connects to the building's network.
Equipment Room - Centralized space for network and telecommunications equipment.
Telecommunications Room (TR) - Houses connectivity equipment such as patch panels and network switches.
Backbone Cabling - Connects different TRs, equipment rooms, and entrance facilities.
Horizontal Cabling - Connects workstations and end-user devices to the TR.
Work Area Components - Includes cables, connectors, and outlets at the end-user level.

Industry Standards and Compliance
Structured cabling systems adhere to various industry standards, including:
TIA/EIA-568 - Telecommunications Cabling Standards
ISO/IEC 11801 - International Cabling Standards
BICSI Standards - Best practices for cabling installation and maintenance
NEC (National Electrical Code) - Electrical safety regulations
Installation Best Practices
To ensure an efficient and reliable structured cabling system, follow these best practices:
Plan for Future Growth - Design the system with scalability in mind.
Use High-Quality Components - Ensure all cables, connectors, and hardware meet industry standards.
Follow Labeling and Documentation Procedures - Maintain accurate records for easy management and troubleshooting.
Ensure Proper Cable Management - Use cable trays, racks, and pathways to organize cables neatly.
Adhere to Distance Limitations - Follow maximum cable length recommendations for optimal performance.
Test and Certify the System - Perform thorough testing to ensure compliance with performance standards.
Conclusion
A well-designed structured cabling system is essential for a reliable, scalable, and efficient communication network. A network cabling contractor ensures proper installation by adhering to industry standards, implementing best practices, and planning for future expansion. Businesses can optimize their infrastructure and ensure seamless connectivity by leveraging professional expertise. Whether setting up a new network or upgrading an existing one, investing in a structured cabling system is a strategic decision that yields long-term benefits.
1 note
·
View note
Text
GPZ Cabling Inc: Your Trusted Telecommunications and Network Cabling Contractor
In today's fast-paced digital world, businesses rely heavily on efficient and reliable communication networks. Whether it's for day-to-day operations, customer interactions, or internal communications, having a strong telecommunication and cabling infrastructure is vital. GPZ Cabling Inc. stands as a trusted name in the industry, offering top-tier telecommunications and network cabling solutions to meet your specific needs. Our services ensure that your business remains connected, competitive, and ready for the future.
The Role of a Telecommunications Contractor
As a leading telecommunications contractor, GPZ Cabling Inc. specializes in designing, installing, and maintaining structured cabling systems that support data, voice, and video transmission. Telecommunications infrastructure is the backbone of any organization's communication network, and our team ensures that the cabling systems are robust and scalable.
Our experts provide comprehensive services that include fiber optic cabling, copper cabling, and wireless networks, ensuring seamless integration of all components. We take pride in offering solutions tailored to different industries, from corporate offices to data centers, warehouses, and retail establishments. With our extensive experience, we are committed to delivering projects that meet both technical and operational requirements.
Expert Network Cabling Solutions
In the world of networking, precision and expertise are crucial. GPZ Cabling Inc. is recognized as a premier network cabling contractor, offering a wide range of services designed to ensure that your business runs smoothly. Our team of certified professionals excels in the installation of Ethernet cabling, structured cabling systems, and fiber optics, ensuring that your IT infrastructure is equipped for high-speed data transmission and optimal performance.
From designing custom cabling layouts to integrating state-of-the-art network components, we make sure that your network is not only efficient but also scalable for future needs. Our network cabling services include everything from data cable management to cable labeling, patch panel installation, and testing to guarantee that your infrastructure is optimized for reliability and efficiency.
GPZ Cabling Inc: A Leader Among Cabling Companies
What sets GPZ Cabling Inc. apart from other cabling companies is our customer-centric approach and commitment to excellence. We are dedicated to understanding the specific needs of our clients and offering tailored solutions that exceed their expectations. Our team of professionals brings years of experience and industry knowledge to every project, ensuring that all installations are performed to the highest standards of quality.
We understand that each business has unique requirements, and our ability to provide flexible and scalable solutions makes us a top choice for cabling services. Whether it’s upgrading an existing system or deploying a completely new network, GPZ Cabling Inc. delivers solutions that are reliable, future-proof, and cost-effective.
Comprehensive Cabling Services
At GPZ Cabling Inc., we offer a full range of cabling services, including:
Data Cabling: Our data cabling solutions are designed to support high-speed data transmission, ensuring that your network performs efficiently even under heavy traffic.
Voice Cabling: Voice cabling is crucial for clear, uninterrupted communication. We specialize in installing reliable voice cabling systems that ensure flawless phone and VoIP operations.
Fiber Optic Cabling: For businesses that require high bandwidth and fast data transfer, our fiber optic cabling services provide a future-ready solution. Fiber optic cables offer superior performance over long distances and are ideal for data centers, corporate offices, and telecommunications companies.
Security System Cabling: We provide the cabling infrastructure required for security systems, including surveillance cameras, access control systems, and alarm systems. Our experts ensure that your security infrastructure is integrated into your network seamlessly.
Wireless Network Cabling: Wireless networks are becoming an essential part of modern businesses, and our team is equipped to design and install the necessary cabling infrastructure to support them. This includes access points, routers, and switches, ensuring uninterrupted connectivity across your entire network.
Server Room and Data Center Cabling: Our expertise extends to the design and installation of cabling systems for server rooms and data centers, ensuring that these critical components of your IT infrastructure operate efficiently and securely.
Why Choose GPZ Cabling Inc.?
Choosing the right telecommunications and network cabling contractor can make all the difference in the success of your business operations. GPZ Cabling Inc. is dedicated to providing solutions that are not only reliable but also tailored to the unique needs of each client. Here's why we are a preferred partner for businesses:
Experienced Team: Our team consists of highly trained professionals with years of experience in the telecommunications and cabling industry. We stay up-to-date with the latest technology trends and standards to ensure that your cabling system is always ahead of the curve.
Quality and Precision: We adhere to the highest industry standards, using only the best materials and equipment to guarantee the longevity and performance of your network. Our meticulous attention to detail ensures that every installation is completed with precision.
Customer Focused: At GPZ Cabling Inc., we believe that customer satisfaction is paramount. We work closely with our clients to understand their needs and provide solutions that meet both their current requirements and future growth plans.
End-to-End Services: From the initial consultation to the final installation and ongoing maintenance, we provide end-to-end services that cover all aspects of your cabling needs. Whether it’s a small office or a large-scale enterprise, we handle every project with the same level of commitment and expertise.
Cost-Effective Solutions: We offer competitive pricing without compromising on quality. Our solutions are designed to deliver maximum value, ensuring that you get the most out of your investment.
Conclusion
In the ever-evolving world of telecommunications and networking, having a reliable cabling infrastructure is crucial. GPZ Cabling Inc. is your go-to partner for all your cabling needs, offering a comprehensive range of services designed to keep your business connected and running efficiently. Whether you need a new installation, an upgrade, or ongoing maintenance, our team is here to provide expert solutions tailored to your unique requirements.
0 notes
Text

Network cabling contractor - Network Data Cabling
If you see any of these signs, consider updating the network cabling in your company. Select the top network cable service provider who is aware of your company's particular difficulties and challenges. Don't allow outdated wiring to hinder your company's growth. Contact the right cable service provider and develop your company.
0 notes
Video
youtube
Network Connections Group USA | Engraved labels | Cable labels | Low Vol...
#youtube#cables wireless cat5e cat6 fiberoptics electrical electricalwork termination contractor network lsl77 lsl78 cablelabels wiremarkers av cable
0 notes
Text
How Can Network Cabling Service Providers Improve Network Speed Rate?

Network speed is actually crucial for businesses in today's swiftly developing digital landscape to remain competitive and also effective. While advancements in technology engage in a notable task in boosting network efficiency, the groundwork depends on the infrastructure set out by cabling contractors. Whether it's for records centers, workplace structures, or industrial areas, the quality of network cabling directly impacts the speed and also integrity of information transmission. In this particular short article, we examine just how cabling specialists may strengthen network speed through key preparation and implementation.
The Ways Network Cabling Professionals Boost Network Speed
Making Use Of Advanced Wiring Solutions
The cabling contractors play a vital duty in picking as well as implementing the appropriate cabling options to improve network speed. Technologies like Cat6 cabling and also Fiber optic options deliver greater transmission capacity and faster information transmission costs contrasted to more mature criteria. By taking advantage of these enhanced cabling options, contractors can guarantee that the network infrastructure can supporting fast information transfer, thereby enhancing total network functionality.
Improving Network Structure
Successful network facilities is the backbone of any type of organization's IT ecosystem. Cabling contractors are actually liable for developing as well as putting up the framework that sustains the seamless flow of records within a company. This features LAN cable wiring, IP networking, as well as low current cabling for different units and also systems. By properly planning as well as executing the network structure, specialists can easily remove hold-ups as well as optimize data circulation, thereby enhancing network speed and integrity.
Executing Internet Protocol Networking Solutions
Along with the spreading of IP-based units as well as systems, the requirement for IP networking solutions has climbed. Cabling professionals focusing in IP networking possess the skills to concept as well as release networks that support IP-based interaction procedures properly. Whether it is actually for protection electronic cameras, VoIP systems, or even IoT devices, effective IP networking facilities is actually essential for maximizing network speed and efficiency. Cabling specialists proficient in cam system setup may make sure that surveillance networks function at optimal speeds, delivering real-time video clip nourishes without latency or buffering concerns. To ensure smooth connection, check out https://rapidtec.net/ site for choosing professional cabling service providers skilled in network infrastructure installation and also maintenance.
Taking On Greatest Practices in Network cable Installation
youtube
The method through which network cable televisions are actually set up may considerably affect network speed and also dependability. Cabling service providers should stick to field absolute best practices when putting up network cables to lessen sign interference and make certain steady performance. Proper cable administration methods, including arranging cable televisions and also preserving appropriate bend distance, can easily prevent indicator degeneration and make best use of information transmission speeds. Furthermore, conducting extensive screening and license of put in wires aids recognize as well as resolve any type of concerns that could possibly restrain network efficiency.
Conclusion:
In end, cabling specialists participate in a critical role in strengthening network speed with tactical preparation, implementation, as well as adherence to sector greatest strategies. Through taking advantage of innovative cabling solutions including Cat6 cabling and Fiber optic solutions, optimizing network framework, applying IP networking options, and also adopting greatest methods in network cable setup, specialists can easily aid institutions obtain faster and even more trusted records transmission. In today's fast-paced electronic world, spending in quality cabling and wiring services is actually vital for maintaining a competitive edge as well as ensuring soft business procedures.
0 notes
Text
Adaptive Solutions | Telecommunications Contractor | Network Cabling in Bellevue WA
We have a well-earned reputation as the most trusted Telecommunications Contractor in Bellevue WA. Our experienced technicians specialize in the installation, repair, and maintenance of phone systems, security systems, and other telecommunications equipment. We pride ourselves on delivering exceptional customer service to ensure that your business has access to reliable and efficient communication solutions. Moreover, we are also renowned for Network Cabling in Bellevue WA. Whether you're establishing a new office or upgrading an existing system, we are here to help. From us, you can have ongoing support and maintenance to ensure that your cabling continues to perform optimally. So, if you need our expert assistance, call us today.

#Telecommunications Contractor in Bellevue WA#Network Cabling in Bellevue WA#Security Camera Installation near me#Network Cabling Company near me#CCTV Installation Services near me
1 note
·
View note
Text
In his book In the Garden of Beasts: Love, Terror, and an American Family in Hitler’s Berlin, Erik Larson cites a cable sent to the State Department in June 1933 by a U.S. diplomat posted in Germany that provided a far more candid assessment of the Nazi leadership than the one that President Franklin Delano Roosevelt’s administration was then conveying to the public. “With few exceptions, the men who are running this Government are of a mentality that you and I cannot understand,” read the cable, which was written five months after Adolf Hitler was appointed chancellor. “Some of them are psychopathic cases and would ordinarily be receiving treatment somewhere.”
I’ve thought about that passage from the cable many times over the past several weeks as I’ve been reading excerpts from a private WhatsApp group chat established last December by Erik Prince, the founder of the military contractor Blackwater and younger brother of Betsy DeVos, the secretary of education during President Donald Trump’s administration, who invited around 650 of his contacts in the United States and around the world to join. Prince, who has a long track record of financing conservative candidates and causes and extensive ties to right-wing regimes around the world, named the group—which currently has around 400 members—“Off Leash,” the same name as the new podcast that he’d launched the month before.
Among the group’s hottest topics:
• The “Biden Regime,” which a consensus of Off Leash participants who weighed in view as an ally of Islamic terrorists and other anti-American forces that needs to be crushed along with them and its partners in the deep state, such as former Joint Chiefs of Staff Chairman Mark Milley, who “deserves to burn in hell,” Lara Logan shared with the group chat.
• The shortcomings of democracy that invariably resulted from extending the franchise to ordinary citizens, who are easily manipulated by Marxists and populists. “The West is at best a beautiful cemetery,” lamented Sven von Storch, whose aristocratic German family fled the country after World War II to Chile, where their son was raised before returning to the land of his ancestors, where he married the granddaughter of the Third Reich’s last de facto head of state, who was convicted at Nuremberg.
• Israel-Palestine, a problem that Michael Yudelson, Prince’s business partner at Unplugged, which markets an allegedly supersecure smartphone, said should be handled by napalming Hamas’s tunnel network. “I would burn all those bastards, and have everything above ground, everything left of Gaza, collapse into this fiery hell pit and burn!” he wrote.
• The Houthi rebels in Yemen, whom Yoav Goldhorn, who was an Israeli intelligence officer until last year and now works for a Tel Aviv–based security contractor headed by former senior national security veterans, thinks should be “dealt with” as soon as possible to ensure they don’t grow from “an inconvenience to a festering mess [that] will eventually require an entire limb to be amputated.”
• And most of all, Iran, which participants agreed, with a few exceptions, also needed to be wiped out. Saghar Erica Kasraie, a former staffer for Republican Representative Trent Franks when he served on the House Armed Services Committee and whom, according to her LinkedIn profile, she advised on Middle East issues, urged that the Islamic Republic’s clerical leaders be targeted by weaponized drones that “take them out like flys 😎.”
Not all of the group’s members are conspiracy theorists in the mold of Logan, the former CBS correspondent. I know many people who are in roughly the same political ballpark as the average Off Leash participant, including some of the chat group’s members, who are razor-sharp, even if I strongly disagree with a lot of their opinions. I don’t know Prince other than having been in the same room with him on a few occasions, but we have mutual acquaintances who say he’s not a one-dimensional evil mercenary as typically portrayed but brilliant and funny, and over drinks greatly prefers to discuss business and history rather than expound upon the latest developments in right-wing political circles.
Frank Gallagher, a former Marine who once provided security for Henry Kissinger and who worked in a high-level position at Blackwater in Iraq following the 2003 U.S.-led invasion, isn’t a fan of Prince but offered a similar assessment. “We had issues from time to time, but I can’t deny that he’s extraordinarily smart,” he recounted. “When he came to Iraq, he’d cover 10 topics, and he had command over all of them.”
All of which makes Off Leash arguably more concerning, because the group can’t be dismissed as merely a collection of harmless cranks. Many of the participants, though not all household names, are wealthy and politically wired—which makes their incessant whining in the group chat about being crushed under the bootheel of the deep state particularly grating—and they will collectively become wealthier and more influential if Trump wins the November election. That’s especially true of the Americans in the group, but the same holds for the international figures because the global right will become immensely more powerful and emboldened if the former president returns to the White House. That prospect is a source of great hope to Off Leash participants. “Trump, Orban, Milei, it’s happening,” former Blackwater executive John LaDelfa posted to the group during a trip to Argentina on December 4, two days after Prince created it. “Around the Globe, we are the sensible, the rational, the majority. Don’t give in to fear. We will defeat the Marxists.”
His hopes were shared by many other Off Leash participants, among them Horatiu Potra, a Romanian mercenary who has recently been operating in the mineral-rich, conflict-plagued Democratic Republic of Congo. “The globalists want to control the entire planet [and] the only chance to get rid of them is a spark from a great power (the USA),” Potra wrote. “Surely there will be a strong man like Erik who will initiate it, otherwise there is no chance of regaining our freedom. If this spark is started, all countries will follow suit.… We were waiting for the signal, the spark!!”
A December 2023 United Nations report alleged that Potra owns a company that has provided combat support and fighters to Congolese government troops fighting a vicious rebel insurgency. Prince unsuccessfully sought to negotiate a deal with the DRC government to fly 2,500 mercenaries from Colombia, Argentina, and Mexico into the country to fight alongside Potra’s men, the report said.
About three-quarters of the people Prince invited to the group chat are from the U.S. or live here. The largest overseas blocs are from Israel (32 members), the United Arab Emirates (20 members), and the United Kingdom (20). There are smaller contingents, sometimes a single person, from 33 other countries in Africa, Asia, Europe, Latin America, and the Middle East.
Collectively, Off Leash provides an informal virtual gathering place for current and former political officials, national security operatives, activists, journalists, soldiers of fortune, weapons brokers, black bag operators, grifters, convicted criminals, and other elements in the U.S. and global far right. The roster of invitees includes:
• Icons of the MAGA ecosphere such as Tucker Carlson, the most revered figure among group chat participants, with the exception of the Supreme Leader himself; Kimberly Guilfoyle, the longtime fiancée of Donald Trump Jr.; and retired Lieutenant General Michael Flynn, Trump’s convicted-then-pardoned first national security adviser. Flynn has participated, Carlson only minimally, and Guilfoyle not at all.
• Current and former lawmakers and aides, such as Tennessee Congressman Mark Green of the House Freedom Caucus; Vish Burra, who was director of operations for Congressman George Santos; and Stuart Seldowitz, a national security adviser to Barack Obama from 2009 to 2011 who was arrested last November after harassing an Egyptian halal street cart vendor in New York City for two weeks, during which time he called him a “terrorist” and said, “If we killed 4,000 Palestinian kids, it wasn’t enough.”
Prominent figures in the Off Leash crew are well known for their paleoconservative political views, but the private opinions expressed in the group chat are even more extreme and jarring than we normally see voiced publicly. Participants chirpily discussed the desirability of clamping down on democracy to deal with their enemies at home and regime change, bombings, assassinations, and covert action to take care of those abroad. The group’s overall bloodlust periodically proved to be too much for a few more judicious individual members, who in almost any other setting would be considered ultraconservatives but in the context of Off Leash sound like hippie peaceniks. One of the dissidents—a National Rifle Association firearms instructor who runs a weapons company—joked that he was worried about an “unsupervised” subgroup of especially enthusiastic military adventurers that formed to discuss topics too “hot” for WhatsApp, saying, “I imagine their ‘to be bombed’ list is over 49 countries and growing.”
Many other Off Leash participants have also stated that they don’t view the group chat as merely a forum to exchange ideas but want it to become a vehicle to put their theories into action. “If we band together … we can damage the other side like no one has ever seen before!” exclaimed Jeff Sloat, who worked with a U.S. Army psyops unit in Central America during the Reagan era.
I don’t want to disclose much about how I learned of the group chat and the nature of its discussions, but I will say that multiple sources in the U.S. and elsewhere shared information, including two journalists who I discovered had learned about Off Leash, which nearly gave me a heart attack for fear I’d lose my scoop. Participants did occasionally express concerns about security, but their worries were mostly centered on the possibility that their conversation was vulnerable to hackers. It apparently never occurred to any of them that their confidentiality might be compromised not by sophisticated cyberwarfare specialists but by old-fashioned leakers, which was virtually inevitable given the group’s size.
Off Leash was still active as of Wednesday, though I expect it won’t be, at least in its current form, for much longer, given that the conversation Wednesday included much discussion about their security being breached, which became evident after I reached out to participants for comment. Fortunately, I obtained details about a large slice of the chat group’s discussions over the past six months. Here’s some of what they discussed.
Solving the Middle East Crisis: Nukes, Napalm, and Other “Extreme Measures”
Off Leash was launched less than two months after Israel commenced its assault on Gaza following Hamas’s deadly October 7 attack on Israel, and that topic has been one of the group chat’s main concerns since it was established by Prince on December 2. Five days later, Omer Laviv, an executive with the Mer Group, a private security company with many former Israeli intelligence officials in its senior ranks, posted a story to the group that ran two days earlier in The Times of London and reported Prince had been seeking to sell the Israel Defense Forces equipment for a plan he’d devised to flood Hamas tunnels with seawater.
“I was involved,” remarked Moti Kahana, the Israeli American businessman who runs GDC, the firm where Off Leash member Stuart Seldowitz previously worked. Kahana pointedly added that at least one part of The Times’ story was false—for example, Prince had offered to donate the equipment, not sell it, he said.
“Why do you expect accuracy from journalists?” retorted Laviv, who during the Trump administration retained 27 U.S. lobbyists and consultants to run a $9.5 million lobbying campaign on behalf of President Joseph Kabila, the corrupt, brutal leader of the Democratic Republic of Congo, who used surveillance equipment supplied by the Mer Group to monitor his regime’s opponents. Among those Laviv involved were Rudy Giuliani, Trump’s former personal lawyer, fixer, and dirt-digger, and Robert Stryk, whose clients have included Saudi Arabia and El Salvador’s state intelligence agency under crypto-fascist President Nayib Bukele.
Yudelson, who also reportedly partnered with Prince in an attempt to buy weapons for resale from Belarus dictator Aleksandr Lukashenko (whom the two men praised for bringing “peace, stability, and prosperity to your country”), predicted the tunnel-flooding proposal would be shot down by the “Israeli left,” a force he labeled the country’s “biggest enemy,” ahead of Hamas and Iran, over concerns about the environmental impact in Gaza. “Who gives a shit about that,” Yudelson posted to the group. “If it was up to me … I would flood them with Napalm! I would burn all those bastards, and have everything above ground, everything left of Gaza, collapse into this fiery hell pit and burn!”
Even that was deemed to be insufficiently hawkish for some Off Leash participants. In a lengthy tirade on February 14, Tzvi Lev, who formerly worked in Israel’s Ministry of Foreign Affairs, said it was rare to see a people as “twisted” as Palestinians, whose culture “worships death and bloodshed.” The only solution, he wrote, was to “completely uproot the radical Islamic Palestinian nationalism,” which was possible to do based on the historical precedent of Japan, which “went from being nuked twice to one of the world’s strongest economies within two decades.” Dropping nuclear weapons on what’s left of densely populated Gaza, which is roughly the size of Detroit, would be a war crime and kill huge numbers of civilians.
Yoav Goldhorn, the former Israeli intelligence officer, also cited “fucking nukes in Japan” as an appropriate remedy to the Palestinian problem. Sadly, wrote Goldhorn, whose LinkedIn profile says he has “a passion for strategic planning,” there was no one in the Israeli government with “the balls nor vision to go all those extra miles.”
Iran: Off Leash’s Public Enemy No. 1
It was hard to keep track of all the wars, invasions, covert operations, coups, and assassinations Off Leash members favored. One region ripe for a bit of good old-fashioned Western intervention was Africa, which was described as a “pot about to boil over” by Emma Priestley, who posts as “Customer” in the group chat and is the CEO of GoldStone Resources Limited in Jersey, the English Channel island that is one of the world’s most popular offshore secrecy havens. China would have to be taken down a peg as well, particularly as Biden wasn’t going to stop the country “from doing a damn thing,” and indeed he would pave the way for it to do “whatever it is they want to accomplish,” posted Randy Couture, the former UFC heavyweight champion and actor who had the role of arsonist and killer Jason Duclair in the TV series Hawaii Five-0 and starred in the 2011 movie Setup with 50 Cent and Bruce Willis.
But the No. 1 target on Off Leash’s hit list, by orders of magnitude, was Iran. “Follow the source of evil,” wrote Montana Congressman Ryan Zinke, who served as interior secretary under Trump. “Hamas. Hezbollah. Houthis. Iran is the center of gravity.”
“Zinke is right,” agreed Tennessee Congressman Mark Green of the House Freedom Caucus.
Yemen’s Houthi rebels were most immediately in the group’s crosshairs, due to their attempts to halt arms shipments to Israel. Finishing them off would be a cakewalk, but time was of the essence as the Houthis were “relatively limited in strength” at the moment but could become a major problem if swift action wasn’t taken, wrote Yoav Goldhorn, a former Israeli intelligence operative.
To Goldhorn’s way of thinking, the Houthis were best compared to “rot [that] stinks a lot more than the flesh it ate”:
As we’ve seen countless times in the Middle East, if you don’t treat rot it will grow and spread and turn from an inconvenience to a festering mess, and will eventually require an entire limb to be amputated. The Houthi threat has to be dealt with now, while they’re still relatively limited in strength. Otherwise it’ll become a problem too big to handle without extreme measures, or worse yet—remain a problem for future generations to come.
As for moving against Iran itself, the leading cheerleader in the group chat for military action is Kasraie, who worked for Representative Franks of Arizona until 2017, when he resigned amid charges of sexual harassment by two female staffers. “The IRGC is the head of the snake,” Kasraie wrote in one post, referring to the Islamic Revolutionary Guard Corps. “It’s time to cut the head of that snake.”
An Iranian American who converted to Christianity after her family moved to the U.S. following the 1979 Islamic Revolution, Kasraie has worked closely with fellow exile Amir Abbas Fakhravar, the co-founder of the Confederation of Iranian Students, which claimed to represent a worldwide pro-Western movement in support of domestic opponents of the Islamic government.
Fakhravar was hailed by the neoconservative think tanks American Enterprise Institute and Foundation for Defense of Democracies—which were leading advocates of the 2003 invasion of Iraq and are currently leading the drumbeat for regime change in Iran—as his country’s 2.0 version of Ahmed Chalabi, the CIA-backed Iraqi exile whom the Bush administration promoted as a beloved figure among citizens of his native land during the run-up to the 2003 invasion that toppled Saddam Hussein. That didn’t pan out as promised when Chalabi 1.0 led a political coalition in parliamentary elections two years after his triumphant return that won less than 1 percent of the total vote.
Now Kasraie, who organizes congressionally hosted “global conferences in Washington for activists to plan the constitutional future of a free, democratic Iran,” according to an online bio, is touting Reza Pahlavi, the shah’s oldest son and crown prince of Iran, as “the only viable opposition leader” and the man the U.S. should install in power after seeing to the formality of dispatching the current government.
“I assure you, the Iranian people want nothing more than to be free from the bloodthirsty mullahs,” Kasraie wrote in the group chat on January 27, and added with equal certainty that younger Iranians were “pro-Israel and pro-America” and that millions in the country felt a deep “sense of nostalgia” for the former royal dynasty. If Reza Pahlavi received strong international support—he would merely be a “mouthpiece” to be handled by a team of “good advisors,” Kasraie stated—the internal opposition “would be much more inclined to rise up and we would see far more defectors.”
For his part, Reza Pahlavi, who hasn’t stepped foot in Iran for 45 years and lives in a lavish estate in the Washington suburbs, said in an interview last year he wasn’t sure he wanted to have an official role in a future government if the current one was overthrown, or even live in the country. This didn’t dampen the ardor of Kasraie, who in one post labeled the mullahs a “cancerous venom that need to be eradicated from … the planet,” with her preferred method to accomplish that being weaponized drones that would “take them out like flys 😎.”
That type of approach was endorsed by others in the group, including Gabriel “Kaz” Kazerooni, a former U.S. intelligence officer, Special Forces veteran, and Blackwater employee in Iraq, who described Iran’s religious leaders as “pedofile [sic] Mullahs” and a “bacteria to humanity” who he hoped would soon “die away.”
“EP [Erik Prince] has the right people in place,” Kazerooni added cryptically, saying it was only a matter of time before the “Mullah Pigs” would be removed from power.
Washington should “take out” the commander of the IRGC’s Quds Force that replaced Maj. Gen. Qassem Soleimani, who was killed in a 2020 operation ordered by President Trump, Lara Logan said. Prince had urged he be targeted for killing four years earlier, when he was informally advising the Trump campaign, in a memo to White House chief strategist Steve Bannon.
Logan proposed the U.S. also assassinate other “key targets” in the Middle East, specifically mentioning “the head of Hamas,” whose name she didn’t mention, but she presumably was talking about Mohammed Deif, who leads the group’s military wing. “That will send a message,” she said.
Nathan Jacobson, a 69-year-old Canadian Israeli businessman who told The New Republic he is a longtime friend of Israeli Prime Minister Benjamin Netanyahu and fought with the IDF as a young man, had a more ambitious proposal. In order to topple the Islamic regime, he said blithely, “We need to hit” Iran’s nuclear facilities, ports, Qom, where the mullahs reside, IRGC headquarters and bases, and oil industry production facilities, which would shut down the country’s economy for months.
The calls for carnage elicited pushback from two Off Leash members. “The problem is while doing nothing could empower them, bombing might empower them more,” warned Mark Farage, who owns a firearms and ammunition manufacturer in Virginia and made the joke about the “unsupervised” subgroup’s ever-growing list of countries they wanted to be targeted for airstrikes. “I don’t think we have successfully bombed anyone into an ally since WWII.… Maybe we should consider more tools than just a hammer?”
“Huge mistake to attack Iran directly,” concurred Matt Heidt, a Special Forces veteran who deployed to Africa, South America, and Asia, including a 2007 stint in Iraq’s Anbar Province. “We would be inviting 10/7 here.”
Jacobson was infuriated by the criticism of his blueprint for war.
“We don’t want them as an ally,” he said in a comment directed at Farage. “Let them spend their time stoned on qat and screwing their sheep.”
He was even more contemptuous of Heidt’s opinions. “You remind me of the Jews in Germany in the 30’s that thought that by being quiet that the problem would go away,” he sneered. “We have no choice but to hit them hard and then kill these cells if they raise their ugly heads. Why are you taking a coward’s standpoint?”
“So you’re going to waddle your fat ass over there and put some skin in the game or are you content to put others at risk?” retorted Heidt.
“Unlike you, I’ve had skin in that game for years,” said Jacobson, who served in the IDF in the 1970s. “What have you done?”
“Retired SEAL Senior Chief with a Bronze Star with V,” shot back Heidt. Bronze Stars are awarded for heroism in a combat zone, and are not uncommon, but a Bronze Star with V, for Valor, are relatively rare.
Those in Off Leash’s overwhelmingly dominant hard-line faction were having none of the namby-pamby defeatism from Heidt and Farage.
“Bomb the hell out of them,” Kazerooni insisted. “Mess with US and you will eat your Sh_t. We the United States Of America is still the strongest Country in the world.”
More recently, the Off Leash crew has been in a chronic state of agitation over political developments that have led them to further ratchet up their calls for jihad against their worldwide enemies. In mid-April, after Tehran fired missiles into Israel in retaliation for an airstrike in Syria that killed two of its generals in a diplomatic building, Sloat, the psyops specialist, excitedly declared it was “time to disintegrate Iran.” In May, their fury turned to Biden’s brief pause in arms shipments to Israel, though none were surprised by the president’s treachery, as his “Regime is infiltrated by Muslim Brotherhood” (Yudelson) and “compromised … by Iranian regime influencers” (Zinke).
The group finally got good news recently with the helicopter crash that killed Iranian President Ebrahim Raisi, though nerves frayed as they awaited confirmation he was dead. If he’d tragically survived, wondered Tzvi Lev, perhaps it would be possible to dispatch a Special Forces search and rescue unit to “disappear” him before he was found.
The Future of American Democracy: “It’s Trump or Revolution!”
Even more worrying to group chat members than the state of global affairs was that democracy was under attack across the world, especially in the West and most of all in the U.S. They blamed the same barbarians at the gate science fiction writer Robert Heinlein pointed to in To Sail Beyond the Sunset, which was published in 1987, the year before his death. “Democracy often works beautifully at first,” but the day the franchise is extended “to every warm body … marks the beginning of the end of that state,” Heinlein wrote. “For when the plebs discover that they can vote themselves bread and circuses without limit and that the productive members of the body politic cannot stop them, they will do so, until the state bleeds to death, or in its weakened condition … succumbs to an invader—the barbarians enter Rome.” The passage about bread and circuses was posted in its entirety on February 16 by former Virginia Congressman Tom Garrett, who offered it as an explanation for why democratic governance made it impossible to address the problems facing the United States.
“Definitely an issue,” agreed Scott Taylor, another former House member from Virginia, and Republicans were responsible as well. Too many GOP lawmakers campaigned as principled opponents of government spending, Taylor wrote on the list, but were “more concerned about their individual selves then actually advancing conservative policy” and chased federal money for their home districts like common Democrats in hopes of currying favor with their pleb constituents.
Former President Trump’s campaign to return to the White House posed an even graver and more imminent threat to American democracy. It wasn’t Trump, per se, or his efforts to reverse the results of the 2020 presidential election that troubled the group, needless to say. The danger was that following his landslide victory this November, which was a foregone conclusion, the deep state would “steal it again,” just as it had four years ago, Yudelson posted. “I just hope and pray that they will not JFK Trump before the elections, physically, or with some of their other methods.”
Despite such trepidations, Congressman Zinke spoke for the group when he wrote, “There is only one path forward. Elect Trump.”
“It’s Trump or Revolution!” Yudelson chimed in from the chorus.
“You mean Trump AND Revolution,” a right-leaning Canadian businessman shot back. “The Left is too violent to sit back and let Trump win again.”
John Mills, a retired Army colonel who held a cybersecurity post at the Pentagon under Trump, was overcome with emotion when his hero appeared at the Conservative Political Action Conference in February. “Tears streamed down my face,” he wrote to the Off Leash group chat from the event. “DJT and the J6ers are in the house.”
The view that Trump represented a unique hope was shared by group chat members outside of the U.S. “He is the best thing … even in Africa,” offered N.J. Ayuk, a native of Cameroon who currently lives in Johannesburg, where he founded a law firm that assists clients with interests in the oil and gas sector. “Trump all the way 💯”
“I live in darkest west Africa,” posted Emma Priestley of GoldStone Resources Limited. The overall situation was such an irredeemable mess, Trump himself might not be able to “save this shithole of a continent.”
“Completely agree,” replied Ayuk, who once worked as an intern for the late New Jersey Democratic Congressman Donald Payne but was deported in 2007 after pleading guilty to using his boss’s stationery and signature stamp to illegally obtain visas to the U.S. for citizens of his home country. The Biden administration had been “a disaster” for Africa. “They only give us lectures and talk about renewables,” said Ayuk. “These latte liberators are actually the problem.”
That was a minor offense among the long litany of crimes Off Leash participants laid at Biden’s door. “Looks like the globalists are enabling this mass illegal immigration,” Yudelson, citing an article at Zerohedge, wrote in one post. “Surely with tremendous assistance from the Biden Regime.” But Biden was merely a figurehead controlled by “elements that are actually ruling for the Deep State,” he continued. The real problem was that Democrats had been “in cahoots with the Muslim Brotherhood and infiltrated by their proxies and agents, as well as Ayatollah sympathizers” ever since President Bill Clinton’s administration.
With the Democratic Party captured by Islamic terrorists, Marxists, globalists, and other foreign and domestic evildoers, the U.S. was “being destroyed from within,” warned Kasraie, whose fears were shared by many among the Off Leash crew.
“The insurgency within our country today is going to bite us,” said Scott Freeman, the CEO of a Virginia company called International Preparedness Associates, which designs “unique special programs” that help defend U.S. national security, friendly foreign governments, and private-sector interests, according to its website.
Many Off Leash participants were even less restrained. When a chat group participant posted a story that revealed JPMorgan Chase had hired General Mark Milley—whom Trump appointed chairman of the Joint Chiefs of Staff but clashed with during and after his presidency—as a senior adviser, Lara Logan went off the rails. “Milley is a piece of shit and a traitor and he deserves to burn in hell,” posted Logan, who holds a seat on the board of America’s Future, a conservative nonprofit chaired by Off Leash member and former Lieutenant General Michael Flynn, Trump’s national security adviser for less than a month.
At a February 23 America’s Future event, Logan shared that she’d originally been skeptical of the Pizzagate conspiracy theory, which spread in far-right circles during the 2016 election and proposed that Hillary Clinton and other Democratic Party officials were running a child sex trafficking ring out of the pizzeria Comet Ping Pong. However, after conducting her own independent investigation, Logan told the audience at the event, she’d discovered, “Holy guacamole! This actually is all true.”
What, then, was to be done?
The answer was clear to Freeman, a.k.a. “ScottyF” in the group chat. “Apply all tenets of warfare internally against the many enemies living among us. America is capable of being fully capable again. Do we have the will to levy the toll?”
Jesse Barnett, a retired Navy SEAL specializing in “Active Shooter Prep ... and Crisis Prevention” who ran the Indianapolis-based indoor shooting simulator Poseidon Experience, offered a harsh but necessary recipe. “We need a Nuremberg style clean up of this global cabal,” he proposed. “Only through accountability can we cleanse our spirits.” Once the cleansing was out of the way, security could be maintained by using “technology to identify sociopaths and keep them in their place.”
On the roster of Off Leash participants, there was one—a poster with the handle of “S,” whom it took me weeks to identify—who stood out as a particularly dark character. There were some in the group who expressed more unhinged views and others who more casually called for violence against their enemies; what made S distinctive was his dry, bloodless manner and businesslike espousal of a disciplined worldview that was unmistakably fascist.
“This is no longer politics, this is an open war against freedom and human nature. And wars aren’t won with more balloons and confetti as we know,” S wrote. “It’s no longer a ‘game’ either.… It is time to adapt strategies to reality and stop pretending that we live in a free democracy in the West.”
S was later revealed to be Sven von Storch, born to a German family that left for Chile after World War II, whose wife, Beatrix von Storch, is the granddaughter of Lutz Graf Schwerin von Krosigk, Hitler’s finance minister from 1933, the year he took power, until he killed himself in Berlin in April 1945, as Russian troops closed in on the bunker where he and the dregs of his loyalists were holed up. In his last will and testament, Hitler appointed von Krosigk to serve under Joseph Goebbels, his handpicked successor as chancellor, but since his minister of propaganda committed suicide the day after Hitler, von Krosigk became the Third Reich’s head of state during its final days. “Von Krosigk never wavered in his enthusiasm and labors for the Nazi cause,” prosecutor Alexander Hardy said during his trial at Nuremberg, where he was sentenced to 10 years for financing the concentration camps and other crimes.
Beatrix von Storch is a leader and Bundestag member with Alternative for Germany, arguably the most radical of Europe’s far-right parties, which calls for a crackdown on immigration into the country to protect its “Western Christian culture,” a variant of the “great replacement” theory espoused by white supremacists in the United States. Sven von Storch doesn’t hold elected office, but he’s considered to be a prominent figure in the AfD. An admirer of Steve Bannon, von Storch has close ties to Chile’s pro-Pinochet political bloc; he and his wife met with Jair Bolsonaro, the country’s former president, at the presidential palace in Brazil, and the latter’s powerful son Eduardo gave the couple a bottle of the first family’s brand wine as a gift.
“Law and justice no longer mean anything in the West,” von Storch wrote during the same conversation. “Stupid and naive people may still believe it. And probably not even them anymore.”
It’s not clear how many in the group knew S’s real identity, but he was clearly a pedigreed German fascist who even within the rarefied far-right ecosphere of Off Leash sat at a distinctly extreme end. No one seemed troubled by his views, and indeed von Storch was warmly embraced. “This is getting interesting,” Kazerooni wrote in response to his post. “Love this Group.”
Freeman was one of a number of group chat participants who, like the former psyops specialist Sloat, wanted to look for ways to implement their policy ideas. A group with so much “experience, accomplishments and resources” should look for a few issues we “might be able to influence together,” Freeman proposed. “Not to save the world or the idiots in the USA but rather a core of us or perhaps a broader group of like minds/patriots of some sort. 🤷♂️”
Reading the group chat’s conversations would be comical if it wasn’t so pitiful and disturbing in equal measure. Group members clearly regard themselves as natural elites who are more intelligent, virtuous, and honorable than Heinlein’s tired, poor, unwashed plebs.
Yet none of the four current and former members of Congress who are active in the group distinguished themselves as model public servants. In 2018, Zinke resigned as Trump’s secretary of the interior after an Inspector General’s report concluded he was a serial violator of ethics laws. Green withdrew his nomination to be Trump’s army secretary after being criticized, including by GOP John McCain, for past statements he’d made that called for his fellow citizens to “take a stand on the indoctrination of Islam in public schools” and labeled transgender people “evil.” Garrett resigned his House seat in 2018 after it was alleged he and his wife used his congressional staff to run errands, chauffeur their children, and clean up after their dog, though he denied those charges and cited alcoholism as the reason he had stepped down. Four staffers who worked on Taylor’s 2018 reelection campaign were subsequently indicted for election fraud, which he said he knew nothing about, but he lost that race and did again when he ran for his old seat two years later.
Even more farcical was the manner in which group chat members portrayed themselves as rightful guardians of democracy, even as they proposed employing military force against their unarmed domestic political opponents and rounding up members of the “global cabal” for trial at a Nuremberg-style tribunal. It’s blazingly evident that many in the group can’t even define democracy, and those who can don’t like it.
Dallas real estate developer Scott Hall informed the group he was moving his family to the UAE, which is ruled by an authoritarian monarchy, because “freedom is real” there. When President Gustavo Petro, Colombia’s first leftist president, was running for office two years ago, the rural oligarch Sergio Araujo Castro publicly declared that his employees “have the right to vote freely for whoever they want,” but he’d fire any who supported Petro. After protests against the Biden administration’s support for Israel’s assault on Gaza erupted at Stanford in January, Goldhorn wondered how it was legal that students who took part weren’t summarily expelled as they received benefits from the U.S. government, but “[wished] for its destruction,” which he evidently equated with criticism of its policies.
I sent messages seeking comment to Prince and the 29 participants whose comments in the group chat are cited in this story. Prince did not respond. Of the others, only Barnett, Jacobson, and Goldhorn were willing to be interviewed.
Barnett, who once worked for Blackwater, said participants in the group chat “love the country and want good solutions” and that he was not an ideologue and favored “checks and balances, and transparency.” A “centrist who leans libertarian” and Barack Obama voter in 2008, Barnett said the 9/11 attacks seven years earlier were an “inside job 100 percent,” and that they “woke me up” and triggered the political evolution that led to his current “conspiracy observationist perspective.”
Barnett said he was a Trump fan in part because “the establishment hates” the former president, adding that the Russiagate scandal that led to his first impeachment had been cooked up by Democrats as part of a politically motivated attack to drive him from office. (An opinion I share.) When I told Barnett his remarks about the need for a new Nuremberg tribunal sounded like a call for an attack of the same type but against enemies of the group chat, he said he didn’t favor a politically driven kangaroo court but envisioned a scrupulously fair judicial process that “truly enables our country to move forward,” which could be ensured by establishing panels with impartial experts such as journalist Matt Taibbi, psychologist and commentator Jordan Peterson, and others of similarly “high integrity” to help determine who would be prosecuted.
Jacobson also said his remarks in the group chat sounded harsher than he’d intended. Despite having been friendly with Netanyahu for many years, he said the Israeli prime minister and his government were “long past their expiry date,” and he considered the military attack on Gaza to be “a complete failure.” On Iran, Jacobson said he “loved Iranian culture, cuisine, and people” and noted that he’d spent time with Reza Pahlavi last week when the latter was in Toronto, where he lives.
“I hate the mullah’s regime,” Jacobson added, but “I’m not calling to go to war” but to help the domestic opposition bring the regime down by bombing Iranian oil infrastructure and related targets. About a month ago, he’d proposed that during an informal discussion with an unnamed Israeli official, telling his interlocutor that Iran’s missile strikes against Israel were “our opportunity to hit their oil facilities so they can’t make money to finance terrorism.” About Off Leash itself, Jacobson said, “I enjoy the banter of the group, but it’s not a political conspiracy.”
“I have no idea what you’re talking about,” Goldhorn, who told me he knows Prince “very tentatively,” replied when I paraphrased his remarks about dropping nuclear weapons on Gaza and regarding the Houthis. “I didn’t see anyone proposing or discussing such actions in the group, so I can’t really comment on these claims.” When I sent him the relevant excerpts, his memory was refreshed regarding the Houthis, though he said he was “referring to the naval threat mostly,” as the group was seeking to sink merchant ships. “I was not [referring] to the Yemenese [sic] people as a whole, only the military organization.” He continued to insist he’d “never suggested to nuke Gaza, which is a laughably dumb idea,” though I had excerpts of the respective conversations about both topics, which were faithfully recounted earlier, and the quotes from Goldhorn are verbatim.
Off Leash’s participants want a “democracy” where the “plebs” vote the way they want in every election and the government only approves their preferred policies, which would give them the absolute certainty they want that their outsize wealth, privileges, and influence will be protected. That’s not the way democracy works, it’s the way dictatorships do, which no doubt feels comfortable to group chat members who have thrived doing business with corrupt, repressive regimes and leaders, which is the way many met each other and Prince, and how they came to be part of Off Leash in the first place.
To paraphrase the assessment of Nazi officials made by the U.S. diplomat from Erik Larsen’s In the Garden of Beasts, during ordinary times, people who hold such opinions would be receiving treatment somewhere. However, to continue with the analogy, many Off Leash participants currently hold powerful political roles or are intimate allies of those who do.
The key to expanding their influence, in the collective view of the group chat, and not only its American members, is a victory by Trump in the November election. “The freedom of the Western world is decided in the USA,” as von Storch put it. “As long as the USA lets the globalists do whatever they want, we patriots in the rest of the world can only try to maintain and survive our positions.”
Comparing the contemporary United States to Nazi Germany is an admittedly imprecise analogy. Nevertheless, it’s impossible not to be alarmed by the crypto-fascist, off the leash views expressed by Trump’s allies in the group chat about exterminating their foreign and domestic enemies and needing to “find the will to levy the toll.” However imprecise the comparison, as a model political capital, Berlin 1933 is far more compatible with the worldview of Off Leash participants than Washington 2024, and in the event they and like-minded associates gain power in the U.S. or elsewhere, they’ll be pushing backward in that general direction.
4 notes
·
View notes
Text

The man who stole America’s stealth fighter secrets for China 🇨🇳
It’s not uncommon to hear people say that China’s most advanced stealth fighters, the in-service Chengdu J-20 and forthcoming Shenyang FC-31, incorporate stolen design elements from existing American and Russian fighter programs. Russian allegations of copycat technology are born largely out of overall similarities between the J-20 and Russia’s long-defunct MiG 1.44 program. However, although Russian allegations leave at least some room for debate the same can’t be said for China’s theft of American stealth fighter designs.
In March 2016, a 51-year-old Chinese national named Su Bin pled guilty to charges associated with what the American Justice Department described as a “years-long conspiracy” conducted in concert with high-ranking members of the Chinese military to steal American military secrets – most notably, the designs for advanced stealth fighters like the F-22 and F-35.
“Su admitted that he conspired with two persons in China from October 2008 to March 2014 to gain unauthorized access to protected computer networks in the United States – including computers belonging to the Boeing Company in Orange County, California – to obtain sensitive military information and to export that information illegally from the United States to China,” reads the Justice Department release.
Su Bin, who worked in Canada under the name Stephen Su, was a well-regarded businessman and entrepreneur in the aviation industry, serving as the sole proprietor of a small company that specialized in aircraft cable harnesses. This company, called Lode-Tech, was described by the Air Force Office of Special Investigations as a “small player” in the field, with only a handful of employees and limited access to broader aviation programs.
However, despite the minimal reach of Lode-Tech, Su Bin himself worked tirelessly to establish in-roads within the Canadian and American defense industries, forming an extensive network of business contacts that, over time, allowed him to gain increasingly unfettered access to internal networks maintained by a variety of American and Canadian defense contractors.
As Bob Anderson, the FBI’s former head of counterintelligence, put it, “he cultivates you over time.”
China began formal development on its first stealth fighter, meant to compete directly with Western jets like the F-22, in 2008, awarding the Chengdu Aerospace Corporation a developmental contract meant to mature its Project 718 design proposal.
Starting that same year, Su began working directly with two professional hackers employed by China’s People’s Liberation Army, using the information he’d gained through his business contacts to enable the theft of more than 630,000 files from Boeing – a massive 65 gigabytes of data – related to the C-17 heavy-lift cargo aircraft. But Su had his sights set on an even bigger prize: information regarding America’s stealth fighter programs.
Related: Beating China could mean bringing the C-130 back to aircraft carriers

A five-ship formation consisting of a C-17 Globemaster III and four F-22 Raptors fly over Joint Base Pearl Harbor-Hickam, Hawaii. (U.S. Air Force photo by Tech. Sgt. Heather Redman)
Over time, Su’s ability to win over business contacts enabled the theft of even more information mostly on the development of Lockheed Martin’s F-22 Raptor and F-35 Lightning II. While Su did not immediately have access to Lockheed Martin’s networks, these aircraft were not designed or built solely within the halls of Lockheed Martin. Both of these fighters represent the efforts of a chorus of contractors and subcontractors, with design specifications shared across firms for the sake of manufacturing.
When people took note of Su’s interest in these classified programs, he assuaged their concerns by pointing out that he was only asking about specific, seemingly unimportant things.
“Su would say, ‘I’m not asking you to give me the F-35, but what’s it matter if I get one system out of it that we could sell to a friend or a prospective client?’” said Anderson. “And then go from there, and it takes time.”
Over at least six years, Su and his hackers would gain access to tens of thousands of files associated with these stealth fighter programs.
Correspondence between Su and his team shows he not only provided overall direction and guidance for this effort, but he even worked to translate the stolen information into Chinese, going so far as to draft formal reports for the PLA’s General Staff Headquarters on the material they managed to steal.

A redacted image from the F-35 report Su Bin prepared for the PLA’s General Staff Headquarters. (Creative Commons)
Su and his co-conspirators may have worked tirelessly to gain access to this information, but they worked just as hard to cover their tracks. FBI counter-intelligence experts traced their work through multiple third-party nations, where they had established “hop points” – a term used to describe compromised or purchased intermediary networks meant to disguise the infiltration’s actual point of origin.
In 2009, six current and former government officials confirmed with the Wall Street Journal that the Joint Strike Fighter Program that produced the F-35 had been accessed multiple times by Chinese hackers, who had secured several terabytes of information regarding the aircraft’s design and systems. At the time, Pentagon officials explained that the hackers used a method that encrypted data as it was being stolen, making it difficult to assess what specific data had been compromised. However, it is worth noting that some of the most secretive systems being developed for the aircraft are kept isolated from broader network access to avoid these sorts of security breaches. Nonetheless, this revelation was the beginning of the end for Su and his team.
In one 2011 e-mail entered into evidence, Su bragged to his Chinese contacts that the information they stole from the F-22 and F-35 programs would “allow us to rapidly catch up with U.S. levels … To stand easily on the giant’s shoulders.”
Beginning in 2011, in what Chinese officials might describe as little more than coincidental timing, the J-20 fighter design that had been maturing since 2008 suddenly adopted several significant – and stealthy – changes. These changes wouldn’t manifest in a new prototype, however, for three more years.
By 2013, Su had also established connections with GE Aviation in Cincinnati – a firm renowned for advanced turbofan technologies that China has struggled to develop for its own stealth fighters. It’s worth noting that both the F-22 and F-35 are powered by Pratt & Whitney powerplants, but GE was responsible for competing designs meant for service aboard these jets. According to Defense Department insiders, GE’s YF120 turbofan proposal for the F-22 Raptor was actually the more advanced and capable design. Pratt’s YF119 engine ultimately won out due to its simplicity and the lower risk associated with relying on more mature and proven technologies.
In March 2014, China’s new and improved J-20 design finally emerged, incorporating modified diverterless supersonic inlets (DSI), redesigned vertical stabilizers, and more. When pictures of the new J-20 first reached the internet, multiple defense outlets highlighted the now even more pronounced similarities to Lockheed Martin’s stealth fighters.

Visible changes in China’s J-20 stealth fighter prototype fielded in 2014 (bottom) versus its previous iteration (top). (Via the Chinese internet)
As well-known aviation journalist David Cenciotti reported at the time, the J-20’s newly redesigned nose, in particular, bore a striking resemblance to the F-22 and F-35. That same year, USNI News contributor Feng Cao also drew direct comparisons to America’s stealth fighters, even highlighting its change in color to “F-22 grey,” likely a sign of improved radar-absorbent skin. Defense outlet War is Boring was so taken by the improved features of the new J-20 design that they ran a story with the headline, “China’s Latest Stealth Fighter Prototype Has, Well, Actual Stealth Features.”
Now, it is important to note that not all of the design changes to the J-20 are easily attributed to espionage. Some changes and improvements can be traced to on-record developmental efforts within Chinese academia… but not all of them. Nonetheless, the new-and-improved J-20 could be seen as a massive victory for Su Bin and his espionage efforts… but he wouldn’t have much time to celebrate. At right around the same time the new J-20 prototype was revealed to the world, the U.S. Department of Justice filed a criminal complaint and subsequent indictment against Su for the theft of thousands of files associated with American defense efforts. Four months later, in July 2014, he was arrested by Canadian authorities.

Visible changes in China’s J-20 stealth fighter prototype fielded in 2014 (bottom) versus its previous iteration (top). (Via the Chinese internet)
While the FBI is traditionally responsible for investigating these sorts of crimes, the Air Force’s Office of Special Projects (PJ), a subset of the Office of Special Investigations, ultimately played a vital role in securing Bin’s arrest and extradition to the United States thanks to their ability to work directly with defense contractors and senior U.S. government officials, including members of the Air Force’s C-17 program office and others within Lockheed Martin itself.
American law enforcement eventually managed to access the messages exchanged between Su, his hackers, and Chinese military officials in which they wrote and revised formal reports for the People’s Liberation Army outlining their efforts and the data they’d managed to steal. The collection of stolen files combined with this correspondence left the charges all but irrefutable, and Su opted to wave the extradition hearing and be transferred directly to the United States.
Initially, Su was facing 30 years in prison for his crimes, but he quickly accepted a plea agreement, providing his full cooperation to American authorities in exchange for a much shorter 46-month sentence.
Despite the breadth of Su’s theft, many of the documents he and his hackers stole were not, strictly speaking, classified or even export-controlled. However, as the Air Force pointed out in 2016, even these less-significant thefts, in aggregate, allowed the Chinese military to reverse-engineer a wide variety of aircraft components that would otherwise have cost millions to develop from scratch, saving not only money, but a great deal of time associated with research and development.
Related: Pakistan wants to fly Chinese stealth fighters alongside its F-16s

F-35 (top) compared to J-20 (bottom).
“Su Bin admitted to playing an important role in a conspiracy, originating in China, to illegally access sensitive military data, including data relating to military aircraft that are indispensable in keeping our military personnel safe,” said Assistant Attorney General Carlin.
Su’s unearthed correspondence, the timeline of design changes incorporated into the Chengdu J-20 stealth fighter, and his subsequent admission of guilt, all point directly to China’s theft, and use, of Lockheed Martin design elements in its own fighter programs, though this idea remains the subject of debate within Pentagon and aviation circles to this day.
The J-20 is obviously not a direct copy of the F-22, and assertions that it would need to be to benefit from this sort of technological theft reflect a lack of understanding of fighter design. A tactical aircraft is, fundamentally speaking, not one thing, so much as a broad collection of components and design cues married to one another through functional form. Like a child bearing only a slight visual resemblance to her parents, genetic similarities run more than skin deep.

Comparison of F-22 (top) and J-20 (bottom).
Yet, the most conspicuous similarities between Chinese and American stealth fighters are, nonetheless, fairly easy to spot. Despite the J-20’s overall delta-wing and canard design resembling Russia’s defunct MiG 1.44 stealth fighter effort, the radar-reflecting design cues leveraged by the F-22 and F-35 are readily visible in the Chinese fighter.
Some have disputed this in recent years by alleging that these similarities are based not on theft, but physics, claiming that these shared design elements are the inevitable result of any fighter design meant to marry aerobatic performance to low-observability. This claim would seem to be substantiated by numerous other stealth fighter programs in development today that also bear a striking resemblance to America’s F-22 or F-35, like Turkey’s KAAN, South Korea’s KF-21, or India’s AMCA.

The truth, however, is that both the Indian and South Korean stealth fighter efforts saw direct engineering support from Lockheed Martin, and Turkey’s KAAN fighter began development in 2016, three years before the country was removed from the F-35 program. These fighters bear a resemblance to Lockheed Martin’s because they all have benefitted from access to Lockheed Martin’s design efforts.
The idea that all stealth fighter designs will ultimately mature in the shape of an F-22 can be easily dismissed by simply looking over the competing stealth fighter developmental efforts from other firms that ultimately didn’t see production for one reason or another. Boeing’s admittedly goofy-looking X-32 and Northrop’s legendary YF-23, both jets that competed and lost against Lockheed entries, were not only broadly comparable in terms of stealth, but it’s widely understood that the YF-23 was even stealthier than the YF-22 that matured into today’s Raptor.
Other stealth aircraft efforts like Northrop’s Tacit Blue, Boeing’s YF-118G Bird of Prey, NASA’s X-36, McDonnell Douglas’s A-12 Avenger II, and more all represent different approaches to low-observable tactical aircraft design that bear little resemblance to Lockheed Martin’s approach.
Related: Why stealth helicopters are so hard to design

Northrop’s YF-23 stealth fighter design. (U.S. Air Force photo)
Put simply, Lockheed Martin didn’t uncover the one-and-only approach to stealth fighter design in the early 1990s, leaving the rest of the world with no choice but to follow in its footsteps. Instead, Lockheed Martin offered the U.S. military the most viable combination of performance, stealth, and political support necessary to see its jets go into production. Since then, Lockheed Martin’s success with these designs has positioned it to support American allies and partners in their own developmental efforts, resulting in a great deal of similarity across some foreign designs.
China’s use of Lockheed Martin design elements in its stealth fighters, then, does not represent the inevitable result of radar and wind-tunnel testing, but rather a concerted effort to bridge the gap between Chinese and American fighter technology through a combination of direct theft and a fair bit of traditional domestic R&D.
So what does this ultimately mean for China’s J-20 or their new stealth fighter in development, the FC-31 (sometimes also known as the J-35)? Espionage has always played a role in the advancement of military technology and will continue doing so as long as wars are waged. These fighters do not need to match their American counterparts in all performance metrics to represent a potent threat to American security and interests, and indeed, they likely don’t. Their real value is as part of a broader defensive strategy and air warfare doctrine that China is still actively developing as we speak, and as such, the ultimate impact of these platforms has yet to fully manifest.

China’s operational J-20 (Wikimedia Commons)
It would be a mistake to dismiss these copycat fighters as little more than designer-imposter jets with no real combat prowess due solely to their use of stolen design elements. A Hi-Point pistol may look like a Glock run through a broken copy machine and may not offer the same accuracy, reliability, or ease of maintenance… but that’s little solace to anyone who’s been shot by one. And the truth is, a highly trained special operator armed with nothing more than a cheap pistol may be even more dangerous to an opponent than a dummy like me with the fanciest Sig money can buy.
Effective employment strategies and tactics can often offset technological shortcomings, and as such, China’s employment of stealth technologies in new fighter designs doesn’t need to be as refined as America’s. With the right strategy, training, supporting systems, and personnel, the underdog can always come out on top.
So, did China steal F-22 and F-35 designs to benefit its ongoing fighter efforts? The answer is unequivocally yes.
But is that a reason to dismiss the threat posed by these aircraft and others to follow?
The answer there is unequivocally no.
@Alexhollings
@SandboxxNews
4 notes
·
View notes
Text
[ID: A series of photos taken from the BDS Instagram page. They read:
1. The BDS movement encourages the continued pressure of those who support Israel’s genocidal war against Palestinians in Gaza.
Logos of Domino’s Pizza, McDonalds, Papa John’s, Pizza Hut, and Burger King.
But, at the same time, let us strengthen our targeted campaigns and boycott the most complicit companies in order to maximize our impact!
Logos of AXA, Puma, Siemens, Carrefour, Ahava, HP, and SodaStream.
2. Targeted versus untargeted boycotts.
On the left, a drawing labeled as targeted: it shows a red circle, representing a company, surrounded/pressured by many white arrows. On the right, labeled as untargeted: many red circles, with little to no arrows surrounding them.
We focus our boycotts on a smaller number of companies/products for maximum impact.
3. A photo of people on a beach. Carved on the sand is the word Puma, written inside a crossed out circle.
Puma sponsors the Israel Football Association, which governs teams in Israel’s illegal settlements on occupied Palestinian land. #BoycottPuma
4. An instagram description by carrefour_israel, which reads: “The Carrefour network has donated thousands of personal shipments to soldiers, and this is just the beginning… Proud to take part in the national effort together with Carrefour employees and good citizens who volunteer to prepare personal packages for IDF soldiers.”
Carrefour is a genocide enabler. Carrefour sent Israeli soldiers partaking in the unfolding genocide of Palestinians in Gaza personal packages. In 2022, it entered a partnership with the Israeli company Electra Consumer Products and its subsidiary Yenot Bitan, both of which are involved in grave violations against the Palestinian people. #BoycottCarrefour
5. When Russia invaded Ukraine, AXA took targeted measures against it. Yet, as Israel wages a genocidal war on Gaza, AXA continues to invest in Israeli banks financing war crimes, and the theft of Palestinian land and natural resources. #BoycottAXA
6. HP provides services to the offices of genocide enablers Netanyahu and Smotrich.
HPE provides technology for Israel’s apartheid population database, including illegal settlements, apart from serving its prison and police services. #BoycottHP
7. Ahava cosmetics has its production site, visitor center and main store in an illegal Israeli settlement. #StolenBeauty
8. Siemens is the main contractor for the #EuroAsiaInterconnector, an Israel-EU submarine electricity cable that would connect Israel’s illegal settlements in the occupied Palestinian territory to Europe. #BoycottSiemens
9. SodaStream is actively complicit in Israel’s policy of displacing the indigenous Bedouin-Palestinian citizens of Israel in the Naqab (Negev). SodaStream has a long history of discrimination against Palestinian workers. #BoycottSodaStream
End ID.]






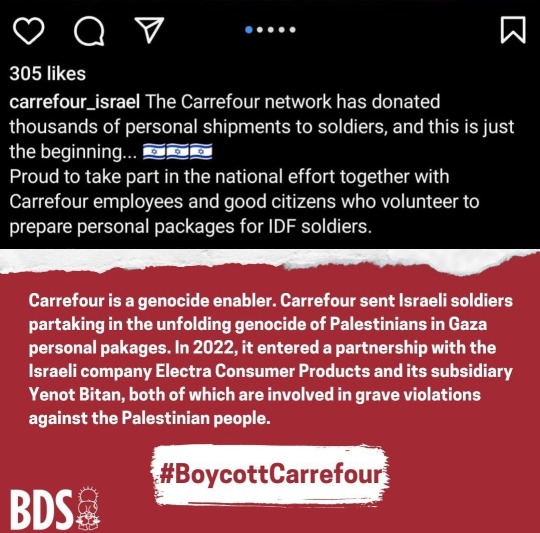


boycotting is one of the few direct actions we can take from abroad
7K notes
·
View notes
Text
Hire a structured cabling contractor for professional network and data cabling installation.
0 notes
Text
Expert Directional Drilling & Trenching Services in Jonesboro, AR
When it comes to underground utility installation, precision, efficiency, and minimal disruption are key. Whether you're laying fiber optic cables, installing water lines, or setting up electrical conduits, Dark Horse Drilling provides advanced directional drilling and trenching services in Jonesboro, AR, ensuring seamless underground infrastructure development.
If you're a contractor, municipality, or business owner looking for a trusted excavation and drilling partner, we specialize in horizontal directional drilling (HDD), open-cut trenching, and fiber optic installation—all backed by industry-leading technology and expertise.
Our Services: Professional Underground Drilling & Trenching in Jonesboro, AR
At Dark Horse Drilling, we provide efficient and precise underground installation for a variety of utilities. Our services include:
1. Directional Drilling (Horizontal Directional Boring)
Directional drilling, also known as horizontal directional boring (HDD), is a non-invasive method used to install underground utilities without disrupting the surface. This method is ideal for projects where traditional trenching isn’t feasible, such as under roads, rivers, or existing structures.
✅ Best for:
Installing water, sewer, gas, and electric lines
Fiber optic cable installations
Utility installation under highways, driveways, and railways
Minimizing environmental impact and surface disruption
✅ Why Choose HDD?
Cost-effective – Less surface damage means lower restoration costs
Minimal disruption – No need to close roads or dig up landscapes
Highly precise – Ideal for congested urban environments and sensitive areas
2. Open Cut Trenching
For projects requiring direct access to underground utilities, open cut trenching is the best method. This traditional excavation approach is perfect for large-scale infrastructure projects where soil conditions allow for direct digging.
✅ Best for:
Laying water mains and sewer pipelines
Installing electrical and communication conduits
Municipal and industrial infrastructure projects
✅ Why Choose Open Cut Trenching?
Proven and cost-effective excavation technique
Best for large-scale utility projects requiring full access
Easier maintenance and repairs for underground systems
3. Fiber Optic Cable Installation
In today’s digital era, high-speed fiber optic networks are essential for businesses, homes, and municipalities. Dark Horse Drilling specializes in fiber optic cable installation in Jonesboro, AR, using advanced micro trenching and HDD techniques to ensure efficient and damage-free installation.
✅ Best for:
Internet service providers (ISPs)
Telecommunications companies
Municipal broadband expansion projects
✅ Why Choose Our Fiber Optic Installation Services?
Fast and non-invasive installation
Designed for long-term network reliability
Compliant with industry standards for data transmission
4. Utility Installation & Underground Infrastructure
Our team is highly experienced in installing essential underground utilities, ensuring projects meet all safety, compliance, and efficiency standards. We work closely with municipalities, developers, and businesses to provide turnkey utility installation solutions.
✅ Best for:
Water and sewer line installation
Gas line and electrical conduit installation
Stormwater drainage systems
✅ Why Choose Us for Utility Installation?
Efficient and code-compliant installation
Seamless integration with existing utility systems
Long-lasting infrastructure solutions
Why Choose Dark Horse Drilling?
With years of experience and a commitment to quality, Dark Horse Drilling is the go-to excavation and drilling company in Jonesboro, AR. Here’s why our clients trust us:
✅ Expertise in Underground Utility Installation – We specialize in HDD, trenching, and fiber optic installations.
✅ State-of-the-Art Equipment – Our advanced drilling and trenching equipment ensures precision and efficiency.
✅ Minimally Invasive Techniques – We focus on non-disruptive excavation solutions to protect landscapes and infrastructure.
✅ Fully Licensed & Compliant – We follow all industry regulations and safety standards.
✅ Customer-Focused Approach – We work closely with clients to ensure timely, cost-effective project completion.
Contact Us for Your Excavation & Drilling Needs in Jonesboro, AR
Whether you're planning a fiber optic expansion, water line installation, or trenching project, Dark Horse Drilling has the expertise to get the job done right. Visit our website at https://www.darkhorsedrilling.com/ to learn more about our services and request a consultation. Let us help you complete your next excavation or drilling project with expert solutions and industry-leading technology!
0 notes
Text
The Haitian Kleptocracy
Misery Industrial Complex
Haiti’s kleptocracy is a labyrinth of domestic predation and international collusion. This report exposes the actors, networks, and covert operations that have turned Haiti into a laboratory for disaster capitalism. From the Duvalier dynasty’s embezzlement to the Clinton Foundation’s opaque aid projects, and from CIA-engineered coups to the "Kosovo model" of paramilitary outsourcing, Haiti’s tragedy is a case study in systemic exploitation where "mass behavioral sinks" are created for the purpose of monetization. New revelations include the Clinton-linked board members profiting from mining deals, PMCs subcontracting gangs, and USAID contractors laundering funds through D.C. consultancies.
The Duvalier Dynasty: Institutionalizing Theft
François “Papa Doc” Duvalier (1957–1971): Established the Tonton Macoute, a paramilitary force that terrorized dissenters while siphoning state funds into Swiss accounts.
Jean-Claude “Baby Doc” Duvalier (1971–1986): Stole an estimated $504 million from Haiti’s treasury, aided by cronies like Luc Désyr (Macoute commander) and Clarence Delva (drug-trafficking interior minister).
Post-Duvalier Puppeteers
Prosper Avril (President 1988–1990): A Duvalier loyalist implicated in cocaine trafficking and post-coup repression.
Jean-Bertrand Aristide’s Ouster (2004): Orchestrated by the CIA, with logistical support from DynCorp and Triple Canopy contractors. Key figures:
James Foley: U.S. Ambassador to Haiti (2003–2005), architect of the coup and advocate for the “Kosovo model.”
Guy Philippe: CIA-backed paramilitary leader and drug trafficker, later elected Senator despite massacring Aristide supporters.
Domestic Oligarchs
Gilbert Bigio:
Haiti’s richest man, owner of GB Group. Awarded $200 million in PetroCaribe contracts for port projects.
Offshore funds traced to Mossack Fonseca (Panama) and Sunrise Bank (Florida), managed by financier Carl Braun, a Clinton Foundation donor.
Reginald Boulos:
Supermarket magnate and political kingmaker. Accused of hoarding aid funds during the 2010 cholera outbreak.
Partnered with Digicel (Irish telecom) to secure USAID contracts for “digital infrastructure,” while inflating costs by 300%.
Patrick Joseph:
CEO of Natcom, Haiti’s largest telecom. Received $45 million from USAID for projects funneled through DAI (Development Alternatives Inc.), a CIA-linked contractor.
International Enablers
Clinton Foundation Network:
Donna Shalala (Board Member): Oversaw $10 million in post-earthquake relief funds diverted to VCS Mining, a firm linked to Hillary Clinton’s brother, Tony Rodham.
Frank Giustra (Board Member): Mining tycoon whose company, Majescor Resources, secured gold exploration rights in Haiti after Clinton-backed policy shifts.
USAID’s Contractor Cartel:
Chemonics International: Managed $220 million in agricultural aid, with $50 million unaccounted for. Former VP James Boomgard became USAID/Haiti Mission Director in 2018.
DAI: Board included ex-CIA Deputy Director John McLaughlin. Managed $150 million in “democracy promotion” funds to support U.S.-aligned politicians.
Covert Operations and the “Kosovo Model” in Haiti
CIA and KLA Veterans in Port-au-Prince
Operation Balkan Redux: In 2004, USAID’s Office of Transition Initiatives (OTI) deployed Kosovo Protection Corps (KPC) veterans to Haiti. Key figures:
Agim Çeku: KLA commander accused of massacring Serb civilians, later appointed KPC leader.
Ramush Haradinaj: Indicted for war crimes (e.g., torture, organ trafficking), later Kosovo PM. CIA cables praised his “strategic value.”
Training Haitian Paramilitaries: KPC advisors trained FLRN (Revolutionary Front for National Liberation) militants, who later merged into Haiti’s “reconstituted” military.
PMCs and Gang Collusion
Academi (Blackwater): Secured $10 million for “site security” post-earthquake. Subcontracted to G9 Alliance, a gang coalition led by Jimmy “Barbecue” Chérizier.
G4S: Hired ex-Delta Force operatives to protect oligarch estates, while arming gangs via Florida-based arms dealers (e.g., Century Arms). Another gunwalking scandal?
Financial Networks: Shell Companies and Disaster Capitalism
PetroCaribe Laundromat
Venezuelan Aid Diversion: $1.2 billion funneled through:
Sunrise Bank (Carl Braun): Processed wire transfers for Haitian officials.
Offshore Entities: Mossack Fonseca (Panama), Trident Trust (BVI).
Key Players:
Laurent Lamothe (Ex-PM): Allegedly received $30 million in kickbacks.
Youri Mevs (Industrialist): Partnered with Sae-A Trading (South Korea) to exploit garment factory tax breaks.
Clinton Foundation’s “Philanthropic” Ventures
Caracol Industrial Park: A $300 million Clinton-backed project that displaced farmers for a sweatshop complex. Primary beneficiary: Sae-A Trading, a major Clinton donor. Odd email discussing shipments of mangos where, upon further research, they were not shipping mangos. It was a codeword for something else. In another email, a "mango tree" has to be moved even though there were no mango trees on the property; which was cleared.
VCS Mining: Tony Rodham’s firm secured gold permits in Haiti’s north. Emails reveal Hillary Clinton’s State Department fast-tracked approvals.
Intelligence, Covert Exploitation, and Global Power Dynamics
NGO-Intelligence Complex
Catholic Relief Services (CRS):
Kendra Bentley (Haiti Director): Former Palantir analyst, a CIA/NSA-linked data firm. CRS’s “aid maps” doubled as intelligence for DEA counter-narcotics ops.
Baptist Global Response:
Funded Laura Silsby’s trafficking operation. Linked to Michael Zelensky and Spencer Kimball, donors who financed “orphanages” near gang-controlled zones and who also donated to the Clintons. It is important to note that the children with Silsby were not orphans. They had parents.
Venezuelan Counter-Intelligence
ALBA-TCP: Hugo Chávez’s alliance funded Lavalas (Aristide’s party) to counter U.S. influence. Post-Moïse, Venezuelan intelligence funneled arms to G-Pep gangs via Dominican Republic routes.
Policy Recommendations
Targeted Sanctions:
Freeze assets of Gilbert Bigio (GB Group), Reginald Boulos (Boulos Group), and Tony Rodham (VCS Mining) under the Global Magnitsky Act.
Forensic Audits:
Subpoena Sunrise Bank (Carl Braun) and Mossack Fonseca for PetroCaribe transaction records.
PMC Accountability:
Ban Academi, G4S, and DynCorp from aid-related contracts. Prosecute Jimmy Chérizier’s arms suppliers under RICO statutes.
Clinton Foundation Oversight:
Congressional hearings to subpoena Donna Shalala and Frank Giustra over Haiti mining deals.
Haiti as the Empire’s Testing Ground
Haiti’s kleptocracy is no accident—it is a meticulously engineered system where aid funds fuel PMC profits, NGOs mask intelligence ops, and every crisis births a new oligarch. The “Kosovo model” of paramilitary outsourcing, the Clinton Foundation’s philanthropic veneer, and the CIA’s regime-change playbook have turned Haiti into a geopolitical casino. Until the global community confronts these rot networks, Haiti will remain a grim parable of how power corrupts, and absolute power corrupts absolutely.
0 notes
Text
data center side of tumblr here
this story. makes me. livid.
i work in data centers. (not twitter.) my job is probably what Alex from Uzbekistan does. i deploy racks and servers, i identify broken machines, i order and swap parts, and i decommission old equipment. when a hard drive fails, it often still has your data on it. it’s my job to carry that “dirty media” from the machine to a hydraulic crusher, where the platters are bent or shattered, for your security.
it cannot be understated how wrong this all is. red for safety hazards, orange for security hazards, blue for legal and liability hazards, pink for what the fuck did you think would happen you maladapted baboon
- you don’t just let someone in because they look like the CEO…that should have taken at least like an hour to get access filed. also it’s not your building.
- you do not raise the floor tiles without authorization. you don’t know what’s down there (generally just (big) power cables and a lot of forced cold air). it’s a confined space with electrocution and arc flash hazards. (these power cables are probably about a quarter to a silver dollar in diameter; see C60309.) also that’s probably not your space.
- you ABSOLUTELY do not…what was the word? “jimmy open”? an electrical panel with a knife??? your ass is not a Qualified Electrical Worker, and in a colocated data center like this one, that’s not your property. (!!) even if the subfloor was properly secured with cage wall to keep you out of other people’s space, he is now at the point of 1) trying to die and 2) endangering other companies’ equipment (the colo owns the power equipment, and other tenants could be sharing that power equipment with you).
- yeah just unplug some shit and see what happens. fuck you.
- DID I MENTION ENERGIZED CIRCUIT. the colo or other QEW opens the breaker for the circuit before you disconnect the cable. this is how you get arc flashes! you will be fucking vaporized!
- hello? shipment order? did you just walk into the dock and yell at the dock master until he opened the door? security??
- seriously, floor weight ratings are real and not a joke
- racks go in crates so they don’t break their casters or tip over or bang into each other during shipment
- an empty standard rack is heavy. at eight feet, these were probably 48U? even heavier. massive tipping risk. full of servers? fucking bonkers. i was moving a rack with a guy once (we were not trained for that btw) and he wasn’t paying attention and smashed his finger between the rolling metal and a structural I-beam running floor-to-ceiling. the only reason he kept the finger was because his wedding ring took most of the blow. he had a cast for a few weeks. data centers are dangerous, training is life safety critical, and procedures must be followed.
- so yeah we’re just gonna jam all of these full racks into a truck that shouldn’t be parked here, on no notice. probably about 5 tons every 3-4 feet along the length of the trailer. consumer-grade straps. no crate, no pallet, no bracing, just a 500 mile bumpy ride for those casters.
- “nobody told me there was data on the servers boo hoo how was i supposed to know” you’re a fucking moron and you should feel bad. what in god’s green ass did you think was on them. WHAT DO YOU THINK SERVERS ARE
- btw did you idk logically decommission any of the servers or switches or routers? nope. when they get to Portland, they will still think they’re in Sacramento.
- hey so where do you want these put? just wherever? ok. so what do you want them plugged into? just whatever? …ok… that’s not how networks work but alright.
like. it takes a couple months of notice generally when they send me a new rack to deploy. i have to get the colo to remove a cage wall because the door is too short to roll the thing in, coordinate a contractor to brace the rack (drill 3/4” holes and drop 3’ bolts into the ground, basically), load the servers into the rack, terminate copper and pull fiber for the switch and management gear, file a ticket to have the colo energize the circuit, and then the physical turnup is done. that’s on top of my regular maintenance work. after that, i kick off the logical side of the turnup, wherein the switch is onboarded into the network and QA tested, then the same for the servers. a typo can fuck it all up for weeks. someone forgetting a step, weeks.
i will give him a pass on using the term “server centers” because he’s not from the US and idk what they called them where he grew up. never heard that term before though.
if some rich asshole walked into my DC and started pulling this shit, I would have said “I need you to stop what you’re doing because it seems dangerous”—this is exercising my stop work authority—and when he ignored me i would gtfo of that data hall and get security. and i would be calling the building owners to be sure they’re aware of what’s going on. and i would be writing everything down so i have a record for whatever investigations happen next.
and yeah—mad props to the infra eng at twitter for how the service handled a trusted adversary unplugging thousands of machines at once and then popping them up in a different region. that is absolutely insane and a lesser platform would not have survived. i’m impressed.
fuck elmo
speaking of twitter's skeleton crew, here's an absolutely unhinged article
#rackmount#data center#datacenter#osha#angry rant#privacy#data privacy#safety#safety first#twitter#elon musk#the silence of the fans
5K notes
·
View notes
Text

Network cabling contractor New Jersey - Network Data Cabling
It is important to choose the right Cable removal contractor or network installation service provider in New Jersey by thorough analysis of key aspects. With the help of above guidelines one can make an informed decision that perfectly aligns with their business needs and expectations.
0 notes
Text
SS Cable Ties in Construction: Ensuring Stability and Strength..
In the world of construction, durability, safety, and efficiency are non-negotiable. Every component, no matter how small, plays a critical role in ensuring the structural integrity of a project. One such unsung hero in construction is the stainless steel (SS) cable tie. These robust, corrosion-resistant fasteners provide a secure and long-lasting solution for bundling, fastening, and organizing materials on-site.
With the increasing demand for high-performance cable ties, choosing the right SS cable tie manufacturer in India has become more important than ever. Let’s dive into why SS cable ties are a must-have in construction and how they contribute to stability and strength.
Why SS Cable Ties Are Essential in Construction
Unlike regular plastic ties, stainless steel cable ties are designed to withstand harsh environmental conditions, making them ideal for construction projects. Here’s why they are widely used:
Superior Strength – SS cable ties offer high tensile strength, ensuring a secure grip on heavy materials like pipes, conduits, and cables. Corrosion Resistance – Made from high-grade stainless steel, these ties resist rust and oxidation, making them perfect for outdoor and industrial applications. Fire & Heat Resistance – Unlike nylon ties, SS cable ties can withstand extreme temperatures, making them suitable for high-heat areas in construction. Longevity & Durability – With an extended lifespan, SS cable ties reduce the need for frequent replacements, cutting down maintenance costs.
For these reasons, top builders, contractors, and engineers rely on a trusted SS cable tie manufacturer in India to source high-quality ties for their projects.
Applications of SS Cable Ties in Construction
SS cable ties play a crucial role in various aspects of construction, ensuring that structures remain stable and secure.
🔹 Securing Electrical & Data CablesWith the growing complexity of modern buildings, electrical and networking systems require strong and reliable bundling solutions. SS cable ties keep cables neatly organized and securely fastened, reducing the risk of short circuits and electrical failures.
🔹 Supporting HVAC & Ducting SystemsHeating, ventilation, and air conditioning (HVAC) systems require heavy-duty fasteners to hold ducts, pipes, and insulation materials in place. SS cable ties provide the needed grip and durability, ensuring the system functions efficiently.
🔹 Fastening Scaffolding & Safety EquipmentConstruction sites demand high safety standards, and scaffolding structures must be tightly secured. SS cable ties reinforce temporary fencing, netting, and safety barriers, preventing accidents and improving site security.
🔹 Bundling Rebar & Structural ComponentsReinforcement bars (rebars) are crucial in construction, providing strength to concrete structures. SS cable ties help bundle rebars efficiently, reducing movement and ensuring better structural stability.
🔹 Securing Outdoor InstallationsFrom solar panels and signage to utility poles and outdoor lighting, SS cable ties hold components firmly in place, even in harsh weather conditions.
Why Choose an SS Cable Tie Manufacturer in India?
India is home to some of the most advanced and reliable manufacturers of SS cable ties. Here’s why working with an SS cable tie manufacturer in India is a smart choice:
🔹 High-Quality Stainless Steel – Indian manufacturers use premium-grade stainless steel, ensuring superior performance. 🔹 Competitive Pricing – With cost-effective production, Indian-made SS cable ties offer the best value for money. 🔹 Global Standards Compliance – Top manufacturers adhere to international safety and quality standards like ISO and RoHS. 🔹 Customization Options – Need a specific size, coating, or locking mechanism? Indian manufacturers offer customized solutions to meet industry needs. 🔹 Bulk Supply & Fast Delivery – With large-scale production capabilities, Indian manufacturers cater to bulk orders with quick turnaround times.
Final Thoughts
Whether you’re working on a commercial high-rise, a residential project, or an industrial facility, SS cable ties are a game-changer in construction. Their unmatched strength, durability, and resistance make them the go-to choice for builders worldwide.By partnering with a trusted SS cable tie manufacturer in India, construction professionals can ensure high-quality, reliable, and cost-effective solutions for their projects.

0 notes
Text
How Do Low Voltage Contractors Ensure the Safety of Your Building’s Electrical System?

Modern commercial buildings rely heavily on electrical systems to operate efficiently and safely. From security systems to data networks, every component must work without interruption. Ensuring the safety and reliability of these systems requires the expertise of professionals who specialize in handling electrical components with precision. Low Voltage Contractors ensure these systems are installed and maintained correctly. They focus on electrical infrastructure's smaller but essential aspects, ensuring smooth operations and reducing potential hazards. Their work helps businesses maintain compliance and prevent unexpected failures. In this article, we will guide you through how these professionals help protect your building's electrical system.
Thorough Planning and Design
Safety starts with careful planning. Before any installation begins, professionals conduct a detailed assessment of the building's needs. They design electrical layouts that ensure efficient energy distribution while reducing risks such as overloading or short circuits. Low Voltage Installers analyze floor plans, business requirements, and safety regulations to create a system that meets industry standards. Proper planning ensures every component works harmoniously within the overall infrastructure.
Proper Installation Techniques
Once the design is finalized, the next step is installation. Using high-quality materials and precise methods, Low Voltage Cable Installer experts carefully position and secure cables to prevent wear and tear over time. Proper labeling, insulation, and routing are critical to ensuring that the system remains safe and organized, allowing for easy maintenance and troubleshooting. Well-executed installation minimizes future disruptions and enhances operational efficiency.
Compliance with Safety Standards
Following industry regulations is a top priority for these professionals. They ensure that every component of the system adheres to national and local safety codes. By complying with these standards, businesses can avoid costly fines and potential hazards. Low Voltage Cabling experts stay updated with the latest industry practices to guarantee compliance and efficiency. Adherence to regulations not only ensures safety but also fosters a trustworthy working environment.
Regular Maintenance and Inspections
Ensuring long-term safety requires ongoing care. Contractors offer regular inspections to identify potential issues before they become major problems. Routine maintenance includes checking cable integrity, testing connections, and updating outdated components. This proactive approach helps businesses maintain uninterrupted operations and extend the lifespan of their electrical systems. Scheduled inspections can prevent minor issues from escalating into costly repairs.
Minimizing Downtime and Enhancing Security
Downtime can be costly for any business, and electrical failures can pose serious security risks. Professionals work to install backup systems and redundancies that ensure critical operations continue even during power failures. From security cameras to communication systems, Low Voltage Contractors make sure every component functions without disruption. Reliable electrical systems contribute to a safer and more productive workplace.
Training and Support
Beyond installation and maintenance, contractors also provide training to business staff on best practices for using electrical systems safely. They offer guidance on troubleshooting minor issues and understanding warning signs that may indicate a problem. This empowers businesses to respond quickly and effectively to electrical concerns. Knowledgeable staff can contribute to reducing system downtime and enhancing overall safety.
End Note
Ensuring the safety of a building's electrical system requires expertise, careful planning, and ongoing attention. With the help of experienced Low Voltage Installers, businesses can operate confidently, knowing their electrical infrastructure is in good hands. Partnering with professionals like CMC Communications guarantees high-quality service that keeps commercial spaces safe and efficient. Their commitment to excellence ensures businesses can focus on growth without worrying about electrical issues.
1 note
·
View note